Blockchain digital signature method and device based on distributed storage
A distributed storage and digital signature technology, which is applied in the field of computer communication, can solve the problems of easy theft of user information, poor security, and difficulty in verifying the integrity of files, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0029] see figure 1 , a distributed storage-based blockchain digital signature method provided in Embodiment 1 of the present invention, such as figure 1 As shown, the method includes:
[0030] S101: The sending node generates a public key and private key pair; roles in the blockchain provided by this application include peer nodes (peers), orderers, client applications, administrators, and so on. The identities of these participants are encapsulated in digital certificates conforming to the X.509 standard, which determine their specific rights as participants in the network. Each identity is verifiable (that is to say, it must be a real identity), and these identities are authorized to receive the node membership distribution verification system. The system uses X.509 standard certificates as identities and adopts the traditional public key infrastructure (PKI) layered model.
[0031] S102: The sending node performs a hash operation on the identity data information to gene...
Embodiment 2
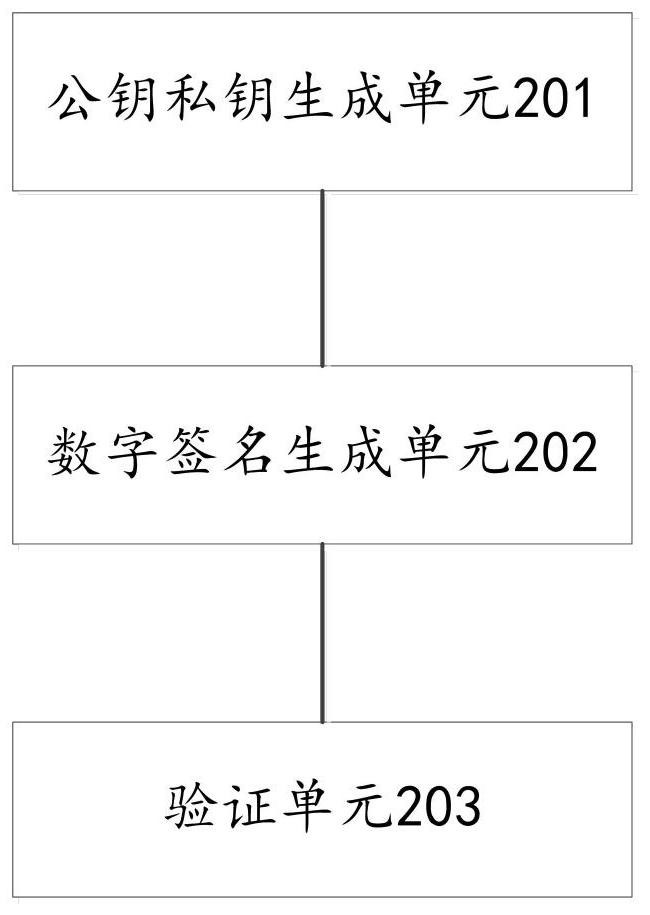
[0038] Corresponding to the blockchain digital signature method based on distributed storage provided in Embodiment 1 of the present invention, Embodiment 2 of the present invention also provides a blockchain digital signature device based on distributed storage. Please refer to figure 2 , is a schematic diagram of a distributed storage-based blockchain digital signature device provided according to an embodiment of the present invention, such as figure 2 As shown, the device includes:
[0039] A public key and private key generating unit 201, configured for the sending node to generate a public key and private key pair;
[0040] The digital signature generating unit 202 is used for the sending node to perform a hash operation on the identity data information to generate abstract information, and use the private key to process the abstract information to generate digital signature information;
[0041] The verification unit 203 is configured to broadcast the digital signat...
Embodiment 3
[0048] Embodiment 3 of the present application also provides a processor, the processor is used to run a program, wherein the distributed storage-based blockchain digital signature method is executed when the program is running.
[0049]It can be known from the above description of the implementation manners that those skilled in the art can clearly understand that the present application can be implemented by means of software plus a necessary general-purpose hardware platform. Based on this understanding, the essence of the technical solution of this application or the part that contributes to the prior art can be embodied in the form of software products, and the computer software products can be stored in storage media, such as ROM / RAM, disk , CD, etc., including several instructions to make a computer device (which may be a personal computer, server, or network device, etc.) execute the methods described in various embodiments or some parts of the embodiments of the presen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com