Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
170results about How to "Reduce memory space" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
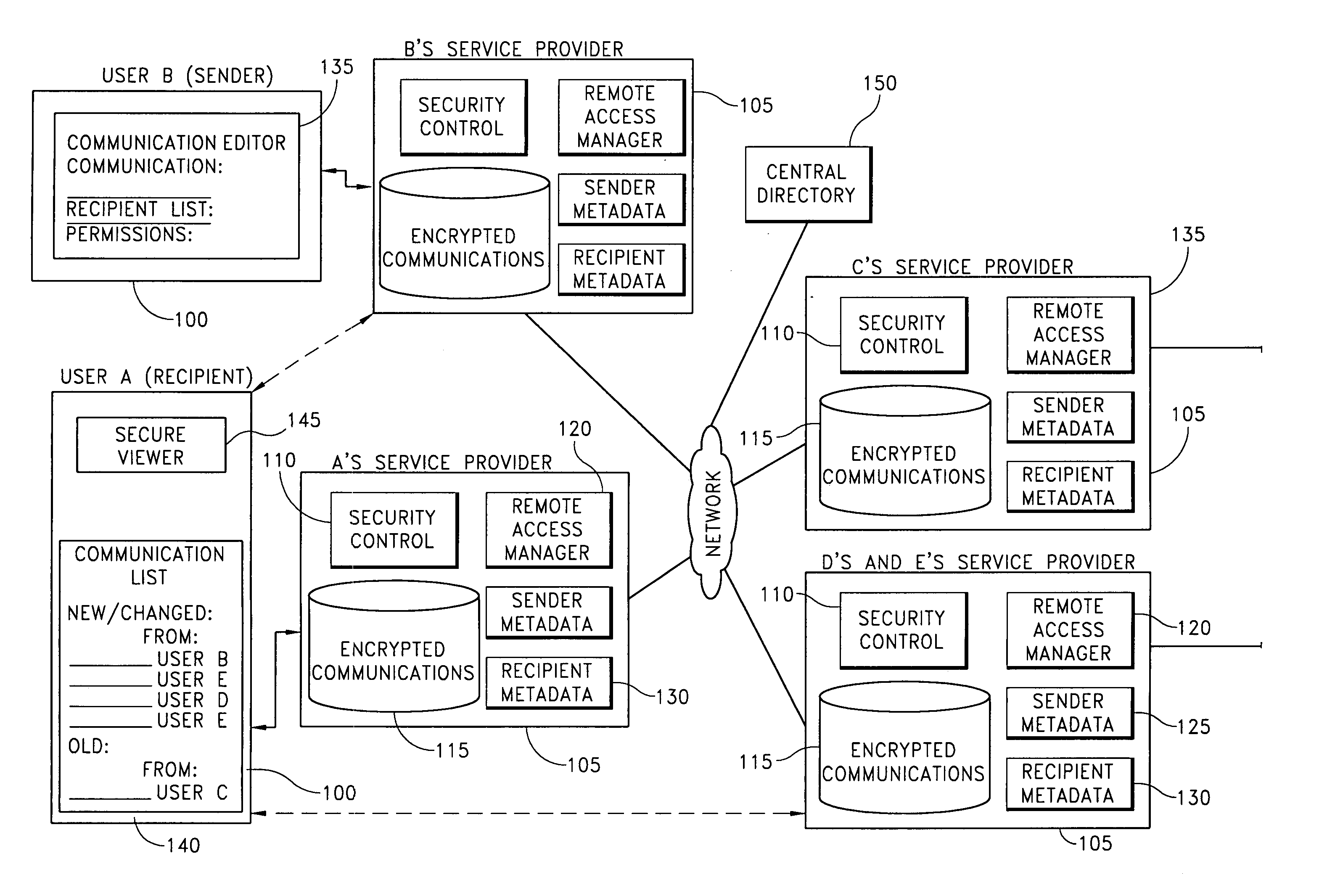
Distributed secure repository
InactiveUS20060059544A1Reduce memory spaceRetain controlDigital data processing detailsUser identity/authority verificationInternet privacyMetadata
A distributed secure repository and related methods allow users of a communications management system to securely store and share communications with other users. A user shares a communication by securely storing the communication, identifying the recipient, and specifying permissions that limit actions that the recipient is permitted to take with respect to the communication. Mechanisms are provided for limiting a recipient's ability to view, copy, store, forward, print, and modify the communication. Metadata associated with the communication is transmitted to the recipient, notifying the recipient of the securely stored communication. The recipient uses the metadata to request an encrypted copy of the communication, to view the communication, or to otherwise interact with the communication in accordance with the sender's permissions. The sender retains control of the communication and can modify the communication and associated permissions.
Owner:H-E-B
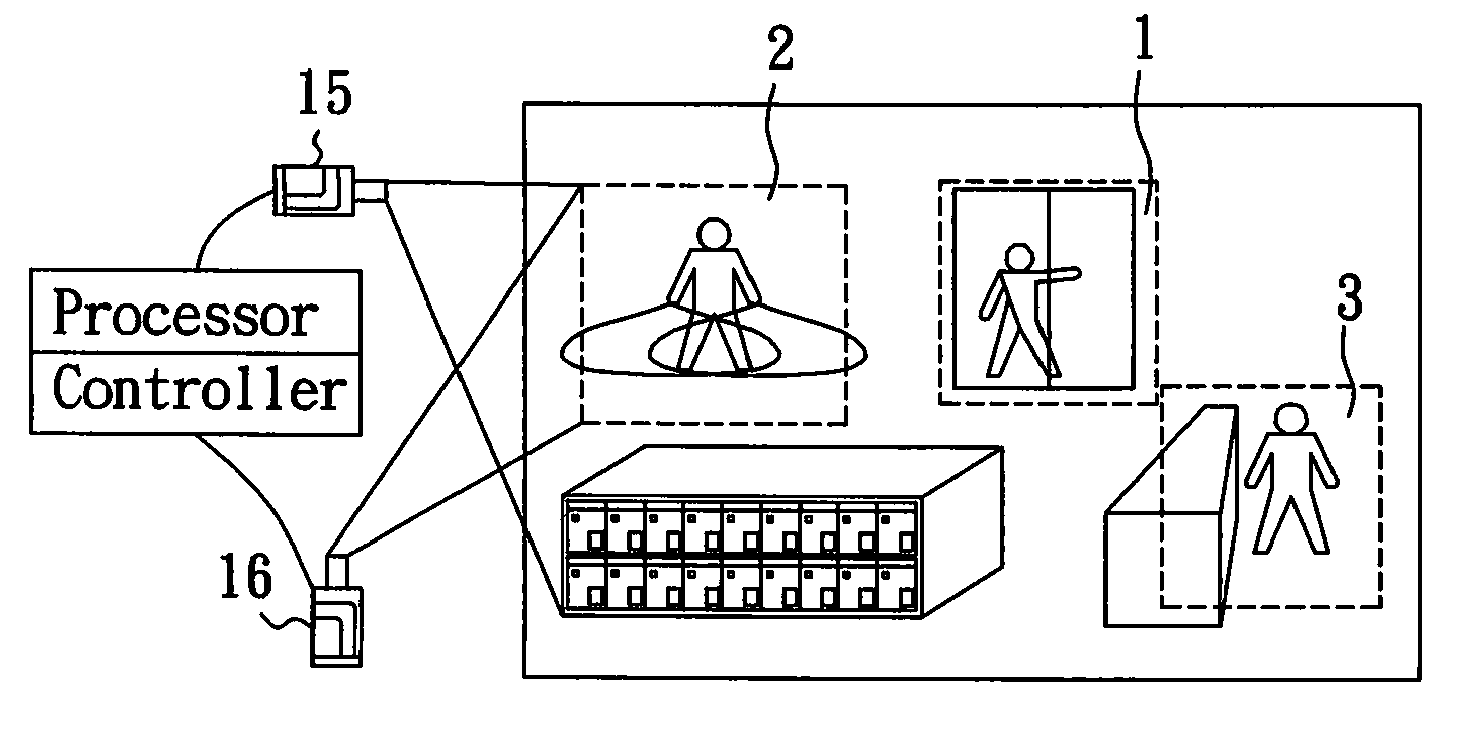
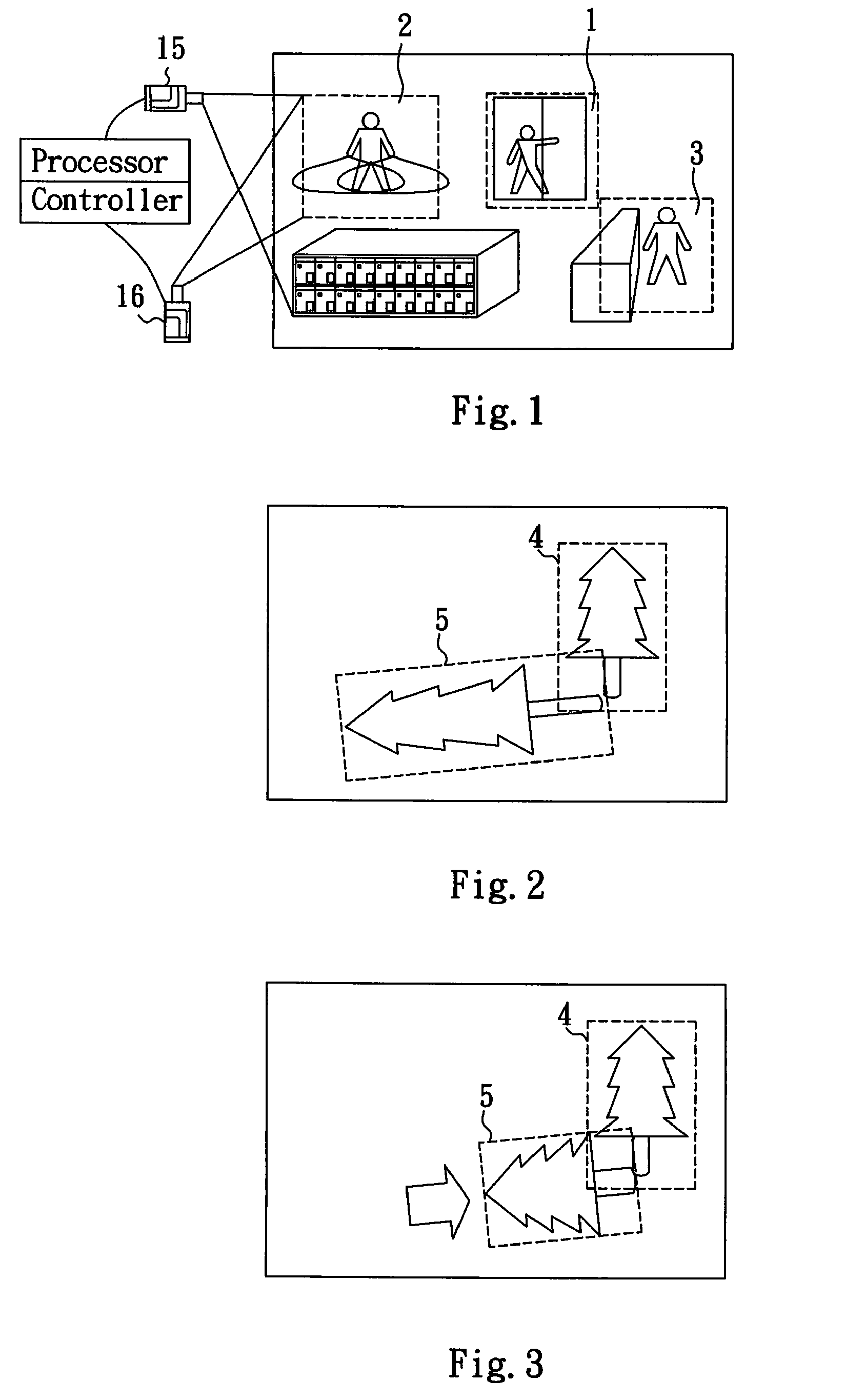
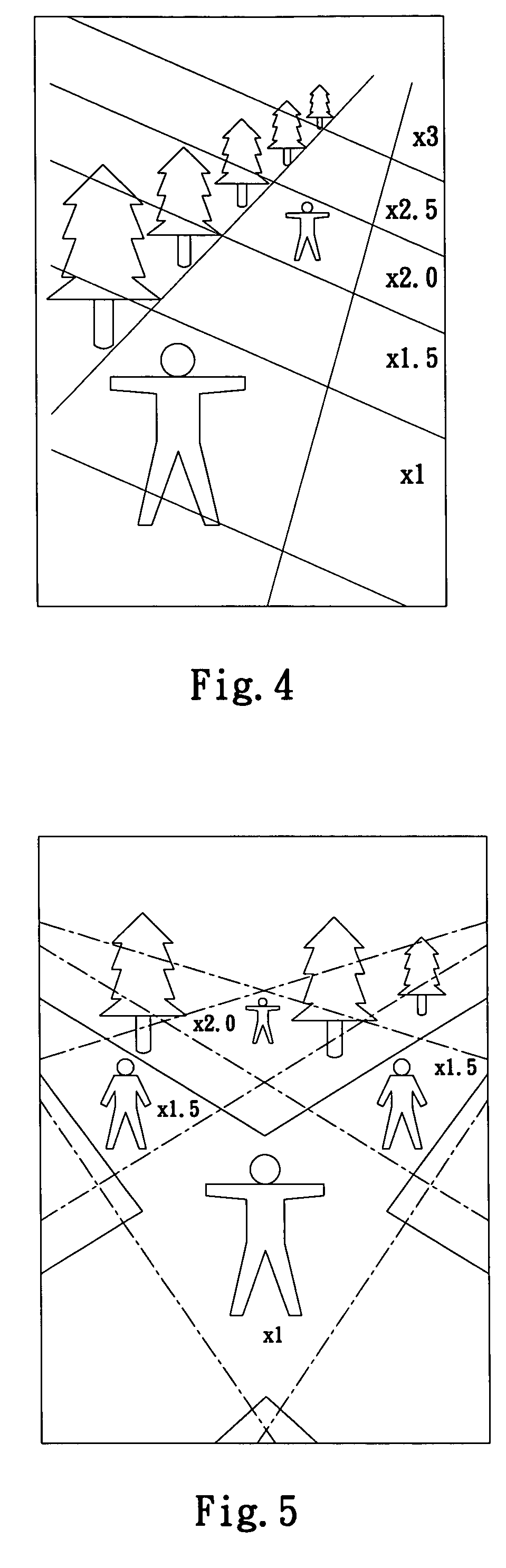
Object detection system and method
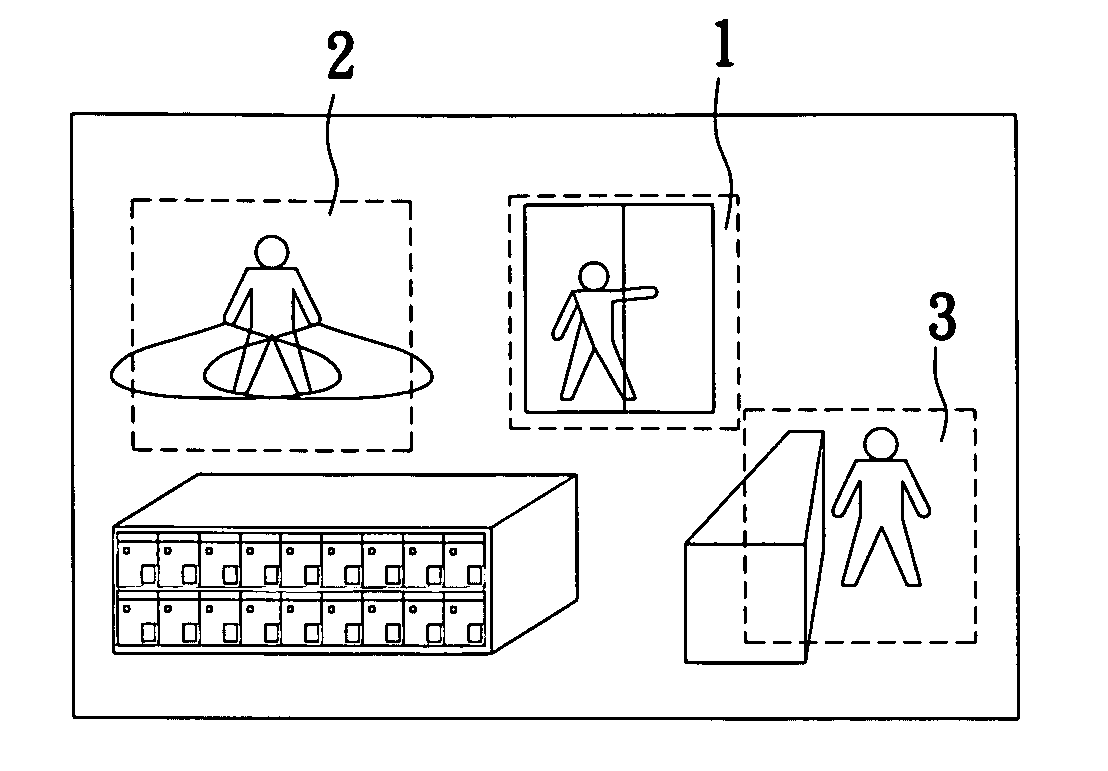
InactiveUS7574131B2Reduce distractionsImprove accuracyClosed circuit television systemsPanoramic photographyMonitoring systemObject detection
An object detection system and method is applied to an active surveillance system for detecting at least one target object appeared in an area of interest. The object detection system includes a processor for defining the area of interest into at least a first and a second zone; a controller for assigning a first and a second weight to the first and the second zone, respectively, wherein the first weight is higher than the second weight; and a first image capturing device for capturing an image of the target object appeared in the first zone prior to capturing an image of the target object appeared in the second zone. With these arrangements, the detection of at least one target object appeared in more than one zone having a specific weight assigned thereto may be implemented with improved efficiency and accuracy in object selection and reduced interferences from environmental variables.
Owner:SUNVISION SCI
Method for dynamic memory management
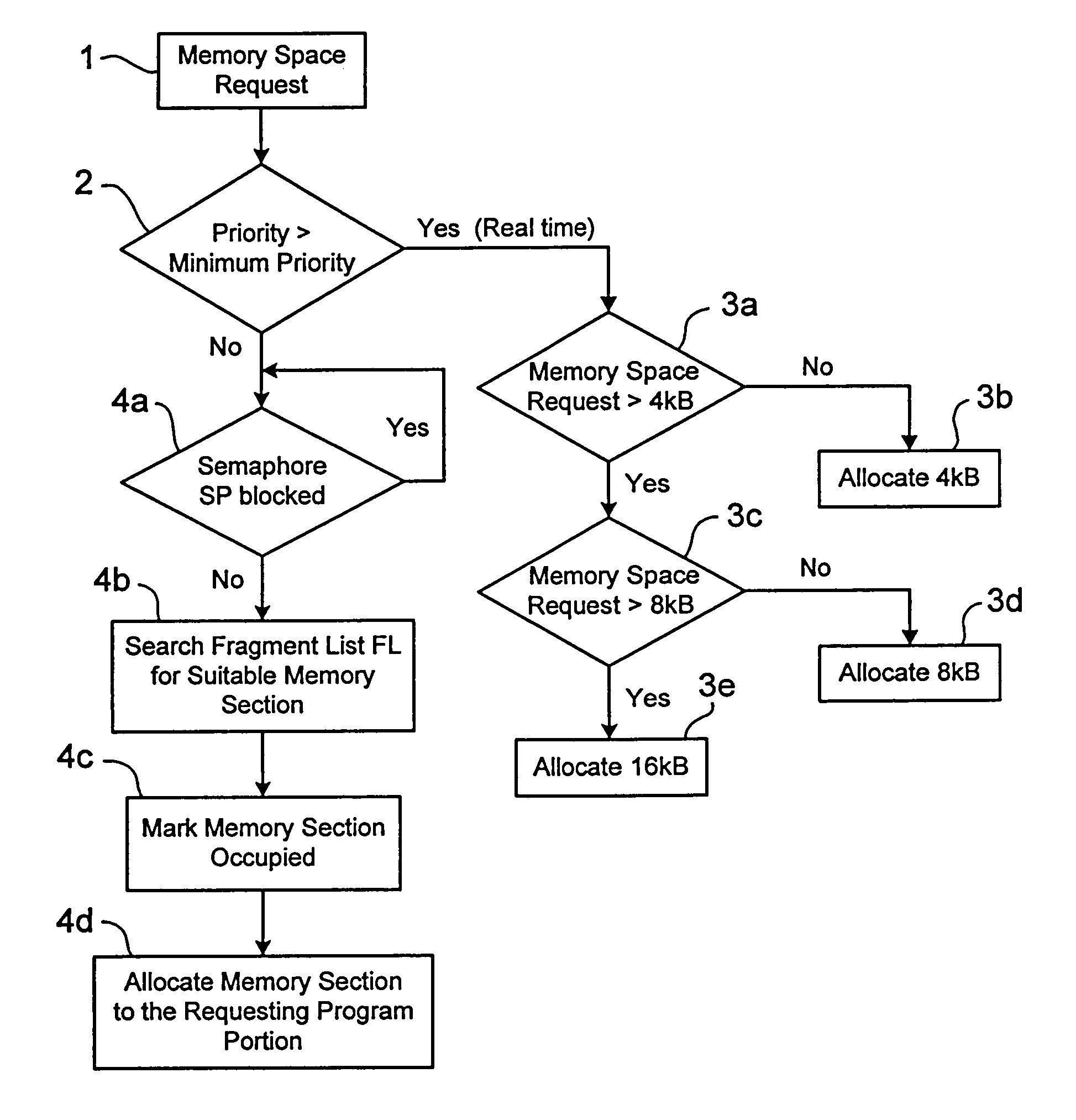
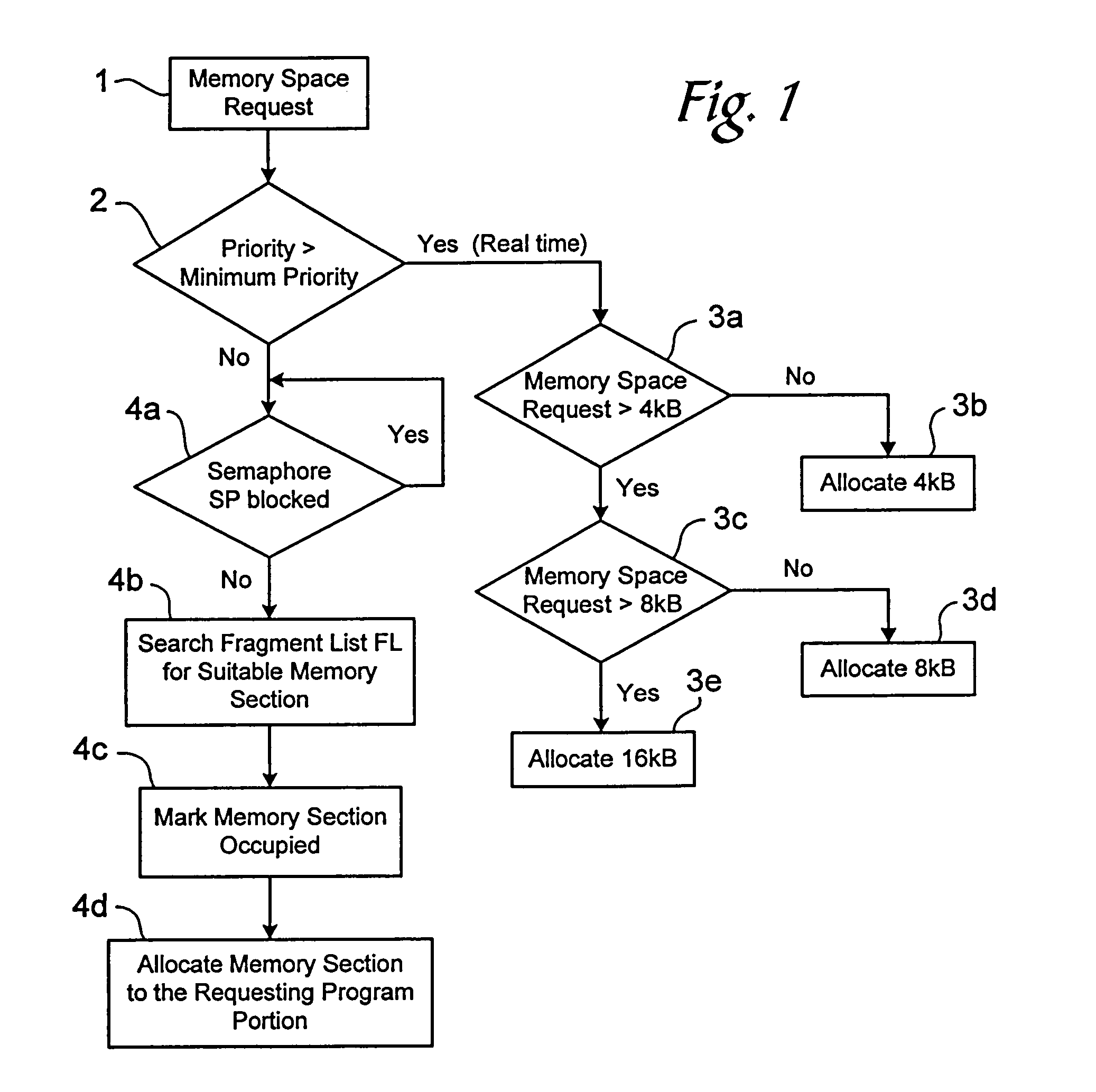
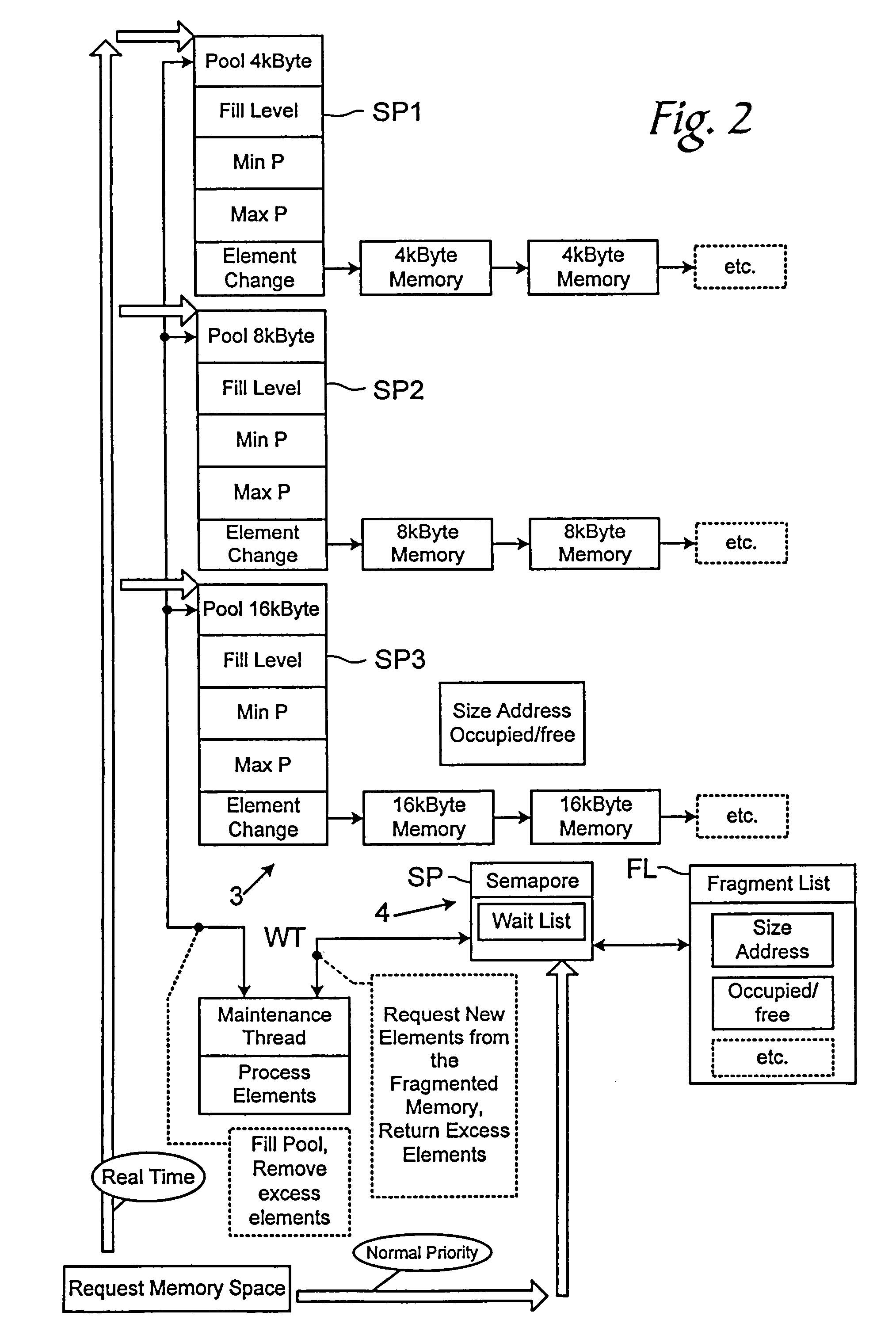
InactiveUS7035990B1Memory space rapidlyAllocation of memory spaceData processing applicationsResource allocationReal-time computingDynamic memory management
A method for dynamic memory management that includes determining a priority of a requesting program portion and, based on the determined priority of the requesting program portion, either allocating a memory area in real time to the requesting program portion or allocating a memory area not in real time to the requesting program portion.
Owner:DR JOHANNES HEIDENHAIN GMBH
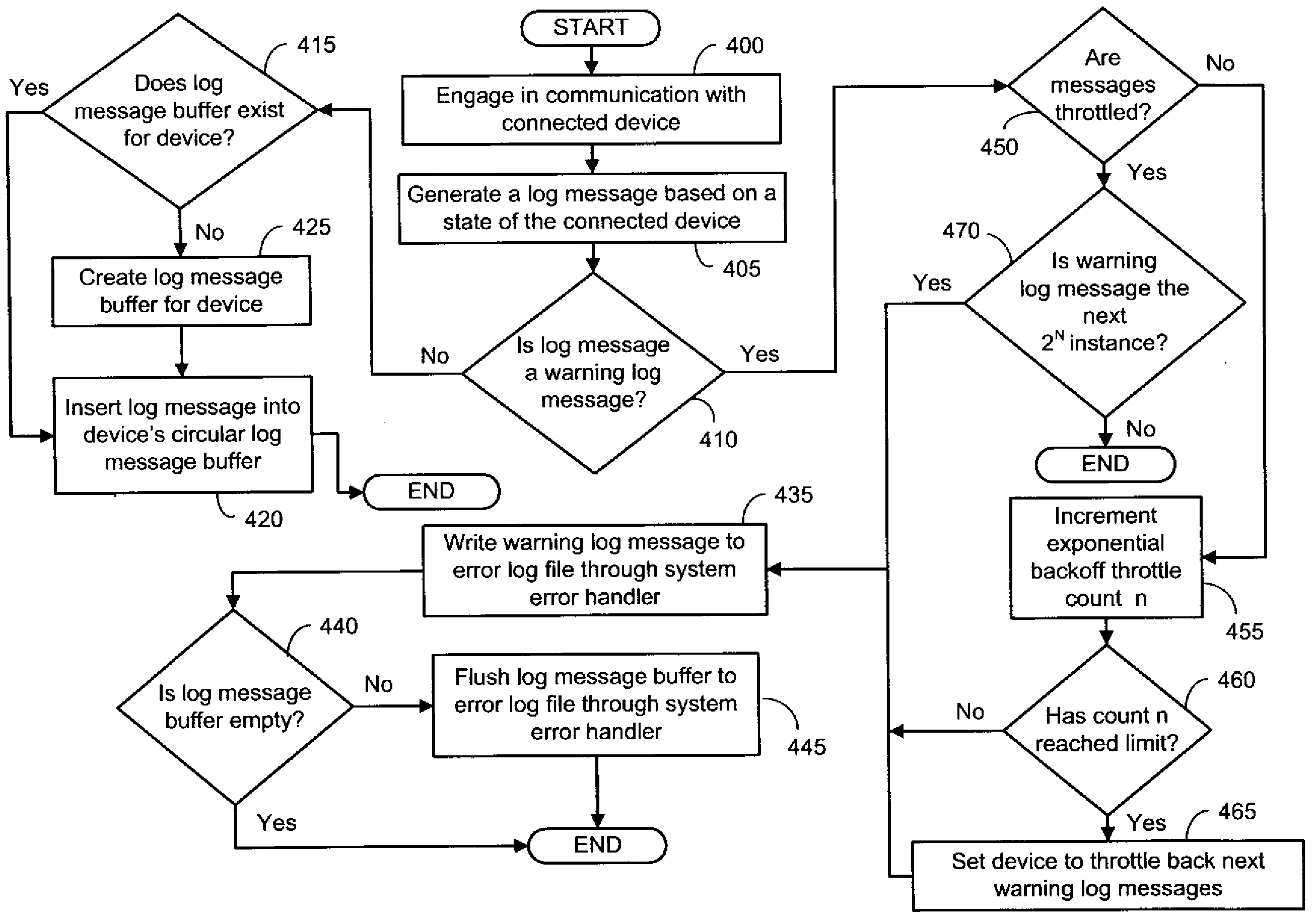
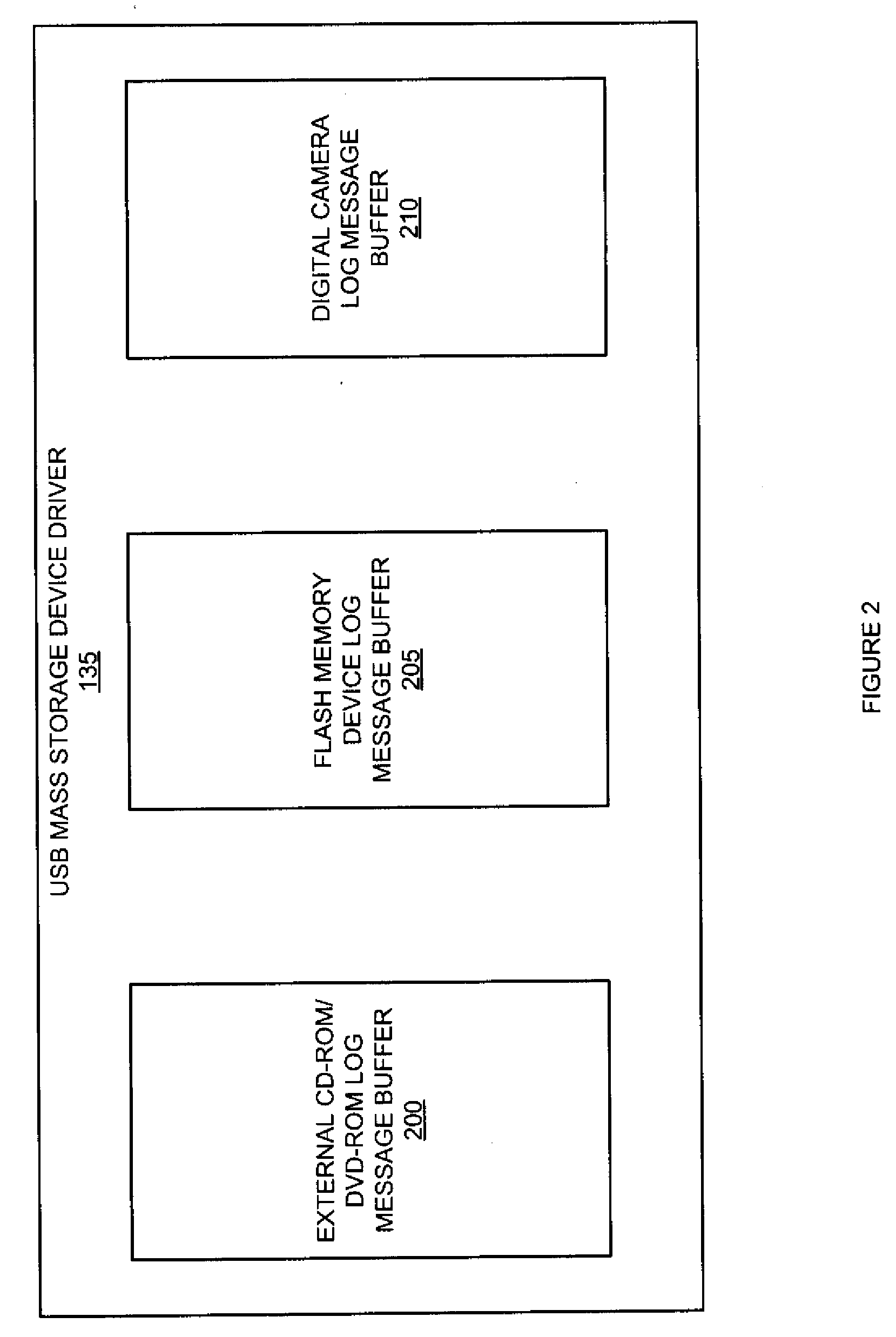
Method and System for Throttling Log Messages for Multiple Entities
ActiveUS20100306599A1Convenient reviewReduce memory spaceNon-redundant fault processingService provisionProcedural approach
A software module capable of simultaneously supporting multiple services provides log message throttling for each service with a separate “per service” log message buffer. When the software module is a device driver, for example, each device controlled by the device driver is allocated a message buffer to store descriptive log messages. Upon generation of a warning log message, descriptive log messages in the message buffer are flushed to a log file for review by an administrator. Furthermore, log message throttling may be implemented by only flushing the message buffer upon certain occurrences of warning log messages, such as in accordance with an exponential back-off algorithm.
Owner:VMWARE INC
Apparatus, method, and computer readable medium for transmitting data via a plurality of network interfaces
InactiveUS20080125163A1BandwidthAvoid problemsNetwork traffic/resource managementSubstation equipmentMobile deviceThroughput
An apparatus, a method, a computer program, and a computer readable medium for transmitting data via a plurality of network interfaces are provided. The apparatus derives statuses of transmission media and then transmits data based on the statuses. In addition, each base station adopts tunneling technique by adding a tunnel header to each of the transmitted packets. By the aforementioned arrangement, a mobile device is capable of adjusting the data amount for each of the network interfaces. Thus, the throughput of mobile host can be increased and connection can be dependable.
Owner:INSTITUTE FOR INFORMATION INDUSTRY
Authentication method and device using a single-use password including biometric image information
ActiveUS20140250517A1Improve reliabilityImprove stabilityImage analysisDigital data processing detailsComputer terminalIris image
The present invention relates to an authentication method and device using a single-use password generated from iris image information. The device comprises: a terminal and a server storing, in respective memories thereof, the iris image information for authentication; a camera attached to and installed on the device to capture the iris image information for authentication; the terminal, which generates the single-use password from the iris image information acquired through the camera, and transmits the single-use password to the server; and the server, which has a built-in algorithm for comparing and determining whether or not the single-use password transmitted from the terminal matches single-use password stored in the server.
Owner:IRITECH
Method, device and system for realizing Java application installation via cloud compilation
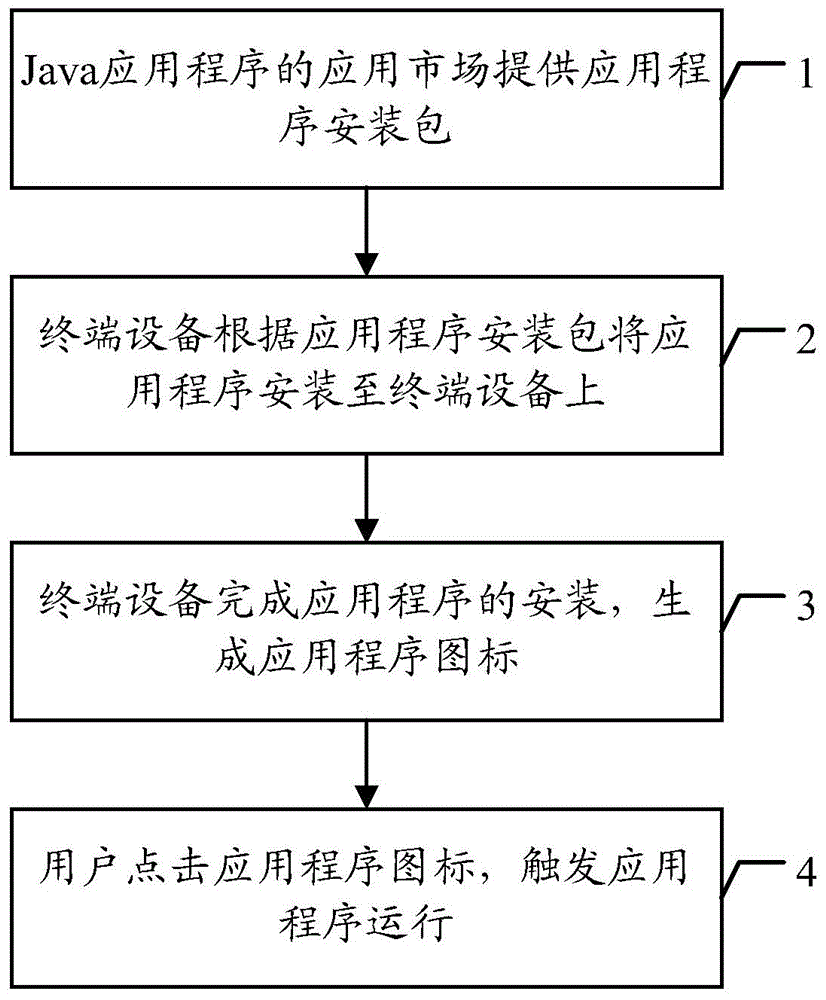
ActiveCN105100191AReduce memory spaceReduce storage spaceTransmissionSoftware deploymentTerminal equipmentApplication software
The embodiment of the invention discloses a method for realizing Java application installation via cloud compilation. The method comprises the following steps that: terminal equipment transmits the hardware configuration information of the terminal equipment and the version information of a target application to an application market server in order to obtain the upgrade information of the target application corresponding to the hardware configuration information and the version information of the target application through the application market server; the terminal equipment receives the upgrade information of the target application fed back by the application market server, wherein the upgrade information includes a target code file corresponding to newest version information obtained by compilation of an intermediate code file corresponding to the version information of the target application on a cloud server; and the terminal equipment performs optimal installation of the target application according to the upgrade information in order to update the version of the target application. Through adoption of the embodiment of the invention, the method has the advantages that the equipment memory occupied by the optimal installation of the application can be reduced specifically; the efficiency of optimal installation of the application is increased; and the user experience of application installation is enhanced.
Owner:HUAWEI TECH CO LTD
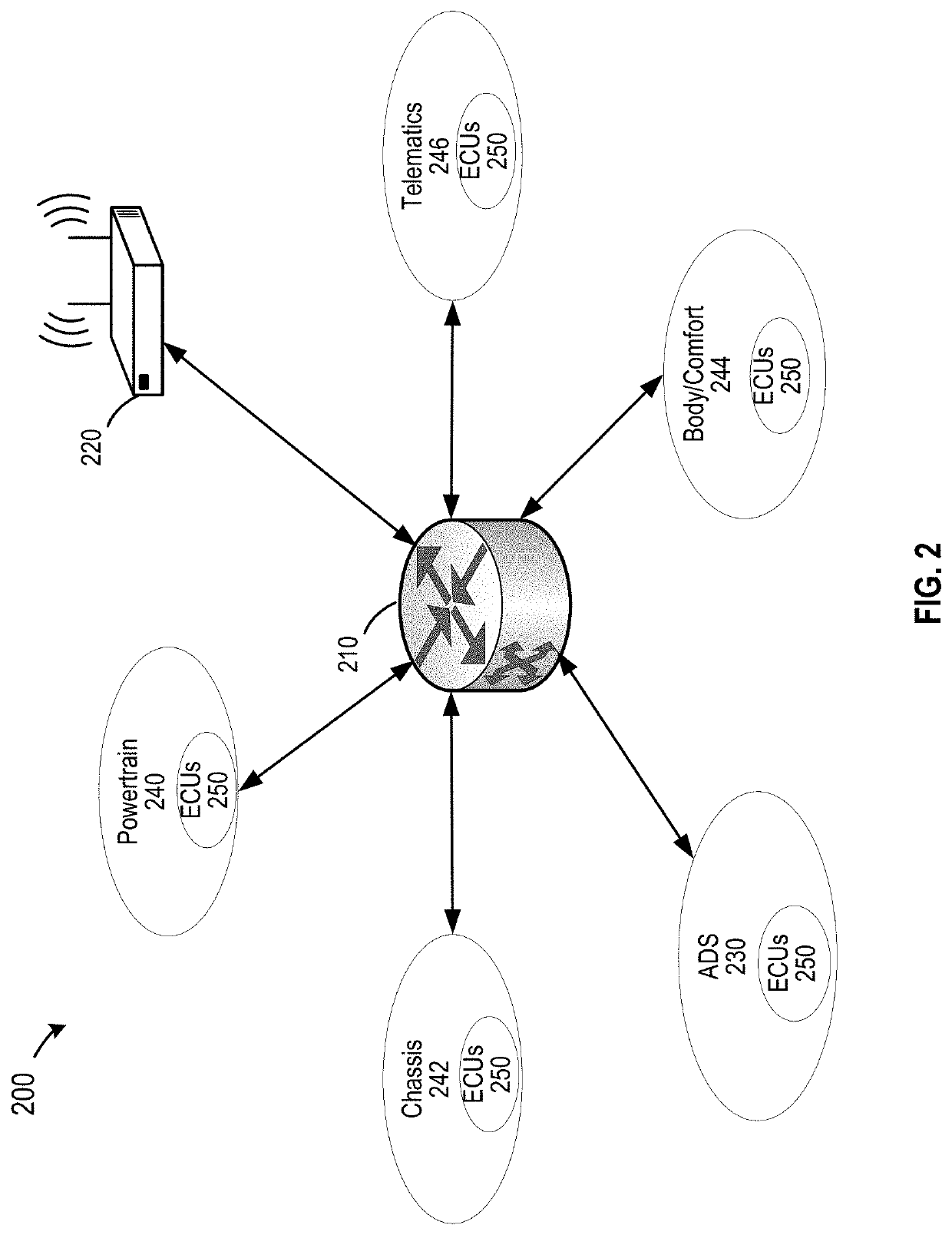
Trusted platform protection in an autonomous vehicle
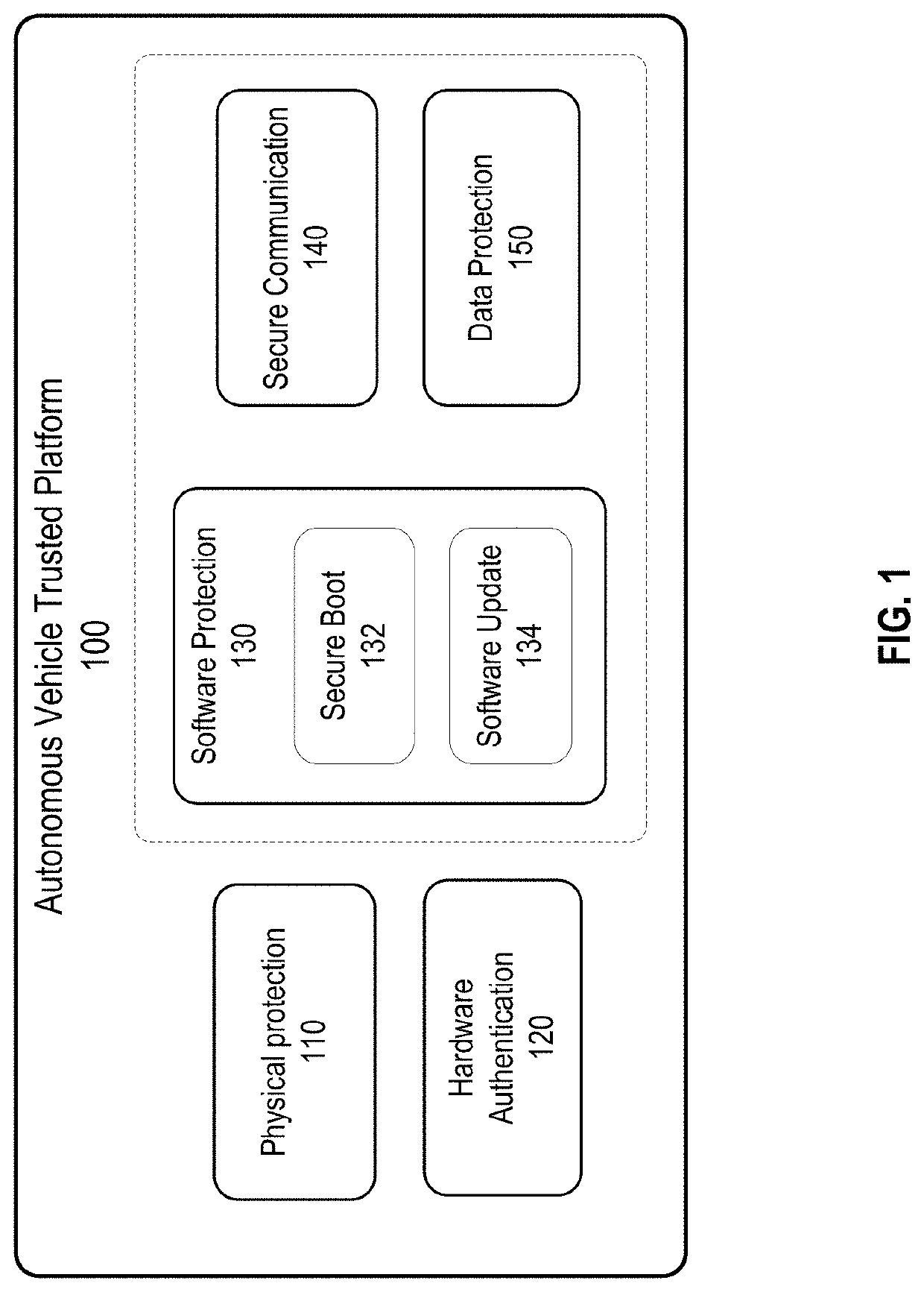
ActiveUS20200213287A1Reduce and minimize safety and security issueSafety and security be improveParticular environment based servicesDigital data authenticationEmbedded systemSecure communication
Disclosed are techniques for securing electronic control units (ECUs) in a vehicle. A security platform for a vehicle includes a key distribution center (KDC) for the vehicle. The KDC is configured to verify that a digital certificate associated with a first electronic control unit (ECU) on the vehicle is a valid certificate, where the digital certificate indicates a first security level of the first ECU. The KDC is configured to generate, based on the first security level of the first ECU, one or more security keys for secure communication between the first ECU and a set of ECUs on the vehicle, and provision the one or more security keys to the first ECU and the set of ECUs. In some embodiments, the KDC uses the provisioned keys to authenticate each ECU when the vehicle is powered up.
Owner:BEIJING VOYAGER TECH CO LTD
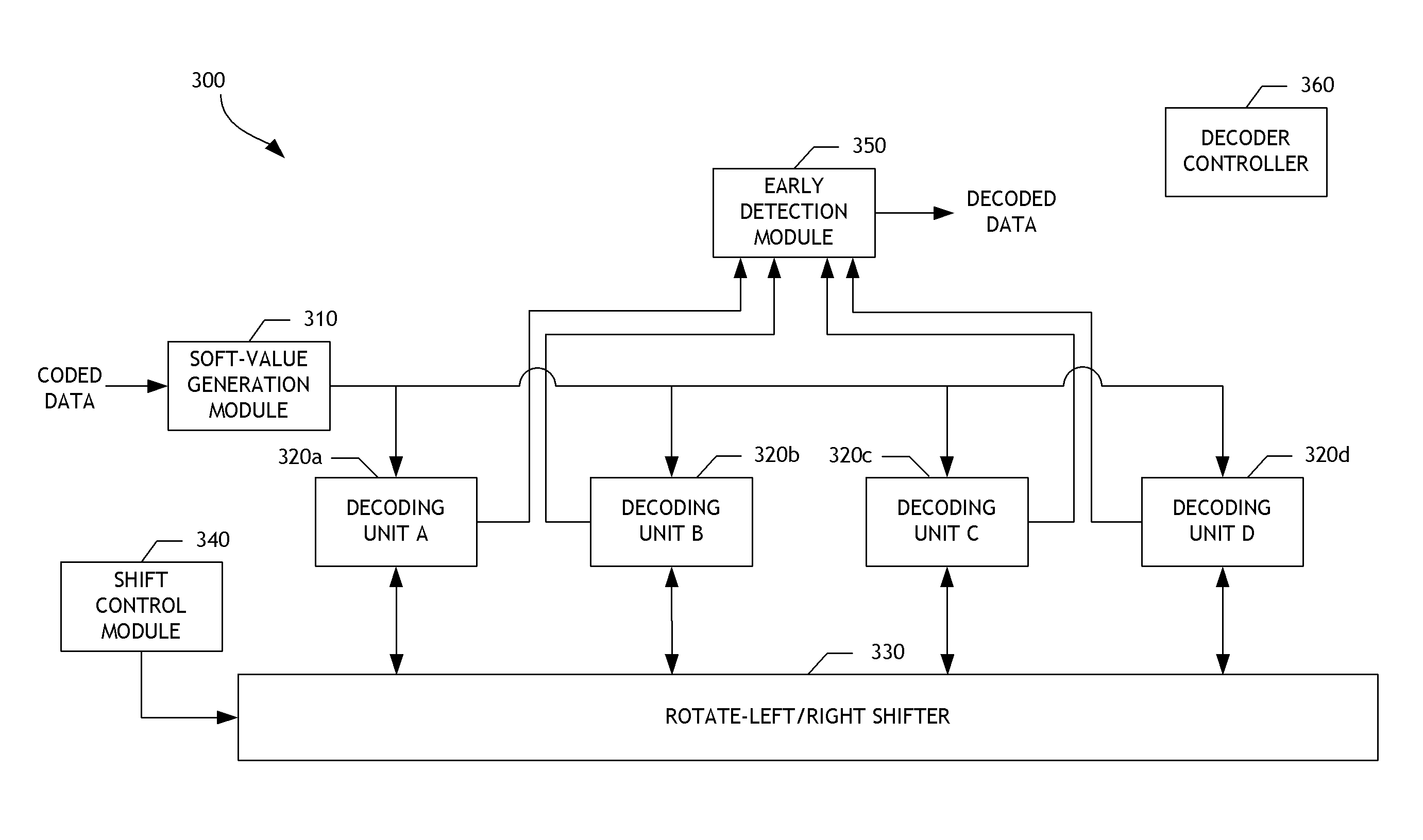
Decoder supporting multiple code rates and code lengths for data storage systems
ActiveUS8966339B1Reduce memory spaceHigh bit rateCode conversionError correction/detection using linear codesParallel computingCode rate
Embodiments of decoders supporting multiple code rates and code lengths for data storage systems are disclosed. The decoders can provide for flexible and scalable decoding, particularly when quasi-cyclic low-density parity-check code (QC-LDPC) decoding is used. The decoder can be scaled in size based on, for example, the desired decoding throughput and / or computational cycle duration. In one embodiment, a rotate-left / right shifter is configured to support data having processing units of one of multiple matrix sizes and independently shift portions of the data. In another embodiment, one or more decoding modules are configured to share with one or more other decoding modules an output value from a layer decoding operation. This sharing can facilitate parallel decoding of data by the decoding modules. As a result, decoding speed, efficiency, and system performance can be improved.
Owner:WESTERN DIGITAL TECH INC
Program code conversion
InactiveUS7203933B2Shorten the timeReduce memory spaceBinary to binarySoftware simulation/interpretation/emulationProgramming languageObject code
A method of dynamic real time translation of first program code written for a first programmable machine into second program code (target code) for running on a second programmable machine employing run time generation of an intermediate representation of the first program code. Upon first encountering a given portion of program code, only the target code necessary to execute that portion of program code under a prevailing set of entry conditions is initially generated and stored. When the same portion of program code is again encountered, a determination is made as to whether intermediate representation corresponding to a second subsequent set of conditions has been generated. If not, the target code necessary to execute the same portion of program code under that second set of conditions is generated.
Owner:IBM CORP
Device and method for image compression and decompression
ActiveUS20070237391A1Reduce the amount of dataReducing occupied memory spaceTexturing/coloringCharacter and pattern recognitionPattern recognitionFloating point
An image compression device includes a floating-point texture-loading unit, a shader, a RGB to YCrCb compressor, and a parameter adjusting unit. The floating-point texture-loading unit receives raw image data that includes N number of RGB pixels. The shader receives the raw image data and shades the N number of RGB pixels. The RGB to YCrCb compressor receives the shaded image data and calculates the brightness / chroma value of each of the RGB pixels, wherein the chroma value of the RGB pixel having the smallest brightness value among all the RGB pixels is selected as a common chroma value for all the RGB pixels. The parameter adjusting unit receives and adjusts N number of brightness values of the RGB pixels and the common chroma value and stores them in a form of compressed image data into a memory.
Owner:XIAHOU HLDG
Image capturing method and image-capturing device thereof
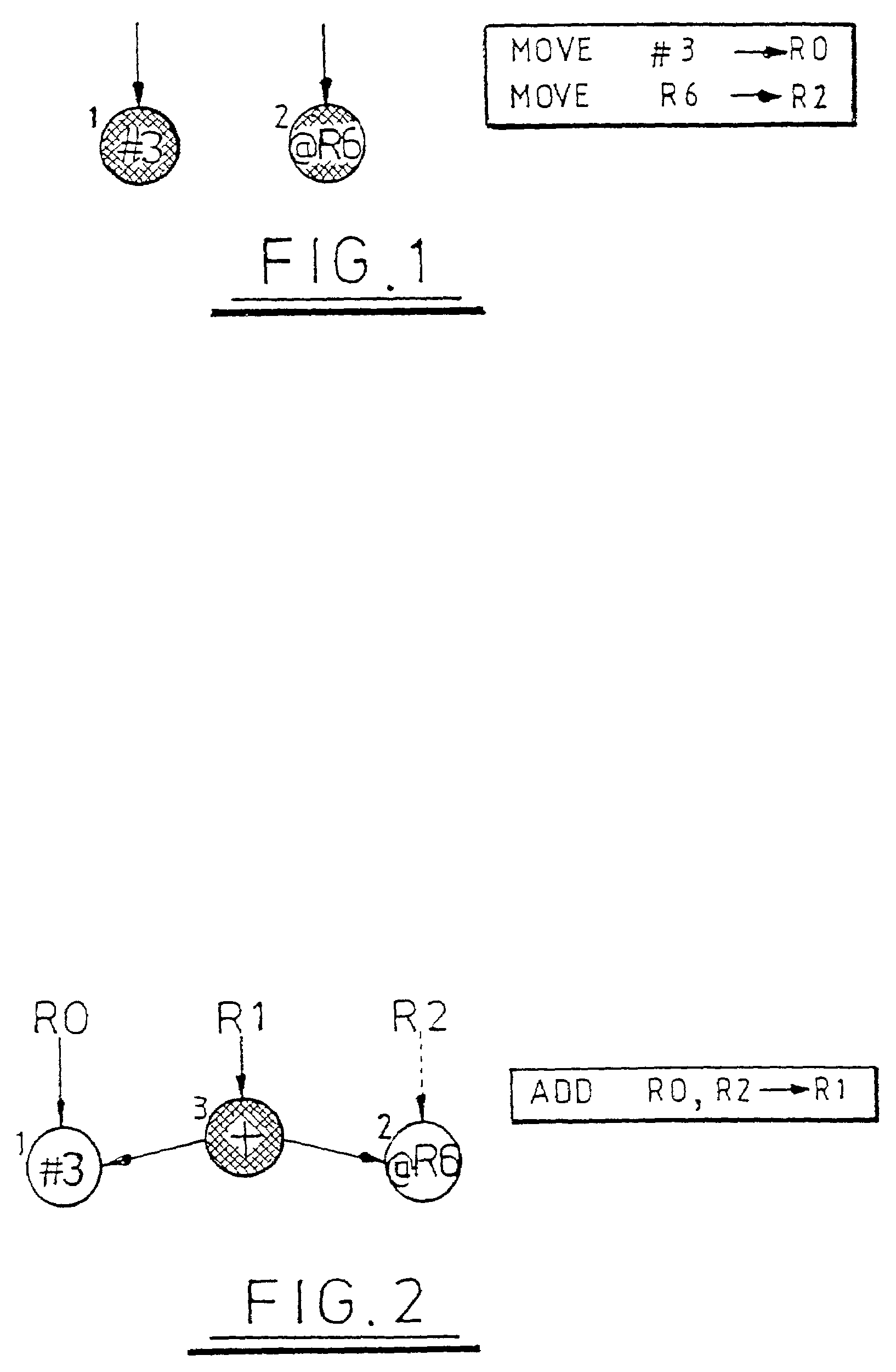
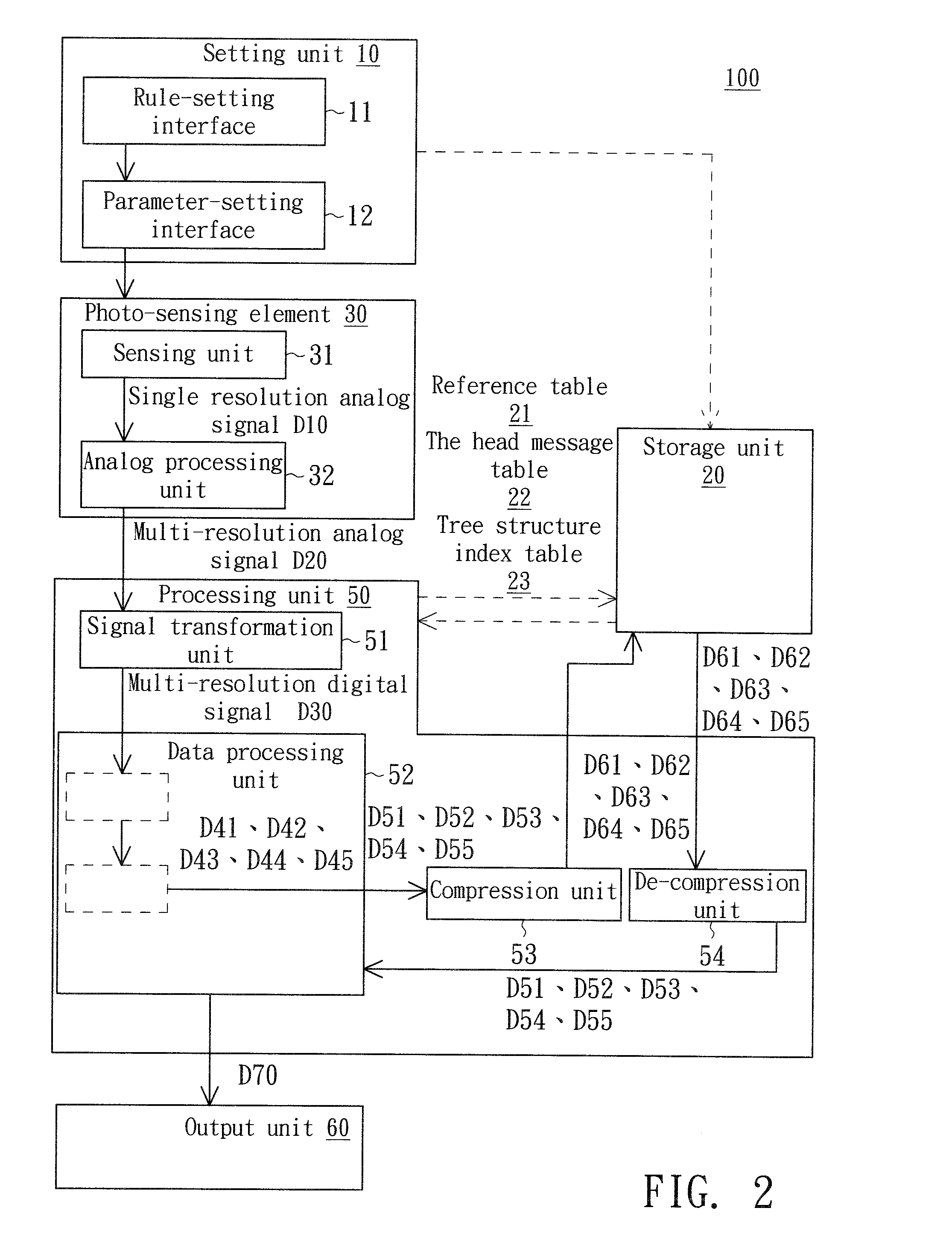
InactiveUS20070188624A1Reduced memory spaceMaintain qualityTelevision system detailsColor television detailsImage resolutionReference table
An image capturing method and an image-capturing device thereof are provided. Firstly, a dividing rule for dividing a first part and a second part is set, such that the positions and sizes of the first and the second parts are obtained accordingly. Next, a first resolution corresponding to the first part and a second resolution corresponding to the second part are set respectively. Then, the positions and sizes of the first and the second parts, the first resolution and the second resolution are recorded in a reference table. Next, an image of an object is captured to obtain a multi-resolution analog signal. Then, the multi-resolution analog signal is transformed to a multi-resolution digital signal. After that, a first part image corresponding to the first part and a second part image corresponding to the second part are respectively obtained with reference to the multi-resolution digital signal.
Owner:BENQ CORP
Object detection system and method
InactiveUS20070230943A1Improve efficiencyImprove accuracyClosed circuit television systemsPanoramic photographyMonitoring systemObject detection
An object detection system and method is applied to an active surveillance system for detecting at least one target object appeared in an area of interest. The object detection system includes a processor for defining the area of interest into at least a first and a second zone; a controller for assigning a first and a second weight to the first and the second zone, respectively, wherein the first weight is higher than the second weight; and a first image capturing device for capturing an image of the target object appeared in the first zone prior to capturing an image of the target object appeared in the second zone. With these arrangements, the detection of at least one target object appeared in more than one zone having a specific weight assigned thereto may be implemented with improved efficiency and accuracy in object selection and reduced interferences from environmental variables.
Owner:SUNVISION SCI
Method for loading configuration data onto a non-volatile memory and a device using the same
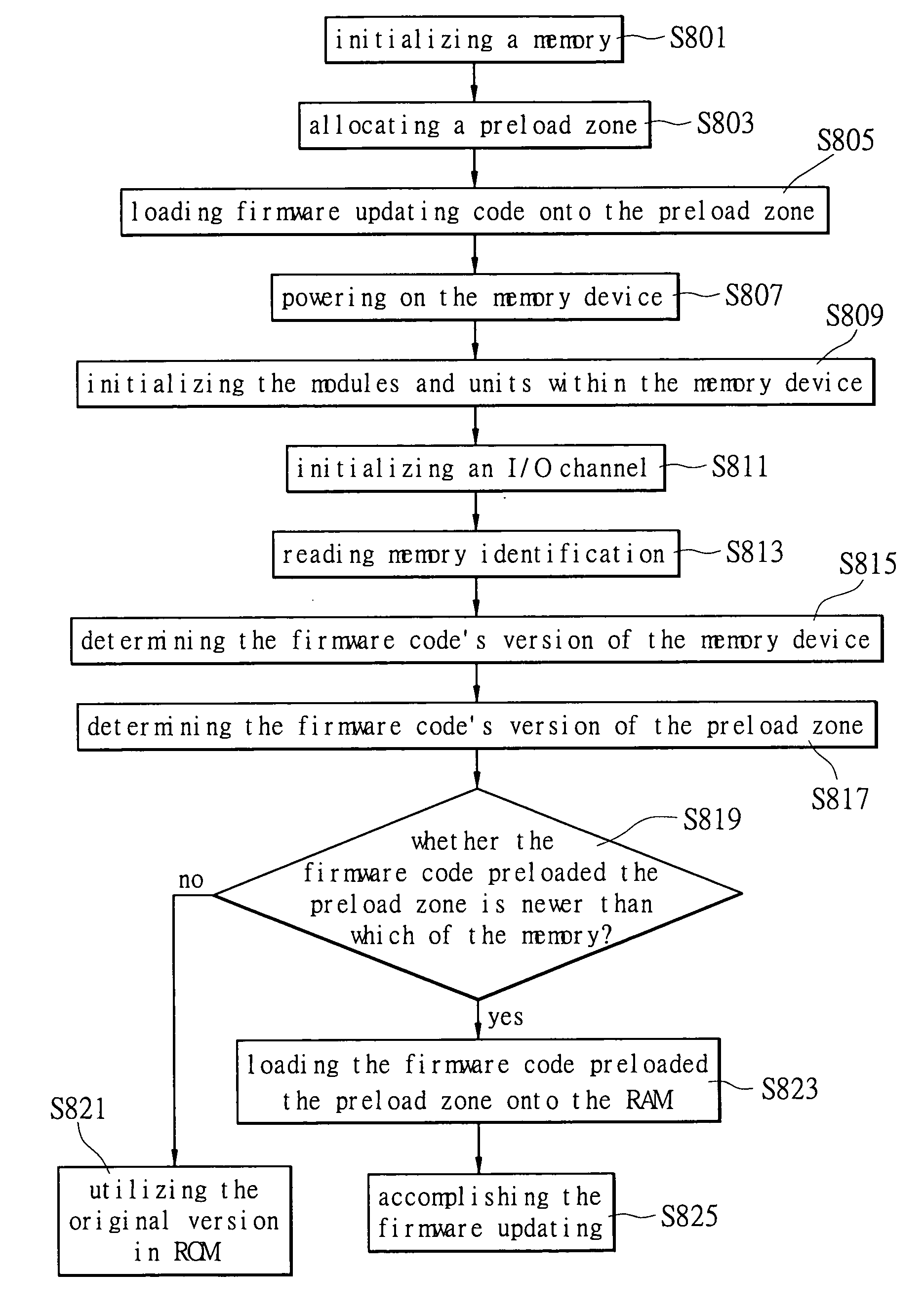
ActiveUS20070055854A1Reduce memory spaceRead-only memoriesDigital computer detailsRandom access memoryData memory
A method for loading configuration data onto a non-volatile memory and the device using the same is provided. A non-volatile memory block is preloaded with a certain compatible memory configuration data in advance when the memory device is being manufactured. The memory configuration data comprises plural parameters corresponding to the non-volatile memory. When readying the memory device, the preloaded configuration data is loaded onto a random-access memory thereof so as to save the space in a read-only memory used for storing the memory's identification and its specification. Additionally, means for loading the configuration data from the preload zone onto the random-access memory is introduced to update the firmware.
Owner:ALCOR MICRO CORP
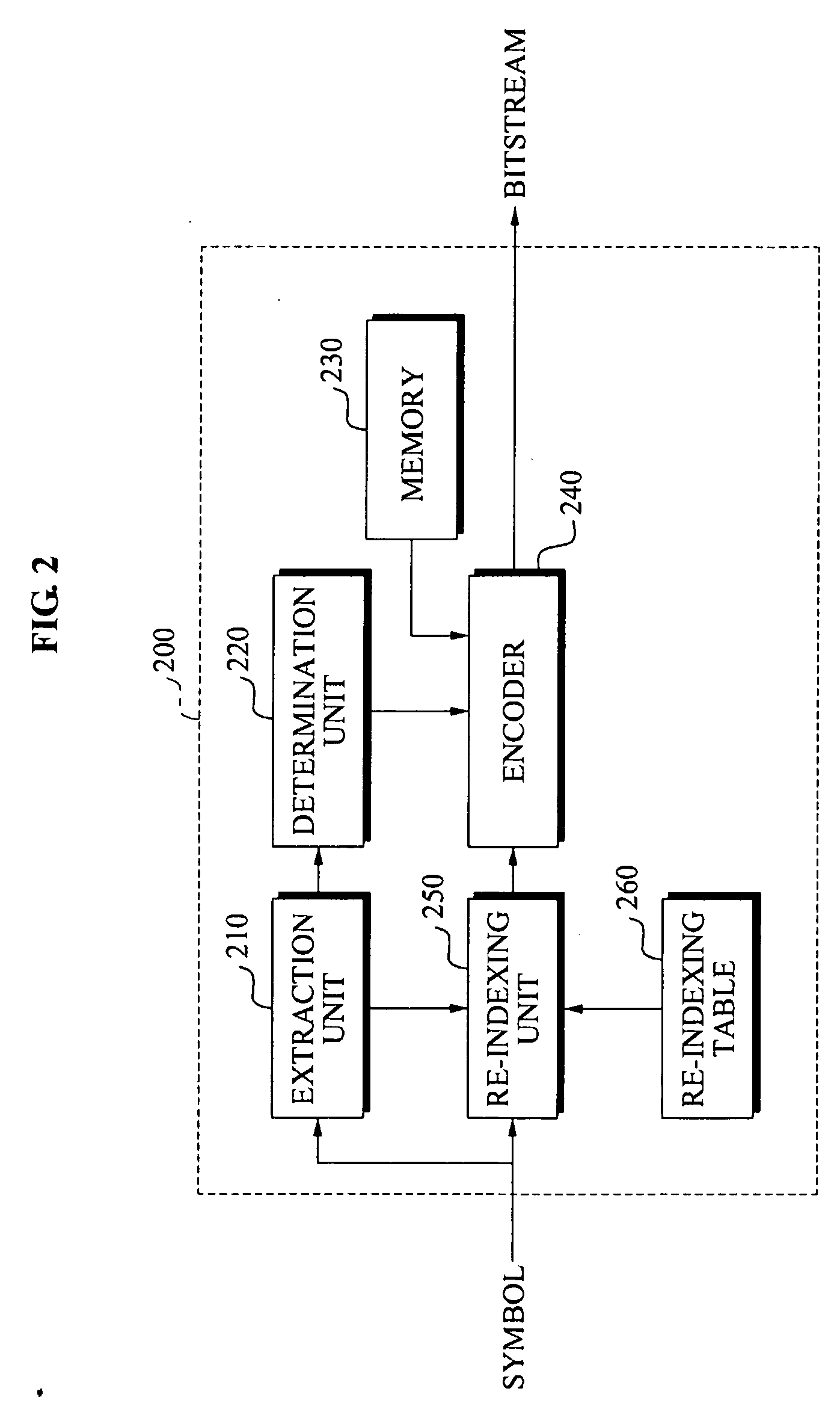
Method for the creation of a bit stream from an indexing tree
InactiveUS20060064424A1Search for indexed data is made easily and efficientlySimple indexingPulse modulation television signal transmissionData processing applicationsTheoretical computer scienceEngineering
A method is disclosed for creating a bit stream from an indexing tree including a plurality of hierarchical levels, to each of which one or several index nodes are assigned. The index nodes contain index data which is sorted in the indexing tree according to one or several given criteria. Index data of the index nodes is inserted into the bit stream, and the information concerning the position within the bit stream, where the index data of one or several index nodes of the hierarchical level located below the hierarchical level of the respective node is situated, is inserted into the bit stream for an index node.
Owner:SIEMENS AG
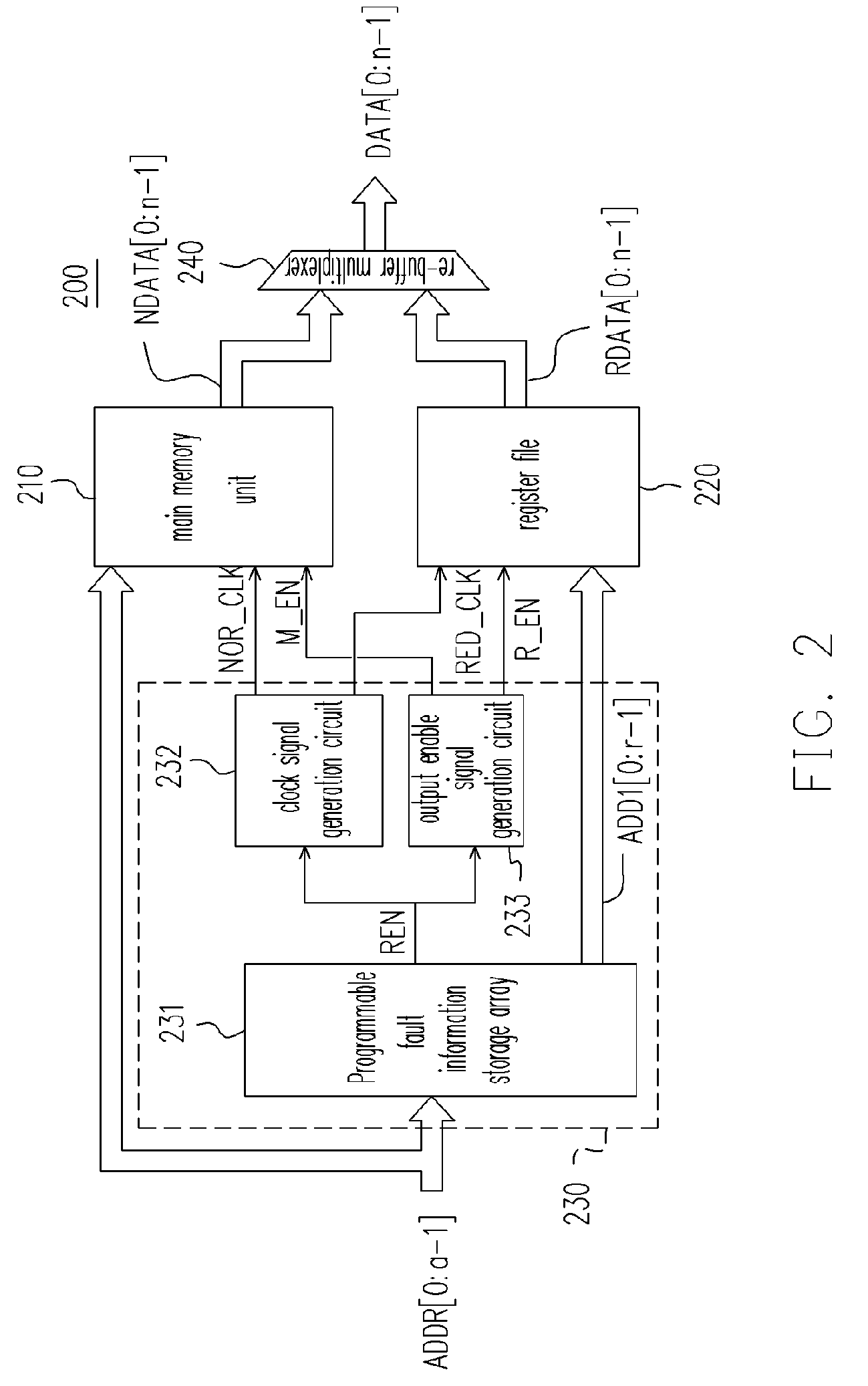
Memory structure with repairing function and repairing method thereof
InactiveUS7221604B2Improve memory efficiencyImprove access efficiencyDigital storageProcessor registerModularity
A memory structure with a repair function and a repairing method thereof are provided. The memory structure has an independent main memory unit and register file design. It also incorporates a record control unit for storing the fault information of the main memory unit. Upon receiving an access command, the memory structure determines if the main memory space pointed by the access command is faulty according to the stored fault information. When the main memory space pointed by the access command is faulty, a backup memory space is selected from the register file to replace the faulty main memory space. Therefore, the present invention can provide the convenience of a modularized design and reduce the space occupation of the register file, and also improve the access efficiency of the memory.
Owner:AMIC TECH TAIWAN
Three-dimensional reinforcement arrangement method for concrete structure on surface of circular truncated cone
ActiveCN104951632AImprove work efficiencyAccurately reflectSpecial data processing applicationsState of artRebar
The invention relates to a three-dimensional reinforcement arrangement method for a concrete structure on the surface of a circular truncated cone, and aims to solve the problem that in the prior art, a method for directly arranging reinforcements on a concrete structure on the surface of a circular truncated cone is not yet discovered. The three-dimensional reinforcement arrangement method comprises the following steps: at first, selecting a reinforcement arrangement surface of the concrete structure on the circular truncated cone, and determining circular truncated cone reinforcement arrangement guide wires according to geometric topology information of the concrete structure of the circular truncated cone and the thickness of a reinforcement protection layer; then, determining reinforcement arrangement points and an auxiliary plane generated by reinforcement objects on the reinforcement arrangement guide wires according to the spacing between reinforcements on the circular truncated cone, the number of the reinforcements and the thickness of the reinforcement protection layer; finally, generating reinforcement axes on the reinforcement arrangement points and the auxiliary plane according to reinforcement positioning points and reinforcement end parameters, calling a reinforcement template, and assigning reinforcement attribute data to the three-dimensional reinforcement objects. The method is suitable for design of reinforcement arrangement on the concrete structure.
Owner:POWERCHINA CHENGDU ENG
Apparatus and method for lossless coding and decoding
InactiveUS20100052956A1Improve coding efficiencyReduce excess spaceSpeech analysisCode conversionLossless codingMultiple context
A lossless coding and / or decoding apparatus and method. The lossless coding apparatus may read a probability model corresponding to each of a plurality of context groups. Here, the probability model stored in a memory may be generated by grouping a context. The lossless coding apparatus may code a symbol using the probability model and generate a bitstream. The lossless coding apparatus may enhance coding efficiency and reduce an amount of space utilized by the memory.
Owner:SAMSUNG ELECTRONICS CO LTD
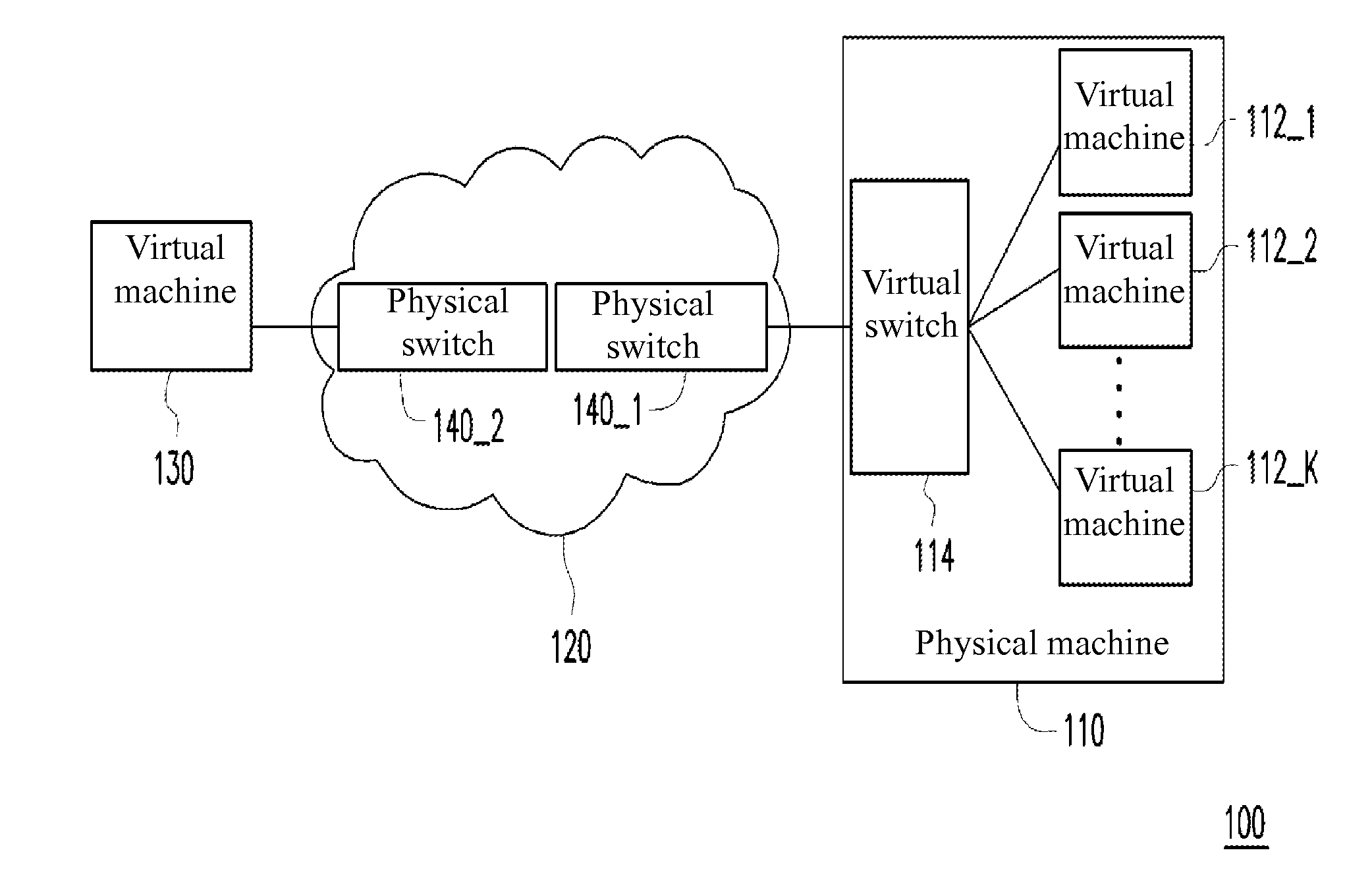
Network communication system and network communication method
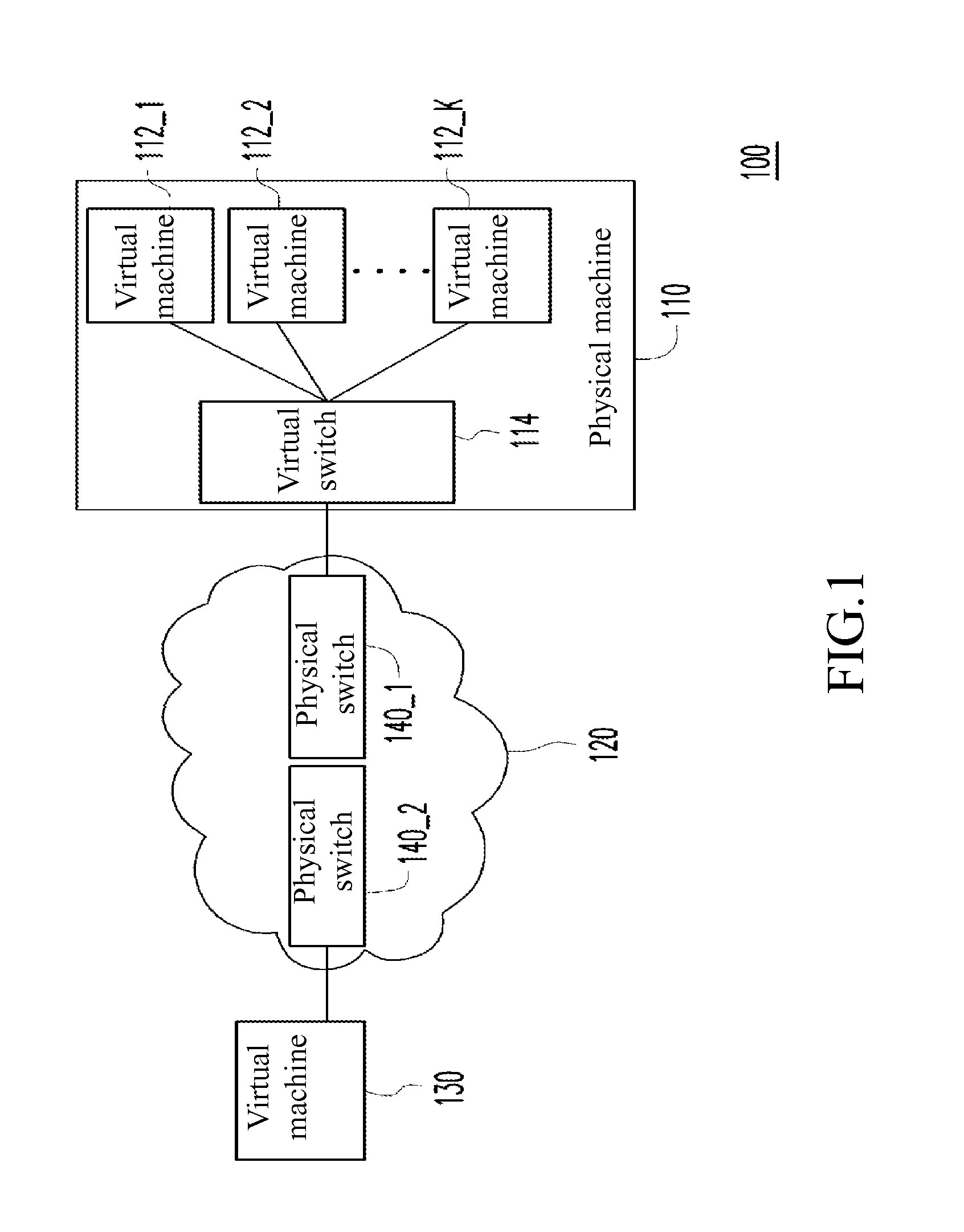
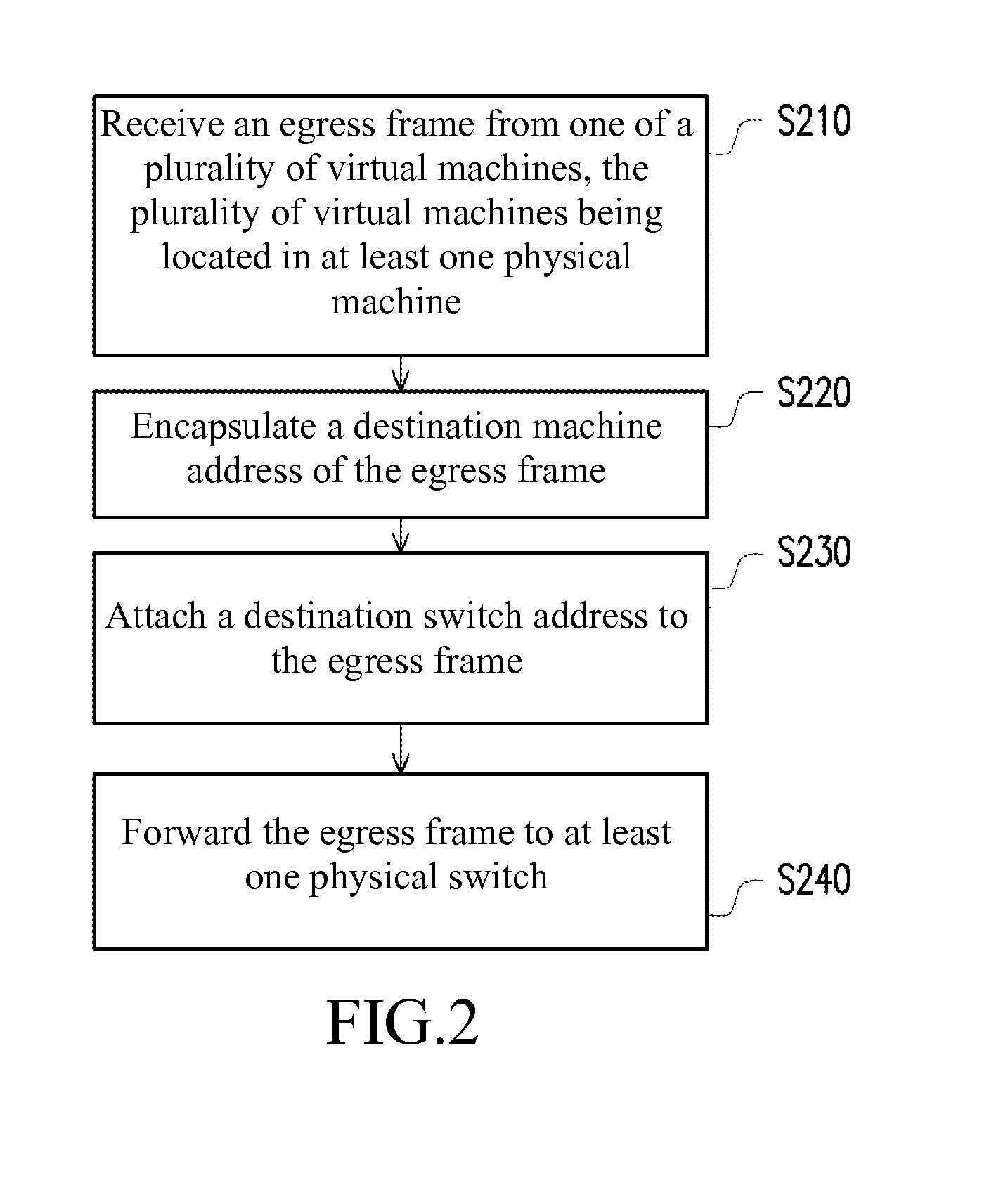
ActiveUS20140119375A1Reduce storage spaceReduce storage capacityData switching by path configurationComputer hardwareNetwork communication
A network communication system comprises a cloud network and at least one physical machine. The cloud network comprises at least one physical switch. Each the physical machine comprises a plurality of virtual machines and a virtual switch. Each of the virtual machines is connected to the at least one physical switch in the cloud network through the virtual switch. The virtual switch encapsulates a destination machine address of an egress frame sent by the virtual machines, attaches a destination switch address to the egress frame to be forwarded to the at least one physical switch, and receives and analyzes an ingress frame obtained from the at least one physical switch, so as to convert the destination switch address of the ingress frame to the destination machine address, for forwarding the ingress frame to one of the virtual machines.
Owner:INVENTEC PUDONG TECH CORPOARTION +1
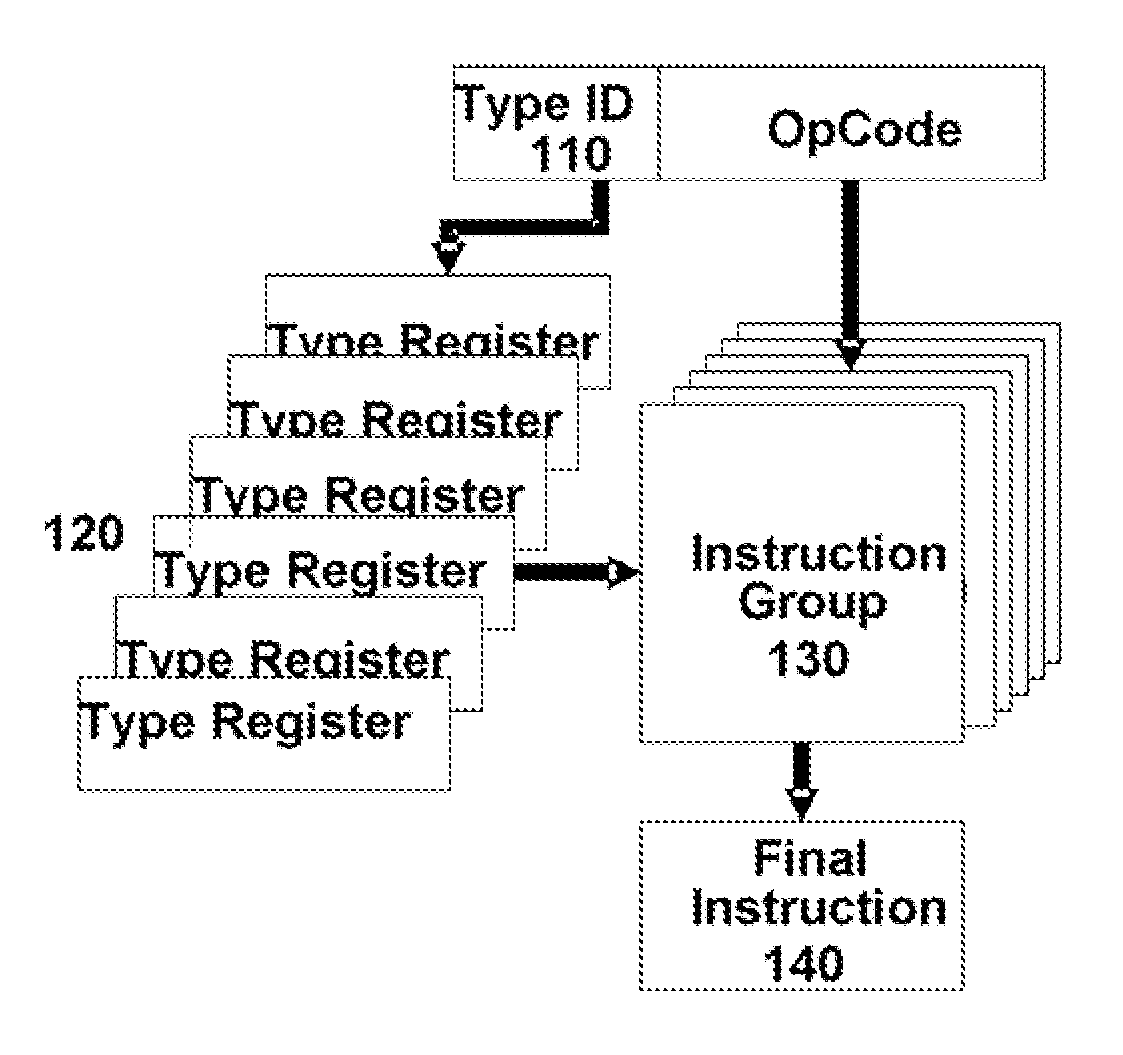
Processing Architectures with Typed Instruction Sets
ActiveUS20080082799A1Reduce volumeReduce memory spaceRegister arrangementsInstruction analysisProcessor registerProcessing element
An architecture for microprocessors and the like in which instructions include a type identifier, which selects one of several interpretation registers. The interpretation registers hold information for interpreting the opcode of each instruction, so that a stream of compressed instructions (with type identifiers) can be translated into a stream of expanded instructions. Preferably the type identifiers also distinguish sequencer instructions from processing-element instructions, and can even distinguish among different types of sequencer instructions (as well as among different types of processing-element instructions).
Owner:RPX CORP
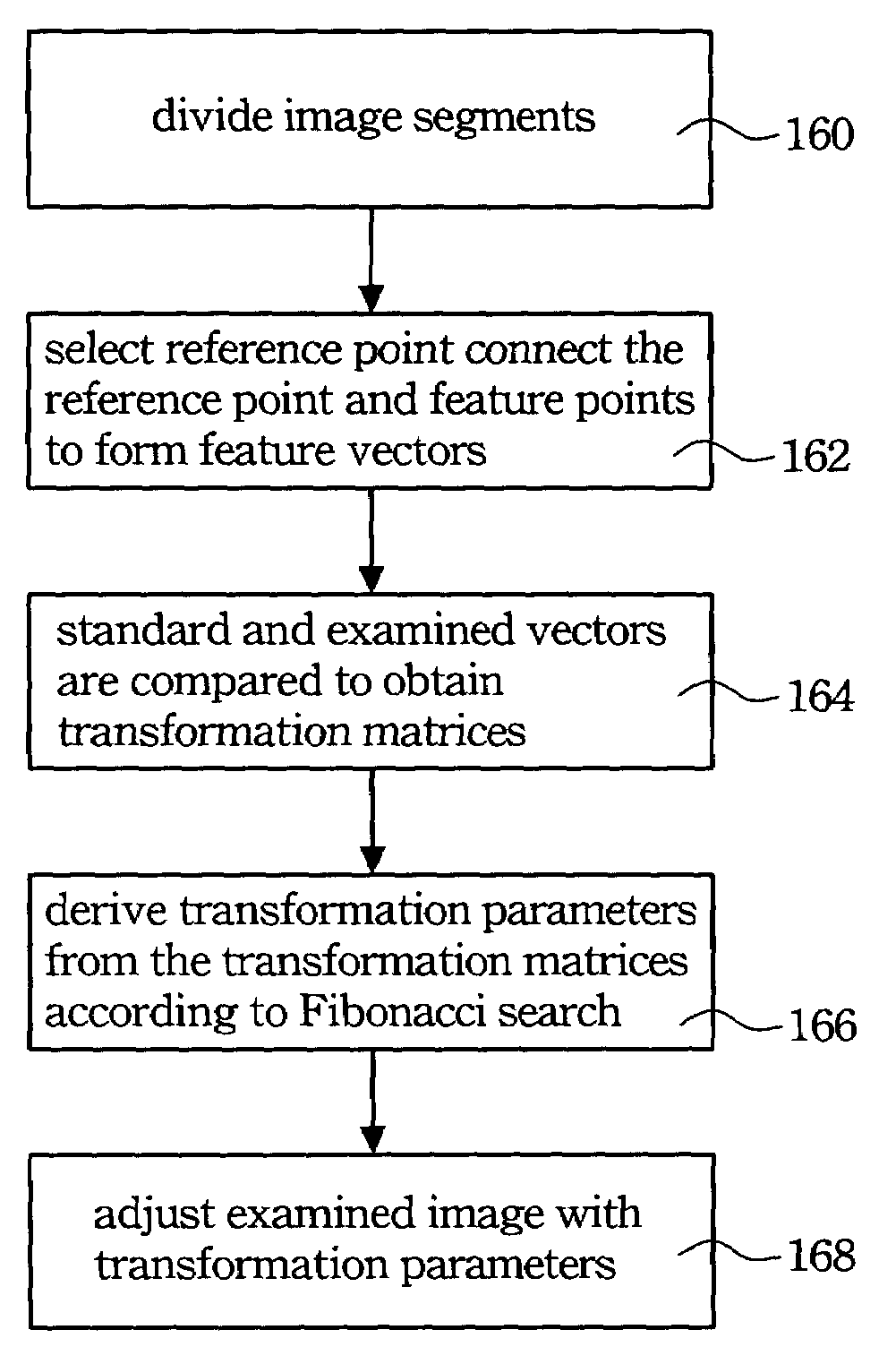
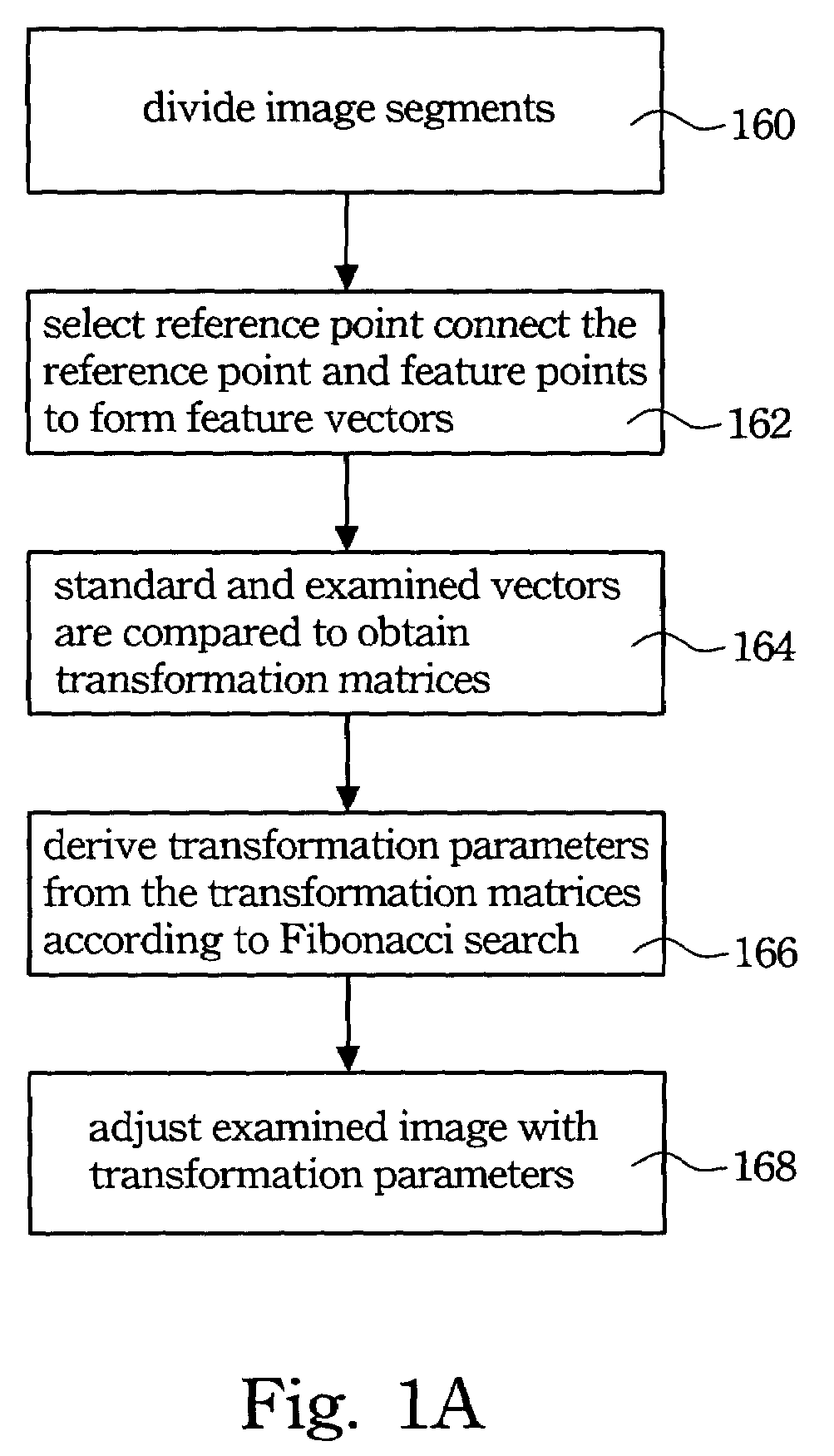
Segment based image registration method
InactiveUS7400783B2Improve accuracyIncrease flexibilityCharacter and pattern recognitionCathode-ray tube indicatorsServomechanismComputer science
An examined image is segmented, where a segment thereof may correspond to an area scan image or a line scan image of which the size is defined by considering the performance of the servo mechanism. In the segment, vectors between feature points of the examined image and a standard image are compared, and based on the required tolerance, a Fibonacci search having a predetermined number of iterations is used for matching an optimal corresponding relationship between the examined image and the standard image.
Owner:NAT TAIWAN UNIV OF SCI & TECH
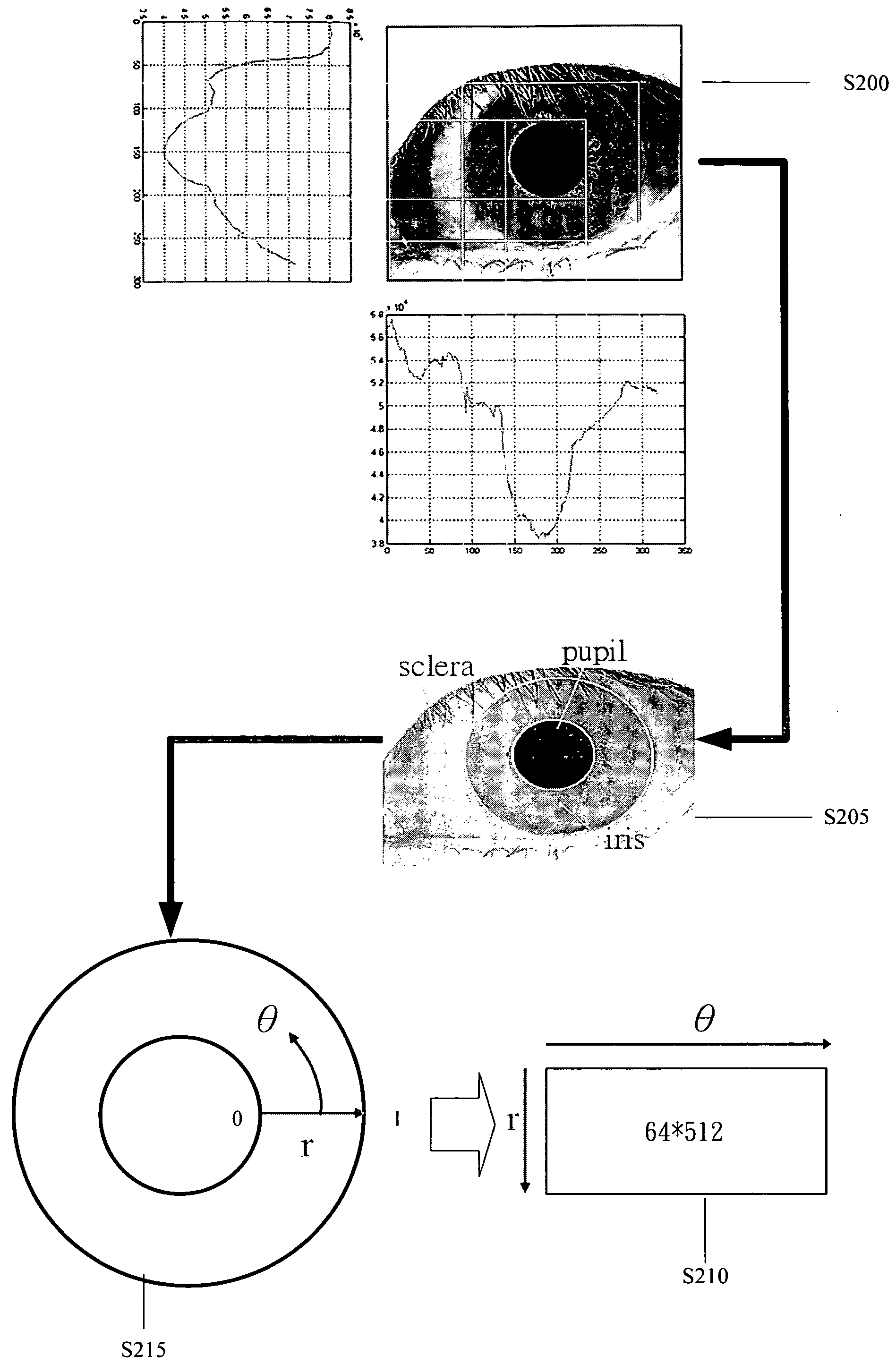
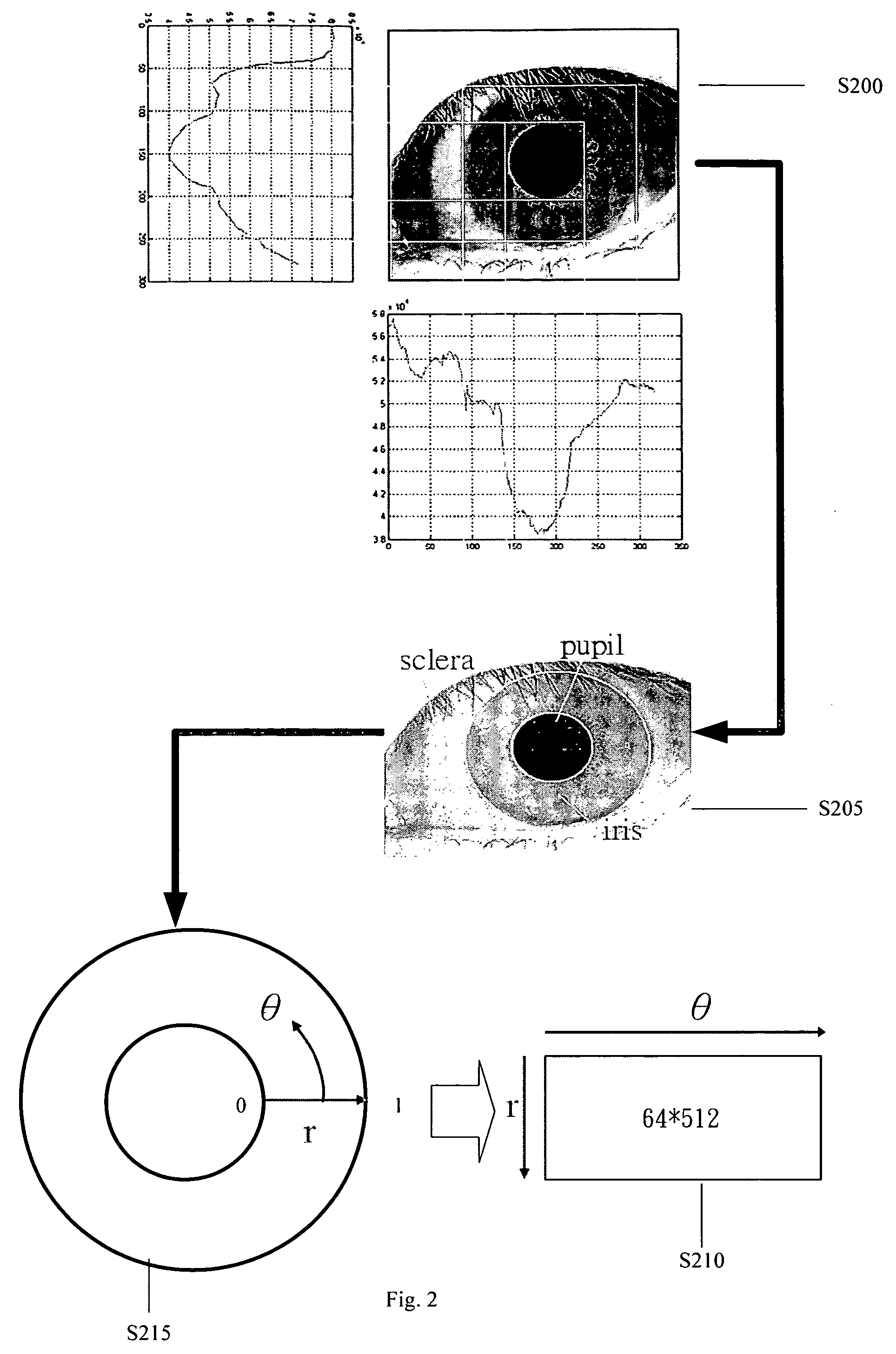
Iris recognition method
InactiveUS20080095411A1Simplify extraction and reconstructionReduce memory spaceAcquiring/recognising eyesFeature vectorPattern matching
The present invention disclose an iris recognition method, which utilizes a matching pursuit algorithm to simplify the extraction and reconstruction of iris features and reduce the memory space required by each iris feature vector without the penalty of recognition accuracy. The iris recognition method of the present invention comprises an iris-localization component and a pattern matching component. The iris-localization component locates the iris region via the color difference between different portions of the eyeball. The primary iris features are extracted from iris information and transformed into a sequence of iris feature vectors by a matching pursuit algorithm. Thus, the iris image can be represented by a sequence of atoms, and each atom contains base, amplitude and location. Then, the comparison between the feature vectors of two irises is performed to determine whether the two irises match.
Owner:NAT CHIAO TUNG UNIV
Method and apparatus for data normalization
ActiveUS7356599B2Avoid transmission delaysReduce ambiguityMultiple digital computer combinationsData switching networksTraffic capacityEnd system
A method that allows the normalization of traffic data that is simultaneously transferred to a network intrusion detection system (NIDS) and monitored end-systems located in a network, such as a TCP / IP network, in which packets of data such as IP datagrams, are fragmented and reassembled. Accordingly, the information of received fragments and / or the topology of the network comprising the network intrusion detection system (NIDS) and the monitored end-systems are entered into a normalization table, that is dynamically established and maintained. Subsequently packets of data such as IP datagrams are modified, redirected or discarded in case that ambiguities are detected when comparing information contained in the normalization table with information contained in the headers of the received data packets.
Owner:TREND MICRO INC
Method and device for compressing table based on finite automata, method and device for matching table
ActiveUS20100293153A1Large degree of redundancySave memory spaceDigital data processing detailsRelational databasesAutomatonAlgorithm
Owner:HUAWEI TECH CO LTD
Method for indirect tire pressure monitoring and tire pressure monitoring system
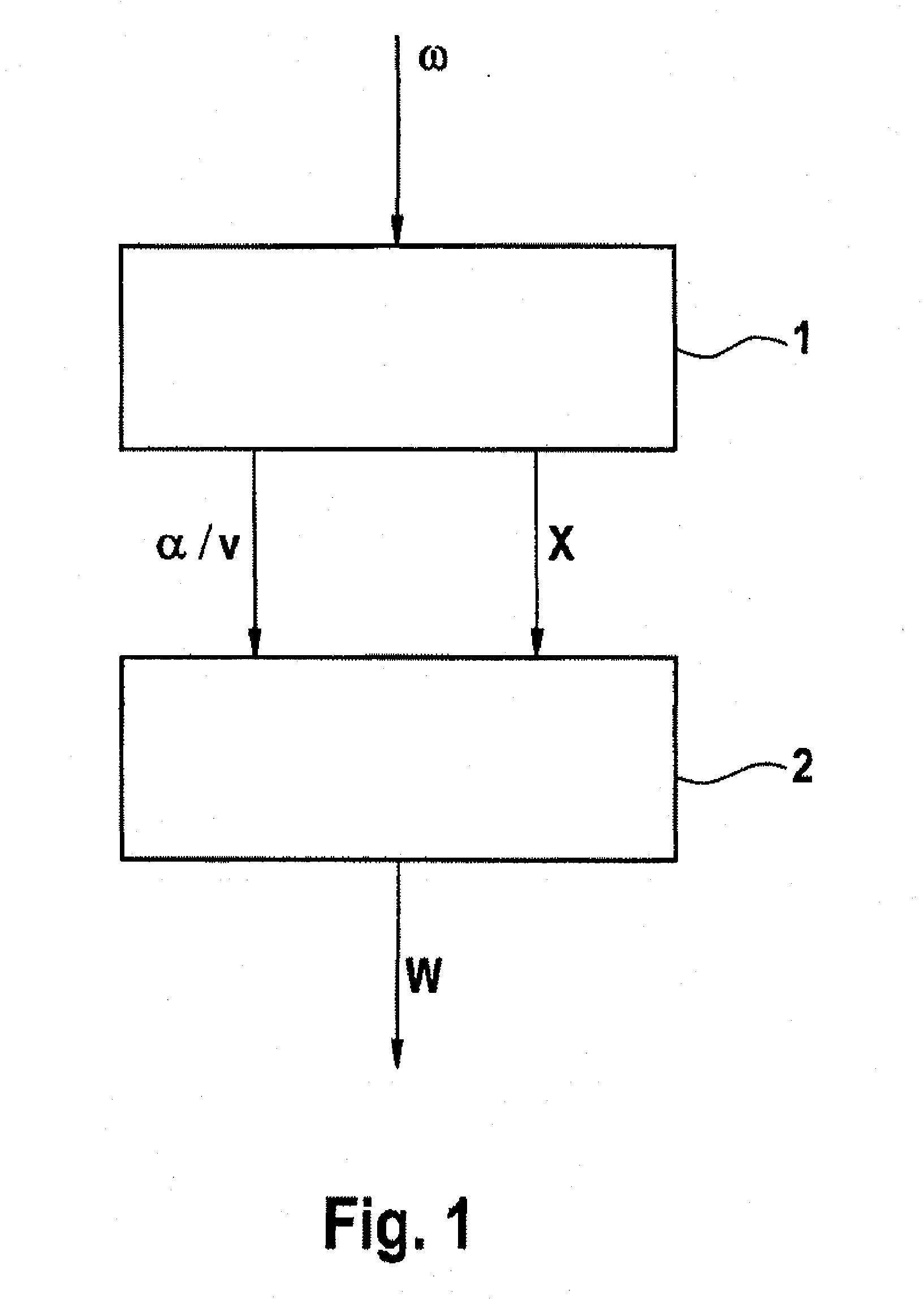
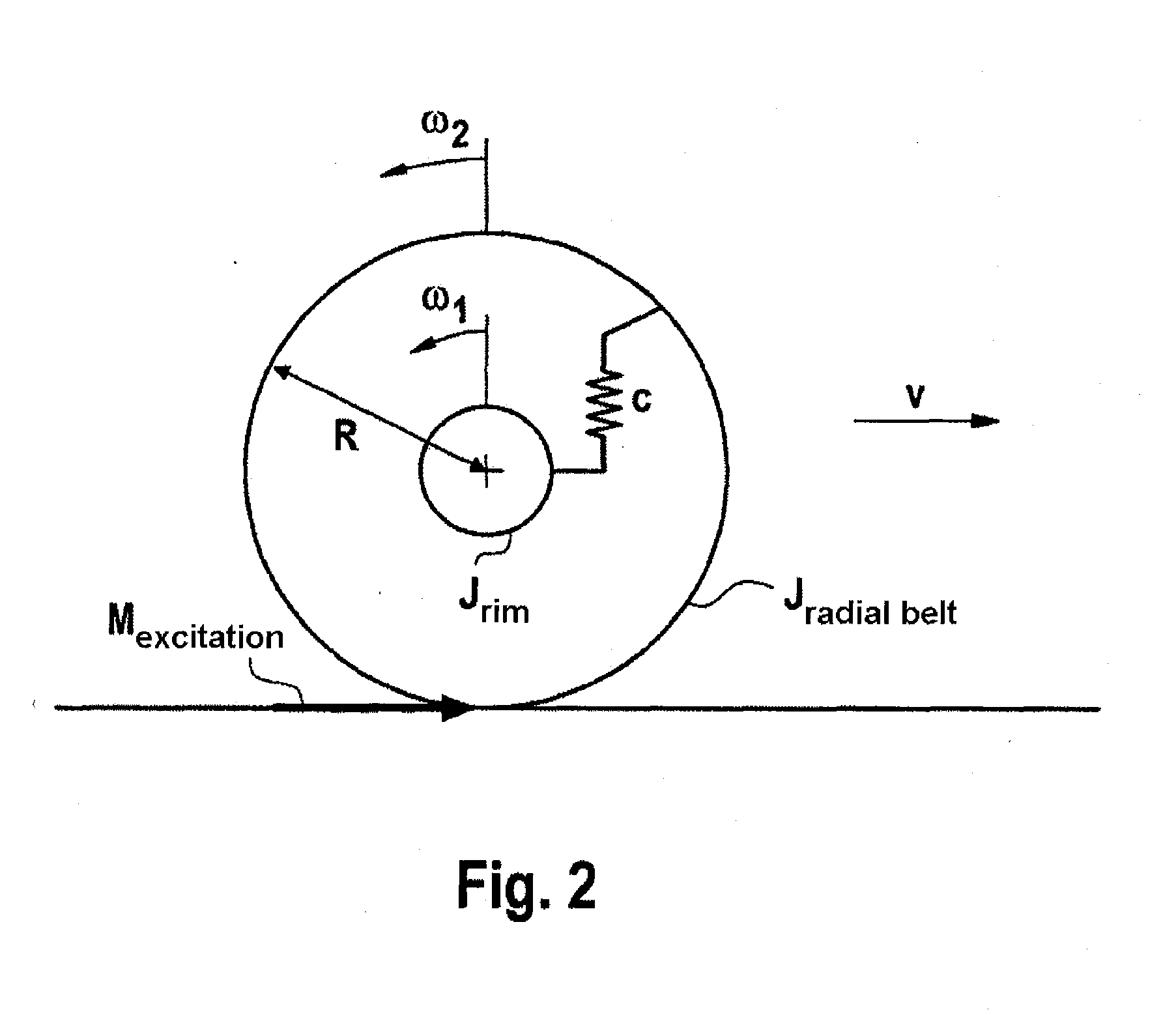
InactiveUS20100211250A1Reliable warningEasy to carryVehicle testingRegistering/indicating working of vehiclesEngineeringTire-pressure monitoring system
A system and method for indirect tire pressure monitoring. A pressure loss variable (X, f, c) is determined based on an analysis of an oscillation behavior of a tire of a motor vehicle for the detection of a pressure loss in the tire of a wheel. A variable (α, α / v) representing an increase (α) of a wheel torque slip curve, or depending on an increase (α) of a wheel torque slip curve (α / v), is determined from the oscillation behavior of the tire, and the variable (α, α / v) and the pressure loss variable (X, f, c) are used for detecting the pressure loss.
Owner:CONTINENTAL TEVES AG & CO OHG
Coding method and system with an adaptive bitplane coding mode
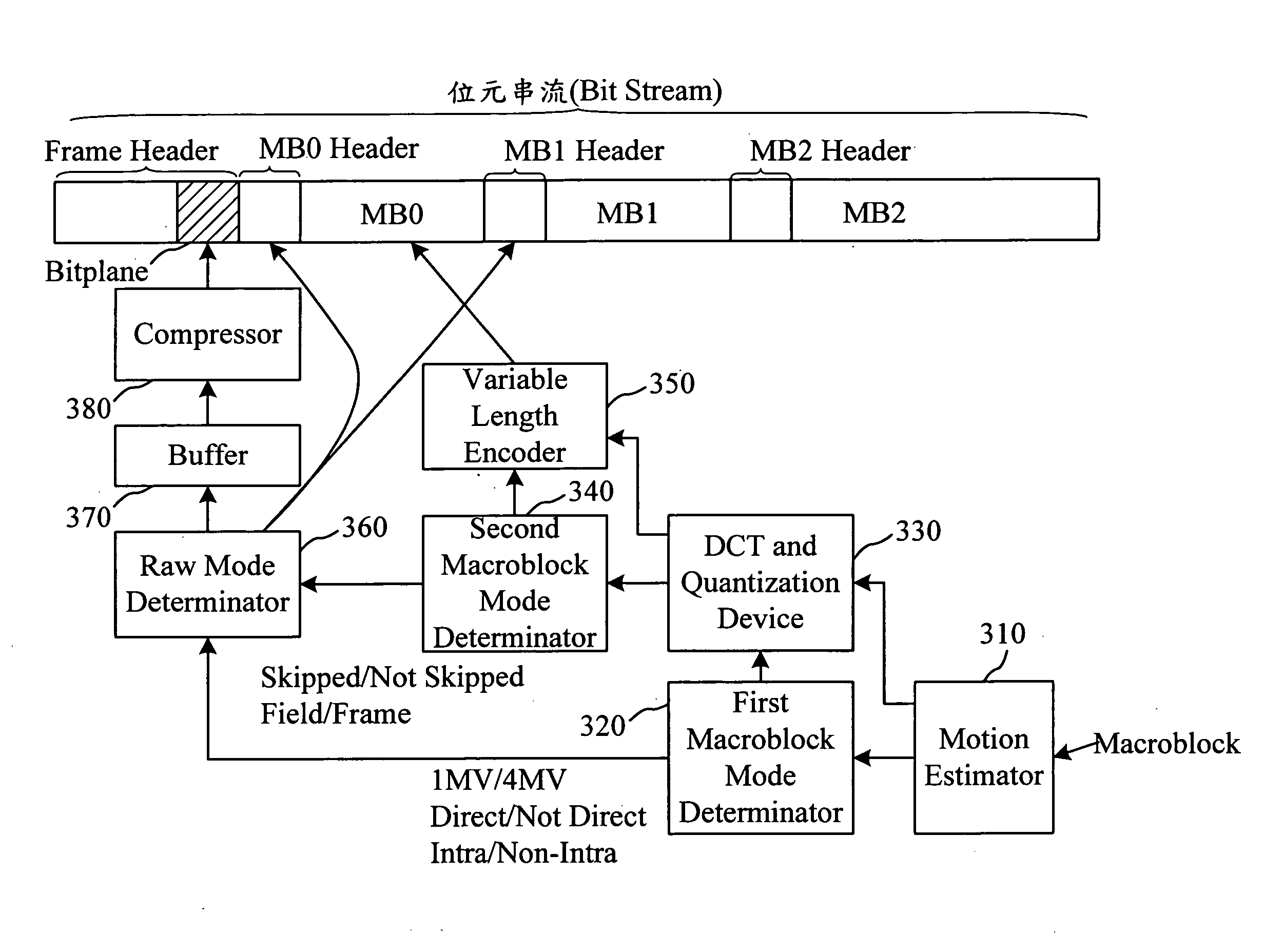
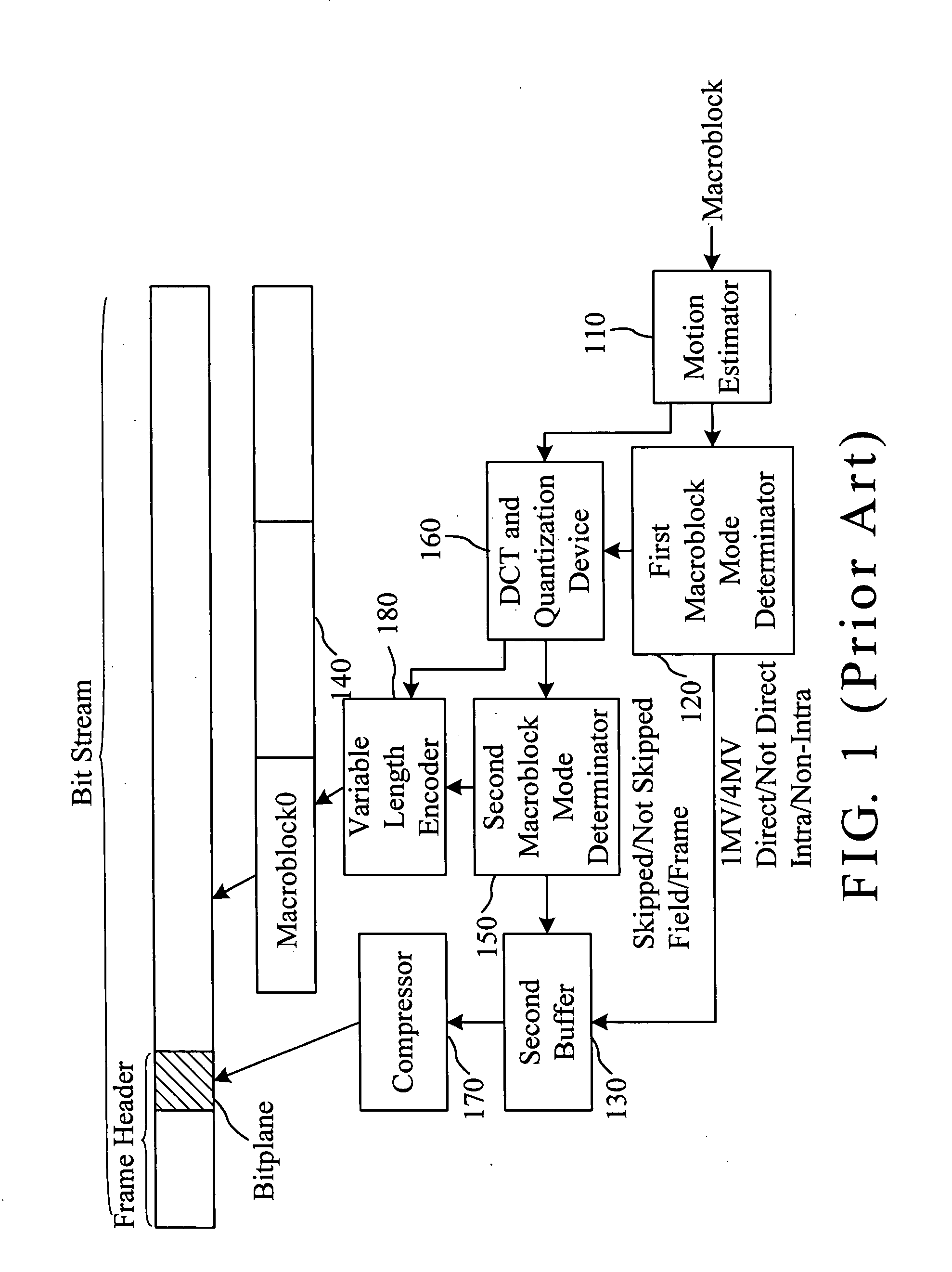
InactiveUS20080063290A1Reduce hardware costsReduce memory spaceCharacter and pattern recognitionDigital video signal modificationComputer architectureBit plane coding
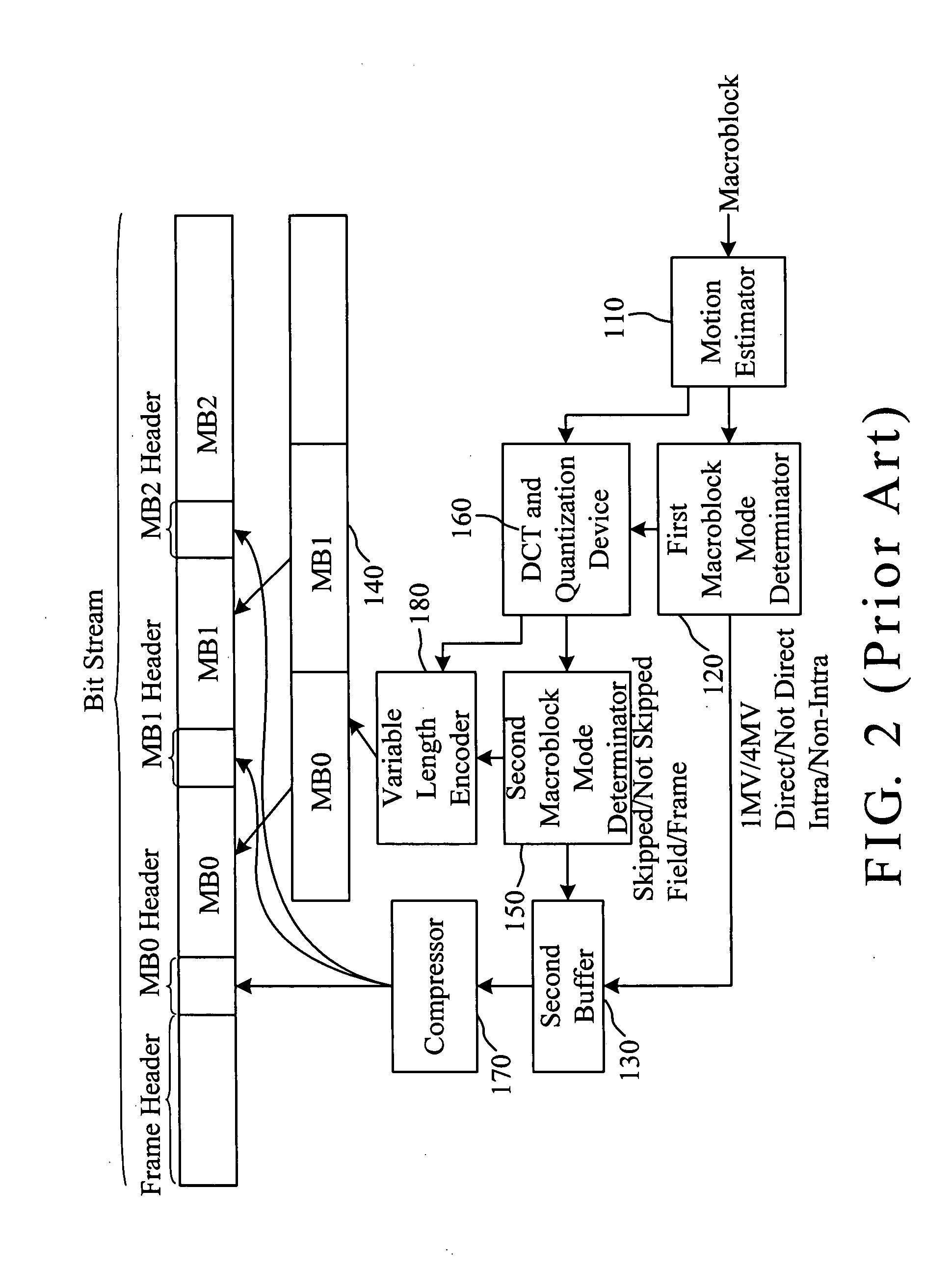
A coding method and system with an adaptive bitplane coding mode is provided to code multiple bitplanes of a frame consisting of multiple macroblocks. Each bitplane consists of macroblock modes used by the macroblocks of the frame. The method includes the steps of: (A) initializing a bitplane coding mode of the frame as a compress mode; (B) coding the frame and the bitplanes to thereby obtain coded bitplanes, and calculating the bit number of coded bitplanes; (C) calculating the bit number of uncoded bitplanes; (D) executing step (A) when the bit number of coded bitplanes is smaller than the bit number of uncoded bitplanes; (E) initializing the bitplane coding mode of the frame as a raw mode when the bit number of coded bitplanes is not smaller than the bit number of uncoded bitplanes.
Owner:SUNPLUS TECH CO LTD
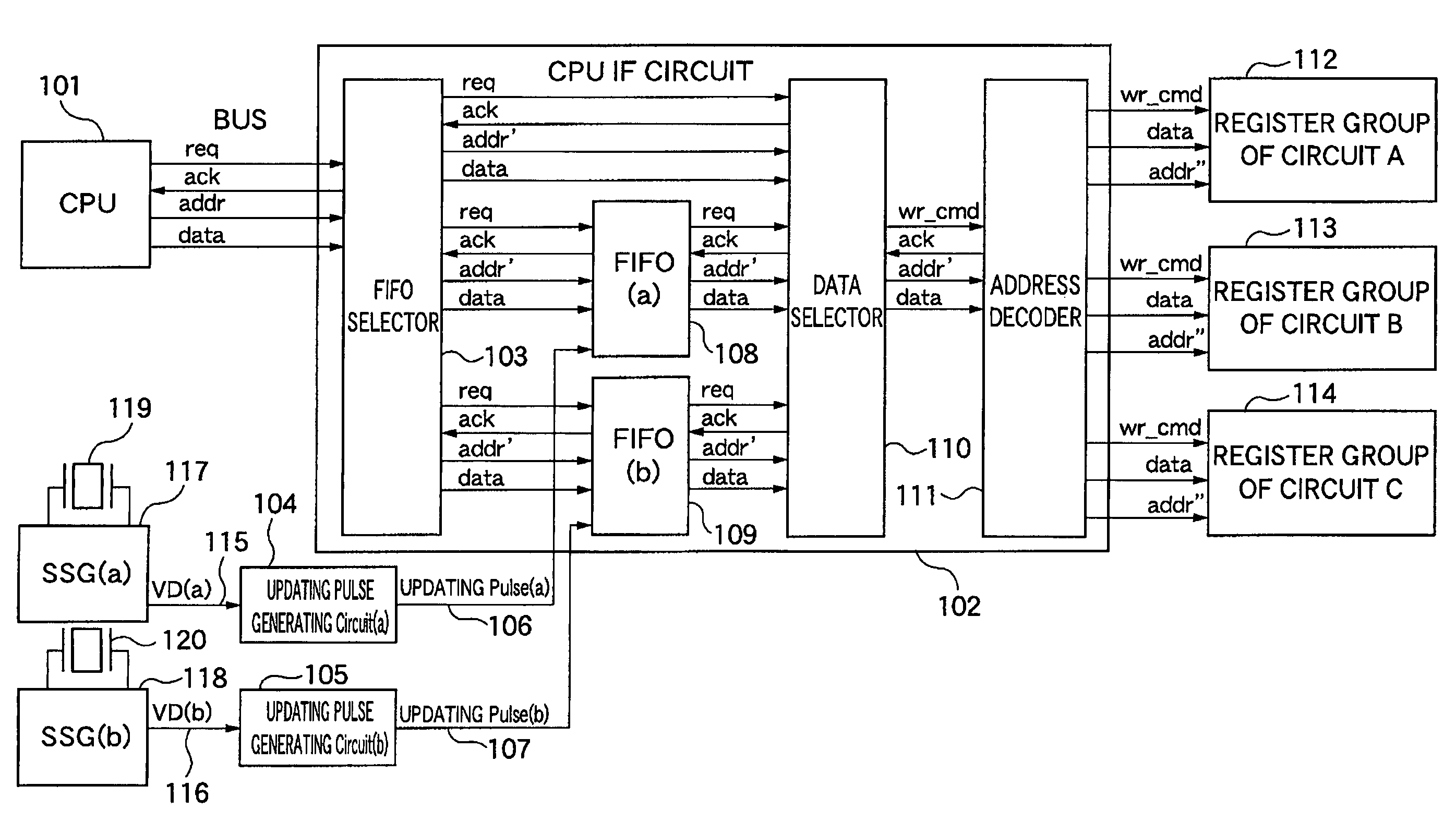
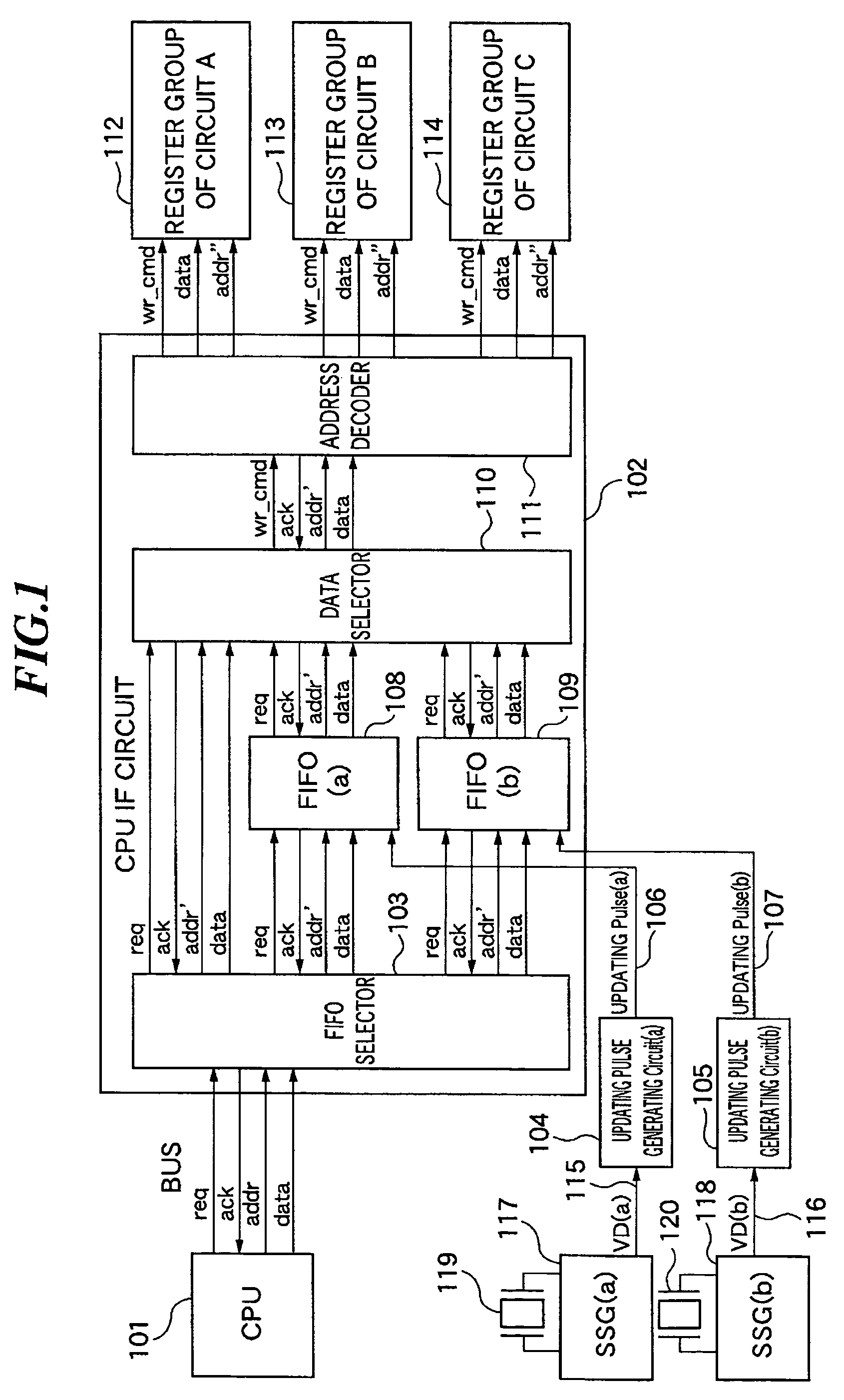
Register configuration control device, register configuration control method, and program for implementing the method
InactiveUS7512021B2Possible to updateImprove scaleCathode-ray tube indicatorsDigital storageRegister allocationData selection
Owner:CANON KK
Support of the determination of a correlation
InactiveUS7359429B2Reduce memory spaceReduce areaTime-division multiplexAmplitude-modulated carrier systemsComputer scienceSoftware
Owner:NOKIA CORP
Method for accessing a data entity and its versions
InactiveUS7788239B2Reduce memory spaceDigital data processing detailsSpecial data processing applicationsParallel computingData entity
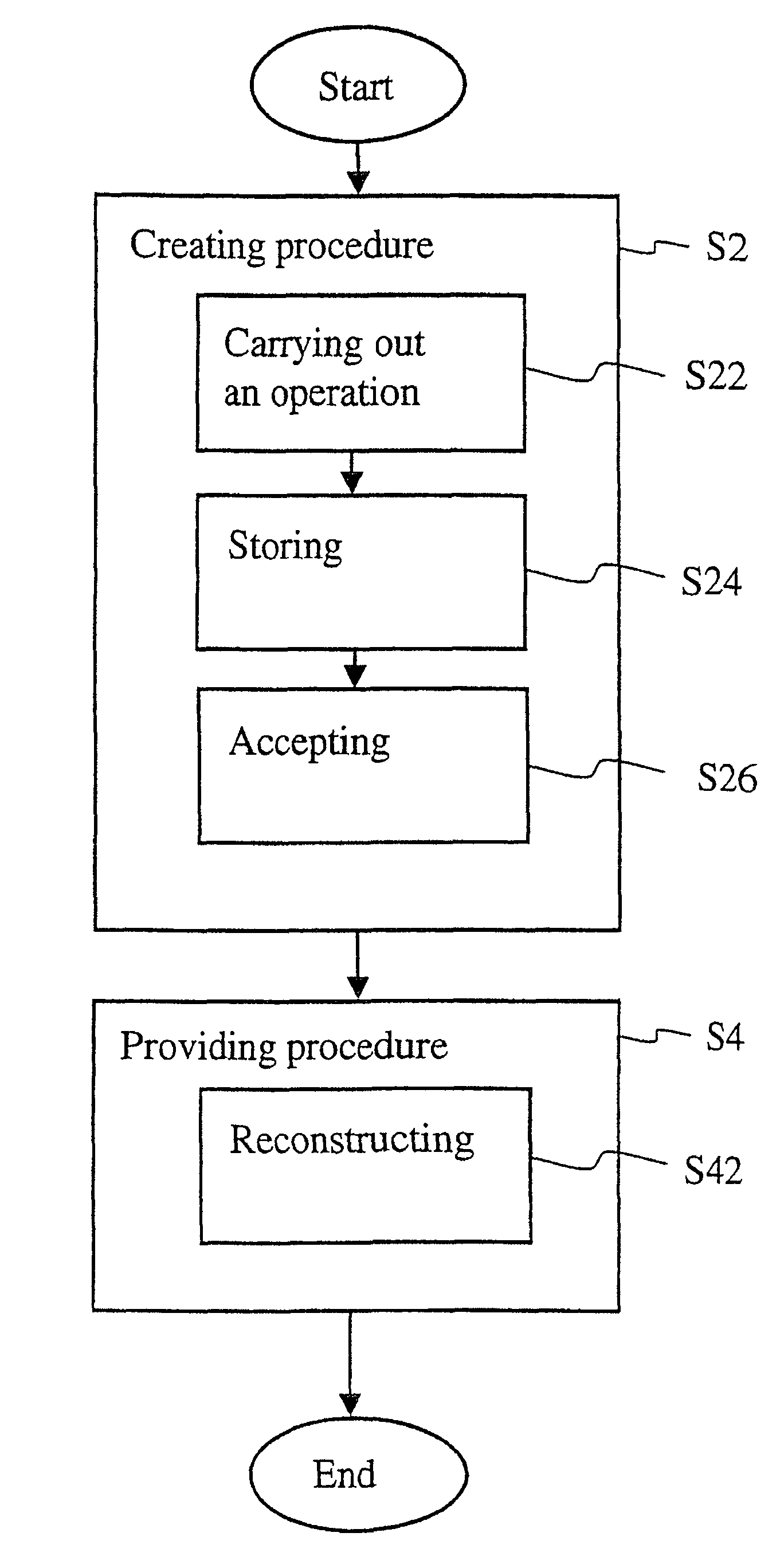
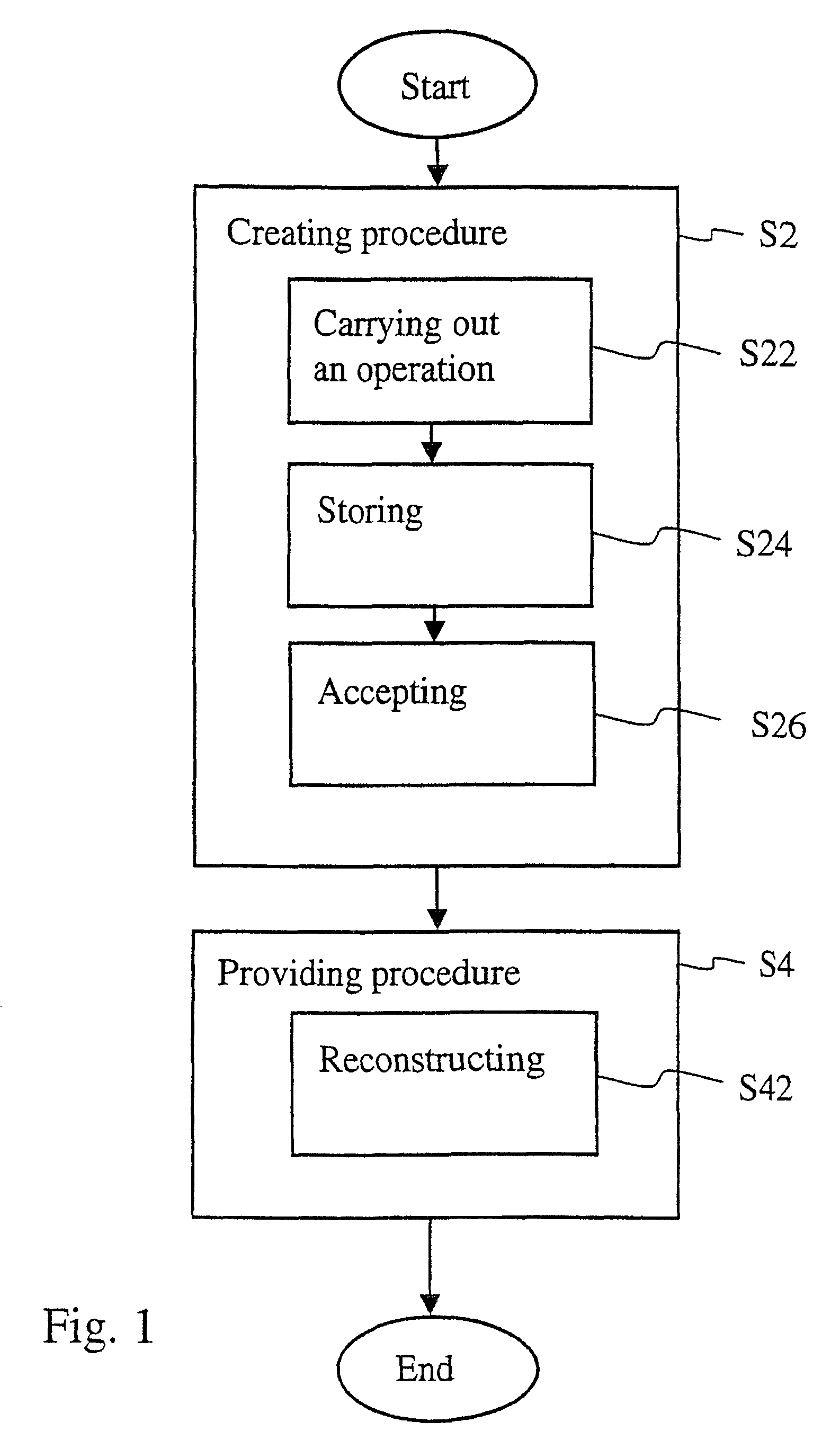
A method provides access to a data entity having a basis version and the creation of derived versions. The method includes a creating procedure for creating a derived version, by carrying out one or more operations on the basis version, storing them, and accepting them. The method further includes a providing procedure for providing access to the derived version through first addresses mapped to second addresses of the basis version and of the accepted one or more operations, by reconstructing the derived version based on the basis version and the accepted one or more operations.
Owner:GLOBAL INFINIPOOL
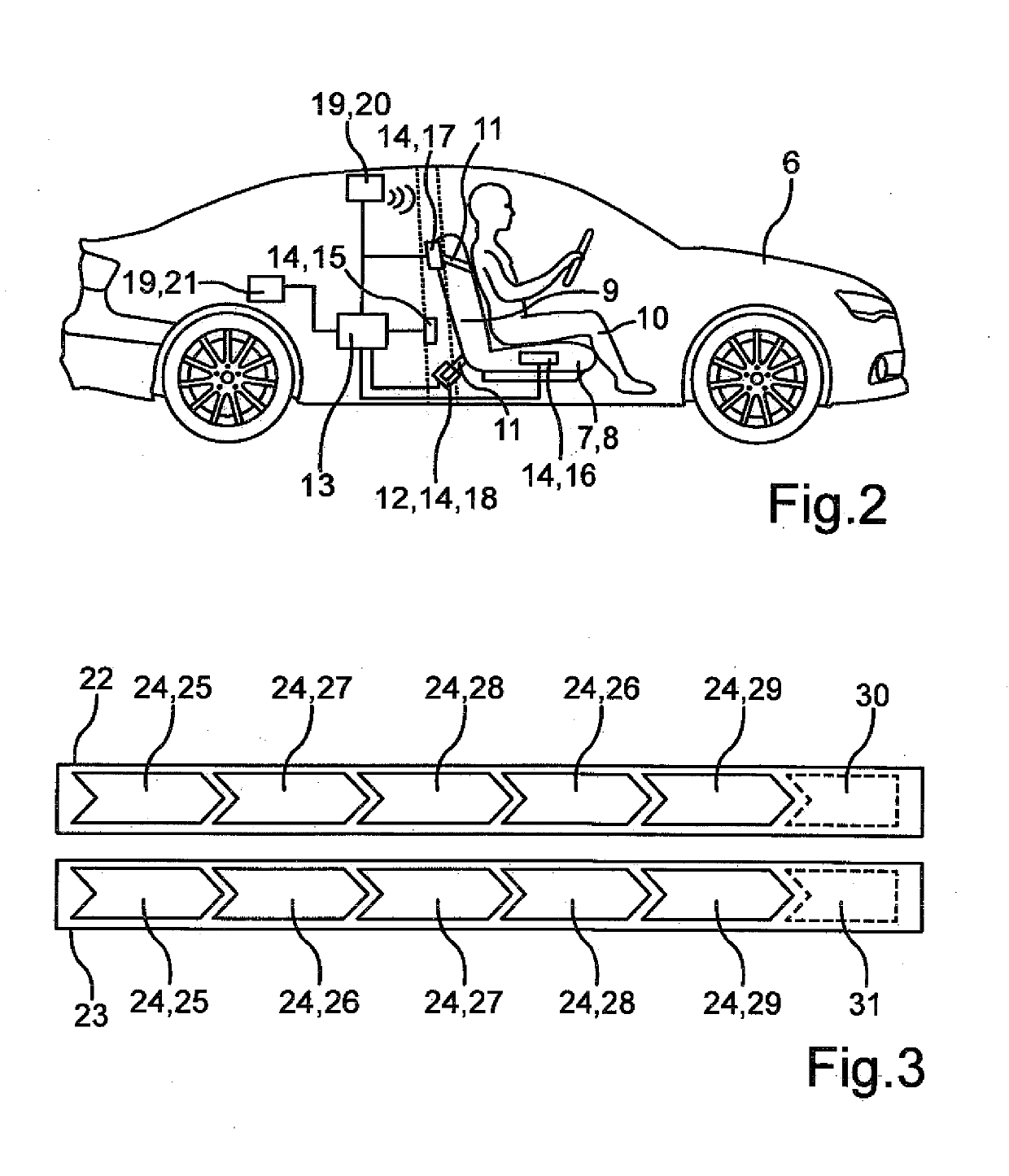
Method for operating a safety system for a motor vehicle, safety system and motor vehicle
ActiveUS20190111889A1Enhanced securityImprove visibilityBelt control systemsPedestrian/occupant safety arrangementSafe systemSeat belt
In a method for operating a safety system of a motor vehicle, a corresponding safety system, and a motor vehicle equipped with such safety system, status signals from several sensor devices are captured by the safety system, wherein the status signals indicate respective status change of a functional unit of the motor vehicle. Thereafter, a chronological order of the status changes is determined and evaluated to detect a consistency or an inconsistency with the proper application of a seat belt of the motor vehicle. If an inconsistency is detected and it persists over a predetermined period of time, a control signal is transmitted by the safety system to a safety device of the motor vehicle.
Owner:AUDI AG
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com