Detection method and device for DNS hijacking
A detection method and detection device technology, applied in the Internet field, can solve problems such as economic loss of users, influence on normal operation of Internet services, and failure of users to perform normal network access, so as to achieve the effect of avoiding normal access
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0059] figure 1 It is a flowchart of steps of a method for detecting DNS hijacking provided by an embodiment of the present invention.
[0060] refer to figure 1 As shown, the DNS hijacking detection method provided by this embodiment is applied to the DNS system, i.e. the domain name system, to detect whether a domain name resolution request is hijacked, that is, maliciously returns a wrong IP address to the user's domain name resolution request or does not return correct IP address, the detection method specifically includes the following steps:
[0061] S101: Obtain the first IP address returned by the local DNS server.
[0062] When a user sends a domain name resolution request, the request is first sent to the local DNS server. When the local DNS server receives the domain name resolution request, it analyzes the domain name information carried in the request and gives the domain name corresponding to the domain name. IP address, the parsed IP address will be returned to...
Embodiment 2
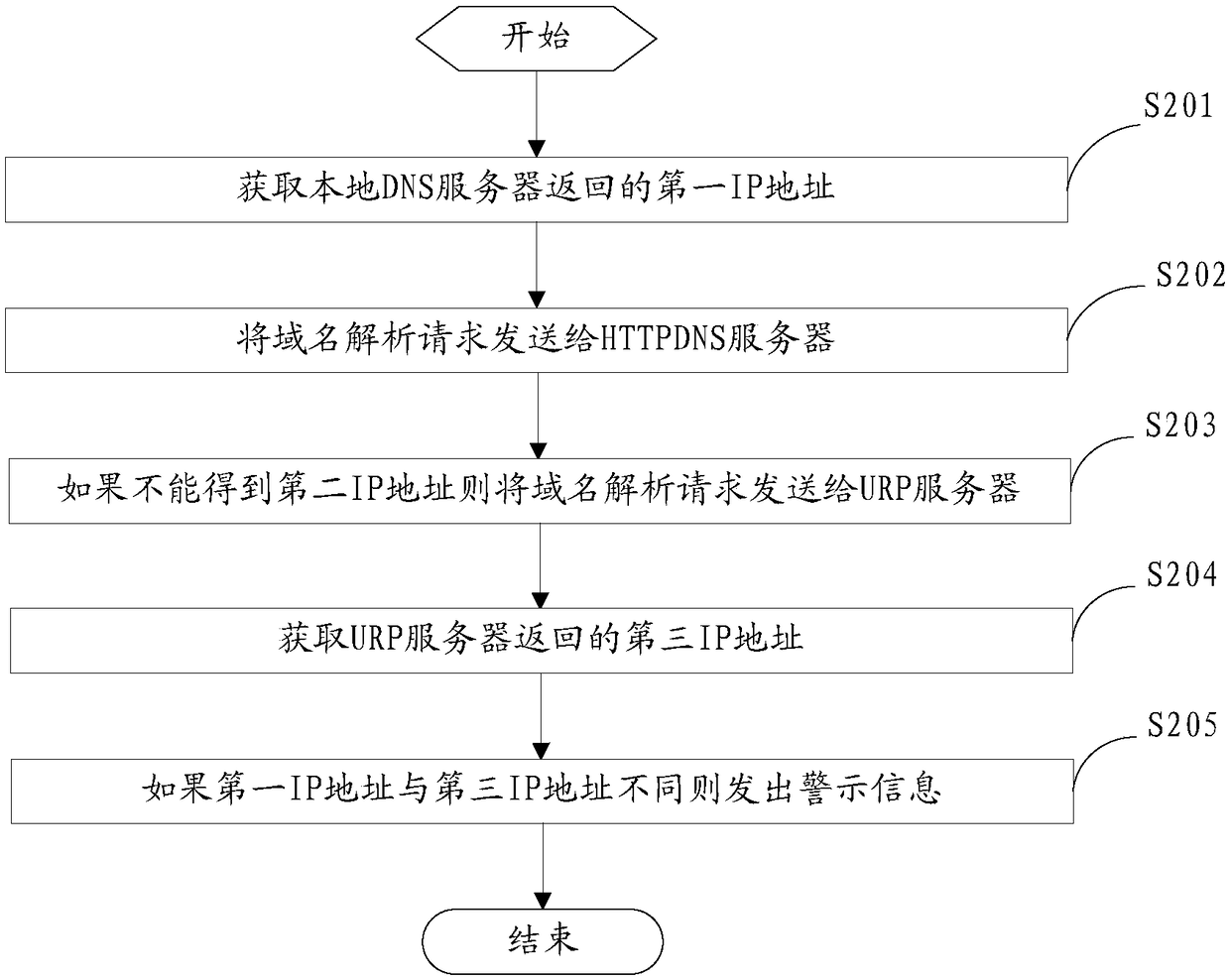
[0075] figure 2 It is a flowchart of steps of another DNS hijacking detection method provided by the embodiment of the present invention.
[0076] refer to figure 2 As shown, the DNS hijacking detection method provided by this embodiment is applied to the DNS system, i.e. the domain name system, to detect whether a domain name resolution request is hijacked, that is, maliciously returns a wrong IP address to the user's domain name resolution request or does not return correct IP address, the detection method specifically includes the following steps:
[0077] S201: Obtain the first IP address returned by the local DNS server.
[0078] This is the same as or similar to the solution for obtaining the first IP address in the previous embodiment, and will not be repeated here.
[0079] S202: Send the domain name resolution request to the HTTPDNS server.
[0080] While sending the user's domain name resolution request to the local DNS server, the request is also sent to the H...
Embodiment 3
[0094] image 3 It is a flow chart of steps for yet another DNS hijacking detection method provided by the embodiment of the present invention.
[0095] refer to image 3 As shown, the DNS hijacking detection method provided by this embodiment is applied to the DNS system, namely the domain name system, and is used to detect whether a domain name resolution request is hijacked, that is, maliciously returns a wrong IP address to the user's domain name resolution request or does not return correct IP address, the detection method specifically includes the following steps:
[0096] S301: Obtain the first IP address returned by the local DNS server.
[0097] This is the same as or similar to the solution for obtaining the first IP address in the previous embodiment, and will not be repeated here.
[0098] S302: Send the domain name resolution request to the HTTPDNS server.
[0099] While sending the user's domain name resolution request to the local DNS server, the request is ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com