Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
148results about How to "Enhanced security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
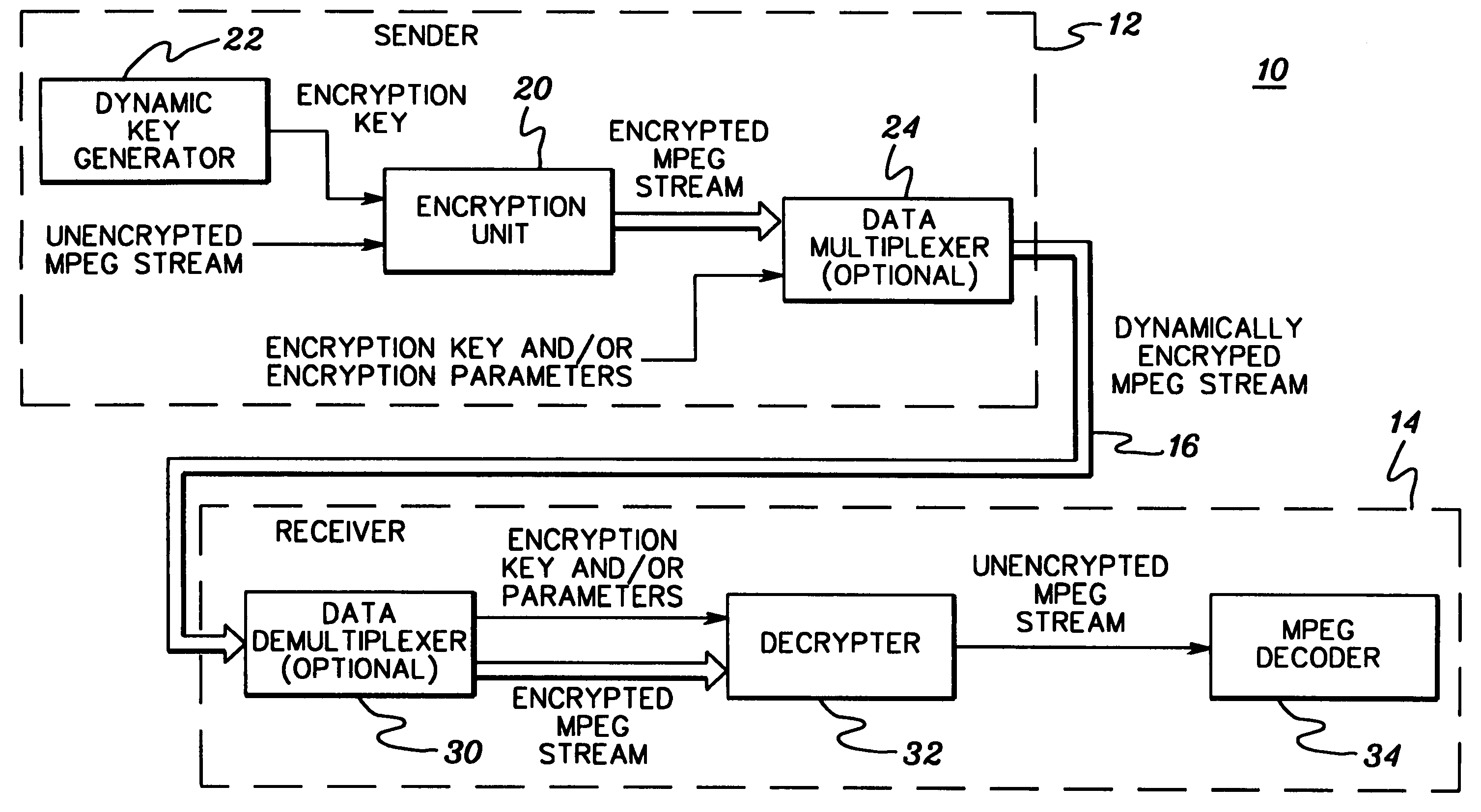
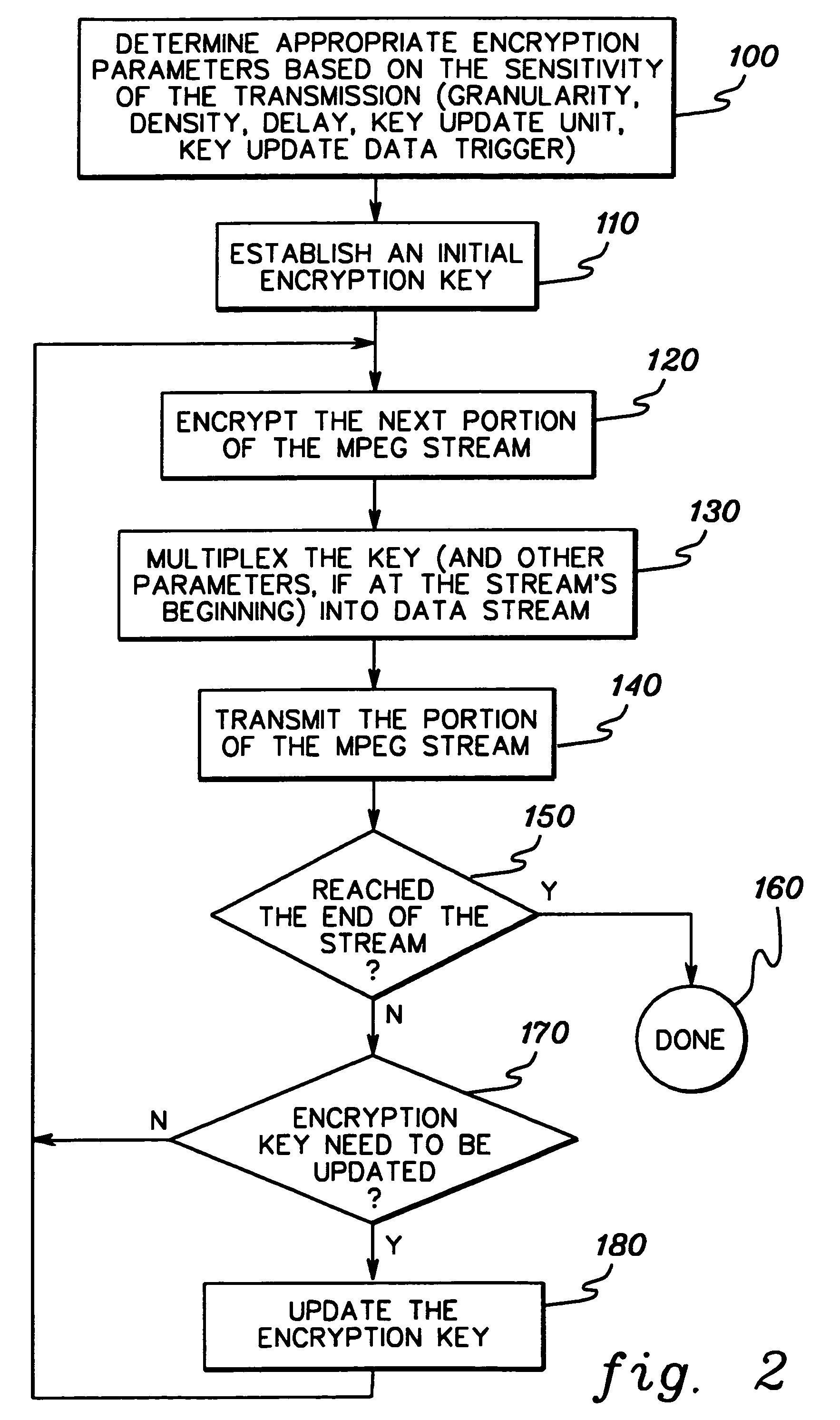
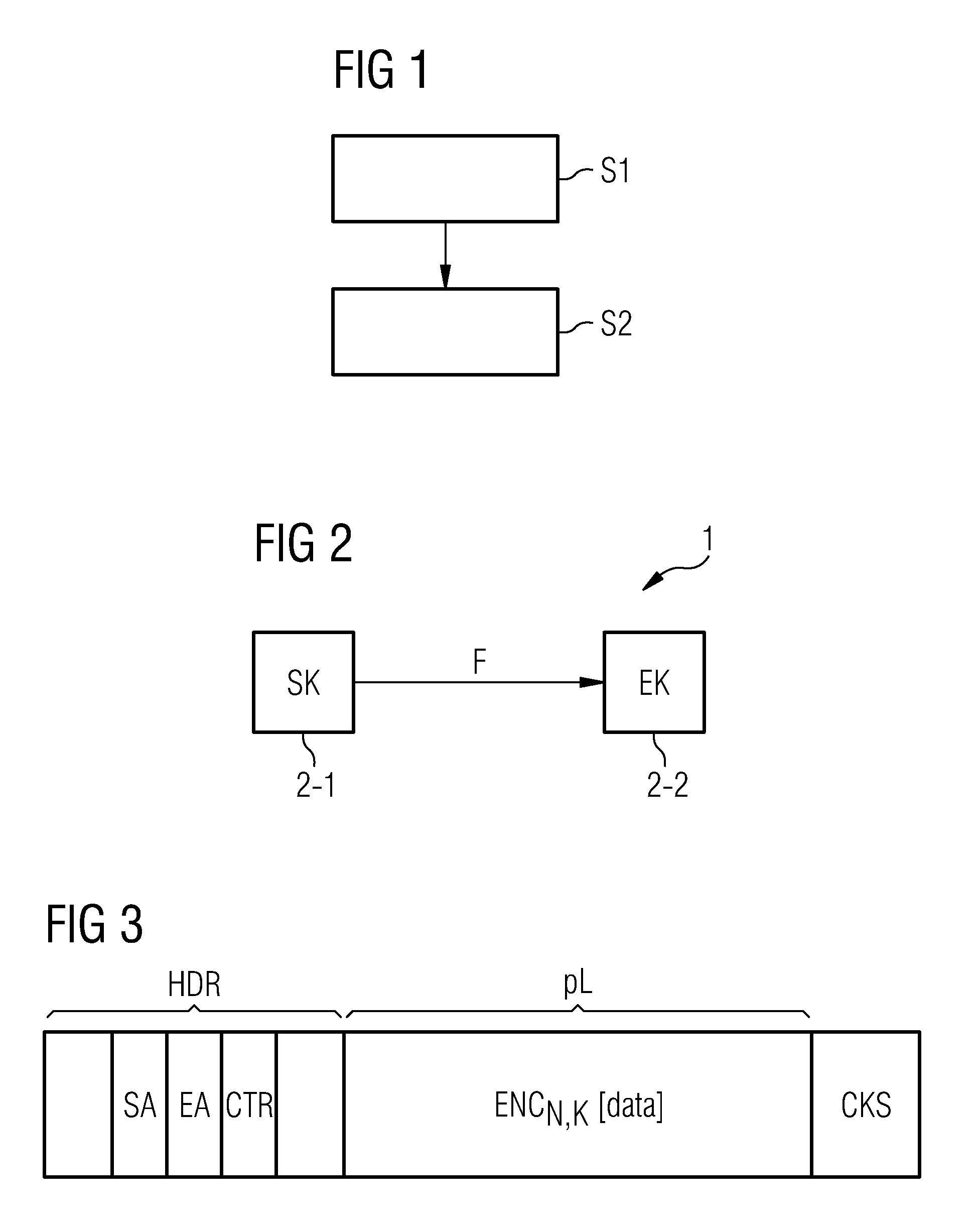
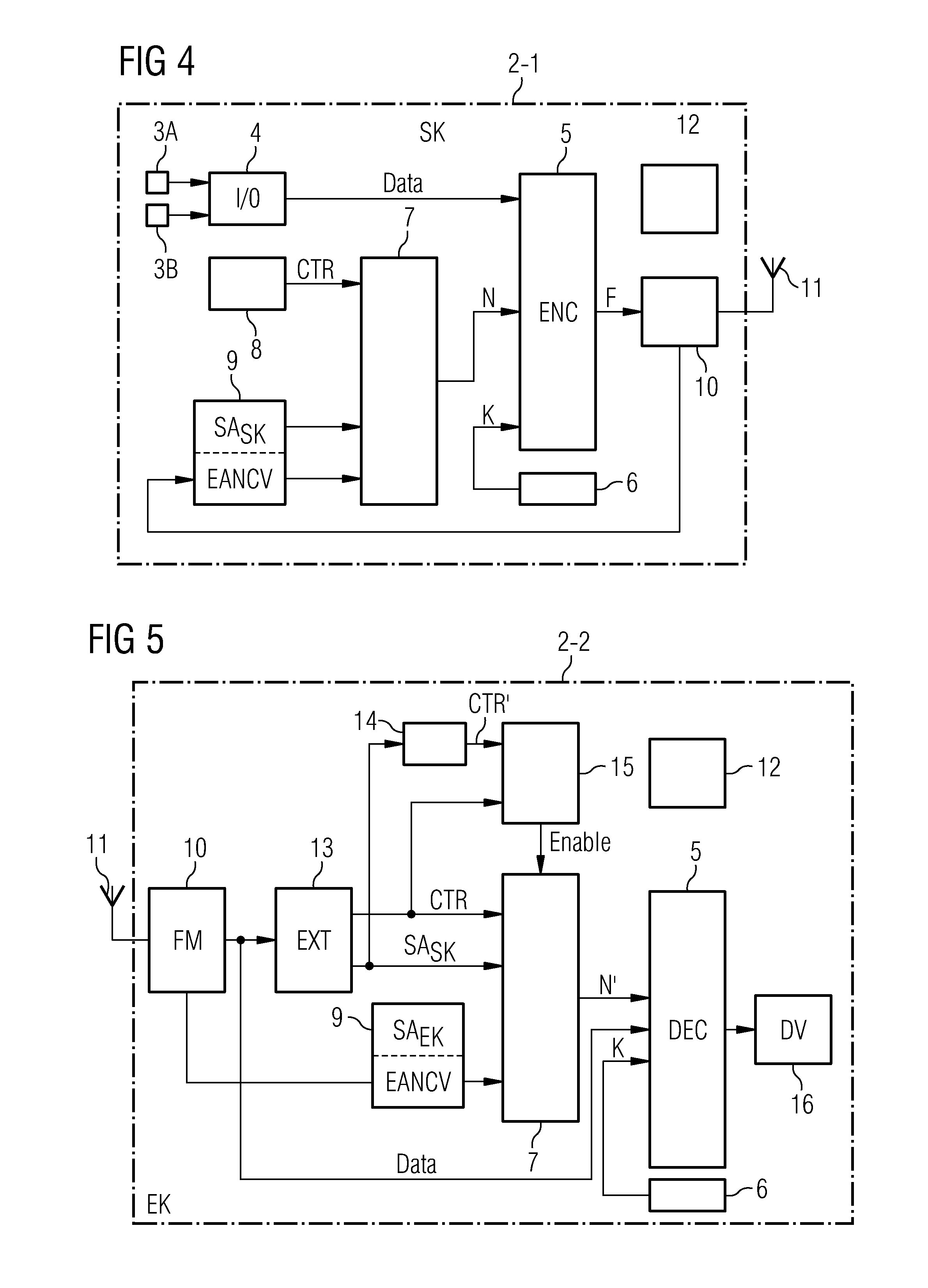
Dynamic encryption and decryption of a stream of data
InactiveUS7151832B1Easily extensibleEnhanced securitySynchronising transmission/receiving encryption devicesMultiple keys/algorithms usageDisk encryptionData content
Dynamic varying of encrypting of a stream of data at an encryption unit based on data content is disclosed. The dynamic varying of the encrypting, which can be responsive to passage of a predefined number of units of physical data or passage of a predefined number of conceptual units of data, is accomplished by changing at least one encryption parameter over different portions of the data. The at least one encryption parameter can comprise one or more of an encryption key, an encryption granularity, an encryption density scale, an encryption density, an encryption delay, an encryption key update variable, and an encryption key update data trigger. The change in encryption parameter is signaled to a receiver's decryption unit and used by the decryption unit in decrypting the dynamically varied encrypted stream of data. The stream of data may comprise, e.g., MPEG compressed video or audio.
Owner:IBM CORP
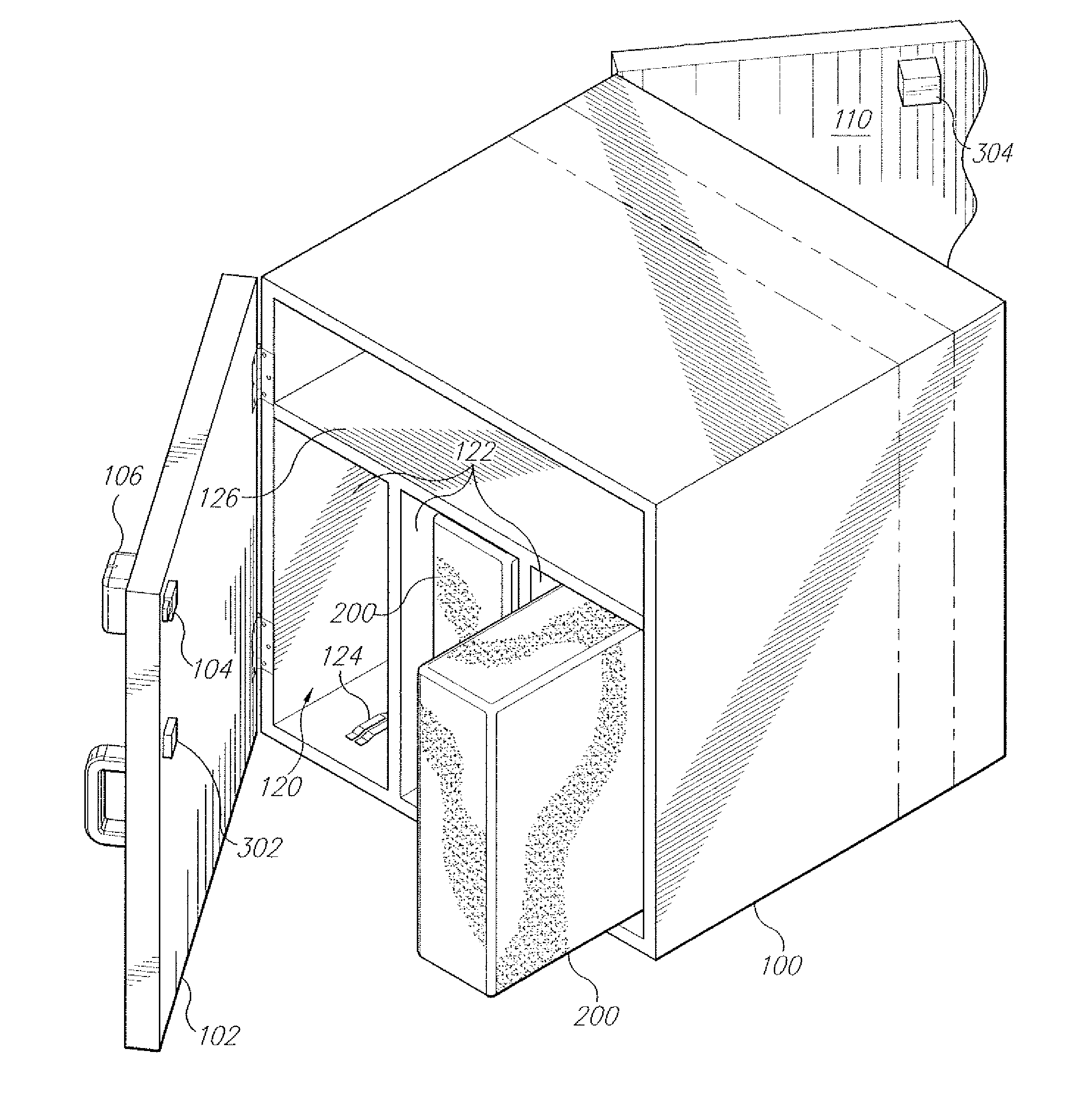
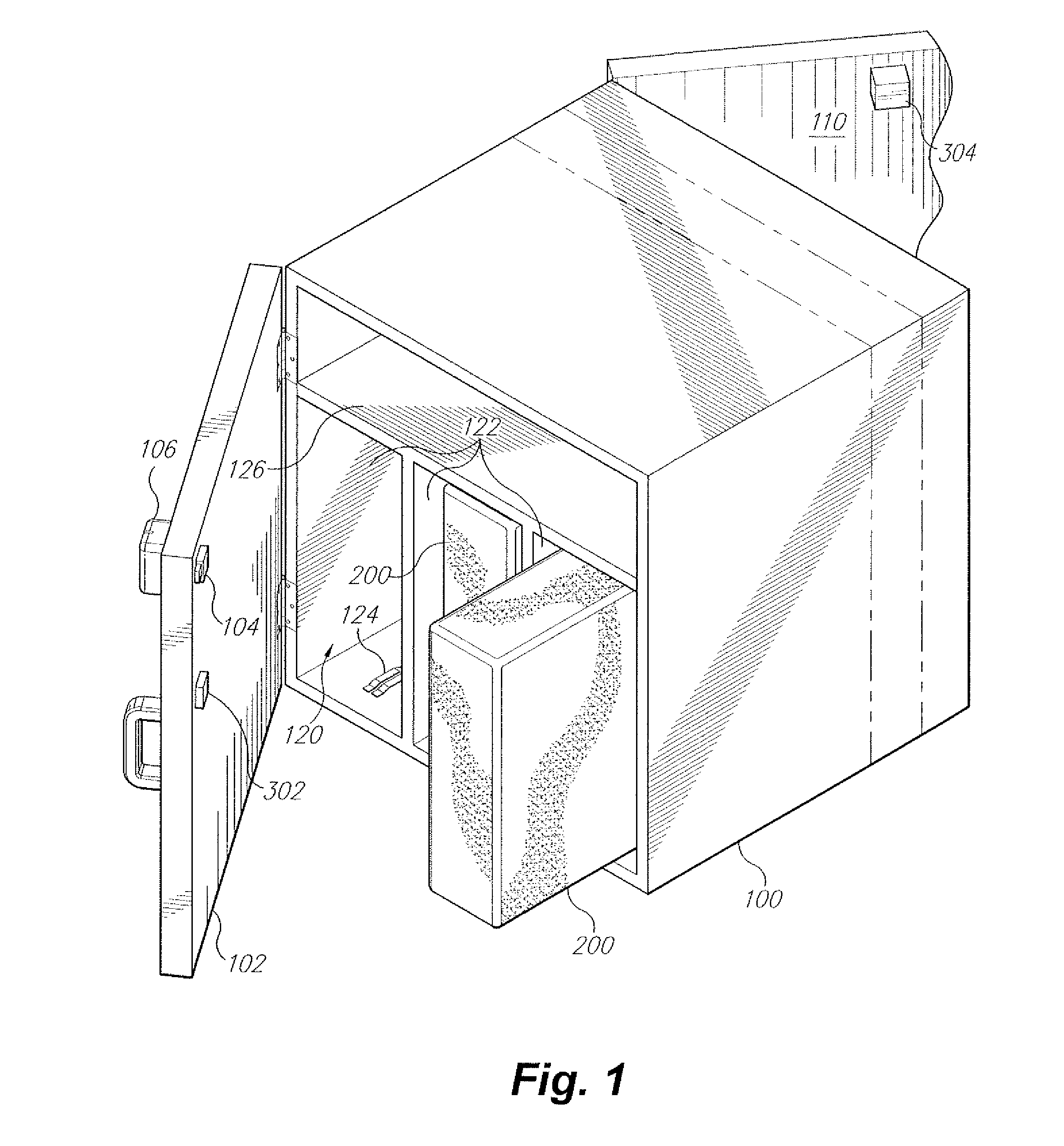
System for delivery of goods ordered via the internet
InactiveUS20120158606A1Enhanced securityErroneous delivery be preventApparatus for meter-controlled dispensingDomestic articlesReceiptInterior space
The system for delivery of goods ordered via the Internet utilizes a delivery box having a front door with an electronic lock and electronic key reader for receipt of goods ordered via the Internet. Goods are shipped in a transport box having an interior space and a device for controlling the temperature within the interior space. The delivery box has at least one interior transport box receptacle where a transport box containing goods is placed on delivery. A power and data interface is established between a delivery box control circuit and a transport box control circuit. The transport box is placed into one of the receptacles, so that the delivery box control circuit can power the transport box control circuit and environment-controlling device. A security code is downloaded from an Internet merchant site to the delivery box and stored onto a keycard when an order is placed.
Owner:MOUDY CHRISTOPHER
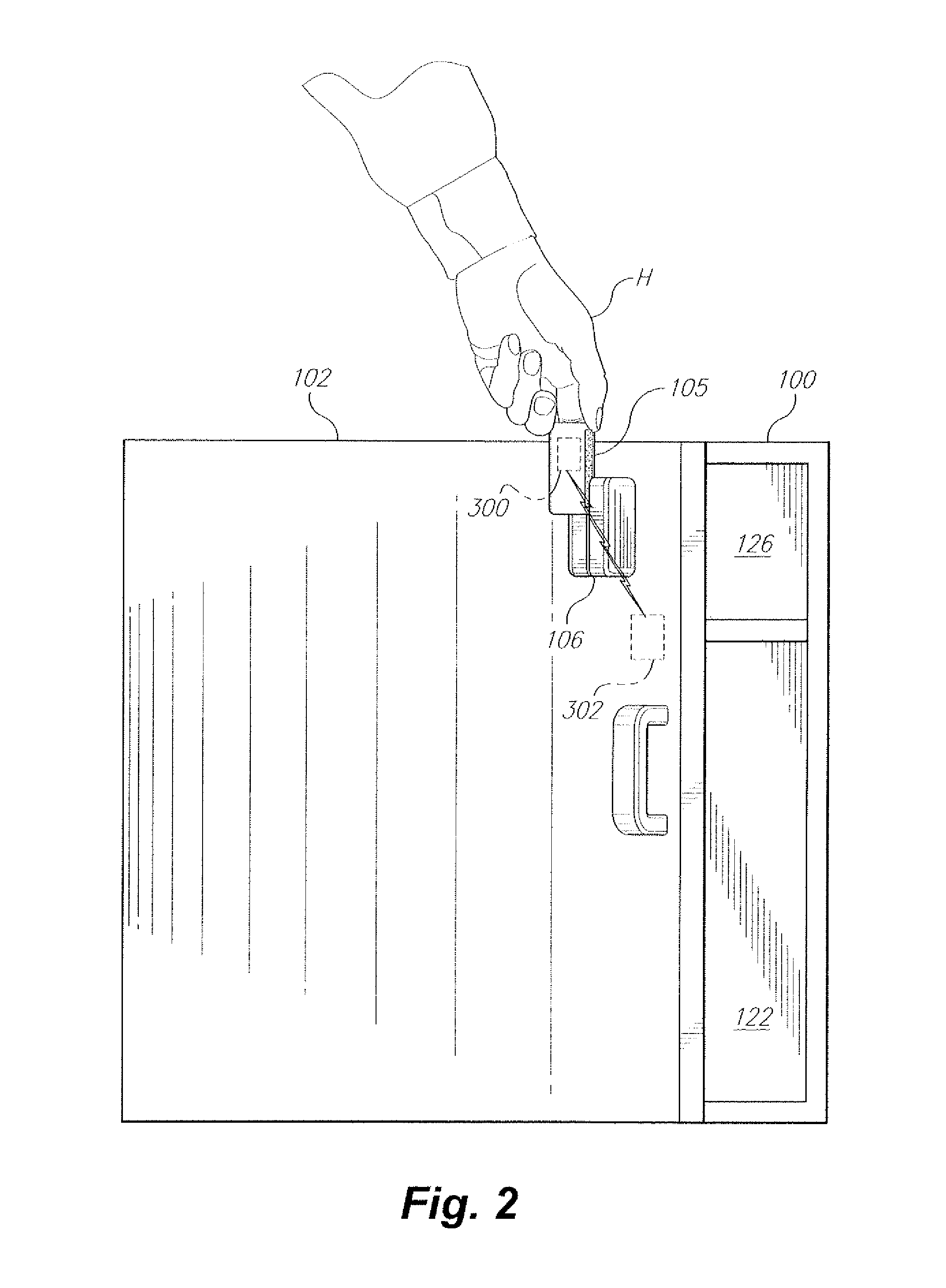
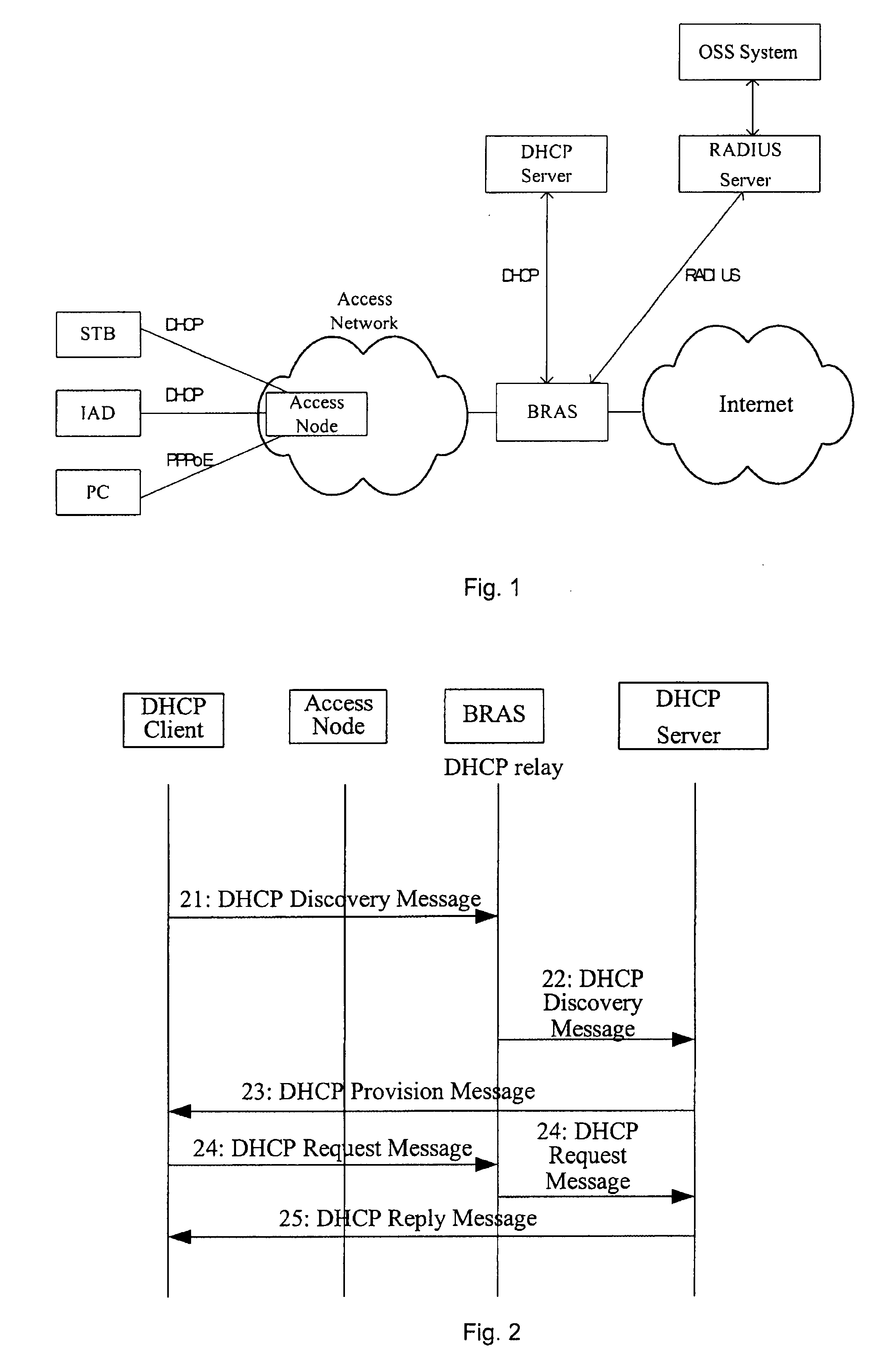
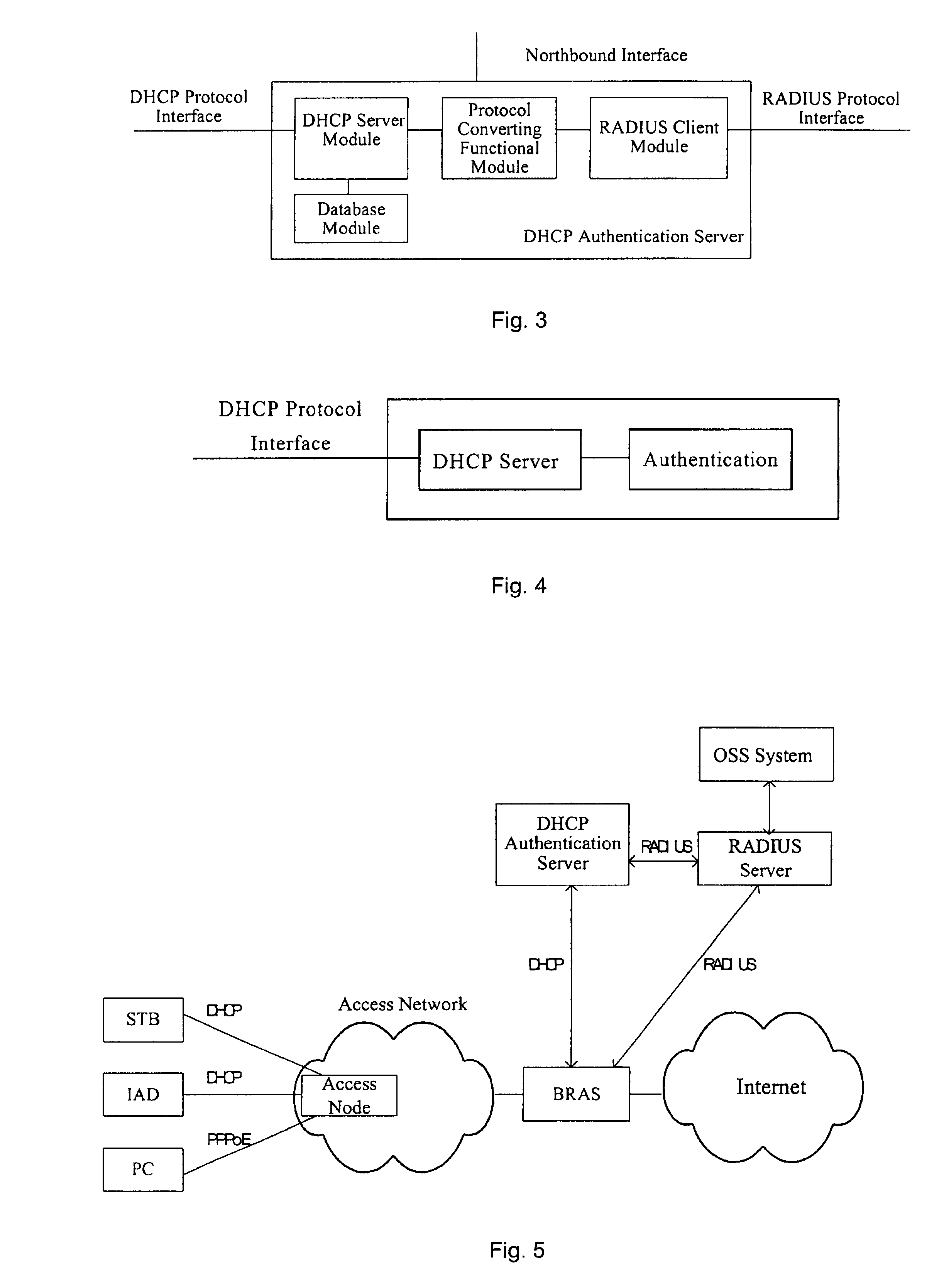
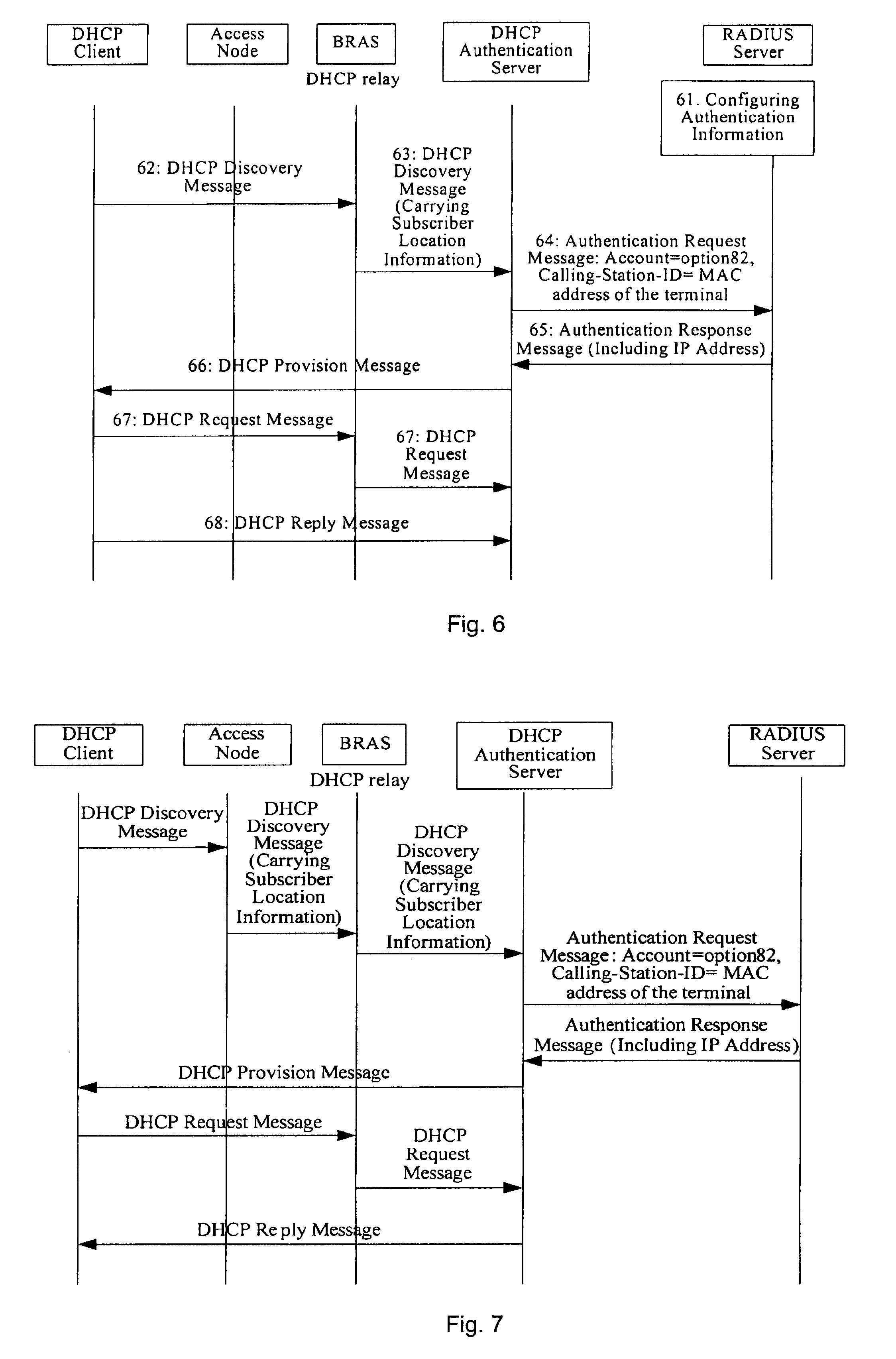
Method, system and server for realizing secure assignment of DHCP address
InactiveUS20080092213A1Enhanced securityNetwork cost be lowerDigital data processing detailsComputer security arrangementsClient-sideIp address
A method, a system and an authentication server for realizing a secure assignment of a DHCP address are disclosed. The method includes: sending a DHCP Discovery message via an access network; obtaining the identification information of the DHCP client and performing an authenticating to the DHCP client based on the identification information; and only assigning the address to the DHCP client has passed the authentication. Therefore, in the present invention, access authentication may be performed on a subscriber according to location information, and IP address is only assigned to the valid subscriber and terminal. Therefore, the security of the address assignment in DHCP mode may be enhanced greatly. Moreover, in the present invention, addresses may be managed by an AAA server unitedly, or the addresses may be assigned after being authenticated by the AAA server successfully.
Owner:HUAWEI TECH CO LTD
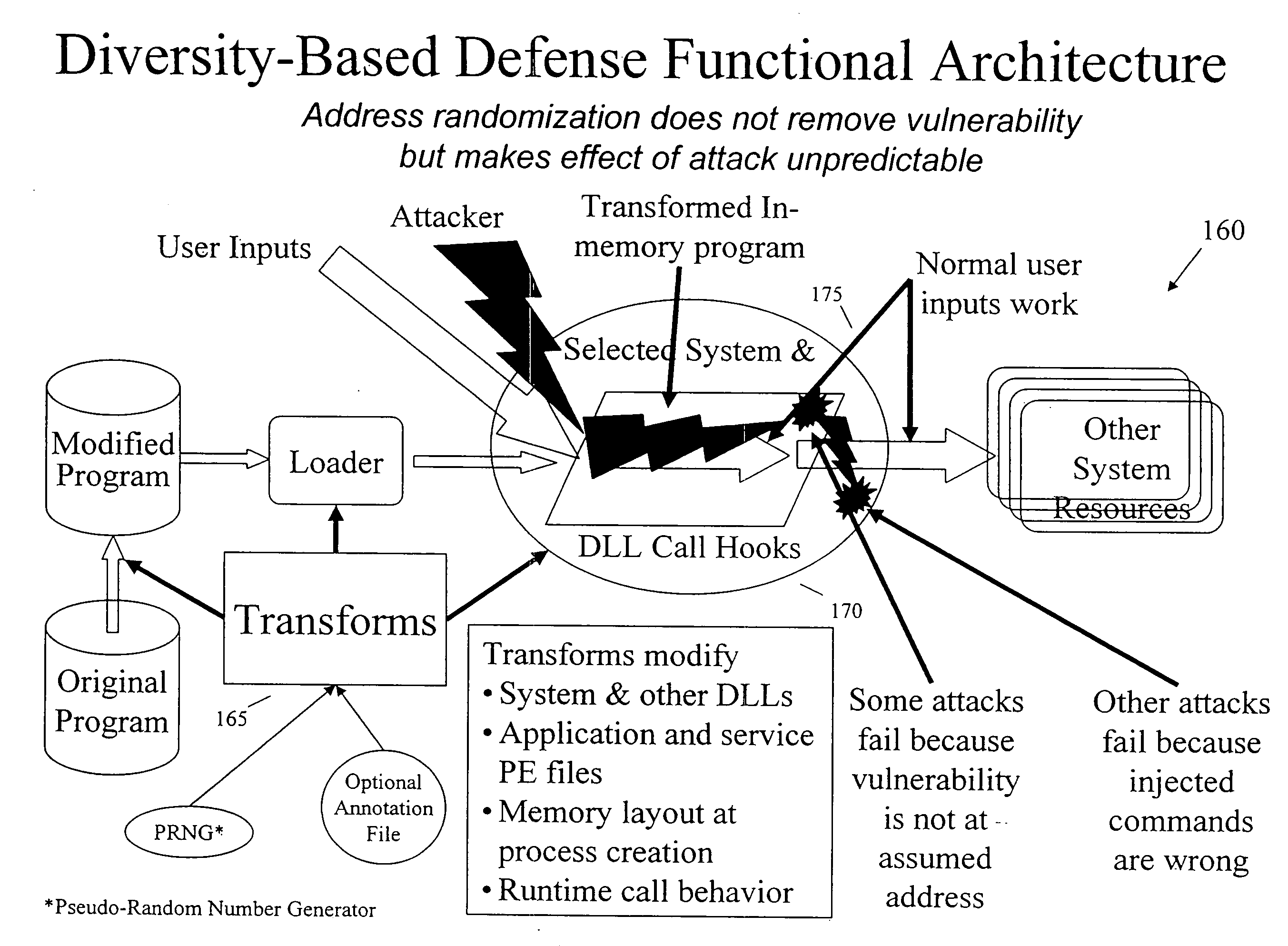
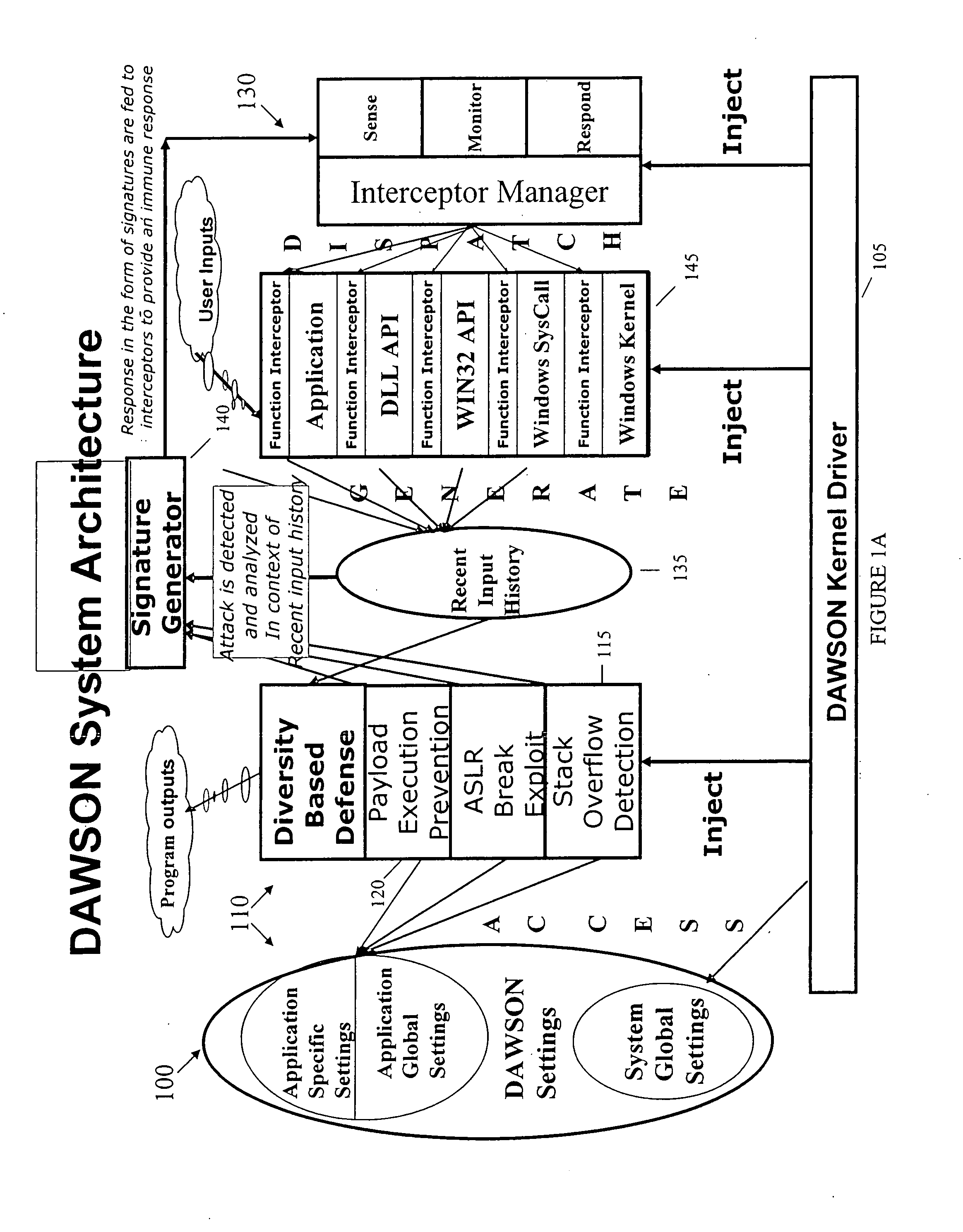
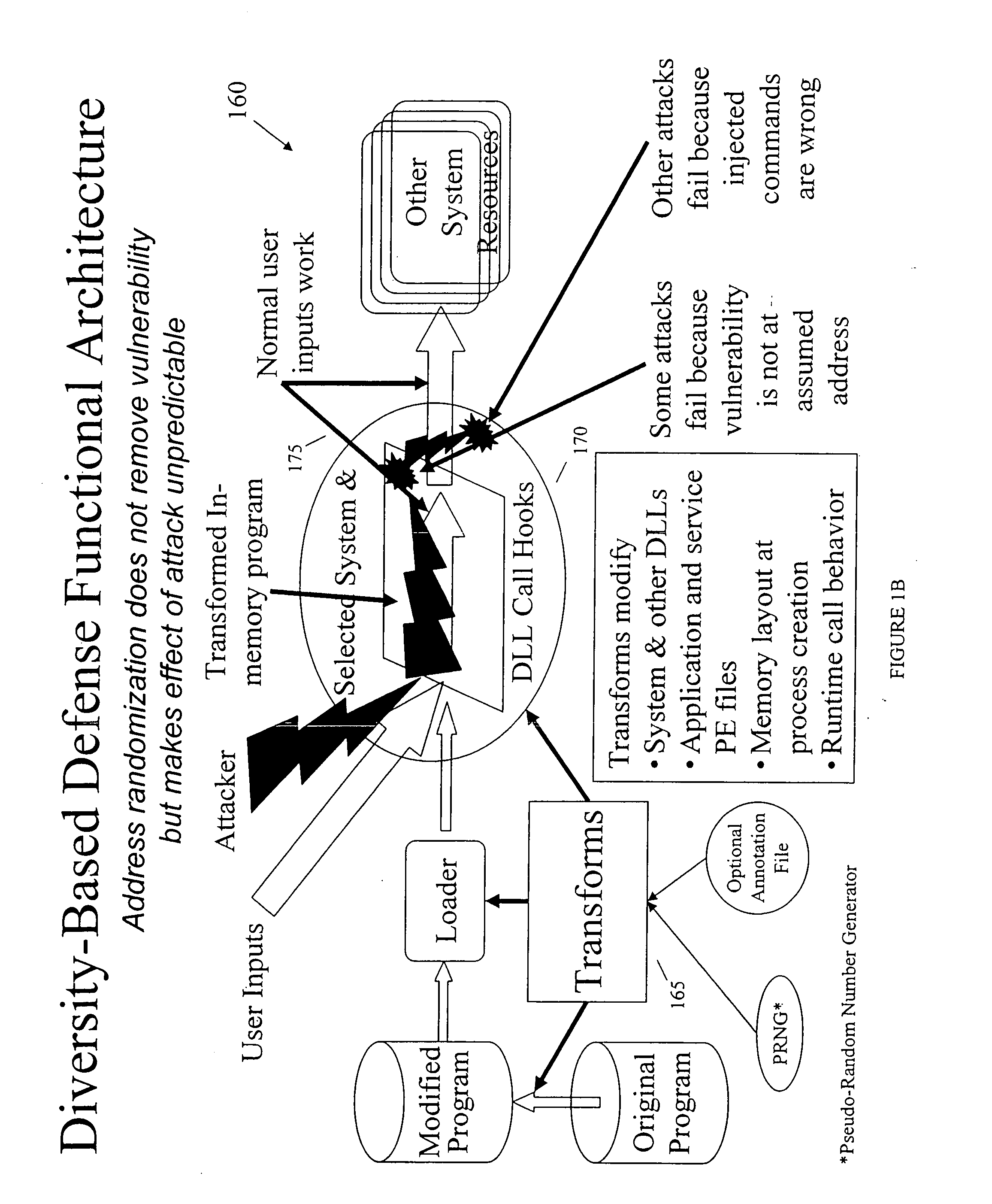
Diversity-based security system and method
InactiveUS20080016314A1Enhanced securityAlleviate deficiencyUnauthorized memory use protectionPlatform integrity maintainanceSoftware diversitySafe system
Owner:LI LIXIN +1
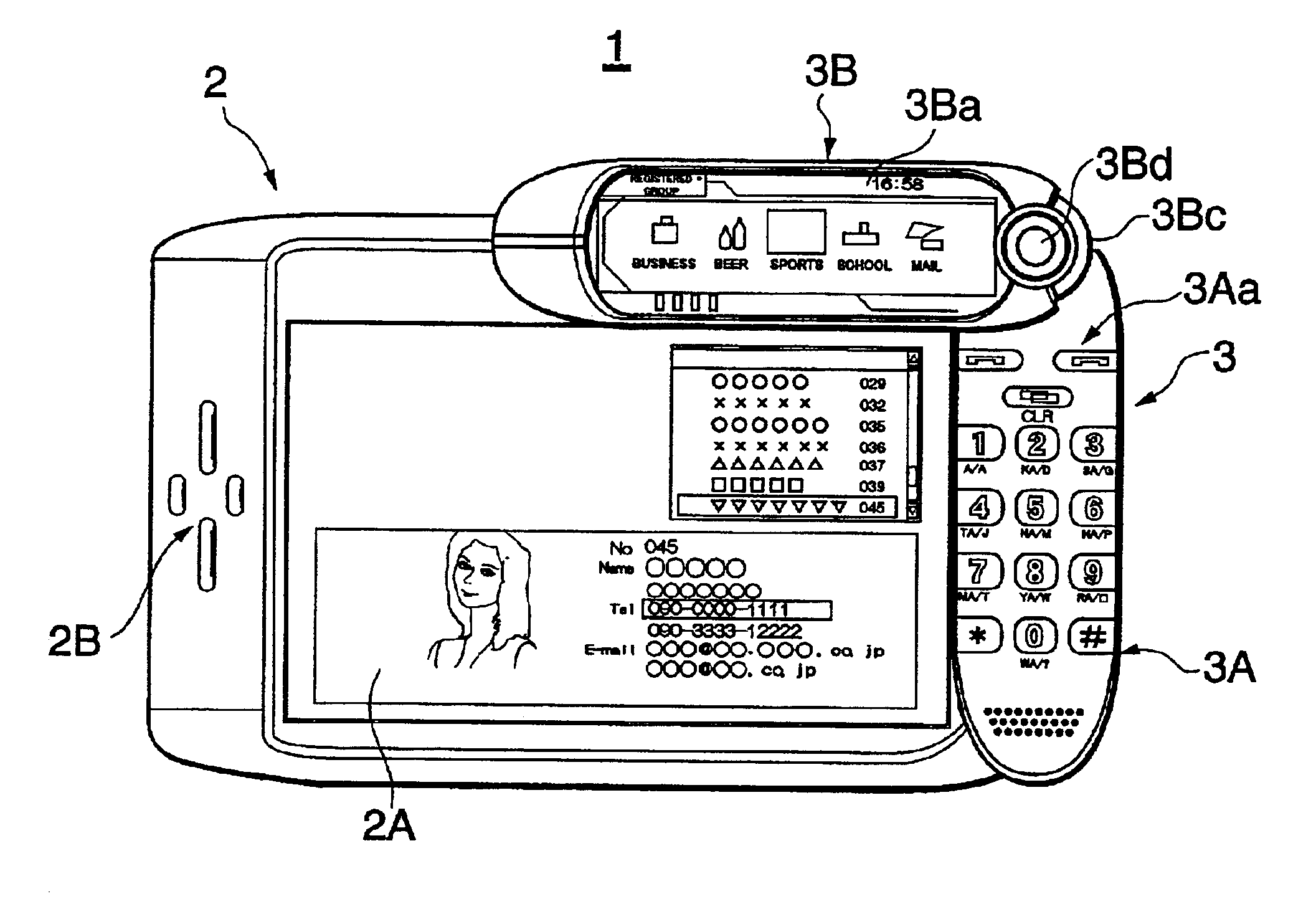
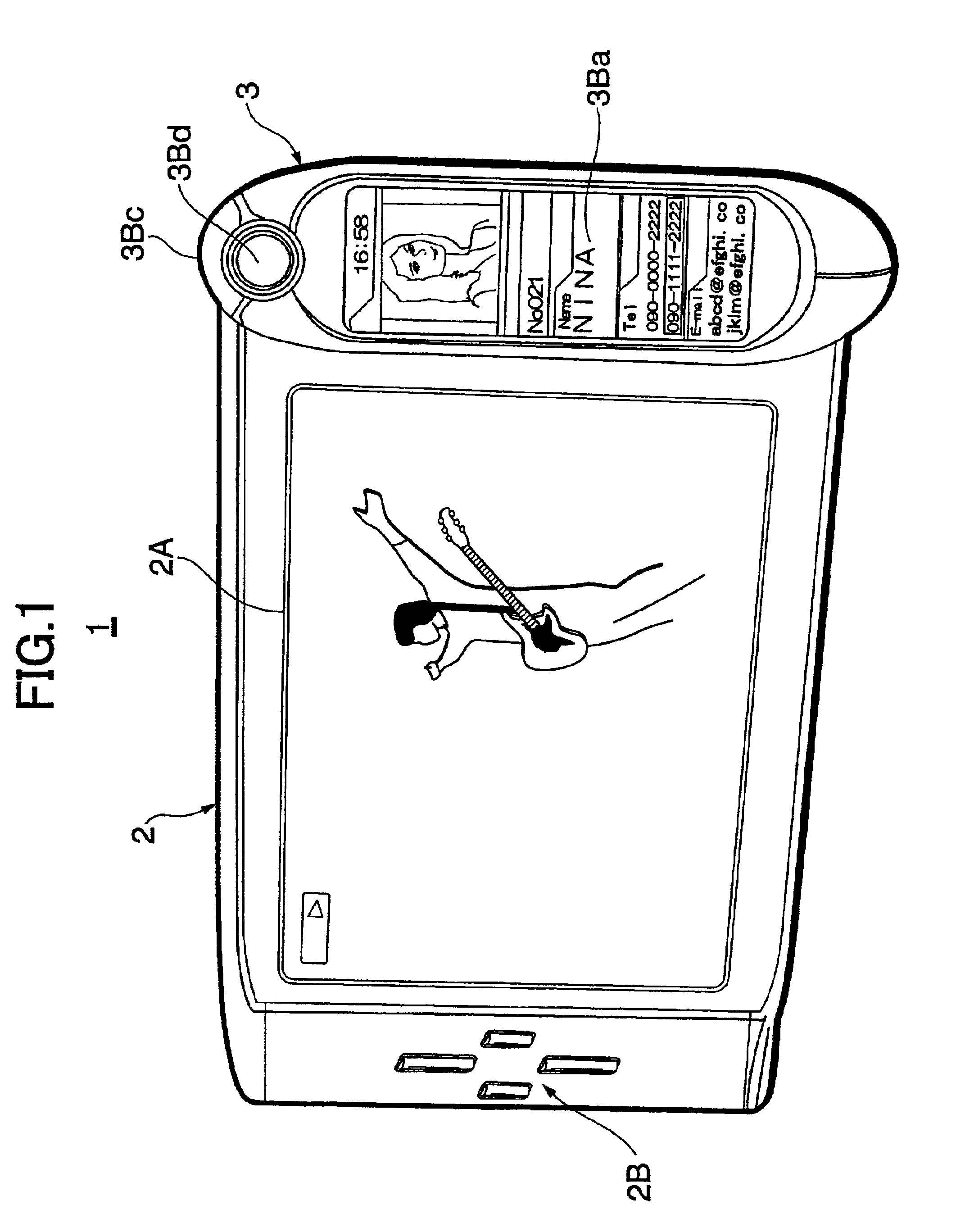
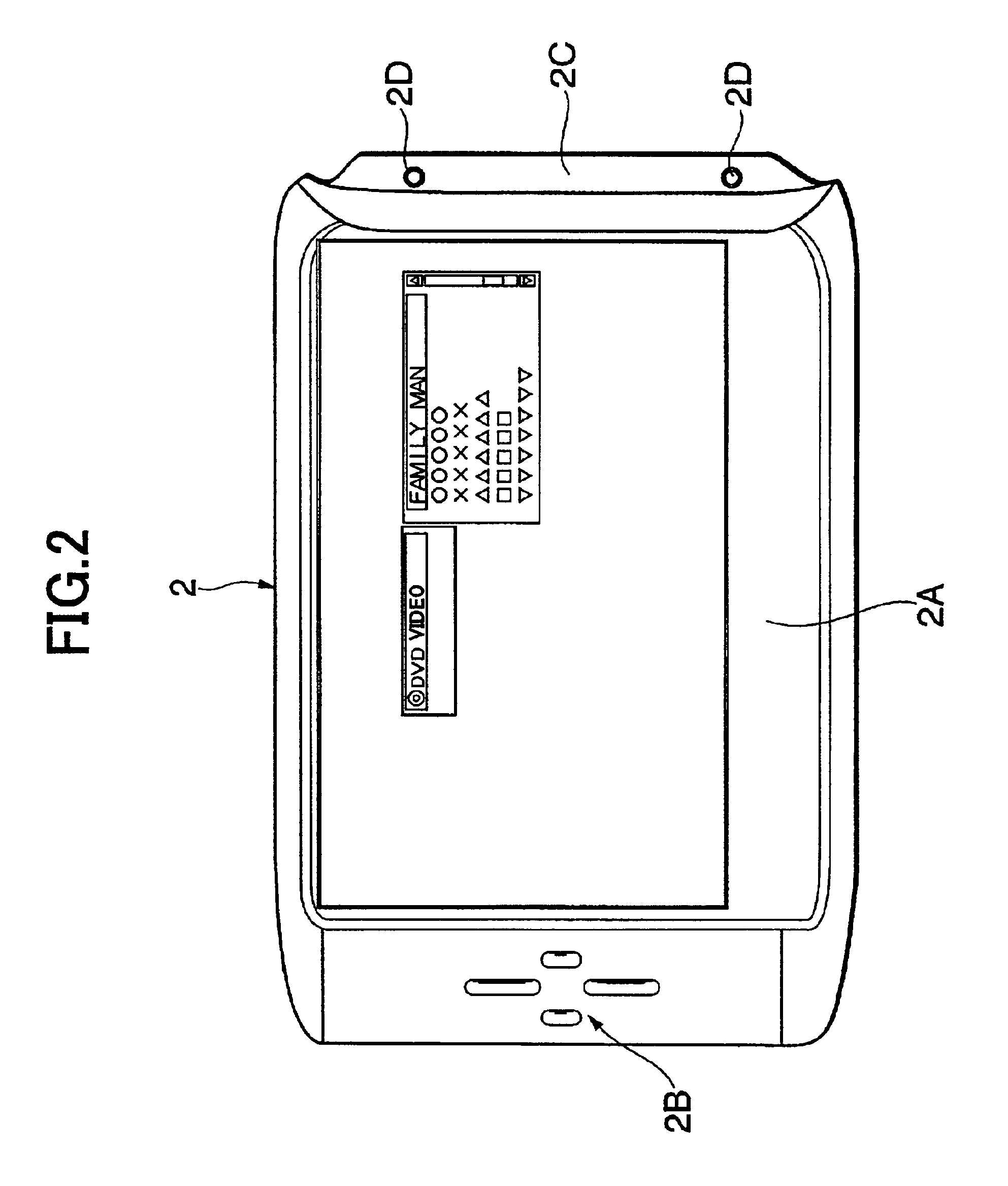
Portable information terminal
InactiveUS6882326B2Enhanced securityImprove securityInput/output for user-computer interactionCordless telephonesDisplay deviceComputer science
Owner:PIONEER CORP +1
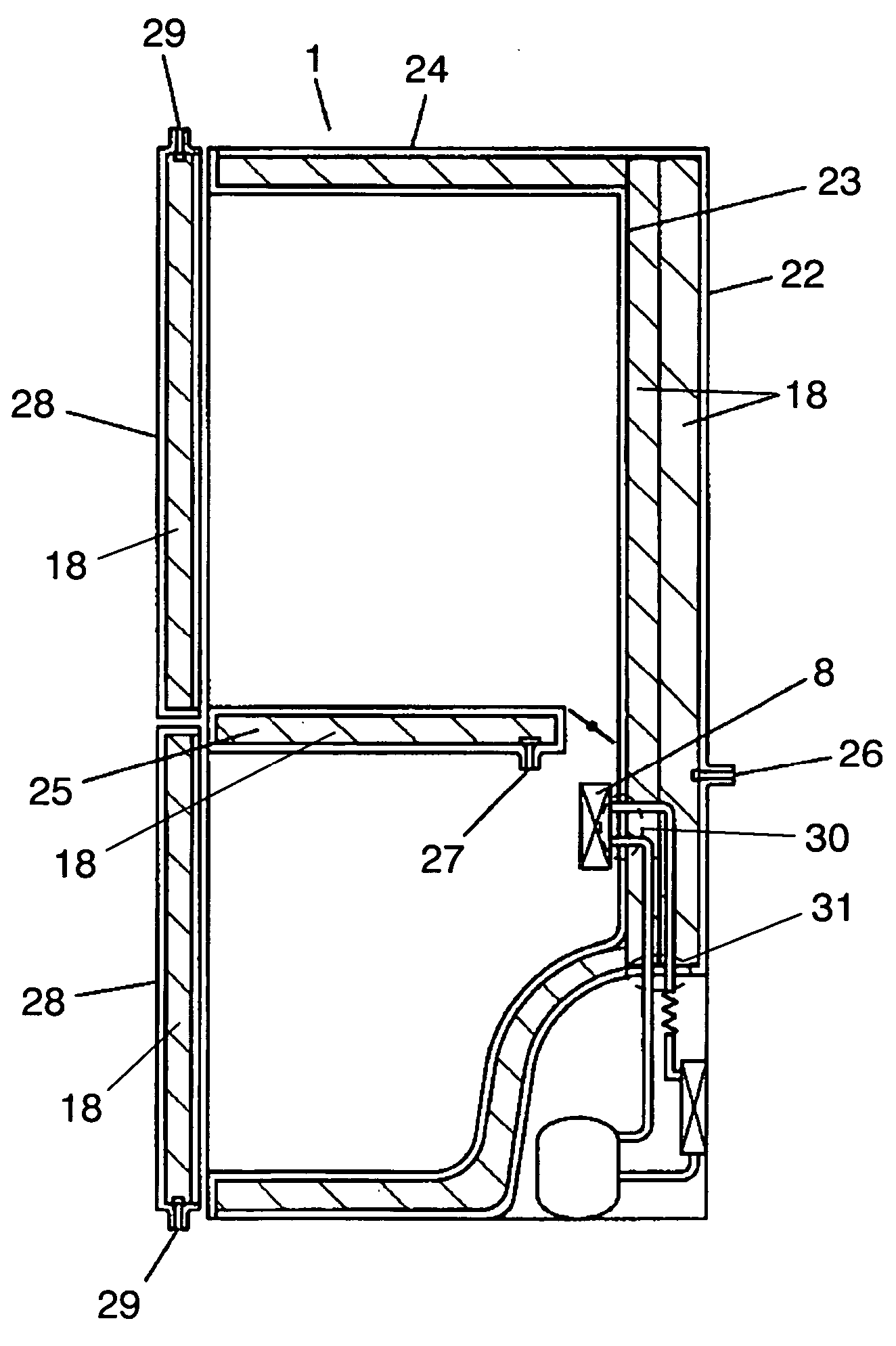
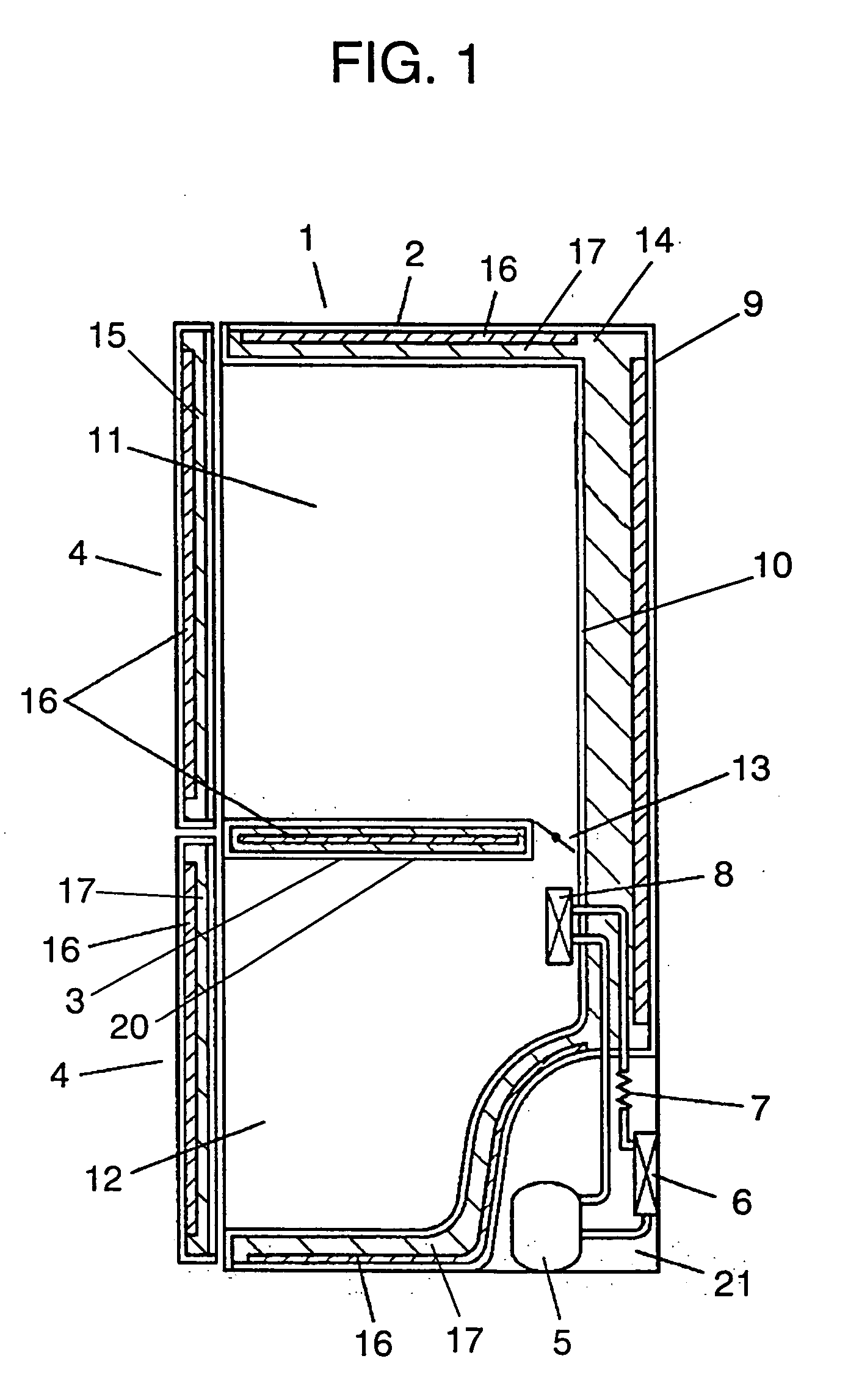
Refrigerator
InactiveUS20050235682A1Improve inflammabilityEnhanced securityLighting and heating apparatusDomestic refrigeratorsRefrigerantRefrigerated temperature
A heat insulating box of a refrigerator includes a inflammable heat-insulator particularly a vacuum heat-insulator made of a board-shape molded inorganic fiber. Therewith inflammability of the heat insulator is ensured and a refrigerator box prevented from catching an outside caused fire is achieved, thus a refrigerator which is safe even when a flammable refrigerant is used and which is high in energy-saving is provided.
Owner:PANASONIC CORP
Solid Electrolyte Material Manufacturable by Polymer Processing Methods
ActiveUS20090075176A1Enhanced securityLow manufacturing costSolid electrolytesAlkaline accumulatorsElastic modulusHigh energy
The present invention relates generally to electrolyte materials. According to an embodiment, the present invention provides for a solid polymer electrolyte material that is ionically conductive, mechanically robust, and can be formed into desirable shapes using conventional polymer processing methods. An exemplary polymer electrolyte material has an elastic modulus in excess of 1×106 Pa at 90 degrees C. and is characterized by an ionic conductivity of at least 1×10−5 Scm−1 at 90 degrees C. An exemplary material can be characterized by a two domain or three domain material system. An exemplary material can include material components made of diblock polymers or triblock polymers. Many uses are contemplated for the solid polymer electrolyte materials. For example, the present invention can be applied to improve Li-based batteries by means of enabling higher energy density, better thermal and environmental stability, lower rates of self-discharge, enhanced safety, lower manufacturing costs, and novel form factors.
Owner:RGT UNIV OF CALIFORNIA +1
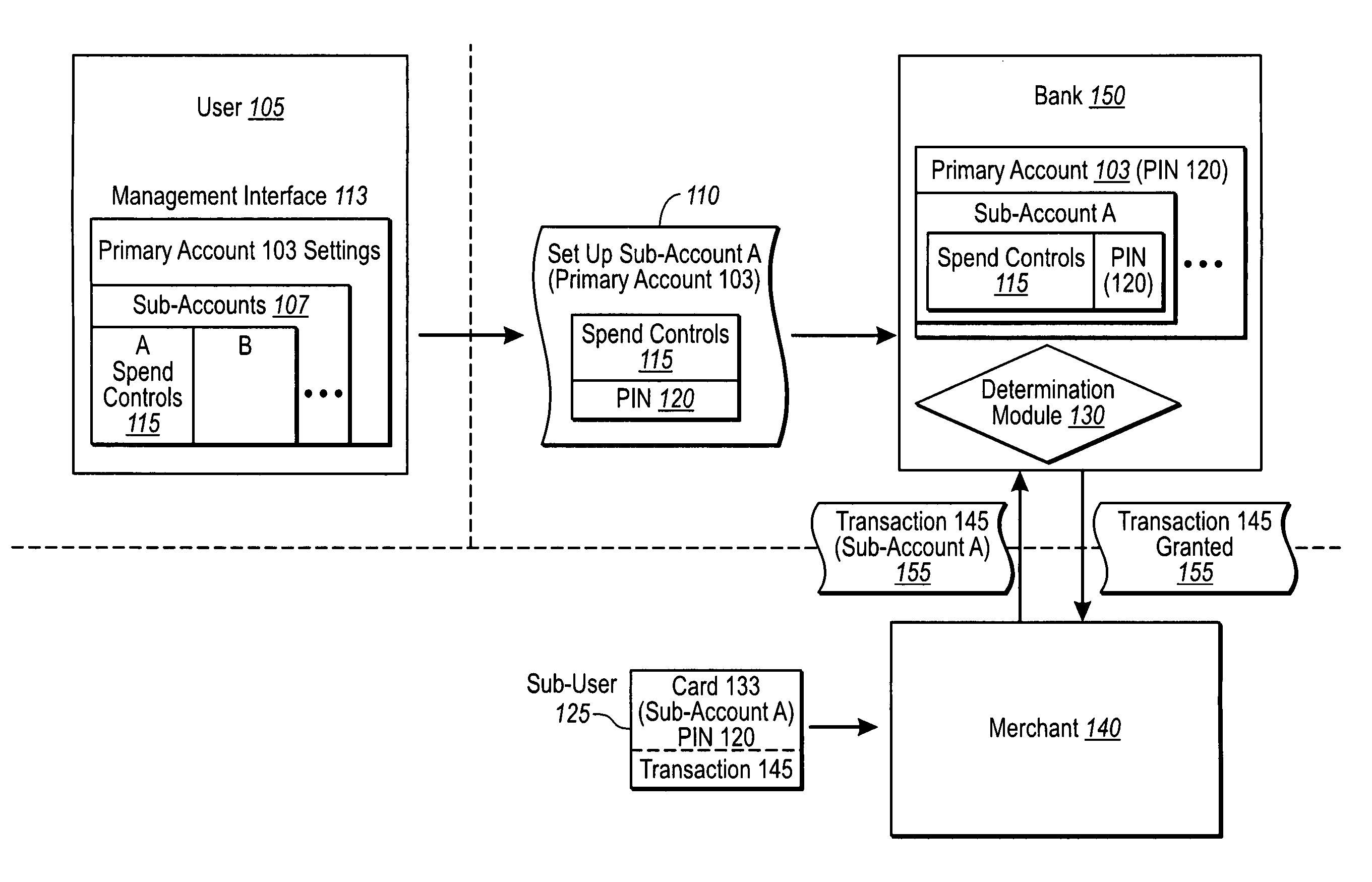
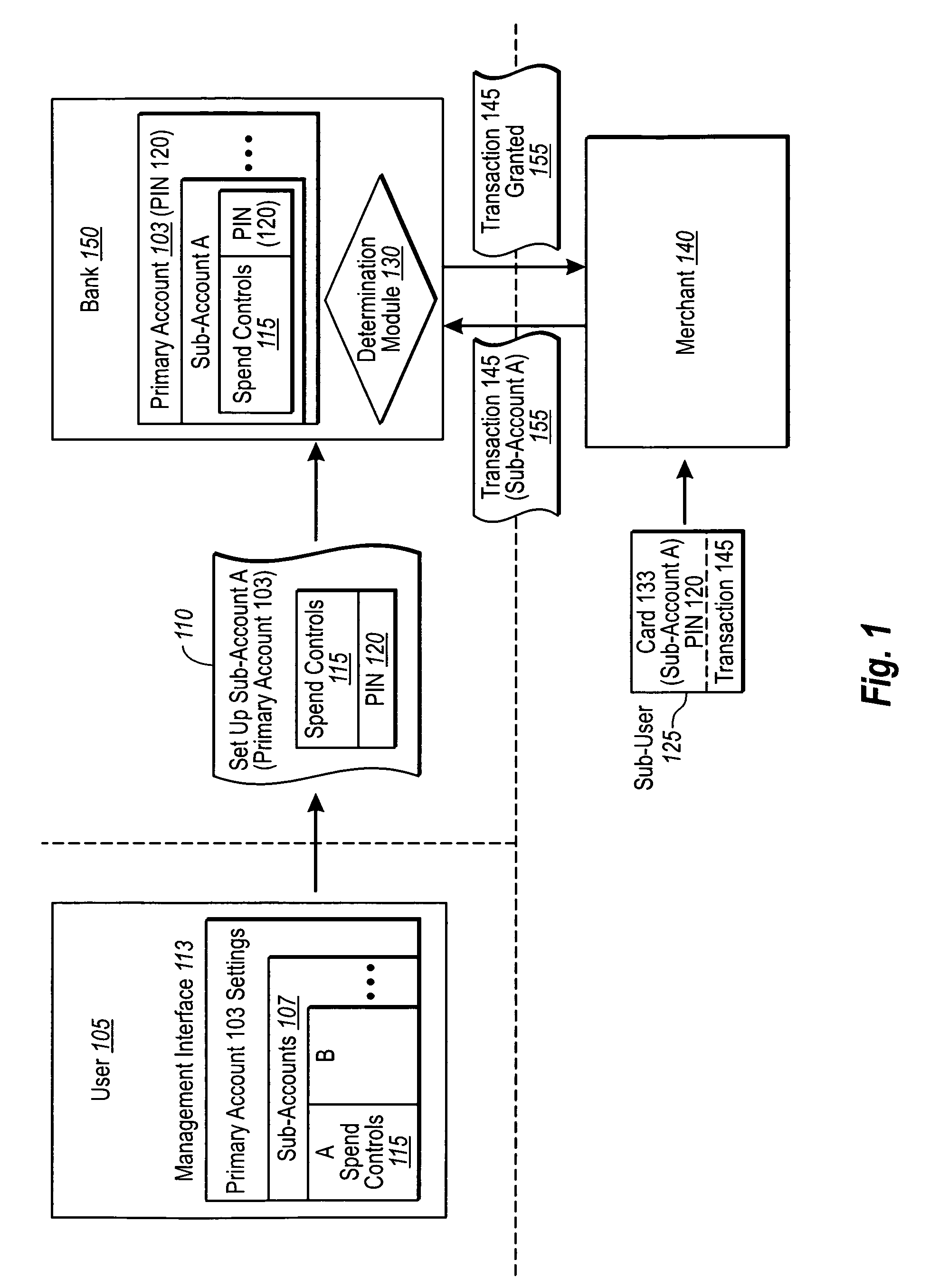
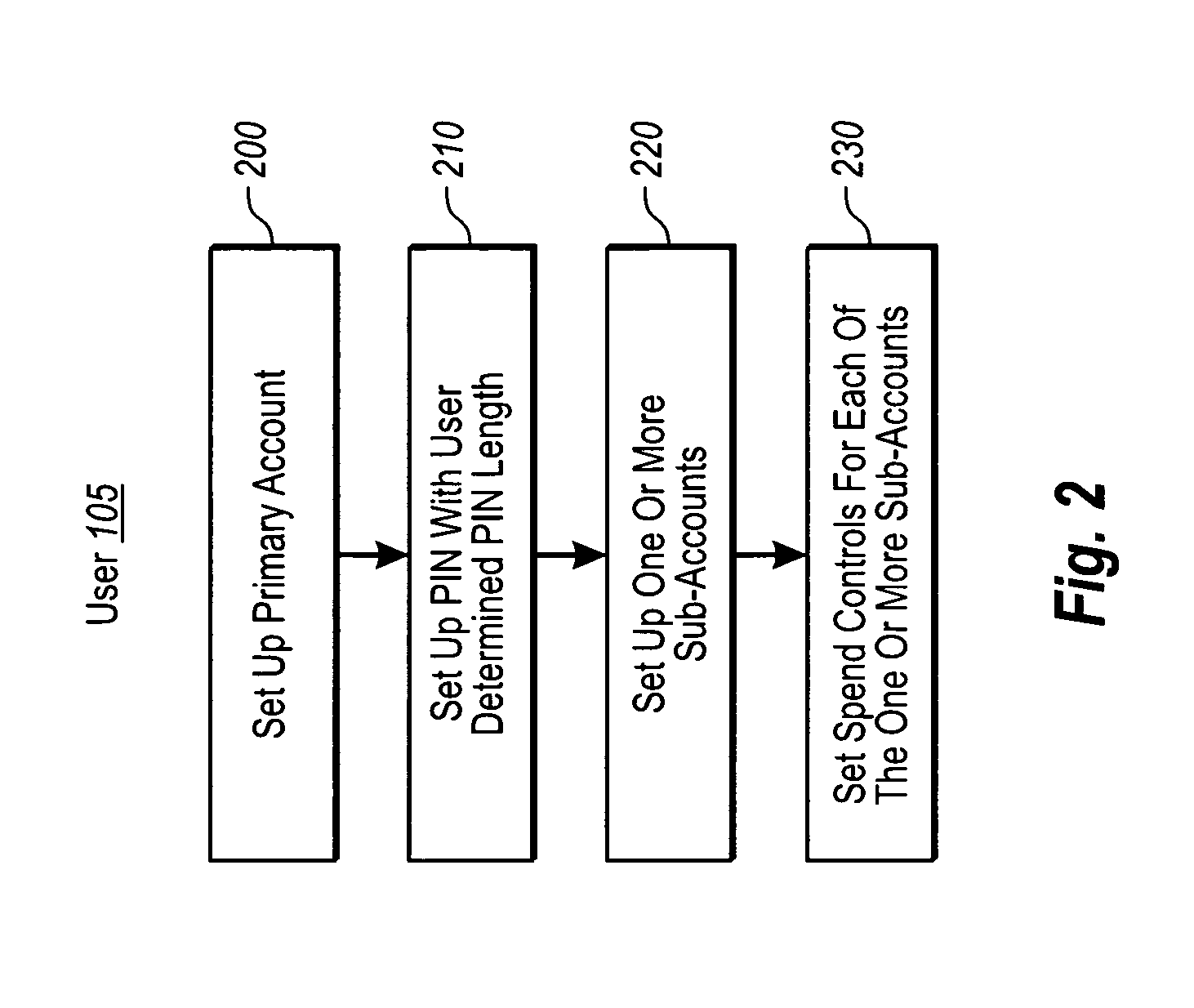
Electronic payment system with PIN and sub-account configurations
ActiveUS7954704B1High degree of control and configurabilityEnhanced securityElectric signal transmission systemsDigital data processing detailsPayment systemMonetary Amount
Owner:KIOBA PROCESSING LLC
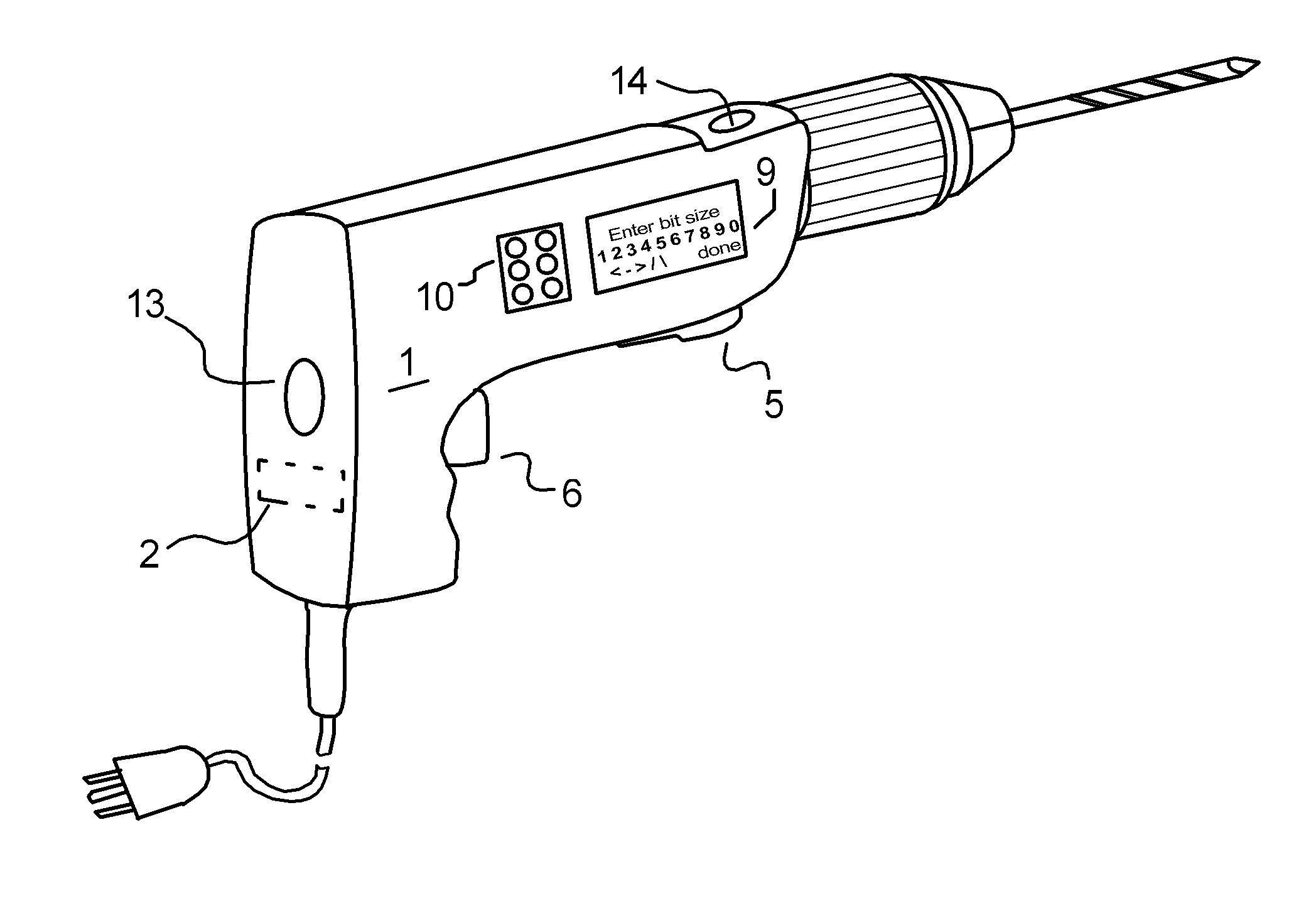
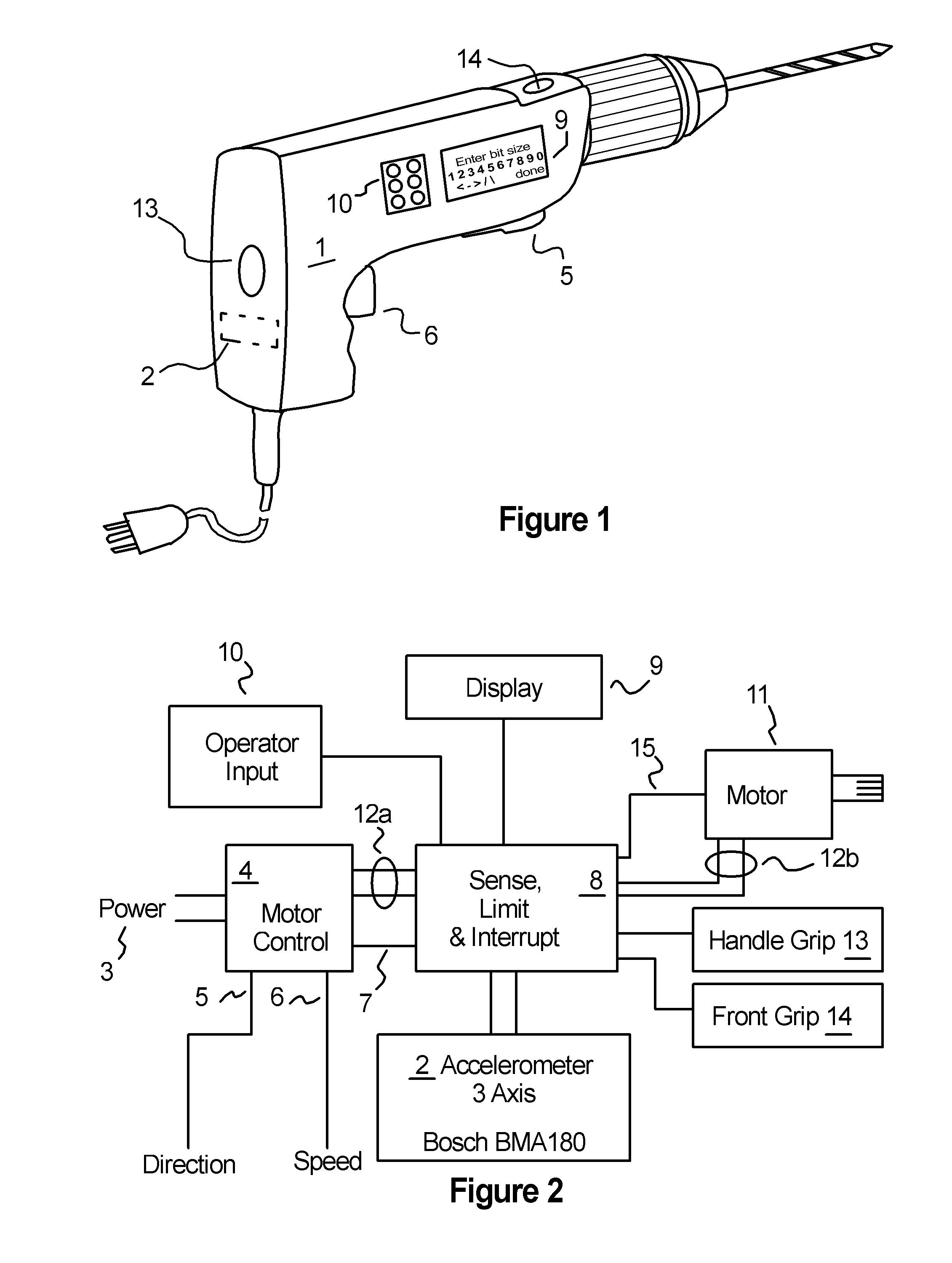
Kickback Reduction for Power Tools and Machines
InactiveUS20140166323A1Secure gripEnhanced securityEngineering safety devicesMetal working apparatusPower toolEngineering
An apparatus and methods are described for protecting an operator from sudden, unexpected or dangerous movement of powered hand held tools and the like. A set of parameters for safe operation of the tool are provided, which parameters may be adjusted or selected based on the manner in which the tool is being operated. The power tool is fitted with sensors including an accelerometer, operating to sense acceleration of the tool in a plurality of axes during operation. The output of the accelerometer is coupled to a computing circuit which determines if the acceleration of the tool is within the safe operation parameters. When acceleration of the tool exceeds one or more of the safe operating parameters, power to the tool motor is limited or otherwise adjusted in order to prevent or reduce the movement of the tool thereby protecting the operator.
Owner:COOPER J CARL
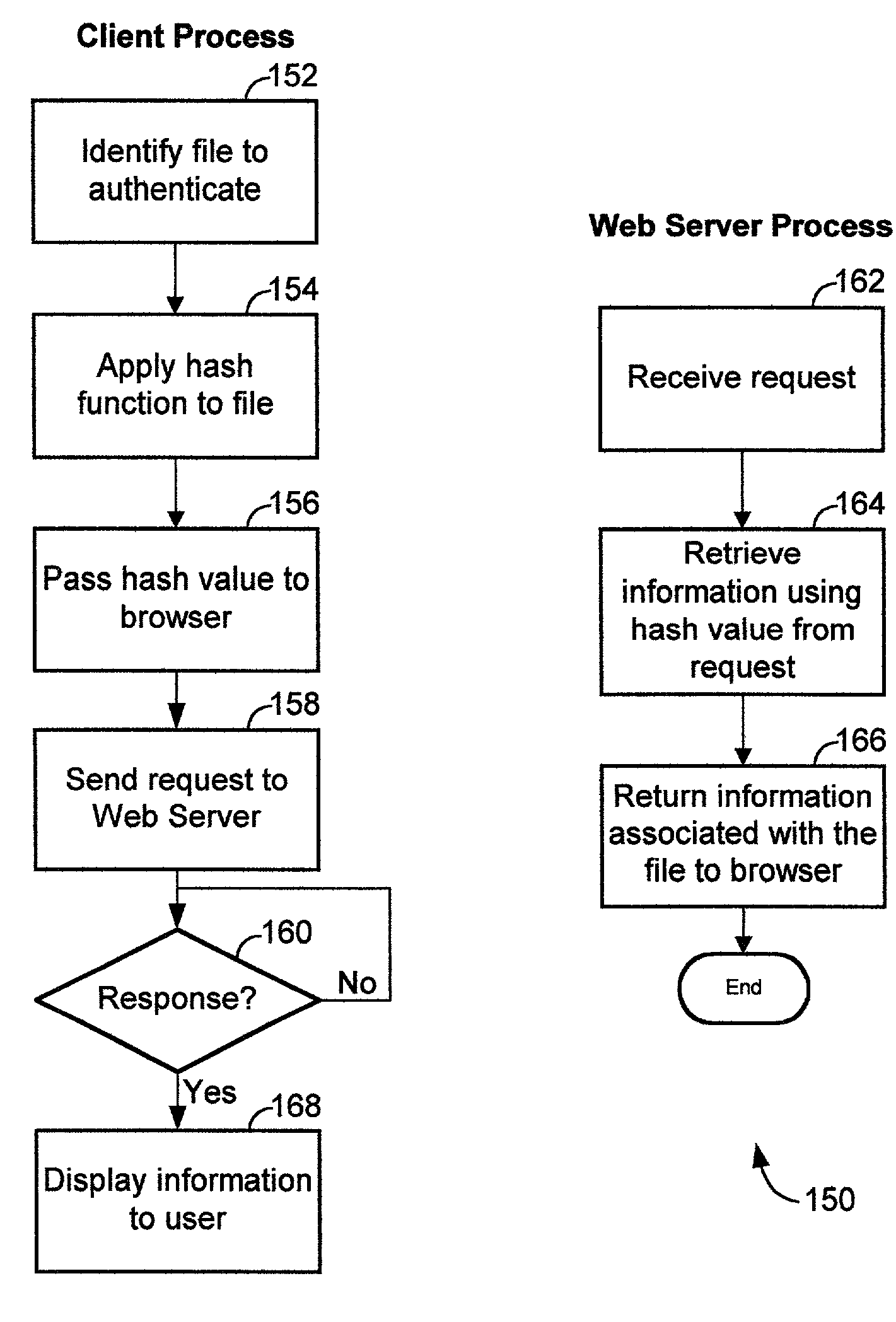
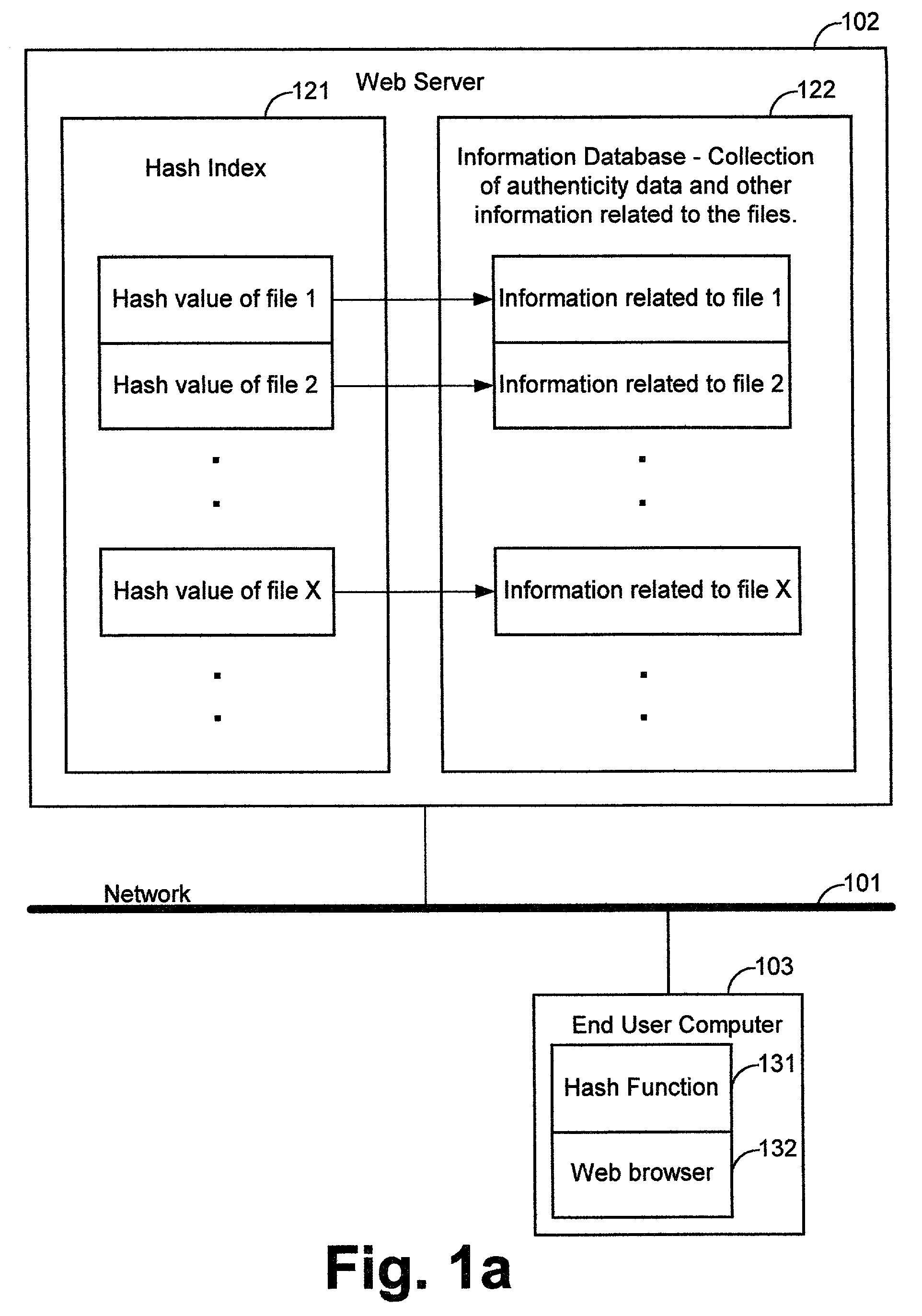
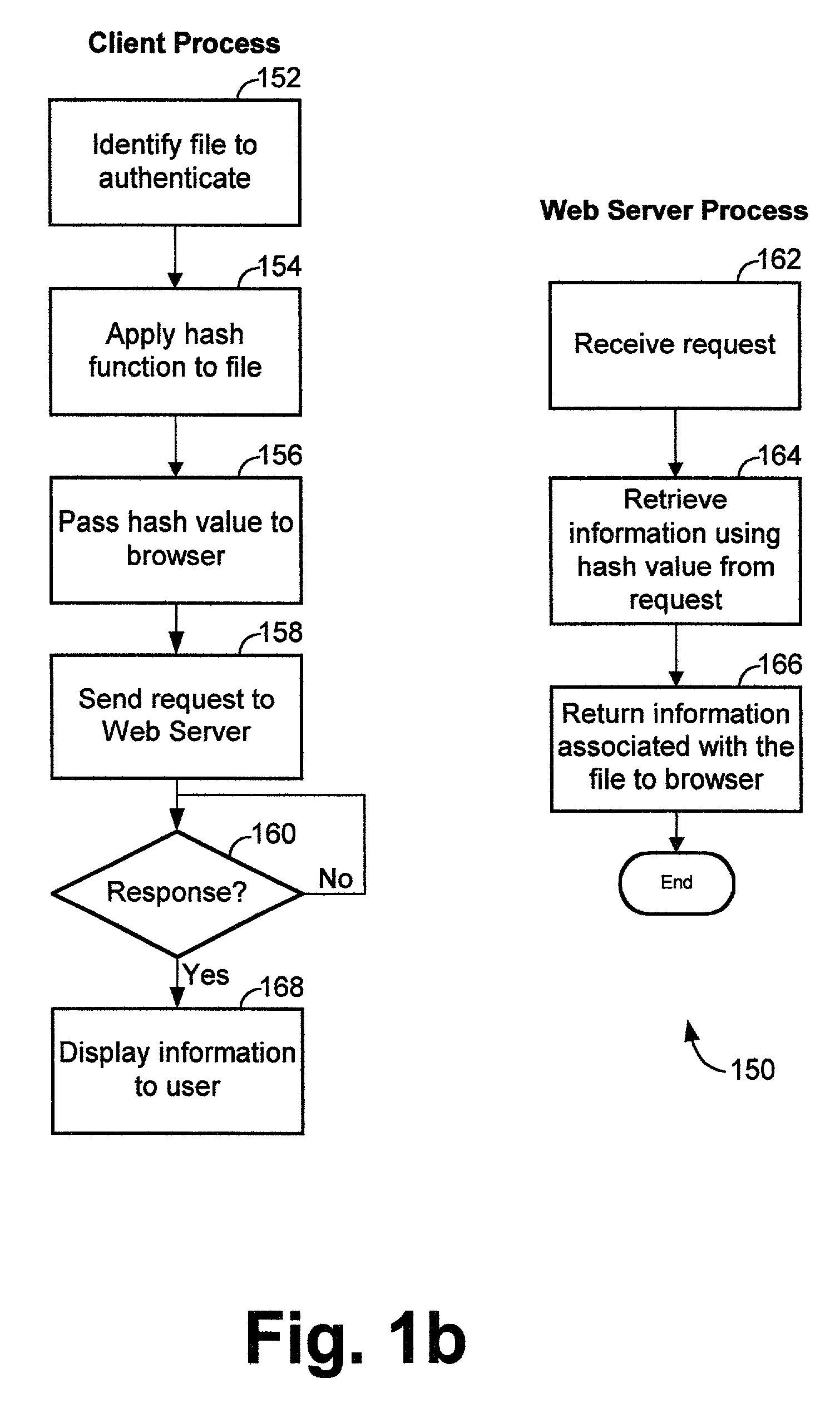
Internet file safety information center
ActiveUS7096493B1Enhanced securityImprove securityDigital data processing detailsDigital data protectionElectronic recordsSecurity information
Systems and methods to enhance safety of computer file distribution. The system includes a computer network, a server computer connected to said computer network one or more electronic records stored in the server computer wherein each record includes information about a particular file and is indexed by a hash value computed from the particular file and at least one user terminal connected to the computer network. The user terminal is operable to verify the authenticity of a particular file including computing the hash value of the particular file and retrieving from the server computer the electronic record that contains information about the particular file including submitting the computed hash to the server computer.
Owner:INTELLECTUAL VENTURES ASSETS 186 LLC
Lithium secondary battery
InactiveUS20050202316A1Enhanced securityImprove cycle lifeSilver accumulatorsNegative electrodesLithiumPhysical chemistry
Disclosed is a lithium secondary battery including a positive electrode comprising a combination of positive active materials. The combination includes a material represented by one or both of Formulae 1 and 2; and a material of Formula 3 as follows: LiaNibMncMdO2 (Formula 1) where 0.90≦a≦1.2; 0.5≦b≦0.9; 0<c<0.4; 0≦d≦0.2; LiaNibCocMndMeO2 (Formula 2) where 0.90≦a≦1.2, 0.5≦b≦0.9, 0<c<0.4, 0<d<0.4, and 0≦e≦0.2; LiaCoMbO2 (Formula 3) where 0.90≦a≦1.2 and 0≦b≦0.2; and each M of Formulae 1-3 is independently selected from the group consisting of Mg, Ca, Sr, Ba, Ra, Sc, Y, Ti, Zr, Hf, Rf, V, Nb, Ta, Db, Cr, Mo, W, Sg, Tc, Re, Bh, Fe, Ru, Os, Hs, Rh, Ir, Pd, Pt, Cu, Ag, Au, Zn, Cd, B, Al, Ga, In, Tl, Si, Ge, Sn, P, As, Sb, Bi, S, Se, Te, Po, and combinations.
Owner:SAMSUNG SDI CO LTD
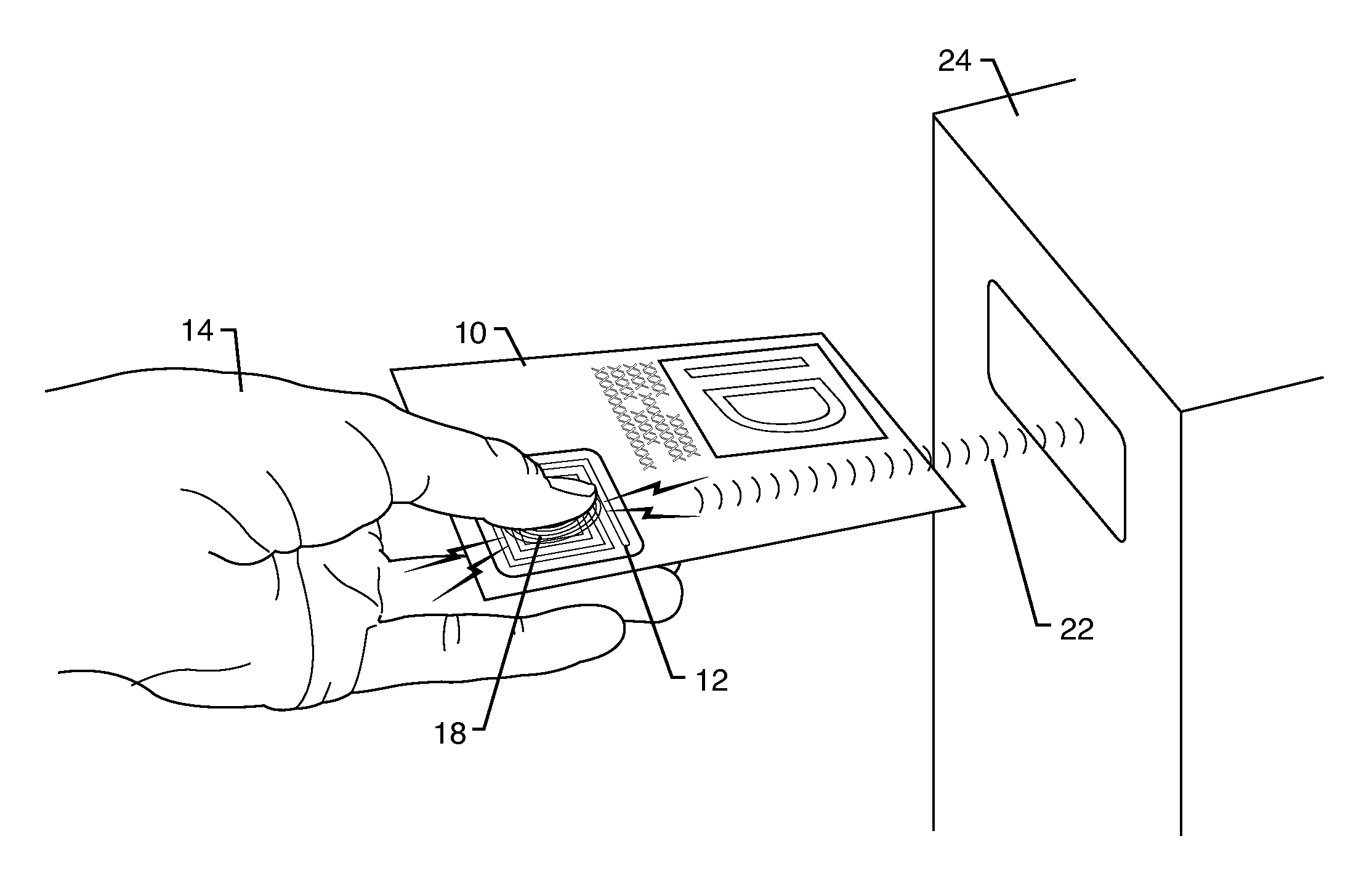
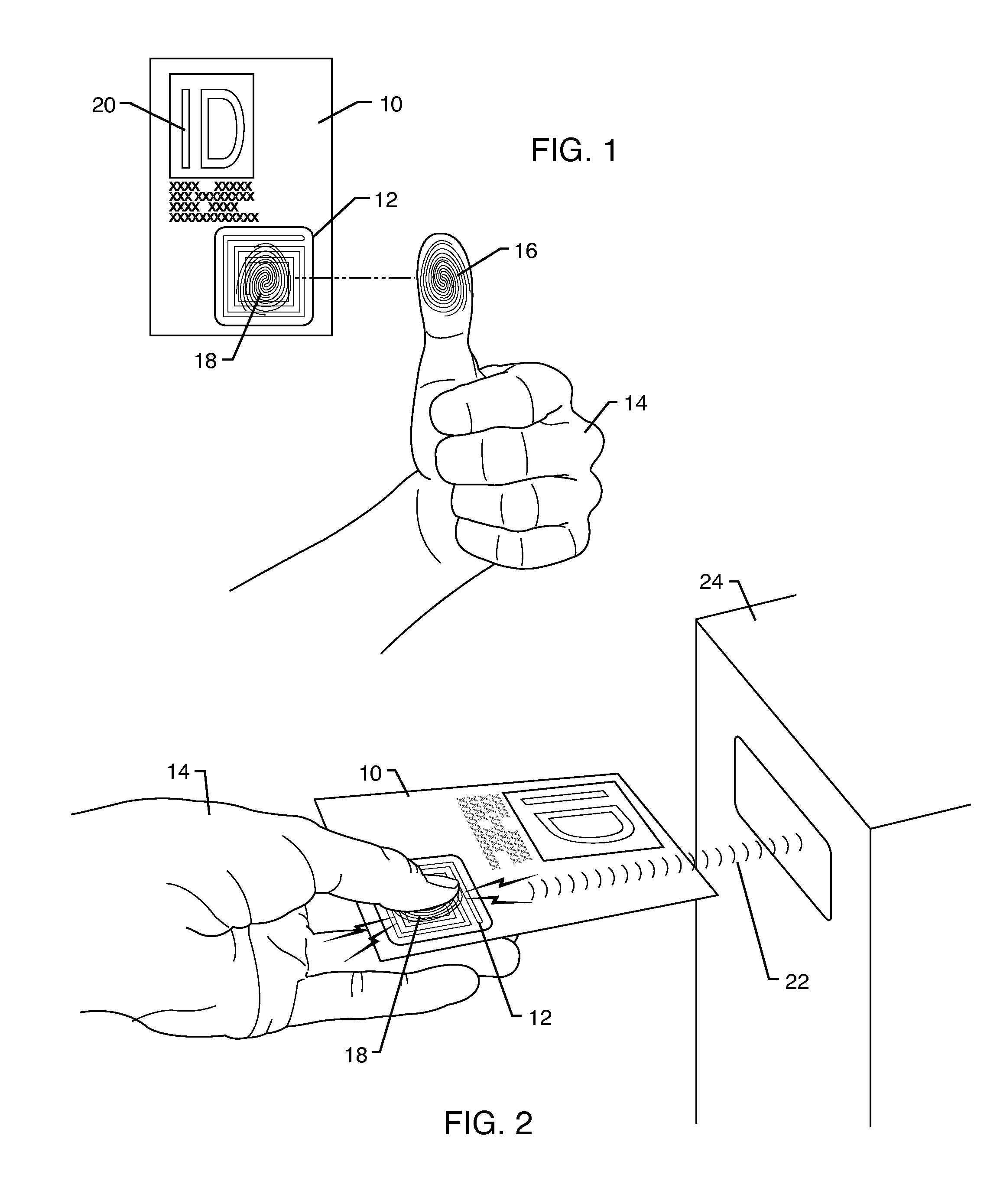
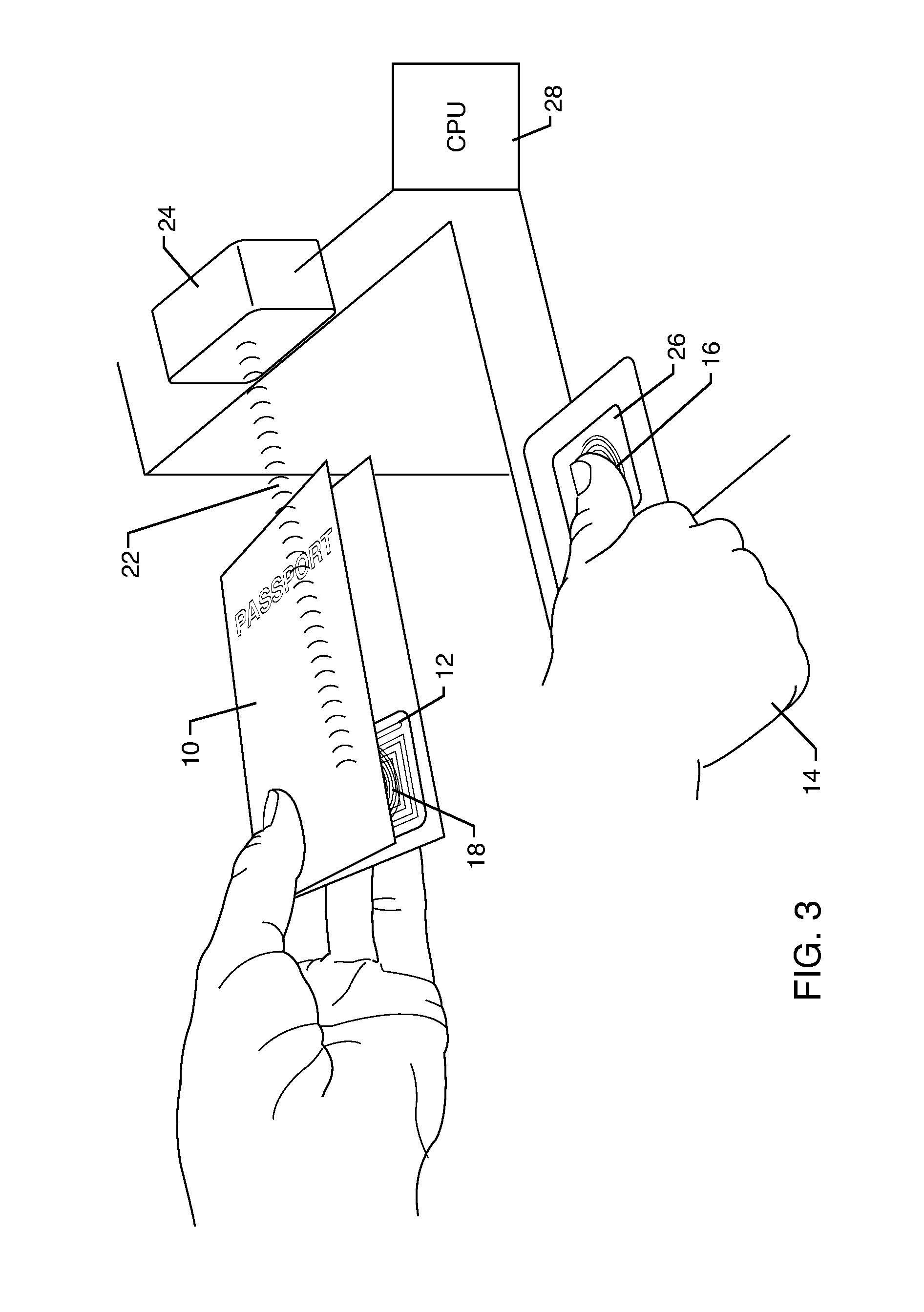
Secure photo carrying identification device, as well as means and method for authenticating such an identification device
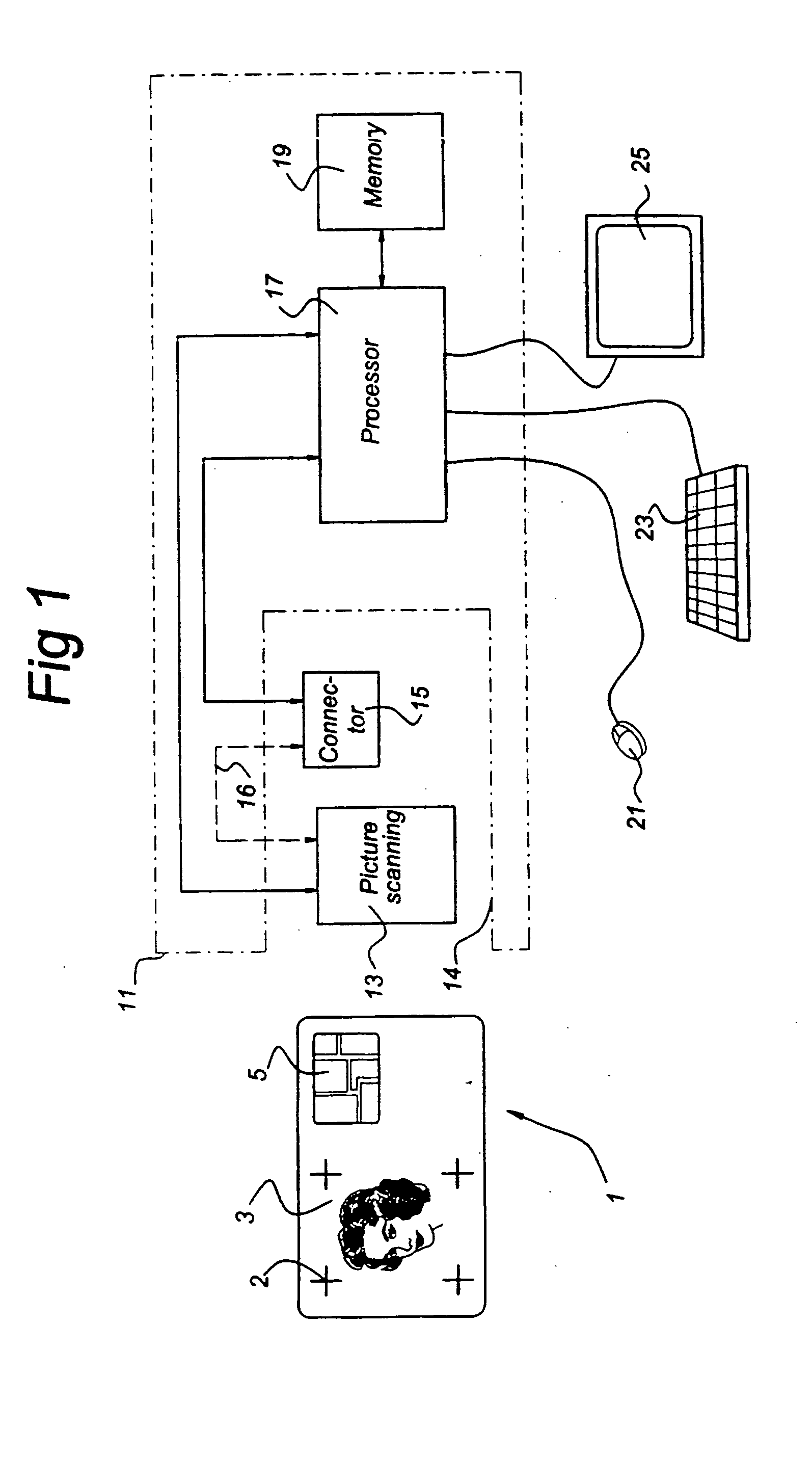
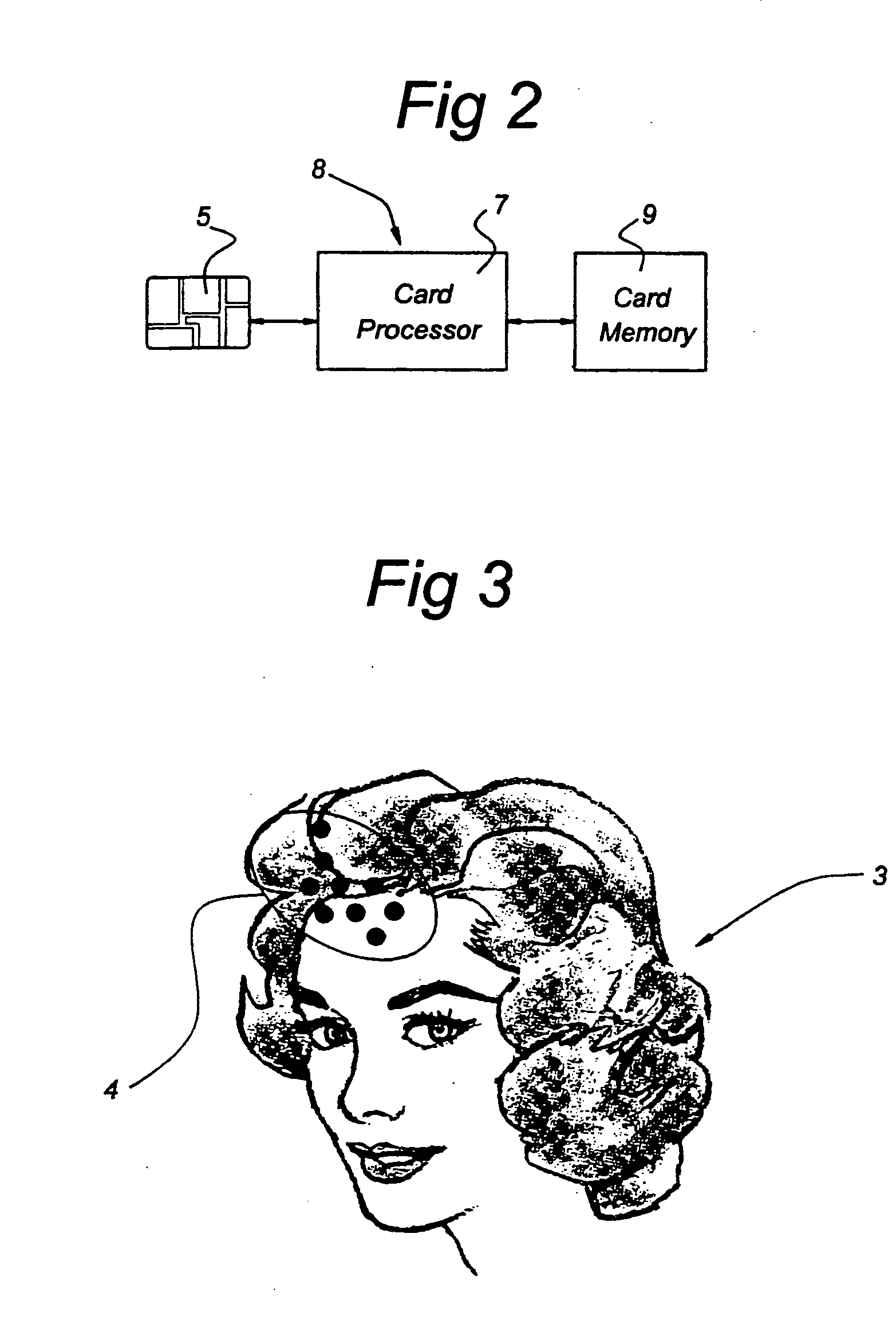
InactiveUS20050077351A1Enhanced securityImprove securityPayment architectureImage data processing detailsImage analysisInternet privacy
Means and a method for authenticating a photographic image (3) on an identification device (1), the identification device (1) being provided with: a photographic image of a person (3) and a microprocessor (8), the microprocessor (8) having: a) a processor (7), b) a memory (9) connected to the processor (7) and having stored authentication data, and c) interface means (5) connected to the processor (7) for communicating with an external device, wherein said photographic image (3) comprises stegano-graphically hidden information, the content of which together with said authentication data allows authentication of said photographic image (3), the method having the following steps: a′) scanning the photographic image (3) and generating image data. b′) analyzing these image data in accordance with a predetermined image analysis procedure to derive said hidden information, and c′) carrying out the authentication of the photographic image (3) based on the hidden information and the authentication data.
Owner:SUN MICROSYSTEMS INC
Personal token read system and method
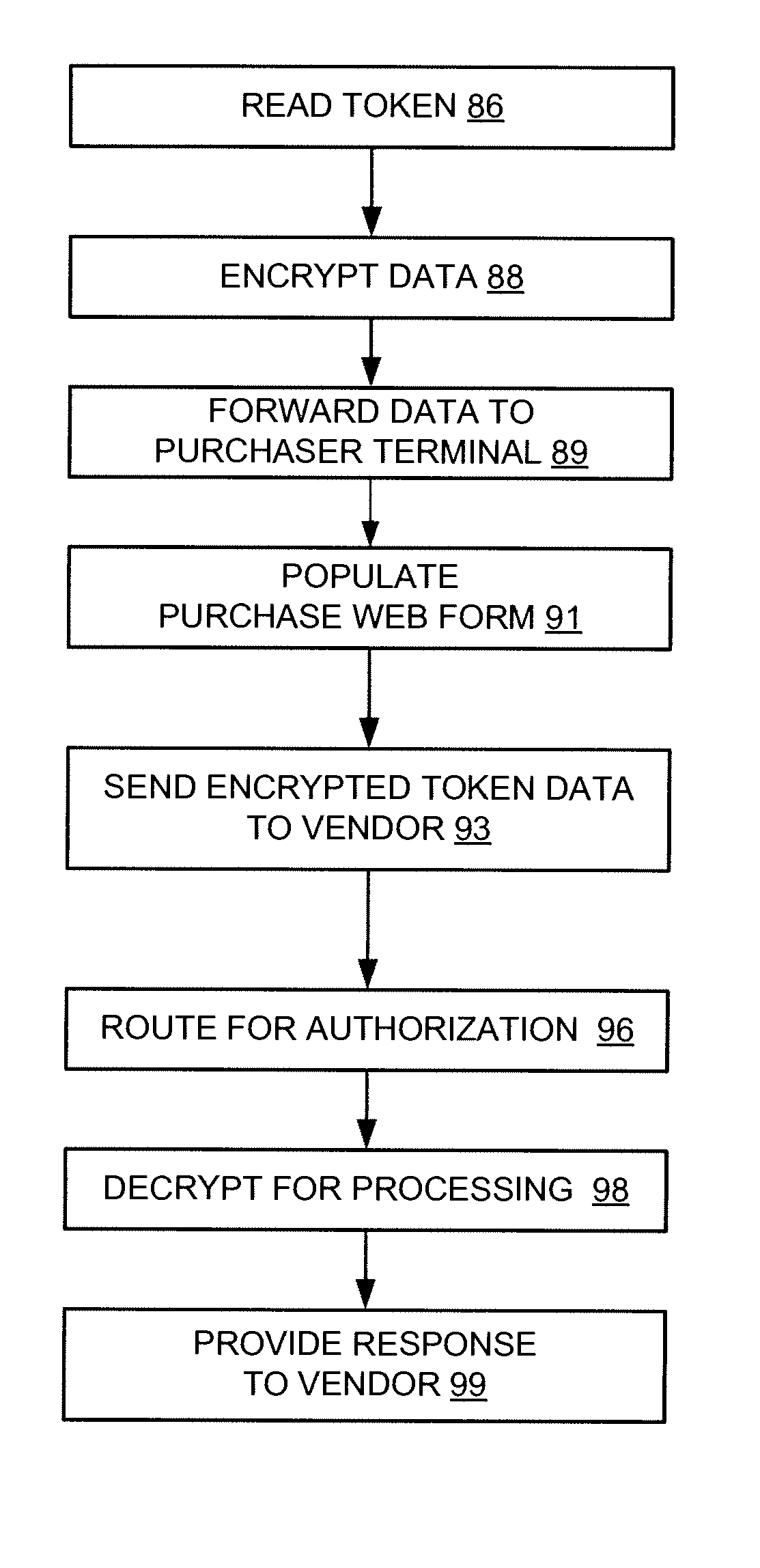
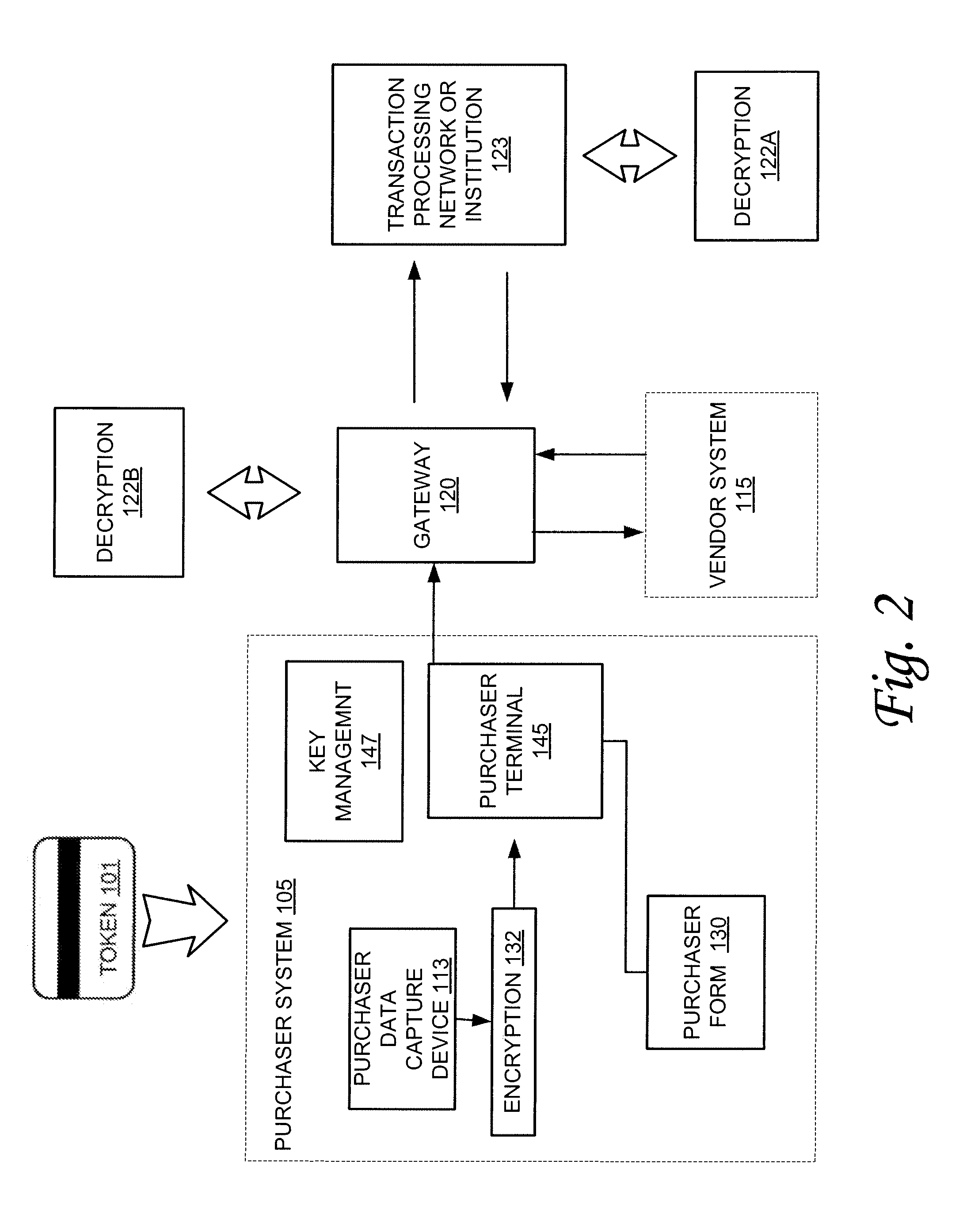
ActiveUS20080091617A1Enhanced securityFacilitate consummationCryptography processingComputer security arrangementsData shippingEncryption
A system for facilitating secure transactions between a purchaser and a vendor is provided. The system might include a purchaser token data capture device for reading token data into the system, an encryption module for encrypting the token data and a network based vendor input form for communicating the encrypted token data to the vendor. The system might further include a purchaser terminal for routing the encrypted token data to a transaction processing network or a vendor for providing payment and confirmation to the vendor of an authorized token.
Owner:VERIFONE INC
Apparatus system and method for real-time migration of data related to authentication
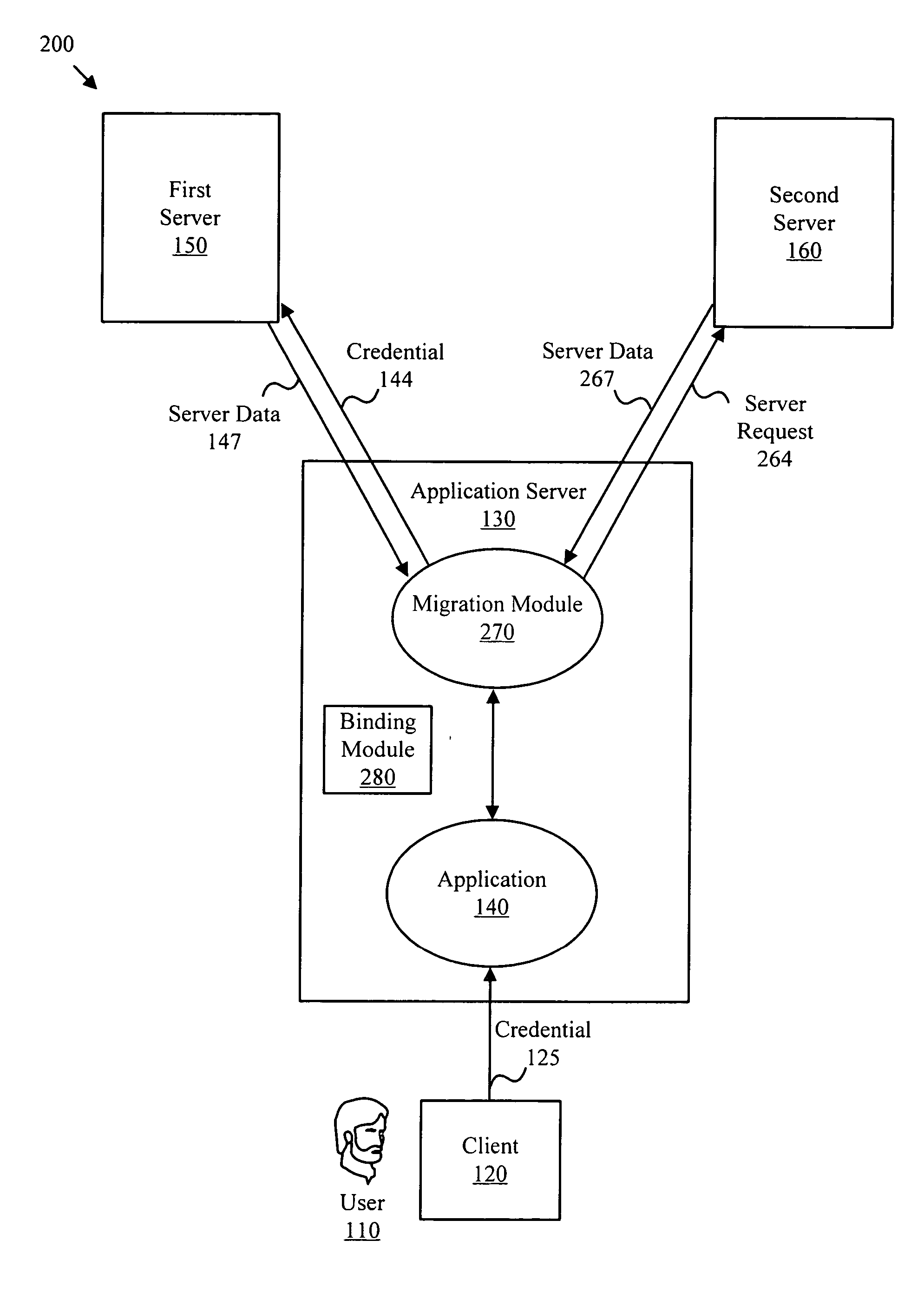
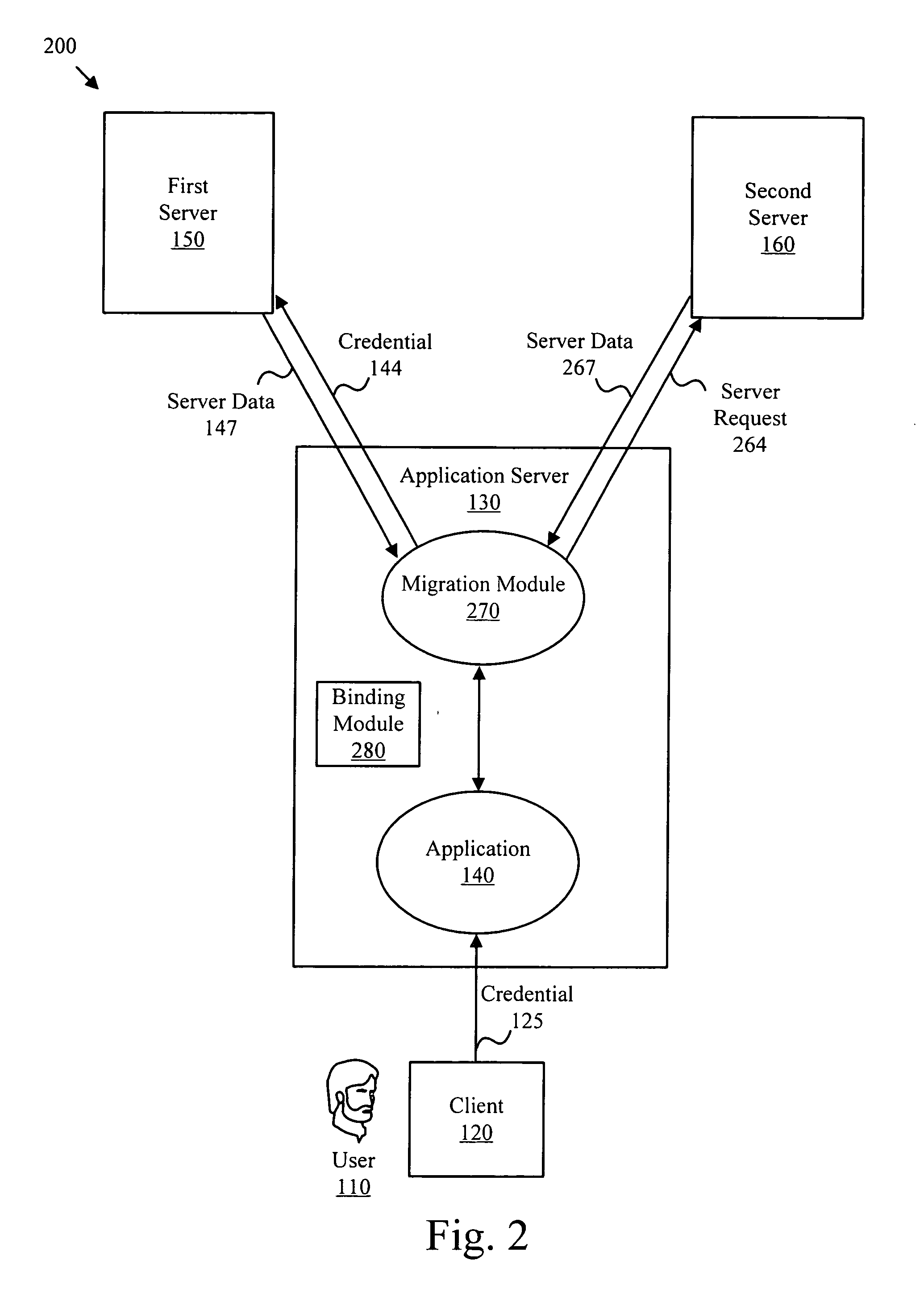
InactiveUS20070083917A1Enhanced securityImprove securityDigital data processing detailsUser identity/authority verificationAuthentication protocolAuthentication server
The present invention facilitates deploying a new authentication protocol in an established application environment. In one embodiment, an authentication credential is intercepted by a migration module that determines whether data associated with the specified account needs to be migrated from an established server to a target authentication server. A binding module may redirect authentication credentials intended for the established server to the migration module. In one embodiment, new user accounts may be added on the target authentication server, if specified by configuration options. Data associated with user accounts such as titles, telephone numbers, addresses, or the like may be migrated from the established server to the target server with the authentication data.
Owner:QUEST SOFTWARE INC
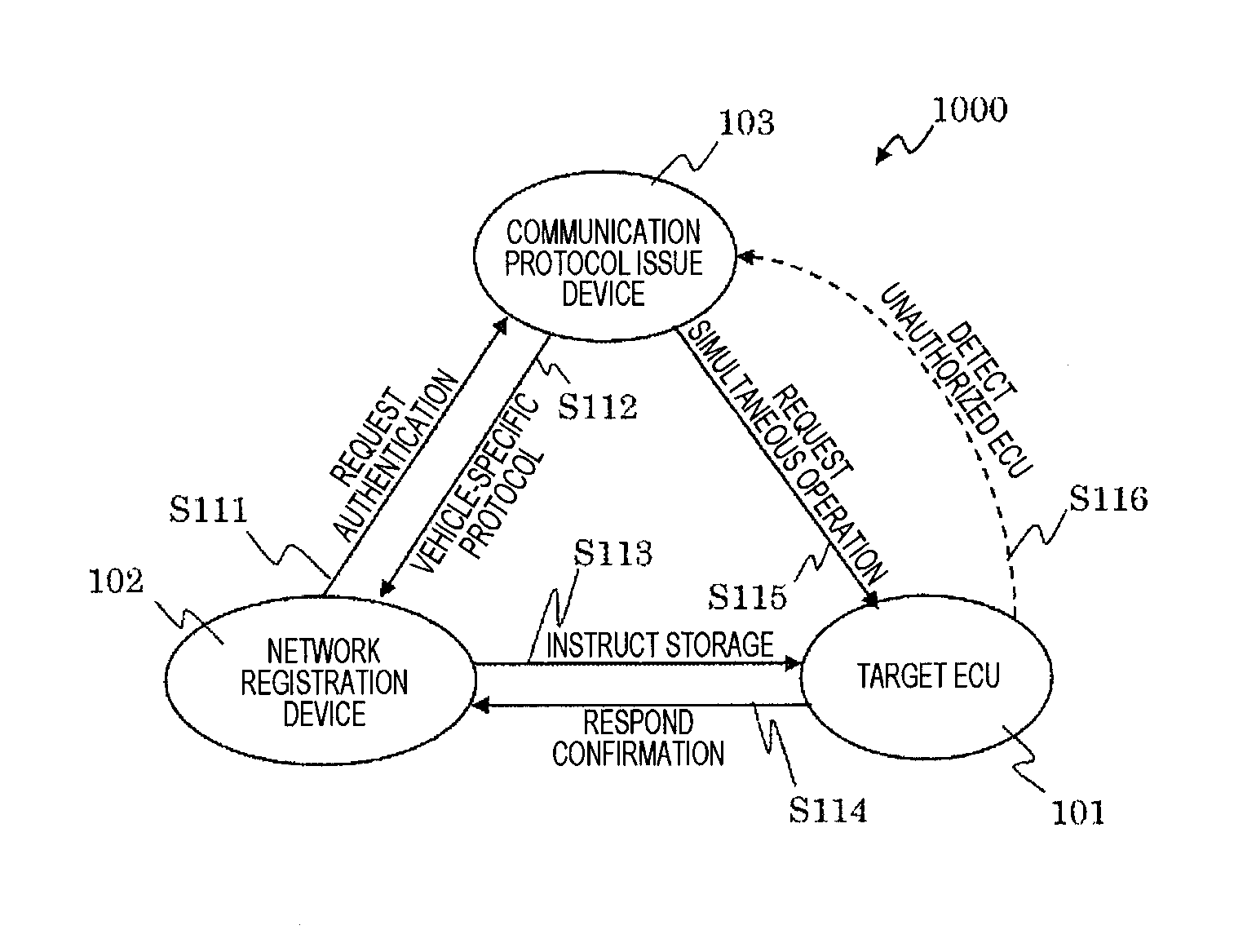
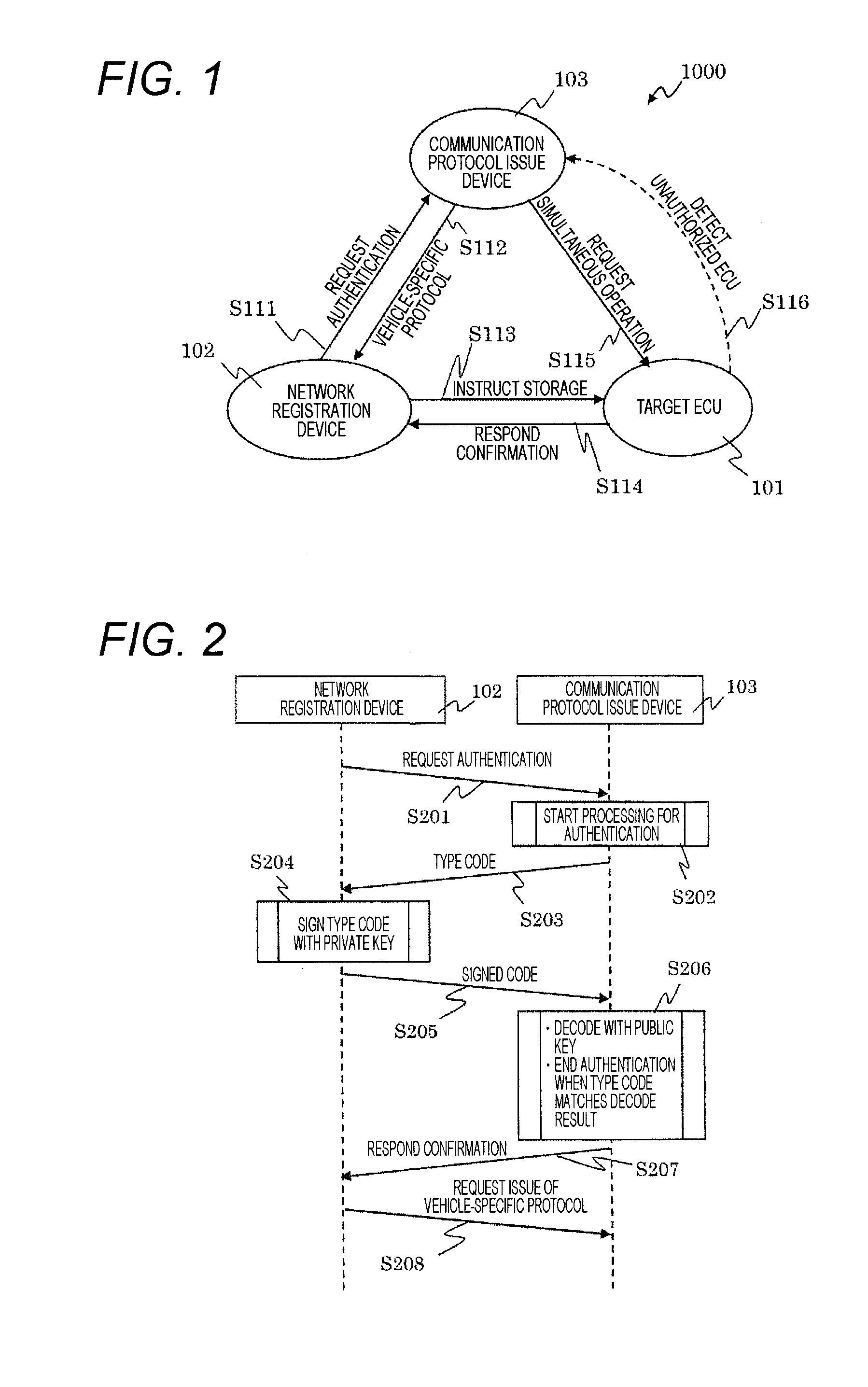
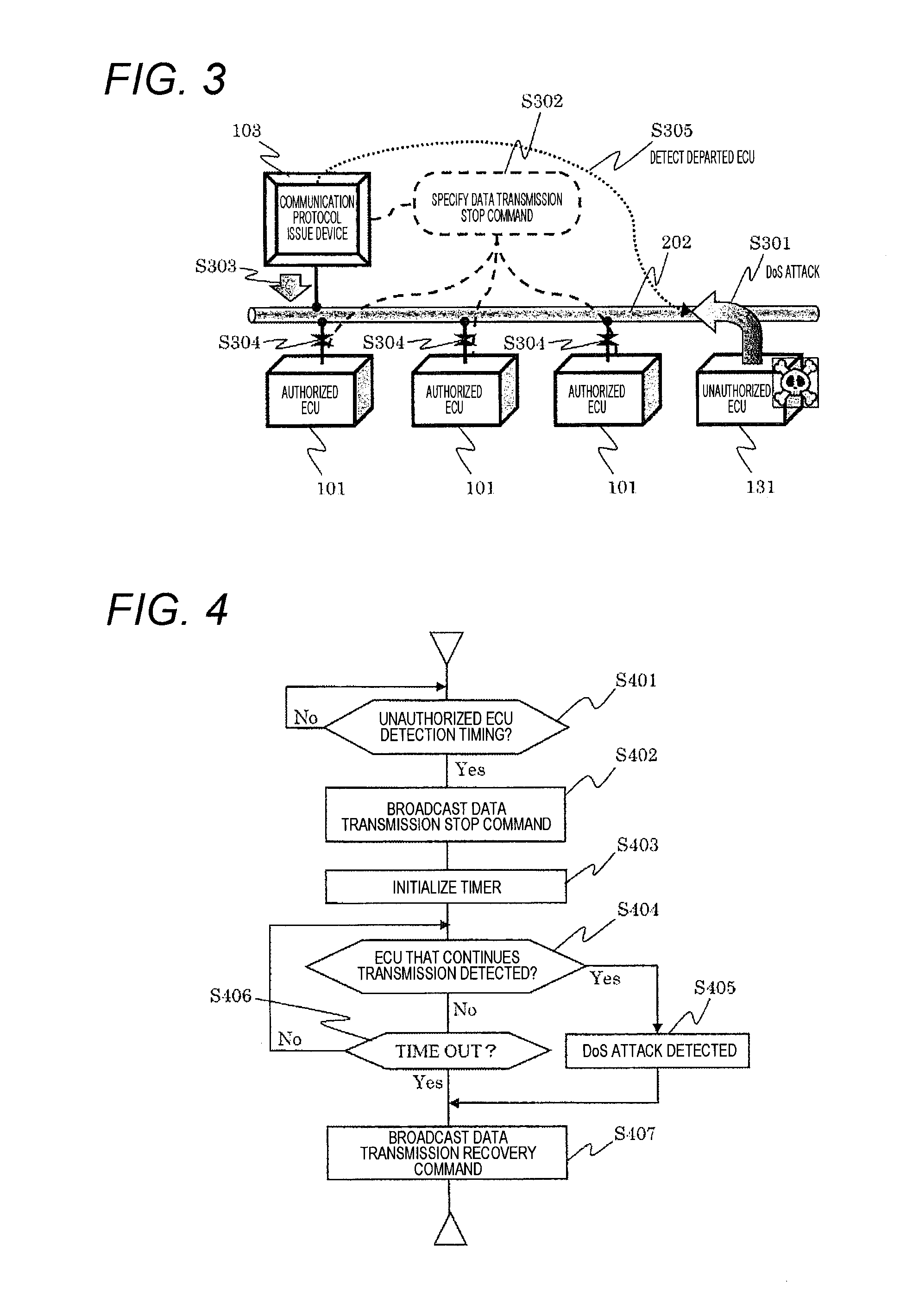
Vehicle-Mounted Network System
InactiveUS20160173530A1Secure reliabilityEnhanced securityDigital data processing detailsMultiple digital computer combinationsReal-time computing
Provided is a vehicle-mounted network system that enhances security of a vehicle by detecting or eliminating an attack on a vehicle-mounted network from an unauthorized ECU while reducing an increase in a processing load (and cost) of each vehicle-mounted control device.The vehicle-mounted network system according to the present invention provides a communication protocol issue device having a function of distributing definition data that defines a portion that is based on implementation on the vehicle-mounted network among communication protocols to the vehicle-mounted control device via a registration device that allows the vehicle-mounted control device to register in the vehicle-mounted network.
Owner:HITACHI AUTOMOTIVE SYST LTD
Method and apparatus for creation and use of digital identification
ActiveUS20200042685A1Enhanced securityAuthorization may be expandedDigital data authenticationTransmissionComputer visionComputer graphics (images)
A method for generating a digital ID comprising capturing one or more user images of user's face, transmitting the one or more user images or data derived therefrom to a verification server and determining if the one or more images represent a live person. Capturing an ID image of a photo identification for the user and transmitting the ID image to the verification sever. Comparing at least one of the one or more user images or data derived therefrom to the image of the user on the photo identification to determine if user in the one or more user images is the same person as the image on the photo identification. Responsive to a match from the comparing and a determination that a live person was captured in the one or more user images, generating a user digital ID and transmitting the user digital ID to the user.
Owner:FACETEC INC
Anti-identity theft and information security system process
ActiveUS20120200389A1Enhanced securityImprove securityElectric signal transmission systemsImage analysisSecurity informationIdentity theft
The anti-identity theft and information security system process includes storing secure information in association with an electronic device having a communication circuit for sending and receiving data. Biometric information is read with a scanner so that the identity of a user can be authenticating in connection with the supplied biometric information. Once approved, a data communication line is established with a remote device and access to the secure information is unlocked. Thereafter, the secure information may be transmitted between the electronic device and the remote device.
Owner:THE COOPER UNION FOR THE ADVANCEMENT OF SCI & ART
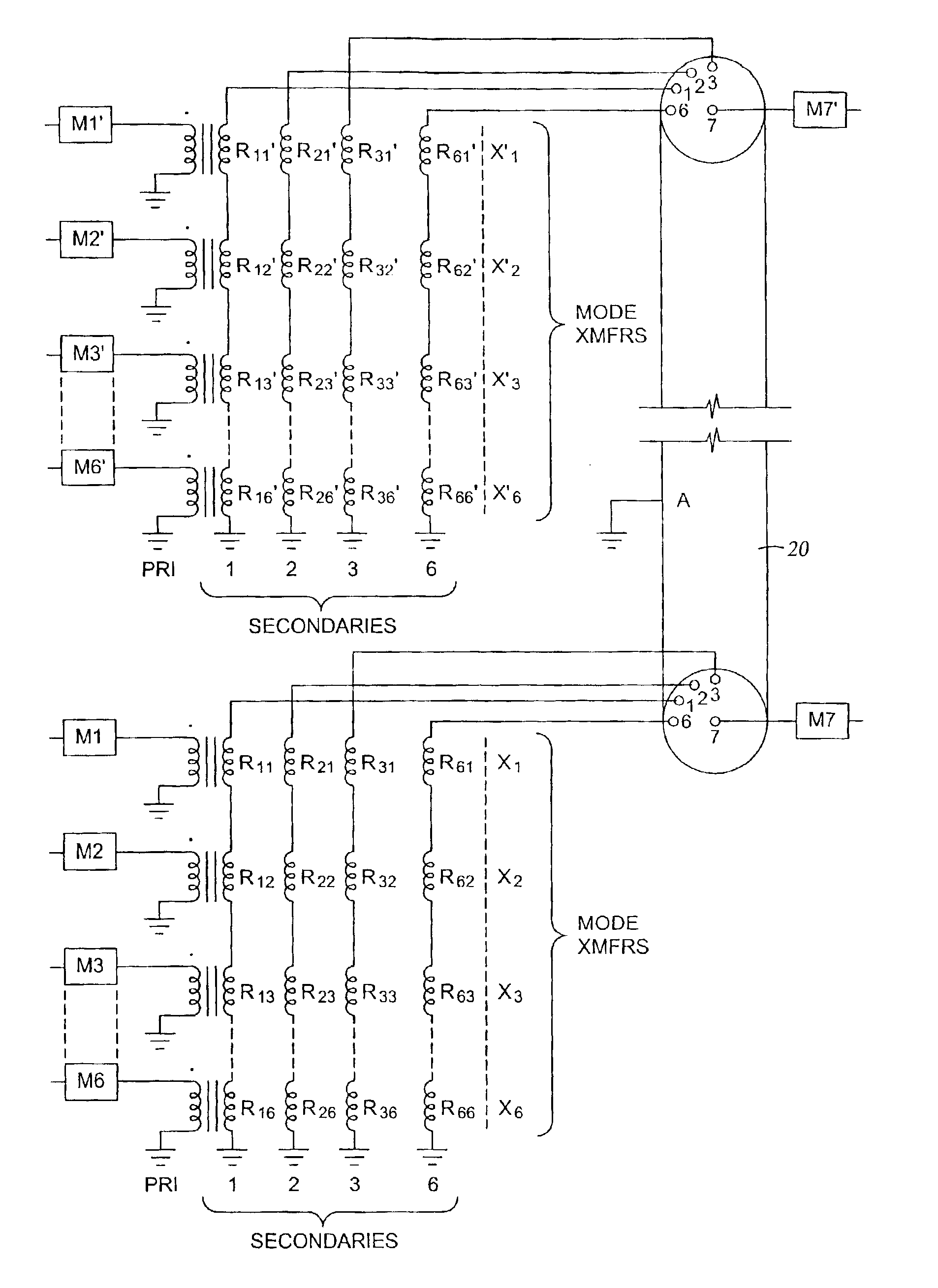
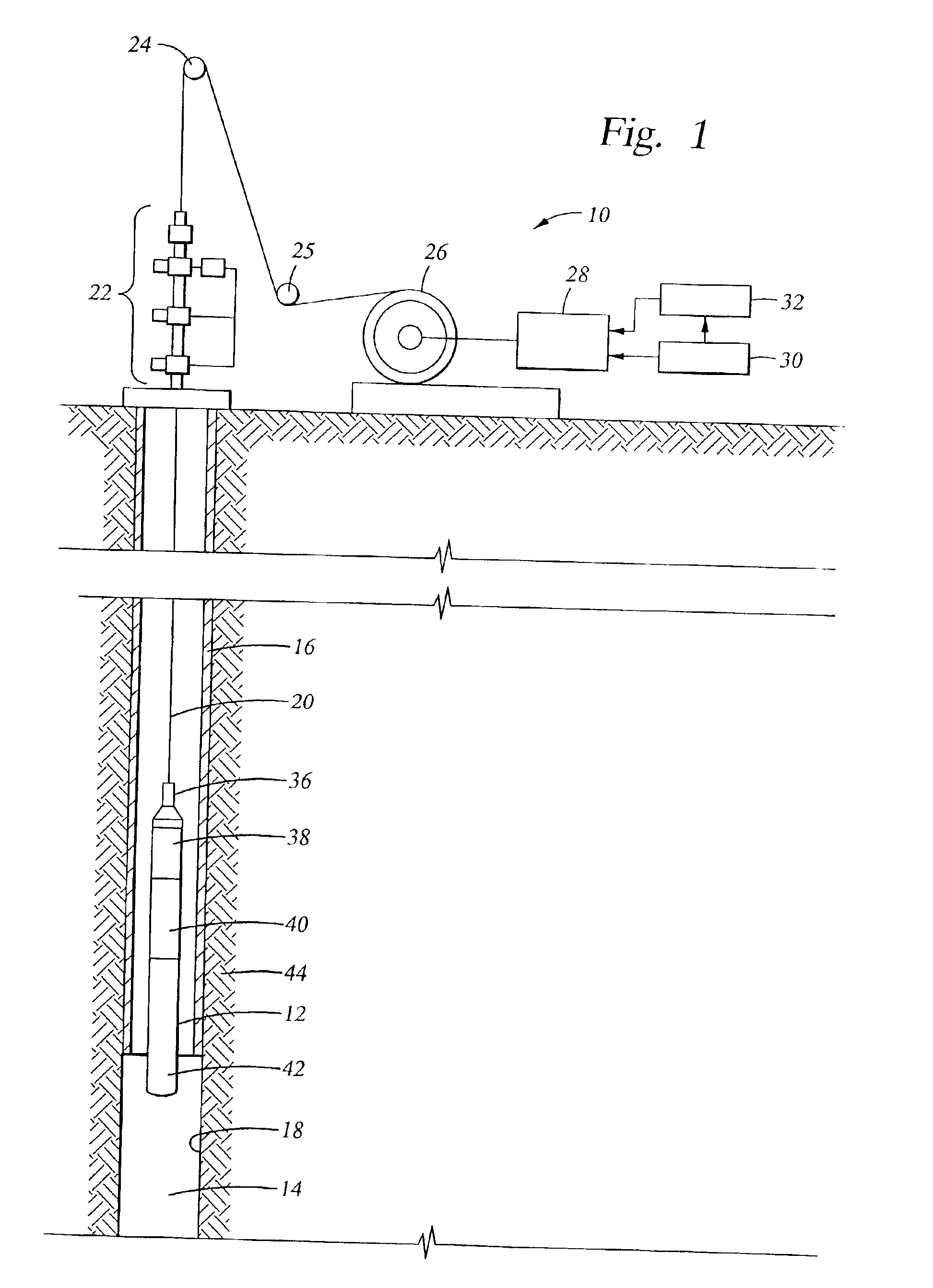
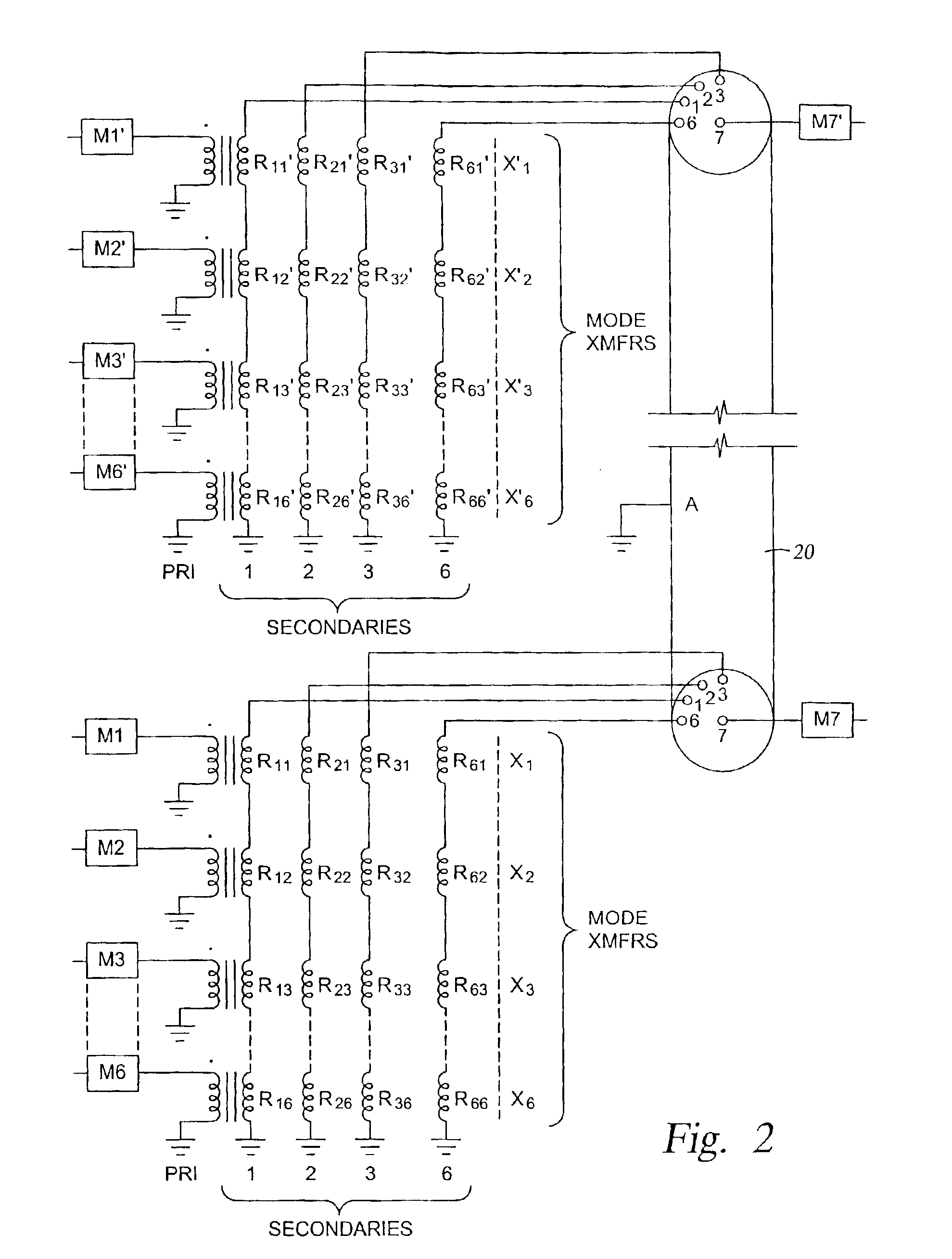
High-power well logging method and apparatus
A system and method for downhole power delivery. In one embodiment, the system delivers computer-regulated downhole power voltages, and may be configured to customize signal waveforms and power allocation on the various independent signal transmission modes to maximize the power capacity of the logging cable subject to its maximum voltage rating. In one embodiment, the system includes a standard multiconductor logging cable which supports orthogonal signal transmission modes on circumferentially spaced insulated conductors. A high-power power source on the surface is coupled to the insulated conductors in the cable to drive a power signal on the lowest impedance signal transmission mode. The system may further include multiple power sources operating on different independent signal transmission modes, and may also include multiple telemetry channels which share the power transmission modes via frequency multiplexing.
Owner:HALLIBURTON ENERGY SERVICES INC
Robot controller and robot system
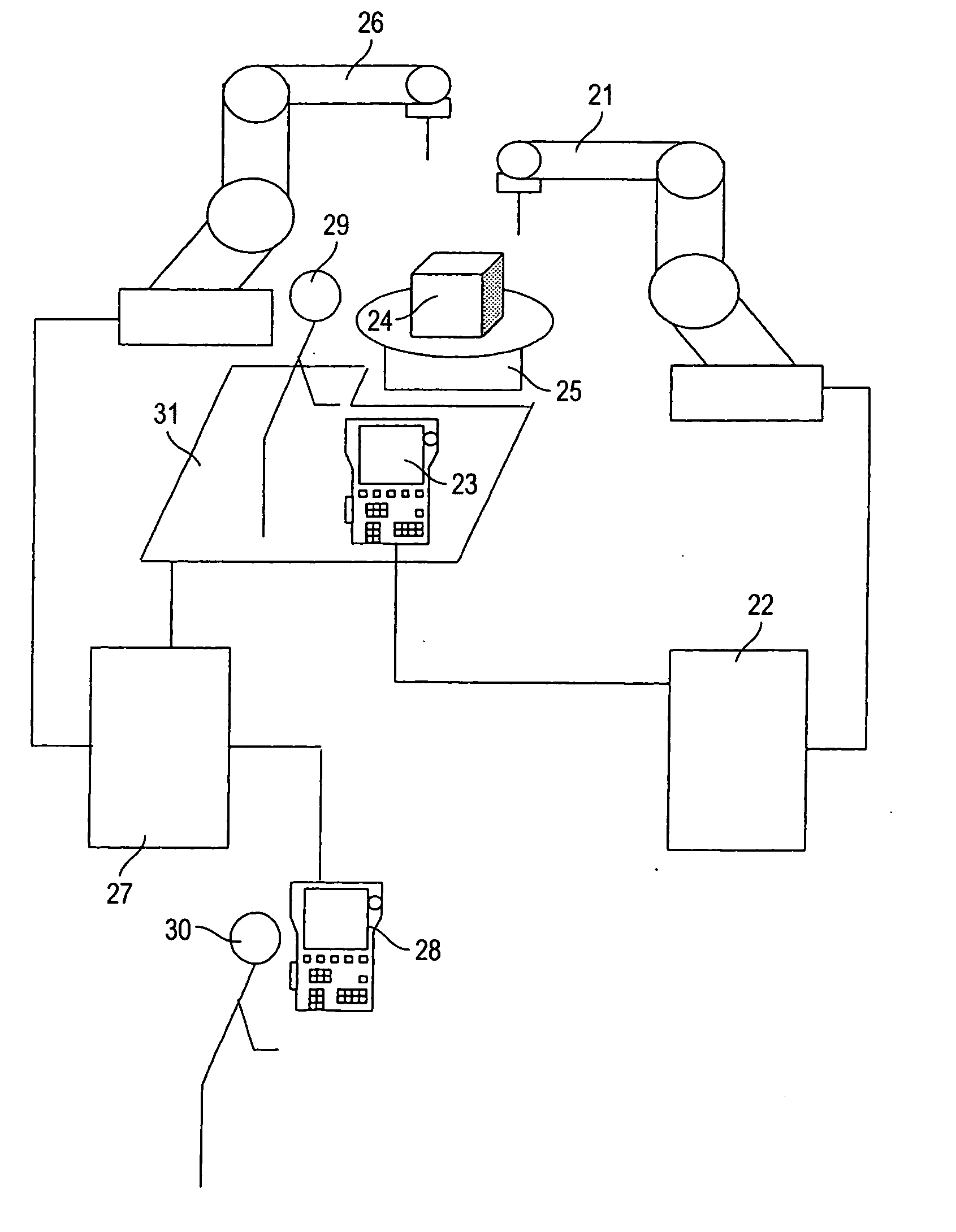
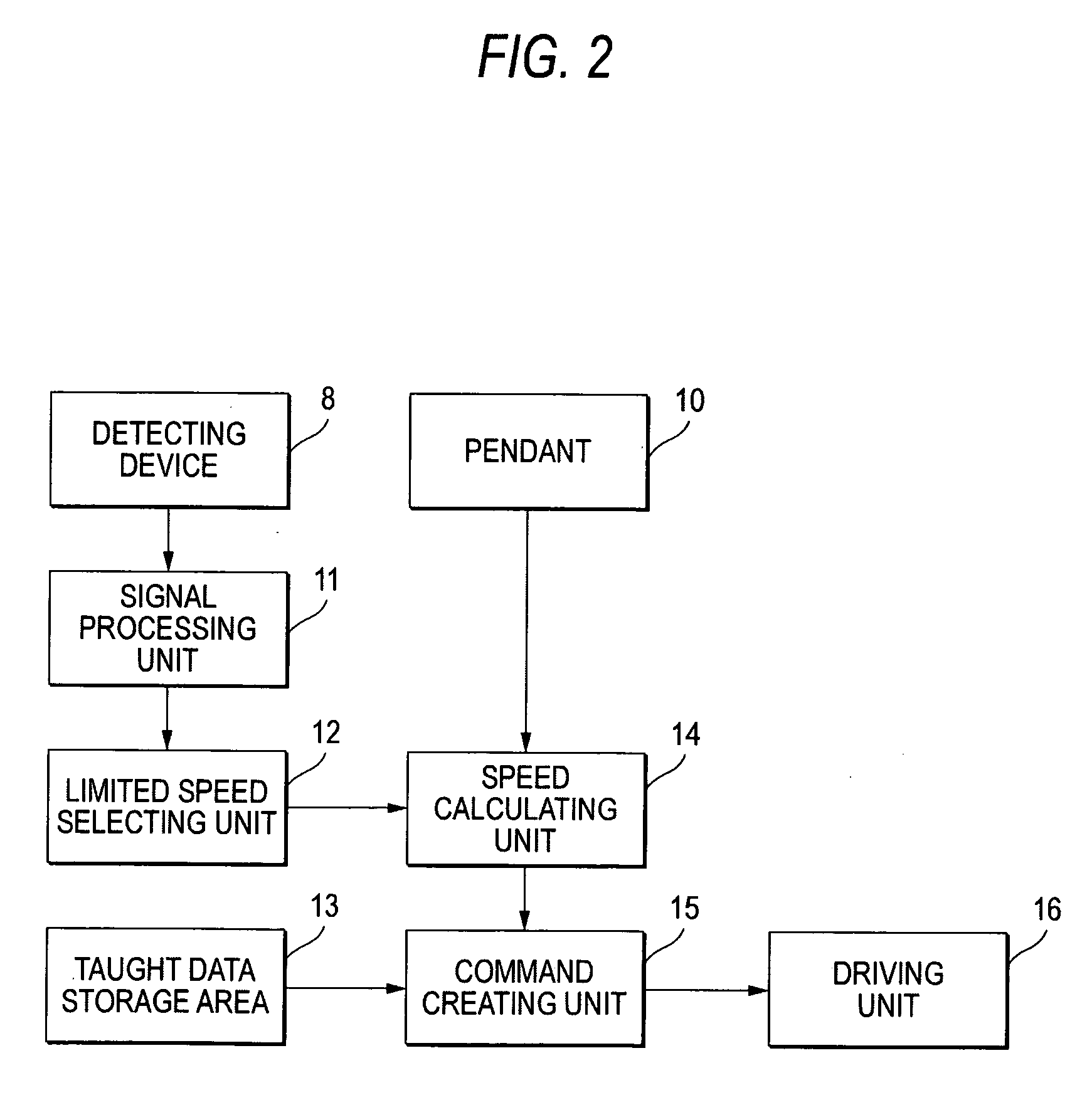
ActiveUS20060108960A1Enhanced securityTake timeProgramme-controlled manipulatorComputer controlRobotic systemsRobot control
A robot control apparatus with great safety is provided by detecting access of a teacher to a robot and automatically reducing the operating speed of the robot when the teacher accesses the robot. The robot control device equipped with a pendant (10) to be manipulated by a teacher, for controlling the operation of a robot on the basis of an operation command from the pendant (10), includes a detecting device (8) for detecting the position of the teacher; a signal processing unit (11) for receiving a signal from the detecting device to produce the position information of the teacher; and a limited speed selecting unit (12) for selecting the operating speed of the robot on the basis of the position information. The robot is controlled at the maximum speed set at the operating speed selected by the limited speed selecting unit (12) on the basis of the operation command from the pendant (10).
Owner:YASKAWA DENKI KK
Controlling session keys through in-band signaling
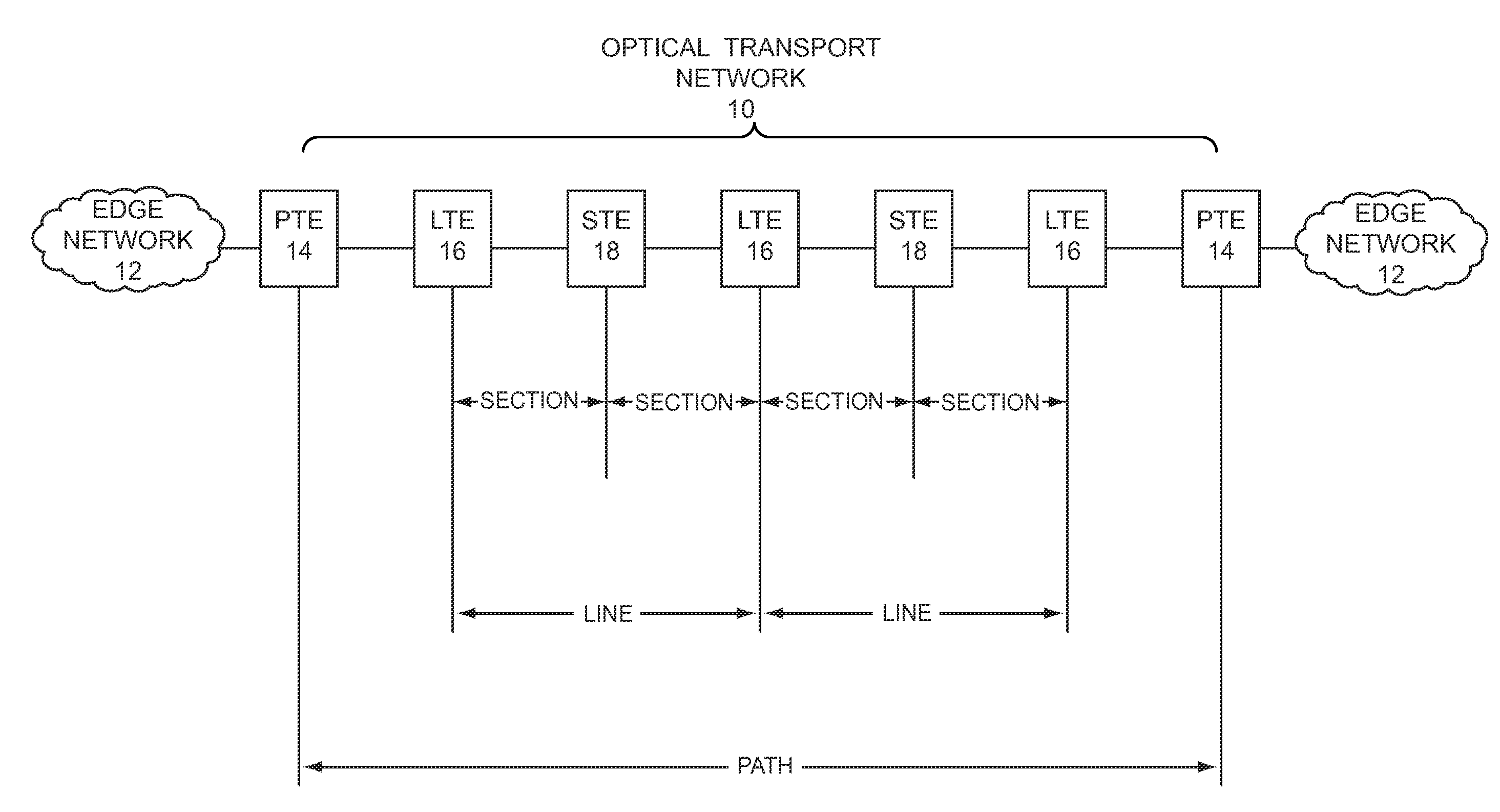
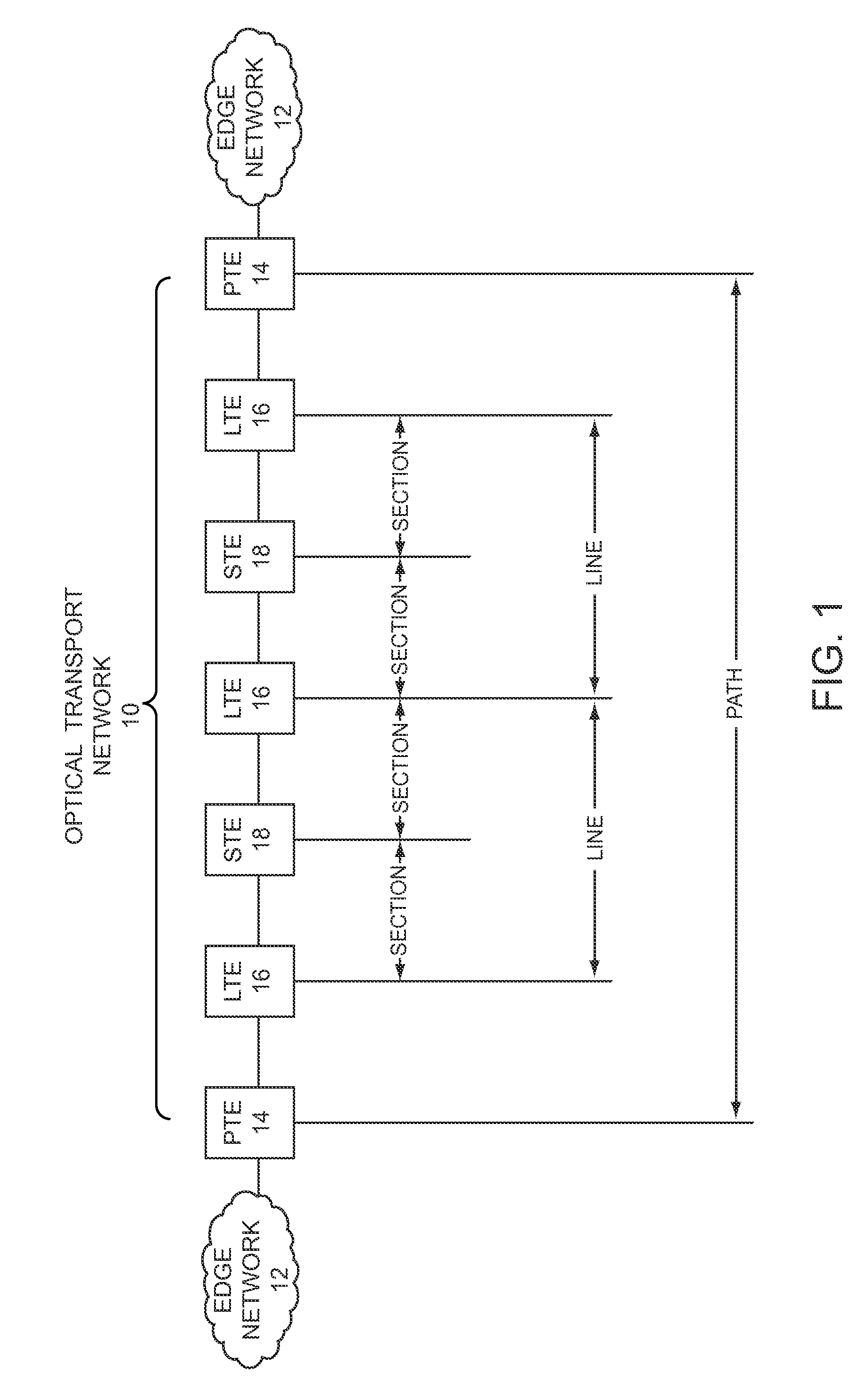
ActiveUS20100111307A1Reduce impactEnhanced securityEncryption apparatus with shift registers/memoriesSignalling and co-ordinationTraffic volumeIn-band signaling
The present invention employs in-band signaling between PTEs to provision and control session keys, which are used by the PTEs for encrypting and decrypting traffic that is carried from one PTE to another over a transport network. In operation, a first PTE will receive incoming traffic from a first edge network, map the traffic to frames, encrypt the traffic with a session key, and send the frames with the encrypted traffic over the transport network to a second PTE. The second PTE will extract the encrypted traffic from the frames, decrypt the encrypted traffic with a session key, and send the recovered traffic over a second edge network toward an intended destination. If symmetric encryption is employed, the session key used by the first PTE to encrypt the traffic will be identical to the session key used by the second PTE to decrypt the traffic.
Owner:CIENA
System and methods for detecting software vulnerabilities and malicious code
ActiveUS20090165135A1Enhanced securityMemory loss protectionError detection/correctionVulnerabilitySource code
A system and method determines whether software includes malicious code. A validation machine is instrumented with tools and monitors that capture the static and dynamic behavior of software. Software under examination is executed on the validation machine, and the tools and monitors are used to log data representative of the behavior of the software to detect vulnerable or malicious code. If possible, one or more operations are automatically performed on the software to enhance the security of the software by neutralizing the vulnerable or malicious code. Activities that cannot be neutralized automatically are flagged for human inspection. The software executed on the validation machine may be source code or non-source code, with different operations being disclosed and described in each case.
Owner:CYBERNET SYST
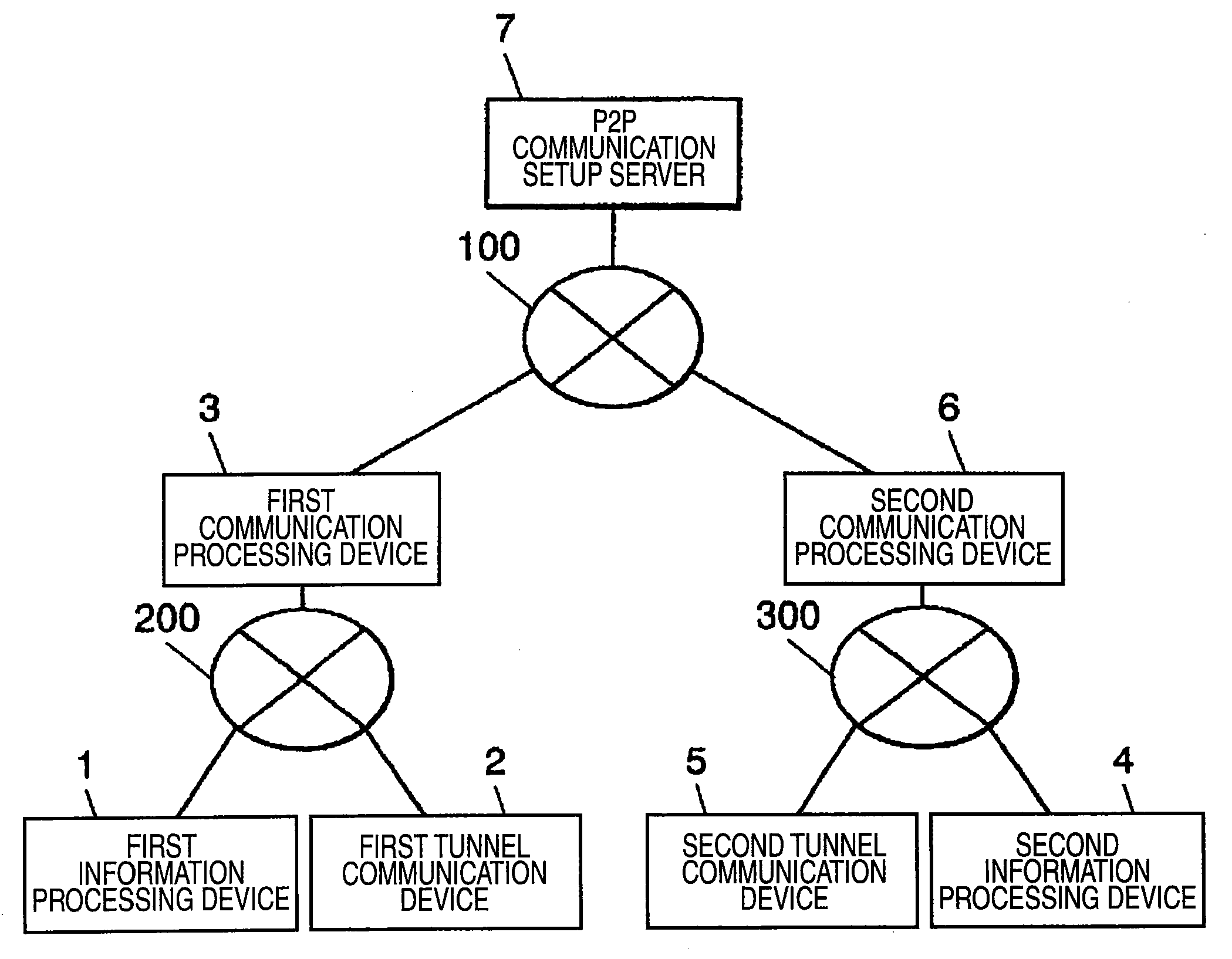
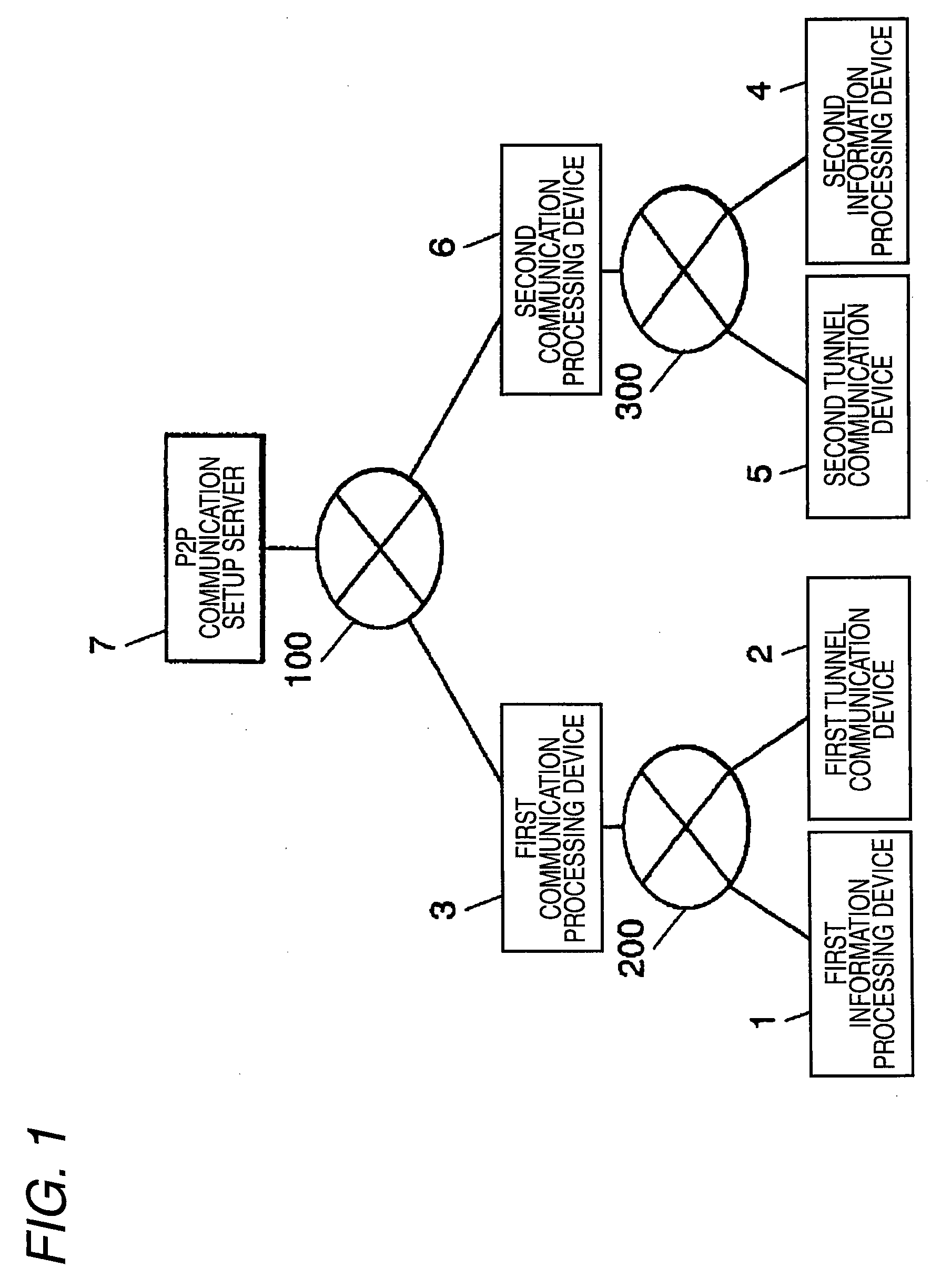
Information processing system, tunnel communication device, tunnell communication method, proxy response device, and proxy response method
ActiveUS20090232138A1Easily distinguishEnhanced securityData switching by path configurationMultiple digital computer combinationsInformation handling systemCommunication unit
Provided is an information processing system and the like that can make a communication between plural information processing devices belonging to different LANs. A first tunnel communication device includes a first address correlating information memory unit that stores information for correlating an address in a first LAN with an address in a second LAN, a first address translating unit that translates an address of a packet on the basis of the correlating information, a first P2P communication setup unit that sets up a P2P communication with a device as a destination, and a first tunnel communication unit that makes a tunnel communication through a path of a P2P communication. The packet transmitted from a first information processing device is translated in address, is encapsulated, and is then transmitted through the path of the P2P communication. The packet transmitted from the device as a destination is decapsulated, is translated in address, and is then transmitted to the first information processing device.
Owner:PANASONIC CORP
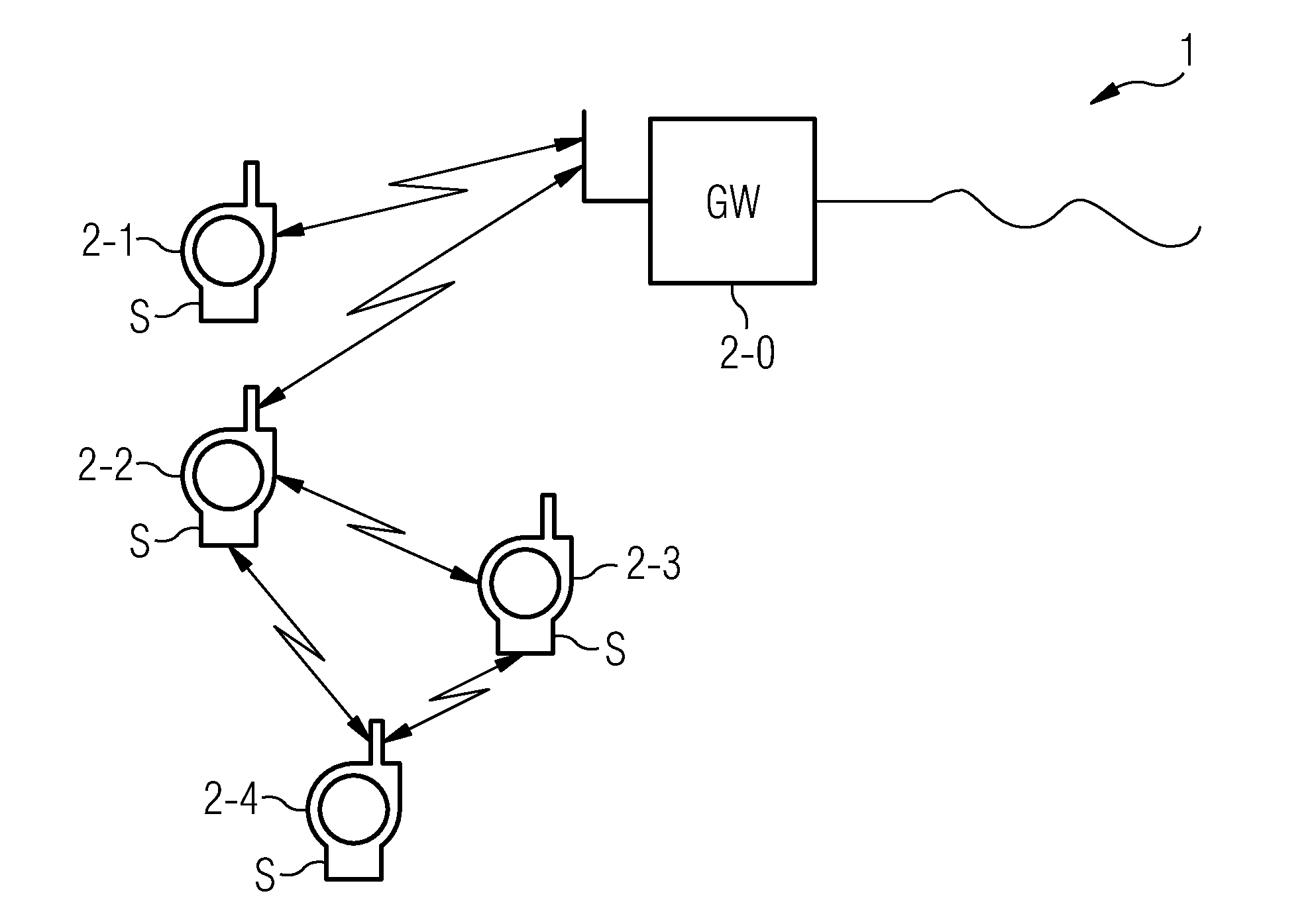
Method for transmitting data between network nodes
ActiveUS20110158410A1Enhanced securityImprove securityNetwork topologiesSecret communicationSensor nodeWireless sensor networking
A method transmits data between network nodes of a network in a cryptographically protected manner. The network nodes are, for example, sensor nodes of a wireless sensor network. In the method, in order to transmit the data in a message, a NONCE value is created from a count value which is updated in the transmission of the message and from a constant value which is provided in a shared manner to the network nodes of the network. The data transmitted in the message is then encrypted and decrypted within the network nodes by a cryptographic key and the created NONCE value. The method offers in particular protection against replay attacks while at the same time minimizing the use of resources of the network nodes.
Owner:SIEMENS AG
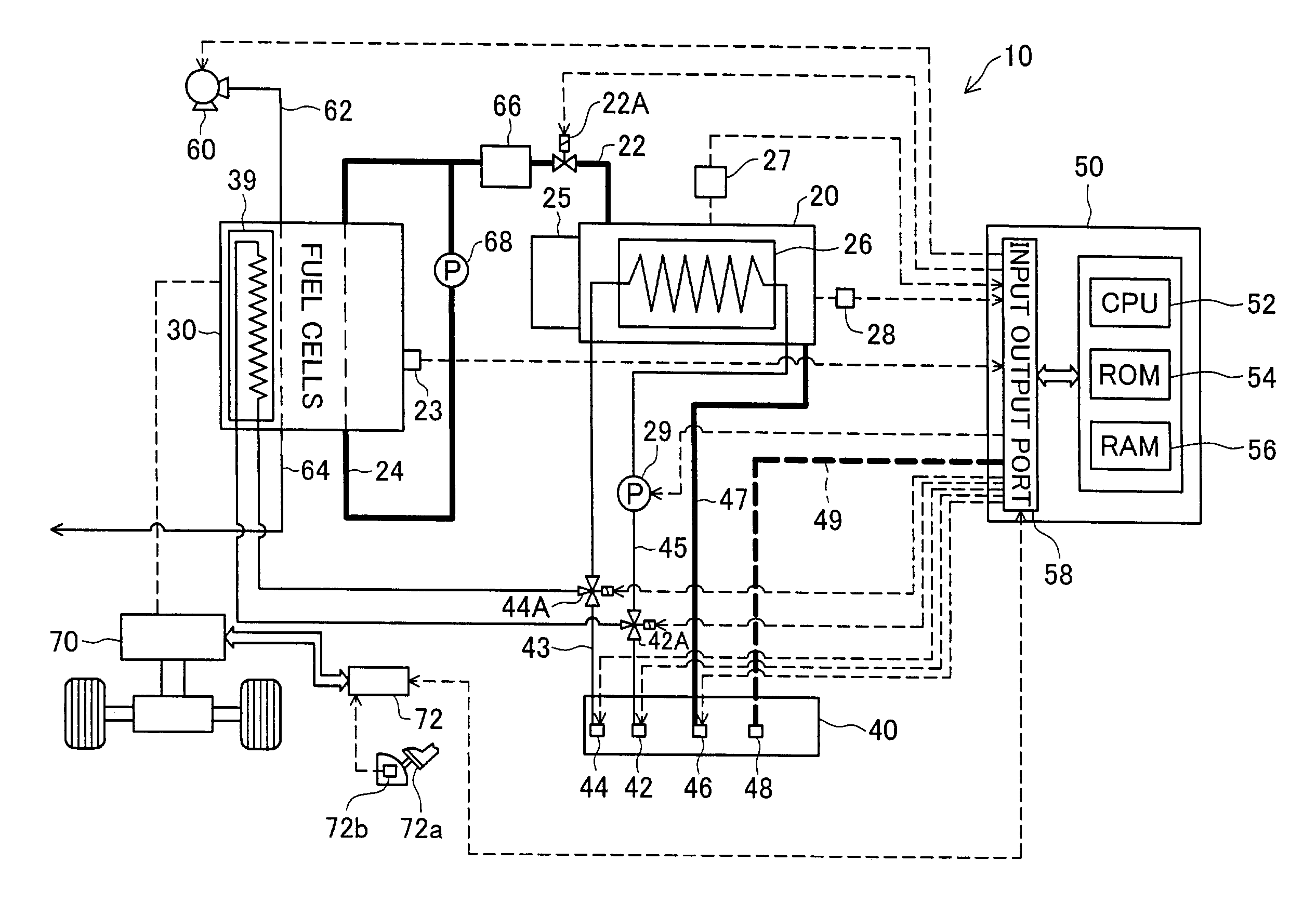
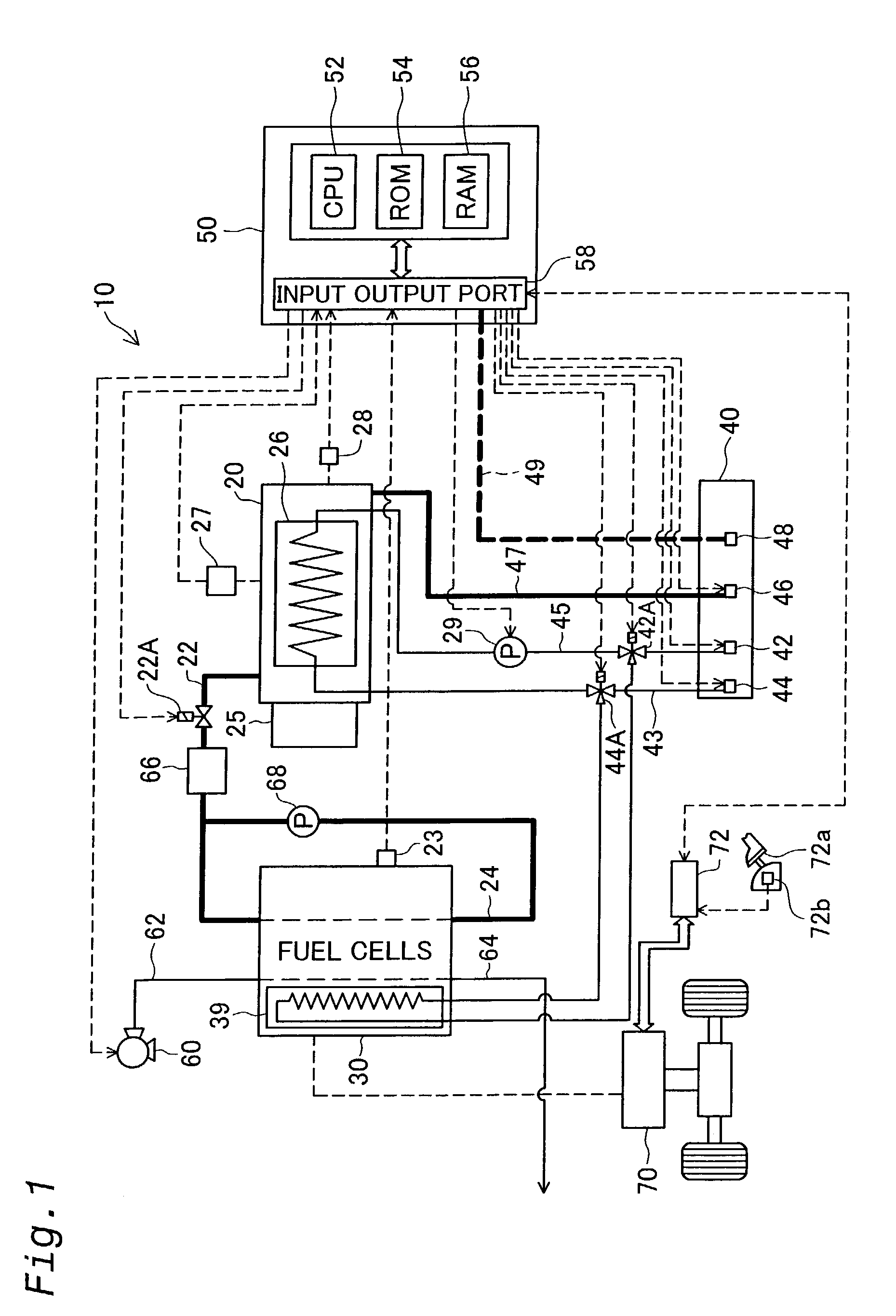
Fuel cell fuel supply system and mobile body
InactiveUS6964821B2Enhanced securityEnsure safetyAuxillary drivesReactant parameters controlFuel supplyElectric vehicle
An electric vehicle with fuel cells mounted thereon has a fuel tank that stores a fuel therein, and a connector receptor that is connected to the fuel tank and is open to the surface of the vehicle body. A connector of a predetermined hydrogen supply device is fitted in and attached to the connector receptor, so that a supply of fuel is fed from the hydrogen supply device to the electric vehicle. The connector receptor is provided with a fuel lid for covering over the connector receptor. When it is determined that the fuel cells are in a working state, the fuel lid is not opened in response to input of an opening instruction of the fuel lid in the course of fuel supply. When it is determined that the fuel lid is open, on the other hand, operation of the fuel cells is not started in response to input of a starting instruction of the fuel cells in the electric vehicle. Such an arrangement enhances the safety of fuel supply to any system with fuel cells.
Owner:TOYOTA JIDOSHA KK
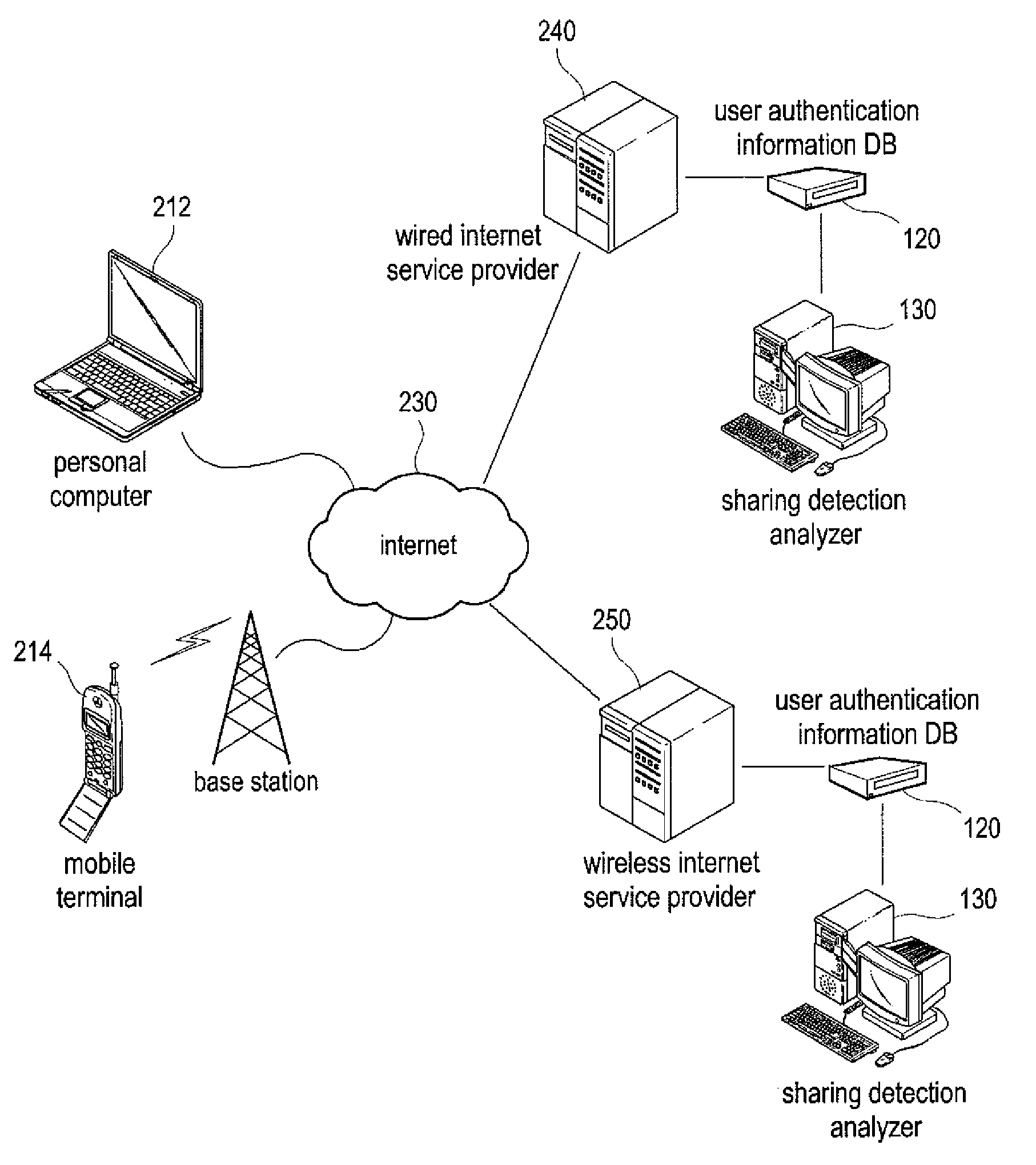
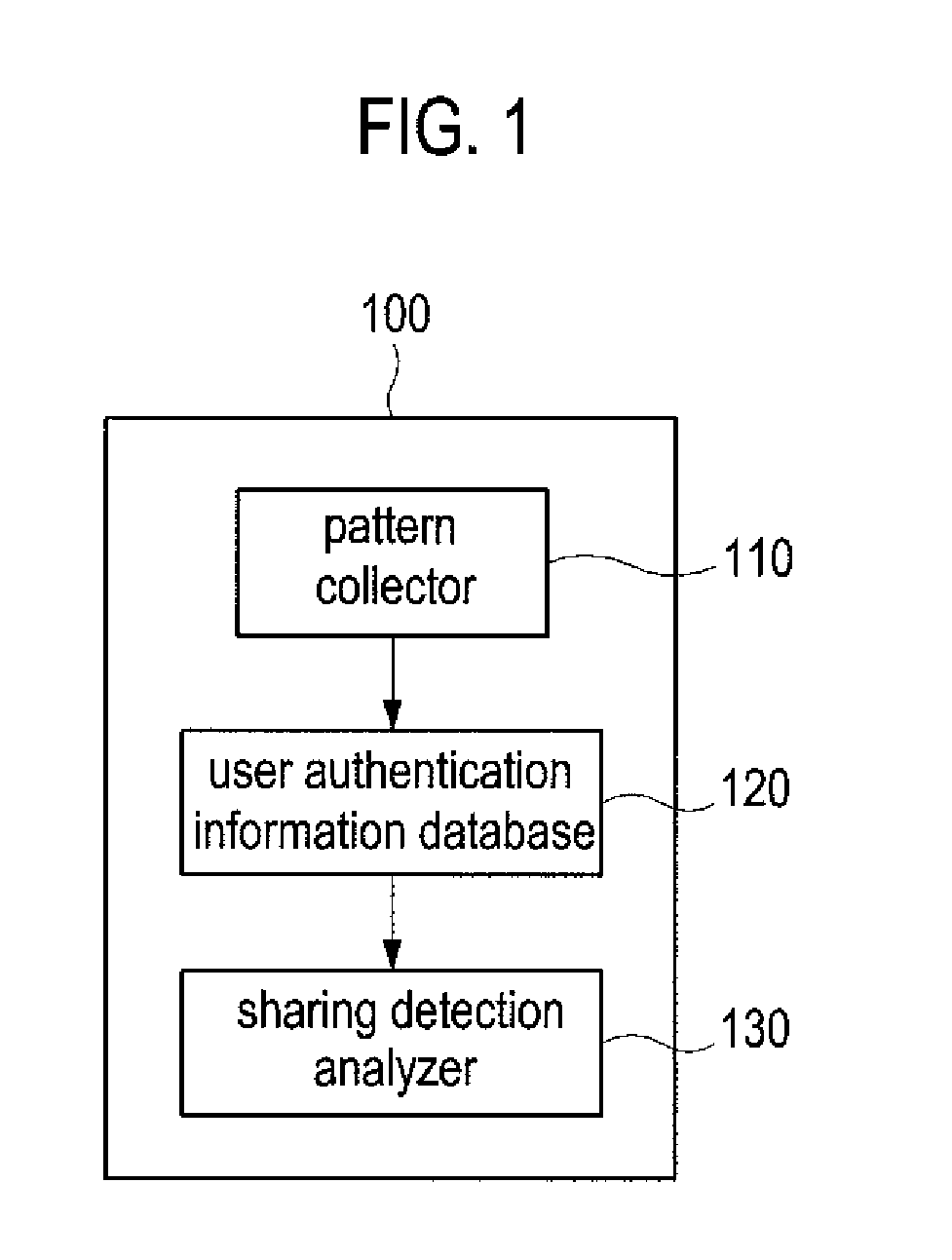
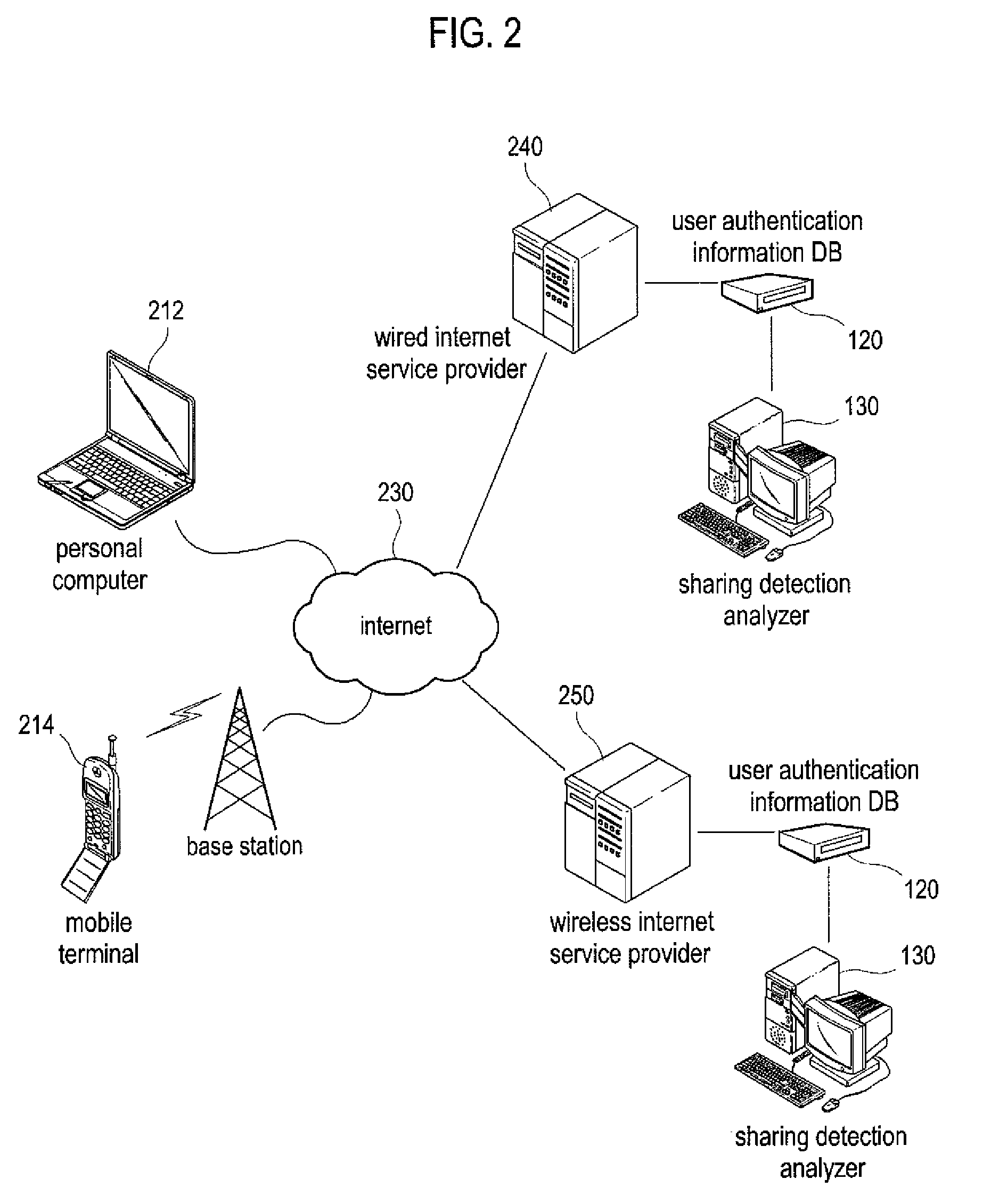
Method and system of detecting account sharing based on behavior patterns
InactiveUS20090049555A1Prevent illegal useEnhanced securityDigital data processing detailsDigital computer detailsUser authenticationBehaviour pattern
A system of detecting account sharing, based on analysis of users' behavior patterns is provided. In the present invention, the system comprises: a user authentication information database storing keystroke dynamics patterns related to a particular account in association with the account; and a sharing detection analyzer to analyze a cluster distribution of the keystroke dynamics patterns stored in the user authentication information database to determine whether the account is shared.
Owner:SEOUL NAT UNIV R&DB FOUND
Surgical manipulator
InactiveUS7625383B2Enhance precision and dexterityEnhanced securityNanotechDiagnosticsSix degrees of freedomSurgical department
The present invention provides a surgical manipulator which capable of manipulating a surgical or medical tool in up to six degrees of freedom. The manipulator has a relatively lightweight, compact design as a result of the use of high force to mass ratio actuators. The manipulator includes a mounting fixture which permits the manipulator to be fixed relative to a portion of a body of a patient.
Owner:MICRODEXTERITY SYST
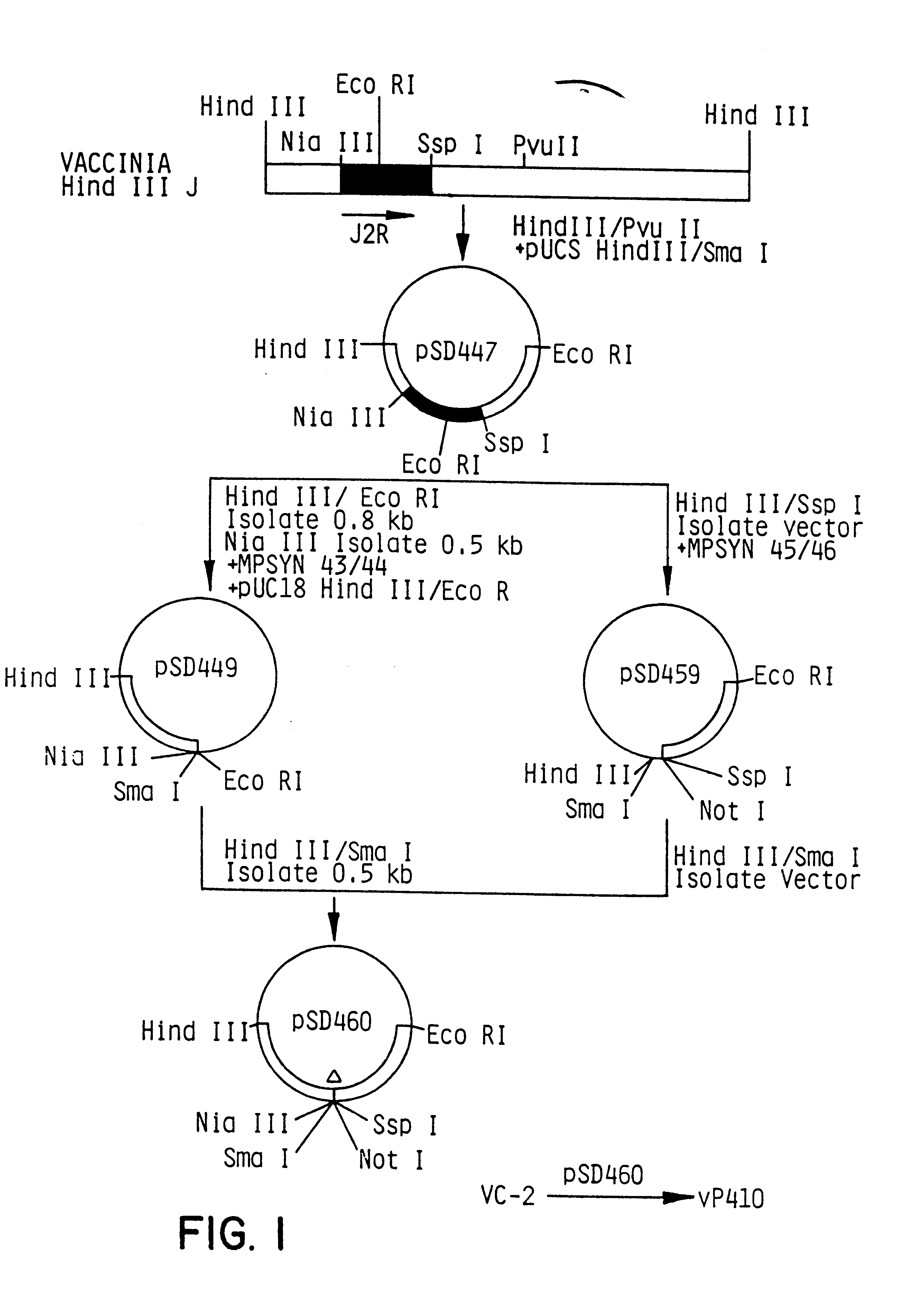
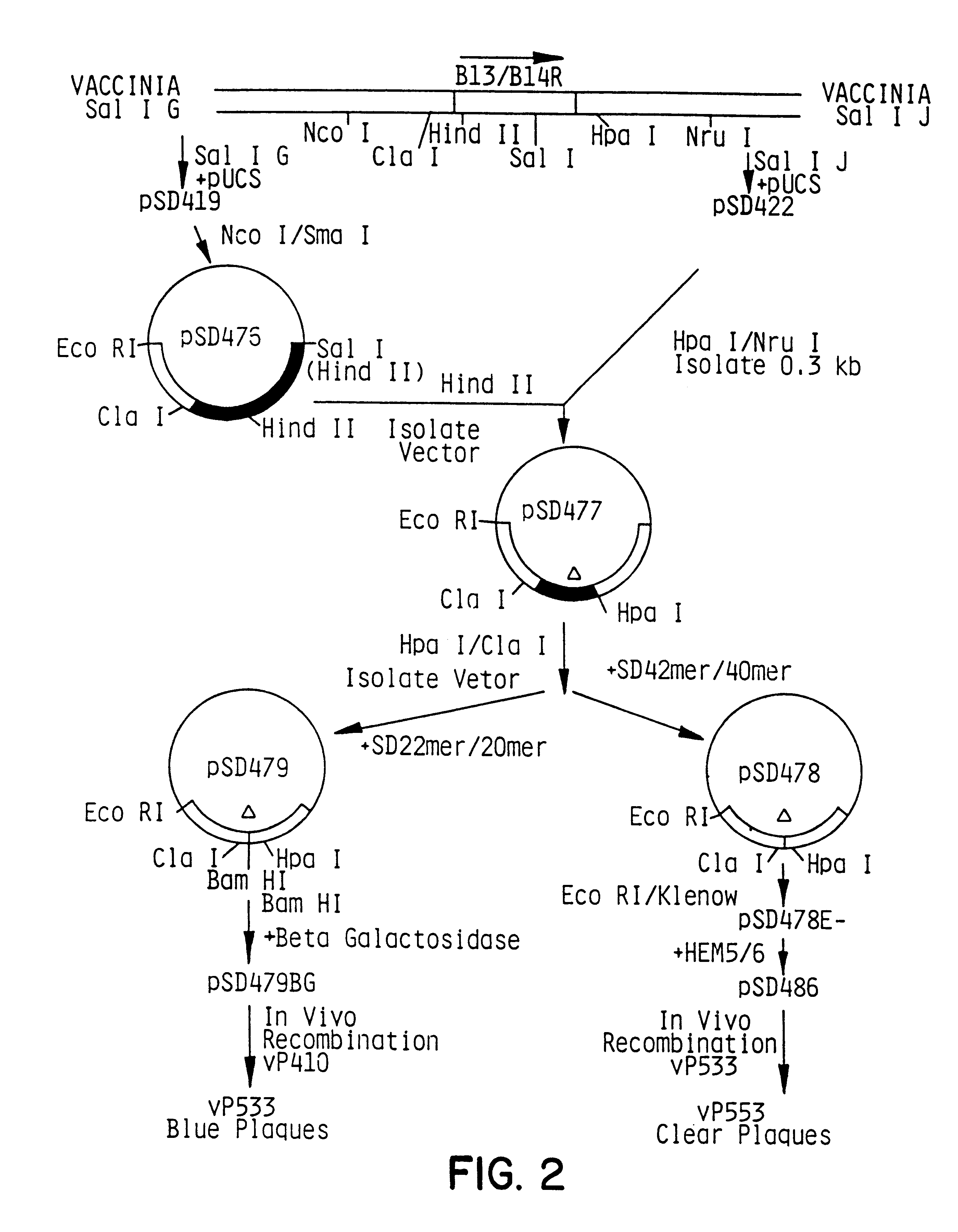
Recombinant poxvirus-cytomegalovirus compositions and uses
InactiveUS6267965B1Enhanced securityImprove securitySugar derivativesPeptide/protein ingredientsDna encodingAntigen
Attenuated recombinant viruses containing DNA encoding an HCMV antigen, as well as methods and compositions employing the viruses, expression products therefrom, and antibodies generated from the viruses or expression products, are disclosed and claimed. The recombinant viruses can be NYVAC or ALVAC recombinant viruses. The recombinant viruses and gene products therefrom and antibodies generated by the viruses and gene products have several preventive, therapeutic and diagnostic uses. The DNA of the recombinant viruses can be used as probes or for generating PCR primers.
Owner:VIROGENETICS
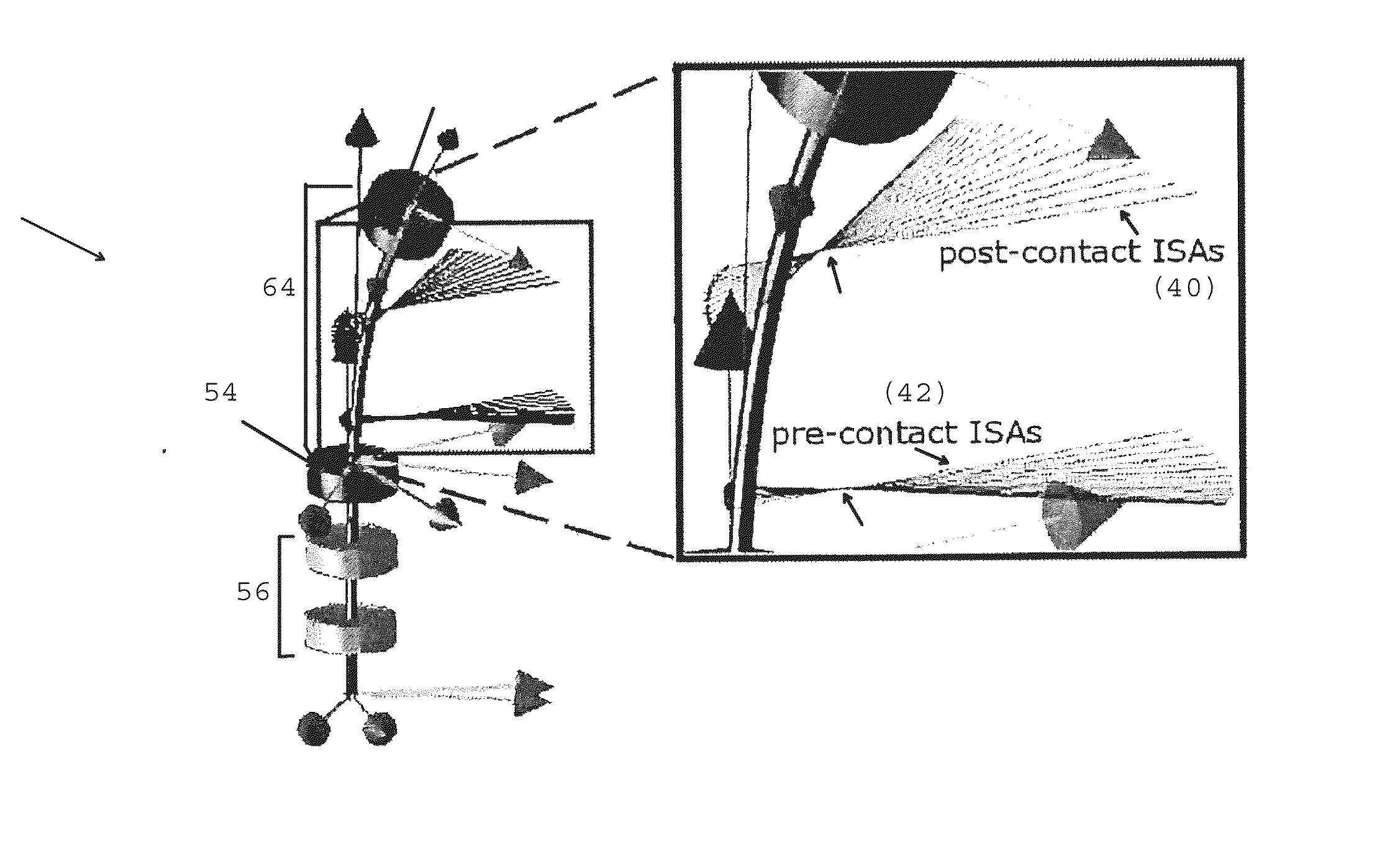
Method and system for contact detection and contact localization along continuum robots
ActiveUS20130300537A1Enhanced securityImprove securityProgramme-controlled manipulatorDiagnosticsRobotic systemsEngineering
A robotic system and methods for manipulation of multi-segment continuum robots. The methods relate to contact detection and estimation of contact location along a multi-segment continuum robot.
Owner:VANDERBILT UNIV
Personalized conference call system and method
InactiveUS20080013706A1Enhanced securityImprove securityInterconnection arrangementsSpecial service for subscribersRetargetingComputer science
An enhancement for an electronic calendar provides a single call-in number and, preferably a pass code established for a user / participant in any and all conference call(s) in which use of the invention is authorized by an owner / caller initiating a conference call. The call-in number accesses the computer corresponding to the user / participant and is redirected to the conference call using information which is stored in memory separate from the electronic calendar and thus not accessible therefrom.
Owner:IBM CORP
Methods and Systems for Electronic Payment for Parking using Autonomous Position Sensing
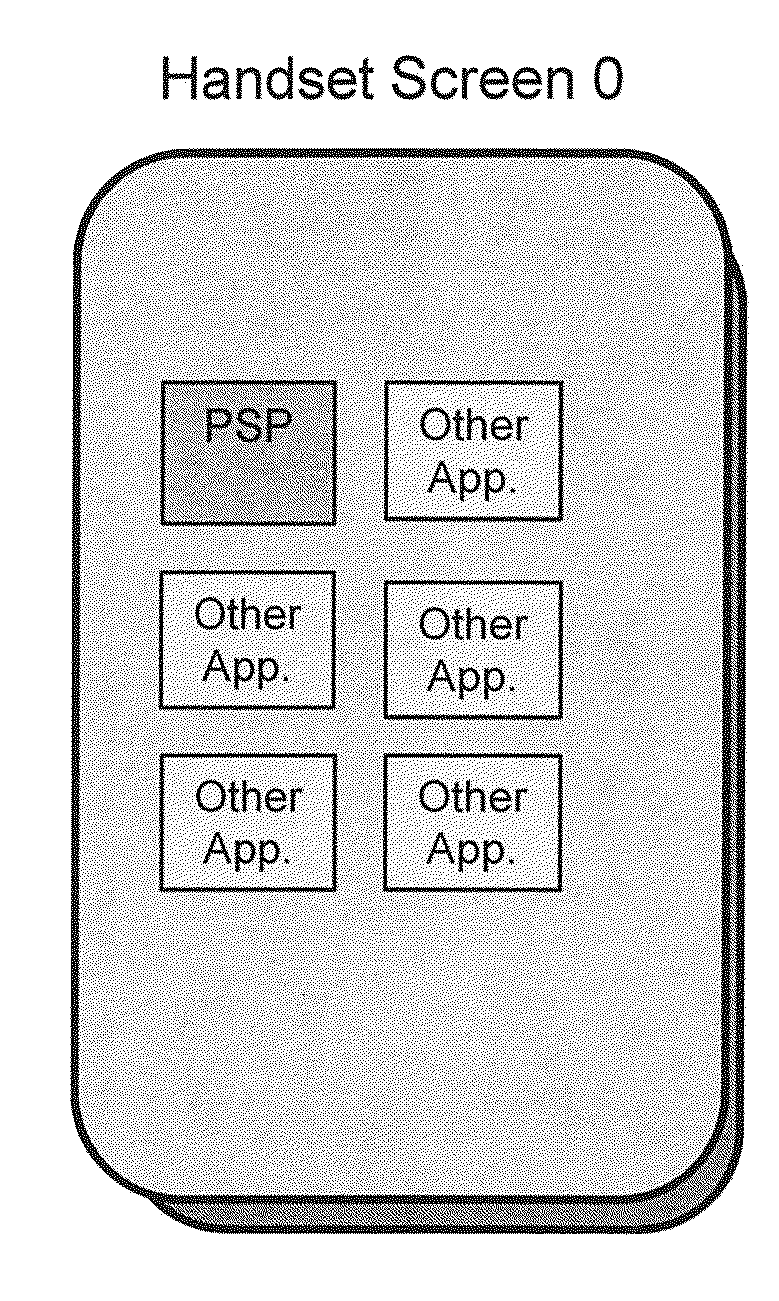
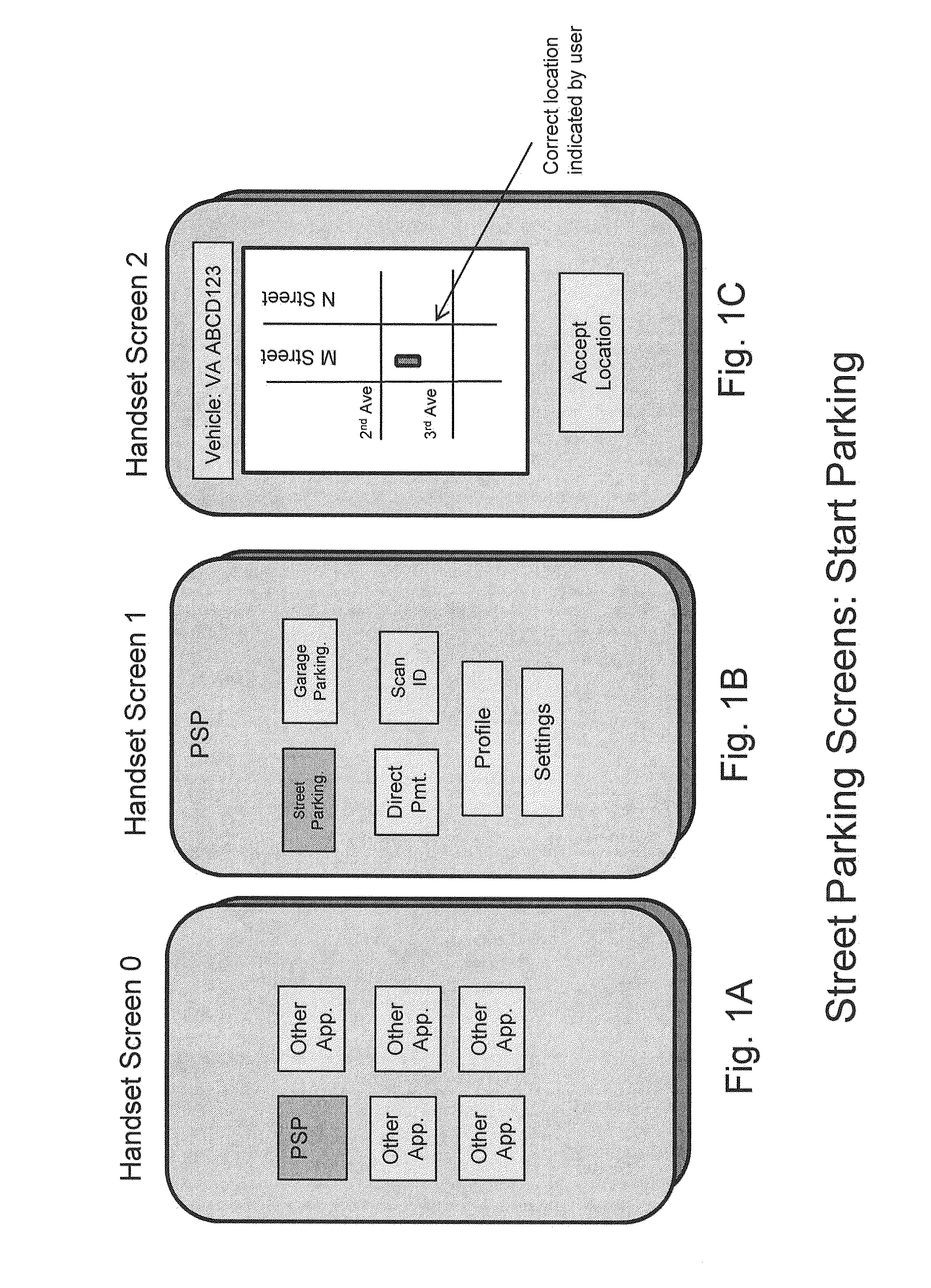
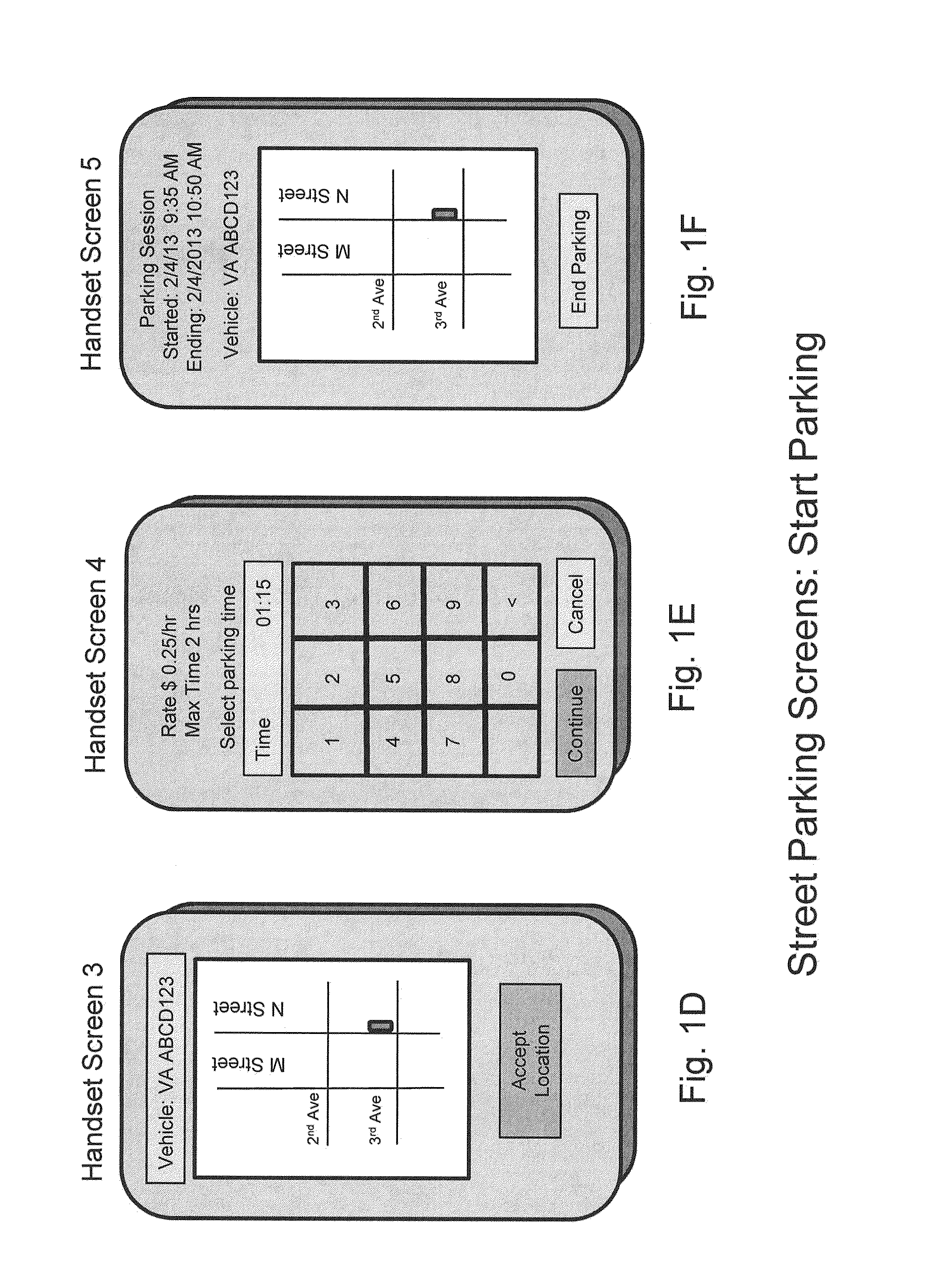
ActiveUS20130282448A1Enhanced securityLow accuracyTicket-issuing apparatusIndication of parksing free spacesHandsetEnforcement
A method / system of wireless payment of parking fees for a vehicle, applicable to both open street and closed garage parking, wherein the user and checker experiences are enhanced relative to the prior art by a number of means, including: autonomous sensing of the user's / vehicle's location and allowing the user to correct the indicated location if required; enabling a handset to automatically sense the ID of the vehicle in which it is located; enabling rapid and facile enforcement by providing the Checker with information about the location, parking session status and other attributes of parked vehicles and displaying the information on a portable terminal in a manner facilitating rapid validation; and further facilitating the identification of vehicles with expired sessions by a method / system of RF interrogation involving RF tags located in / on the vehicles and the checking terminal querying the RF tags.
Owner:TRANSPARENT WIRELESS SYST
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com