Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
78 results about "DNS hijacking" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
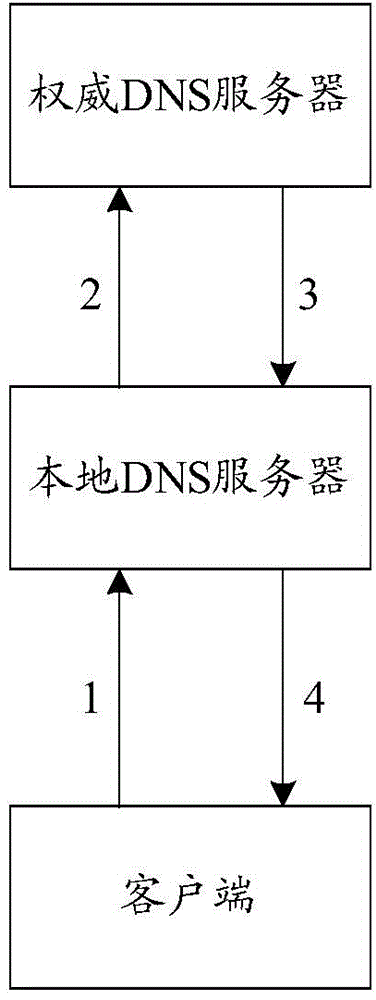
DNS hijacking, DNS poisoning, or DNS redirection is the practice of subverting the resolution of Domain Name System (DNS) queries. This can be achieved by malware that overrides a computer's TCP/IP configuration to point at a rogue DNS server under the control of an attacker, or through modifying the behaviour of a trusted DNS server so that it does not comply with internet standards.
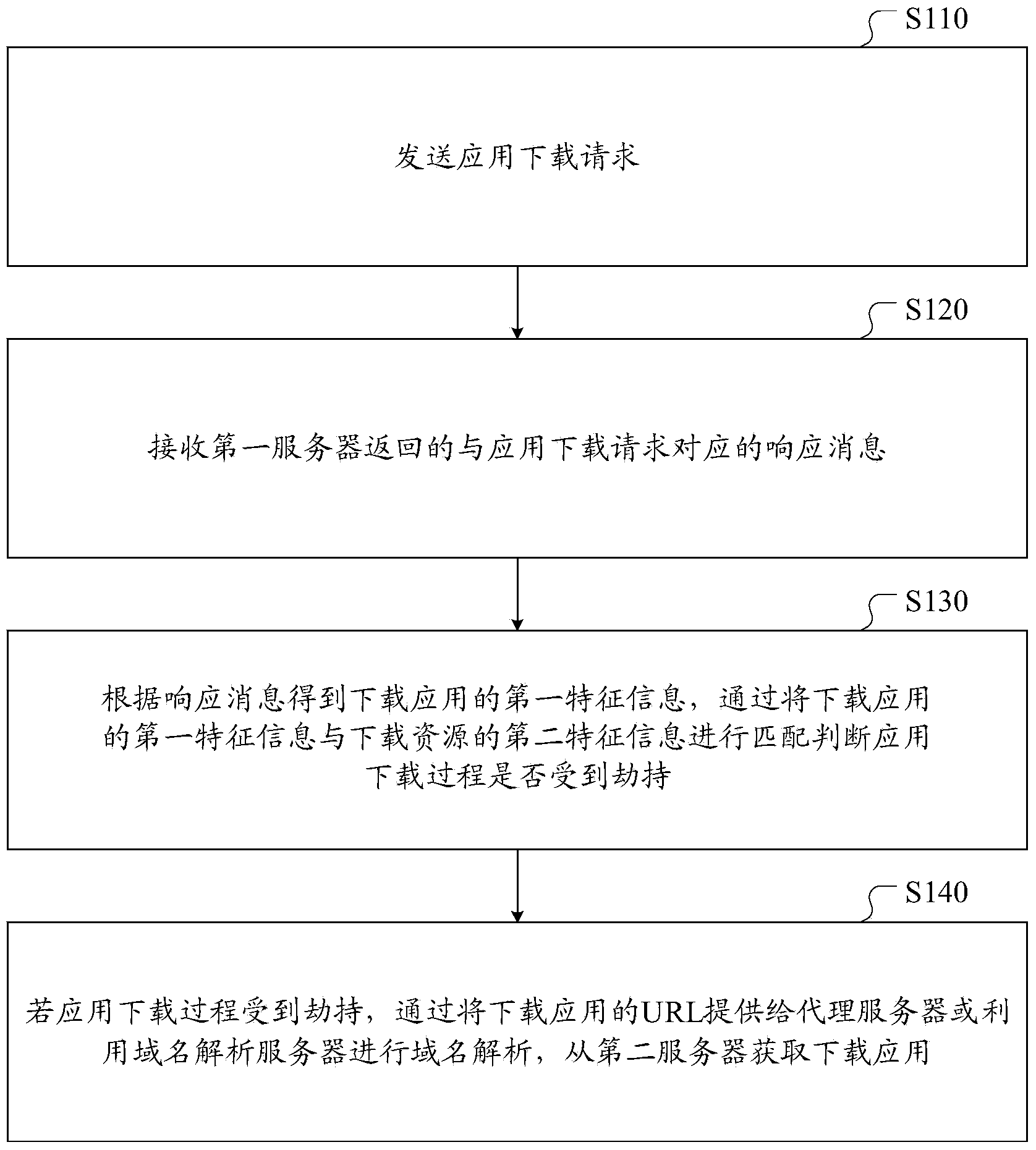
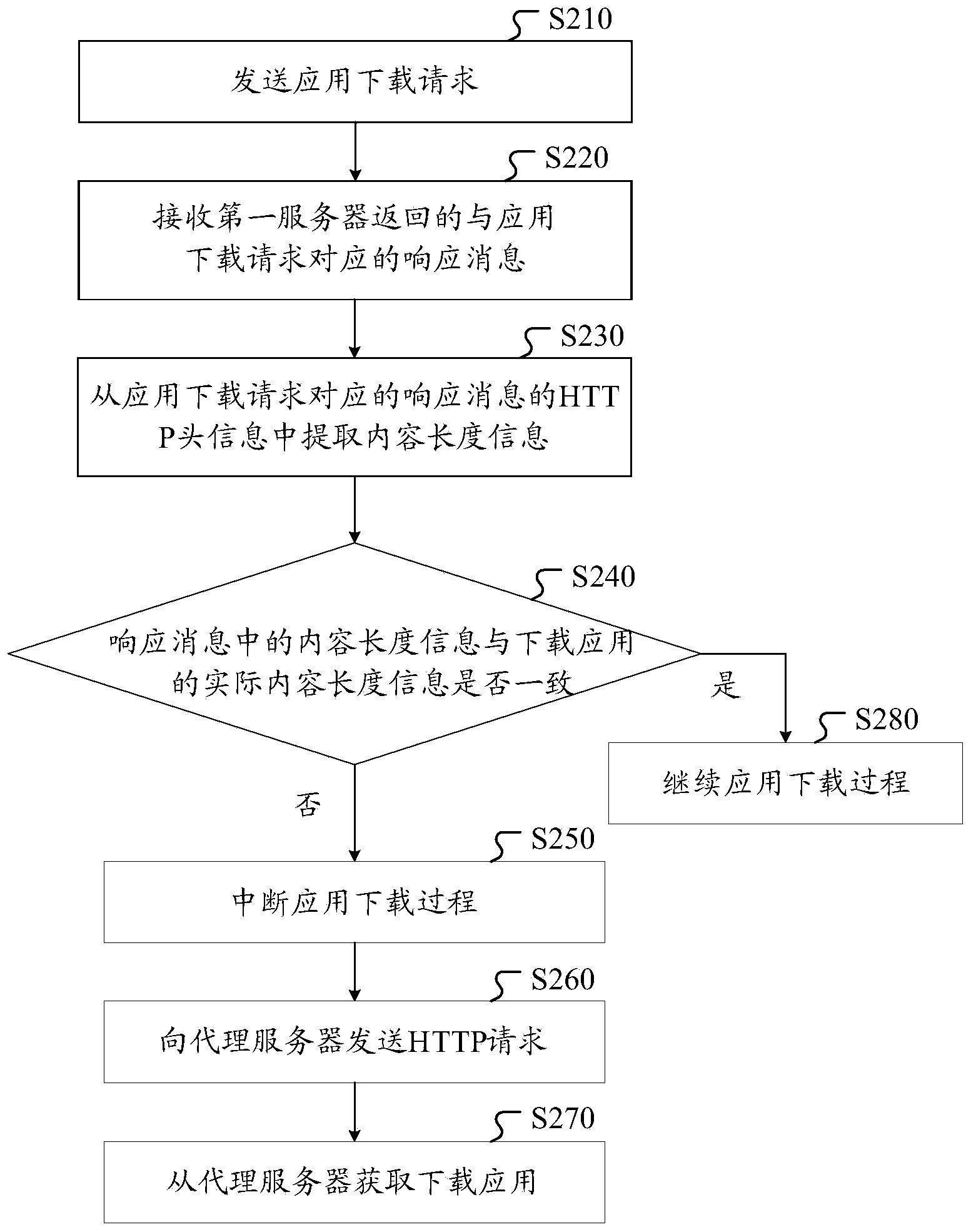
Method, device and system for preventing DNS hijack during application download
The invention discloses a method, device and system for preventing DNS hijack during application download. The method comprises the following steps: sending an application download request; receiving a response message returned by a first server and corresponding to the application download request; according to the response message, obtaining first feature information for downloading the application, matching the first feature information with second feature information for downloading the application and obtained from a second server providing the application in advance, and judging whether the application download process is hijacked; if yes, providing the URL for downloading the application for a proxy server or utilizing a DNS server to perform domain name resolution, and obtaining the download application from the second server. According to the method, the problems in the prior art that the application download and installation fail, a data package is replaced, the model change fails and the like caused by network hijack of an operator are solved, and the time, traffic and cost of a user are saved.
Owner:三六零数字安全科技集团有限公司
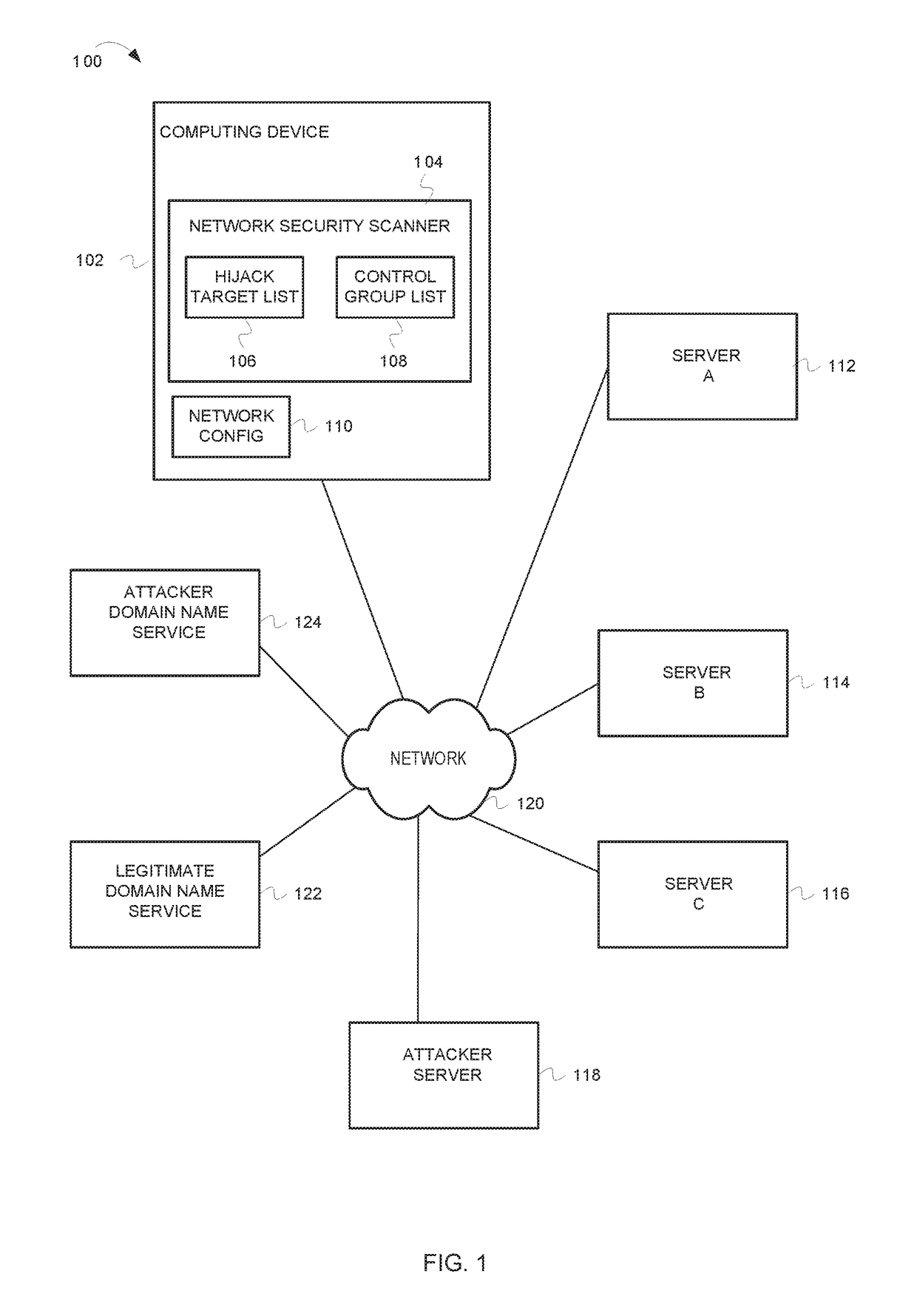
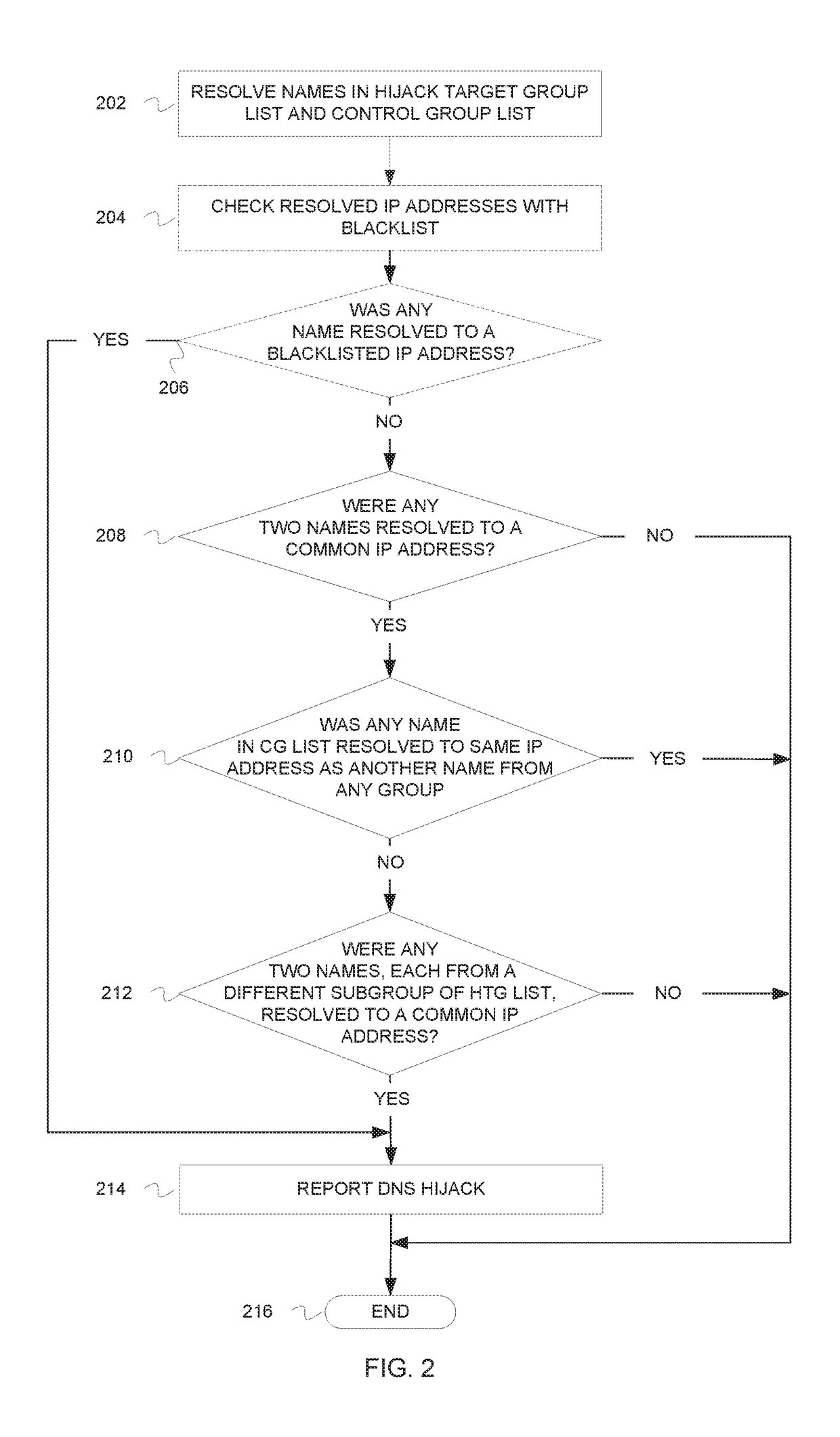
Detection of domain name system hijacking
Detecting a Domain Name Service (DNS) hijacking includes resolving names in a hijack target group list to their respective Internet Protocol (IP) addresses. In response to determining that two names in the hijack target group list resolved to a common IP address, a determination is made whether a legitimate reason exists for the two names in the hijack target group list to resolve to the common IP address. In response to determining that a legitimate reason does not exist for the two names in the hijack target group list to resolve to a common IP address, a DNS hijacking is indicated.
Owner:AVAST SOFTWARE
Method and system of implementing HTTP (Hyper Text Transport Protocol) cache
The invention discloses a method and a system of implementing an HTTP (Hyper Text Transport Protocol) cache. The system comprises a user terminal, a Local DNS (Domain Name Server), a DPI (Data Processing Installation) system, a DNS redirect server, an ICP (Internet Content Provider) DNS server and a cache server, wherein through starting using and monitoring a timer, if only a DNS resolution result fed back by the DNS redirect server is guaranteed to be received in a valid time bucket of T2-T1, a user can be guaranteed to use the cache, thereby avoiding the problems that the existing DNS hijack scheme replies the DNS resolution result more early in the ICP DNS server than in the DNS redirect server, and then the cache is unable to serve the user of a home network, and through TTL (Time To Live) advanced iterative query and cache refresh mechanisms, effective duration of the resolution result of the cache in the Local DNS server is implemented, the problem that the user needs to wait DNS query in a DNS query process to generate time delay is avoided, user perception is greatly improved and system efficiency is improved.
Owner:CHINA MOBILE GRP BEIJING
Credible website identity installation and identification method
ActiveCN102611707ASolve the installationSolve security identification problems such as the inability to prevent dns hijackingUser identity/authority verificationData switching networksThird partyDNS hijacking
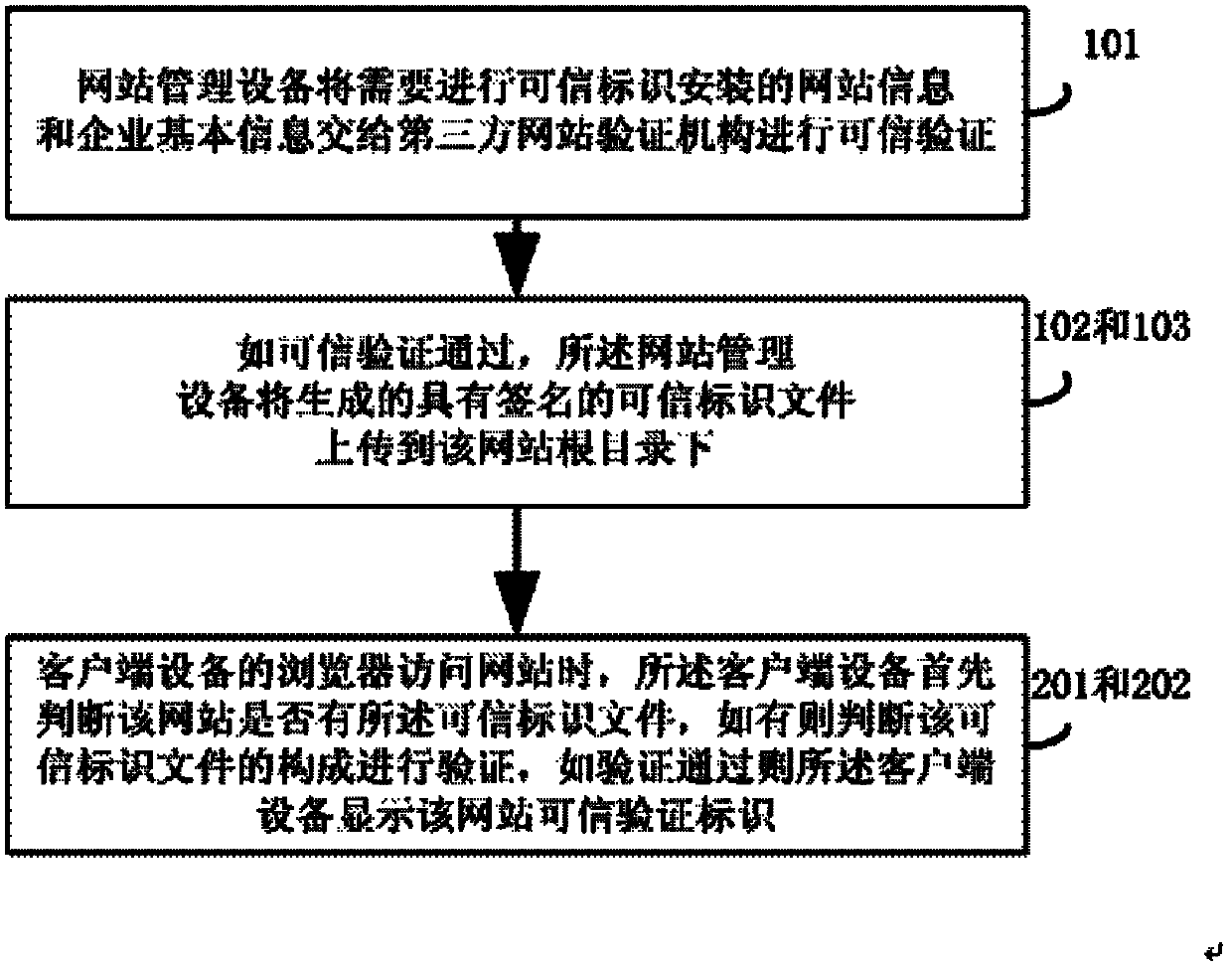
The invention discloses a credible website identity installation and identification method which comprises the following steps that: website management equipment sends the information of a website on which a credible identity needs to be installed and the basic information of an enterprise to a third party website authentication institution to authenticate the credibility; if the credibility authentication is passed, the website management equipment uploads a generated credible identity document with a signature to a root directory of the website or to a website server to configure; when the browser of client terminal equipment accesses a website, the client terminal equipment fist judges whether the website has the credible identification document or not; if yes, the composition of the credible identity document is judged and authorization is carried out; and if the authentication is passed, the credible authentication identity of the website is displayed through the client terminal equipment. The invention can solve the installation problem of the credible identities of existing websites and the safety identification problems that domain name system (dns) hijacking cannot be prevented and the like, and provides the method which is simpler, safer, easier to identify and has better compatibility.
Owner:北龙中网(北京)科技有限责任公司
Secure and reliable network access method for hardware device
ActiveCN108933757AReduce overheadAddress riskEncryption apparatus with shift registers/memoriesCommunications securityAccess method
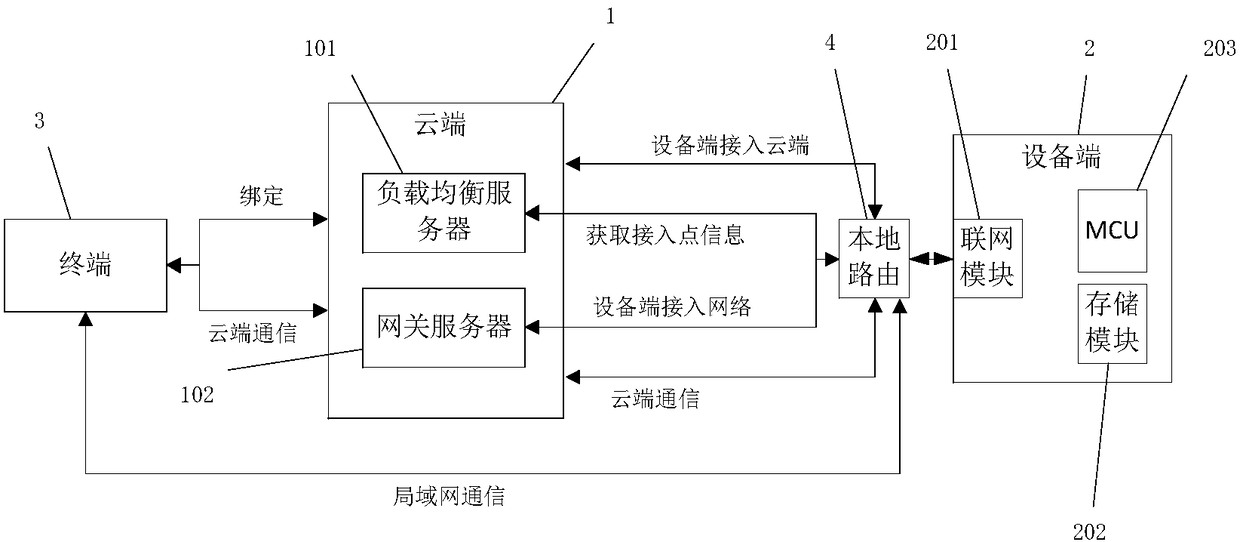
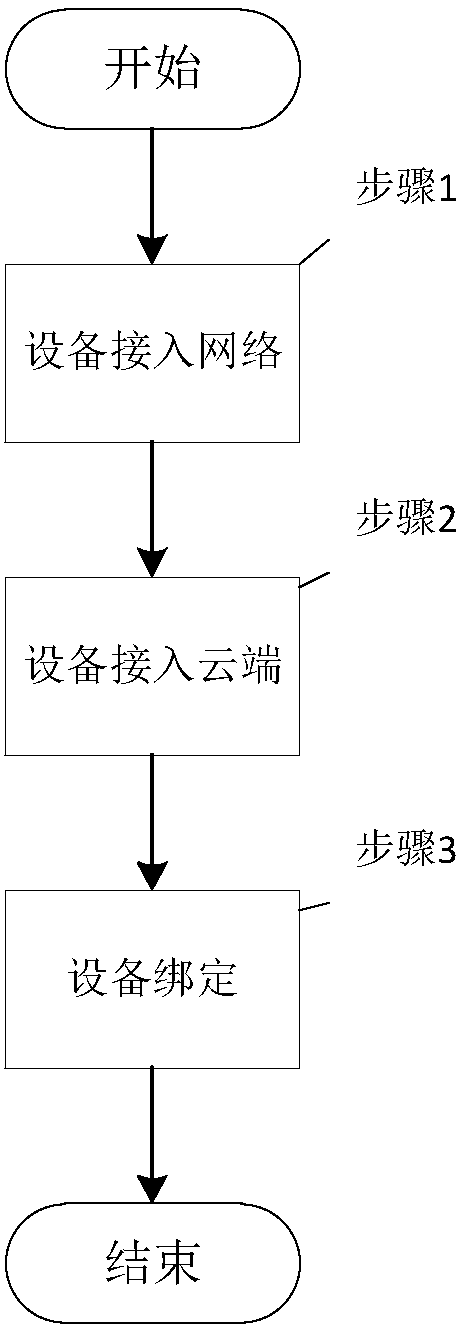
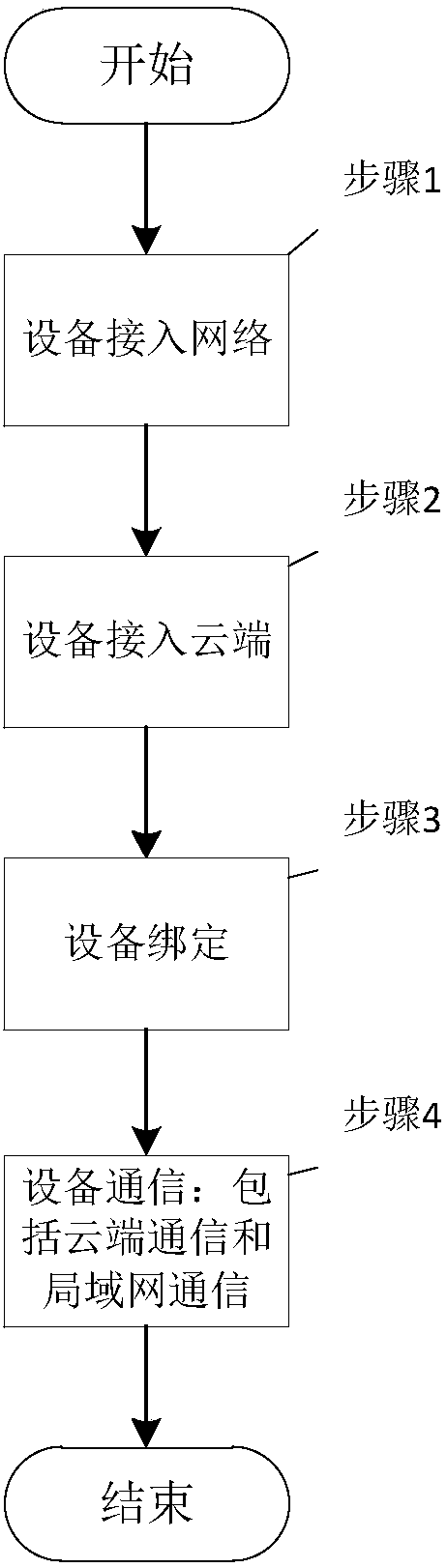
The invention discloses a secure and reliable network access method for a hardware device. The method includes the following steps: a device end networking module and a cloud end are connected to a network after being subjected to encryption two-way authentication; a dynamic encryption secret key is obtained for data communication security device binding, and uplink and downlink communication canbe realized. The method disclosed in the invention helps solve a problem of security risks such as device camouflage, cloud end DNS hijacking and the like in network accessing processes, security of an Internet of Things communication protocol and validity authentication of the device and the cloud end can be ensured, and reliable data transmission capacity can be provided for cloud end communication and local area network communication. The method is suitable for a WIFI module, a wired module, a GPRS module, a Linux system-based device, an Android system-based device, networking devices basedon Windows systems, and the like.
Owner:北京君泊网络科技有限责任公司
Network access method and system based on DNS
The invention provides a network access method and system based on a DNS. The network access method comprises the steps of pre-storing domain name configuration files recording domain name information in the server; downloading the domain name configuration files from the server before initiating a network access request; initiating the network access request according to the domain name information recorded by the domain name configuration files. In the technical scheme, a multi-domain-name information mode is adopted for access, when a front end executes the network access request, the network access request is initiated by utilizing multiple domain name information recorded in the domain name configuration files downloaded from the server, and the influence brought by DNS hijacking or breakdown can be effectively reduced. In addition, load fluctuation and snow slide phenomena of a default IP server during accessing in a default IP information mode can also decreased, and the success rate of service access can be improved.
Owner:成都酷狗创业孵化器管理有限公司
Installation and identification method of website credible identity based on domain name system technology
ActiveCN102629923ASolve security identification problems such as inability to identify DNS hijackingEasy to identifyTransmissionThird partyDomain name
The invention discloses an installation and identification method of a website credible identity based on the domain name system technology. The installation is realized by the steps: website management equipment sends the website information and enterprise essential information requiring the credible identity installation to a third party website verifying mechanism to carry out credibility verification; if passing the credibility verification, the generated credible identity file with signature is sent to the website management equipment; the website management equipment converts the host name part of which the domain name is verified into a credible query domain name of which the domain name is verified by using a hashing algorithm code converting manner; and the credible identity file is compressed and grouped by the third party website verifying mechanism, and is converted into at least one text character string to be added to the record of the credible query domain name. According to the invention, the installation problem of the traditional website credible identity and safety identification problems that the DNS (domain name system) hijack and the like cannot be identified are solved; and the method is simpler, safer, easier to distinguish and better in compatibility.
Owner:北龙中网(北京)科技有限责任公司
Domain name analysis method and device, storage medium and electronic device
ActiveCN108270882AFix technical issues with less securityImprove securityTransmissionDomain nameDNS hijacking
The invention discloses a domain name analysis method, a domain name analysis device, a storage medium and an electronic device. The method comprises the steps of acquiring a first domain name requested to be accessed by a first client; acquiring a first address of the first server, wherein the first server is used for analyzing a target address corresponding to the first domain name, the first address is configured by a second client, and the first client and the second client are installed on a same terminal; sending a first request to the first server via the first address of the first server, wherein the first request is used for acquiring the target address corresponding to the first domain name requested to be accessed by the first client; and accessing the server to which the targetaddress points via the first client under the condition of receiving the target address returned by the first server. According to the method, device, medium and electronic device provided by the invention, the technical problem that in related technologies, the network security is relatively low due to DNS hijacking is solved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
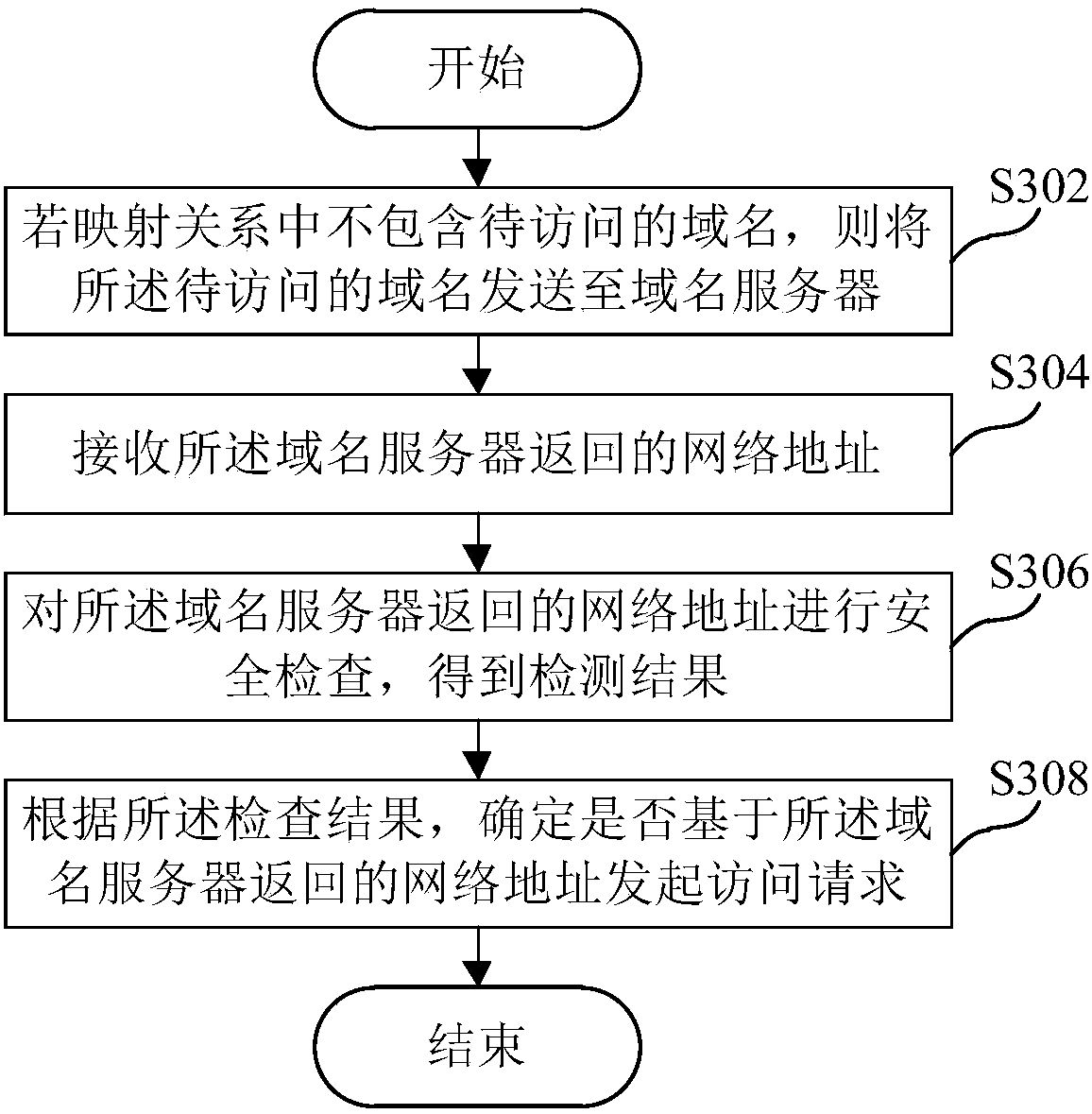
Domain name resolution method and device
The present invention provides a domain name resolution method and device. The method comprises the following steps: determining a domain name to be accessed; obtaining a mapping relationship betweena local domain name and a network address; determining, according to the domain name to be accessed and the mapping relationship, a target address to be accessed; and initiating an access request based on the target address. The technical scheme of the invention can avoid the problem of DNS hijacking, can reduce the delay of the network request and effectively improves the network performance.
Owner:ELONGNET INFORMATION TECH (BEIJING) CO LTD
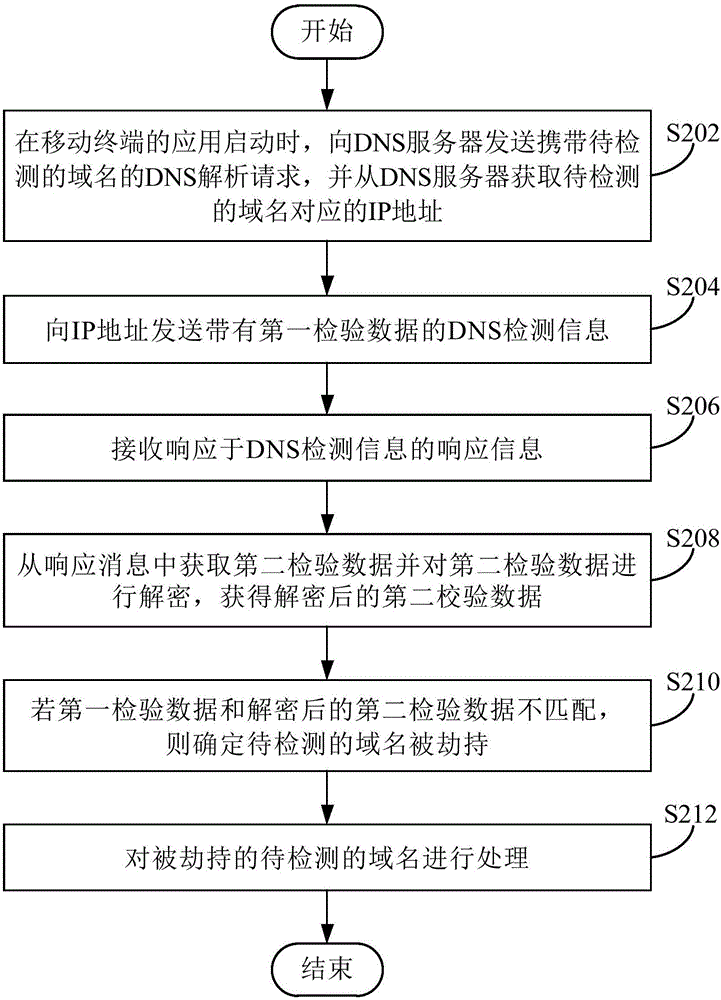
Detection method and device for DNS hijacking as well as mobile terminal
Embodiments of the invention provide a detection method and device for DNS hijacking as well as a mobile terminal. The detection method for DNS hijacking comprises the following steps of obtaining an IP address corresponding to a to-be-detected domain name from a DNS server, wherein the to-be-detected domain name is a domain name associated with an application of the mobile terminal; sending DNS detection information to the IP address, wherein the DNS detection information carries first inspection data; receiving a response message which responds to the DNS detection information and obtaining second inspection data from the response message; and detecting whether the to-be-detected domain name is hijacked according to the first inspection data and the second inspection data. Through adoption of the technical scheme in the embodiments of the invention, the DNS hijacking can be detected accurately to be convenient for subsequently carrying out DNS hijacking prevention processing, so that the security of the application of the mobile terminal for accessing the network is guaranteed, and the DNS hijacking prevention is realized based on the mobile terminal.
Owner:深圳掌阅动漫科技有限公司
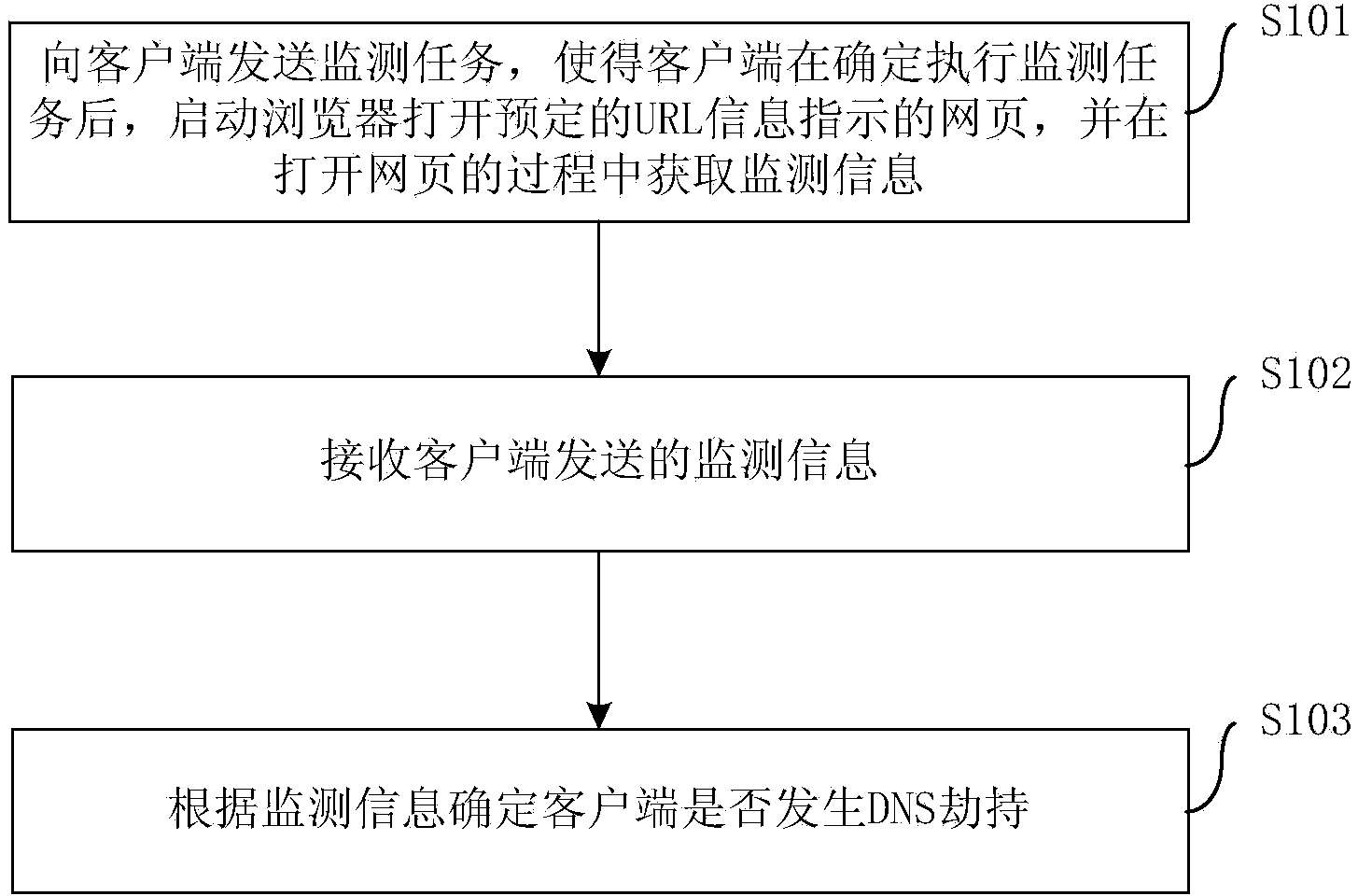
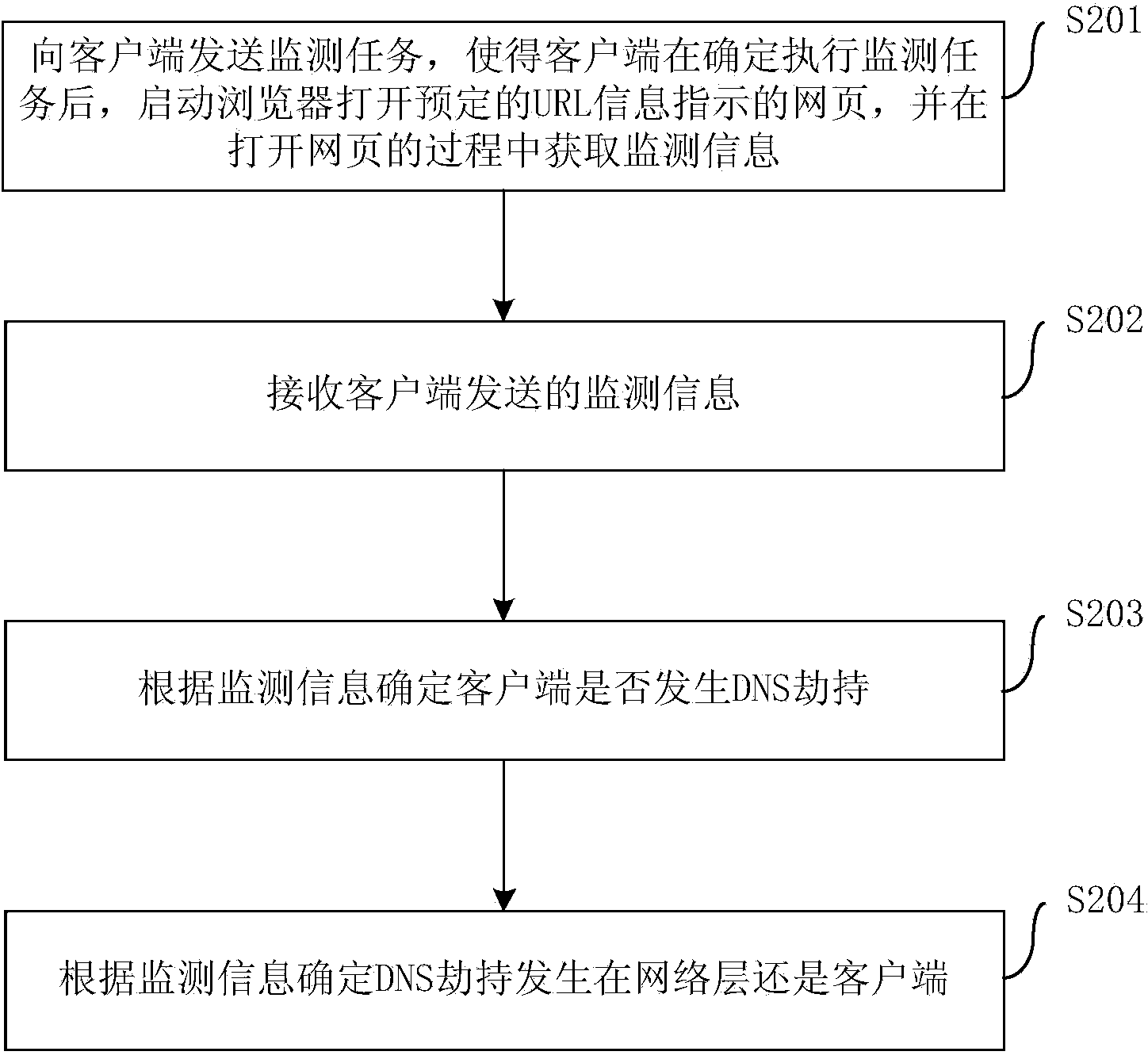
DNS hijack monitoring method and device
ActiveCN103905273AReproduce in timeEfficient reproductionData switching networksDNS hijackingClient-side
The invention provides a DNS hijack monitoring method and device. The method comprises the steps that a monitoring task is sent to a client side, so that after determining the monitoring task, the client side starts a browser to open a predetermined webpage which is indicated by URL information and obtains monitoring information in the webpage opening process; the monitoring information sent by the client side is received; if the client side has DNS hijack is determined according to the monitoring information. The method can actively find out the DNS hijack problem in time, effectively enable corresponding DNS hijack to reoccur in time, lower labor cost, and improve efficiency.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Method and device for pushing control data
InactiveCN105657072AReduce lossesReduced instances of geographical information discrepanciesAdvertisementsTransmissionDomain nameDNS hijacking
An embodiment of the invention discloses a method and a device for pushing control data. The method and the device are applied to a control server. The method includes steps of applying for an auxiliary URL (uniform resource locator) for directional advertisements for target regions; receiving first requests for accessing the corresponding auxiliary URL for each advertisement request; extracting second source IP (internet protocol) addresses according to the first requests; establishing corresponding relations between first source IP addresses and the second source IP addresses; determining IP addresses of the directional advertisements for the target regions according to the multiple established corresponding relations; transmitting the determined IP addresses to media servers so as to stop the media servers from transmitting the directional advertisements for the target regions to advertisement front ends corresponding to the determined IP addresses. The first requests are transmitted by the advertisement front ends. The second source IP addresses correspond to the advertisement front ends. The directional advertisements at the determined IP addresses need to be stopped from being released. The method and the device have the advantages that regional information difference due to strategy routes on basis of domain names and DNS (domain name server) hijacking can be reduced, and accordingly loss of media can be decreased.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
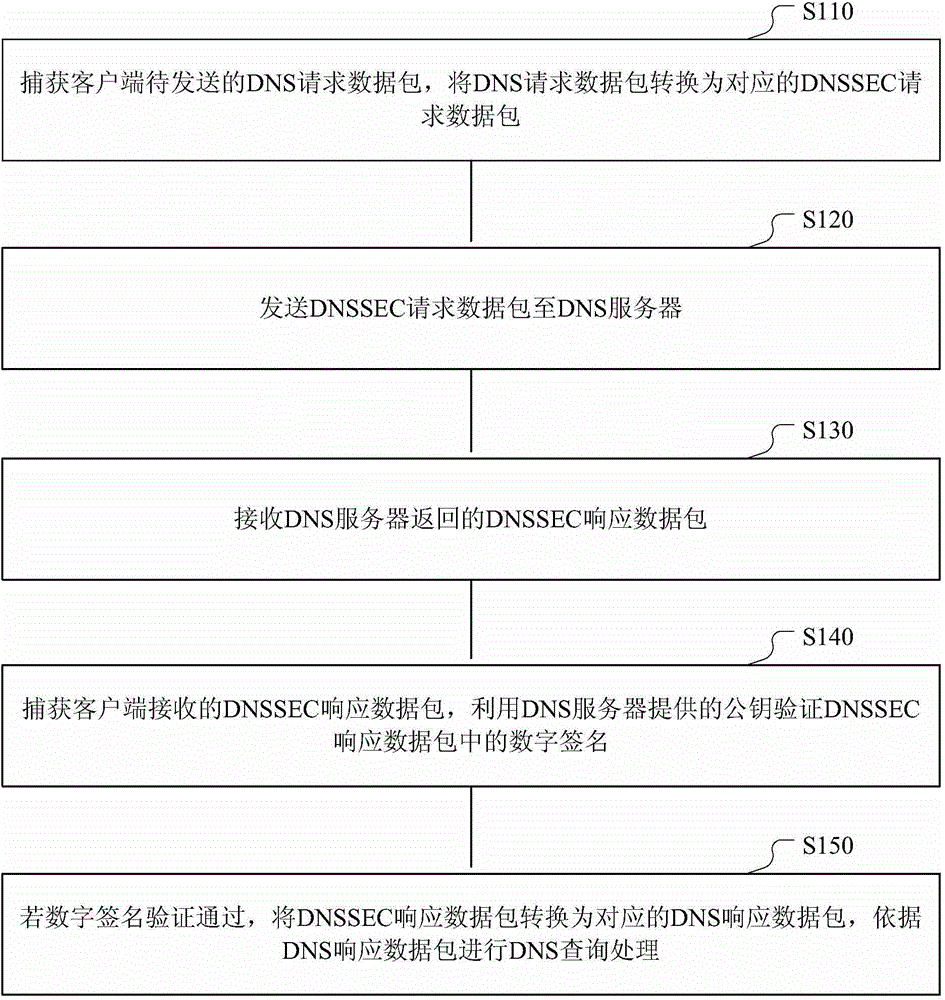
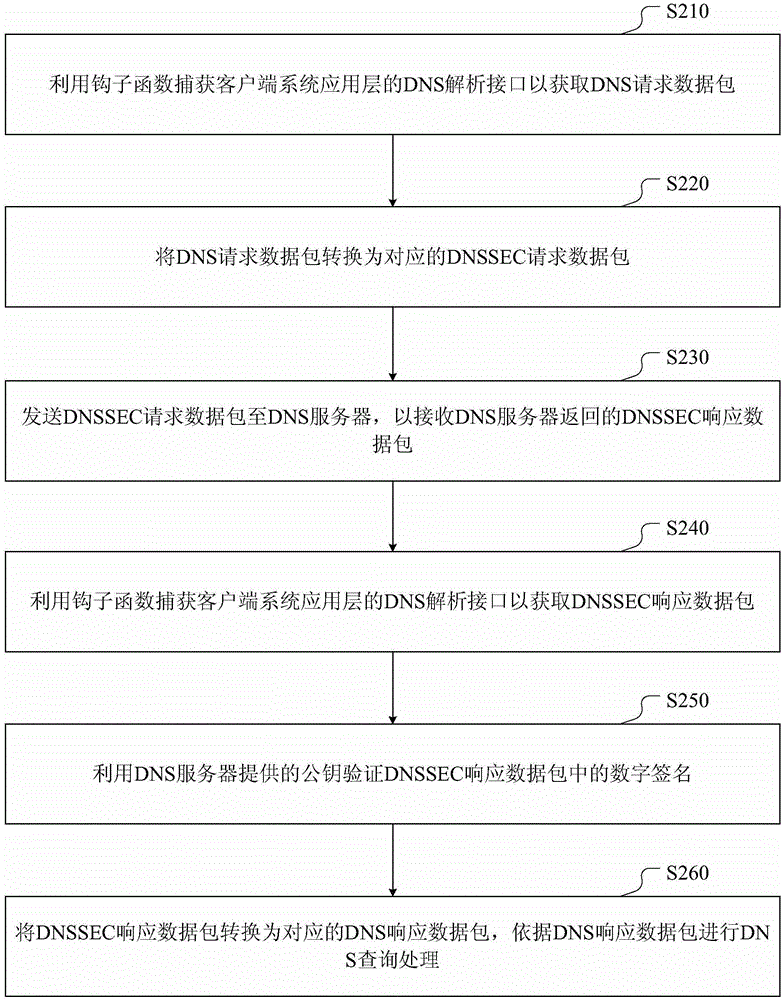
DNS (Domain Name Server) safety querying method and device
The invention discloses a DNS (Domain Name Server) safety querying method and device. The method comprises the steps of capturing a DNS request data packet to be sent by a client; converting the DNS request data packet into a corresponding DNSSEC (Domain Name System Security Extensions) request data packet; sending the DNSSEC request data to a DNS server to receive a DNSSEC response data packet returned by the DNS server; capturing the DNSSEC response data packet received by the client; verifying to a digital signature in the DNSSEC response data packet through a public key provided by the DNS server; if passing the digital signature passes the verification, converting the DNSSEC response data packet into the corresponding DNS response data packet; performing DNS querying processing according to the DNS response data packet. According to the scheme, the method has the advantages that the DNSSEC verification process is applied to the client, and a trust relationship between the client and the closest DNS server is configured, so as to form a complete trust chain with the DNS servers at each level; the truth and integrity of the data can be verified through the client, and thus the problems of DNS hijacking and cheating can be further avoided.
Owner:三六零数字安全科技集团有限公司
Network selection method, device and system
InactiveCN104954431AExcellent connection speedSolve the problem of loadingTransmissionIp addressDNS hijacking
The invention discloses a network selection method, device and system. The method comprises that an IP address list which includes multiple IP addresses is obtained from a server; the speed of each IP address in the IP address list is measured to obtain a speed measurement result; and an IP address used for data access is selected from the IP address list according to the speed measurement results. According to the network selection method, device and system, the problem that data cannot be loaded or is loaded slowly due to DNS hijack or access across the network segment can be effectively solved, it is ensured that the IP address of the optimal / preferable connection speed can be used for data access, and user experience is improved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Method for detecting previous connection of network based on DNS hijacking technology
The invention discloses a method for detecting a previous connection of a network based on a DNS hijacking technology. The method comprises the following steps that a gateway hardware is arranged on a bypass on a gateway; the gateway hardware carries out monitoring and mirroring on data on the gateway and analyzes the data after mirroring through the gateway hardware; once data flow including an HTTP protocol is discovered, the gateway hardware carries out hijacking; the gateway hardware forges a corresponding HTTP response packet for a HTTP protocol request and sends the HTTP response packet to a terminal device requesting an Internet connection; as long as the terminal device runs the HTTP response packet, the gateway hardware receives a DNS resolution request and responds, and returns an IP address on an appointed cheat server; when the terminal device initializes a request of the IP address, the cheat server can obtain and record Internet access data left by the terminal device; and the cheat server can judge whether the terminal device is connected previously or a previously connected time node of the terminal device through analysis of history access data. Through adoption of a passive monitoring way, the accuracy of detection can be extremely improved.
Owner:ZHEJIANG YUANWANG INFORMATION CO LTD
DNS hijacking detection method and device
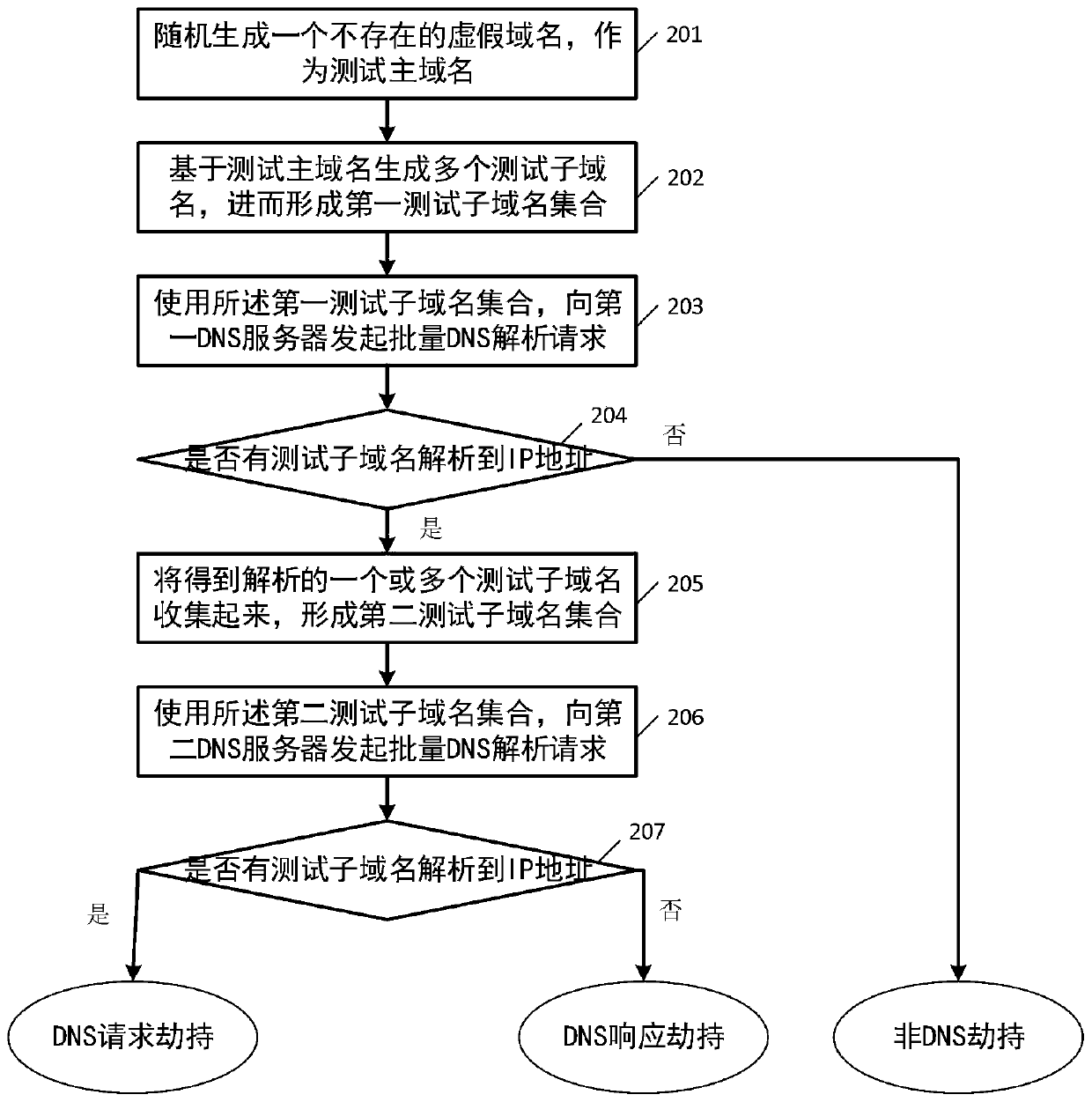
The invention relates to the technical field of network safety, in particular to a DNS hijacking detection method and device. The method comprises the following steps: randomly generating an inexistent false domain name as a test main domain name; generating a plurality of test sub-domain names based on the test main domain name so as to form a first test sub-domain name set; initiating a batch DNS resolution request to a first DNS server by using the first test sub-domain name set, wherein the first DNS server is a real DNS server; checking a DNS response result, and judging whether DNS hijacking exists or not according to whether each test sub-domain name in the first test sub-domain name set is analyzed or not; If the test sub-domain name is analyzed, determining that the DNS hijackingexists, and determining the keywords of the DNS hijacking. According to the method, batch detection is carried out by using a large number of false sub-domain names through active DNS request detection, so that whether DNS hijacking exists or not can be quickly and accurately detected, and matching keywords of DNS hijacking can be identified.
Owner:WUHAN GREENET INFORMATION SERVICE
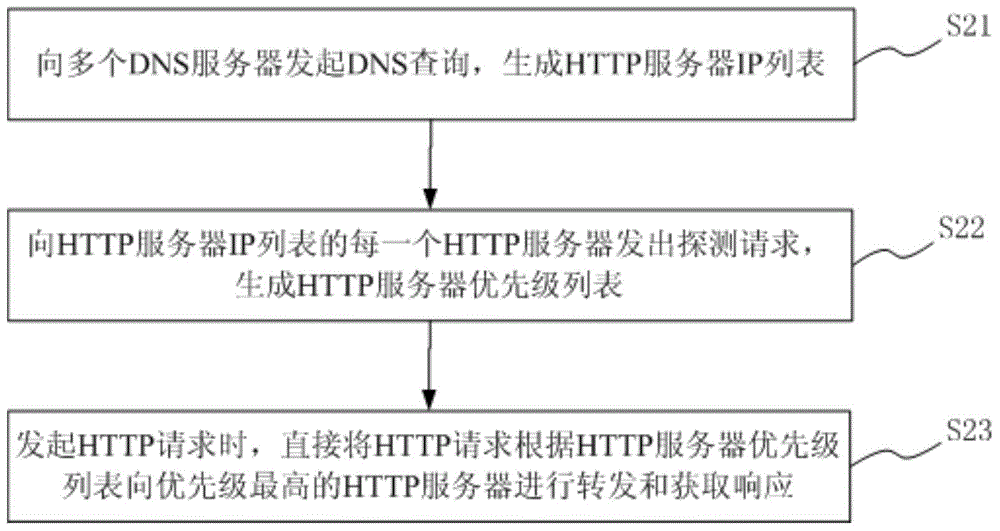
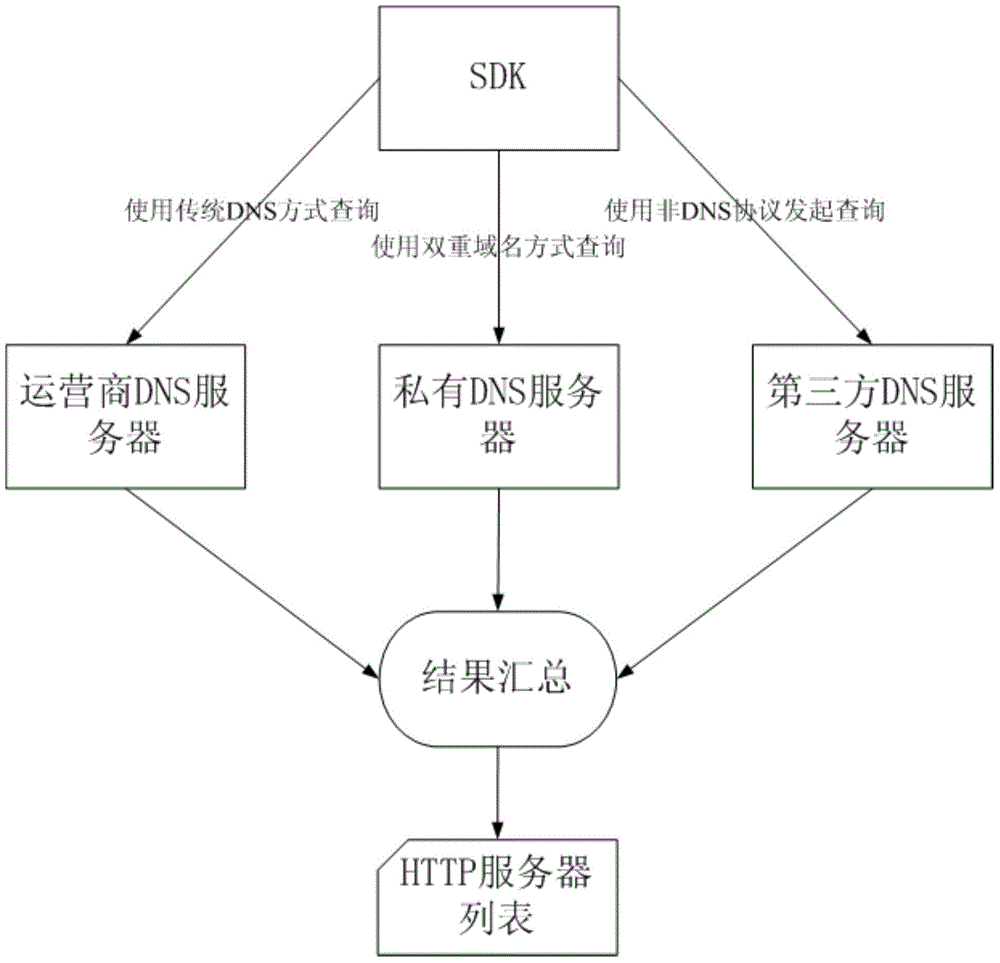
HTTP access availability optimization method and mobile intelligent terminal
The present invention provides an HTTP access availability optimization method and a mobile intelligent terminal. The mobile intelligent terminal comprises a SDK module. The HTTP access availability optimization method comprises: initiating DNS query for a plurality of DNS servers, and generating an HTTP server IP list; sending detection requests for each HTTP server of the HTTP server IP list through the mobile intelligent terminal, and generating an HTTP server priority list according to the response time and the response accuracy; when there is provided HTTP requests at the mobile intelligent terminal, directly forwarding the HTTP requests according to the HTTP server priority list to the HTTP server with the highest priority and obtaining responses through the mobile intelligent terminal; and when the abnormities of forwarding and response occur, the fault switch of the HTTP server is performed according to the priority rating. According the invention, the DNS access is optimized, the DNS hijacking and pollution are avoided, and the optimization cost is reduced.
Owner:CHINANETCENT TECH
DNS hijacking detection method
The invention discloses a DNS (Domain Name System) hijacking detection method. The DNS hijacking detection method includes the following steps: the step 1: issuing a standard DNS lookup for an IP, wherein the domain name of the IP does not enable DNS service lookup support abroad; and if a returned result IP does not exist, directly deciding that the domain name is not hijacked; and if a returned result IP exists, performing the step 3; the step 2: performing a standard DNS lookup on the domain name in the step 1 on a local DNS server to obtain a result IP returned by the local DNS; and the step 3: comparing the result IP returned by the server which does not enable the DNS service lookup support abroad with the result IP returned by the local, deciding that the domain name is not hijacked if the two result IPs are identical to each other, and deciding that the domain name is hijacked if the two result IPs are not identical to each other. The DNS hijacking detection method does not need maintenance of a hijacked IP list, and can decide whether the domain name is hijacked by means of comparison of the result IPS after analysis of the two domain names, so that the DNS hijacking detection method is more efficient and accurate.
Owner:成都知道创宇信息技术有限公司
Domain name hijacking defense method and device, computer device and storage medium
The invention provides a domain name hijacking defense method. The domain name hijacking defense method comprises the following steps of sending a DNS detection request to a standard DNS server; judging whether the DNS hijacking occurs or not according to a DNS detection response returned by the standard DNS server in response to the DNS detection request; if the DNS hijacking occurs, encrypting the standard DNS query request to obtain an encrypted DNS query request, and sending the encrypted DNS query request to an encrypted DNS server; and converting the encrypted DNS query response returnedby the encrypted DNS server in response to the encrypted DNS query request into a standard DNS query response. The invention further provides a domain name hijacking defense device, a computer deviceand a computer readable storage medium. According to the present invention, the domain name hijacking can be defended, and the network security is improved.
Owner:SHENZHEN ONETHING TECH CO LTD
Method and apparatus for reducing DNS hijacking risk
The invention provides a method and apparatus for reducing a DNS hijacking risk. The method comprises the following steps: sending a dynamic configuration request to a dynamic host configuration protocol DHCP device in a local area network; receiving dynamic configuration information returned by the DHCP device, wherein the dynamic configuration information comprises an internet protocol IP address of user equipment UE; sending the IP address of the UE to a security server; receiving a candidate wide area network DNS server address of a candidate wide area network DNS server, which belongs to the same operator as the UE, is determined by the security server on the basis of the IP address of the UE and is sent by the security server; determining the candidate wide area network DNS server address as a target wide area network DNS server address; switching a dynamic configuration networking state to a static networking state, wherein the main DNS server address of the secure configuration information is the target wide area network DNS server address; and accessing the network based on the secure configuration information.
Owner:BEIJING QIHOO TECH CO LTD
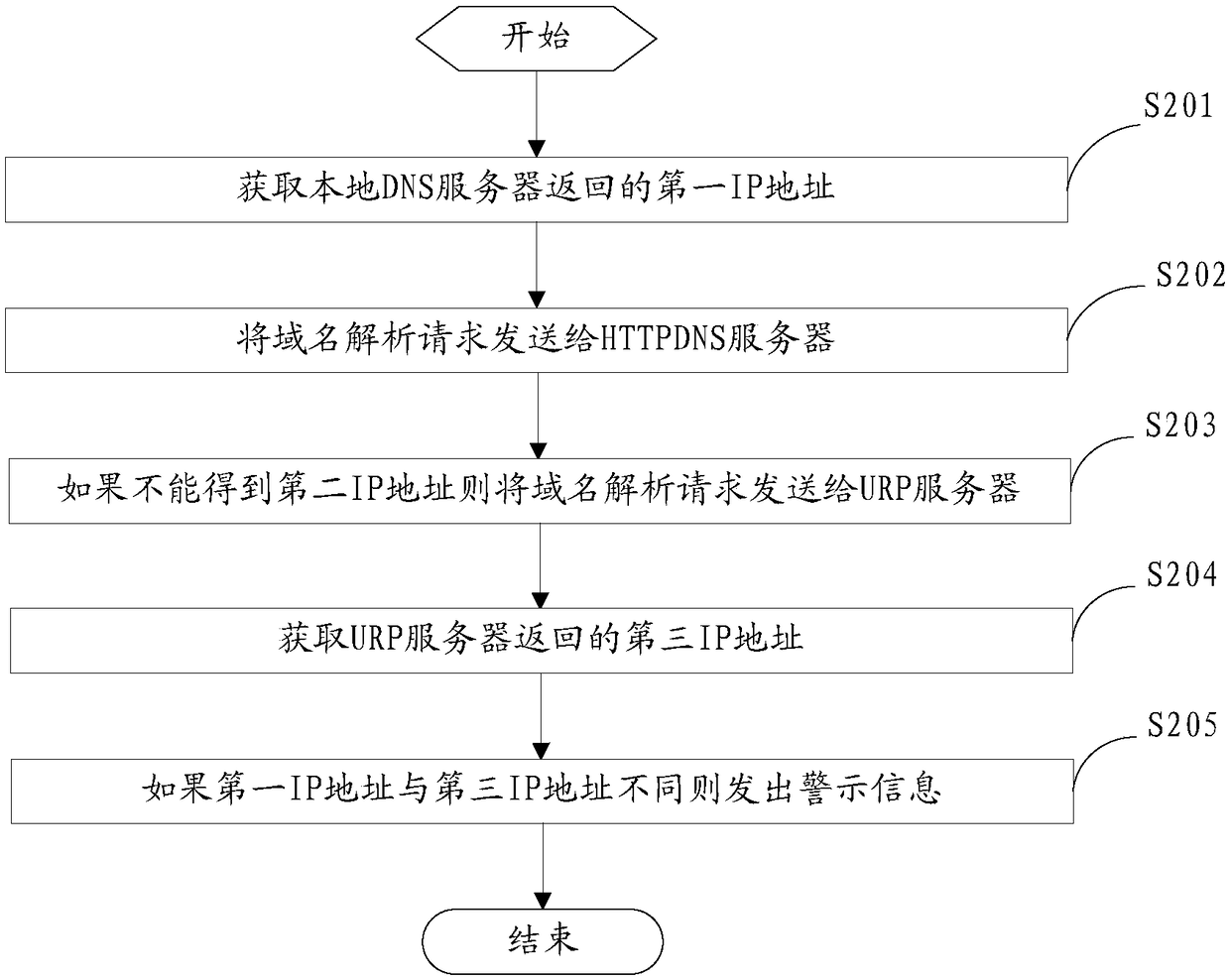
Detection method and device for DNS hijacking
The embodiment of the invention provides a detection method and a detection device for DNS hijacking. The method and device are applied to a DNS system. The method specifically comprises the steps ofwhen a user sends out a domain name analysis request, acquiring a first IP address through analyzing the domain name analysis request by a local DNS server; sending the domain name analysis request toan HTTPDNS server; acquiring a second IP address through analyzing the domain name analysis request by the HTTPDNS server; and if the first IP address is different from the second IP address, returning warning information that the domain name analysis request is hijacked back to the user. Through sending the warning information to the user when the hijacking occurs, the user can be stopped from accessing the wrong content server to which the hijacked domain name points, the user even can further adopt the corresponding treatment measure according to the warning information, and thus the situation that the normal access of the user to the Internet is influenced by DNS hijacking can be avoided.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
DNS hijacking detection method based on Internet of Things equipment
The invention discloses a DNS hijacking detection method based on Internet of Things equipment. The method comprises the steps that S100, an agent program is installed on the Internet of Things equipment to collect logs and upload the logs to message middleware; and a cloud server consumes middleware message, analyzes and calculates a detection result, judges whether DNS hijacking occurs or not, and stores an original log; S210, after the cloud server obtains the data collected by the agent from the rabbitmq, assets are found according to the equipment fingerprint information, and a log sourceis judged; S220, the equipment fingerprint information is stored into a MongoDB of a cloud server to serve as an equipment asset set; and S230, DNS hijacking analysis is performed. According to the method, analysis and judgment are carried out from multiple dimensions, the detection accuracy is improved, and false alarms and missing alarms are effectively reduced.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
Method and device for detecting DNS hijacking of domain name system, and storage medium
The invention provides a method and device for detecting DNS hijacking of a domain name system, and a storage medium, and the method comprises the steps: transmitting a domain name resolution requestto a DNS server; wherein the domain name resolution request is used for requesting to obtain an internet protocol IP address corresponding to a target domain name needing to be accessed; receiving a first IP address returned by the DNS server based on the domain name resolution request; determining at least one second IP address corresponding to the target domain name in a pre-stored correspondingrelation list of domain names and IP addresses; and determining whether the target domain name is hijacked or not according to the first IP address and the at least one second IP address. Whether thedomain name is hijacked or not can be quickly detected according to the corresponding relation list between the domain name and the IP address pre-stored on the terminal, and the method is easy to maintain, low in cost and high in availability.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
Method and system for preventing DNS (Domain Name System) cache from being stained and local DNS server
The invention discloses a method and a system for preventing DNS (Domain Name System) cache from being stained and a local DNS server. The method comprises steps: all analytical records for the local cache DNS are analyzed to acquire the number of analytical records which change in a preset time; when the acquired number of analytical records which change in a preset time meets a first preset condition, the DNS cache is determined to be stained; and after a DNS analysis request is received, the DNS analysis request is forwarded to a disaster recovery server, an IP address corresponding to the DNS analysis request returned by the disaster recovery server is acquired, and the IP address serves as an analytical record to be stored. Through the method and the system for preventing the DNS cache from being stained and the local DNS server, timely judgment can be carried out when abnormal DNS hijacking happens, recovery is carried out as soon as possible, and the system stability is improved.
Owner:CHINA MOBILE COMM GRP CO LTD
Safety communication method and device based on wireless local area network and electronic equipment
InactiveCN108111516AAvoid hijackingProtection securityTransmissionSecurity arrangementDomain nameDNS hijacking
The invention provides a safety communication method and device based on a wireless local area network and electronic equipment, wherein the method comprises the steps of identifying whether a connected wireless local area network has a safety risk or not; if the wireless local area network has the safety risk, according to a preset network address of a security domain name server DNS, establishing a virtual private network VPN connection for communicating with the security DNS; and performing a domain name resolution communication process by adopting the VPN connection. According to the method, the VPN connection is not required to be established for all the wireless local area networks, and the VPN connection is only established for the wireless local area network with the safety risk; the DNS request is directed to a safe DNS through the VPN, so that a DNS hijack is prevented and the network safety is protected; meanwhile, due to the fact that the pertinence is high, the cruising ability of the electronic equipment can be improved. In addition, due to the fact that the IP address and the domain name are encrypted and transmitted through the VPN technology, network access behavior leakage of a user can be prevented.
Owner:ZHUHAI JUNTIAN ELECTRONICS TECH
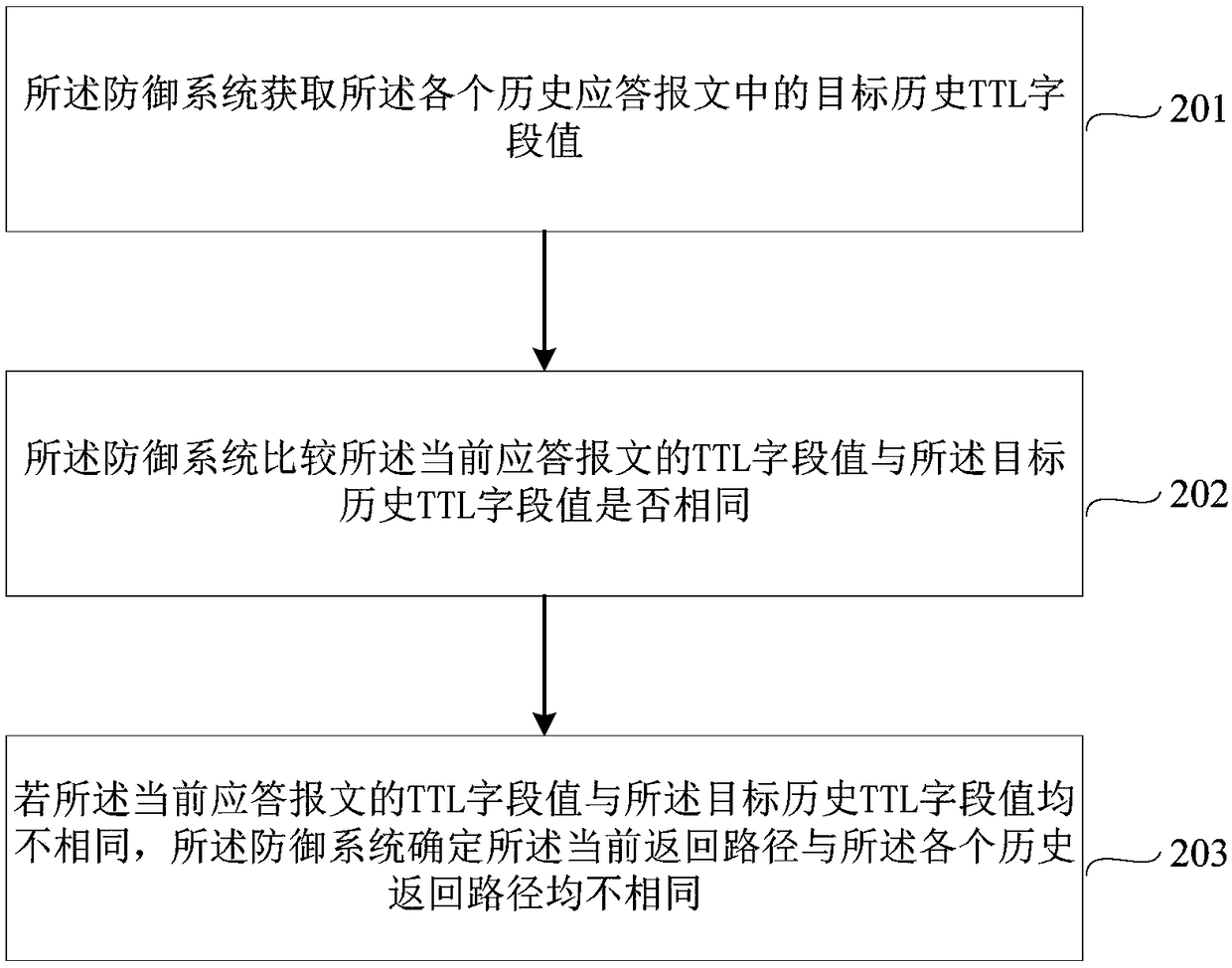
DNS (Domain Name System) hijacking defending method and device
The embodiment of the invention discloses a DNS (Domain Name System) hijacking defending method and device. The method comprises the following steps: acquiring history response messages generated by aDNS server according to a preset number of history domain name resolution requests based on a preset time interval through a defending system; after a current response message generated according toa current domain name resolution request is received, comparing a current return path included in the current response message with history return paths included in the history response messages; if the current return path is different from the history return paths, comparing whether an IP address of a target host in the current response message is the same as an IP address of a target host in a credible response message or not; and if not, feeding back the credible response message to a client. Through adoption of the method and the device, the problem of incapability of avoiding receiving phishing site IP addresses in an existing DNS hijacking defending method can be solved, thereby improving the network security.
Owner:武汉思普崚技术有限公司
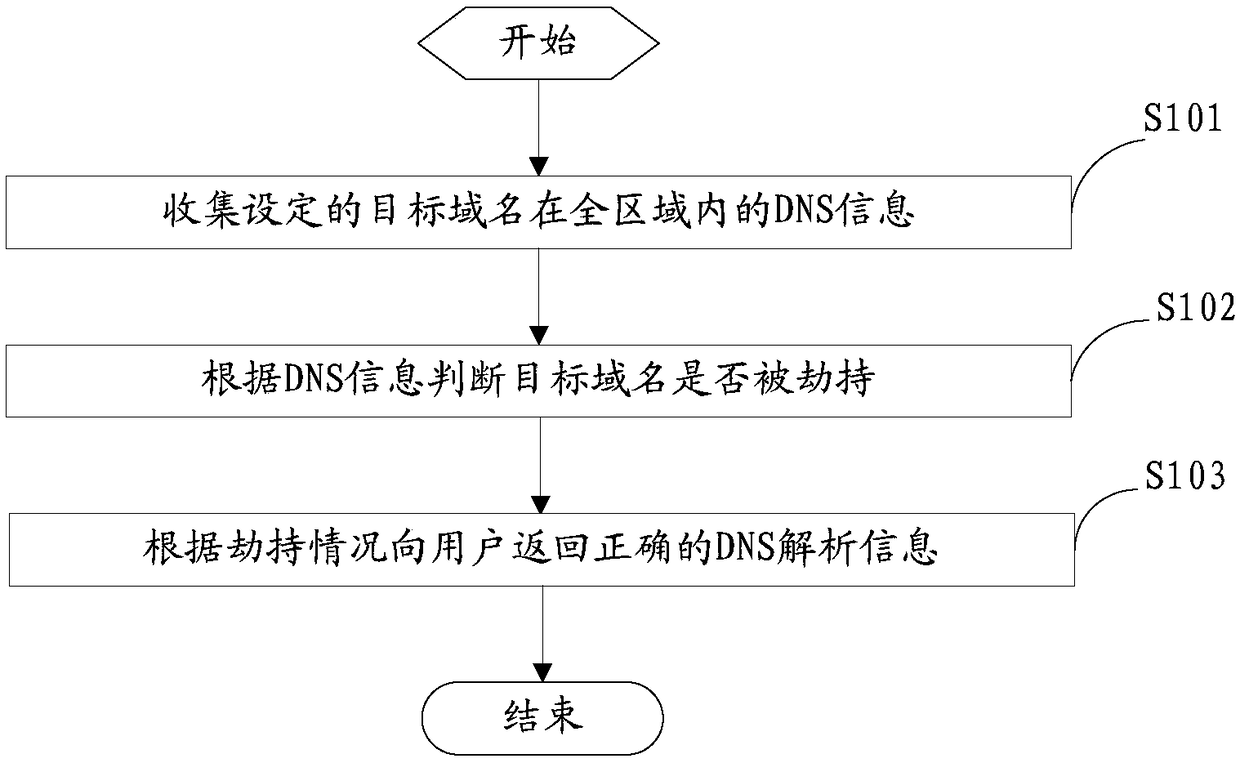
DNS hijacking defense method and apparatus
The embodiment of the invention provides a DNS hijacking defense method and apparatus. The method and apparatus are applied to a DNS system, and the method specifically comprises the following steps:collecting DNS information of a set target domain name in the whole area; judging whether the target domain name is hijacked according to the DNS information; and returning correct DNS resolution information according to whether the target domain name is hijacked. Through the above operations, a DNS request of a user can be prevented from being hijacked, so that the user can securely use the Internet.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
DNS hijack defending method, device and system based on firewall system
InactiveCN109361676ARealize the defense function of hijackingRealize the defense functionTransmissionDomain nameThird party
The application discloses a DNS hijack defending method, device and system based on a firewall system. The method comprises the following steps: configuring a first credible domain name server and a second credible domain name server; judging whether parsing results relevant to domain name information returned by the first credible domain server and the second credible domain server are the same or not; if so, storing the parsing results in a domain cache list; comparing whether a third parsing result returned by a local authorized domain name server is the same as the parsing results in the domain name cache list or not; and if not, hijacking a third parsing result by the firewall system since the third parsing result is hijacked. Third parties, namely, the first credible domain name server, the second credible domain name server and the local authorized domain name server are used for confirmation to realize the defending function of the firewall system for DNS hijacks, so that DNS hijack attack behaviors can be detected and intercepted reasonably and effectively, and harm to a user caused by phishing sites is avoided.
Owner:天津睿邦安通技术有限公司
Method and apparatus for reducing DNS hijacking risk
InactiveCN106713309ALow risk of hijackingReduced risk of hijackingTransmissionDomain nameDNS hijacking
The invention provides a method and apparatus for reducing a DNS hijacking risk. The method comprises the following steps: sending a dynamic configuration request to a dynamic host configuration protocol DHCP device in a local area network; receiving dynamic configuration information returned by the DHCP, wherein the dynamic configuration information comprises a main primary domain name resolution system DNS server address; switching a dynamic configuration networking state to a static networking state, wherein the dynamic configuration networking state is a state of receiving the dynamic configuration information sent by the DHCP device and accessing the network based on the dynamic configuration information, the static networking state is a state of accessing the network according to static secure configuration information, and the main DNS server address of the secure configuration information is a target wide area network DNS server address; and accessing the network based on the secure configuration information.
Owner:BEIJING QIHOO TECH CO LTD
Browser page acquisition method and device and electronic equipment
The invention provides a browser page acquisition method and device and electronic equipment. The method comprises the steps of: after a browser is started, reading a network address of a preset secure domain name server (DNS); acquiring a virtual private network (VPN) connection in communication with the secure DNS according to the network address of the secure DNS; when a domain name to be accessed is acquired, sending the domain name to the secure DNS through the VPN connection; receiving a network address obtained by parsing the domain name by the secure DNS through the VPN connection; andaccessing based on the network address to obtain the required page. After the user starts the browser, a DNS request is directed to the secure DNS by using the VPN connection to prevent DNS hijacking. At the same time, because the IP address and the domain name are transmitted in an encrypted manner by adopting the VPN technology, the leakage of user's network access behavior can be prevented andthe privacy of users can be protected.
Owner:ZHUHAI JUNTIAN ELECTRONICS TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com