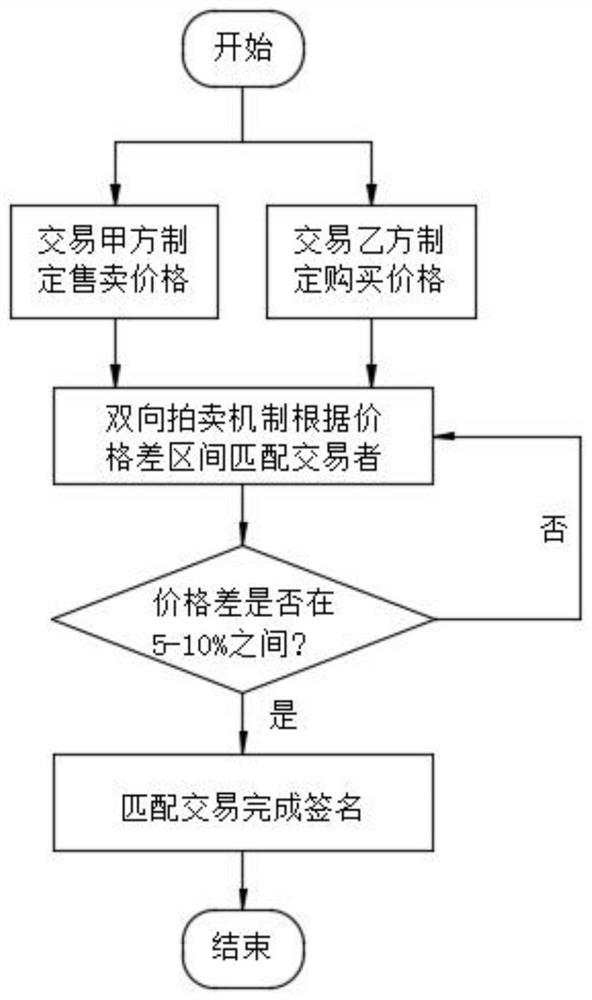
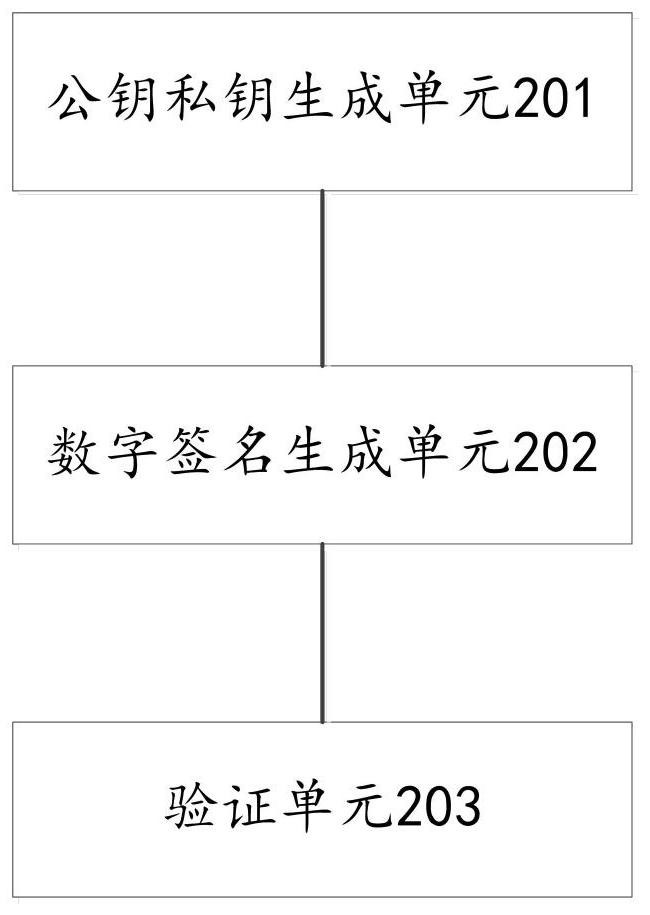
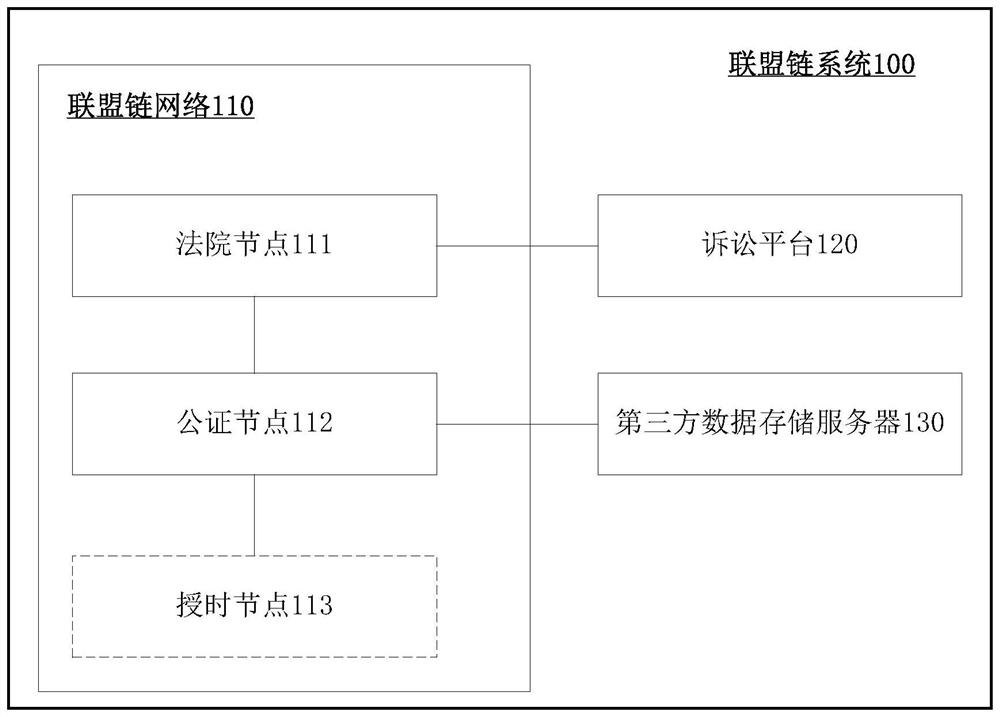
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
109results about How to "Will not be tampered with" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
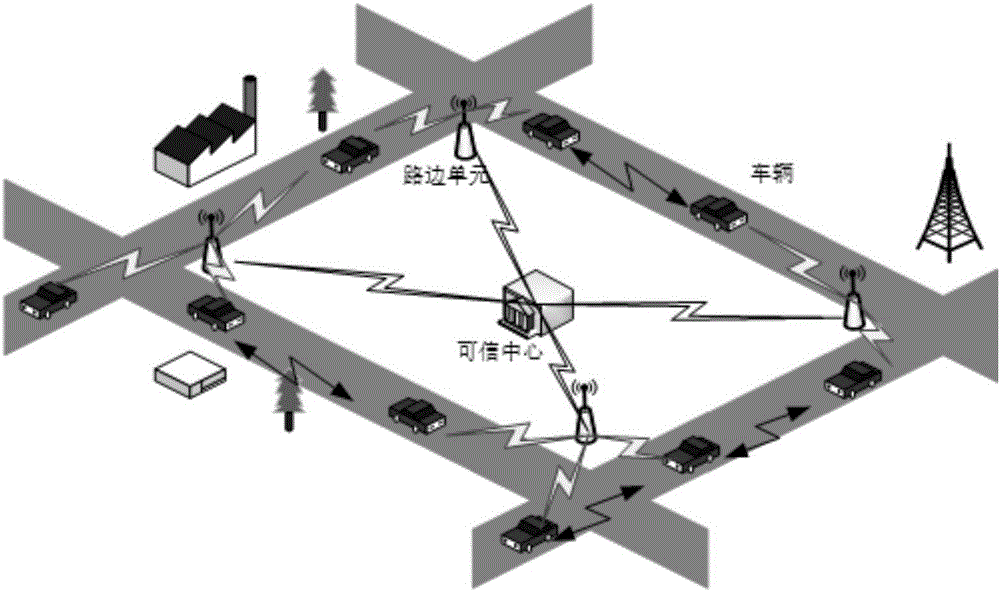
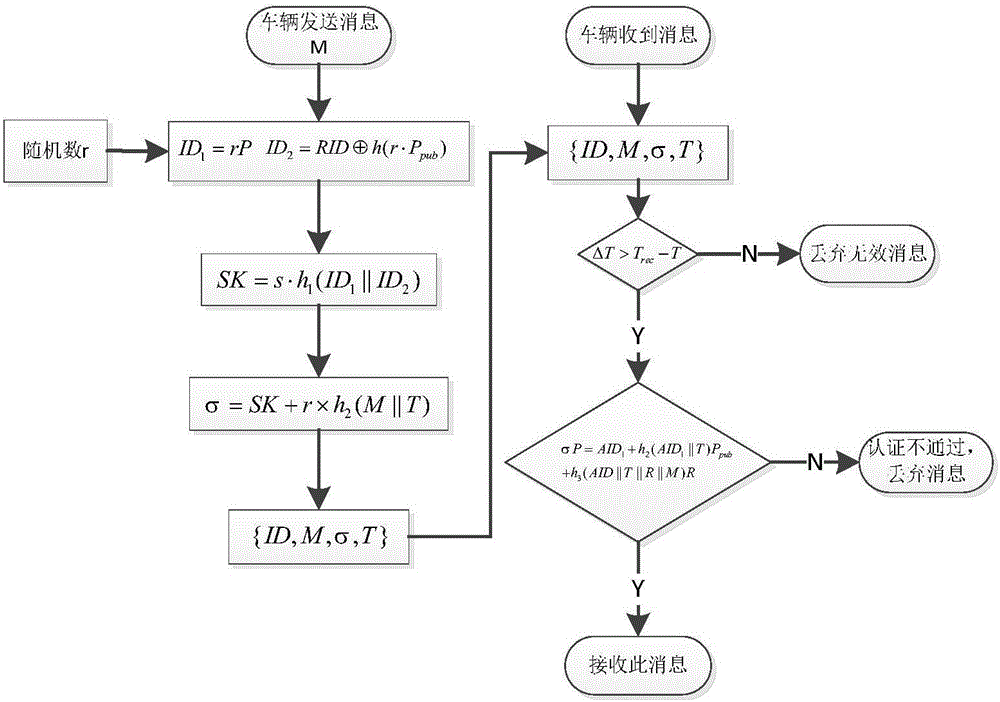
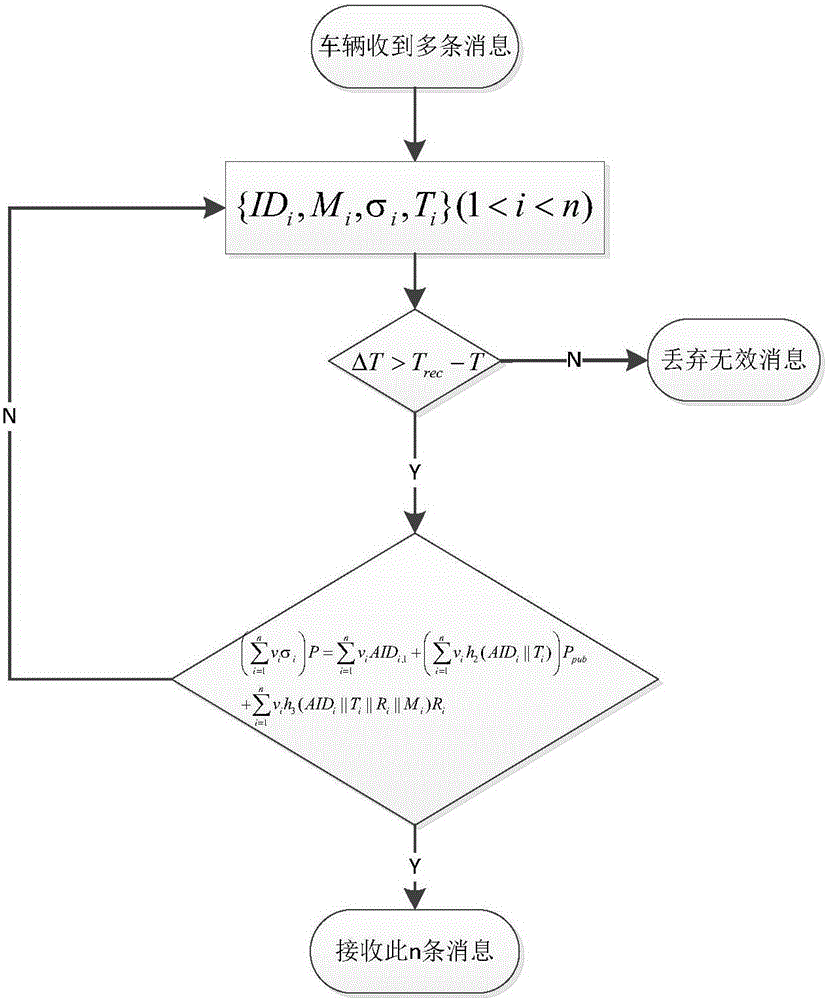
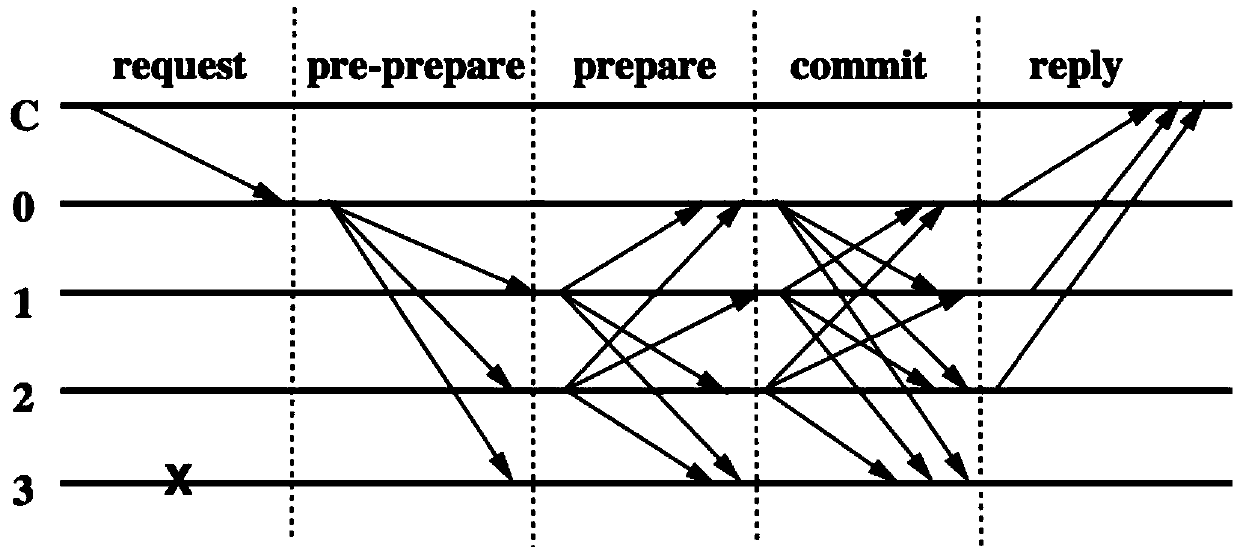
Efficient condition privacy protection and security authentication method in internet of vehicles
ActiveCN106027519AReduce computational overheadWill not be tampered withKey distribution for secure communicationPublic key for secure communicationOn boardThe Internet
The invention discloses an efficient condition privacy protection and security authentication method in an internet of vehicles. The efficient condition privacy protection and security authentication method comprises the following steps of: system initialization, generation of pseudonym identities and signature private keys of vehicles, signing and authentication of a message and tracing of real identities of the vehicles. The vehicles carry out cooperative communication with surrounding vehicles and roadside units deployed at both sides of a road by on-board units assembled on the vehicles, driving security of the vehicles can be effectively improved, and vehicle users can more conveniently and rapidly acquire related traffic services. The efficient condition privacy protection and security authentication method disclosed by the invention not only can meet security requirements in the internet of vehicles, but also optimizes the computing process of signature generation and verification in the communication. The efficient condition privacy protection and security authentication method is greatly improved on the aspect of efficiency of computing cost, communication cost and the like, and is more applicable to communication and application in the internet of vehicles.
Owner:ANHUI UNIVERSITY
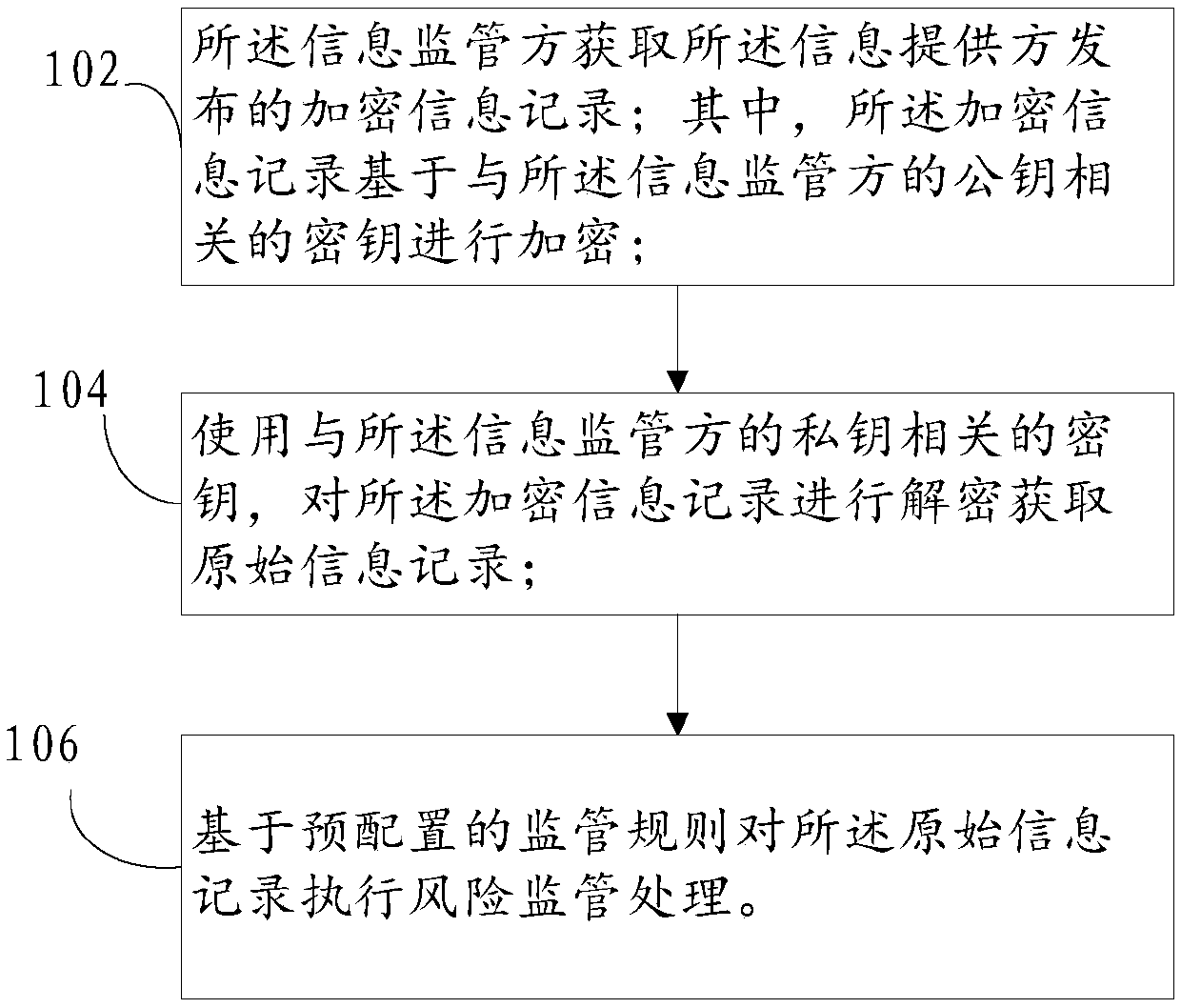
Block chain-based information supervision method and device
ActiveCN108681966AEnsure safetyGuaranteed authenticityFinanceDigital data protectionInformation provisionInformation providers
The specification provides an information supervision method and device, and is used for an information supervisor to supervise information provided by an information provider. The information supervisor and the information provider are set to be nodes of a block chain; the information supervisor obtains an encrypted information record issued by the information provider, wherein the encrypted information record is encrypted based on a key associated with a public key of the information supervisor; the encrypted information record is decrypted to obtain an original information record by using akey related to a private key of the information supervisor; and risk supervision processing is executed on the original information record based on pre-configured supervision rules.
Owner:ADVANCED NEW TECH CO LTD
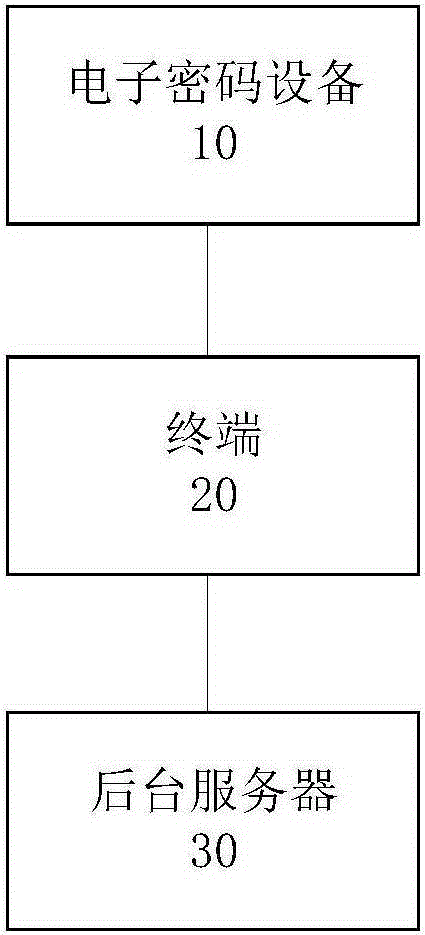
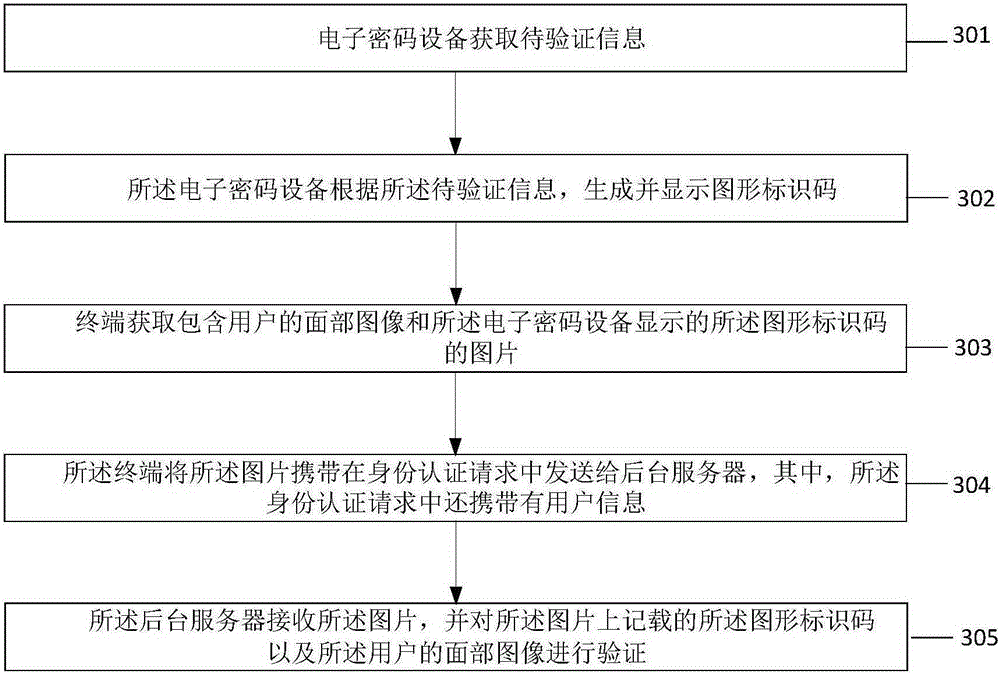
Remote identity authentication method and system and remote account opening method and system
ActiveCN105245341AGuaranteed non-repudiationWill not be tampered withUser identity/authority verificationDigital data authenticationGraphicsComputer terminal
The invention provides a remote identity authentication method and a system and a remote account opening method and a system. The remote identity authentication method comprises steps: electronic cipher equipment acquires to-be-authenticated information, a graph marking code is generated and displayed according to the to-be-authenticated information, a terminal acquires a picture comprising a facial image of the user and the graph marking code displayed by the electronic cipher equipment, the picture is sent to a backstage server, the backstage server receives the picture, and the graph marking code and the facial image of the user recorded on the picture are authenticated.
Owner:TENDYRON CORP
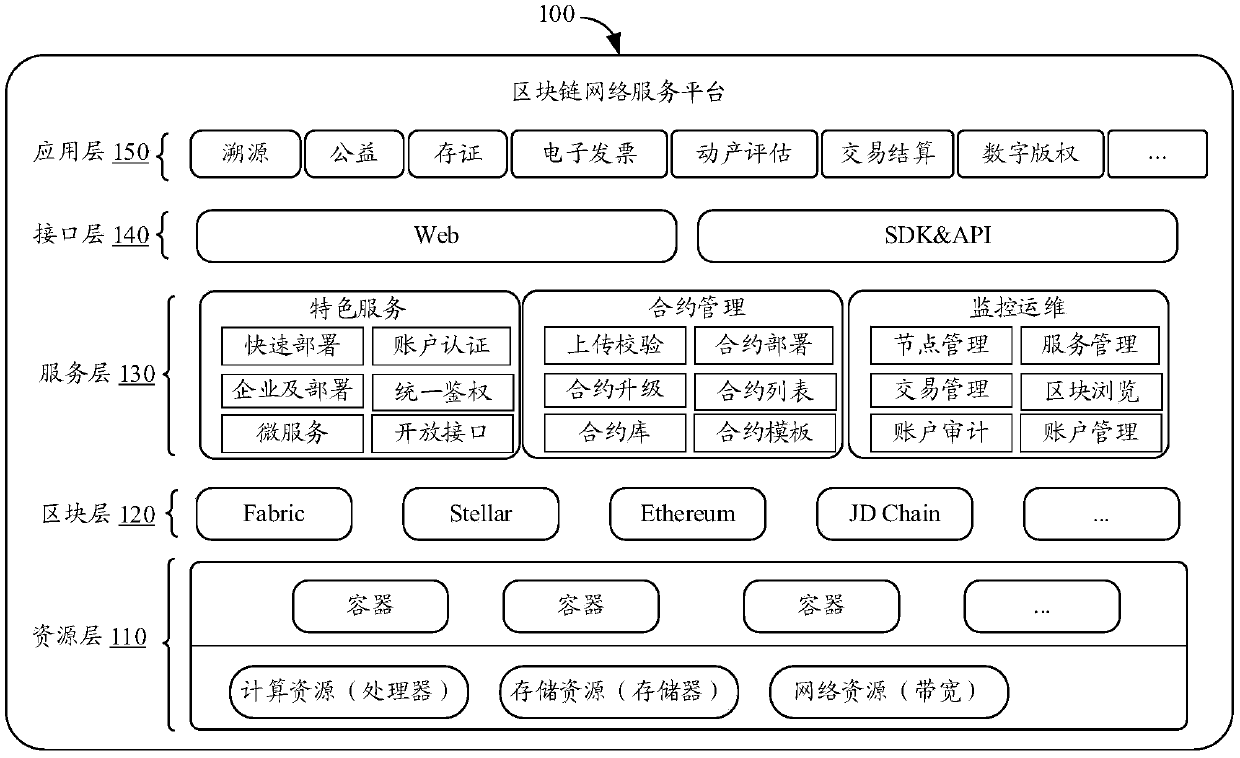
Key generation methods, block chain network service platform and memory medium
PendingCN109617699AAvoid certificate queriesAvoid queryKey distribution for secure communicationUser identity/authority verificationChain networkBlockchain
Owner:BEIJING WODONG TIANJUN INFORMATION TECH CO LTD
User identity certificate storage and verification method and device based on block chain and verification system
ActiveCN109889479AGet goodWill not be tampered withDigital data protectionDigital data authenticationValidation methodsUser identifier
The invention discloses a user identity certificate storage and verification method and device based on a block chain and a verification system. The user identity certificate storage method based on ablock chain comprises the following steps: distributing a user identifier for representing a user identity to a user according to a storage request, wherein the unique private key and the unique public key are associated with the user identifier; obtaining identity information of a user, performing Hash calculation on the identity information of the user to generate a digital fingerprint, sendingthe digital fingerprint to a block chain, encrypting a user identifier, the identity information of the user, a storage identifier of a block chain distribution user and the digital fingerprint according to a unique private key, and generating a user identification code representing the identity information. By implementing the method and the device, the identity information of the user is storedby utilizing the identity information storage platform on the basis of the blockchain technology, so that the stored identity information cannot be tampered once the stored identity information is online, the credibility of the electronic identity storage information is enhanced, and meanwhile, the identity information is acquired more conveniently and quickly.
Owner:中积教育科技有限公司
Method and device for processing communication charging
ActiveCN107294738AWill not be tampered withGuaranteed correctnessMetering/charging/biilling arrangementsAccounting/billing servicesBlockchainCurrent time
The invention provides a method and a device for processing communication charging. The method comprises: according to a charging strategy of each communication service, generating a charging strategy block; sending the currently generated charging strategy block to each user terminal node; according to expense recorded information of each communication service of each user terminal node in a preset time period, generating a user phone bill block; sending the currently generated user phone bill block to each user terminal node, to make the user terminal node identify the user phone bill block; according to an identification result sent by each user terminal node, when the currently generated user phone bill block is determined to be correct, generating a charging bill according to the charging strategy block and the user phone bill block. The chain mode of the charging strategy block and the user phone bill block ensures that a charging strategy in current time and information in a user phone bill would not be tampered. The user terminal node can identify information in the user phone bill block, so that a user terminal knows whether communication charging has faults.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Method and equipment for medical image data decentralized management based on block chain
ActiveCN109243583AHigh transparencyGood for long term storageDigital data protectionMedical imagesFile systemSmart contract
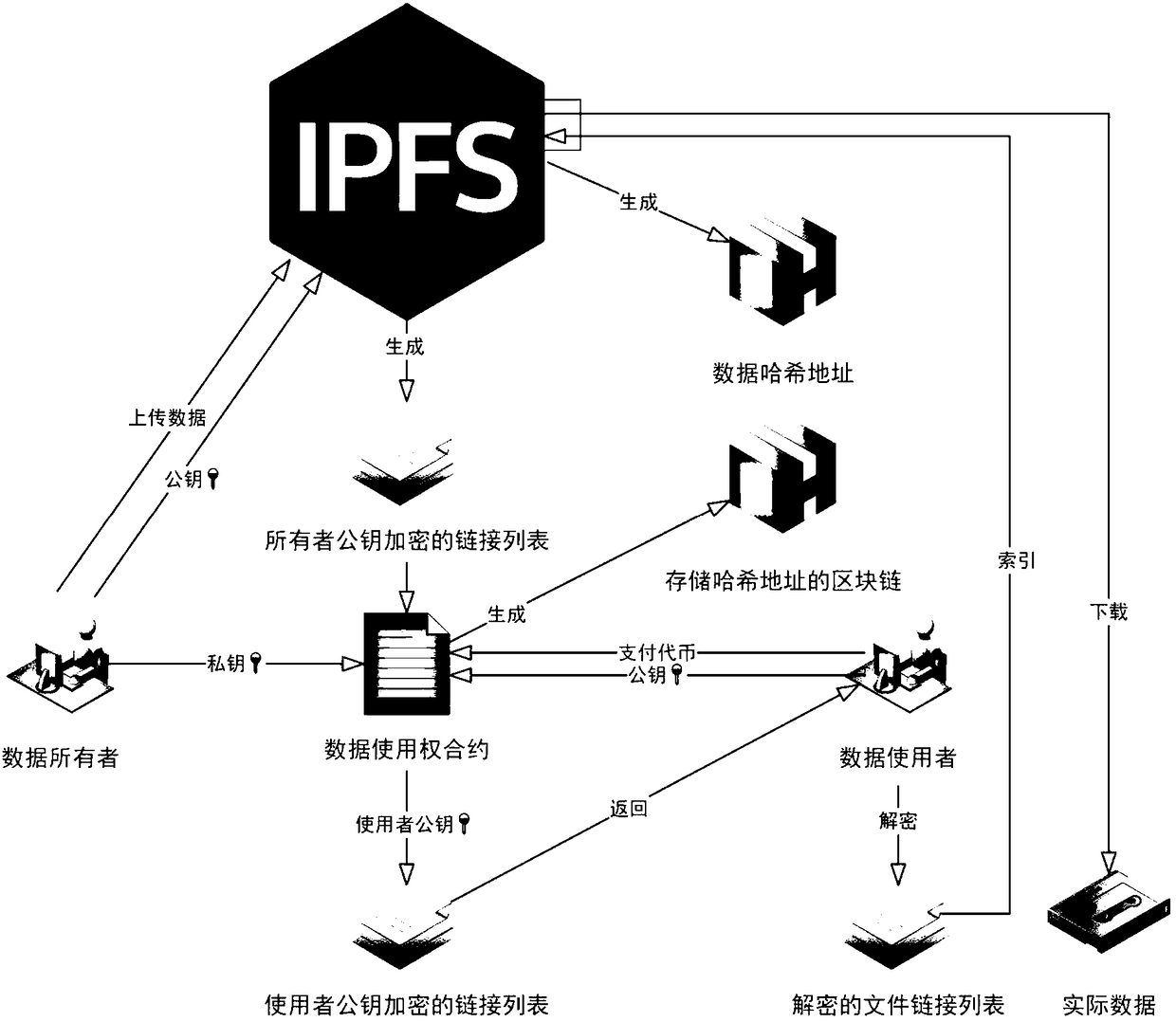
The invention relates to a method for medical image data decentralized management based on a block chain. The data owning end uploads the owned medical image data stores the medical image data as an interstellar file system (IPFS) file, the hash value for the medical image data is taken and the link list file in the IPFS is encrypted by using the public key of the data owning end; the data accesscontract uses the private key of the data owning end to decrypt the encrypted link list file in the step according to the smart contract, and when the data use end transmits the data use end public key information and the payment tokens to the data access contract to request for obtaining the medical image data, the data access contract uses the user public key to encrypt the decrypted link list file again to be transmitted to the data use end and also generates the block chain storing the hash address; and the data use end performs decryption operation through the data use end private key toobtain the link list file and retrieves the interstellar file system to obtain the actual medical image data.
Owner:上海全景医学影像诊断中心有限公司
Cyclic writing method and system of data on the basis of block chain
InactiveCN106446705AWill not be tampered withControl volumeInput/output to record carriersDigital data protectionOriginal dataChain system
The invention discloses a cyclic writing method and system of data on the basis of a block chain. Before new data is written into the block chain, whether data stored in a block chain database meets a preset trigger condition or not is judged, the new data is written to cover and destroy original data under a situation that a preset condition is met, and usefulness data can be destroyed while the volume of the block chain is effectively controlled. The data is stored into the block chain database to guarantee that data is not tampered and can be safely stored, in addition, a cyclic writing way is adopted to effectively control the volume of the block chain database, the data which meets the preset trigger condition is not displayed in a block chain system and is covered and destroyed by the new data, privacy and privacy are good, the storage of a hash value corresponding to a data block also can guarantee to verify whether the downloaded data is correct or not, and the cyclic writing method and system is safe, convenient and high in practicality.
Owner:杨鹏
Trusted intelligent salary paying method and system based on blockchain
InactiveCN108776890AExpand application scenarios and scopeImprove securityPayment architectureOffice automationHuman errorSmart contract
The invention provides a trusted intelligent salary paying method and system based on blockchain. The method and system are based on Ethereum (ETH), and employ the solidity language for writing an intelligent contract. After the intelligent contract is deployed on the blockchain, the method and system achieve the interaction between a user and the salary information of employees through the calling of the intelligent contract. The method and system have the following advantages that 1, the characteristic of blockchain decentration enables data not to be tampered; 2, the charging characteristicof the Ethereum (ETH) prevents a DDos attack; 3, the salary payment is automatically completed by a system, thereby avoiding the possible loss caused by human errors.
Owner:QINGDAO UNIV
Credit data storage method and device based on block chain, equipment and medium
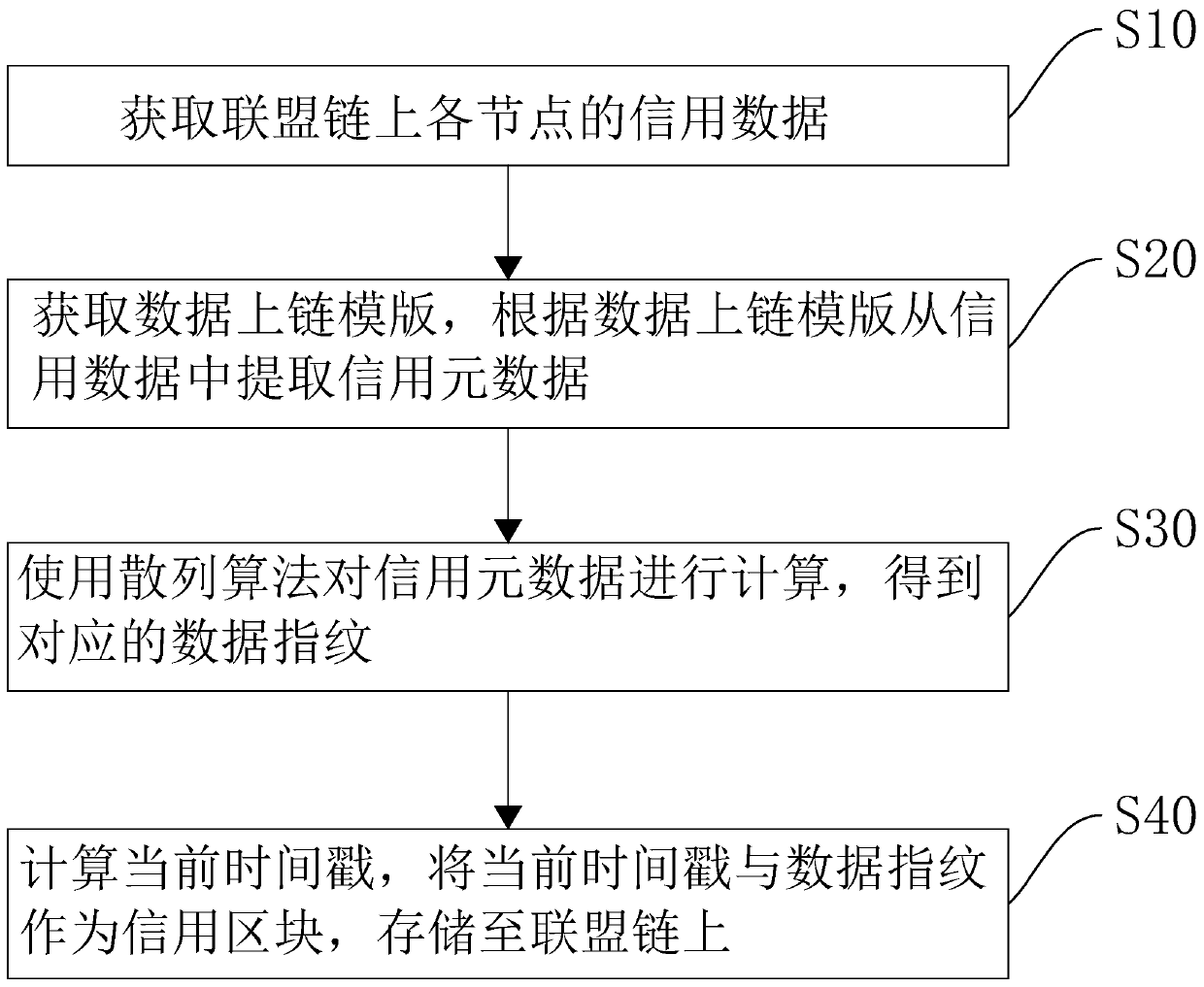
InactiveCN110096551AIncrease profitIncrease diversityEncryption apparatus with shift registers/memoriesDatabase distribution/replicationTimestampComputer software
The invention relates to the technical field of computer software, in particular to a credit data storage method and device based on a block chain, equipment and a medium, and the credit data storagemethod based on the block chain comprises the steps: S10, obtaining credit data of each node on an alliance chain; S20, obtaining a data chaining template, and extracting credit metadata from the credit data according to the data chaining template; S30, calculating the credit metadata by using a hash algorithm to obtain a corresponding data fingerprint; and S40, calculating a current timestamp, taking the current timestamp and the data fingerprint as credit blocks, and storing the credit blocks on the alliance chain. The method has the effect of improving the data richness of the credit investigation system.
Owner:浙江泰链科技有限公司
Electronic evidence collection method, relevant device, and readable storage medium
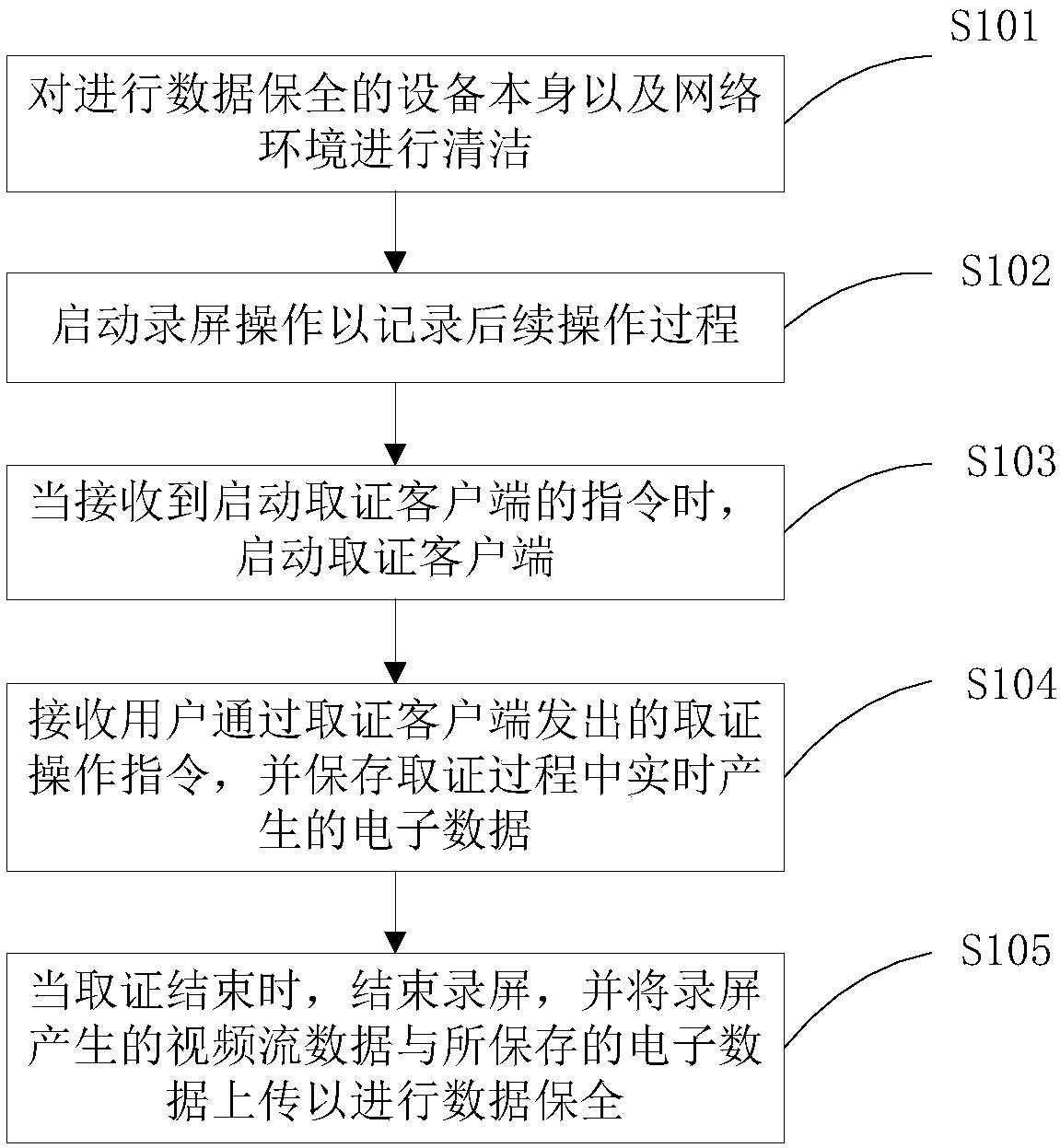
InactiveCN107682734AGuaranteed cleanlinessGuarantee authenticityTelevision system detailsColor television detailsStream dataEvidence collection
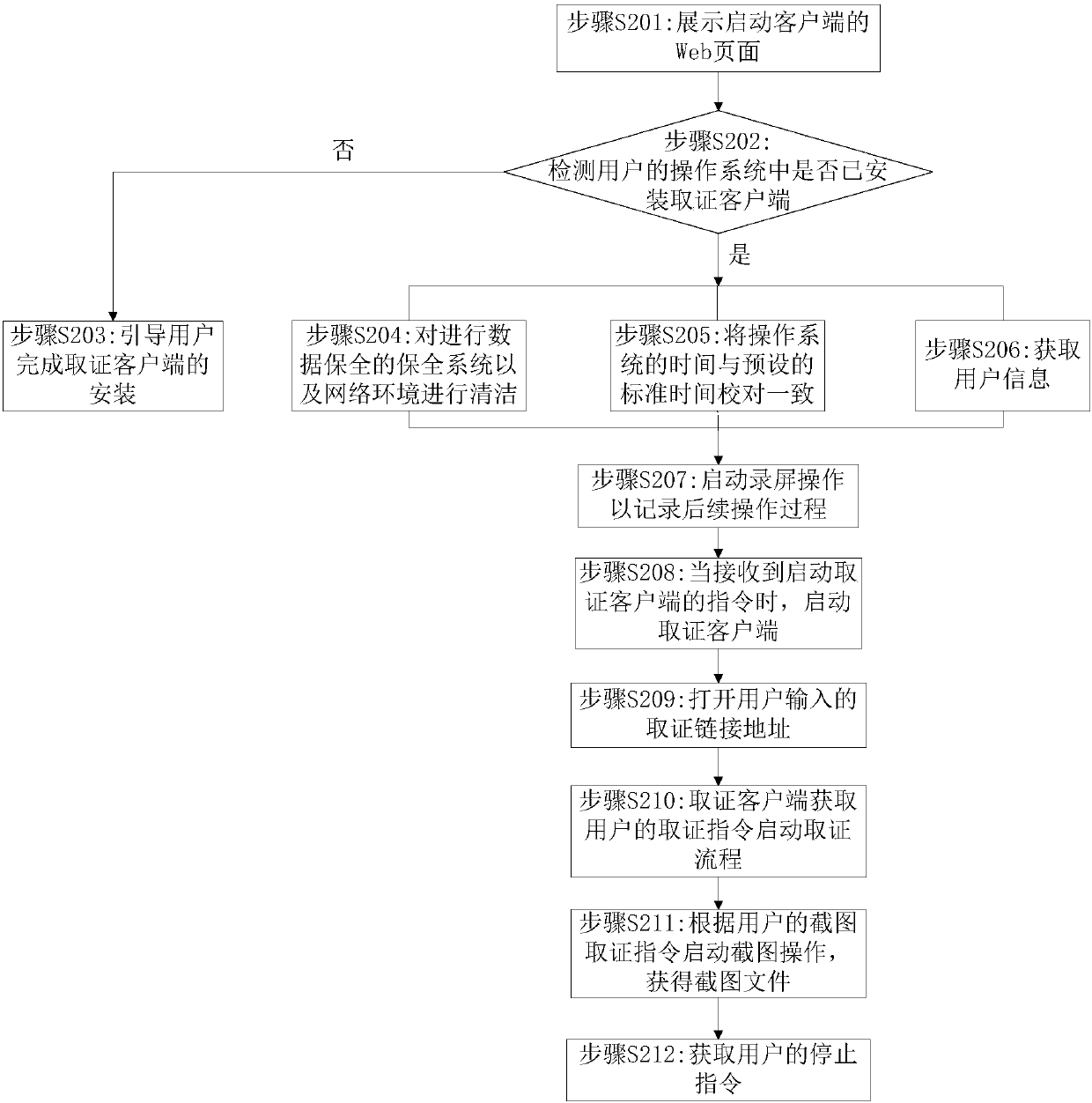
The invention discloses an electronic evidence collection method, a relevant device, and a readable storage medium. The method comprises the following steps: cleaning data security protection equipment and a network environment; starting a screen recording operation to record subsequent operation processes; when a command for starting an evidence collection client is received, starting the evidence collection client; receiving an evidence operation command sent by a user through the evidence collection client, and saving electronic data generated during an evidence collection process in a real-time manner; and when evidence collection is completed, stopping screen recording, and uploading video stream data generated during the screen recording and the saved electronic data for data security protection. The method, the device and the readable storage medium have the advantages that high authenticity and validity of the electronic evidence collection process can be ensured, so that highreliability of electronic evidence can be guaranteed.
Owner:国信嘉宁数据技术有限公司
Method for detecting failure nodes of wireless sensor network
ActiveCN102238602AGuaranteed correctnessImprove efficiencyWireless communicationWireless mesh networkNetwork packet
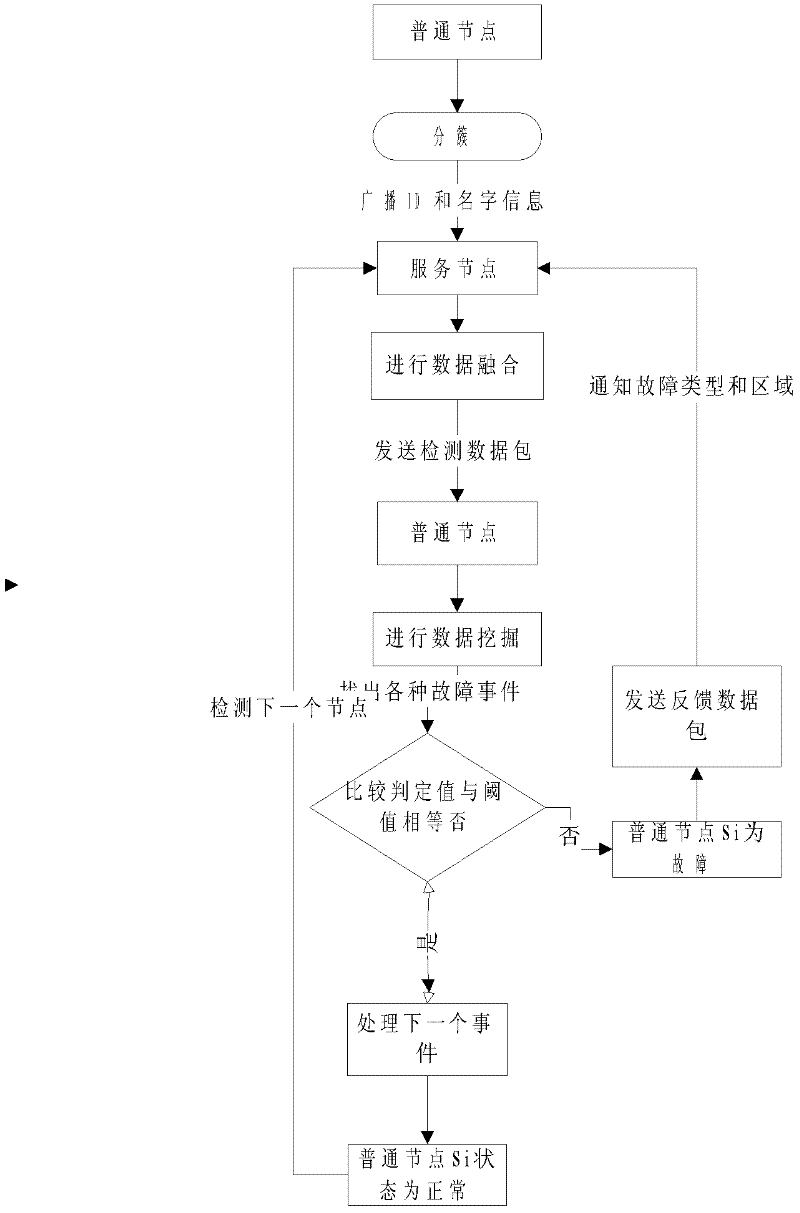
The invention provides a mechanism for detecting failure nodes of a wireless sensor network based on high reliability, which is used for detecting the failure nodes in the wireless sensor network and finding out the types of the failures, wherein the failures include the Byzantine failure, namely uncertain failure with various reasons. The mechanism is characterized by sending a detection data packet to nodes to be detected, using a threshold-based failure node detection algorithm for the nodes to be detected, reporting a failure and requiring further processing of the failure after the failure is detected, and continuing detecting the next node if no failure is detected, thus ensuring that all the failures are detected, wherein the detection data packet is processed by data mining and data fusion technologies. Meanwhile, a failure detection priority is set so as to ensure that the detection priority can be given to the fatal failures.
Owner:NANJING UNIV OF POSTS & TELECOMM
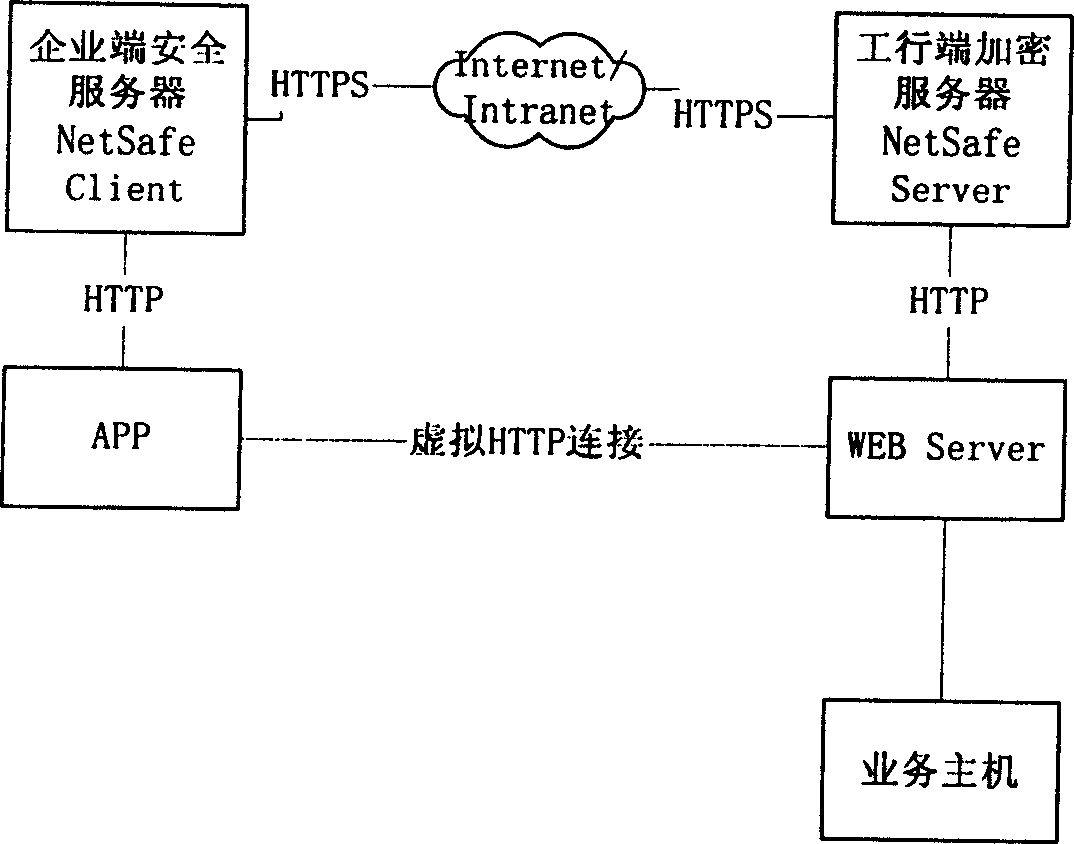
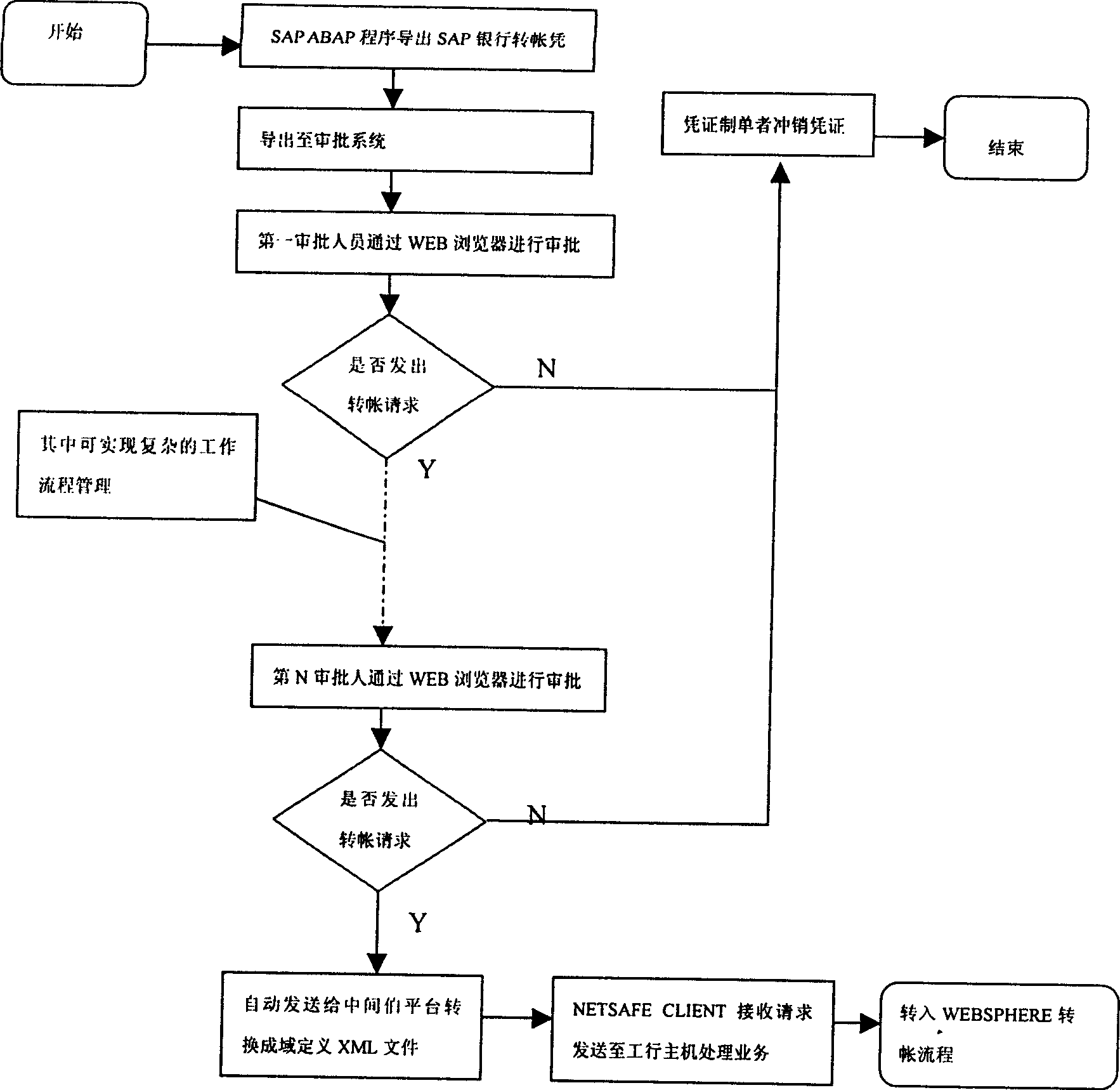
Network bank trade system and method between enterprise and bank
InactiveCN1598841AEnsure safetyWill not be tampered withData switching networksSpecial data processing applicationsPaymentBusiness Personnel
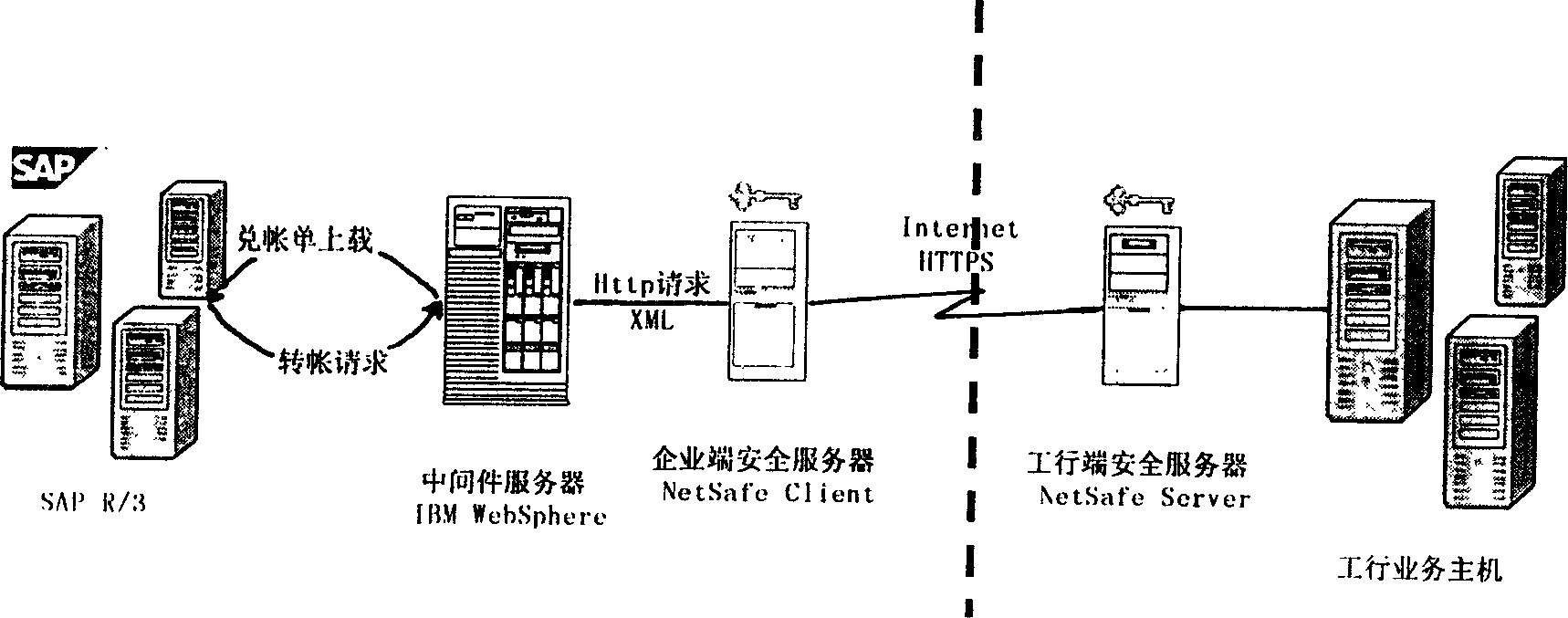
The invention relates to a method of network bank trading between companies and banks. The system includes computer units in bank and company, thereinto, SAP software system is used in company for every finance personnel. Payment service credence is programmed in each client by finance personnel. The payment data is uploaded to company server by special person using eduction program through examination of relative service personnel. Payment check personnel approve payment information through WEB browser in client according to respective rights. Company payment information after approval interacts with bank service host through Internet. In charge of security server in company and bank, trade request is sent to encryption server after encryption and is sent to background to process server after unencrypted by server in bank. At last, the result is returned.
Owner:SINOPEC YANGZI PETROCHEM
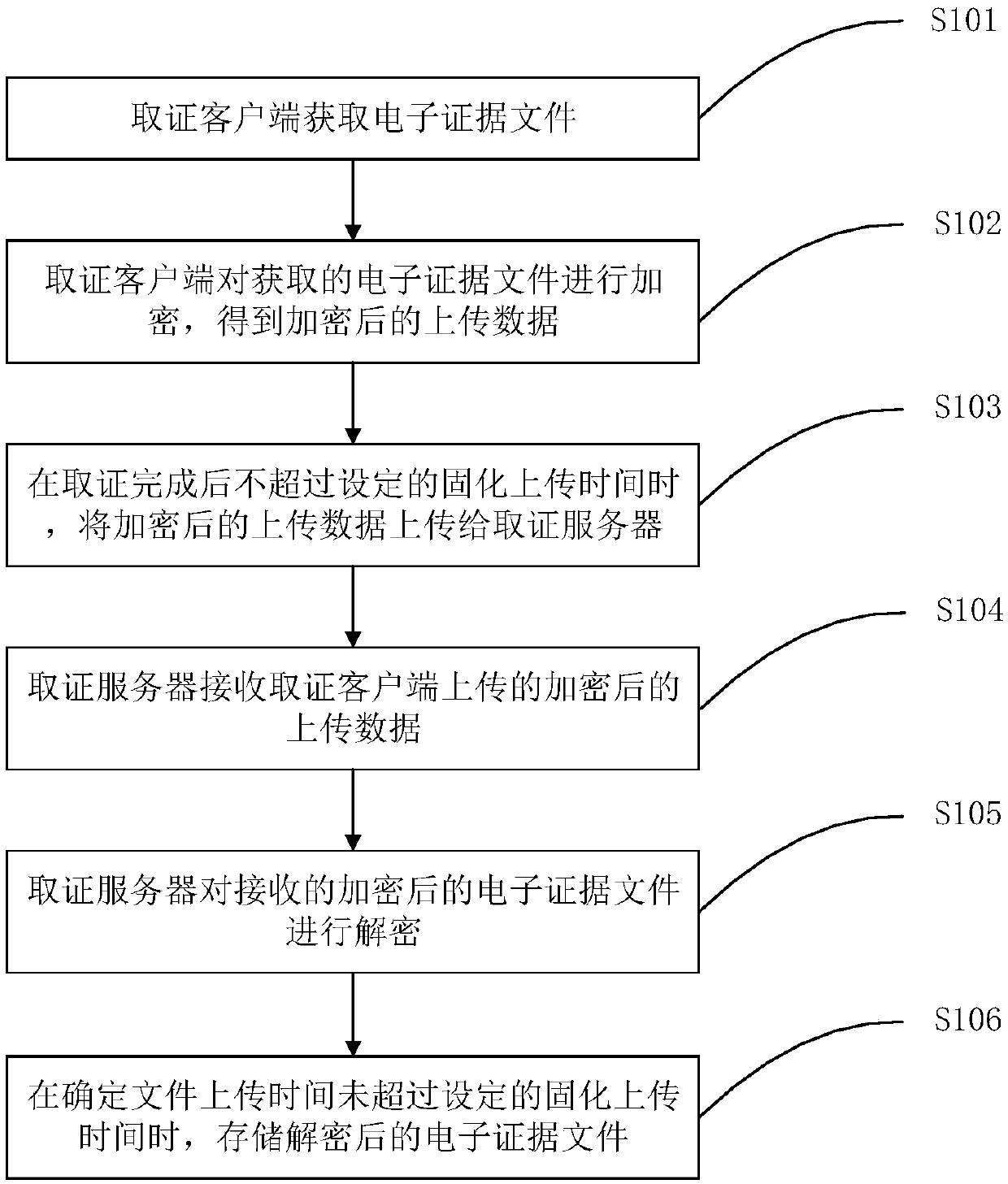
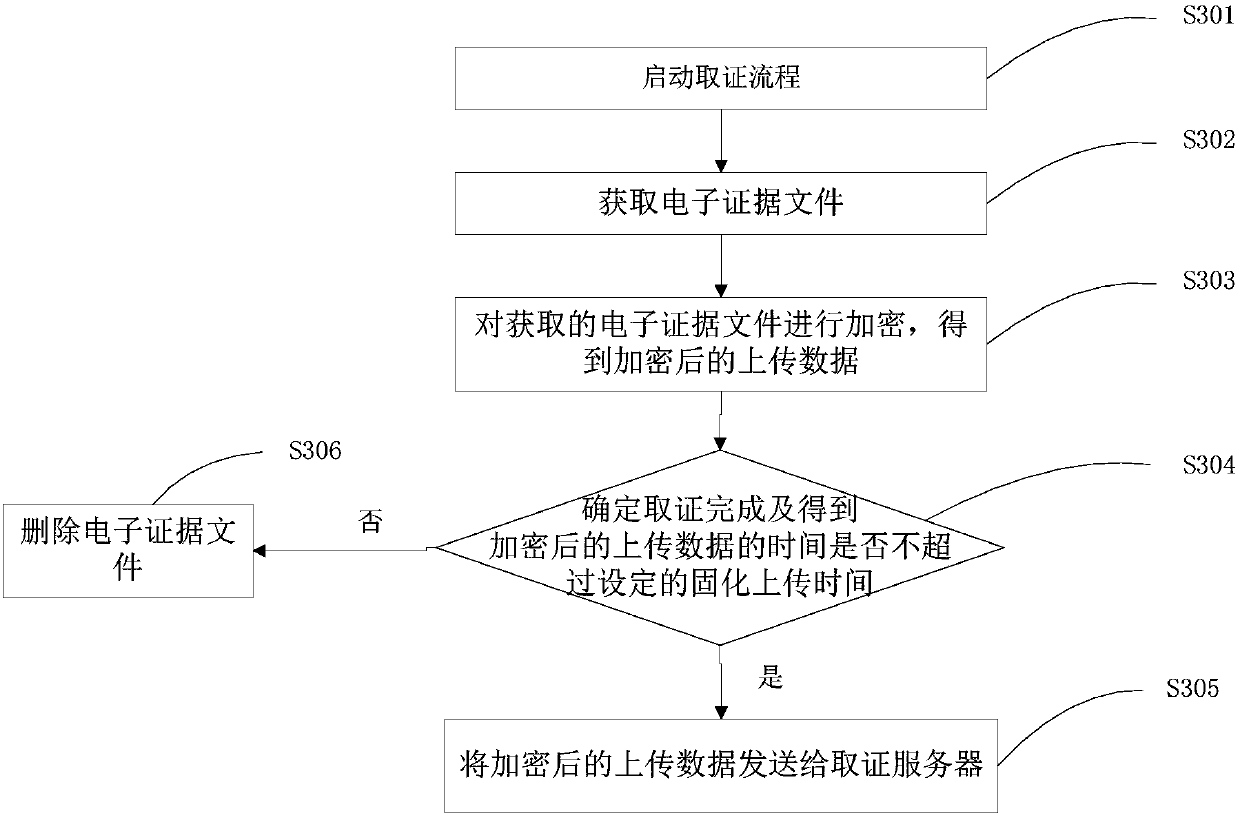
Electronic evidence consolidation method and system, and equipment
InactiveCN107645511AAccurate transmissionReduce the possibility of deletion and tamperingUser identity/authority verificationDependabilityClient-side
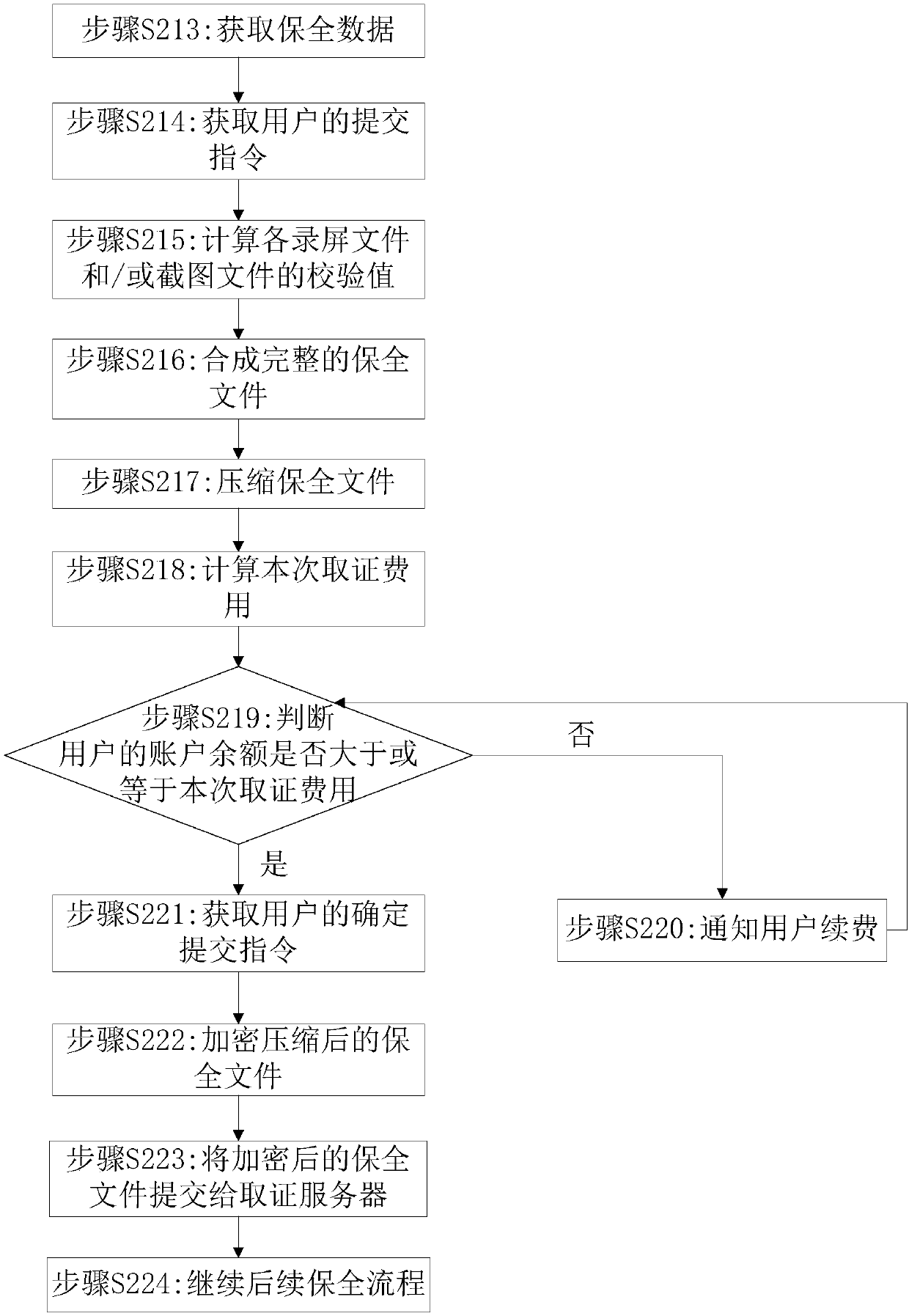
The invention discloses an electronic evidence consolidation method and system, and equipment. The method comprises: an evidence obtaining client obtains an electronic evidence file according to a user instruction; the evidence obtaining client encrypts the obtained electronic evidence file to obtain encrypted uploading data; and when the time for evidence obtaining completion does not exceed setconsolidation uploading time, the encrypted uploading data are uploaded to an evidence obtaining server, so that the evidence obtaining server receives the encrypted electronic evidence file and stores a decrypted electronic evidence file. Therefore, the obtained electronic evidence file are uploaded correctly and the content is protected from being tampered, so that the data transmission correctness and reliability during the electronic evidence consolidation process are improved and the consolidated electronic evidence data are guaranteed to be true and effective.
Owner:国信嘉宁数据技术有限公司
Commodity tracing method and device based on block chain technology
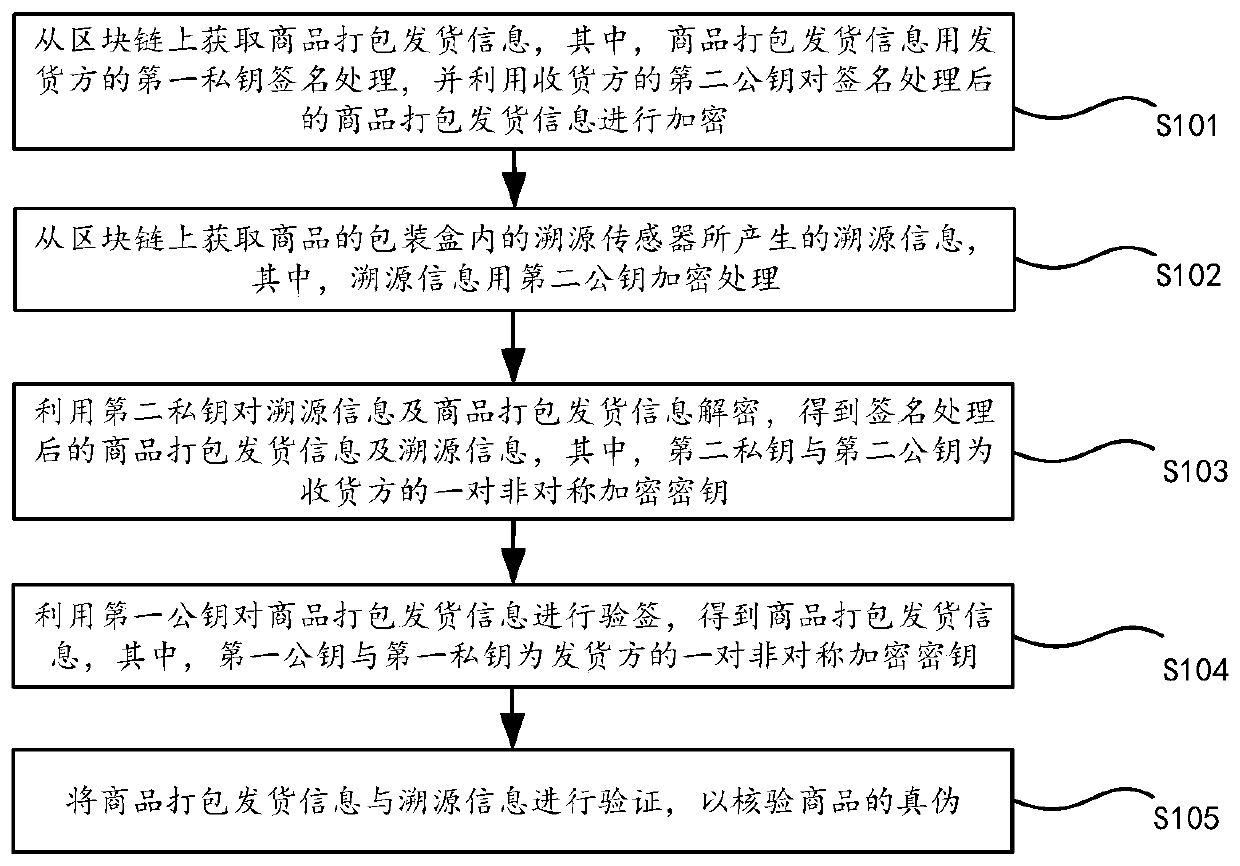
PendingCN110232575AIncrease authenticityWill not be tampered withCo-operative working arrangementsDigital data protectionLogistics managementComputer science
The embodiment of the invention provides a commodity tracing method and device based on a block chain technology. The invention relates to the technical field of block chains. The commodity tracing method comprises the steps: obtaining commodity packaging and delivery information from a block chain, performing signature processing on the commodity packaging and delivery information through a firstprivate key of a delivery party, and encrypting the commodity packaging and delivery information after signature processing through a second public key of a receiving party; obtaining traceability information generated by a traceability sensor in a packaging box of the commodity from the block chain; decrypting the traceability information and the commodity packaging and delivery information by using the second private key to obtain the commodity packaging and delivery information after signature processing and the traceability information; utilizing the first public key to carry out signature verification on the commodity packaging and delivery information to obtain commodity packaging and delivery information; and verifying the commodity package delivery information and the traceabilityinformation to verify the authenticity of the commodity. According to the technical scheme provided by the embodiment of the invention, the problem that the authenticity of commodity logistics data cannot be guaranteed in the prior art can be solved.
Owner:PING AN TECH (SHENZHEN) CO LTD
Internet of things data management method, platform and device
ActiveCN108540553ARealize supervisionImprove management efficiencyFinanceTransmissionData informationTransaction data
The invention provides an Internet of things data management method, platform and device. The method comprises the following steps: a data layer receives the Internet of Things data sent by a terminaldevice and writes the Internet of Things data into a blockchain, wherein each node of the blockchain network comprises a member and a data layer in an application management layer; the data layer receives first tradable data information sent by a first member, and broadcasts the tradable data information to the blockchain network, so that each node of the blockchain network confirms the first tradable data information; if the blockchain network confirms that the tradable data information is legal, the data layer writes the tradable data information into the blockchain, so that a second membersends a transaction request to the first member according to the tradable data information. According to the method, the platform and the device in the invention, the Internet of Things data are stored based on the blockchain technology, and the Internet of Things data can be managed and supervised effectively.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
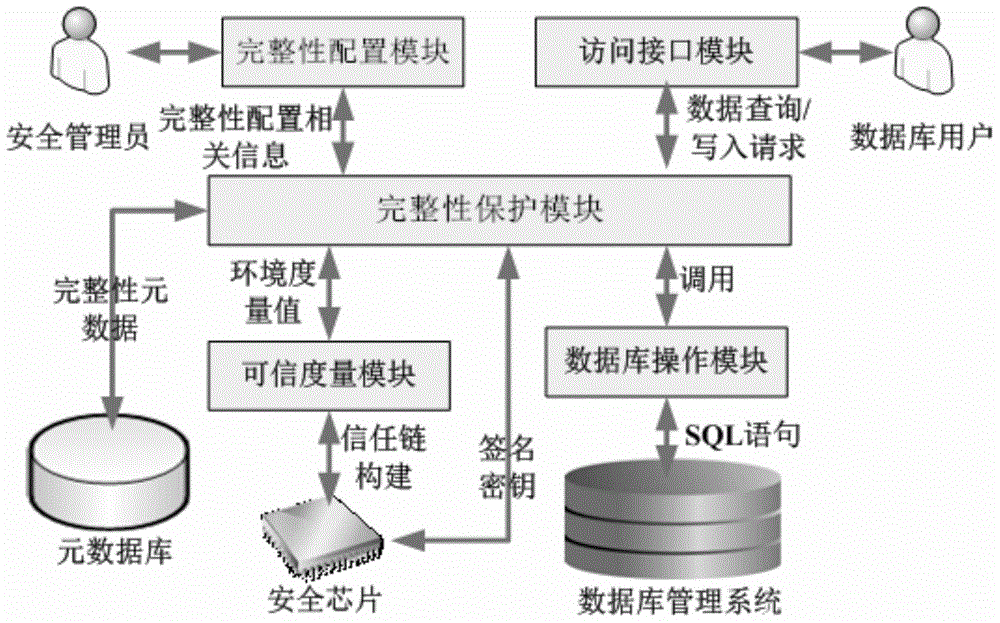
Credible database integrity protecting method and system
ActiveCN104615947AReduce the impactImprove integrity protection strengthDigital data protectionControlling environmentData needs
The invention provides a credible database integrity protecting method and system which are particularly but not just suitable for an industrial control system. The method includes the steps that when sensitive data need integrity protection, whether the current system environment conforms to the environment needed for sensitive data integrity protection or not is checked through a credible measurement technology, and whether the system environment is credible or not is checked similarly before an integrity measurement signature is verified. A signature secret key for carrying out integrity verification is protected by a hardware safety chip in an encipherment mode, and therefore safety based on hardware is achieved. Finally, integrity verification is achieved in a middleware mode, and the normal operation efficiency of a system is ensured while integrity verification of the sensitive data is ensured. Based on the credible database integrity protecting method and system, the safe database system for storing the sensitive data based on the safety chip can be set up for the industrial control environment, the integrity protection intensity of the sensitive data in the safe database system is improved, and it is ensured that production plans, technological processes and other sensitive data are not tampered.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
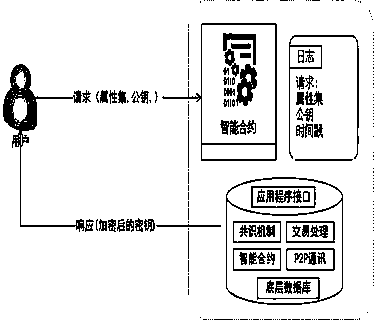
CP-ABE access control scheme based on block chain
PendingCN111079191ASolve the single point of failure problemReduce workloadDigital data protectionTransmissionAttribute authorityAuthorization
The invention discloses a blockchain combined access control architecture based on attribute encryption. Aiming at attribute encryption based on a ciphertext strategy in a multi-authorization-center scene, the work of the authorization centers is executed by a block chain, a trust relationship between the attribute authorization centers is constructed by utilizing an intelligent contract, a key management mechanism is established, and attribute authorization, key management and attribute revocation are completed by the intelligent contract. According to the scheme, the access control process based on attribute encryption is public, transparent, more flexible and safer.
Owner:INNER MONGOLIA UNIVERSITY
Safety certification method and system for intelligent television software based on android operation system
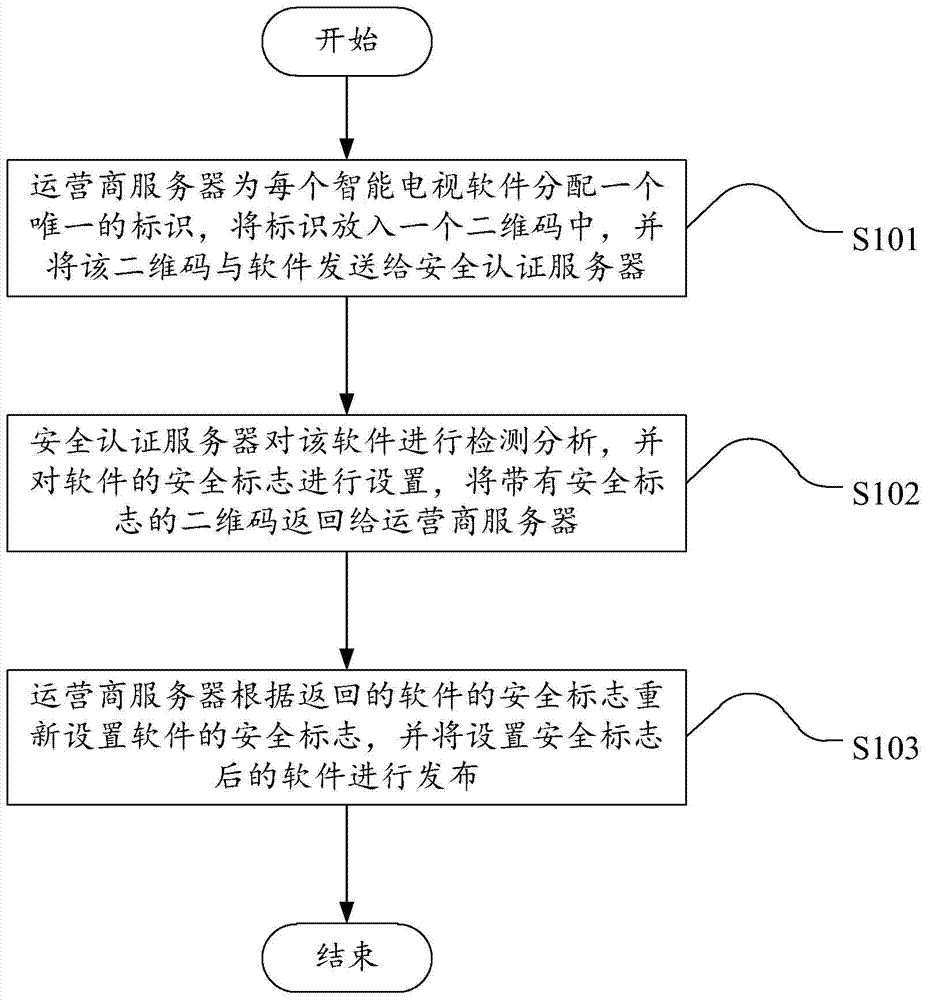
ActiveCN103501307AReduce waste of resourcesImprove processing efficiencyTransmissionOperational systemSoftware engineering
The embodiment of the invention discloses a safety certification method and a safety certification system for intelligent television software based on an android operation system, wherein the method comprises the following steps that an operator server allocates one unique mark for each intelligent television software, the mark is put into a two-dimension code, and in addition, the two-dimension code and the software are sent to a safety certification server; the safety certification server carries out detection analysis on the software and sets the safety mark of the software, and the two-dimension code with the safety mark is returned to the operator server; the operator server resets the safety mark of the software according to the returned safety mark of the software, and in addition, the software after the setting of the safety mark is issued. When the embodiment of the invention is implemented, the safety detection certification can be carried out on the intelligent television software, in addition, the resource waste of intelligent televisions can be reduced, the processing efficiency of the intelligent televisions on the software is improved, and the use by users is convenient.
Owner:SUN YAT SEN UNIV
Automatic driving automobile model sharing method applying block chain
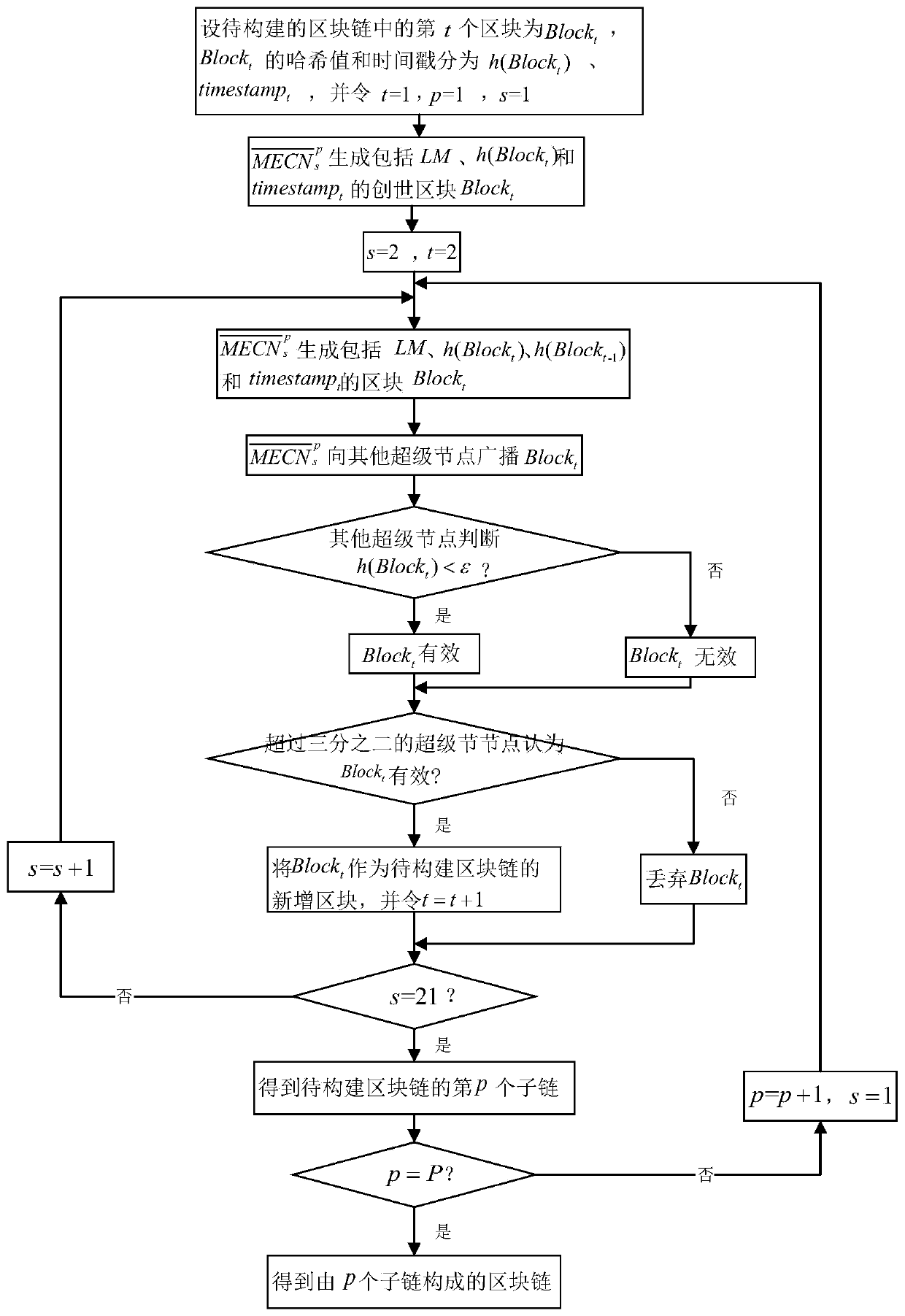
ActiveCN111211893AEnsuring Automated Driving DecisionsWill not be tampered withKey distribution for secure communicationEncryption apparatus with shift registers/memoriesCar modelEdge computing
The invention discloses an automatic driving automobile model sharing method applying a block chain, and aims to improve the accuracy and efficiency of automatic driving automobile decision making. The method comprises the following steps: 1) constructing a mobile edge computing network; 2) generating a key pair of each node in the mobile edge computing network; 3) constructing a local model set of a mobile node set in the mobile edge computing network; 4) each mobile node communicating with the mobile edge computing node closest to the mobile node; 5) moving the edge computing node set to obtain a super node sequence; 6) constructing a block chain based on the super node sequence, and 7) updating the local model set. Compared with an existing automatic driving automobile model training method, the method has the advantages that when the model is used for decision making in the driving process of the automatic driving automobile, the decision making accuracy and efficiency are effectively improved.
Owner:XIDIAN UNIV
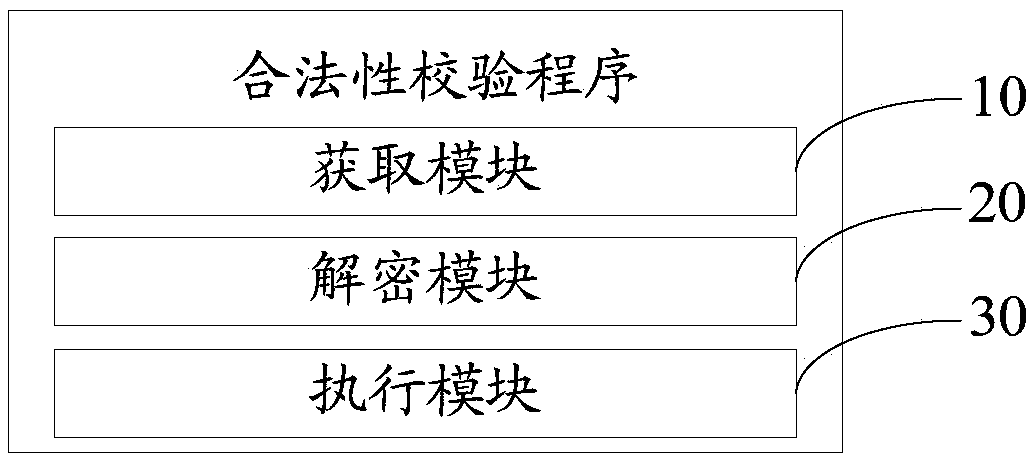
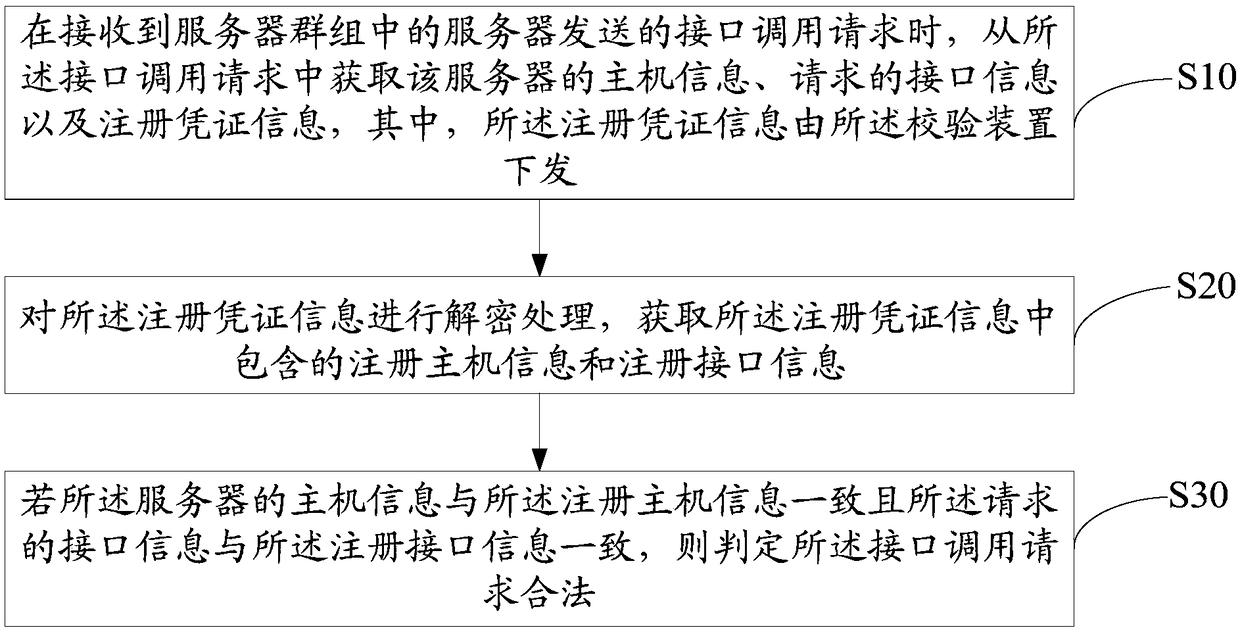
Request legality verification device and method and computer readable storage medium
ActiveCN108449315AQuick responseWill not be tampered withComputer security arrangementsTransmissionOperating system
The invention discloses a request legality verification device. The request legality verification device comprises a storage and a processor, and a legality verification program capable of operating on the processor is stored on the storage. The program is executed by the processor to achieve the following steps that when an interface calling request sent by a server in a server group is received,host information of the server, requested interface information and registration certificate information are acquired from the interface calling request; the registration certificate information is subjected to decryption processing to acquire registration host information and registration interface information which are contained in the registration certificate information; and if the host information of the server is consistent with the registration host information and the requested interface information is consistent with the registration interface information, it is judged that the interface calling request is legal. The invention further provides a request legality verification method and a computer readable storage medium. Accordingly, the request legality verification process is simplified, and then the interface calling responding speed is increased.
Owner:PING AN TECH (SHENZHEN) CO LTD
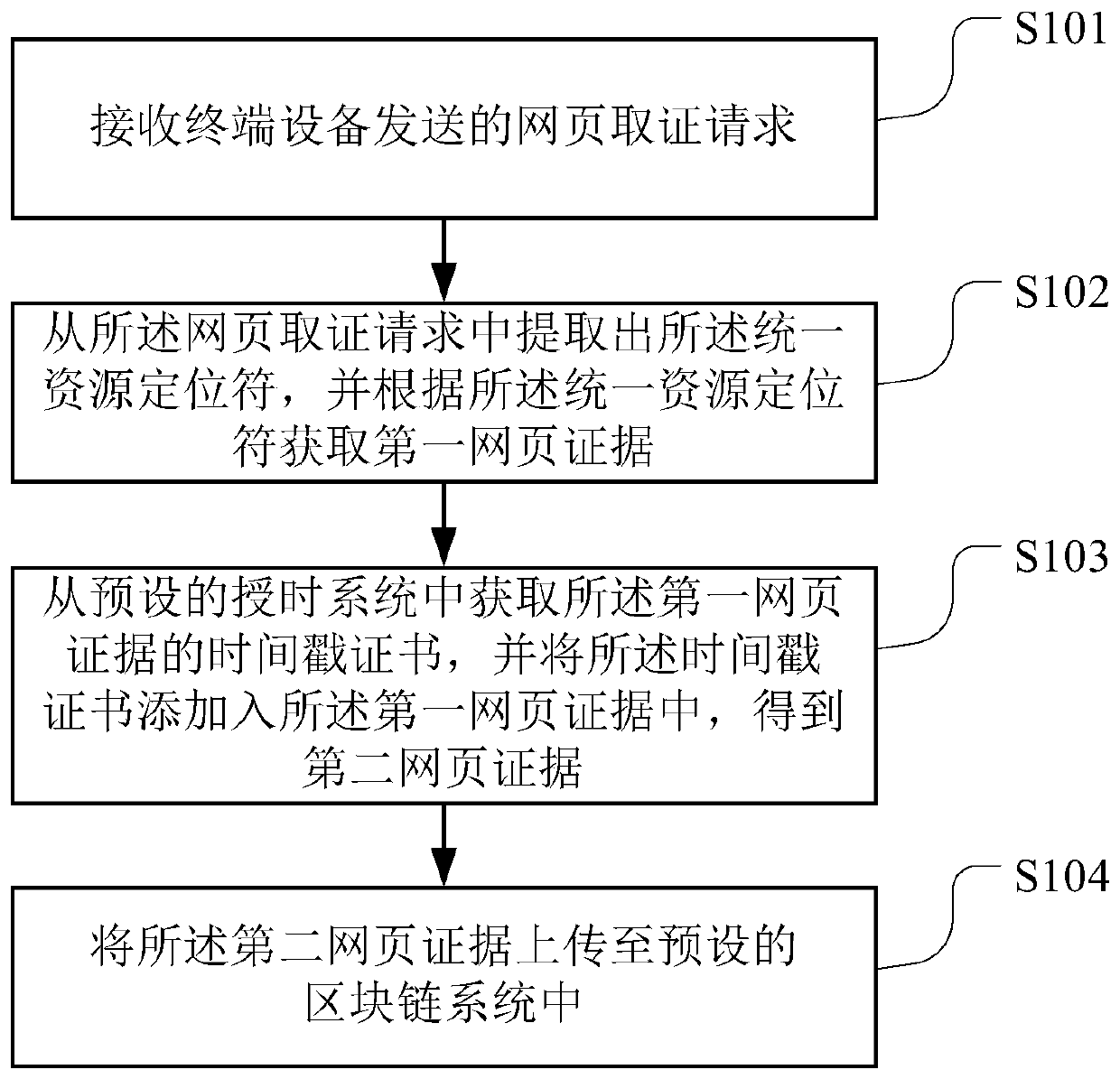
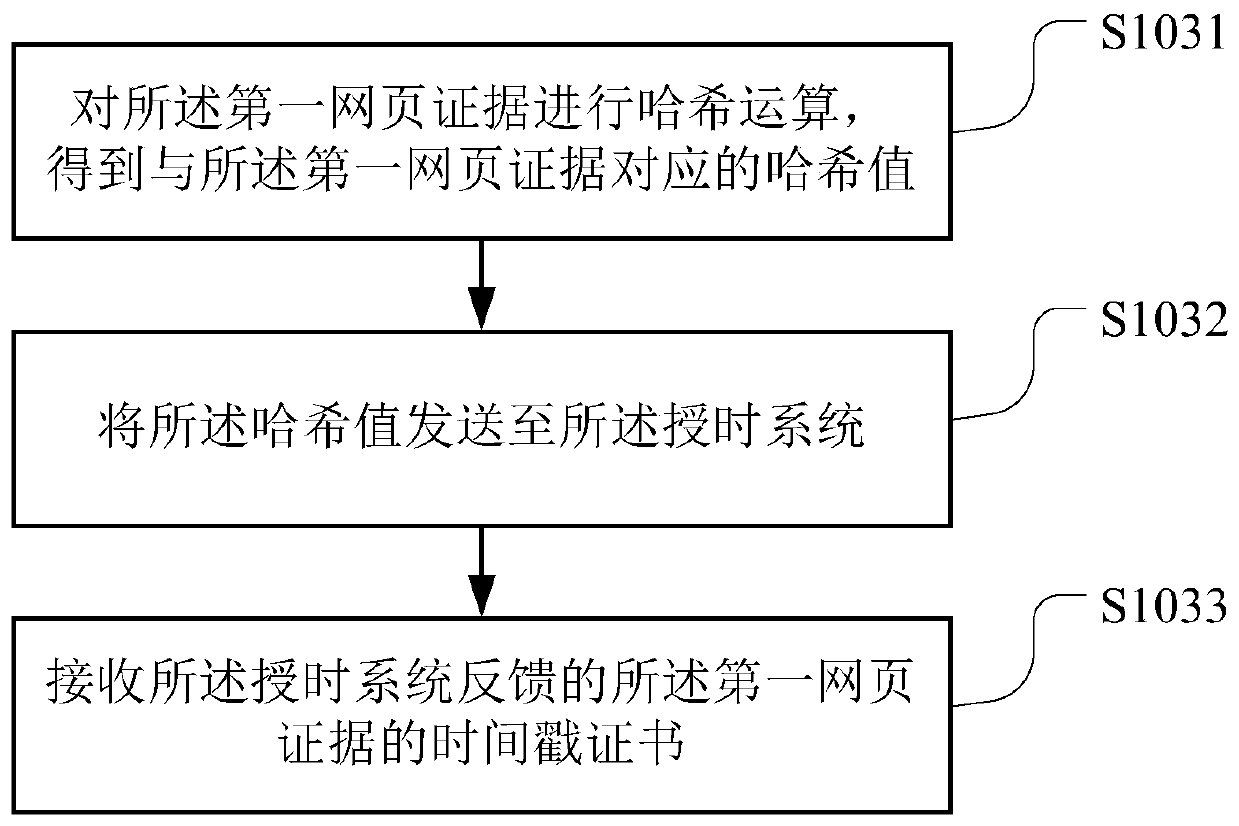
Block chain-based webpage evidence obtaining method, device, storage medium and server
PendingCN110489676AImprove convincing powerRealize acquisitionDigital data protectionSpecial data processing applicationsChain systemService system
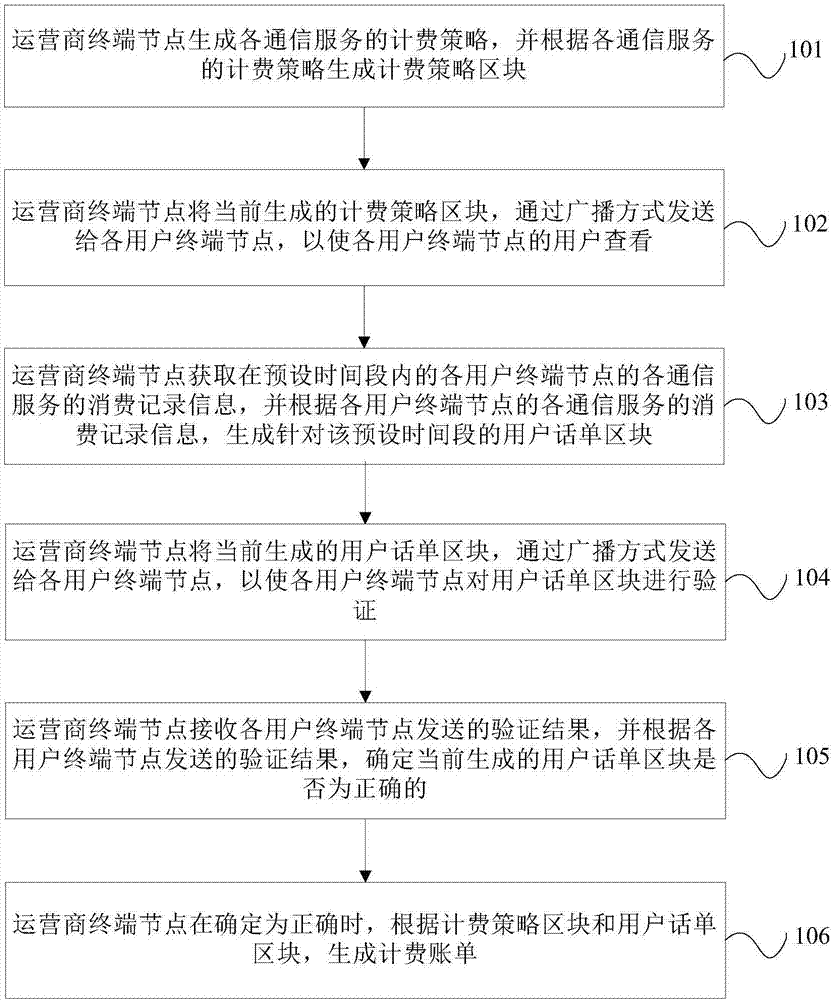
The invention belongs to the technical field of computers, and particularly relates to a block chain-based webpage evidence obtaining method, a device, a computer readable storage medium and a server.The method comprises the following steps: receiving a webpage evidence obtaining request sent by terminal equipment, wherein the webpage evidence obtaining request comprises a uniform resource locator of a target webpage; extracting the uniform resource locator from the webpage evidence obtaining request, and obtaining a first webpage evidence according to the uniform resource locator, wherein the first webpage evidence comprises an image of the target webpage; obtaining a timestamp certificate of the first webpage evidence from a preset time service system, and adding the timestamp certificate into the first webpage evidence to obtain a second webpage evidence; and uploading the second webpage evidence to a preset block chain system. As the evidence obtaining time is proved through the time service system, it is ensured that the evidence cannot be tampered through the block chain system. The credibility of the evidence is greatly improved, and the evidence can be accepted by courts.
Owner:PING AN TECH (SHENZHEN) CO LTD
Blockchain-based data asset transaction method
InactiveCN111899101AInformation tamperingWill not be tampered withFinanceDigital data protectionChain networkEngineering
The invention discloses a blockchain-based data asset transaction method, which belongs to the technical field of blockchains, and comprises the following steps: a blockchain platform deploys a transaction smart contract, a user registers a contract transaction account through the blockchain platform, and the platform returns a pair of public key and private key of the user as an account address and a key for starting an account; the user compiles a transaction demand into a character string in the smart contract and publishes the character string in a blockchain transaction network, and matches an account meeting a transaction condition by using a blockchain consensus mechanism; a contract is triggered to automatically execute the transaction for the two parties meeting the transaction condition, wherein the transaction participants respectively sign by using respective private keys; and the transaction participants decrypt the signatures of the two transaction parties by using the public keys, broadcast the confirmed signatures through the block chain network and store the signatures into the block chain. The two transaction parties perform transaction through the smart contractin the blockchain, and the transaction information is encrypted, packaged and broadcasted to the blockchain by the private keys, so that the transaction information is not tampered, and the security is improved.
Owner:安徽高山科技有限公司
Blockchain digital signature method and device based on distributed storage
InactiveCN111683090AGuaranteed complete consistencyImprove securityEncryption apparatus with shift registers/memoriesUser identity/authority verificationDigital signatureData information
The invention discloses a blockchain digital signature method and device based on distributed storage. The method comprises the steps that a sending node generates a public key and private key pair; the sending node performs hash operation on the identity data information to generate summary information, and processes the summary information by using the private key to generate digital signature information; and the sending node broadcasts the digital signature information, the identity data information and the public key to a receiving node, so that the receiving node verifies the signature information through the public key. According to the method provided by the invention, the adopted digital signature technology is used for ensuring that the sent information is not tampered and ensuring that the integrity and consistency of user files are verified, and the security of the algorithm is improved for a relatively single rsa encryption algorithm.
Owner:盛唐威讯数媒科技(北京)有限公司
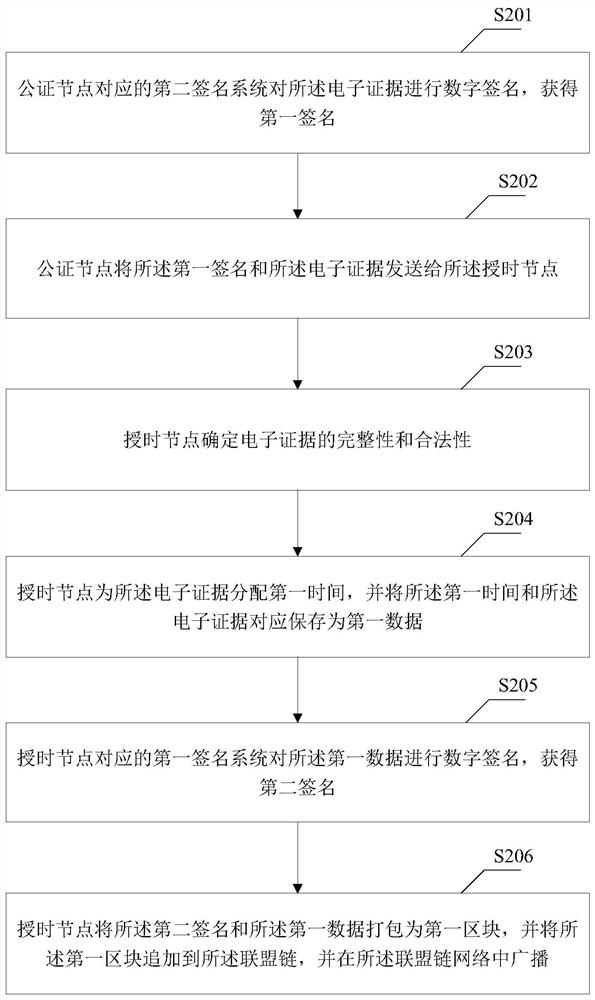
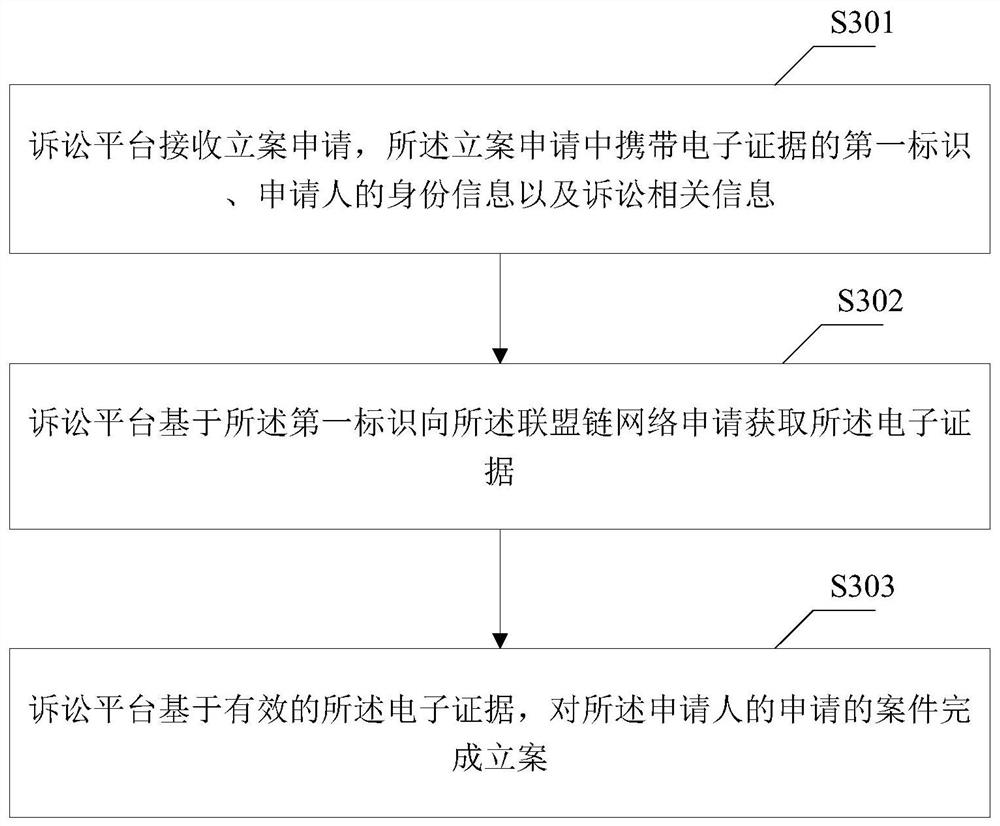
Evidence storage method based on alliance chain, case filing method and related equipment
PendingCN111696006AImprove stability and reliabilityImprove securityData processing applicationsDatabase distribution/replicationChain networkCase files
The embodiment of the invention discloses an evidence storage method based on an alliance chain, a case filing method and related equipment. The method comprises the following steps of: determining the integrity and legality of acquired electronic evidences by a time service node; allocating first time to the electronic evidence, and correspondingly storing the first time and the electronic evidence as first data; performing digital signature on the first data to obtain a second signature; and packaging the second signature and the first data into a first block, appending the first block to the alliance chain, and broadcasting the first block in the alliance chain network. Visibly, the electronic evidence is stored based on the alliance chain; the reliability and the stability of the electronic evidence are improved; time service is performed on complete and legal electronic evidences based on a trusted time service center. The electronic evidence and the given time are digitally signed through the digital signature technology, it is guaranteed that the electronic evidence cannot be tampered in the chaining process and after chaining, the safety of the electronic evidence is improved, and convenience is provided for subsequent judicial procedure examination of the electronic evidence.
Owner:BANK OF CHINA
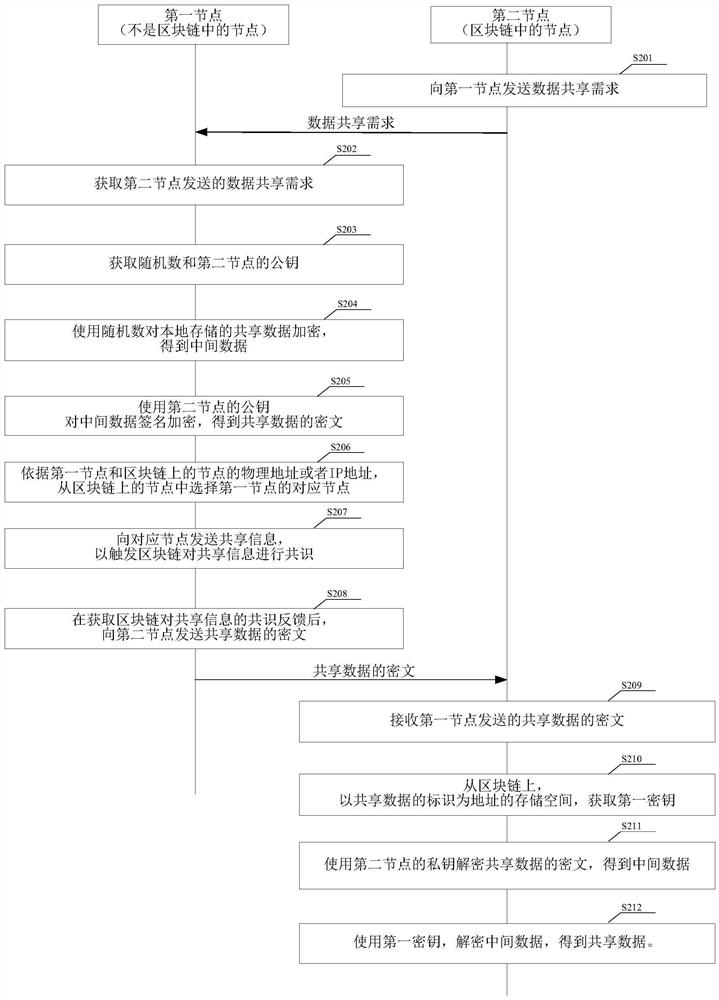
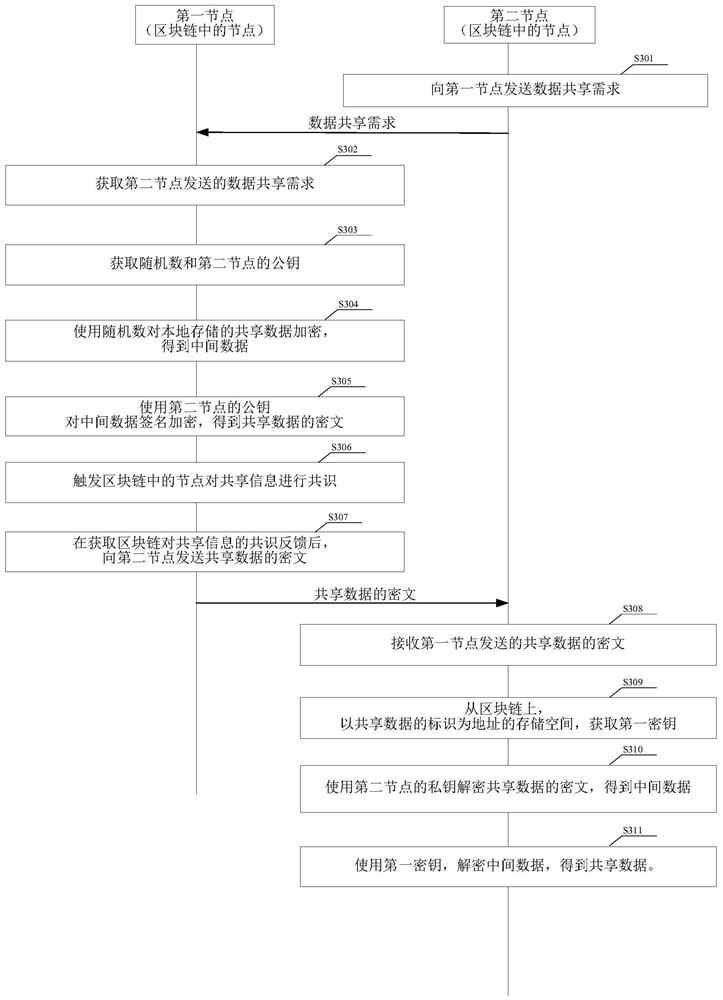
Data sharing method and related device
ActiveCN112039892AImprove securityRecord tamperingUser identity/authority verificationIndustrial InternetBlockchain
The embodiment of the invention provides a data sharing method and a related device, a first node initiates consensus of sharing information to nodes in a block chain after acquiring a data sharing demand sent by a second node, the nodes in the block chain comprise the second node, the data sharing demand comprises an industrial Internet identifier of shared data, shared information comprises an associated industrial Internet identifier of the first node, an industrial Internet identifier of the second node and an identifier of the shared data, and a ciphertext of the shared data is sent to the second node after consensus feedback of the block chain to the shared information is obtained. After receiving the ciphertext of the shared data sent by the first node, the second node decrypts theciphertext by using the key to obtain the shared data. The first node shares the data after the shared information is subjected to consensus, so that the record of data sharing can be traced back, andthe security of data sharing is improved. The data sent to the second node by the first node is the ciphertext after the shared data is encrypted, so that the security is further improved.
Owner:CHINA ACADEMY OF INFORMATION & COMM
Biological characteristic setting method and device
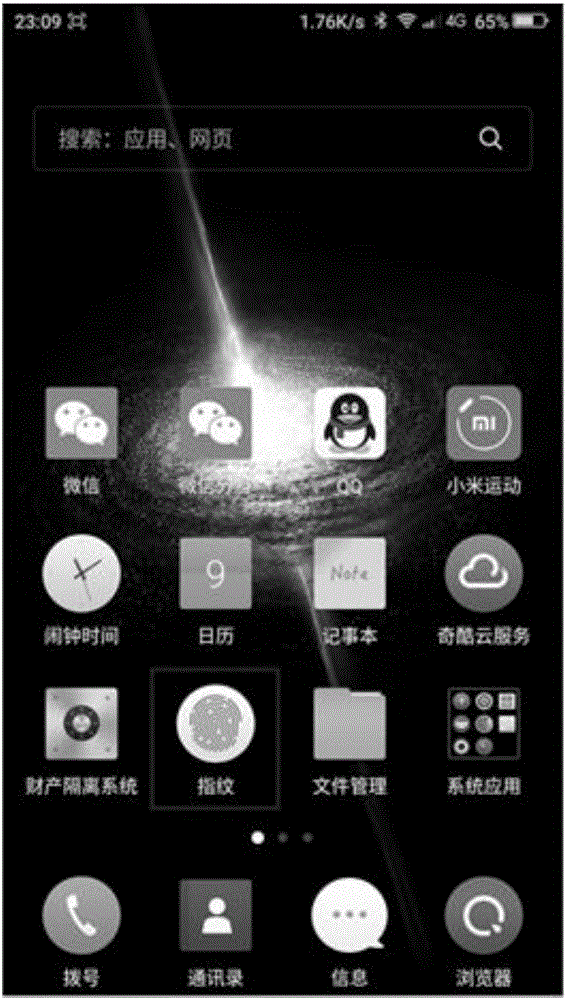
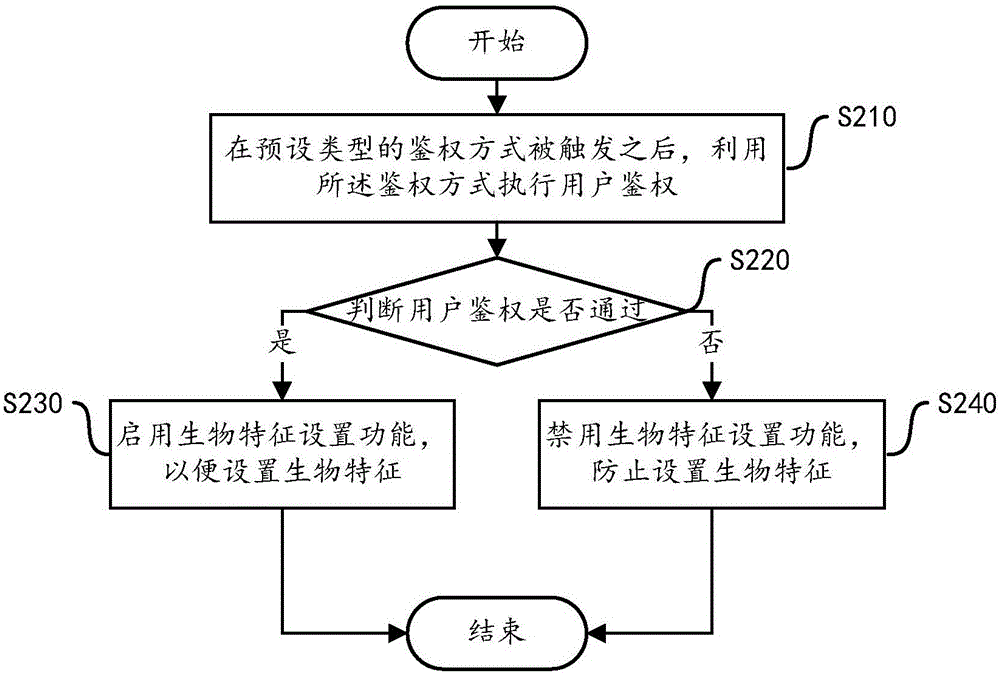
InactiveCN105787327AWill not be tampered withDigital data authenticationUser authenticationComputer engineering
The invention discloses a biological characteristic setting method and device. The method includes the steps of executing user authentication in an authenticating mode after the authentication mode of a preset type is triggered, starting a biological characteristic setting function if user authentication passes so that biological characteristics can be conveniently set, and forbidding the biological characteristic setting function if user authentication does not pass. The biological characteristic setting function for setting the biological characteristics is preset, the corresponding authentication mode is set for the biological characteristic setting function, the biological characteristic setting function is only started when the authentication passes and is forbidden in other circumstances, and the biological characteristics can not be tampered by other people.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Blockchain technology-based data cross-border flow control method
PendingCN113761057AWill not be tampered withAdjust timelinessFinanceDatabase distribution/replicationData streamControl system
The invention relates to a blockchain technology-based data cross-border flow control method. The method comprises: a data cross-border platform and an established cross-border data flow management and control system. For the problems of data cross-border supervision from traditional sampling check to all data checkability, historical data traceability, cross-border record tampering prevention, record multiple back-ups, automatic auditing, and the like, the blockchain technology is used as a novel technology for comprehensive application, and the blockchain technology has the technical characteristics of distributed consistency, non-tampering, and traceability; the above problems existing in data cross-border supervision can be well solved.
Owner:能链众合(上海)信息科技有限公司
Household registration management method, device and equipment and storage medium
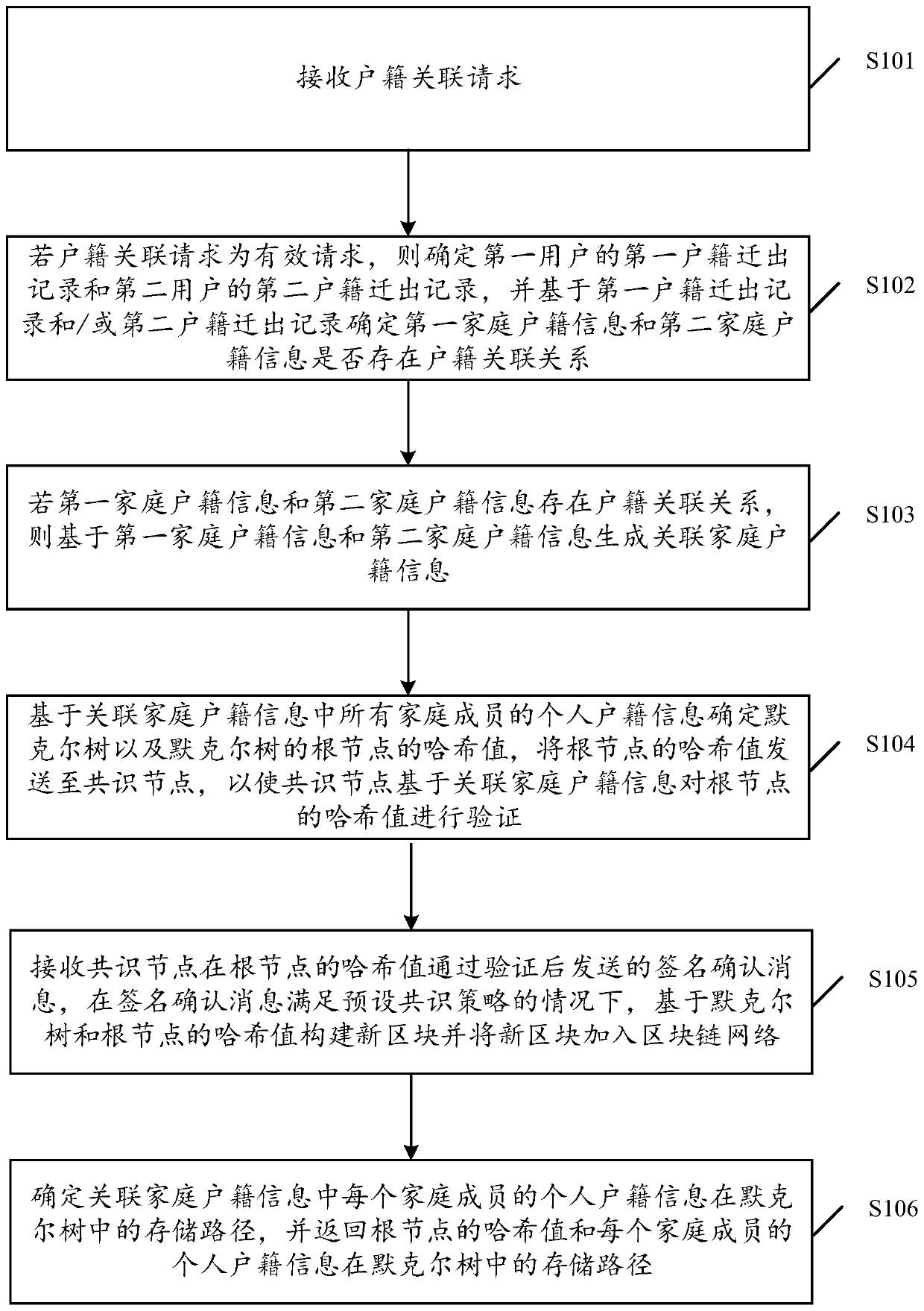
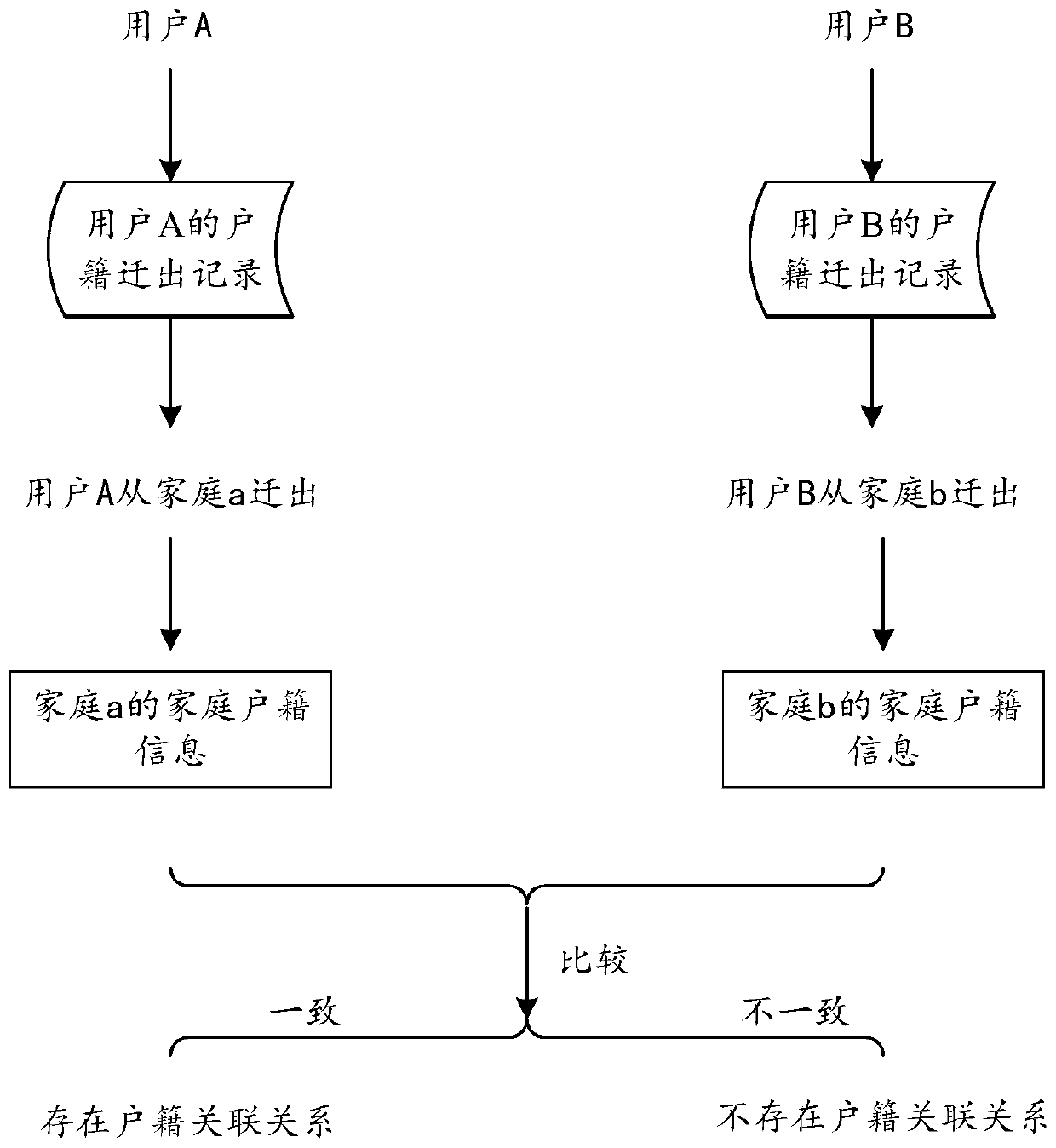
PendingCN110941672AImprove management efficiencyImprove applicabilityDatabase distribution/replicationDigital data protectionChain networkArtificial intelligence
The embodiment of the invention discloses a household registration management method, device and equipment and a storage medium. The method comprises the following steps: receiving a household registration association request; generating associated household registration information based on the first household registration information and the second household registration information, wherein theassociated household registration information comprises personal household registration information of all family parts of the first family and the second family; determining a Merkel tree and a hashvalue of a root node of the Merkel tree based on personal household registration information of all family parts in the associated household registration information; constructing a new block based on the Merkel tree and the hash value of the root node so as to add the new block into the block chain network; and determining a storage path of the personal household registration information of eachfamily part in the associated household registration information in the Merkel tree, and returning the hash value of the root node and the storage path of the personal household registration information of each family part in the Merkel tree. By adopting the embodiment of the invention, multiple parts of household registration information can be stored in an associated manner, and the flexibilityof household registration information management is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
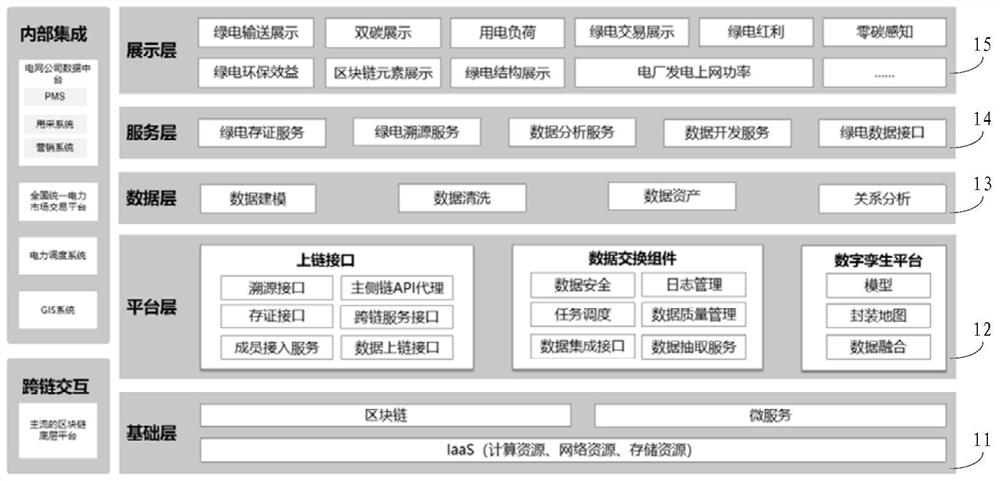
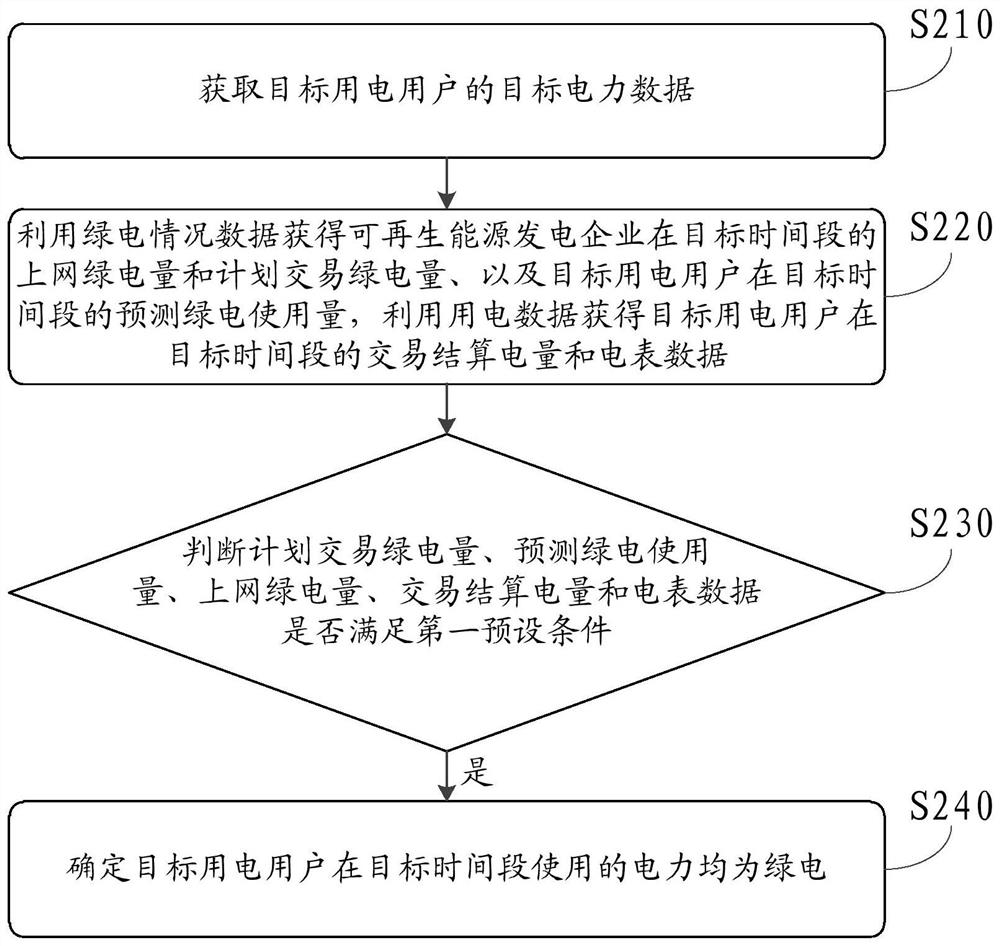
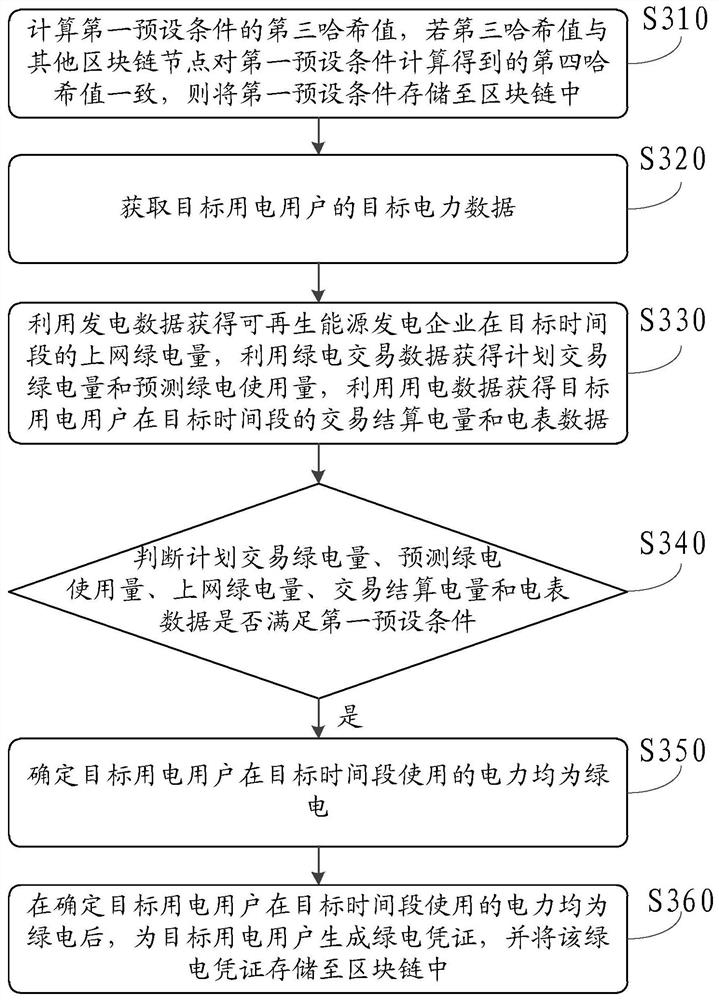
Green electricity confirmation method and device and computer readable storage medium
PendingCN114358969AWill not be tampered withAccurately determineData processing applicationsEnergy industryPower usageElectricity meter
The invention discloses a green power confirmation method and device and a computer readable storage medium, and the method comprises the steps: obtaining target power data of a target power user, the target power data comprising green power condition data about renewable energy and the power consumption of the target power user; obtaining the on-grid green electricity quantity and the planned transaction green electricity quantity of the renewable energy power generation enterprise, and the predicted green electricity usage amount, the transaction settlement electricity quantity and the electricity meter data of the target electricity user; if the planned transaction green electricity quantity, the predicted green electricity usage amount, the online green electricity quantity, the transaction settlement electricity quantity and the electricity meter data meet the first preset condition, it is determined that the electricity used by the target electricity user in the target time period is green electricity, through the above mode, the green electricity usage condition of the target user can be truly and accurately determined, and the user experience is improved. And the above green power confirmation process can be realized by using the block chain, and the target power data is stored in the block chain, so that the target power data can be ensured to be real and errorless and cannot be tampered, and the credibility of green power confirmation is improved.
Owner:YGSOFT INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com