Vulnerability assessment method and device, computing equipment and storage medium
A computing device and vulnerability technology, applied in computing, computer security devices, instruments, etc., can solve the problem of incomplete vulnerability assessment and achieve high accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] In order to make the purpose, technical solution and advantages of the present application clearer, the implementation manners of the present application will be further described in detail below in conjunction with the accompanying drawings.
[0040]In order to facilitate the understanding of the embodiments of the present application, the concepts of the nouns involved are firstly introduced below:
[0041] 1. Vulnerability assessment (va) is the process of identifying, quantifying, and prioritizing vulnerabilities in an operating system.
[0042] 2. A security advisory (sa) is security information regularly released by an operating system provider or a software provider. Security bulletins include but are not limited to vulnerability names, vulnerability types, affected situations, and vulnerability repair methods.
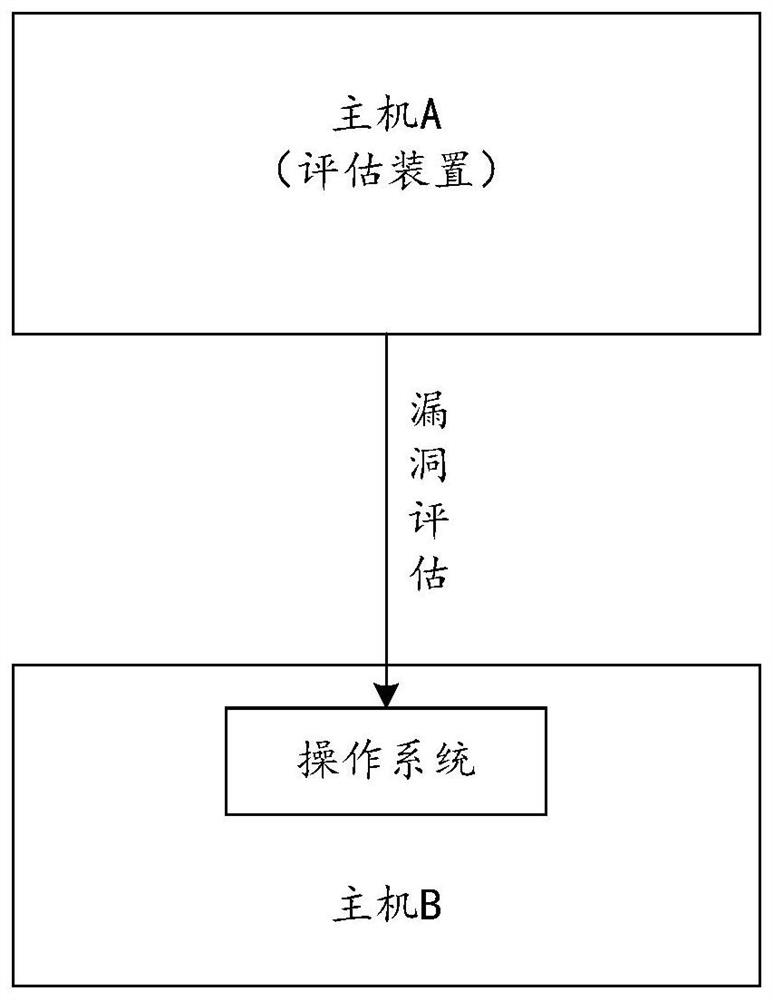
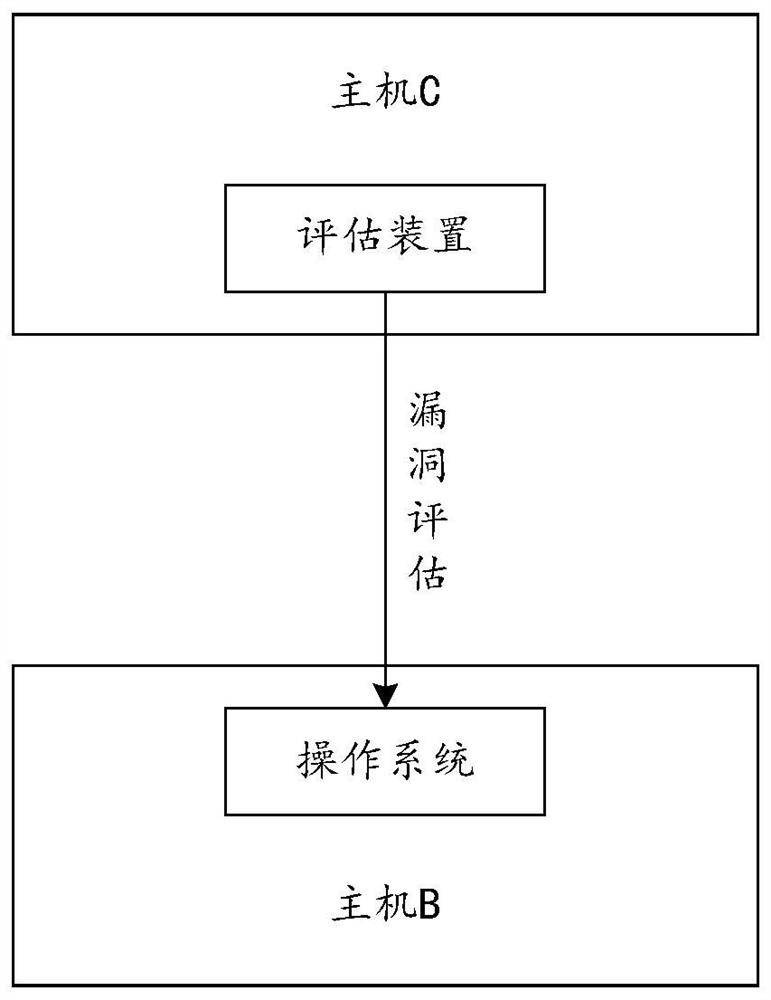
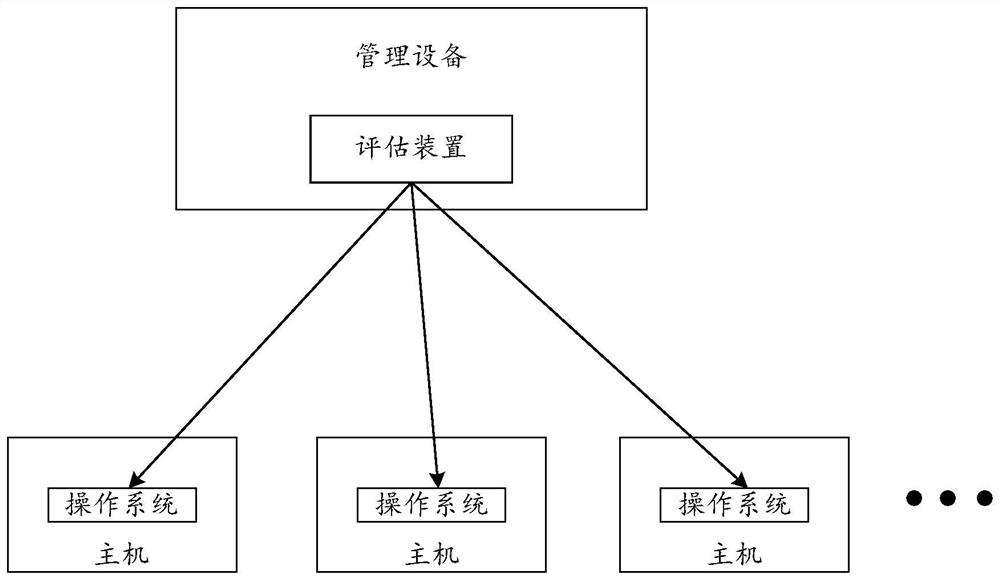
[0043] In order to discover vulnerabilities in the operating system in a timely manner, during the use of the operating system, vulnerability assessmen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com