Cloud data deduplication method based on edge cloud collaboration
A technology of cloud data and edge nodes, applied in digital transmission systems, user identity/authority verification, secure communication devices, etc., can solve the problems of data insecurity and deduplication efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
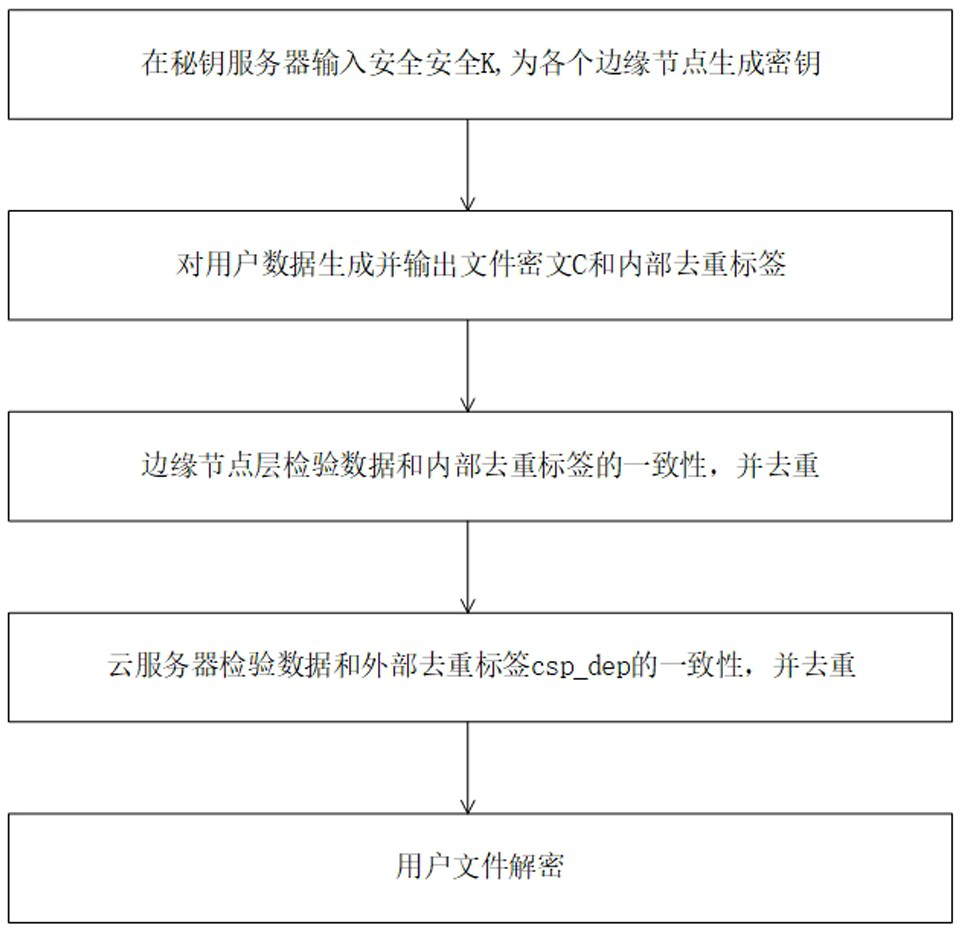
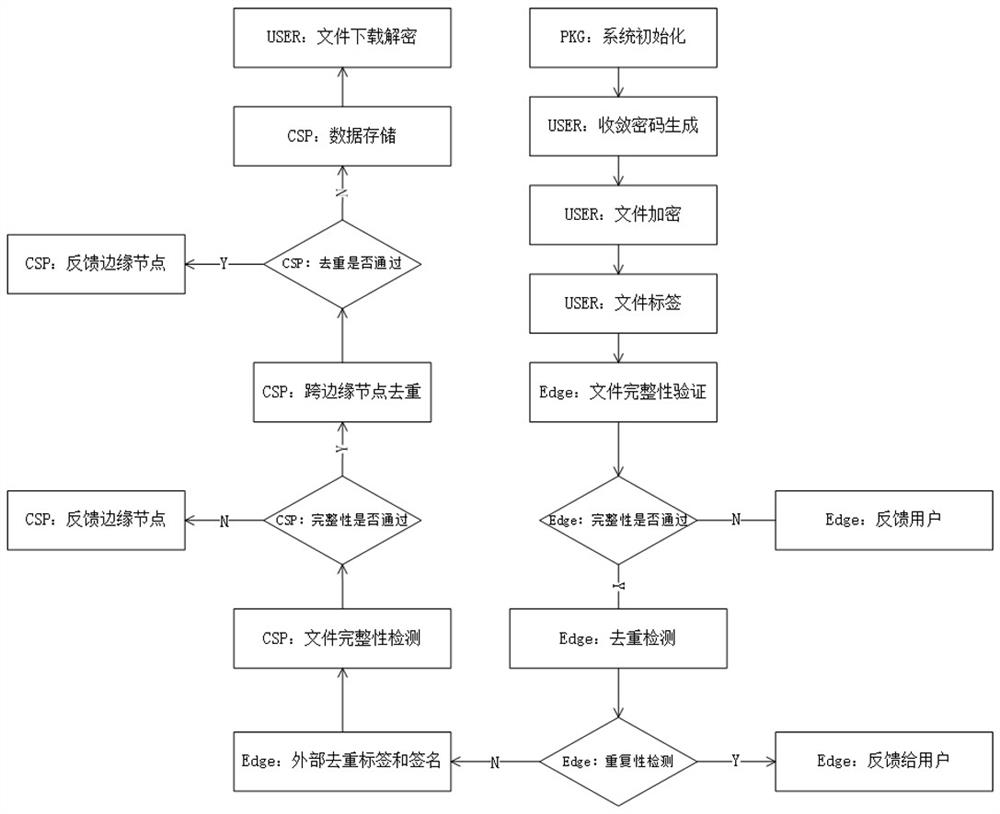
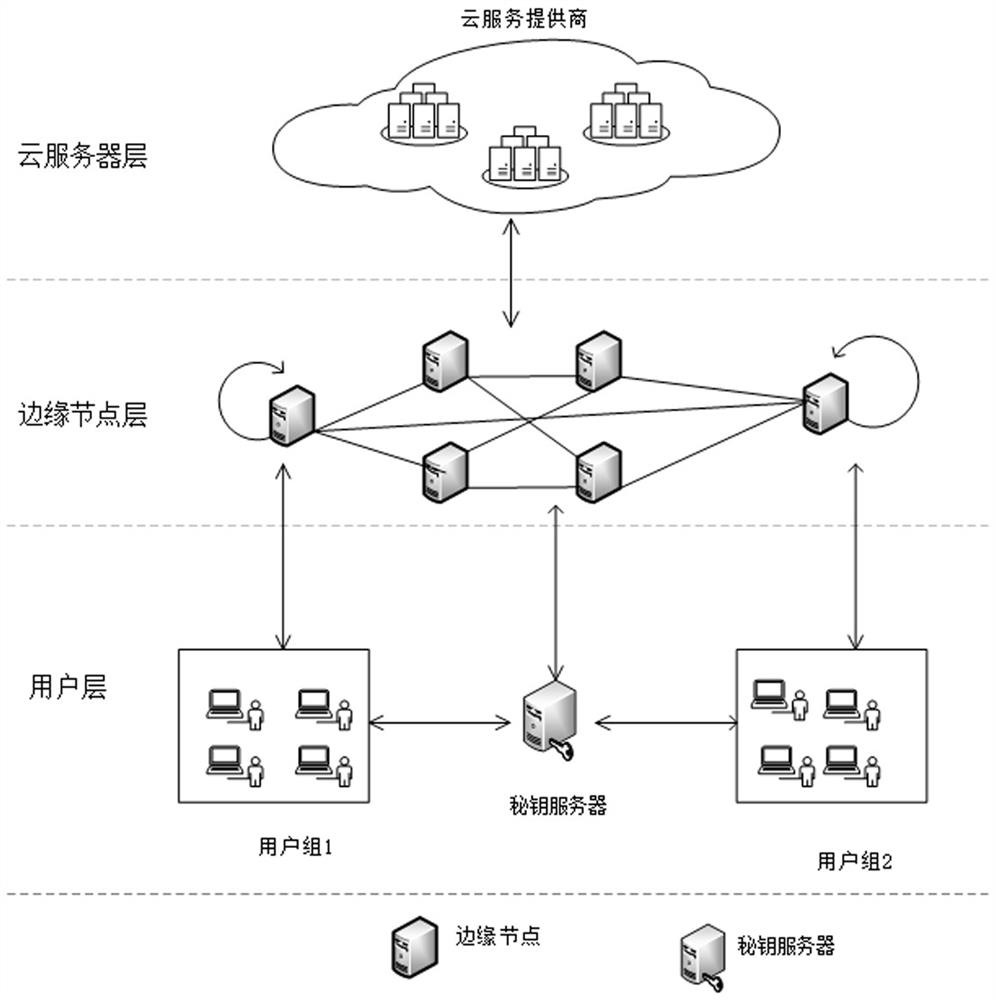
[0039] Such as figure 1 , figure 2 , image 3 , Figure 4 and Figure 5 As shown, the cloud data deduplication method based on edge-cloud collaboration of the present invention includes the following steps:
[0040] A. Input the security parameter k in the key server to generate keys for each edge node.
[0041] Such as image 3 As shown, the system model of the present invention includes four entities: user, key server, edge node and cloud server. Users mainly include user groups based on the coverage of edge nodes. Each user may have two roles. When it is uploading data, it is the first uploader, and after passing the deduplication request, it is the later uploader. The user's functions mainly include encryption key blinding, data encryption, data label generation, data deduplication challenge generation, data upload and download, data decryption and verification. The main function of the key server is to generate the private key and the application's internal dedu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com