Credible database integrity protecting method and system
An integrity protection and database technology, applied in the field of database security, can solve problems such as loss, and achieve the effect of reducing the impact and improving the strength of integrity protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] The specific implementation of the key technical modules described in the summary of the invention will be explained below as examples, but the scope of the invention will not be limited by this explanation.
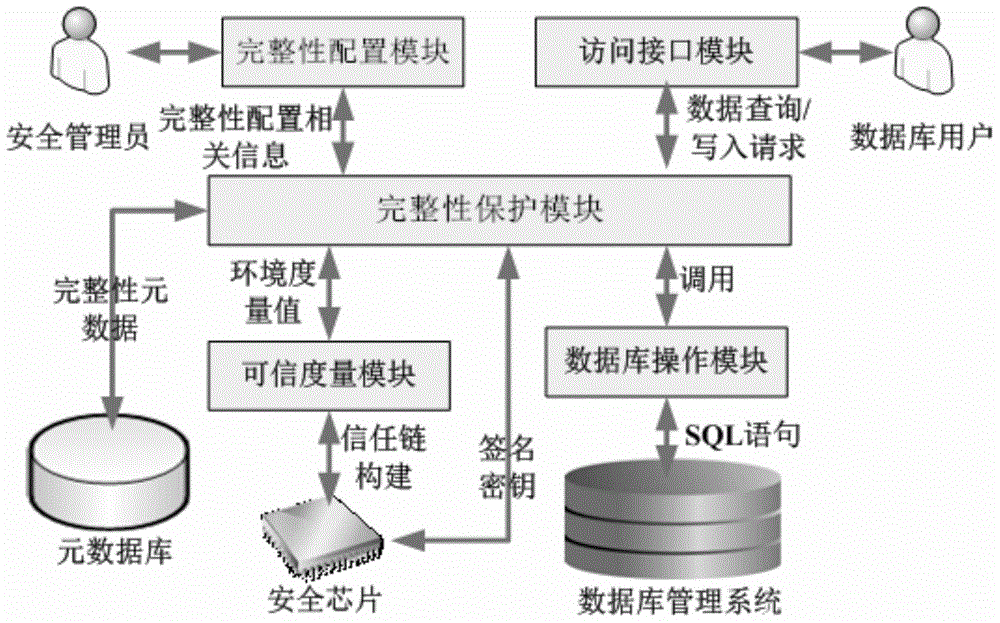
[0032] For the technical architecture of the present invention, see figure 1, mainly including a security chip, a trusted measurement module, an integrity protection module, a metadata database, an integrity configuration module, an access interface module and a database operation module.
[0033] Firstly, introduce the two basic modules, the security chip module and the trusted measurement module. The present invention needs to use some of the functions provided by them, but the implementation of the modules themselves is not within the scope of the present invention. The functions involved in the present invention will be explained below.
[0034] 1. Security chip
[0035] The functions or mechanisms that need to be provided by the security chip in the present...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com