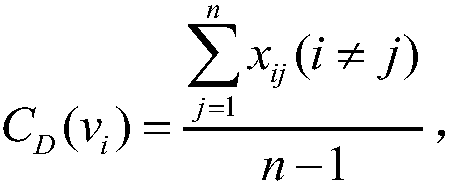Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
128 results about "Software network" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
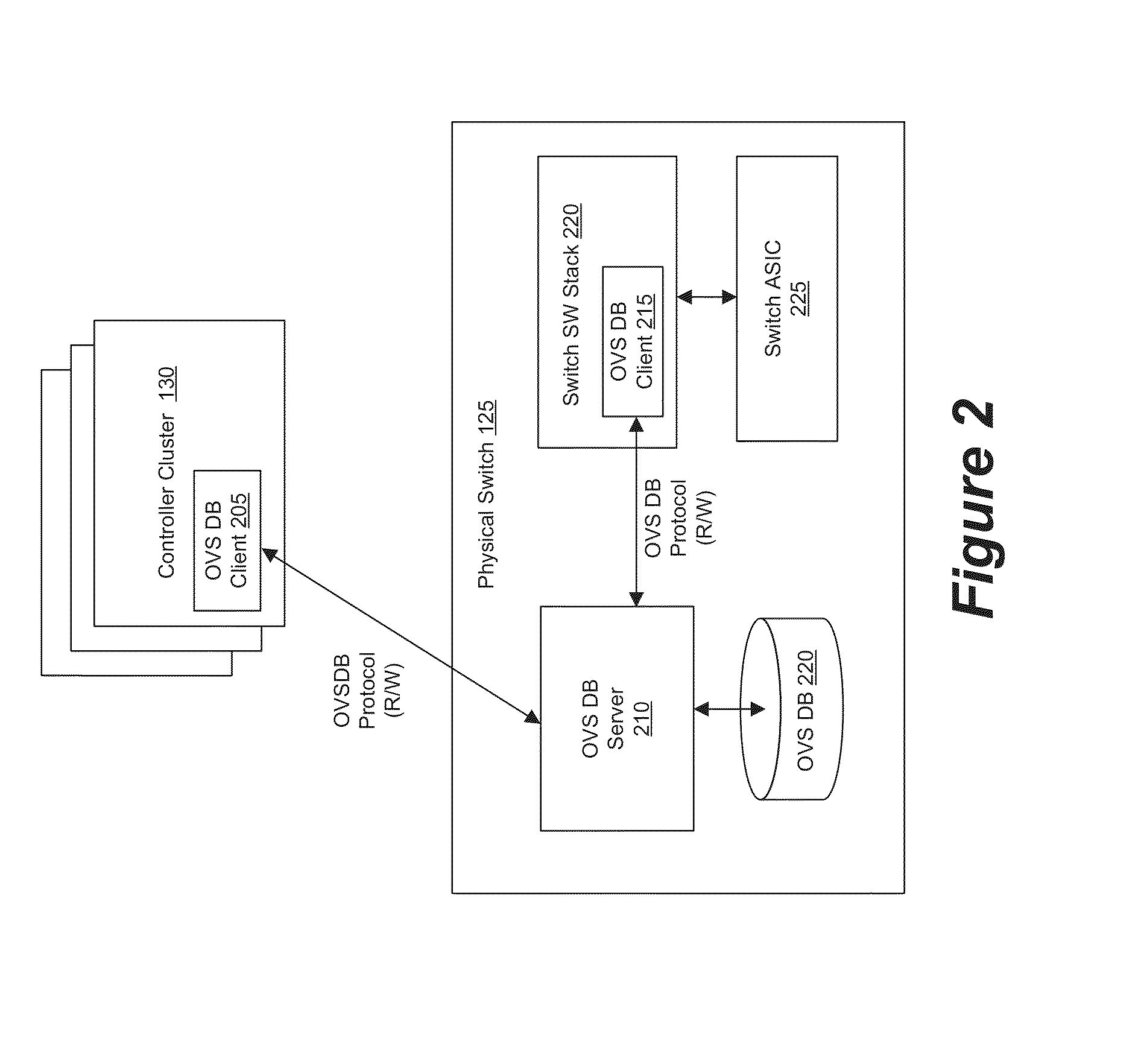
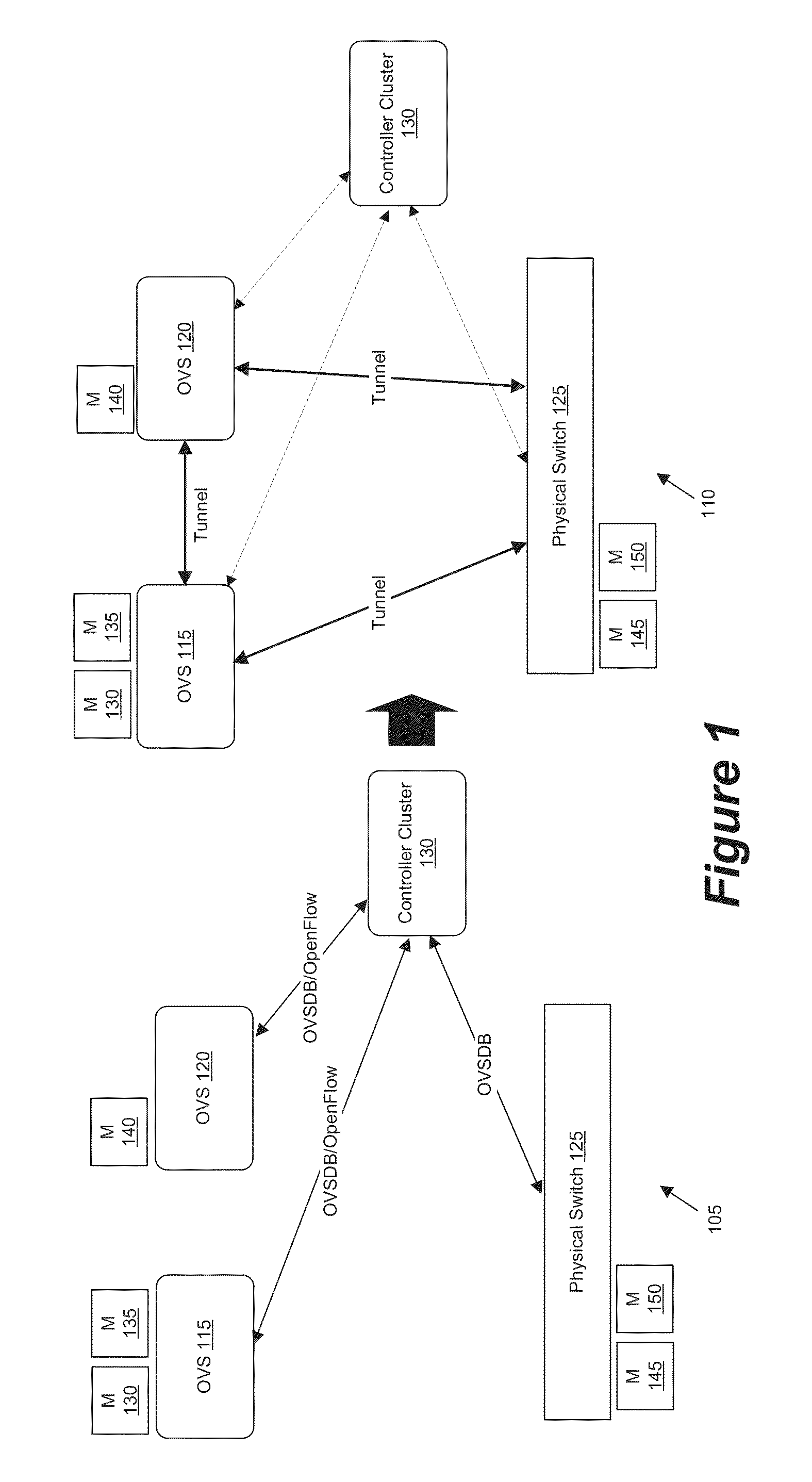
Managing Software and Hardware Forwarding Elements to Define Virtual Networks
ActiveUS20150100704A1Easy to implementMaintain reliabilityDigital computer detailsNetworks interconnectionLoad SheddingSoftware network
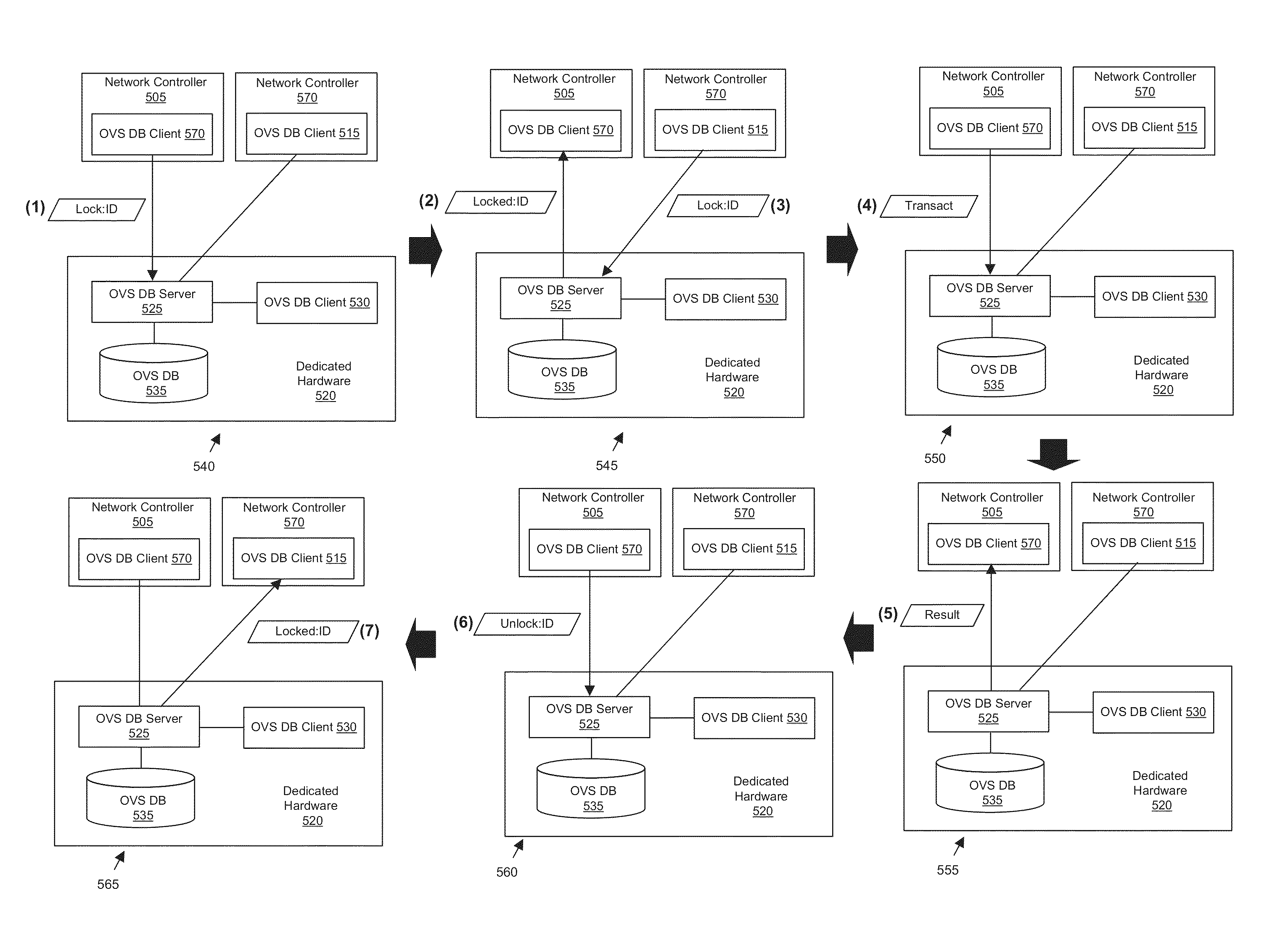
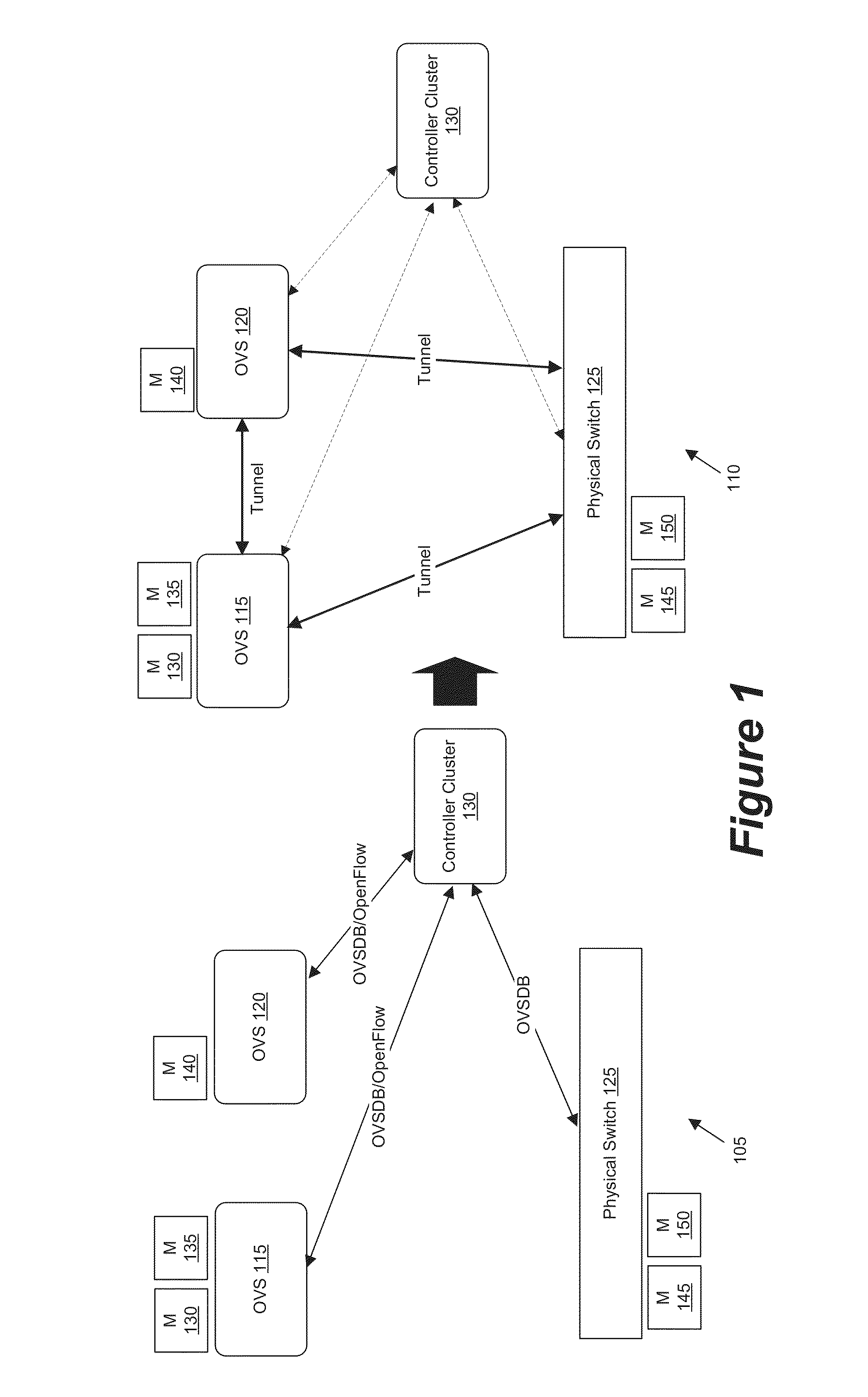
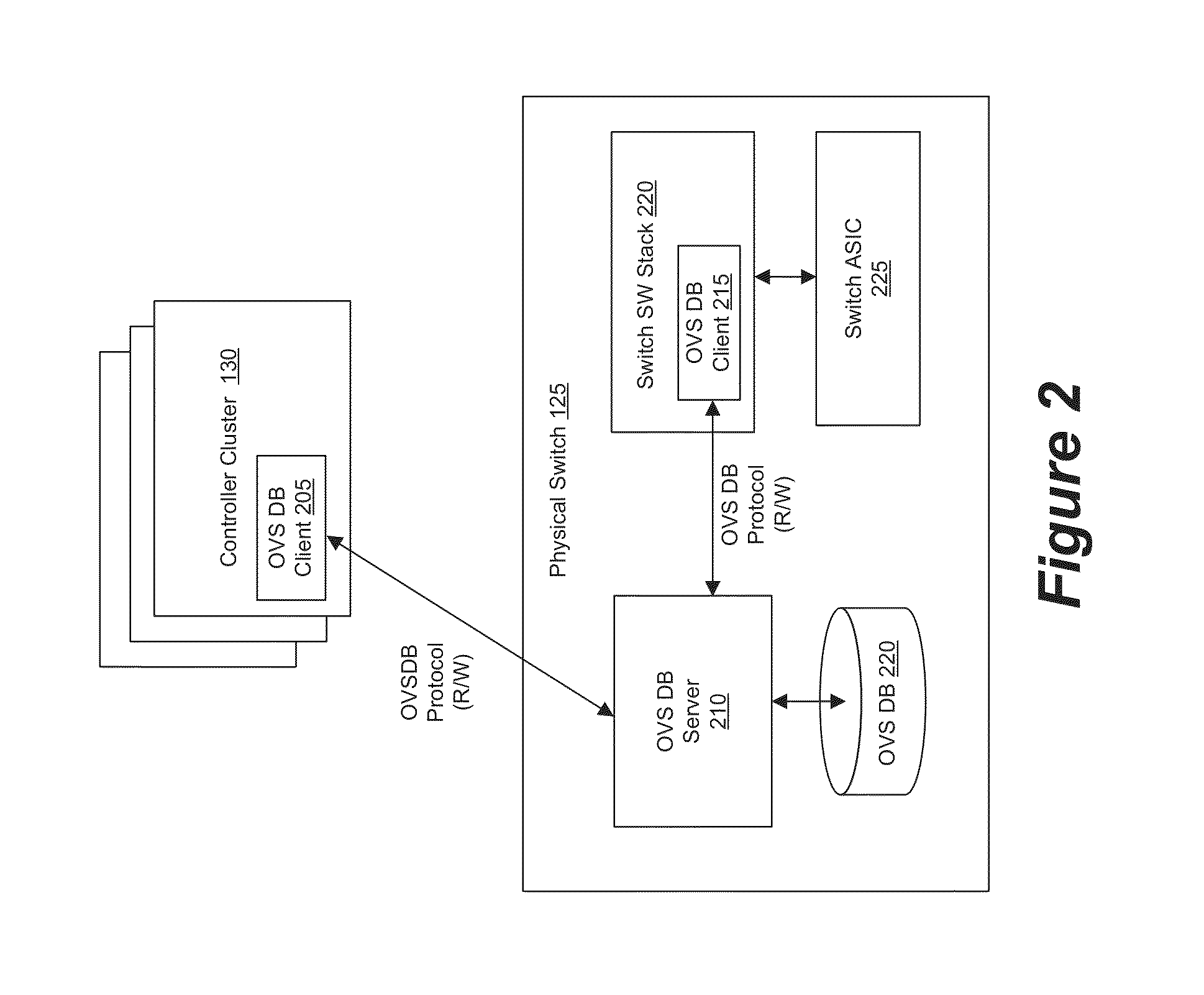
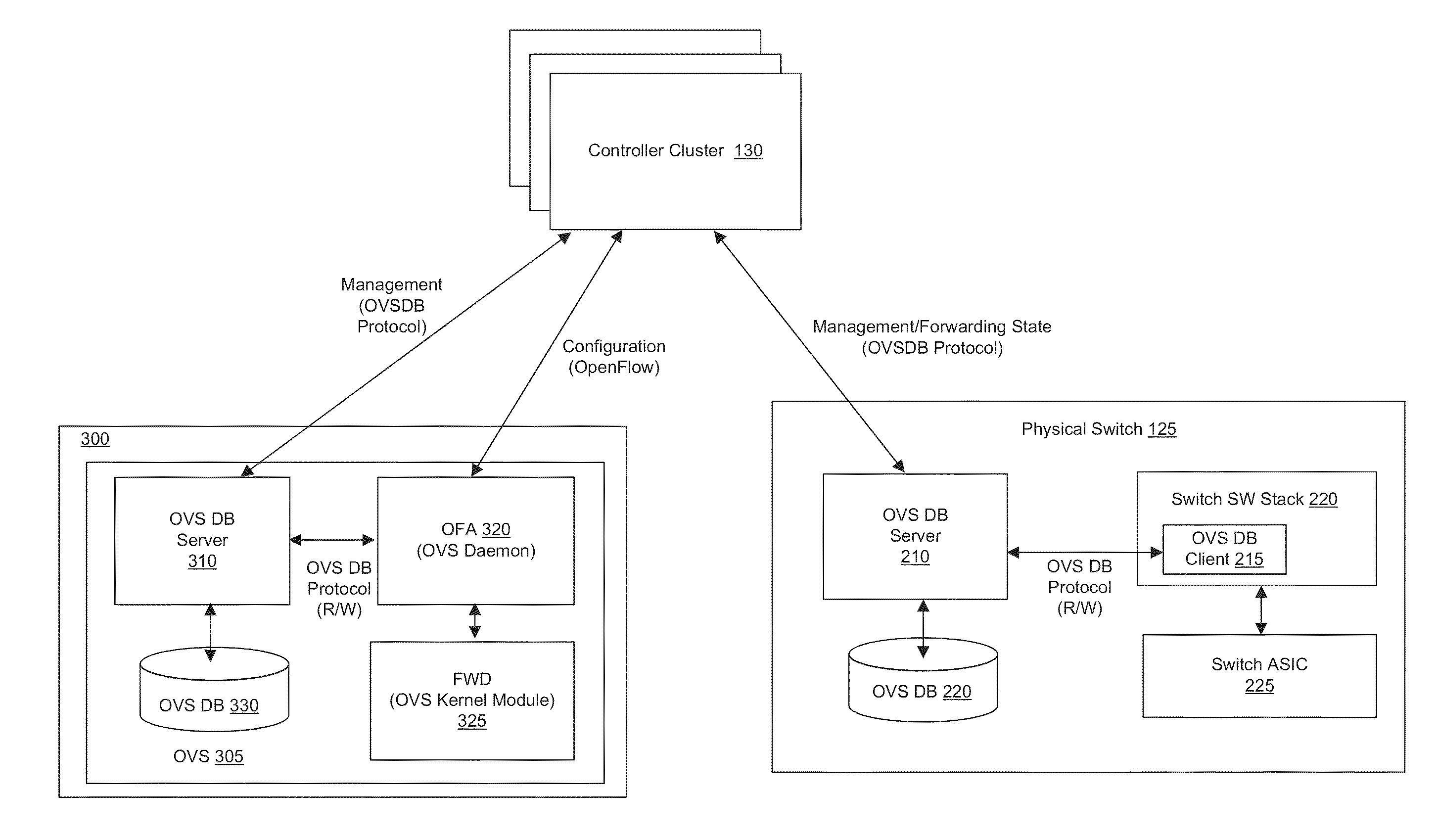
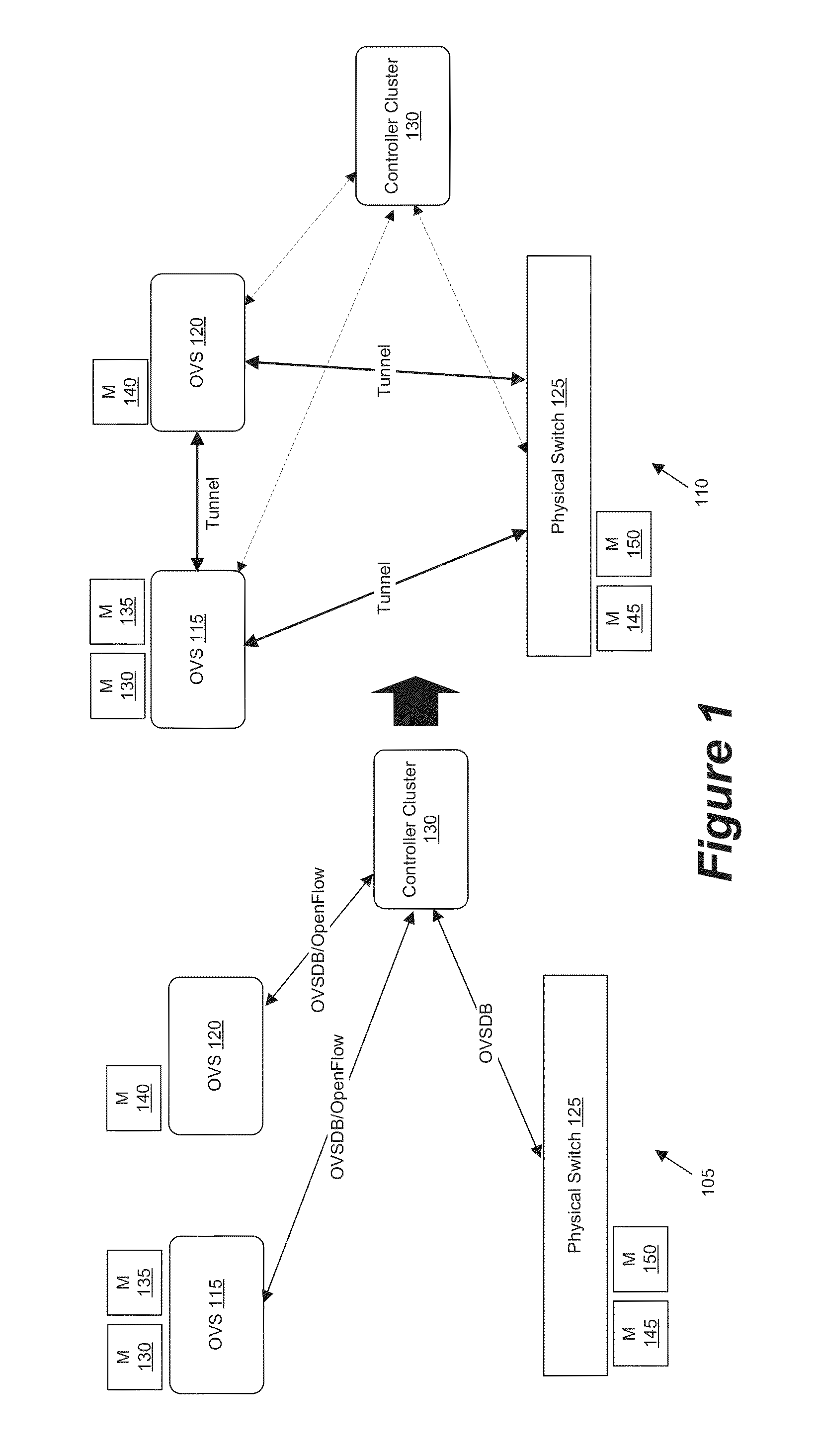
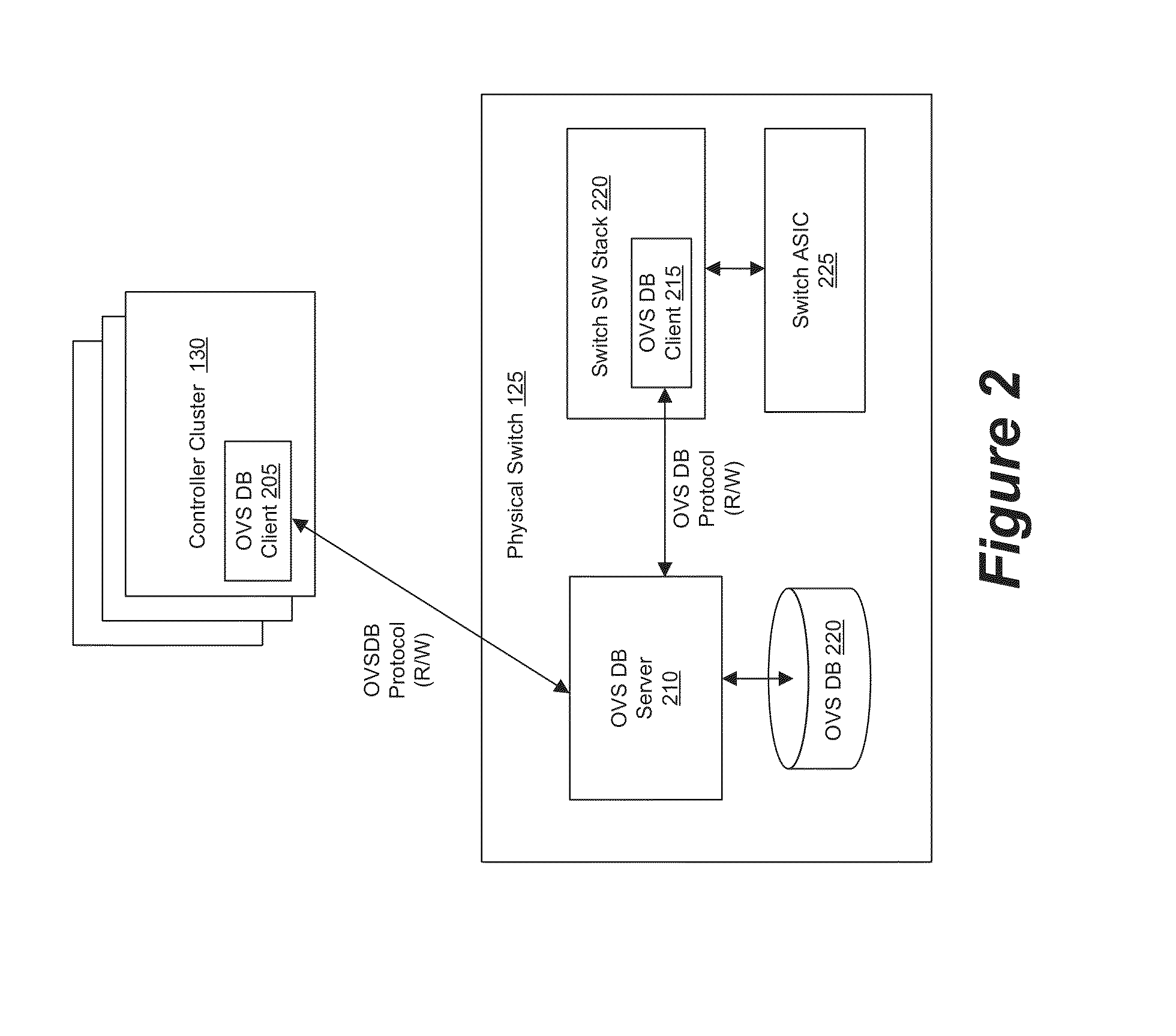
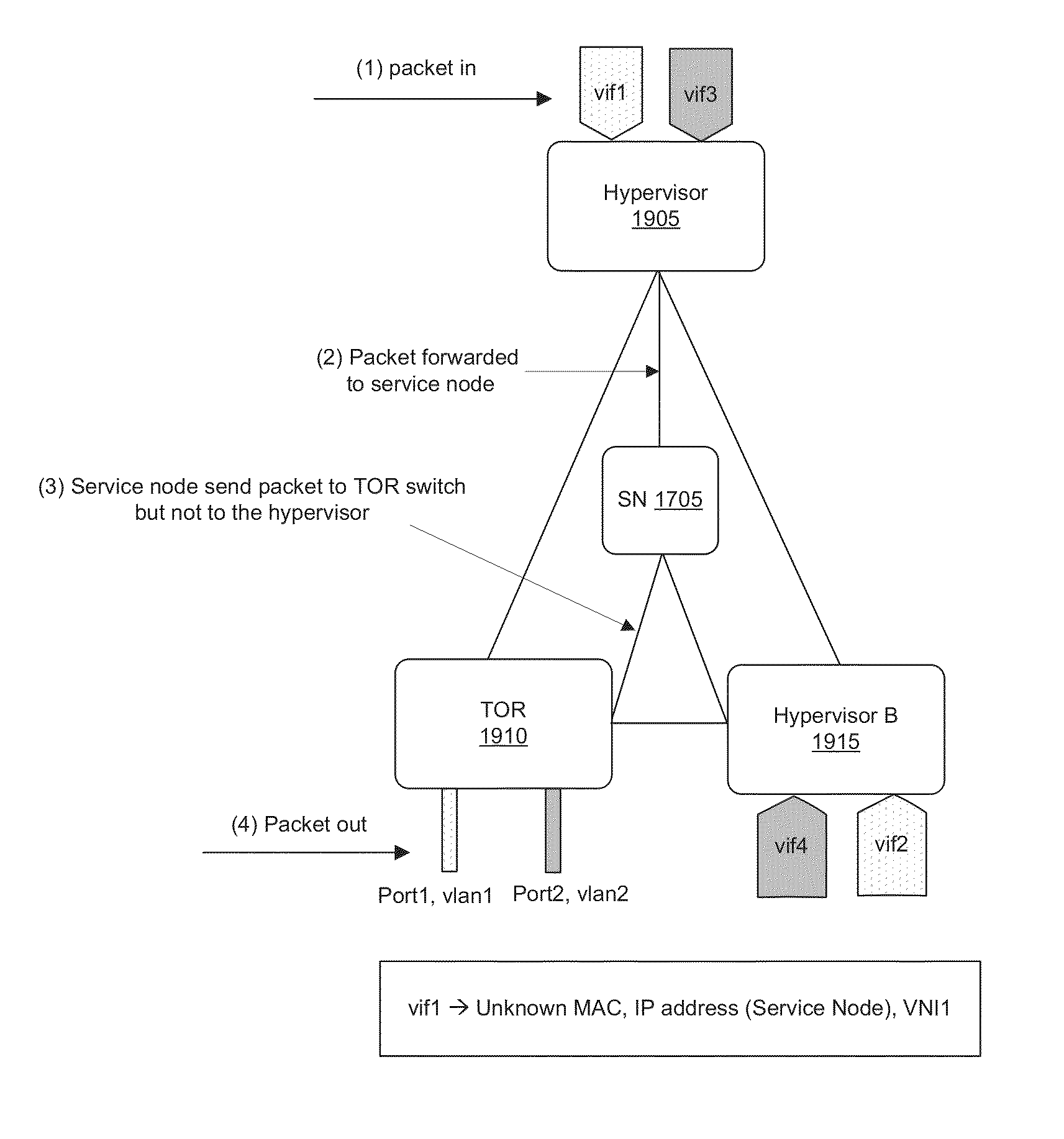
Some embodiments provide a set of one or more network controllers that communicates with a wide range of devices, ranging from switches to appliances such as firewalls, load balancers, etc. The set of network controllers communicates with such devices to connect them to its managed virtual networks. The set of network controllers can define each virtual network through software switches and / or software appliances. To extend the control beyond software network elements, some embodiments implement a database server on each dedicated hardware. The set of network controllers accesses the database server to send management data. The hardware then translates the management data to connect to a managed virtual network.
Owner:NICIRA
Method, Device, and Routing System for Data Transmission of Network Virtualization
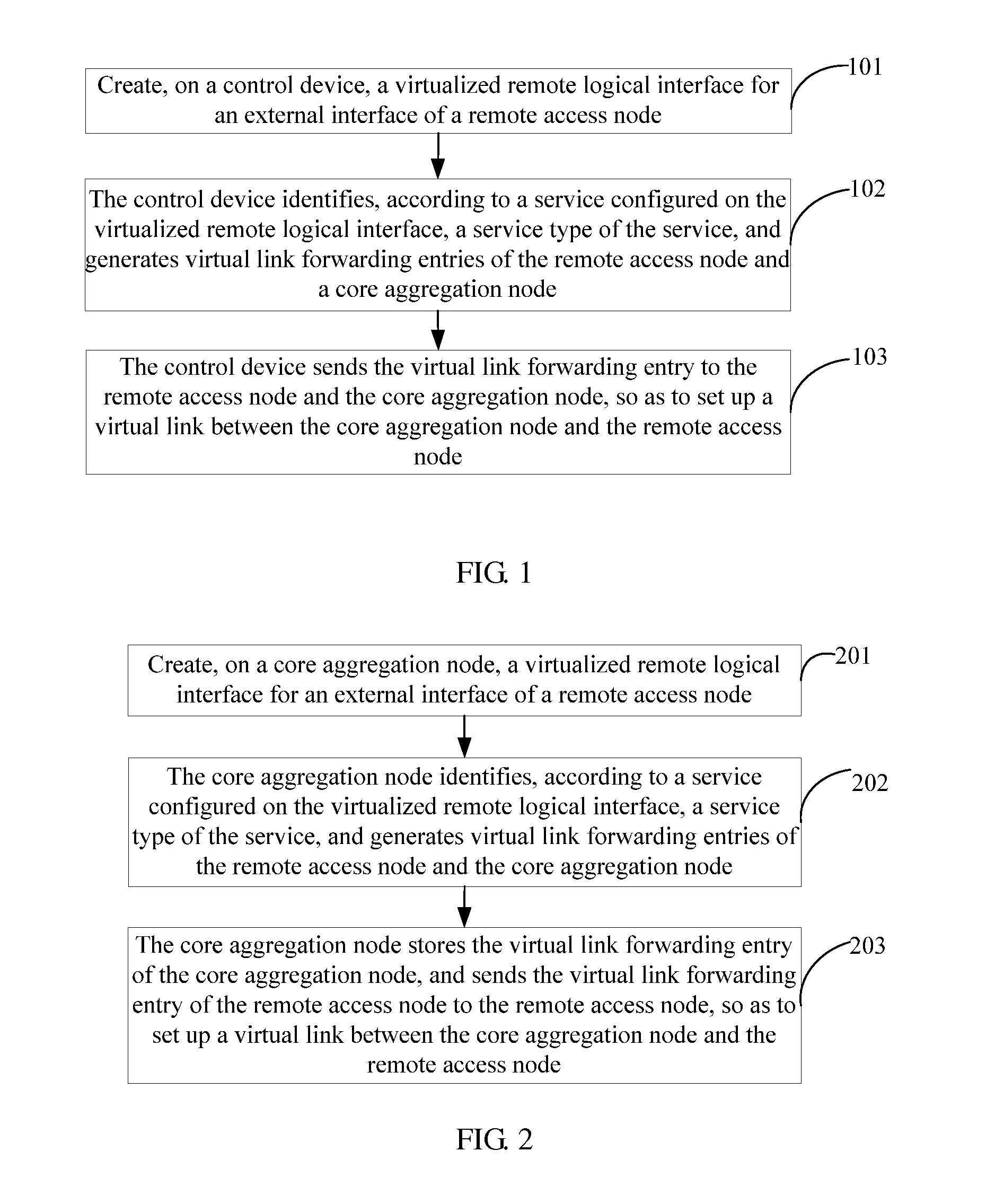
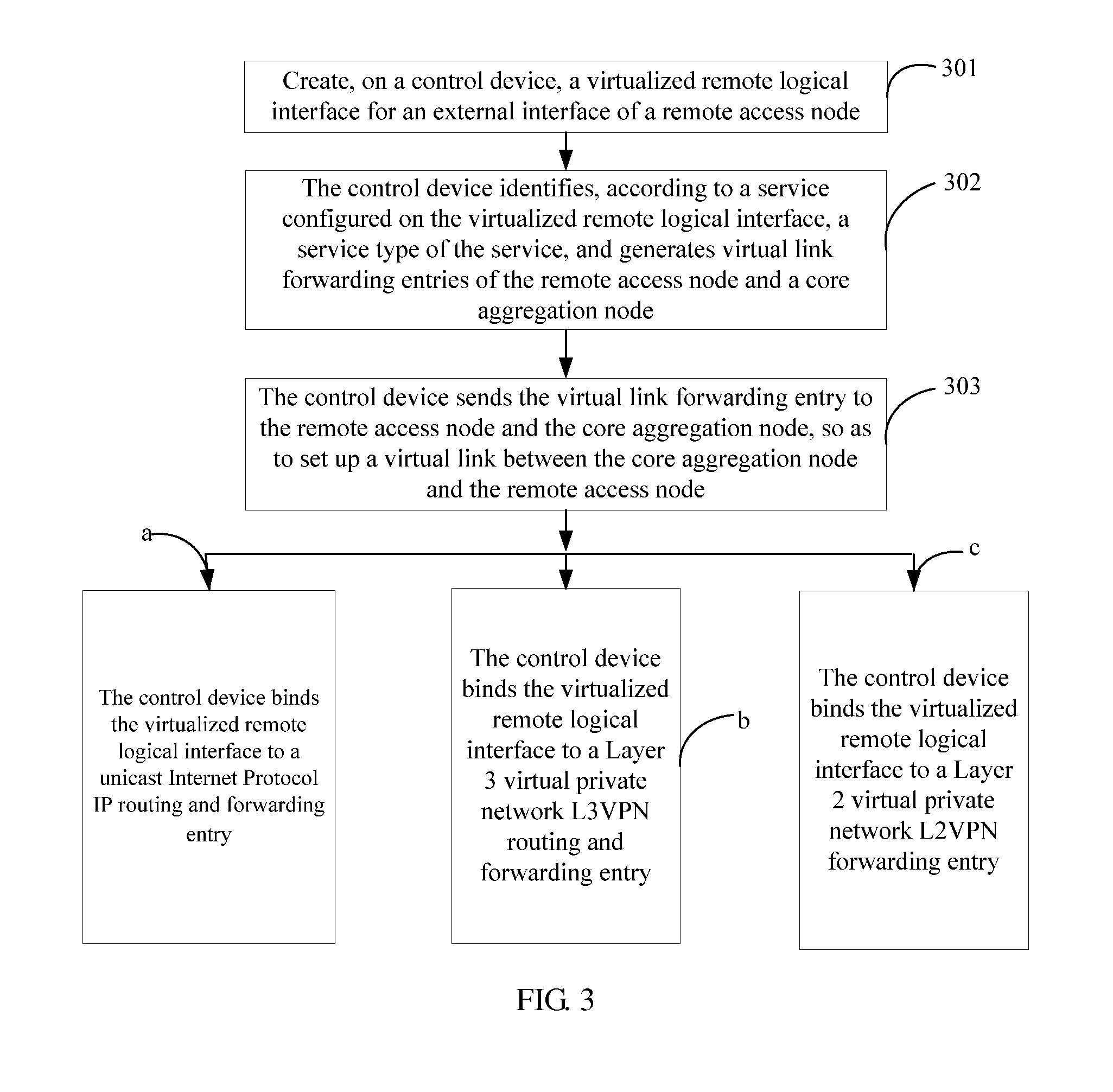
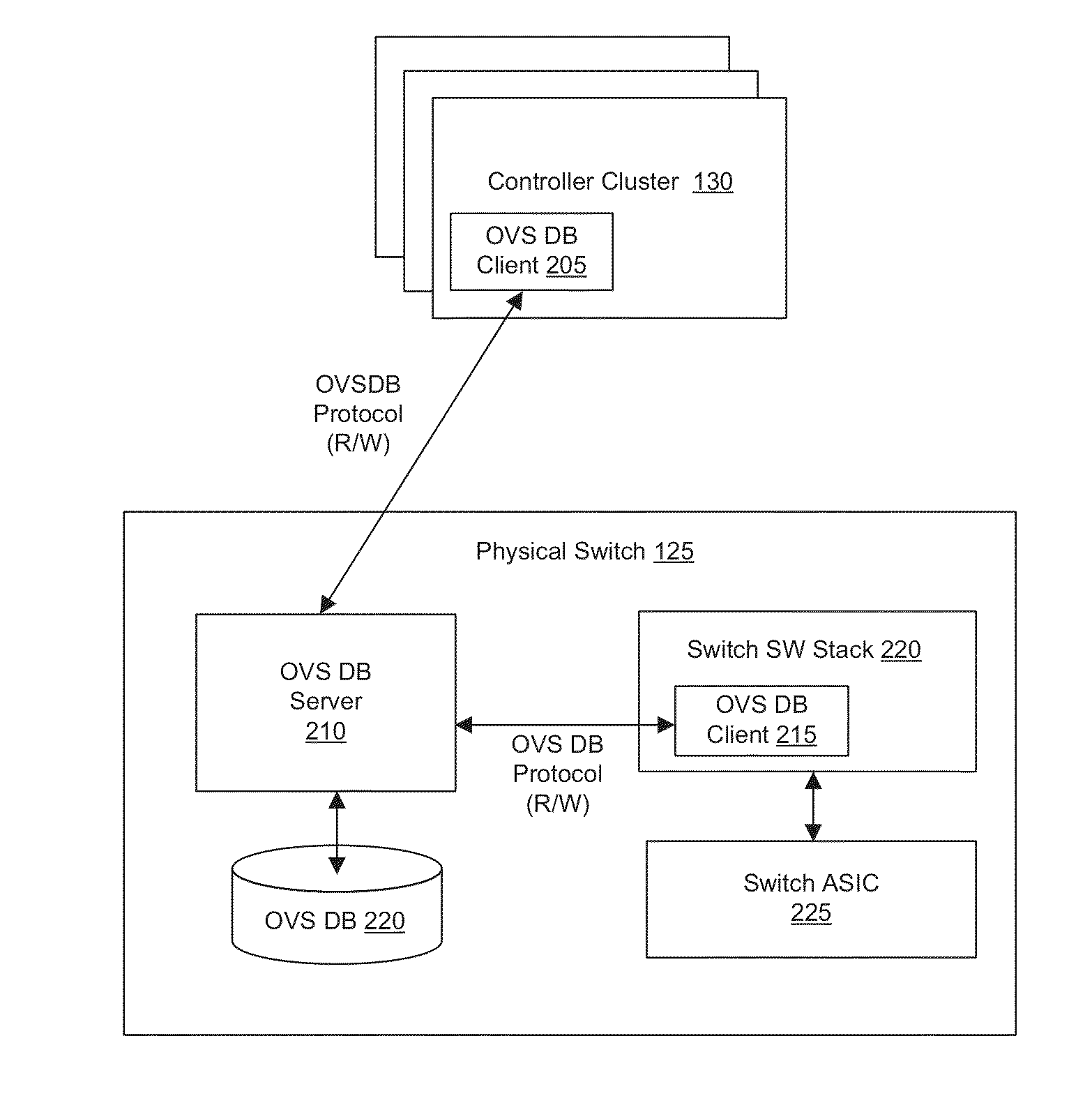
A method resolves connectivity of services inside a network virtualization system when a virtual cluster system supports unicast IP, L2VPN, and L3VPN services, so that the software network virtualization system can support various types of services efficiently and with high quality. The method includes: creating, on a control device, a virtualized remote logical interface for an external interface of a remote access node; identifying, by the control device according to a service configured on the virtualized remote logical interface, a service type of the service, and generating virtual link forwarding entries of the remote access node and a core aggregation node; and sending, by the control device, the virtual link forwarding entry to the remote access node and the core aggregation node, so as to set up a virtual link between the core aggregation node and the remote access node.
Owner:HUAWEI TECH CO LTD
Network Controller for Managing Software and Hardware Forwarding Elements
InactiveUS20150100560A1Easy to implementMaintain reliabilityDigital data information retrievalDigital data processing detailsSoftware networkDatabase server
Some embodiments provide a set of one or more network controllers that communicates with a wide range of devices, ranging from switches to appliances such as firewalls, load balancers, etc. The set of network controllers communicates with such devices to connect them to its managed virtual networks. The set of network controllers can define each virtual network through software switches and / or software appliances. To extend the control beyond software network elements, some embodiments implement a database server on each dedicated hardware. The set of network controllers accesses the database server to send management data. The hardware then translates the management data to connect to a managed virtual network.
Owner:NICIRA
Multi-feature mobile terminal malicious software detecting method based on network flow and multi-feature mobile terminal malicious software detecting system based on network flow
ActiveCN105022960AMeet individual needsImprove accuracyPlatform integrity maintainancePersonalizationCharacteristic type
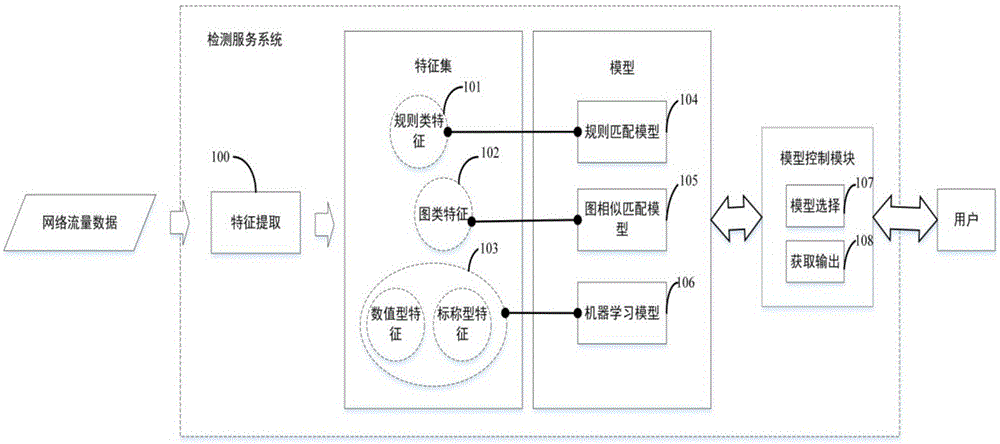
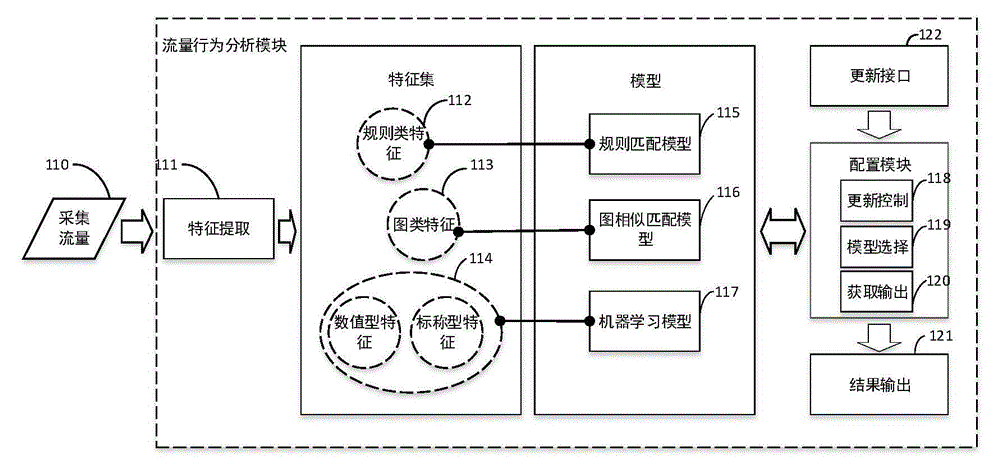
The invention discloses a multi-feature mobile terminal malicious software detecting method based on network flow and a multi-feature mobile terminal malicious software detecting system based on the network flow. The method comprises the following steps of: extracting features capable of effectively representing mobile terminal malicious software network behaviors from network flow data; classifying the extracted features capable of effectively representing the mobile terminal malicious software network behaviors according to different feature types; building detecting models adapting to the classified features, wherein each kind of types has one corresponding unique detecting model; and selecting the corresponding detecting model for each kind of features, and outputting the corresponding detecting result. By aiming at different feature types of the mobile terminal network flow, the detecting models adapting to different feature types are designed; a user can select the required model by the self according to requirements; the detecting accuracy can be improved to a certain degree through different detecting models designed by aiming at different feature types; and the individualized requirements of the user are met.
Owner:UNIV OF JINAN
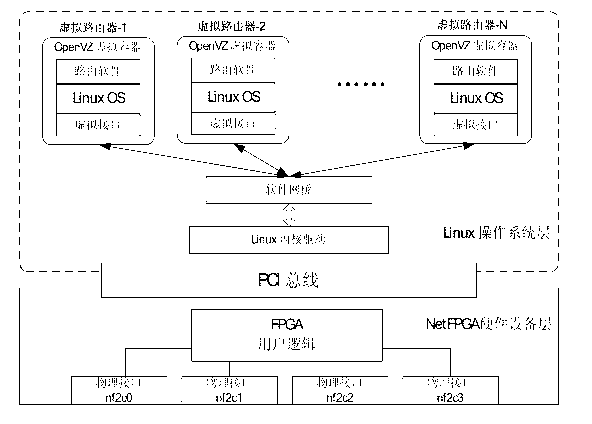
Communication method of programmable virtualized router based on NetFPGA
The invention discloses a communication method of a programmable virtualized router based on NetFPGA. The communication method comprises the steps that virtualized software is installed on a host to acquire a plurality of virtualized containers, and routing protocol software is installed in each virtualized container to acquire a virtualized router; virtualized ethernet cards are set up inside each virtualized router, wherein the number of the virtualized ethernet cards is equal to the number of hardware network interfaces of bottom-layer NetFPGA; a software network bridge is arranged to bridge between the virtualized ethernet cards and the physical hardware network interfaces, each virtualized router receives a data package from a NetFPGA board card network interface through the virtualized ethernet cards and the software network bridge, routing information is acquired through the treatment of each virtualized router, the routing information is transmitted to a register of the NetFPGA through the virtualized ethernet cards and the software network bridge, and then the retransmission of the data package is achieved through the NetFPGA board card network interface and an outside network. Network communication of a plurality of programmable virtualized routers can be achieved through the software network bridge.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
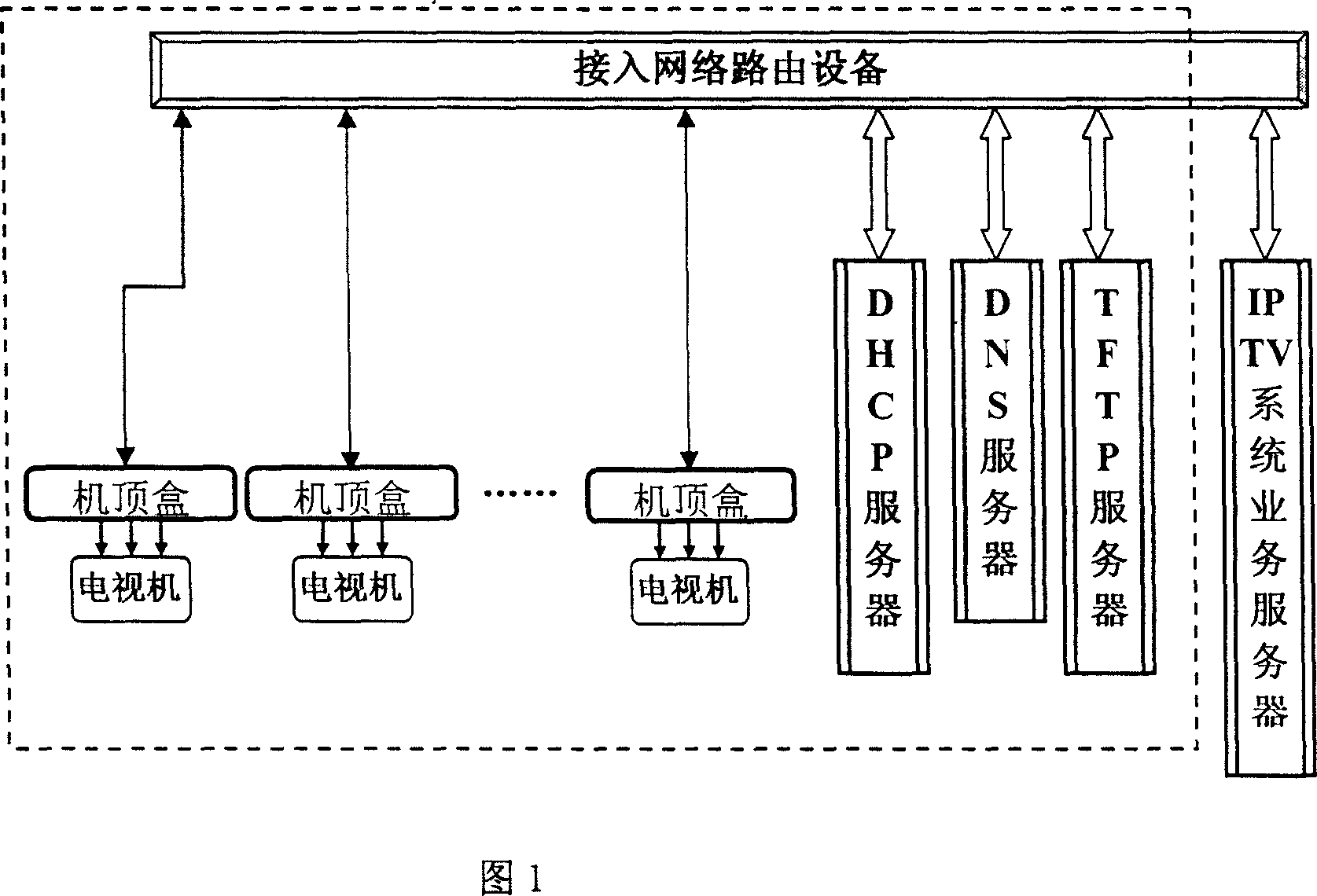
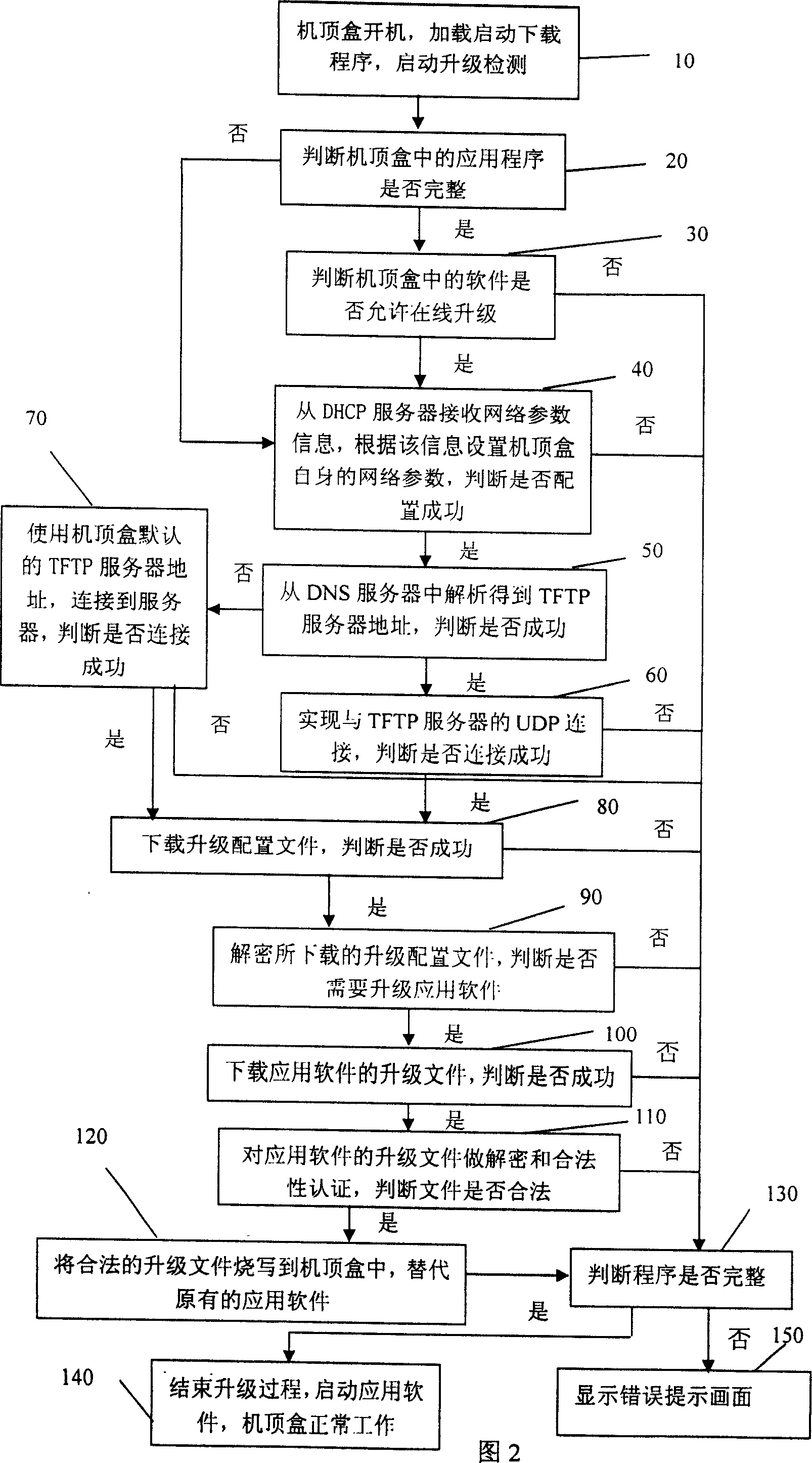
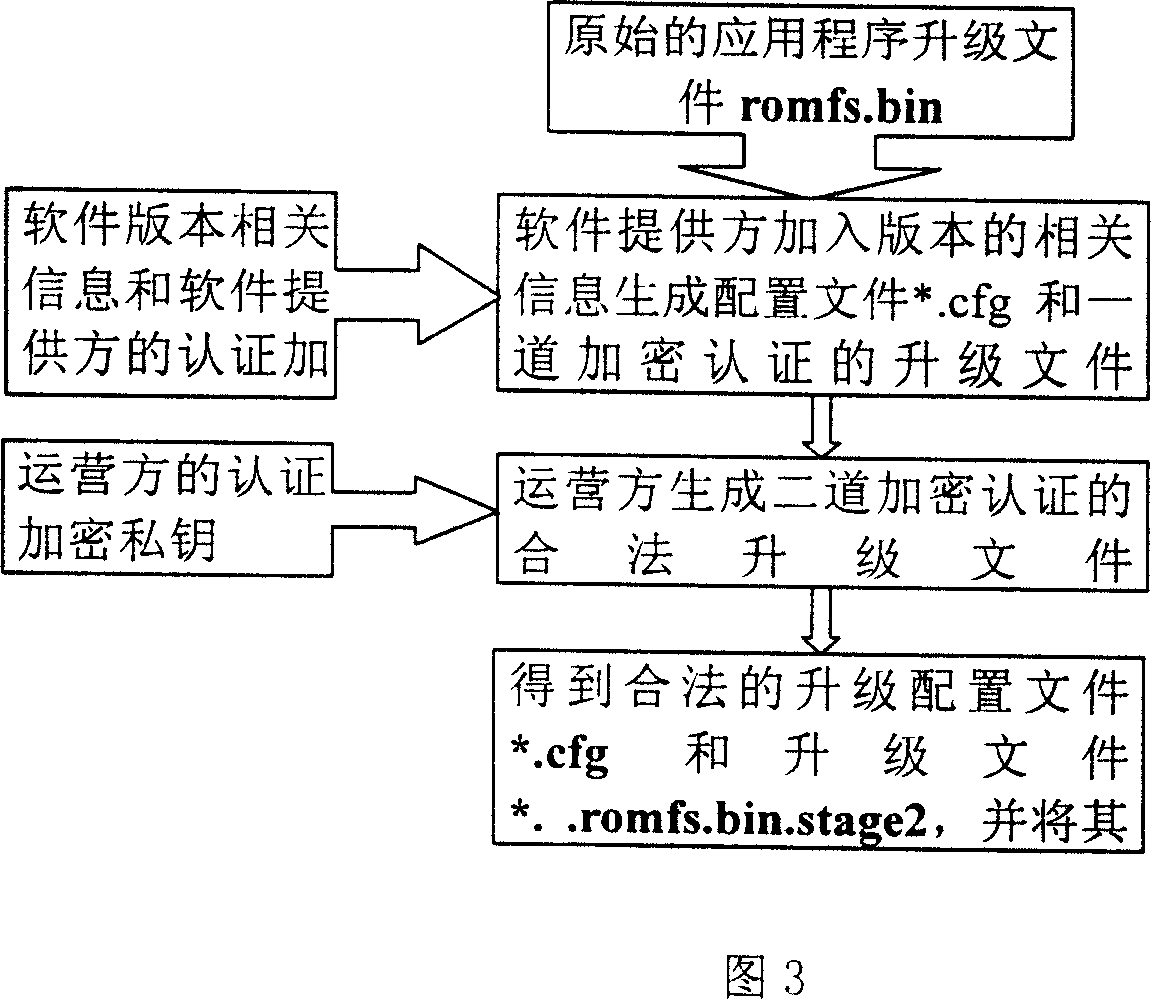
A network upgrade method of the TFTP-based IPTV STB software
InactiveCN101009764AExtend the life cycleEasy to upgradeTelevision system detailsPulse modulation television signal transmissionOperational costsSoftware network
The disclosed network upgrading method for IPTV set-top box (STB) software based on TFTP comprises: during loading Boot Loader, selected downloading the upgrade program through TFTP server-client mode; after identifying validity, automatic upgrading the STB. This invention can prolong the service time of STB, reduces system cost, and provides better service for user.
Owner:INST OF ACOUSTICS CHINESE ACAD OF SCI
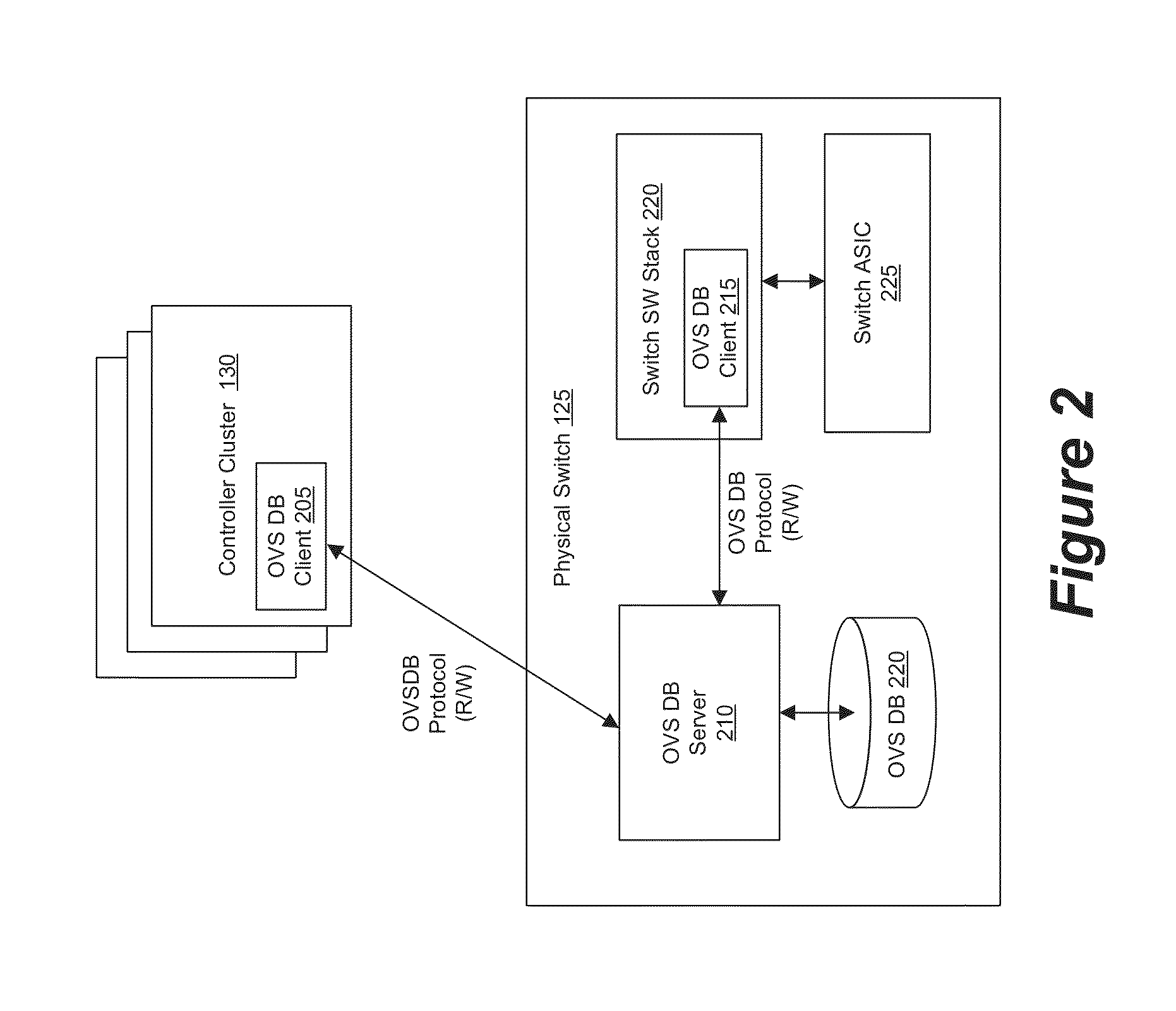
Database Protocol for Exchanging Forwarding State with Hardware Switches
ActiveUS20150100675A1Maintain reliabilityEasy to implementDigital computer detailsNetworks interconnectionSoftware networkDatabase server
Some embodiments provide a set of one or more network controllers that communicates with a wide range of devices, ranging from switches to appliances such as firewalls, load balancers, etc. The set of network controllers communicates with such devices to connect them to its managed virtual networks. The set of network controllers can define each virtual network through software switches and / or software appliances. To extend the control beyond software network elements, some embodiments implement a database server on each dedicated hardware. The set of network controllers accesses the database server to send management data. The hardware then translates the management data to connect to a managed virtual network.
Owner:NICIRA
Managing software and hardware forwarding elements to define virtual networks
ActiveUS9455901B2Maintain reliabilityEasy to implementNetworks interconnectionSoftware simulation/interpretation/emulationComputer hardwareSoftware network
Owner:NICIRA
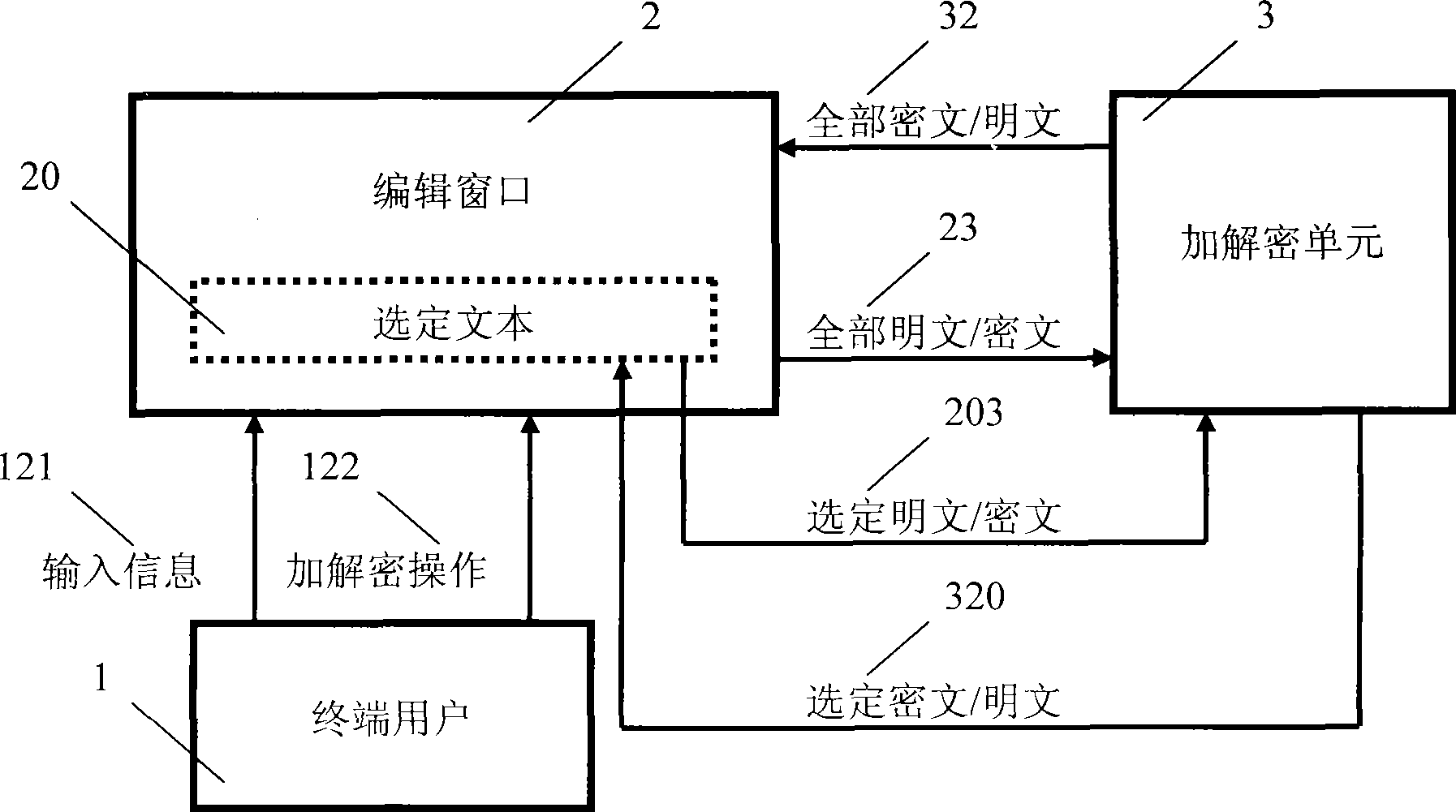
An information security method and procedure
An information security method and procedure relates to the field of computer software, network communications and information security technology, especially used for information security of instant messaging, e-mail and other edited texts. By cipher algorithm procedure and / or by cipher device hardware, complete or selective instant encrypt or instant decipher is performed to text message in the current editing text, so as to instantly replace it from plaintext to ciphertext or from ciphertext to plaintext and present in the same window; when the cursor is stopped at the read-only ciphertext, it can be instant read and the corresponding plaintext can be presented; furthermore, it can be driven by a same shortcut operation, so that the encryption and decryption can be alternately performed, plaintext and ciphertext can be alternately replaced and displayed; a practical information security program is also designed, which is used in synergy with the object program and runs independently, to realize real-time encryption and decryption to information. The invention is general-purpose, convenient, flexible and efficient, and has universality because of its informality in the device hardware and no limitation to the application software.
Owner:杨筑平
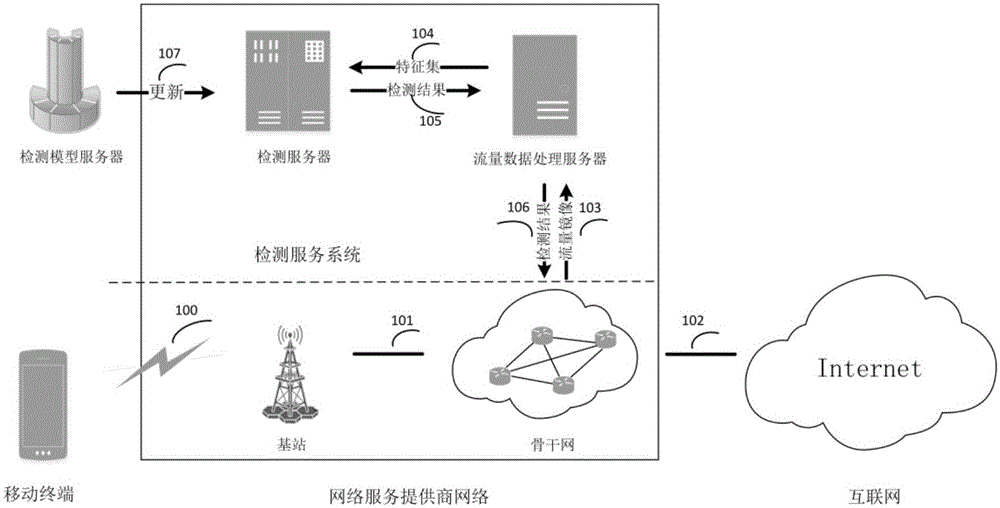
Malicious software network behavior detection method specific to network service provider and system thereof
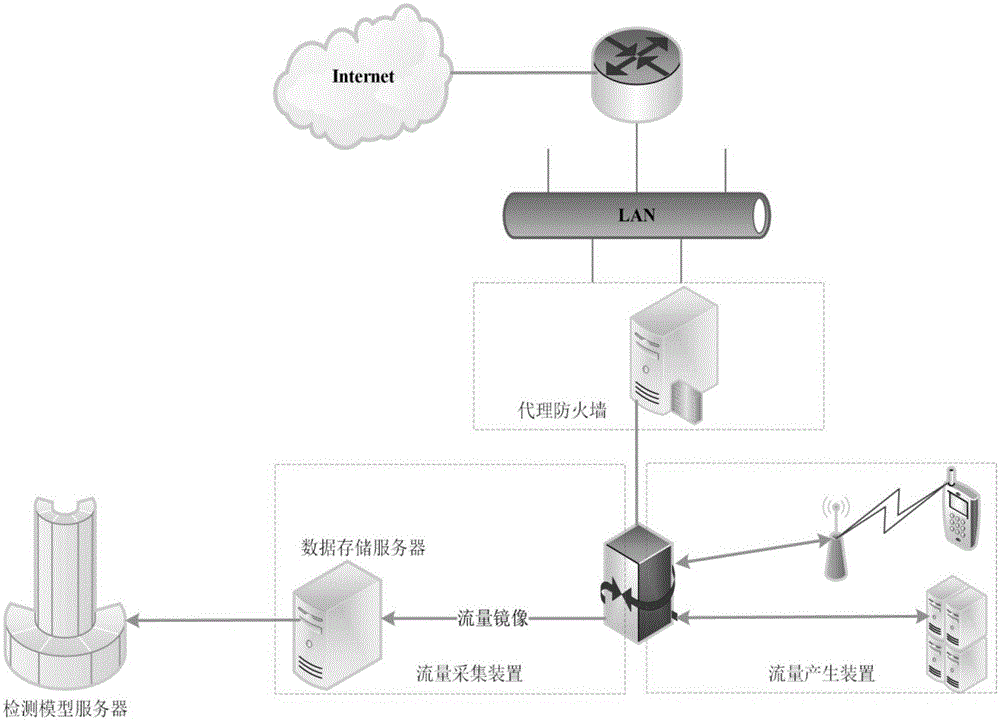
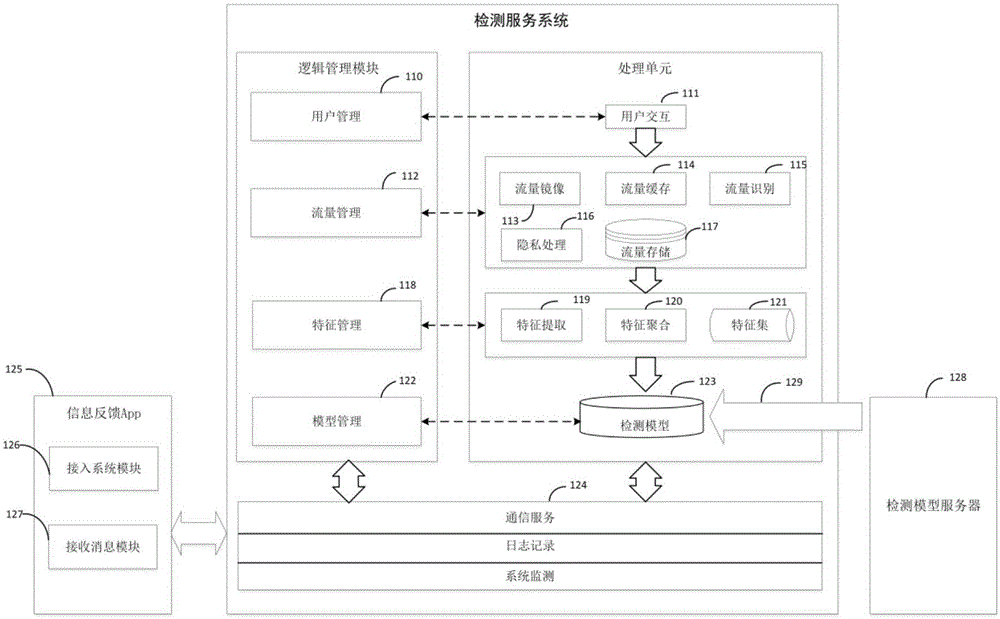
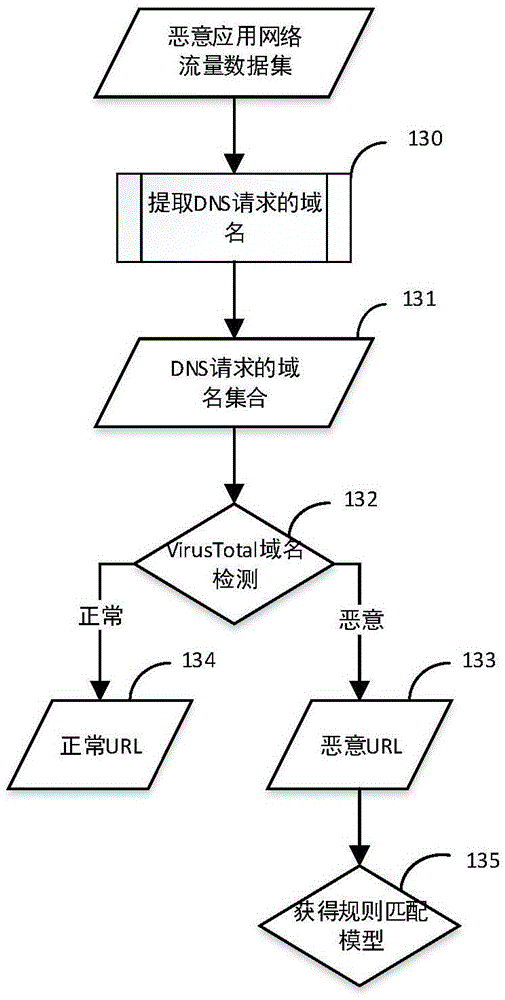
The invention discloses a malicious software network behavior detection method specific to a network service provider and a system thereof. The method comprises: a user mobile terminal is connected with a backbone network of a network service provider by a base station of the network service provider and the backbone network of the network service provider is connected with an internet network; when being connected to the internet network, the user mobile terminal applies to a detection server for authentication; after authentication processing, collection is carried out by a dynamic distribution flow mirror image port and the network flow of the user mobile terminal is cached to a flow data processing server, identification and privacy protection processing is carried out on the obtained network flow of the user mobile terminal, network flow data features are extracted and aggregated to form a feature set, and the feature set is transmitted to the detection server; the feature set is read and a detection model in the detection server detects features in the feature set; and detection results are returned to the backbone network of the network service provider by the flow data processing server and then are returned to the user mobile terminal finally.
Owner:UNIV OF JINAN
System and method of semi-autonomous multimedia presentation creation, recording, display, network streaming, website addition, and playback.
InactiveUS20120300080A1Eliminate needDigital data information retrievalElectronic editing digitised analogue information signalsComputer hardwareSoftware system
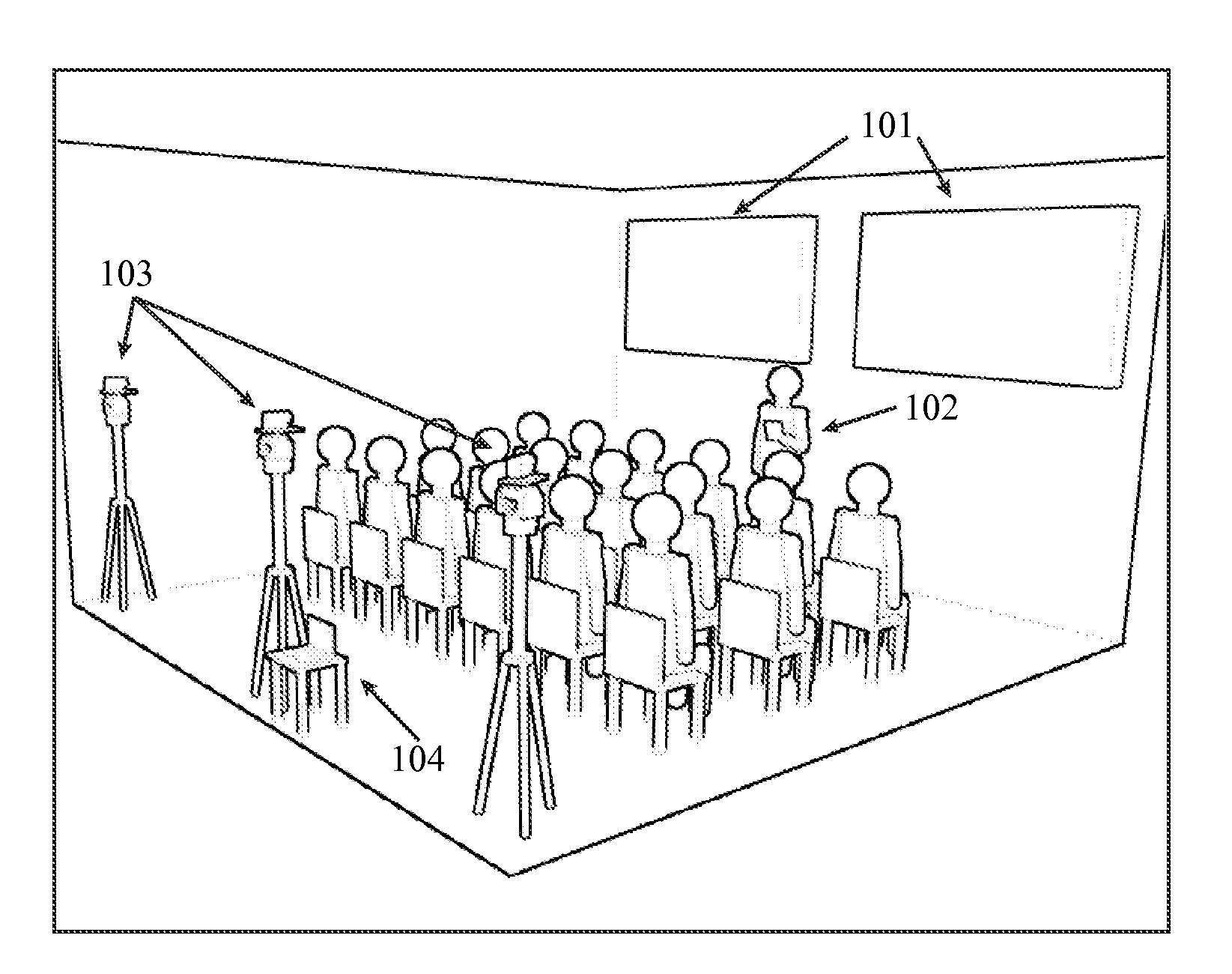
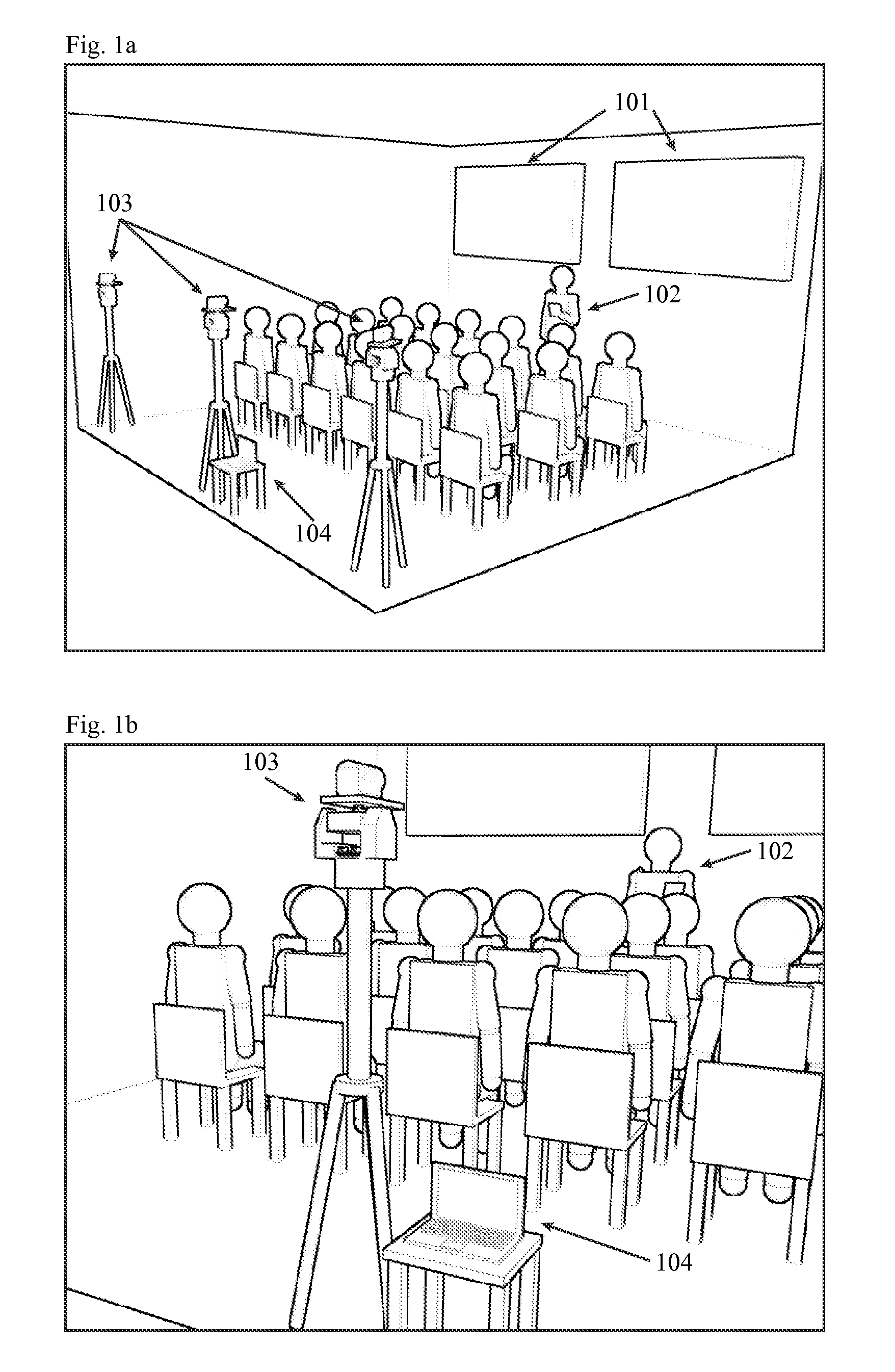
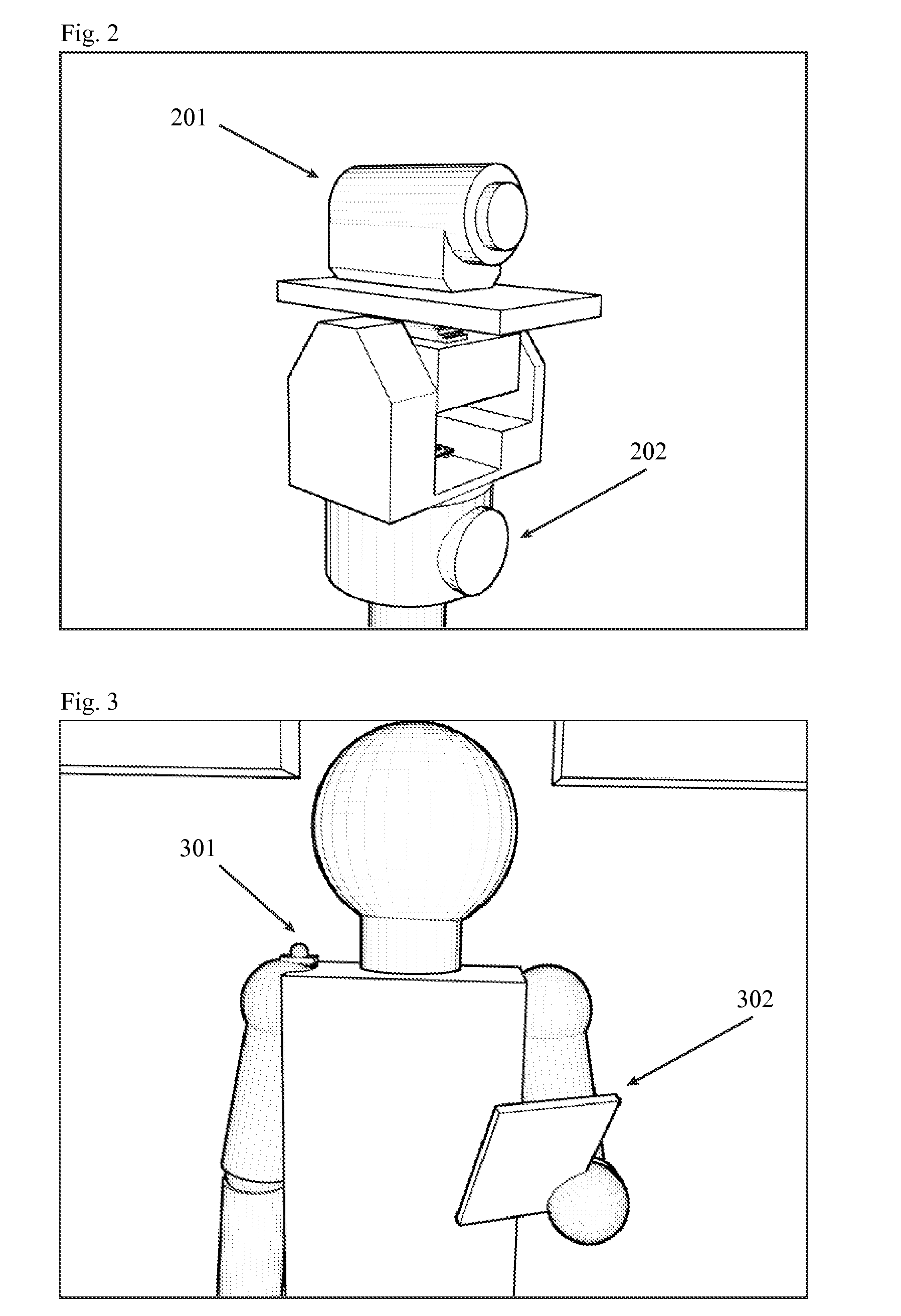
The invention disclosed is a software and hardware system that allows complex multimedia presentations to be created, performed, recorded, streamed over a network, and automatically added to a website, without the need of human input other than that of the presenter. It is the first system to combine the following technologies into a single system of interdependent hardware and software: presentation creation software, network communication, media syncing, multiple remotely controlled motorized camera apparatuses, motion tracking, voice recognition, media projection software, recording and streaming of both live and recorded media, and automated website management.
Owner:BATSON STEVEN GEORGE
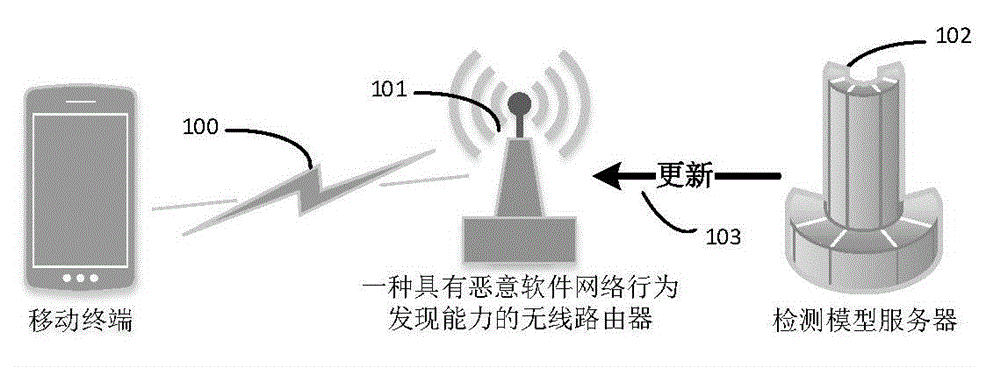
Method and system for performing malicious software network behavior detection based on access router
The invention discloses a method and system for performing malicious software network behavior detection based on an access router. The method comprises the following steps that: a wireless router identifies an accessing mobile terminal, agrees to a networking request of the accessing mobile terminal, starts to capture flow generated by networking of the mobile terminal, transmits the acquired network flow into a flow behavior analysis module, and performs flow-based security detection; a detection model server establishes a detection model through flow data, and stores the detection model; the detection model server periodically updates the flow behavior analysis module accessing the router to enhance security protection of the access router; and the wireless router selects a required detection model, and the detection model starts to process input flow data and outputs a detection result. Through adoption of the method and the system, the problem of high resource consumption of the mobile terminal due to installation of detection programs in the mobile terminal by a user is solved. Meanwhile, the problem of large-scale deployment in actual use is solved.
Owner:UNIV OF JINAN
Distributed debugger environment
ActiveUS7634759B2Error detection/correctionSpecific program execution arrangementsSoftware networkNetwork on
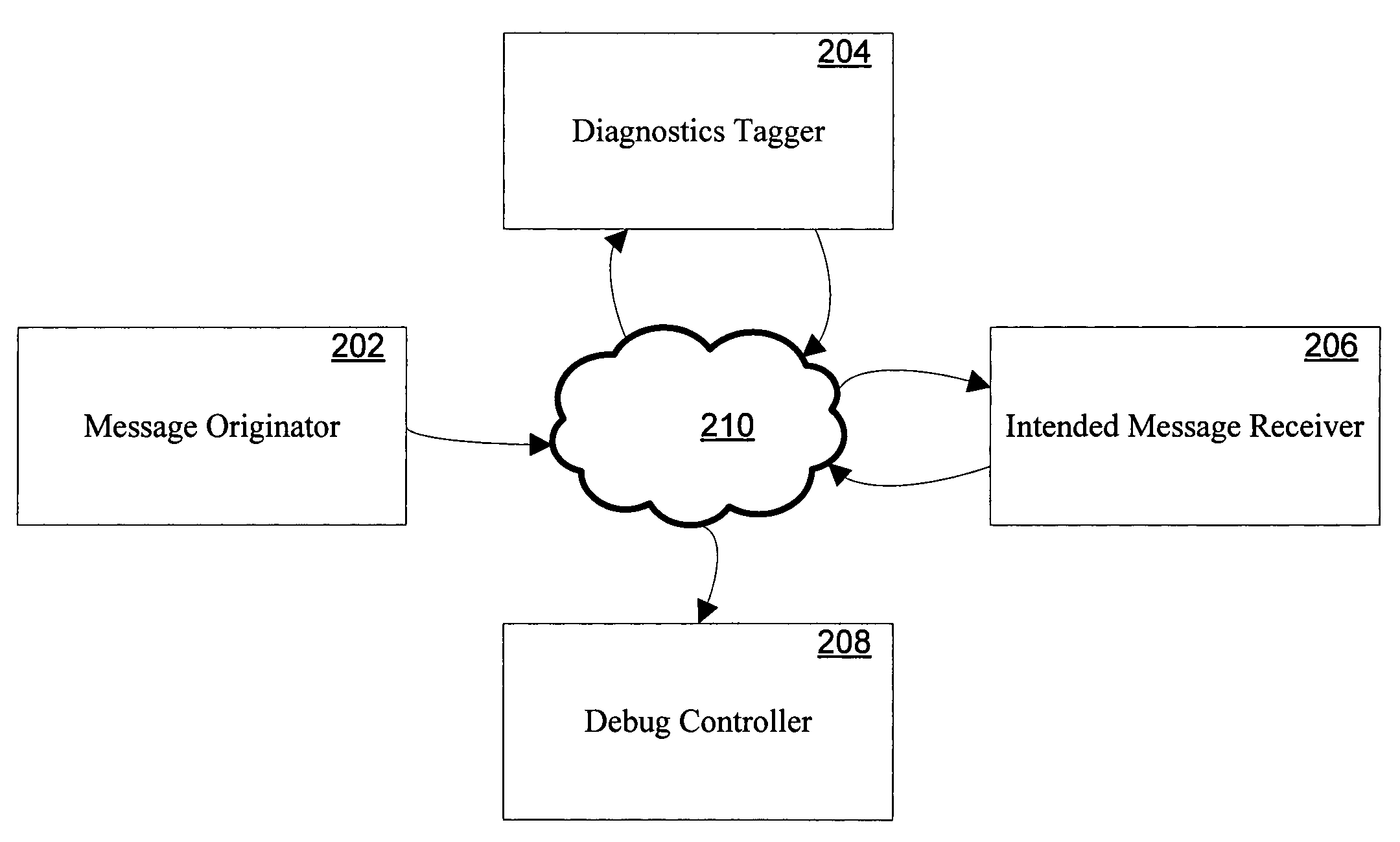
Systems and methods for providing distributed debugging in an extensible SOAP environment of asynchronous software web services are disclosed. Such a system may include a message originator, a diagnostics tagger, an intended message receiver, and a debug controller, which may communicate with one another via SOAP messages. The message originator originally puts the SOAP message onto the network. The diagnostics tagger modifies the SOAP message to include certain diagnostics elements that cause a breakpoint to be triggered. The intended message receiver eventually receives the message and is expected to trigger the breakpoint. The debug controller is a process that is called by the intended message receiver when a breakpoint is detected. The header of the SOAP message may include a security element and a diagnostics element. The diagnostics element may include one or more breakpoint elements. Each breakpoint element may include a debugging controller element, and one or more condition elements. Each condition element may include a logical expression. The intended message receiver determines whether the conditions are met. If the conditions are met, then the breakpoint is triggered.
Owner:MICROSOFT TECH LICENSING LLC
Exposing a bridged network as a single virtual segment
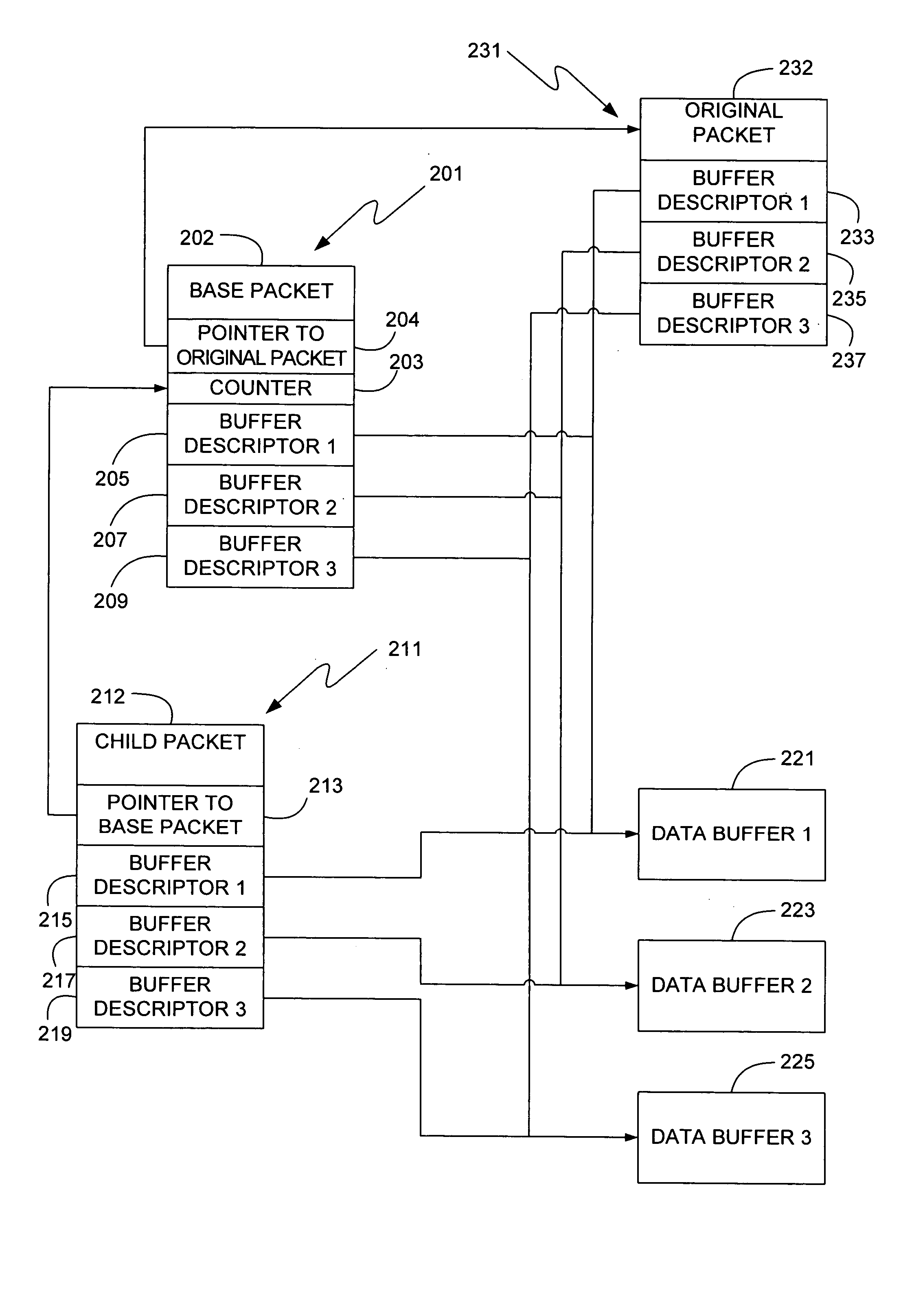
InactiveUS20060010265A1Large and expensive to copyData efficientData switching networksSecuring communicationSoftware networkNetwork packet
A software network bridge is disclosed which allows the connected network segments to be presented as a single network unit to the host computer. The software bridge can be implemented as an intermediate network driver, abstracting multiple network segments into a single network interface for higher level protocols and applications. While the intermediate network driver acts as a software bridge implementing the Spanning Tree Algorithm, it also acts a network interface driver to higher level protocols, conglomerating information from the multiple underlying network interface cards and forwarding along commands from the higher level software to the appropriate network interface card. The intermediate network driver can also simultaneously send the same data packet through multiple network interfaces by creating multiple packet descriptors, each pointing to the same data, but each given individually to the underlying network interfaces to control during their transmission. Further efficiencies can also be achieved by the software bridge, implemented as an intermediate network driver, through the use of a dynamic allocation scheme which increases the size of the useable buffers of each network interface without increasing the overall memory consumption, and the use of a queuing scheme which preliminarily examines incoming data packets to determine if any processing needs to be performed, and queues the packets should they require processing. Additionally, a user interface is presented exposing this functionality of the intermediate network driver.
Owner:MICROSOFT TECH LICENSING LLC
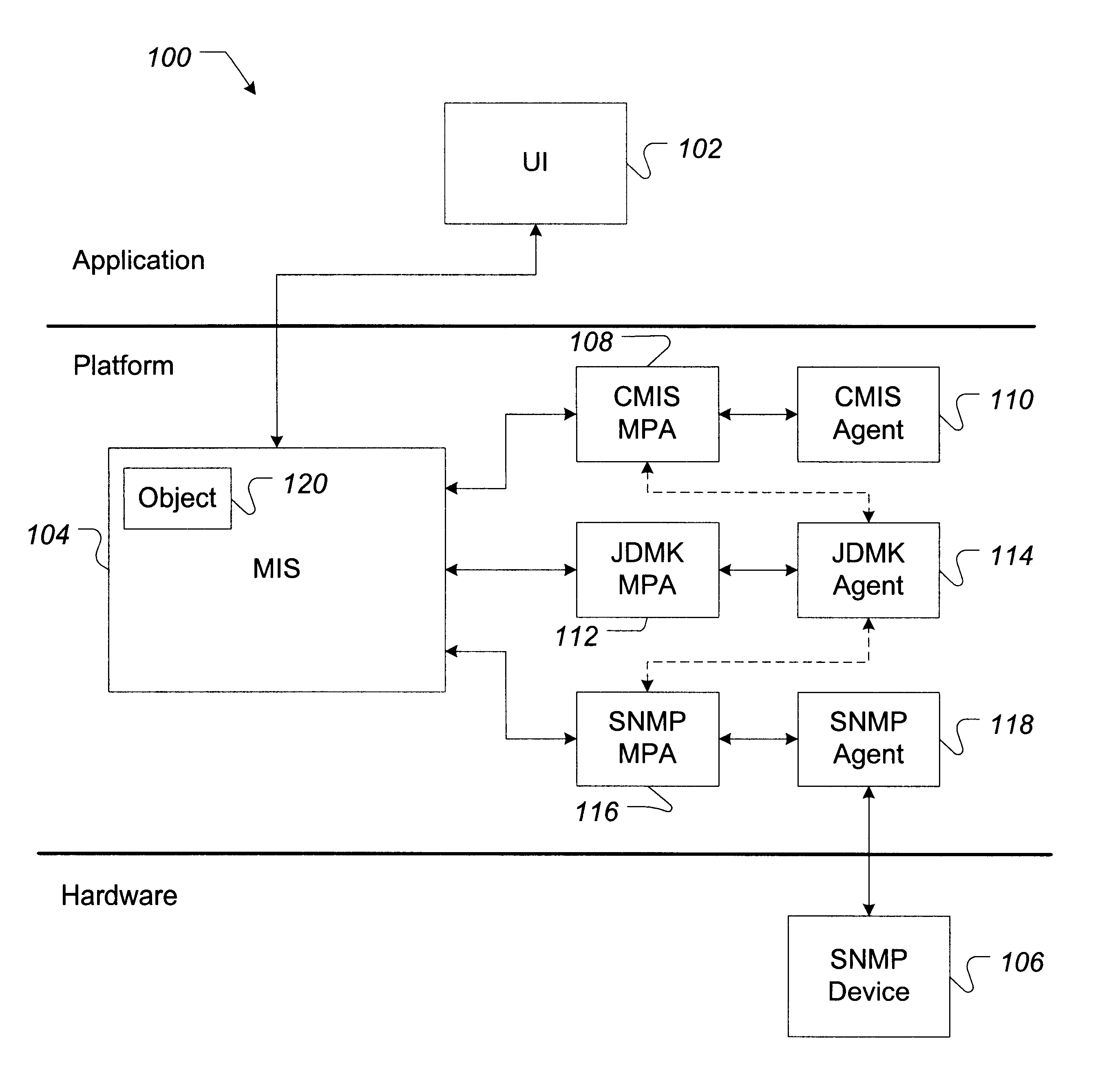
System and method for implementing Java-based software network management objects
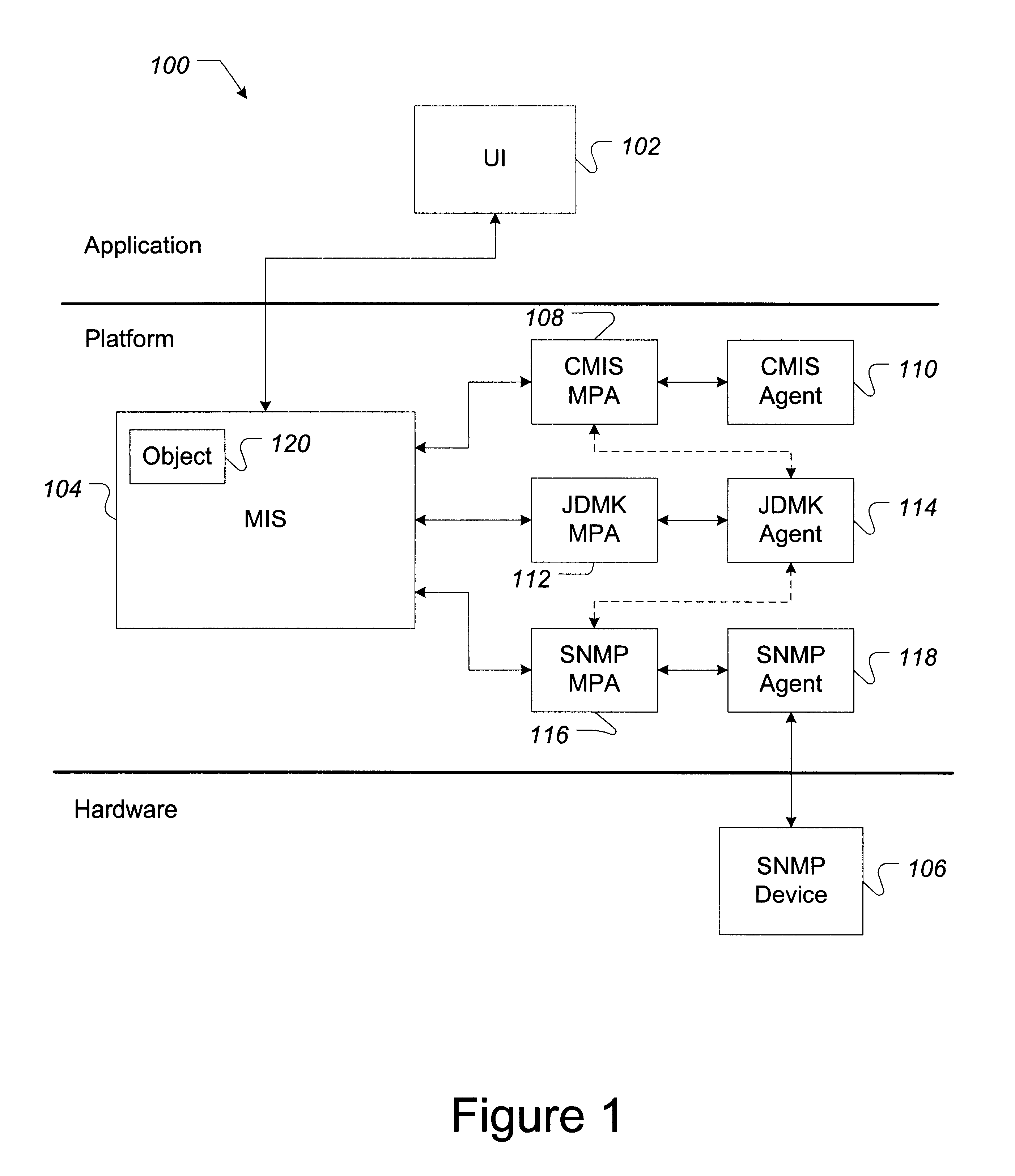
InactiveUS6427153B2Easy accessRapid development timeMultiple digital computer combinationsOffice automationSoftware networkManagement object
Software, systems, and methods for facilitating the development and implementation of computer network management software containing Java-based instructions is provided. In one aspect, the invention includes a system for implementing Java-based software network management objects configured to implement computer network management functions on a computer network. In one embodiment, the system of the invention includes a computer network management information server. The network management server performs communications using a first computer network management communications protocol. The system further includes a Java development management kit ("JDMK") methods protocol adapter ("MPA") that is configured to translate the first computer network management communications protocol into a JDMK communications protocol. A JDMK agent that is configured to communicate with the JDMK MPA using the JDMK communications protocol also is included.
Owner:ORACLE INT CORP
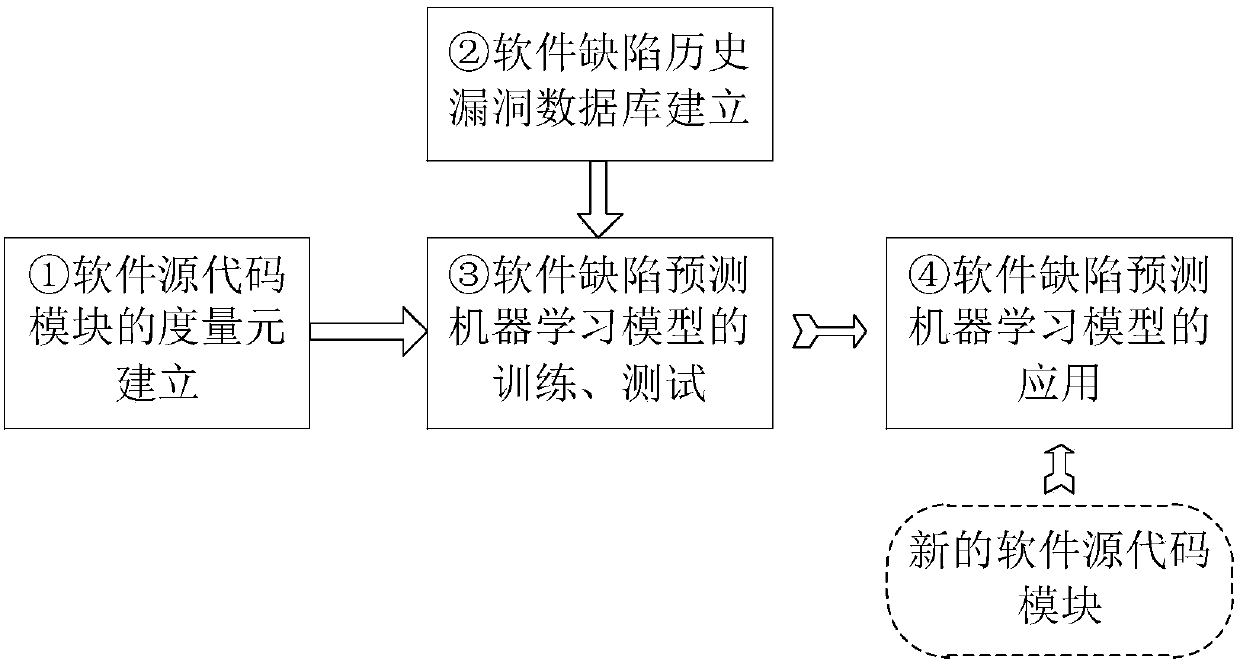
Fault prediction method based on software network feature learning
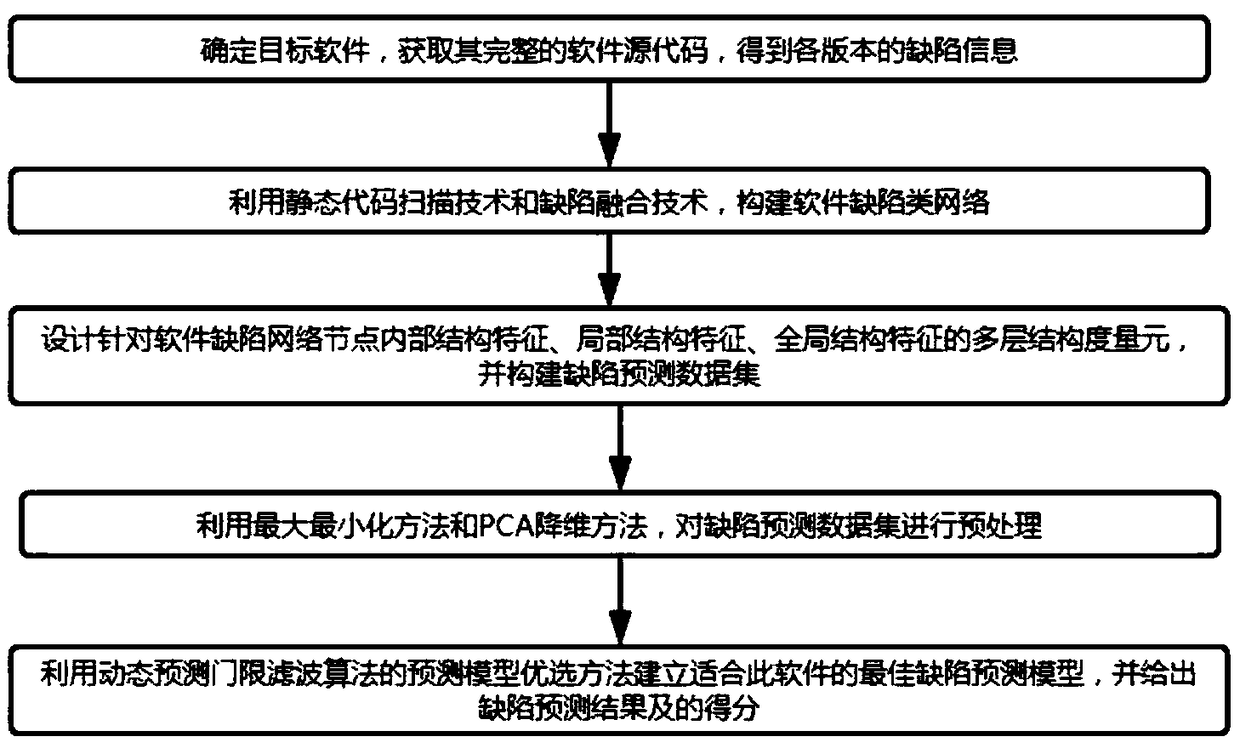
ActiveCN108664402AOptimize ThresholdReduce labor costsSoftware testing/debuggingSoftware networkData set
The invention discloses a fault prediction method based on software network feature learning, and belongs to the field of software complicated networks. The method comprises the steps that source codes and defect information of each version of target software are obtained to construct a software defect network; multi-layered structure metric elements aiming at internal features, local features andglobal features of software defect network nodes are designed to construct a defect prediction data set; preprocessing is conducted on a defect prediction data set by using a maximized minimum methodand a PCA dimensionality reduction method; the best defect prediction model suitable for the software is established by using prediction model preference method of a dynamic prediction threshold filtering algorithm, and defect prediction effects and scores are given. According to the method, a complicated network technology is introduced to the defect prediction, a set of matric elements capableof reflecting the local and global features of defects in the software is designed by using complicated network matric parameters, the most suitable defect prediction model of the target software canbe selected to perform defect and fault prediction on the target software, and manpower and time cost is reduced to the most extent.
Owner:BEIHANG UNIV
Defect high-risk module identification method based on software network
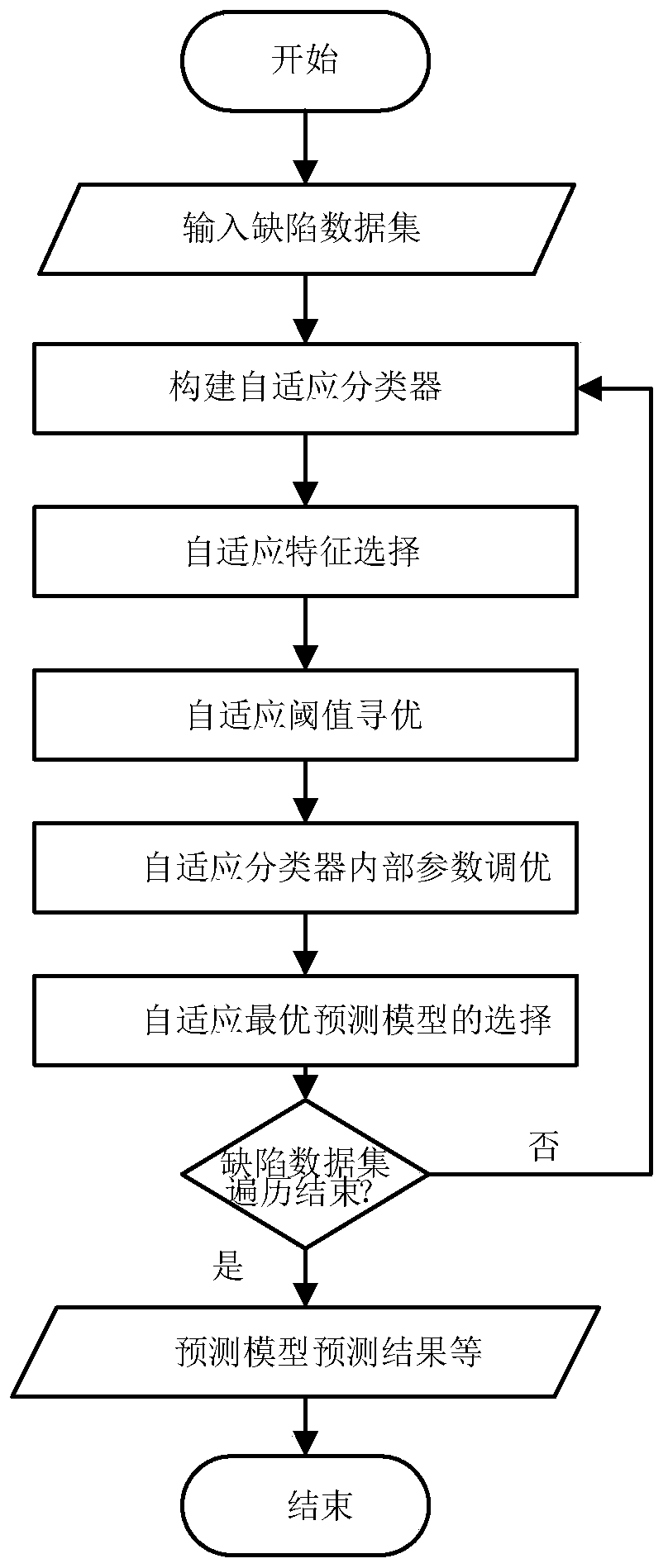
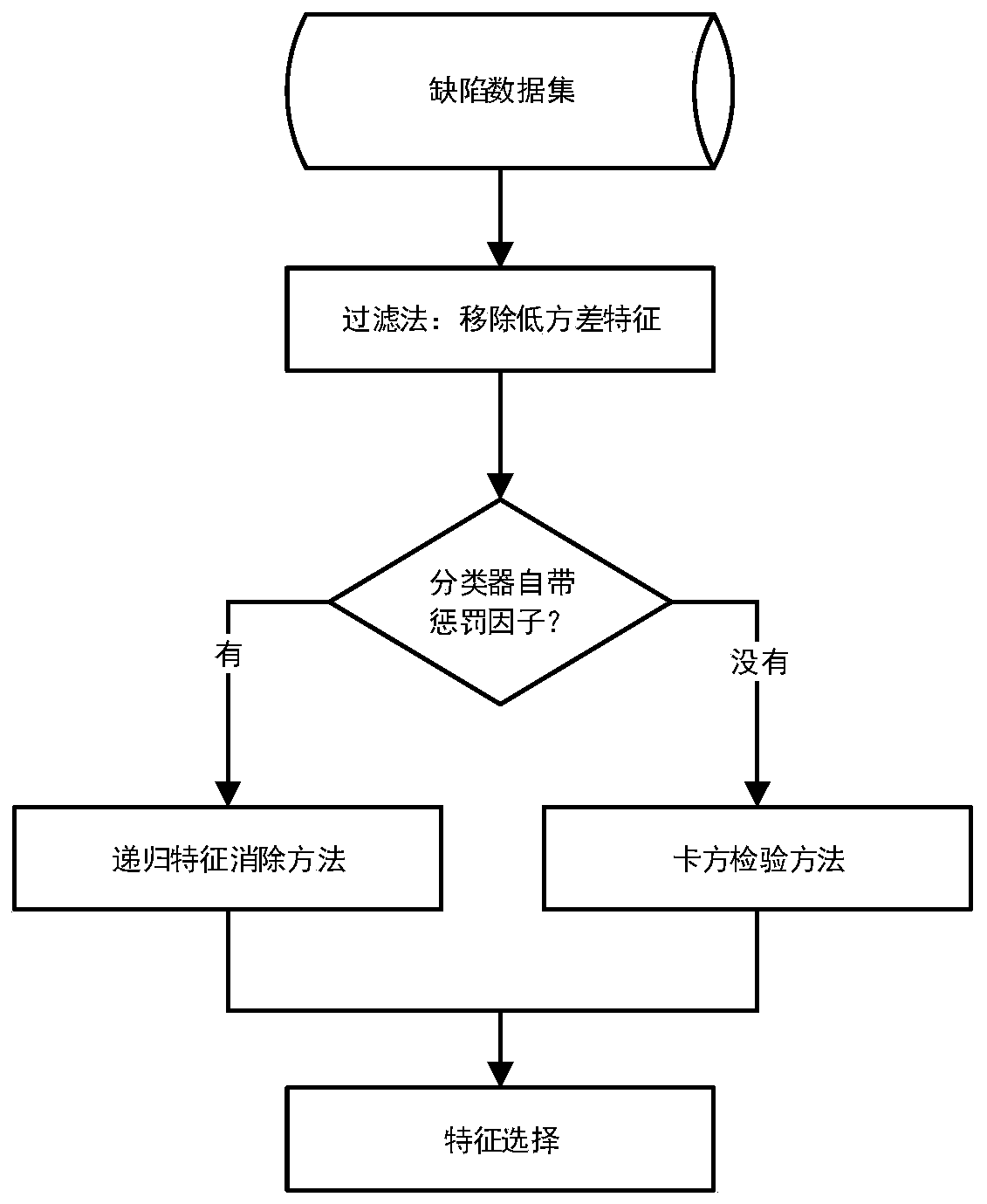
ActiveCN110147321AEasy to identifyReduce labor costsCharacter and pattern recognitionSoftware testing/debuggingData setSoftware network
The invention provides a defect high-risk module identification method based on a software network, and belongs to the field of software complex networks. The method comprises the steps that 1, constructing an adaptive classifier, whrein the adaptive classifier comprises a plurality of classifiers; step 2, performing adaptive feature selection; step 3, performing adaptive threshold optimization; step 4, optimizing the internal parameters of the adaptive classifier; and 5, selecting a self-adaptive optimal prediction model, and performing defect high-risk module identification on the to-be-tested software network by using the optimal prediction model. For any type of defect data set, contents in five aspects of construction of the self-adaptive classifier, self-adaptive feature selection, self-adaptive threshold optimization, self-adaptive classifier internal parameter tuning, selection of a self-adaptive optimal prediction model and the like can be completed according to the characteristics of a data set, the best defect prediction result is obtained, and a high-risk software module is identified.
Owner:BEIHANG UNIV
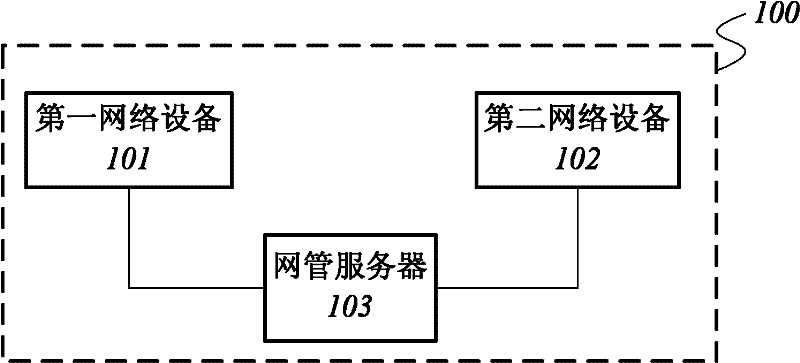
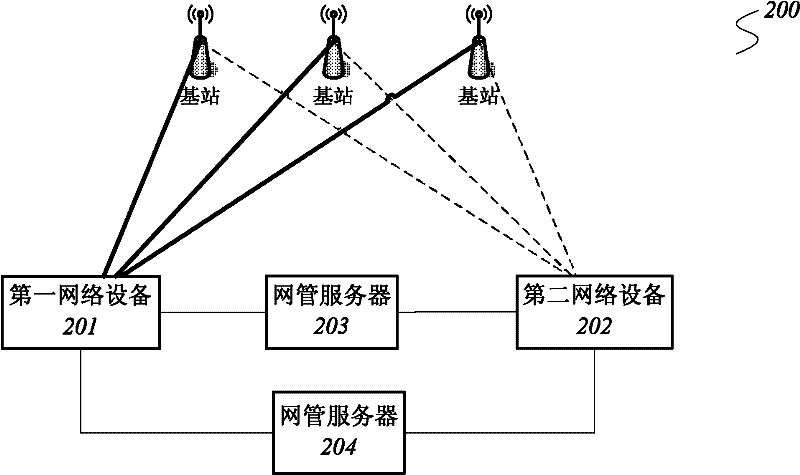
Communication system, switching method used in communication system and network management server
InactiveCN102281563AImprove reliabilityImprove disaster toleranceWireless communicationSoftware networkOperation mode
The present invention relates to a communication system, comprising: a first network device; a second network device having the same hardware configuration as the first network device; a first network management server, used to monitor the working status of the first network device and receive the first network device The working configuration information backed up by the device and transmit the working configuration information to the second network device; when the first network device reaches the preset failure condition, switch the second network device from the hot standby mode to the working mode, so that the second network device can use the working mode configuration information to operate. The invention also relates to a switching method and a network management server. The present invention is based on the fact that the network management server realizes the dual-computer hot standby switching of the network equipment without modifying the software and hardware of the network equipment, which simplifies and standardizes the management and monitoring of the network equipment, especially the switch, and improves the reliability of the communication system. And disaster recovery, saving costs, and it is also applicable to various types and brands of network equipment.
Owner:HYTERA COMM CORP
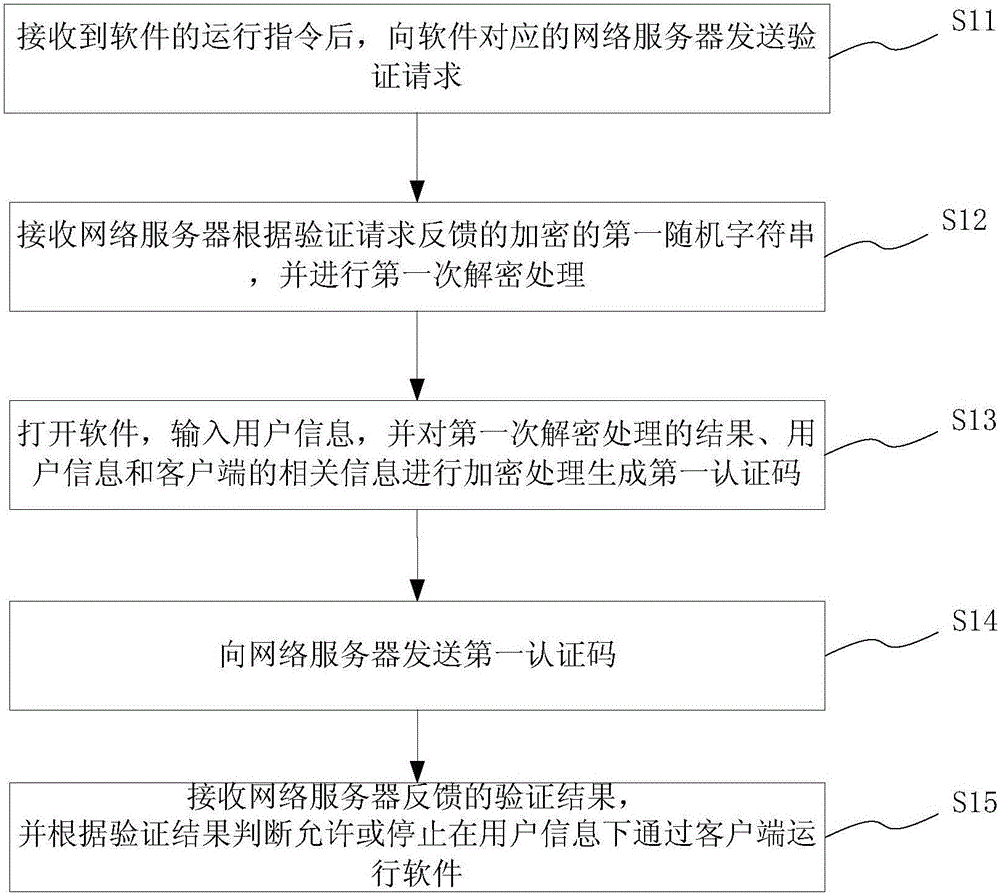
Software network authentication binding method and system
The present invention provides a software network authentication binding method and system, which are executed by the cooperation of the client and the network server: when the software is running on the client, it sends a verification request to the network server; according to the verification request, the network server randomly generates the first Random character strings, encrypted and fed back to the client; the client performs the first decryption process, and encrypts the decryption result, user information and client machine code to generate the first authentication code, and sends the first authentication code to the network Server; the network server performs a second decryption process on the first authentication code, and verifies the result of the second decryption process, and feeds back the verification result to the client. Run the software through the client. The invention not only protects the network server from the attack of the pirated software, but also protects the software from the attack of the counterfeit server, and improves the reliability of the legal authentication of the software.
Owner:MEDELI ELECTRONICS SHANGHAI
Ethernet-leveraged hyper-converged infrastructure
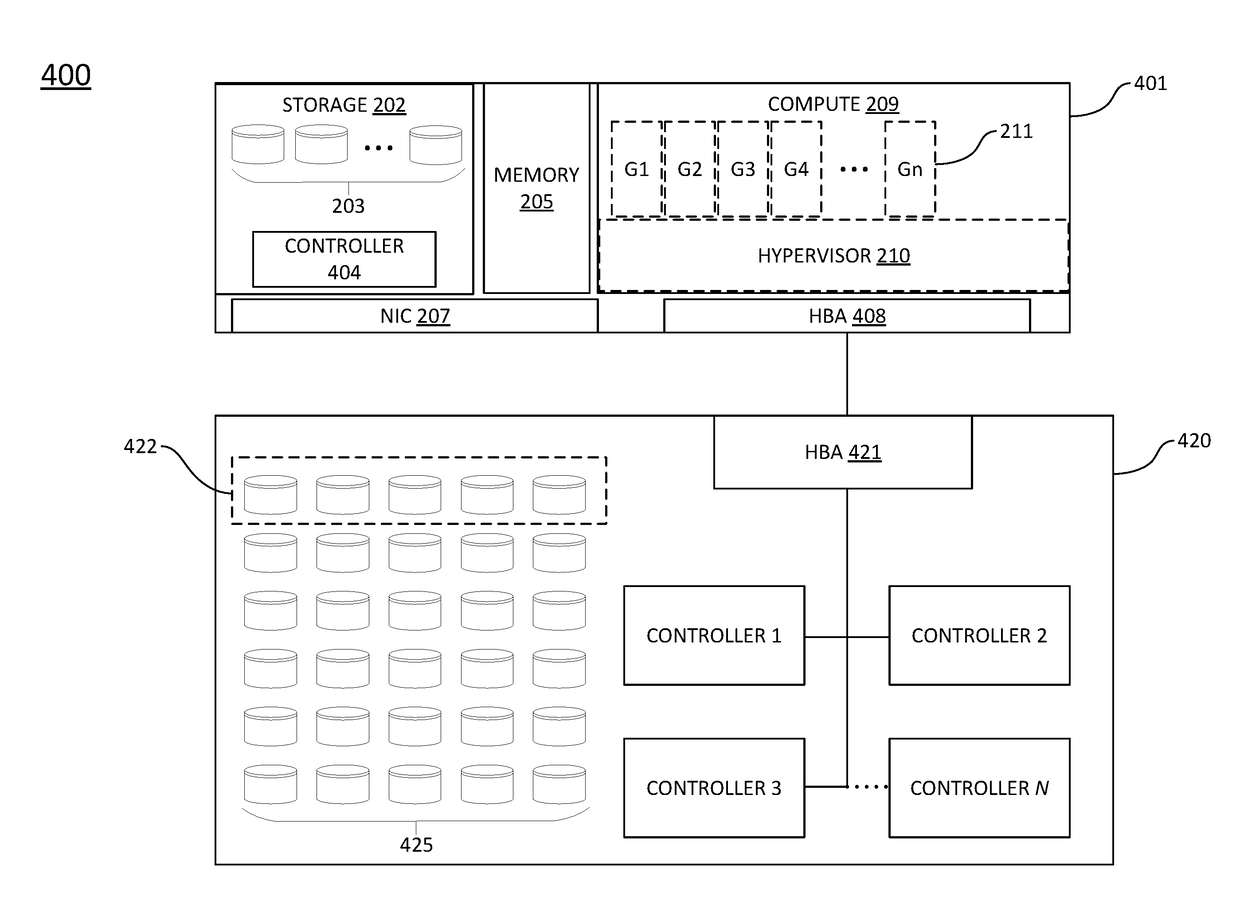
ActiveUS10108560B1Increase ratingsEliminate wasteInput/output to record carriersResource poolExtensibility
Systems and methods are provided for enabling extensibility of discrete components (e.g., memory, storage, cache (hardware- or software-based), network / fabric, capacity, etc.) within a hyper-converged infrastructure. In the context of extending the storage component, an external storage device is connected to a hyper-converged appliance (“node” or “host”) via an Ethernet-based host bus adapter (“HBA”). Utilizing ATA over Ethernet (“AoE”) as the communication protocol, storage drives within the external storage device appear as direct-attached storage to the hypervisor of the hyper-converged appliance, extending the pool of storage resources available for allocation by the hyper-visor.
Owner:BIN 2022 SERIES 822 OF ALLIED SECURITY TRUST I
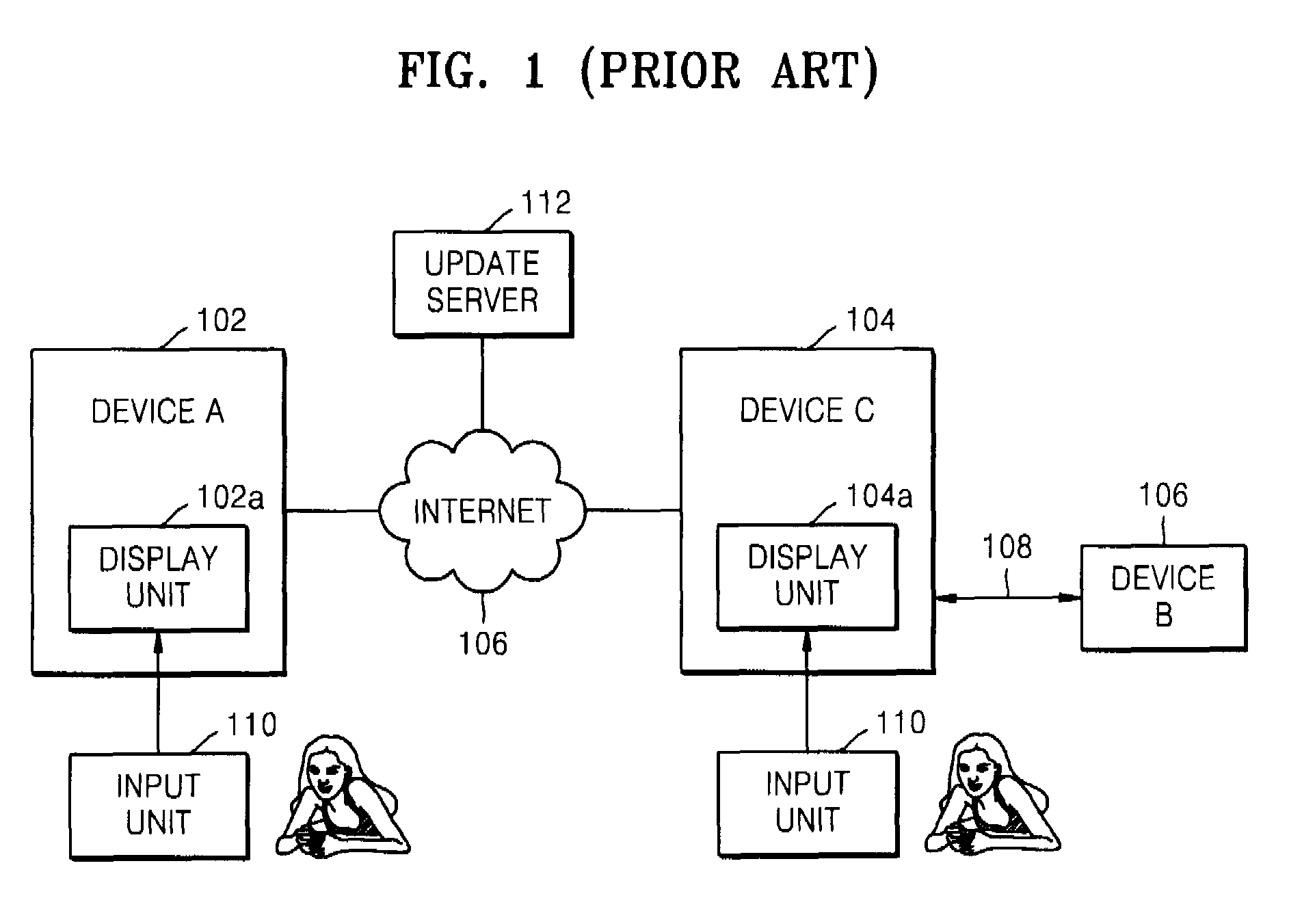
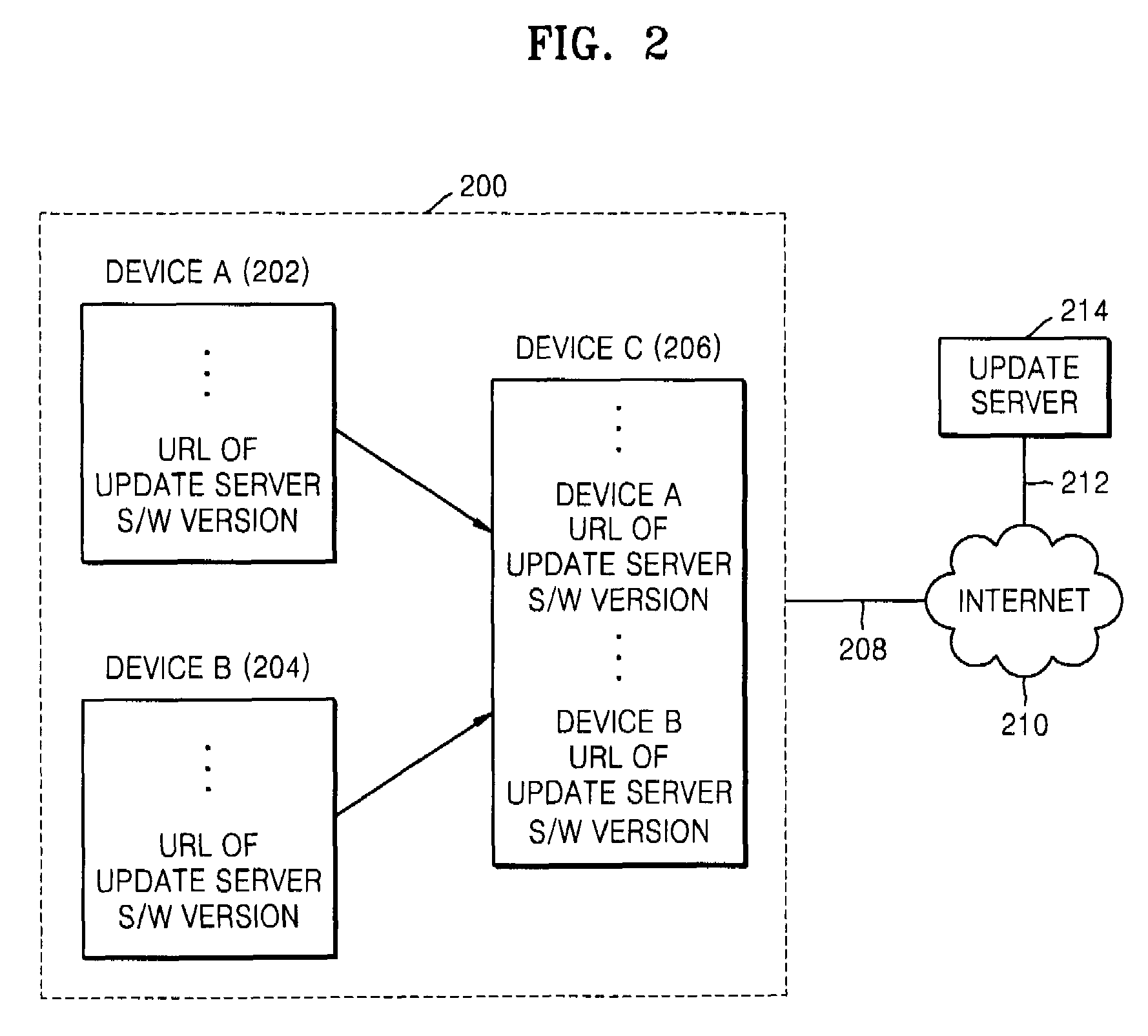
Method of and apparatus for updating software of network device
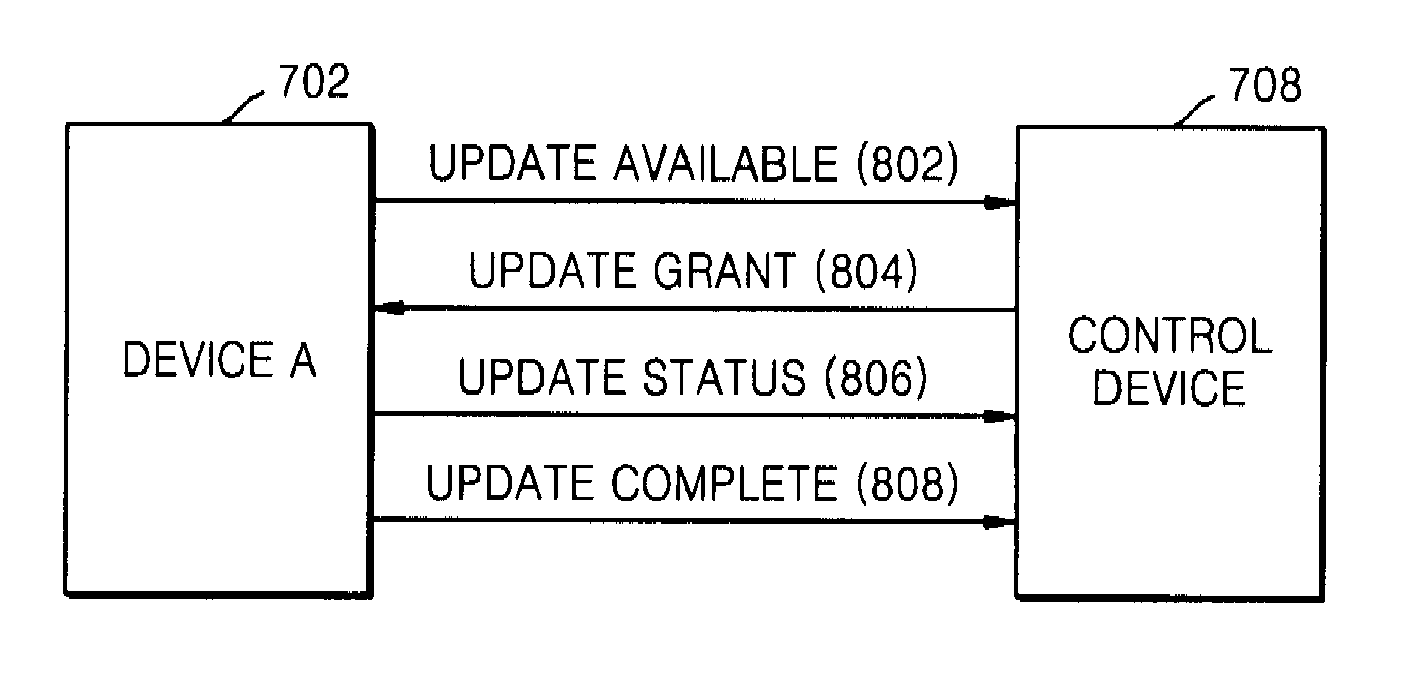
InactiveUS7831967B2Program control using stored programsMultiple digital computer combinationsSoftware networkControl circuit
A method and apparatus for updating the software of a device that is a controlled device linked to a control device over a network. According to the method, a control device obtains information regarding updating of the software of a controlled device, determines whether updating is available using the information, and allows the controlled device to update its software, thereby easily updating the software of device. The apparatus can be a network device, connected to an update server and another network device in a network, for updating software of the other network device. The network device can include a control circuit configured to determine whether the updating of the software is required based on update information; and a transceiving unit configured to communicate with the other network device and the update server.
Owner:SAMSUNG ELECTRONICS CO LTD
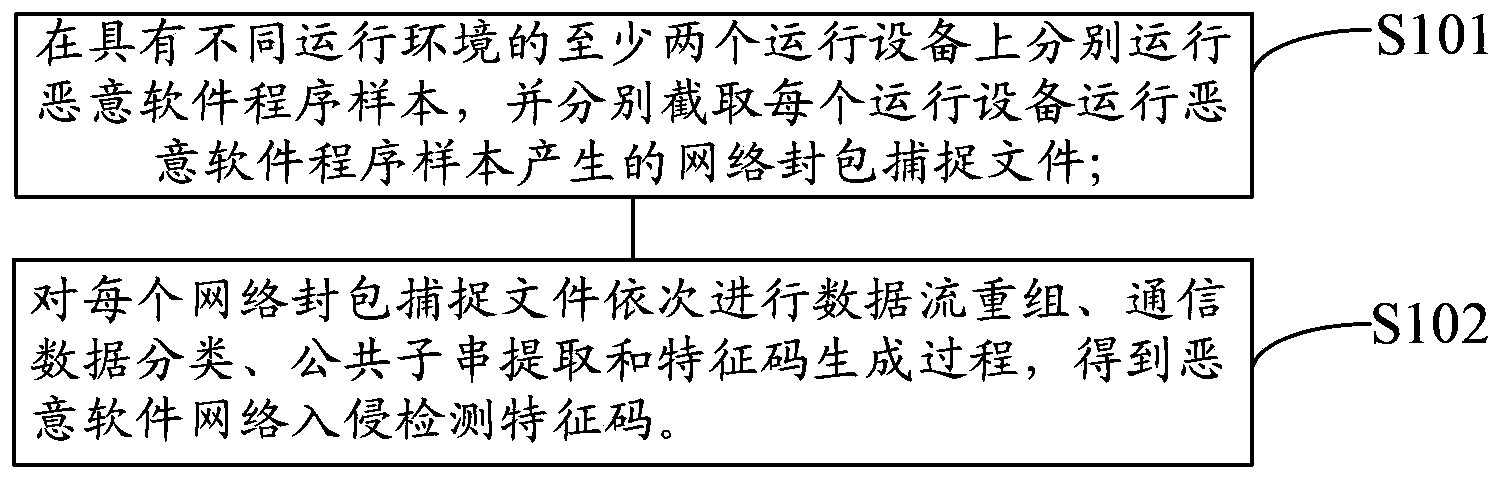
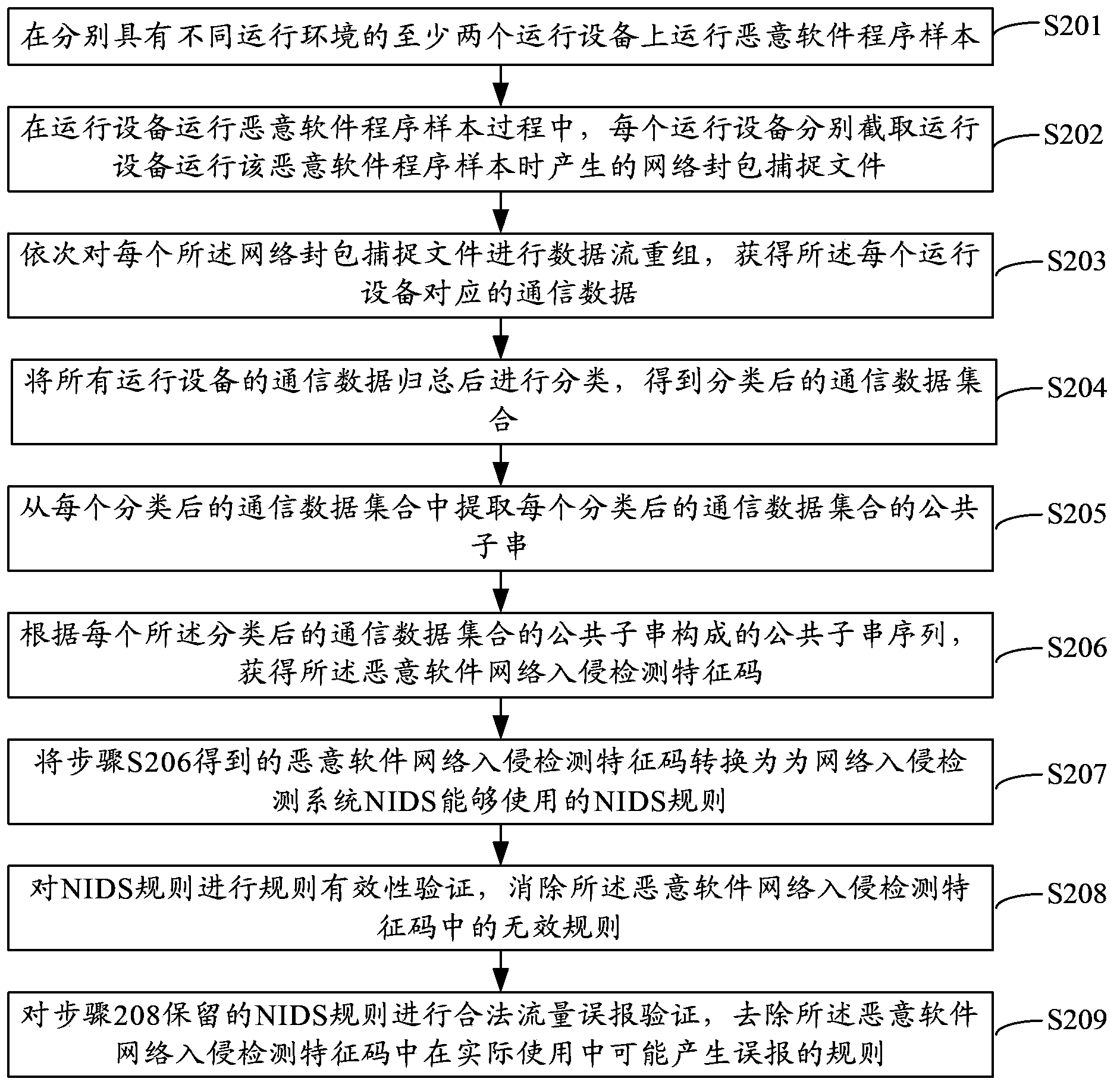
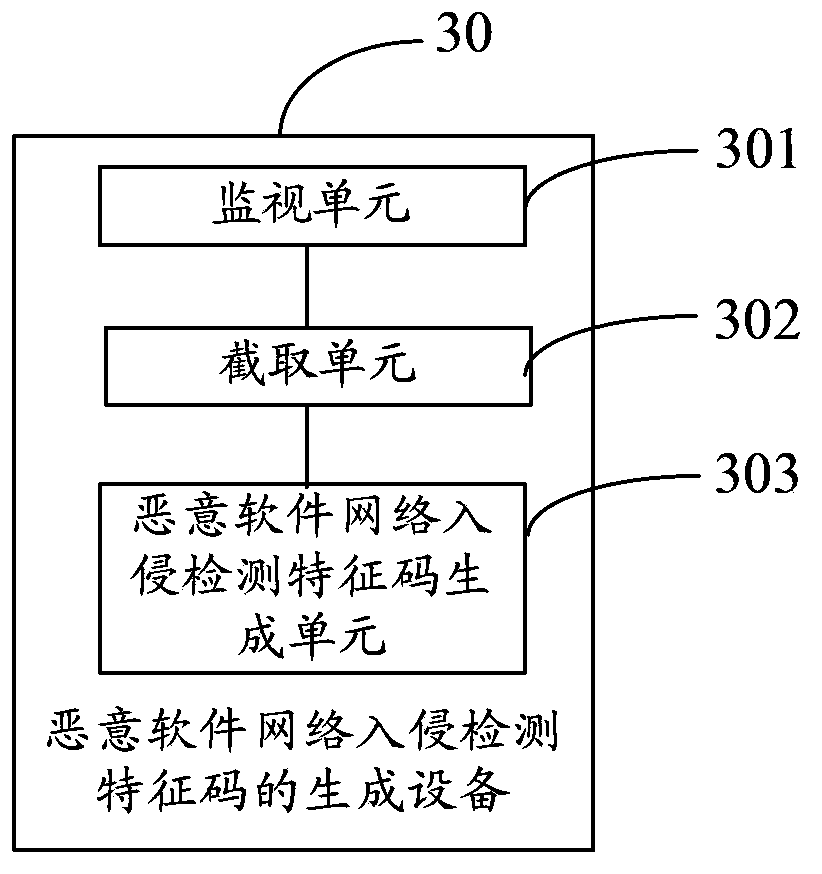
Generation method and device for malicious software network intrusion detection feature codes
InactiveCN104243407AQuick responseImprove extraction efficiencyTransmissionSoftware networkNetwork packet
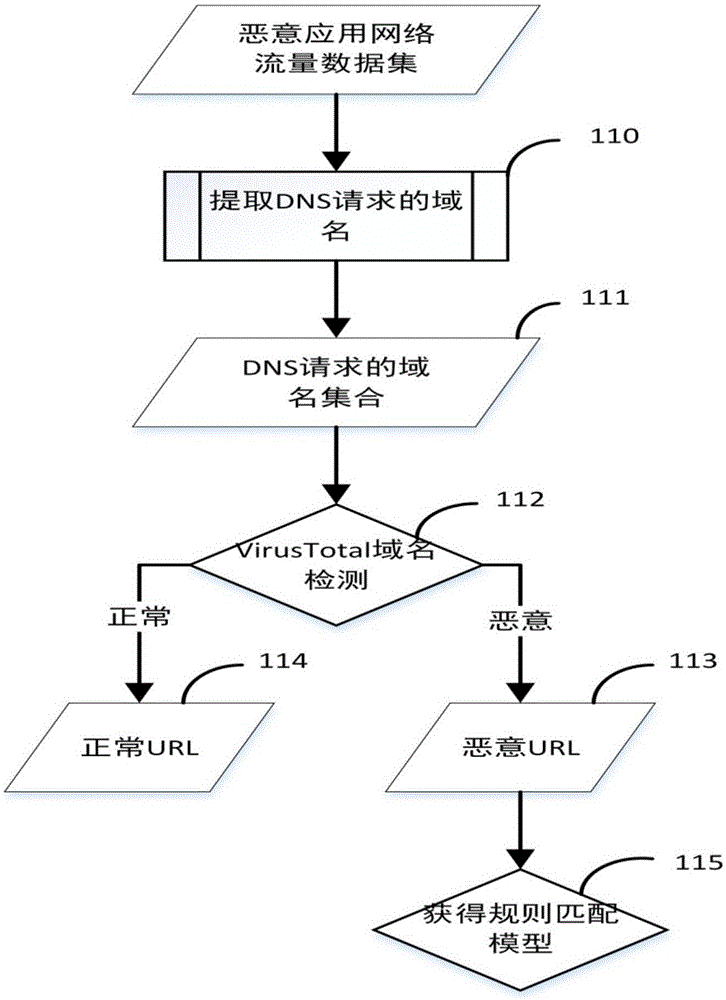
The embodiment of the invention provides a generation method and device for malicious software network intrusion detection feature codes. According to the generation method and device, malicious software network feature codes are automatically extracted under various running environments, and the network feature code extracting efficiency, universality and the speed of the response of an NIDS and an NIPS to newly-developing malicious software are improved. The method comprises the steps that malicious software program samples run on at least two running devices with different running environments, and a network packet capture file generated when each running device runs the corresponding malicious software program sample is intercepted; data flow reassembly, communication data classification, common substring extraction and feature code generation are carried out on each network packet capture file in sequence to obtain the malicious software network intrusion detection feature codes.
Owner:HUAWEI TECH CO LTD +1
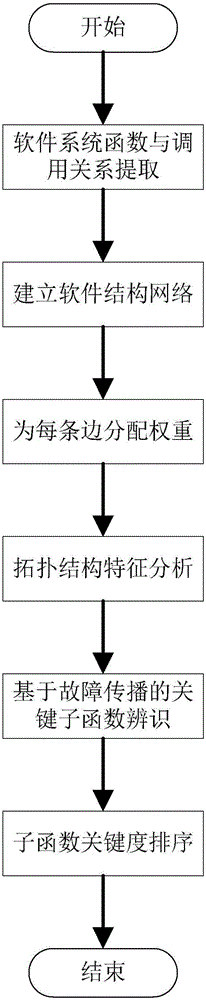
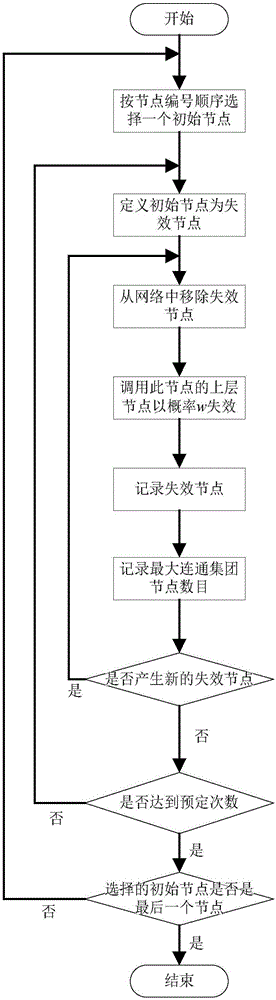
Software key function identification method based on complex network fault propagation
InactiveCN105045574ACompliant with the actual software systemGuaranteed uptimeSpecific program execution arrangementsCascading failureNODAL
The invention discloses a software key function identification method based on complex network fault propagation. The software key function identification method comprises the following steps: 1) according to a source code, carrying out subfunction and calling relation extraction on a program, and carrying out abstraction to obtain a network chart of a software structure; 2) according to a probability of calling and executing each subfunction, endowing each side with a certain weight w, wherein the weight is a failure probability of inter-function cascading faults; 3) analyzing the topological structure characteristics of software, and calculating an in-degree value and an out-degree value of each node, wherein the in-degree value of the node is a frequency that the function is called by other functions, and the out-degree value of the node is the frequency that the function calls other functions; 4) carrying out a cascading failure simulation experiment on each node of a software network, and calculating the node numbers G, i.e., the criticality, of a maximum connected subgraph of the software network after each node is subjected to stable failure; and 5) sorting the G in an increasing sequence to obtain the criticality of each function. The software key function identification method is simple and reliable. Compared with a traditional method, the software key function identification method can precisely identify a software key function.
Owner:ELECTRIC POWER RES INST OF GUANGDONG POWER GRID
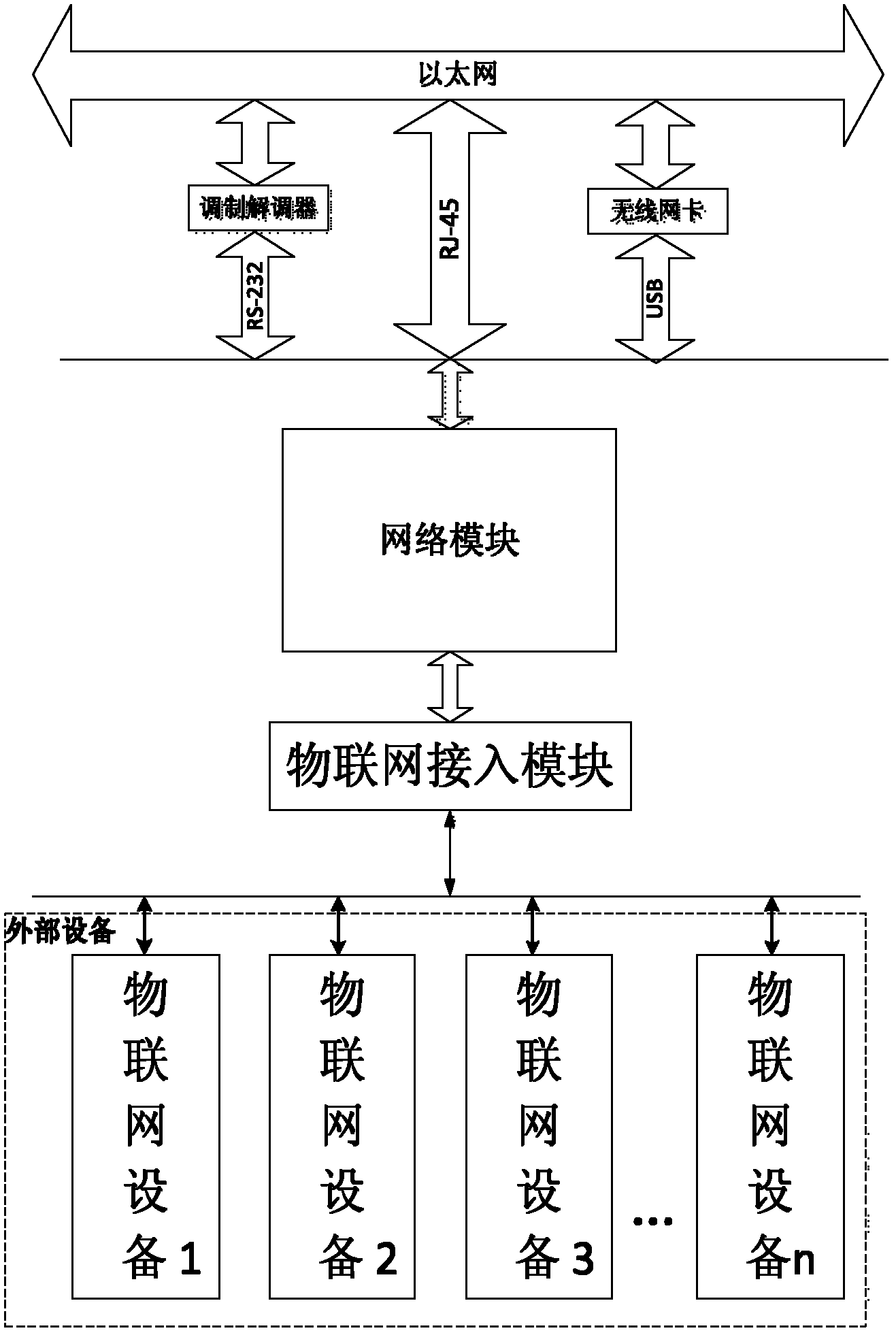
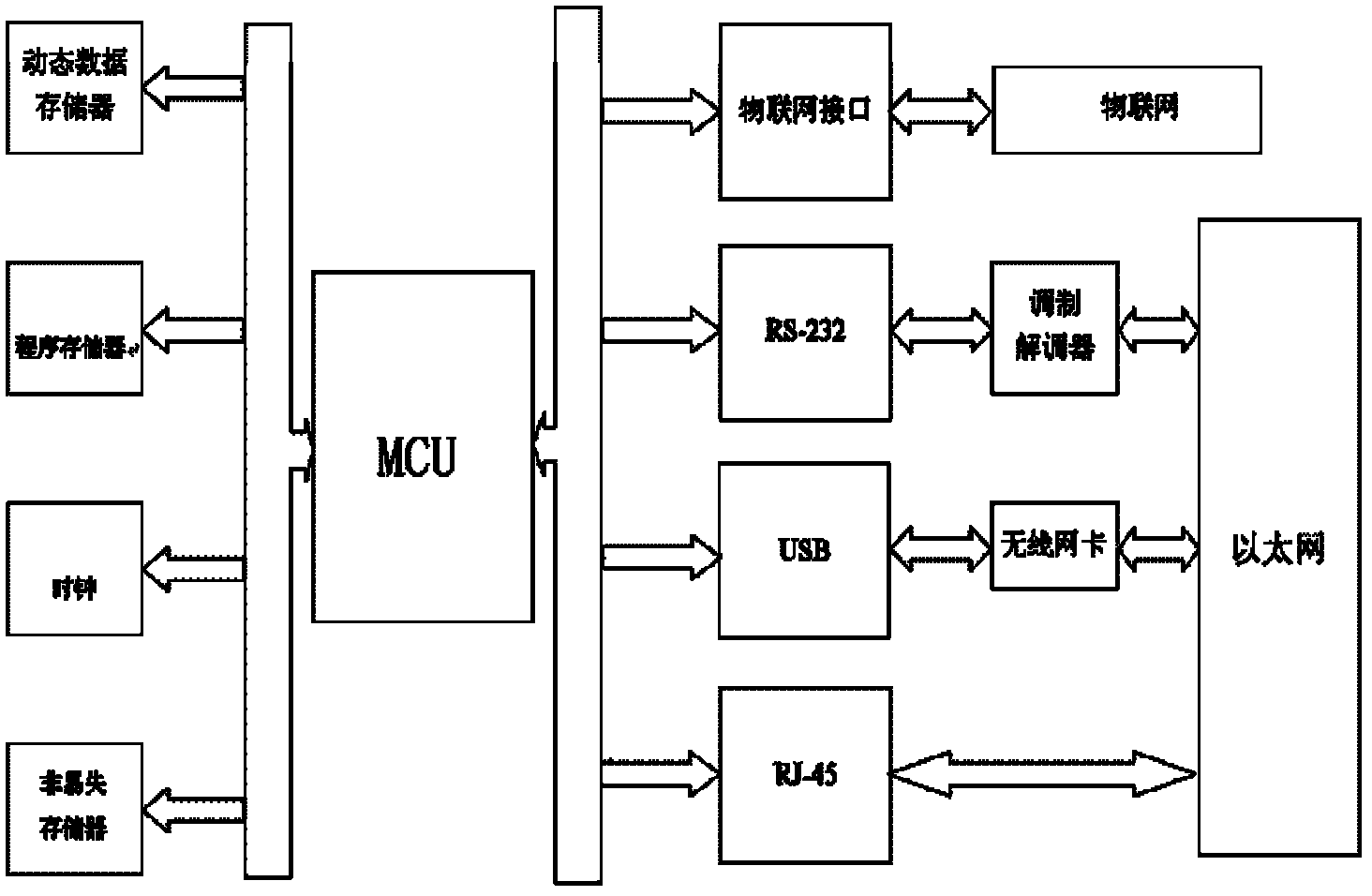
Management system and implementation method used for interconnection between industrial internet of things and Ethernet
The invention discloses a management system and an implementation method used for interconnection between an industrial internet of things and an Ethernet. The management system is a network management system for internets of things, can be operated remotely, and is mainly applied to industrial internets of things and other industrial wireless networks. The management system comprises two major parts of an internet-of-things access module and a network module, wherein the internet-of-things access module adopts a wireless network for industrial automation (WIA) industrial protocol to exchange data with the internet of things, and the network module outputs received data in the internet of things to the remote Ethernet. Three connector modes are provided and include that a traditional registered jack-45 (RJ-45) connector and a traditional recommended standard-232 (RS-232) connector are accessed to the Ethernet through a modem, and a universal series bus (USB) is accessed to the Ethernet through a wireless network card, so that the management system can adapt to different environments and enables mounting and using processes to be more convenient and faster for a user. The implementation method includes that embedded Web services are provided for the user at the same time through a radio frequency data receiving and transmitting module and a software network module, real-time monitoring and control functions can be achieved depending on a Web browser, and the real-time performance, the network performance and the reliability of the management system are hard to match by other systems.
Owner:MICROCYBER CORP
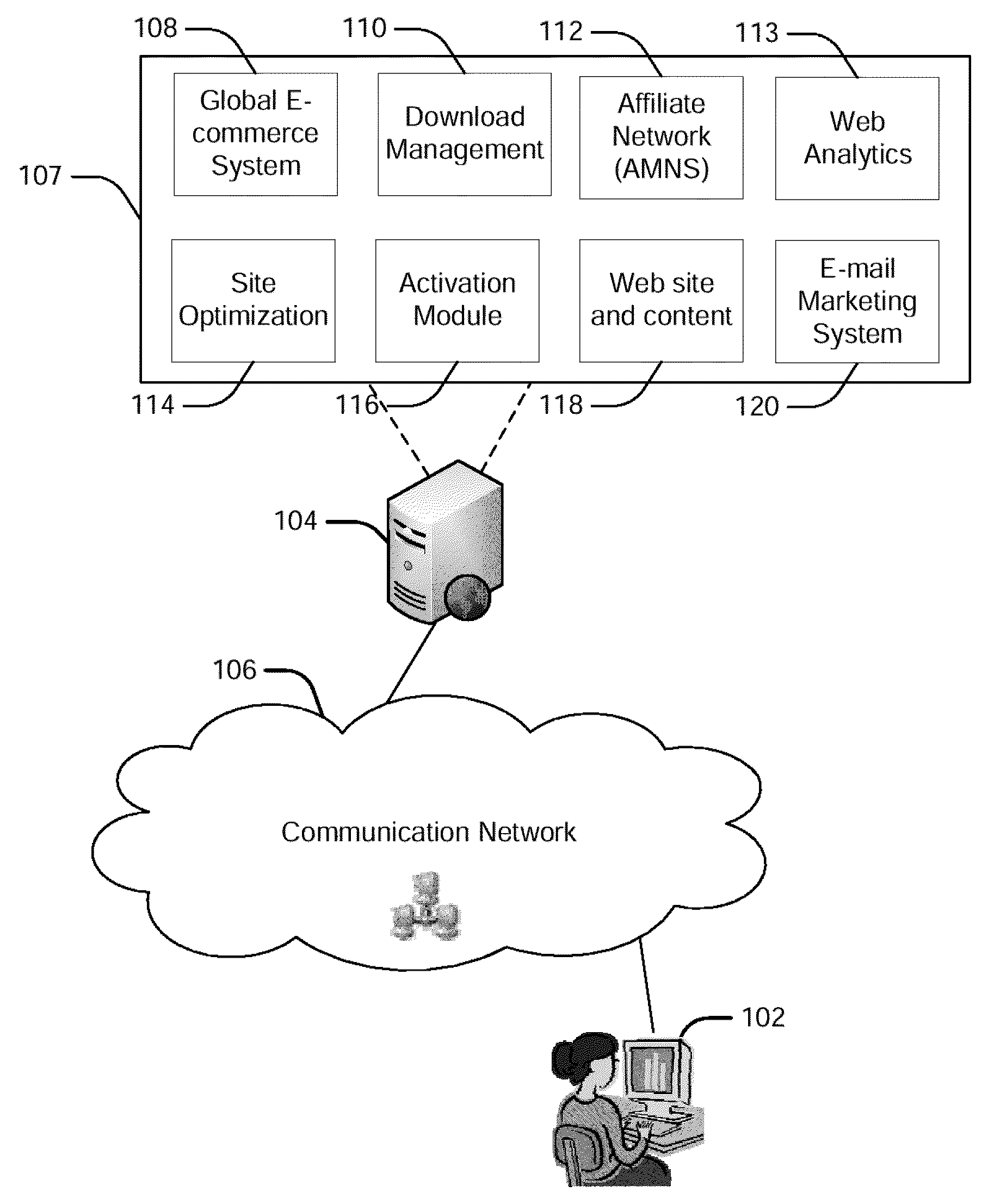
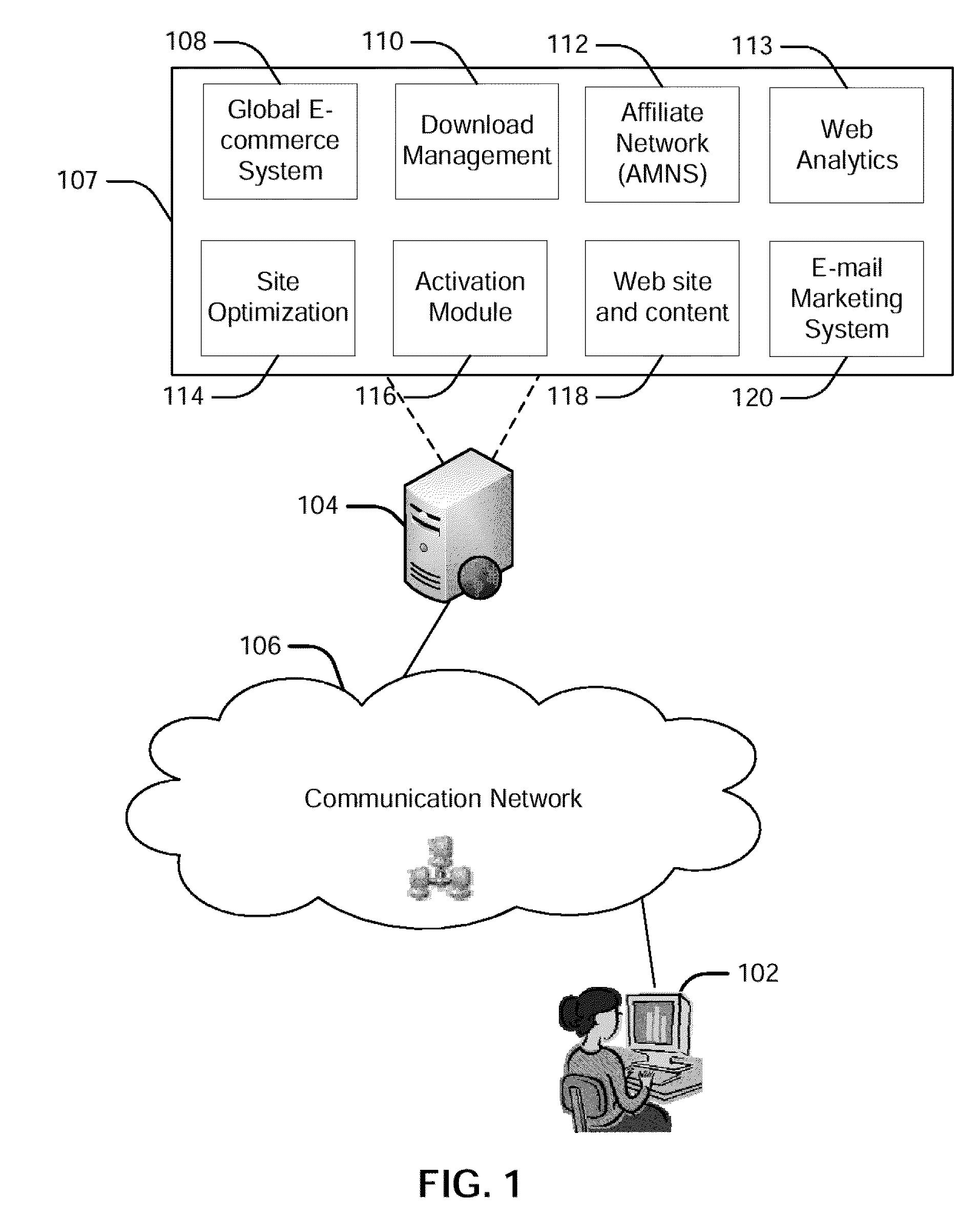
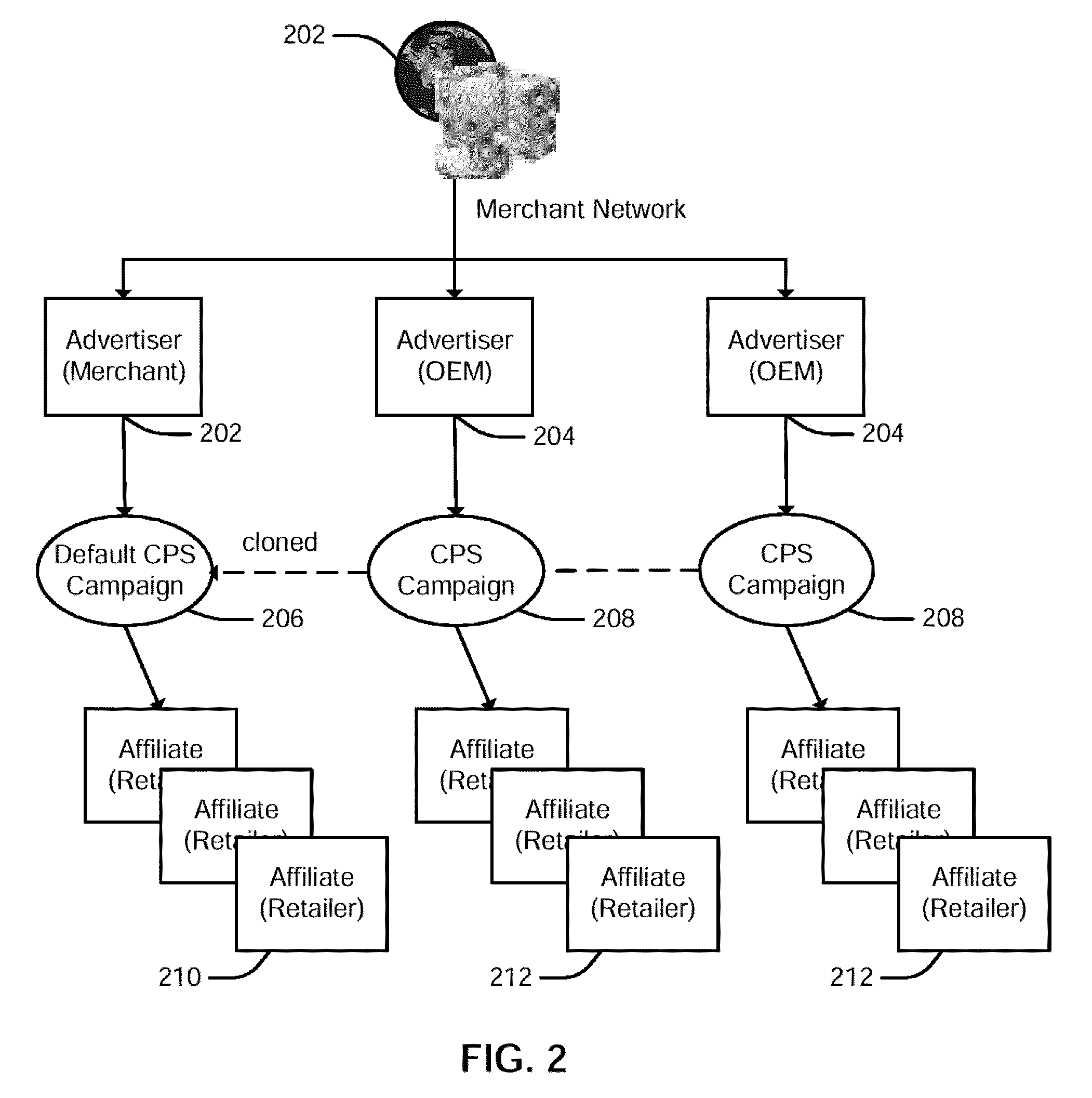
Integrated Software Network Agent
ActiveUS20090216861A1Promote activationMinimal impactMultiple digital computer combinationsBuying/selling/leasing transactionsEmail marketingSoftware network
A model for the next generation of software network agents for downloadable software is provided. The software network agent delivers a streamlined user experience that presents the user with options to try or buy. The agent may be co-branded for merchant and affiliate marketing. The agent may be integrated with a number of services, such as ecommerce systems, affiliate marketing network systems, site optimization, web analytics and email marketing systems that enable a merchant to enhance the user experience and improve marketing. A user's actions may be tracked in order to provide OEMs and retailers payout on purchase referrals to the merchant's online store. Code changes and bug fixes can be made at the server and in a timely manner with minimal impact to the various systems supporting the software activation user experience.
Owner:DIGITAL RIVER INC
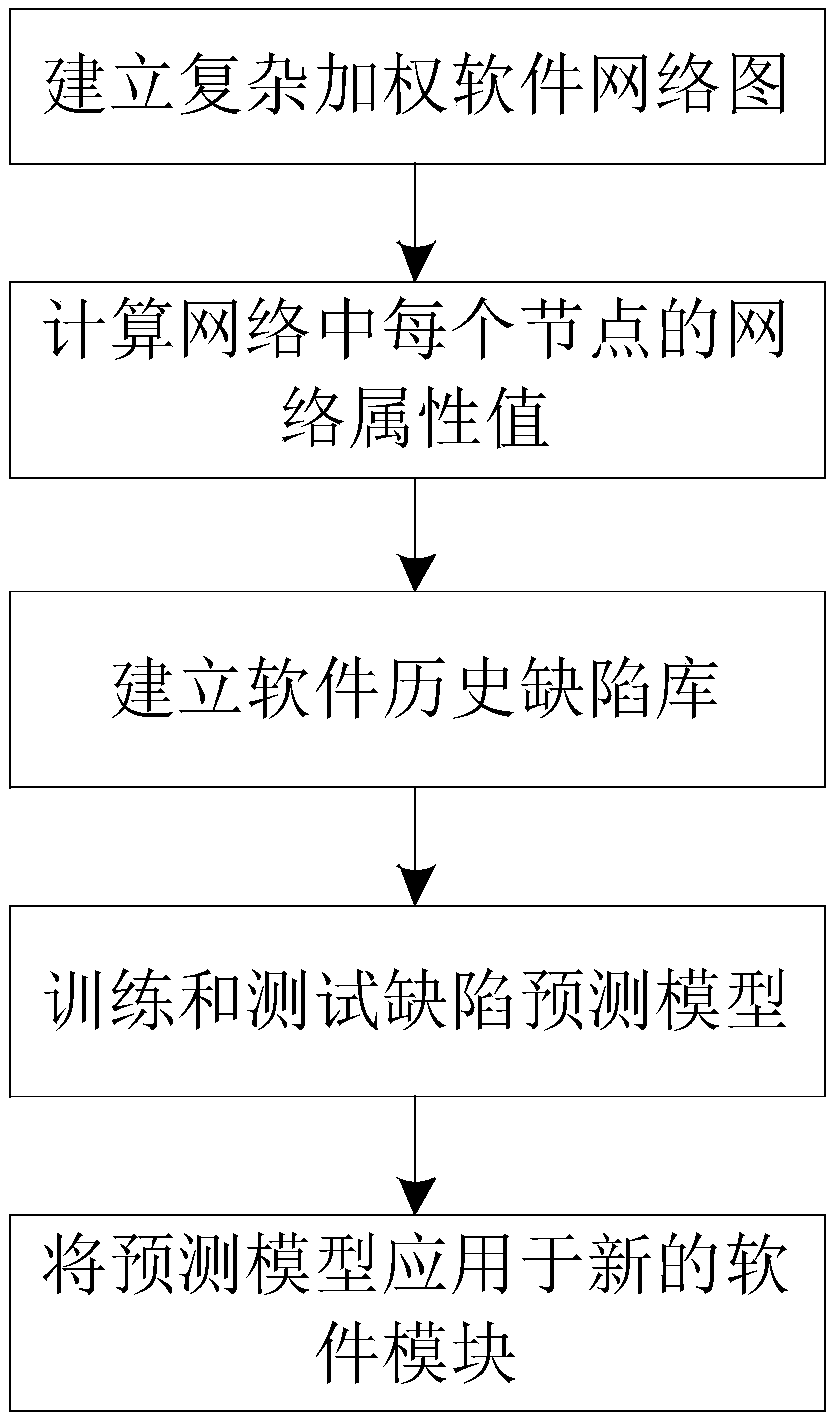
Software defect prediction method based on complex weighted software network
ActiveCN107665172AImproving Defect Prediction AccuracyImprove performanceMathematical modelsSoftware testing/debuggingSoftware networkSoftware engineering
The invention provides a software defect prediction method based on a complex weighted software network diagram. The defect prediction precision of large-scale complex software can be improved. The method comprises the following steps that firstly, the complex weighted software network diagram is established according to predicted software; secondly, the network attribute value of each node in thecomplex weighted software network diagram established in the first step is determined; thirdly, all software defects aiming at the prediction software are collected from a disclosed software defect library, a historical defect library of the software is established, and defect labels of each software module are marked in the historical defect library; fourthly, the network attribute value of eachnode determined in the second step serves as input of a machine learning algorithm, the defect labels marked in the third step serve as output of the machine learning algorithm, the machine learningalgorithm is trained and tested, and according to the performance evaluation index of the machine learning algorithm, an optimal prediction model can be determined.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
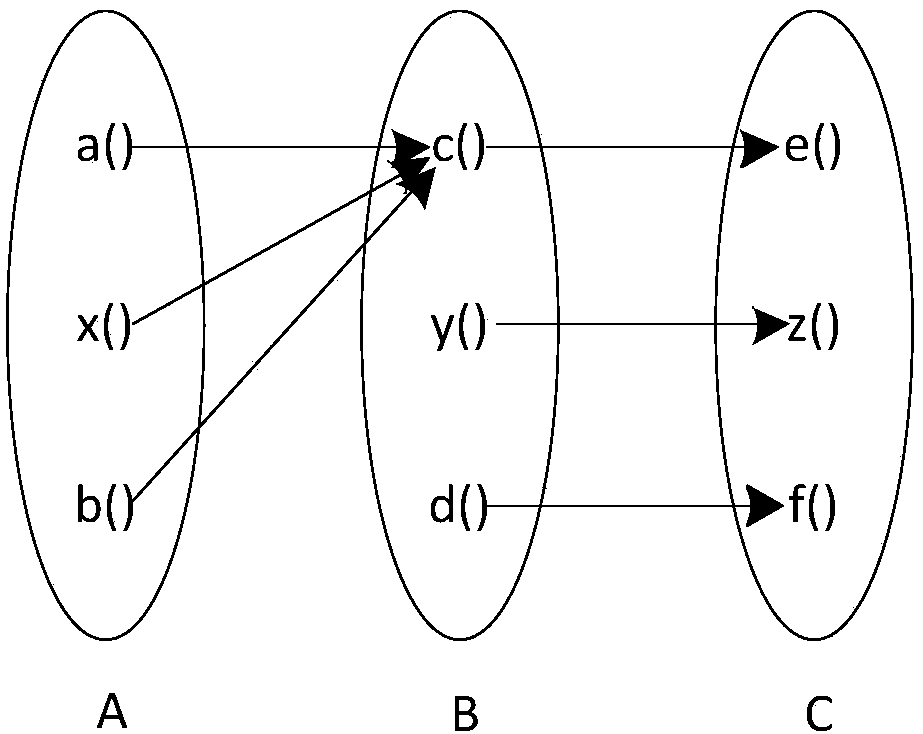
Complex network-based object-oriented integration testing method
InactiveCN101477490AIncrease coverageReduce in quantitySoftware testing/debuggingSoftware networkIntegration testing
The invention discloses an integration test method facing objects and based on a complex network. The method comprises the following steps: (1) establishing a system structural model of detected software by adopting a unified modeling language, and stating a UML (unified modeling language) class diagram to a software network G equal to (V, E); (2) traversing the whole software network, recording the class relied by each class and the in-degree and the out-degree of the class in a tetrad; (3) first, intensively testing the class with a big in-degree and an out-degree of zero; (4) in secession, detecting the relied class utilizing the class without adding classes or a new class in each detection; and repeatedly conducting step (4) along the testing sequence relying on class hierarchy, so as to ensure that the class detected prior is superior to that detected afterwards until the system for constructing complete detected software. The invention combines complex network and the object-facing software test together, and conducts integration test to the object-facing procedures combining with the internal topology structural characteristics of the object-facing software, thereby optimizing test cases and reducing test work load.
Owner:SHANGHAI SECOND POLYTECHNIC UNIVERSITY
Protocol testing device
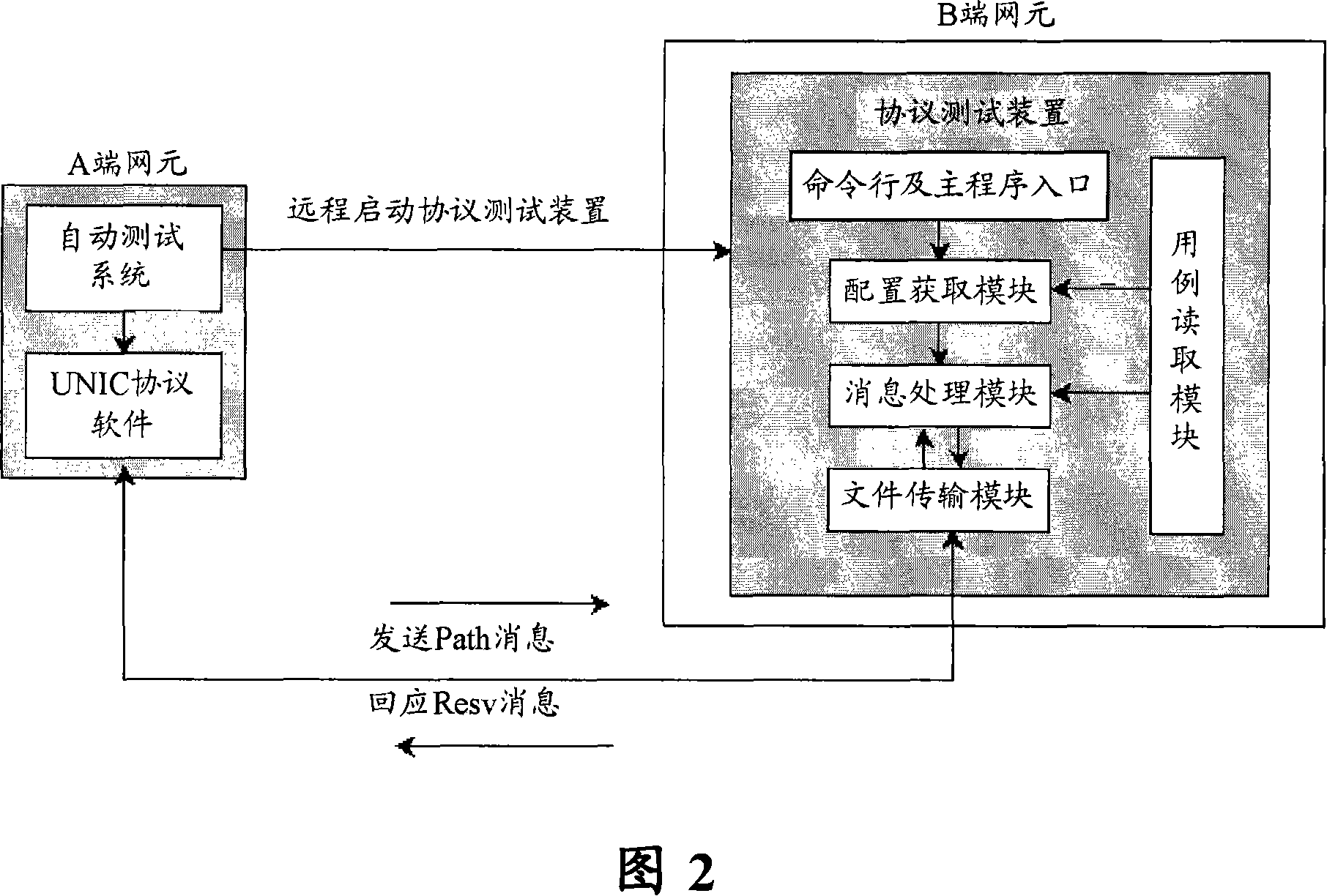
InactiveCN101114954AImprove stabilityImprove adaptabilityData switching networksComputer hardwareSoftware network
The invention discloses a protocol testing device, comprising a case using and reading module which is used for providing an interface to a testing case storage unit, an allocation obtaining module which is used for obtaining the allocation document of the test case using from the test case using storage module by the case using and reading module, a message processing module which is used for responding the message type of the tested protocol software network according to the configuration file, and the message document of the corresponding type of the testing using case is obtained from the testing case storage unit by the case using and reading module, and a document transmission module which is used for transmitting the message document of the corresponding type to the tested software network, wherein, the protocol test device is started by command traveling mode. By the invention, the abnormal case beyond the protocol range can be effectively tested, thereby greatly improving the stability and adaptability.
Owner:ZTE CORP
Communication system for automatic monitoring network environment
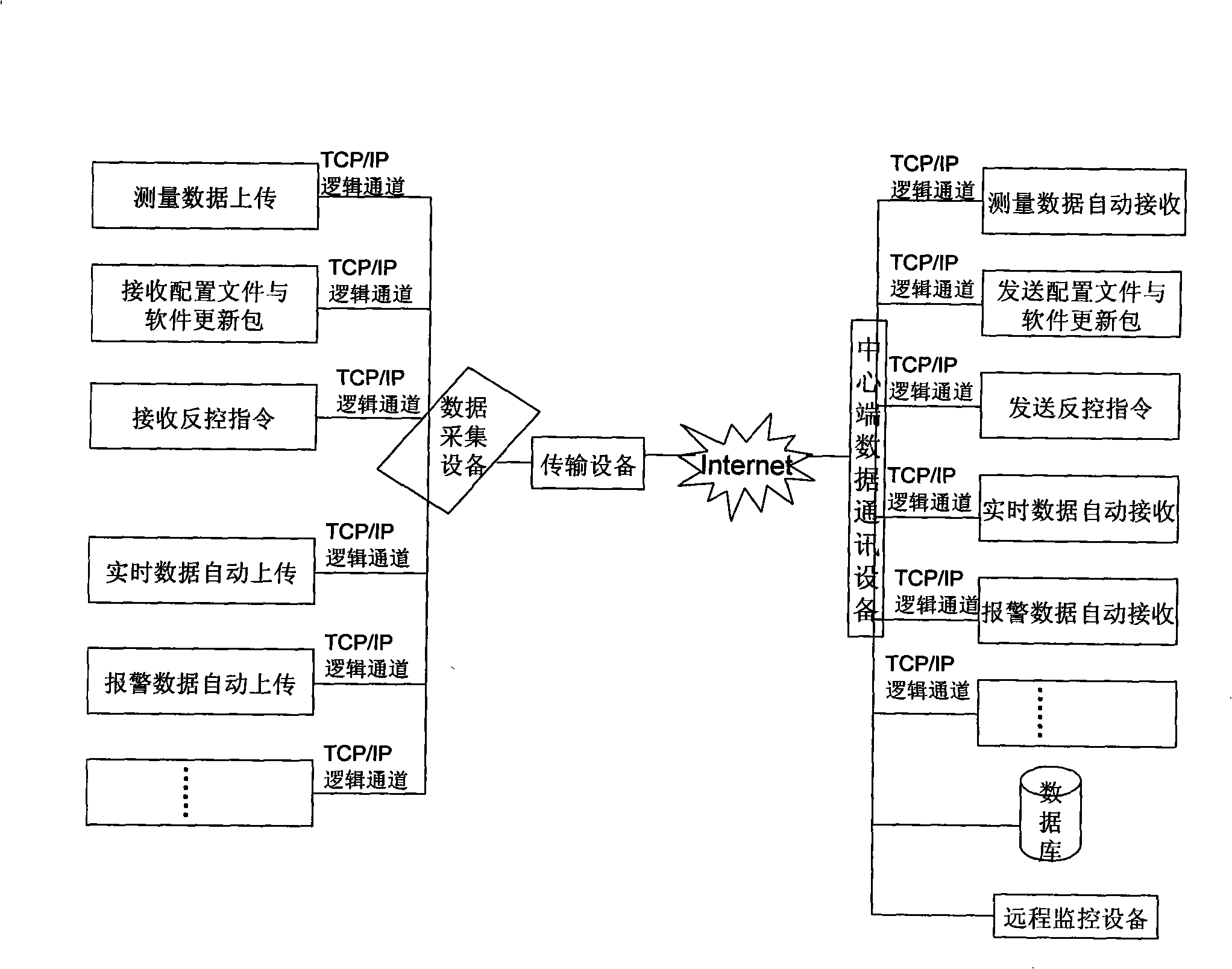
InactiveCN101257408APrevent malfunctionAvoid the situationData switching networksSoftware networkCommunications system
Disclosed is a communication system of an environment automatic monitoring network, mainly comprising: a data acquisition facility, a transmission device of a data acquisition end, a data communication equipment of a center end, and a telemonitor. The invention can achieve the functions of real-time measuring data communication, in time alarm, telemonitoring the operation of an automatic station and updating software network of the data acquisition facility.
Owner:北京泰得思达科技发展有限公司
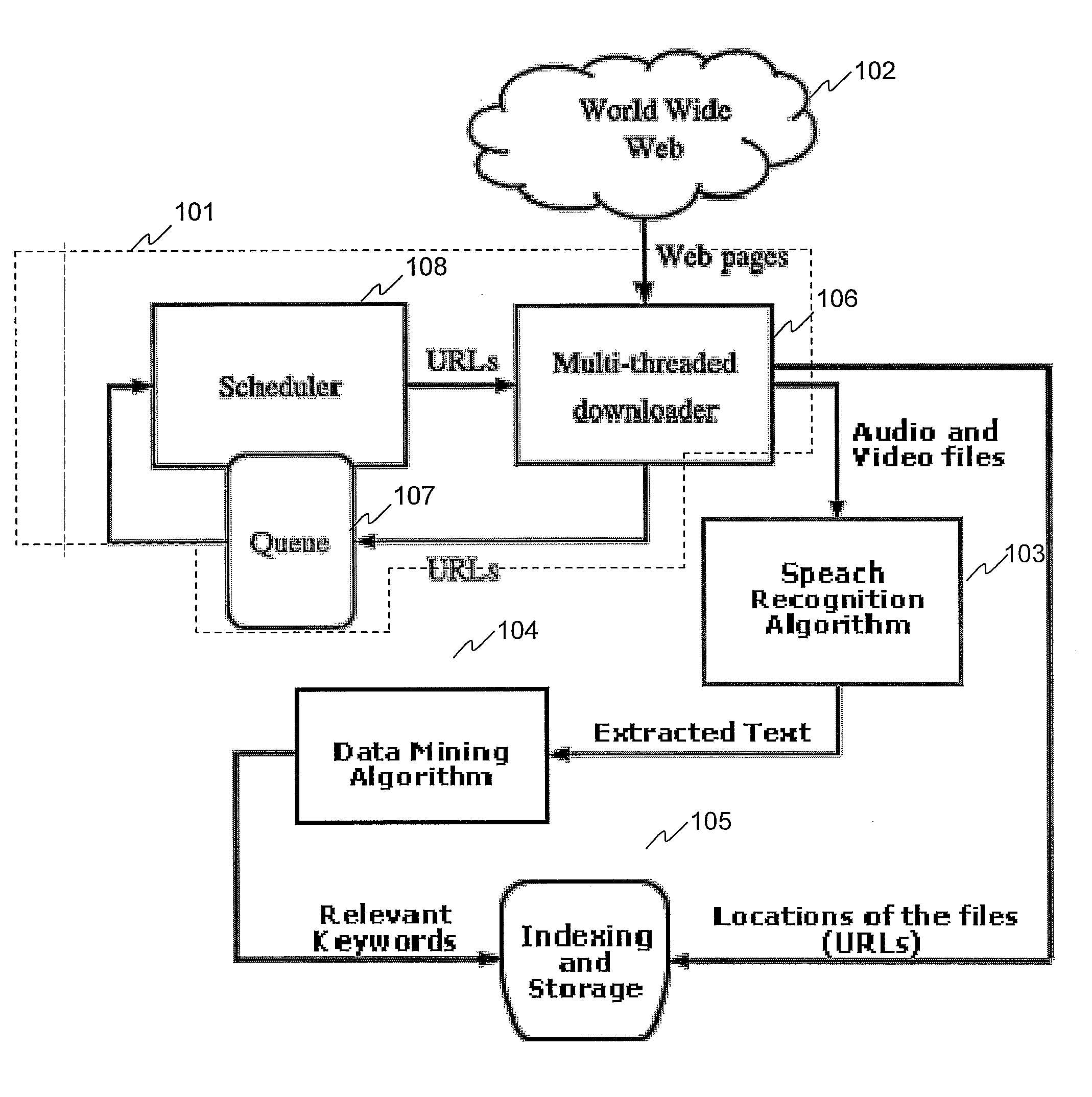
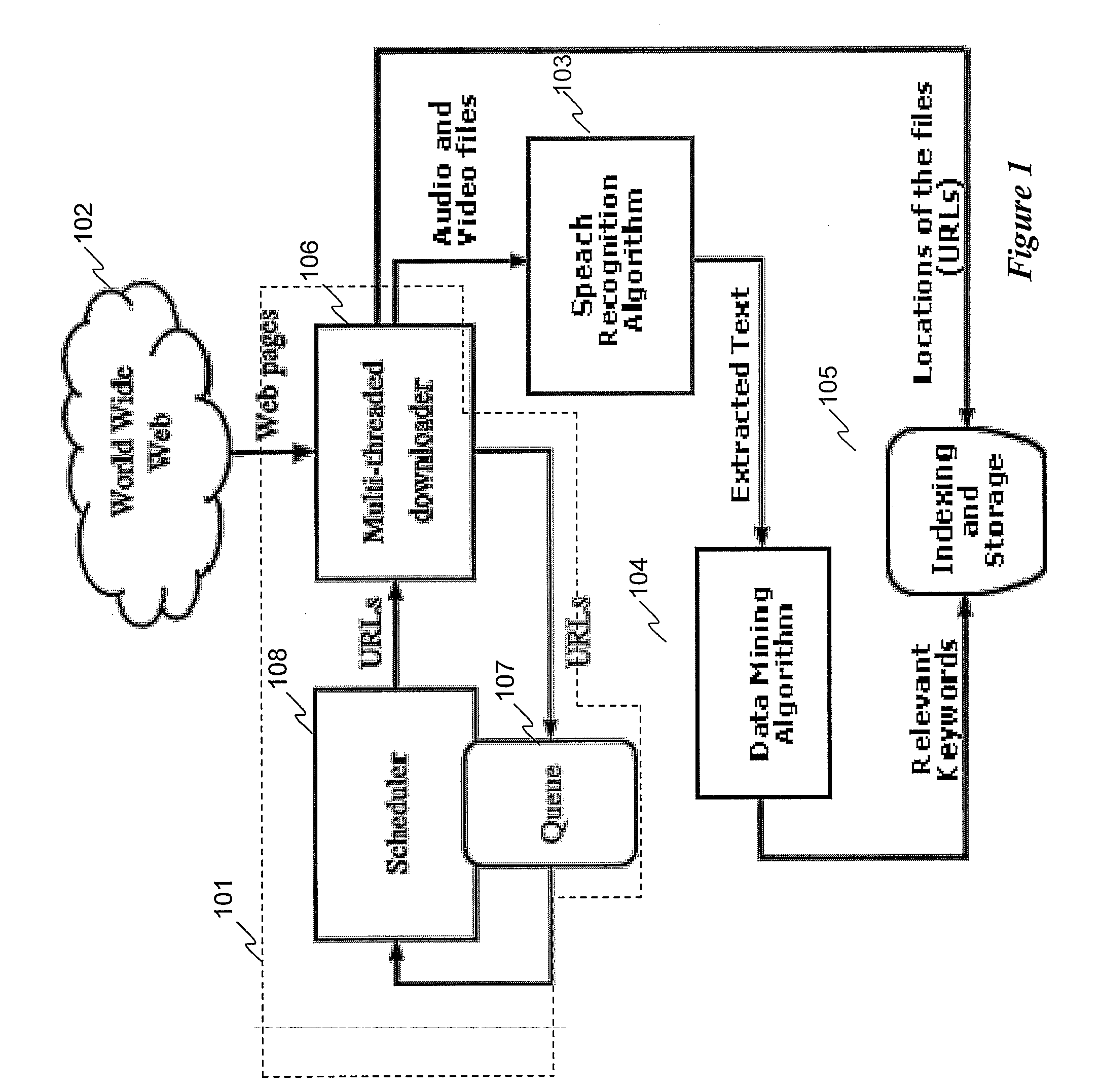
Software web crowler and method therefor
ActiveUS20080046240A1Eliminate the problemData processing applicationsDigital data processing detailsSound analysisWeb crawler
Description of a web crawler that crawlers the web for audio and video files and indexes the files based on sound analysis and algorithmic translation and analysis of sounds in audio and video files to text.
Owner:AURA SUB LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com