Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
59results about How to "Strengthen copyright protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Picture processing method and picture processing device
InactiveCN104462873AEasily identifiableStrengthen copyright protectionCharacter and pattern recognitionProgram/content distribution protectionComputer graphics (images)Algorithm
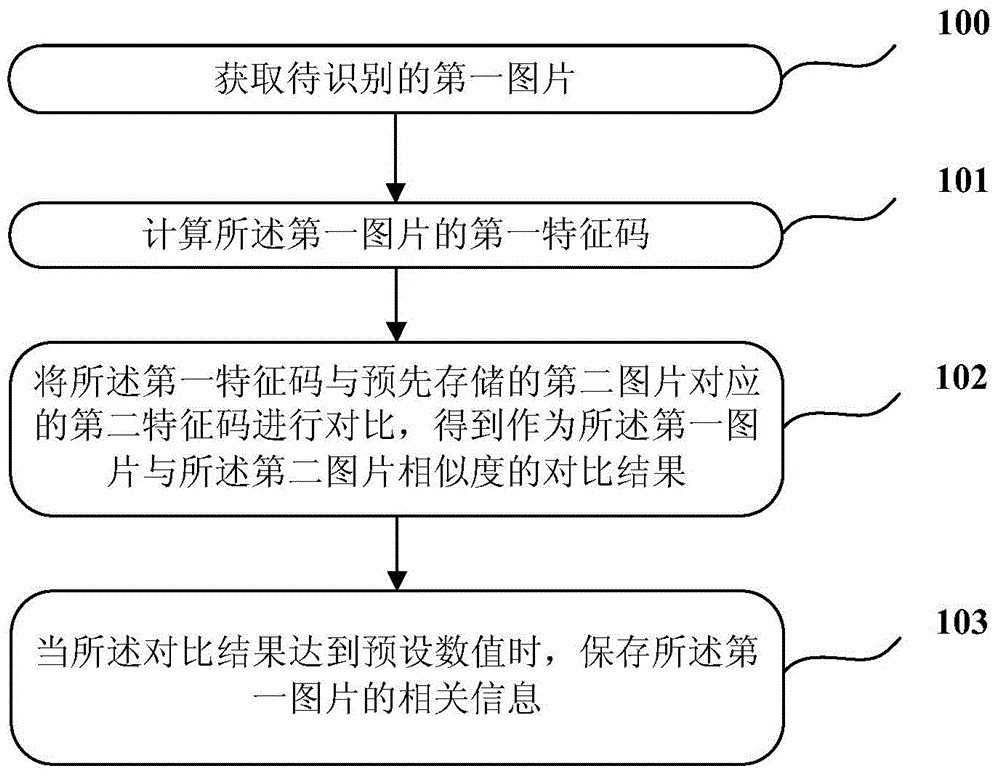
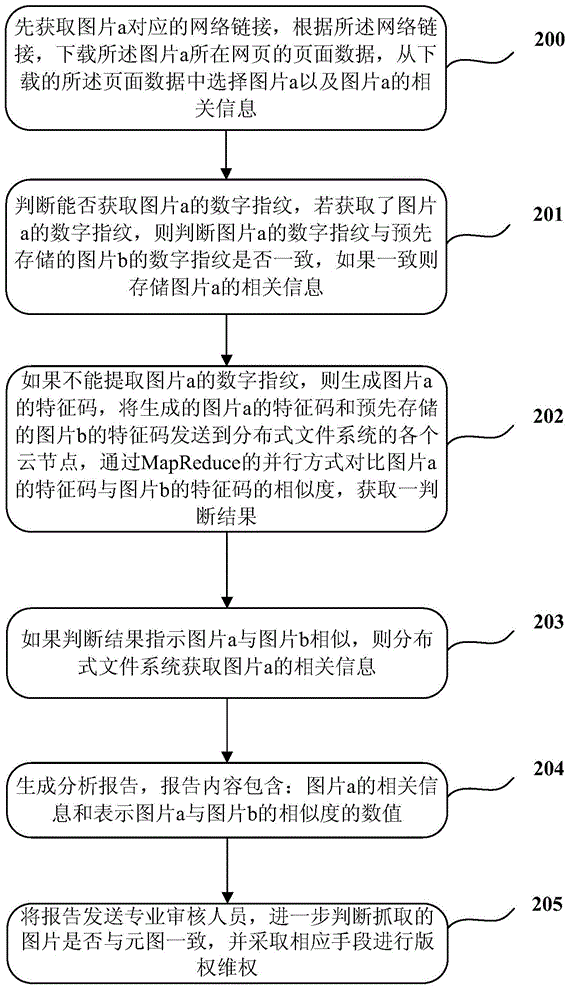
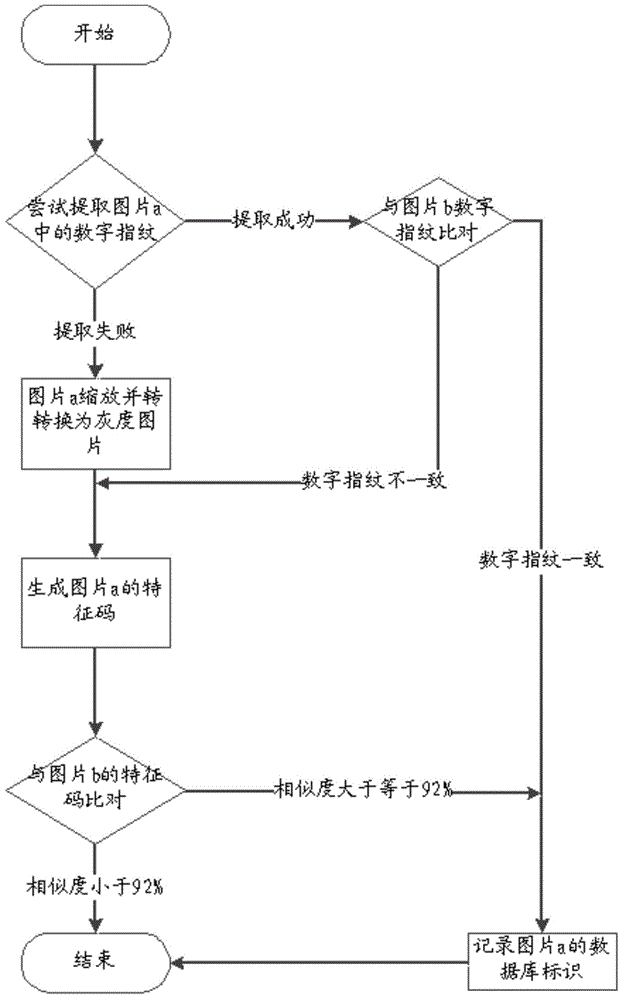
The invention provides a picture processing method and a picture processing device. The method includes acquiring a to-be-recognized first picture, calculating a first feature code of the first picture, comparing the first feature code with a prestored second feature code corresponding to a second picture to acquire a comparison result serving as the similarity between the first picture and the second picture, and storing related information of the first picture when the comparison result reaches a preset value. The picture processing method and the picture processing device have the advantages that similar pictures can be quickly searched out in current massive digital picture databases, whether or not the acquired pictures violate copyrights of original pictures can be easily figured out, and great benefits are brought to copyright protection of digital pictures.
Owner:PEKING UNIV FOUNDER GRP CO LTD +2
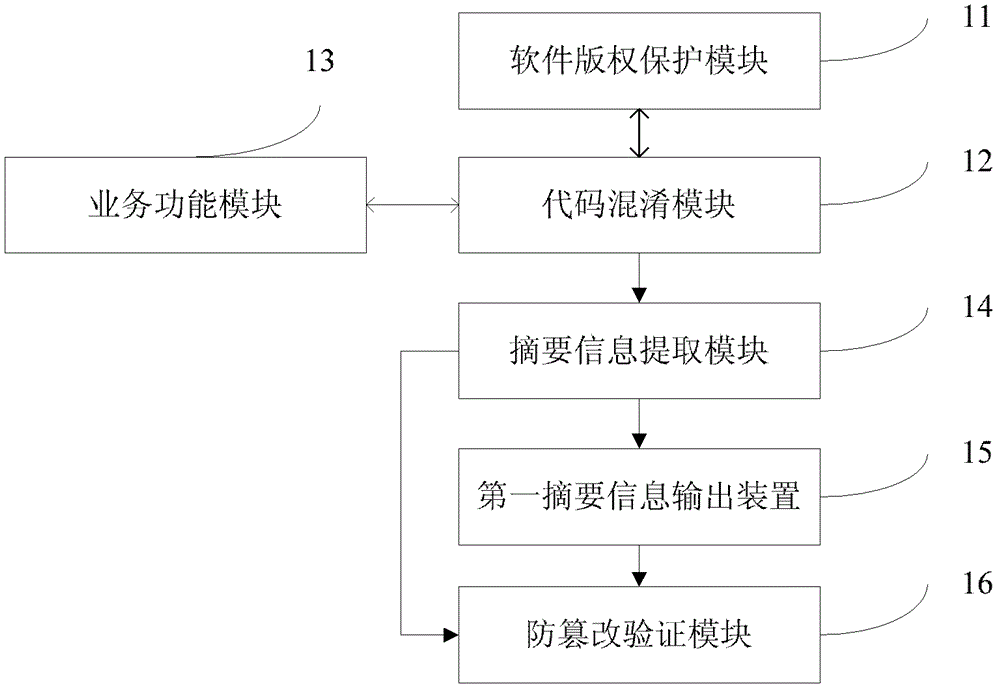
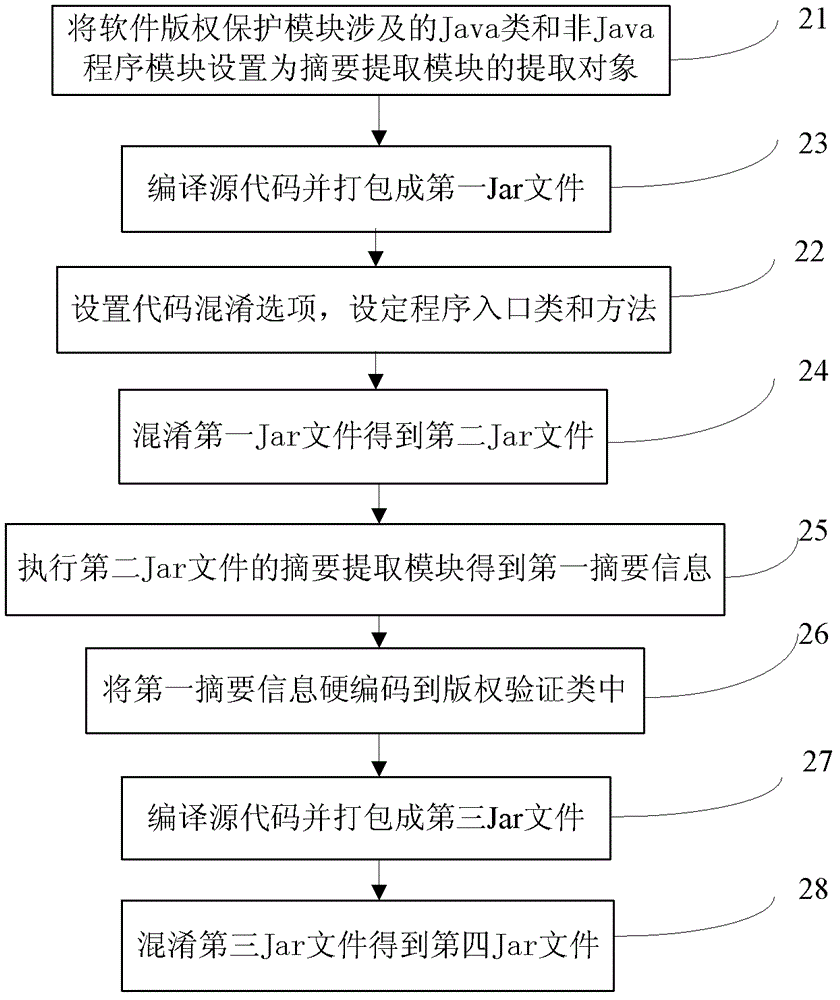
Method and device to improve Java software jailbreak difficulty and copyright verification method
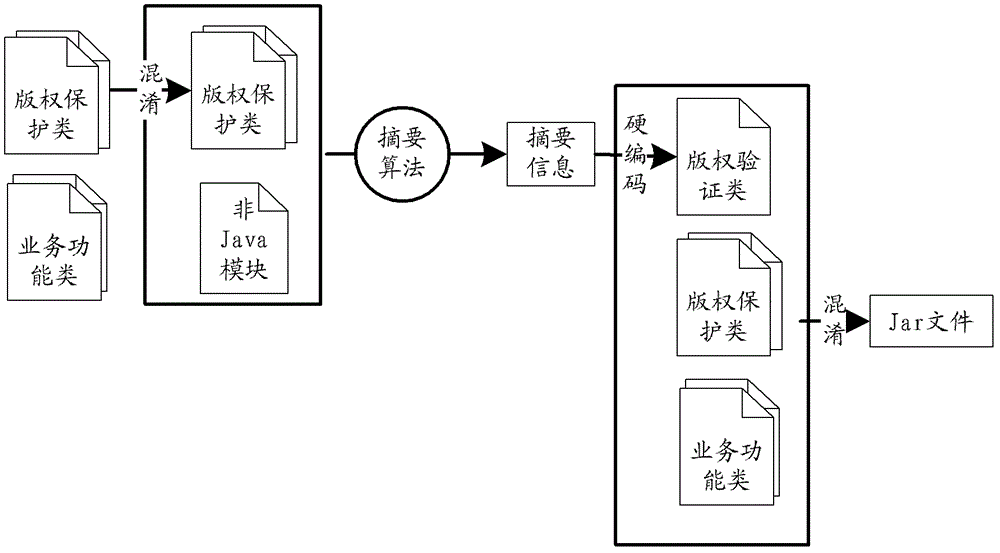
ActiveCN103065072AIncrease the difficulty of crackingStrengthen copyright protectionProgram/content distribution protectionHard codingSummary information
Owner:PEKING UNIV +2
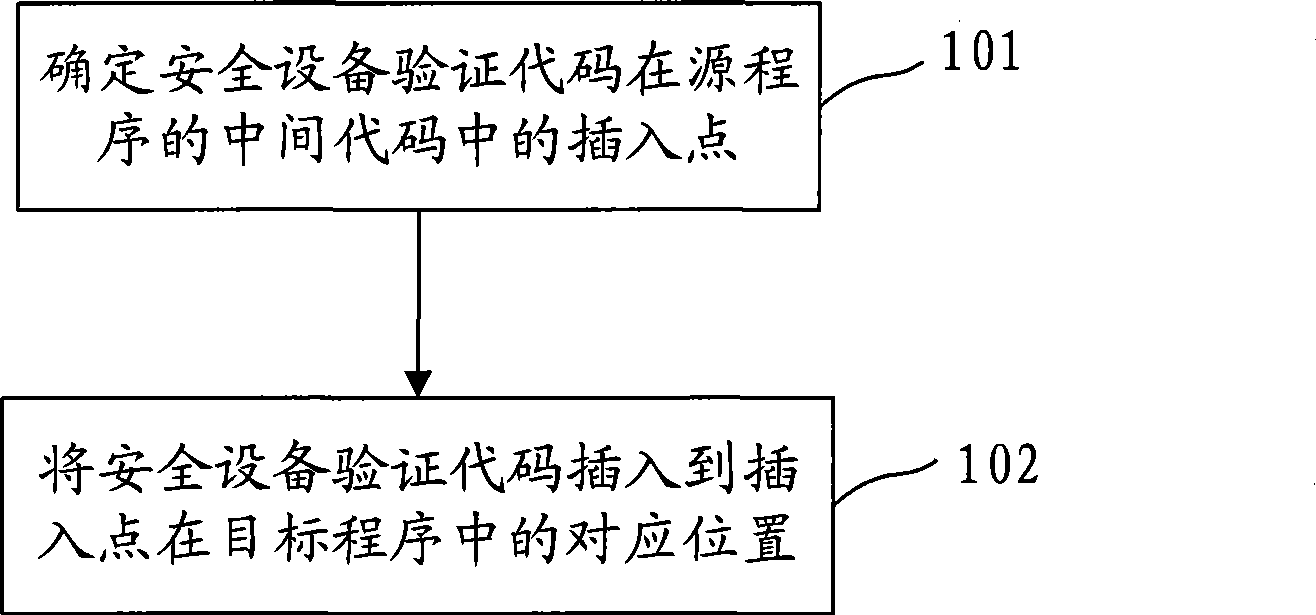
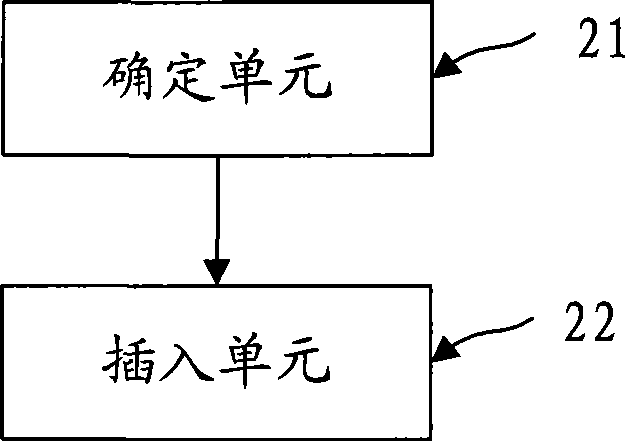
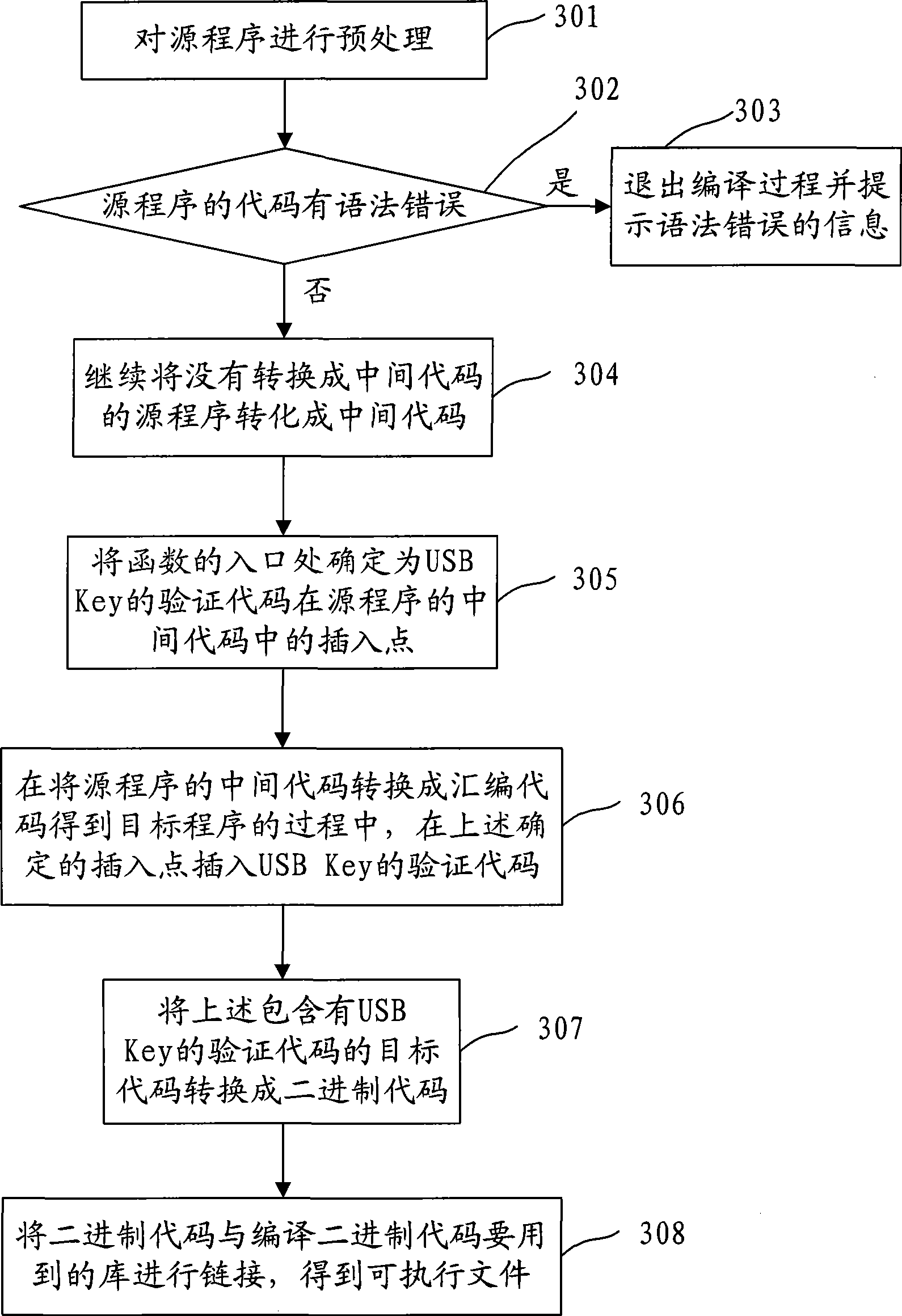
Method for compiling and compiler
ActiveCN101446905ATo achieve the purpose of copyright protectionStrengthen copyright protectionProgram controlMemory systemsHigh-level programming languageComputer programming
The invention discloses a method for compiling and a compiler, relates to the technical field of computers and solves the problem that the copyright of a compiled object program can not be protected securely in the prior art. The method for compiling comprises the following steps: confirming the insertion point of the authentication code of a safety device in the intermediate code of a source program; and inserting the authentication code of the safety device in the corresponding position of the inserting point in the object program during the process of converting the intermediate code of the source program into the assembly code to acquire the object program. The compiler module of the compiler comprises a confirming unit used for confirming the insertion point of the authentication code of the safety device in the intermediate code of the source program, and an inserting unit used for inserting the authentication code of the safety device in the corresponding position of the inserting point in the object program during the process of converting the intermediate code of the source program into the assembly code to acquire the object program. The embodiment of the invention is mainly applicable to computer programming, in particular to compiling of various advanced languages.
Owner:FEITIAN TECHNOLOGIES
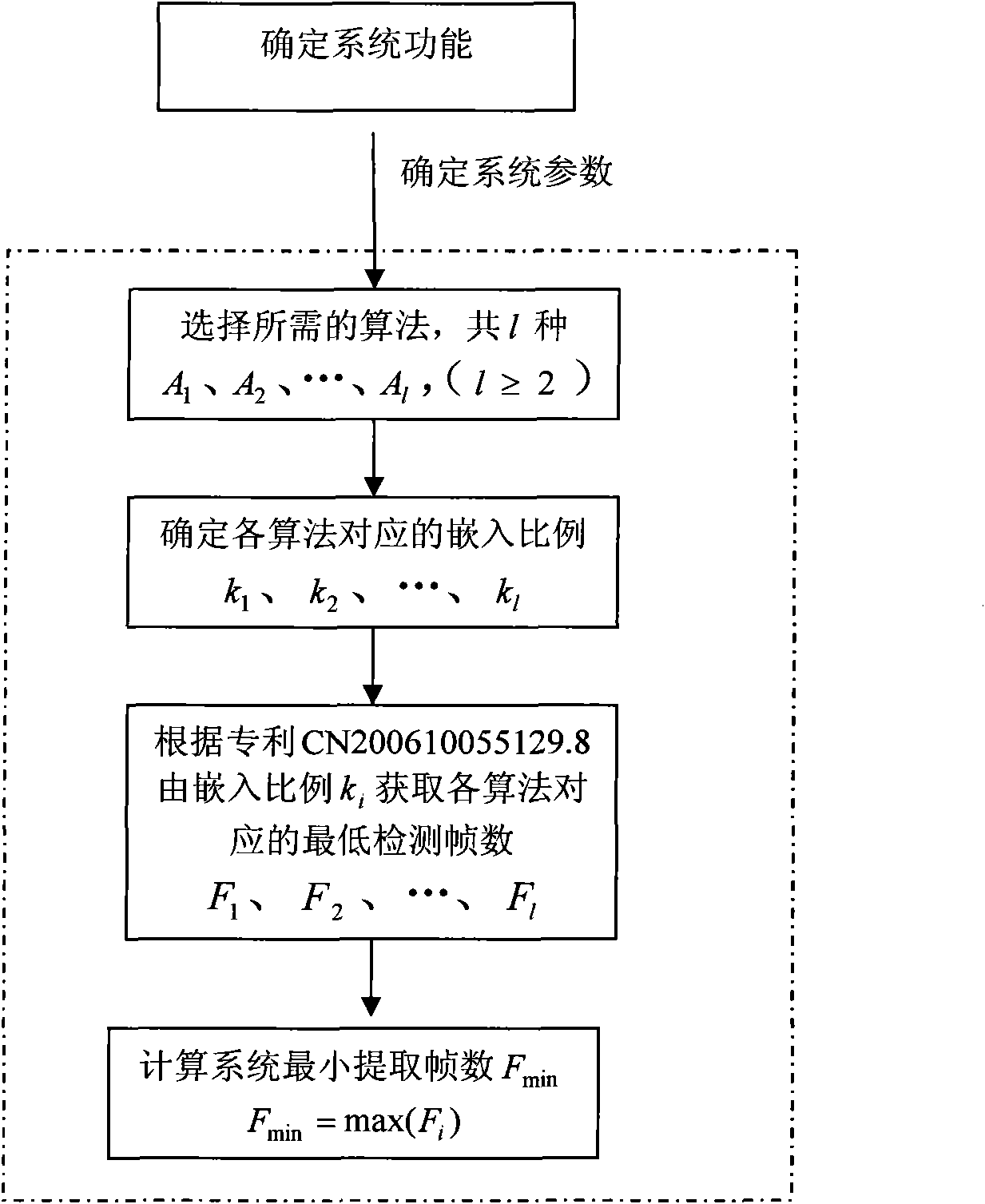
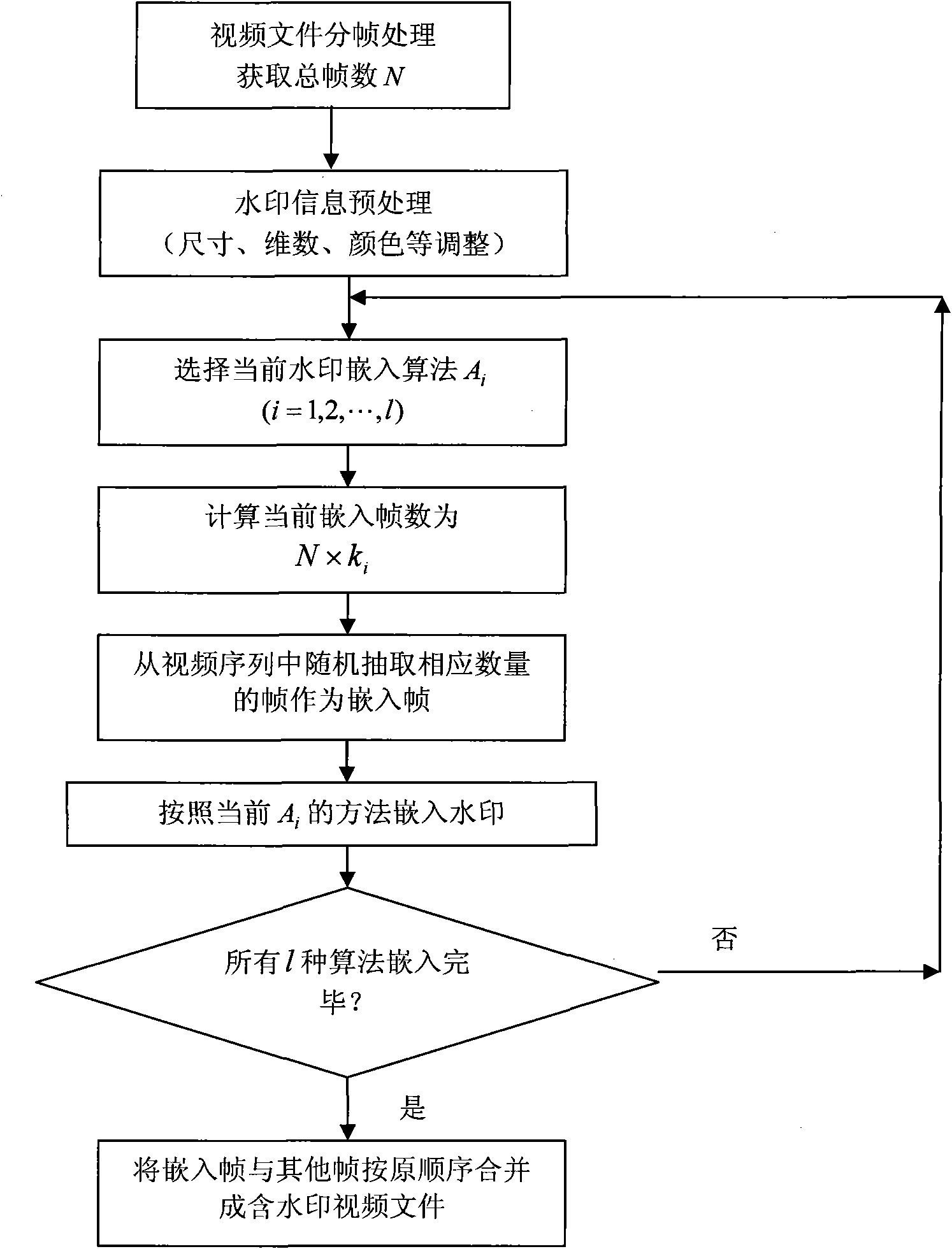
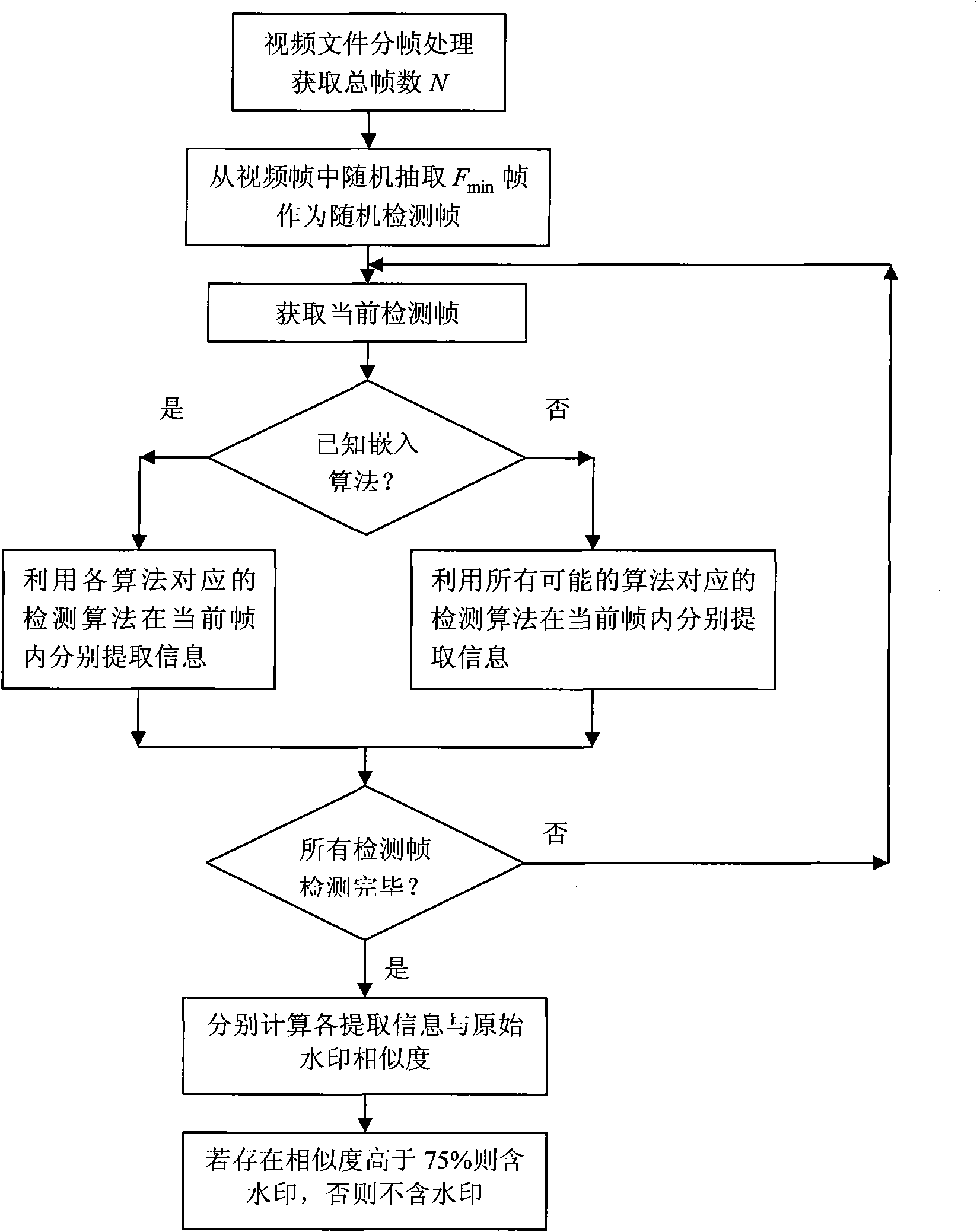
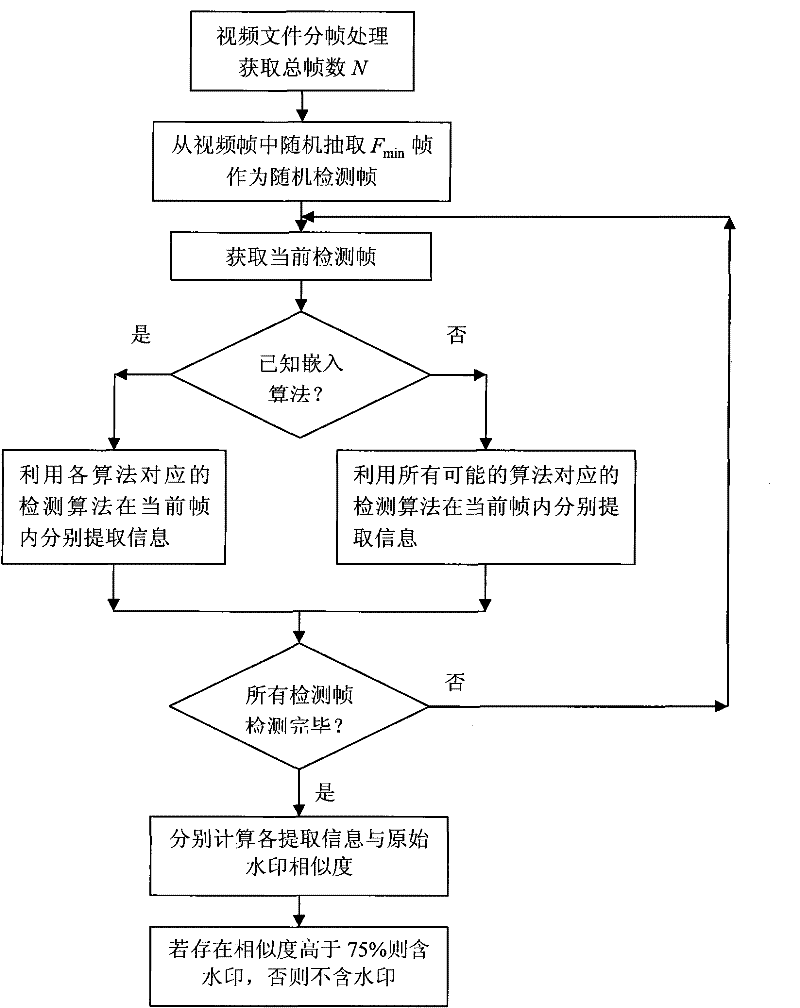
General video digital watermark method
InactiveCN101938618AImprove performanceFlexible adjustment of embedding ratioTelevision system detailsColor television detailsSystems designWatermark method
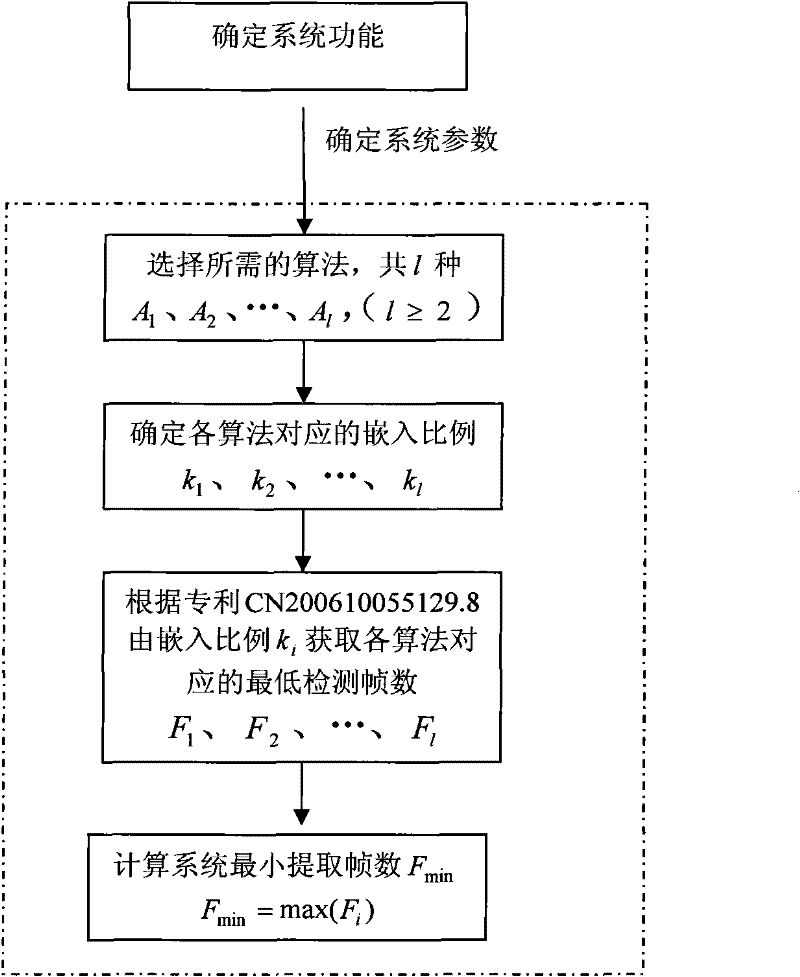
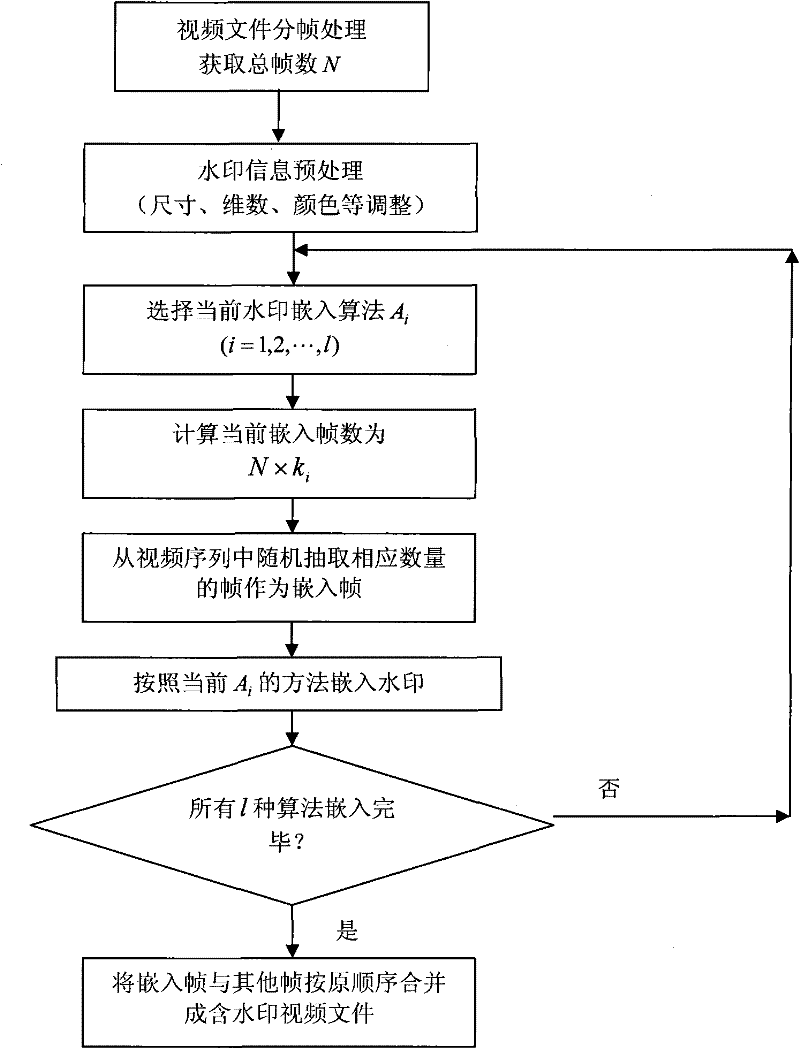
The invention discloses a general video digital watermark method mainly comprising analysis, embedding and extraction processes of a system design scheme. The analysis of the system design scheme comprises determination of a system function, watermark algorithms Ai to be embedded, embedding proportions of all algorithms and minimum extraction frame number Fmin; the watermark embedding process comprises frame distribution of a video file, watermark information pre-processing, embedding of watermark algorithms and formation of video files containing watermarks, wherein the embedding of watermark algorithms comprises the steps of: calculating embedding frame numbers, selecting embedding frames and embedding the watermark; and the watermark extracting process comprises frame distribution of the video file, selection of video frames to be detected, extraction of watermark information and calculation similarity. In the invention, the plurality of watermark algorithms are embedded at the same time and the embedding proportions can be selected, thereby the watermark method obviously enhances attack-resistant property; the watermark embedding ensures the appreciation and the embedding speed of the video file by using a non-frame-by-frame embedding way; in the watermark extracting process, the number of the detecting frames is less and the detection efficiency is improved; in addition, the general video digital watermark method also intensifies the capability of resisting frame edition.
Owner:SHANDONG COMP SCI CENTNAT SUPERCOMP CENT IN JINAN
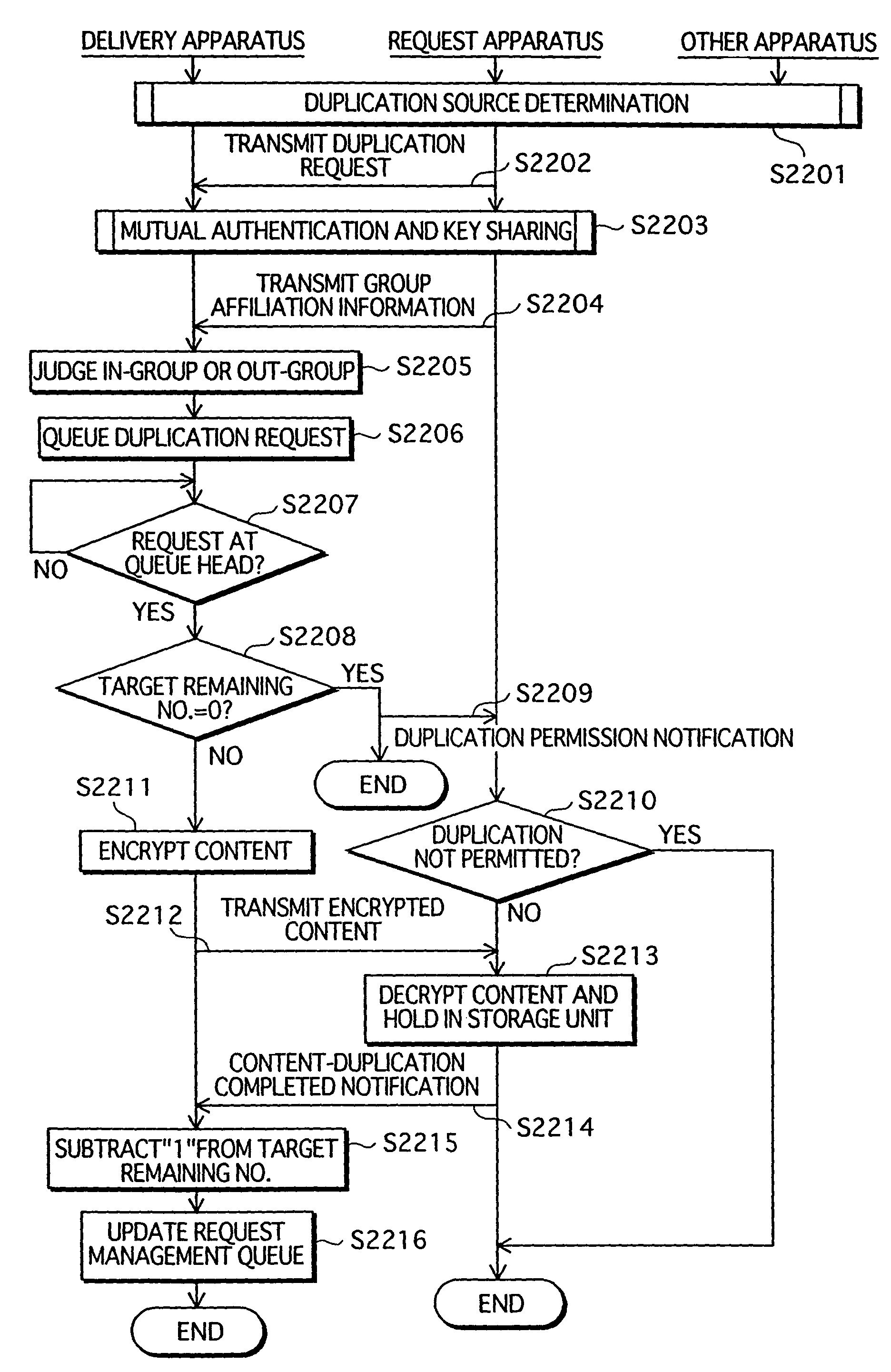
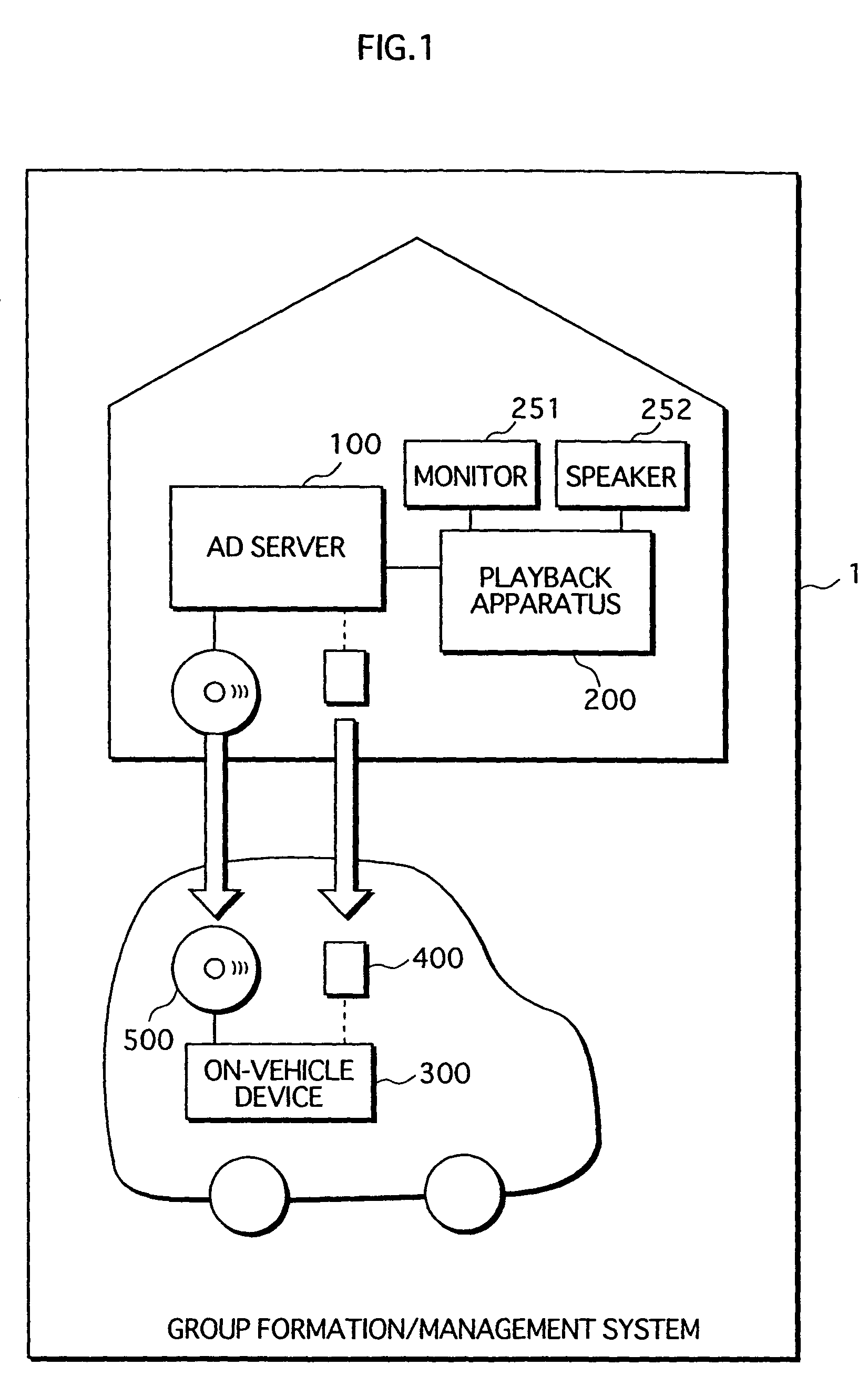
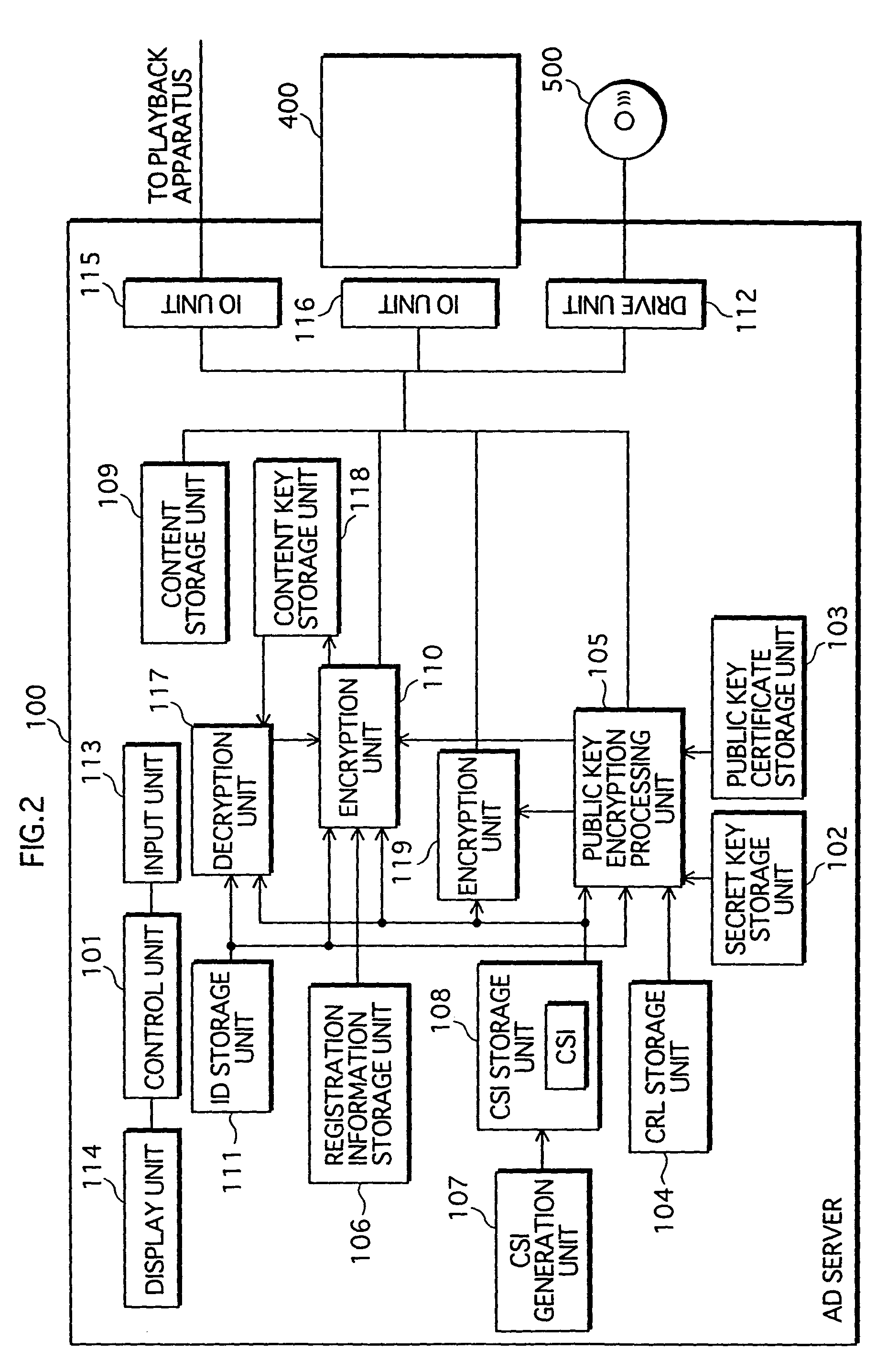
Content-duplication management system, apparatus and method, playback apparatus and method, and computer program
InactiveUS7752433B2Strengthen copyright protectionImprove convenienceDigital data processing detailsDigital computer detailsContent replicationContent management
A content management system formed from a playback apparatus that requests and plays content, and a content management apparatus that manages duplication and deletion of content. The playback apparatus notifies group information of the playback apparatus to the content management apparatus, acquires information from the content management apparatus showing whether requests are permitted, and duplicates / deletes content. By judging whether the playback apparatus belongs to a group, and notifying whether a duplication request is permitted or rejected, based on in-group and out-group remaining numbers that show the remaining number of duplications permitted of apparatuses in-group and out-group, respectively, the content management apparatus relaxes restrictions on in-group content duplication as compared with out-group content duplication, and thus improves convenience for users in a home network, while protecting the rights of copyright holders, with respect to content duplication and usage.
Owner:PANASONIC CORP
Digital watermark algorithm based on text document protection
ActiveCN107688731AStrengthen copyright protectionImprove robustnessImage analysisImage data processing detailsComputer graphics (images)Documentation
The invention discloses a digital watermark algorithm based on text document protection. Implementation of watermark information in a text document consists of watermark embedding and watermark extracting; a watermark embedding treatment process comprises carrier text image pretreatment, ciphertext ID coding, pseudo-random periodic sequence watermark generation and carrier image fusion; and the watermark extracting treatment process comprises image reinforced treatment, extraction of a pseudo-random sequence watermark texture map and decoding of watermark information. For solving the technicalproblem that an existing digital watermark algorithm is poor in robustness, required ID information can be embedded in a text document by the algorithm, and even if a watermarked text is copied, photographed and sheared and the geometric structure of the watermarked text is damaged, watermark information concealed in the watermarked text can still be detected. The digital watermark algorithm based on text document protection can be widely applied to protection and tracing of documents with secret, document copyright protection, web page copyright protection, image mark protection of some commercial products and the like.
Owner:ANHUI ZHONGXIN SOFTWARE
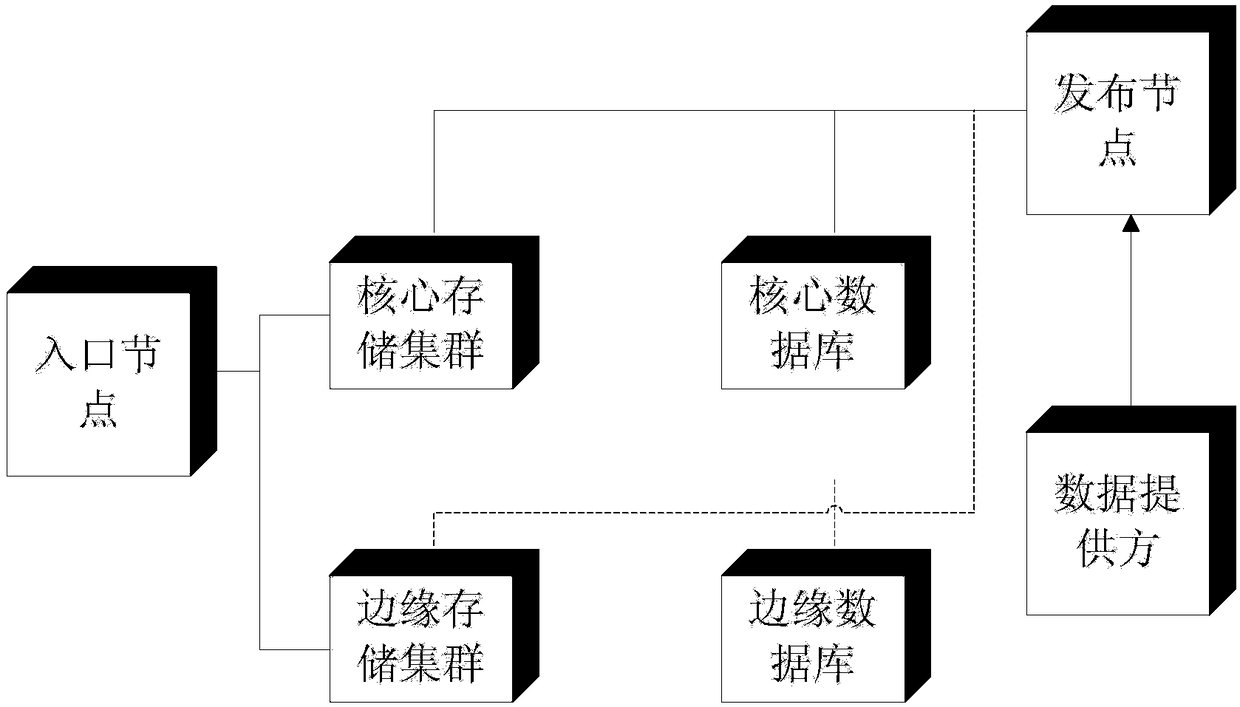
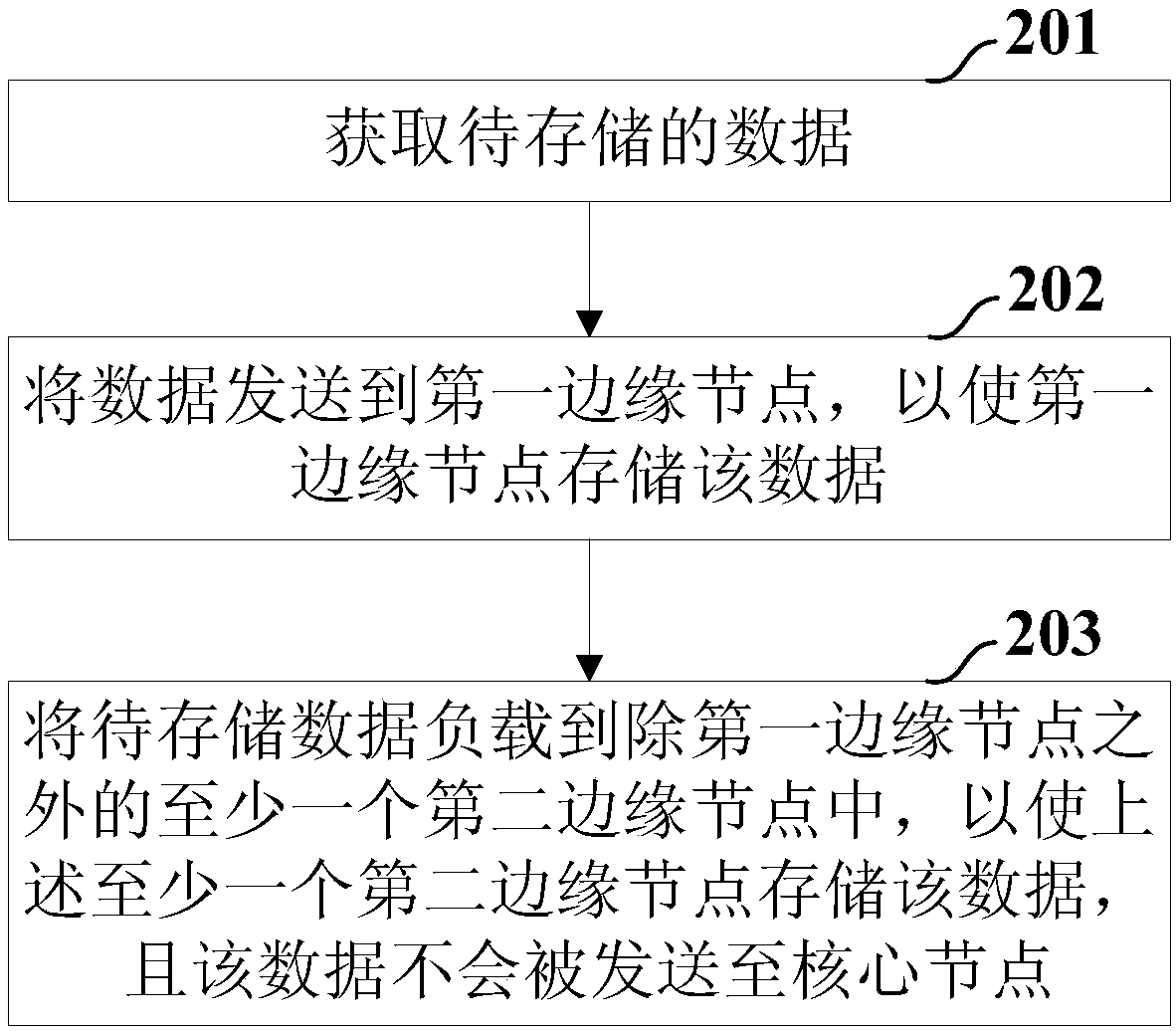
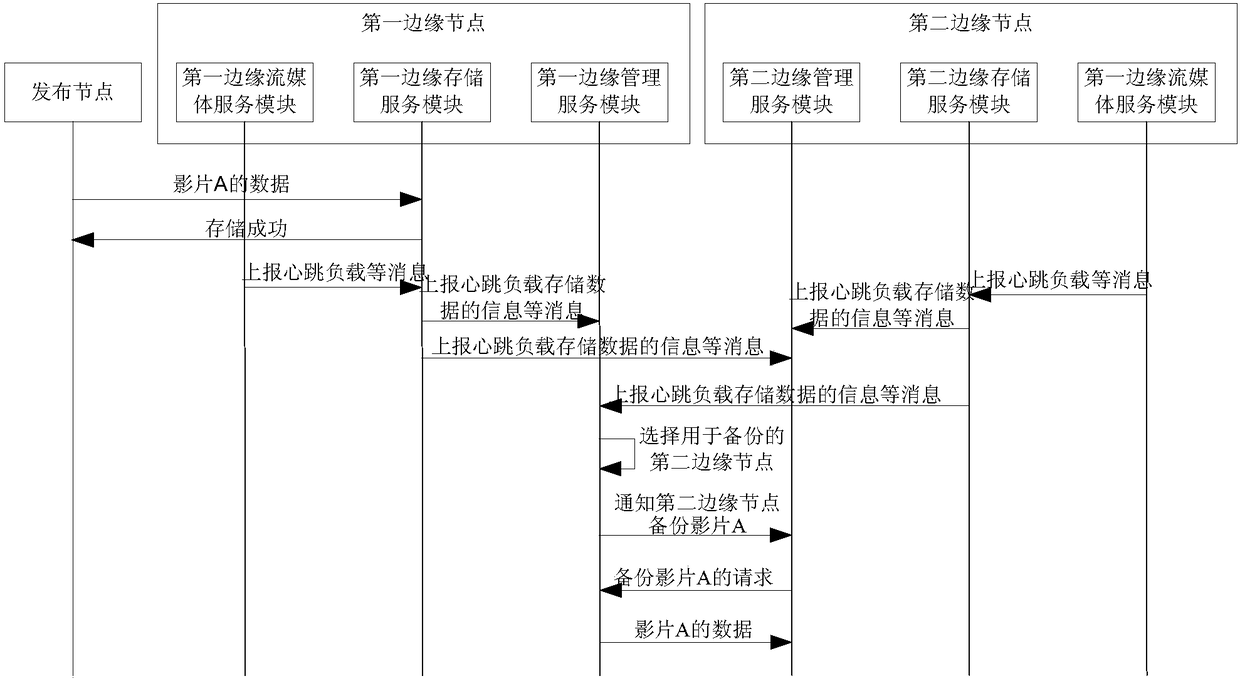
Data storage method in CDN (Content Delivery Network) system, and CDN system
InactiveCN108268209AImprove securityStrengthen copyright protectionInput/output to record carriersDigital data protectionContent delivery networkDistributed computing
The invention discloses a data storage method in a CDN (Content Delivery Network) system, and the CDN system. In the method, after data to be stored is obtained, the data to be stored is sent to a first edge node to enable the first edge node to store the data; the data is copied to at least one second edge node except the first edge node to enable the at least one second edge node to store the data, and in addition, the data can not be sent to a core node. In addition, according to the load situation of the edge node, the data stored in the first edge node and the second edge node is copied or migrated to other edge nodes. In the above method, since the data to be stored is directly stored in the edge node but is not sent to each edge node to be stored after being firstly stored into thecore node, so that the stored data can not be stored in the core node which can be accessed by users, and data safety is increased so as to be more favorable for the copyright protection of the data.
Owner:深圳市优朋普乐传媒发展有限公司
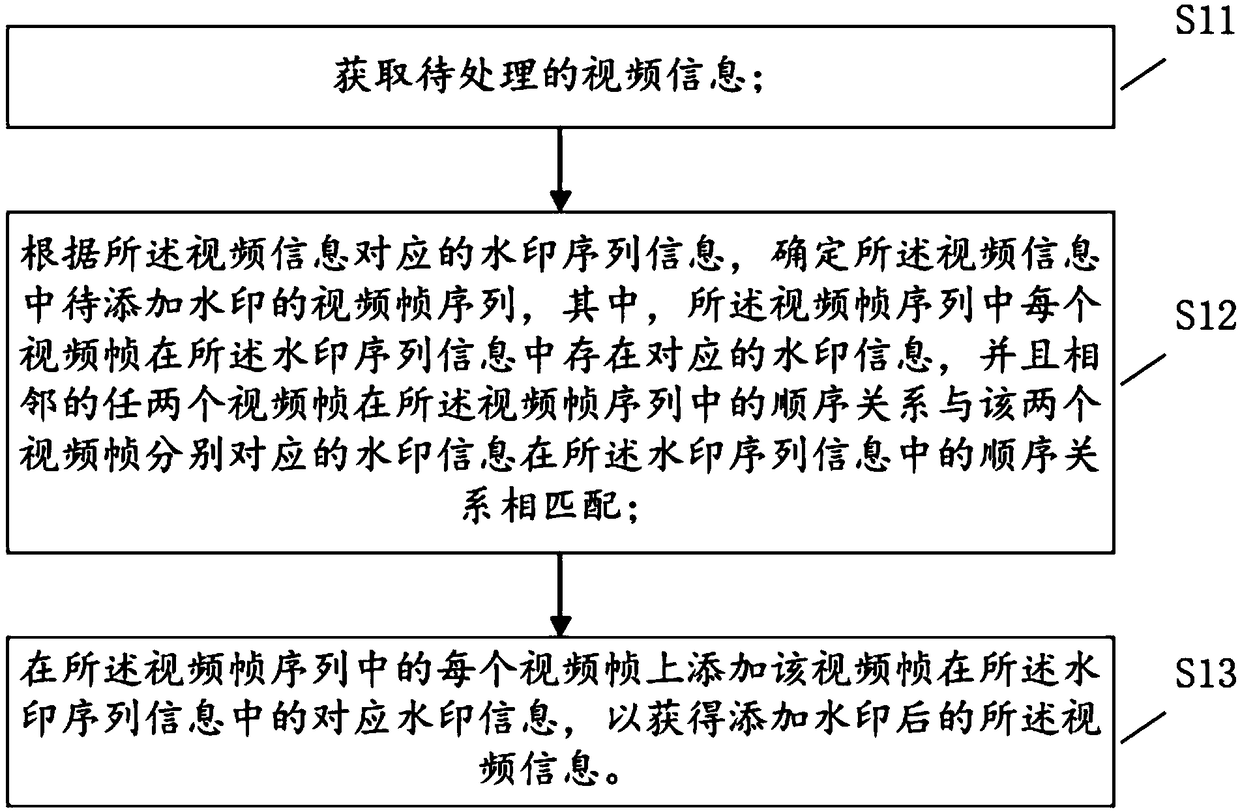
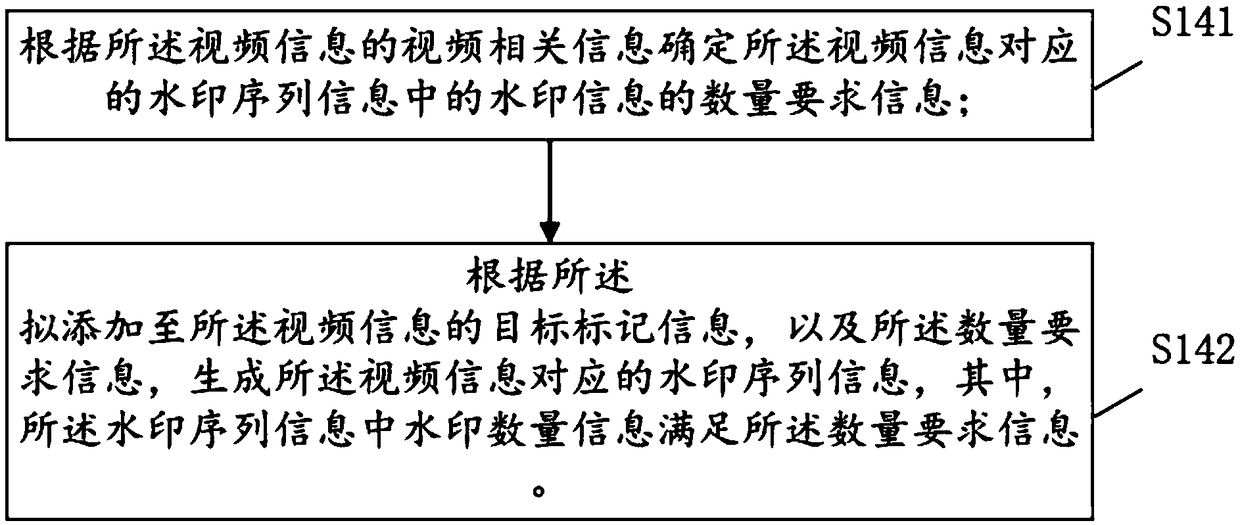
Method and equipment for adding and detection video watermark
ActiveCN109379642AStrong resistance to attackStrengthen copyright protectionSelective content distributionFrame sequenceComputer graphics (images)
The application aims at providing a method and equipment for adding and detecting a video watermark. The method for adding the watermark in a video comprises the following steps: acquiring to-be-processed video information; determining a video frame sequence of a to-be-added watermark in the video information according to the watermark sequence information corresponding to the video information, wherein each video frame in the video frame sequence has corresponding watermark information in the watermark sequence information, and an order relation of two adjacent video frames in the video framesequence is matched with the order relation of watermark information corresponding to two video frames in the watermark sequence information; adding the corresponding watermark information of the video frame in the watermark sequence information on each video frame in the video frame sequence, thereby acquiring the video information added with watermark. Through the method provided by the invention, the attack resistance of the added video watermark is stronger.
Owner:LIANSHANG XINCHANG NETWORK TECH CO LTD
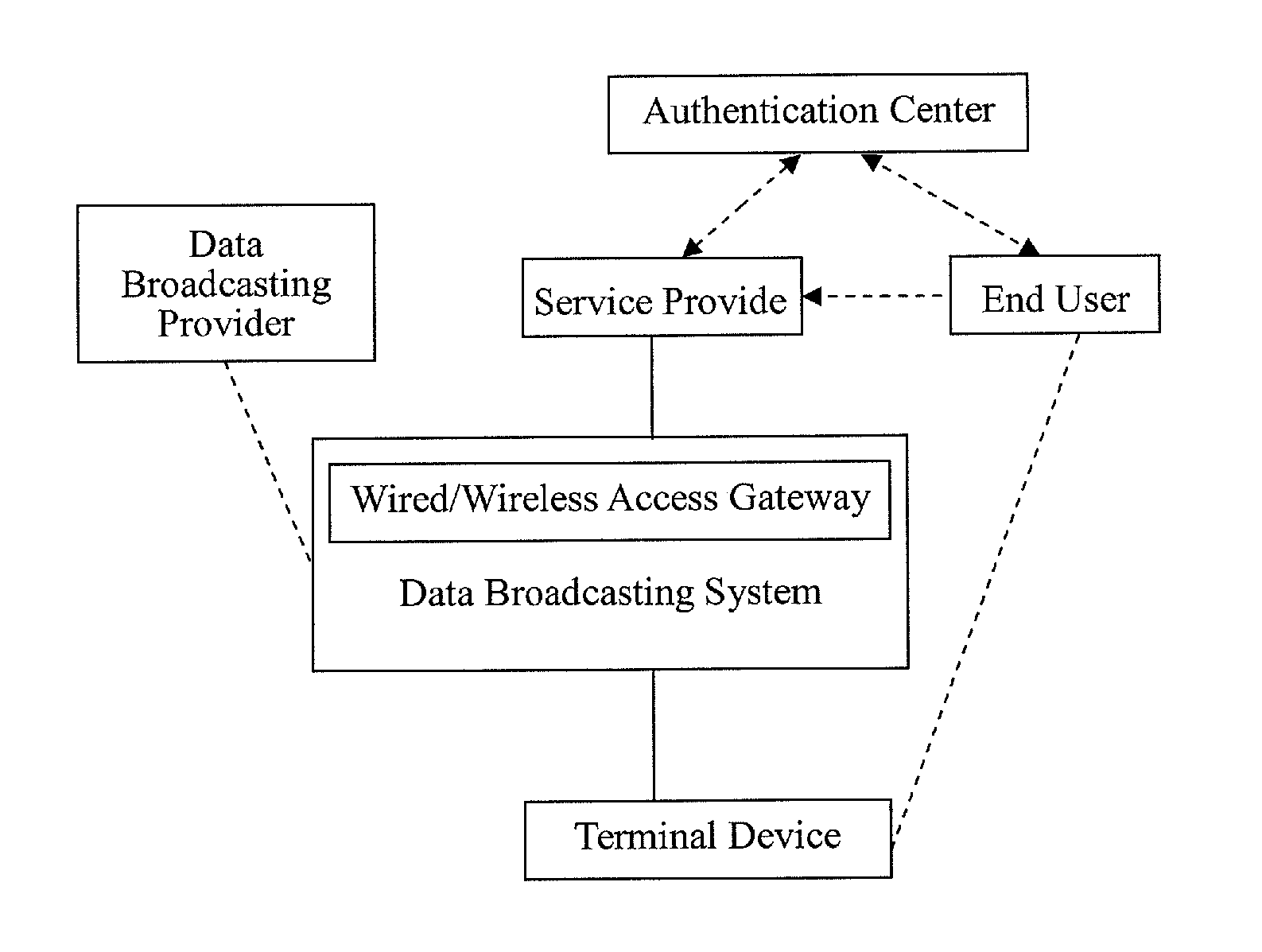
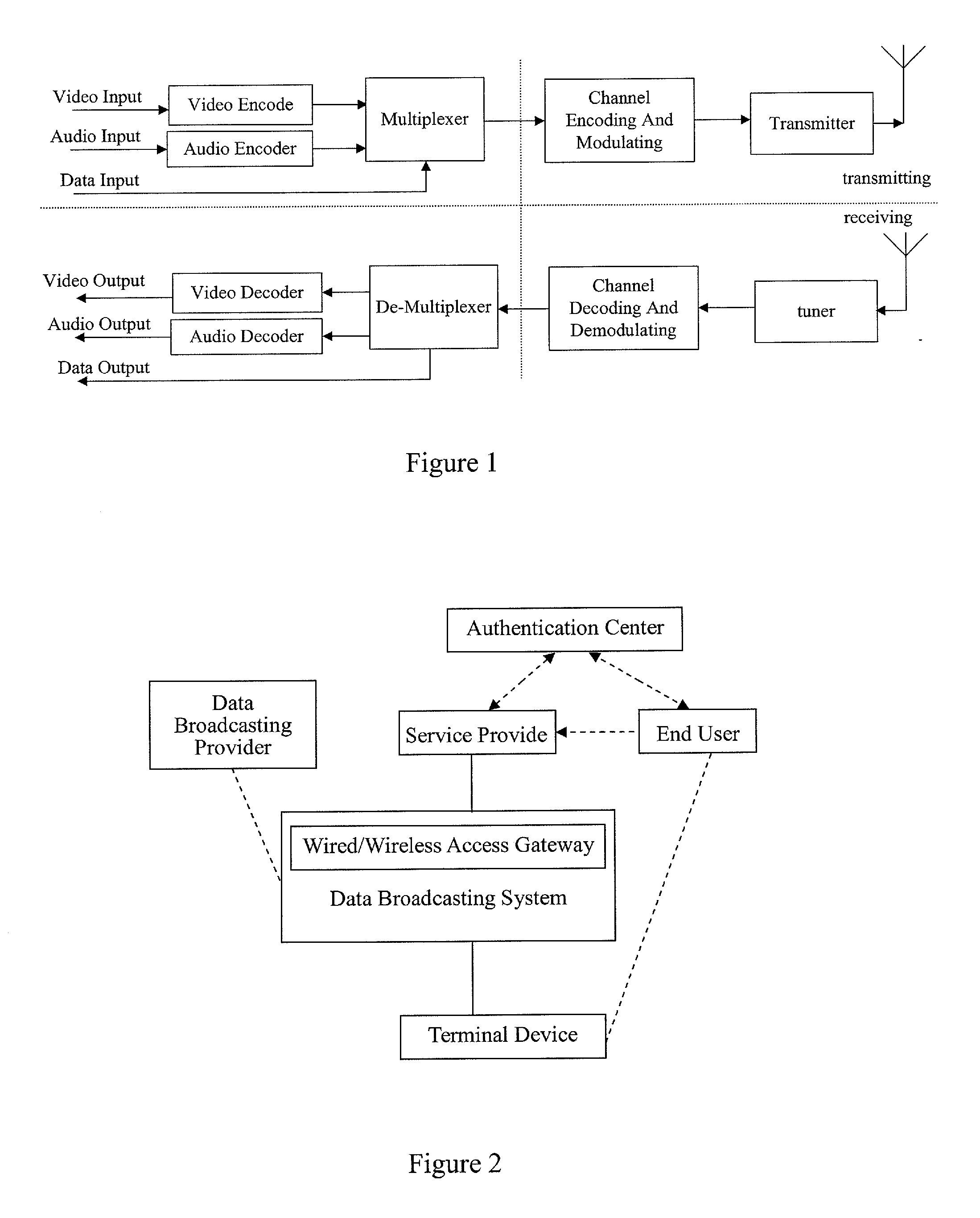
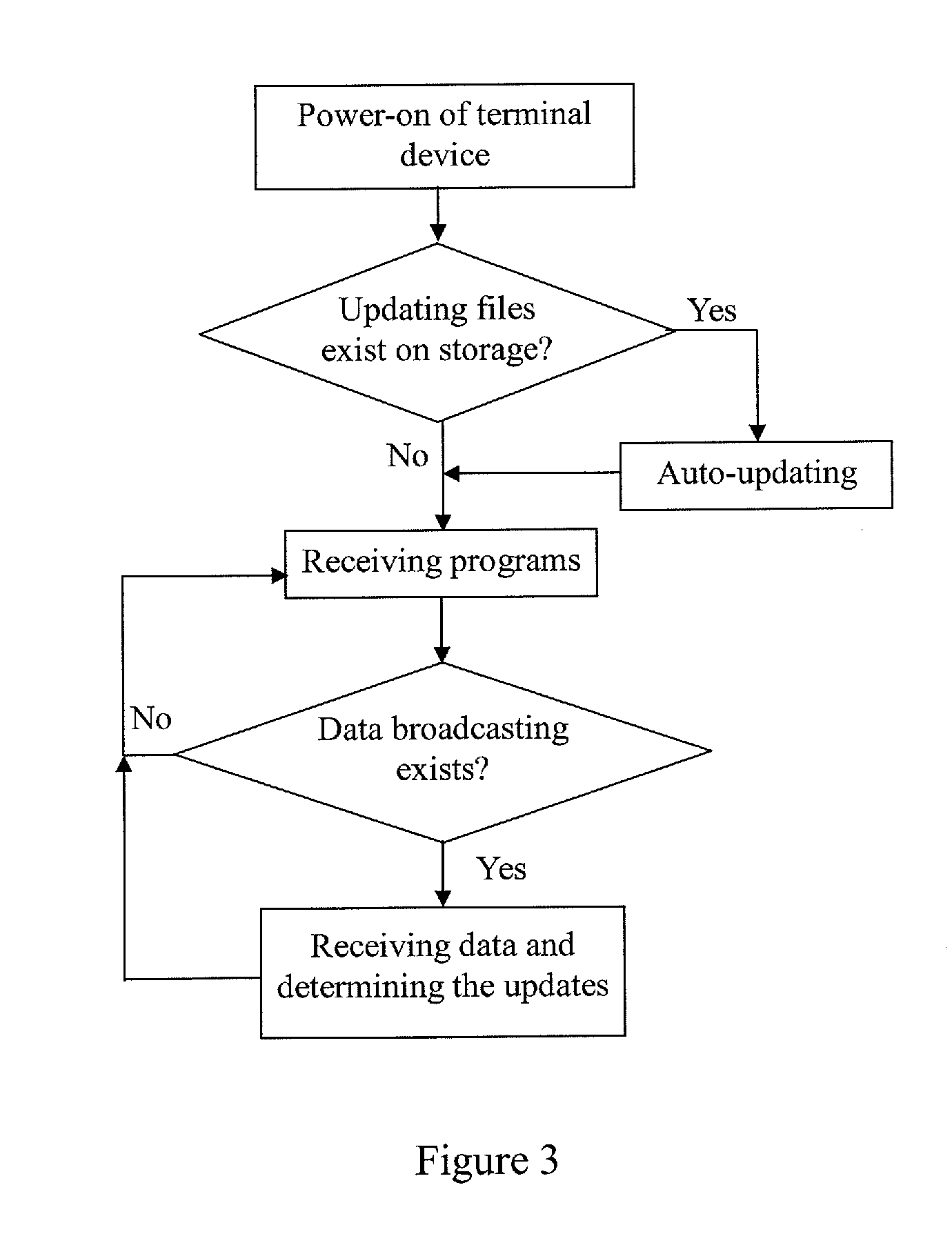
Methods For Upgrading Software Or Updating Contents In Terminal Devices Based On Digital TV Data Broadcast
InactiveUS20110191583A1Low costFacilitates the users to upgrade system timelyTelevision system detailsBroadcast information characterisationService provisionTerminal equipment
A method for upgrading software or contents in a terminal device based on digital TV data broadcasting is provided. The method comprises steps of uploading an upgrading file or content file to an access gateway by a service provider via a data broadcasting system; transmitting the upgrading file or content file to the terminal device in a broadcast mode by the data broadcasting system; and receiving the transmitted upgrading file or content file by the terminal device. The method further comprises a step of determining whether the received upgrading file or content file is of a higher version than that of a currently used software file or content file of the terminal device; and if yes, upgrading the currently used software file or content file. The method according to the present invention decreases maintenance cost of the terminal device, facilitates upgrading system in time, maintains copyright benefit of the service provider, and is convenient for the user to upgrade his terminal device.
Owner:NETAK TECH KO LTD
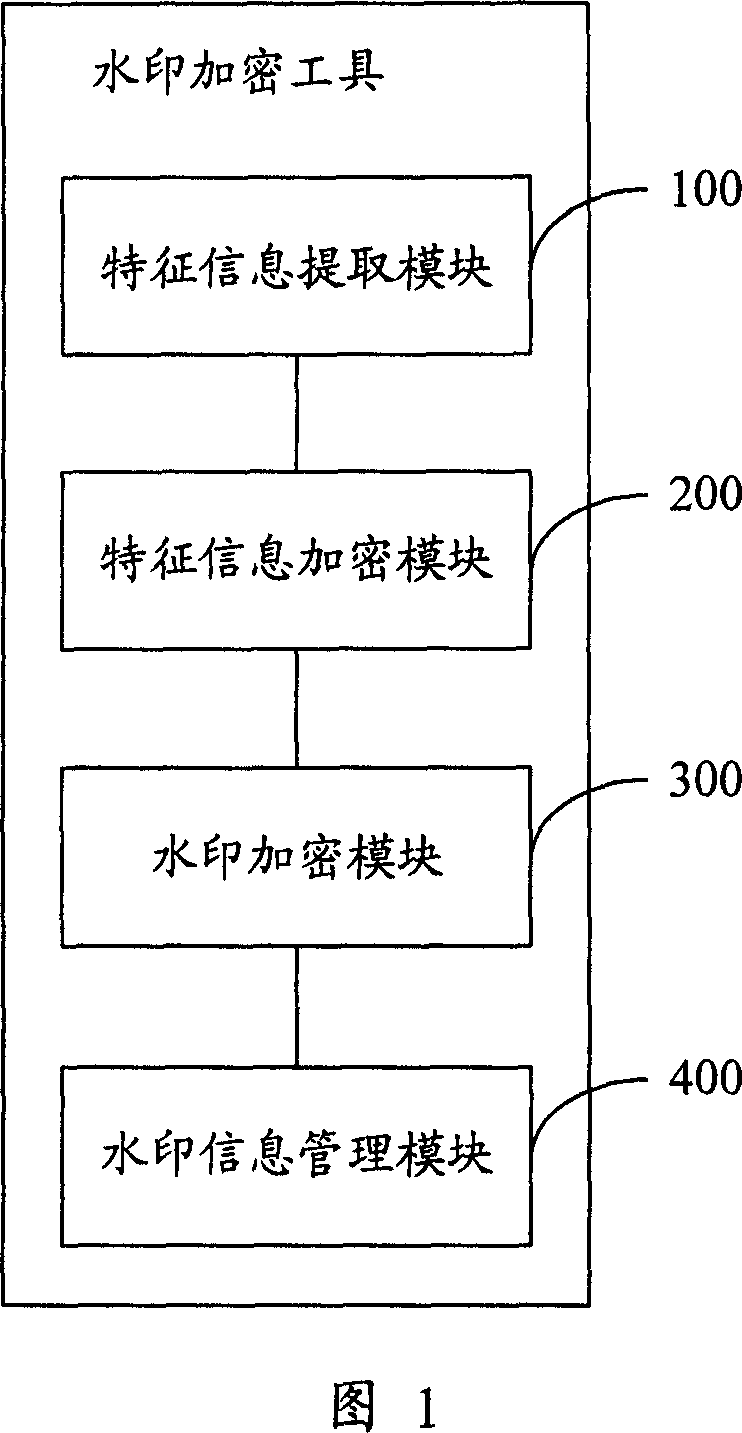
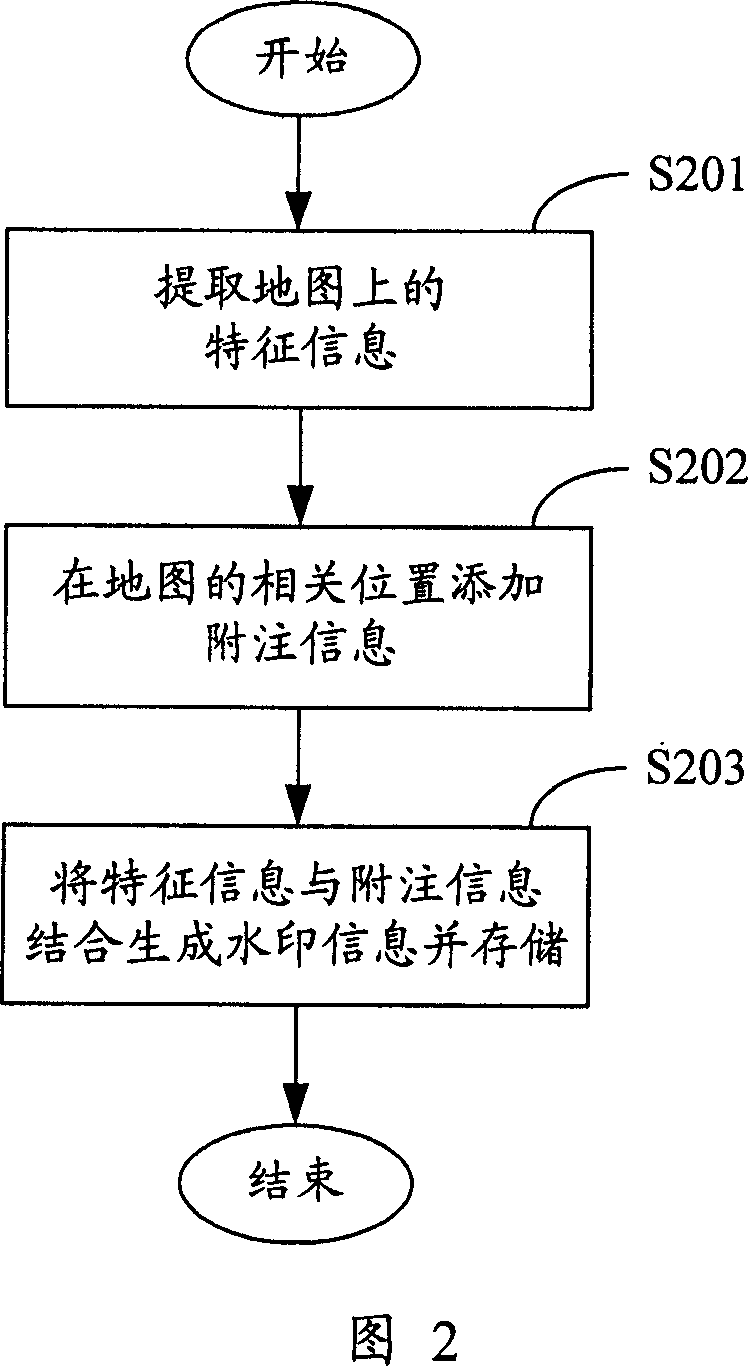
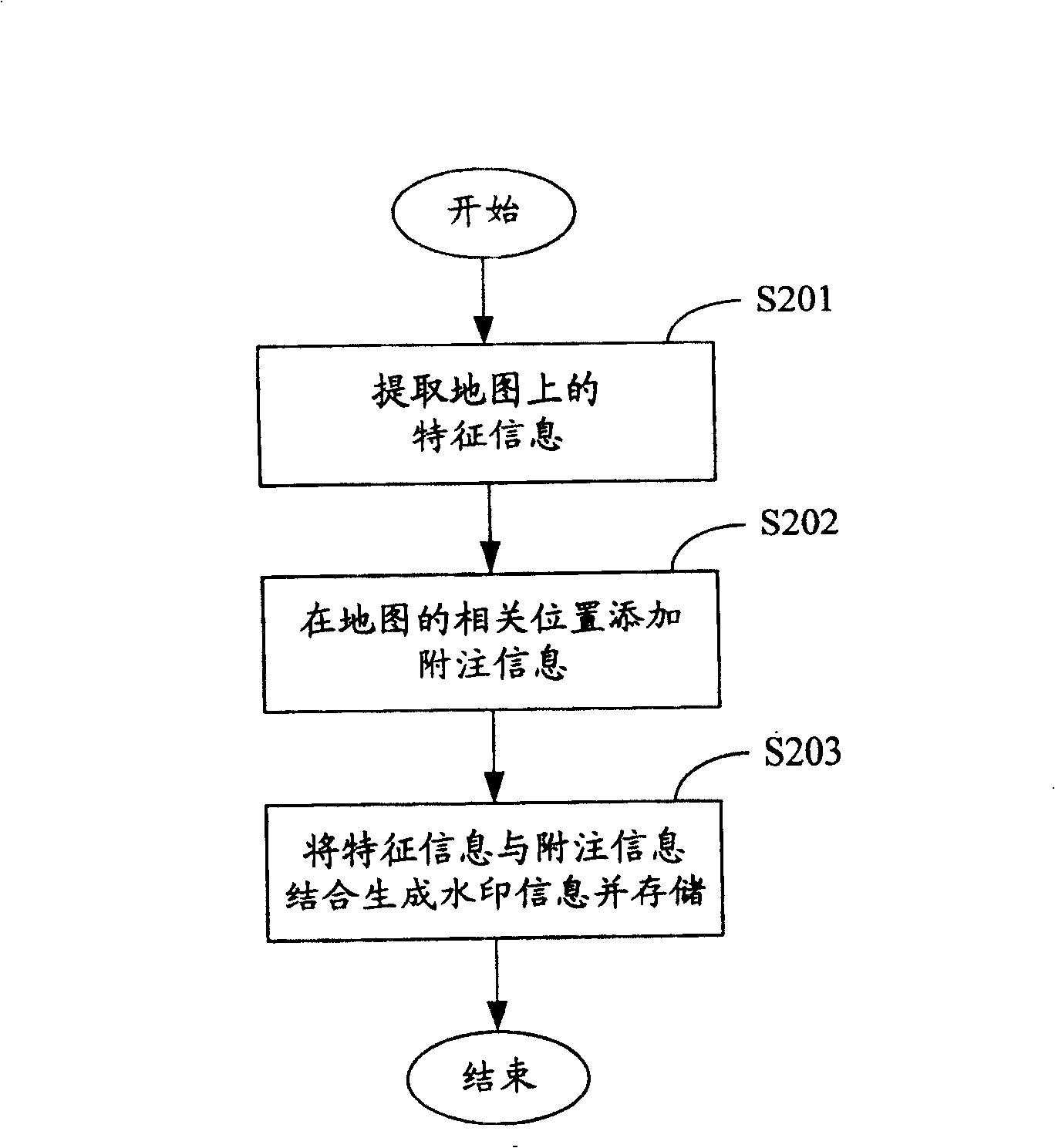
Method of and apparatus for encrypting digital map
ActiveCN1924875AStrengthen copyright protectionImprove the efficiency of copyright verificationProcessor architectures/configurationProgram/content distribution protectionInformation securityComputer science
This invention provides one pair of electron map coding method and device in information safety field, which comprises the following steps: a, catching characteristic information from map; b, adding extra information at relative position of the said electron map and establishing the said information and the characteristic information; c, integrating the above information into watermark information for storage. This invention generates watermark information to code the electron map.
Owner:北京百度智图科技有限公司
Multichannel ultrasonic collecting device for detecting nonmetal medium
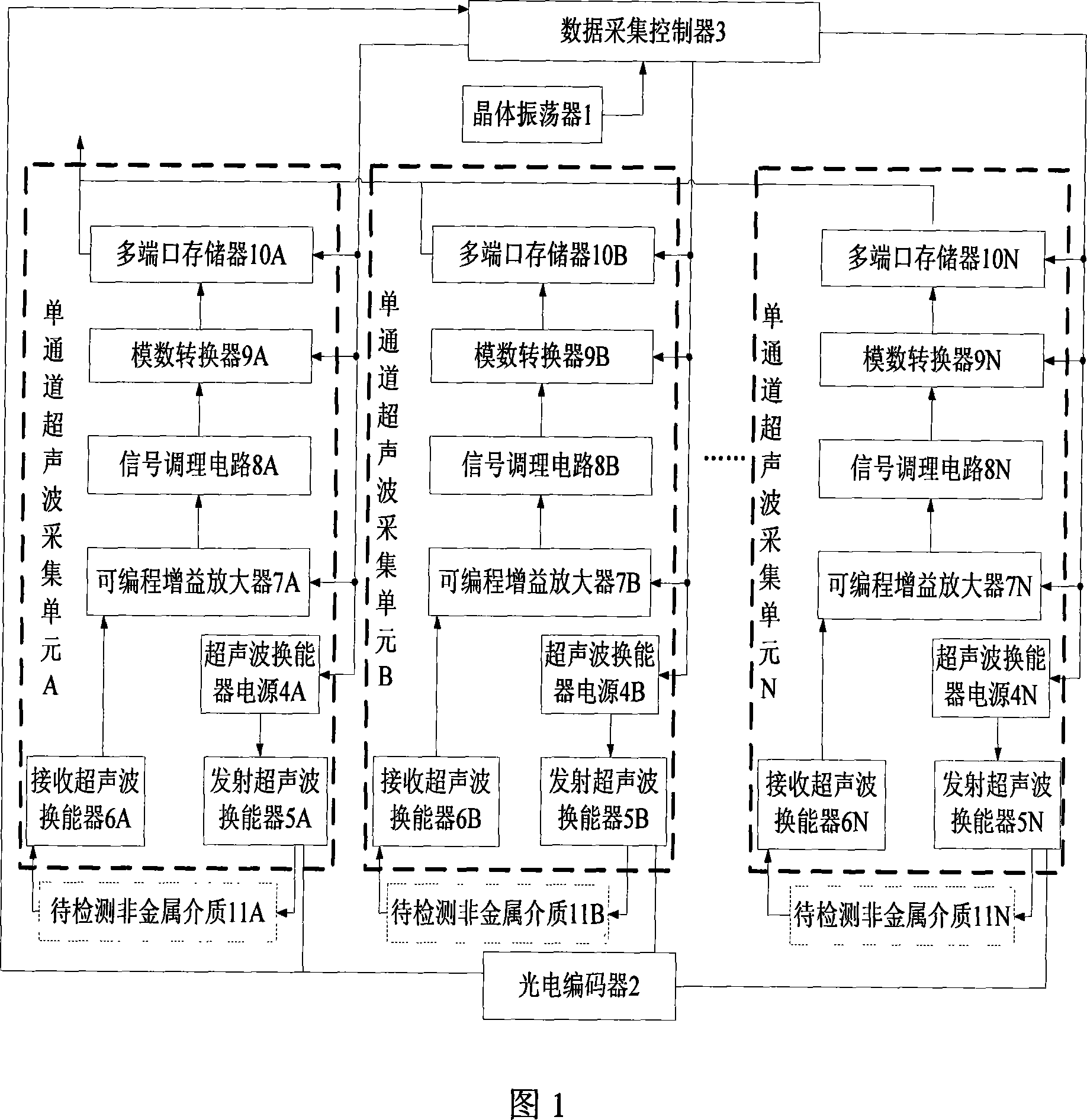
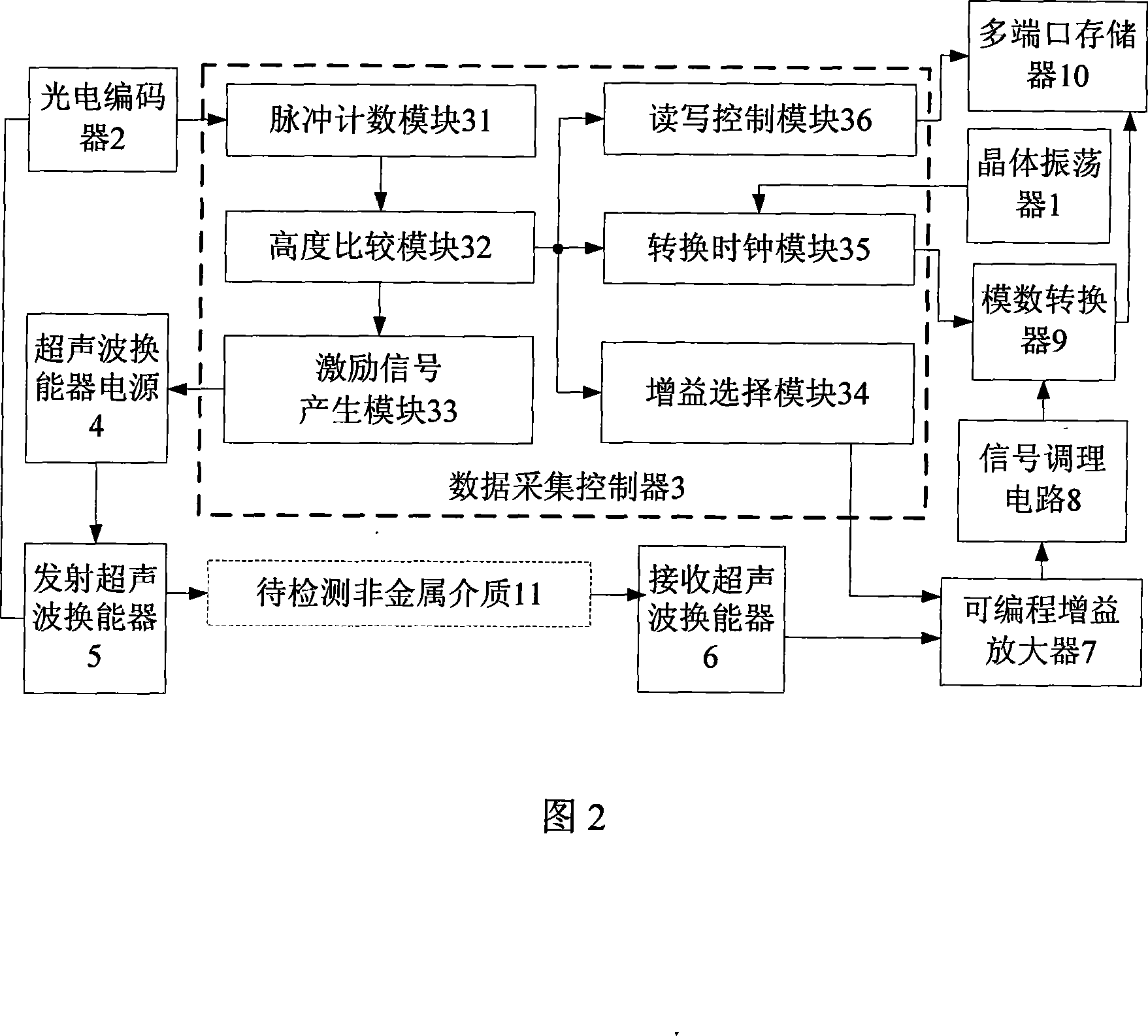
InactiveCN101067618AConvenient parallel acquisitionHighly integratedAnalysing solids using sonic/ultrasonic/infrasonic wavesResponse signal detectionElectricityControl signal
The invention provides a multichannel ultrasonic wave gathering installment which is used to examine the nonmetal medium, which includes crystal oscillator, photo electricity encoder, data acquisition controller and n single channel ultrasonic wave gathering unit. The crystal oscillator used to produce the vibration signal and transmit to the data acquisition controller; the photo electricity encoder is separately connected with n single channel ultrasonic wave gathering unit, produces the pulse under the single channel ultrasonic wave gathering unit impetus and transmits to the data acquisition controller; the data acquisition controller received the crystal oscillator outputs vibration signal and the photo electricity encoder output pulse signal, do the oscillation signal frequency division and the pulse counts to produce the control signal and transmit to the single channel ultrasonic wave gathering unit; the single channel ultrasonic wave gathering unit receives data acquisition controller outputs control signal to start gathering the work. The characteristic of the invention are that it is easy to expand, quickly data acquisition speed, the small volume and the low system power loss.
Owner:HUAZHONG UNIV OF SCI & TECH
System and method for network-loading game data
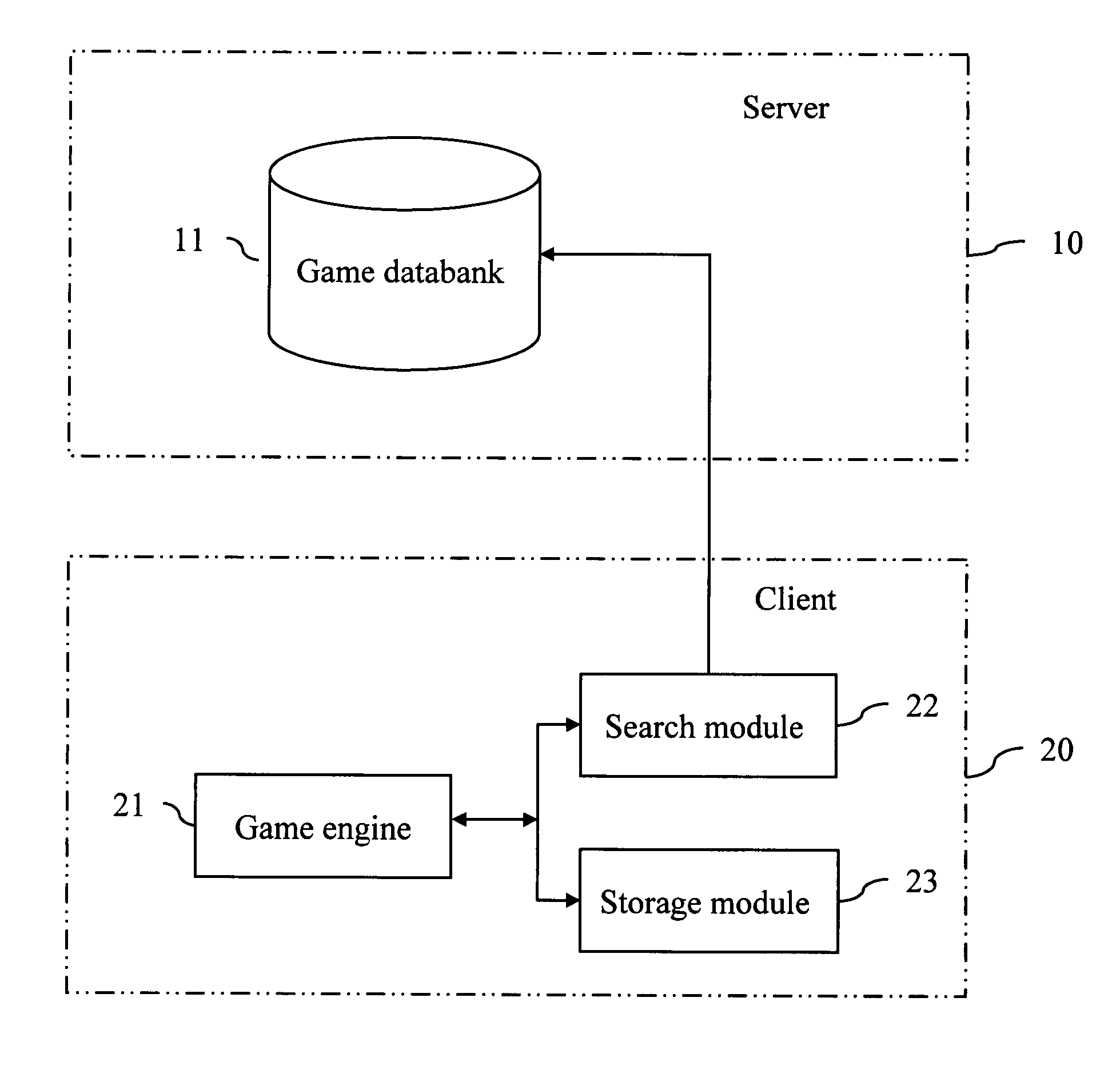
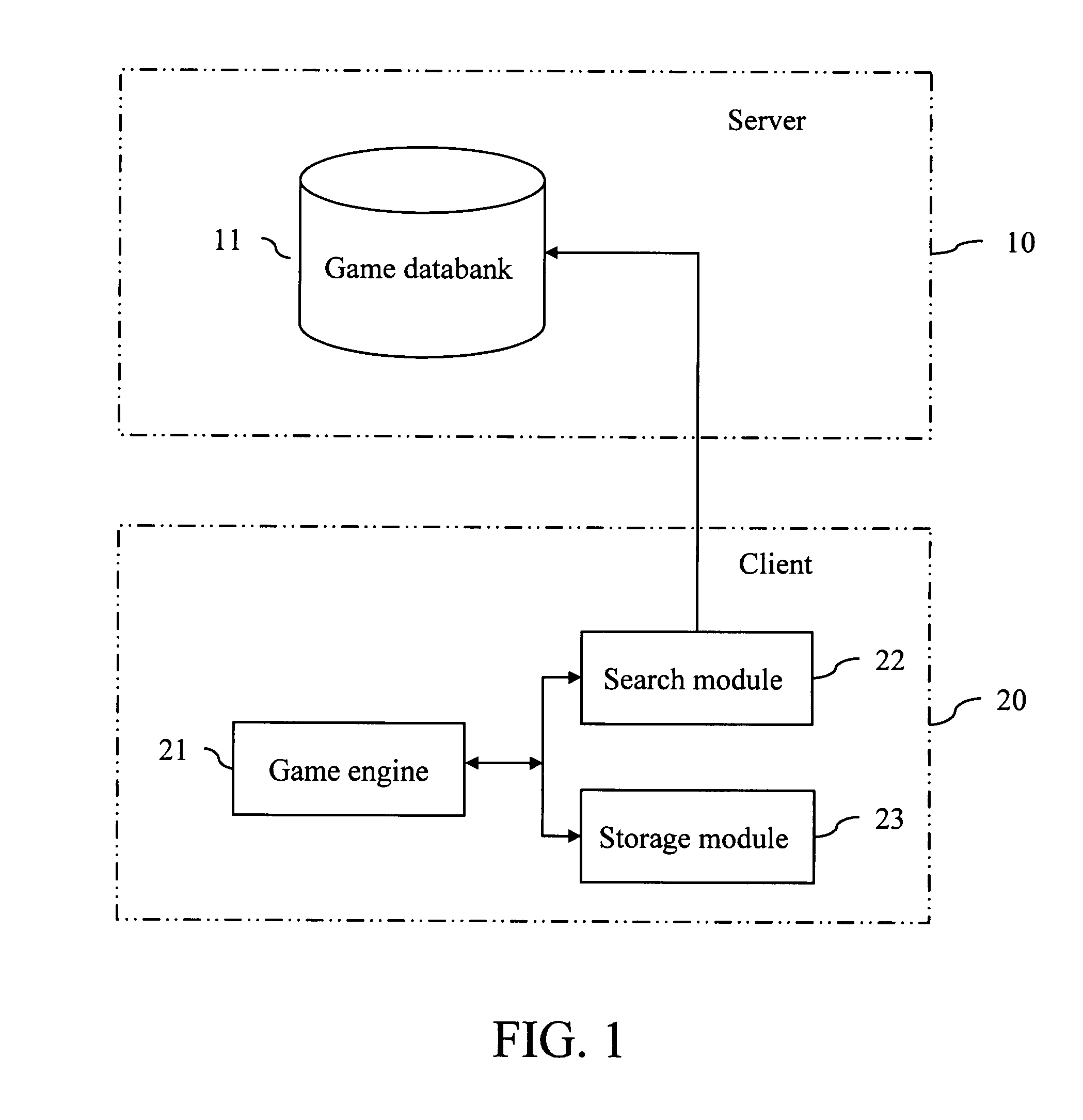
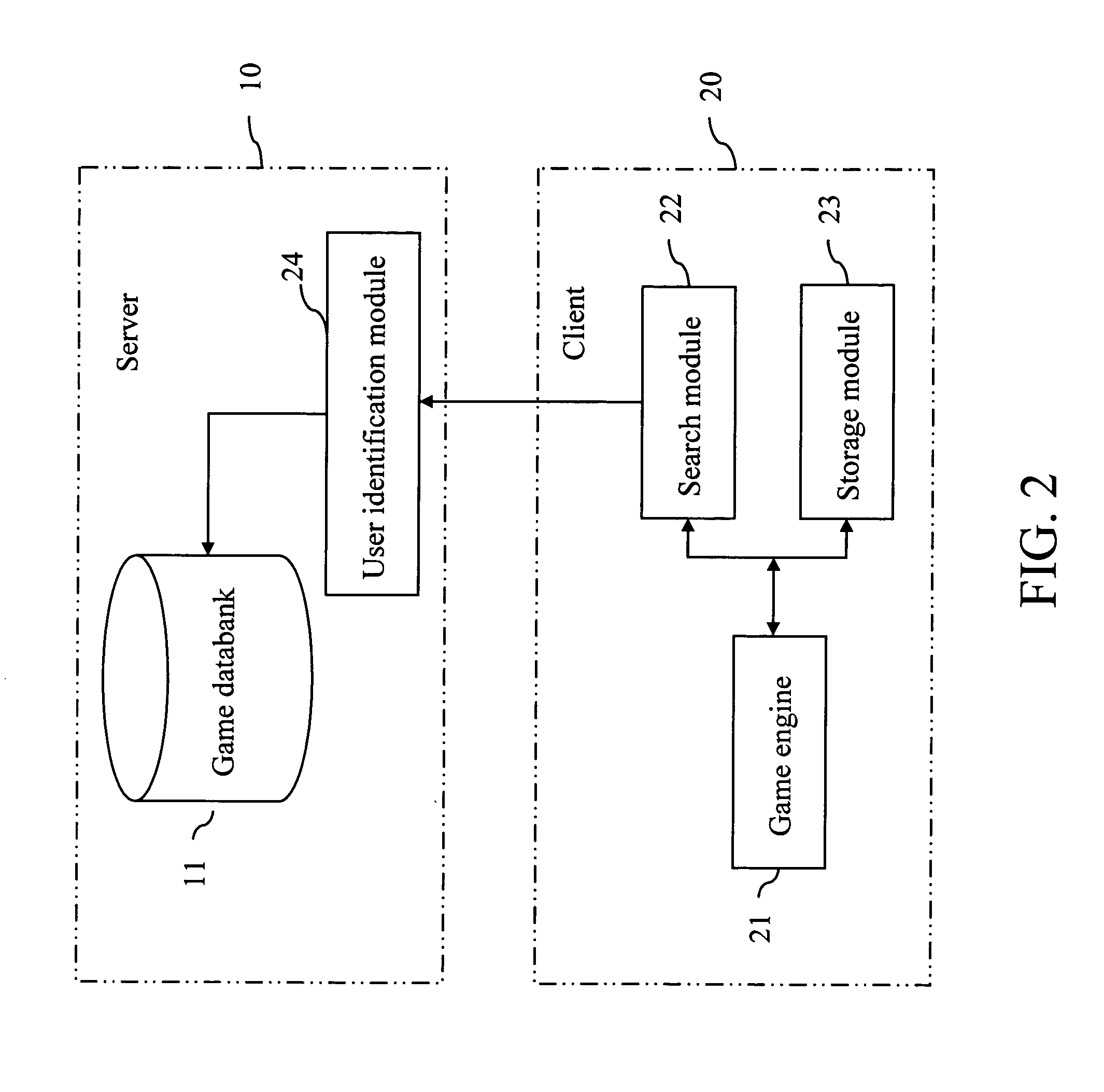
InactiveUS20060142087A1Reduce memory spacePrevents unauthorizedVideo gamesSpecial data processing applicationsData bankGame engine
A system and method for network-loading game data includes a server and a client. The server includes a databank for storing game data. The client includes a game engine; a search module to search corresponding game data from the databank according to control commands generated by the game engine; and a storage module to store the searched corresponding game data for the game engine to use. Therefore, the game engine and the game data are separated, and the game data are real-time loaded from the server when the client runs the game program.
Owner:INVENTEC CORP
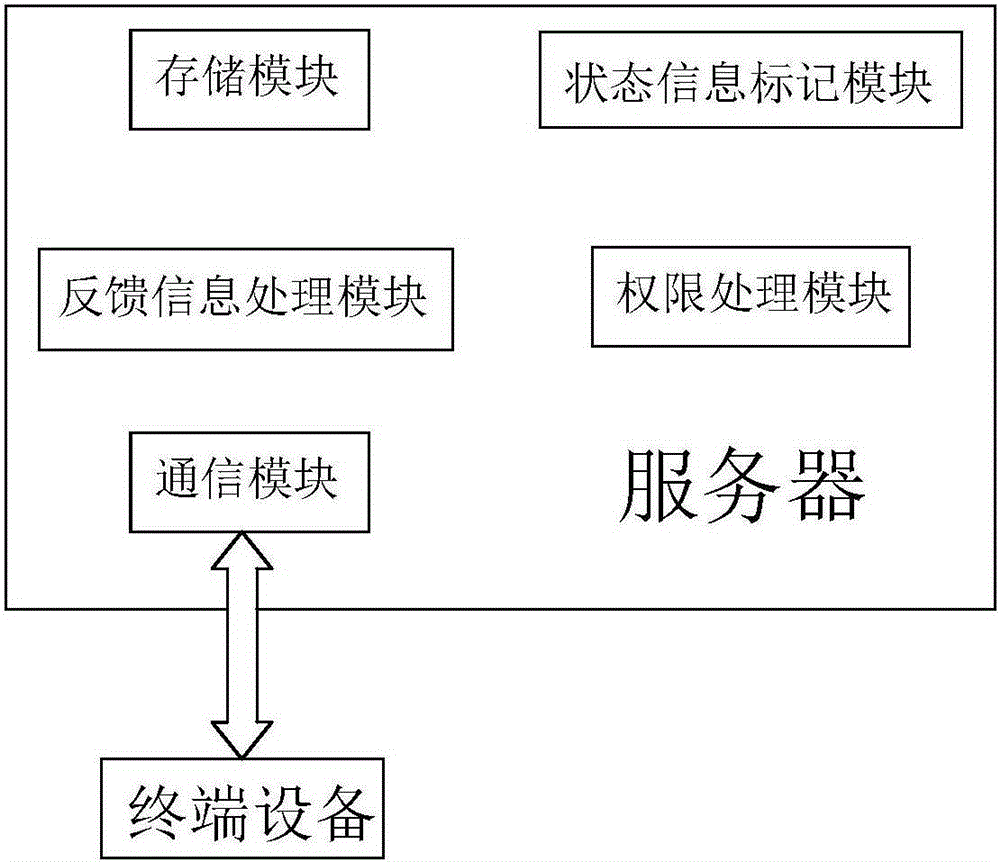
Digital product permission management method and server
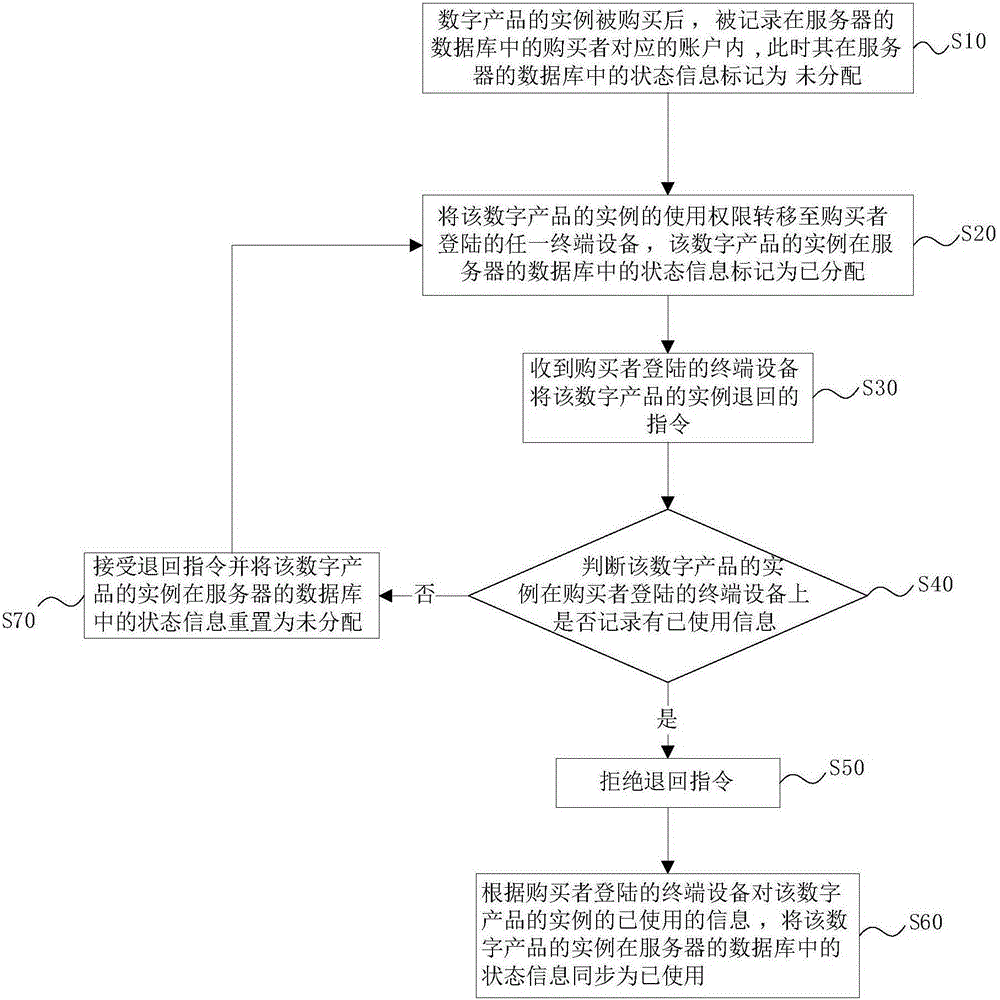
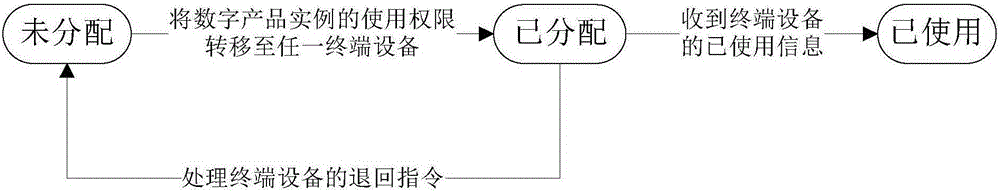
InactiveCN105184495AOptimize copyright protection measuresAvoid abuseResourcesTerminal equipmentComputer terminal
The invention provides a digital product permission management method and a digital product permission management server. When an embodiment of a digital product is purchased, state information of the digital product in a database of the digital product permission management server is marked as undistributed; the permission of the digital product can be transferred to arbitrary terminal equipment in which a purchaser is logged at the moment; the state information is marked as distributed when the permission is transferred to the terminal equipment; and the permission cannot be distributed to any terminal equipment at the moment. If the digital product is not used, a return command is fed back to the digital product permission management server, and the state information is reset to be undistributed; if the digital product is used, usage information is marked on the terminal equipment firstly, and the state information is marked as used when the terminal equipment establishes communication connection with the digital product permission management server; and the permission of the embodiment of the digital product is disabled. The digital product permission management method and the digital product permission management server provided by the invention can be used for protecting copyright of digital products, and effectively prevent theft phenomenon of the digital products.
Owner:ZHUHAI YOUTE SMART KITCHEN TECH CO LTD
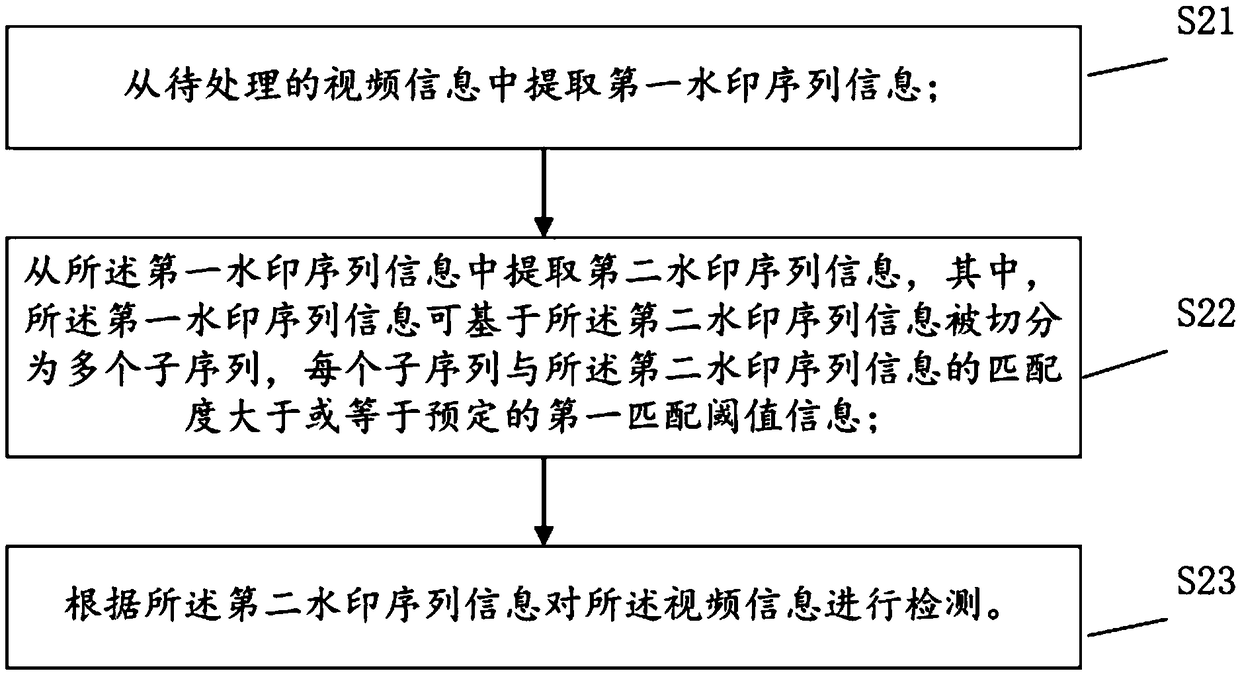
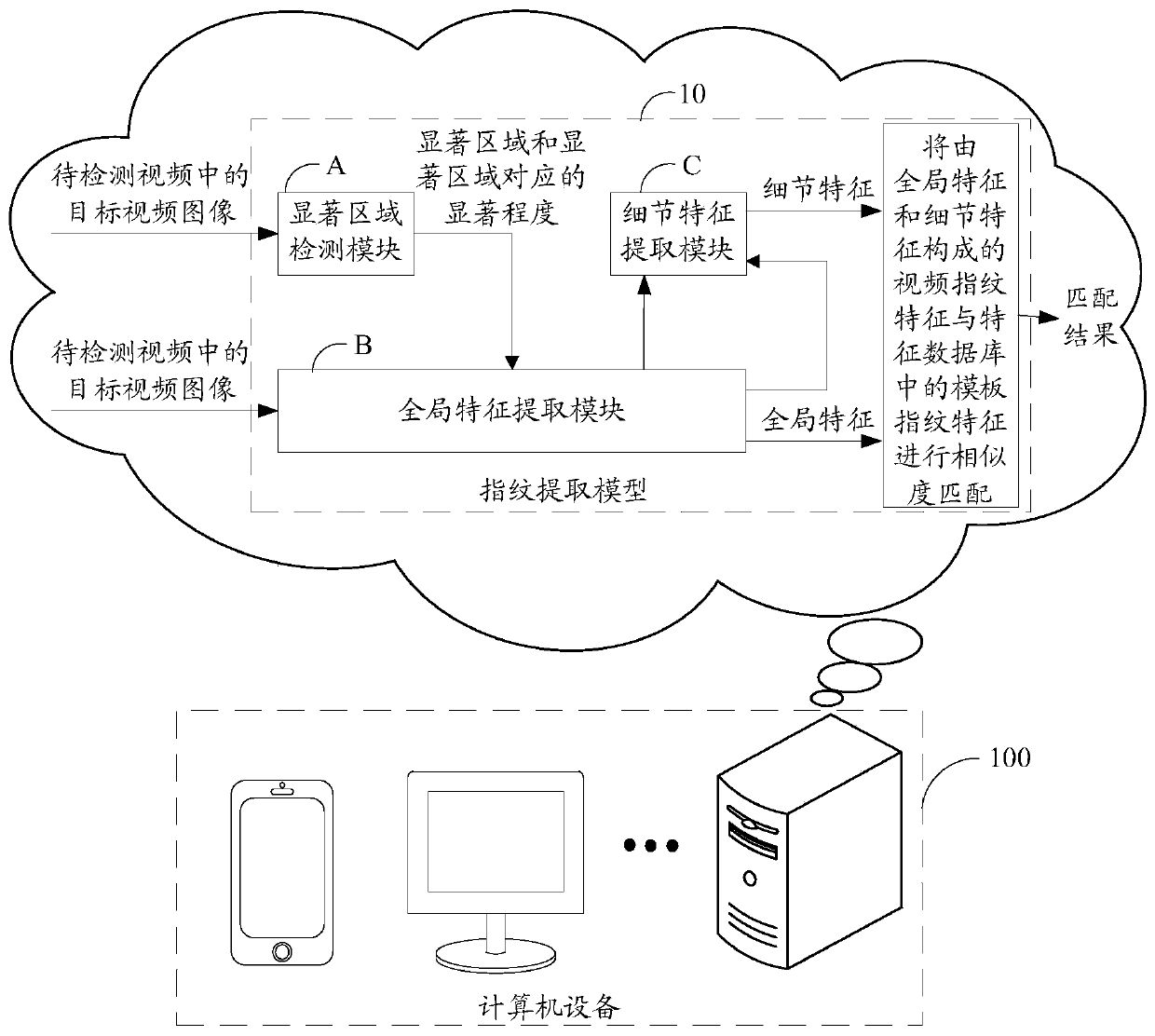
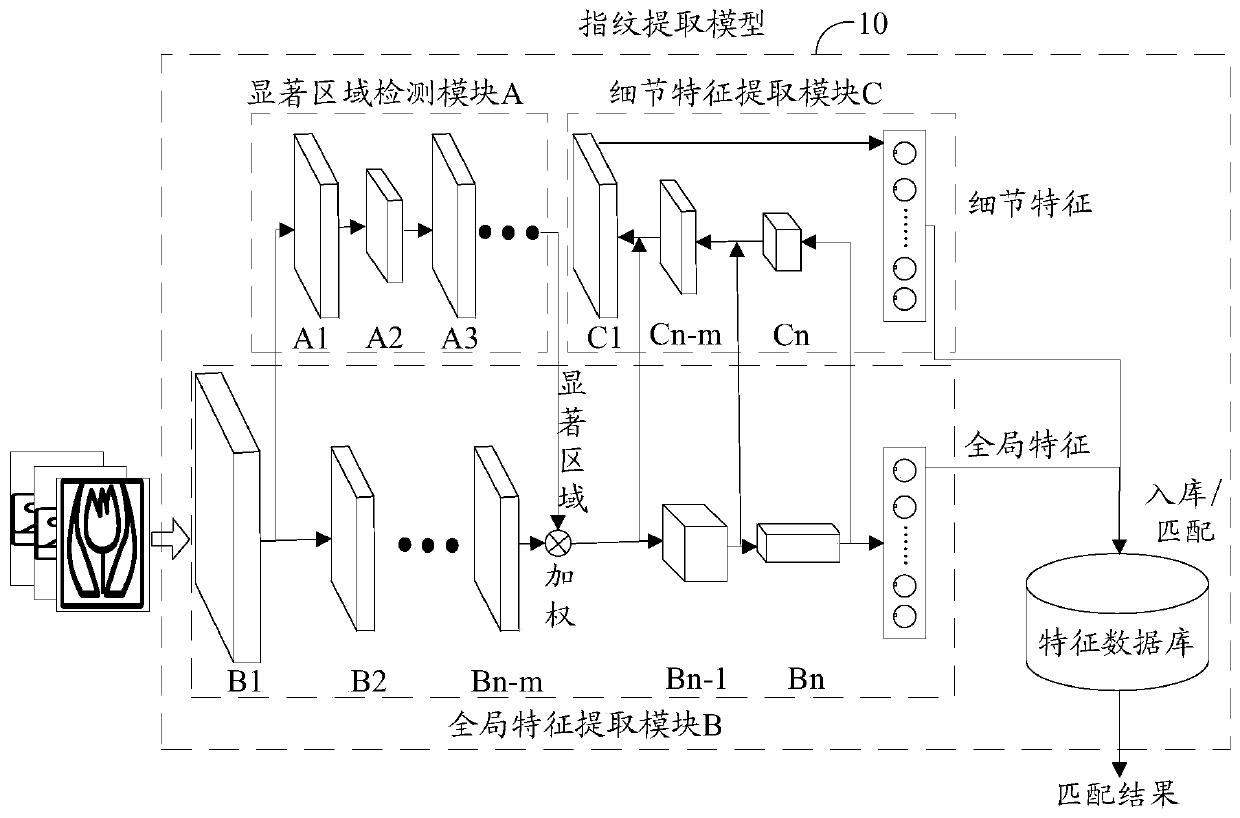
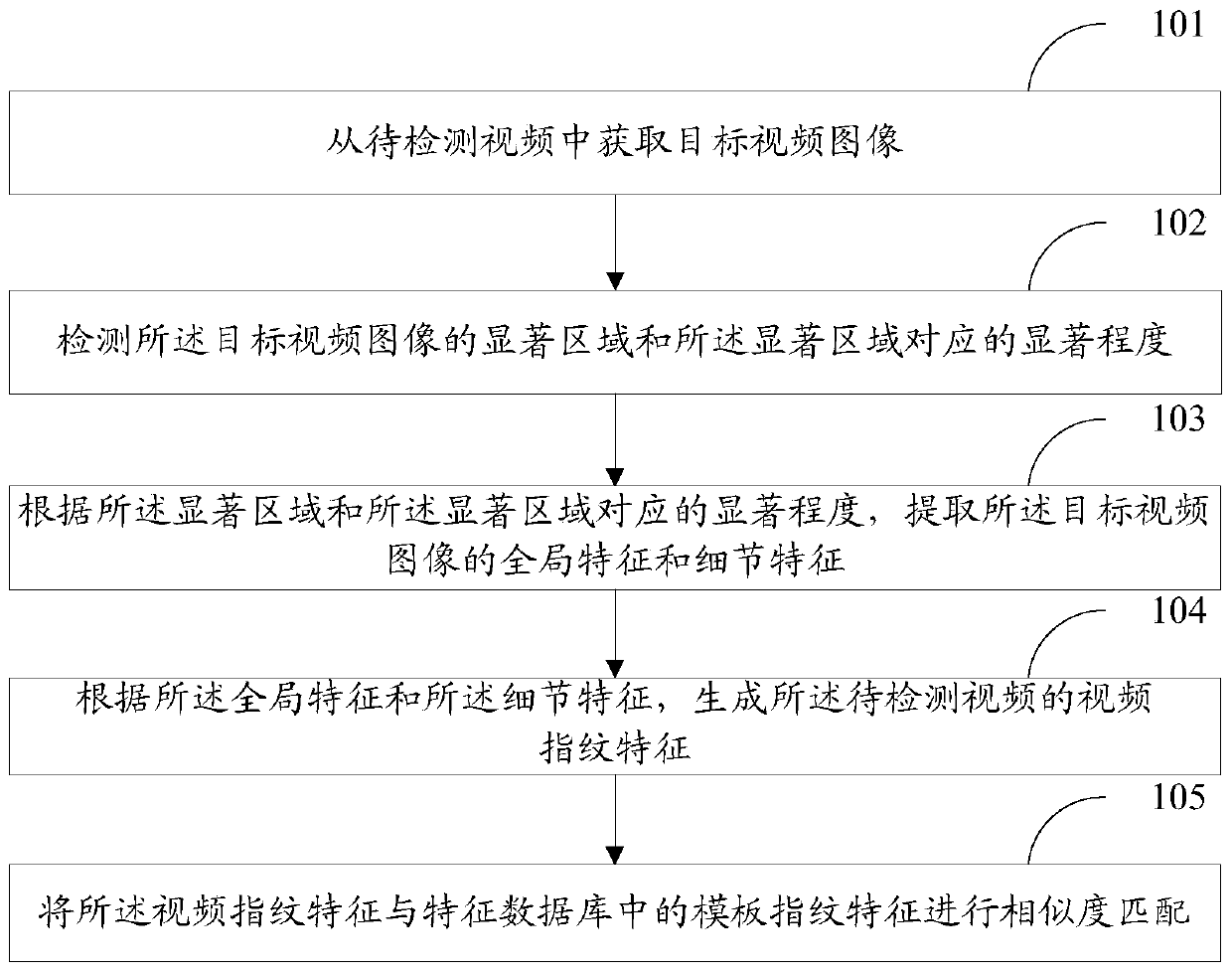
Video detection method and device, storage medium and computer equipment
PendingCN111444826AImprove accuracyReduce video repetition rateCharacter and pattern recognitionNeural architecturesBlack edgeComputer equipment
The embodiment of the invention discloses a video detection method and device, a storage medium and computer equipment. The method comprises the following steps: obtaining a target video image from the to-be-detected video, detecting a salient region of the target video image and a salient degree corresponding to the salient region; according to the salient region and the salient degree corresponding to the salient region, extracting global features and detail features of the target video image; according to the global features and the detail features, generating the video fingerprint featuresof the to-be-detected video, and finally performing similarity matching on the video fingerprint features and the template fingerprint features in the feature database, so that videos with frames, black edges, frosted glass and other complex scenes and videos with similar backgrounds and different main bodies can be effectively identified, and the video identification accuracy is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
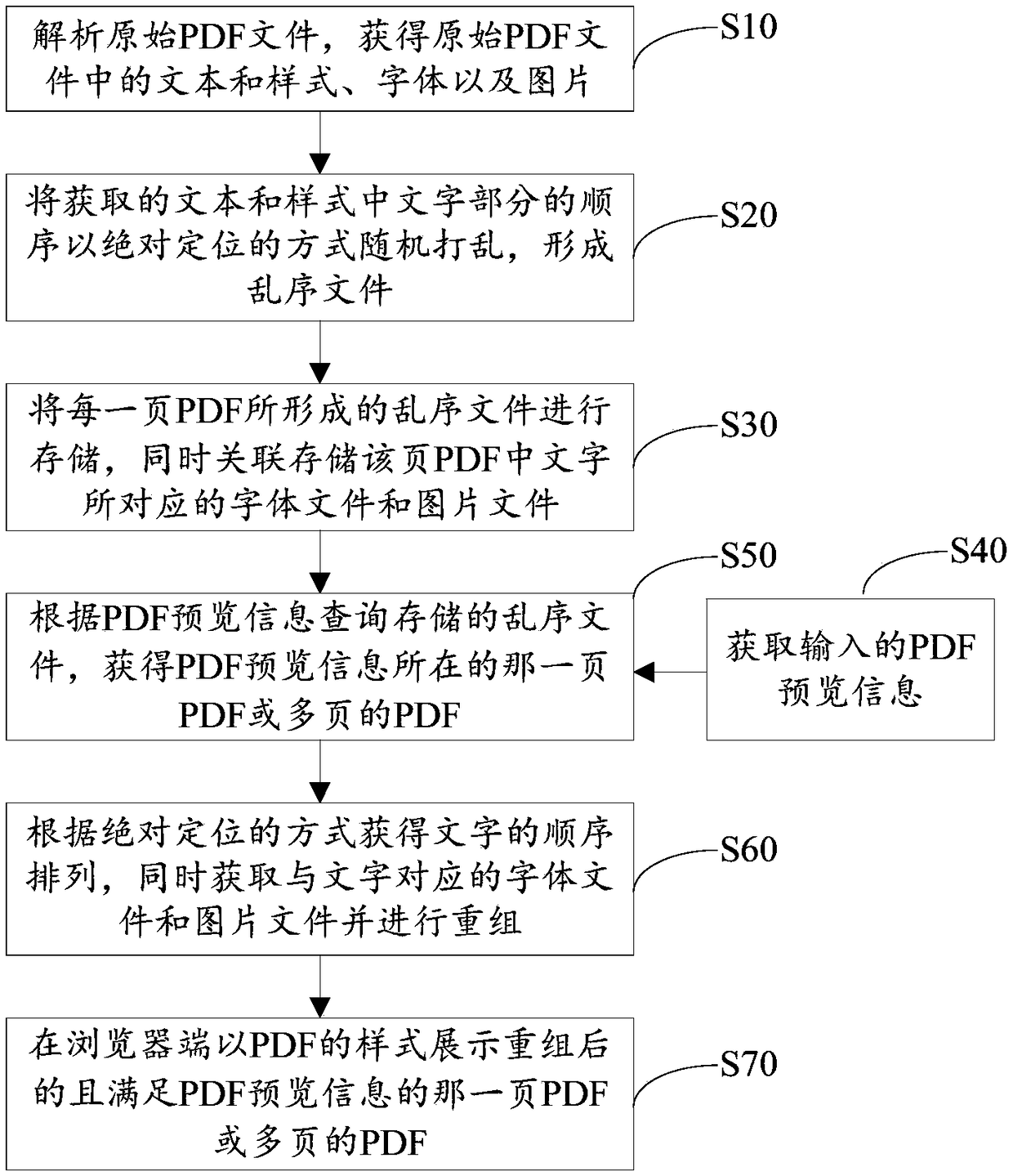
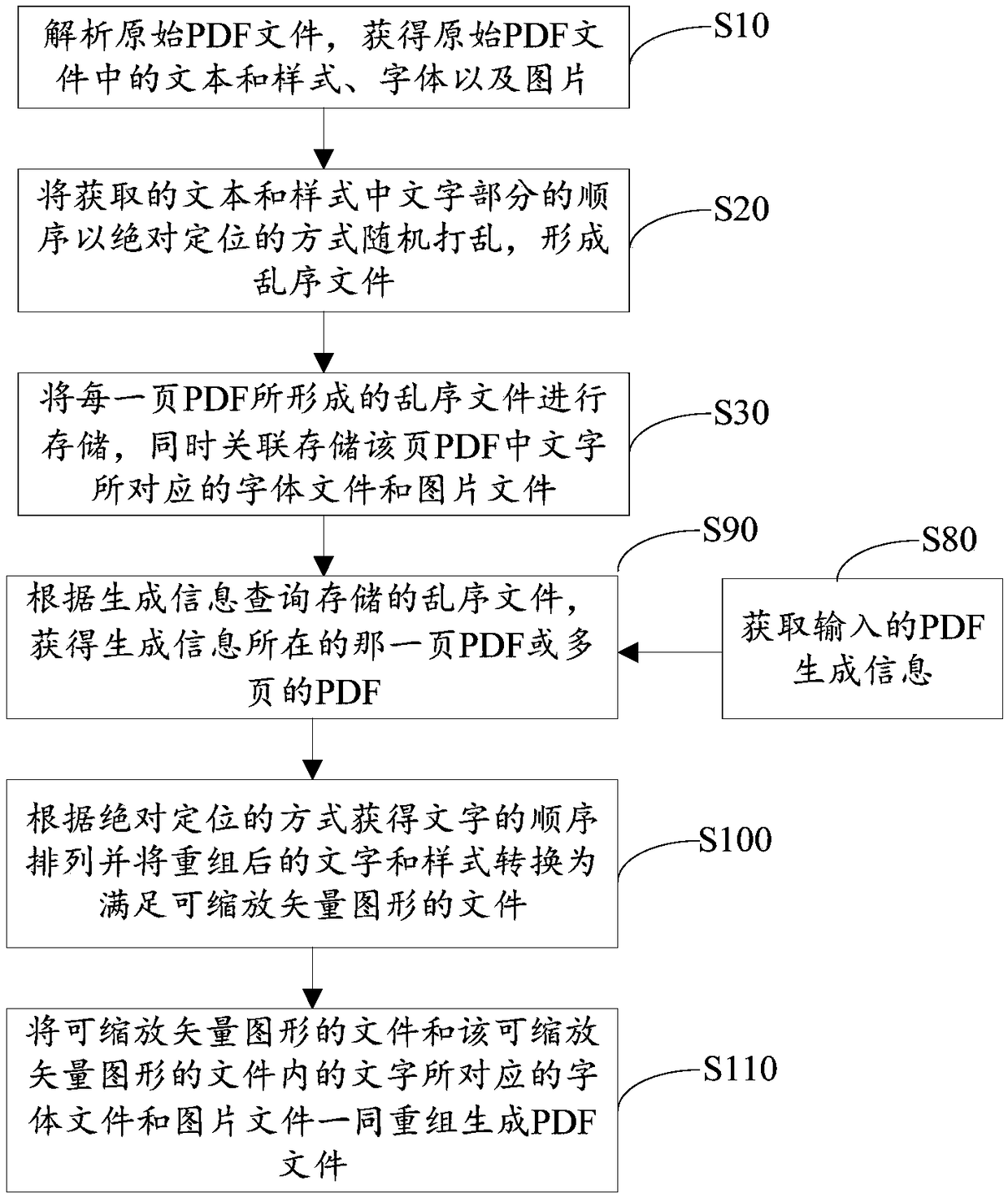
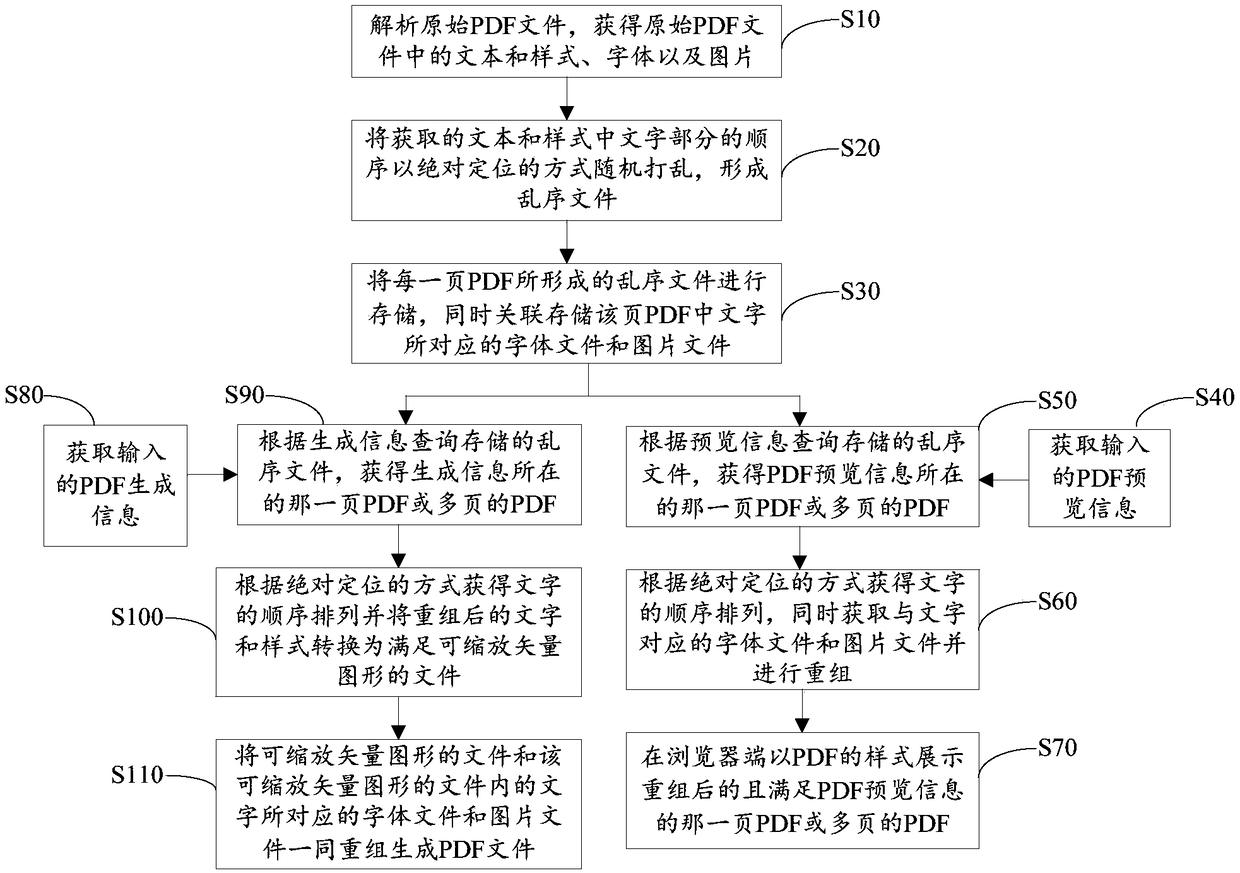
Method for previewing PDF file, method for generating PDF file and method for processing PDF file
ActiveCN109446490AAvoid crawlingStrengthen copyright protectionWeb data indexingText processingDatabaseAbsolute positioning
The invention provides a method for previewing a PDF file, a method for generating the PDF file and a method for processing the PDF file. The previewing method comprises the following steps of analyzing an original PDF file to obtain a text, a pattern, a font and a picture in the original PDF file; randomly scrambling the order of the obtained text and the text part in the style in an absolute positioning manner to form an out-of-order file; storing out-of-order files formed by each page of PDF, and associating and storing font files and picture files corresponding to characters in the page ofPDF; obtaining input PDF preview information; querying a stored out-of-order file according to the PDF preview information to obtain a PDF or a plurality of PDF pages on which the PDF preview information resides; according to the absolute positioning mode, obtaining the order of the characters, obtaining font files and picture files corresponding to the characters and reorganizing the font filesand picture files; and displaying the PDF or multi-page PDF which satisfies the preview information of the PDF in the form of PDF at the browser end.
Owner:杭州索骥数据科技有限公司
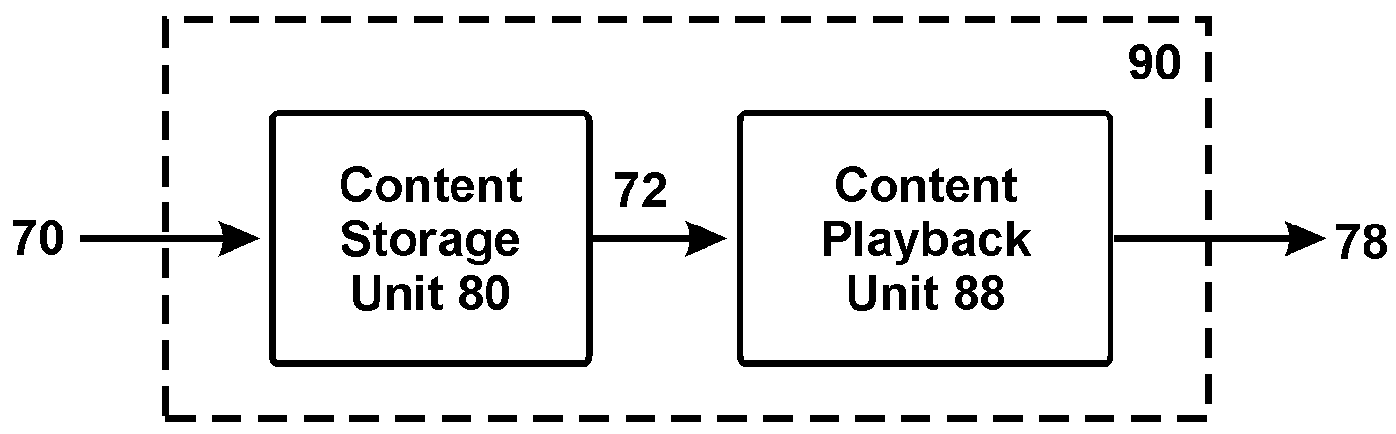
Tamper-Proof Content-Playback System Offering Excellent Copyright Protection
InactiveUS20060159424A1Strengthen copyright protectionImprove power efficiencyTelevision system detailsColor television signals processingData connectionSingle chip
To protect copyright, the present invention provides a tamper-proof content-playback system. Its content-playback unit has the following I / O characteristics: A) at least a portion of its content input(s) is encrypted digital signals; B) at least a portion of its content output(s) is non-digital (e.g. analog) or non-electrical (e.g. image) signals. Only secure data connections are allowed for decrypted contents inside the content-playback unit. Accordingly, its components are preferably integrated into: a single chip, a single package, or a chip / package-on-panel.
Owner:HU CHENMING +1
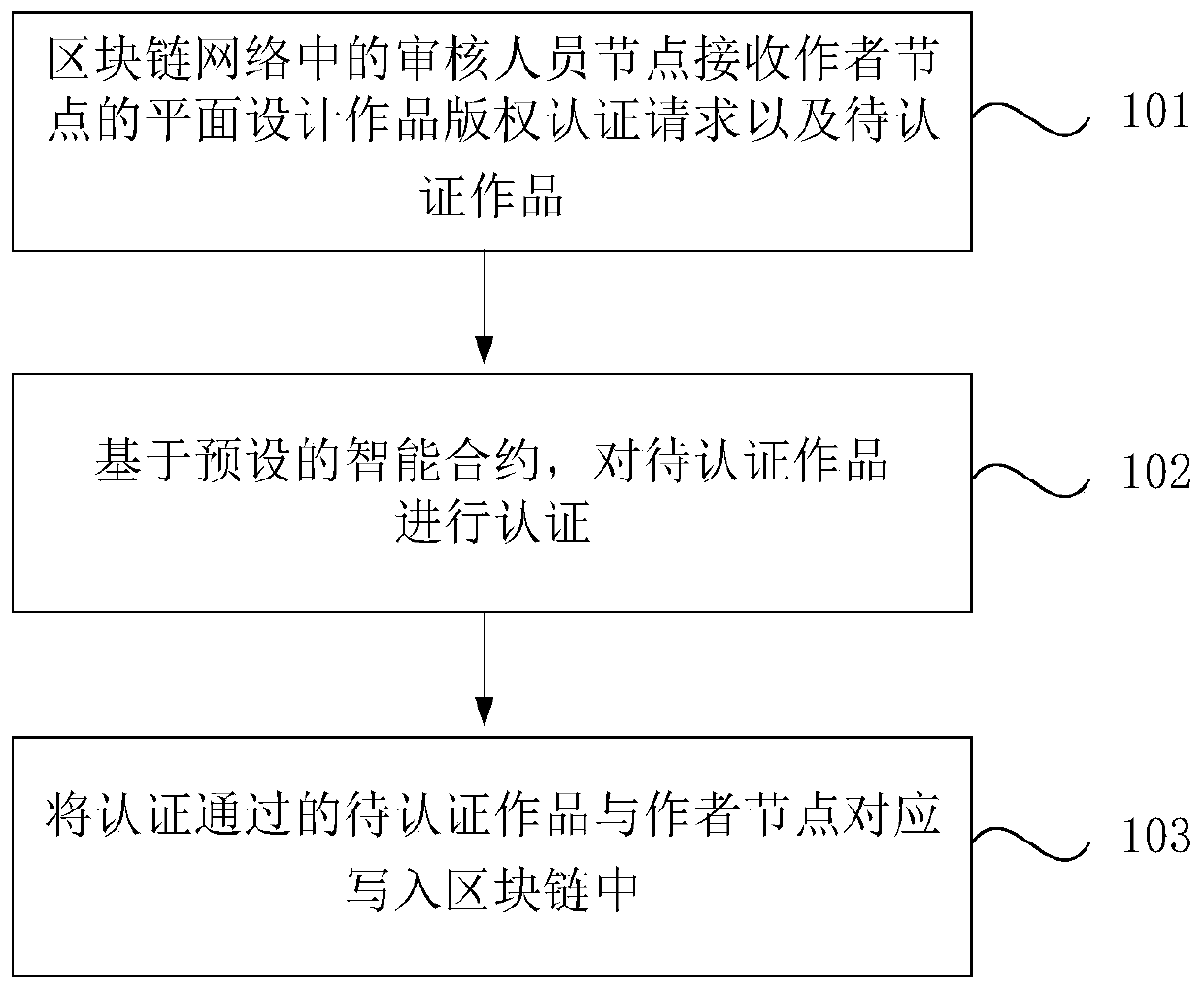
Blockchain-based graphic design work copyright evidence storage method and device and medium
PendingCN111274549AGuaranteed originalityGuaranteed correctnessDigital data protectionProgram/content distribution protectionSoftware engineeringData storing
The invention discloses a blockchain-based graphic design work copyright evidence storage method and device, and a medium, and aims to solve the problems that the development of graphic design relatedtools and the circulation of graphic design works reduce the plagiarism difficulty of the graphic design works and are not beneficial to copyright protection of the graphic design works. The method comprises the following steps: receiving a graphic design work copyright authentication request of an author node and a work to be authenticated by an auditor node in a blockchain network; authenticating the work to be authenticated based on a preset intelligent contract; and correspondingly writing the authenticated work to be authenticated and the author node into a block chain. According to themethod, on the basis of ensuring that the graphic design works have certain originality, the correctness and authenticity of copyright ownership of the graphic design works can be ensured through thecharacteristics of safety and tamper resistance of data stored in the blockchain, and the copyright ownership of the graphic design works is used as a copyright ownership certificate of the graphic design works, so that subsequent data tracing is facilitated.
Owner:浪潮云洲工业互联网有限公司
Digital content copyright protection method and device based on block chain platform
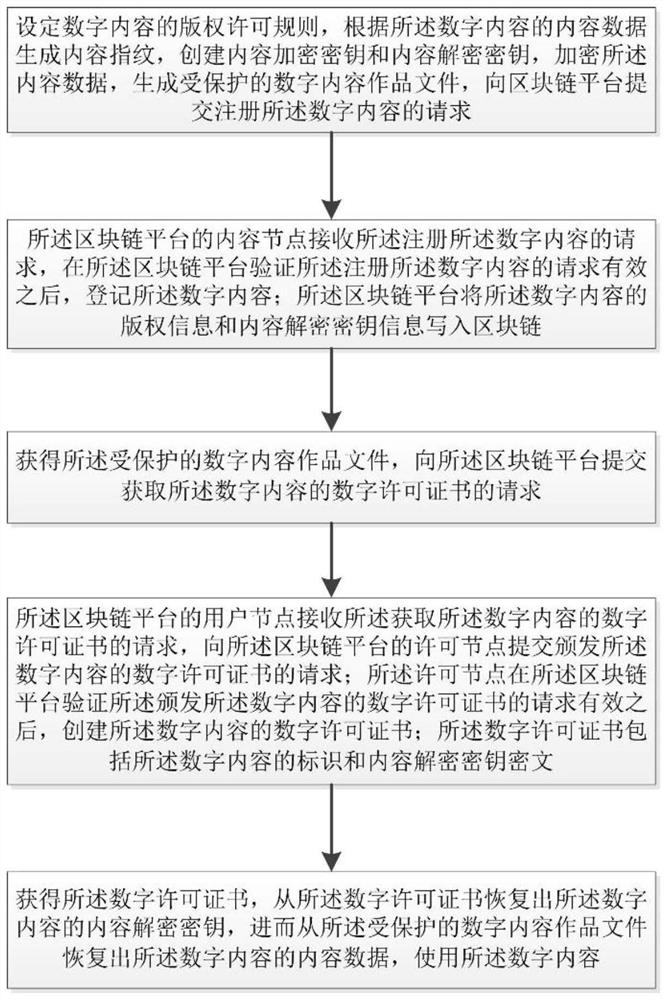
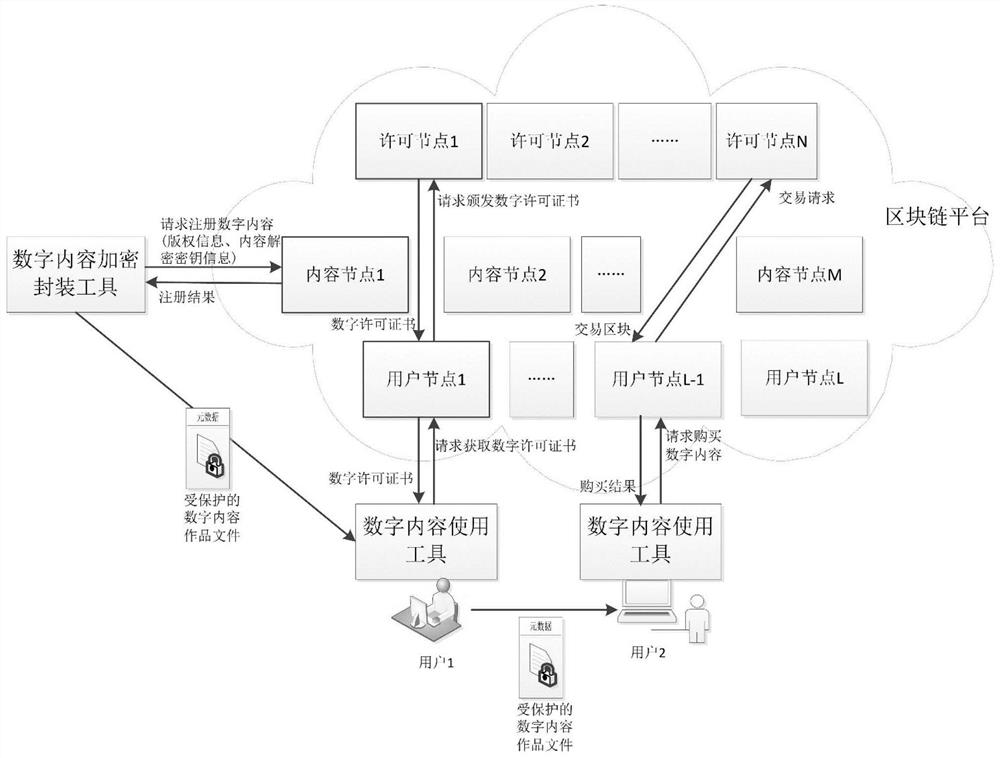
PendingCN112364305AImprove effectiveness and convenienceStrengthen copyright protectionDatabase distribution/replicationDigital data protectionBlockchainEngineering
The invention discloses a digital content copyright protection method and device based on a block chain. The method comprises the steps that a digital content encryption packaging tool encrypts digital content to generate a protected digital content work file; the blockchain platform registers the digital content, and writes copyright information and content decryption key information of the digital content into the blockchain; the digital content use tool obtains the protected digital content work file, and requests a digital license of the digital content from the blockchain platform; the block chain platform creates a digital license; the digital content use tool obtains a digital license and uses the digital content. Based on a super distribution principle method, the copyright information and the content decryption key are managed by adopting a block chain, so that the dependence of a traditional copyright protection system on a central server is overcome, and the credible management of the digital content copyright and the digital license is achieved.
Owner:PEKING UNIV
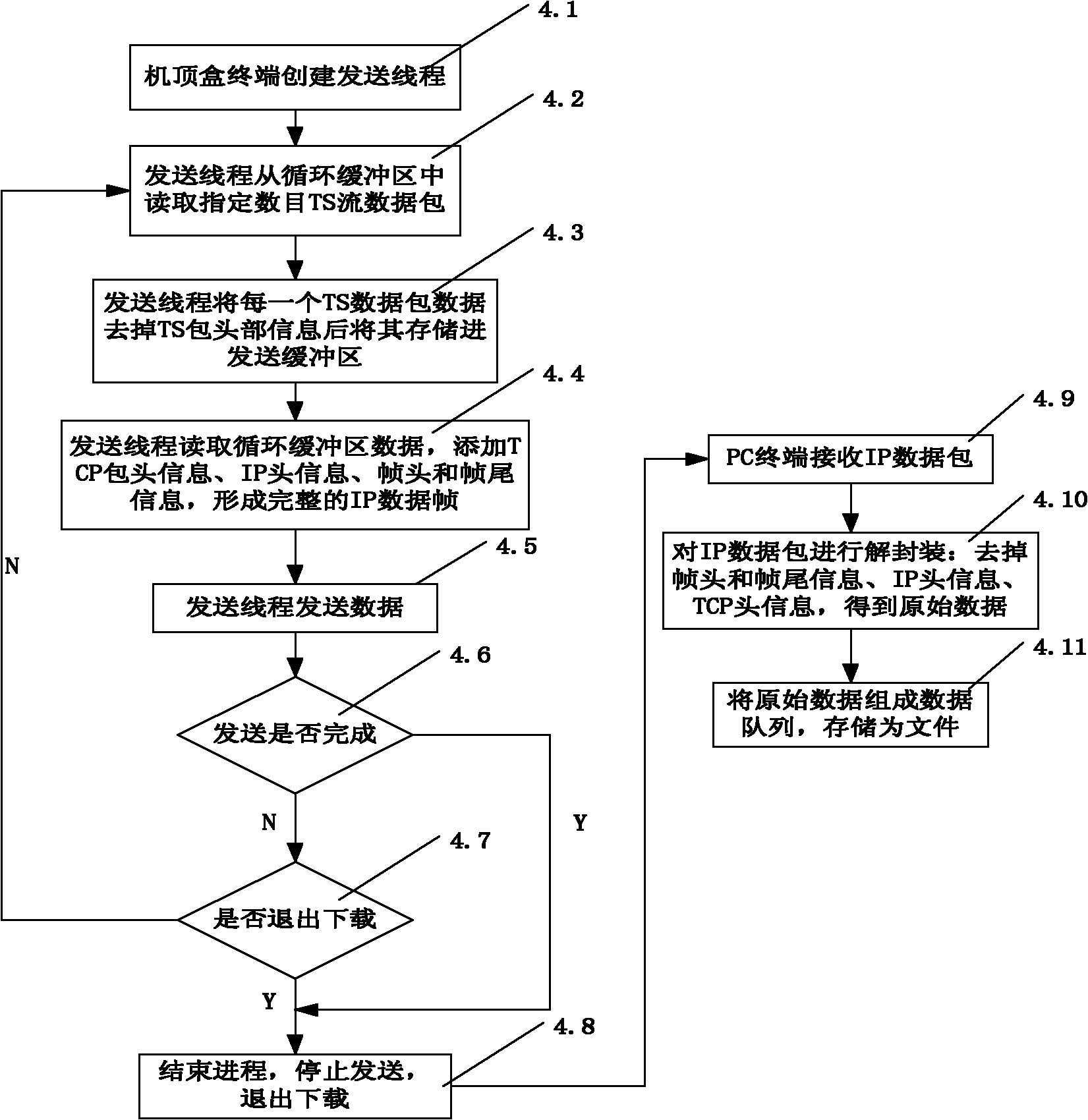
Quick downloading method for large-data documents based on broadcasting television network and communication network
InactiveCN101860543ASolve the problem of difficult downloadShorten the timeTwo-way working systemsTransmissionStructure of Management InformationThe Internet
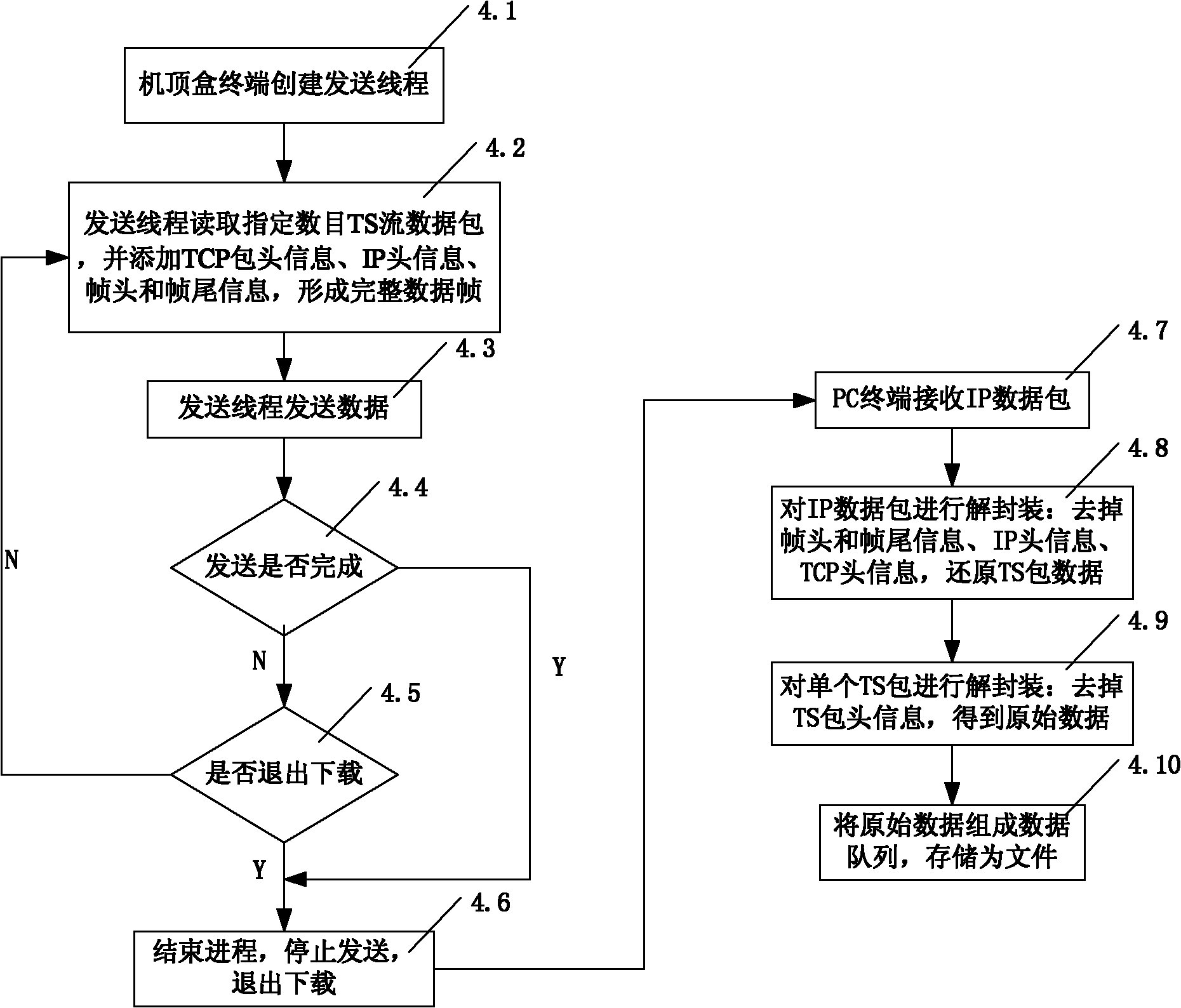
The invention relates to a quick downloading method for large-data documents based on a broadcasting television network and a communication network. The method comprises the steps of: (1) connection: accessing a PC terminal into a broadcasting television network through a set-top box, wherein the terminal of the set-top box is connected with a front servicing device through the broadcasting television network and the communication network, a downloading customer terminal is arranged in the PC terminal, the front servicing device comprises an user accessing managing submodule, a content managing submodule and a content distributing submodule, the content managing submodule stores document resources, and the content managing submodule is connected with an internet; (2) service requesting; (3) service responding; and (4) receiving: receiving the signal containing documents from the broadcasting television network by the set-top box, processing the signal and then sending the signal to the PC terminal. The invention has the advantages of simple and compact structure, low cost, simple realizing principle, easy implementation, great enhancement of downloading speed, and the like.
Owner:龙山
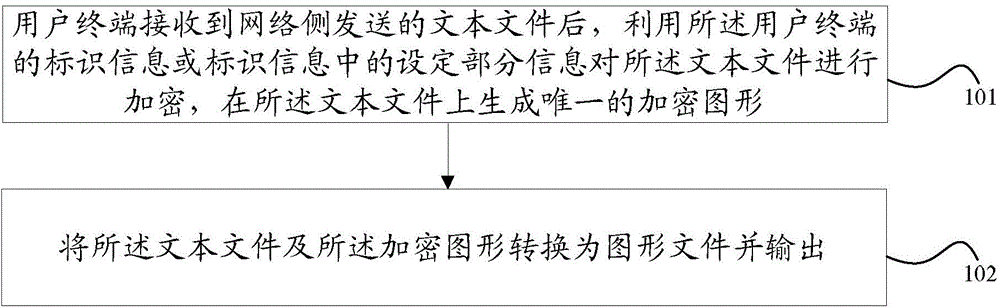
Text encryption method and device
InactiveCN105447401AEasy to readStrengthen copyright protectionDigital data protectionProgram/content distribution protectionText fileComputer hardware
The embodiment of the invention discloses a text encryption method and device. The method comprises the following steps: after a user terminal receives a text file sent by a network side, conducing encryption on the text file by utilizing identification information of the user terminal or set part information in the identification information, and generating a unique encrypted image on the text file; converting the text file and the encrypted image into an image file to be outputted. Or, the method comprises the following steps: when the network side sends the text file to the user terminal, conducing encryption on the text file by utilizing the identification information of the user terminal or the set part information in the identification information, and generating the unique encrypted image on the text file; converting the text file and the encrypted image into a graphic file, and sending the graphic file to the user terminal. According to the embodiment, through the setting of a graphic password on the text file, the identity of an infringer can be accurately positioned.
Owner:CHINA MOBILE COMM GRP CO LTD
Method and device for sharing content protected by digital copyright
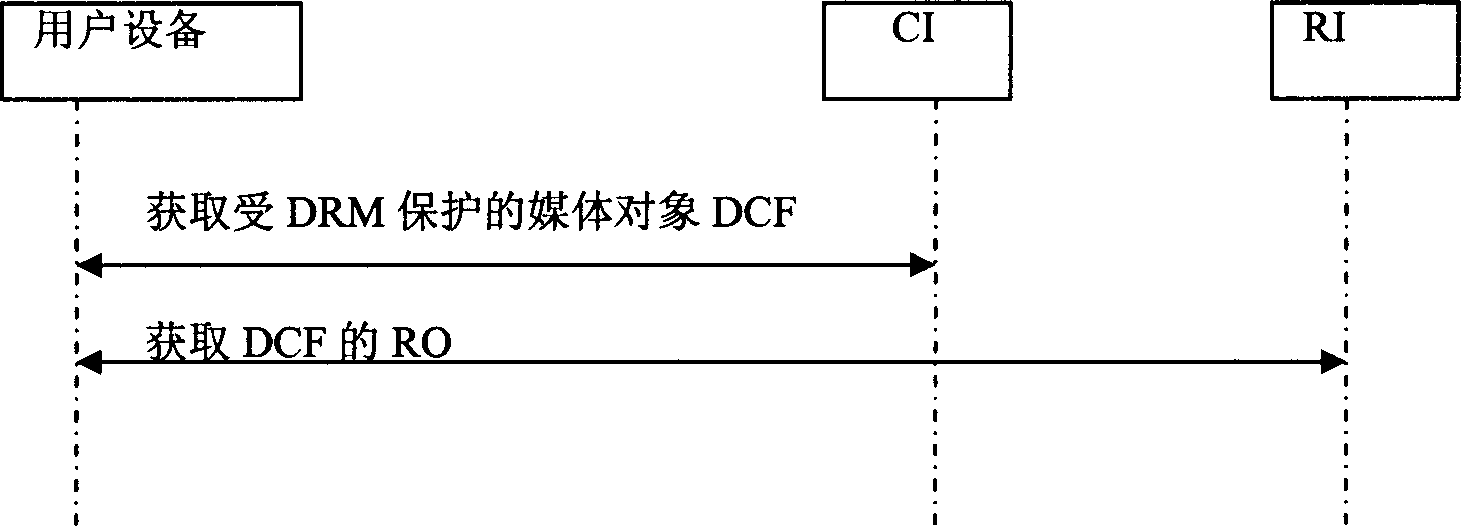
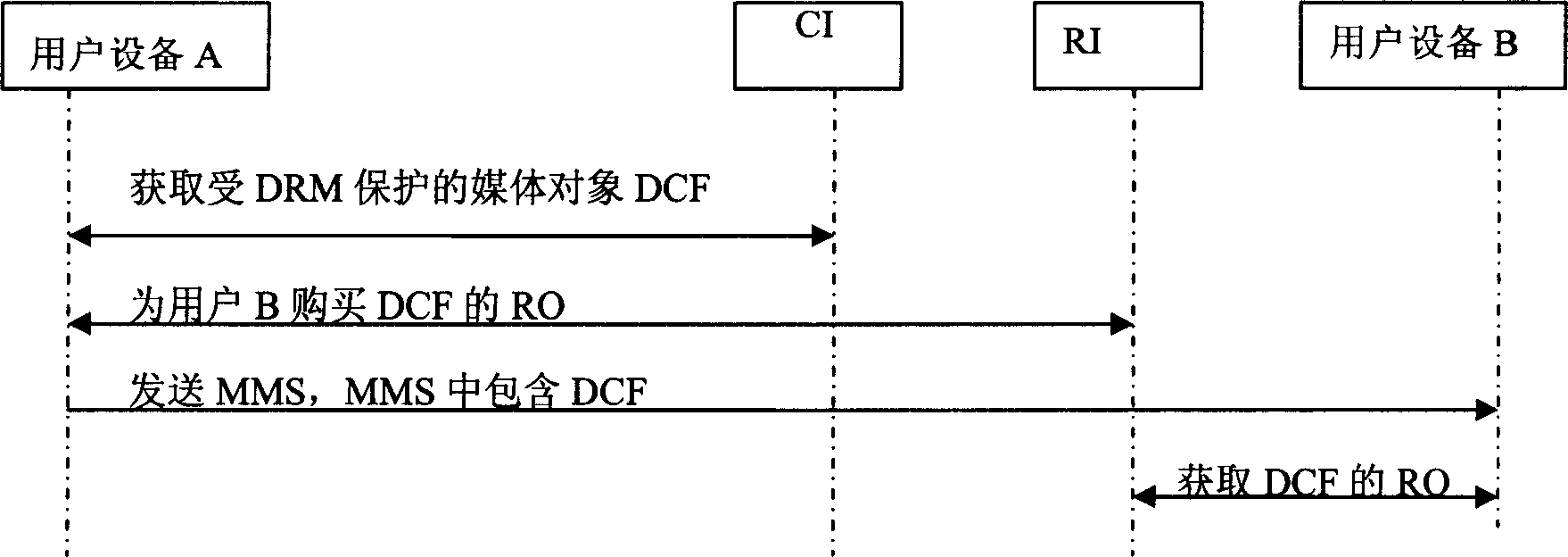
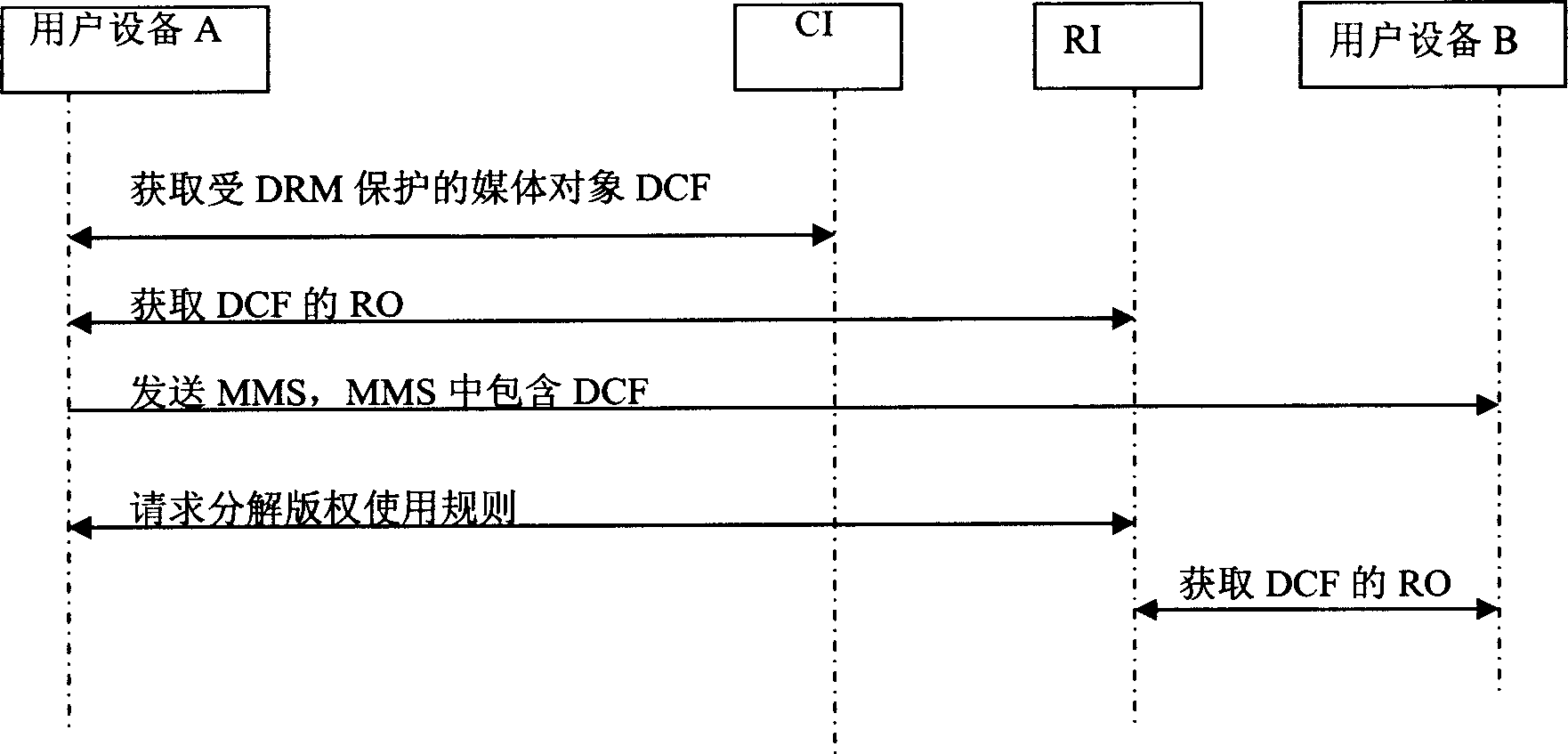
InactiveCN1858765AStrengthen copyright protectionBig spaceProgram/content distribution protectionData switching networksUser deviceComputer security
This invention discloses a method and a device for sharing digital copyright protection content including: User device A sends the content protected by digital copyright DRM protection to user device B via MMS, B receives said MMS and analyses the content protected by DRM to get the copyright object RO of the content protected by DRM and use the content protected by DRM based on the rule in RO.
Owner:HUAWEI TECH CO LTD
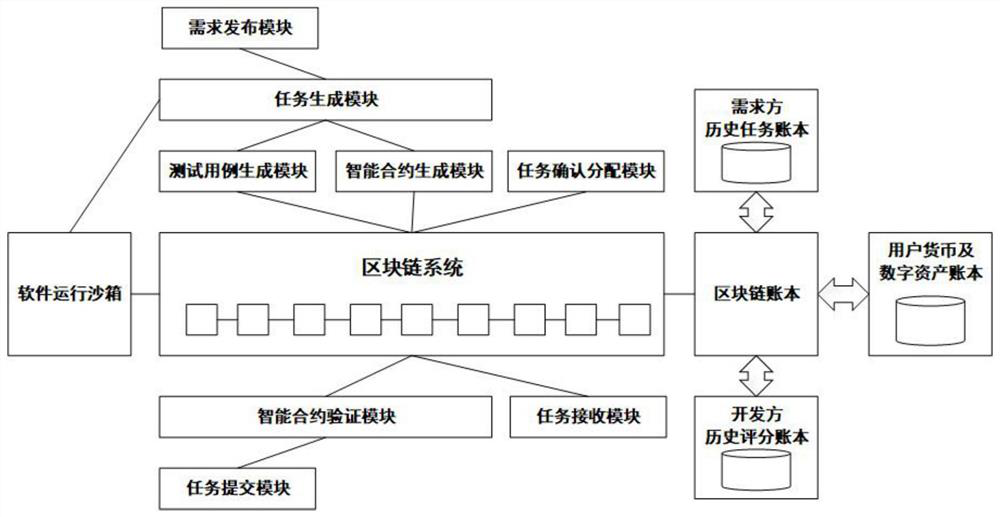
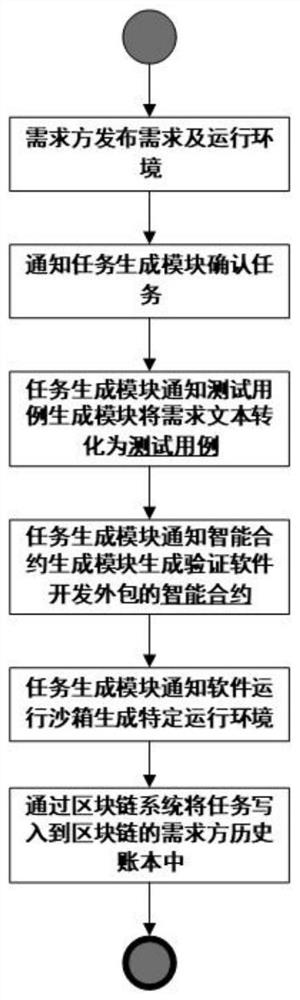
Block chain-based software development outsourcing control system and implementation method
ActiveCN113344535AStrengthen copyright protectionIncrease credibilitySoftware maintainance/managementSoftware testing/debuggingPrivacy protectionReliability engineering
The invention relates to a block chain-based software development outsourcing control system and an implementation method. The system comprises a demand release module, a test case generation module, an intelligent contract generation module, a software operation sandbox, a task generation module, a task confirmation distribution module and a block chain system. According to the method, all nodes participate in task generation, code verification and capability scoring on the basis of decentralization and non-tampering characteristics of a block chain technology, so that the authenticity of a software development outsourcing task, the fairness of software quality evaluation and the authority of software development outsourcing completion capability evaluation of a developer are improved, and therefore, a developer is effectively stimulated to improve the participation degree and the completion degree; and the characteristics of traceability and privacy protection of block chain account book data are utilized, each change of user currency and software copyright is encrypted and recorded, currency assets and software copyright are protected, and the data credibility is improved. The invention further discloses an implementation method of the block chain-based software development outsourcing control system.
Owner:SHANGHAI DEV CENT OF COMP SOFTWARE TECH
Information processing system, information processing device, and program
InactiveCN1722053APrevent unauthorized accessStop the leakDigital data processing detailsUser identity/authority verificationInformation processingPassword
Owner:SONY CORP
Method of and apparatus for encrypting digital map
ActiveCN100428258CStrengthen copyright protectionImprove the efficiency of copyright verificationProcessor architectures/configurationProgram/content distribution protectionInformation securityComputer science
This invention provides one pair of electron map coding method and device in information safety field, which comprises the following steps: a, catching characteristic information from map; b, adding extra information at relative position of the said electron map and establishing the said information and the characteristic information; c, integrating the above information into watermark information for storage. This invention generates watermark information to code the electron map.
Owner:北京百度智图科技有限公司
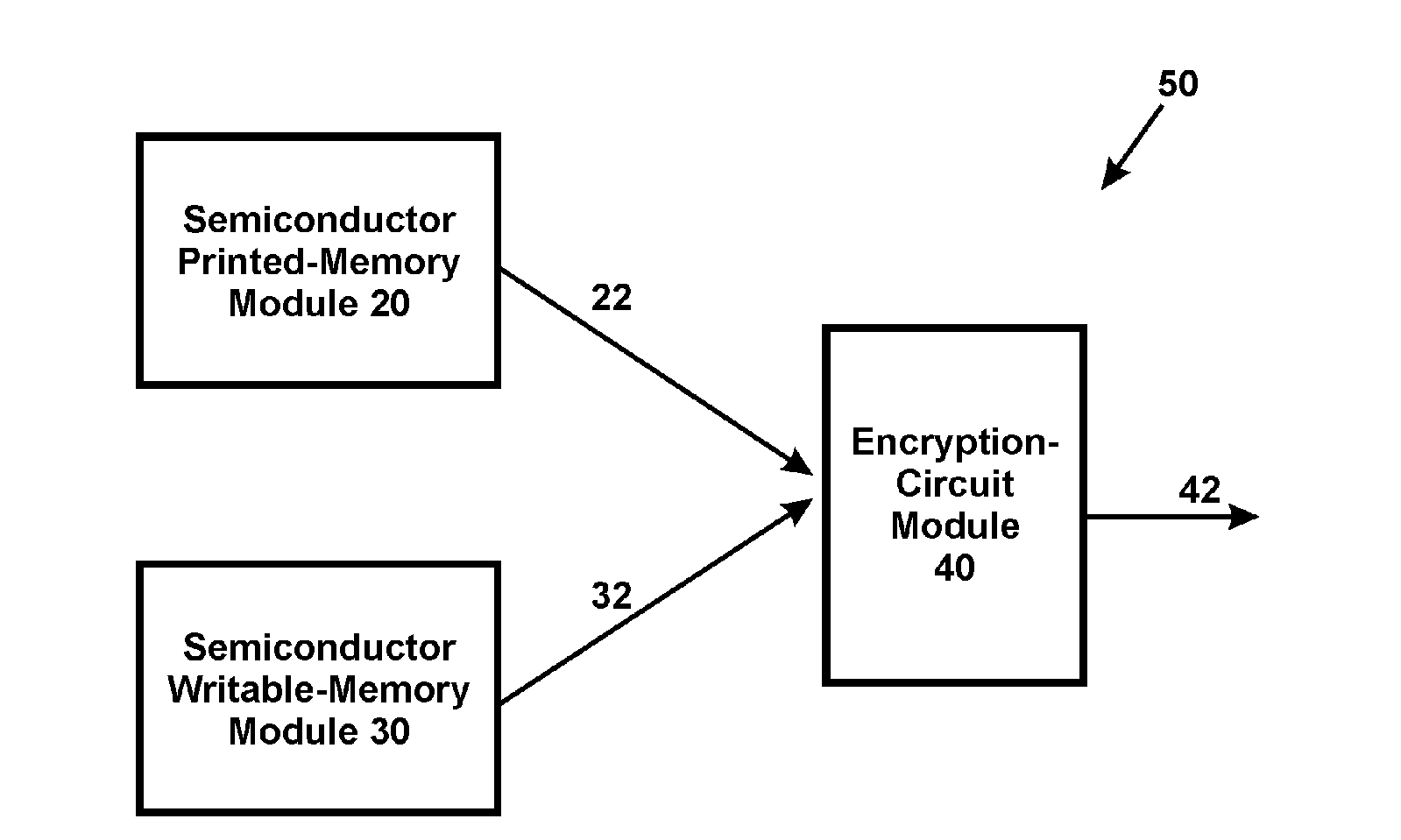
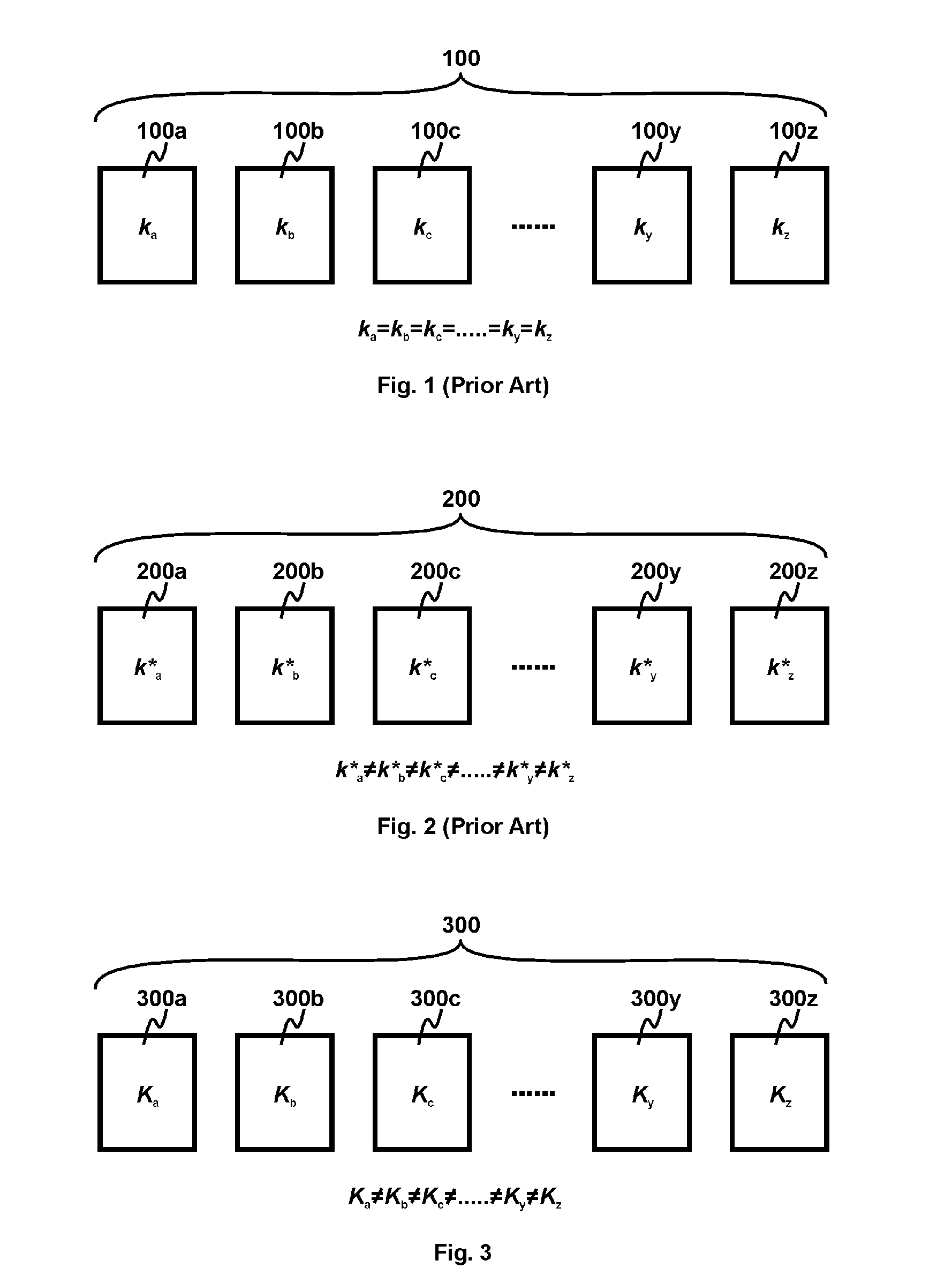
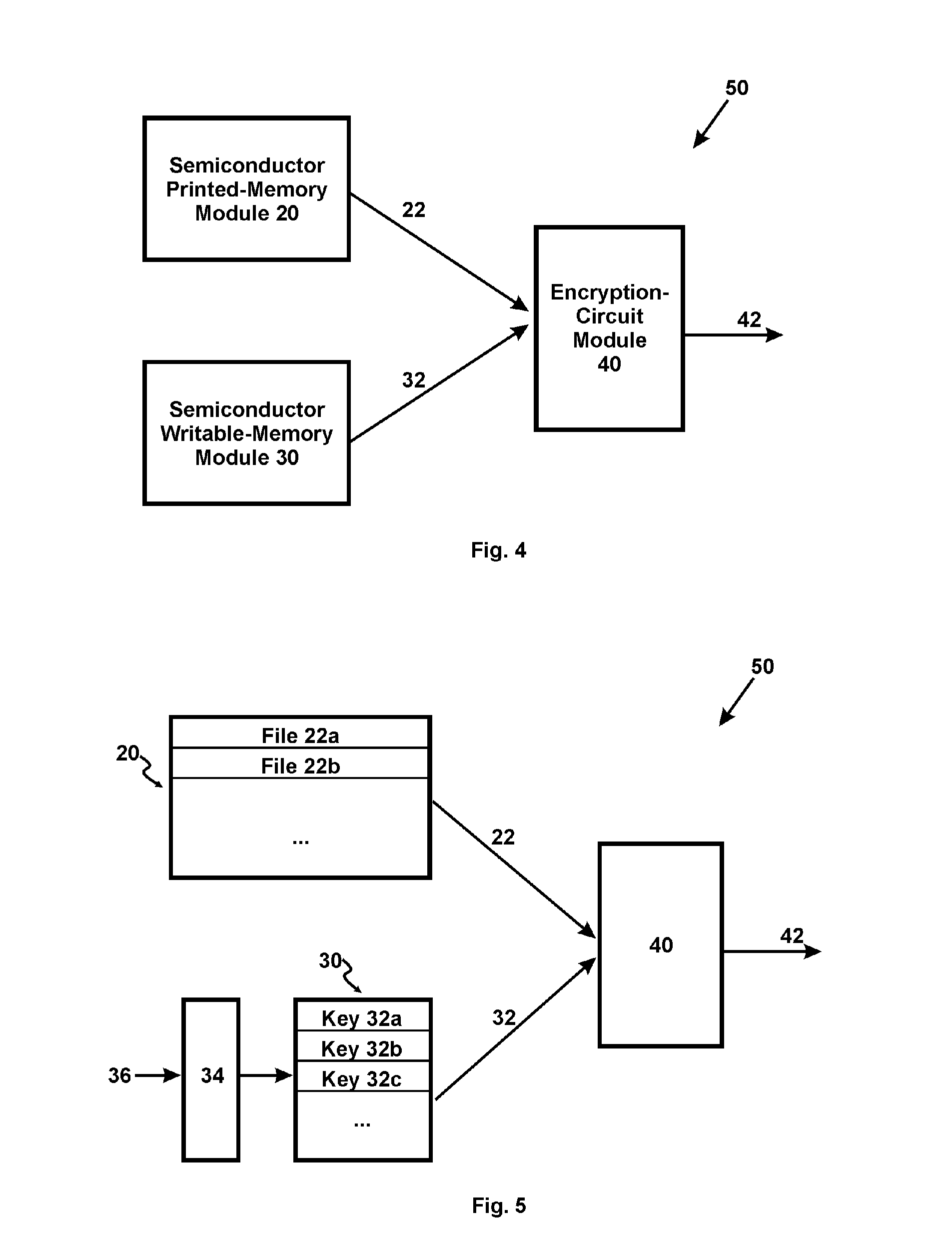
Secure Printed Memory
InactiveUS20150317255A1Strengthen copyright protectionProtected contentMemory architecture accessing/allocationSolid-state devicesComputer moduleEncryption
Copyright protection for printed memory is more difficult than writable memory. Accordingly, the present invention discloses a secure printed memory. Its printed-memory module stores the same content data for all devices in a same family; its writable-memory module stores different encryption keys for different devices in the same family. Because different devices in the same family are encrypted with different keys, compromising a single device does not compromise other devices in the family.
Owner:CHENGDU HAICUN IP TECH
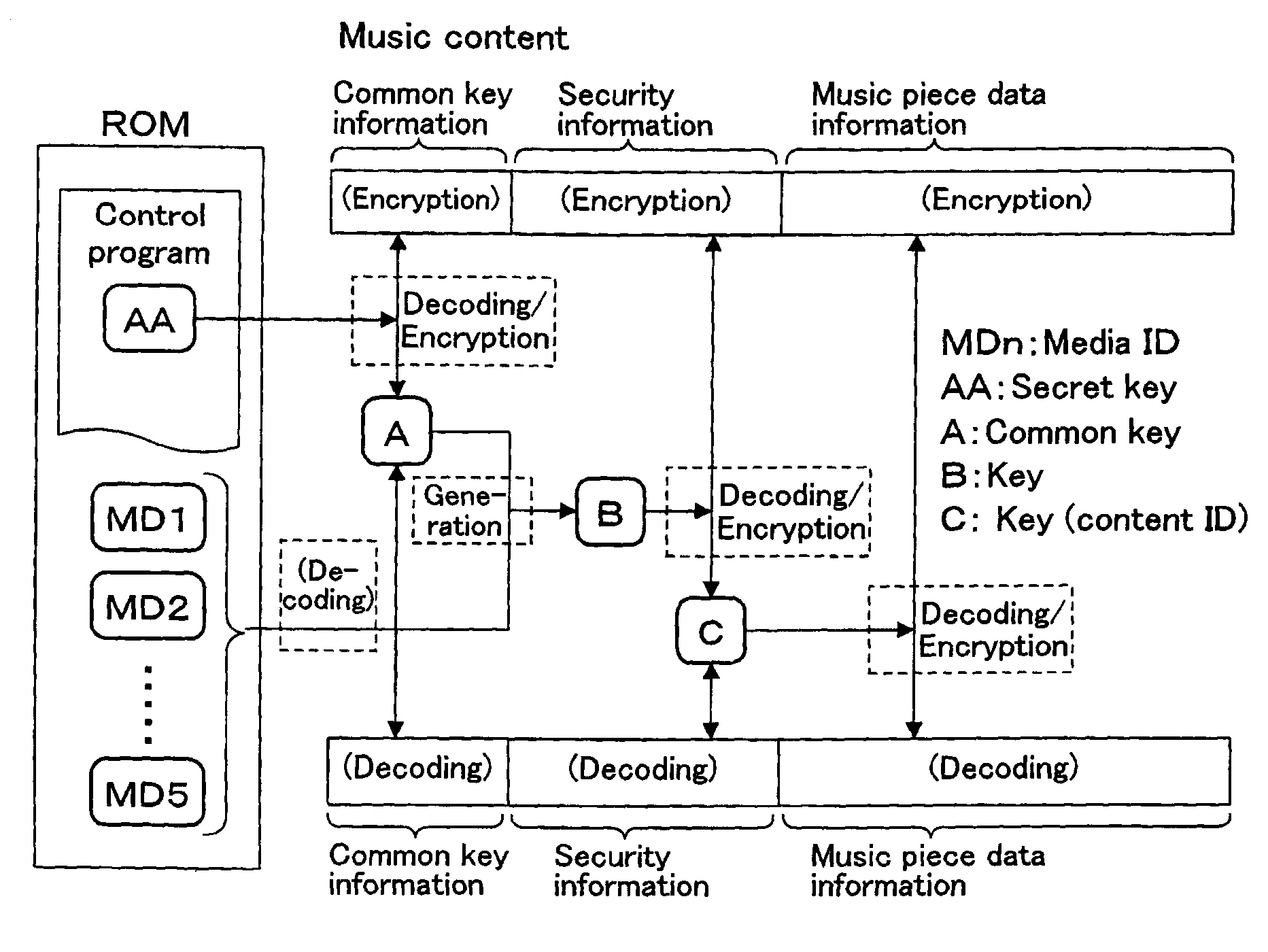
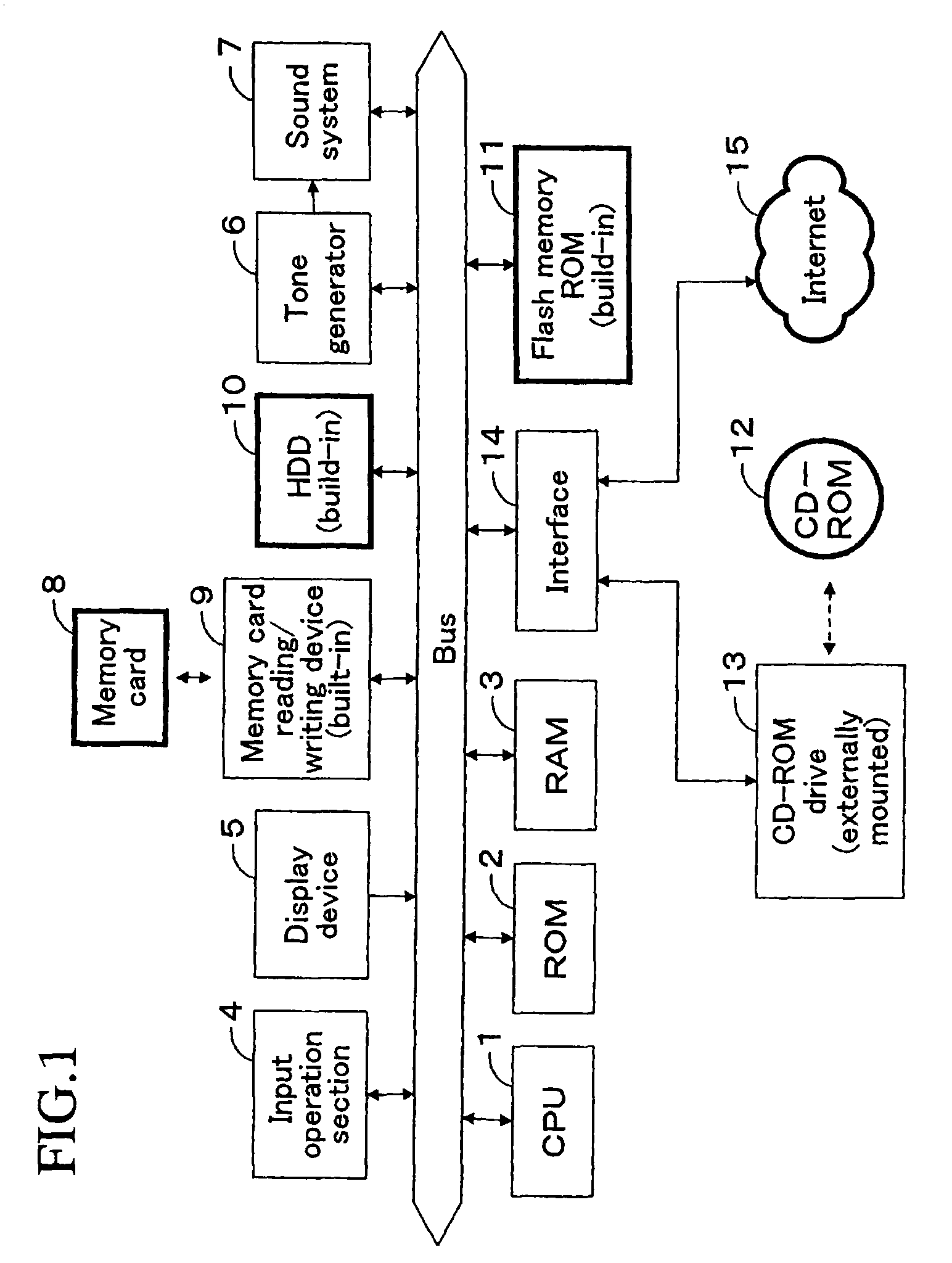
Electronic musical apparatus for recording and reproducing music content
InactiveUS20090132832A1Strengthen copyright protectionEncryption apparatus with shift registers/memoriesUnauthorized memory use protectionThe InternetCD-ROM
Owner:YAMAHA CORP
Method for designing network transmission structure of P2P streaming media with digital rights management
InactiveCN101552777AReduce loadCopyright meetsKey distribution for secure communicationProgram/content distribution protectionIndexing ServiceDigital rights management
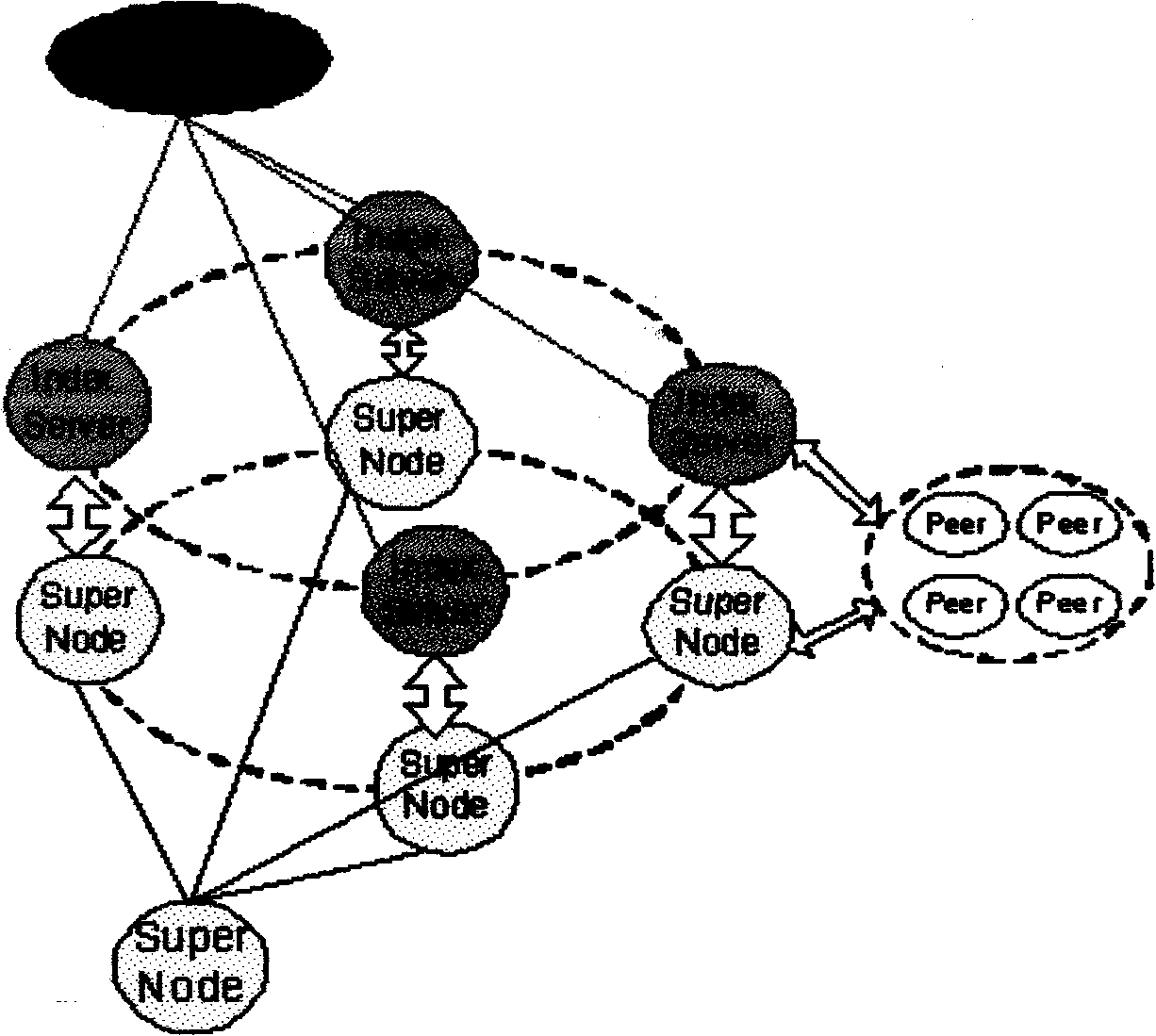
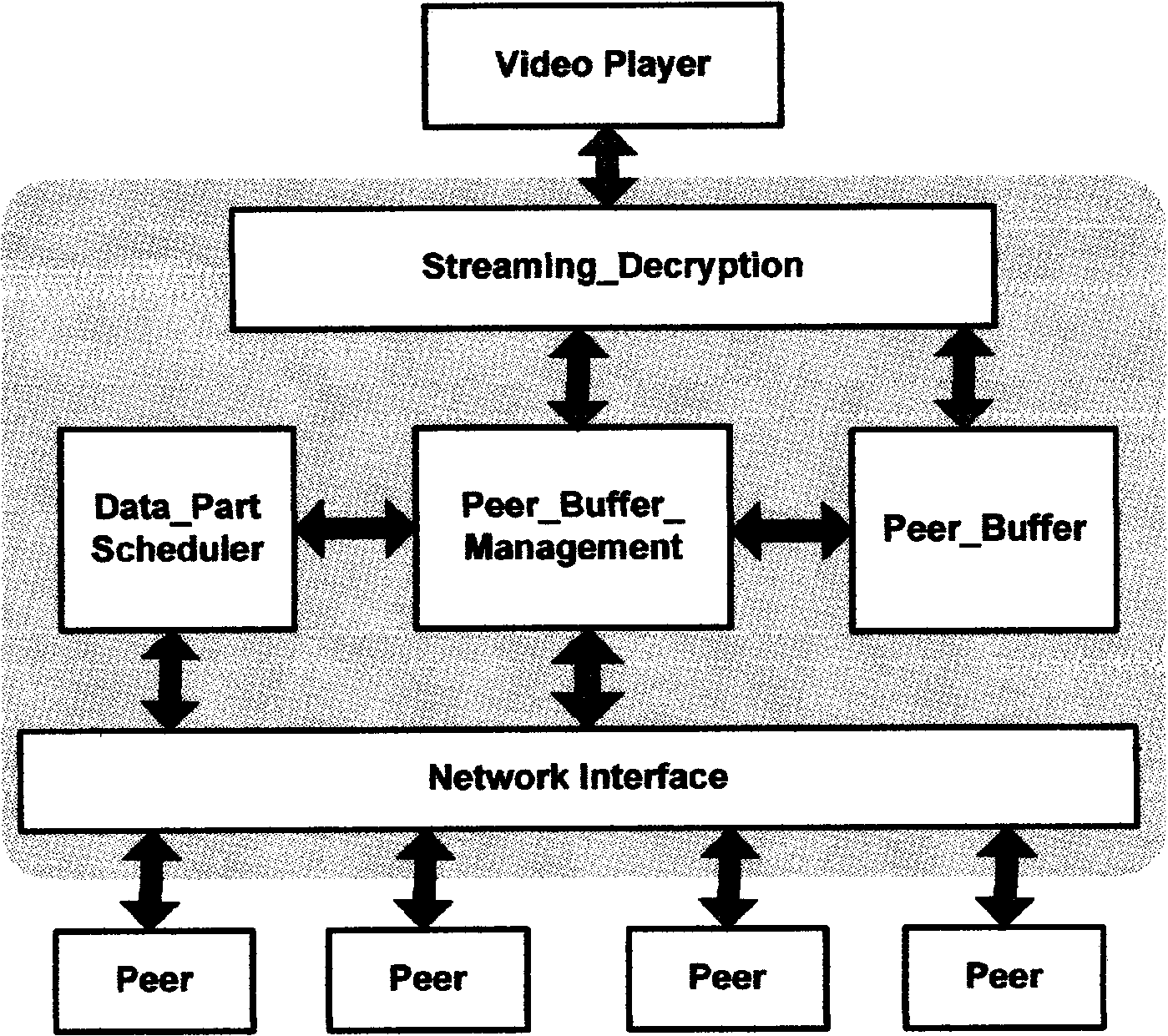
The invention discloses a method for designing the network transmission structure of P2P streaming media with digital rights management, comprising the following steps of using encryption technology to encrypt the steaming media in real time for realizing copyright protection of the digital content; using a certificate server to realize the Peer management, authentication, authorization of P2P network; using an index server to realize the Peer management, clustering, selection and shared service and so on; using Peer clustering technology to enable the heterogeneous Peers broadcasting the same program source to supply downloading and uploading service therebetween; using distributed Super Node to store the streaming media source; using Peer Buffer management technology to realize uploading and downloading service among heterogeneous Peers; and using scheduling algorithm to realize Block-stage parallel downloading. The Peer can be a client or a server, which can sufficiently utilize the resource among Peers and greatly reduce the load of the server, thereby realizing the real-time transmission of the streaming media with a better quality. The invention can meet streaming media network transmission service and real-time requirement for Peer of users.
Owner:XIAN LONGMEI COMM TECH
User-Configurable Pre-Recorded Memory
ActiveUS20060085615A1Copyright feeLittle accessRead-only memoriesUnauthorized memory use protectionMemory typeComputer science
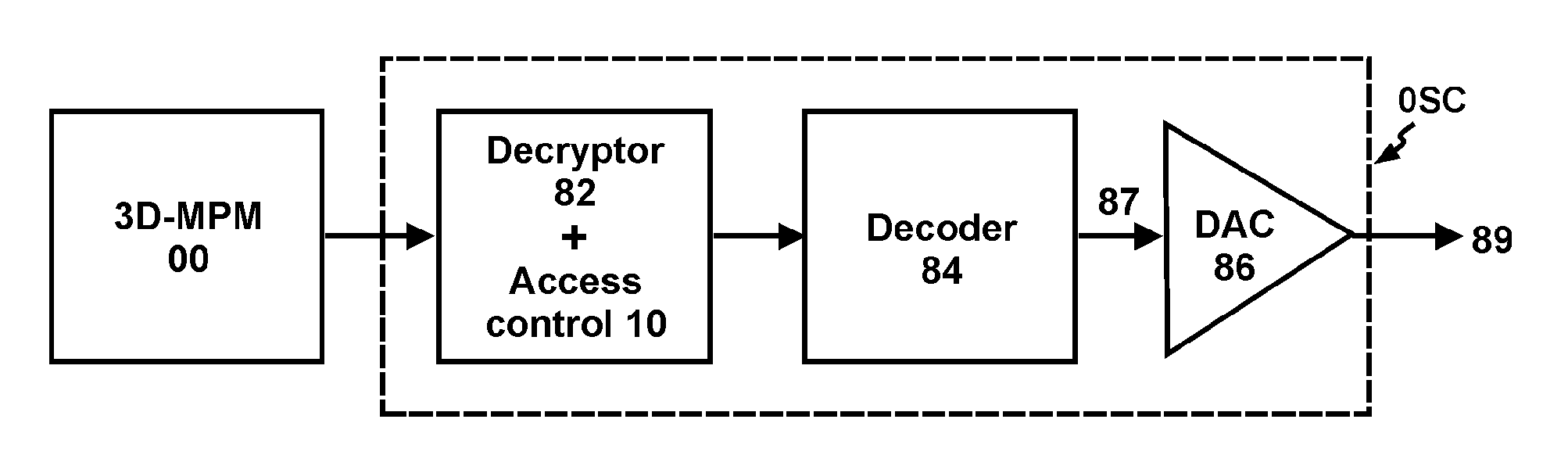
In a user-configurable pre-recorded memory (UC-PM), a user can select contents he is interested in, and pay copyright fees accordingly. With large capacity, low cost and great integratibility, 3D-M, more particularly 3D-MPM, is suitable for UC-PM. It provides excellent access control and impenetrable copyright protection. UC-PM will enable a copyright distribution model fair to both copyright holders and users. On the other hand, the 3D-MPM scaling should be the fastest among all memory types.
Owner:ZHANG GUOBIAO
VR panoramic live video transmission gateway and method
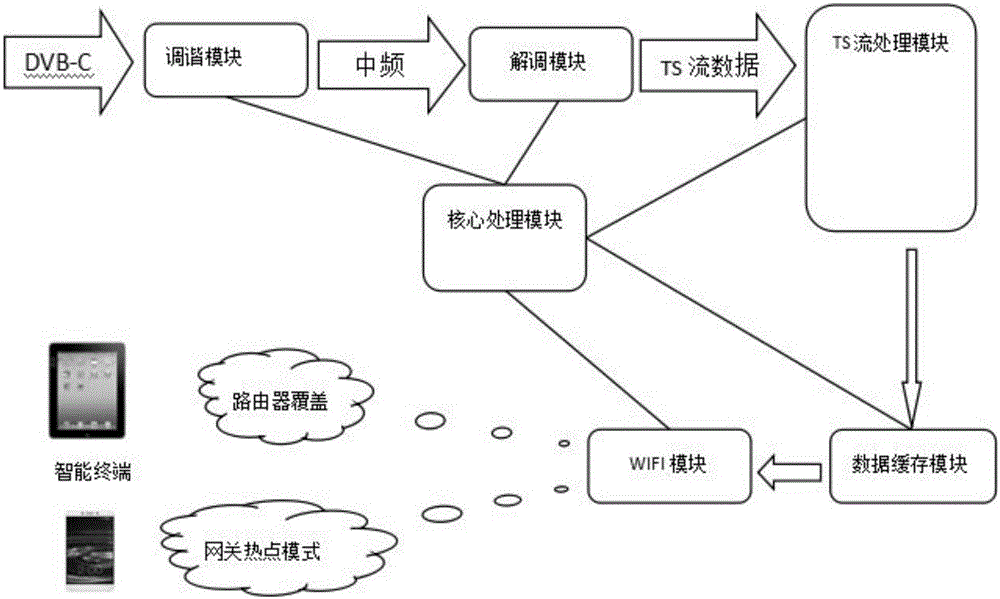
InactiveCN106375844AStable access bandwidthHigh viewingSelective content distributionStreaming dataVideo transmission
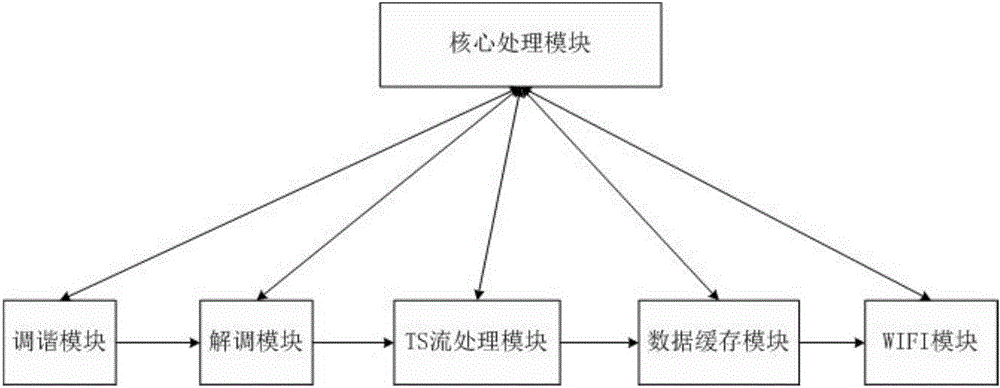
The invention relates to a VR panoramic live video transmission gateway and method. The gateway comprises a tuning module, ademodulation module, a TS stream processing module, a data cache module and a WIFI module which are serially connected in sequence, wherein the gateway further comprises a core processing module; the tuning module is used for receiving a radio frequency signal and tuning the same; the demodulation module is used for demodulating the signal and outputting and transmitting TS stream data; the TS stream processing module is used for collecting and demultiplexing the TS stream data; the data cache module is used for caching the data; the WIFI module is used for pushing the data to a user terminal; and the core processing module is used for processing a communication protocol and coordinating the work of the modules. The VR panoramic live video transmission gateway provided by the invention solves the problem that users cannot view VR panoramic live broadcast signals transmitted by a broadcasting and TV HFC network, the users can access bandwidths more highly and more stably to watch 4K VR panoramic live video signals with higher code rates.
Owner:威睿科技(武汉)有限责任公司 +1
General video digital watermark method
InactiveCN101938618BFlexible adjustment of embedding ratioAccurate extractionTelevision system detailsColor television detailsSystems designWatermark method
Owner:SHANDONG COMP SCI CENTNAT SUPERCOMP CENT IN JINAN
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com