Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
226 results about "Behavior rule" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Rules of behavior are part of a comprehensive program to provide complete information security. These guidelines were established to hold users accountable for their actions and responsible for information security.
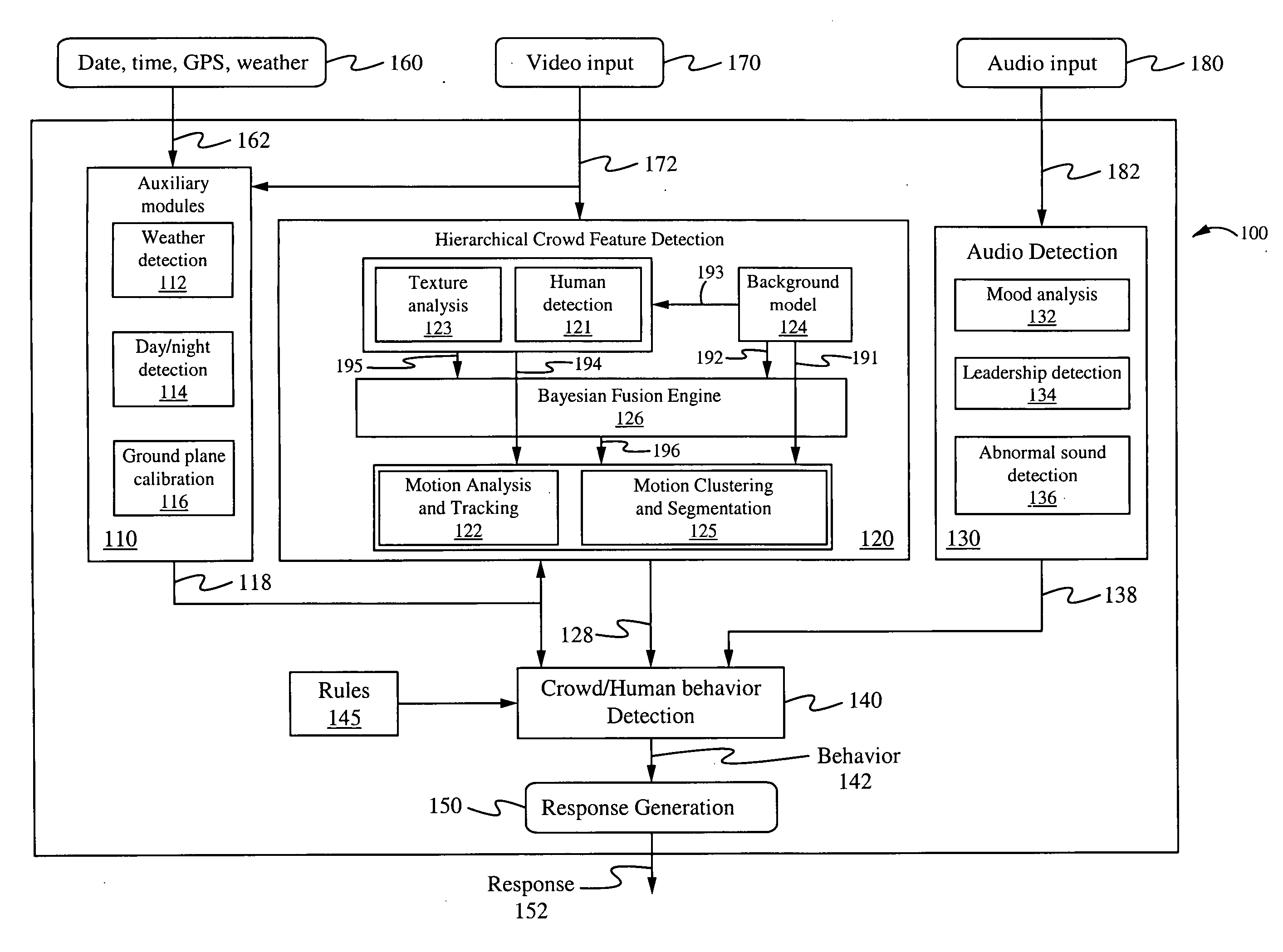
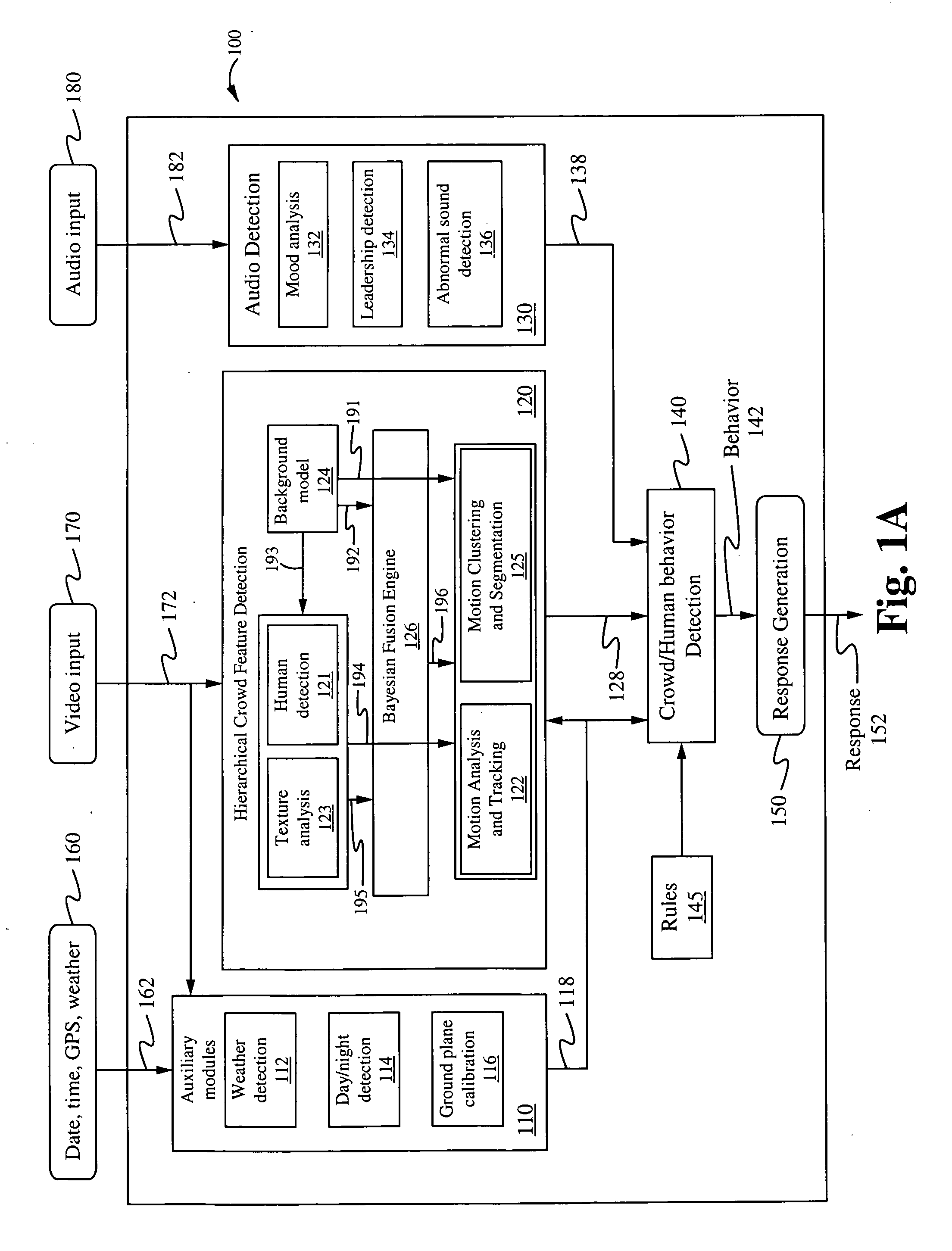
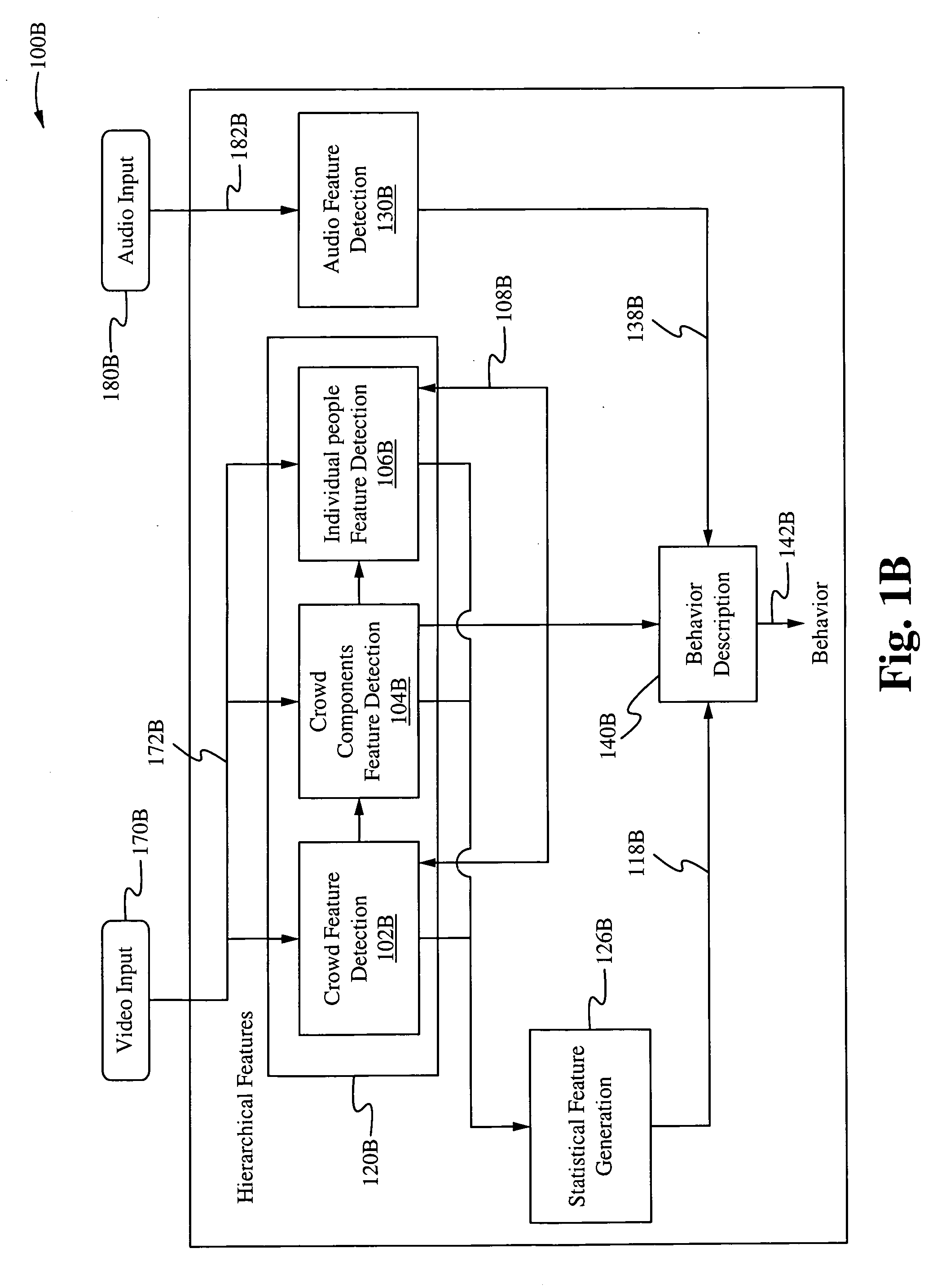
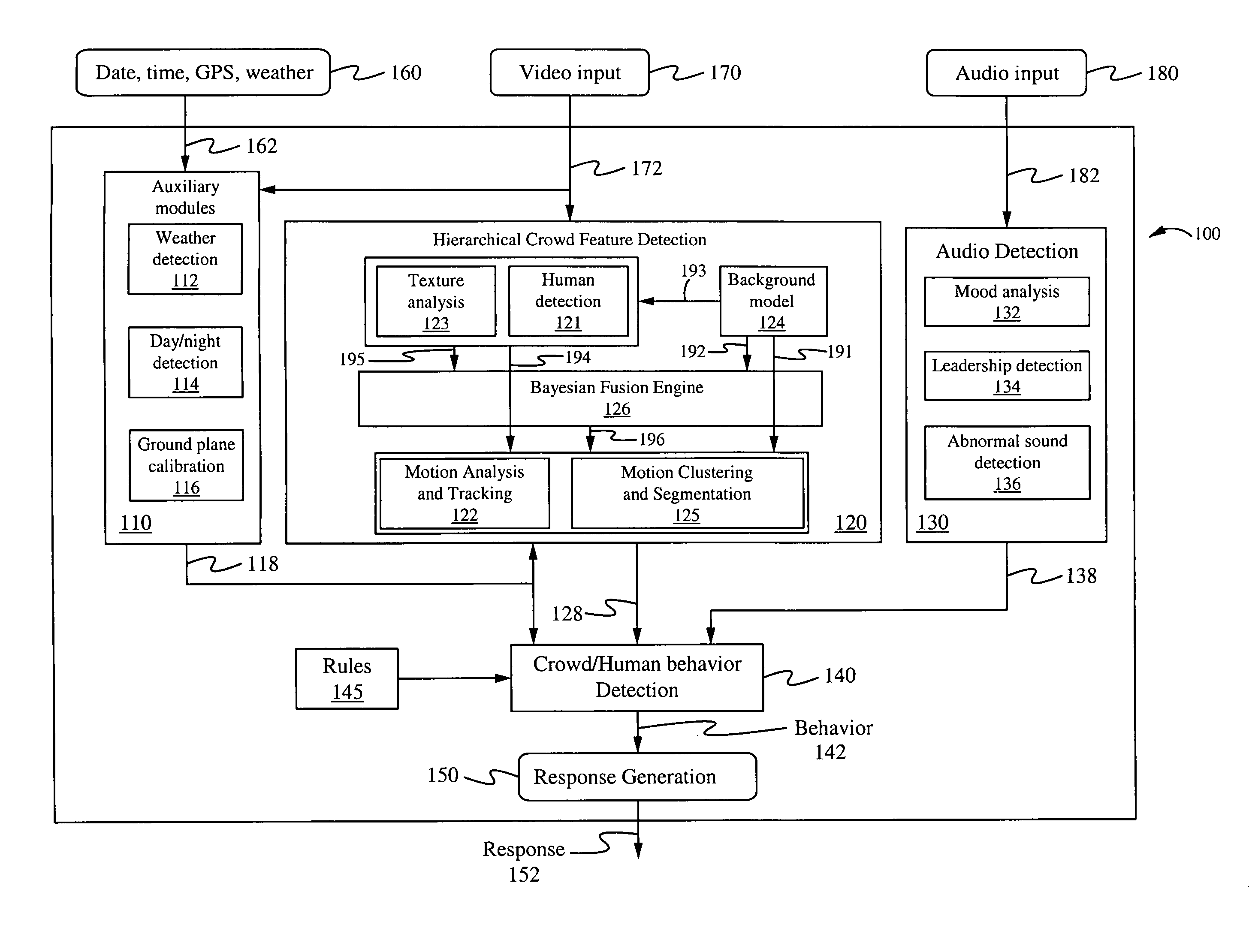
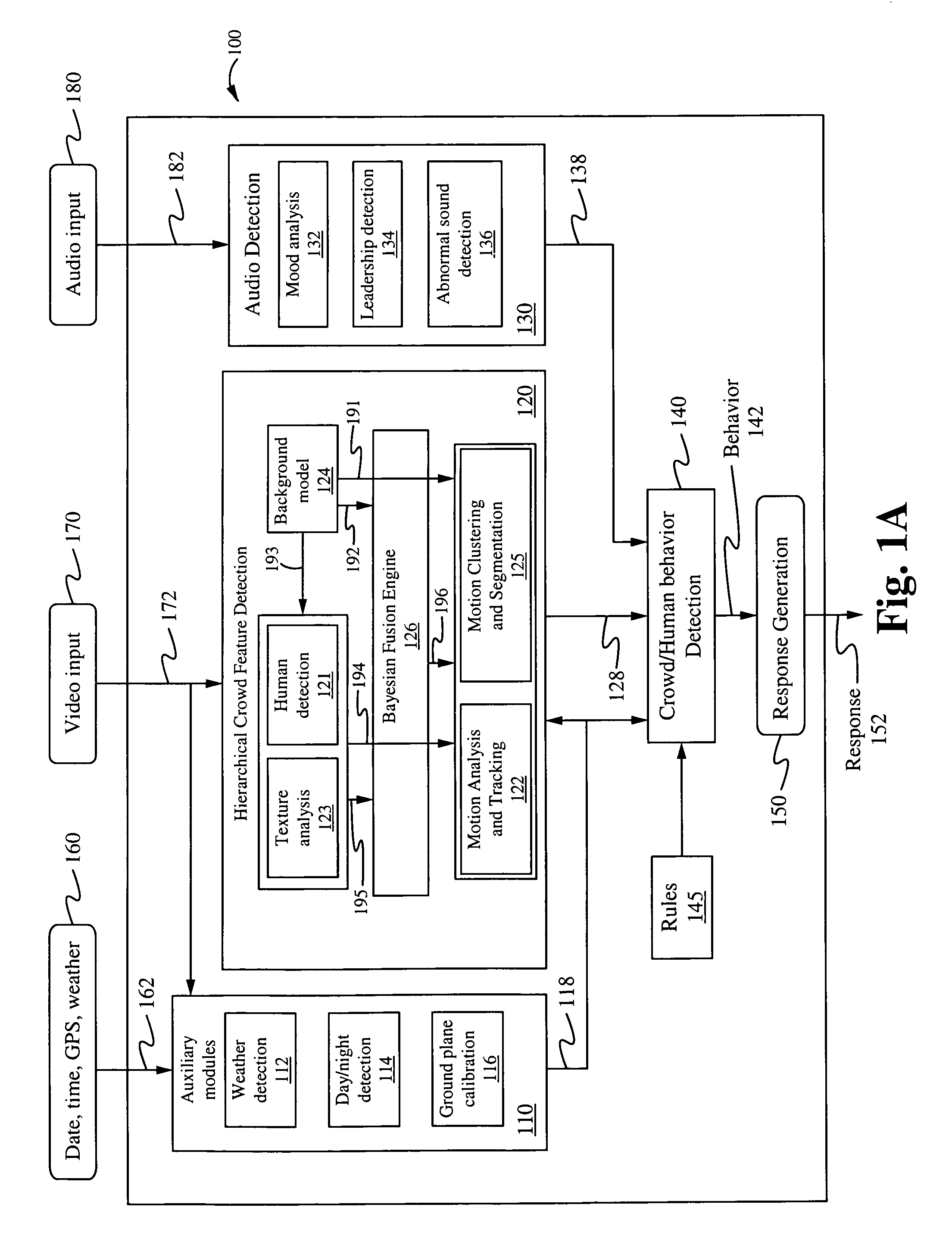
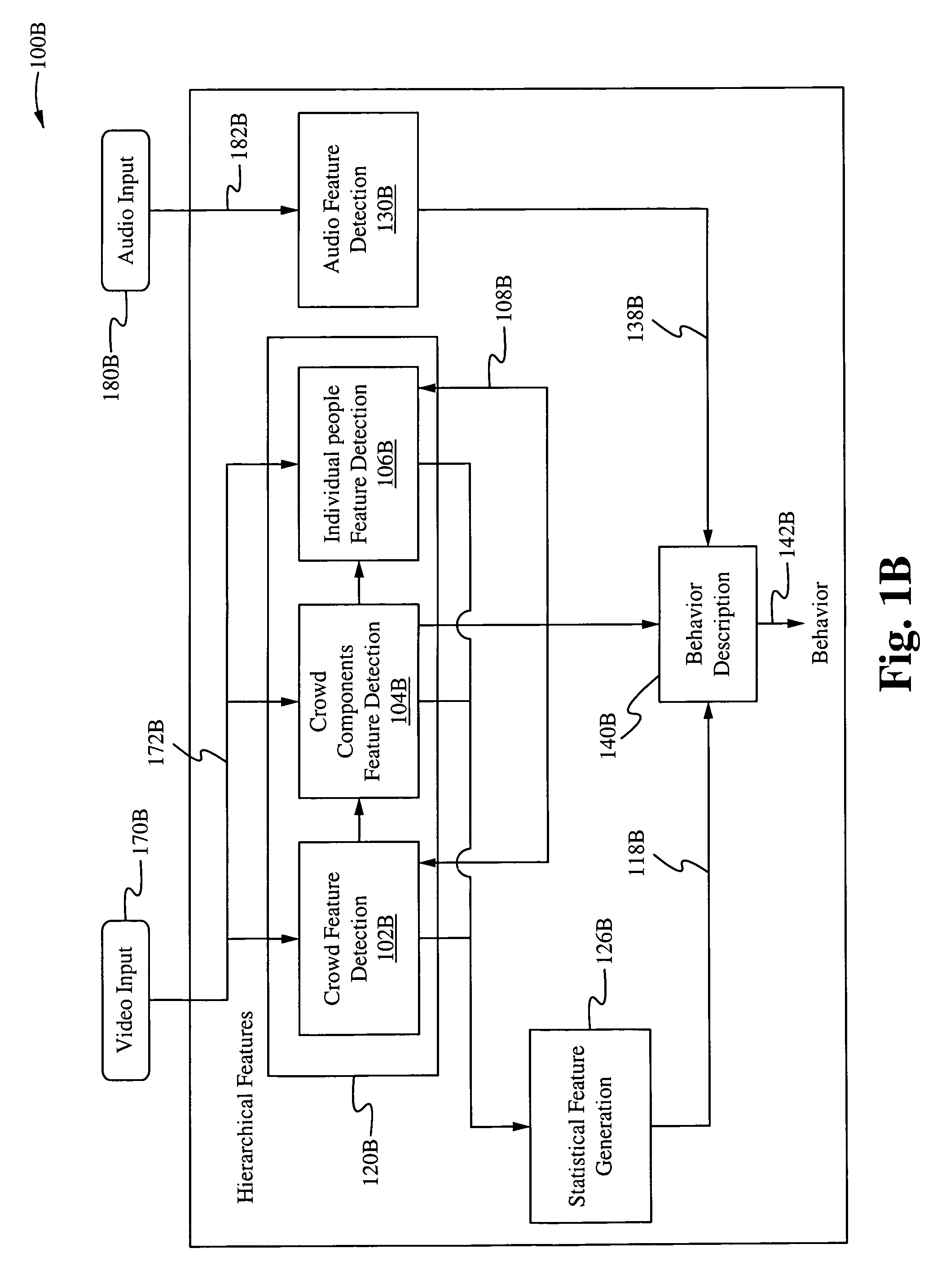
Method of and system for hierarchical human/crowd behavior detection
ActiveUS20090222388A1Improved crowd featureAdd featureKernel methodsDigital computer detailsAdaBoostCrowds
The present invention is directed to a computer automated method of selectively identifying a user specified behavior of a crowd. The method comprises receiving video data but can also include audio data and sensor data. The video data contains images a crowd. The video data is processed to extract hierarchical human and crowd features. The detected crowd features are processed to detect a selectable crowd behavior. The selected crowd behavior detected is specified by a configurable behavior rule. Human detection is provided by a hybrid human detector algorithm which can include Adaboost or convolutional neural network. Crowd features are detected using textual analysis techniques. The configurable crowd behavior for detection can be defined by crowd behavioral language.
Owner:AXIS
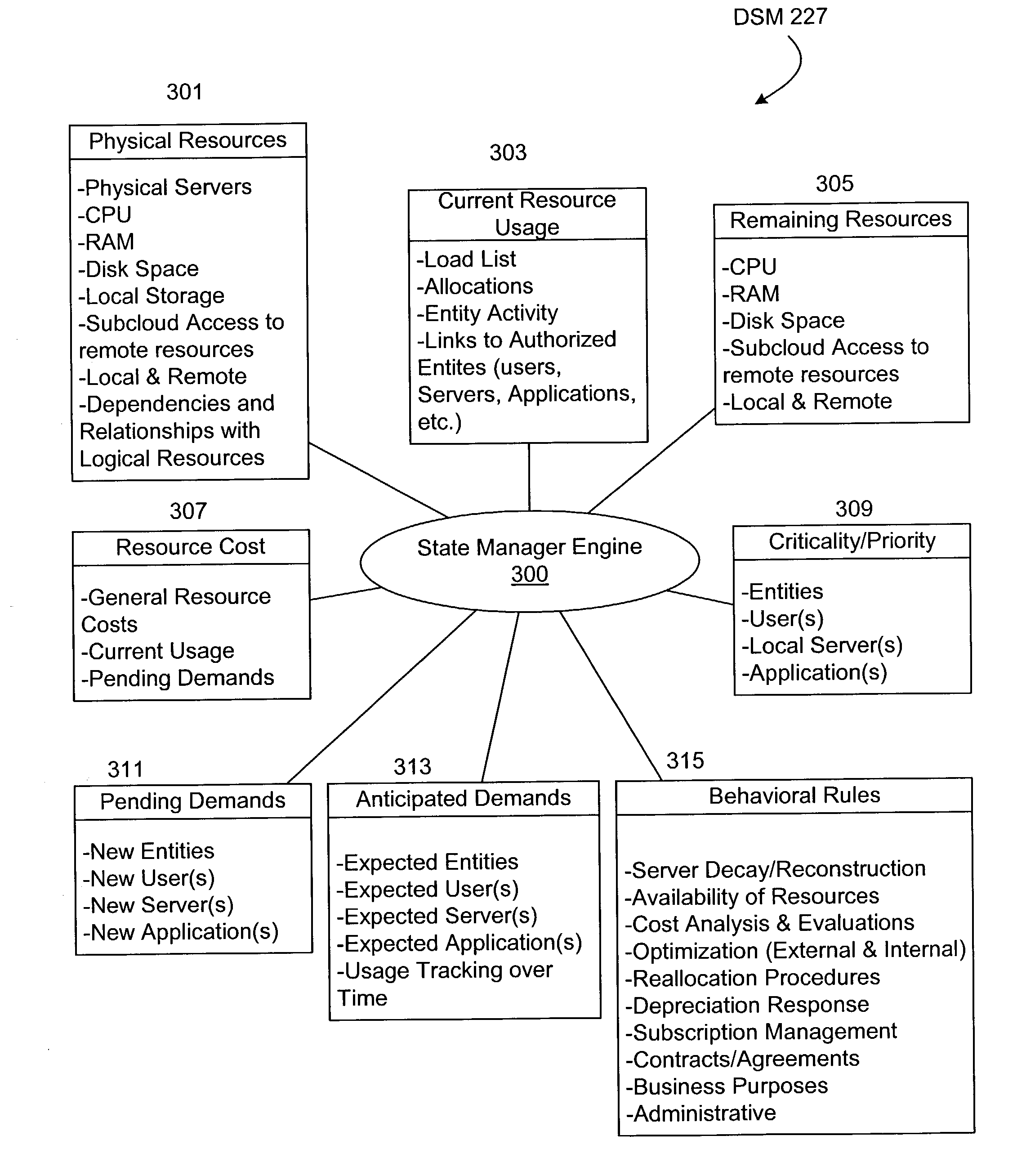
Near on-line servers
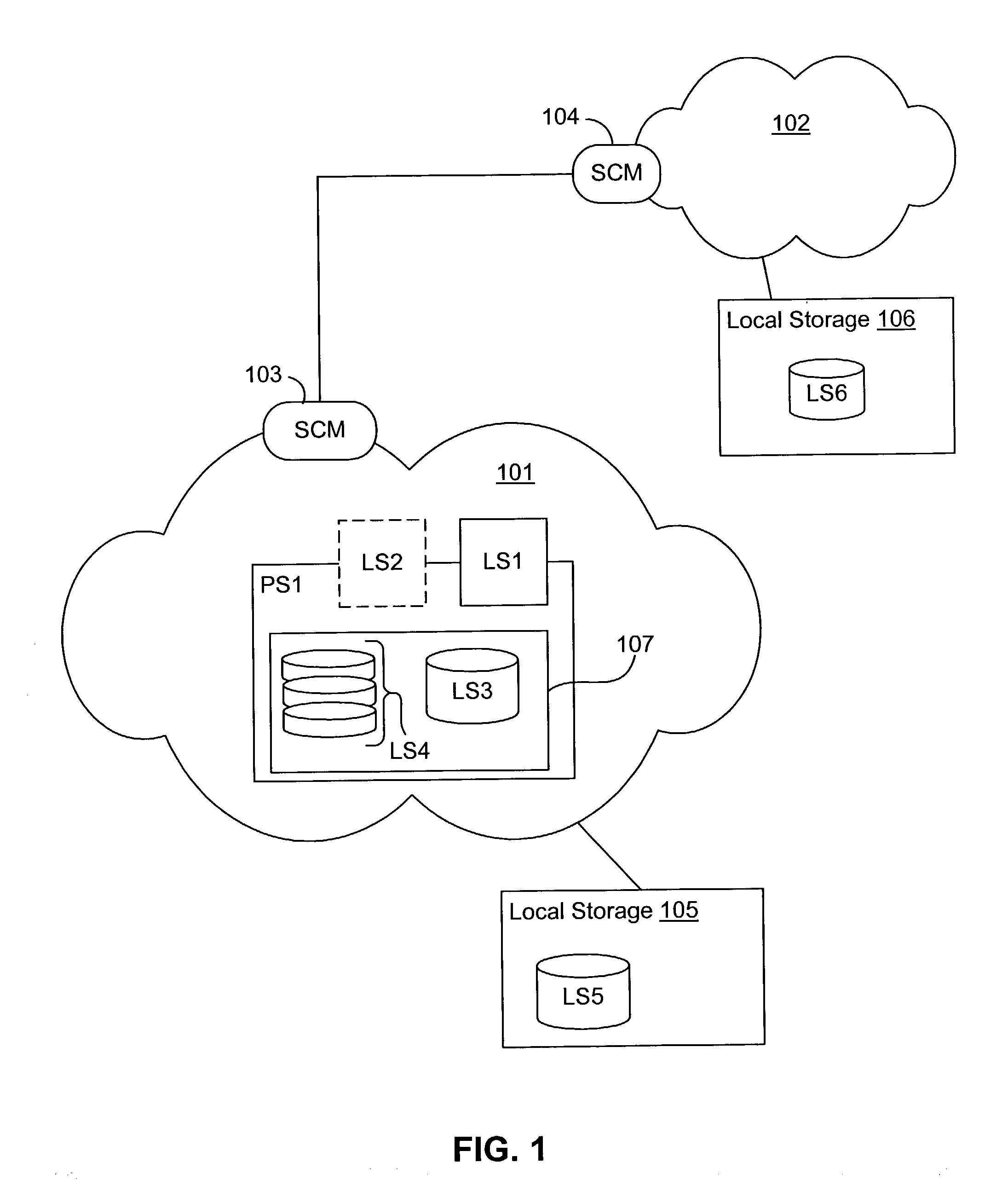
InactiveUS20030177176A1Maximize resource utilizationEnsure availabilityProgram initiation/switchingResource allocationVirtualizationResource utilization
A dynamic state manager (DSM) for a server cloud manager (SCM) of a virtualized logical server cloud including a resource definition, a rules module and a state manager engine. The resource definition incorporates information of the available physical and logical resources of the server cloud, including cost, priority, usage and demand information of the resources. The resource definition further incorporates dependencies and relationships between physical and logical resources. The rules module includes predetermined behavioral rules based on demand, usage, priority and cost information. The behavioral rules define optimized resource utilization of the resources of the server cloud. The state manager engine is linked to the resource definition and the rules module and cooperates with the SCM to apply the behavioral rules to achieve optimized resource utilization.
Owner:DELL PROD LP
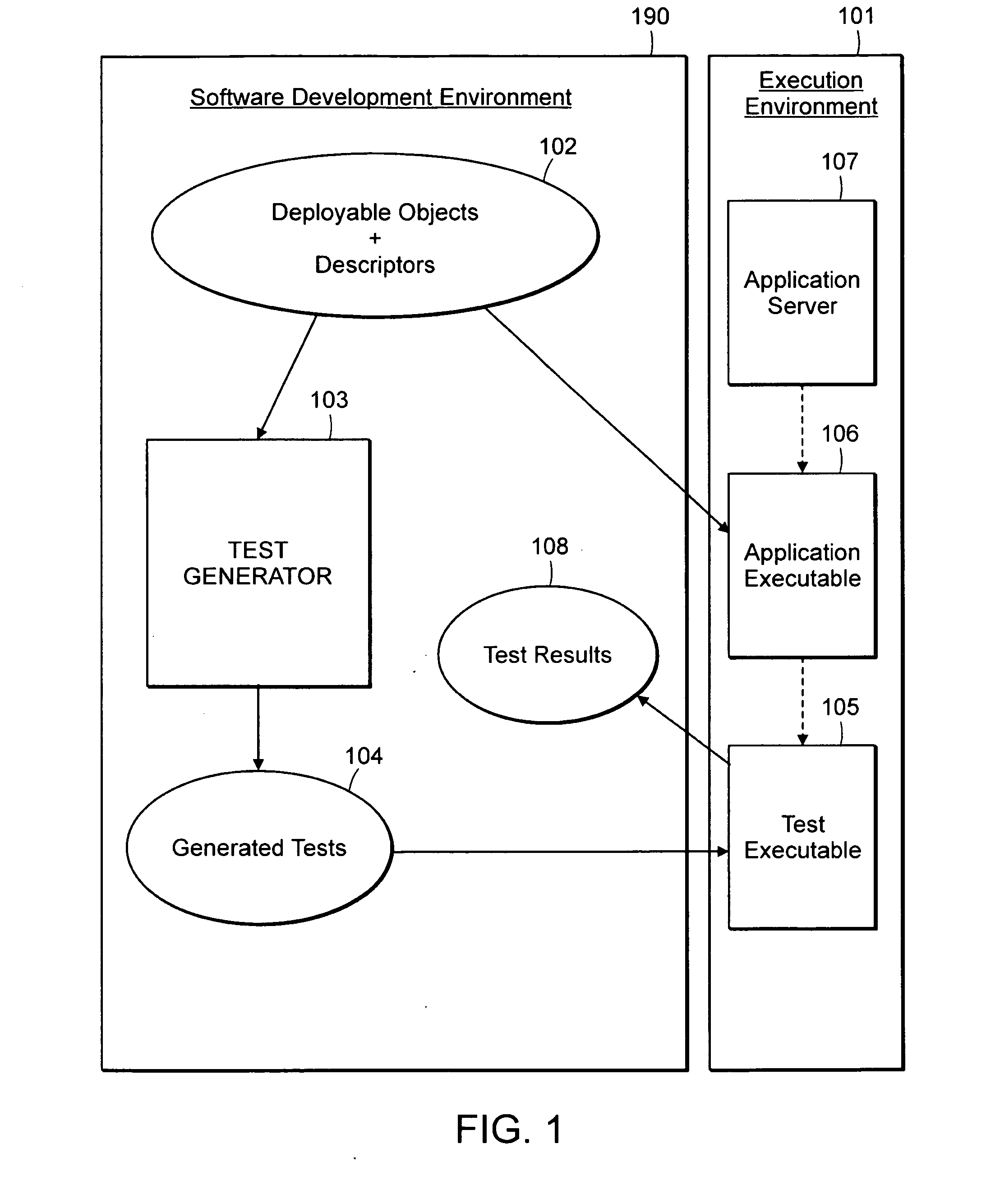
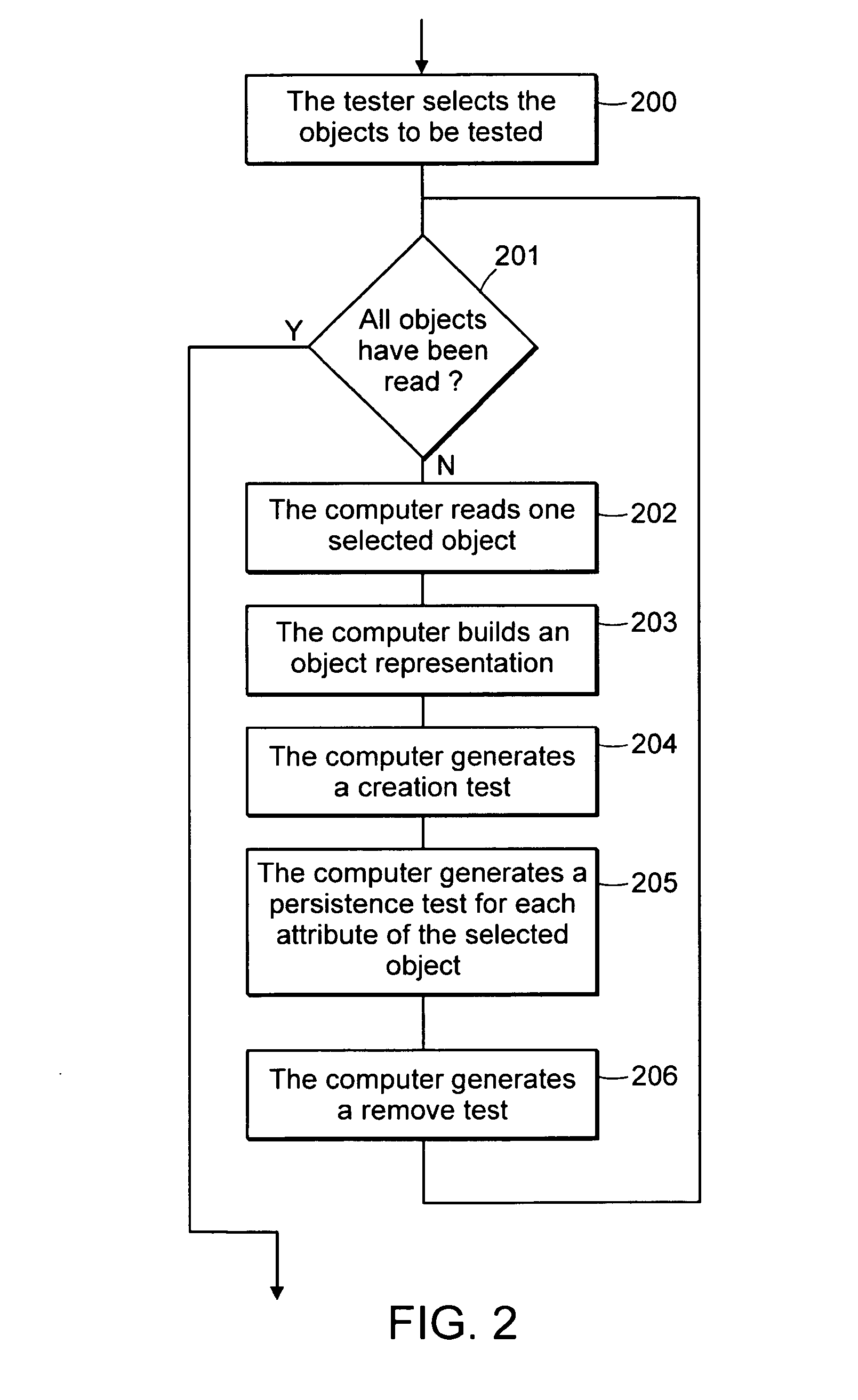
Computer method and system for automatically creating tests for checking software
Computer system and method automatically generates a test source code for checking validity of an application written in an object oriented language. The application includes objects accessible through an interface implementing programming rules and object behavior rules. For each object, the invention extracts object methods and attributes of the object interface which are impacted by the object behavior rules and extracts the object identification. The invention fills the variable fields of a source code template with the extracted information. The template non variable source code is in conformance with the programming rules and implements a scenario for checking a set of object behavior rules; thus the filled template forms a generated test source code. For distributed applications, the specifications may be EJB or CORBA and the Test Generator uses templates for checking the life-cycle (creation, persistency, removal) of deployed objects.
Owner:IBM CORP
Computer method and system for automatically creating tests for checking software
InactiveUS7707553B2Error detection/correctionSoftware engineeringComputerized systemApplication software
Computer system and method automatically generates a test source code for checking validity of an application written in an object oriented language. The application includes objects accessible through an interface implementing programming rules and object behavior rules. For each object, the invention extracts object methods and attributes of the object interface which are impacted by the object behavior rules and extracts the object identification. The invention fills the variable fields of a source code template with the extracted information. The template non variable source code is in conformance with the programming rules and implements a scenario for checking a set of object behavior rules; thus the filled template forms a generated test source code. For distributed applications, the specifications may be EJB or CORBA and the Test Generator uses templates for checking the life-cycle (creation, persistency, removal) of deployed objects.
Owner:INT BUSINESS MASCH CORP
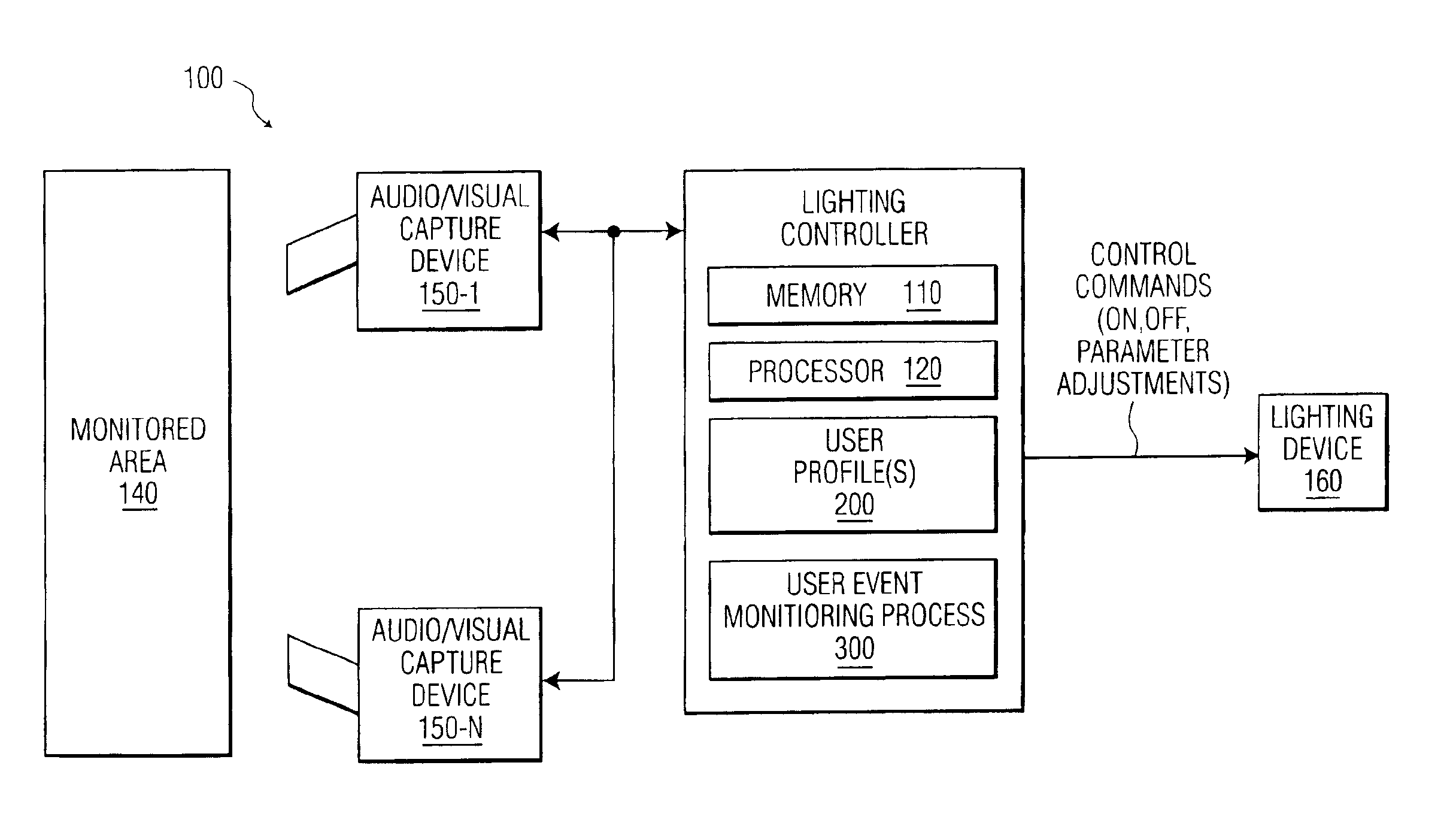
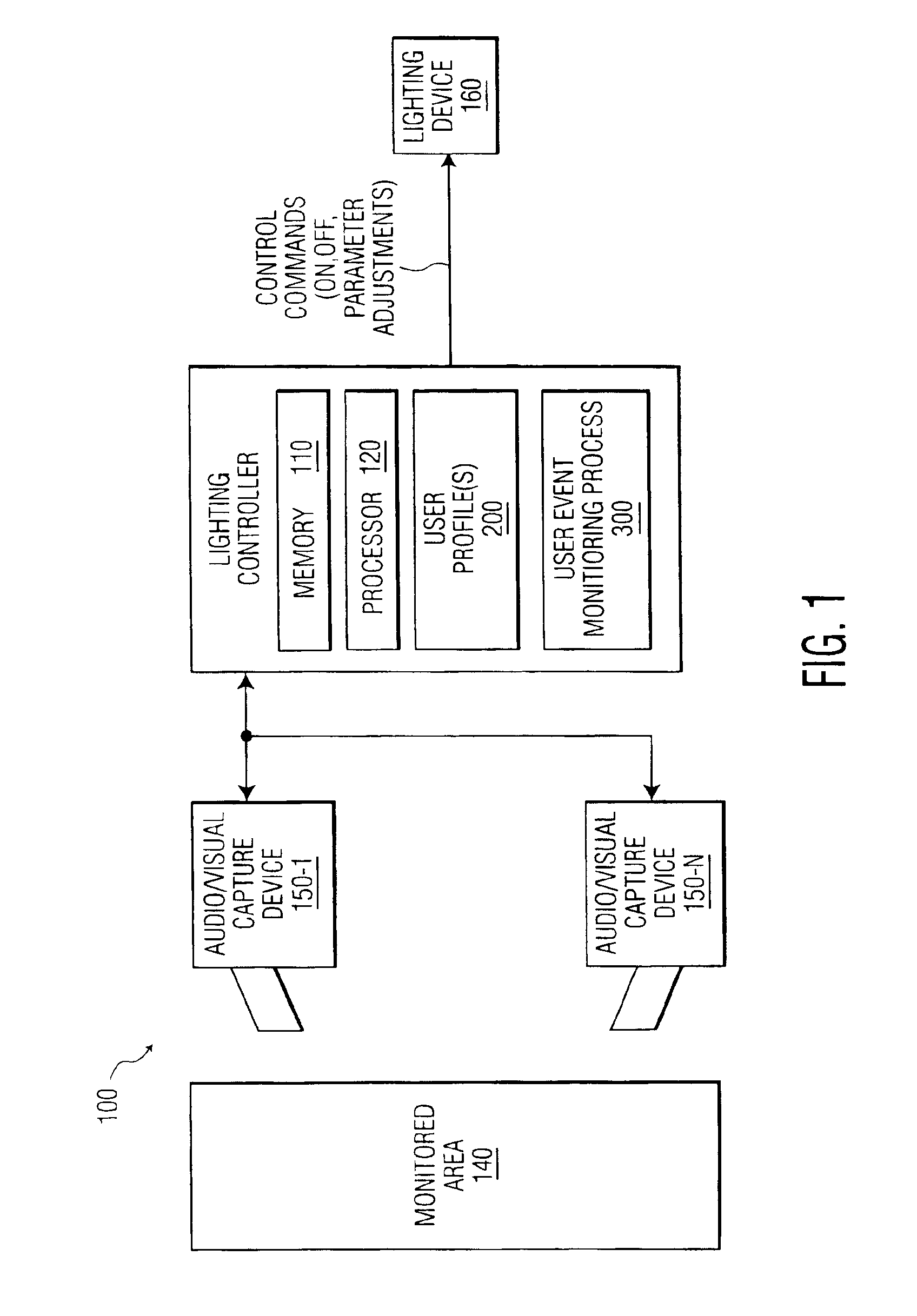
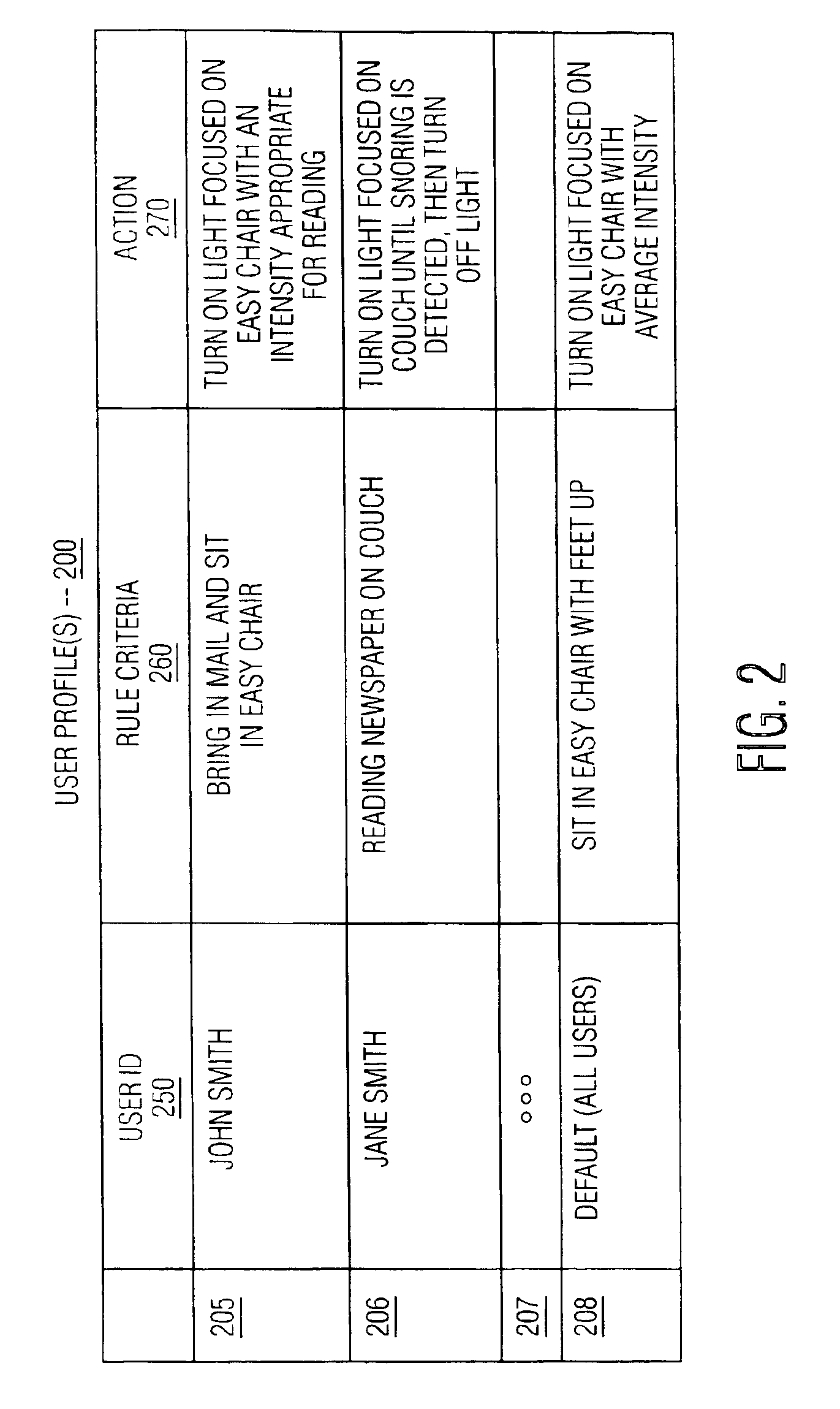
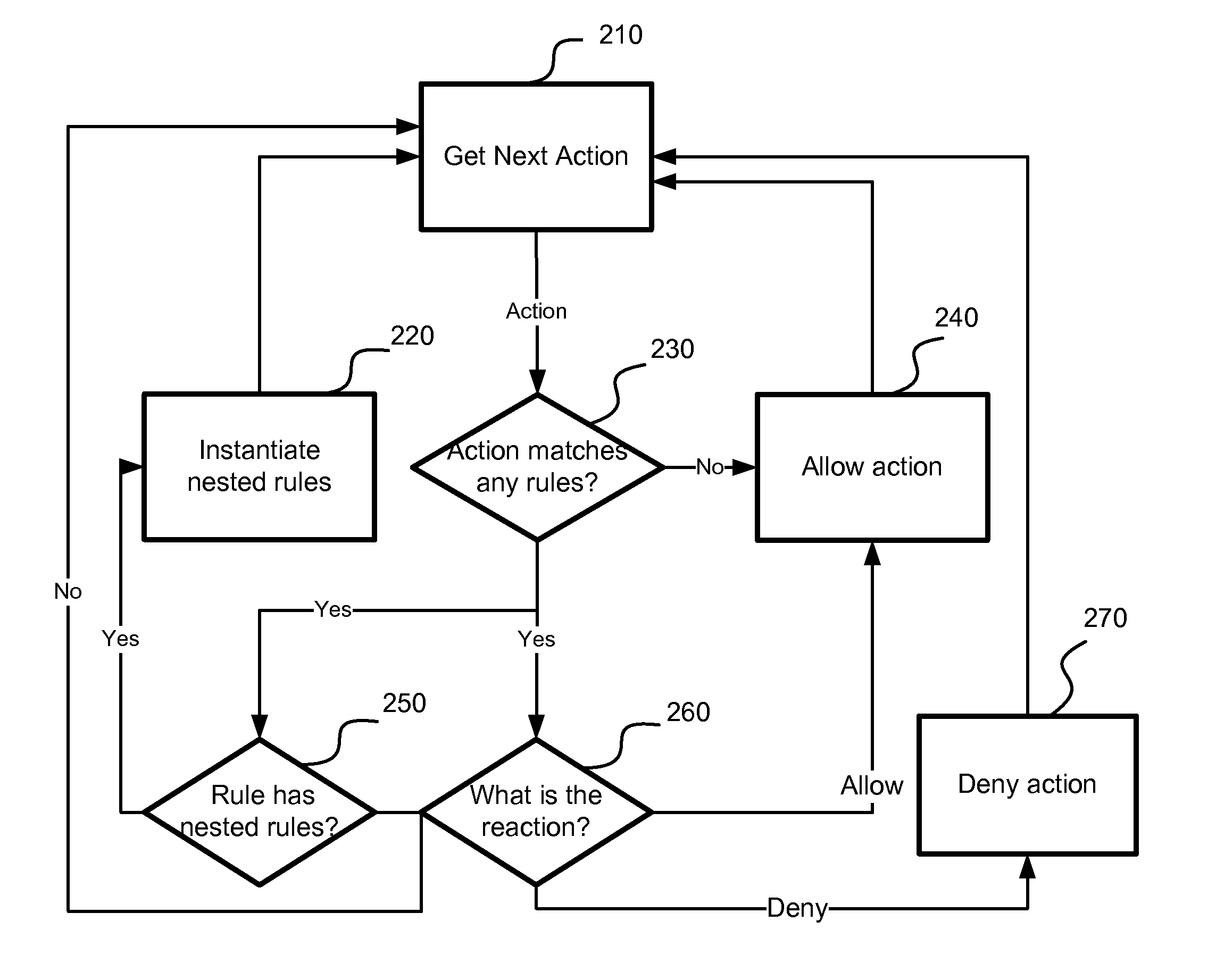
Method and apparatus for controlling lighting based on user behavior
Owner:SIGNIFY HLDG BV
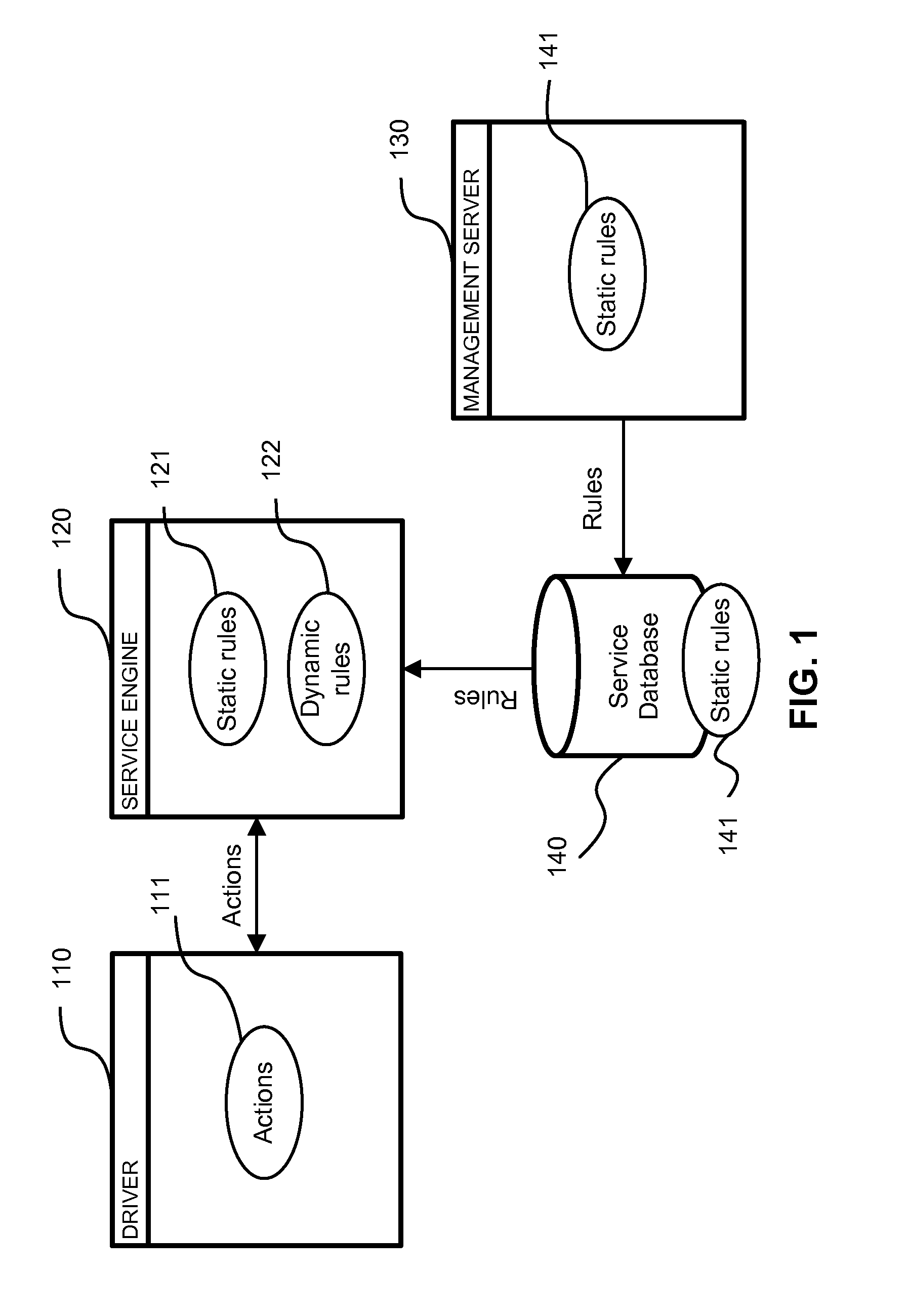
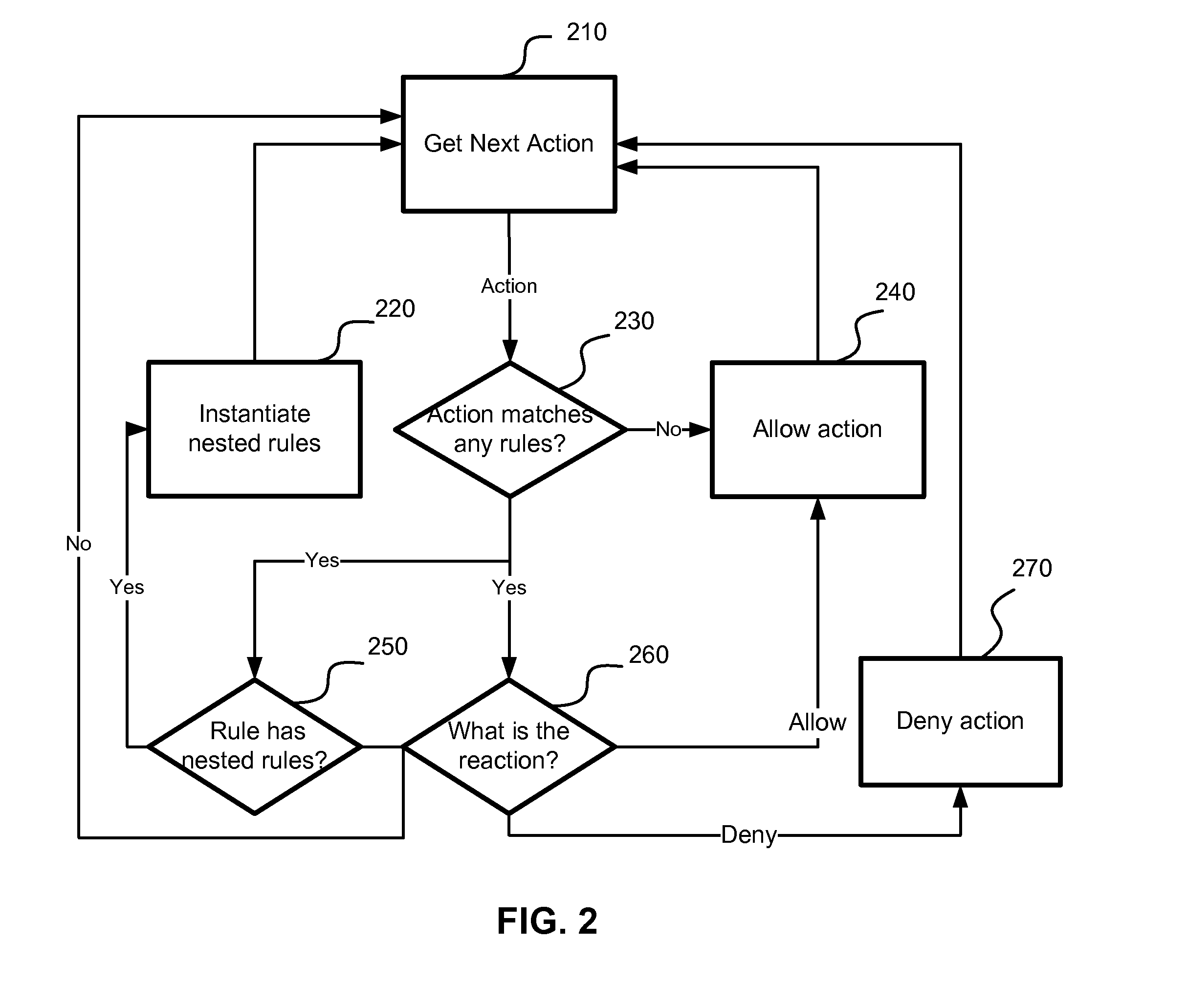
Application of nested behavioral rules for anti-malware processing
InactiveUS8850579B1Save system resourcesLarge actionMemory loss protectionError detection/correctionRequest - actionTheoretical computer science
A system, method and computer program product for implementing dynamic behavior rules for malware detection. A method of heuristic analysis of computer program execution is used. A behavior of a computer program is monitored, analyzed and blocked in runtime. Actions performed or triggered by each executable component are compared against a set of behavioral rules. The behavioral rules determine wherever the requested action is allowed or blocked, and which new behavioral rules are needed to be applied to future actions. Executed actions (allowed or blocked) introduce new dynamic behavioral rules to the computer system, which in turn can apply these rules for analyzing behavior of subsequent components executed on the computer system.
Owner:SAFE N SEC
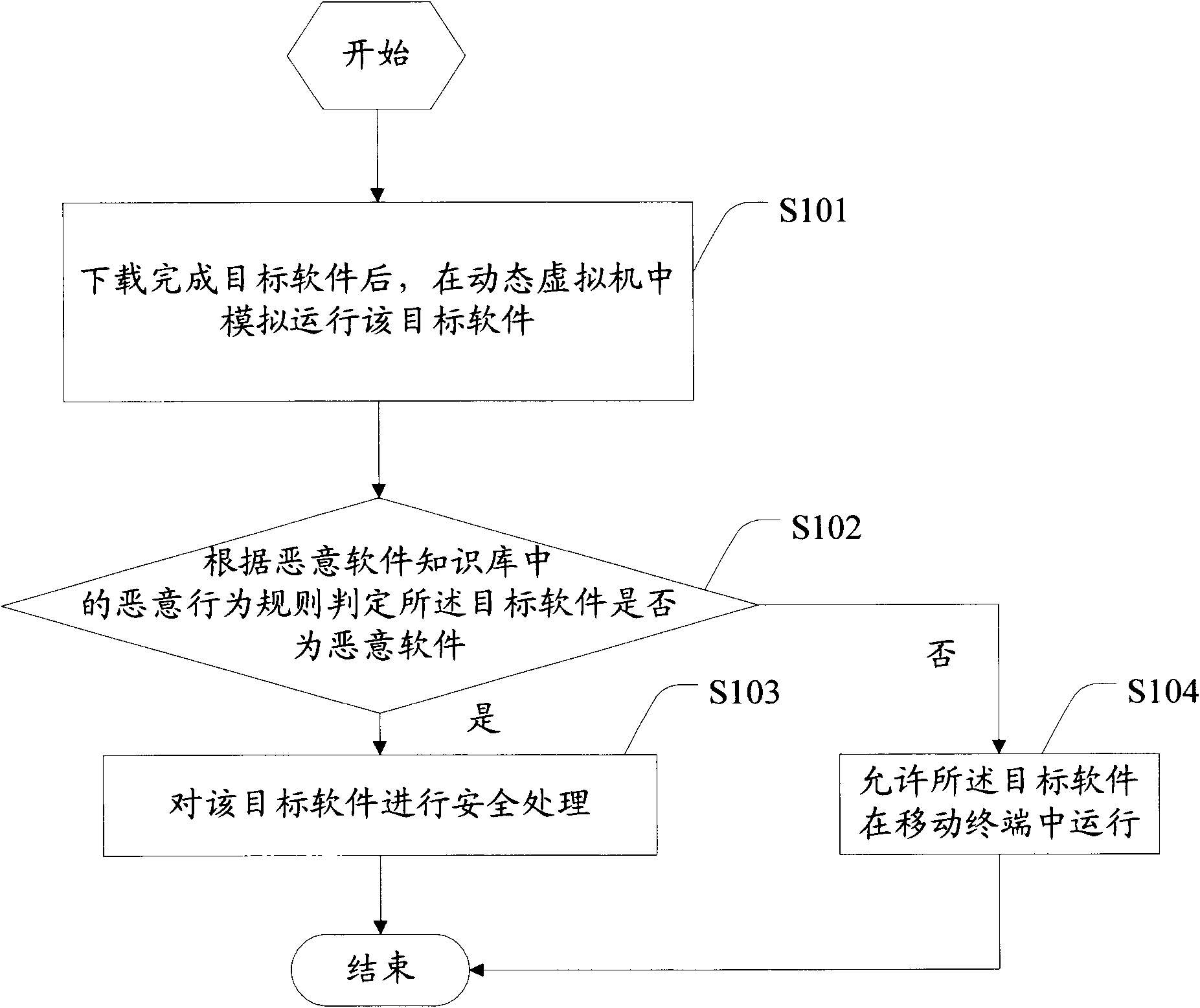
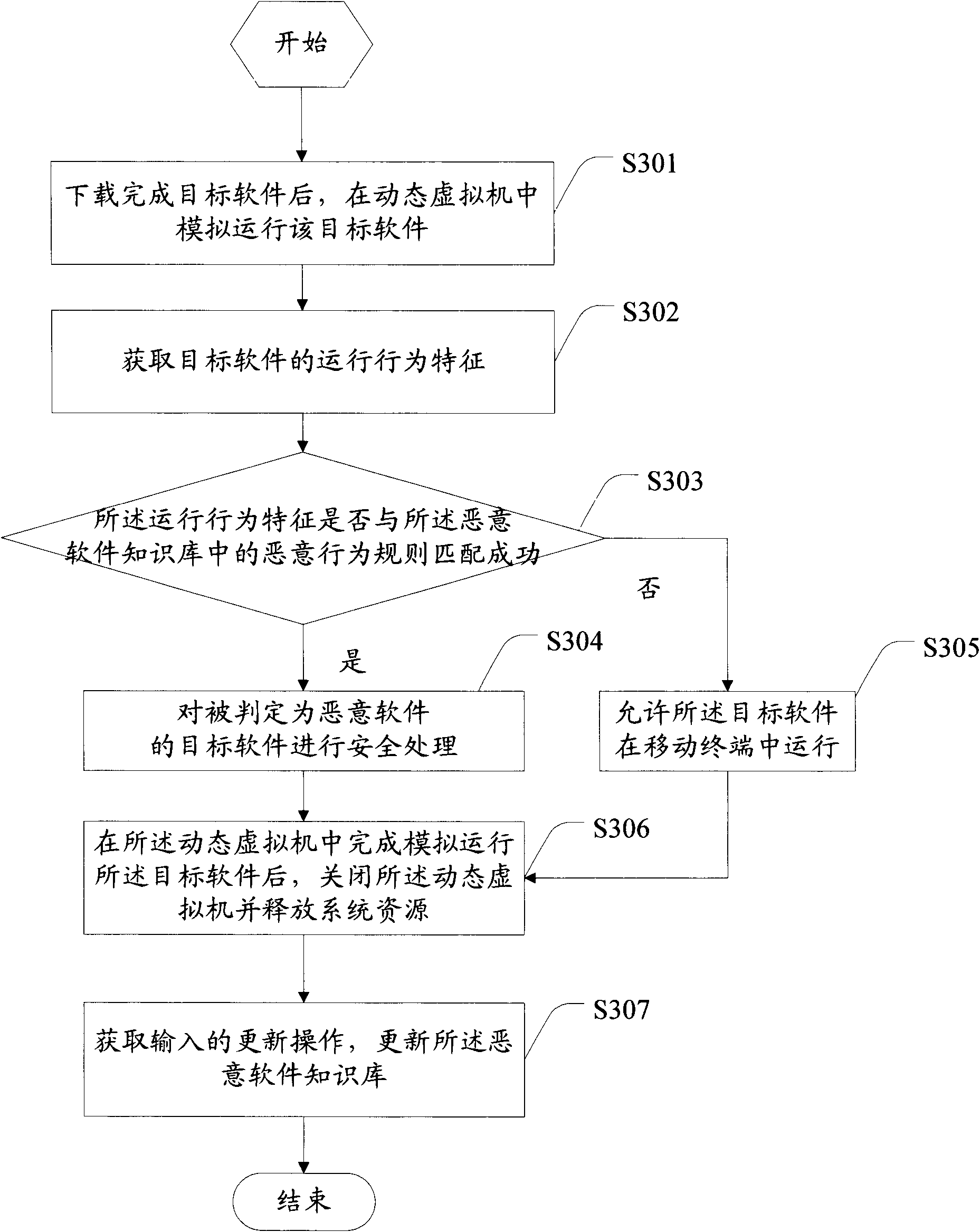
Information safety detection method and a mobile terminal
InactiveCN101959193AEffective interceptionProtection securityProgram loading/initiatingSecurity arrangementSoftware engineeringComputer terminal
The invention discloses an information safety detection method. The method comprises the following steps of: after downloading target software, simulating to run the target software in a dynamic virtual machine; according to malicious behavior rules in a malicious software knowledge base, judging whether the target software is malicious software or not; if the target software is the malicious software, performing safety processing on the target software; and if the target software is not the malicious software, allowing the target software to run in a mobile terminal. Correspondingly, the invention also discloses the mobile terminal used for implementing the method. Because the target software is simulated to run in the dynamic virtual machine, the malicious software does not threaten the mobile terminal, the malicious software can be effectively intercepted at the same time and then the user information safety is protected.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Method of and system for hierarchical human/crowd behavior detection
The present invention is directed to a computer automated method of selectively identifying a user specified behavior of a crowd. The method comprises receiving video data but can also include audio data and sensor data. The video data contains images a crowd. The video data is processed to extract hierarchical human and crowd features. The detected crowd features are processed to detect a selectable crowd behavior. The selected crowd behavior detected is specified by a configurable behavior rule. Human detection is provided by a hybrid human detector algorithm which can include Adaboost or convolutional neural network. Crowd features are detected using textual analysis techniques. The configurable crowd behavior for detection can be defined by crowd behavioral language.
Owner:AXIS
Service flow detection method and system
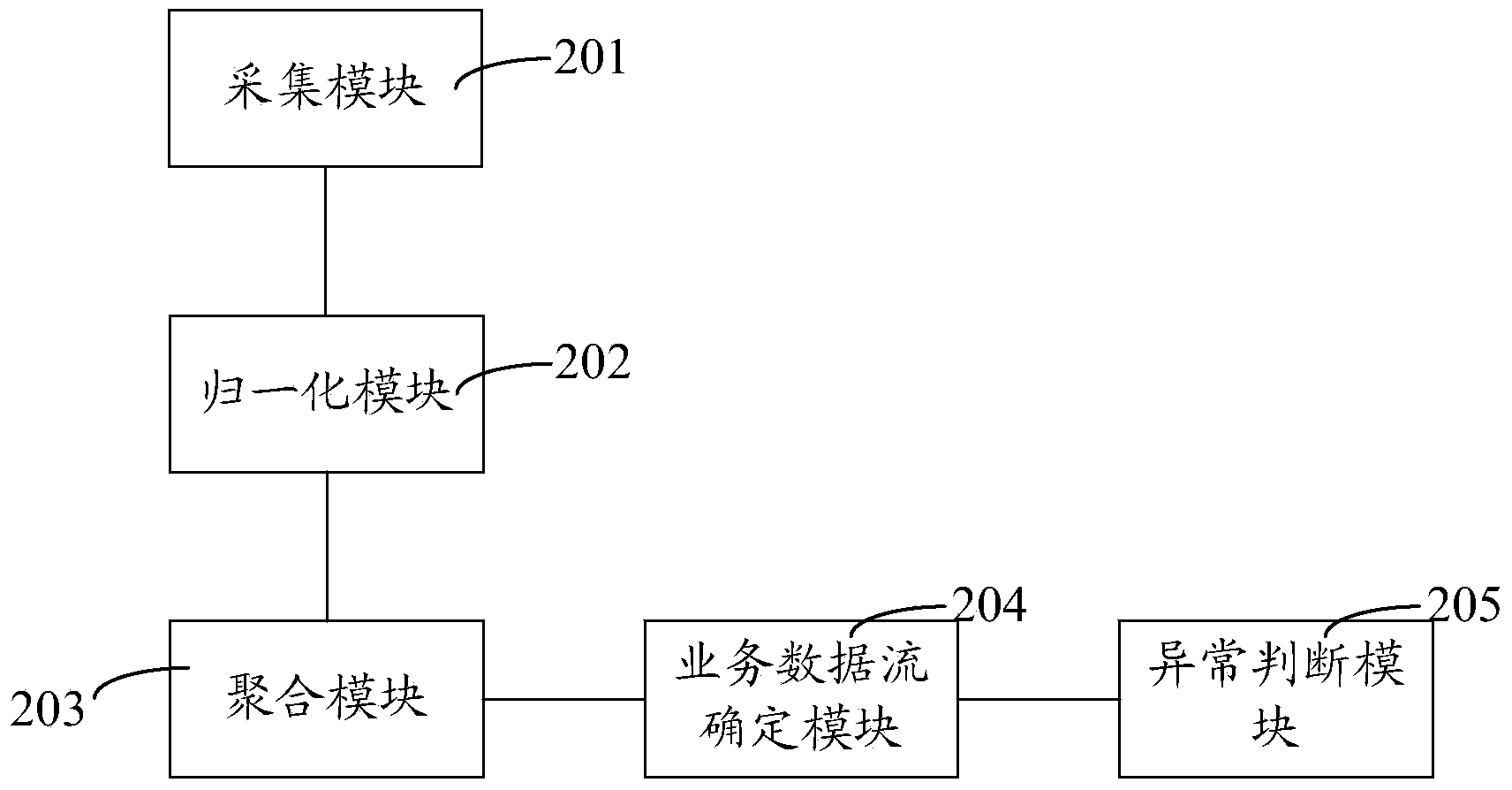
ActiveCN103532776AImprove accuracyAvoid misjudging the business data flow as abnormalData switching networksService flowTime information
The invention discloses a service flow detection method and system. The method comprises the following steps of collecting the flow data of each piece of equipment; carrying out normalization processing on each piece of flow data to obtain an equipment data flow containing space information, time information and technical index information; on the basis of the space information, polymerizing the equipment data flow to obtain a service flow tree; according to the relationship between sub service data flow and the equipment data flow in the service flow tree as well as the equipment data flow, determining the sub service data flow; comparing the service data flow, the equipment data flow and a preset service behavior rule to obtain the abnormal state of the equipment data flow and the sub service data flow; according to the abnormal state of the equipment data flow, the abnormal state of the sub service data flow, the service flow tree, the abnormal weight of the preset equipment data flow and the abnormal weight of the preset sub service data flow, obtaining a main service health degree index; according to the main service health degree index, determining whether the main service data flow is abnormal or not. By adopting the scheme, the detection accuracy is improved.
Owner:POWER DISPATCHING CONTROL CENT OF GUANGDONG POWER GRID CO LTD
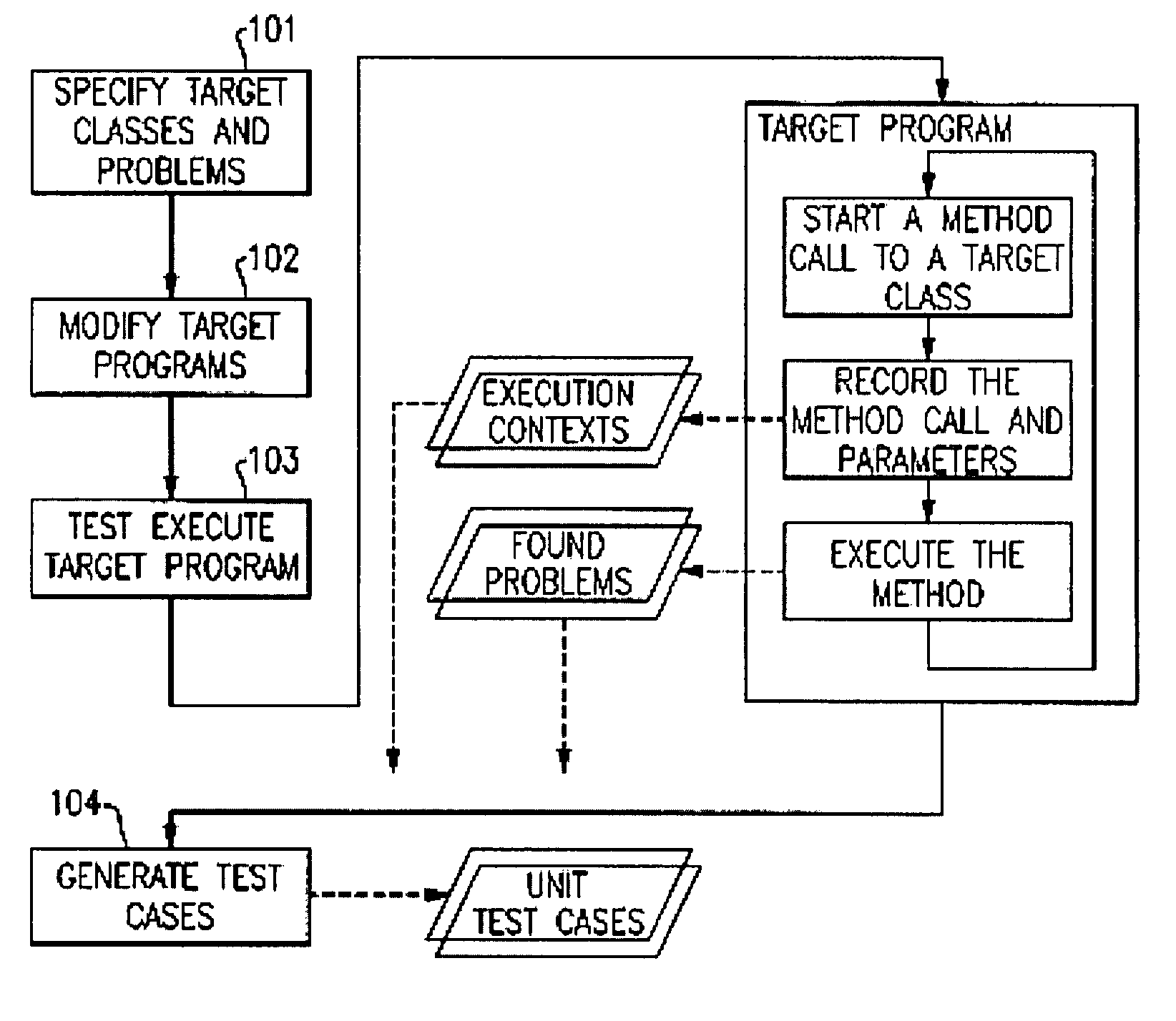
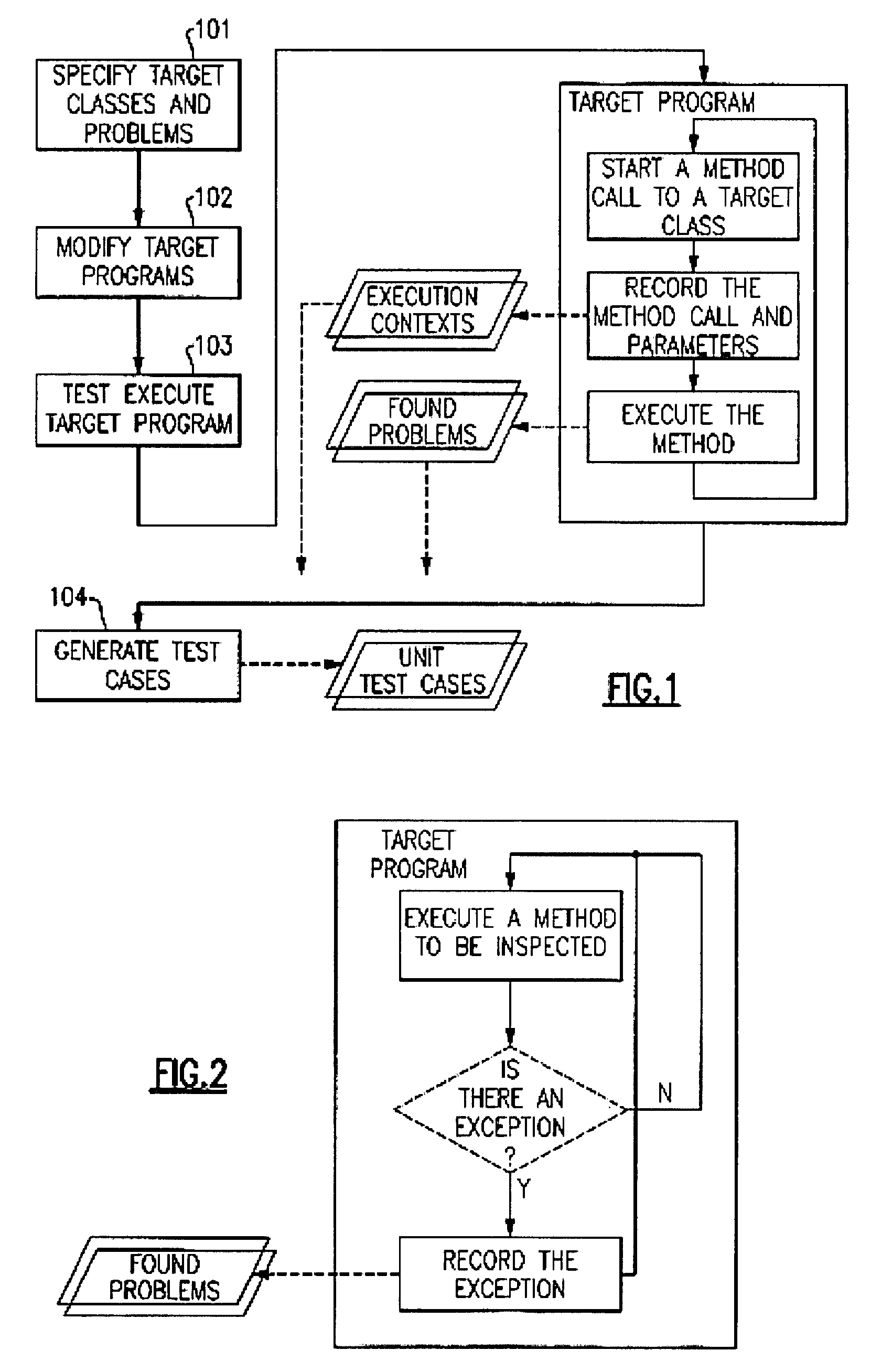
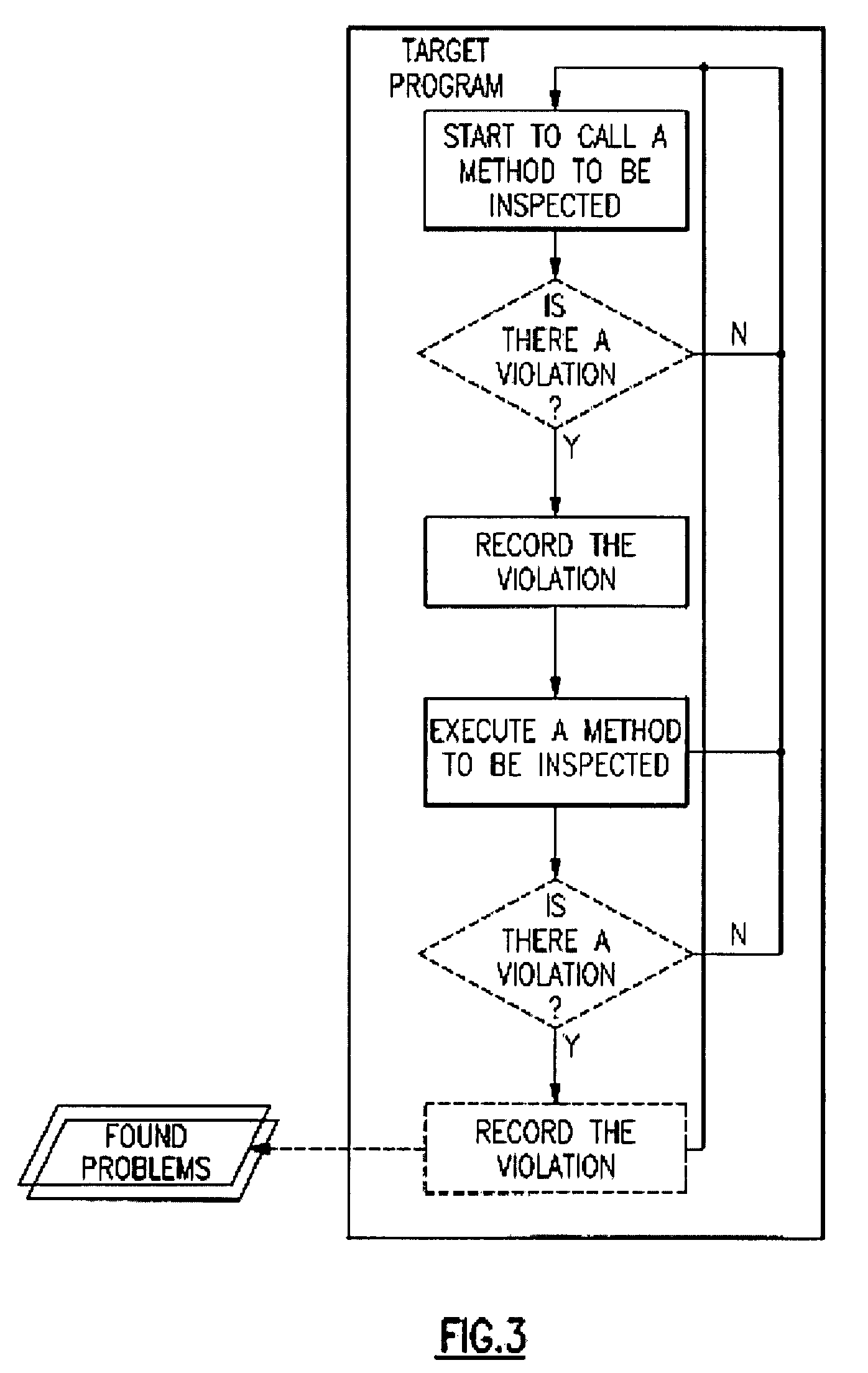
Automatically generating unit test cases which can reproduce runtime problems
InactiveUS8245194B2Improve efficiencyEnsure of regression testError detection/correctionSpecific program execution arrangementsRegression testingProgram testing
Owner:INT BUSINESS MASCH CORP
Video monitoring intelligent early-warning system and method on basis of target space relation constraint
ActiveCN103530995AEfficient detectionRapid positioningClosed circuit television systemsAlarmsVideo monitoringEarly warning system
The invention discloses a video monitoring intelligent early-warning system and a video monitoring intelligent early-warning method on the basis of target space relation constraint. The system comprises a video acquisition module, a target component intelligent analysis functional module, a video content visual analysis module, a general behavior rule sample database and an alarm module. On the basis of behavior comprehension on target components, aiming at spatial correlation between targets, the system carries out behavior characteristic analysis, evolution and classification, establishes a spatial correlation mode sample library, implements detection and identification on abnormal behaviors, can more effectively and accurately carry out identification and judgment on emergencies and can lock an abnormity trigger point to provide evidence for post-mordem forensics. The system introduces target space relation constraint, divides a video scene region to complete defining related concepts of the target components of a video, eliminates a certain fuzziness and faults in space semantic information, solves the problems of incompletion and inaccuracy in video content analysis and is more accurate and more efficient to detect abnormal events in a video monitoring range.
Owner:博拉网络股份有限公司
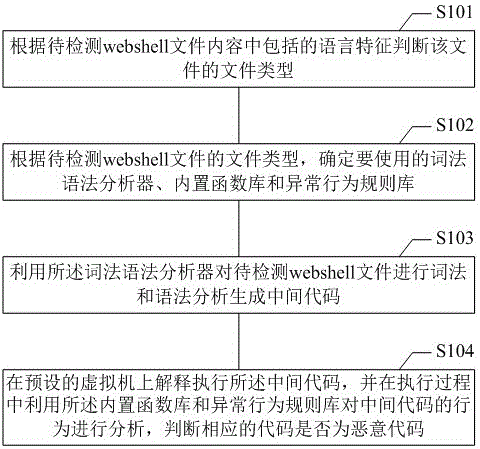
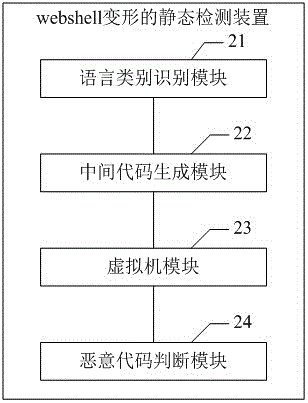
Static detection method and apparatus for webshell deformation
The application provides a static detection method and apparatus for webshell deformation. The method comprises: according to voice features contained in the content of a to-be-detected webshell file, judging the type of the file; according to the type of the file, determining a lexical and syntax analyzer, a built-in function library and an abnormal behavior rule library which are to be used; performing lexical and syntax analysis on the to-be-detected webshell file by utilizing the lexical and syntax analyzer to generate an intermediate code; and interpretively executing the intermediate code in a preset virtual machine, analyzing a behavior of the intermediate code by utilizing the built-in function library and the abnormal behavior rule library in the execution process, and judging whether a corresponding code is a malicious code. According to the scheme of the application, the problem that an existing hook mode possibly influences normal business can be avoided while the deformed webshell code is effectively identified.
Owner:XIAMEN MEIYA PICO INFORMATION
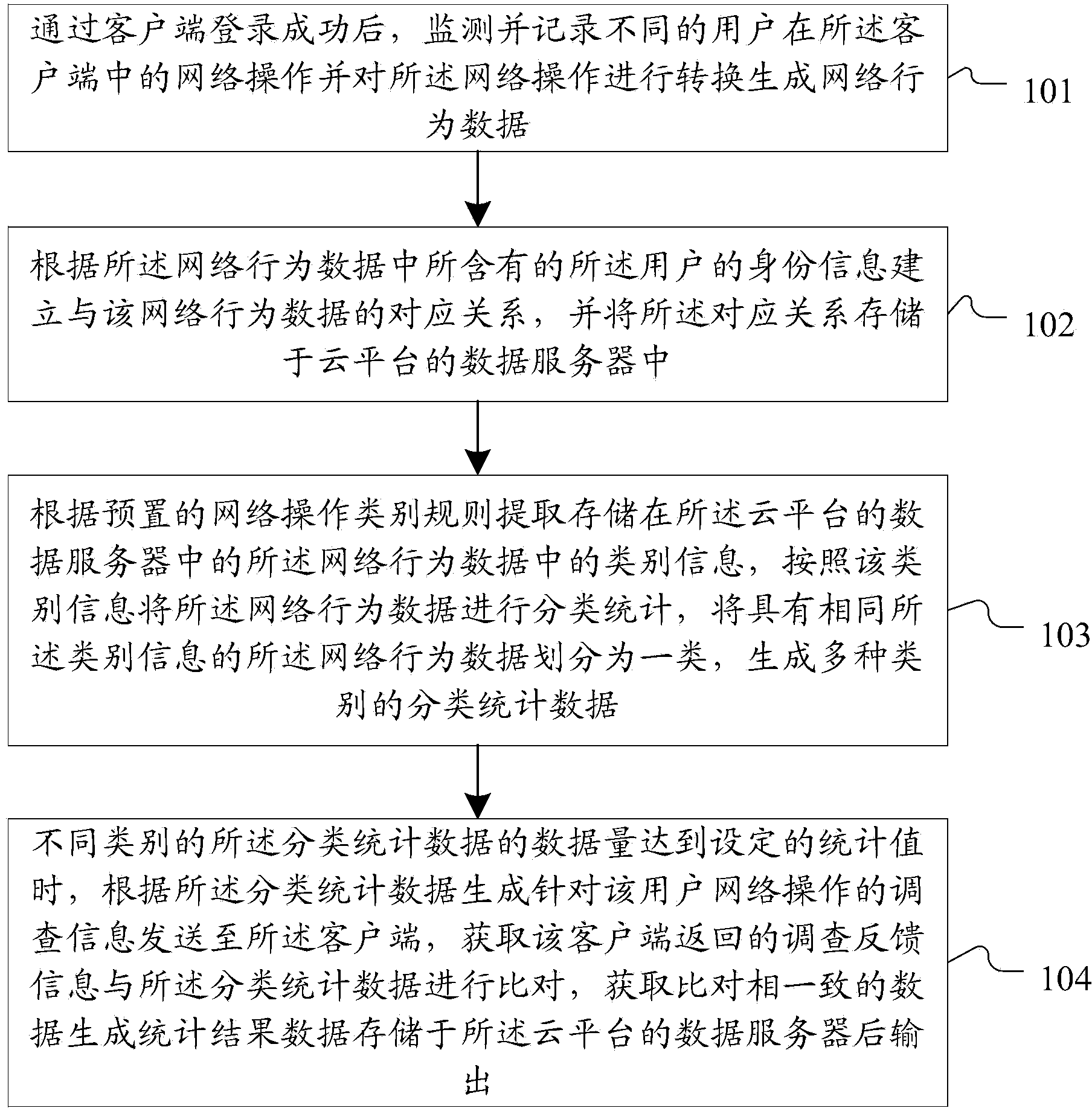
Method and system for analyzing behaviors of internet users based on cloud platform
InactiveCN103873583AAccurate collection and analysisAccurate collection, analysis and predictionData switching networksSpecial data processing applicationsNetwork behaviorInternet users
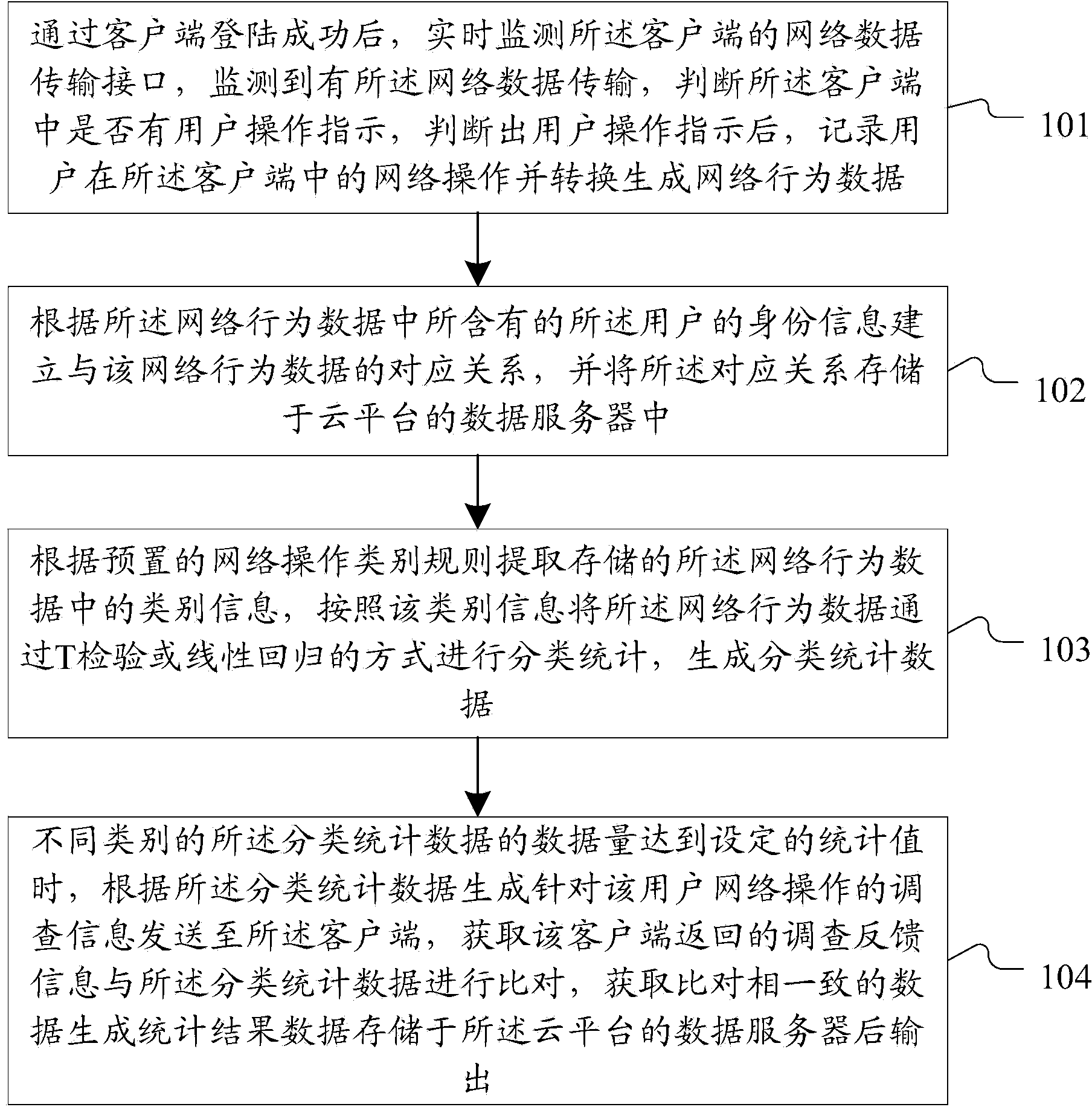
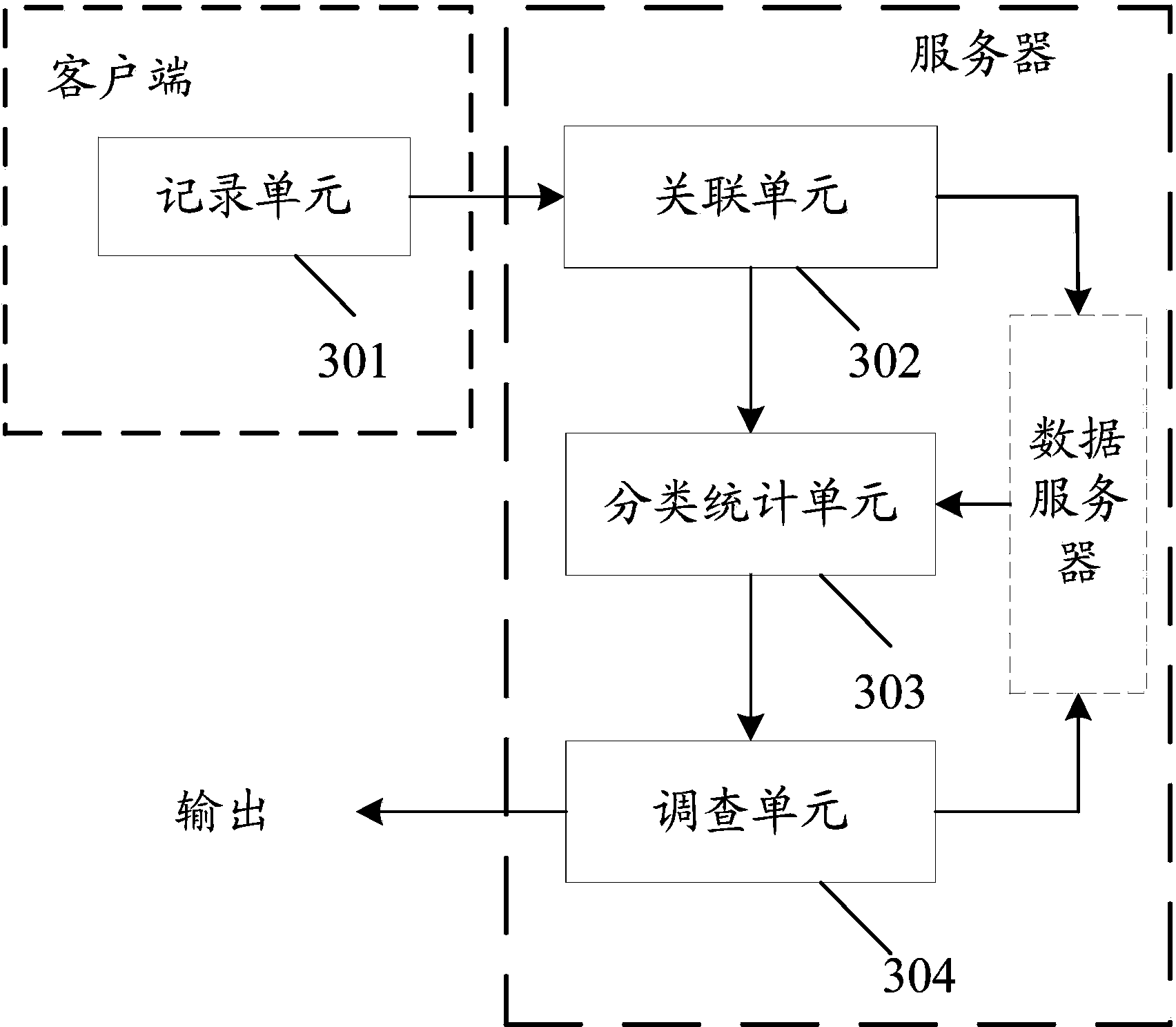
The invention discloses a method and system for analyzing behaviors of internet users based on a cloud platform. The method comprises the steps of monitoring and recording the network operation of different users in client sides to generate network behavior data, building a corresponding relationship with the network behavior data according to the identity information of the users contained in the network behavior data, extracting class information in the network behavior data, carrying out classification statistics on the network behavior data according to the class information, generating classification statistics data, generating survey information according to the classification statistics data when the quantity of the classification statistics data reaches a set statistics value, sending the survey information to the client sides, comparing survey feedback information fed back by the client sides and the classification statistics data, obtaining the consistent data after comparison, and generating and outputting the statistics result after the data are stored. The method and system for analyzing behaviors of internet users based on the cloud platform achieve effective statistics of the behavior data of the users in two types of internet, and accurately collect, analyze and predict the behavior rules of the users in the two types of internet.
Owner:BEIJING VIEWSTAP INFORMATION CONSULTATION
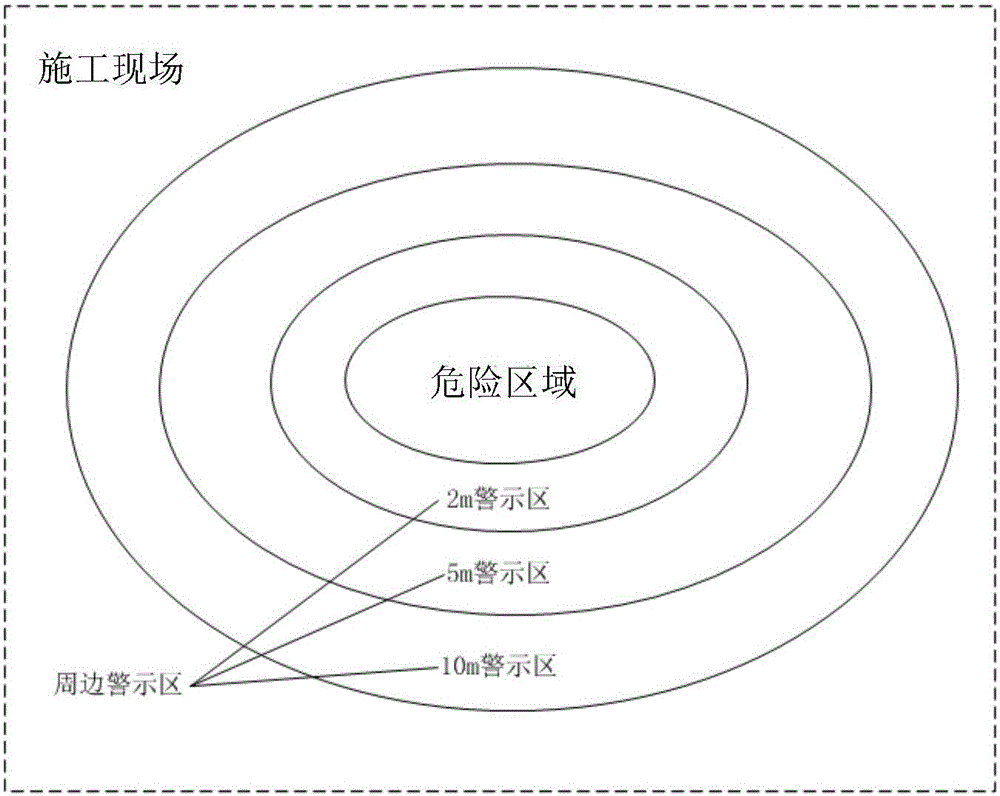
Construction safety behavior intelligent monitoring system based on video and monitoring method thereof
ActiveCN106412501ASimplify the security monitoring processEasy to superviseCharacter and pattern recognitionClosed circuit television systemsMonitoring systemDisplay device
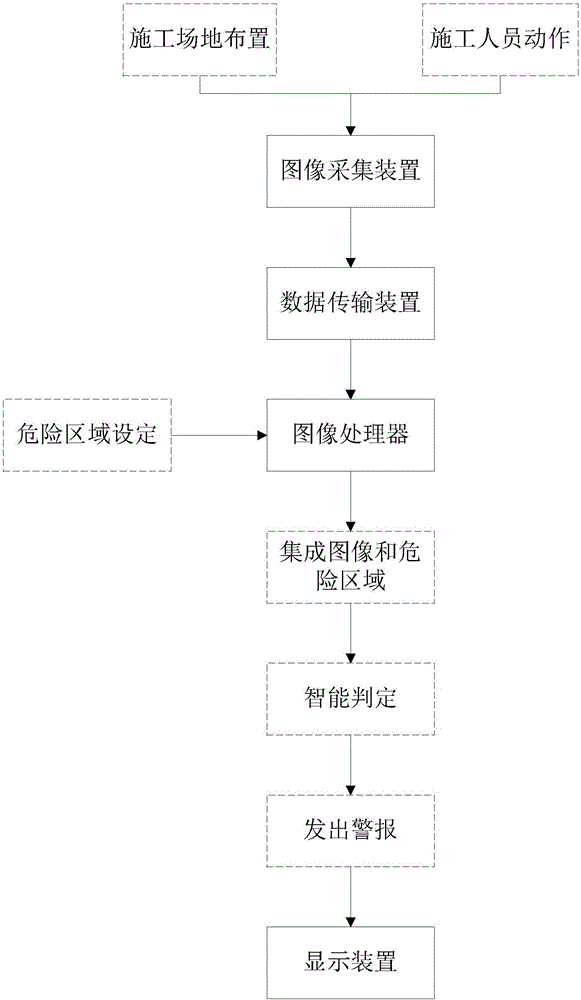
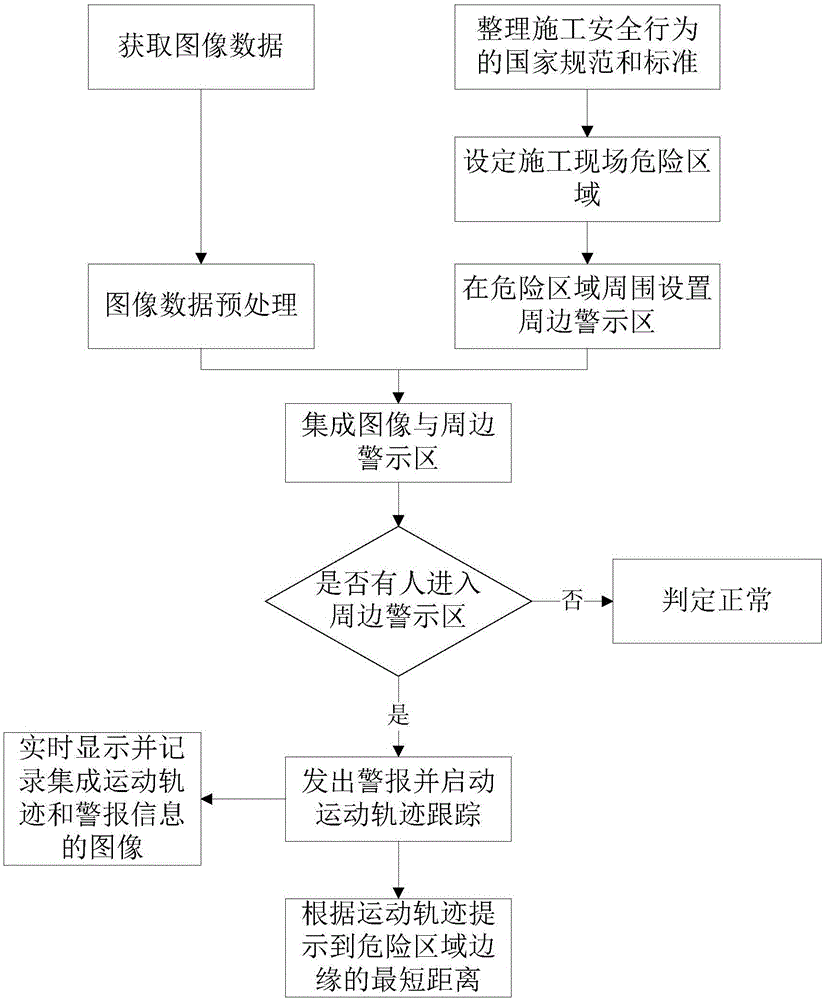
The invention discloses a worker safety behavior monitoring system based on video capture. The monitoring system comprises a video acquisition device, a data transmission device, a video processor and a display device. A monitoring method based on the system comprises the following steps that: the video acquisition device acquires daily working behaviors of workers on a construction site, and converts a video signal into a digital signal; the data transmission device transmits the digital signal to the video processor through the video acquisition device; the video processor is linked with a worker safety behavior rule, wherein the rule is established on the basis of relevant national specifications for construction behaviors; the video processor receives the acquired video after acquiring the video signal, runs a program to form a video in which a construction personnel behavior video and the worker safety behavior rule are overlapped, and inputs the video into display equipment; a dangerous area is set; and whether construction personnel behaviors meet specification requirements or not is judged intelligently according to an overlapped video provided by the display equipment, and an alarm is made.
Owner:HUAZHONG UNIV OF SCI & TECH
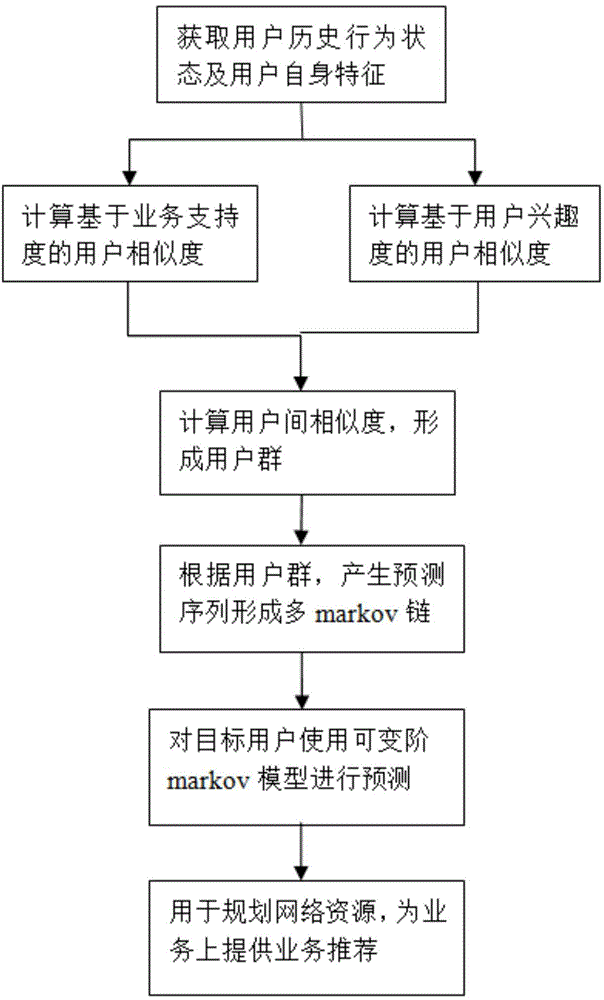
User similarity-based business behavior prediction method under ubiquitous network
The invention discloses a user similarity-based business behavior prediction method under a ubiquitous network. The objective of the invention is to realize effective mining and prediction of user behavior rules under a wireless ubiquitous environment. The method of the invention includes the followings steps that: an interest-based user behavior mining algorithm is researched, so that complete construction and cluster formation of user basic clusters can be realized; behavior rules of the user clusters are researched, and the behavior rules of the user clusters are combined so as to form behavior rules of user individuals; and a variable order Markov chain-based prediction model is researched, and complete mathematical descriptions of a whole theory model are constructed, and the solving of the model can be realized. With the user similarity-based business behavior prediction method under the ubiquitous network adopted, business states of user behaviors can be accurately predicted, and decision references can be provided for personalized customization of businesses, recommendation of optimal businesses and planning and construction of future networks, and the like.
Owner:NANJING UNIV OF POSTS & TELECOMM
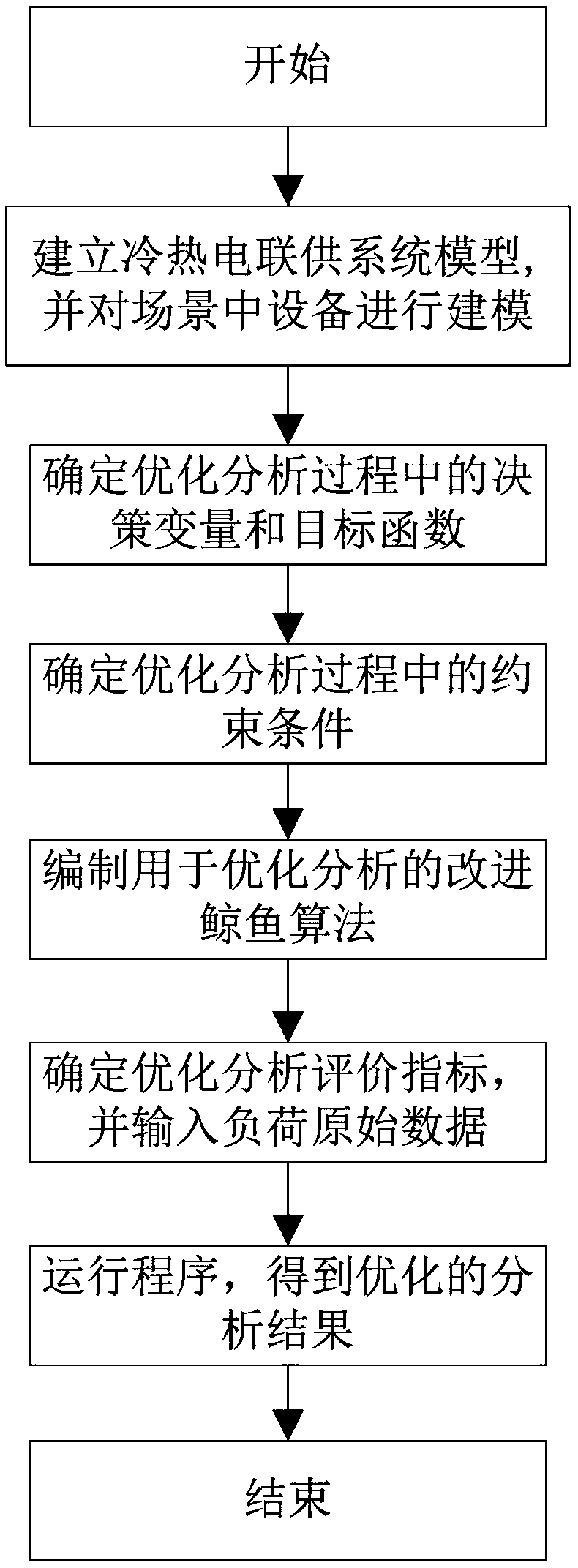
An optimization method of a combined cooling, heating and power system
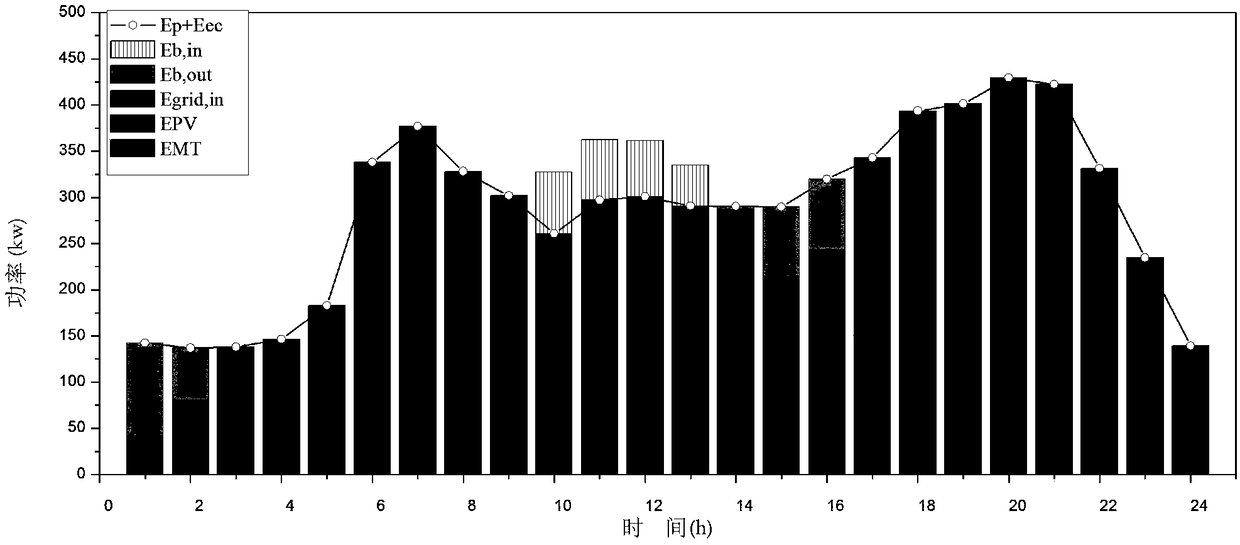
ActiveCN109165788ASmooth load fluctuation phenomenonIncrease flexibilityForecastingResourcesElectricitySystem of systems
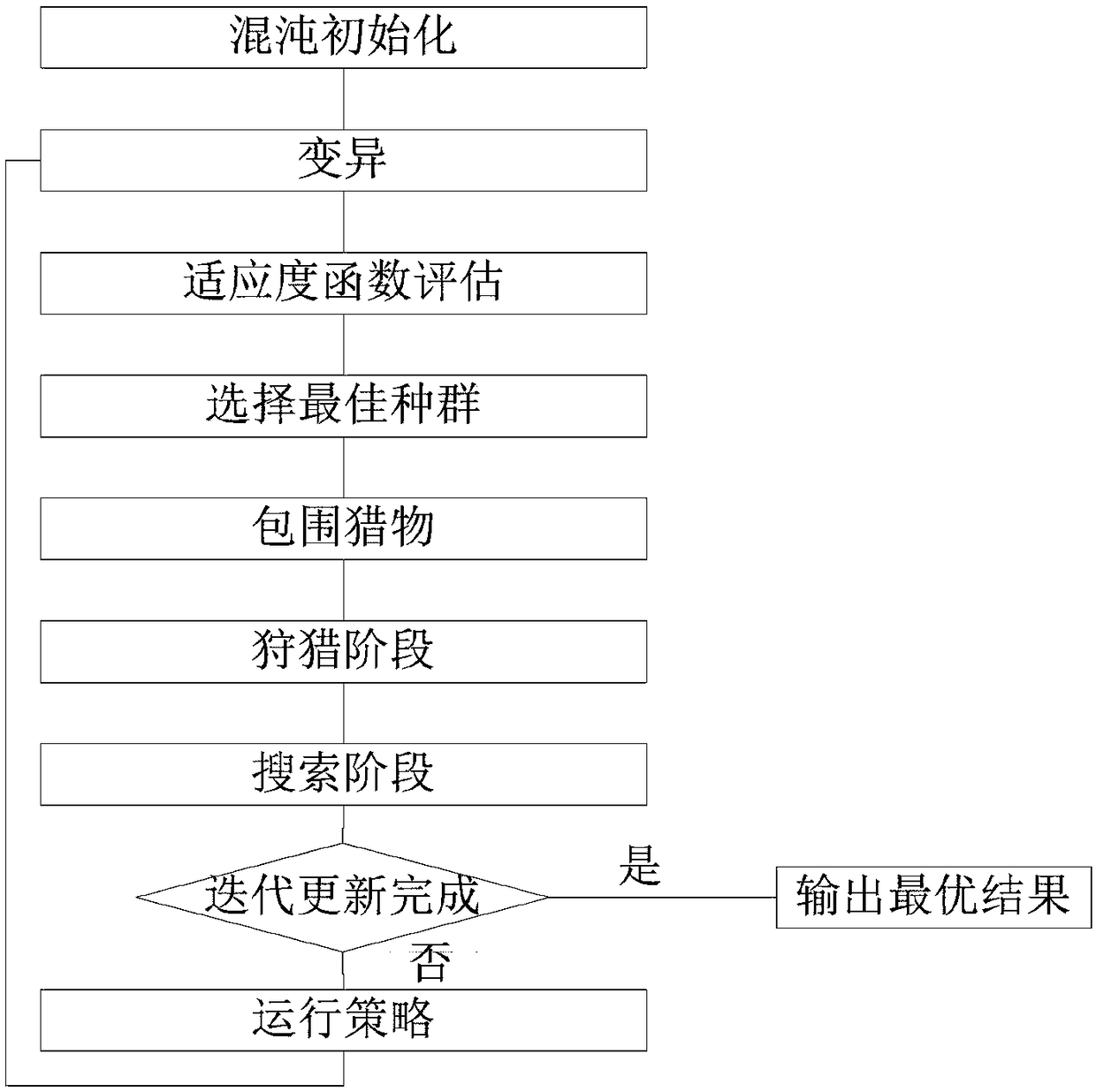
The invention relates to an optimization method of a combined cooling, heating and power supply system, the method comprising the following steps: establishing a model of the combined cooling, heatingand power supply system, selecting a combined cooling, heating and power supply type micro-network as an optimization object to carry out mathematical modeling on the equipment in the scene; determining the decision variables and objective functions of the optimization analysis of the combined cooling, heating and power system; determining the constraint conditions of the optimal operation of thecombined cooling, heating and power system; choosing a whale optimization algorithm and introducing chaotic cube mapping and mutation rules to optimize initial population and behavior rules; adoptinga hybrid heating and power supply strategy as the operation strategy of the combined cooling, heating and power supply system; determining and evaluating the optimized evaluation index. The method adopts the strategy of mixing heat and electricity and applies the improved whale algorithm to solve the combined cooling, heating and power micro-grid model. In the initial stage, the chaotic initialization operation improves the searching ability, and the mutation operation introduced in the trapping stage can find the global optimal value more quickly, thus realizing the purpose of quickly finding the optimal solution for the optimal operation of the combined cooling, heating and power system.
Owner:HEBEI UNIV OF TECH
Abnormity behavior detection method in combination with depth data and abnormity behavior system
ActiveCN105608479AHigh precisionTimely responseImage enhancementImage analysisBehavioral analyticsDomain analysis
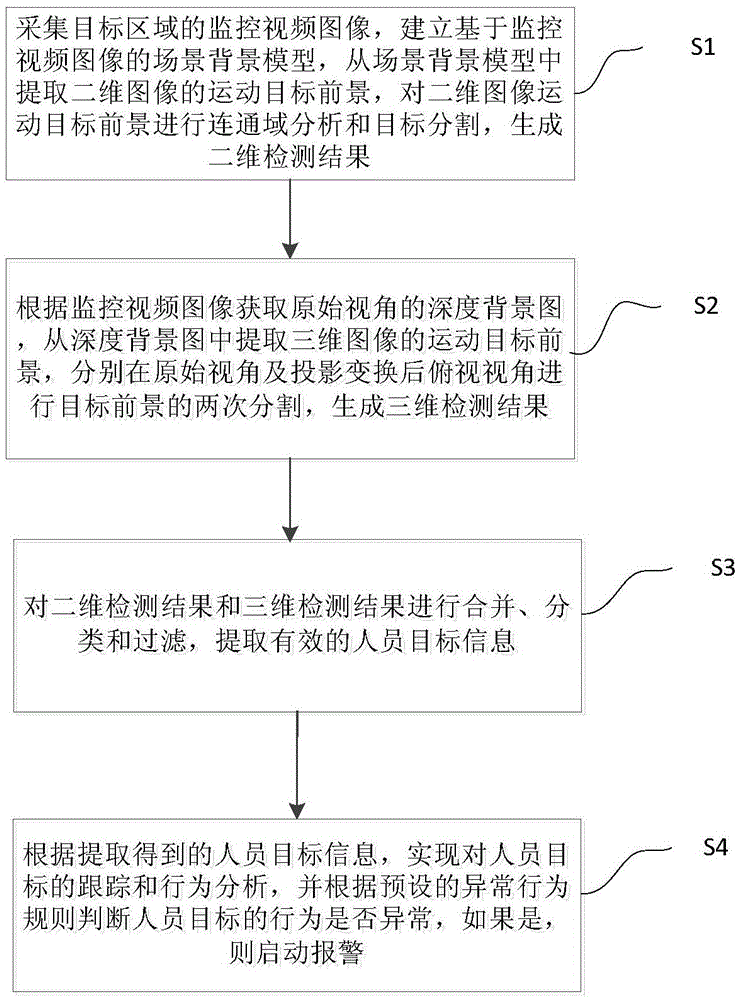
The invention provides an abnormity behavior detection method in combination with the depth data and an abnormity behavior system. The method comprises steps that a monitoring video image of a target area is acquired, a scene background model on the basis of the monitoring video image is established, the motion target prospect of a two-dimensional image is extracted, and communication domain analysis and target segmentation are carried out; a depth background graph of an original visual angle is acquired according to the monitoring video image, a motion target prospect of a three-dimensional image is extracted from the depth background graph, and two times of target prospect segmentation on the original visual angle and a downward-view visual angle after projection transformation is carried out; the effective person target information is extracted; according to the acquired person target information, tracking and behavior analysis on person targets are realized, whether behaviors of the person targets are abnormal can be determined according to preset abnormal behavior rules, if yes, alarm starts. Through the method and the system, abnormal events and abnormal behaviors are automatically identified, detection precision of the abnormal events is improved, and timely response can be realized on the unattended condition.
Owner:BEIJING ZHENGAN RONGHAN TECH
Group identification method based on personnel behavior rule and data mining method
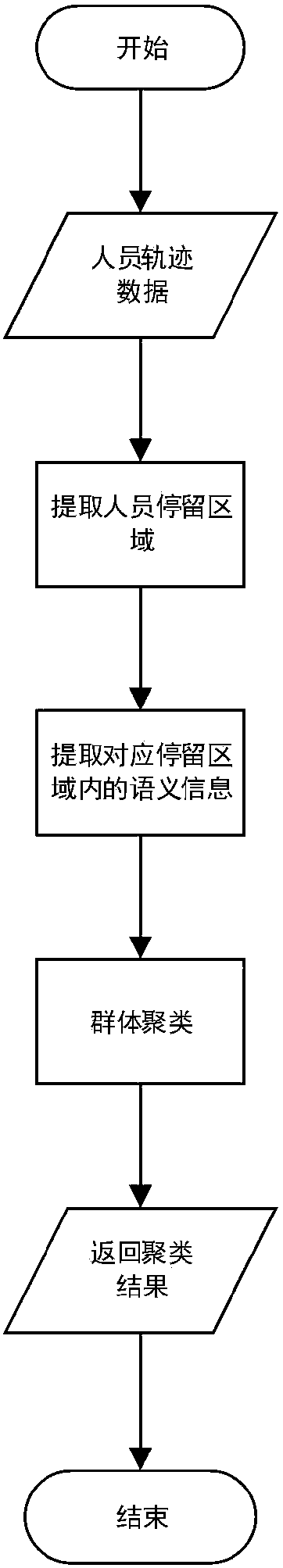
The invention discloses a group identification method based on a personnel behavior rule and a data mining method, belongs to the field of data mining, and particularly relates to a method for identifying key groups in large-scale activities based on the personnel behavior rule. Residence areas and the frequency of the personnel to go to the residence areas are extracted via trajectory data information of the personnel, then semantic information of the areas is further extracted to express user behaviors more accurately based on the extracted residence area information of the personnel, groupclustering is performed by using the data mining method and combining the personnel behavior rule with the feature similarity, and a special key group is identified from the target groups.
Owner:BEIJING UNIV OF TECH
Loop test device for imitating gas phase erosion corrosion of natural gas
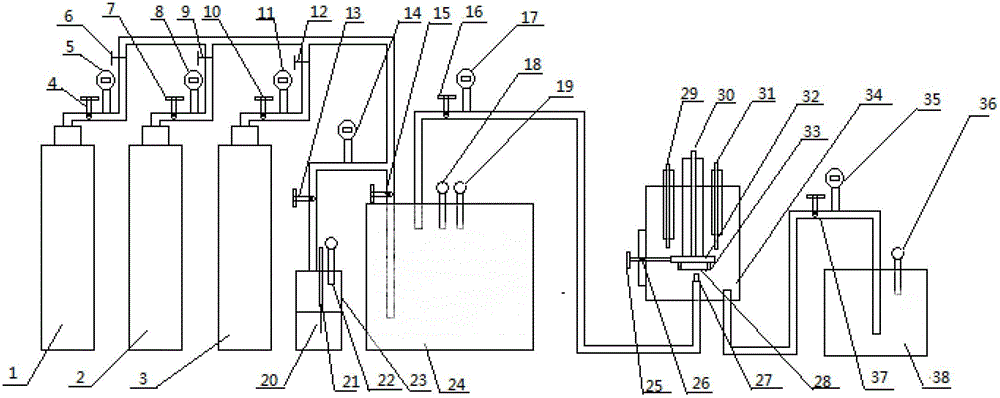
ActiveCN102980823ADeficiencies of changing flushing circuits with low flow ratesEasy to controlWeather/light/corrosion resistanceInvestigating abrasion/wear resistancePilot systemGas phase
The invention discloses a loop test device for imitating gas phase erosion corrosion of natural gas, and belongs to the technical field of imitating experiment devices. The loop test device for imitating gas phase erosion corrosion of natural gas is suitable for imitating conditions of medium components, humidity, flow speed and the like of natural gas gathering pipelines during the actual operation process, and is especially suitable for simulating the erosion corrosion situation caused by the flowing of gases containing trace moisture and corrosion media and having high-speed flowing in natural gas pipes, and testing electrochemistry and corrosion behaviors. The device is composed of three parts including a control system, a test system and a recovery system, wherein the control system comprises a high-pressure air bottle, a high-pressure kettle, a high-pressure flow meter, a regulating valve, a stop valve, an electric heater, a humidity probe, a pressure probe and pipelines; the test system comprises the high-pressure kettle, a three-electrode system, a rotary working bench, a test sample jig and a pressure probe; and the recovery system comprises a recovery tank, a regulating valve, a high-pressure flowmeter and a pressure probe. The device can well imitate the erosion corrosion situation of parts including pipe walls, elbows, tee joints and reducing parts by high-flow-speed wet gases under natural gas intra-pipe environment, can test electrochemistry signals, and has important significances for the research on erosion corrosion behavior rules under the natural gas intra-pipe environment as well as main influence factors of the erosion corrosion behavior rules.
Owner:UNIV OF SCI & TECH BEIJING
Full-flow model rule commercial bank personal loan overdue collection management system
InactiveCN106875272AEnsure safe recyclingSave time and costFinanceSpecial data processing applicationsBlood collectionStatistical Report
The invention discloses a full-flow model rule commercial bank personal loan overdue collection management system and belongs to the software development technology field. With the computing aid of an IT system, the repayment condition of each loan is identified through a loan risk control model; the system automatically judges the most reasonable way of loan collection and can effectively process overdue transactions through collection implementation, collection adjustment supervision, collection historical inquiry and collection statistical report standardization and intelligent management modules so as to push forward collection works according to different layers and with specific purposes, and therefore, the safe collection of credit funds can be ensured. With the full-flow model rule commercial bank personal loan overdue collection management system of the invention adopted, the production of a collection process model and the collection of customer activity data can be realized; and data are accumulated, and therefore, customer overdue behavior analysis can be performed, and customer overdue conduct rules and collection rules are updated.
Owner:SHANDONG INSPUR COMML SYST CO LTD
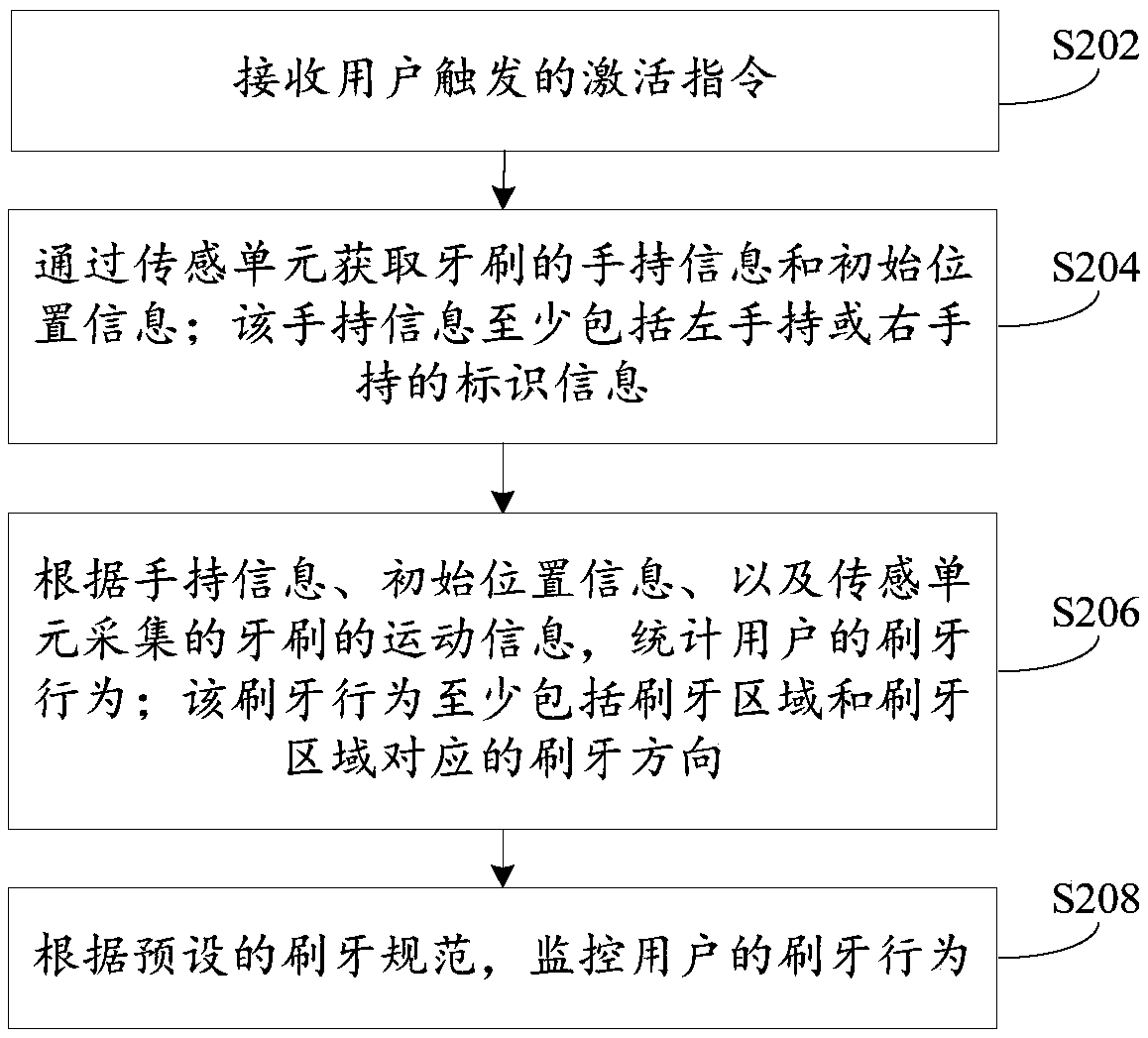
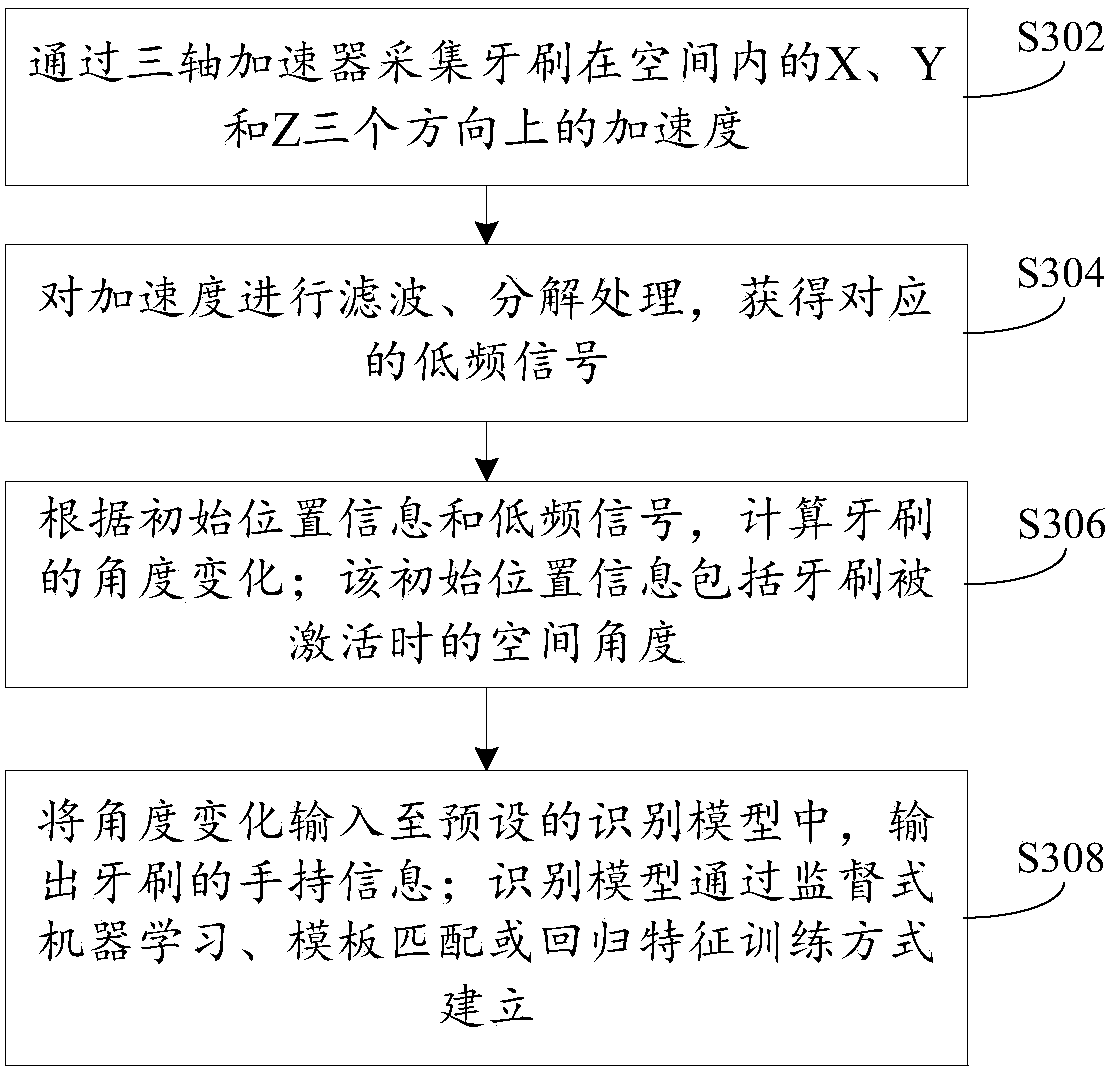
Monitoring method and device for tooth brushing behavior and intelligent toothbrush
InactiveCN107714227AContinuous and reliable trackingGood for healthTooth cleaningHand heldBiological activation
The invention provides a monitoring method and a device for a tooth brushing behavior and an intelligent toothbrush, wherein the method comprises the following steps: receiving an activation instruction triggered by a user; acquiring hand-holding information and initial position information of a toothbrush through a sensing unit, wherein the hand-holding information at least comprises left hand-holding or right hand-holding identification information; according to the hand-holding information, the initial position information, and toothbrush movement information collected by the sensing unit,counting the tooth brushing behavior of the user, wherein the tooth brushing behavior at least comprises a tooth brushing area and a tooth brushing direction corresponding to the tooth brushing area;and according to preset tooth brushing rules, monitoring the tooth brushing behavior of the user. The monitoring method and the device for the tooth brushing behavior and the intelligent toothbrush provided by the invention can reliably track the tooth brushing behavior of the user, timely prompt, guide and correct an incorrect tooth brushing behavior, effectively help the user gradually follow good brushing behavior rules, and improve the health degree of teeth.
Owner:北京朗萌科技发展有限公司
Heating energy-saving control method and device based on human body induction
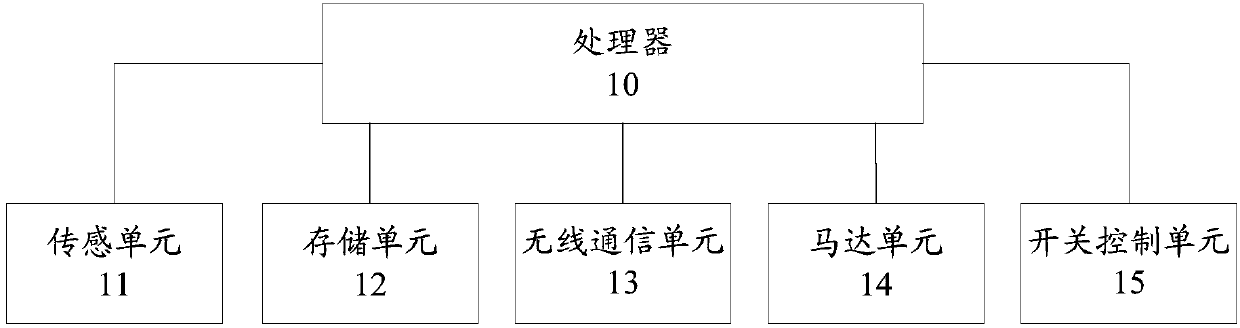
InactiveCN103982939AMeet heating needsControl supplyLighting and heating apparatusSpace heating and ventilation detailsEngineeringRadio frequency
The invention relates to a heating energy-saving control method and device based on human body induction. The heating energy-saving control device comprises an electrical adjusting valve and a human body induction intelligent control module. The human body induction intelligent control module comprises a data processing center, a human body induction probe, a temperature detection unit, a communication interface unit, a power unit, an output control circuit, an operation panel and an infrared communication module, wherein the human body induction probe, the temperature detection unit, the communication interface unit, the power unit, the output control circuit, the operation panel and the infrared communication module are connected with the data processing center. The output control circuit is connected with the electrical adjusting valve, the electrical adjusting valve is connected with a switch end of a radiator, and the operation panel is a radio frequency remote control terminal and is in real-time communication with the data processing center through an infrared wireless technology. According to the heating energy-saving control method and device based on human body induction, the behavior rule of people can be counted, the heating demands of people at different moments can be analyzed, and accordingly a domestic heating system can be controlled.
Owner:WUHAN UNIV OF TECH
Method and device for data rasterization and method and device for user behavior analysis
ActiveCN104598557AImprove data processing efficiencyReduce occupancySpecial data processing applicationsBehavioral analyticsBehavior rule
The embodiment of the invention discloses a method and a device for data rasterization and a method and a device for user behavior analysis. The method for the data rasterization comprises the following steps of acquiring corresponding user associated data according to user behavior data produced in a target time period and located in a target area; computing a two-dimension number corresponding to the user associated data according to position information in the user associated data; acquiring a corresponding two-dimension index number from a two-dimension index number set by taking the two-dimension number as a query condition; associating a raster mark with the user associated data so as to obtain corresponding raster data. The efficiency of the data rasterization is increased, and user behavior rule or preference analysis based on mass of diversified real-time raster data is realized.
Owner:TIANJIN BAOGU INFORMATION TECH CO LTD
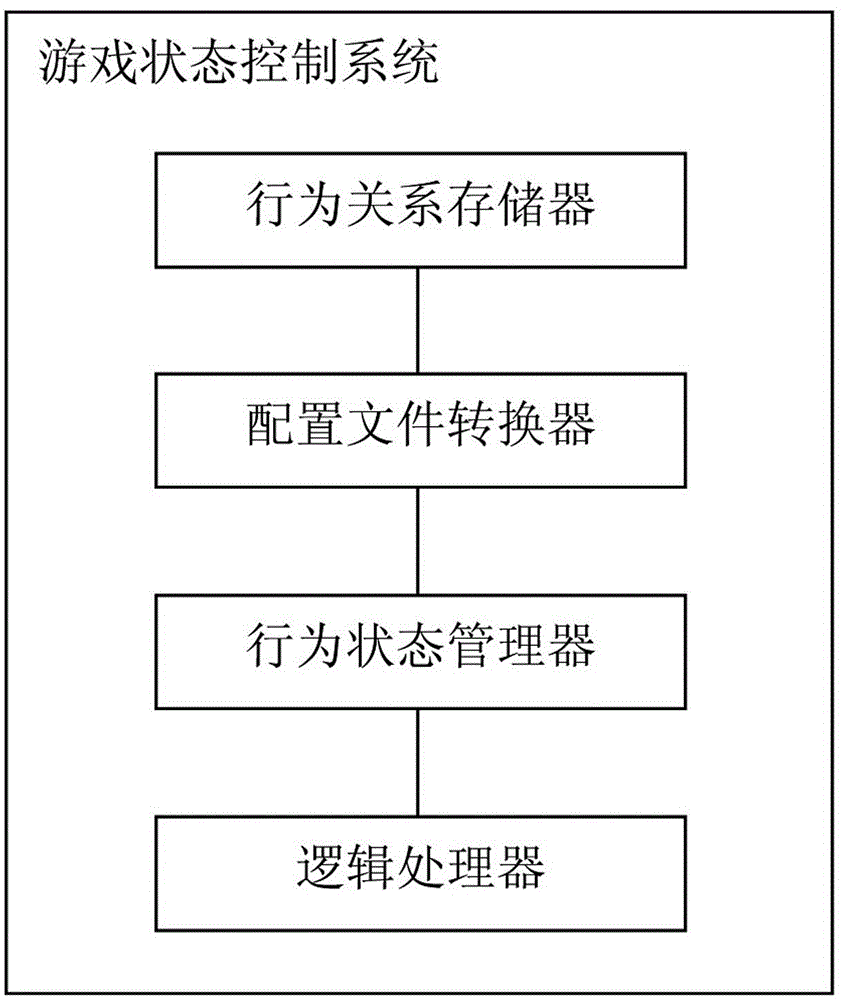
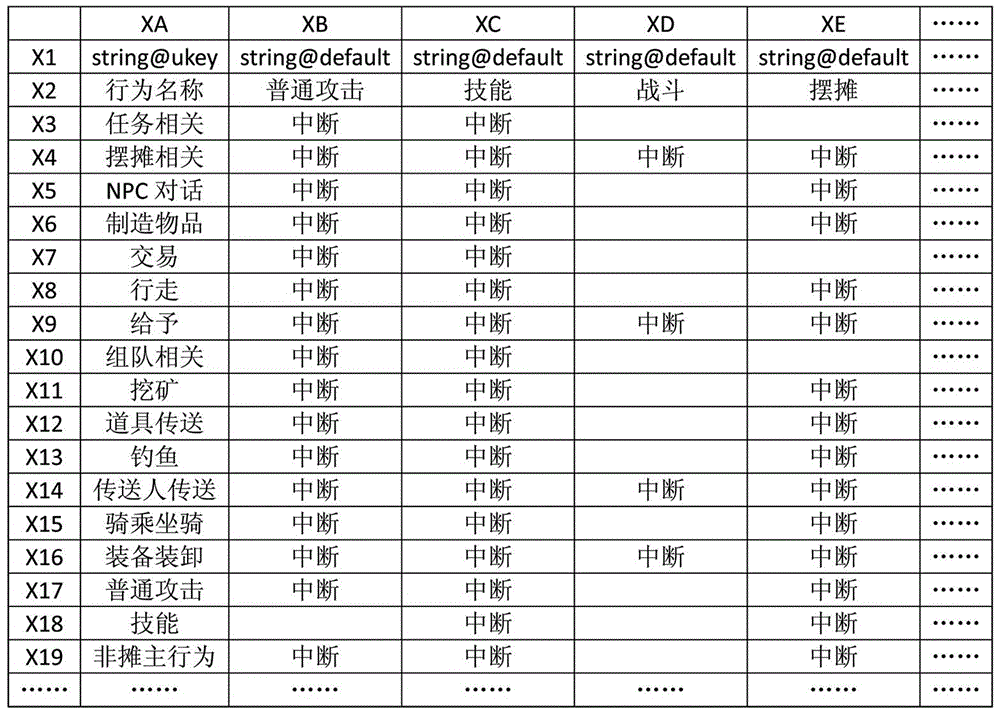
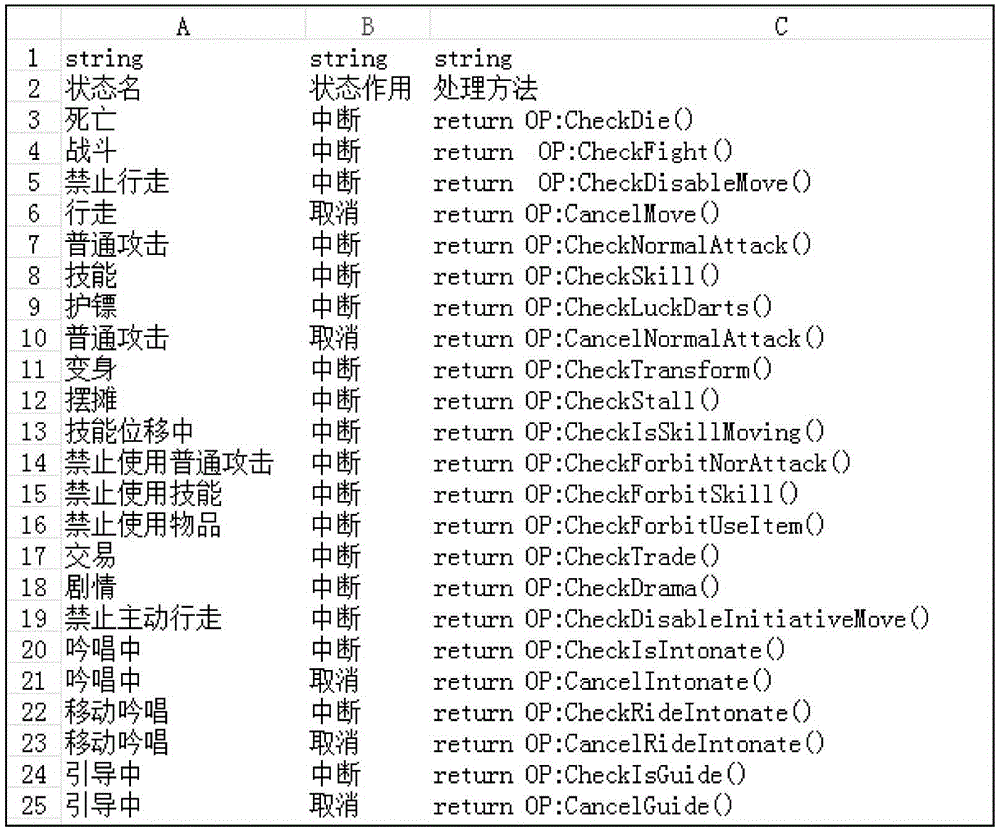
Universal game state control system and method
ActiveCN104383684AImprove development efficiencyFlexible behavior controlVideo gamesSoftware bugControl system
The invention discloses a universal game state control system and method. The system comprises a behavior relation storer, a configuration file converter, a behavior state manager and a logic processor. The method includes that game behavior rules that can be edited in a user-defined mode and predefined behavior state test function fields are stored and then converted into configuration files that can be directly loaded by a Lua script engine of a game program, the Lua script engine of the game program is called to analyze configuration files that are output by the configuration file converter, game behaviors, behavior state functions and behavior state test function ports that are already configured are recognized and managed, a logical relationship between to-be-tested behaviors and about-to-happen behaviors is determined, and a behavioral control command is output. The universal game state control system and method has the advantages that a behavior description table is merely required to be modified and then a game is restarted so that newly modified game behaviors and logics can directly come into effect, thereby, the game developing efficiency is greatly increased, and the conditions of program errors caused by human code modification can be reduced.
Owner:珠海西山居互动娱乐科技有限公司 +1
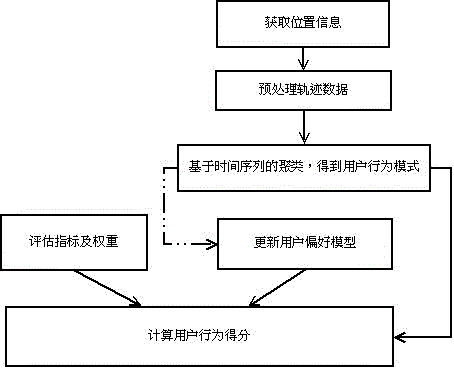
Method for evaluating user behavior on the basis of position mining
InactiveCN105678457AReduce deployment overheadAccurate Response Behavior RulesOffice automationResourcesTime distributionData mining
The invention discloses a method for evaluating user behavior on the basis of position mining. The method comprises following steps: a. obtaining position information to obtain tracking data and performing pretreatment to the tracking data; b. obtaining time distribution of a user at different places in different time through the tracking data to obtain a behavior pattern of the user; c. updating a user preference model by use of historical records of the user behavior pattern and determining whether a user behavior is an abnormal behavior according to the user preference model and calculating user behavior scores. By use of the method, the user behavior pattern is obtained from user original messy tracking data, daily behavior rules of the user can be revealed, and the possibility of cheat in traditional attendance checking is greatly reduced.
Owner:成都小步创想慧联科技有限公司
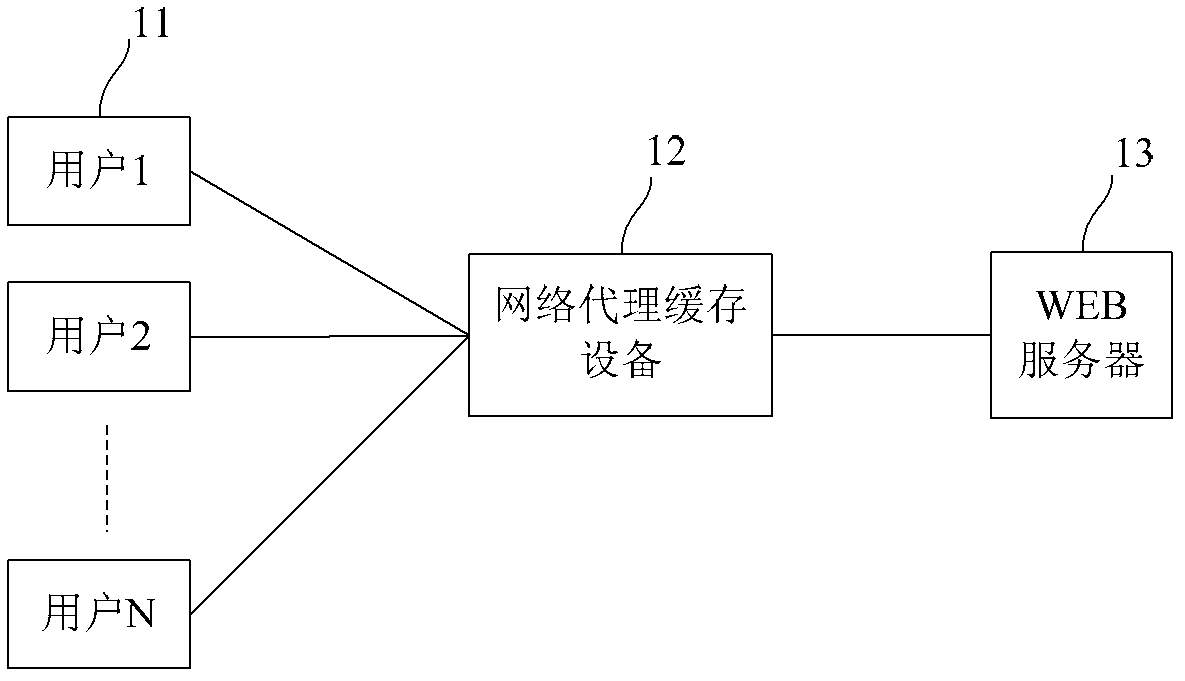
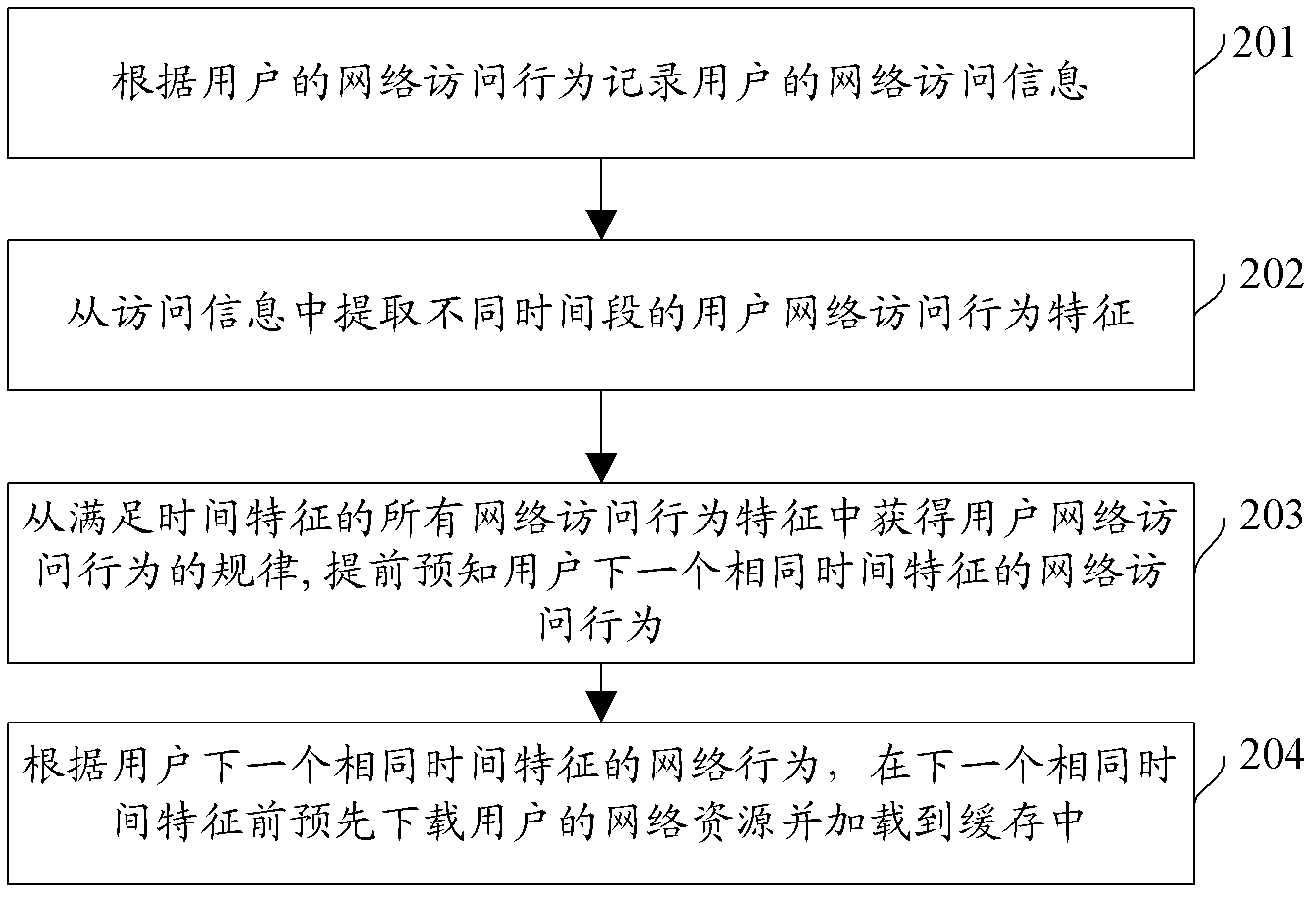
Network resource pre-fetching and cache accelerating method and device thereof
InactiveCN103139278AImprove Internet experienceRespond quickly to network access requestsTransmissionNetwork behaviorDistributed computing
The invention discloses a network resource pre-fetching and cache accelerating method and a device of the network resource pre-fetching and cache accelerating method. The network resource pre-fetching and cache accelerating method includes the following steps. According to network accessing behavior of a user, network accessing information of the user is recorded. Characteristics of network accessing behavior of the user in different periods are fetched from the accessing information. Network accessing behavior rules of the user can be obtained from all characteristics of the network accessing behavior, wherein the characteristics of the network accessing behavior can meet time characteristics. Thus, the network accessing behavior of the next identical time characteristic of the user can be predicted in advance. Based on the network behavior of the next identical time characteristic of the user, network resources of the user are downloaded and loaded into a cache before the next identical time characteristic. The network resource pre-fetching and cache accelerating method and the device of the network resource pre-fetching and cache accelerating method can improve network surfing experience of the user, reduce pressure from concurrent requests of a peak in network accessing, save the width of a band and fully use resources of a system.
Owner:BEIJINGNETENTSEC
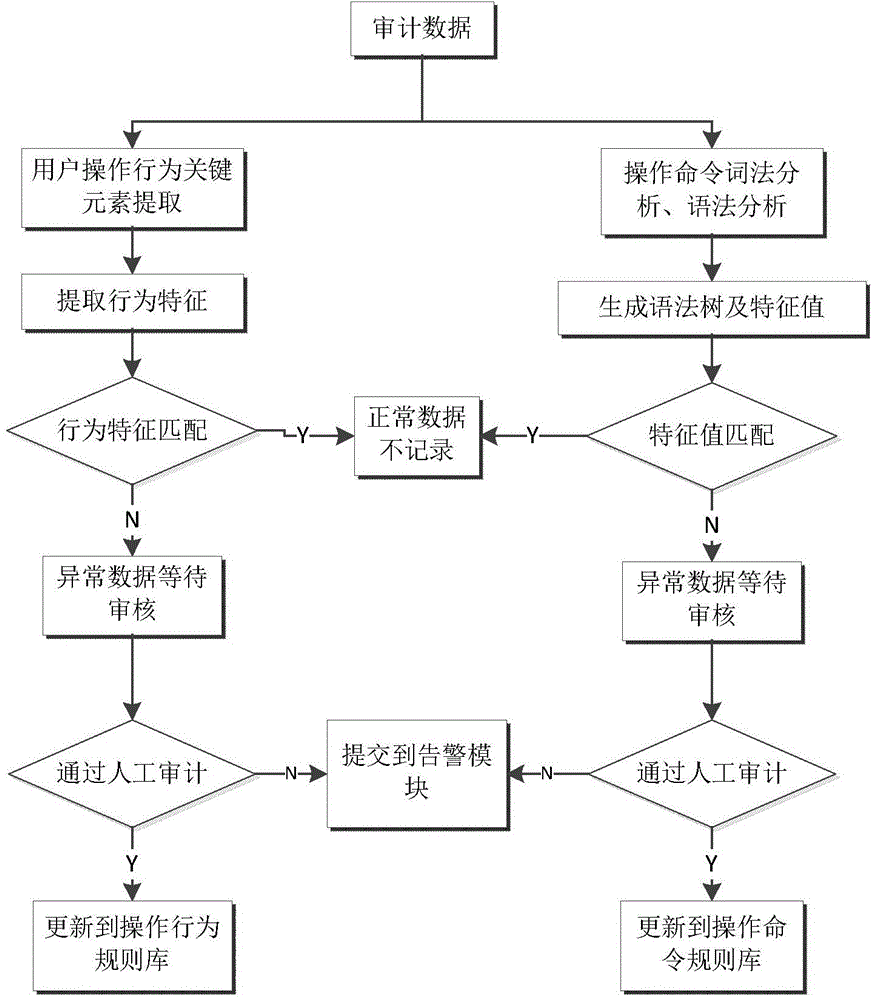
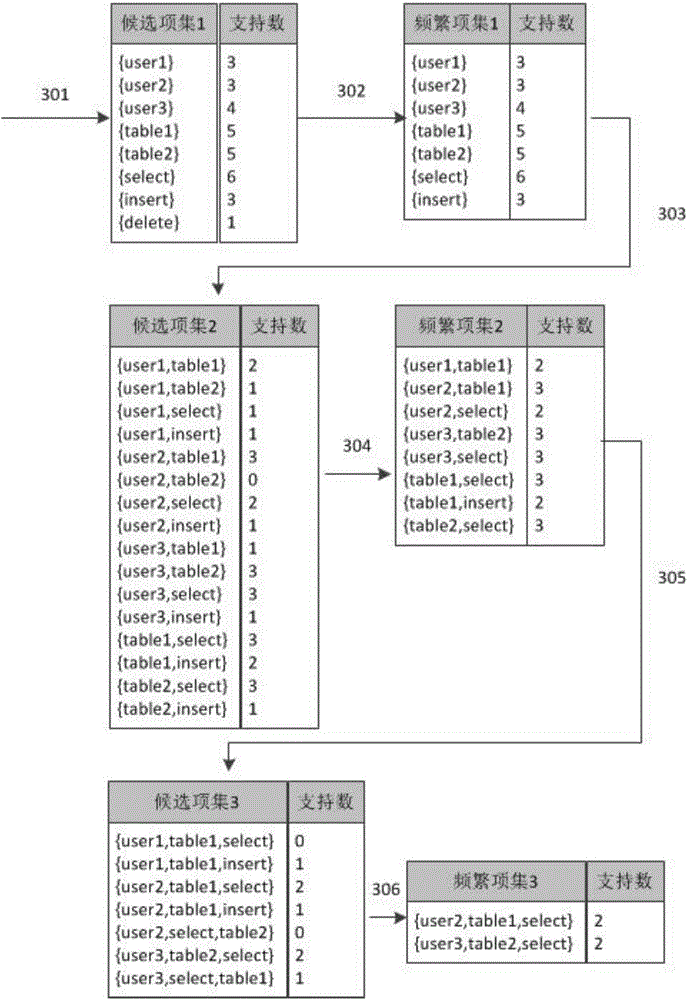
Method for remote intelligent operation and maintenance audit
InactiveCN104156439AEasy to detectMeet security needsData processing applicationsError detection/correctionBehavioral analyticsMatch rule
The invention discloses a method for a remote intelligent operation and maintenance audit. An access gateway is built between a client and a server, operation and maintenance conducted by the client on the server are forwarded by the access gateway to be conducted, and the access gateway collects operation and maintenance data and audits the operation and maintenance data. The method comprises a learning stage and a detecting stage, wherein an operating command rule base and an operating behavior rule base are formed through character command analysis and user behavior analysis in the learning stage; in the detecting stage, whether operation and maintenance operating commands and operating behaviors are normal or not is audited through a matching rule base, and the rule bases can be updated. Compared with the prior art, the method is high in universality and detecting efficiency, detecting can be conducted only after the learning stage lasting for a period of time, maintenance is convenient, and continuous updating of the rule bases guarantees that the false detecting rate is reduced.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
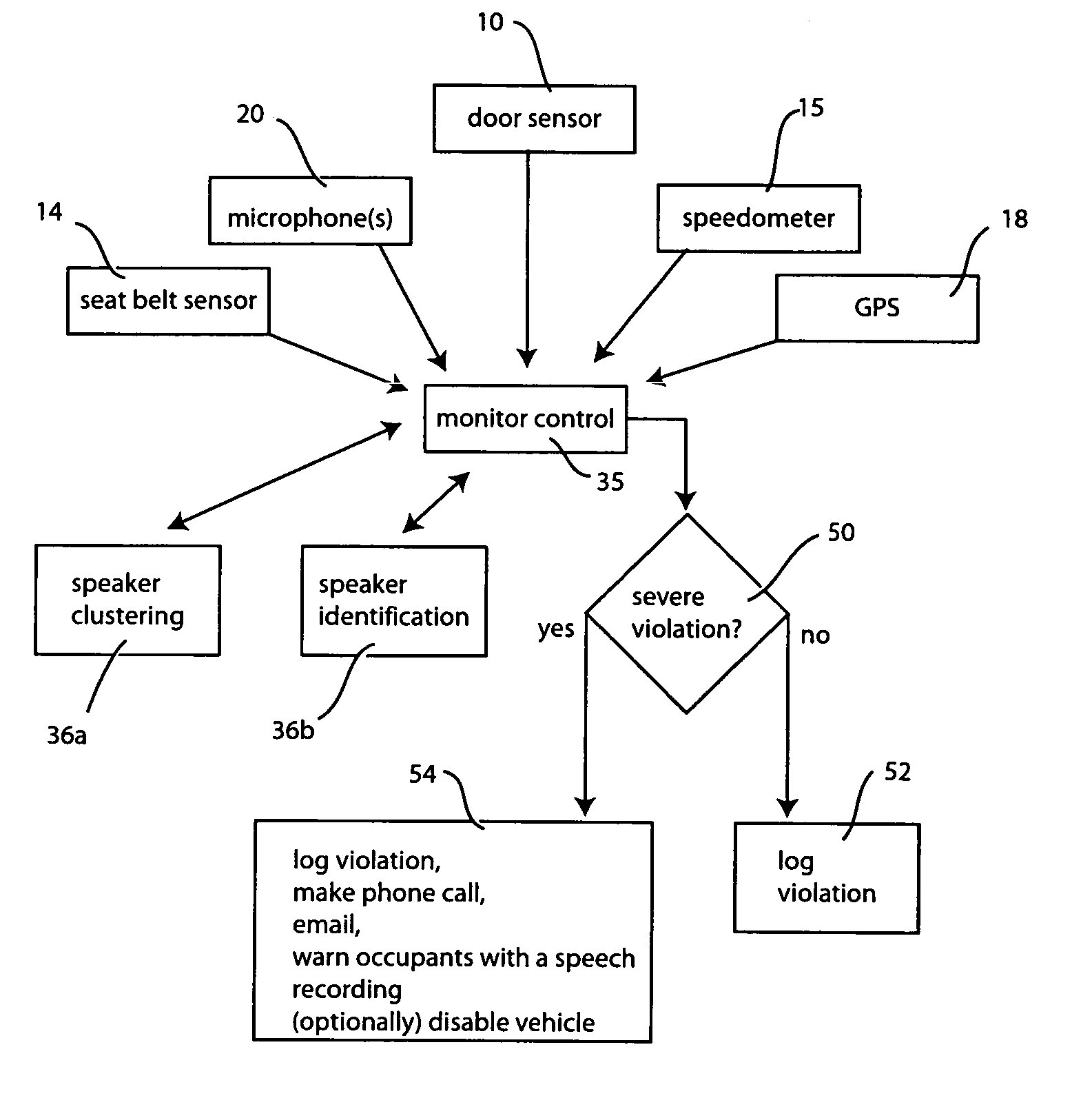
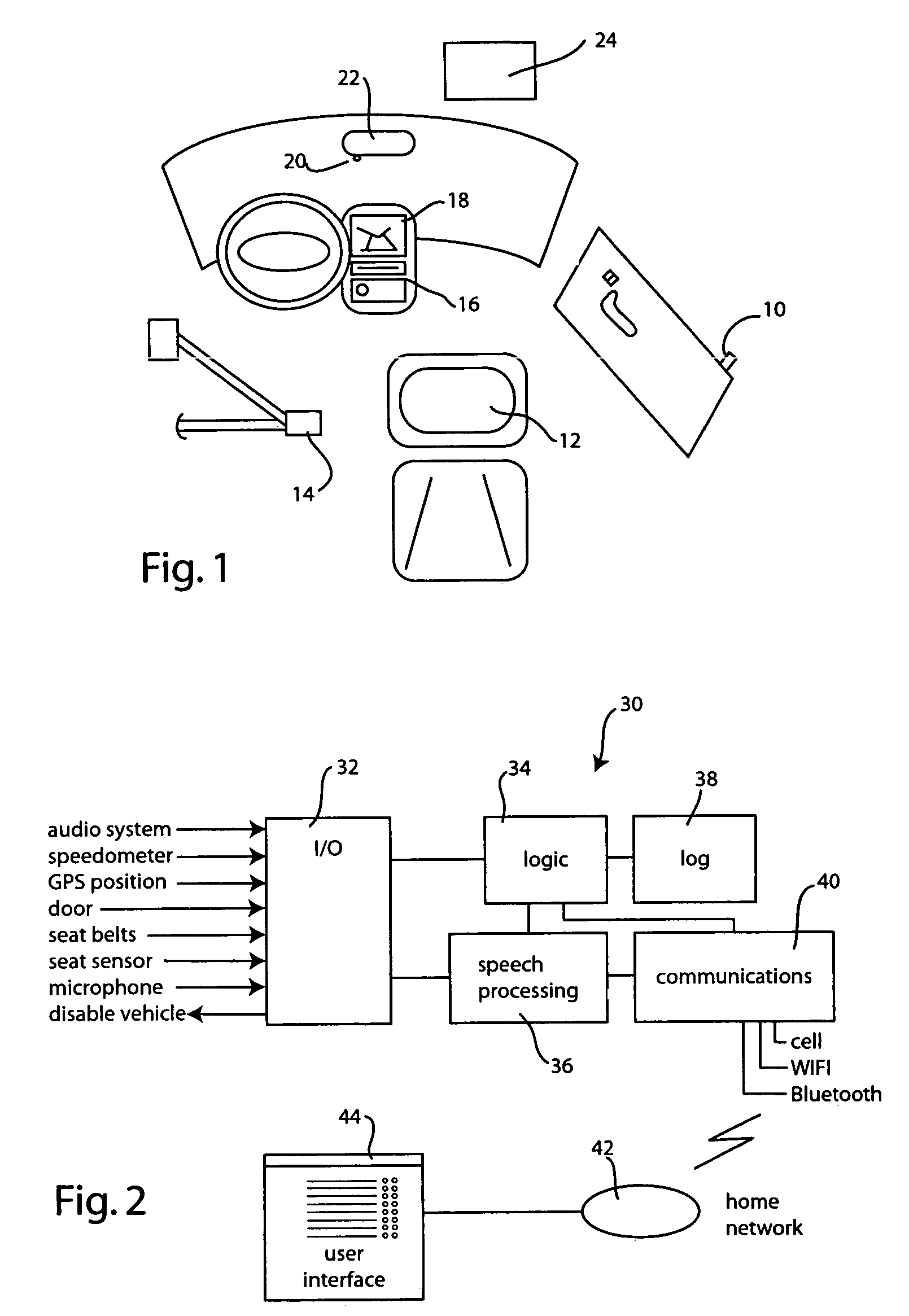
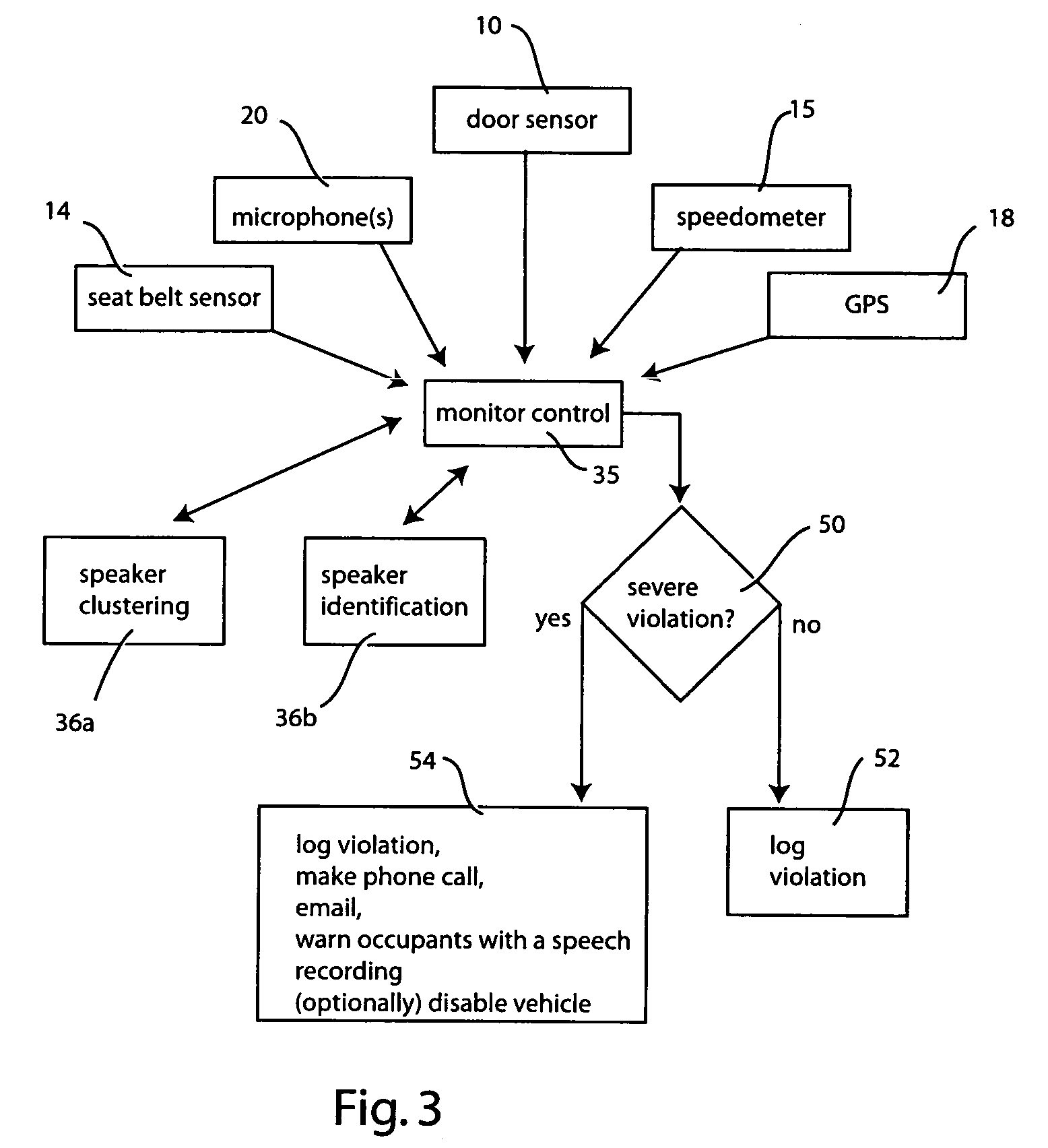
Enhanced automotive monitoring system using sound
The vehicular monitoring system obtains audio information from the speech of occupants within the vehicle and then processes that audio information to extract information about the behavior of the vehicle occupants. Using the behavioral information the system then assesses whether said behavior is in compliance with a predefined set of rules. Severe violations are reported to a third party via cellular telephone or other means. Less severe violations are recorded in a log file that is subsequently uploaded to a networked computer system for review and analysis. The behavioral rules used to assess violations may be modified by the administrative user.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
Methods and apparatus for controlling the transmission and receipt of email messages
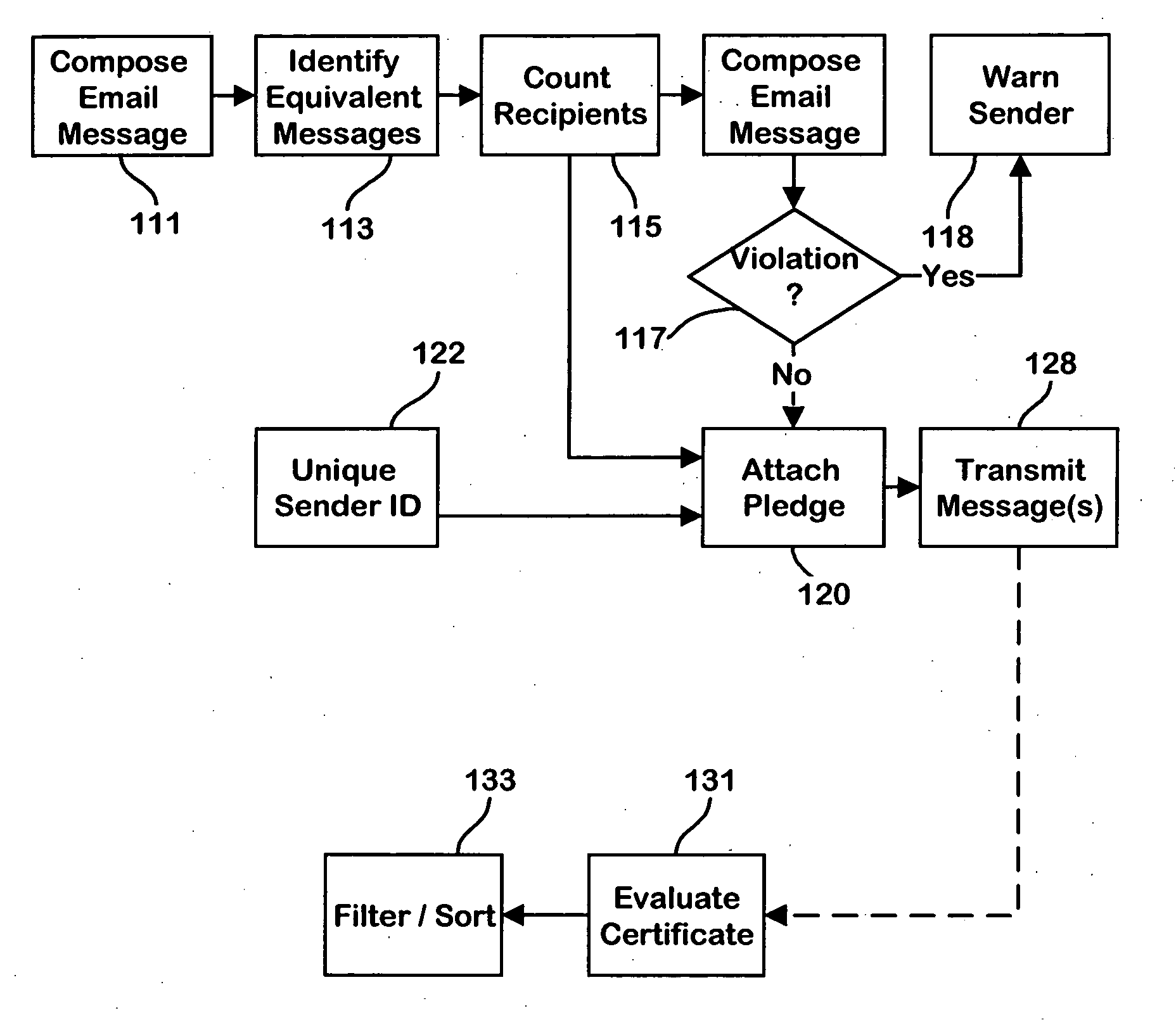
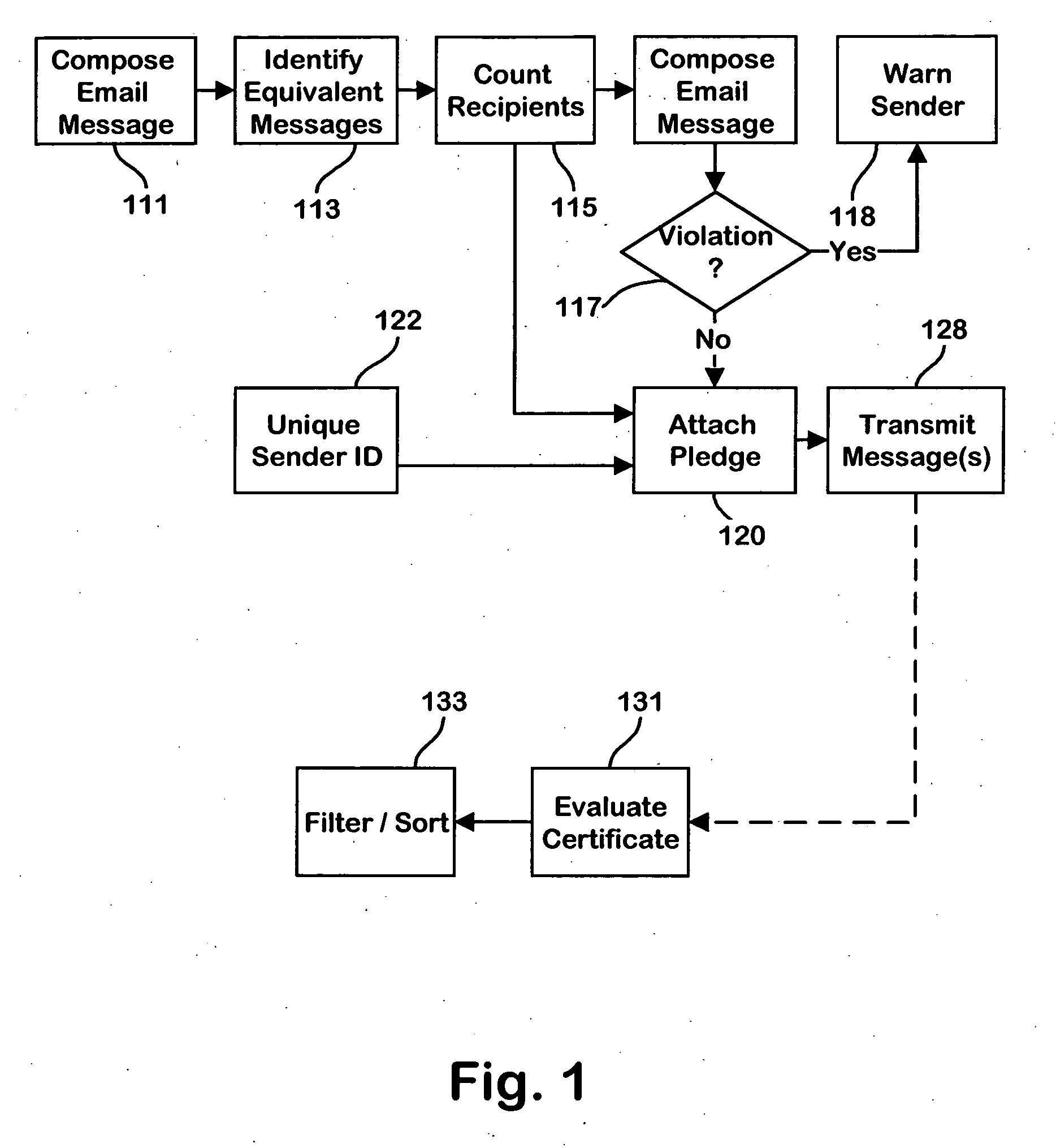
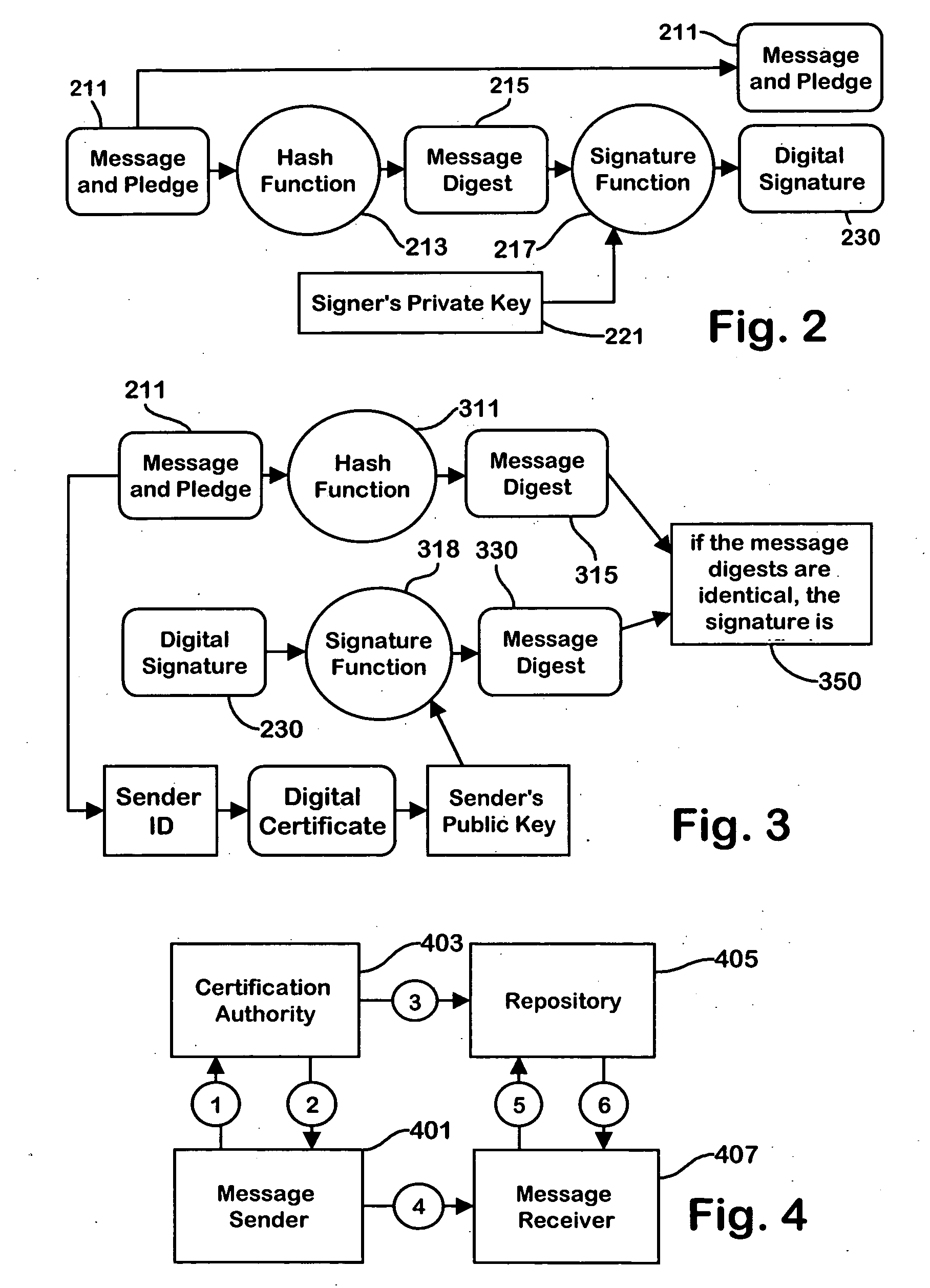
InactiveUS20080256072A1Reduce the burden onUser identity/authority verificationMultiple digital computer combinationsInternet privacyDigital signature
Methods and apparatus for identifying unwanted email messages by transmitting metadata with an outbound email message that indicates the total number of email messages sent by that sender in a predetermined time period, or alternatively indicates the total number of email messages which are equivalent to the outgoing message that have been sent. In addition the metadata may include an identification of the sender and a “pledge” made by the sender. A pledge may take the form of a binding commitment from the sender that the information contained in the metadata is accurate, and / or that the sender promises to abide by predetermined good conduct rules designed to limit unwanted email. The outgoing message may be further signed by the sender with a digital signature that provides means for verifying the content of the message and the pledge as well as the identity of the sender
Owner:TRUEMAIL TECH
City comprehensive emergency intelligent simulation system based on case-based reasoning and operation method thereof
InactiveCN103679611ASolve intelligent generationSolve the problem of dynamic evolutionData processing applicationsInference methodsSimulation basedAction rule
The invention relates to the technical field of comprehensive emergency management, in particular to a city comprehensive emergency intelligent simulation system based on case-based reasoning and an operation method of the city comprehensive emergency intelligent simulation system. According to the method, with structured event information as conditions, a case base is searched for similar cases, effective reasoning is carried out based on action rules of all participating entities according to a model, and scenes in the cases are modified to form new simulation exercise scenes to be used by participating units for participation. When city comprehensive emergency simulation exercises are finished, by carrying out evaluation, modification and summarization on the simulation exercises and saving the cases as new cases finally, self-increasing of the case base and self-learning capacity of a simulation exercise system are achieved, and solid foundations are laid for further simulation exercise scene generation. The method solves the problem that simulation exercise scenes are lack of scene exercise analog simulation based on behavior rules of all current participating entities, and can be applied to the city comprehensive emergency intelligent simulation system.
Owner:CLOUD COMPUTING CENT CHINESE ACADEMY OF SCI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com