Secure and reliable network access method for hardware device
An access method and a technology of hardware equipment, which are applied in the direction of secure communication devices, electrical components, encryption devices with shift registers/memory, etc., can solve problems such as occupying a lot of resources, consuming resources, and complex protocols
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
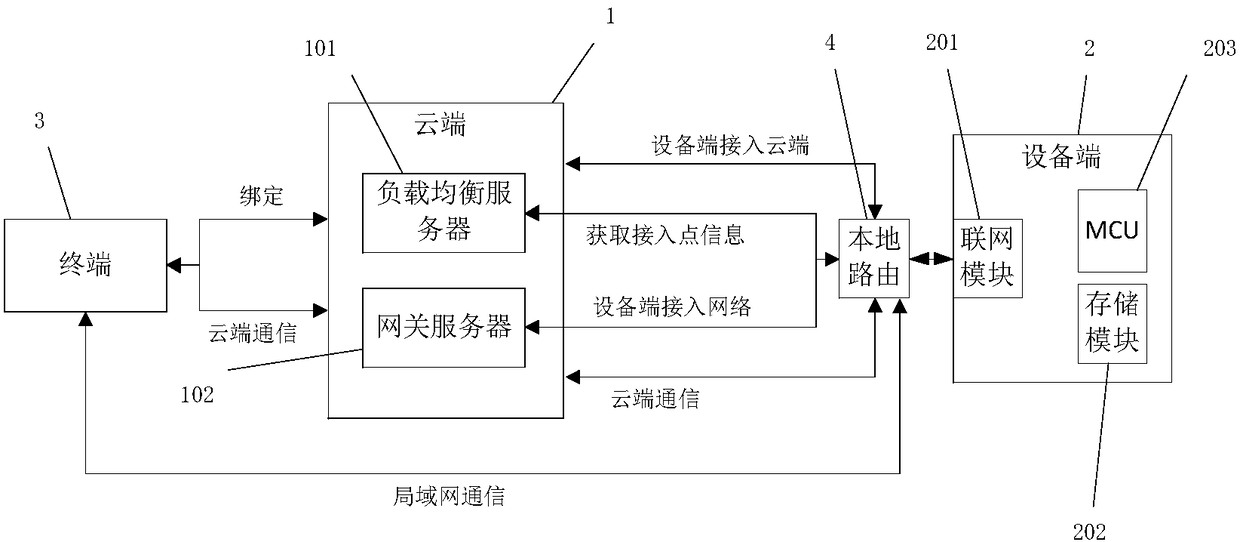
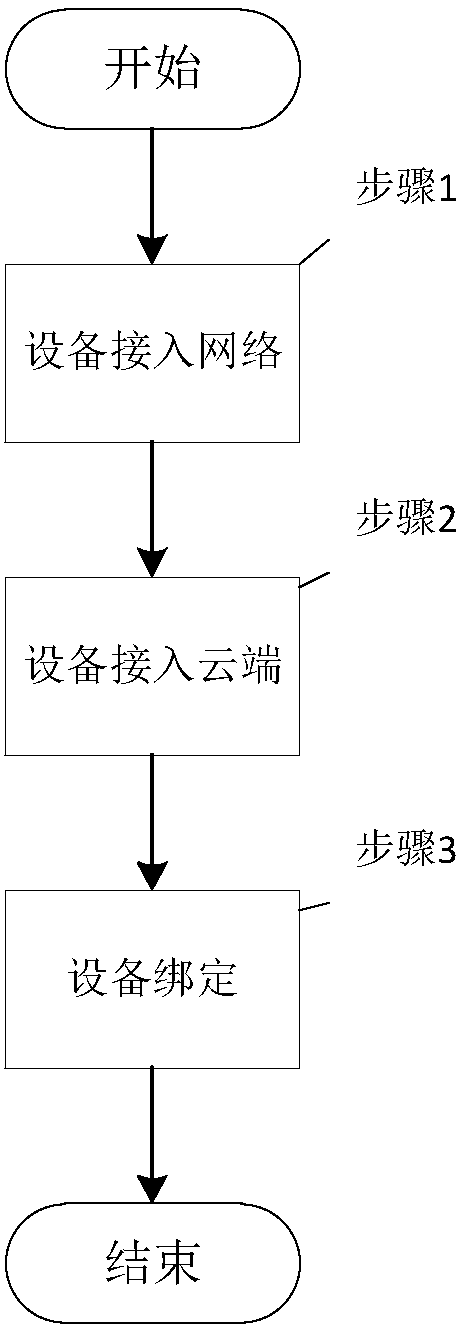
[0095] Example 1, such as figure 2 As shown, the safe and reliable network access method for hardware devices described in the first embodiment of the present invention includes the following steps:
[0096] Step 1, the device accesses the network: the networking module 201 of the device 2 and the load balancing server 101 of the cloud 1 perform the first handshake two-way authentication. Assign the gateway server 102 as the access gateway server, and send the address and port of the access gateway server to the networking module 201, the networking module 201 connects to the access gateway server 102, and the device terminal 2 accesses the network to complete.
[0097] Such as Figure 4 As shown, step 1 specifically includes:
[0098] Step 101, the networking module 201 obtains the address and port of the access gateway server from the storage module 202 of the device terminal 2, and if the acquisition is successful, then turn to step 110, and if the acquisition fails, tur...
Embodiment 2
[0128] Example 2, such as figure 1 As shown, the safe and reliable network access method for hardware devices described in the second embodiment of the present invention differs from Embodiment 1 in that in steps 1 and 2, AES encryption authentication is used instead of RSA encryption authentication. The specific steps as follows:
[0129] Such as Figure 6 As shown, step 1 specifically includes:
[0130] Step 101, the networking module 201 obtains the address and port of the access gateway server from the storage module 202 of the device terminal 2, and if the acquisition is successful, then turn to step 110, and if the acquisition fails, turn to step 102;
[0131] Step 102, the MCU 203 sends the networking authentication information of the device terminal 2 and the AES key for device authentication to the networking module 201, wherein the networking authentication information includes a device product type unique identifier, a device unique identifier, and a random value;...
Embodiment 3
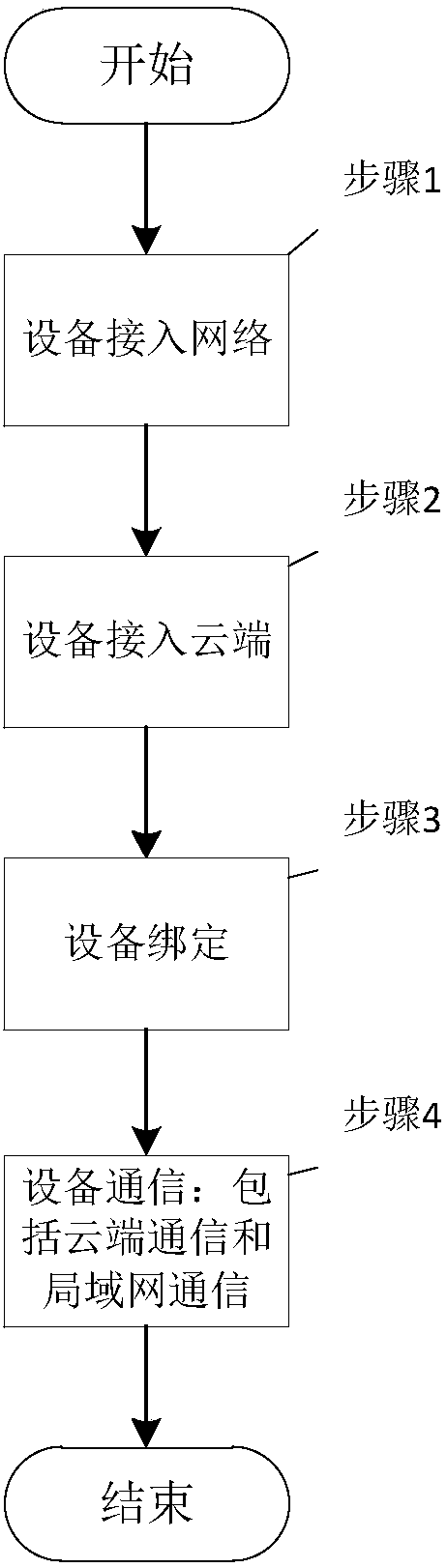
[0152] Embodiment 3, the safe and reliable network access method of the hardware device described in the third embodiment of the present invention, such as image 3 As shown, the difference from embodiment 1 and embodiment 2 is that step 4 is also included:
[0153] Step 4, device communication: including cloud communication and local area network communication, wherein, the cloud communication is encrypted communication between the device end 2 and the cloud 1, and the local area network communication is the encrypted communication between the device end 2 and the terminal 3 in the local area network.
[0154] Cloud communication, specifically including:
[0155] Step 411, such as Figure 9 As shown, the OTA upgrade of the networking module and MCU includes:
[0156] Step A1, after the device terminal 2 is connected to the cloud 1, the cloud 1 obtains the version number of the OTA file uploaded in the background, and compares it with the device version number and the firmwa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com