Method and arrangement for integration of different authentication infrastructures
A technology of infrastructure and user equipment, applied in security devices, electrical components, transmission systems, etc., can solve problems that hinder the development and provision of new services
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
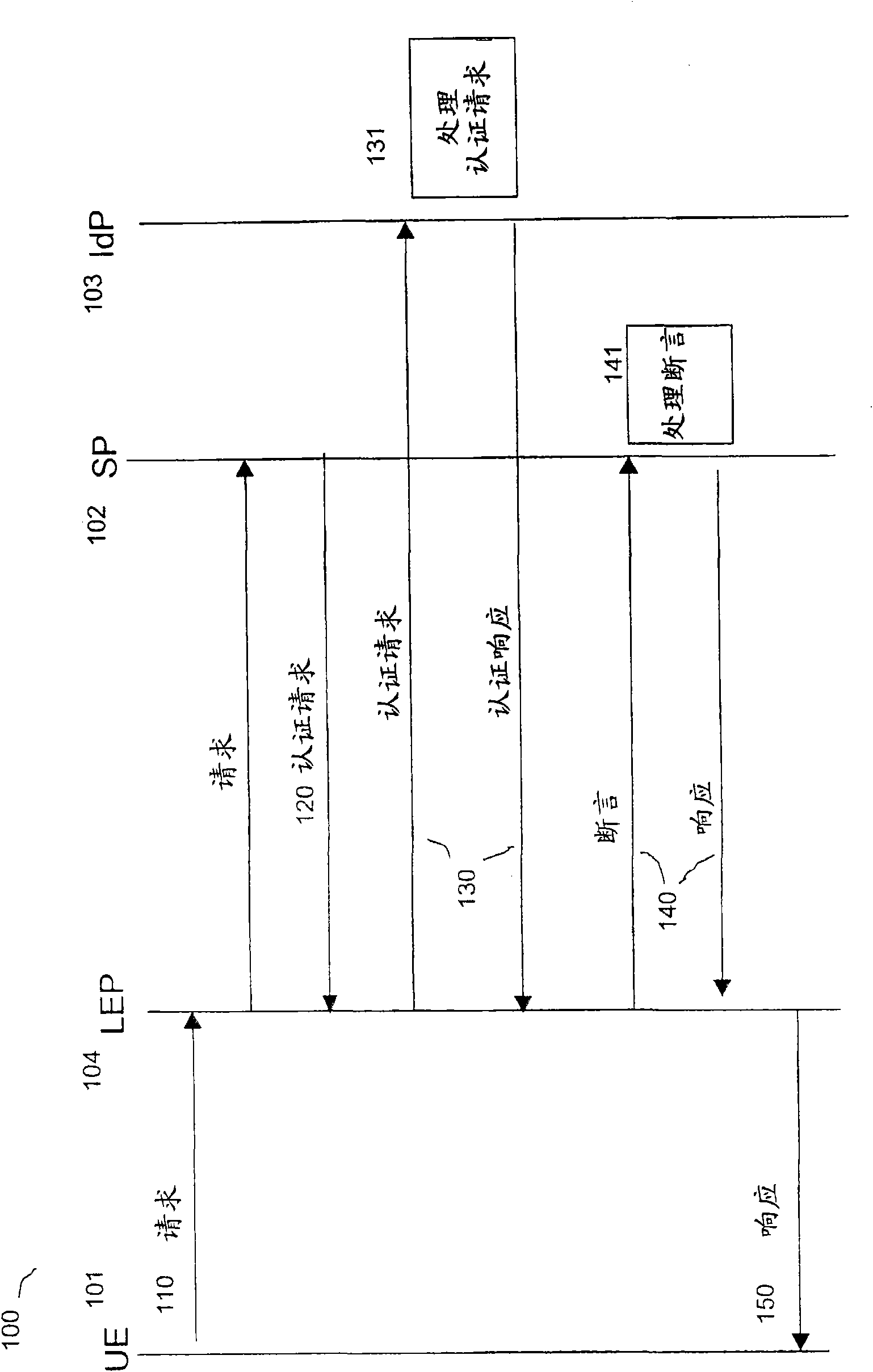
[0042] Figure 1 shows an overview of signaling according to the Free ID-FF framework. At 110, the user entity 101UE makes a request for a service at the service provider 102SP, which request goes through a free enabling proxy 104LEP. At 120, the SP requests authentication. At 130, an authentication request-response communication is shown with the identity provider 103IdP, which at 131 processes the authentication request. The Authentication Response includes an assertion that the UE is authenticated. At 140, the assertion is communicated with the service provider SP, which at 141 processes the assertion. At 150, the proxy LEP responds to the request 110 that the UE is authenticated to access services at the SP.
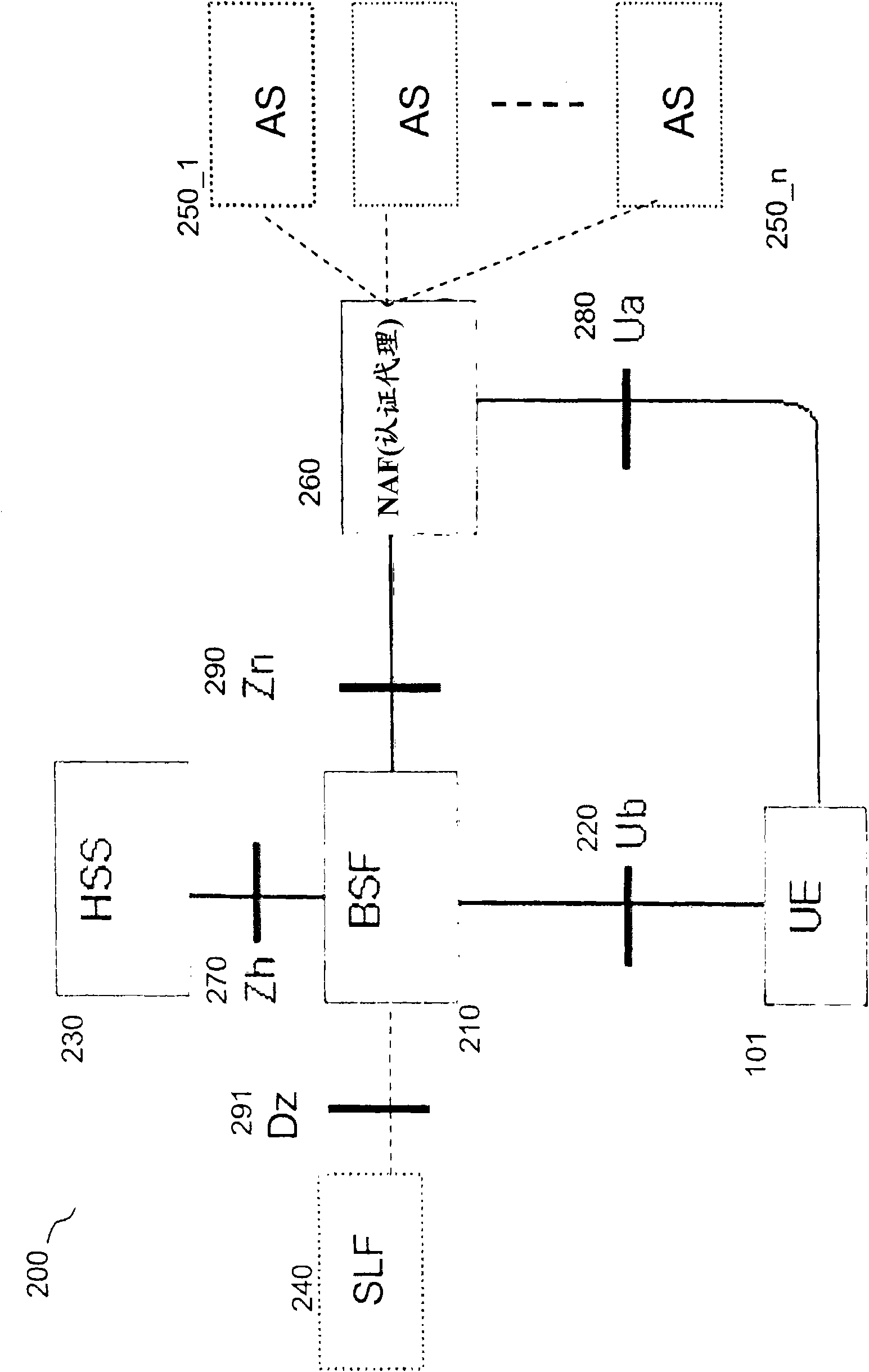
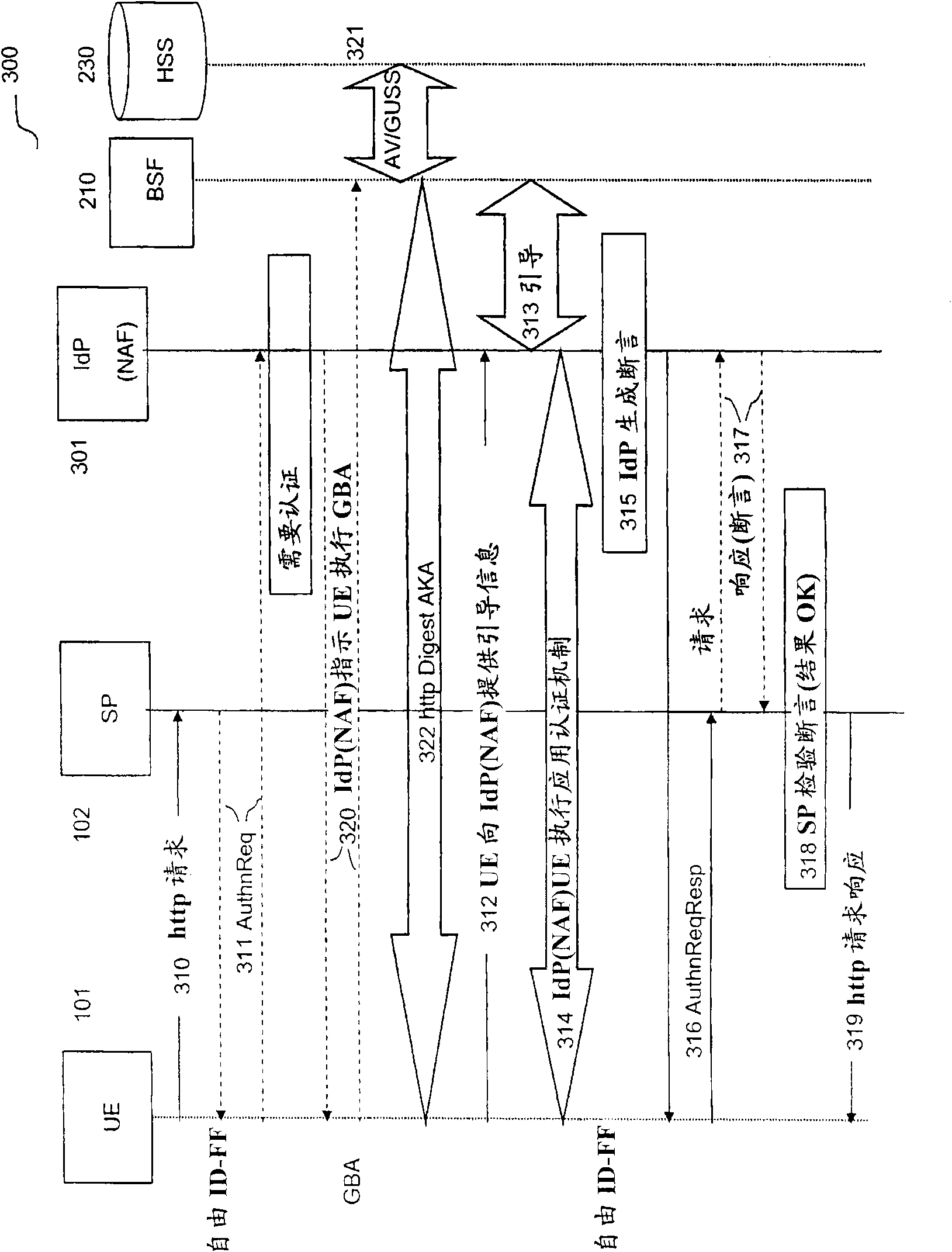
[0043] Figure 2 illustrates a prior art deployment of GBA / GAA with an Authentication Proxy 260 acting as a Network Application Function NAF with respect to the GBA / GAA infrastructure. The Generic Bootstrap Server Function 210BSF and the User Entity 101UE authentic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com