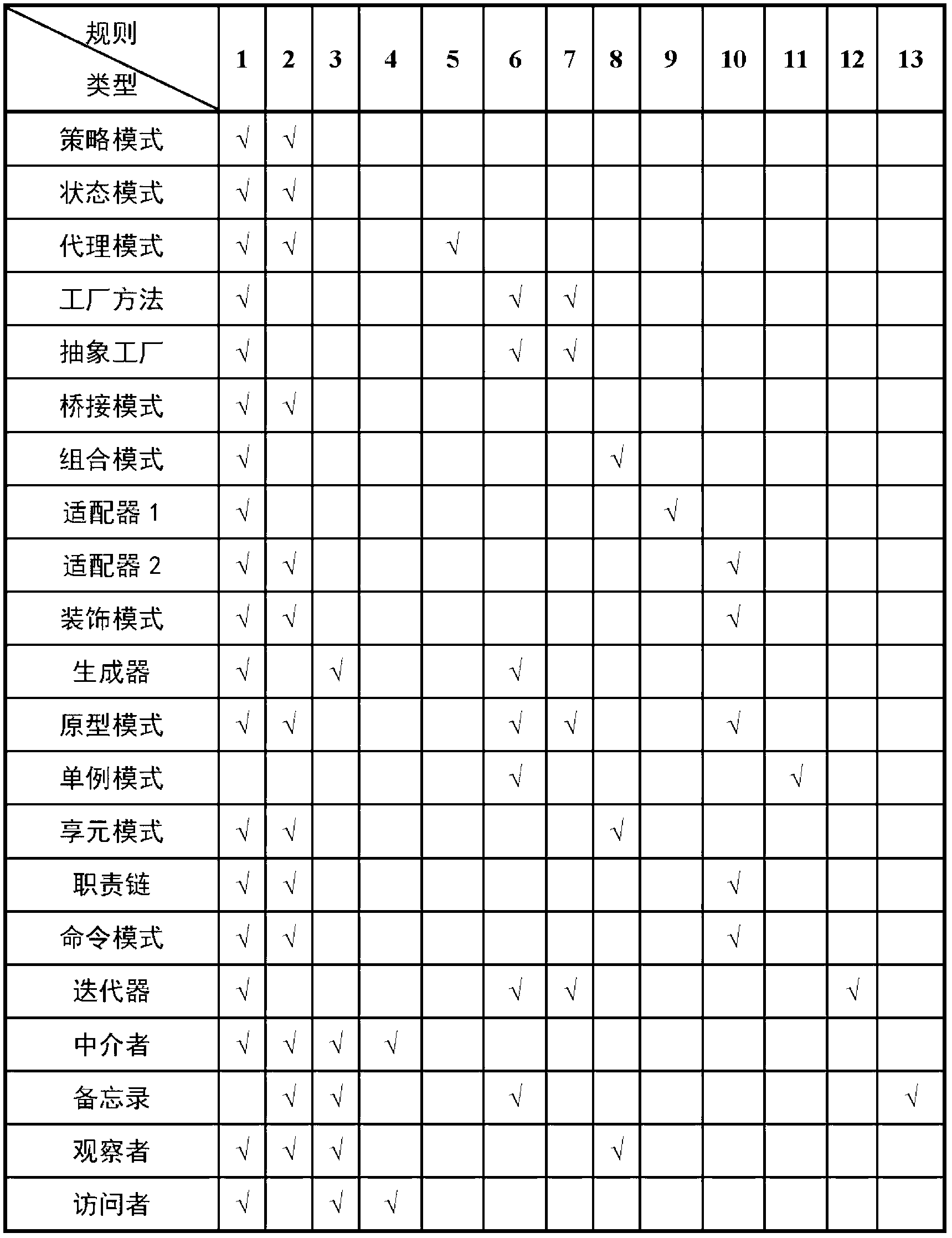
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
76 results about "Class diagram" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
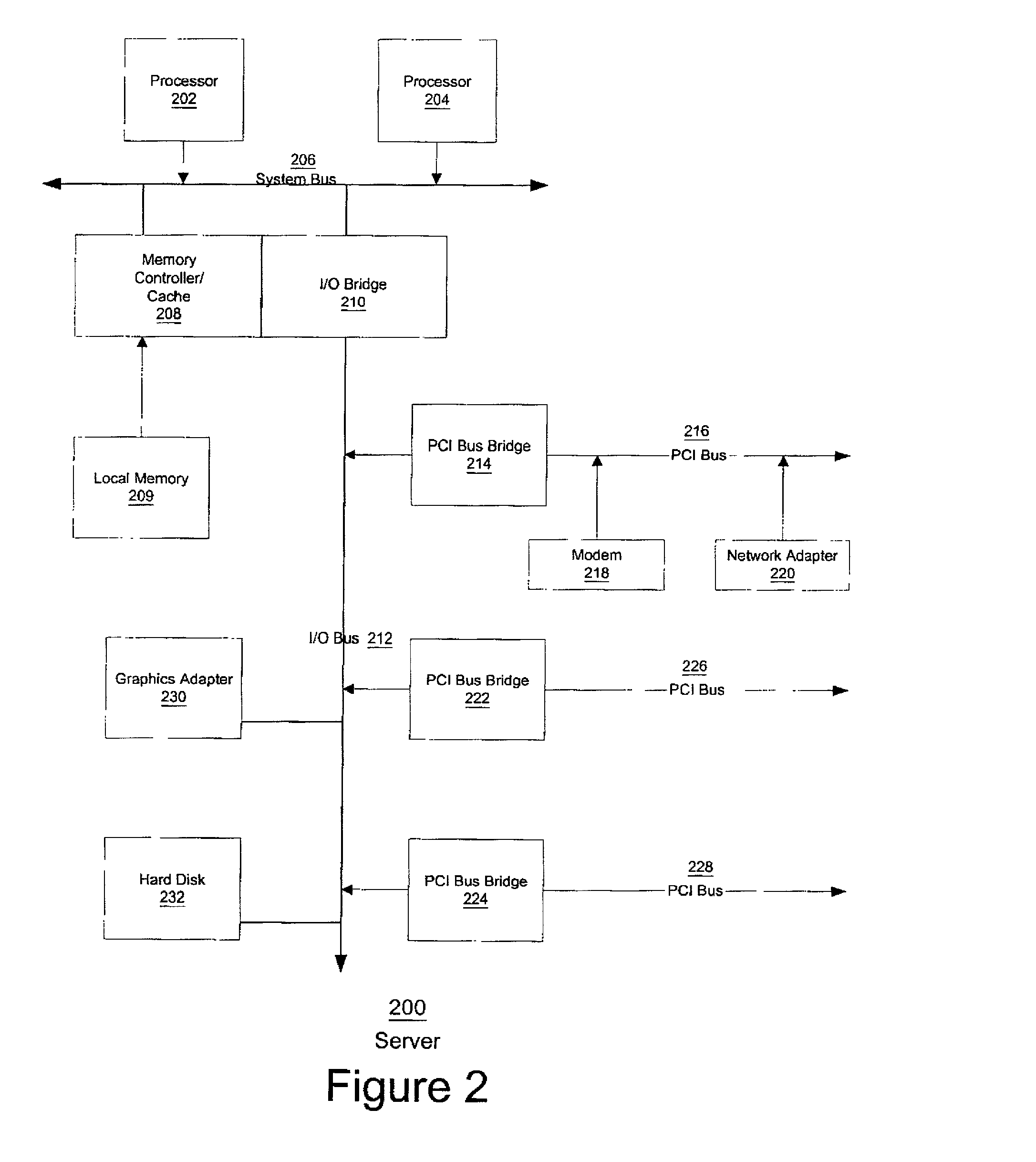
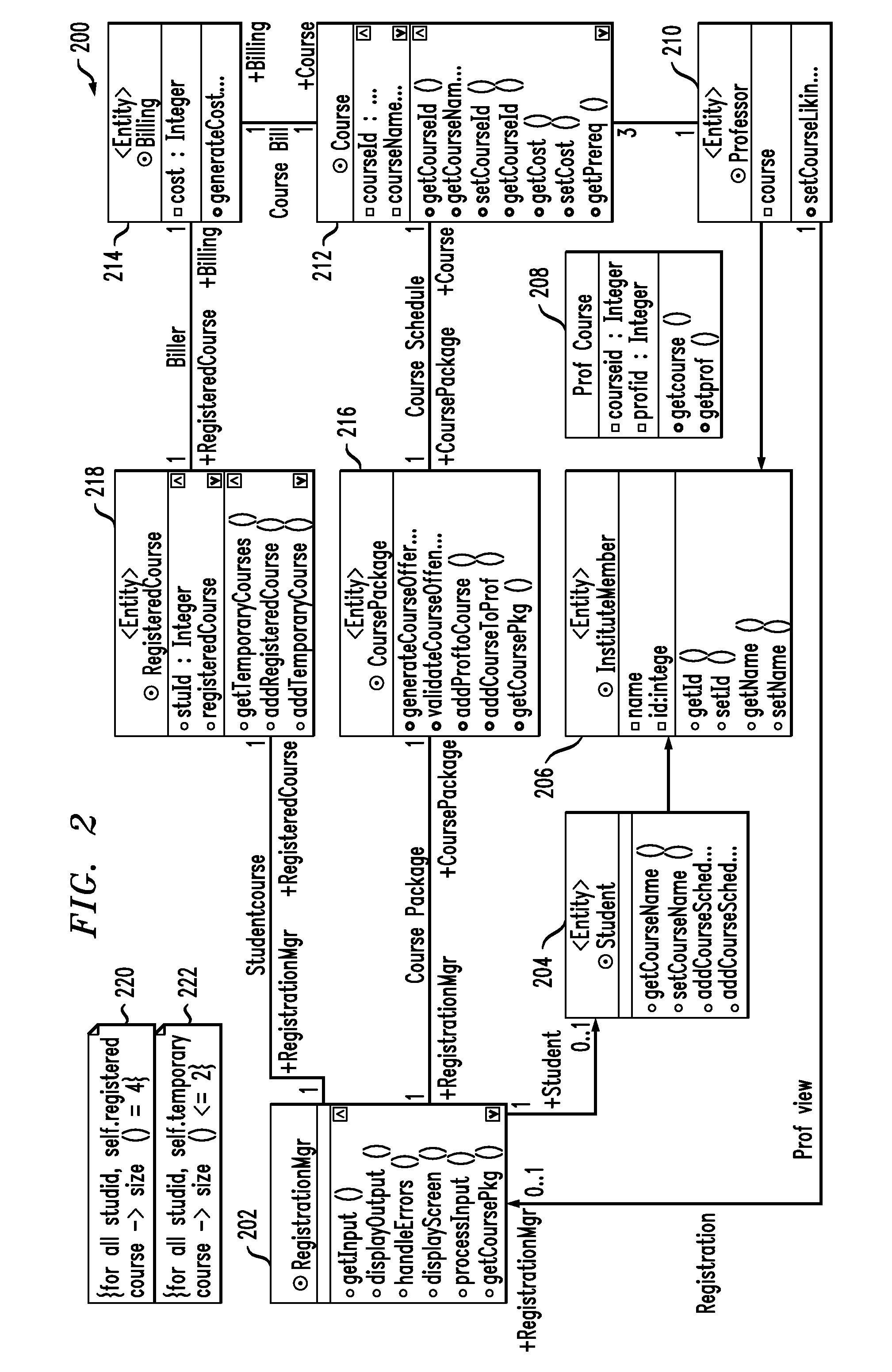
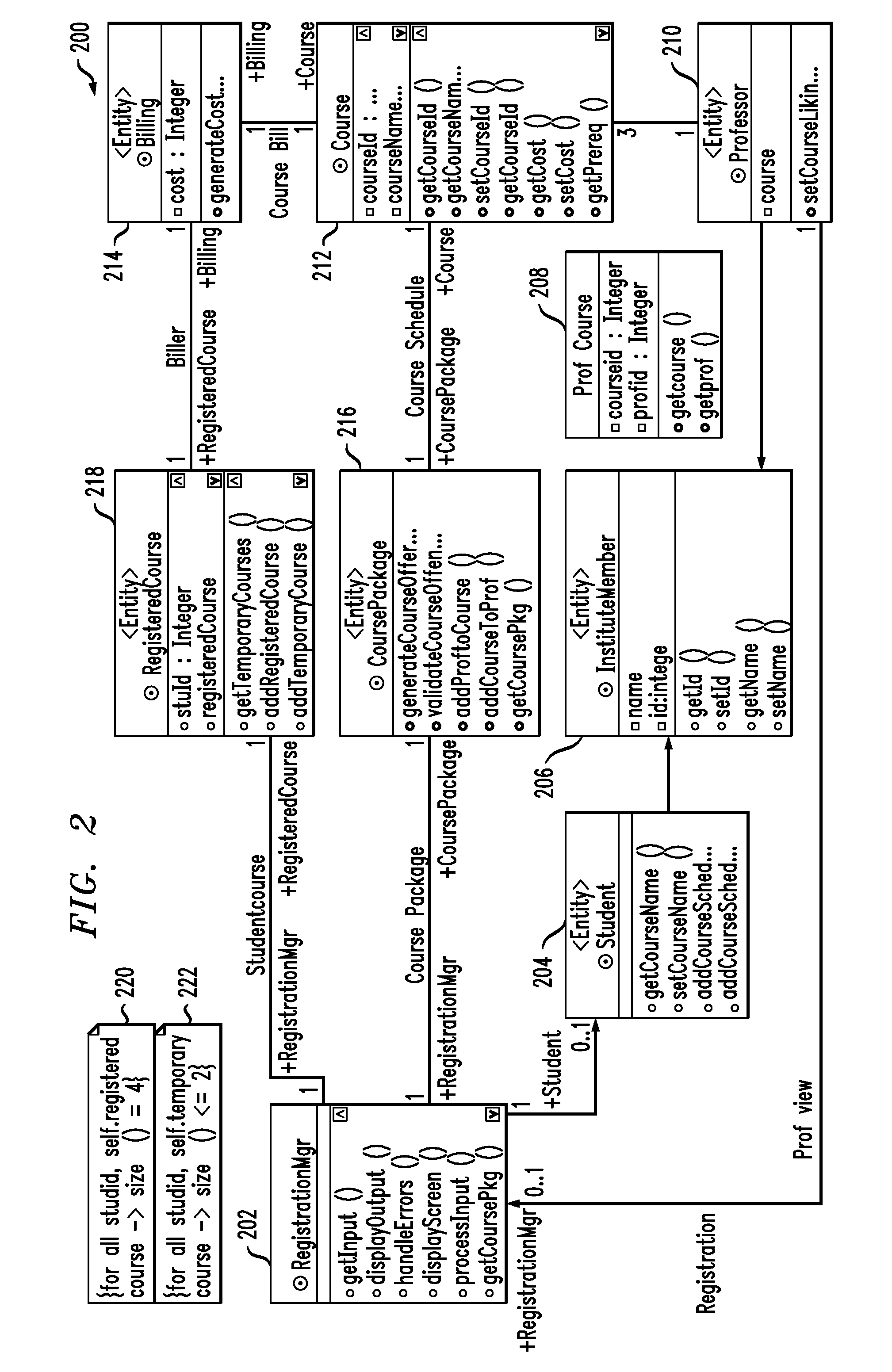
In software engineering, a class diagram in the Unified Modeling Language (UML) is a type of static structure diagram that describes the structure of a system by showing the system's classes, their attributes, operations (or methods), and the relationships among objects.
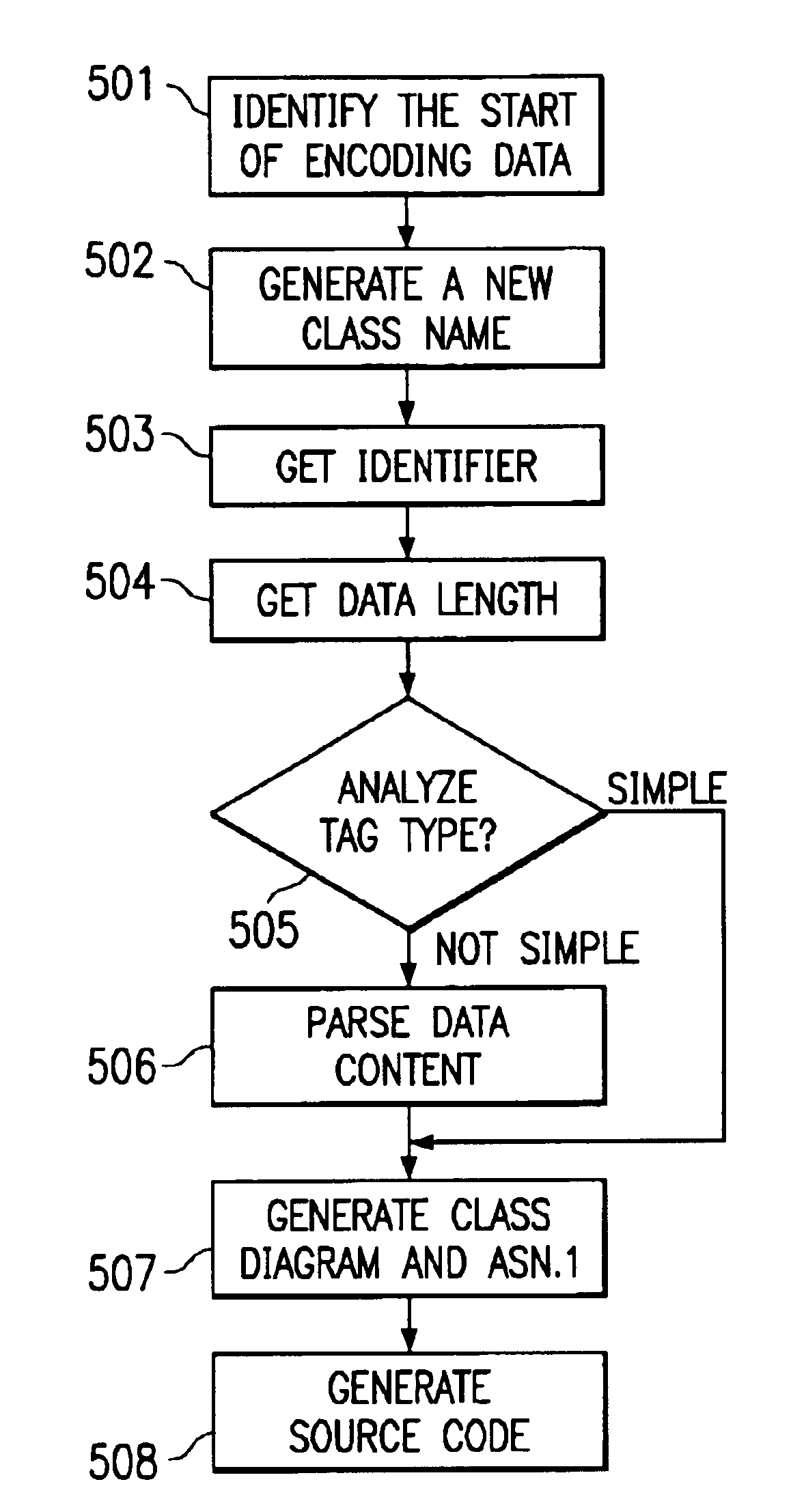
Strategy for dynamically modeling ASN.1 data to an object model
InactiveUS20020129331A1Specific program execution arrangementsSpecial data processing applicationsData streamAnalysis data
A method, program and system for mapping ASN.1 data to an object model are provided. The invention consists of identifying the start of a data stream and then generating a new object name for the data. Next, the data is parsed to get the identifier and the data length. Then the data's tag type is analyzed. If the tag type is simple, a class diagram is generated for the data and then the source code for the data is generated. If the tag type is not simple, a subroutine is called to further parse the data before generating the class diagram and source code.
Owner:IBM CORP
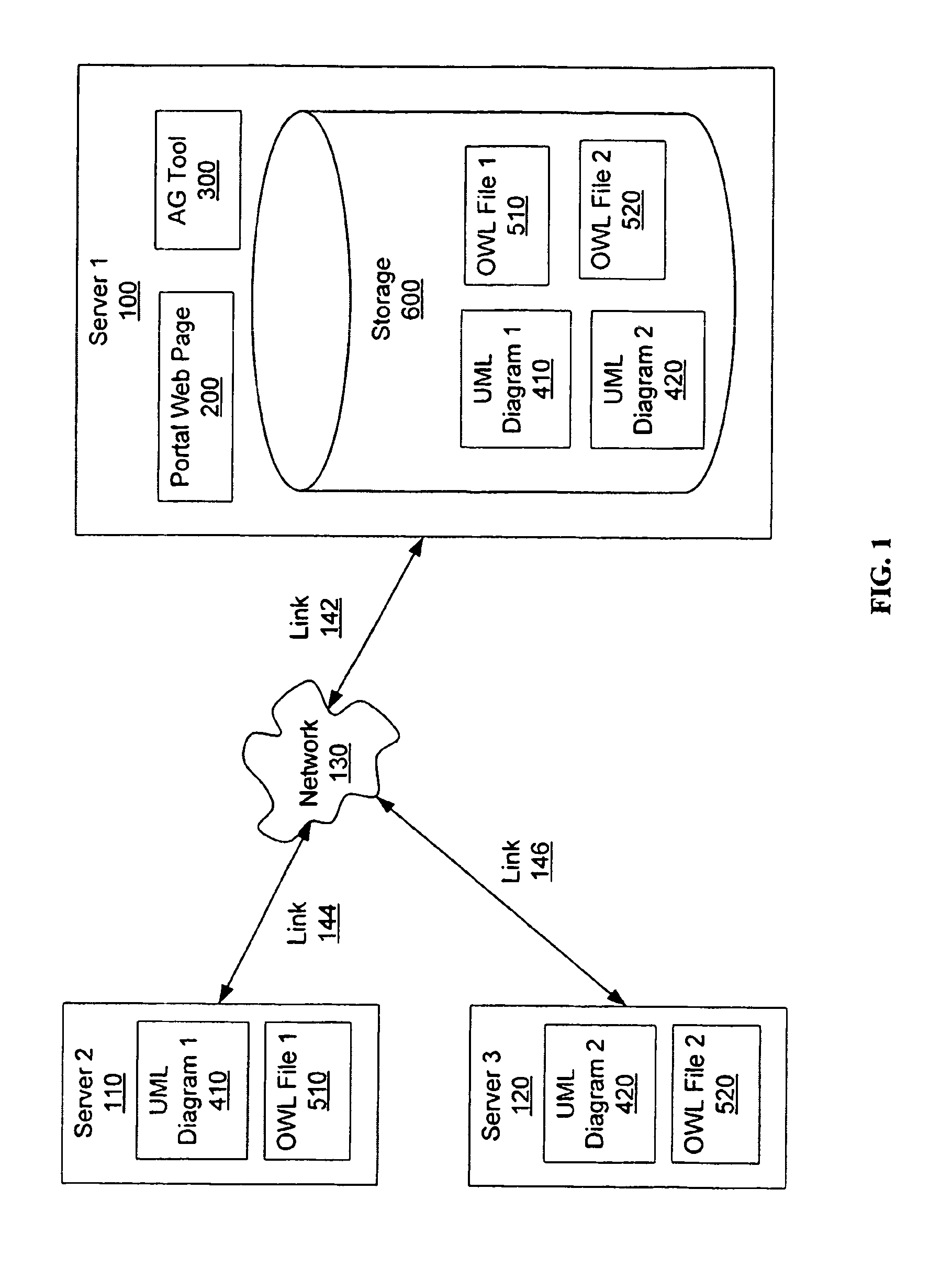
System and method for the autogeneration of ontologies
ActiveUS8065655B1Easily modify/extendExpensive softwareDigital data information retrievalSoftware designDEVSClass diagram
A utility transforms a class diagram representing an ontology, such as a UML class diagram, into a fully-described, standard representation of an ontology such as OWL file. It may be based on Rational Software Architect (RSA) and its model transformation capabilities. The RSA transformation framework uses a Visitor-like pattern for iterating over all of the UML elements in a UML diagram. The framework allows the developer to configure ‘Rule’ classes that are executed when different types of UML elements are encountered. Each UML element is visited once, which causes each rule to be fired for each element type. Rules are configured for just those UML types that are of interest to the transformation, for example classes, primitives, properties, packages and instances. Each rule in the implementation is then written to delegate to a Registrar class, which has a method for building the ontology model from the registered UML elements.
Owner:IBM CORP
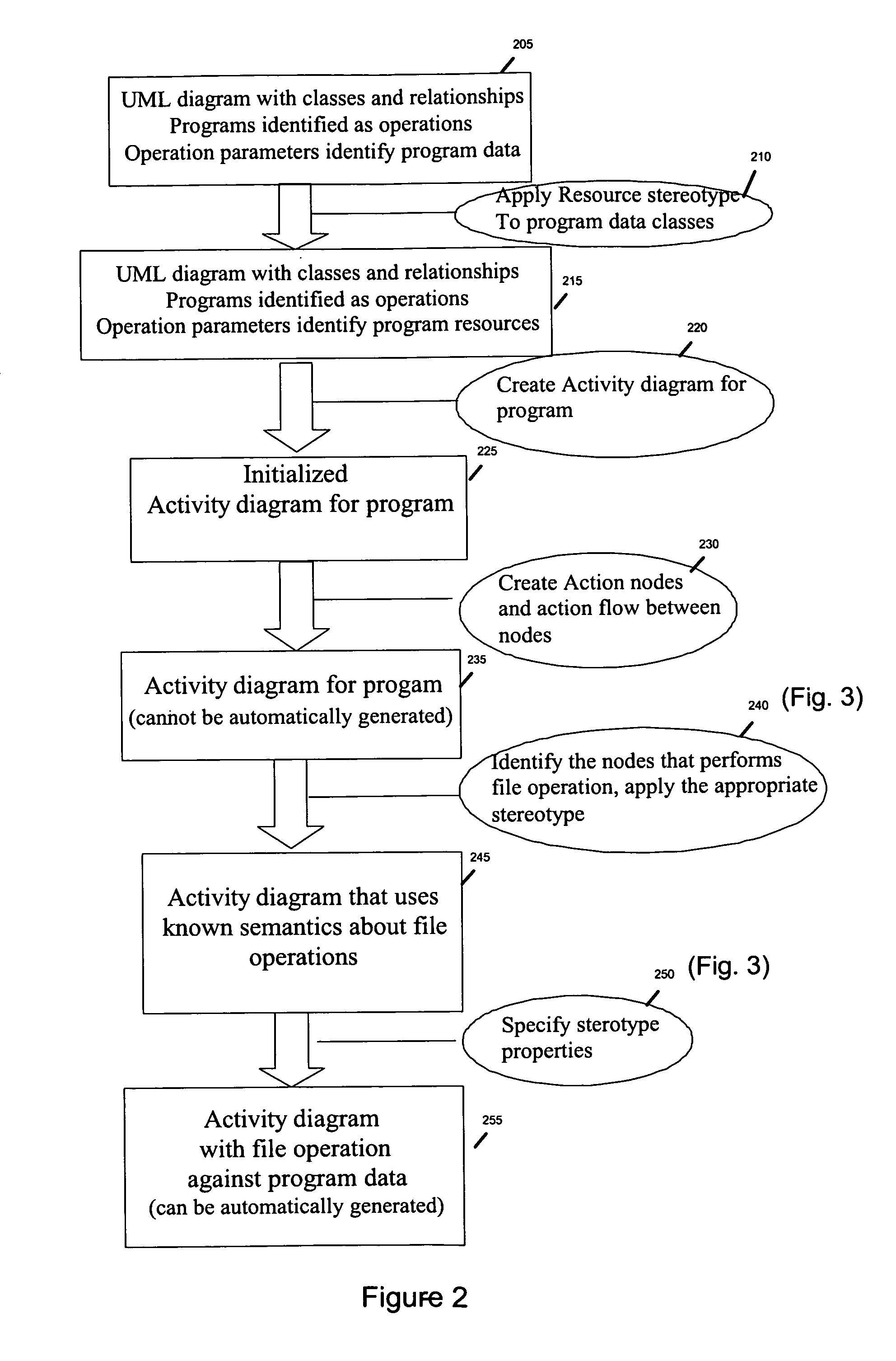
Creating graphical models representing control flow of a program manipulating data resources
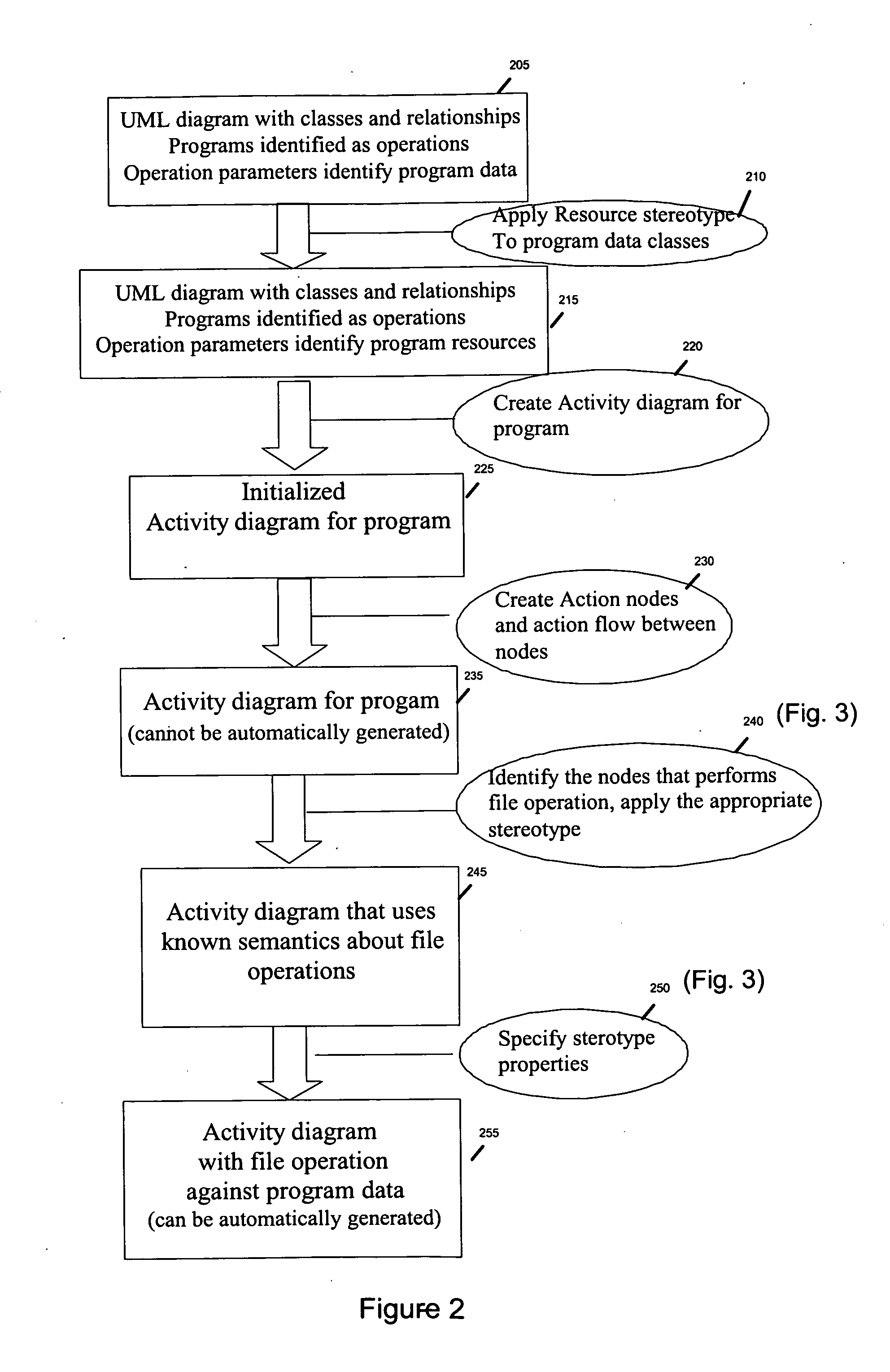
InactiveUS20090241088A1Requirement analysisSpecific program execution arrangementsData classControl flow
A class diagram can be created for an application. The application can use a modeling language. The application can be configured for creation of the class diagram. The class diagram can comprise classes and relationships. The application can also be configured for creating flow diagrams comprising actions, relationships, and definitions of model element types. The application can also be configured to create new model elements in the class diagram and flow diagrams. A program new model element type can be applied to relevant class operations in the class diagram and a resource new model element type to relevant data classes of the class diagram. A flow diagram can be created per program of the application. The flow diagrams can be applied as many new model element types as different types of actions exist in the flow diagrams. These actions can represent the operations on resources.
Owner:IBM CORP
Graphical method of semantic oriented model analysis and transformation design
InactiveUS20090024965A1Input/output for user-computer interactionSemantic analysisInstrumental functionGraphics
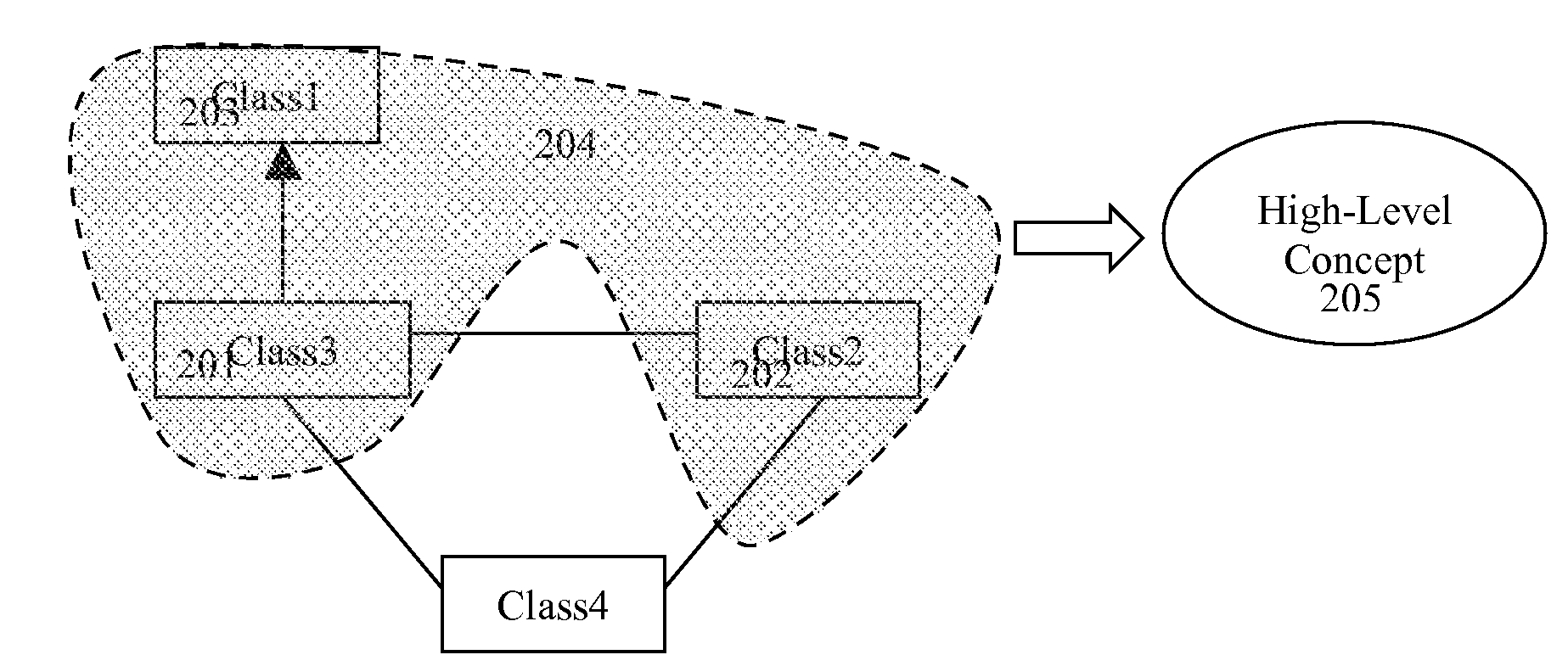
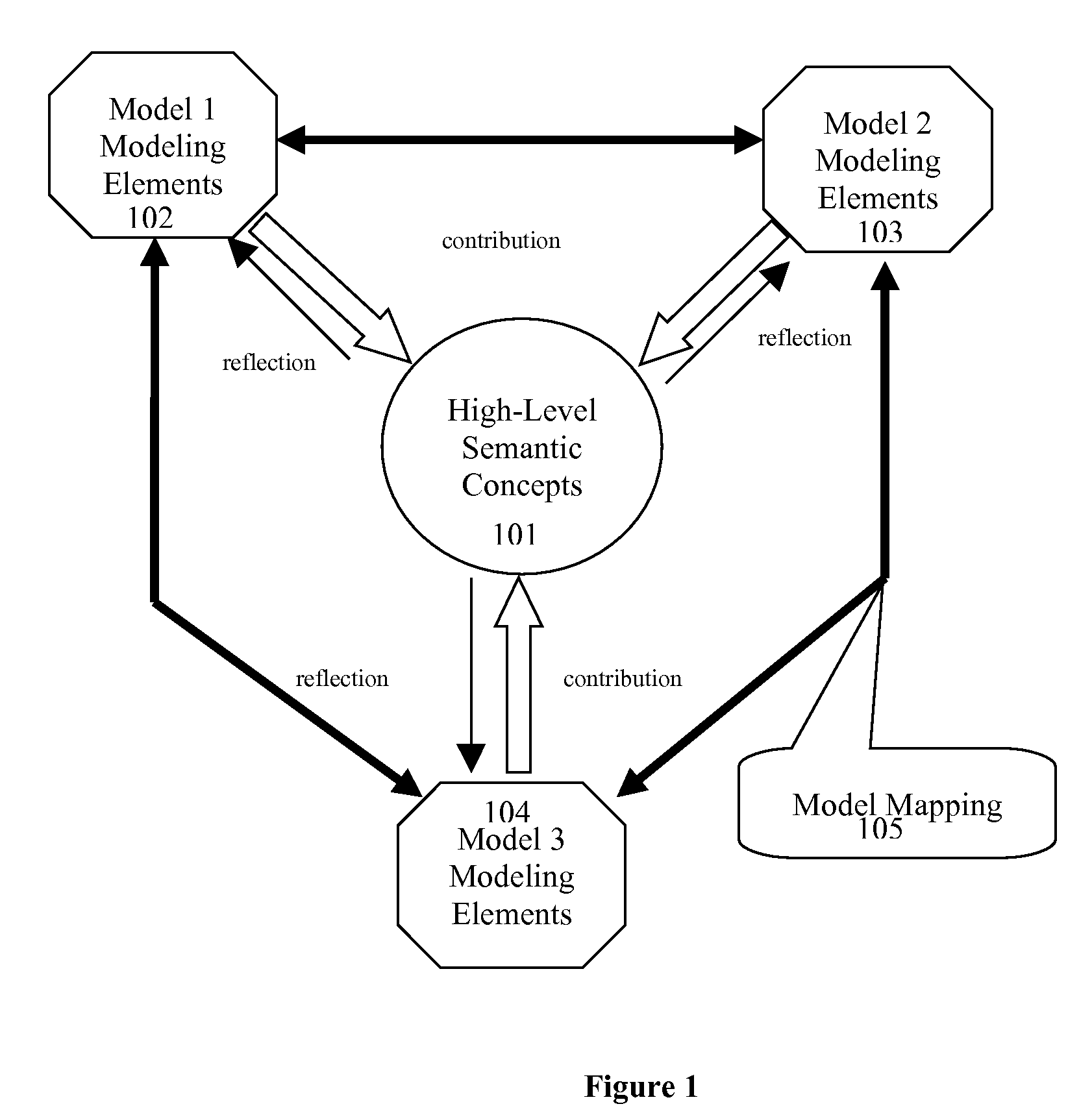
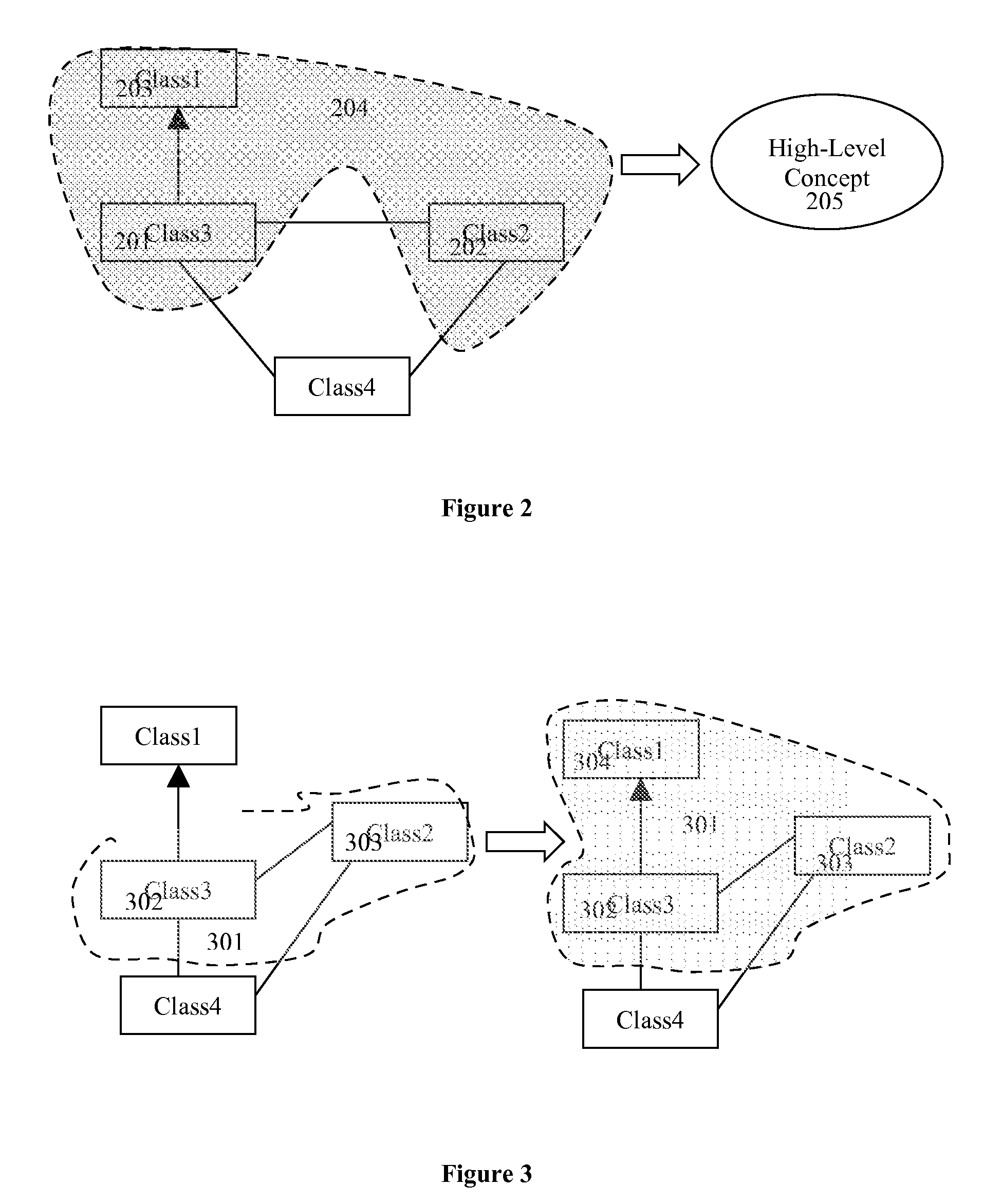
User is given the new modeling capability, a Semantic Lasso, which allows grouping of the model elements, so they can be mapped or transformed to the high-level concepts of business ontology. Such grouping is done by drawing of the line contour around relevant to advertised high-level concept model elements on one of the OMG Unified Modeling Language (UML) class diagrams. In addition the user is given a capability to specify extension points of the high-level concepts and the projection of such extension points to the individual model. Another tooling capability, a Semantic Transformation Lens, allows dynamic graphical projection of the individual model fragments to the high-level concepts as those elements are being selected. Semantic Transformation Lens provides the mechanism of reasoning-based smart selection.
Owner:ZHDANKIN ALEKSANDR +1
High-resolution SAR image classification method based on non-down-sampling contourlet full-convolution network
ActiveCN107239751AHas the ability to classify and discriminateAvoid duplicationScene recognitionData setClassification methods
A high-resolution SAR image classification method based on a non-down-sampling contourlet full-convolution network is provided, which comprises: inputting a high-resolution SAR image to be classified; performing multi-layer non-down-sampling contourlet transform on each pixel in the image; obtaining the low-frequency coefficient and the high-frequency coefficient of each pixel; selecting and fusing the low-frequency coefficients and high-frequency coefficients to form a pixel-based characteristic matrix F; normalizing the element values in the characteristic matrix F to obtain a normalized characteristic matrix F1; dicing the normalized characteristic matrix F1 to obtain a characteristic block matrix F2 used as sample data; constructing a training data set characteristic matrix W1 and a testing data set characteristic matrix W2; constructing a classification model based on a full convolution neural network; training the classification model; utilizing the well-trained model to classify the testing data set T to obtain the category of each pixel in the testing data set T; comparing the obtained category of each pixel with a class diagram; and calculating the classification accuracy. With the method, the classification accuracy and speed are increased.
Owner:XIDIAN UNIV
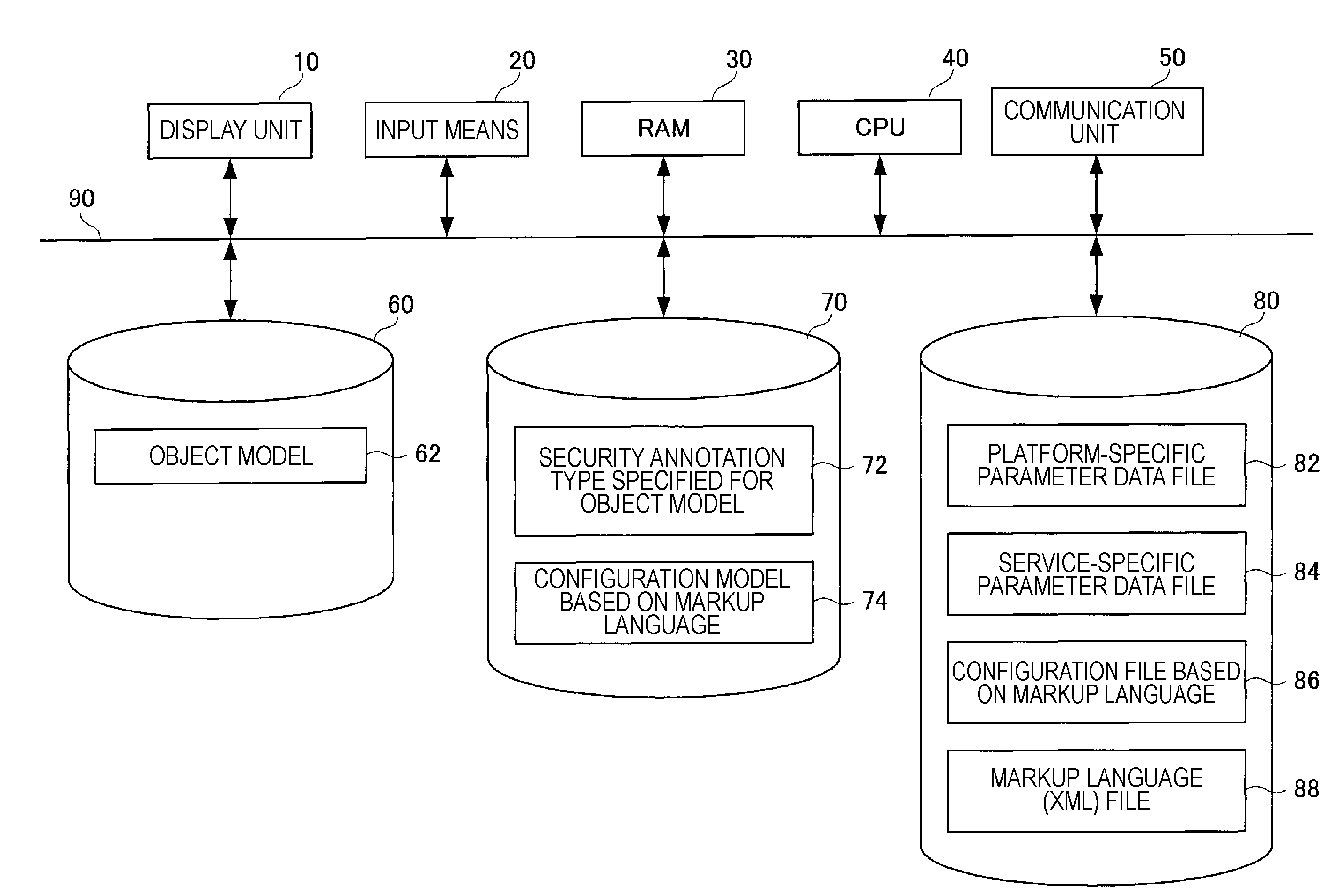
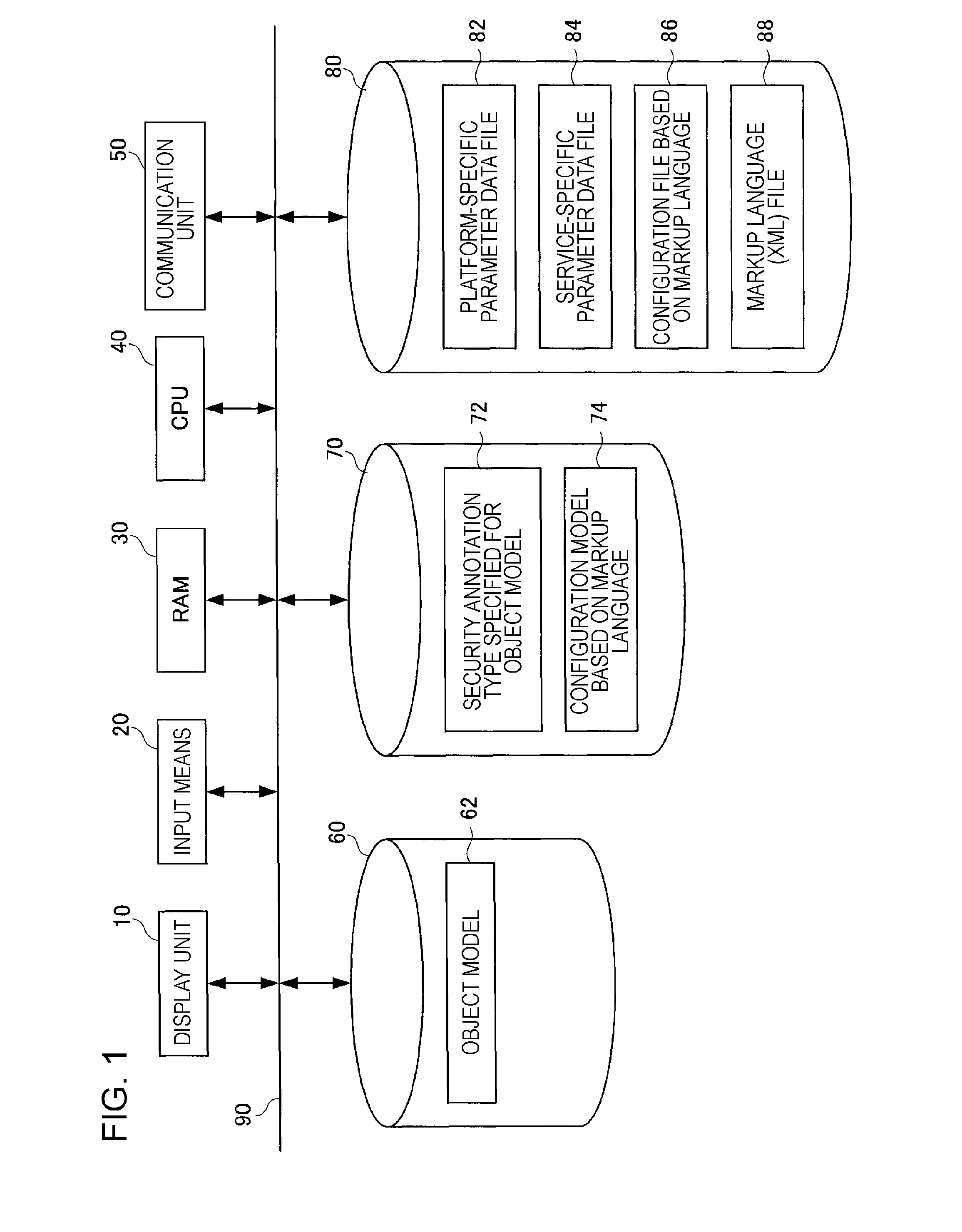
Software development apparatus for model that requires security
InactiveUS20070150935A1Platform integrity maintainanceProgram/content distribution protectionWeb serviceConfigfs
A software development apparatus for developing application software based on an object model that requires security in a web service application is provided. The software development apparatus includes a display unit that displays, in a class diagram of the application software, security annotation for adding security requirements for a service, input means for inputting the security annotation, transforming means for transforming the class diagram into a configuration model based on a markup language, and configuration-file creating means for creating a configuration file based on a markup language by serializing the configuration model based on a markup language. The security annotation includes the security requirements and a token class of a security token that is a certificate for declaring identity of a client to a server.
Owner:SERVICENOW INC
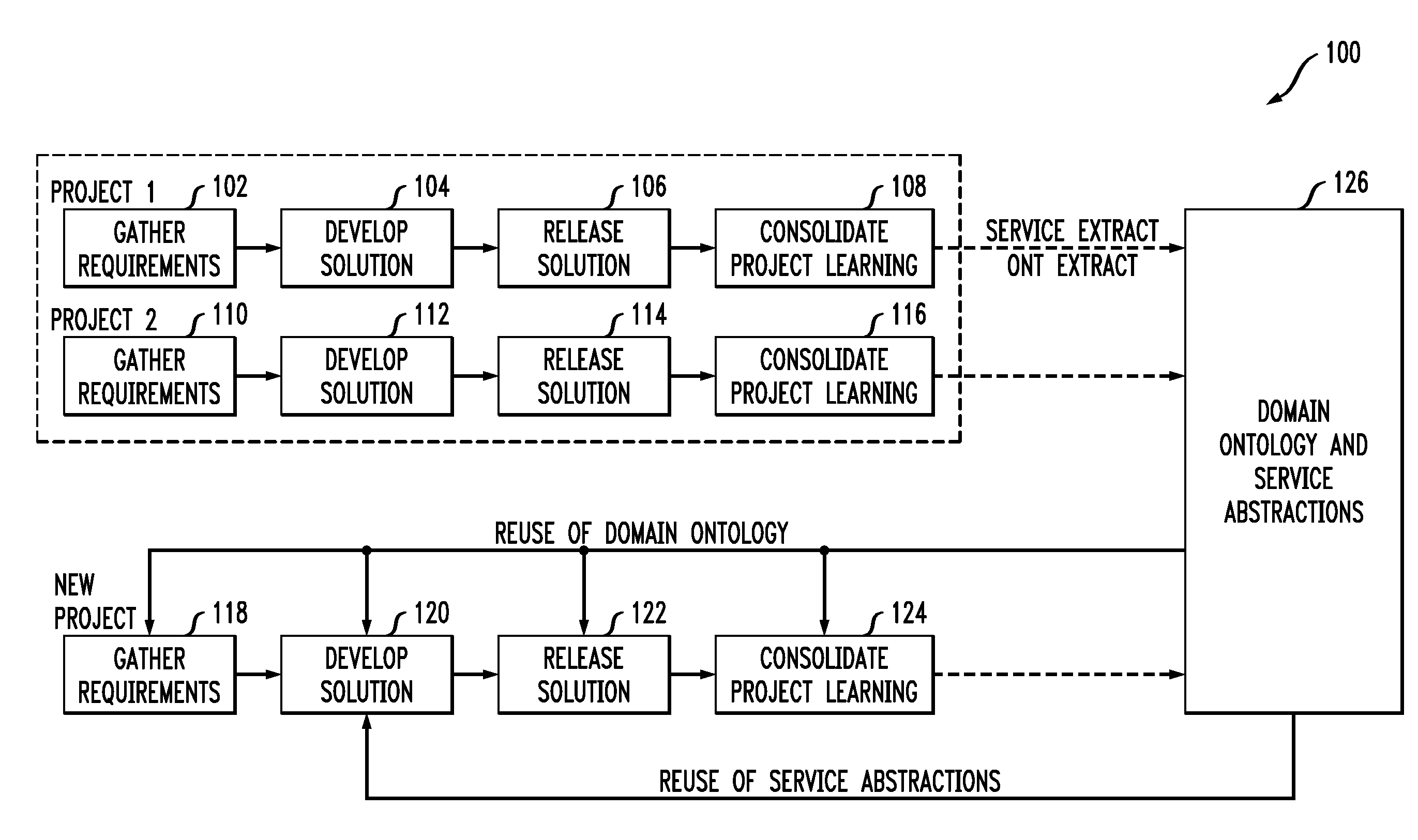
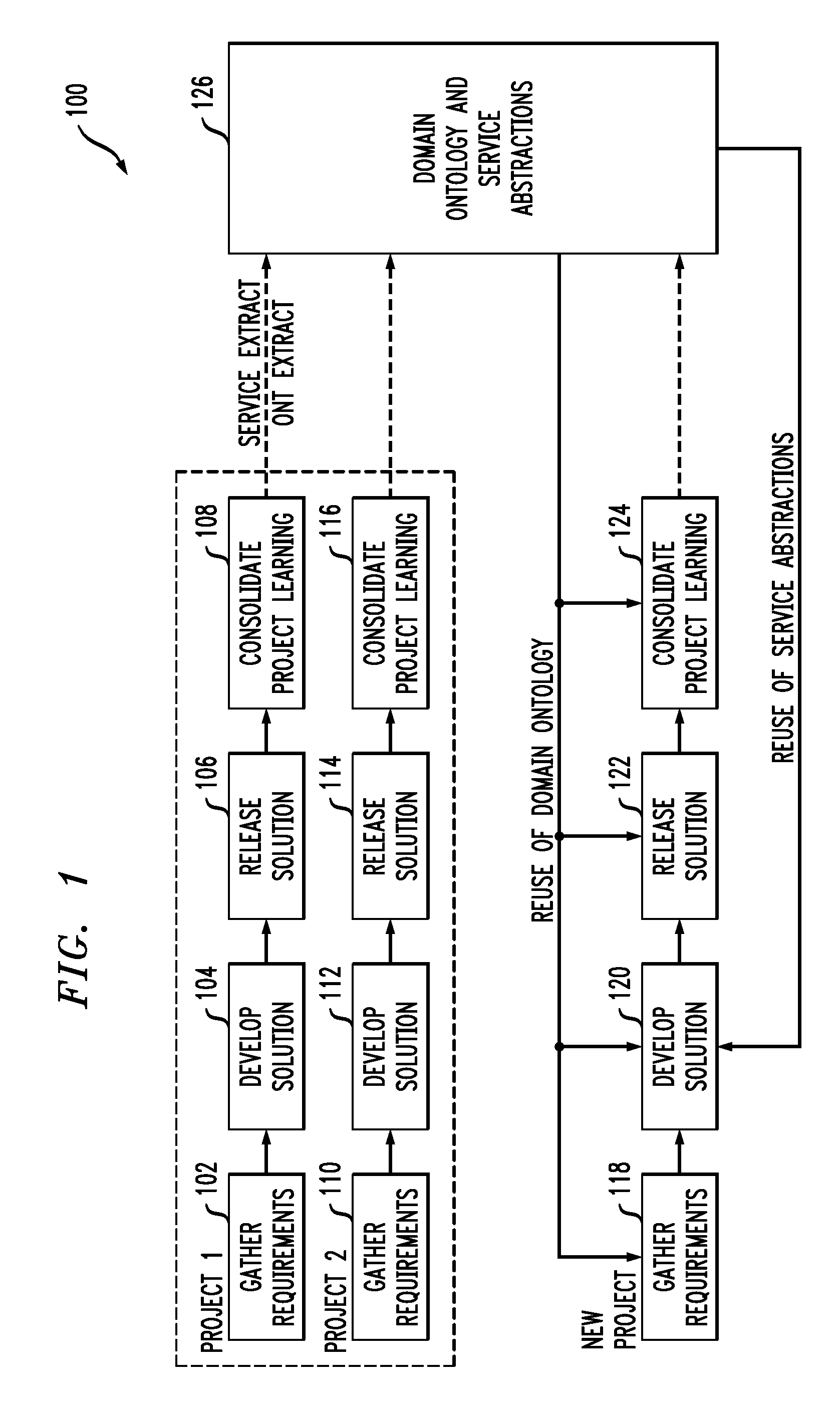
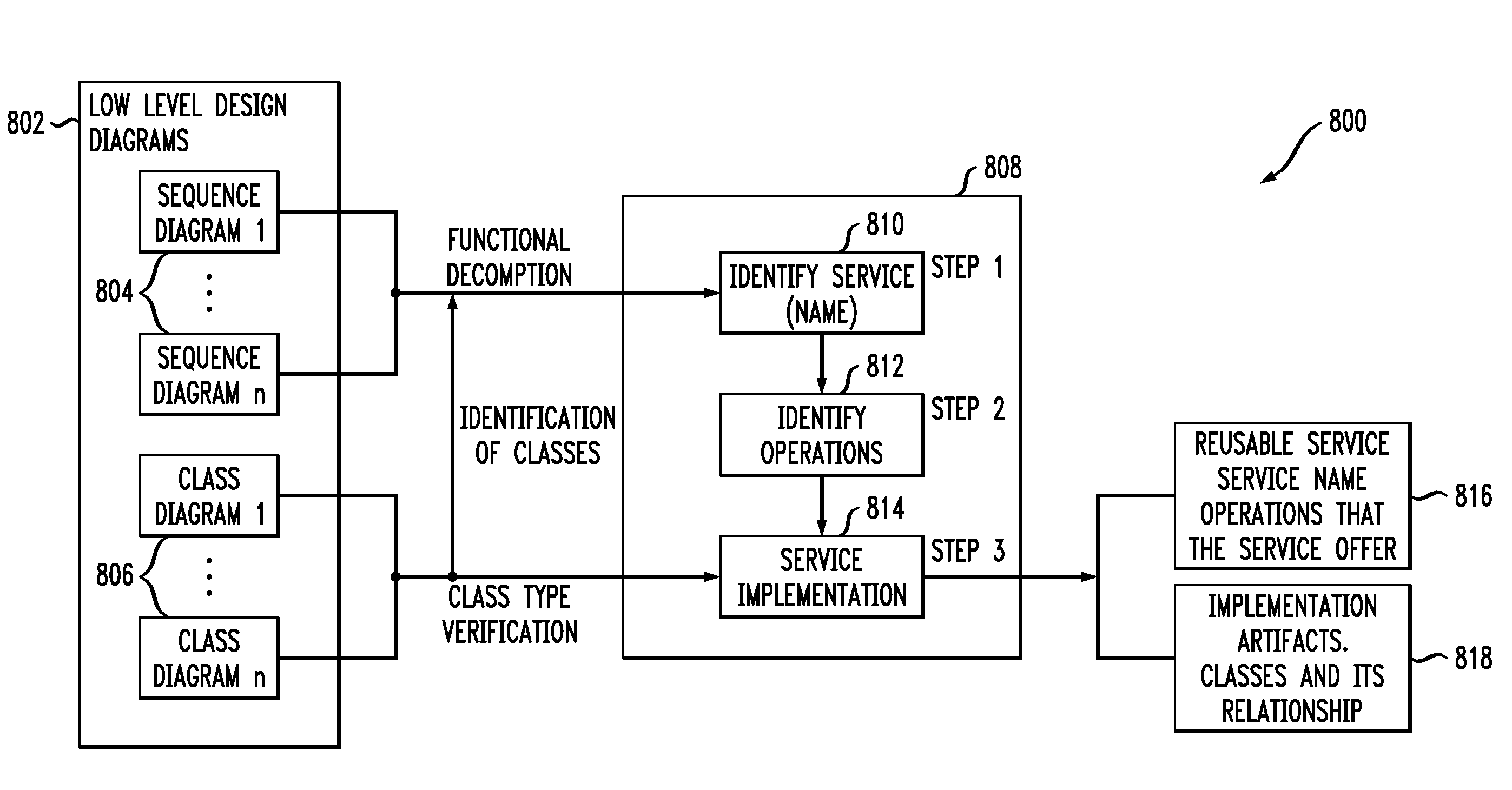
Generating functional artifacts from low level design diagrams
InactiveUS20100122238A1Shorten development timeLess timeRequirement analysisSoftware reuseLevel designClass diagram
At least one design diagram is obtained from at least one previous software project. At least one service abstraction is extracted from the at least one design diagram. The at least one service abstraction is reused in a new software project. In another aspect, requirements are obtained for a current software project; at least one class diagram is obtained from at least one previous software project; a dependency graph is generated from the at least one design diagram, using link analysis; relationships between classes in the dependency graph are analyzed to obtain functional artifacts for the requirements; and the functional artifacts are reused in the new software project.
Owner:IBM CORP
Extension UML-based Web application formalization modeling and verification method
InactiveCN108830085AGuaranteed designEnsure consistencyPlatform integrity maintainanceWeb applicationSoftware system
The invention discloses an extension UML-based Web application formalization modeling and verification method, which comprises the following steps: step (1), extracting functional demands of a software system to be designed, and performing demand analysis, step (2), performing UML modeling; step (3), using XML to represent the aforementioned UML2.3 model; step (4), generating formalization description; step (5), performing security attribute verification. The invention provides a feasible method for automatic conversion from the UML2.3 model to the formalization language to expand class diagram, sequence diagram and state diagram in the UML2.3 to implement protocol verification in Web application and implement automatic conversion from the UML model to pi calculation formalization language, and greatly reduces the difficulty of carrying out formalization modelling on the protocol directly; the formalization modeling verification tool is used, and the formalization verification model isrefined; the loophole of the formalization model is detected through display of the verification result and analysis of the attack path, which facilitates quick refining of the model and efficient defect detection.
Owner:TIANJIN UNIV
Strategy for dynamically modeling ASN.1 data to an object model
InactiveUS6883164B2Specific program execution arrangementsSpecial data processing applicationsAnalysis dataData stream
A method, program and system for mapping ASN.1 data to an object model are provided. The invention consists of identifying the start of a data stream and then generating a new object name for the data. Next, the data is parsed to get the identifier and the data length. Then the data's tag type is analyzed. If the tag type is simple, a class diagram is generated for the data and then the source code for the data is generated. If the tag type is not simple, a subroutine is called to further parse the data before generating the class diagram and source code.
Owner:INT BUSINESS MASCH CORP
Design-mode-guided Java code reviewing method
ActiveCN103279631AImplement the consistency check functionReduce human interventionSpecial data processing applicationsTime informationGenerative Design
The invention provides a design-mode-guided Java code reviewing method. First of all, users provide a source code and design time information of the source code of a Java program to be reviewed, class diagrams in the design time information are analyzed, design mode information is extracted, and corresponding relationship of all participation roles of a design mode is generated. According to the information, by means of a pre-defined rule template, the rule template is instantiated as a group of constraint rules which should be met on codes, an abstract syntax tree of the Java source code to be reviewed is analyzed by reading the rules, whether achievement meets design time constraint is judged, and conditions which do not meet constraint are prompted. By means of the method, the code can be reviewed automatically, work load of manual examination of the code in a whole reviewing process is reduced, and the reviewing efficiency of the code is improved.
Owner:NANJING UNIV
Complex network-based object-oriented integration testing method
InactiveCN101477490AIncrease coverageReduce in quantitySoftware testing/debuggingSoftware networkIntegration testing
The invention discloses an integration test method facing objects and based on a complex network. The method comprises the following steps: (1) establishing a system structural model of detected software by adopting a unified modeling language, and stating a UML (unified modeling language) class diagram to a software network G equal to (V, E); (2) traversing the whole software network, recording the class relied by each class and the in-degree and the out-degree of the class in a tetrad; (3) first, intensively testing the class with a big in-degree and an out-degree of zero; (4) in secession, detecting the relied class utilizing the class without adding classes or a new class in each detection; and repeatedly conducting step (4) along the testing sequence relying on class hierarchy, so as to ensure that the class detected prior is superior to that detected afterwards until the system for constructing complete detected software. The invention combines complex network and the object-facing software test together, and conducts integration test to the object-facing procedures combining with the internal topology structural characteristics of the object-facing software, thereby optimizing test cases and reducing test work load.
Owner:SHANGHAI SECOND POLYTECHNIC UNIVERSITY
Reverse engineering based model base structuring method
InactiveCN104391706ARealize the structureSpecial data processing applicationsSpecific program execution arrangementsSource code fileRelational database
The invention discloses a reverse engineering based model base structuring method. The reverse engineering based model base structuring method includes steps of capturing source codes of an open source project from Internet by web crawlers; clearing the captured source codes to acquire effective source code files; subjecting the effective source codes to reverse engineering analysis to structure an initial UML (unified modeling language) class diagram; simplifying the initial UML class diagram to obtain a simple UML class diagram; storing the simple UML class diagram into a diagram database. A great many source codes on Internet can be converted into UML class diagram models, these models are stored into a non-relation database after simplified, and a model base is structured. By simplifying the reverse engineering, the class diagram models generated contain more code structure information, and the reverse engineering based model base structuring method is more accurate than other methods.
Owner:NANJING UNIV
Stereoscopic image objective quality evaluation method based on physiological and psychological stereoscopic vision
The invention belongs to the field of image process, and provides a quality evaluation method capable of comprehensively considering physiological and psychological stereoscopic vision clues, and can effectively realize objective quality evaluation on a stereoscopic image. According to the technical scheme of the invention, a stereoscopic image objective quality evaluation method based on physiological and psychological stereoscopic vision comprises the following steps of: a first step of calculating absolute difference of a left view and a right view; a second step of converting the absolute difference into a grey-scale image which is taken as a characteristic parameter capable of representing the quality of a stereoscopic image; a third step of carrying out K-means cluster segmentation on a converted grey-scale image; a fourth step of differentially treating by distributing different weights for different class diagrams; a fifth step of calculating a WMSSIM value between a class diagram of the original stereoscopic image and a class diagram of a distortion stereoscopic image; and a sixth step of finally obtaining stereoscopic image quality evaluation index 3DM. The method is mainly applied to stereoscopic image objective quality evaluation.
Owner:TIANJIN UNIV
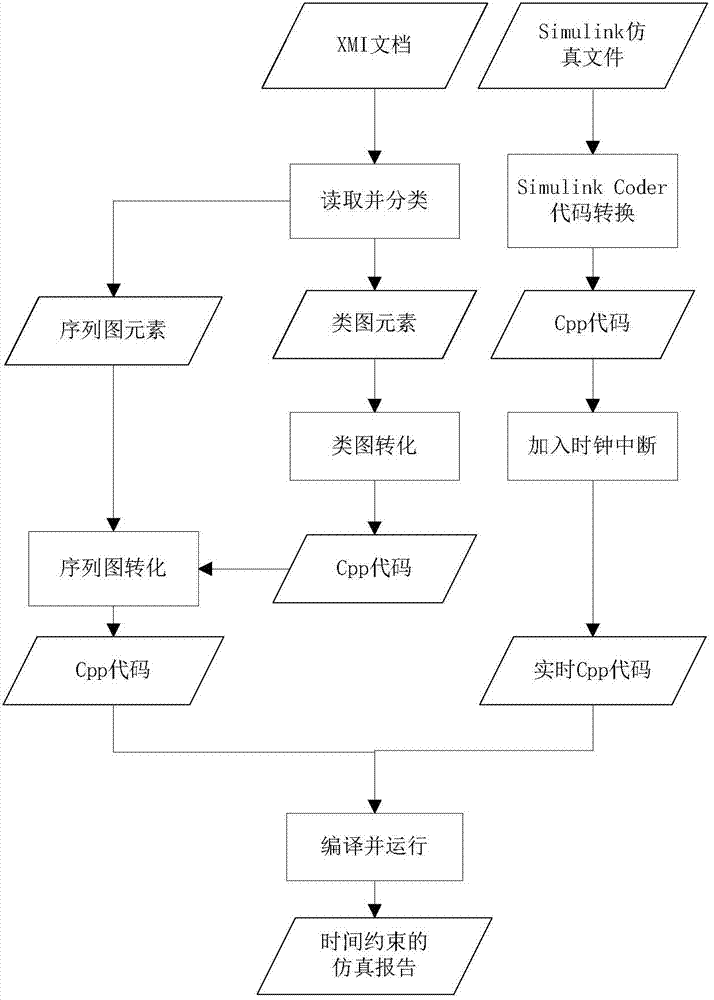
Simulation method of real-time embedded system
ActiveCN103885816AImplement automatic conversionRealize automatic fusionSoftware simulation/interpretation/emulationDocumentationClass diagram
The invention provides a simulation method of a real-time embedded system. Firstly, an XMI document is read, and elements of the XMI document are divided into a class diagram element collection and a sequence chart element collection; then the class diagram element collection is converted to be C++ codes; on the basis of the C++ codes of class diagrams, the sequence chart element collection is converted to be C++ codes; a Simulink model is converted to be C++ codes through a Simulink Coder, clock interrupt is added, and the C++ codes become real-time codes; then the C++ codes and the real-time codes are combined together according to the set in a class diagram model, an executable file can be compiled and generated, the executable file operates on a target platform, then the simulation of the whole real-time embedded system is achieved, and a test result is given. According to the method, automatic codes of the class diagram model, a sequence chart model and the Simulink model based on UML can be generated, time constraint information is extracted, simulation is carried out by executing the generated codes, and a result report whether the time constraint of the system is met or not is given.
Owner:NANJING UNIV
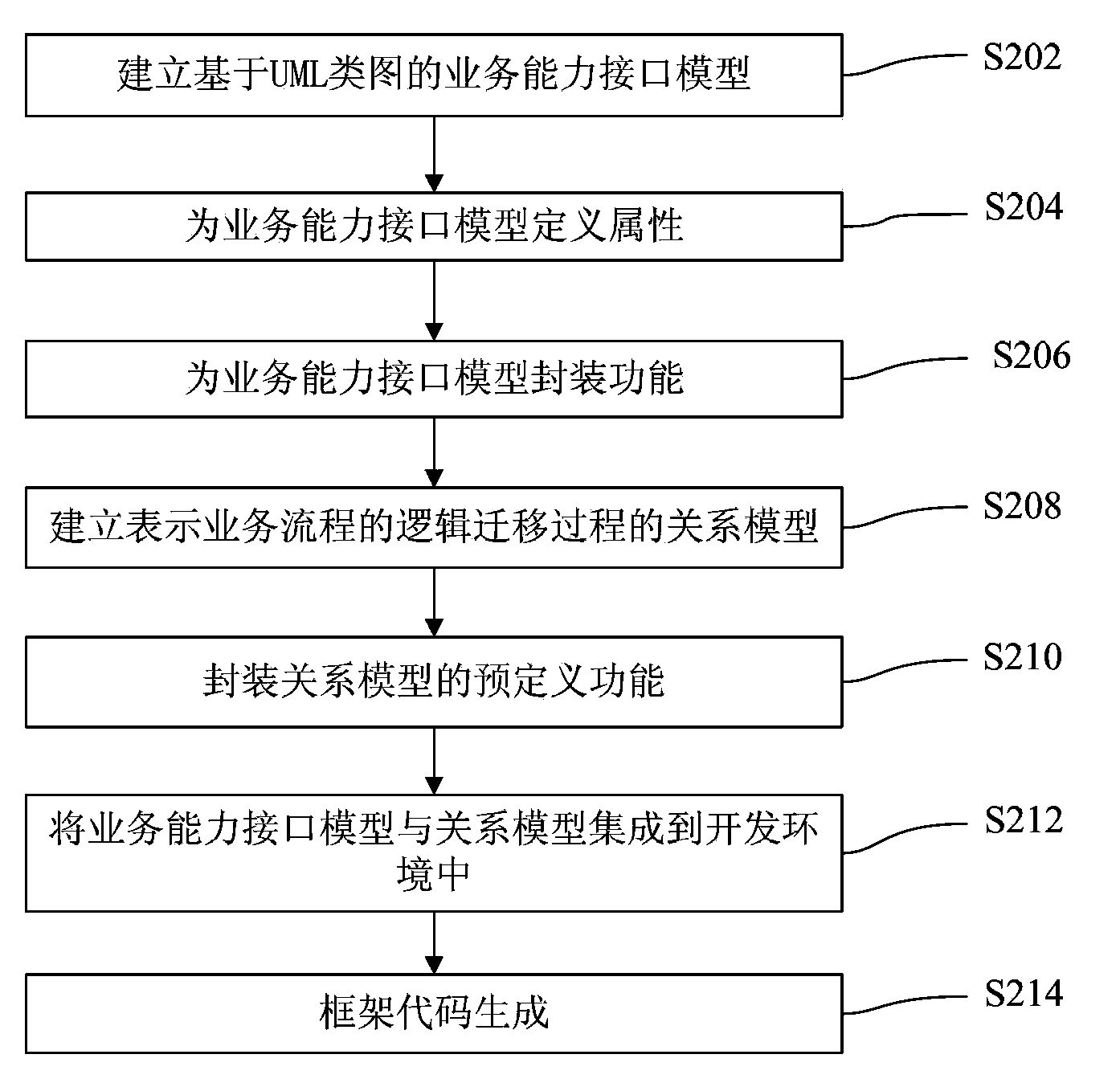
Service process modeling method and device
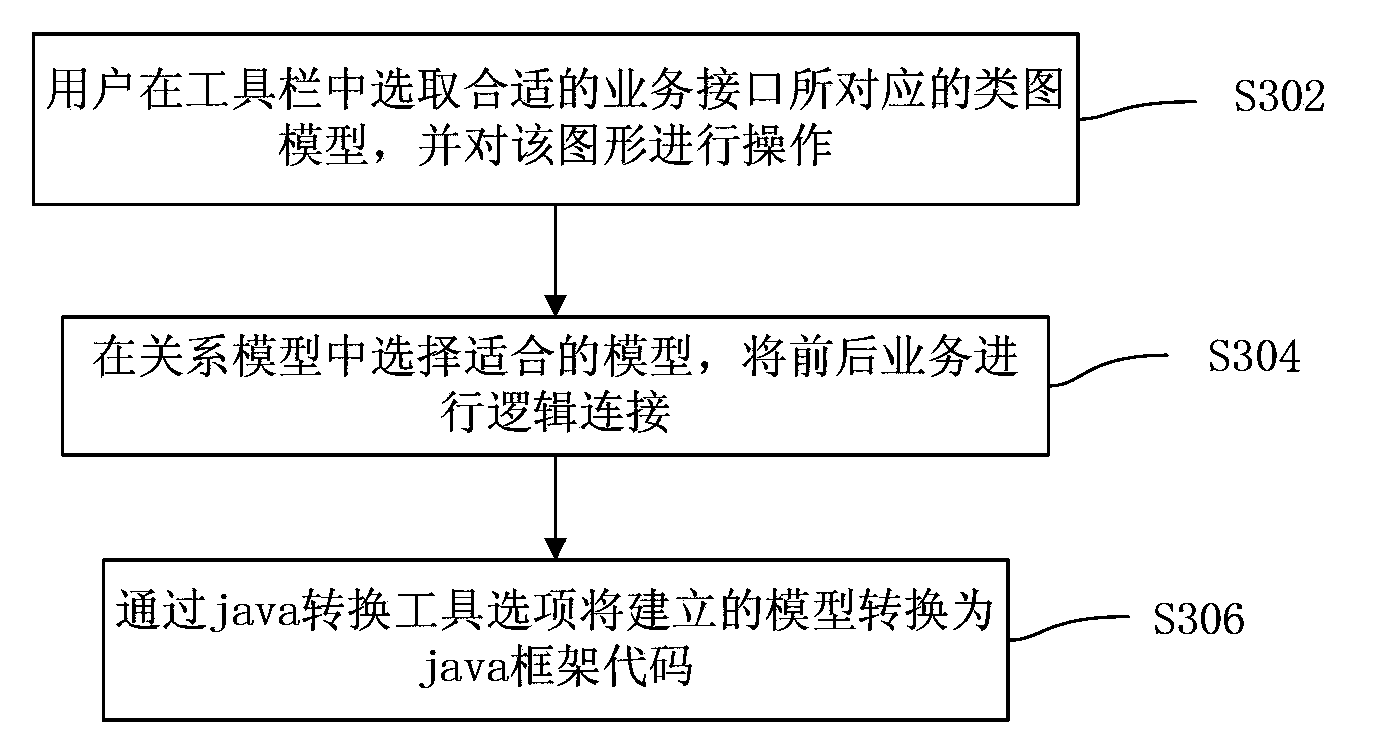
ActiveCN103513976AEasy to useAddress limitationsSpecific program execution arrangementsThird partySoftware engineering
The invention discloses a service process modeling method and device. The method comprises the steps that a service ability interface model of each service ability interface required by service processes is built according to a unified modeling language class diagram; one or more logical relationship models showing the logical relationship between every two service ability interface models are built; according to the fact that the logical relationship models are connected with all the service ability interface models, the service processes are arranged, and skeleton codes of the arranged service processes are obtained. According to the service process modeling method and device, the problem that limitation exists when dynamic graphs are used for showing the service processes is solved, further more, a third party can use service more conveniently, the requirement for programming ability and service ability interface understanding of a developer is reduced, and finally the effect of service ability of 'what you see is what you get' and function use experience is provided for a user.
Owner:ZTE CORP
Software defect measuring method based on complex network
The invention provides a software defect measuring method based on a complex network. The software defect measuring method based on the complex network can predict defects existing in a software system, so that influences in the future are prevented. The software defect measuring method based on the complex network comprises the following steps that first, a system class diagram is generated reversely according to a system executable file; second, the obtained system class diagram is converted into a network diagram of a software structure, wherein classes represent nodes, and relations between the classes represent edges; third, analysis at the level of the complex network is conducted according to the obtained network diagram, and the average shortest distance, an access degree and a clustering coefficient in complex network parameters are calculated by means of complex parameters, and a complex characteristic measuring value of software is obtained; fourth, a hierarchy measuring system is imported according to an object-oriented level, and an object-oriented characteristic measuring value of the software is obtained; fifth, the complex characteristic measuring value obtained in the third step and the object-oriented characteristic measuring value obtained in the fourth step are contrasted with known standard values, an assessment is conducted, and a defect measuring result prediction about the analyzed software is obtained finally.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Fault tree generation method for extended UML class diagram model of safety-critical system
InactiveCN104679510AOvercoming design failuresImplement automatic conversionSpecific program execution arrangementsSystems designSemantics
The embodiment of the invention provides a fault tree generation method for an extended UML class diagram model of a safety-critical system. The method comprises the steps of constructing the UML class diagram model of the safety-critical system, wherein all classes in the UML class diagram model comprise attributes and operations and have a certain relation, and the element semantics of the model is extended by a stereotype; storing the UML class diagram model into a file with a set format, analyzing the file with the set format corresponding to the UML class diagram model by a set information extraction algorithm to extract all the classes and the attributes and the operation information which correspond to all the classes in the UML class diagram model, and generating a fault tree of the UML class diagram model according to a set fault tree generation algorithm. According to the method disclosed by the embodiment of the invention, relevant safety analysis information is successfully embedded into the designed model of the safety-critical system, so that automatic conversion between the designed model of the system and a safety model of the system is realized, and the design fault of the safety-critical system can be effectively overcome.
Owner:BEIJING JIAOTONG UNIV
Software visualization method for object-oriented programming language source code
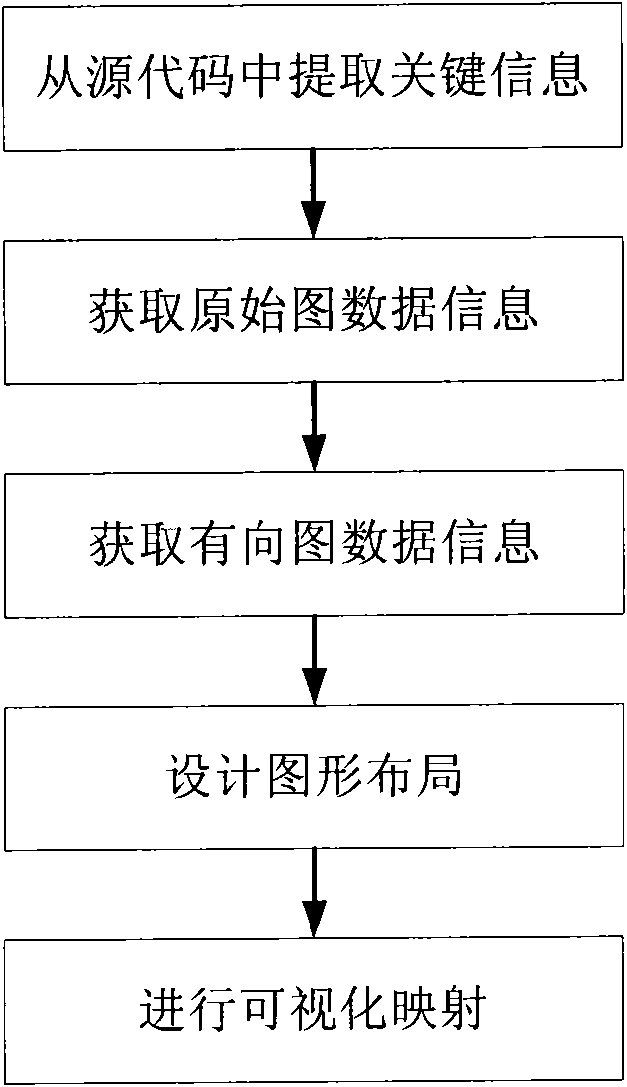
InactiveCN102385505AEasy to understandAccurate and intuitive internal structureSpecific program execution arrangementsDirected graphData information
The invention relates to a software visualization method for an object-oriented programming language source code, belonging to the technical field of software visualization. The method comprises the following steps of: (1) extracting key information from the source code; (2) acquiring data information of an original graph; (3) acquiring data information of a directed graph; (4) designing a graph layout; and (5) performing visualization mapping. With the adoption of the novel software visualization method for the object-oriented programming language source code provided by the invention, the defect of a class graph for the soft visualization is made up, and the internal structure of software and the status and the effect of types in the software can be accurately and intuitively reflected,so that a user can rapidly understand a software design level.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
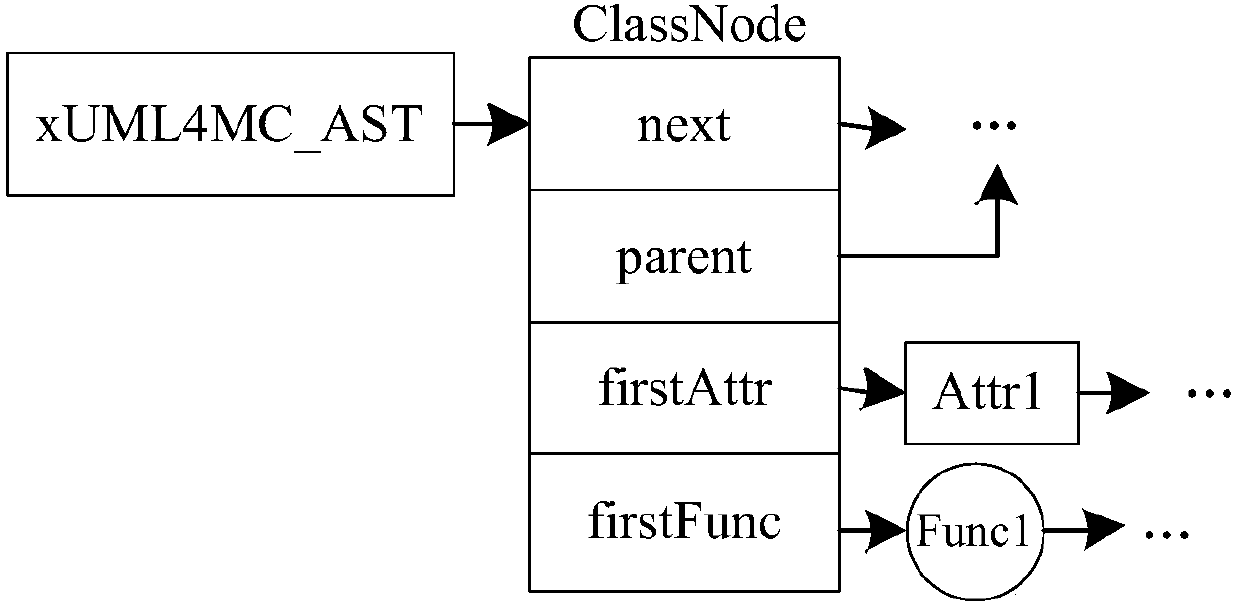
Method for converting xUML4MC model into MSVL program, and computer program
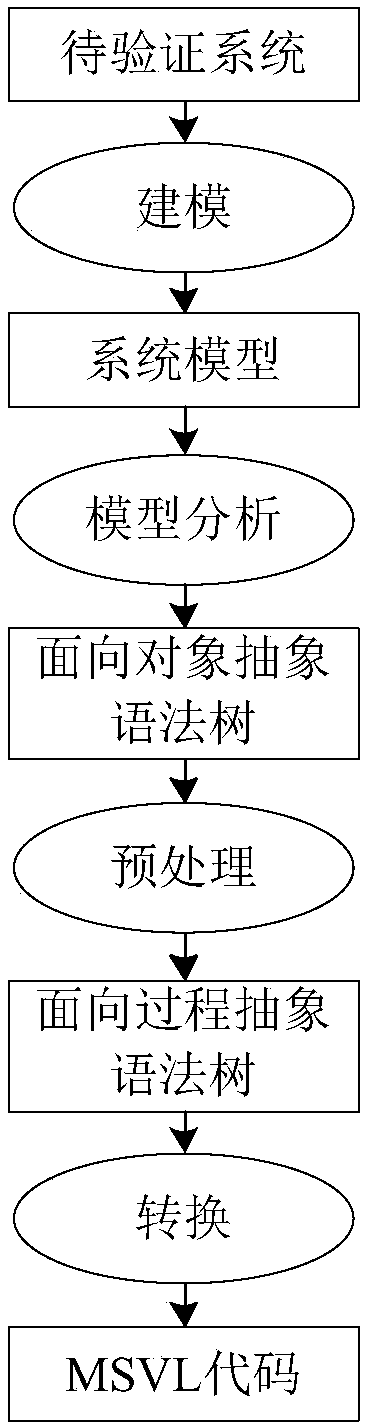
ActiveCN108037913AAchieve unificationImprove development efficiencyTransformation of program codeSoftware designModel descriptionProcess oriented
The invention belongs to the technical field of computer software and discloses a method for converting an xUML4MC model into an MSVL program, and a computer program. The method for converting the xUML4MC model into the MSVL program comprises the steps of establishing a class diagram model and activity diagram model description system; converting a class diagram and an activity diagram into an object-oriented abstract grammar tree; preprocessing and converting the object-oriented abstract grammar tree into a process-oriented abstract grammar tree; and converting the process-oriented abstract grammar tree into the MSVL program. The method is suitable for model detection system modeling; a UML-based visual modeling mode is intuitive in modeling and easy to master, and is more convenient andaccurate compared with a text language-based modeling mode; and the MSVL program generated by conversion can be directly used for model detection. The unification of software design modeling and modeldetection system modeling is realized; and the popularization of a model detection technology in the industrial circles is facilitated.
Owner:XIAN UNIV OF POSTS & TELECOMM
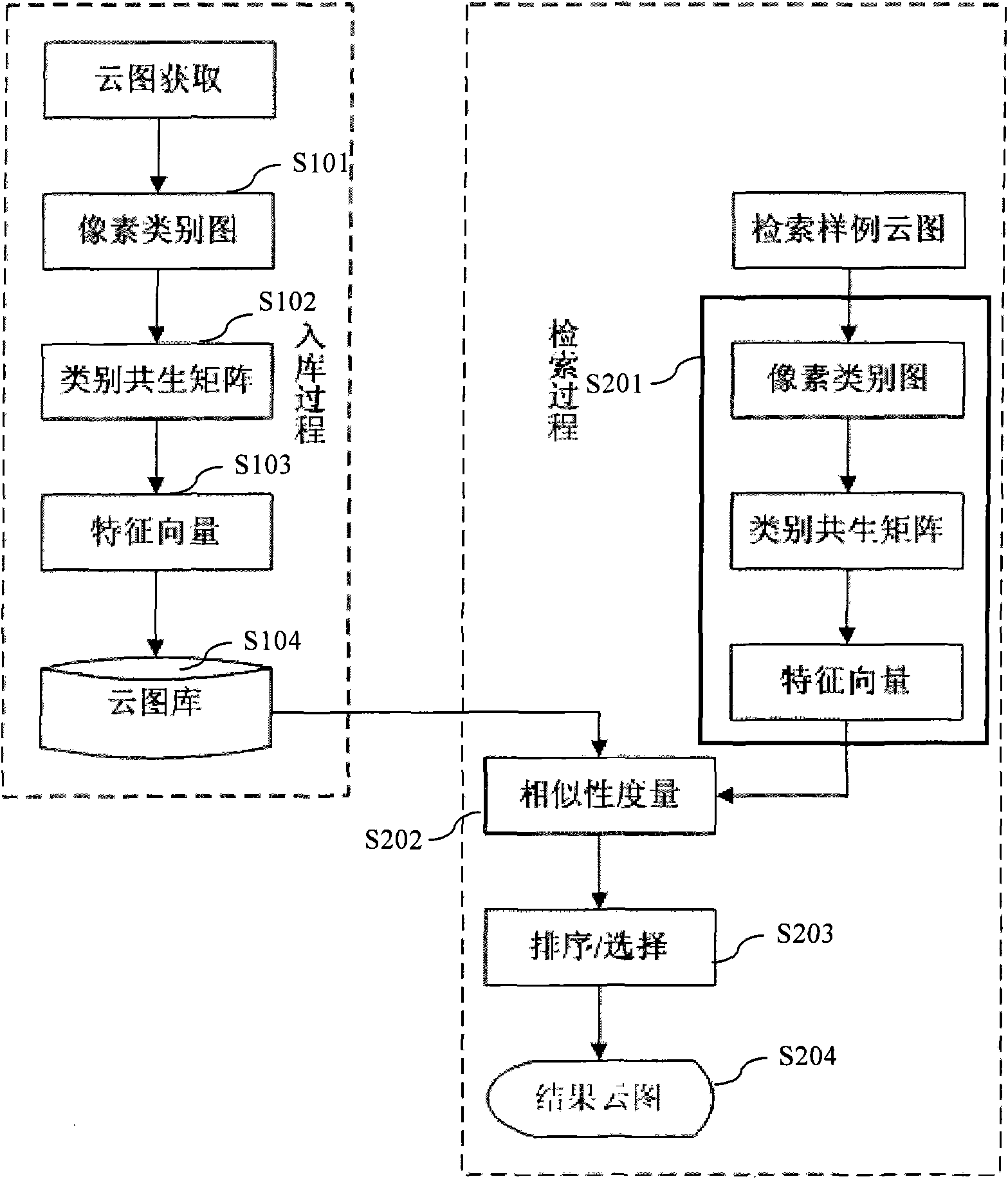
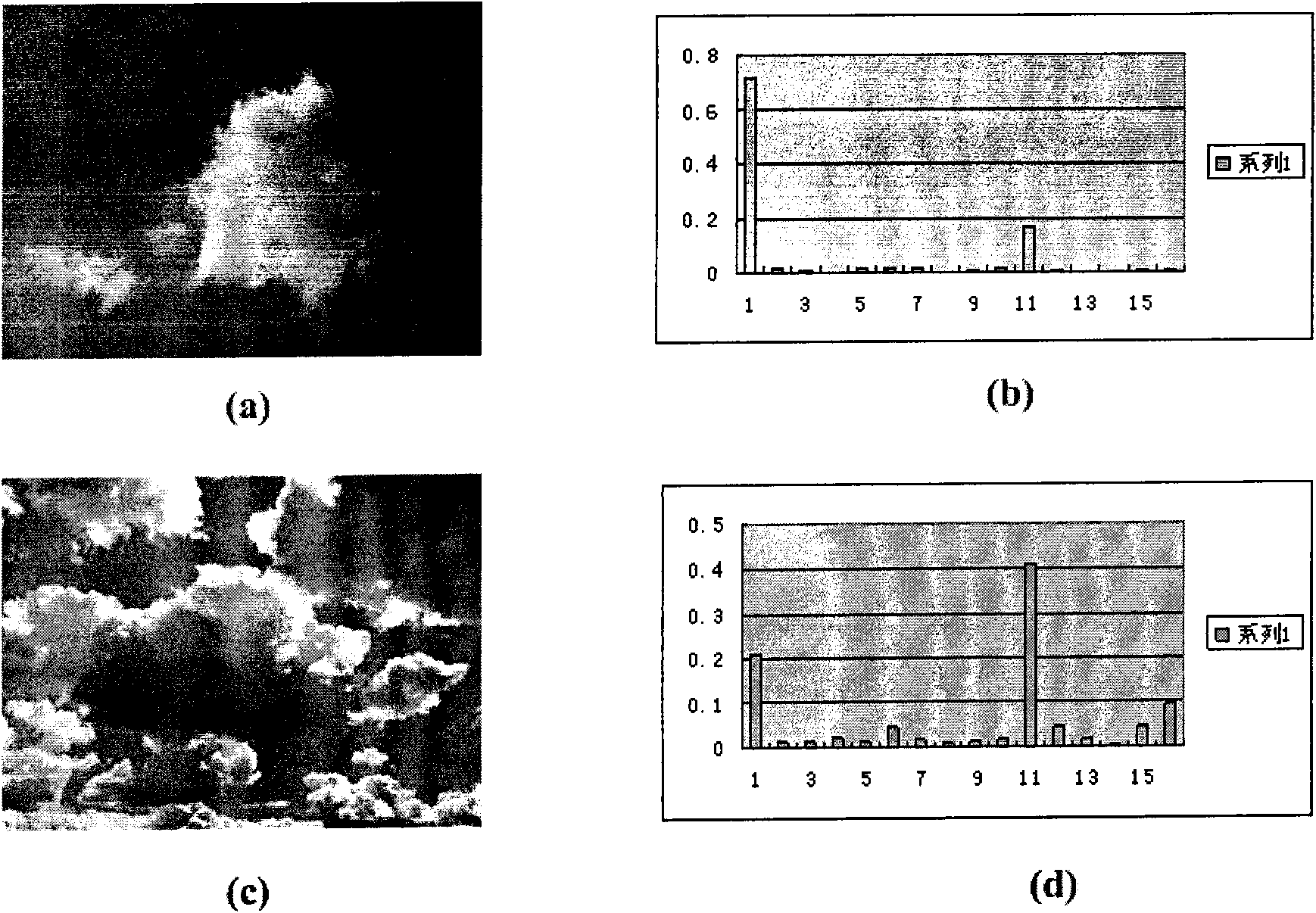
Method for extracting and retrieving textural features from ground digital nephograms
InactiveCN101876993AImprove analysis efficiencyImprove management efficiencySpecial data processing applicationsCo-occurrenceClass diagram
The invention discloses a method for extracting and retrieving textural features from ground digital nephograms, which comprises an extracting method and a retrieving method. The extracting method comprises the following steps: converting a RGB three-channel ground digital nephogram into single-channel pixel class diagrams; analyzing the pixel class diagrams and establishing co-occurrence matrixes to obtain histogram vectors of the co-occurrence matrixes; merging the histogram vectors of the pixel class co-occurrence matrixes to establish textural feature vectors of the ground digital nephogram; and storing the textural feature vectors into the nephogram database. The retrieving method comprises the following steps: extracting the textural features of the sample nephogram according to the feature extracting method; orderly calculating the similarity between the textural features of the sample nephogram and the textural features of every nephogram in the nephogram database; and displaying the most similar nephograms as retrieval results. The invention can automatically analyze and extract the effective textural features of the ground digital nephogram, and automatically retrieve the result nephograms similar to the sample nephogram from the nephogram database.
Owner:CHINESE ACAD OF METEOROLOGICAL SCI +1
Creating graphical models representing control flow of a program manipulating data resources
A class diagram can be created for an application. The application can use a modeling language. The application can be configured for creation of the class diagram. The class diagram can comprise classes and relationships. The application can also be configured for creating flow diagrams comprising actions, relationships, and definitions of model element types. The application can also be configured to create new model elements in the class diagram and flow diagrams. A program new model element type can be applied to relevant class operations in the class diagram and a resource new model element type to relevant data classes of the class diagram. A flow diagram can be created per program of the application. The flow diagrams can be applied as many new model element types as different types of actions exist in the flow diagrams. These actions can represent the operations on resources.
Owner:IBM CORP
Process for extracting Java software program class diagrams reversely
InactiveCN103593222AAccurate understandingProgram controlMemory systemsFunctional testingClass diagram
The invention belongs to the technical field of software testing, and particularly relates to a process for extracting Java software program class diagrams reversely. The technical scheme includes that the process for extracting Java software program class diagrams reversely includes the steps of A, analyzing program class diagrams statically; B, selecting backbone classes as reference points for abstracting and then searching paths among the backbone classes; C, abstracting subpaths having the character of class-relation-class-relation-class from the optional end of each path and matching with the 57 class diagram abstracting rules listed; D, merging the paths which are abstracted according to the specified priority to acquire the abstracted class diagrams if various relations exist after any two of the backbone classes are abstracted. By the process for extracting the Java software program class diagrams reversely, consistency verifying between code implementation of software and detailed design thereof is realized.
Owner:中国人民解放军第二炮兵装备研究院科研试验中心
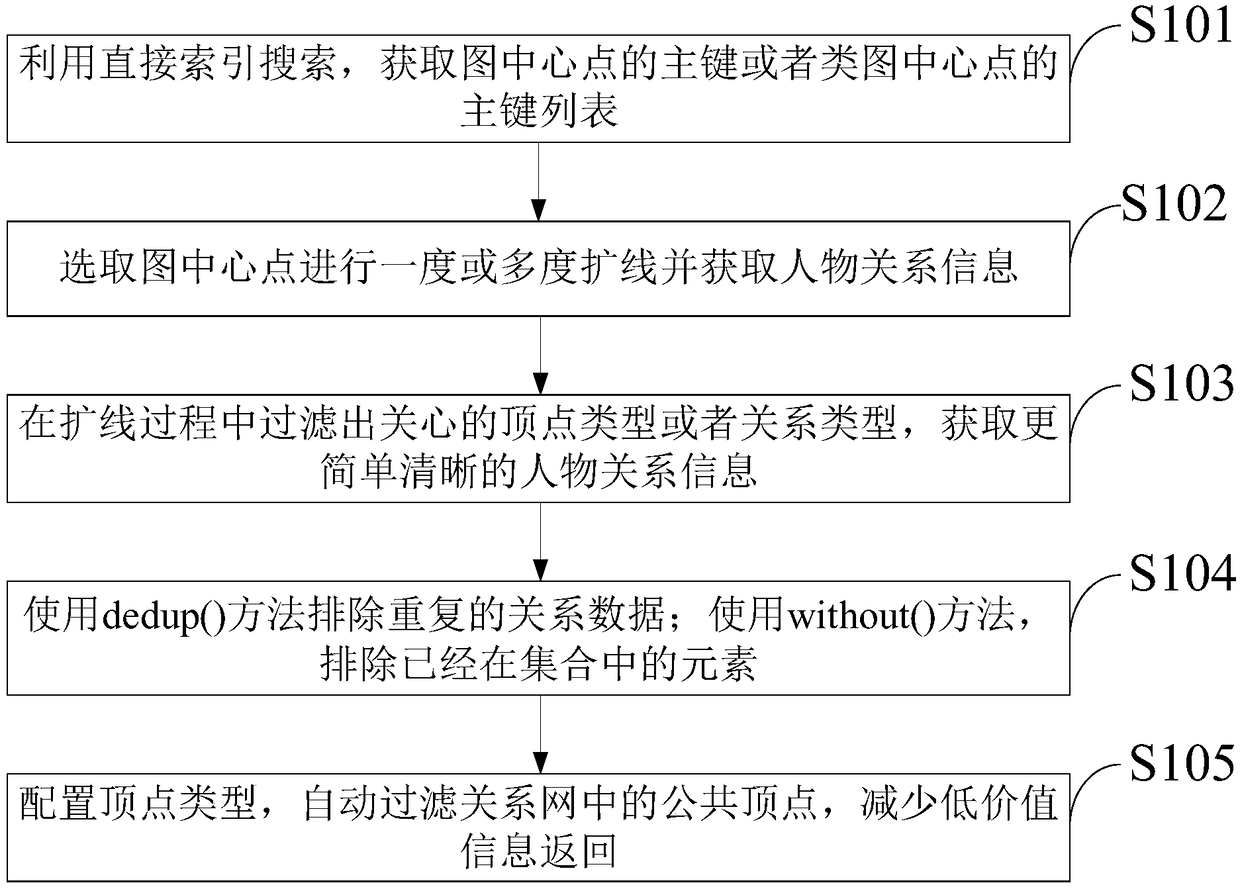
A method and a system for searching a relationship network based on a graph database
InactiveCN109271458AQuery Performance BenefitsDatabase modelsSpecial data processing applicationsClass diagramData mining
The invention belongs to the technical field of data processing and discloses a method and a system for searching a relationship network based on a graph database. The method includes: utilizing a direct index search to obtain a primary key list of a graph center point or a class graph center point, selecting the center point of the graph to expand the line one degree or more and acquiring the relationship information of the characters; filtering out the vertex type or relationship type of interest in the process of line expansion to obtain simpler and clearer character relationship information; using the dedup () method to exclude duplicate relational data; using the without () method to exclude elements that are already in the collection; configuring vertex types to automatically filterpublic vertices in the network. As the data of the invention is stored in an edge division mode, the query performance of the complex graph is more advantageous than that of the traditional relationaldatabase; Request gremlin-Server in gremlin statement is used to obtain query data, to achieve the storage and analysis of relational data.
Owner:LINEWELL SOFTWARE
Polarized SAR terrain classification method based on Gauss filtering and PSO
ActiveCN105069480AImprove classification accuracyChange rangeImage enhancementImage analysisClassification methodsTerrain classification
The invention discloses a polarized SAR terrain classification method based on Gauss filtering and SPO, and mainly solves the problem that a present classification method based on single pixel point is low in classification precision. The method comprises the steps that related information of a polarized SAR image to be classified and a result of classifying the polarized SAR image in the present single pixel point method are input to construct a class diagram; the class diagram is divided into sub class diagrams, objective functions are constructed for the sub class diagrams respectively, the objective functions are optimized in the PSO algorithm to obtain an optimal variance; the optimal variance is used to establish a Gauss filter; Gauss filtering is carried out on the sub class diagrams to obtain classification result of the each sub image; and the classification results of all the sub images are merged to obtain a classification result of the whole polarized SAR image to be classified. Thus, the precision of polarized SAR terrain classification is improved, and the method can be applied to terrain classification and object identification.
Owner:XIDIAN UNIV
Generating functional artifacts from low level design diagrams
InactiveUS9015665B2Shorten development timeLess timeRequirement analysisSoftware reuseLevel designClass diagram
At least one design diagram is obtained from at least one previous software project. At least one service abstraction is extracted from the at least one design diagram. The at least one service abstraction is reused in a new software project. In another aspect, requirements are obtained for a current software project; at least one class diagram is obtained from at least one previous software project; a dependency graph is generated from the at least one design diagram, using link analysis; relationships between classes in the dependency graph are analyzed to obtain functional artifacts for the requirements; and the functional artifacts are reused in the new software project.
Owner:INT BUSINESS MASCH CORP
Creating graphical models representing control flow of a program manipulating data resources
A computing device can store a class diagram of an application in a storage medium. A new model element type is applied to class operations in the class diagram and to a resource new model element type to data classes by defining properties, which include at least a resource name property, for each new model element. Flow diagrams of the application are applied to as many new model element types as different types of actions exist in the flow diagrams. The actions represent the operations on resources.
Owner:IBM CORP
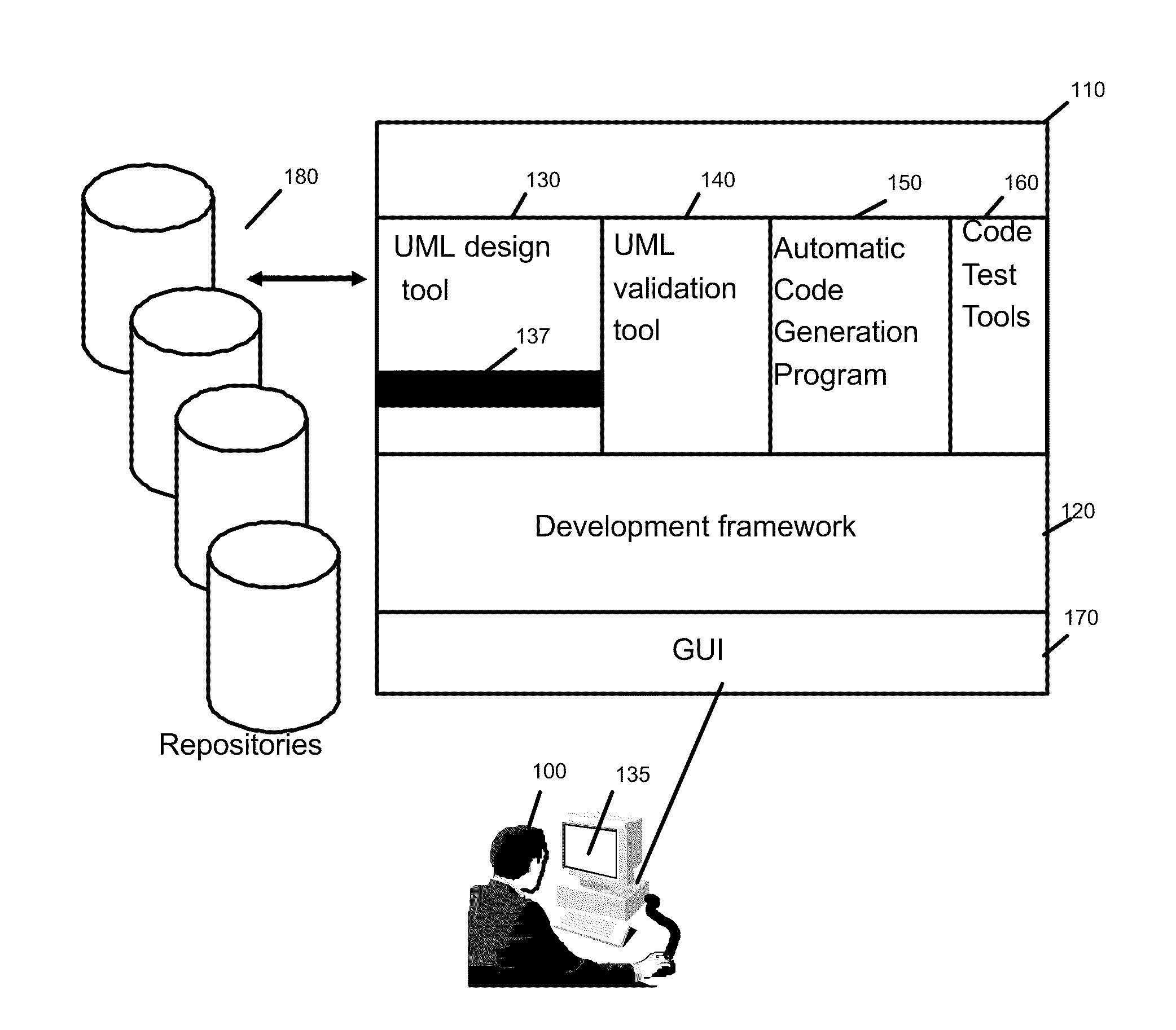
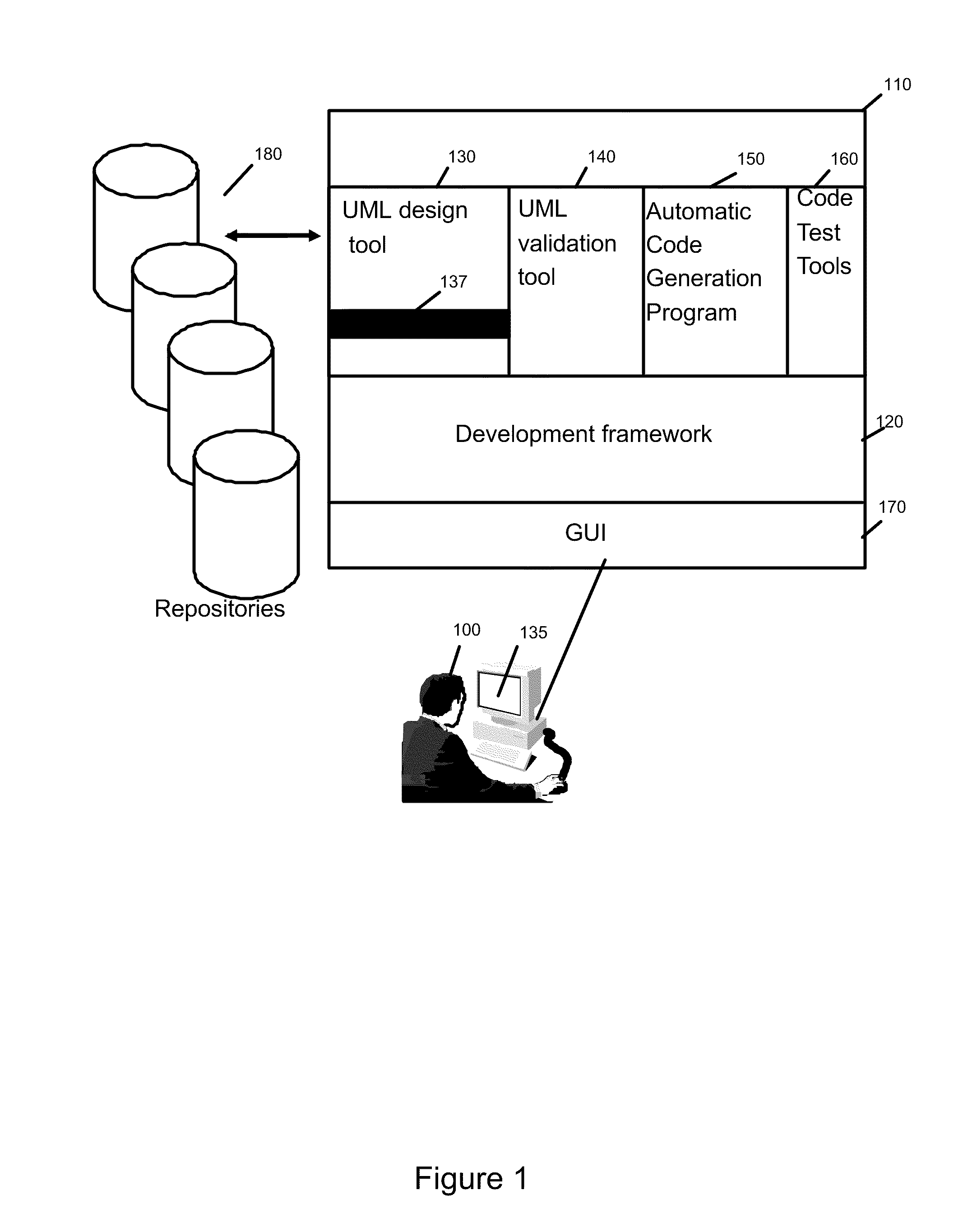
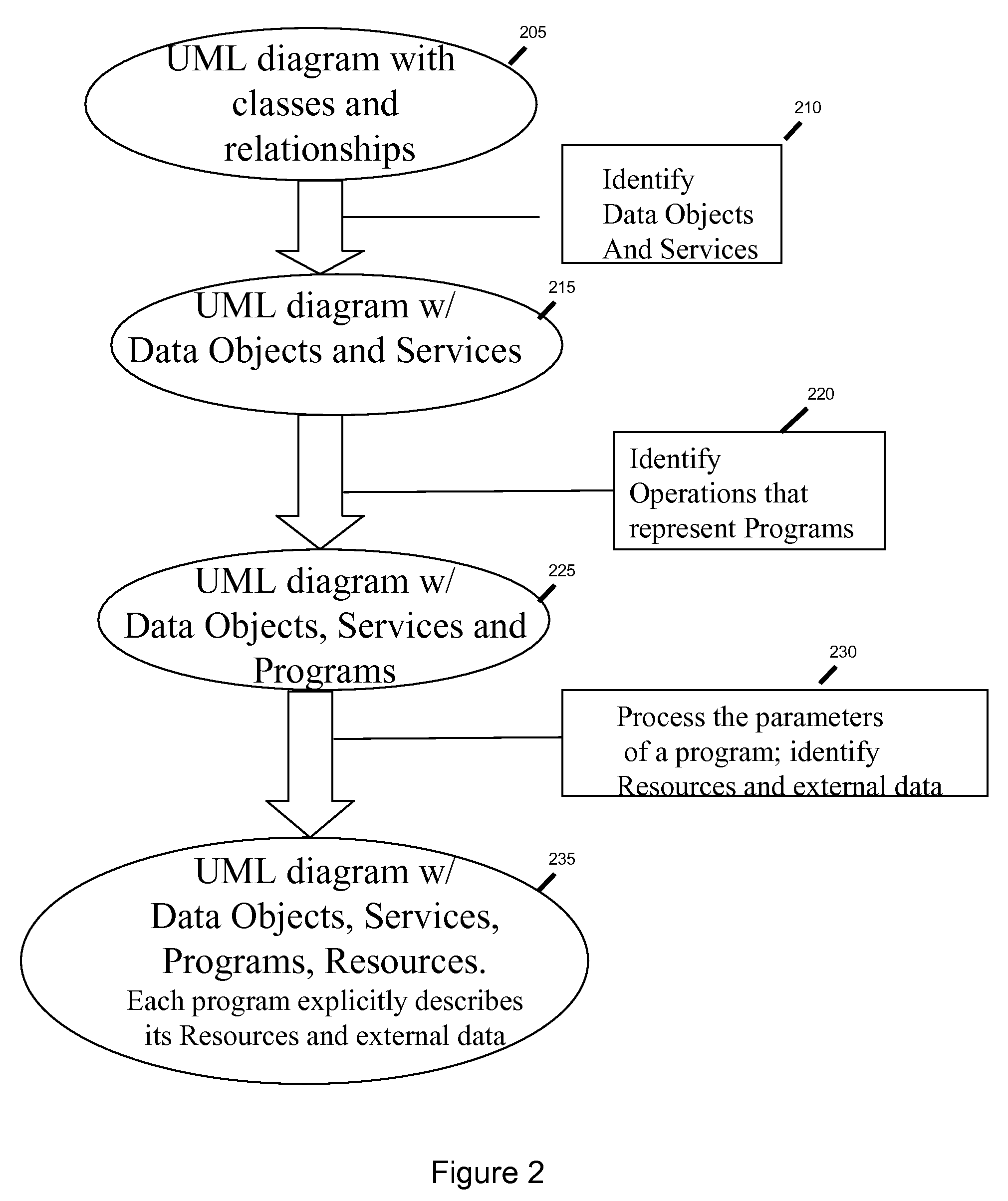
Method and system to modelize resources and external data of a program for procedural language coding
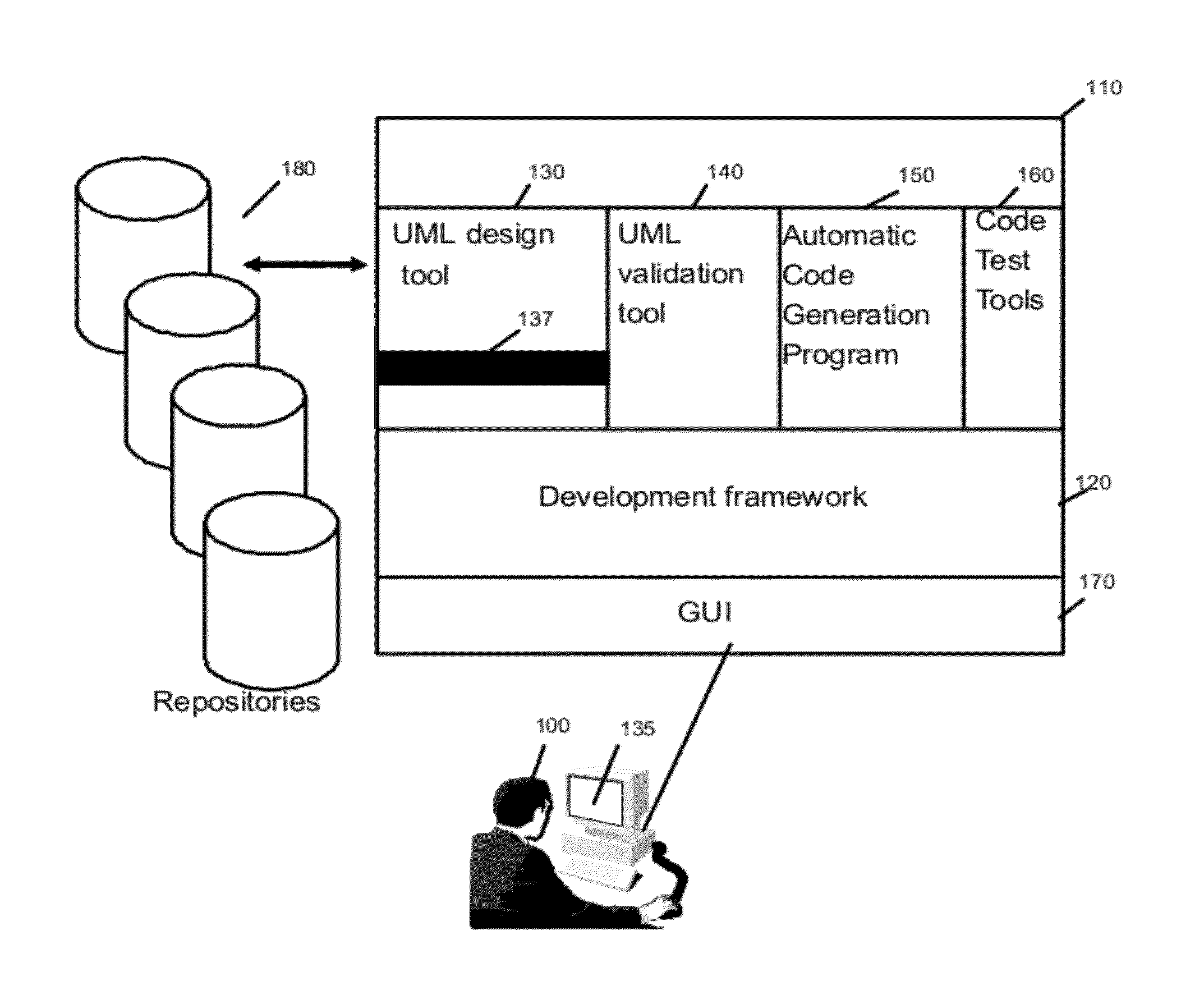
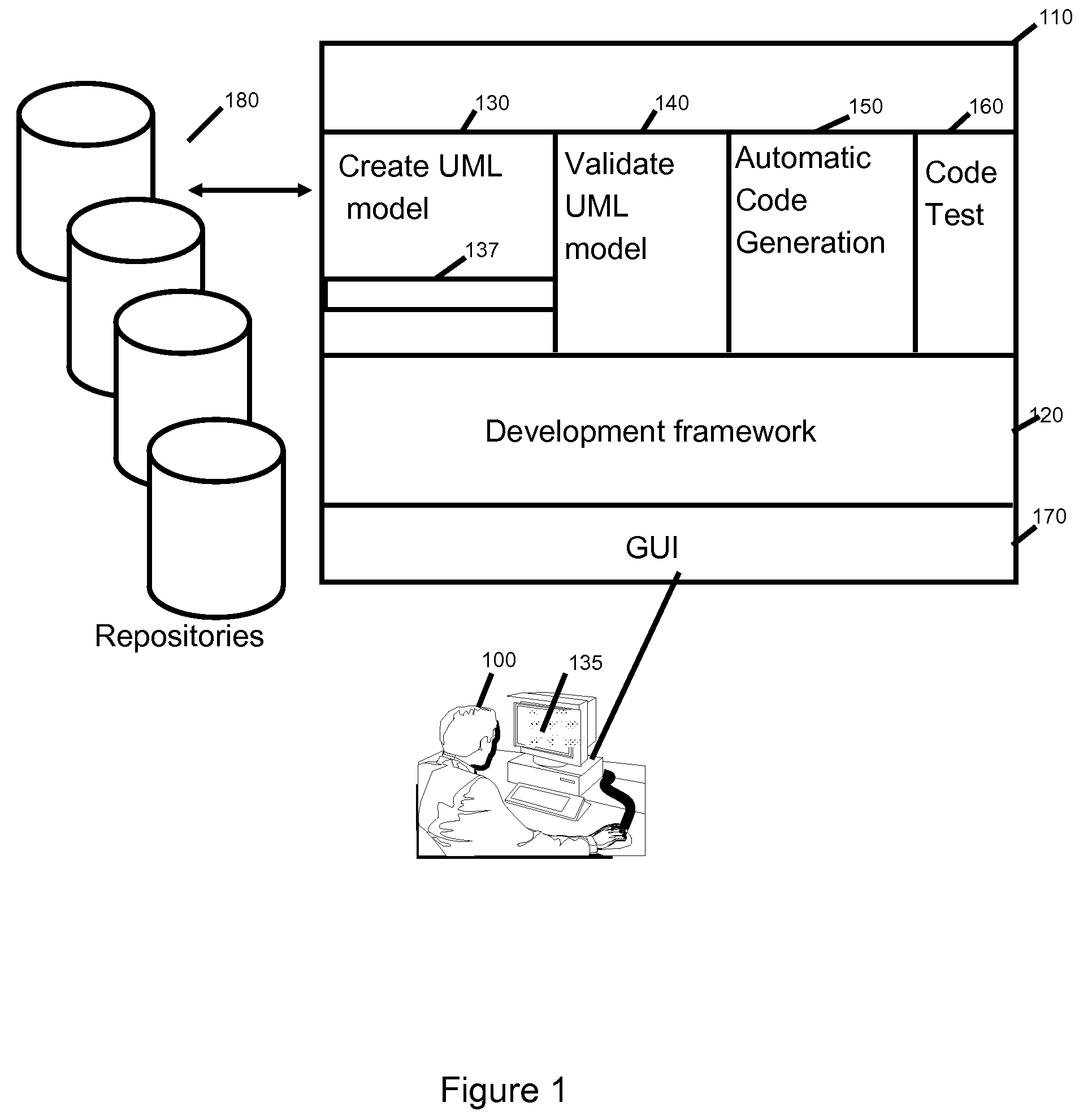
ActiveUS20100088667A1Requirement analysisSoftware simulation/interpretation/emulationProgramming languageExternal data
A method and system to represent in UML the resources and external data manipulated by a program to be coded in a procedural language is disclosed. The usual UML class diagram is enhanced with two new stereotypes “Program” and “Data Object”. The program stereotypes applied to an operation and its parameters describe the data manipulated, through the logical definition provided by the Data Object. This model will be enhanced in order to introduce classes on which the Resource stereotype is applied. These classes will be connected to the appropriate logical data definition (the Data Object) and used as parameter types of the operation instead of the Data Object. A second set of stereotypes will be applied to the Resource classes to indicate the physical type of the resource (a file, table etc. . . . ) and its characteristics. Parameters that point to a DataObject or a primitive type will be considered as external data.
Owner:IBM CORP
Intelligent software programming method
InactiveCN106020788AComplete contentImprove development efficiencyProgramming languages/paradigmsIntelligent editorsElement modelUml metamodel
The invention discloses an intelligent software programming method, which includes the following steps: the first step: drawing a UML model according to the software design requirements; the second step: establishing a UML meta-model meeting the software design requirements; the third step: code conversion rules The fourth step: code generation, according to the code conversion rules established in the third step, use the computer to convert the input UML model into C++ code, wherein the class diagram generates the class in C++, and the specific implementation inside the sequence diagram generation method The present invention maps each element in the UML model to the corresponding metamodel, and then generates C++ codes step by step according to the conversion rules of the metamodel, compared with the method that can only generate the C++ code frame proposed in most documents, the proposed method of the present invention The method can generate codes with more complete content, reduces the work of programmers to manually add codes, thereby improving the efficiency of software development and the quality of software products.
Owner:QILU UNIV OF TECH
Modeling method of steel mill production scheduling system based on Agent and Agent UML (Unified Modeling Language)
InactiveCN102081388AMeet needsHigh dynamicTotal factory controlProgramme total factory controlSystems designModelling methods
The invention discloses a modeling method of a steel mill production scheduling system based on Agent and Agent UML (Unified Modeling Language). The modeling method comprises the following steps: 1, completing system analysis for modeling the steel mill production scheduling system by Agent and Agent UML, and completing static modeling of the system in the system analysis stage, wherein static modeling mainly comprises target analysis, use case application, role definition and the like; and 2, completing system design for modeling the steel mill production scheduling system by Agent and Agent UML, and completing dynamic modeling of the system in the system design stage, wherein dynamic modeling mainly comprises design of a system Agent class diagram, conversation construction, Agent construction, construction of a system deployment diagram and the like. Compared with an object oriented modeling method, the modeling method disclosed by the invention can better meet dynamics, intelligence, autonomy, flexibility and distributivity of the system, thus meeting the requirements of the steel mill production scheduling system.
Owner:KUNMING UNIV OF SCI & TECH
Software visualization method for object-oriented programming language source code
InactiveCN102385505BEasy to understandAccurate and intuitive internal structureSpecific program execution arrangementsDirected graphData information
The invention relates to a software visualization method for an object-oriented programming language source code, belonging to the technical field of software visualization. The method comprises the following steps of: (1) extracting key information from the source code; (2) acquiring data information of an original graph; (3) acquiring data information of a directed graph; (4) designing a graph layout; and (5) performing visualization mapping. With the adoption of the novel software visualization method for the object-oriented programming language source code provided by the invention, the defect of a class graph for the soft visualization is made up, and the internal structure of software and the status and the effect of types in the software can be accurately and intuitively reflected, so that a user can rapidly understand a software design level.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com