Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
126results about How to "Improve system security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Network Access Protection
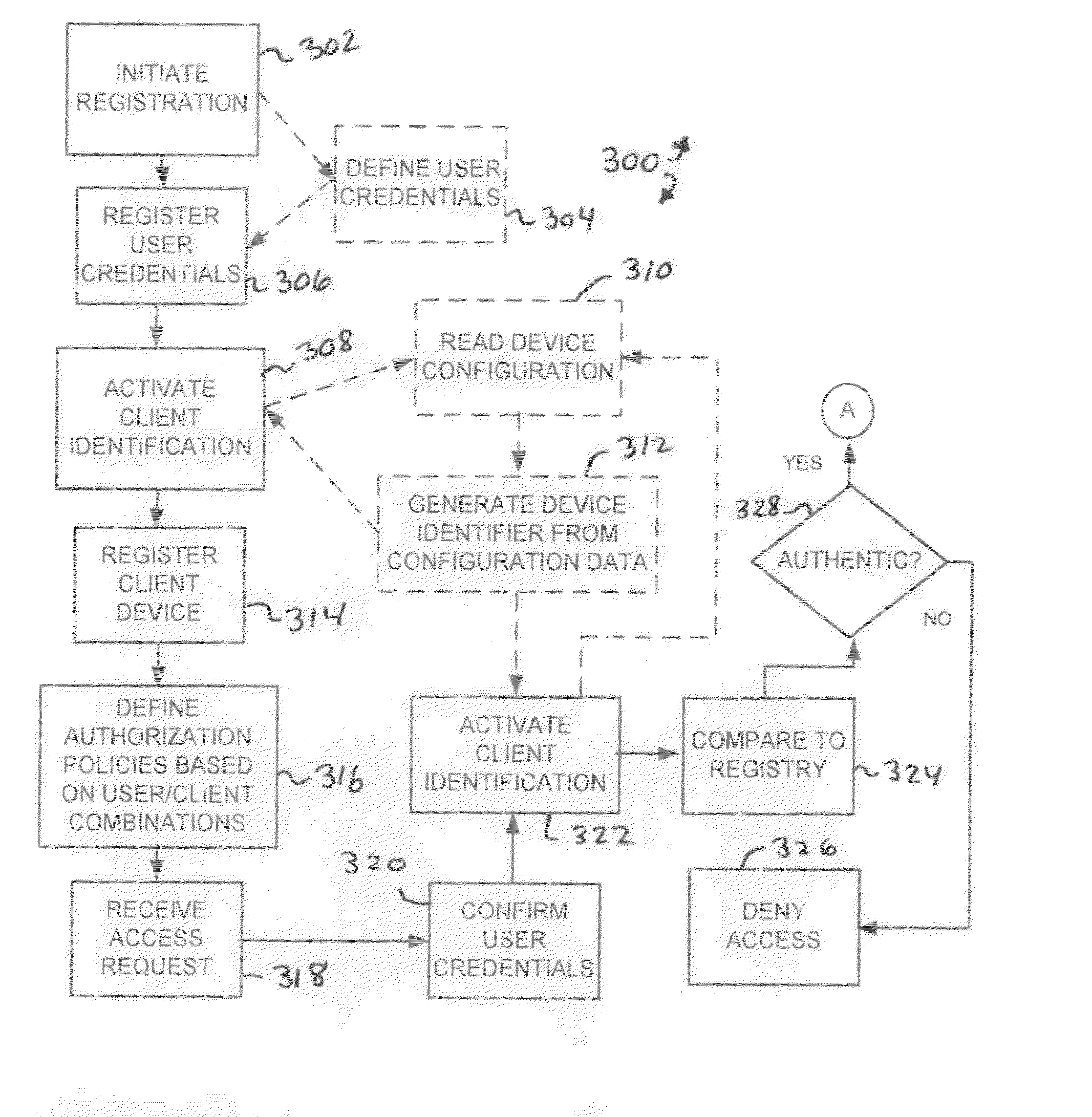
ActiveUS20100325710A1Impossible to guessImprove system securityDigital data processing detailsUser identity/authority verificationNetwork Access ProtectionPassword
A system or method for network access protection executes steps for receiving, at a server, an access request for access to at least one network resource from a client machine, the access request including account authentication information comprising an account identifier and password, obtaining a client machine identifier from the client machine in response to receiving the request for access, and controlling access to the network resource in response to the access request by authorizing access to the network resource for the access request if the client machine identifier matches a registered machine identifier that is registered for use with the account authentication information and the account authentication information matches registered information for a valid account, but denying access to the network resource if the client machine identifier does not match a registered client machine identifier that is registered for use with the account authentication information.
Owner:DEVICE AUTHORITY LTD
Docker implementing system and communication method thereof
ActiveCN105376303AReduce the risk of attackImprove system securityNetworks interconnectionSoftware simulation/interpretation/emulationMessage passingSystem safety
The invention provides a Docker implementing system and a communication method thereof. The Docker implementing system comprises a management VPC and a user VPC. Each VPC comprises a virtual routing device and a virtual machine. The management VPC comprises a VPC management module, a control node, a container database, and a configuration service discovery storage system. The virtual machine of the user VPC is provided with a local container management module, a proxy module, and containers. The containers are used for storing the application of a user. A safe tunnel is provided between the virtual routing device of the management VPC and the virtual routing device of the user VPC. The control node sends messages to the virtual machine of the user VPC via the safe tunnel between the virtual routing device of the management VPC and the virtual routing device of the user VPC. The virtual machine of the user VPC transmits the messages to the local container management module of the virtual machine of the user VPC. The Docker implementing system may reduce a risk that the application of the user is attacked by other users and improve system security.
Owner:CLOUDMINDS SHANGHAI ROBOTICS CO LTD
Translation Engine for Computer Authorizations Between Active Directory and Mainframe System
InactiveUS20080263640A1Extended processing timeImproved security flexibilityDigital data processing detailsComputer security arrangementsComputer accessMainframe computer
The invention provides a method and system of implementing a high performance “non-RACF external security-manager product,” which maintains and translates a merged single source of authorizations to both mainframe and Microsoft Windows Active Directory (AD) systems. In one embodiment, a method comprises generating at a server computer access information for a mainframe computer indicative of mainframe authorization for a set of users, receiving from the mainframe computer information indicative of an authorization request, the information indicative of the authorization request identifying a user trying to access the mainframe computer, and sending at least a portion of the access information from the server computer to the mainframe computer, the portion of the access information including mainframe access information for the user.
Owner:REDPHONE SECURITY INC
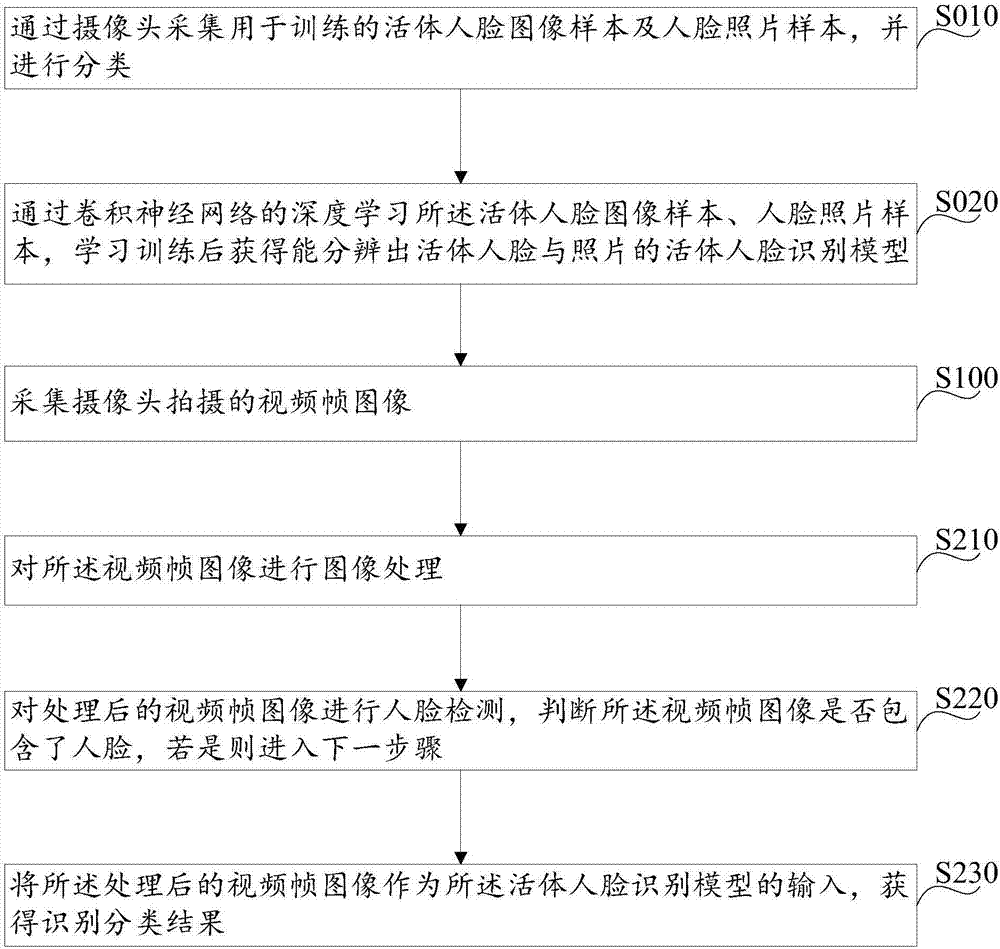
Live face identification method and system
InactiveCN107066942AImprove system securityShorten recognition timeNeural learning methodsSpoof detectionFace detectionDeep learning
The invention discloses a live face identification method. The method comprises steps that video frame images shot by a camera are acquired; whether the video frame images are live face images can be identified through a trained convolutional neural network. The invention further discloses a live face identification system, the system comprise a camera module, an acquisition module and a live face detection module, wherein the acquisition module is connected with the camera module and the live face detection module, the acquisition module is used for sampling videos shot by the camera module to acquire the video frame images, and the live face detection module is used for detecting and identifying whether the video frame images are live face images through the trained convolutional neural network. The method and the system are advantaged in that brains of human beings are simulated through employing a depth learning neural network, whether the video frame images are live face images is identified through the trained convolutional neural network, whether the images are live faces or pictures can be identified through intuition of a computer to a great degree but not a designed algorithm, so algorithmic defects can be avoided, and identification accuracy is substantially improved.
Owner:PHICOMM (SHANGHAI) CO LTD
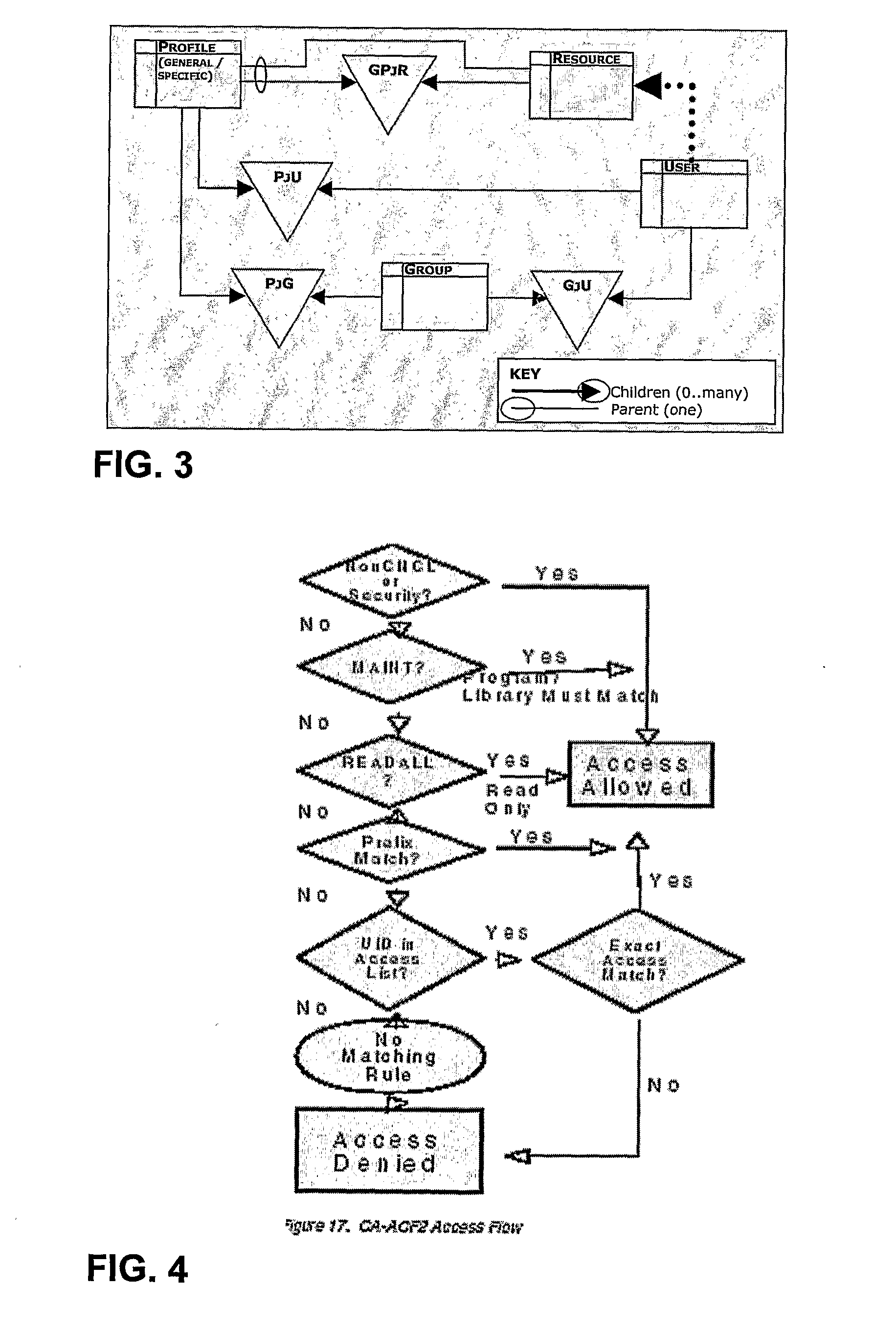
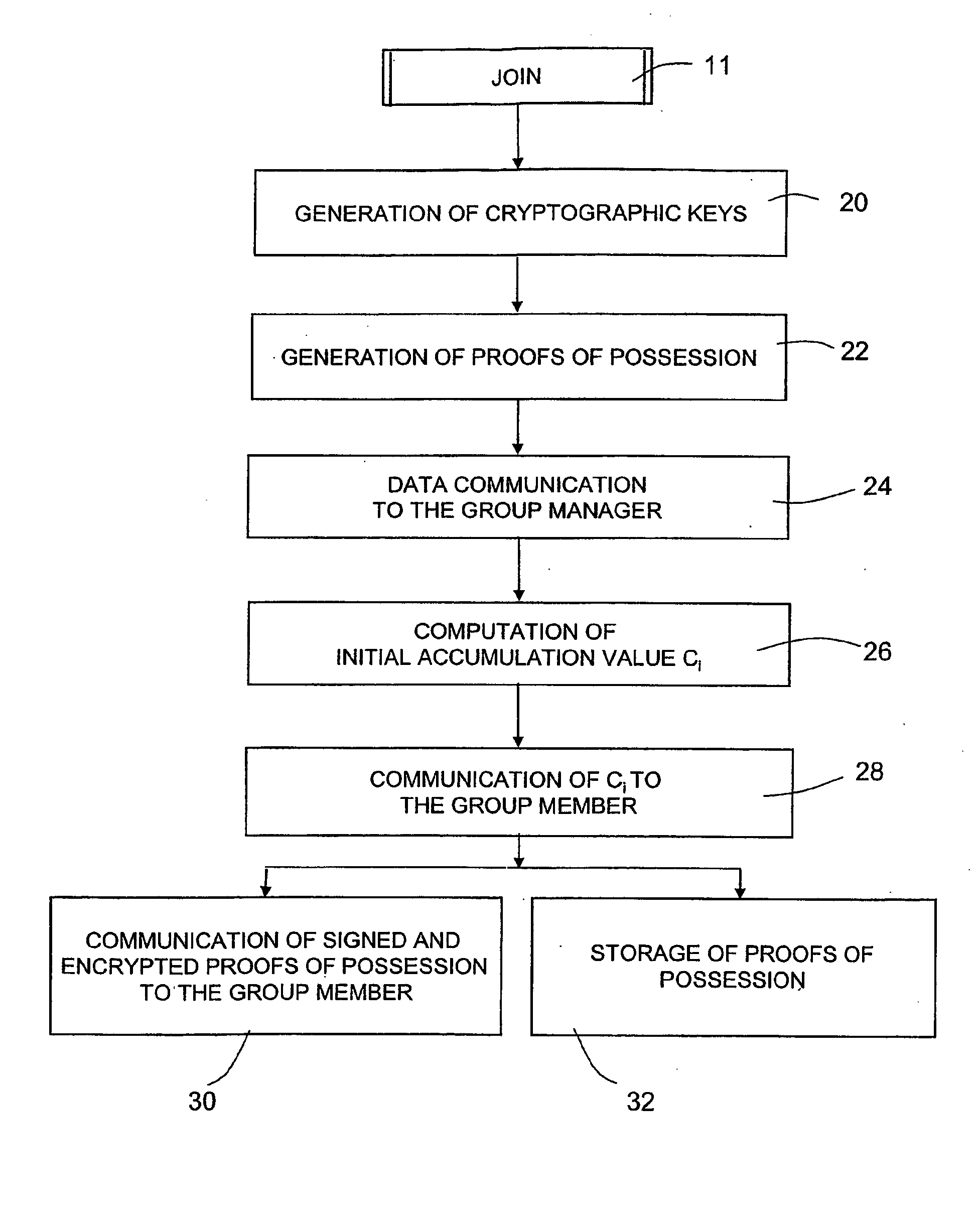
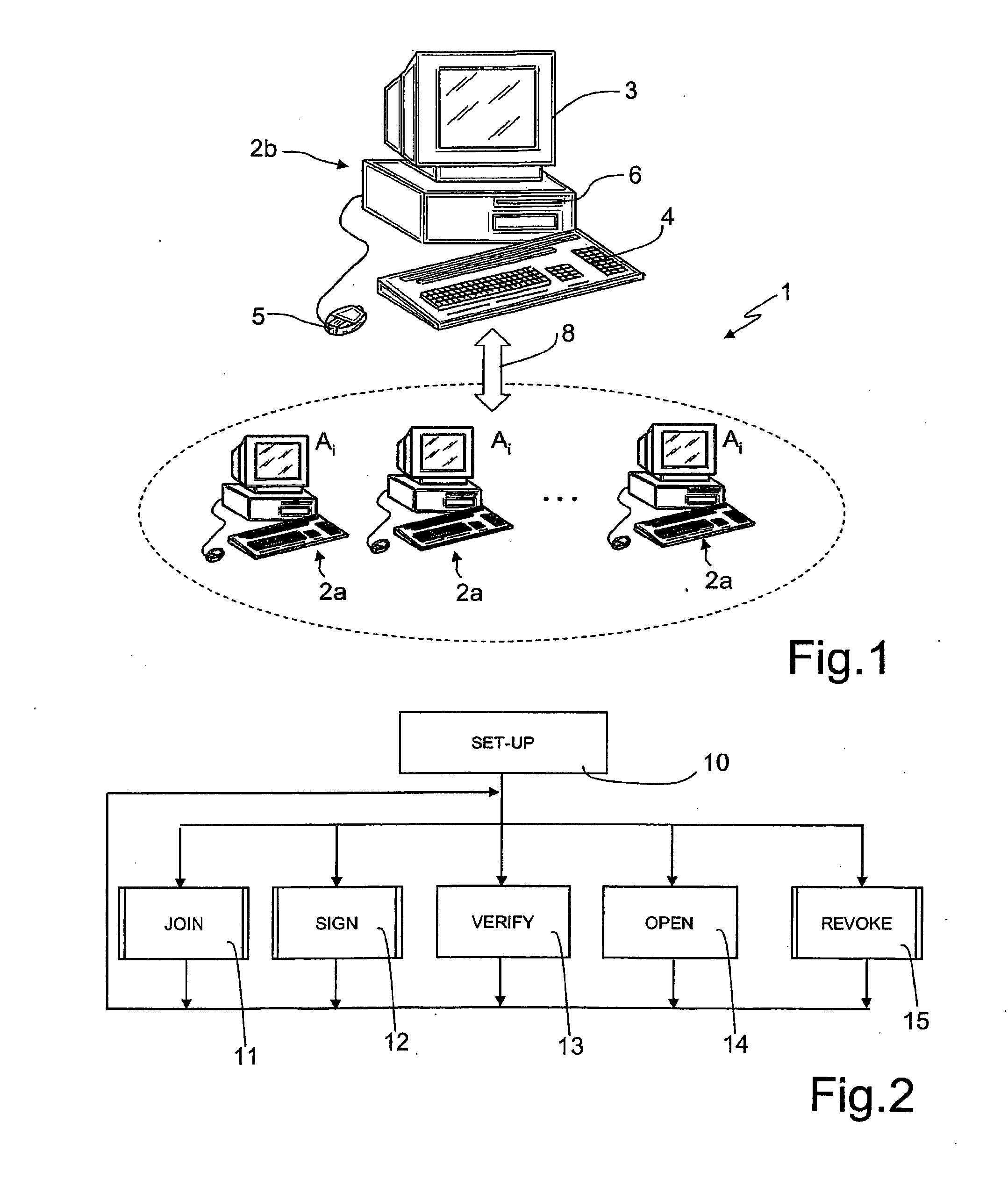
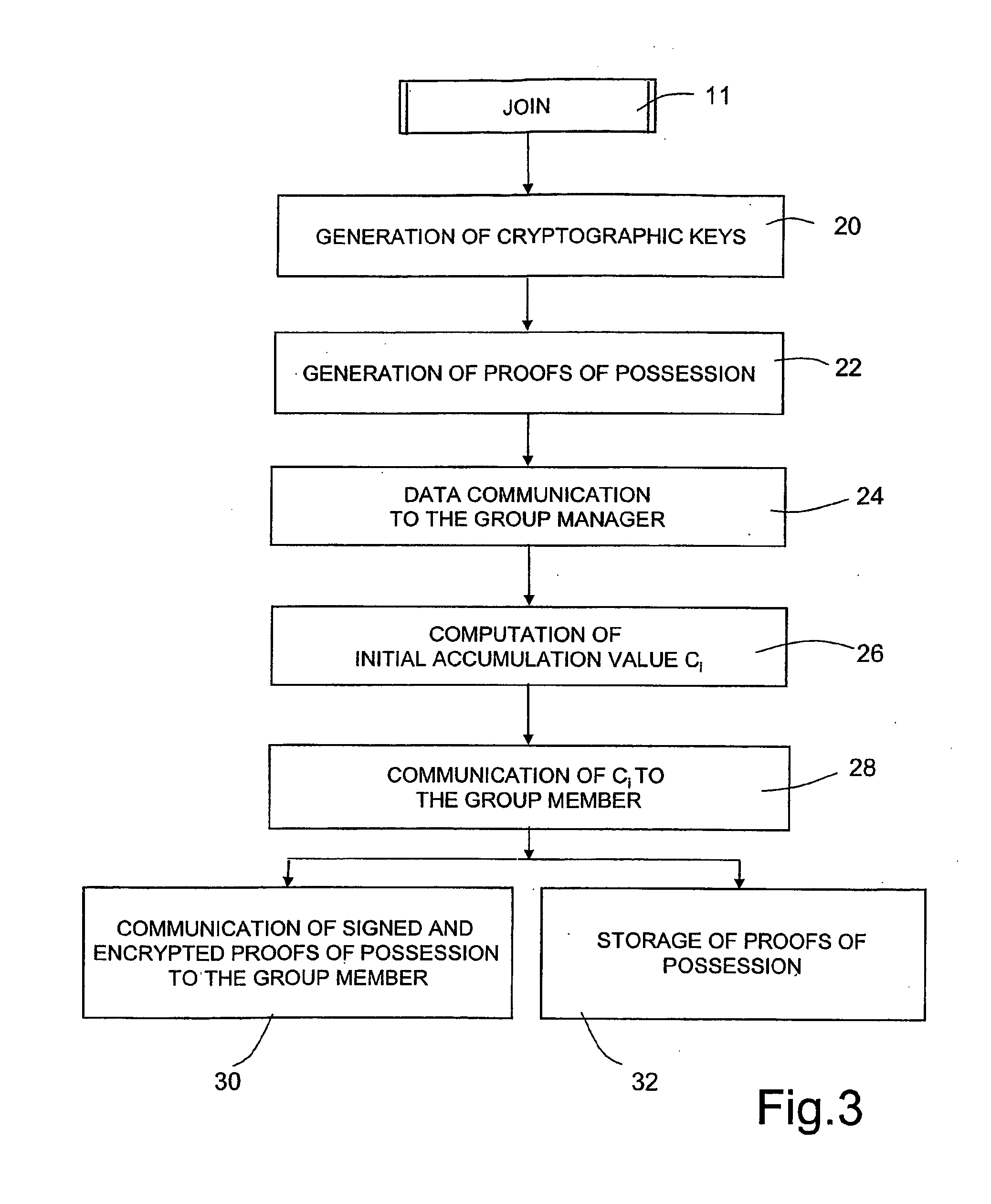
Group Signature Scheme With Improved Efficiency, in Particular in a Join Procedure
ActiveUS20090222668A1Avoiding possible attackImprove system securityKey distribution for secure communicationMultiple keys/algorithms usageGroup signatureDistributed computing
A method for managing a group signature scheme includes in a setup procedure for group initialization, generating, by a group manager, a group public key. In a join procedure for the group manager to add a new member to the group, the method includes generating by the new member, user information, and providing the generated user information to the group manager, and computing, by the group manager, membership information for the new member based on the user information received by the new member and on the group public key, and providing to the new member the computed membership information. In particular, the membership information is computed, by the group manager, as a function of the inverse of a given hash function of the user information. In a signing procedure for a group member to sign a message on behalf of the group, the method includes: using, by the group member, the membership information and the user information. The method further includes the use of digital certificates, in order for the group member to prove to the group manager the possession of said user information.
Owner:TELECOM ITALIA SPA
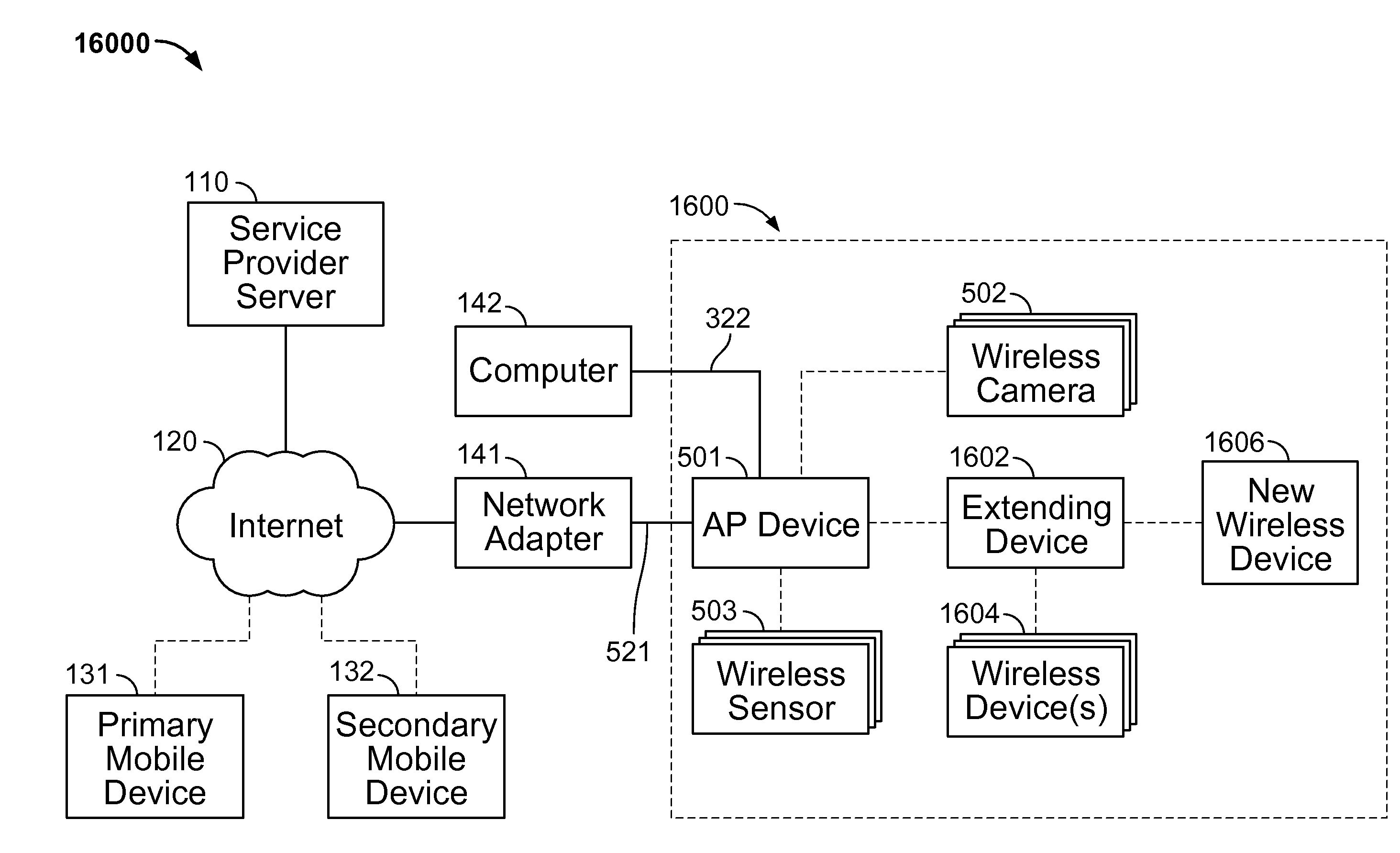
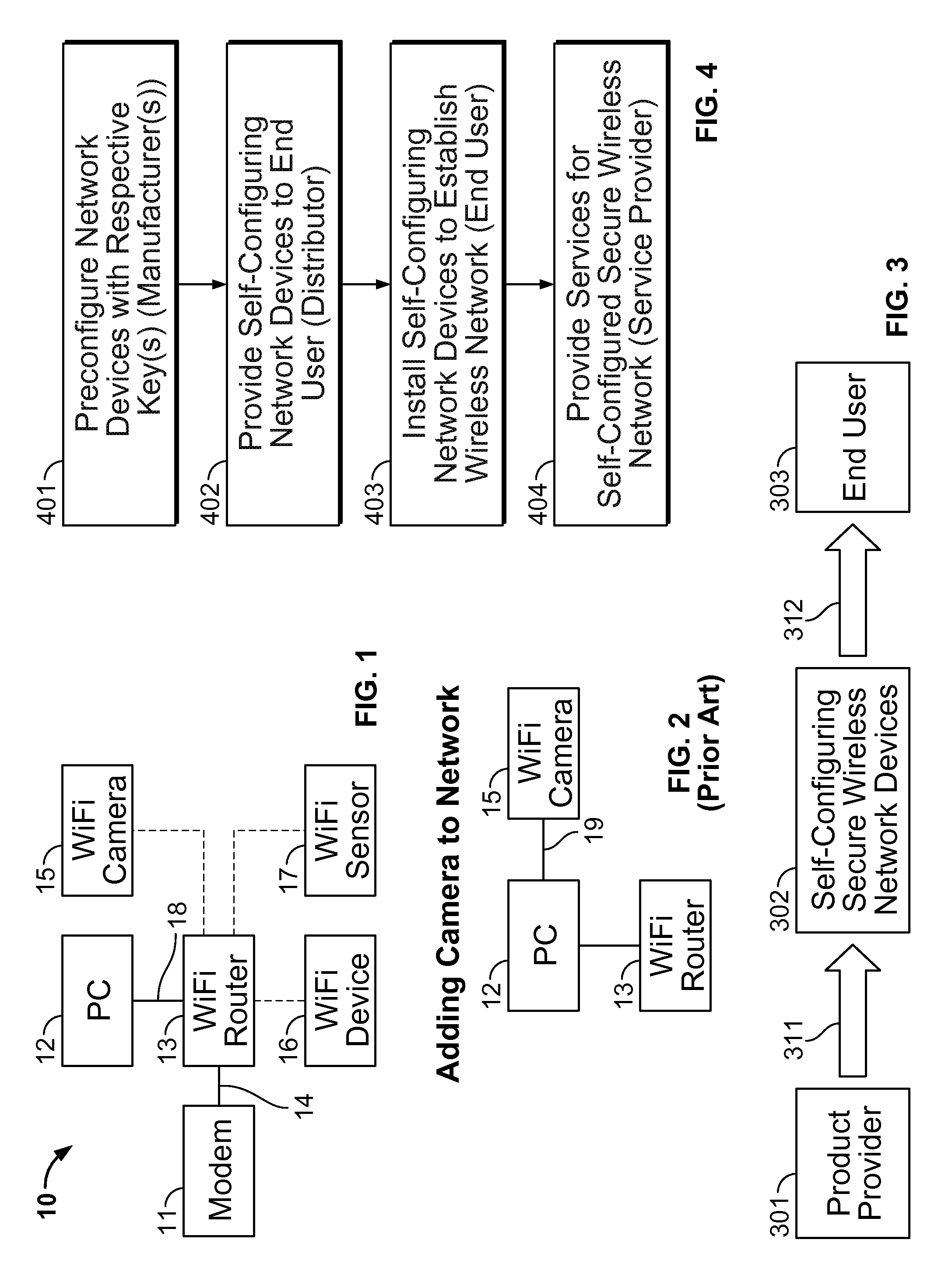
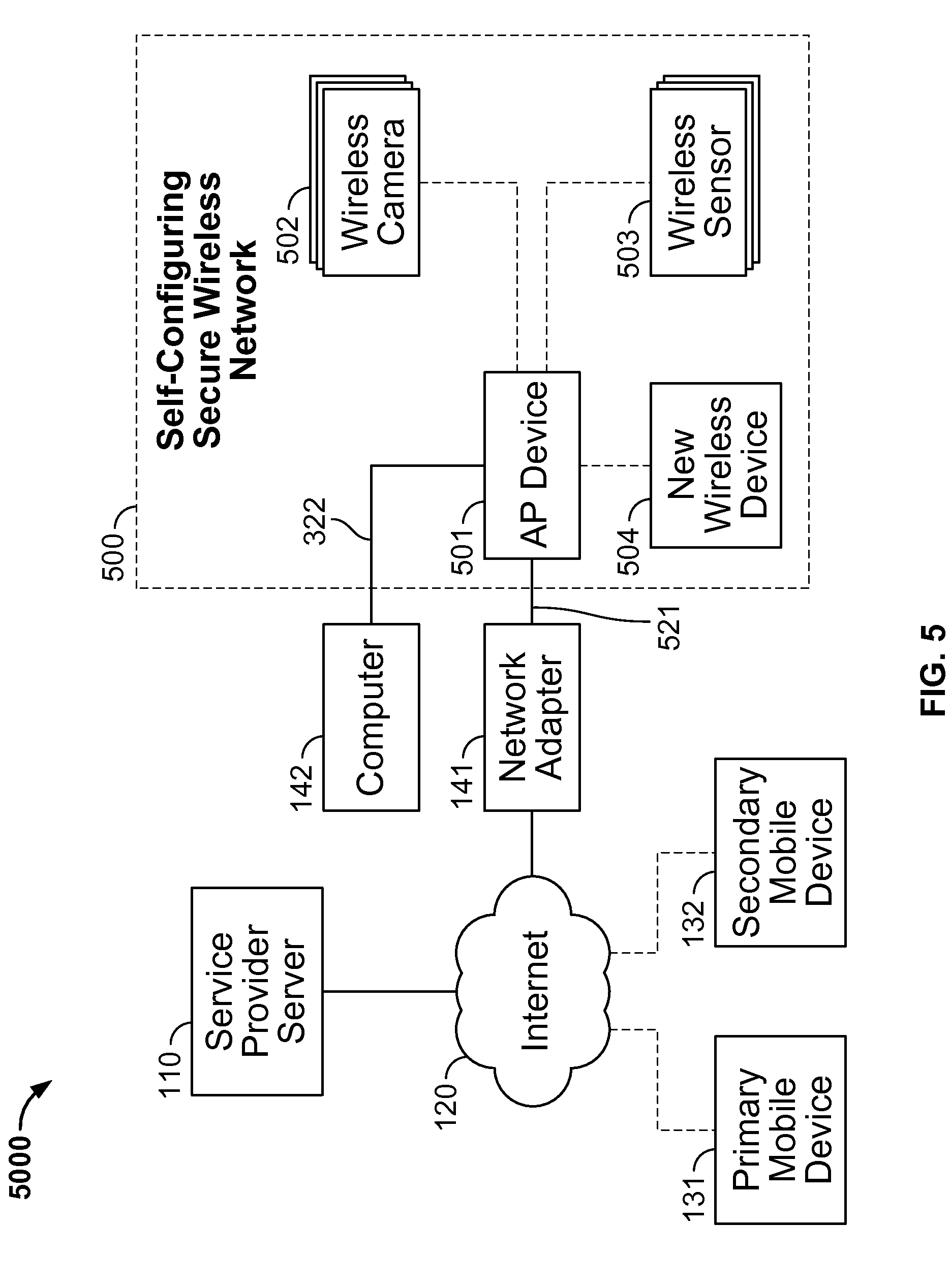
Self-configuring wireless network
InactiveUS20140247941A1Improve system securityImprove securityNetwork topologiesSecret communicationComputer networkPointing device
Methods, systems, and apparatus, are provided for wireless networking. In some implementations, a self-configuring wireless system includes one or more wireless network devices; and an access point device, wherein the one or more wireless network devices are each preconfigured with a respective key, and wherein the access point device is configured to obtain the respective keys so as to enable the access point device to establish a secure wireless network with the one or more network devices using the respective keys upon powering up the access point device and the one or more wireless network devices at a user location.
Owner:MIVALIFE MOBILE TECH
Self-adaption method of zero compensation detection of rotary transformer of permanent magnet motor
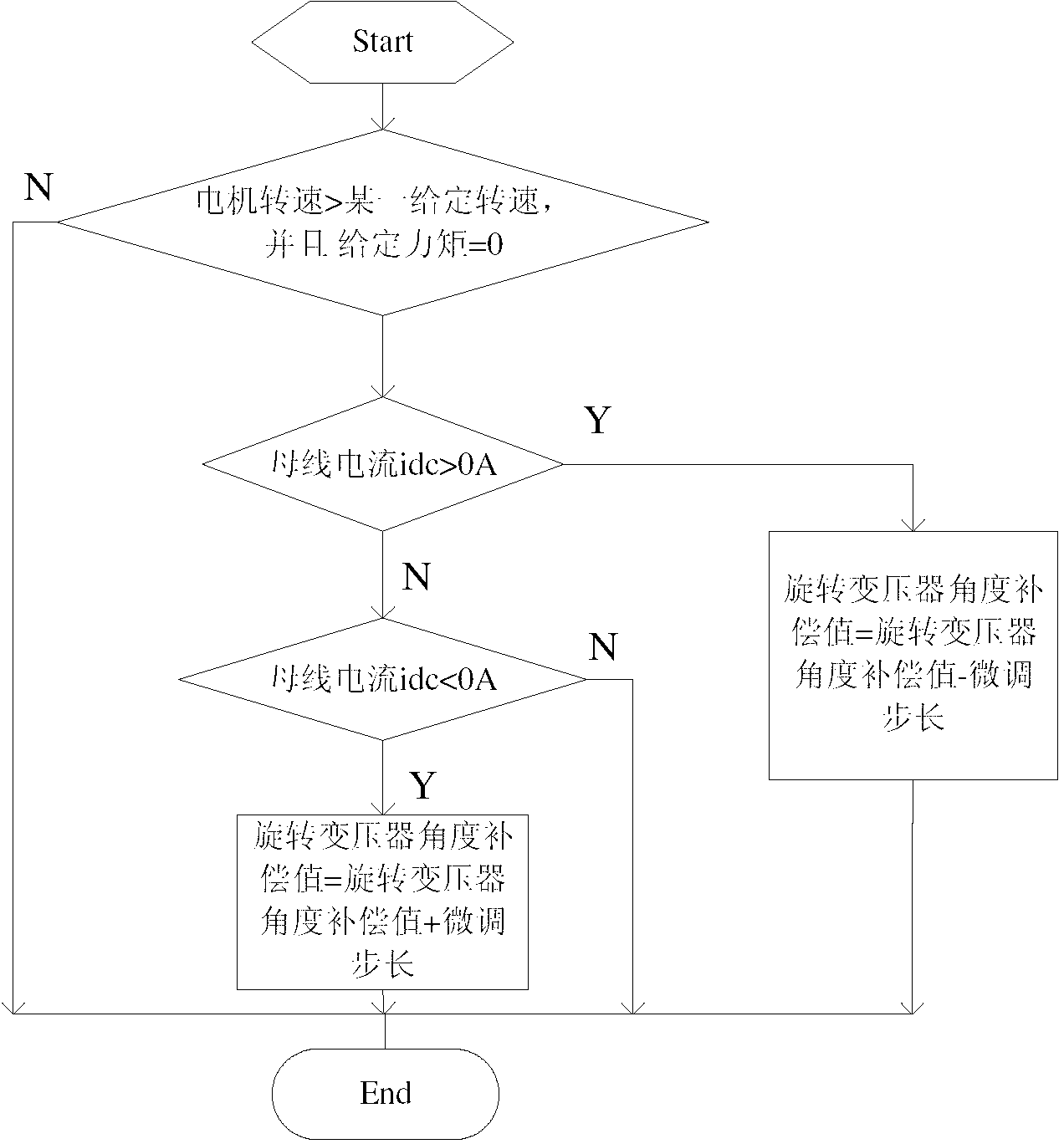
ActiveCN103151982AHigh precisionImprove system securityElectronic commutation motor controlVector control systemsPhase currentsElectric machine
The invention discloses a self-adaption method of zero compensation detection of a rotary transformer of a permanent magnet motor. The rotary transformer detects the rotate speed, the direction of rotation and the rotor position of the permanent magnet motor; three current sensors respectively detect direct current bus current Idc, motor V-phase current Iv and motor U-phase current Iu, and rotor d shaft current Id and rotor q shaft current Iq are obtained by means of CLARK conversion and PARK conversion through a micro-programming controller; the permanent magnet motor is adjusted to be in a zero torque control mode, at the moment the Id equals to flux-weakening current and the Iq equals to zero; when a magnetic field of the permanent magnet motor is zero position alignment, the Idc is approximate to zero; in case that the zero position of the magnetic field deviates, the Idc is not approximate to zero; a rotary transformer deviation angle is regulated and rotated through the micro-programming controller until the Idc is approximate to zero and a rotor of the permanent magnet motor and a d shaft coincide. The self-adaption method can detect the accurate position of a motor rotor in real time, avoids a process of zero compensation manual calibration, improves torque control accuracy of a motor and system security, and is suitable for mass manufacturing of the motor.
Owner:SHANGHAI DAJUN TECH
Liquid filling system with improved set-up and fill weight calibration/verification capabilities
InactiveUS6941981B2Improve system securityImprove accuracyLiquid fillingSolid materialProduction rateEngineering
An improved method and apparatus for a liquid filling system is herein disclosed incorporating means for generating greater overall production rate efficiencies (i.e. number of filled containers per minute per filling station) for automatic systems utilizing diverter valve and / or walking beam (i.e. continuous-motion) filling technologies with, for example, non-traditional ratios between the number of filling stations and the number of filling nozzles. The methods / apparatus disclosed herein also incorporate means to more efficiently changeover and clean up, in either a clean-in-place (CIP) or clean-out-of-place (COP) configuration, the product contact parts that become “dirty” when used in a production environment. Finally, an improved method and apparatus designed to provide a means for priming and air purging the product contact path of liquid filling machinery, a fill volume calibration procedure, and a fill weight verification cycle is also herein described.
Owner:ROSEN ROBERT A
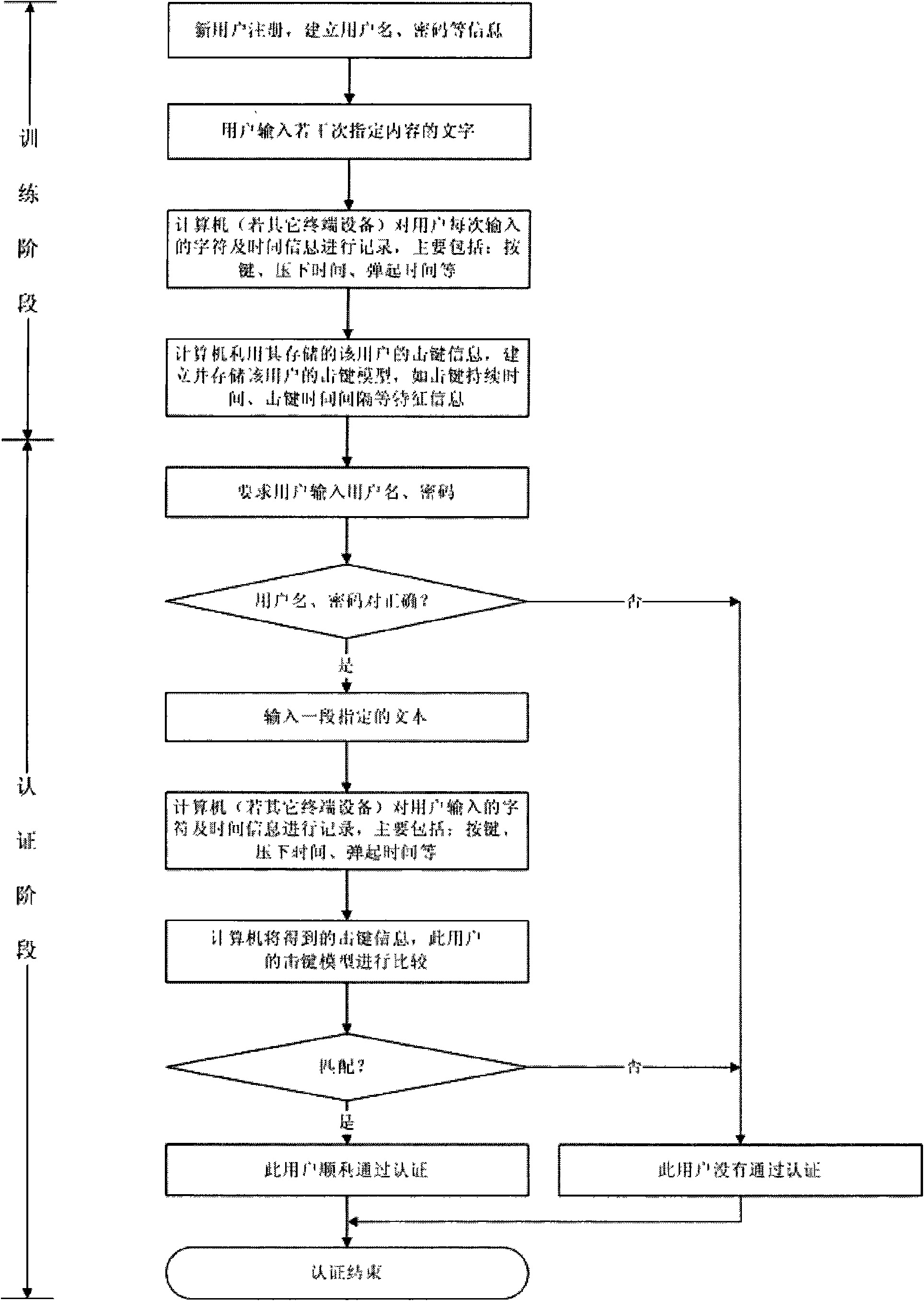
Method for identity identification according to characteristics of user keystroke
InactiveCN101557287AReduce the possibilityImprove system securityUser identity/authority verificationPasswordTerminal equipment
The invention relates to a method for identity identification of a user of a computer and other terminal devices, in particular to a method for identity identification of users in the network world in the inputting process through a keyboard. The method is characterized in that a method for identification according to the characteristics of a user keystroke is added on the basis of a traditional username / password pair identification mechanism. Due to the adoption of the method, the safety of the system can be enhanced, and the disabled users are prevented from logging in by the identity of a validated user to access the resources in the system; and even if the disabled user knows the username / password pairs of the validated user, since the keystroke characteristic of the validated user is generally different from that of the user corresponding to the username / password pairs, the authentication is not available, therefore, the provided identification method has higher security.
Owner:冀连有 +1
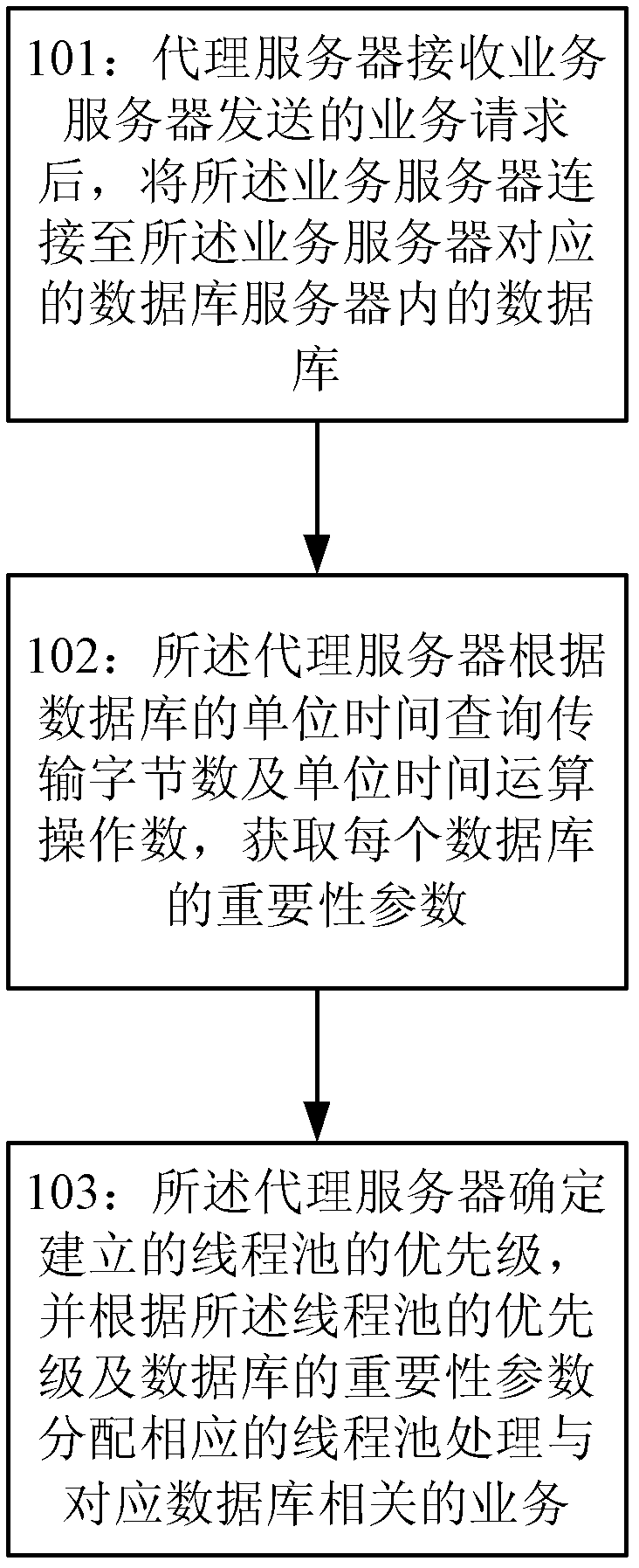
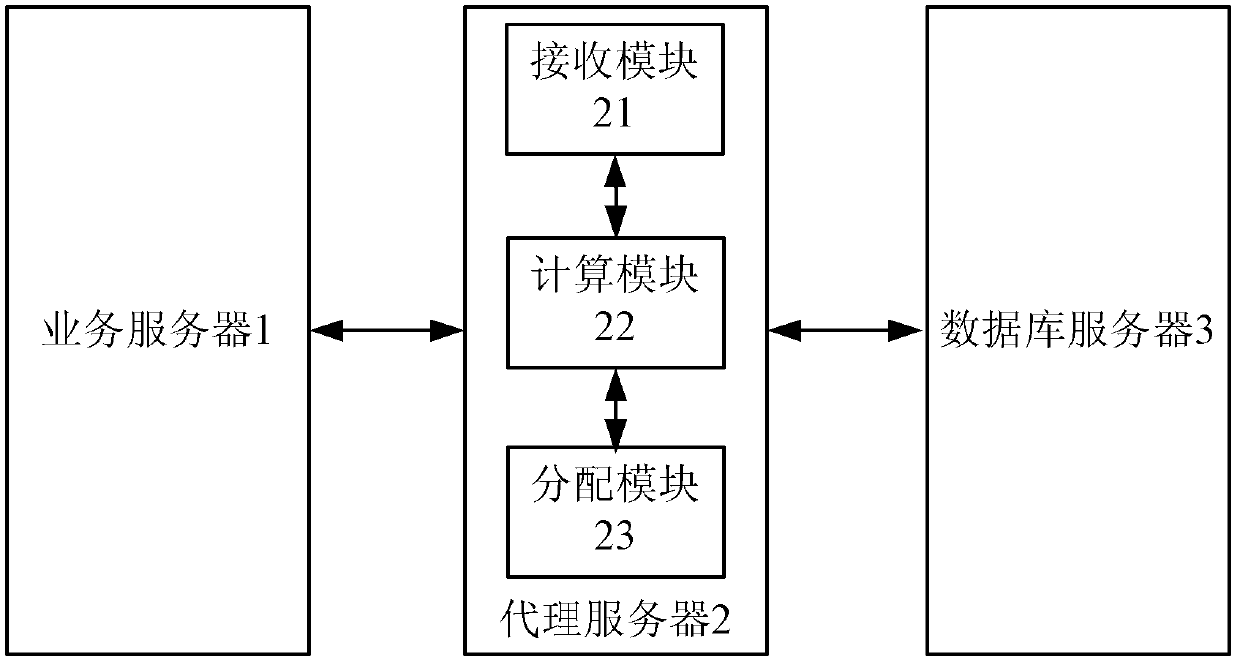
Agent method and system for connecting databases
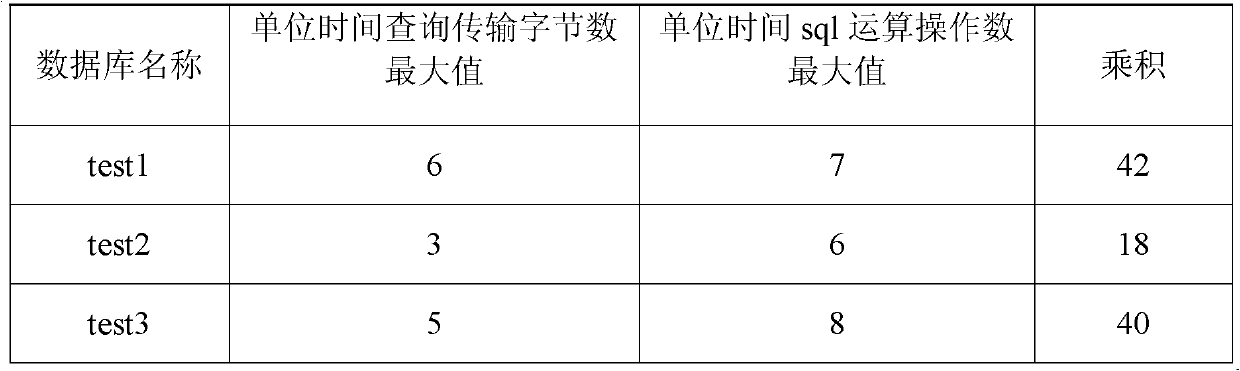
InactiveCN102594798APrevent leakageImprove system securityTransmissionSpecial data processing applicationsThread poolDatabase server
The invention provides an agent method and an agent system for connecting databases. The method comprises the following steps that: an agent server receives a service request sent by a service server and connects the service server to the databases in a database server corresponding to the service server; the agent server acquires an importance parameter of each database according to a unit time inquiry transmission byte number and a unit time operation number of each database; and the agent server determines the priority level of an established thread pool and distributes corresponding thread pool processing and relevant services corresponding to the databases according to the priority level of the thread pool and the importance parameters of the databases.
Owner:SUZHOU CODYY NETWORK SCI & TECH
Monitoring the flow of a data stream
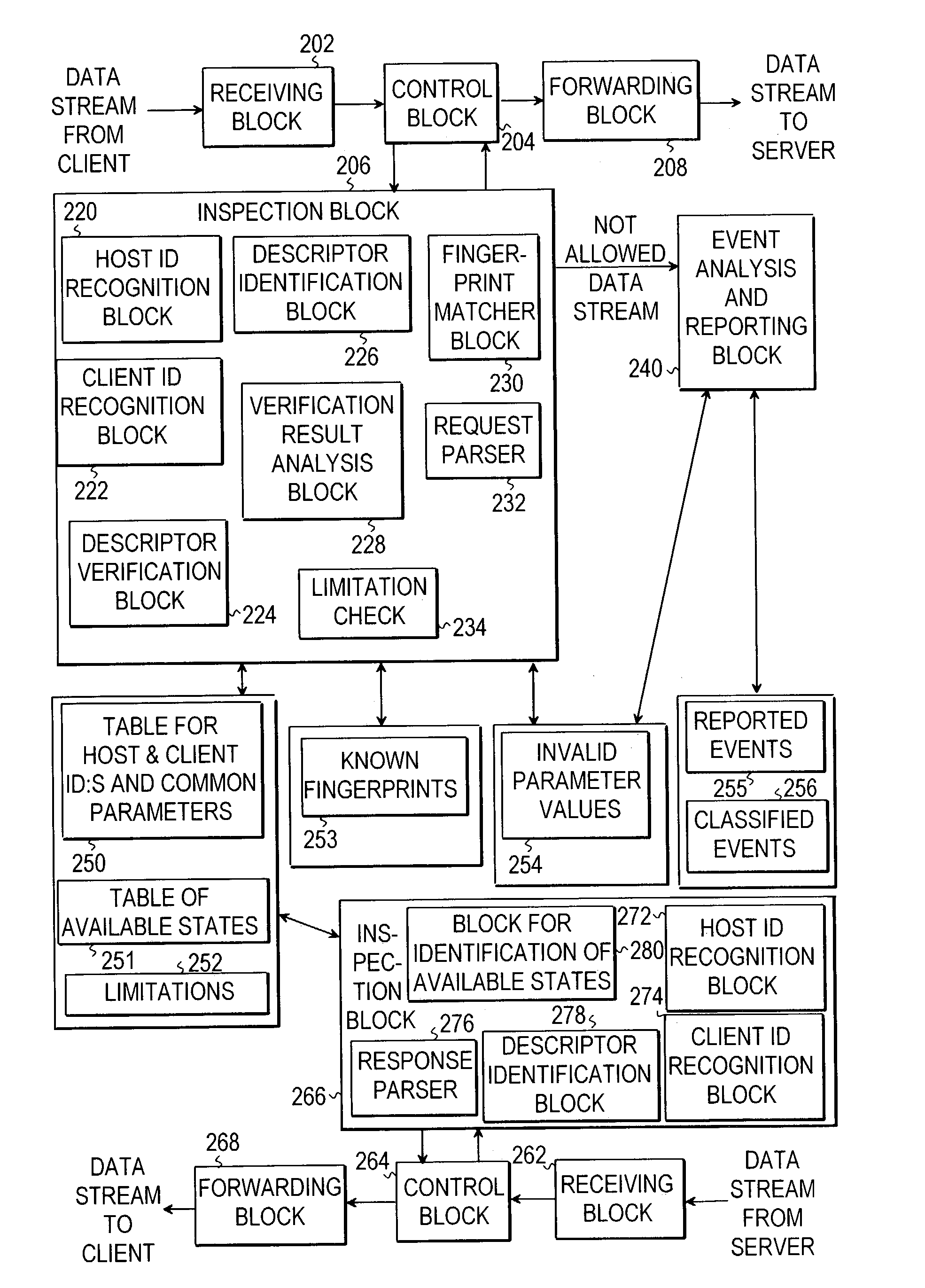
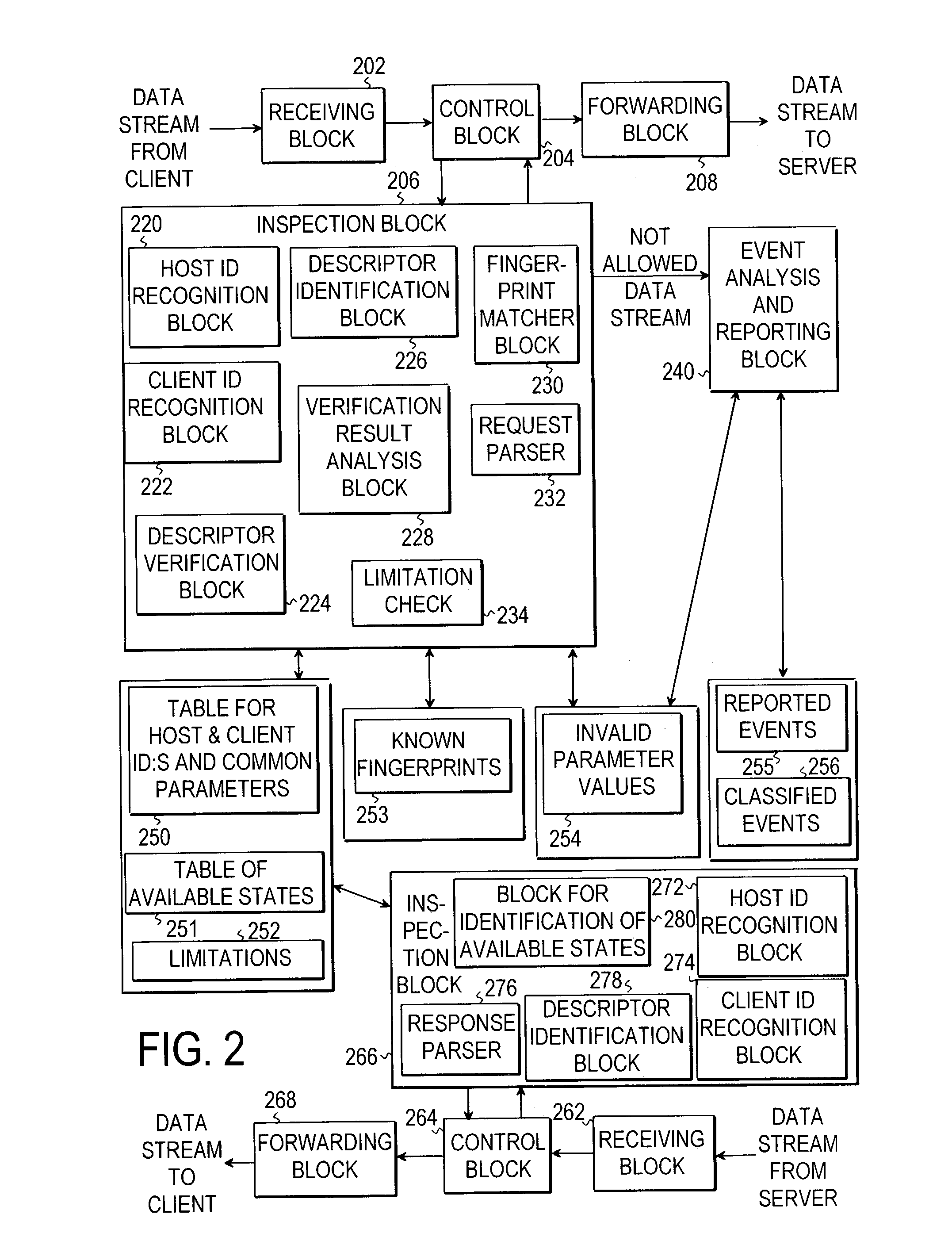
ActiveUS7302480B2Improve system securityImprove securityMemory loss protectionDigital data processing detailsTraffic capacityData stream
The invention relates to the monitoring of the flow of a data stream travelling between a client and a server system. The invention is intended particularly for such communications protocols carrying representation data above some connection-oriented protocol layer. The objective of the present invention is to bring about a flow monitoring mechanism enhancing system security. This is achieved by analyzing a data stream travelling from the server to the client in order to identify at least one response descriptor in the data stream. The identified response descriptors are stored in a set of available states for said client. Then the data stream travelling from the client to the server is analyzed in order to identify at least one request descriptor. The request descriptors identified are compared with the set of available states for said client, and in response to the comparing step, a monitoring result is generated.
Owner:FORCEPOINT LLC
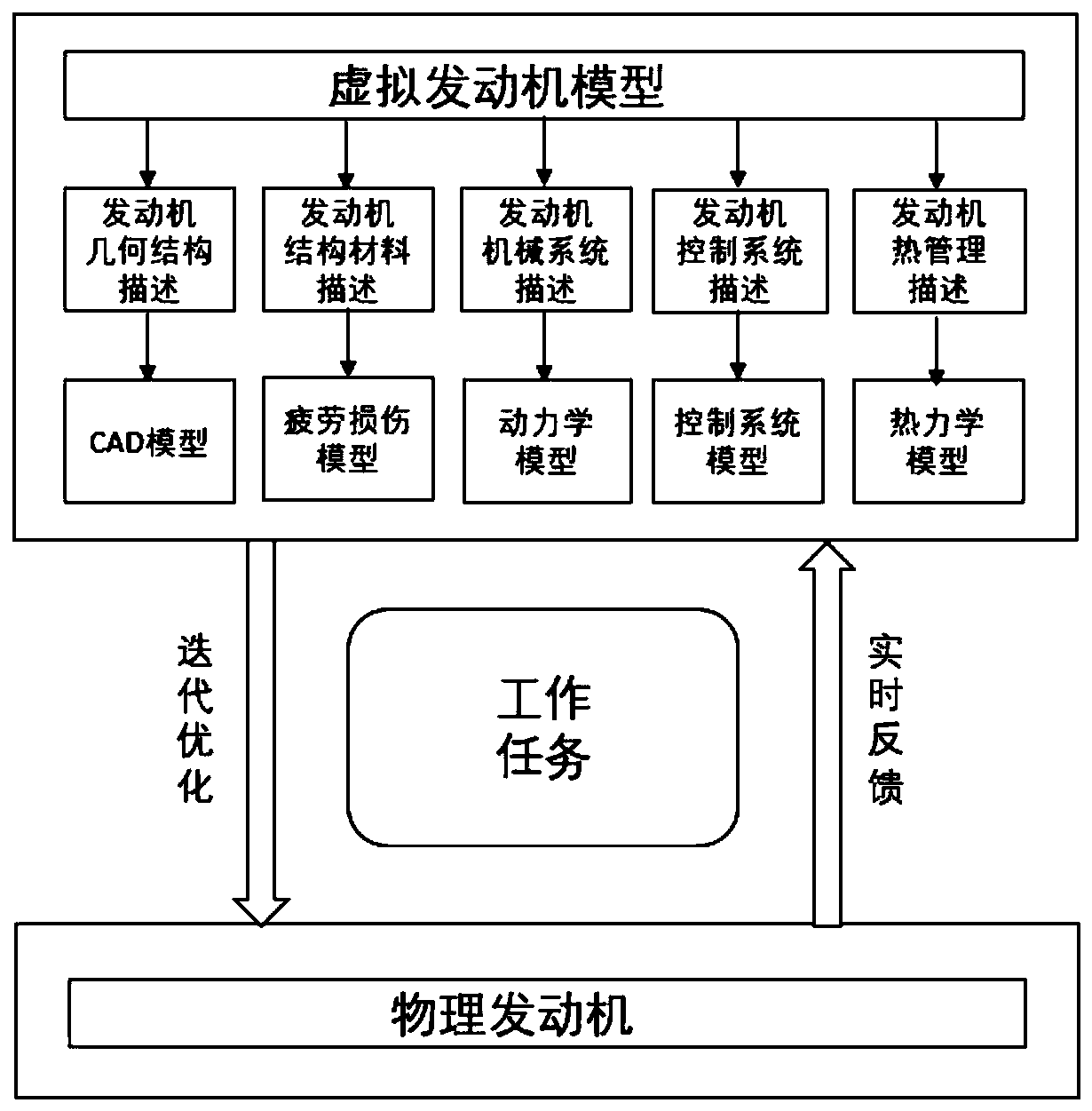
Automobile engine control method based on digital twin technology
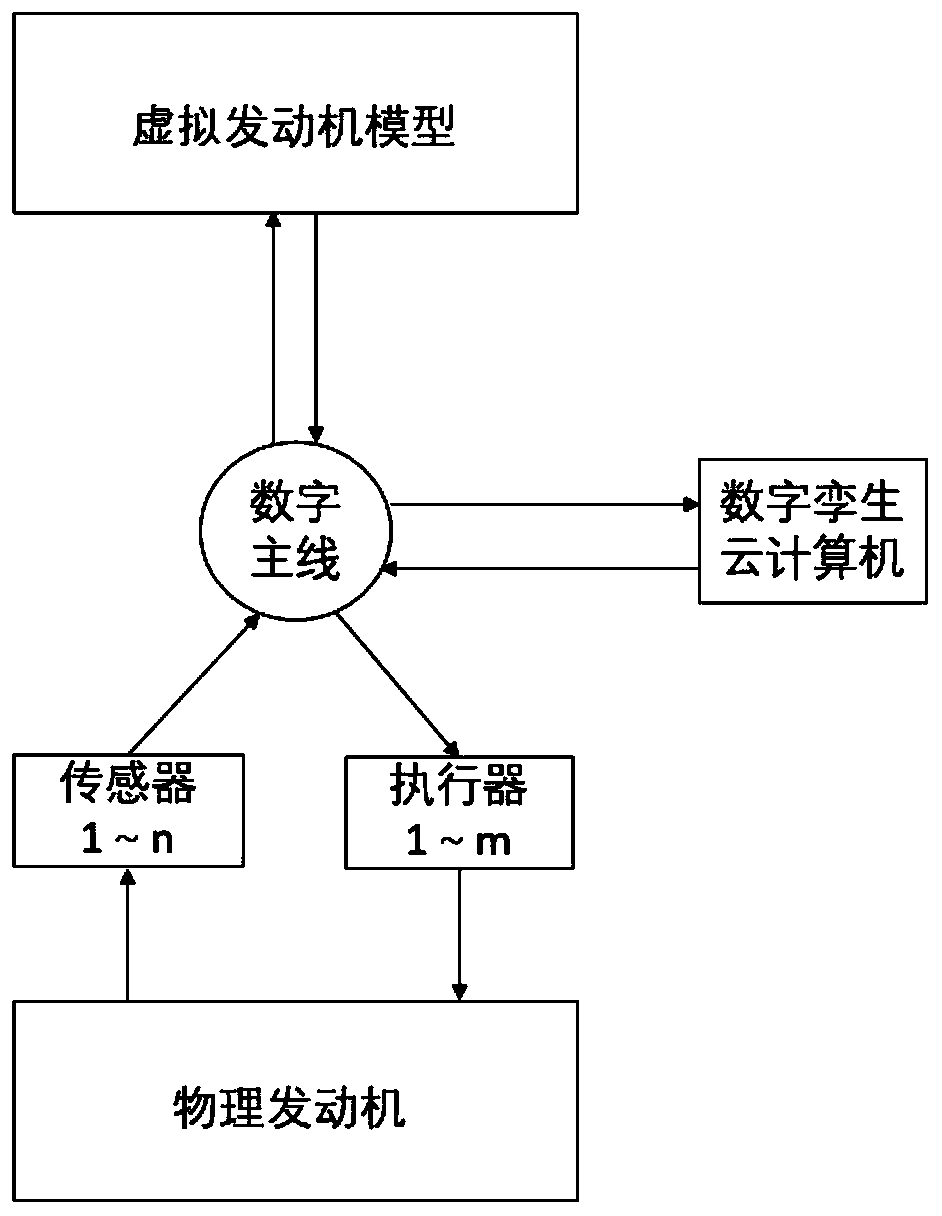
ActiveCN110454290AImprove efficiencyImprove work efficiencyElectrical controlMachines/enginesWorking environmentOptimal control
The invention relates to an automobile engine control method based on digital twin technology. The automobile engine is regarded as a physical engine in the actual working environment, based on the digital twin technology, a digital twin virtual engine model which is matched with the physical engine is built on the simulation platform, and the simulation working environment of the virtual engine model is configured; the physical data generated by the operation of the physical engine and the virtual data generated by the operation of the virtual engine model are received by digital thread and alarge plurality of heterogeneous physical data and virtual data are subjected to data analysis fusion processing; and according to the processing results, the virtual engine model is updated, and thecorresponding optimal control strategy under the latest model is obtained based on the physical engine calibration performance and the current state of the vehicle combined with online simulation technology, according to the optimal control strategy, the physical engine is controlled by the engine management system, and the virtual engine model and the optimal control strategy are updated with real-time feedback, so that the dynamic rolling data exchange is formed to realize dynamic optimal control
Owner:BEIHANG UNIV
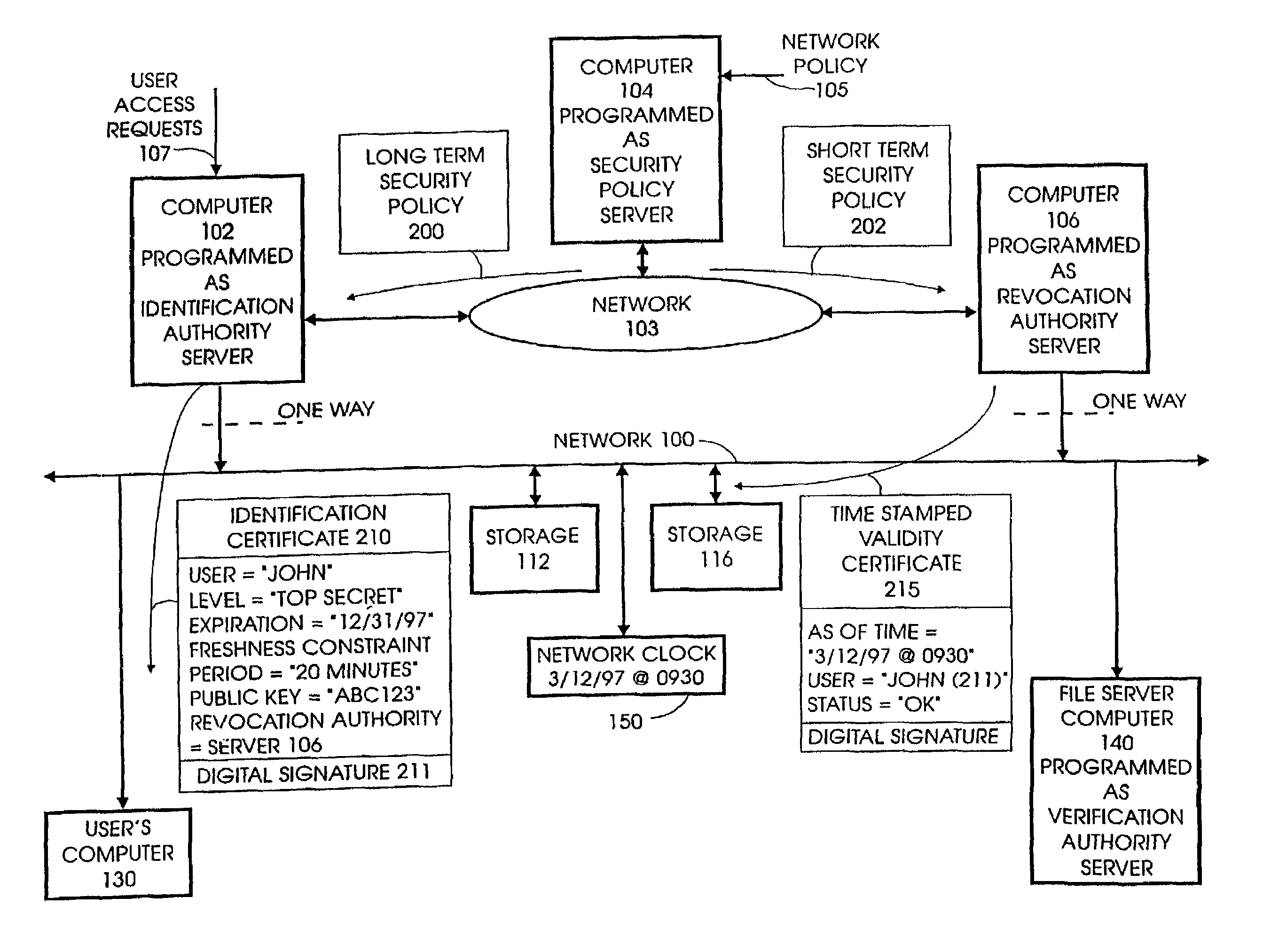
Specifying security protocols and policy constraints in distributed systems
InactiveUS7644284B1Improve system securityDigital data processing detailsUser identity/authority verificationCryptographic protocolSecure authentication
A recent secure authentication service enforcing revocation in distributed systems is provided. Authenticity entities impose freshness constraints, derived from initial policy assumptions and authentic statements made by trusted intermediaries, in authenticated statements made by intermediaries. If freshness constraints are not presented, authentication is questionable. The freshness constraints can be adjusted. The delay for revocation can be arbitrarily bounded. The freshness constraints within certificates results in a secure and highly available revocation service such that less trust is required of the service.
Owner:HANGER SOLUTIONS LLC
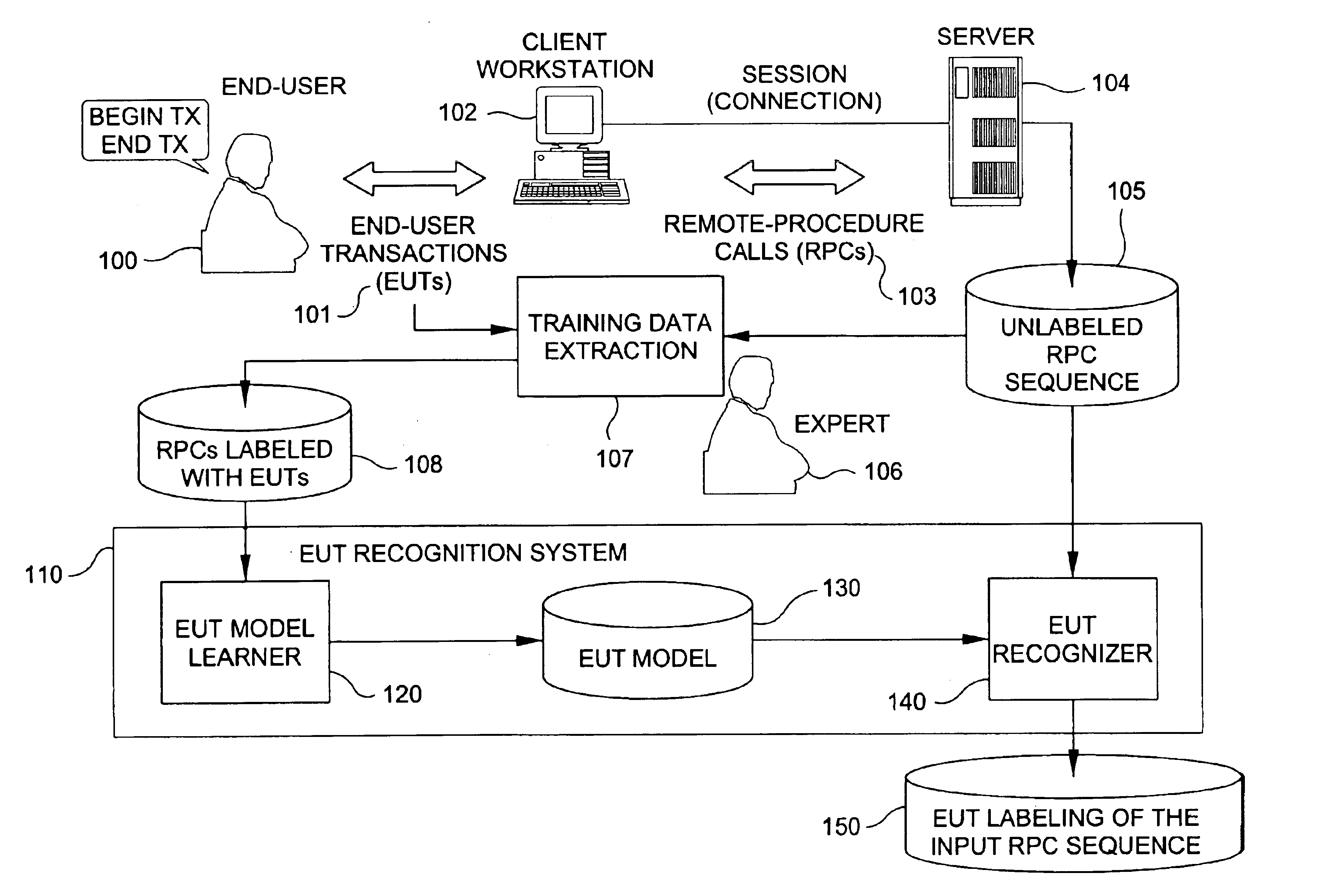
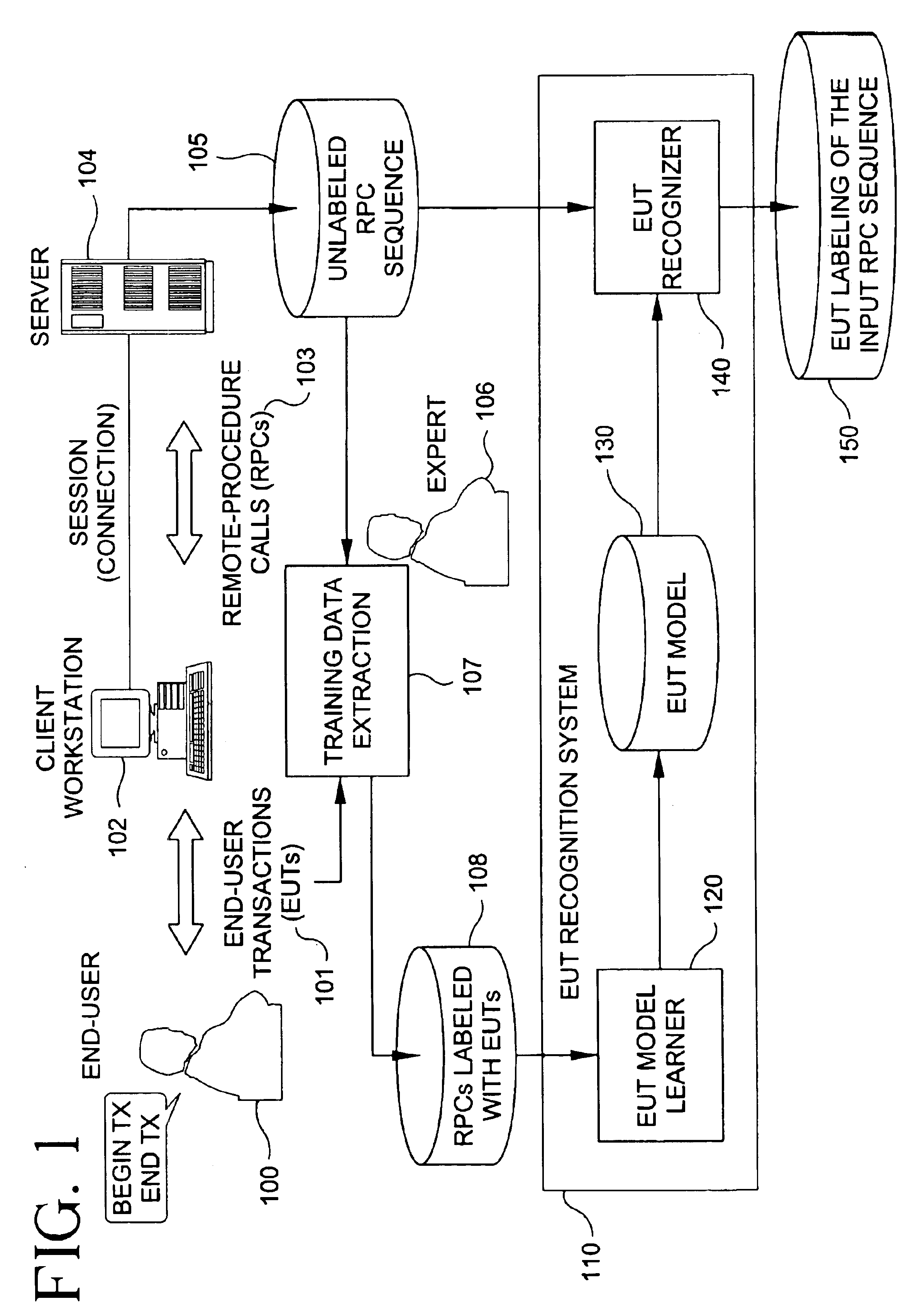
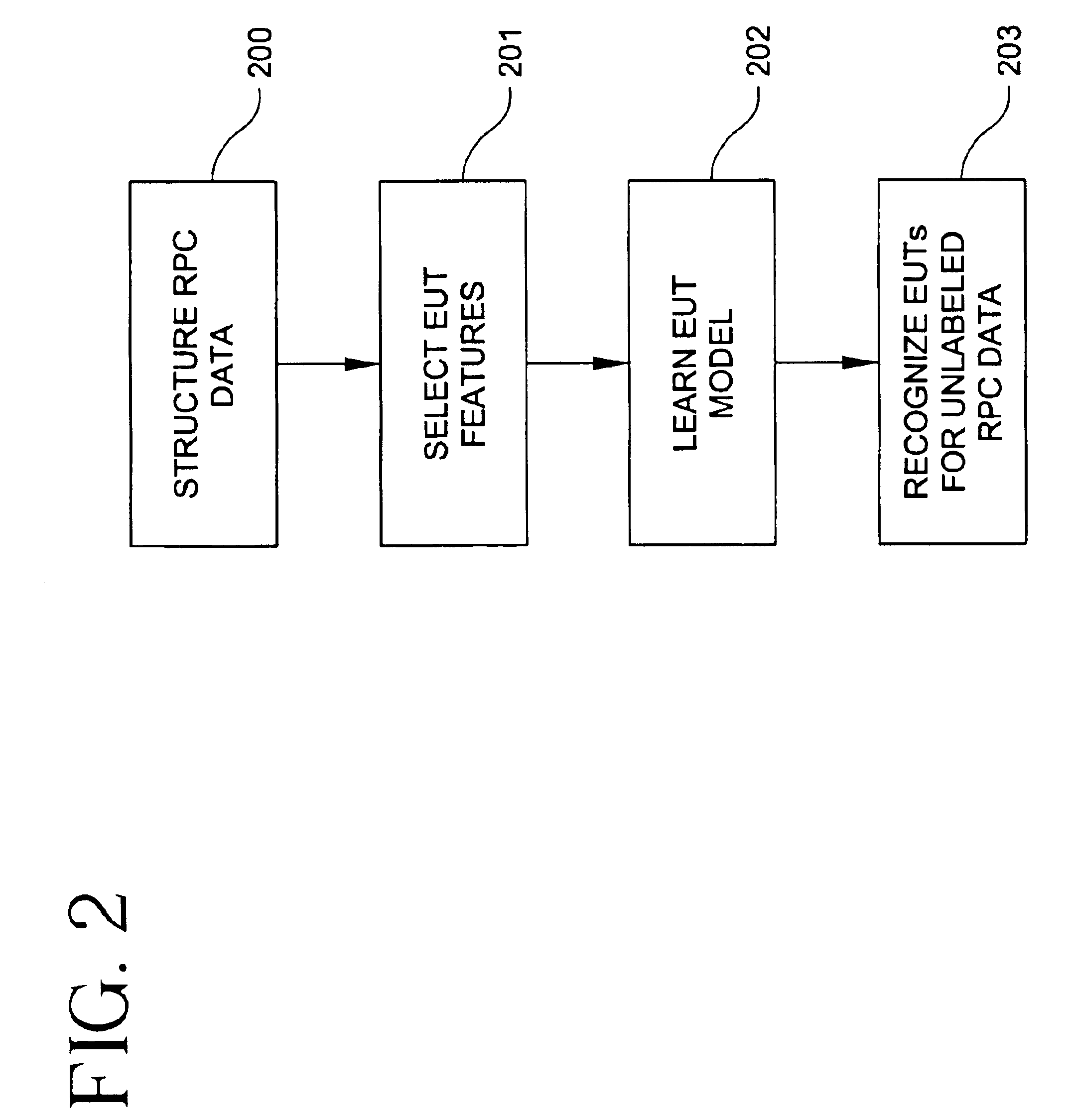
Method and system for recognizing end-user transactions
InactiveUS6925452B1Improve performanceImprove system securityDigital computer detailsMultiprogramming arrangementsFeature extractionProcedure calls
A method and system are described for end-user transaction recognition based on server data such as sequences of remote procedure calls (RPCs). The method may comprise machine-learning techniques for pattern recognition such as Bayesian classification, feature extraction mechanisms, and a dynamic-programming approach to segmentation of RPC sequences. The method preferably combines information-theoretic and machine-learning approaches. The system preferably includes a learning engine and an operation engine. A learning engine may comprise a data preparation subsystem (feature extraction) and a Bayes Net learning subsystem (model construction). The operation engine may comprise transaction segmentation and transaction classification subsystems.
Owner:IBM CORP
Nanometer medicine loading system, method for preparing same and application of nanometer medicine loading system
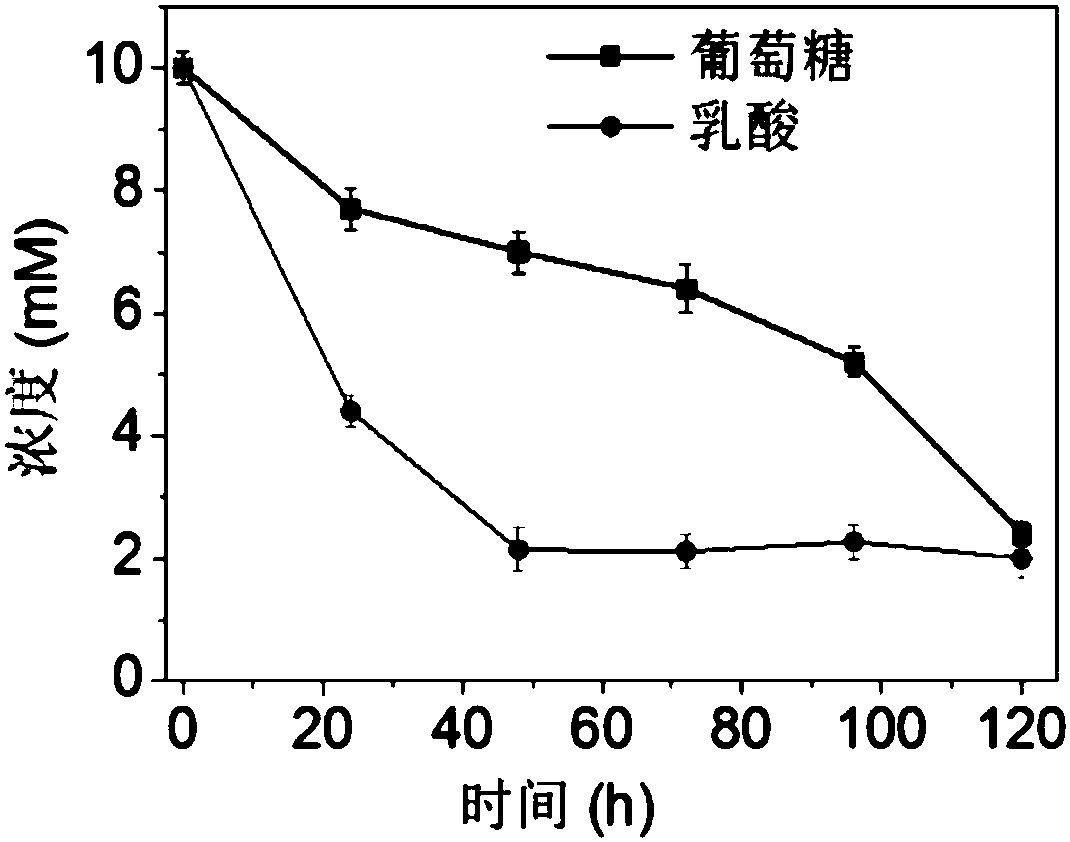
InactiveCN108524934AGood biocompatibilityImprove system securityOrganic active ingredientsEnergy modified materialsMedicineMetal-organic framework
The invention discloses a nanometer medicine loading system, a method for preparing the same and application of the nanometer medicine loading system, and belongs to the field of nanometer biomedicine. The nanometer medicine loading system, the method and the application have the advantages that a lactic acid protein inhibitor CHC (alpha-cyano-4-hydroxycinnamate) is carried into cells by the aid of porphyrinic zirconium metal organic framework materials for the first time, targeting polymers are coated, the intratumor oxygen consumption can be reduced after the CHC is released, equivalently, the intratumor oxygen concentration is increased, accordingly, the shortcomings of photodynamic cancer therapy in the prior art can be overcome by the aid of the nanometer medicine loading system, andphotodynamic antitumor effects can be greatly improved; the nanometer medicine loading system is excellent in biocompatibility and system safety.
Owner:WUHAN UNIV
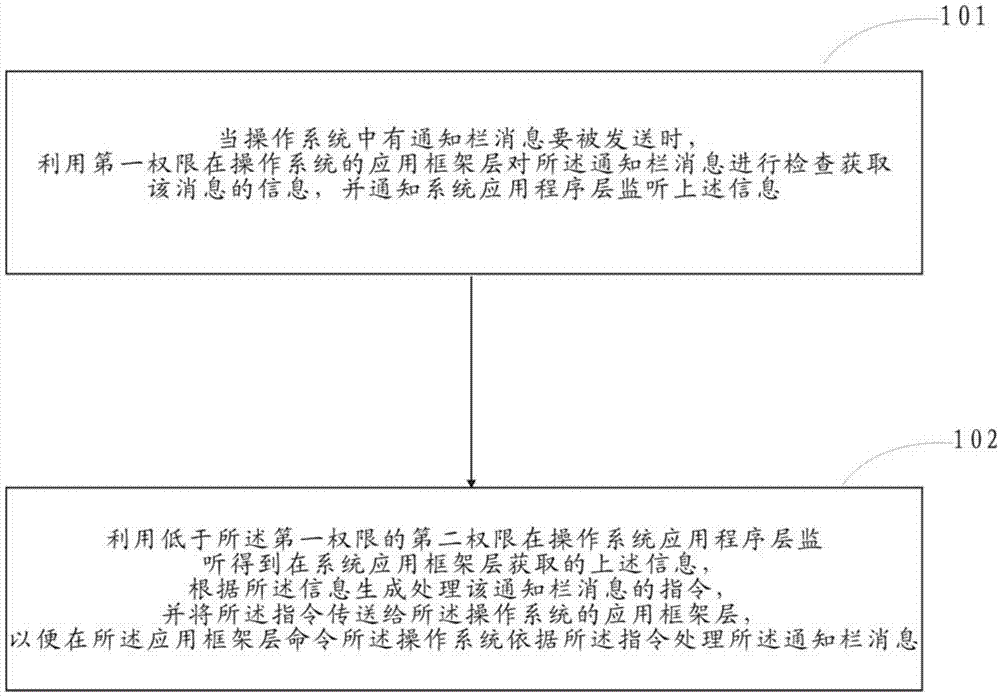
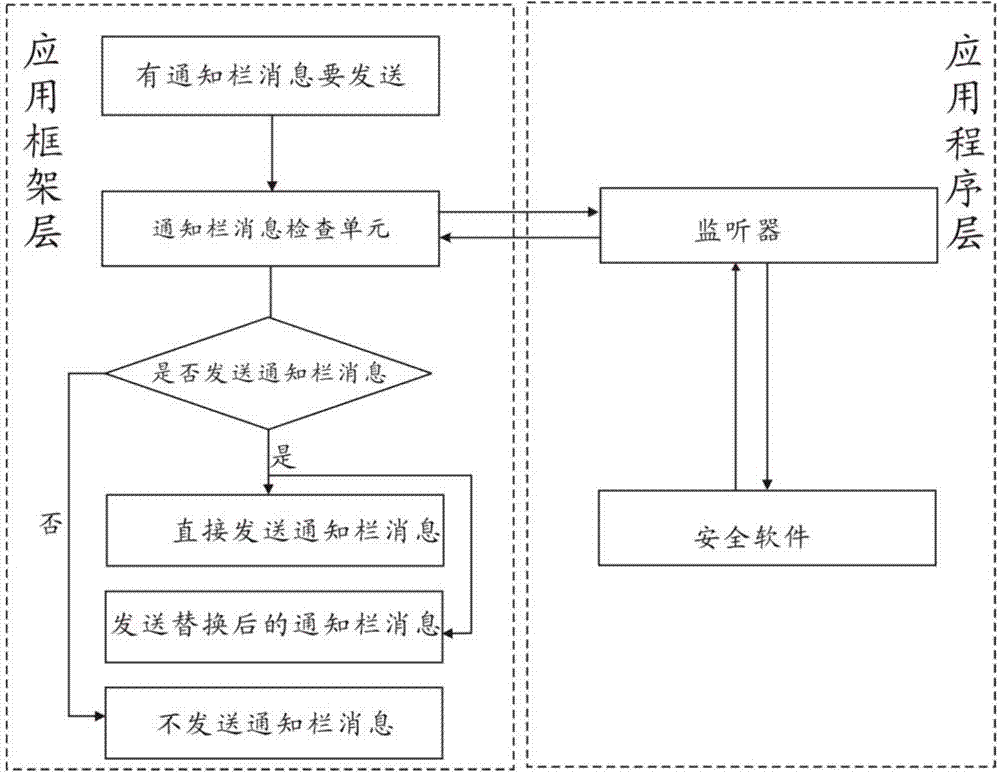
Method and device for processing notification column message
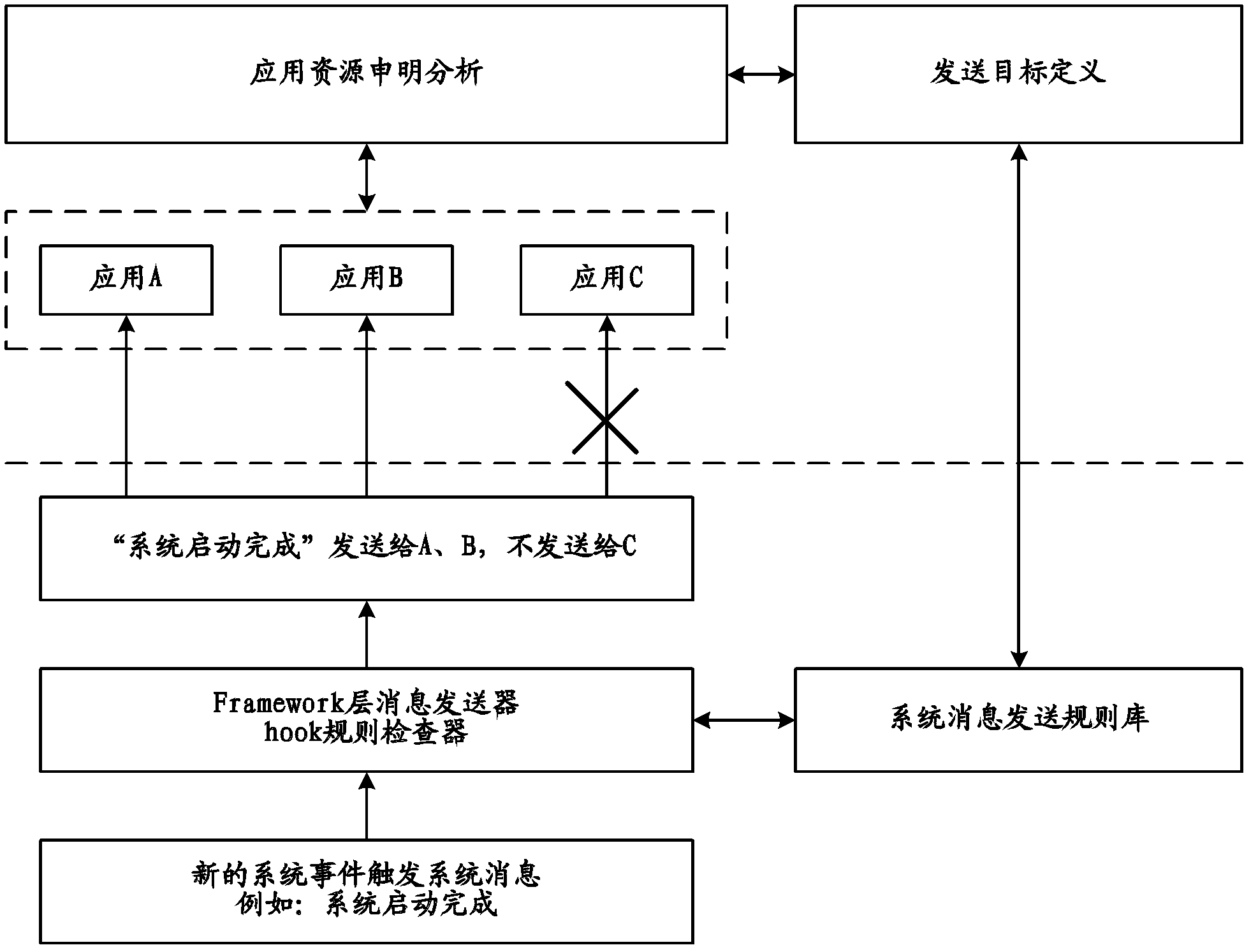
ActiveCN103577749AImprove system securityImprove securityPlatform integrity maintainanceSystem safetyThird party
The invention relates to a method for processing a notification column message. The method for processing the notification column message comprises the steps that when the notification column message about to be sent exists in an operating system, the notification column message is checked in an application framework layer of the operating system, so that information of the notification column message is obtained, and an application program layer of the operating system is noticed to monitor the information; the information obtained on the application framework layer of the operating system is monitored and obtained on the application program layer of the operating system, an instruction for processing the notification column message is generated according to the information, and the instruction is transmitted to the application framework layer of the operating system so that the operation system can be ordered to process the notification column message on the application framework layer according to the instruction. By the adoption of the method and device for processing the notification column message, a user can use third-party safety software to process the notification column message without the step that through cracking of the user terminal operating system, the highest authority of the operating system can be obtained. The method for processing the notification column message has the advantage that the safety performance of the system is improved.
Owner:BEIJING QIHOO TECH CO LTD
Cell membrane tumor vaccine and preparation method and application thereof
InactiveCN110090298AImprove immunityGood biocompatibilityFused cellsCancer antigen ingredientsAbnormal tissue growthDendritic cell
The invention discloses a cell membrane tumor vaccine and a preparation method and an application thereof. For the first time, exogenous tumor antigens and adoptive cells are not used, a cell fusion technology is used to fuse dendritic cells and tumor cells, and after culture, the whole tumor antigen and costimulatory molecules are expressed on the cell membrane of the fused cells. A nano cell membrane vaccine prepared by coating the nanoparticle with the cell membrane subjected to peeling of the fused cell can directly activate the T cell like the antigen presenting cell, can also be recognized by the dendritic cell, processed and presented to the T cell, and indirectly activates the T cell. Two T cells are combined for activation of pathways, which can cause the strong anti-tumor immuneresponse. A cell membrane tumor vaccine strategy that mimics the tumor cells and the antigen presenting cells enables the development of the vaccines against a variety of tumor types, and has good biocompatibility and system safety. Therefore, the cell membrane vaccine is very suitable for the field of tumor vaccines.
Owner:WUHAN UNIV
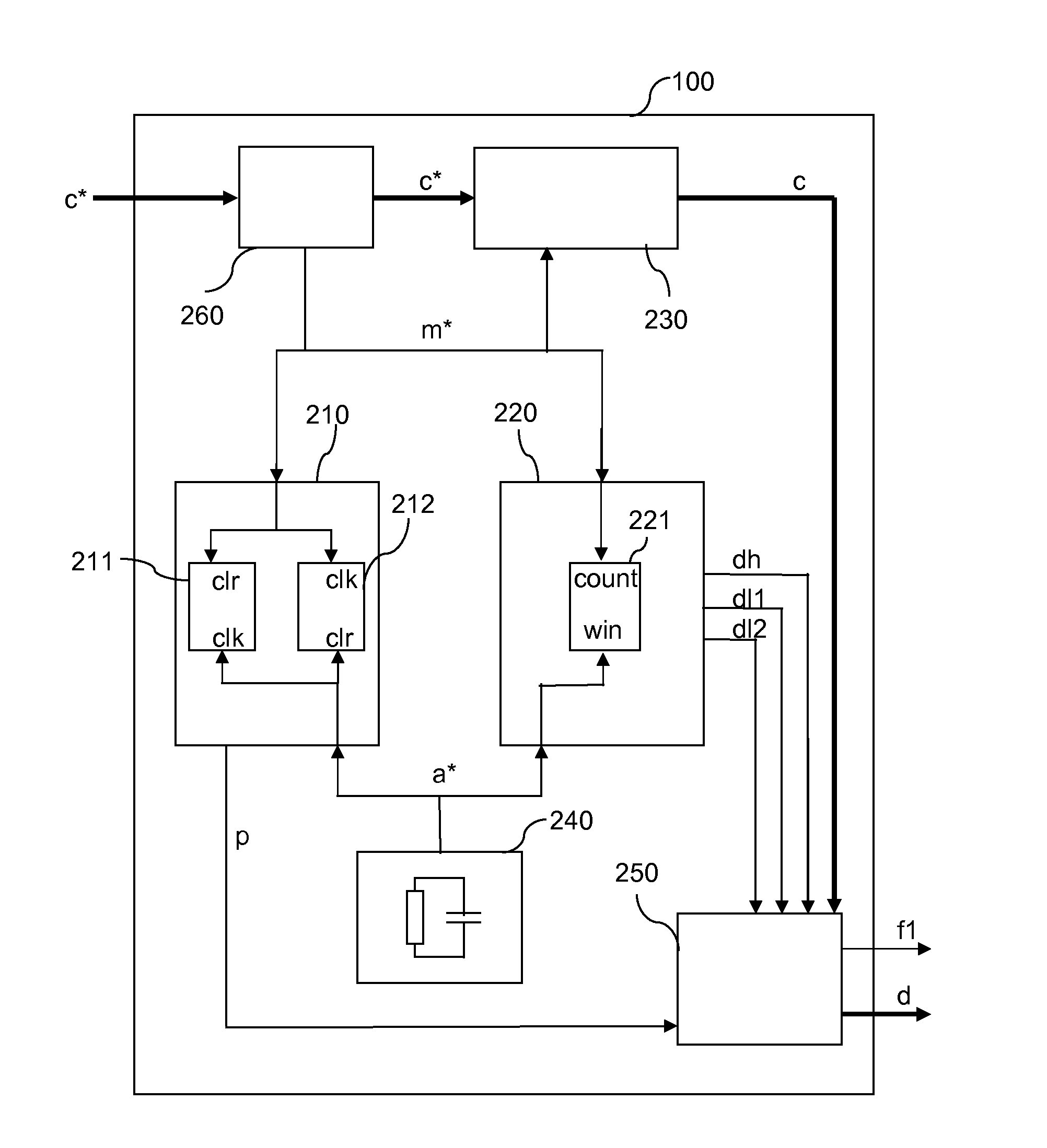
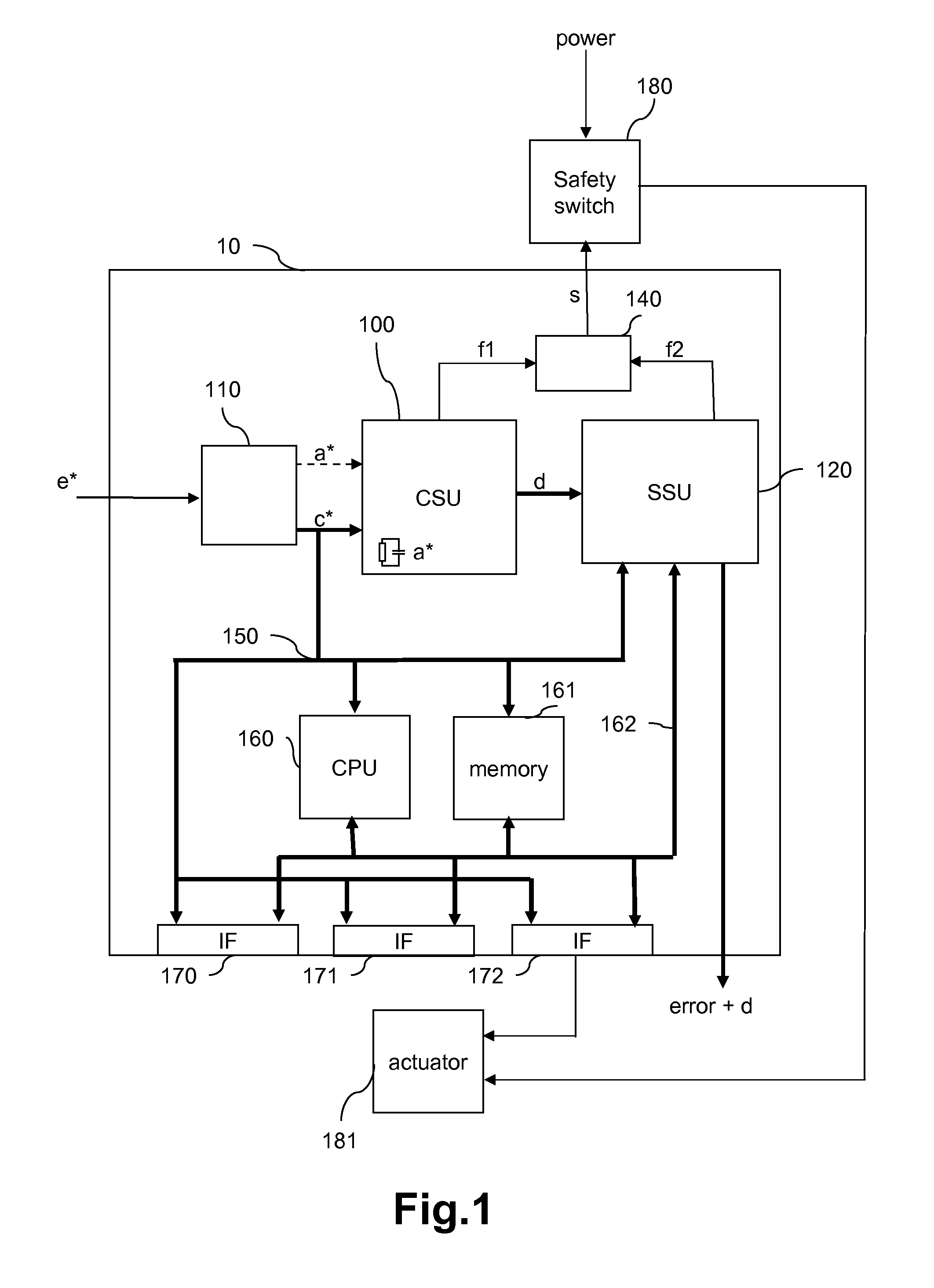
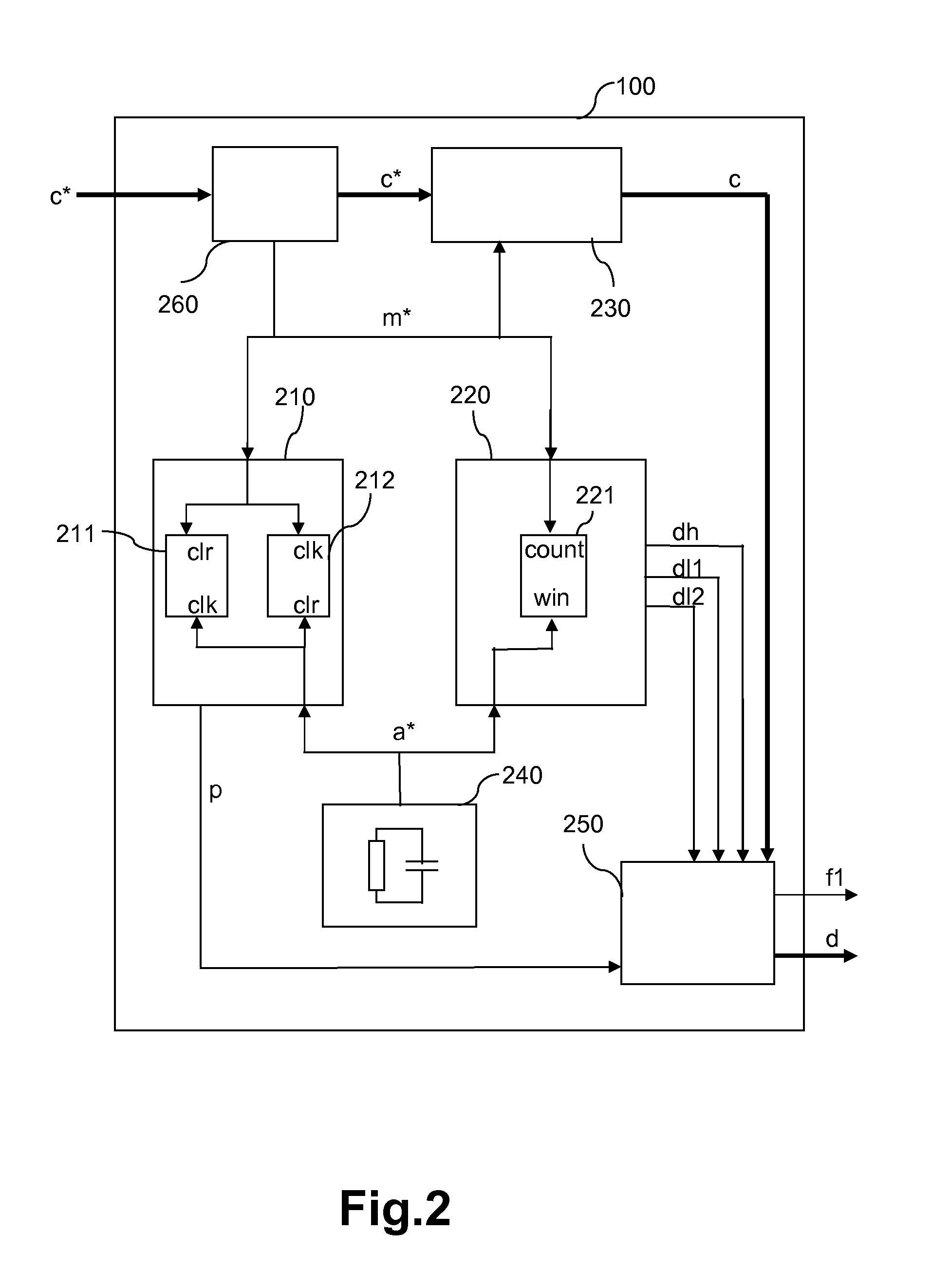
Clock supervision unit
ActiveUS20100308868A1Precise clock frequencyImprove system securityPulse automatic controlError detection/correctionElectronic systemsEngineering
The present invention relates to a clock supervision unit (100) and an electronic system clocked by at least one clock (c*) and using the clock supervision unit (100). The clock supervision unit (100) analyzes the at least one clock (c*) based on a monitor clock (m*) provided together with the at least one clock (c*) or separately to the clock supervision unit (100). The clock supervision unit (100) at least comprises an activity unit (210), a deviation unit (220) and an auxiliary clock generator (240). The auxiliary clock generator (240) outputs an auxiliary clock (a*). The activity unit (210) detects the presence of the monitor clock (m*) based on the auxiliary clock (a*) and the presence of the auxiliary clock (a*) based on the monitor clock (m*). The deviation unit (220) detects clock faults in the monitor clock (m*) based on the auxiliary clock (a*). With the clock supervision unit (100) according to the present invention, the at least one clock (c*) can be supervised in more detail and it is possible to react on different clock faults in the at least one clock c* with different error handling procedures, e.g. by initiating a shutdown of the devices controlled by the electronic system.
Owner:NXP BV
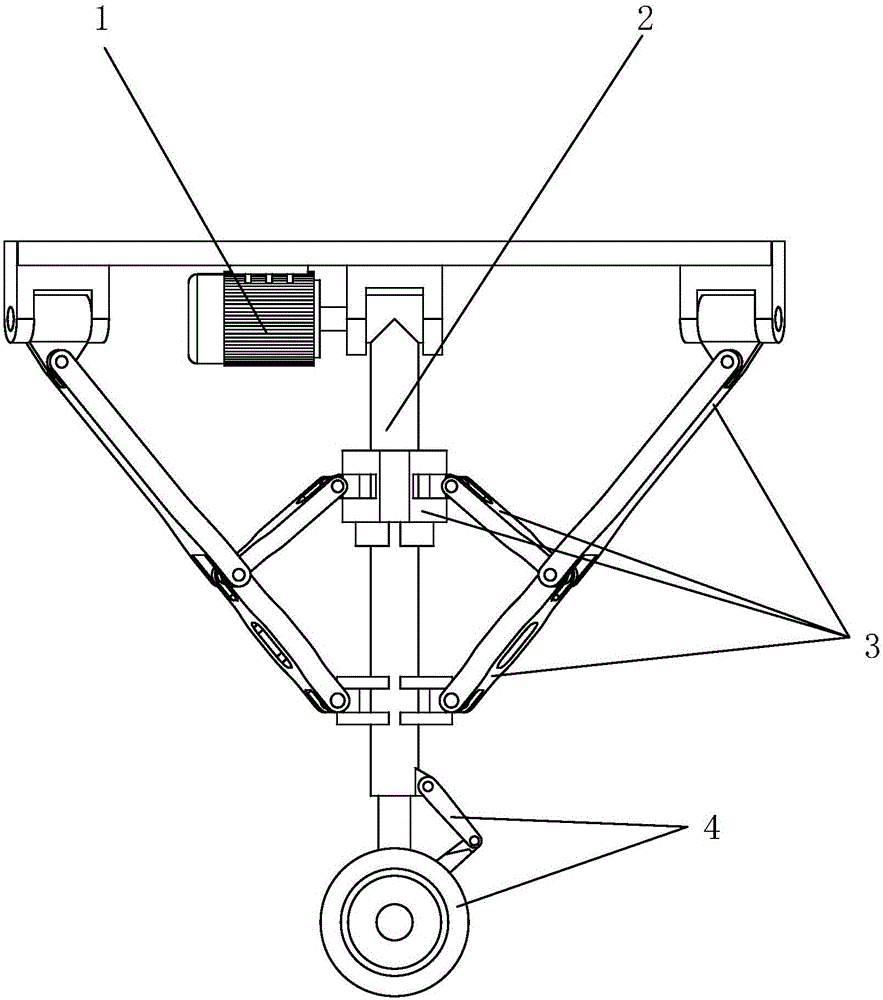
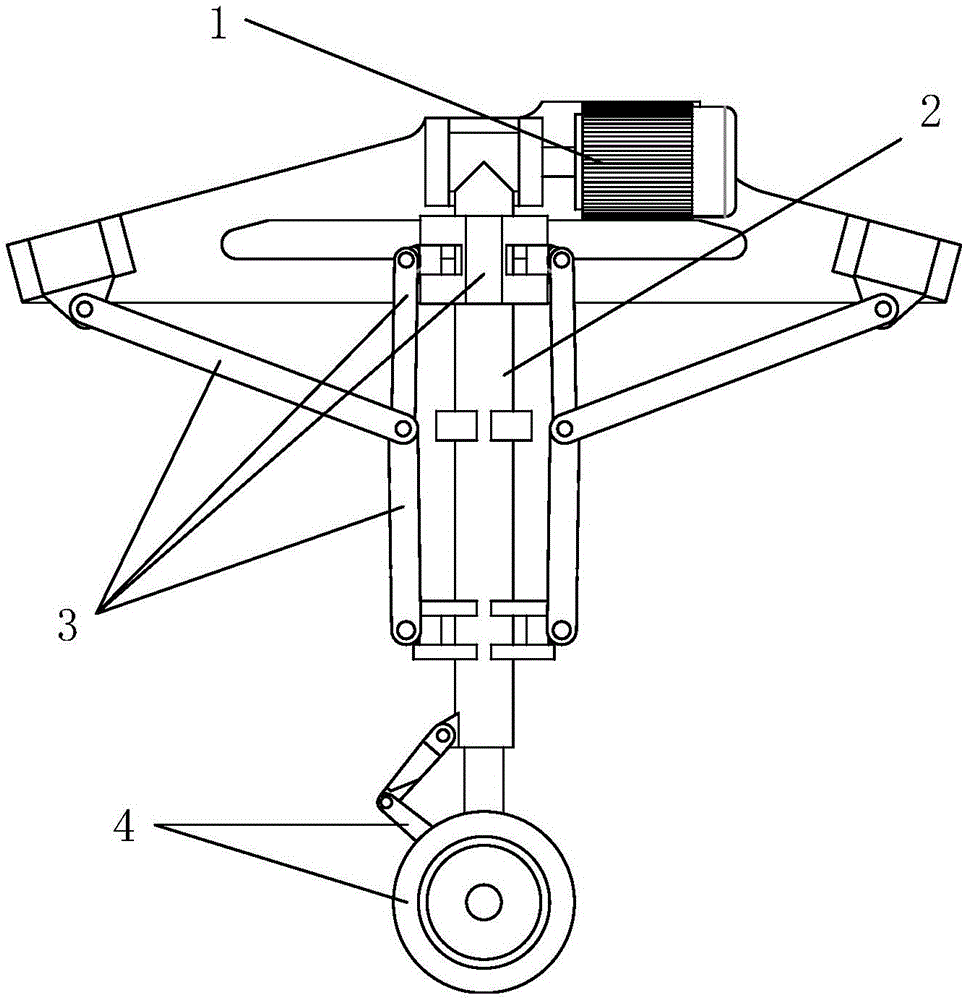
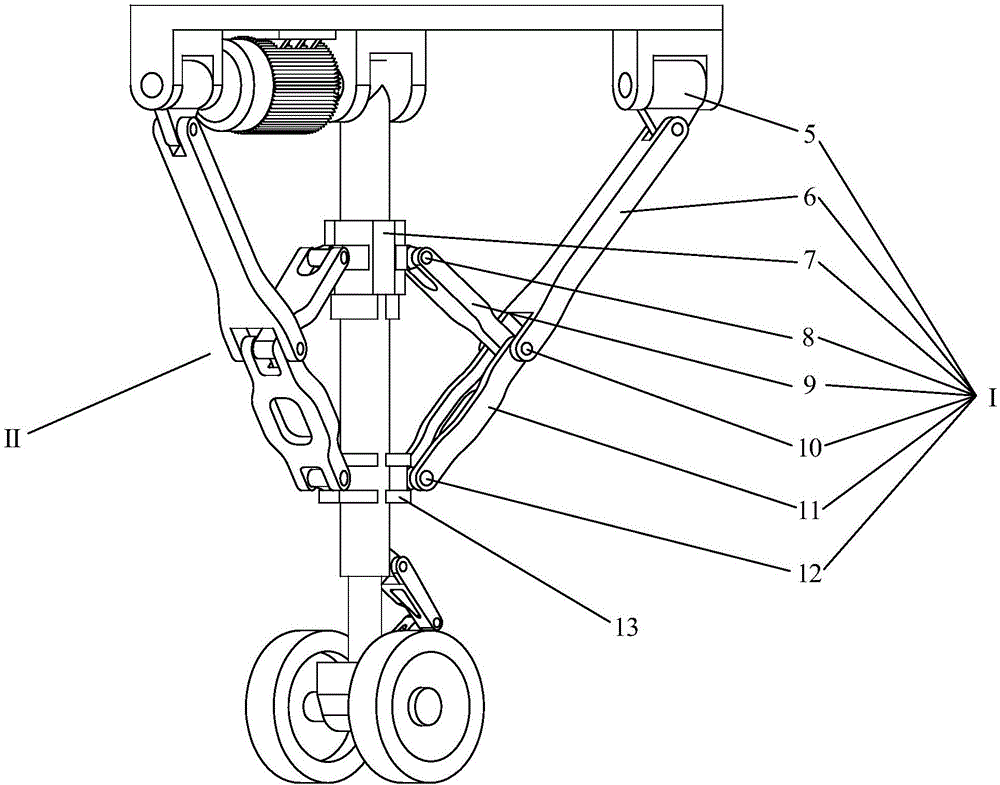
Novel high-strength high-compactness lightweight aircraft landing gear
InactiveCN106516087AWith double locking functionReliable double locking structureWheel arrangementsUndercarriagesLocking mechanismAircraft landing
The invention discloses a novel high-strength high-compactness lightweight aircraft landing gear. The novel high-strength high-compactness lightweight aircraft landing gear comprises a driving system, a main bearing rod, a locking mechanism and a damping system, wherein the driving system is arranged on the upper part of the main bearing rod; the main bearing rod is arranged between an aircraft fuselage and the damping system; the locking mechanism is arranged between the aircraft fuselage and the main bearing rod; the locking system comprises two identical kinematic chains which are not arranged in the same plane and respectively include a first kinematic chain and a second kinematic chain; the damping system is arranged on the lower part of the main bearing rod and comprises a damper and a pneumatic tire; and the lower end of the damper is connected with the pneumatic tire. According to the novel high-strength high-compactness lightweight aircraft landing gear disclosed by the invention, a conventional plane four-link landing gear is changed into a space four-link mechanism, and the reliable double-locking structures are a great contribution to the prior aircraft landing gear technology; and two sets of double-locking mechanisms are separated from each other and distributed symmetrically, and the safety of the aircraft landing gear is greatly improved by such a redundant design.
Owner:TSINGHUA UNIV
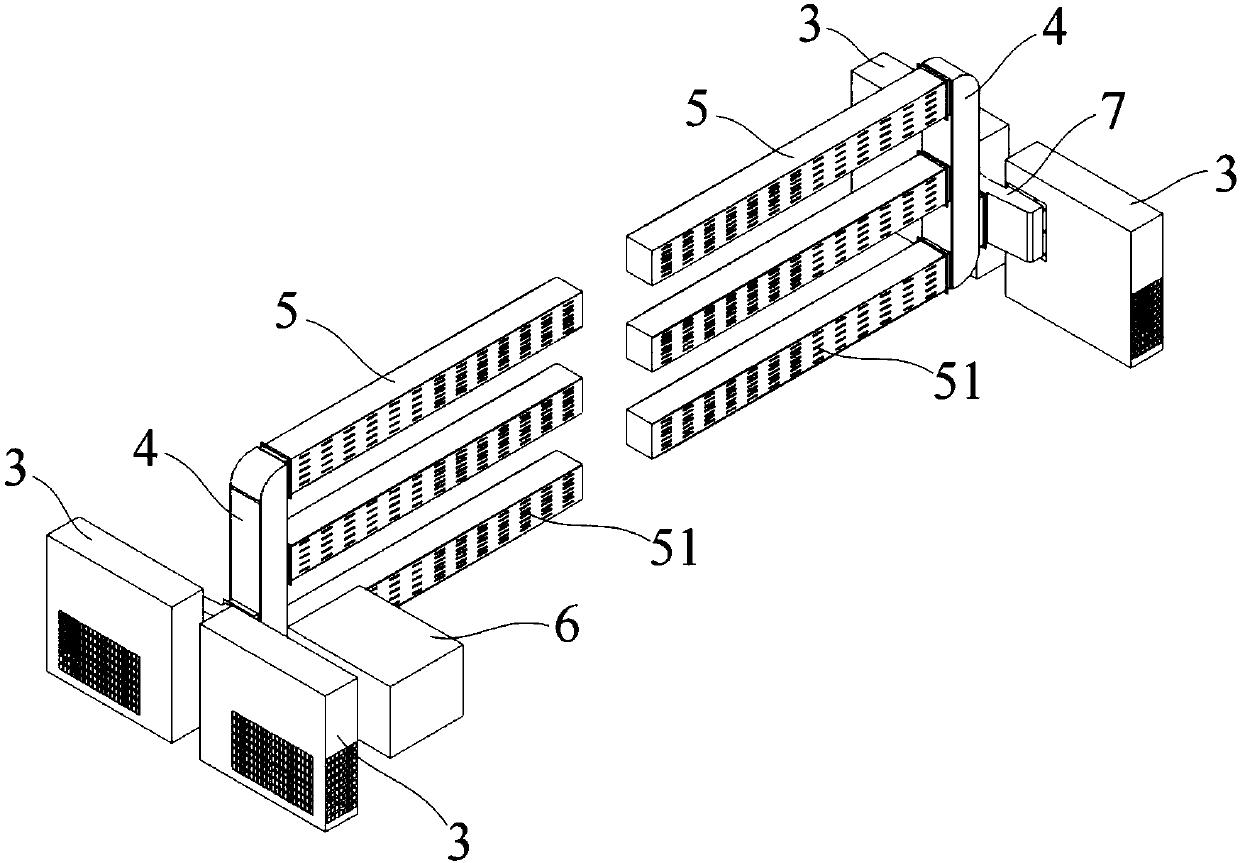
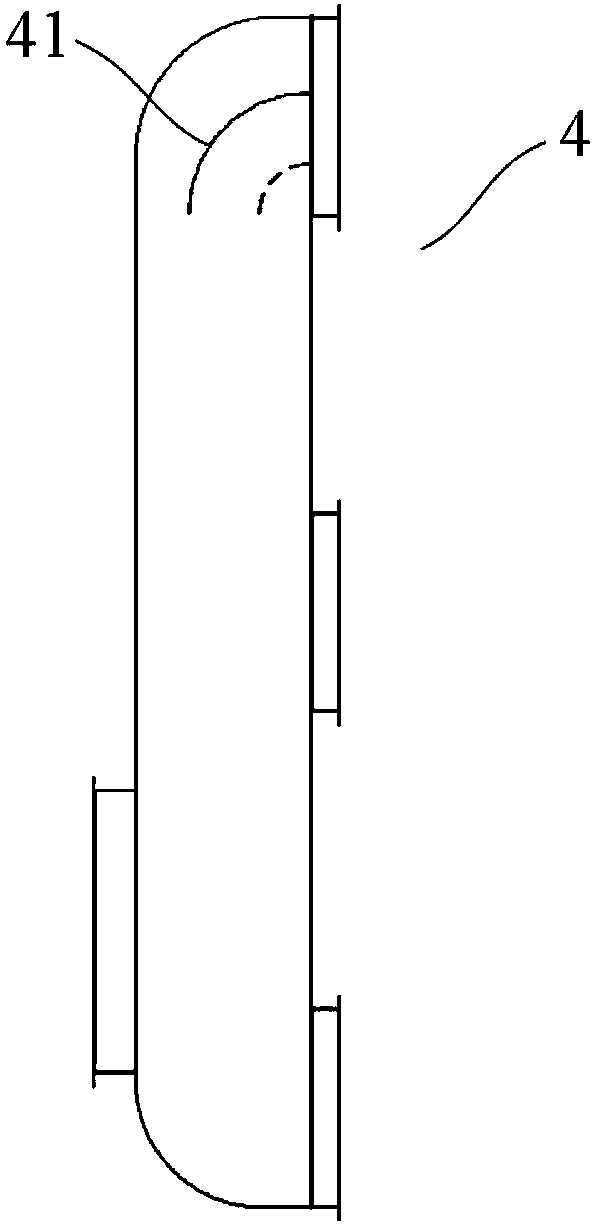
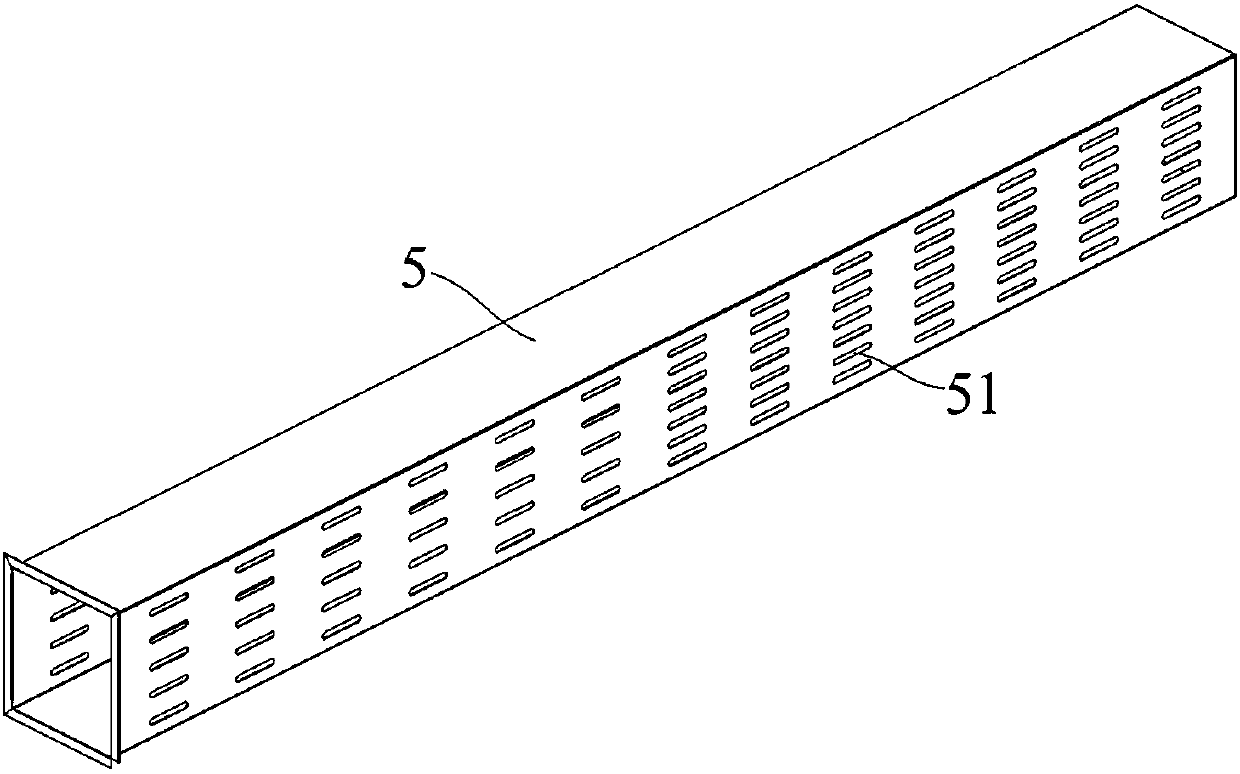
Battery module cooling system and battery pack
InactiveCN107565190AExtend your lifeImprove system securitySecondary cellsCell component detailsCold airCooling effect
The invention provides a battery module cooling system and a battery pack. The battery module cooling system is used for cooling battery modules in a battery box and comprises cooling devices, main air ducts and a plurality of branch air ducts; cold air outlets of the cooling devices communicate with the plurality of branch air ducts through corresponding main air ducts; the branch air ducts extend to the side edges of the battery modules; and a plurality of air outlet holes are formed in the surface, facing the battery modules, each branch air duct. According to the battery module cooling system and the battery pack, cold air can be transported to the specified part to solve the problem of uniform transportation of the cold air through arranging the main air ducts and the branch air ducts, so that the plurality of battery modules in the battery box can reach the same cooling effect, the service life of the battery modules is prolonged and the security of the system is improved.
Owner:SHANGHAI ELECTRICGROUP CORP
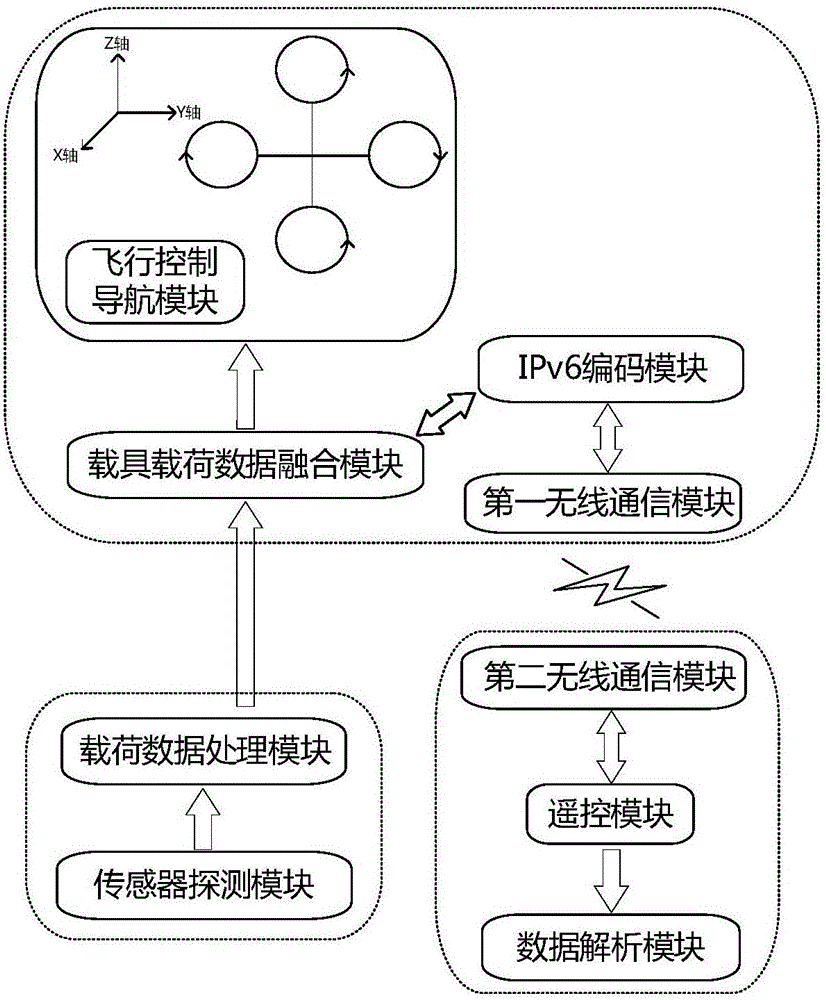
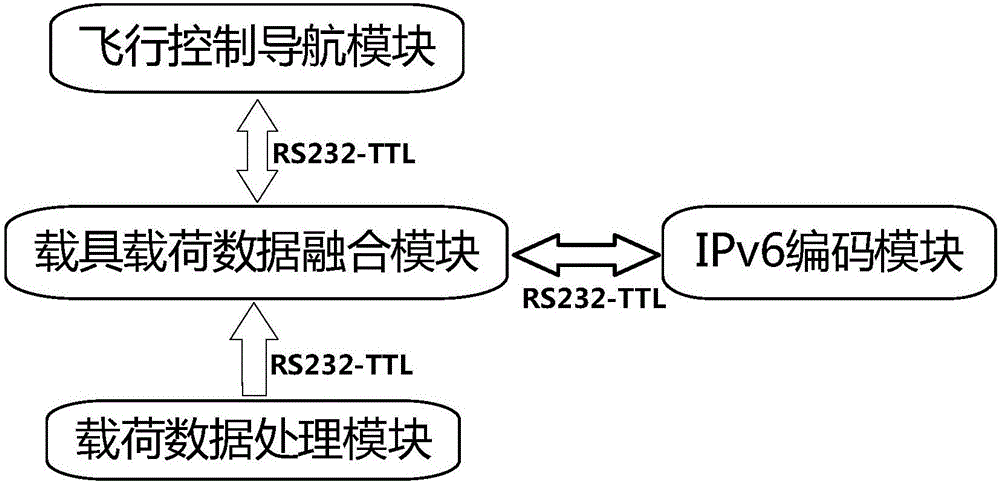
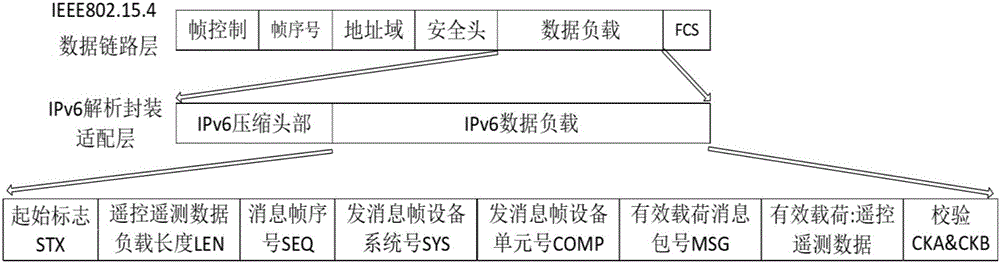
Sensing data access and transmission system and method based on IPv6 standardization of unmanned aerial vehicle
InactiveCN106789463AImprove the timeliness of data transmissionImprove system scalabilityTransmission systemsPosition/course control in three dimensionsSensing dataNetwork packet
The invention discloses a sensing data access and transmission system and a sensing data access and transmission method based on IPv6 standardization of an unmanned aerial vehicle. The system comprises a sensor load, an IPv6 standardized unmanned aerial vehicle carrier platform carrying the sensor load, and a ground remote control telemetering unit, wherein the ground remote control telemetering unit is connected with the IPv6 standardized unmanned aerial vehicle carrier platform in a wireless communication mode; the sensor load is used for collecting information, performing waveform conditioning and mode conversion on the collected information, and generating telemetering data; the IPv6 standardized unmanned aerial vehicle carrier platform is used for packaging and encoding the telemetering data and remote control data, and generating an IPv6 standardized network data packet according an appointed protocol; the ground remote control telemetering unit is used for controlling the posture and the air route of the IPv6 standardized unmanned aerial vehicle carrier platform, and also used for acquiring the telemeteirng data and the posture data of the unmanned aerial vehicle by analyzing the network data packet. According to the method based on the system, sensing data access and transmission of the IPv6 standardized unmanned aerial vehicle are achieved, data transmission timeliness of the unmanned aerial vehicle and the sensor carried by the same is improved, and the characteristic of global unique addressing is provided.
Owner:HUAZHONG UNIV OF SCI & TECH
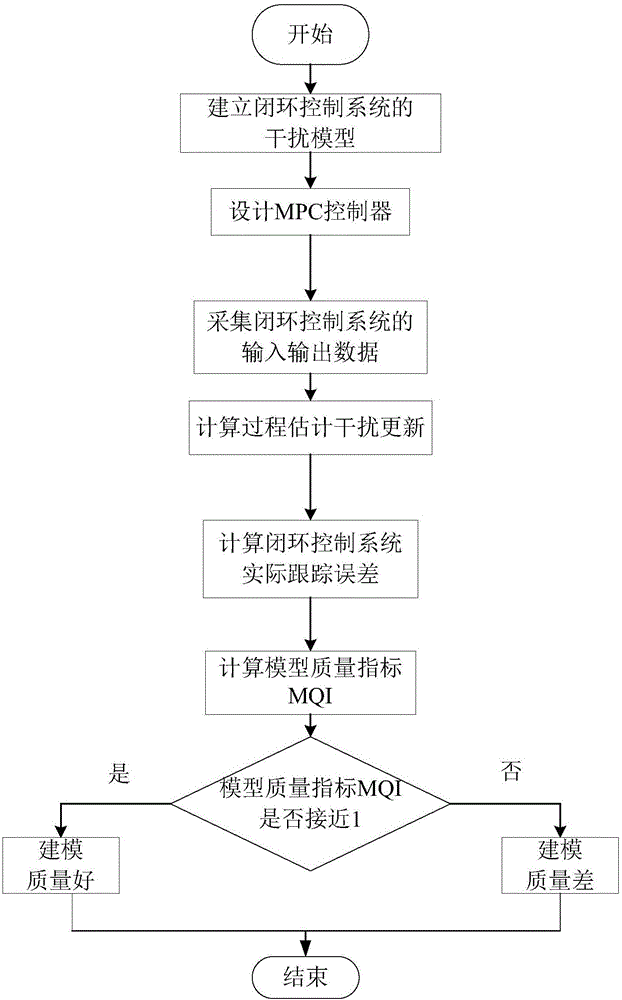
Modeling quality monitoring method for model predictive controller (MPC) with drift interference
InactiveCN105700358AHigh feasibilityConsume less resourcesAdaptive controlDynamic modelsControl system
The invention discloses a modeling quality monitoring method for a model predictive controller (MPC) with drift interference. The method comprises the following steps: an interference model for a closed loop control system is built; according to the actual condition of the closed loop control system and a given control target, a dynamic model predictive controller (MPC) for a process is designed; the interference model and the MPC are adopted for controlling the closed loop control system, and process data obtained by operation of the closed loop control system are acquired; according to the structure of the closed loop control system, orthogonal projection is carried out on process output and process input data, and process estimation interference update is acquired; according to an established reference signal of the closed loop control system and the process actual output, the actual tracking error of the closed loop control system is acquired; according to the process estimation interference update and the actual tracking error, a model quality index for the closed loop control system is acquired; and according to the structure of the closed loop control system, the model quality index is used for monitoring the modeling quality. The method of the invention has the advantages of high feasibility, few consumed resources for processing, and high evaluation result accuracy.
Owner:HUAZHONG UNIV OF SCI & TECH
Thick plastered exterior wall outer heat-insulation system with double-layer gridding cloth compounded with foam cement boards
InactiveCN103276822AImprove wind pressureImprove system securityHeat proofingLoad resistanceCement board
The invention discloses a thick plastered exterior wall outer heat-insulation system with double-layer gridding cloth compounded with foam cement boards. The thick plastered exterior wall outer heat-insulation system comprises an interface layer, a leveling layer, an adhesion mortar layer, a heat-insulation layer with the foam cement boards, an anti-crack protective layer with the inlaid double-layer gridding cloth and a finishing layer. The interface layer, the leveling layer, the adhesion mortar layer, the heat-insulation layer with the foam cement boards, the anti-crack protective layer with the inlaid double-layer gridding cloth and the finishing layer are sequentially fixedly connected with one another from the inside to the outside on the basis of a base-layer wall, joint filling and leveling heat-insulation materials are embedded in gaps of the foam cement boards in the heat-insulation layer with the foam cement boards, and the anti-crack protective layer with the inlaid double-layer gridding cloth comprises first gridding cloth, anchoring parts, second gridding cloth and three layers of anti-crack mortar. The thick plastered exterior wall outer heat-insulation system has the advantages that common quality problems of plate marks, anchor bolt marks, cracks and the like of a thin plastered system can be solved, the anchoring parts are assuredly positioned on the outer side of the gridding cloth, performance indexes of the wind load resistance, water absorption, impact resistance and the like of the outer heat-insulation system are increased, and the safety of the system is improved.
Owner:JIANGSU NIGAO SCI & TECH +1
Lock bolt release system and method
ActiveUS20070222229A1Good flexibilitySecurity lock be reducedNon-mechanical controlsWing fastenersMechanical engineering
A lock bolt release system operable with a door bolt supported by a door providing access to a secure area. A pawl is pivotally mounted on a distal end of a lock bolt, and the pawl is pivoted by operation of the door bolt prior to the lock bolt being movable by the door bolt. A wedge block is movably mounted on the lock bolt and is effective to block motion of the pawl and the door bolt. A stop member is located adjacent the wedge block and blocks motion of the wedge block, thereby preventing the door bolt from being disengaged from the structure. The stop member is movable, which permits the wedge block to be moved by the pawl and the door bolt to contact and move the lock bolt, thus, permitting the door bolt to be disengaged from the structure.
Owner:LOCKMASTERS
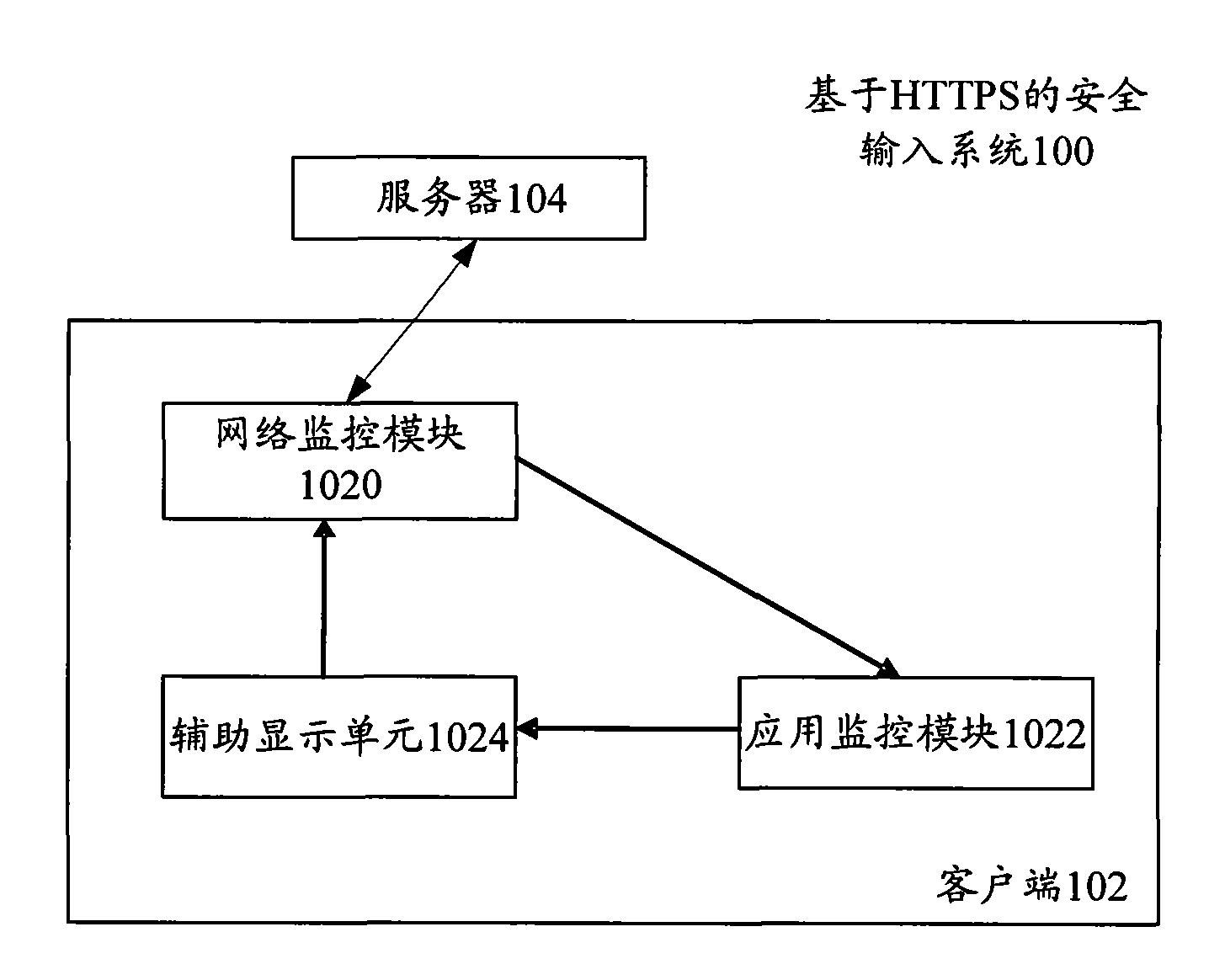
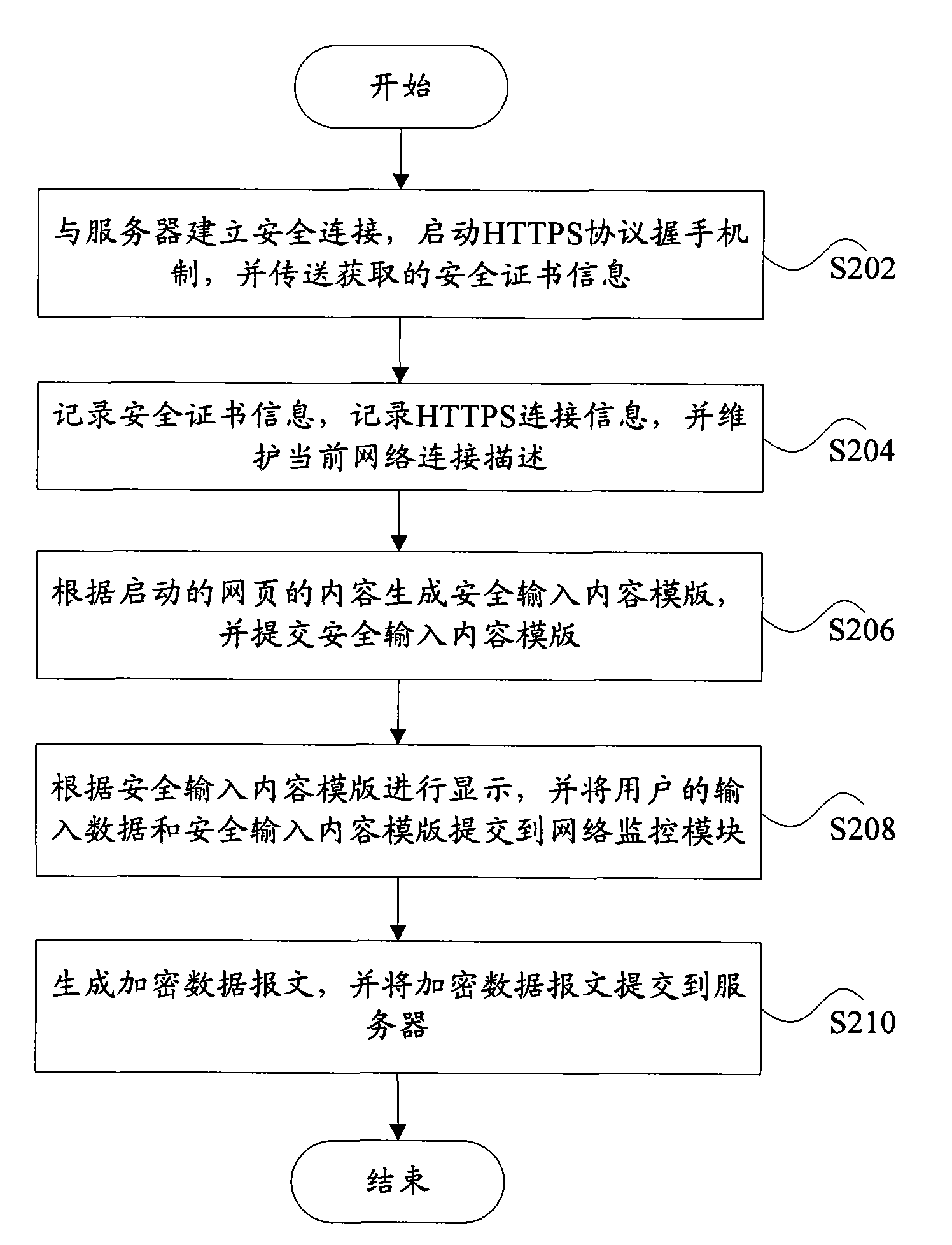
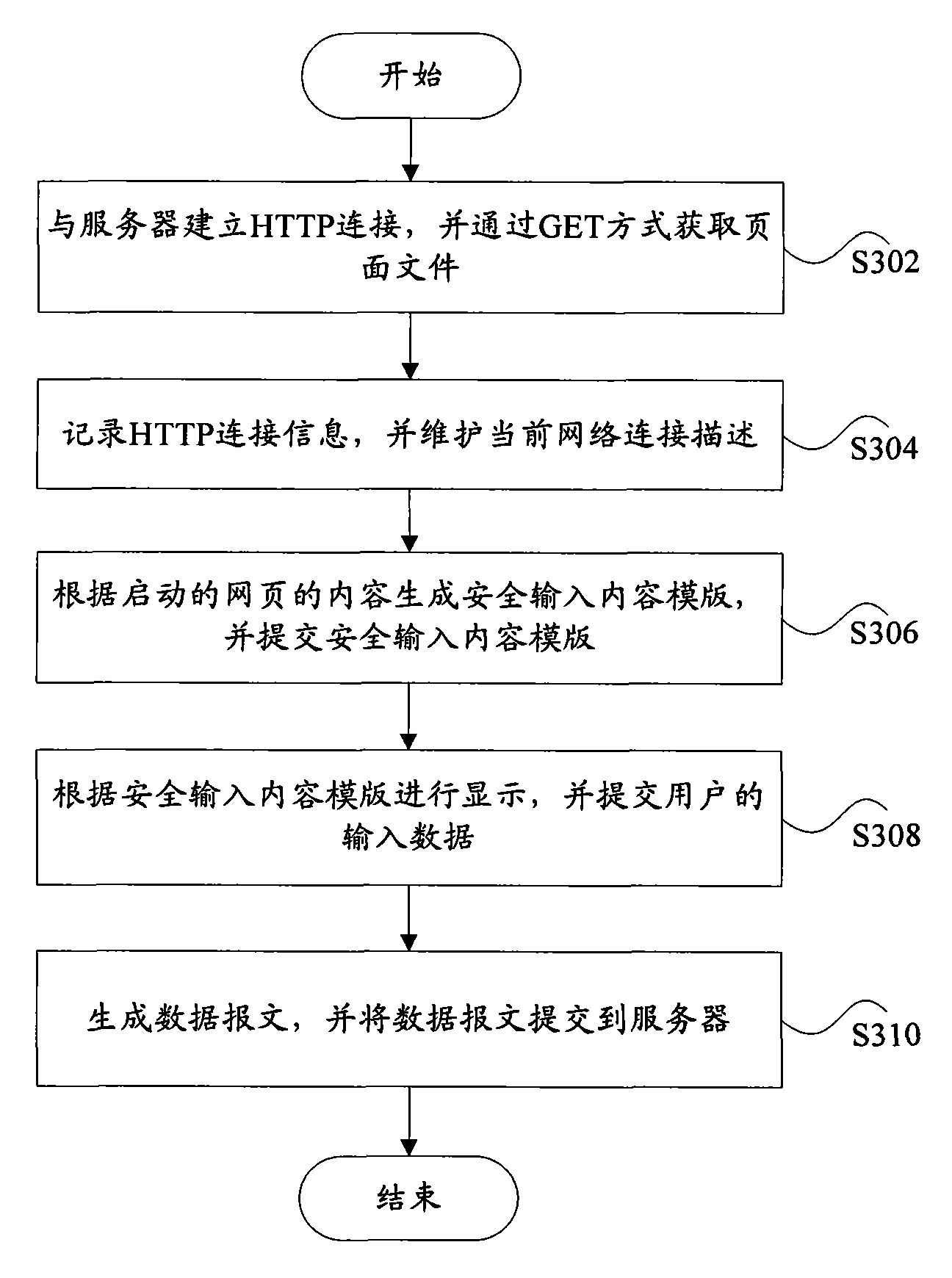
Safety input system, safety input method and auxiliary display device based on auxiliary display unit
ActiveCN101599954AImprove system securityImprove securityData switching networksReal-time computingData messages
The invention discloses a safety input system and a safety input method based on an auxiliary display unit. The safety input system comprises a network monitoring module, an application monitoring module and an auxiliary display unit, wherein the network monitoring module is used for recording network connection information, maintaining current network connection description and submitting input data from the auxiliary display unit to a server after the input data is formed into a data message; the application monitoring module is used for generating a safety input content stencil according to the content of the started network application and transmitting the safety input content stencil; the auxiliary display unit is used for displaying according to the safety input content stencil and submitting the input data of a user and the safety input content stencil to the network monitoring module.
Owner:LENOVO (BEIJING) CO LTD
Active-passive-combined rope net dragging safety orbit leaving control method
ActiveCN104407620AEnsure safetyTo achieve the purpose of anti-collision controlPosition/course control in three dimensionsIn planeActive tension
An active-passive-combined rope net dragging safety orbit leaving control method includes: tethered system mass center acceleration is designed according to tethered satellite orbit leaving task, and a propelling system applies corresponding push force on a primary satellite so as to track the designed orbital maneuver path in real time; tension control quality is designed, a tethered winch mechanism generates corresponding tension to be applied to the primary satellite so as to actively control the in-plane swing angle of a tether, and orbital maneuver of the tethered system is achieved by dragging secondary satellites through the orbital maneuver of the primary satellite and tether tension control. The method has the advantages that the large vibration of the in-plane swing angle of the tether is avoided during dragging, the in-plane swing angle of the tether is stabilized in a constraint range, and collision is prevented; meanwhile, the in-plane swing angle is restrained by the appropriate orbital maneuver path design and the active tension control applied to a combined body, and safety orbit leaving control of a target is achieved.
Owner:BEIJING INST OF CONTROL ENG
Detection method for mismatching of model of closed-loop control system and object
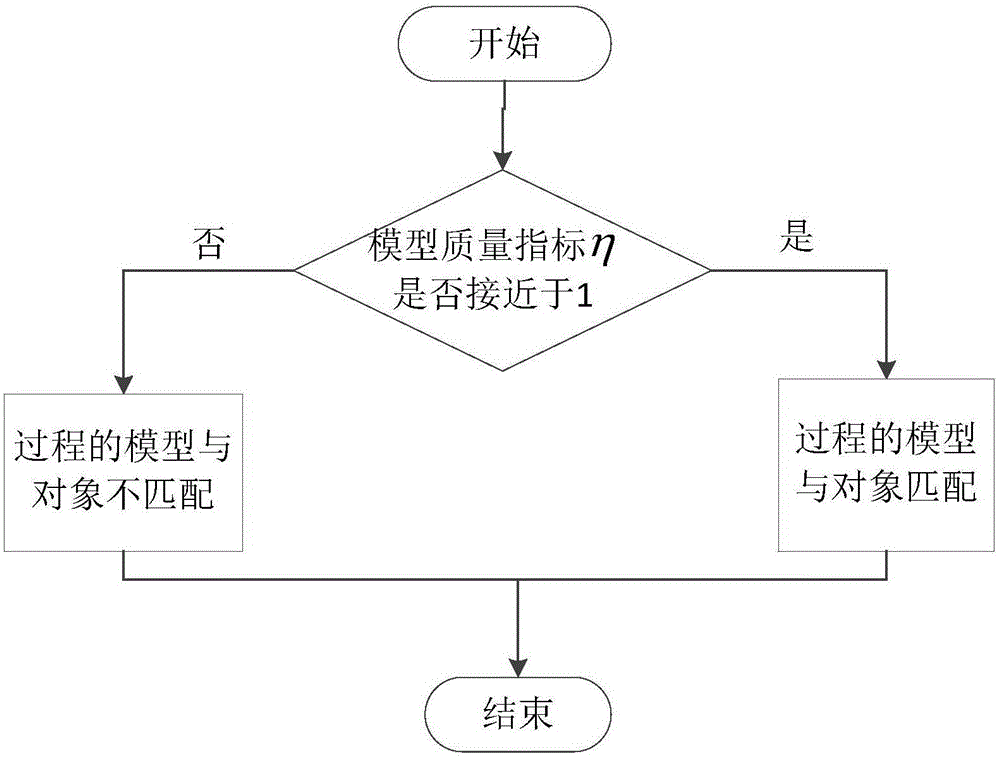
InactiveCN105807611AInterference updatePerformance impactAdaptive controlControl systemSystem maintenance
The invention discloses a detection method for mismatching of a model of a closed-loop control system and an object. Closed-loop data of the current system is obtained during normal operation of an industrial process. A model quality index is obtained by utilizing the data. The matching degree of the model and the object is detected according to the values of the model quality index. The more the model quality index is approximate to 1, the higher the matching degree of the model and the object is. The model quality index is insusceptible of change of adjusting parameters of the controller and the change of an interference model. By adopting the method, the mismatching of the model and the object can be removed from other elements affecting control performance effectively and influence on the control system performance by the mismatching of the model and the object can be analyzed more clearly. Besides, by adopting the method for detecting the mismatching of the model and the object, no external excitation signals are needed to add during the industrial process in normal operation. The mismatching of the model and the object can be detected in normal operation condition of the industrial process, so that the system maintenance cost is reduced and the system safety is improved.
Owner:HUAZHONG UNIV OF SCI & TECH
Message handling method and device and electronic equipment
ActiveCN103034542AIncrease flexibilityImprove system securityInterprogram communicationComputer hardwareElectric equipment
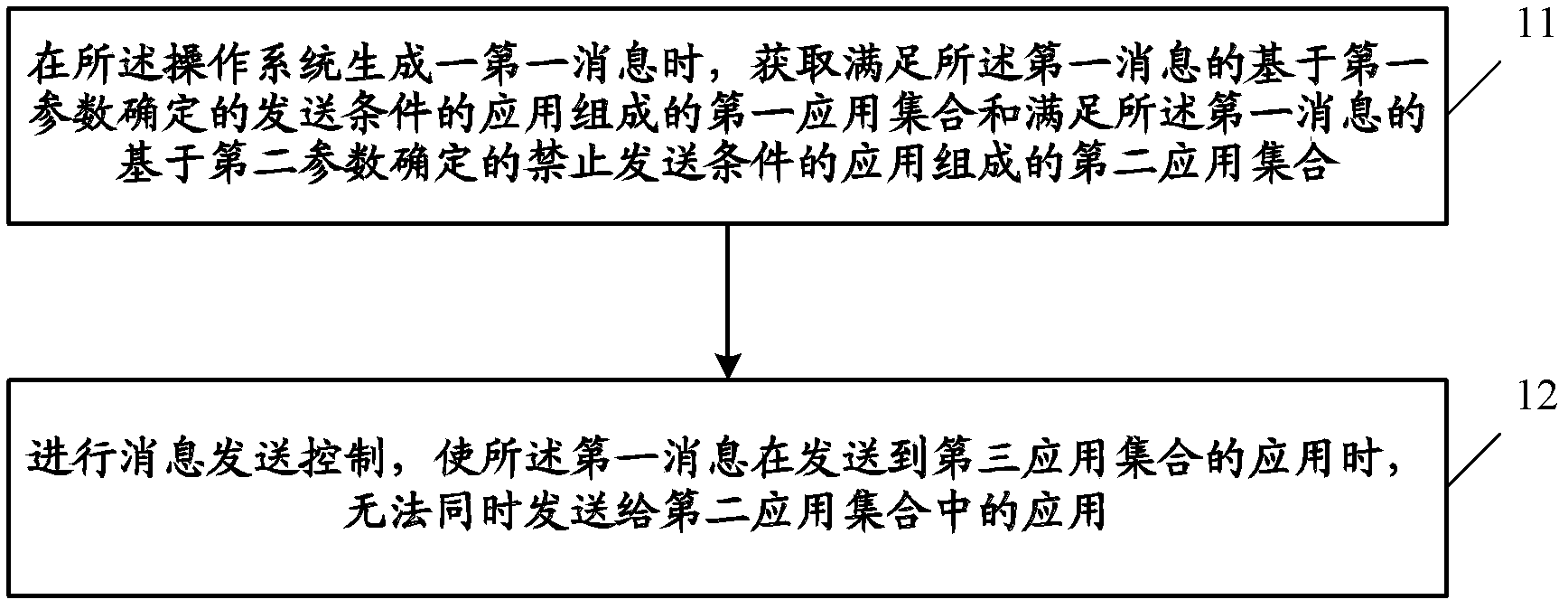
The invention aims at providing a message handling method, a message handling device and message handling electronic equipment. The message handling method comprises that a first application collection and a second application collection are obtained when an operating system generates a first message, the first application collection is composed of application which meets sending conditions that are determined on the basis of a first parameter, and the second application collection is composed of application which meets prohibited sending conditions that are determined on the basis of a second parameter. Message sending is controlled, when the first message is sent to a third application collection, the first message cannot be sent to the application in the second application collection, wherein the third application collection is a difference collection of the first application collection and the second application collection. According to the message handling method, the message handling device and the message handling electronic equipment, flexibility of message sending of the operating system is improved.
Owner:LENOVO (BEIJING) CO LTD
Method for model quality statistics of on-line monitoring closed-loop control system
InactiveCN108646553AMonitor qualityReal-time monitoring of mismatch detection indicatorsAdaptive controlLoop controlProcess model quality
The invention discloses a method for model quality statistics of an on-line monitoring closed-loop control system. The method comprises: using closed-loop data in a normal stage to obtain a model mismatch detection index in the normal stage; obtaining a control chart for monitoring the model mismatch detection index in the normal stage according to a progressive statistical distribution of the model mismatch detection index in the normal stage; calculating a sample mean value and a sample standard deviation of the model mismatch detection index in the normal stage, and obtaining a control lineand an alarm line of the control chart of the model mismatch detection index in the normal stage; using the closed-loop data in a monitoring phase to obtain a model mismatch detection index in the monitoring phase, wherein a controlled object of the closed-loop control system is not changed if the model mismatch detection index in the monitoring phase is within the control line, otherwise the process model quality of the closed-loop control system is changed. The method enables online evaluation of the process model quality of the closed loop control system.
Owner:HUAZHONG UNIV OF SCI & TECH
Mobile phone and method for preventing repeated sending of mobile phone by using same
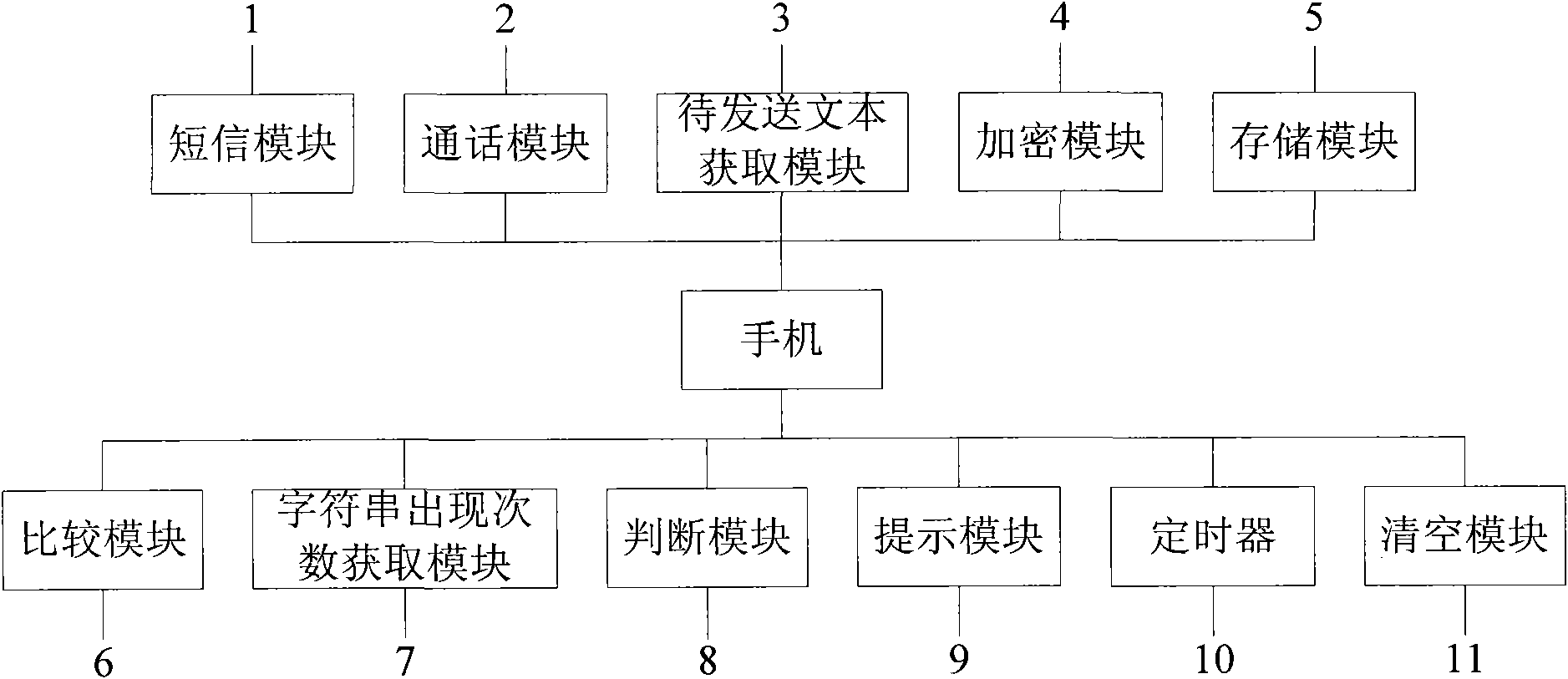
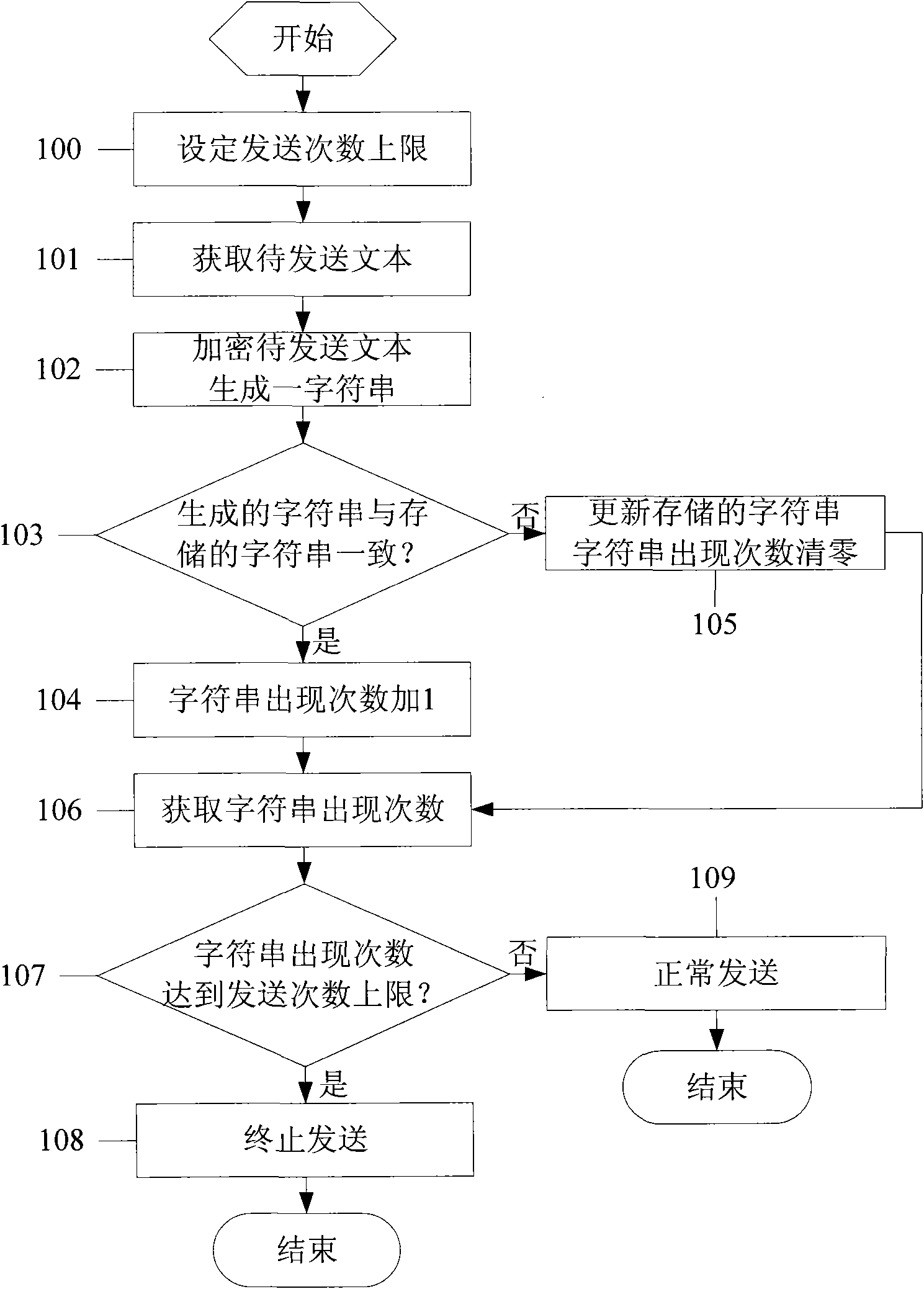
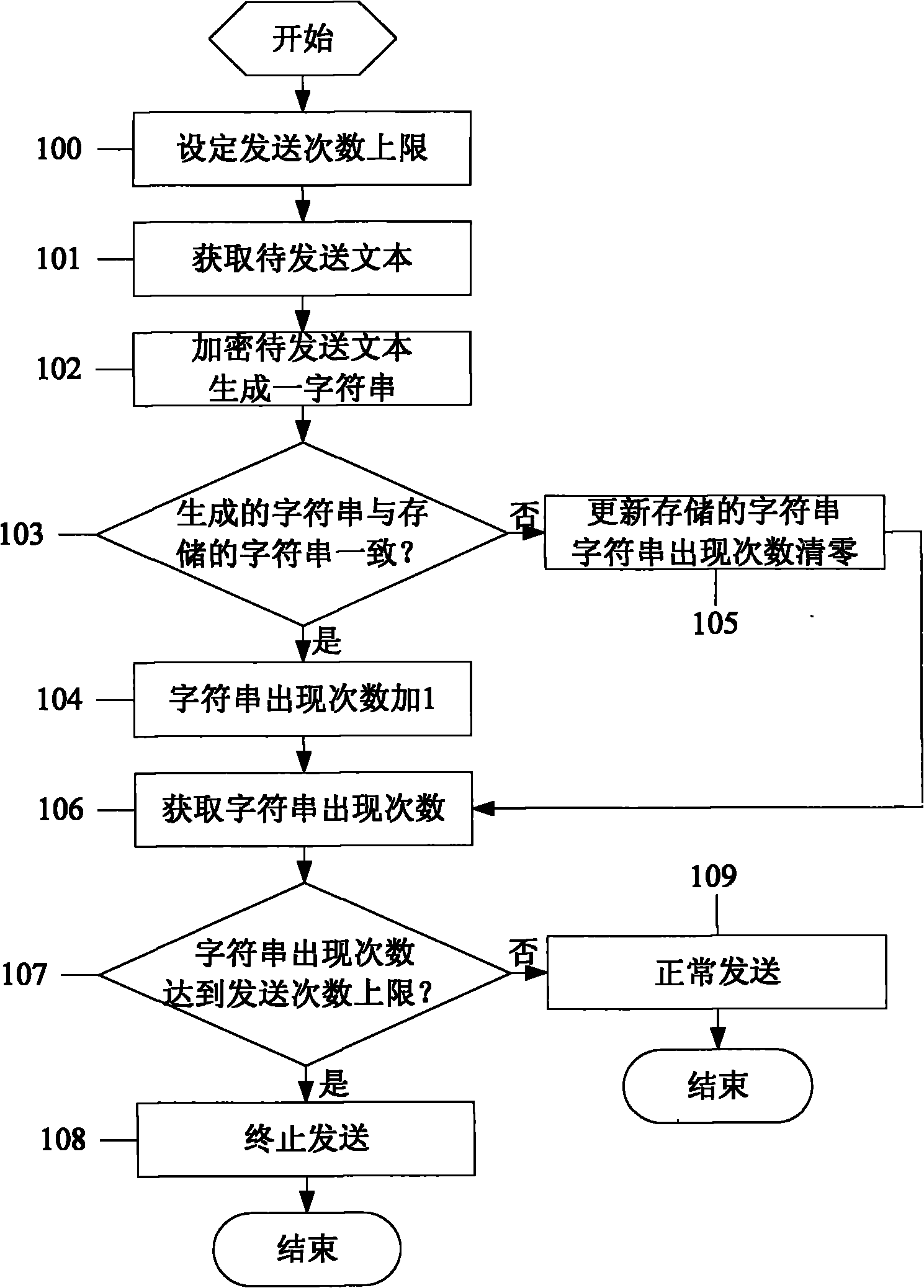
InactiveCN102340580AImprove system securityAvoid inconvenienceSubstation equipmentSecuring communicationComputer scienceMobile phone
The invention discloses a mobile phone, which comprises a module for acquiring a text to be transmitted, an encryption module, a memory module, a comparison module, a character string appearance frequency acquisition module and a judgment module. The invention further discloses a method for preventing the repeated sending of the mobile phone by using the mobile phone. According to the invention, the mobile phone can be prevented from continuously sending messages or dialing calls under the condition of software defect or unexpected unlocking, thus the system security of the mobile phone is improved and the inconvenience for users using the mobile phone and receivers caused by repeated sending can be avoided.
Owner:SHANGHAI SIMCOM LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com