Detection method and device for DNS hijacking as well as mobile terminal
A detection method and mobile terminal technology, applied in the detection of DNS hijacking, in the field of mobile terminals, can solve the lack of DNS anti-hijacking technology and other problems, and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0019] refer to figure 1 , shows a flowchart of steps of a method for detecting DNS hijacking according to Embodiment 1 of the present invention.
[0020] The method for detecting DNS hijacking in this embodiment can be executed and implemented by any device capable of transmitting, receiving and processing data, including but not limited to mobile terminals. In this embodiment, a mobile terminal is used as an example for description.
[0021] The detection method of the DNS hijacking of the present embodiment comprises the following steps:
[0022] Step S102: Obtain the IP address corresponding to the domain name to be detected from the DNS server.
[0023] Wherein, the domain name to be detected is a domain name associated with an application of the mobile terminal.
[0024] For applications on mobile terminals, it is usually only necessary to visit the domain name associated with it. For example, an e-book application only needs to visit websites that provide e-books, we...
Embodiment 2
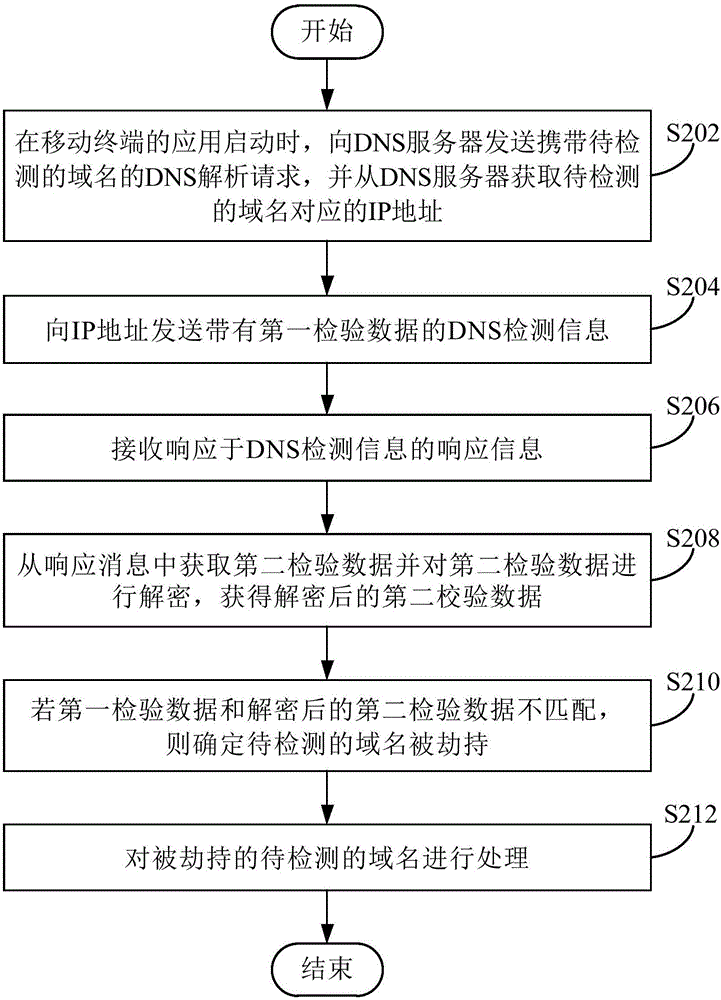
[0039] refer to figure 2 , shows a flowchart of steps of a method for detecting DNS hijacking according to Embodiment 2 of the present invention.
[0040] The detection method of the DNS hijacking of the present embodiment comprises the steps:
[0041] Step S202: When the application of the mobile terminal is started, a DNS resolution request carrying the domain name to be detected is sent to the DNS server, and an IP address corresponding to the domain name to be detected is obtained from the DNS server.
[0042] In this embodiment, when the application of the mobile terminal is started, the application of the mobile terminal sends a DNS resolution request (domain name resolution request) to the DNS server to obtain the IP address corresponding to the domain name to be detected. That is to say, the detection of DNS hijacking is performed immediately after the application of the mobile terminal is started, so that the application of the mobile terminal can normally access th...
Embodiment 3
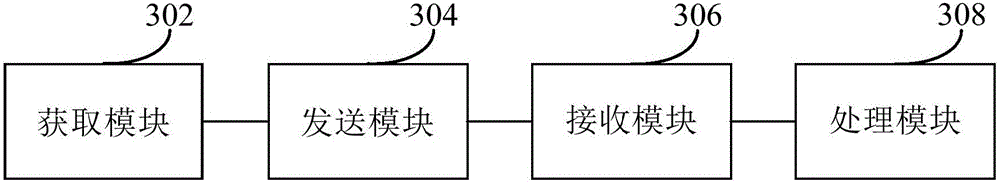
[0072] refer to image 3 , shows a structural block diagram of an apparatus for detecting DNS hijacking according to Embodiment 3 of the present invention.
[0073] The device for detecting DNS hijacking in this embodiment includes an acquisition module 302 , a sending module 304 , a receiving module 306 and a processing module 308 . Wherein, the obtaining module 302 is used to obtain the IP address corresponding to the domain name to be detected from the DNS server, wherein the domain name to be detected is a domain name associated with the application of the mobile terminal; the sending module 304 is used to send DNS detection information to the IP address, Wherein, the DNS detection information carries the first verification data; the receiving module 306 is used to receive the response information in response to the DNS detection information, and obtain the second verification data from the response information; the processing module 308 according to the first verification...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com