Request legality verification device and method and computer readable storage medium
A technology of a verification device and a verification method, which is applied in the field of data communication, can solve the problems of cumbersome verification process, slow response speed of interface call requests, and maintenance of a large amount of authority management data at the authentication server, so as to simplify the verification process and improve The effect of response speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
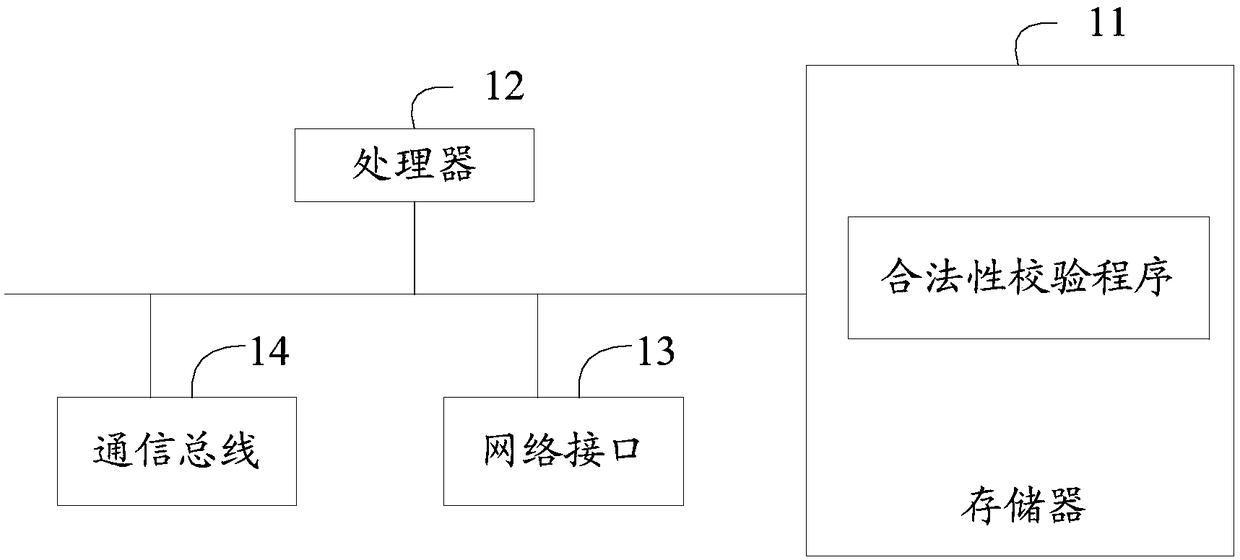
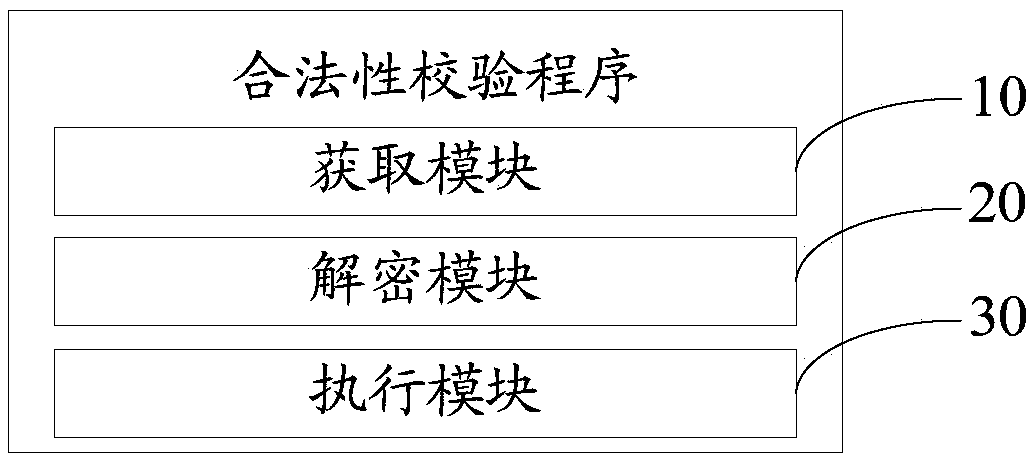
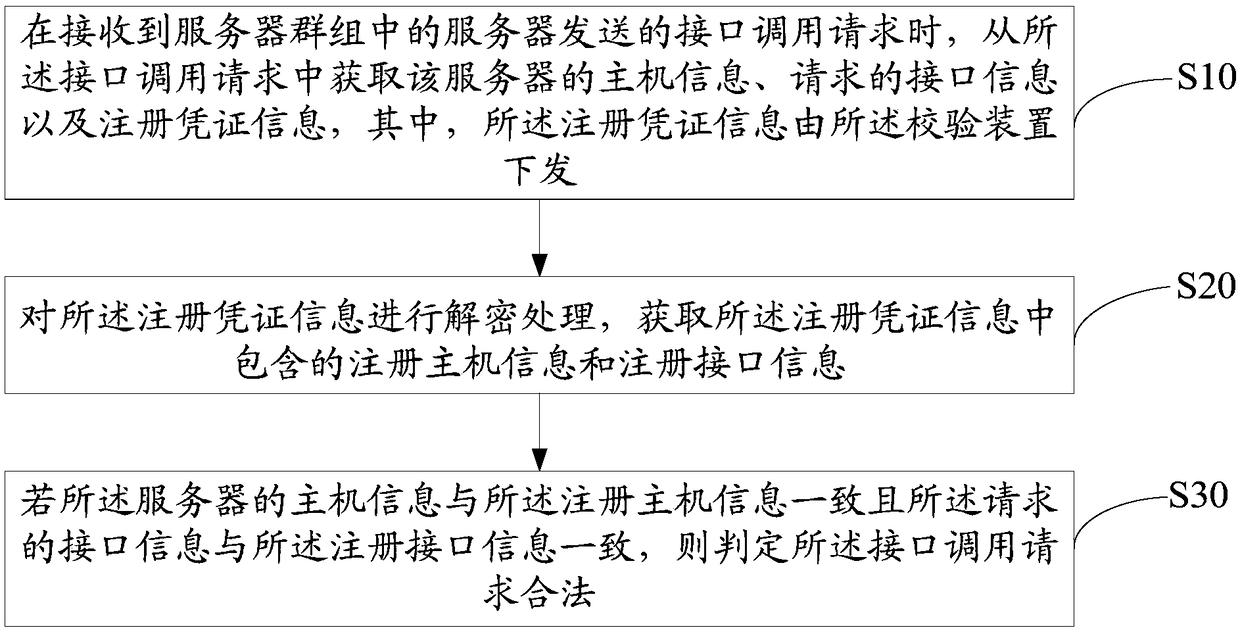
[0044] The invention provides a verification device for request legality. refer to figure 1 As shown, it is a schematic diagram of a preferred embodiment of a device for verifying the validity of a request in the present invention.
[0045]In this embodiment, the device for verifying the validity of the request may be any server in the server group. The device for verifying the legality of the request at least includes a memory 11 , a processor 12 , a communication bus 13 , and a network interface 14 .
[0046] Wherein, the memory 11 includes at least one type of readable storage medium, and the readable storage medium includes flash memory, hard disk, multimedia card, card-type memory (eg, SD or DX memory, etc.), magnetic memory, magnetic disk, optical disk, etc. In some embodiments, the storage 11 may be an inter...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com