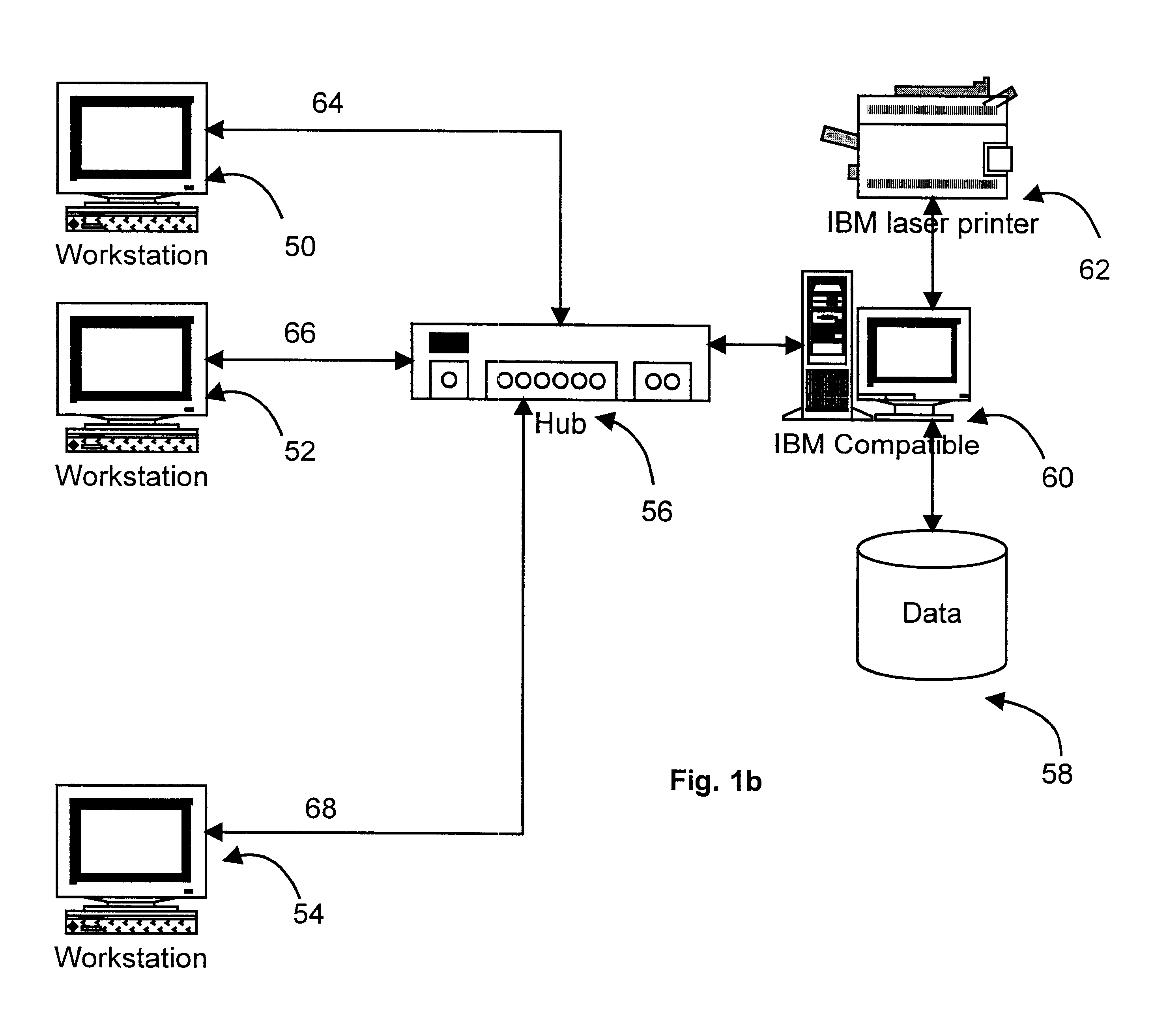
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1043 results about "DEVS" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
DEVS abbreviating Discrete Event System Specification is a modular and hierarchical formalism for modeling and analyzing general systems that can be discrete event systems which might be described by state transition tables, and continuous state systems which might be described by differential equations, and hybrid continuous state and discrete event systems. DEVS is a timed event system.
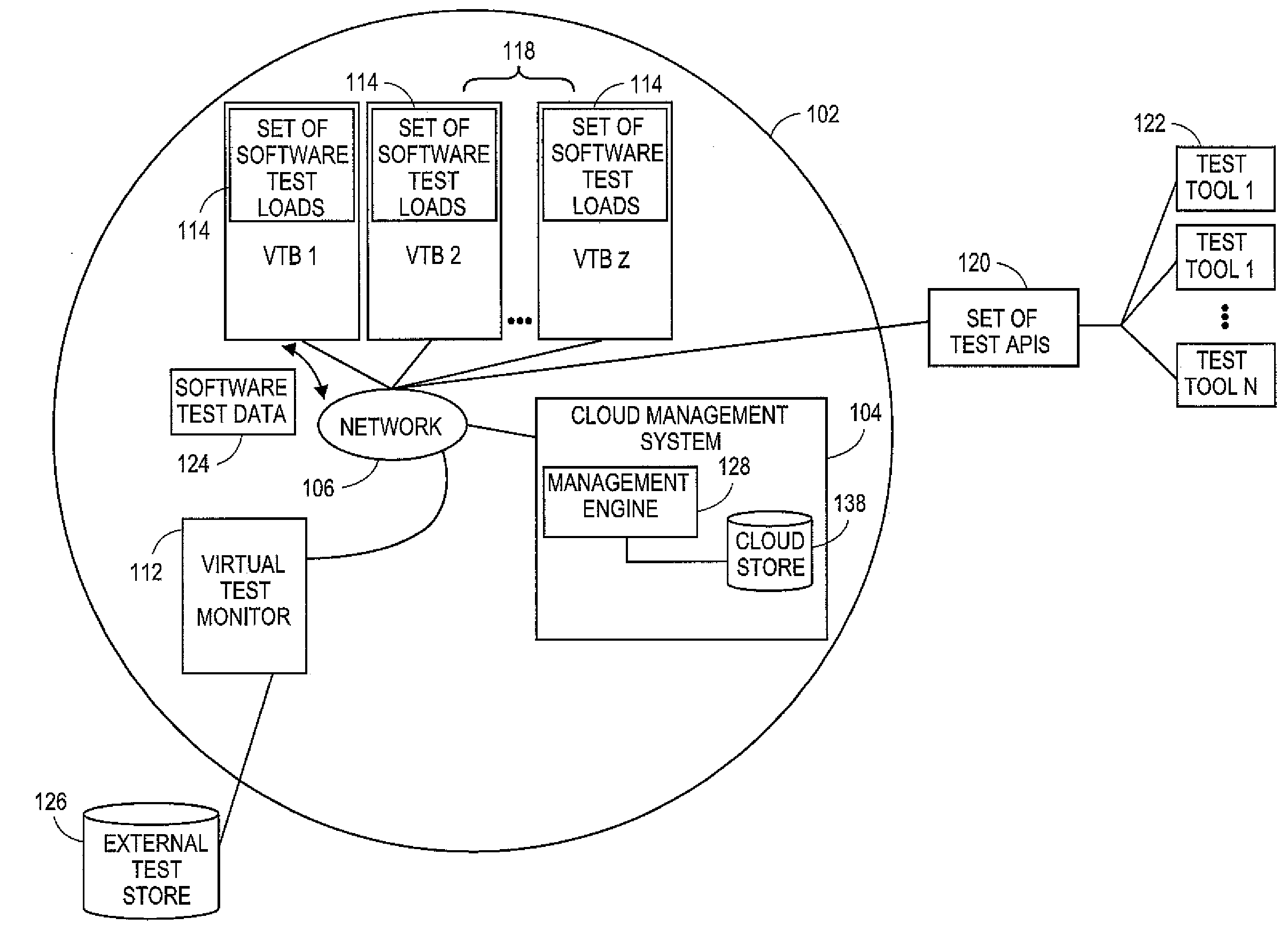
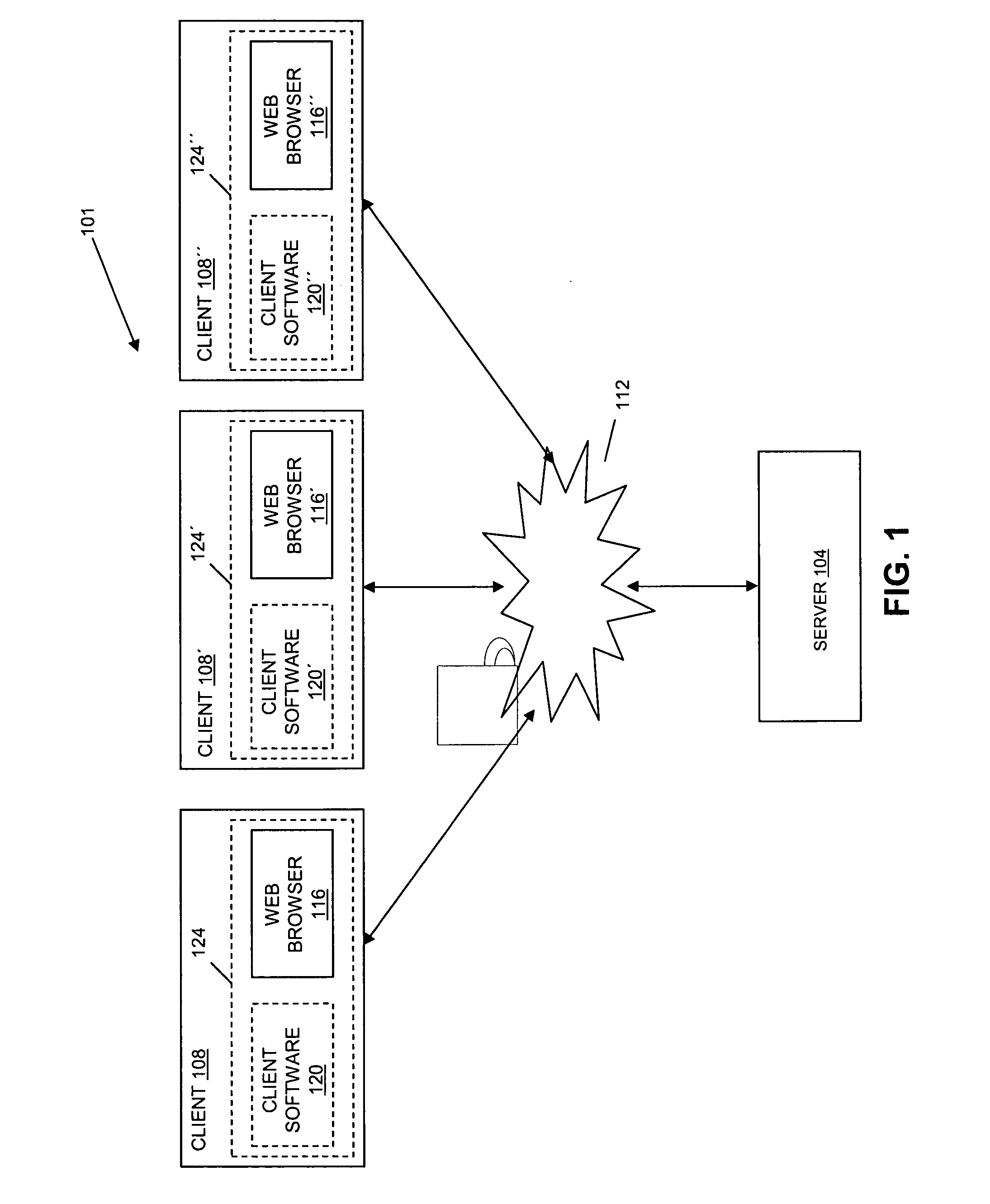
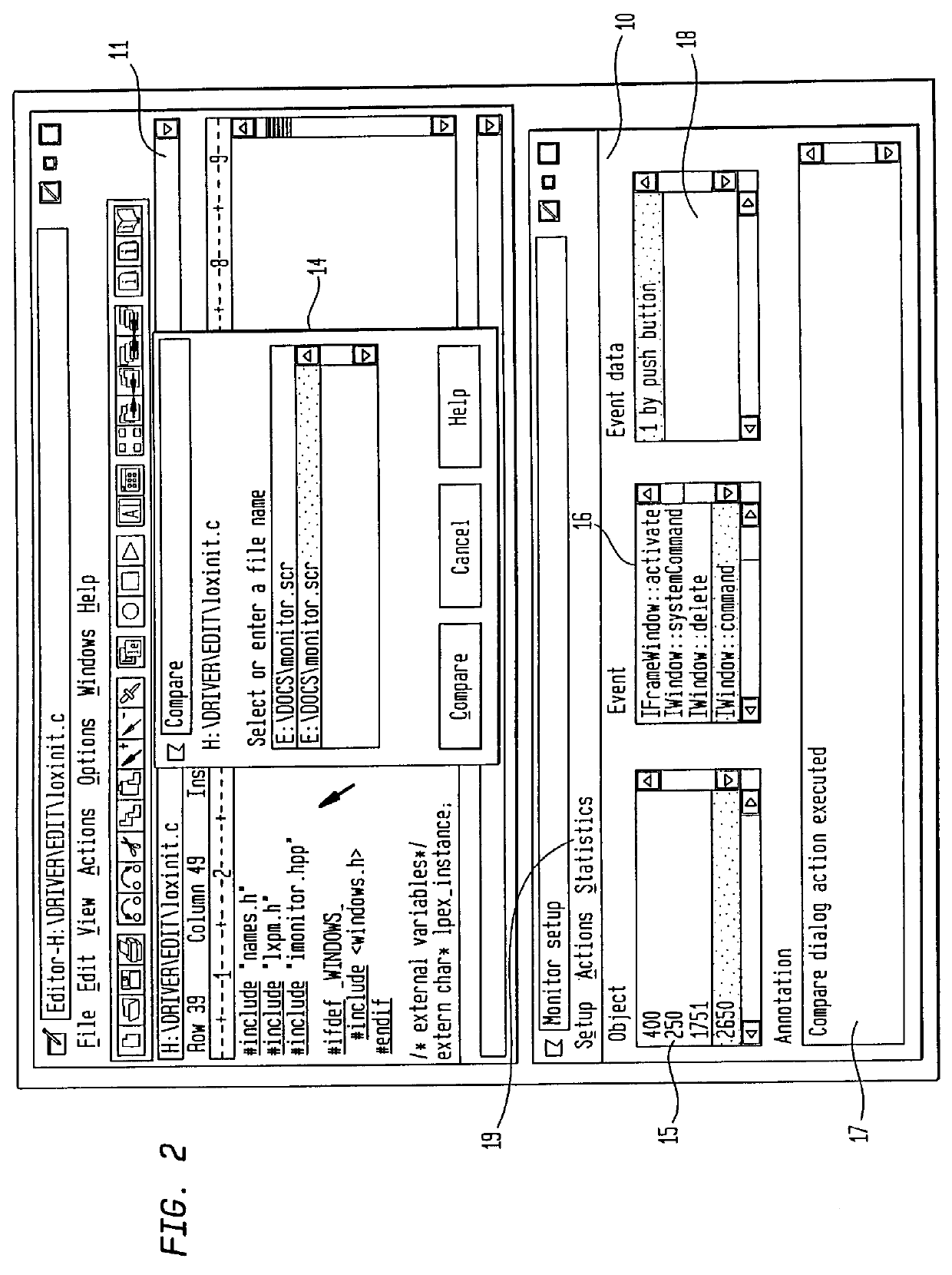
Systems and methods for software test management in cloud-based network
Embodiments relate to systems and methods for testing and evaluating software in the network cloud. A developer or other operator may wish to debug, modify, or update a set of test software based on testing of that software. The developer can instantiate a set of virtual servers or other test beds in the cloud, and install the subject software to the virtual test beds. A test management module can monitor the execution of the set of test software on the set of virtual test beds, to detect execution faults, measure processing performance, stress-test the software with predetermined data inputs, and manage other aspects of software life cycle development. The test management module can provide or access a set of application programming interfaces to a set of software tools external to the cloud, so that the set of test software can be tested and optimized using external programming development tools.
Owner:RED HAT
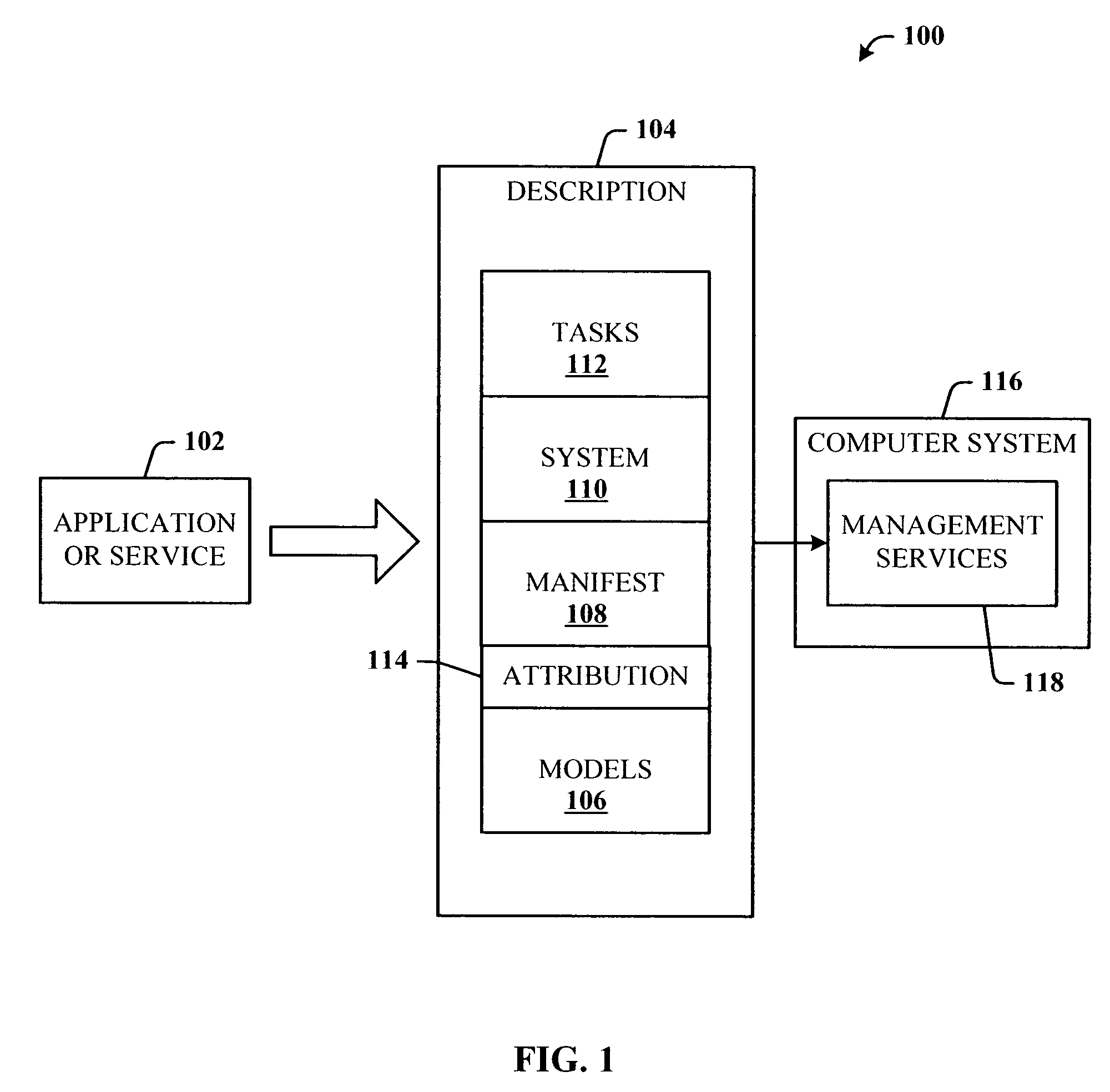
Model-based management of computer systems and distributed applications
ActiveUS7103874B2Configure the management servicesEnsure availabilityData processing applicationsError detection/correctionComputerized systemApplication software
Owner:SERVICENOW INC
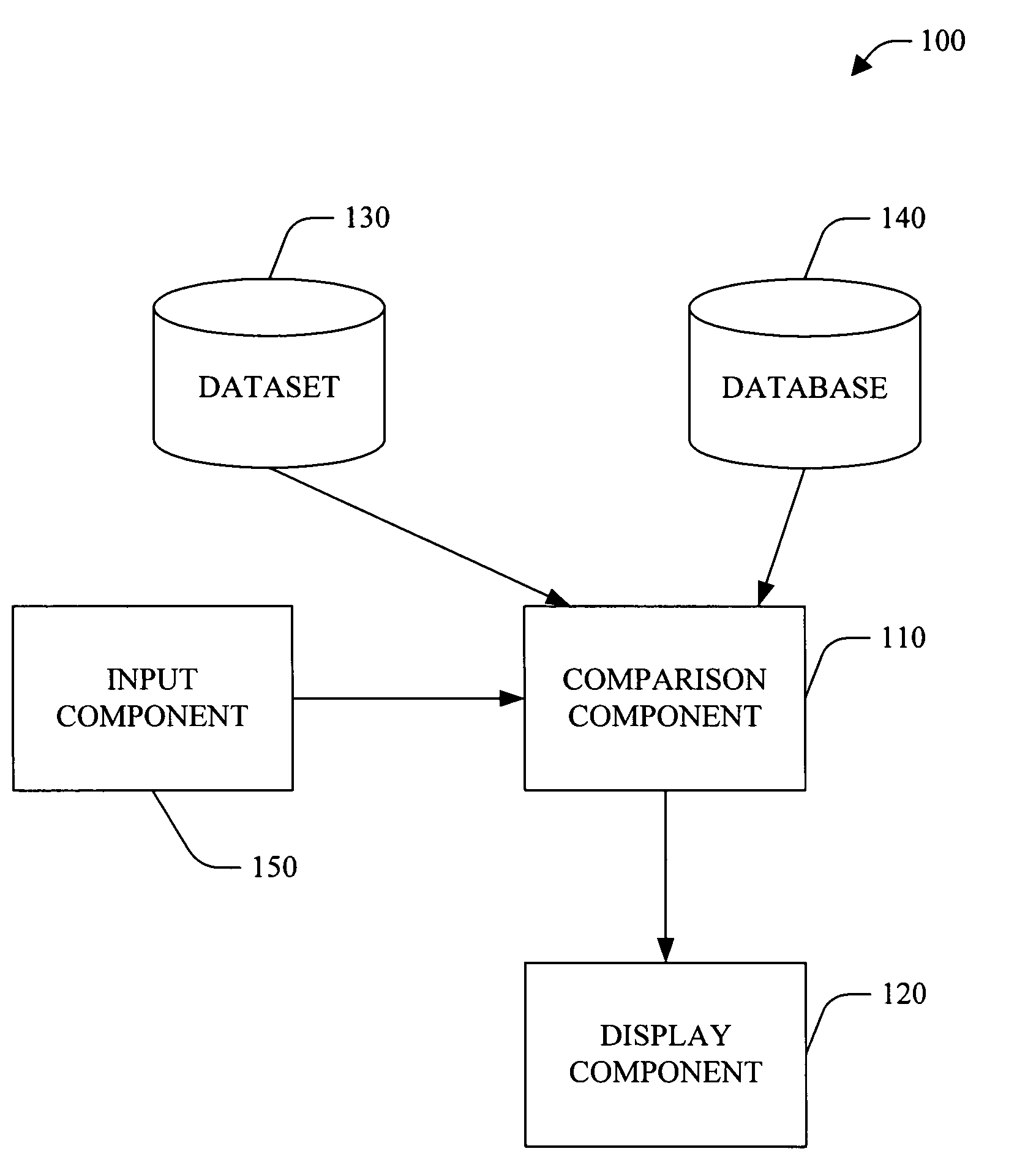
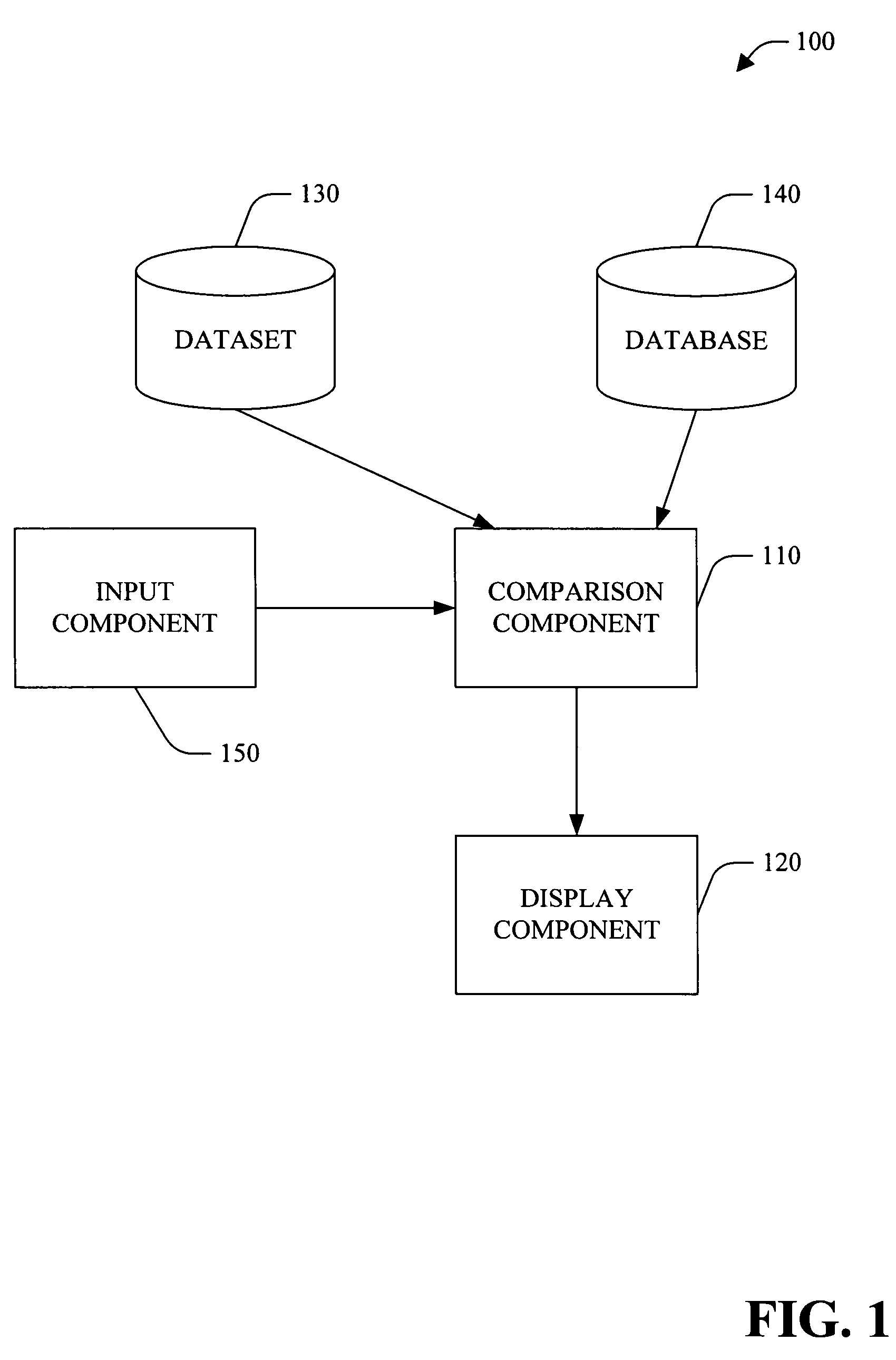
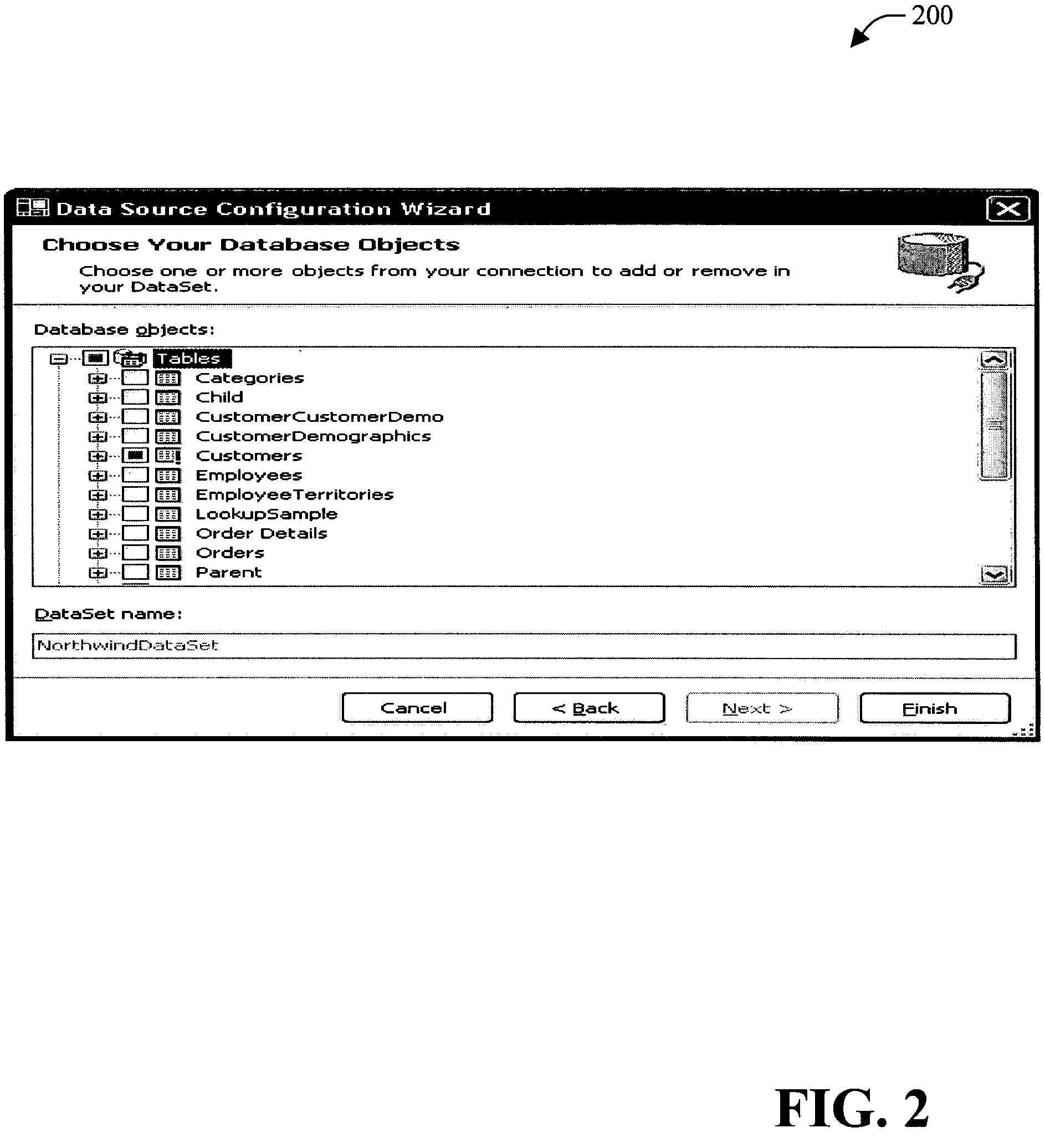
Reentrant database object wizard
InactiveUS7620644B2Data processing applicationsDigital data processing detailsData setApplication software
A system and method for a reentrant database object wizard is provided. The system provides the ability to compare a currently generated dataset to the objects of the underlying database. Columns and tables that are not common between both the dataset and the database are visually displayed for the user to make a decision on inclusion or exclusion. The system includes a comparison that provides comparison information based upon a comparison of a dataset to an associated database and a display component that displays the comparison information. The system further includes an input component which provides information associated with the user's decision on inclusion and / or exclusion of column(s) and / or table(s) to the system. The system is reentrant thus providing long-term value to the developer over the application development cycle.
Owner:MICROSOFT TECH LICENSING LLC
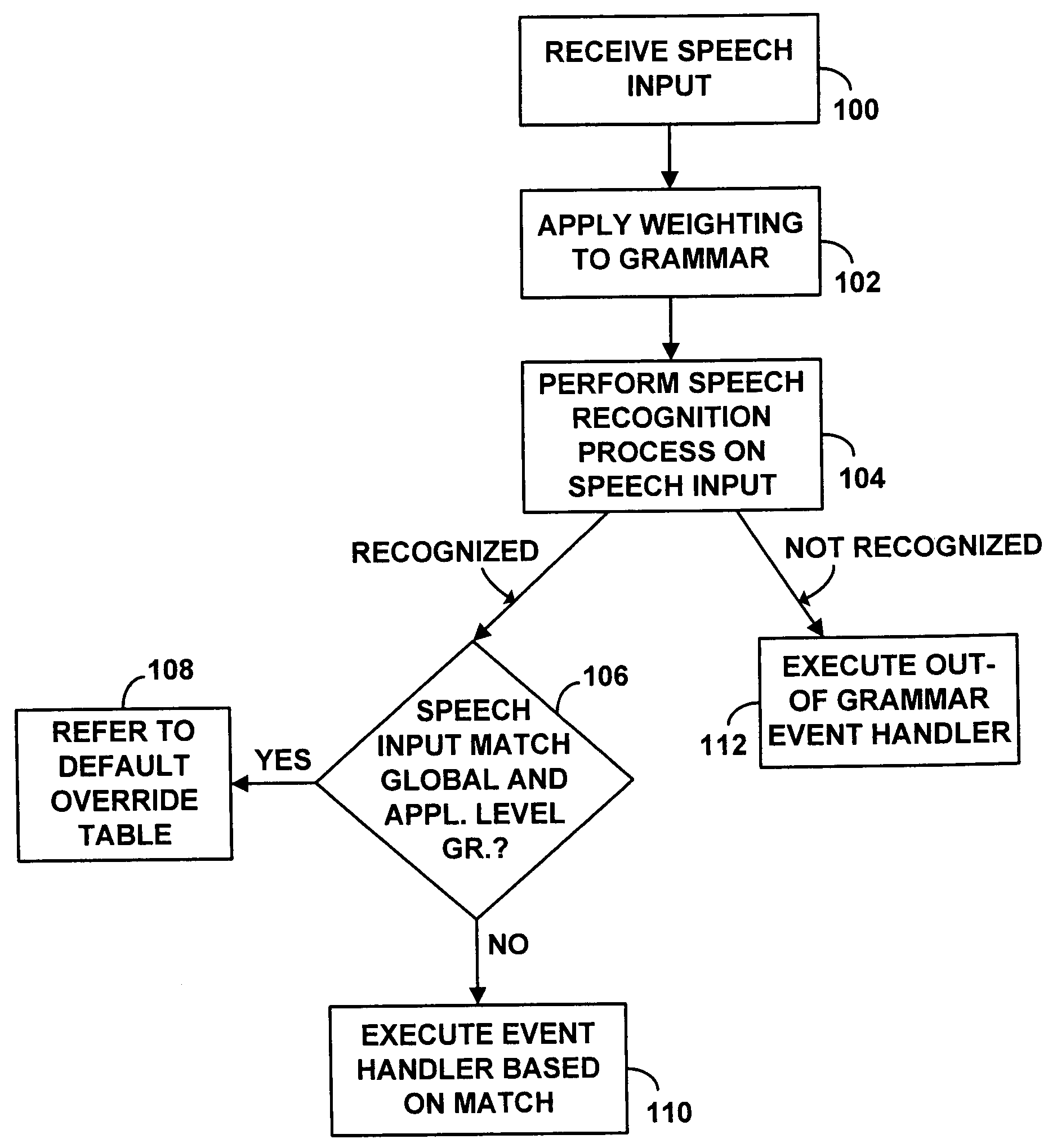
Voice browser with weighting of browser-level grammar to enhance usability
A computer system in the form of a voice command platform includes a voice browser and voice-based applications. The voice browser has global-level grammar elements and the voice applications have application-level grammar and grammar elements. A programming feature is provided by which developers of the voice applications can programmably weigh or weight global-level grammar elements relative to the application-level grammar or grammar elements. As a consequence of the weighting, a speech recognition engine for the voice browser is more likely to accurately recognize voice input from a user. The weighting can be applied on the application as a whole, or at any given state in the application. Also, the weighting can be made to the global level grammar elements as a group, or on an individual basis.
Owner:SPRINT SPECTRUM LLC
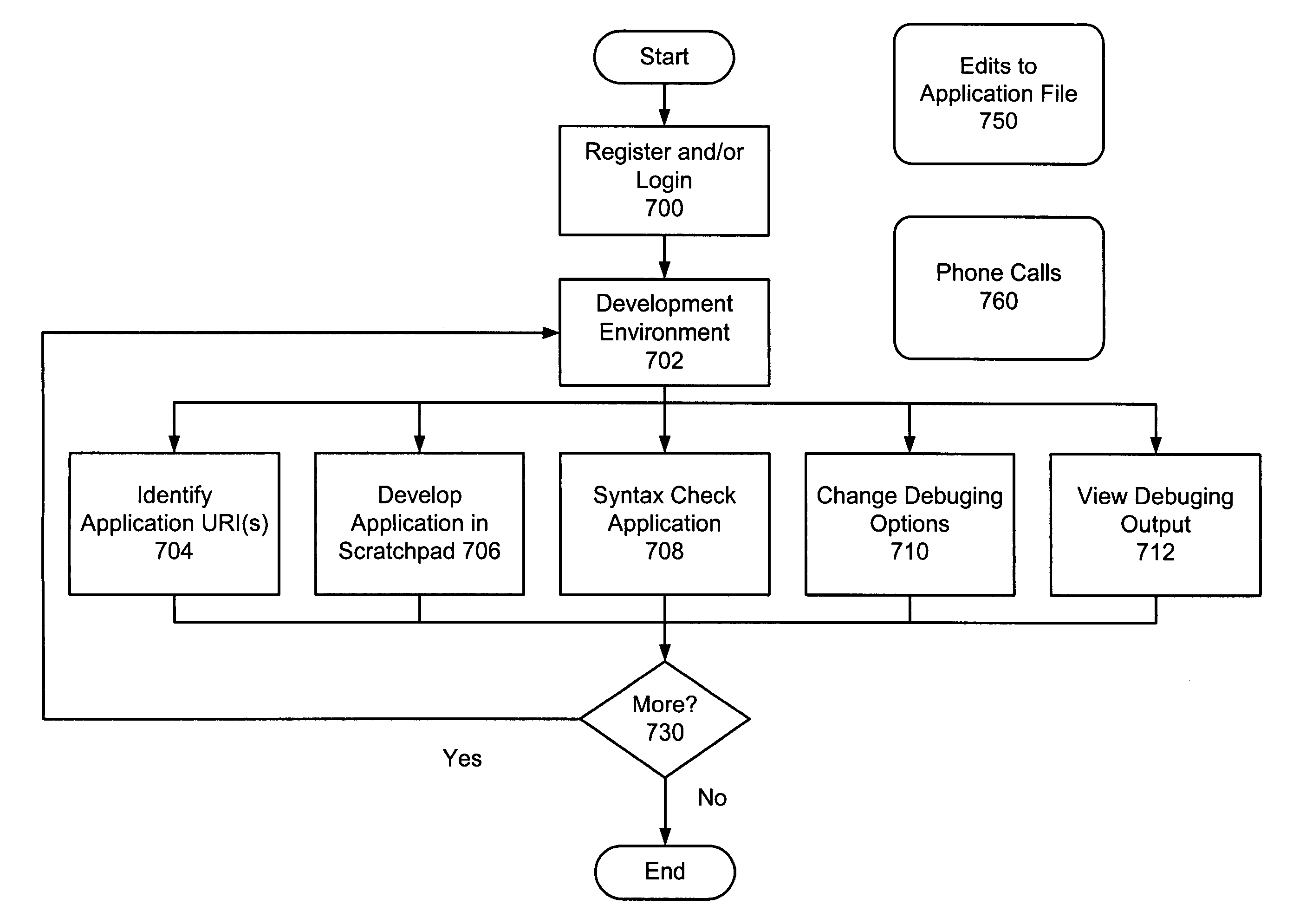
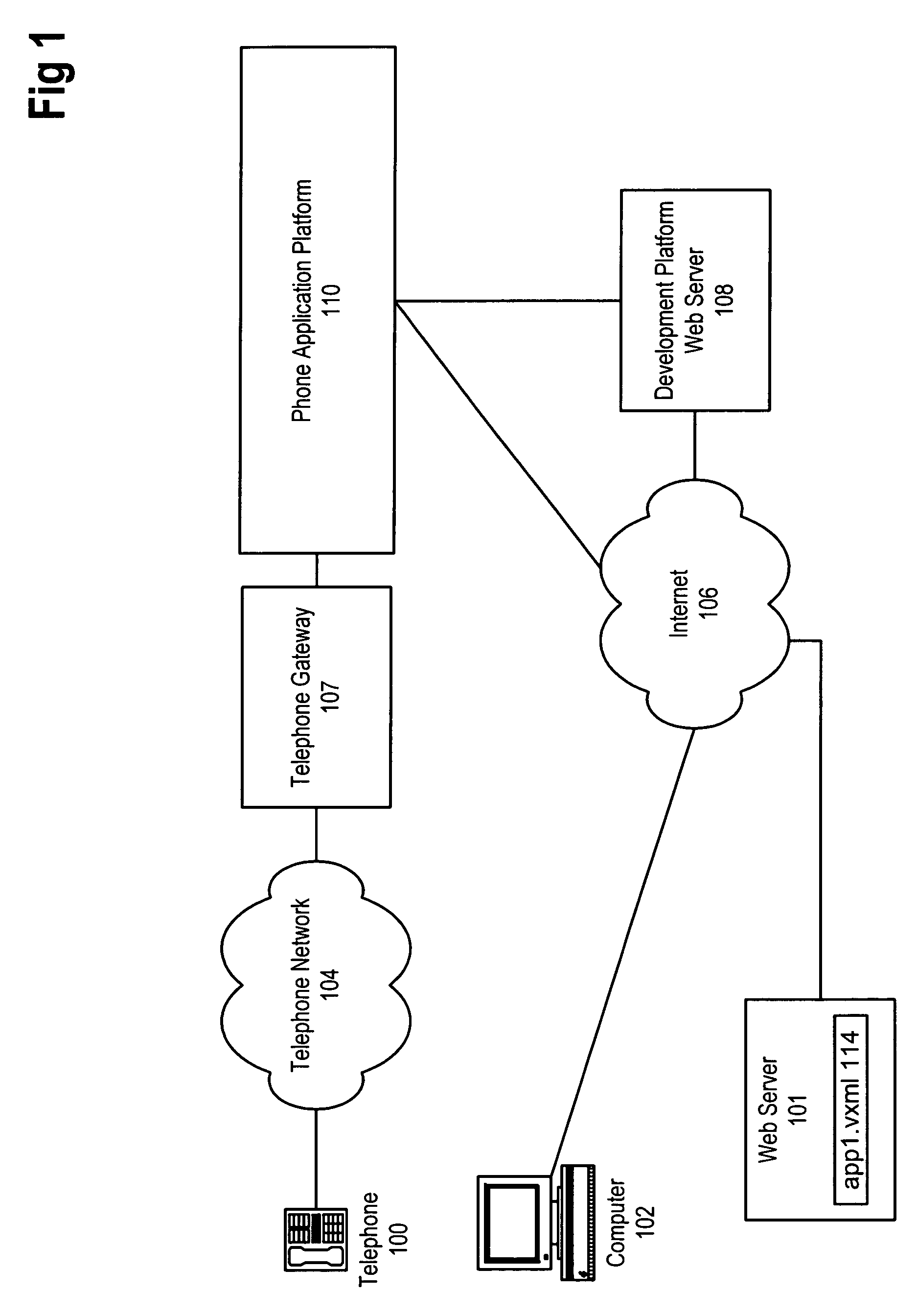
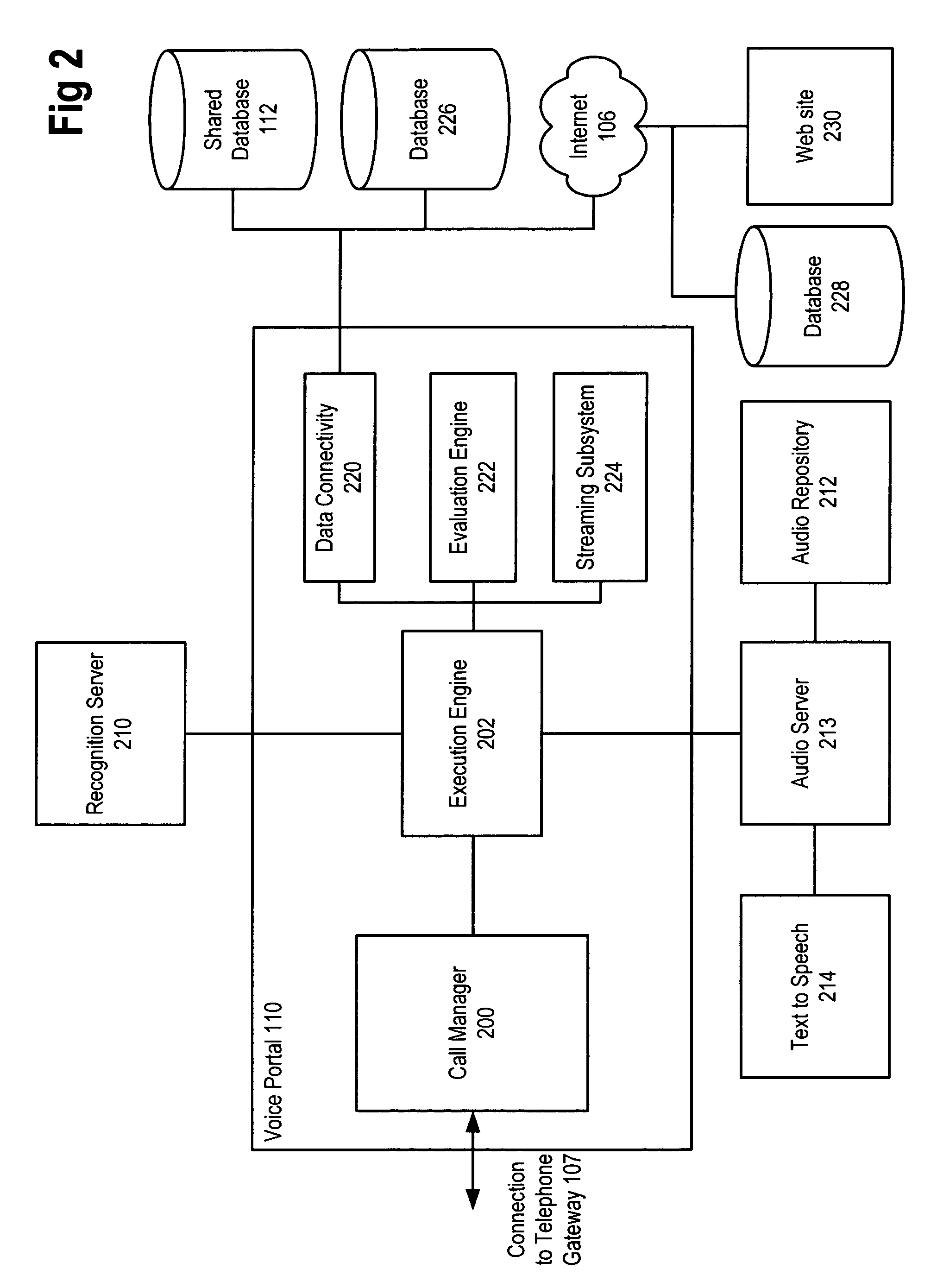
Method and apparatus for zero-footprint phone application development
InactiveUS7140004B1Avoid any surpriseTelephone data network interconnectionsError detection/correctionWeb browserApplication procedure
A zero-footprint remotely hosted phone application development environment is described. The environment allows a developer to use a standard computer without any specialized software (in some embodiments all that is necessary is a web browser and network access) together with a telephone to develop sophisticated phone applications that use speech recognition and / or touch tone inputs to perform tasks, access web-based information, and / or perform commercial transactions. Some embodiments support concurrent call flow tracking that allows a developer to observe, using a web browser, the execution of her / his application. A variety of reusable libraries are provided to enable the developer to leverage well-developed libraries for common playback, input, and computational tasks. Embodiments support rapid application deployment from the development environment to hosted application deployment to the intended audience.
Owner:MICROSOFT TECH LICENSING LLC
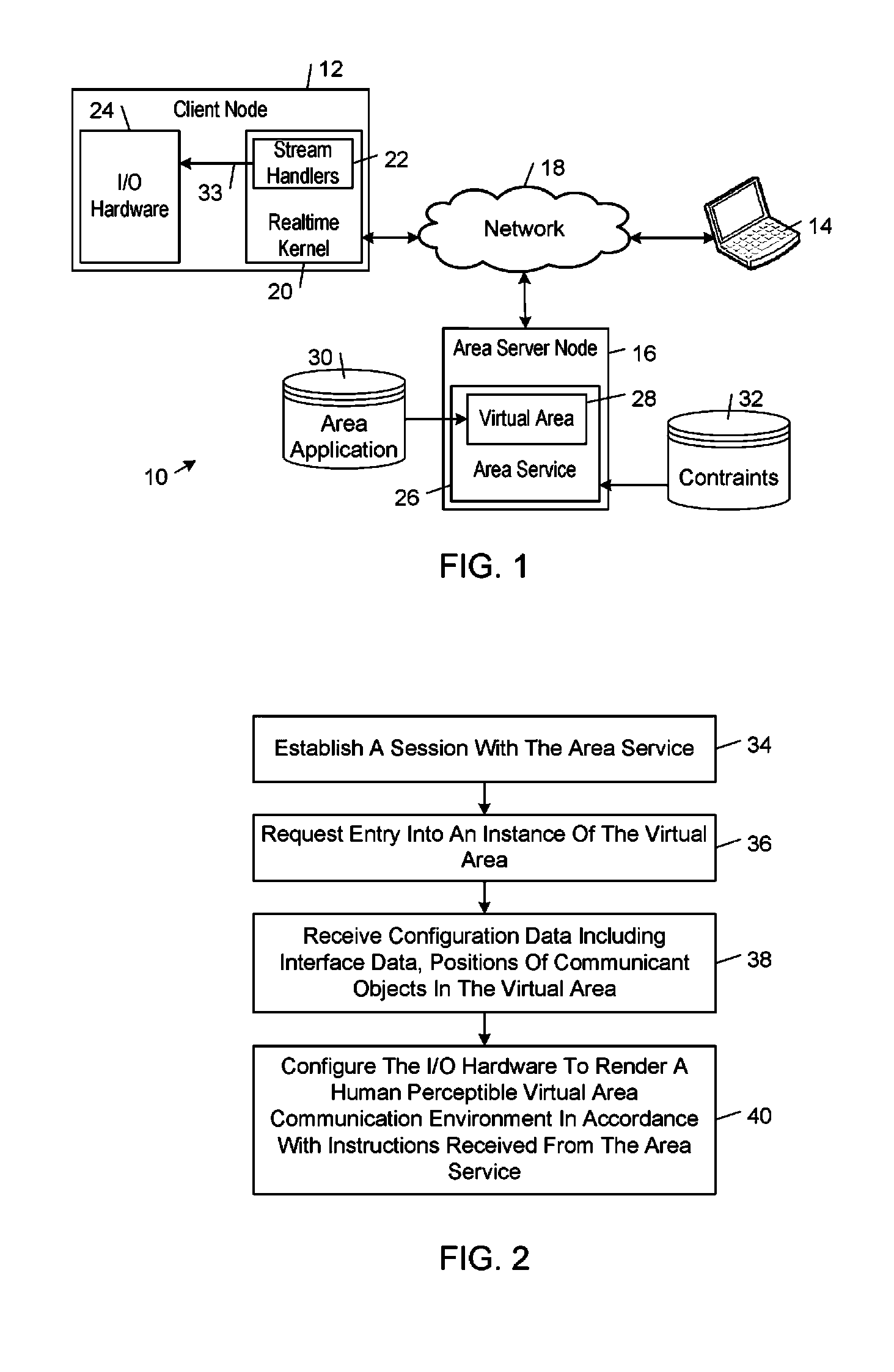
Realtime kernel
ActiveUS20100146085A1Multiprogramming arrangementsMultiple digital computer combinationsData streamNetwork connection
A realtime kernel supports realtime communications between communicants operating on respective network nodes. The realtime kernel handles the complex tasks of connecting to communicants, virtual areas, and other network resources, switching those connections in response to user inputs, and mixing realtime data streams. The realtime kernel enables developers to focus on developing high-level communications functionality instead of low-level plumbing code. The realtime kernel imposes relatively low computational resource requirements so that realtime communications performance can be achieved using a wide range of computing devices and network connections that currently are available.
Owner:SOCOCO INC
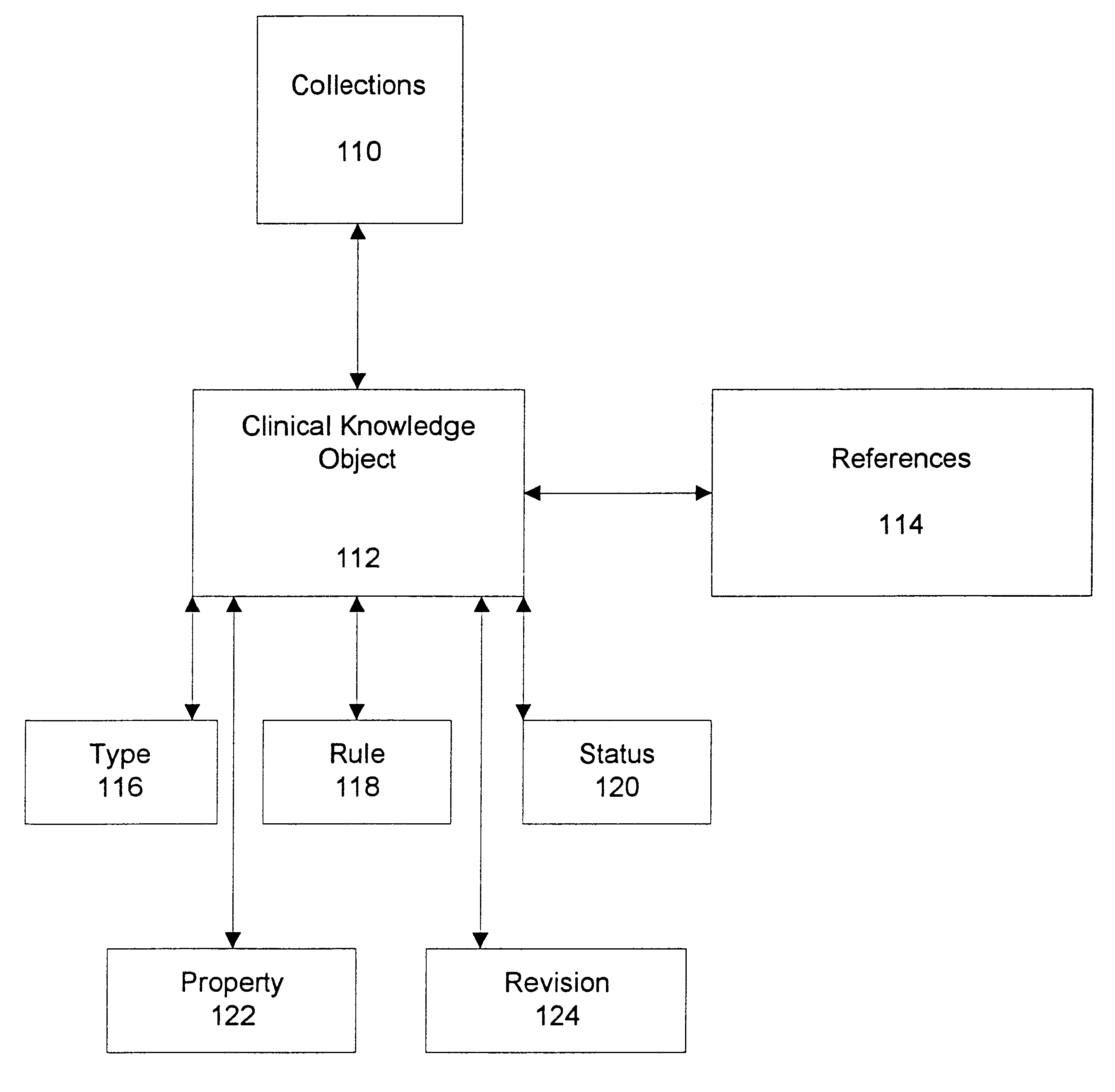
Multi-user system for creating and maintaining a medical-decision-making knowledge base
InactiveUS6353817B1Eliminate needWave based measurement systemsMedical automated diagnosisMultiuser systemHand held
A multi-user system for creating and maintaining a knowledge base is implemented on a variety of computer systems, including single-user personal computers, networked personal computers, and data communications networks, including the Internet. The system has a graphic user interface which can be easily learned by non-programmers. The knowledge base is displayed as a hierarchical multiplicity of nodes, in which each node is related to one or more superior nodes. Title of text, rules, references, and attributes associated with each node are displayed, and may be modified. Simulation is used to verify the knowledge base once generated. Data may be extracted from the bases in the form of hard-copy books, databases for downloading into Web browsers, and databases for downloading into hand-held computers including a multiplicity of grids, and a multiplicity of branches in the form of a logic tree. The user may choose one of the alternative display formats, and the hierarchy can be displayed in either collapsed view or expanded view. Interference between two or more users accessing the system concurrently is prevented by a locking and authorization subsystem, which also prevents unauthorized access to the environment. The system provides an organization of workflow into a multiplicity of development stages. Each such stage has associated with it an authorization level, developers working on the system concurrently are limited by these levels to access only particular stages and levels of development.
Owner:CHANGE HEALTHCARE HLDG LLC
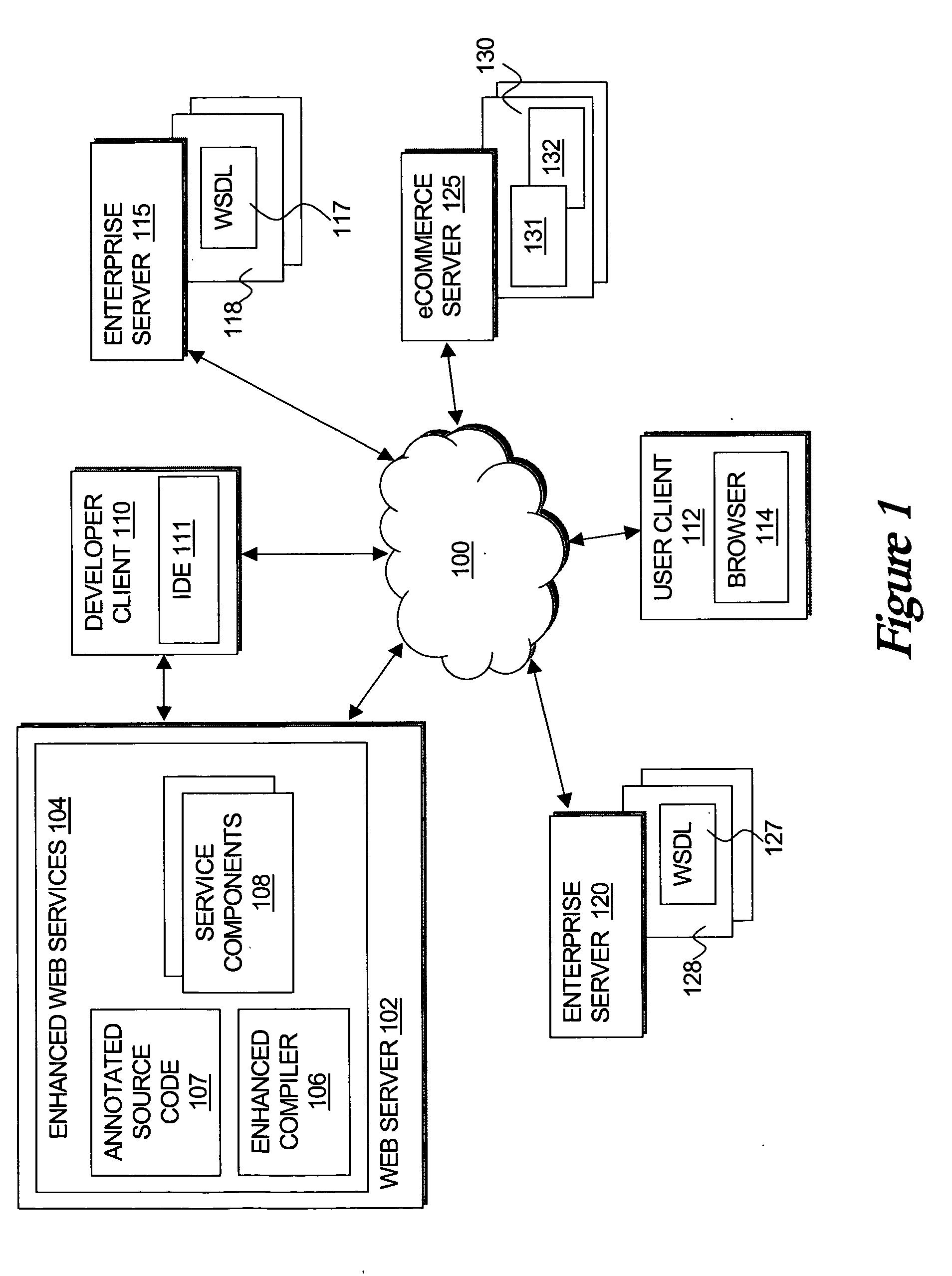
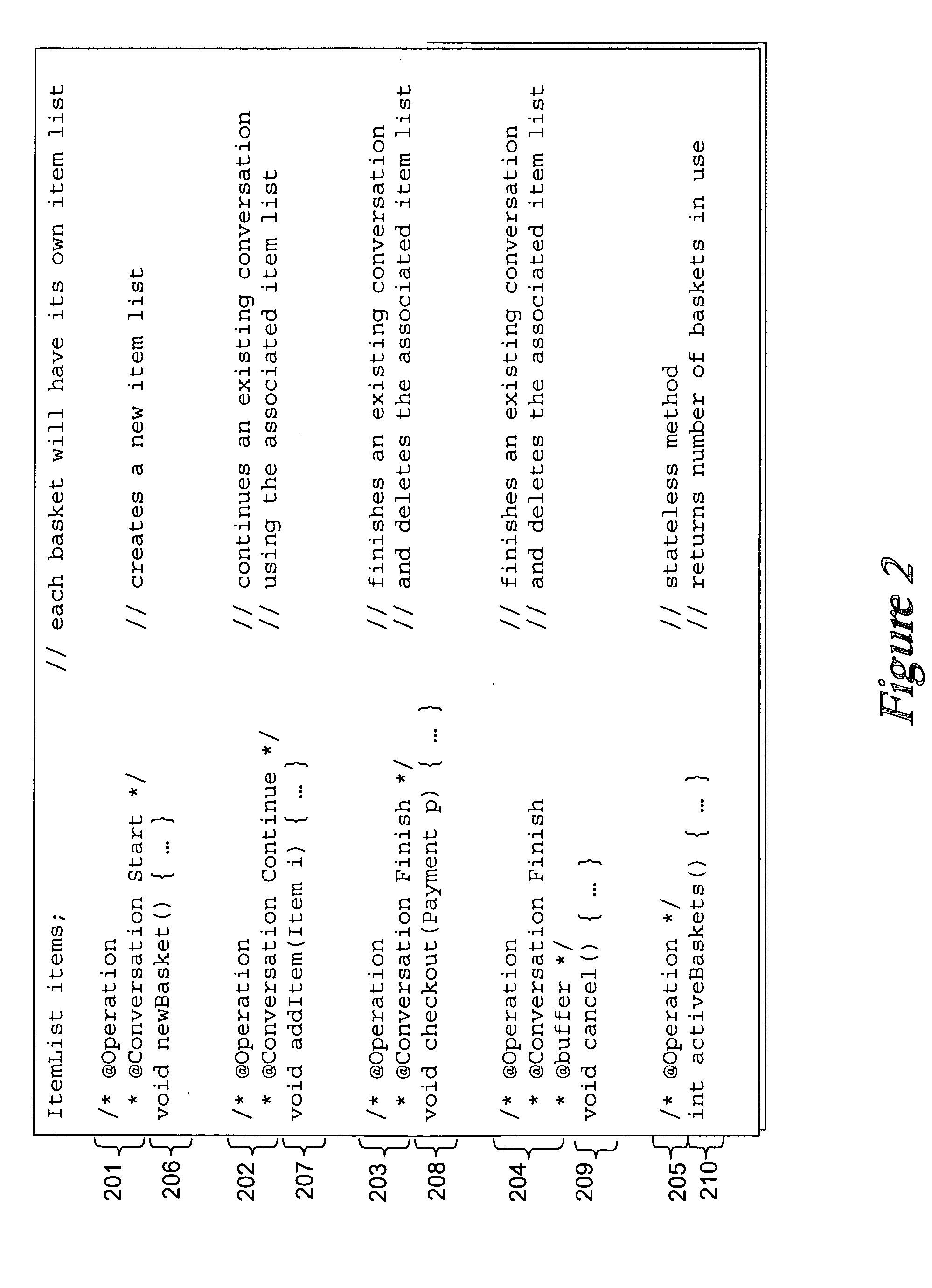
Systems and methods for creating network-based software services using source code annotations
ActiveUS20050021689A1Digital data processing detailsUnauthorized memory use protectionWeb serviceDEVS
A developer can express the logic offered by a Web service, or other network accessible service, using a standard programming language augmented with declarative annotations specifying preferences for exposing that logic as a Web service. At compile time, an enhanced compiler can analyze the annotated source file and automatically generate the mechanisms required to expose its functionality as a Web service or network accessible service. Because the annotations are declarative, they may be easily visualized, created, and modified such as by using a graphical user interface, further simplifying the developer's task. Thus, such an approach decreases the time, knowledge, skill and ultimately cost required to develop the complex support required to proved services in these environments. This description is not intended to be a complete description of, or limit the scope of, the invention. Other features, aspects, and objects of the invention can be obtained from a review of the specification, the figures, and the claims.
Owner:ORACLE INT CORP
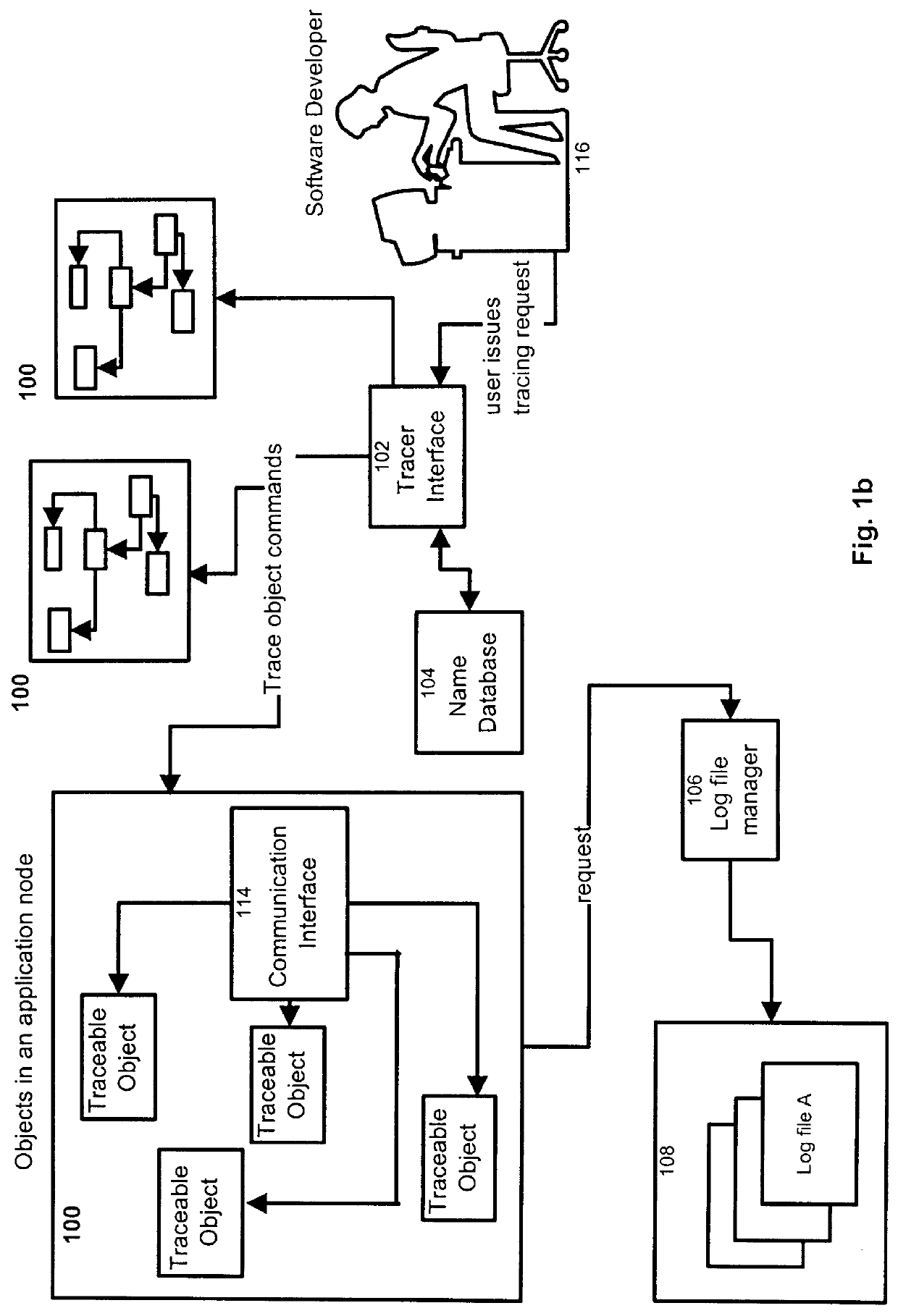
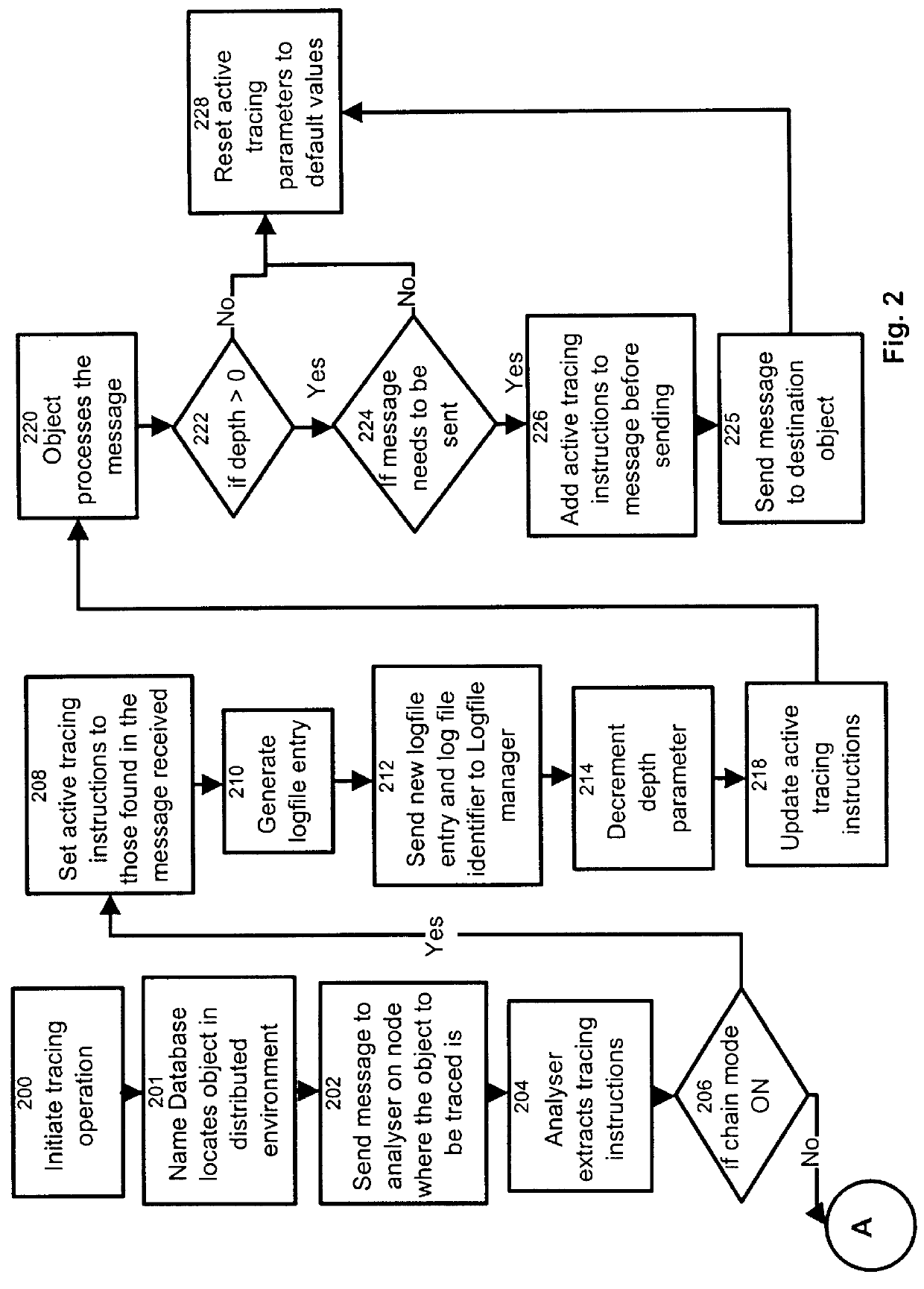
Process and apparatus for tracing software entities in a distributed system
InactiveUS6083281AHardware monitoringSoftware testing/debuggingControl flowDistributed Computing Environment
The invention relates to a process and apparatus for tracing software entities, more particularly a tracing tool providing tracing capabilities to entities in an application. The object-tracing tool provides software components to allow tracing the execution of an application. Tracing software entities is important for software developers to permit the quick localization of errors and hence facilitate the debugging process. It is also useful for the software user who wishes to view the control flow and perhaps add some modifications to the software. Traditionally, software-tracing tools have been confined to single node systems where all the components of an application run on a single machine. The novel tracing tool presented in this application provides a method and an apparatus for tracing software entities in a distributed computing environment. This is done by using a network management entity to keep track of the location of the entities in the system and by using a library of modules that can be inherited to provide tracing capabilities. It also uses a log file to allow the program developer or user to examine the flow, the occurrence of events during a trace and the values of designated attributes. The invention also provides a computer readable storage medium containing a program element to direct a processor of a computer to implement the software tracing process.
Owner:RPX CLEARINGHOUSE
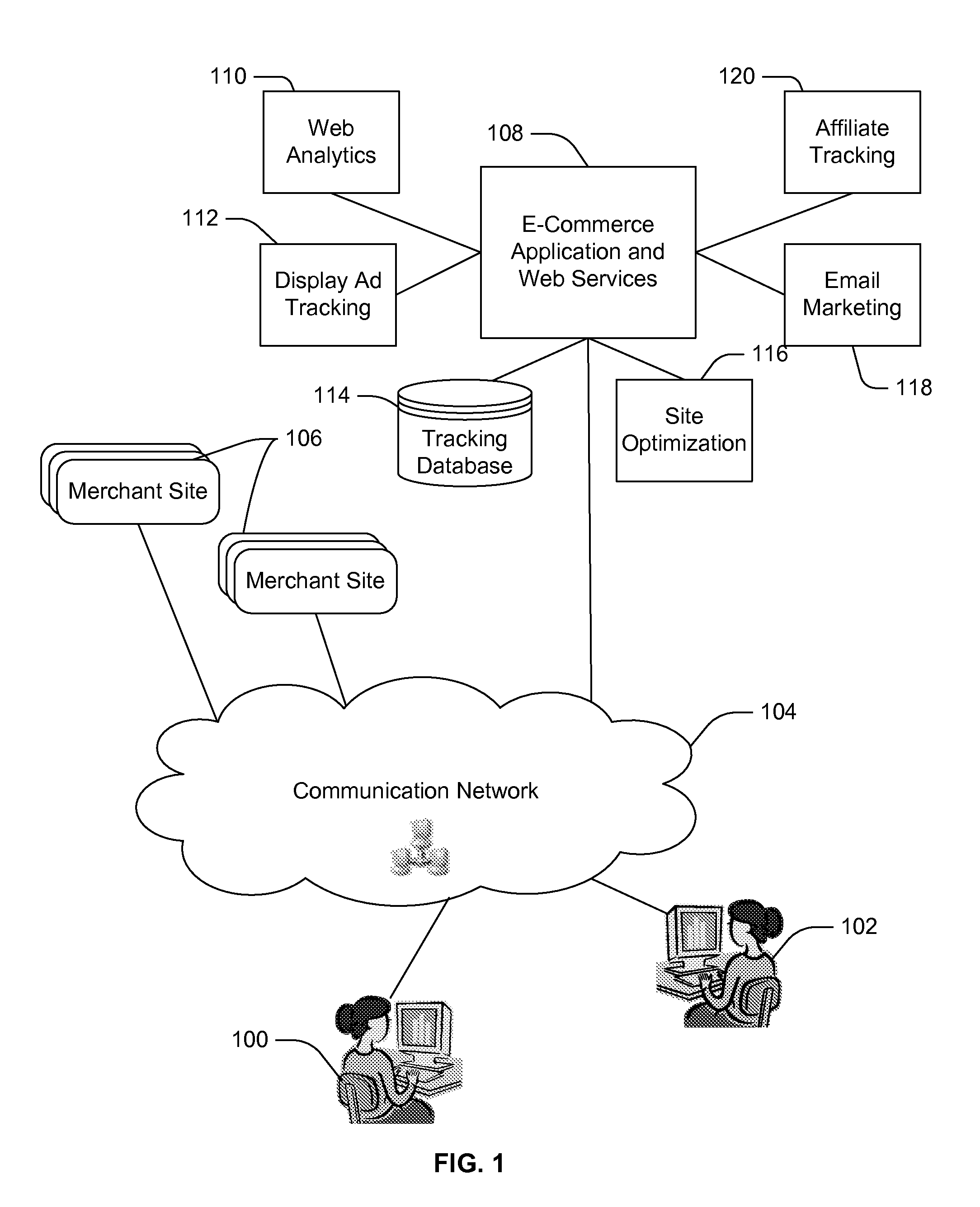
Universal Tracking Agent System and Method
A universal tracking agent system and method are described. The system utilizes a single, universal tag on merchant web pages in a commerce system. The tag collects data for marketing tracking and analysis from a local computer (e.g., a cookie or session variable set on a user computer browser) when the web pages are accessed. The system to receive the data, along with tracking code to collect the data, is determined when the program code accesses a back end database containing records of the marketing providers to which the merchant site subscribes. Only those systems requiring data for a particular user access event receive a report, and each receives a report based on its own requirements. Any changes to providers may be made in the database rather than the web page, providing a very efficient method of changing providers or code without waiting for release schedules or requiring developer resources.
Owner:DIGITAL RIVER INC
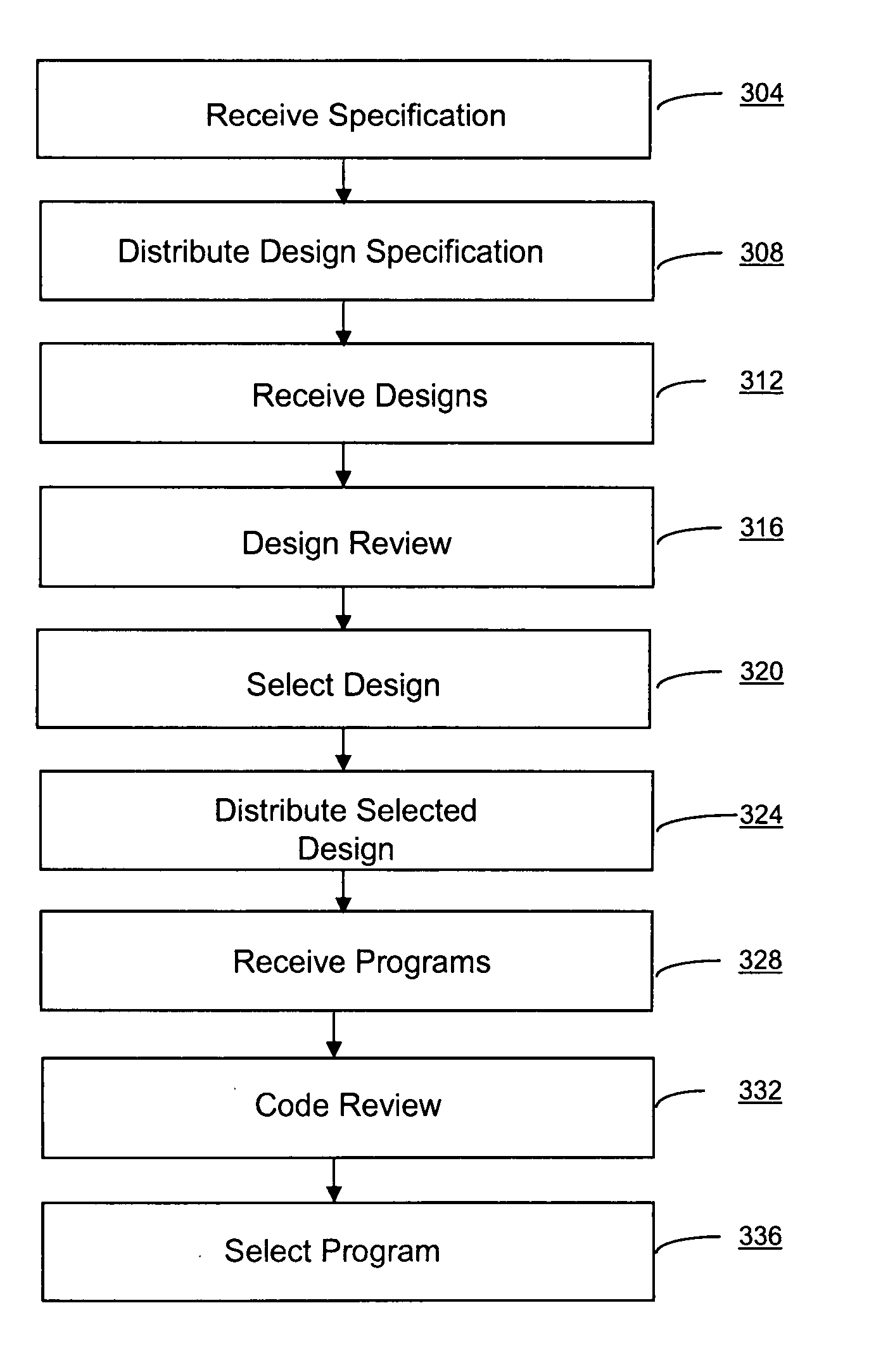
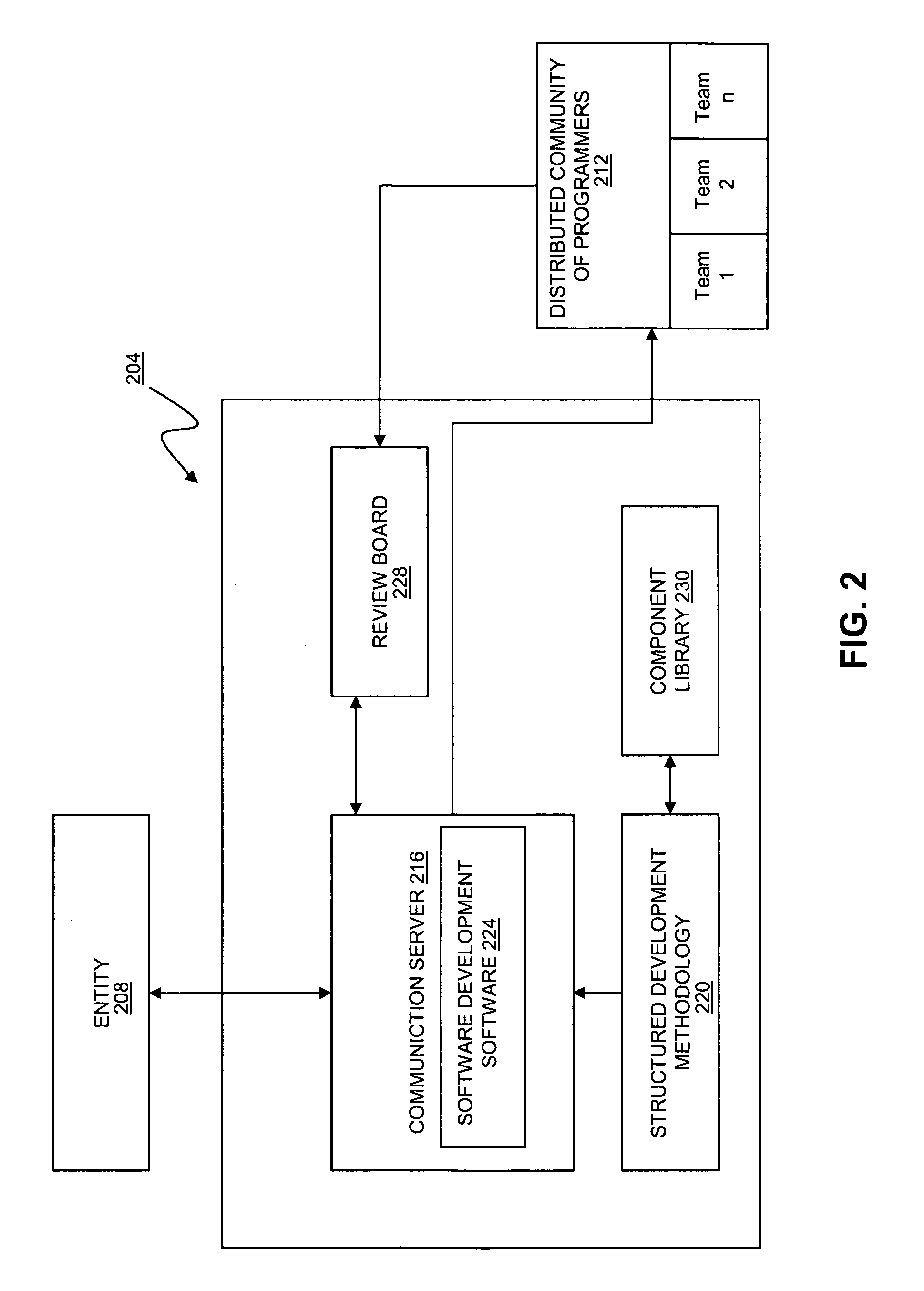
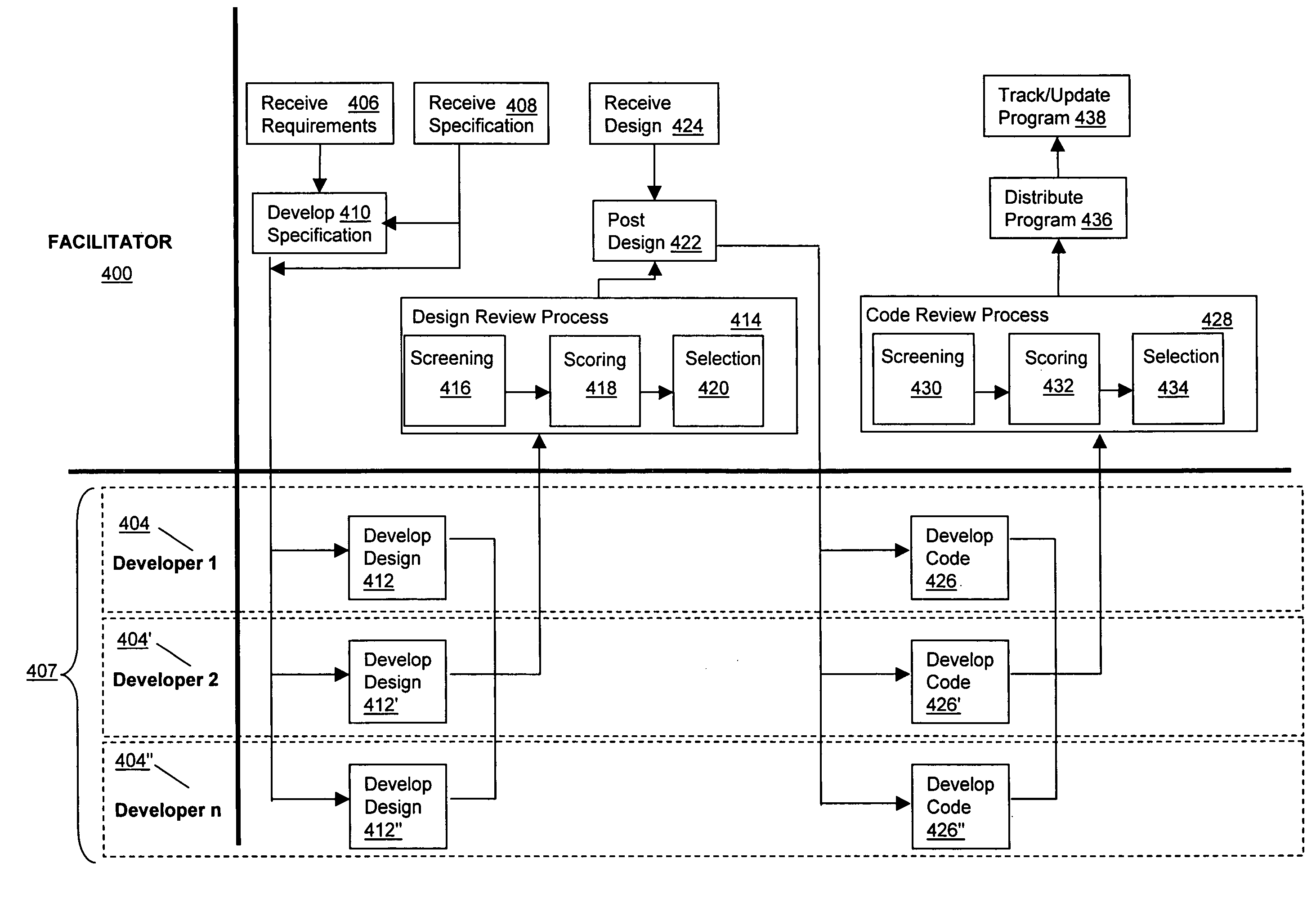
Systems and methods for software development
InactiveUS20070220479A1Without sacrificing qualityQuality improvementSoftware engineeringMarketingSoftware development processAgile software development
Software applications are developed by facilitating online software programming contests that result in functional software components. Teams of two or more developers form to compete in the competition, and a specification for the design of the software application describing the software components to be used in the development of the application are sent to the teams. In response to the specification the teams submit an assembled application built using the software components. A review process is used to score the applications, and one application is selected based on the score.
Owner:TOPCODER
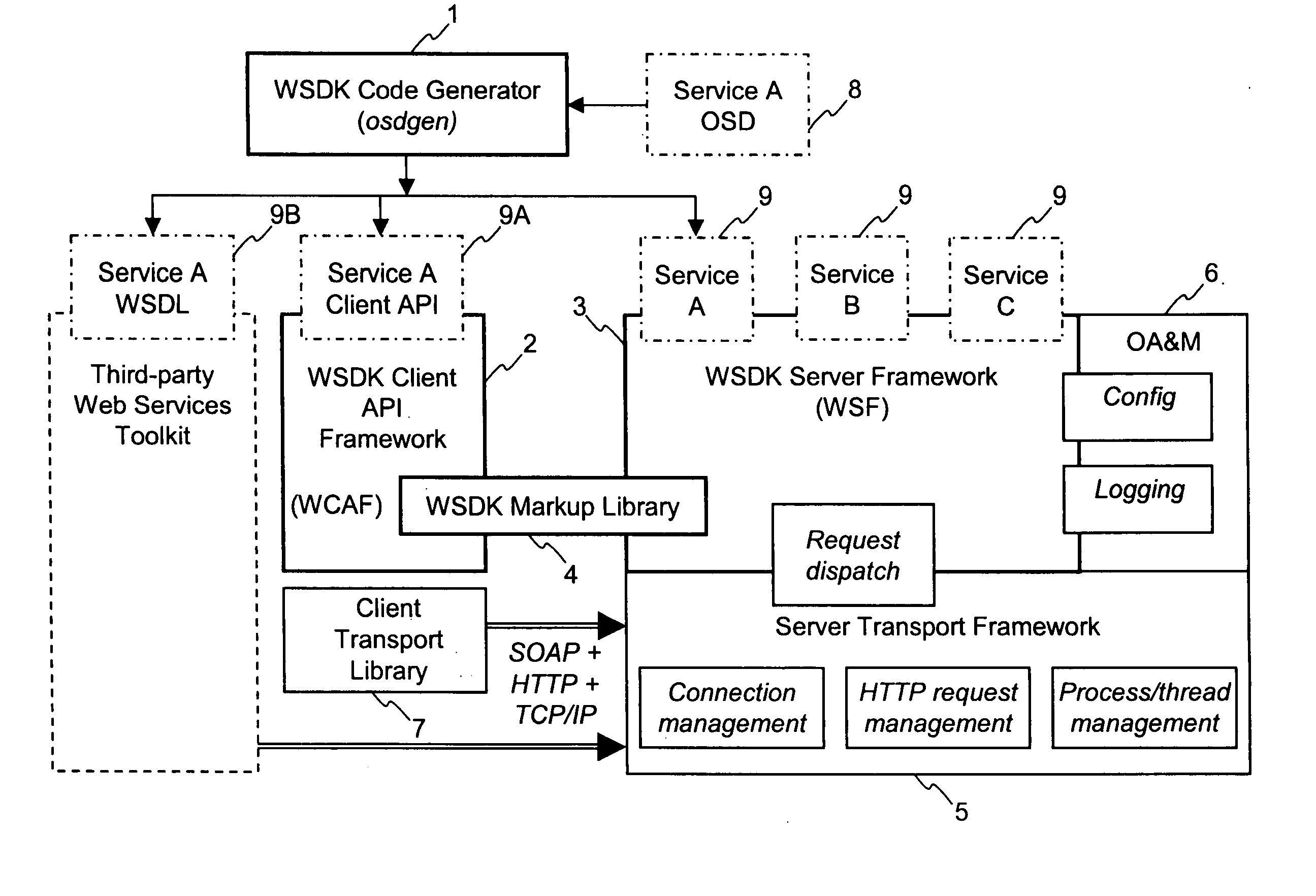
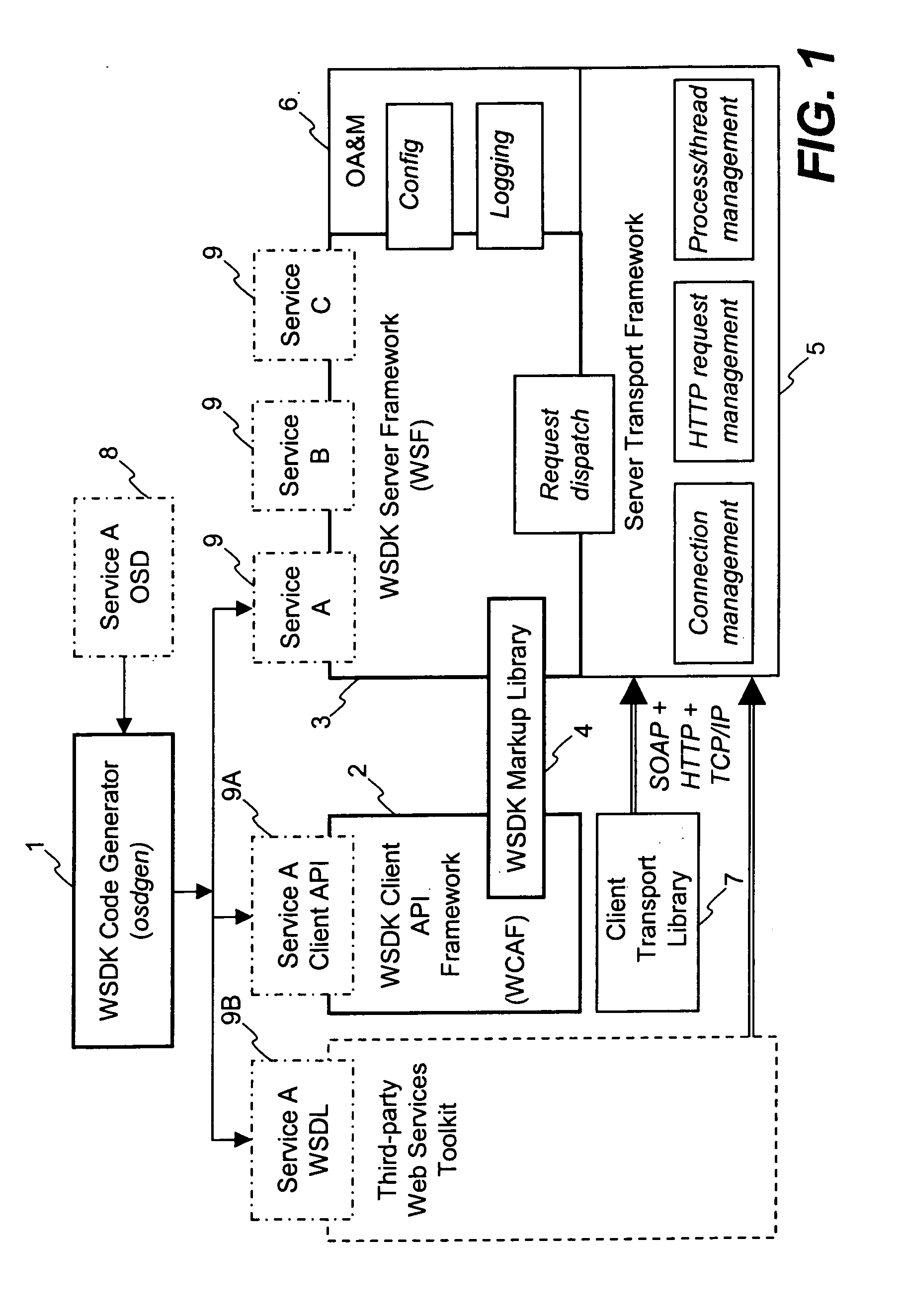
Method and apparatus for developing web services using standard logical interfaces to support multiple markup languages
InactiveUS7127700B2Website content managementSpecific program execution arrangementsTransport layerService development
The Web Services Development Kit (WSDK) comprises a set of build-time tools and run-time components designed to support the development of web services and the interface to those services. WSDK provides a framework for the development of web services that isolates developers from the implementation details of the markup and transport layers, by separating the logical aspects of the service development from the physical aspects. A “call” generated by a client contains a batch of operations to be executed in the context of a single request / reply message exchange. A markup library translates logical structure to a specific markup language. Additional markup languages are supported by adding additional modules to the markup library.
Owner:UNWIRED PLANET
Inserting device specific content
InactiveUS7428725B2Reduce deliveryDigital data information retrievalDigital computer detailsApplication softwareDEVS
A server-based application includes at least one page file that identifies one or more server objects. The page file describes the particular layout and interaction of the server objects, such as controls, in such a way that a page of information may be transmitted to a target device. When designing the page file a developer may use declarative statement, so that certain properties of the specified controls may be altered based on the particular type of target device.
Owner:MICROSOFT TECH LICENSING LLC
Systems and methods for managing content associated with multiple brand categories within a social media system
Embodiments of the present disclosure generally relate to aspects of an Internet-accessible brand management system (BMS) that allows marketers (e.g., corporations, organizations, etc.) to efficiently organize, create, maintain, and display content associated with many brand categories or brand items within a brand category on a single social media system (SMS) page / account, or alternatively, across many SMS pages or accounts with one or more common content themes. Administrators / developers of individual marketing pages or accounts (global and local) may update their pages through the BMS using standard configurable templates. The system may integrate content from one or more developers to create content for varying pages (for example, by incorporating some global content into local pages according to configurable rules, or vice versa). Subsequently, when a social media system user requests content associated with a particular brand category or brand item within that category on a social media system, the brand management system renders the updated, requested marketing page associated with that category, but within a global marketer page, or with common marketer content also provided.
Owner:ORACLE INT CORP
System, method and apparatus for providing functions to applications on a digital electronic device
InactiveUS20100257539A1Enabling and simplifying application developmentShorten development timeService provisioningInterprogram communicationDiscrete functionsApplication software
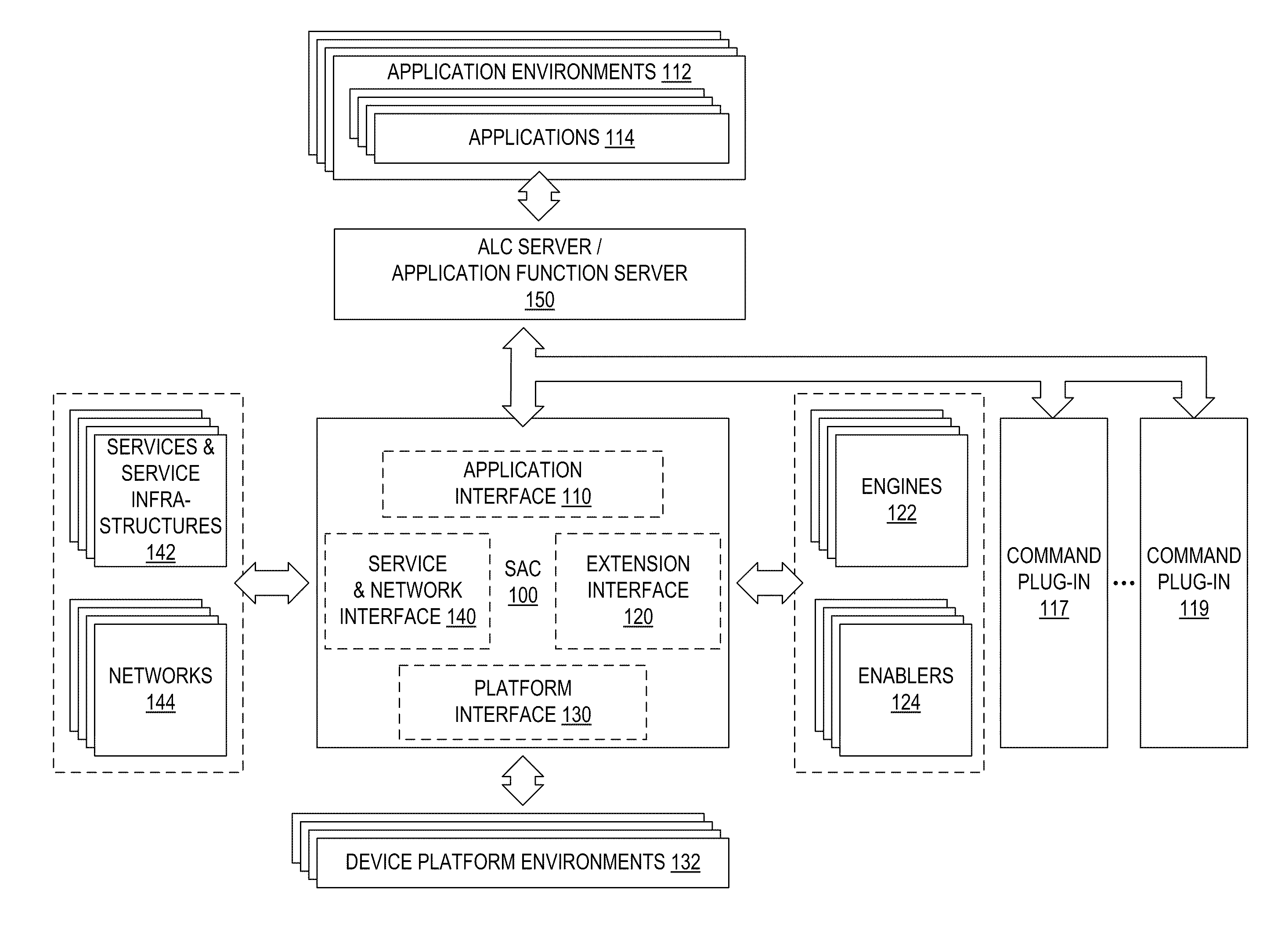
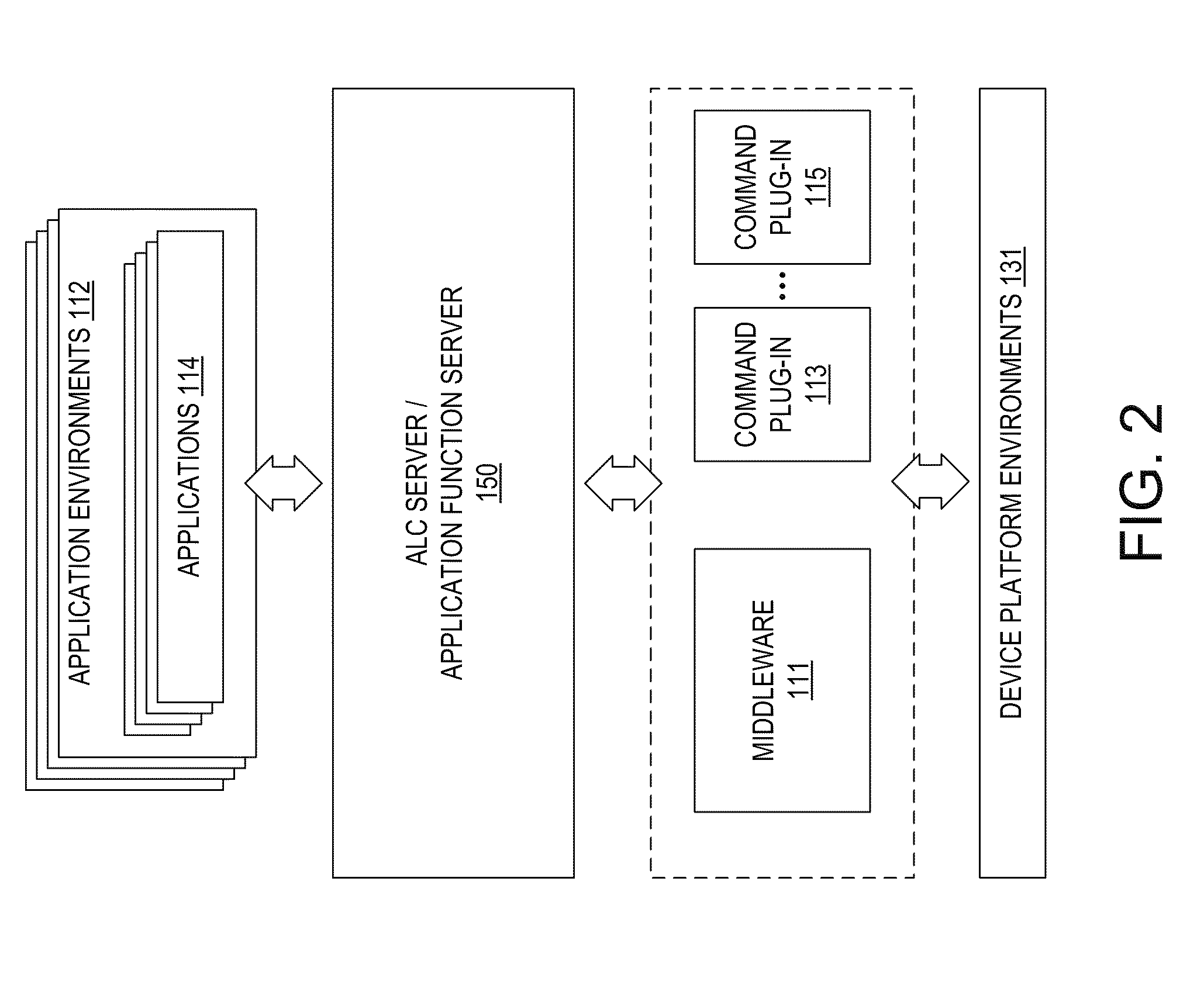
To greatly simplify the developer's task, an application function server or application logic controller (“ALC”) server runs on a digital electronic device with a common set of tools and methods to deliver high-value capabilities to applications developed in different application languages and running in various different application environments. The applications and the application function server have a local client-server relationship. The functions themselves are provided by various plug-ins. The interface of a plug-in illustratively is a discrete set of functions, common to the command plug-ins. The ALC Server accepts simplified commands directly from the applications, applies the appropriate policy, and interacts with the plug-ins to perform the requested functions on behalf of the applications. The result is that applications can use various capabilities without dealing with the complex methods, standards, and system interoperability required to make the technologies work, and technology additions and upgrades can be performed independently from the applications that use them.
Owner:ECRIO
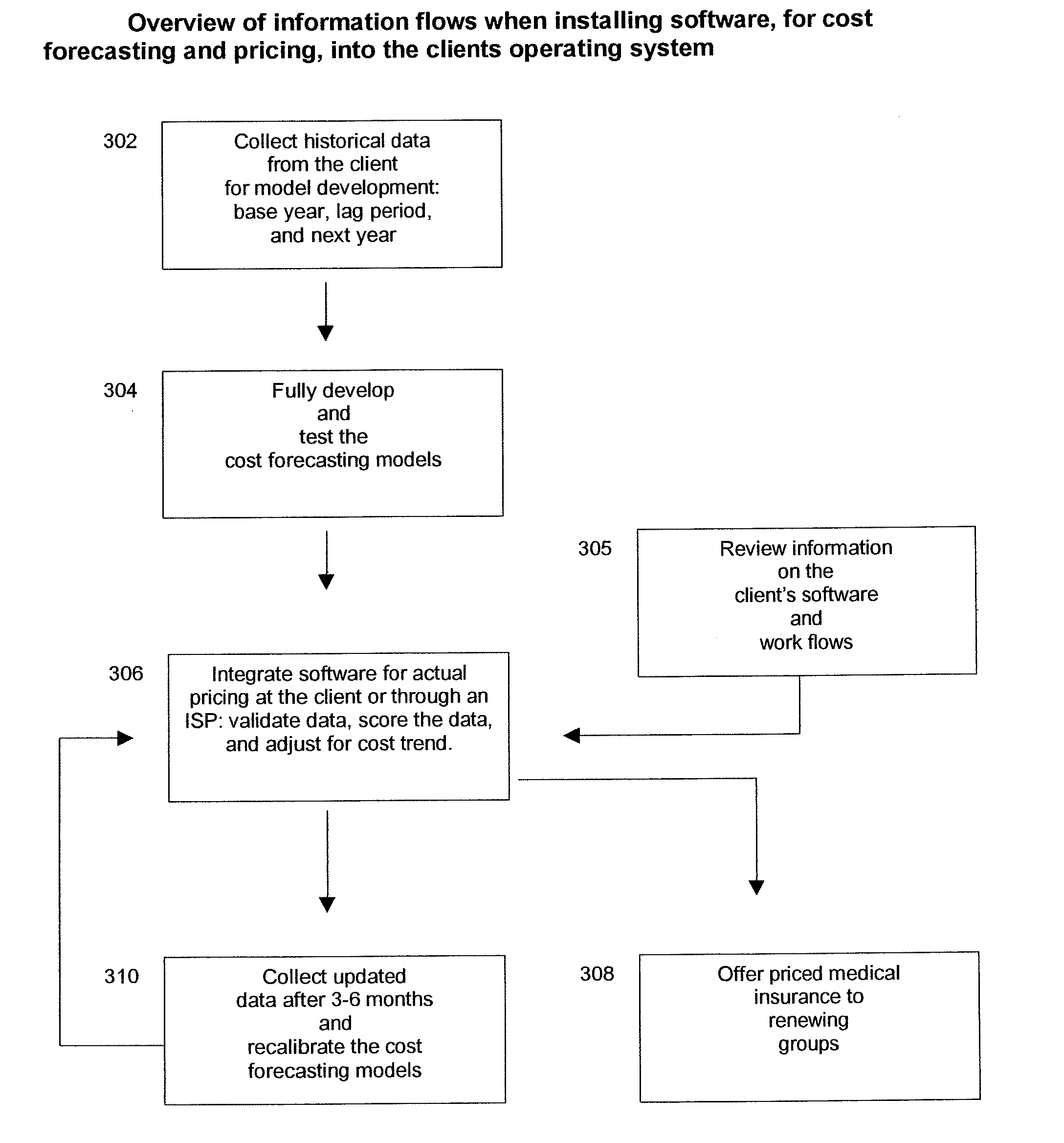
Insurance claim forecasting system
A computer-implemented process of developing a person-level cost model for forecasting future costs attributable to claims from members of a book of business, where person-level data are available for a substantial portion of the members of the book of business for an actual underwriting period, and the forecast of interest is for a policy period is disclosed. The process uses development universe data comprising person-level enrollment data, historical base period health care claims data and historical next period claim amount data for a statistically meaningful number of individuals. The process also provides at least one claim-based risk factor for each historical base period claim based on the claim code associated with the health care claim and provides at least one enrollment-based risk factor based on the enrollment data. The process also develops a cost forecasting model by capturing the predictive ability of the main effects and interactions of claim based risk factors and enrollment-based risk factors, with the development universe data through the application of an interaction capturing technique to the development universe data.
Owner:BINNS GREGORY S +1
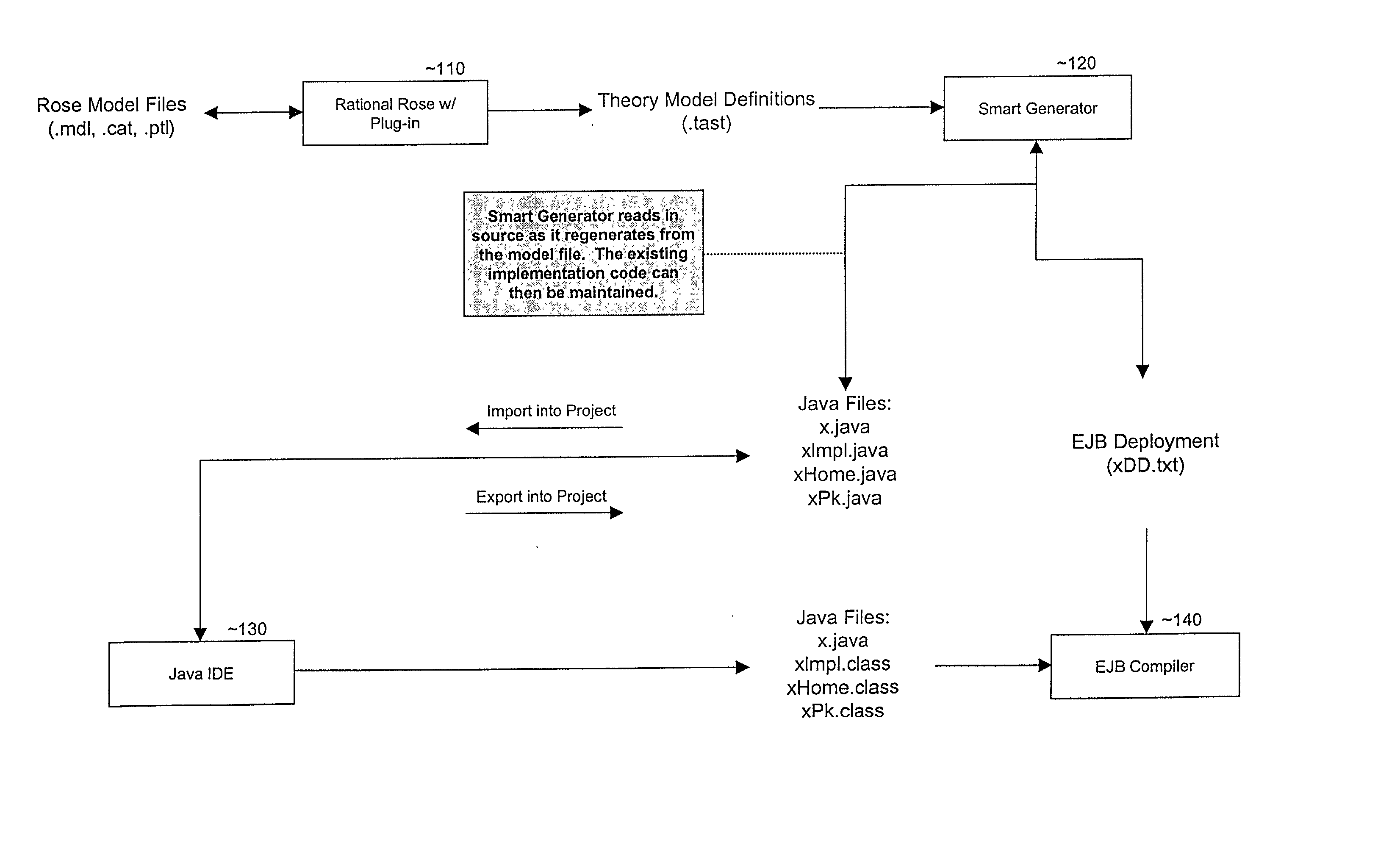
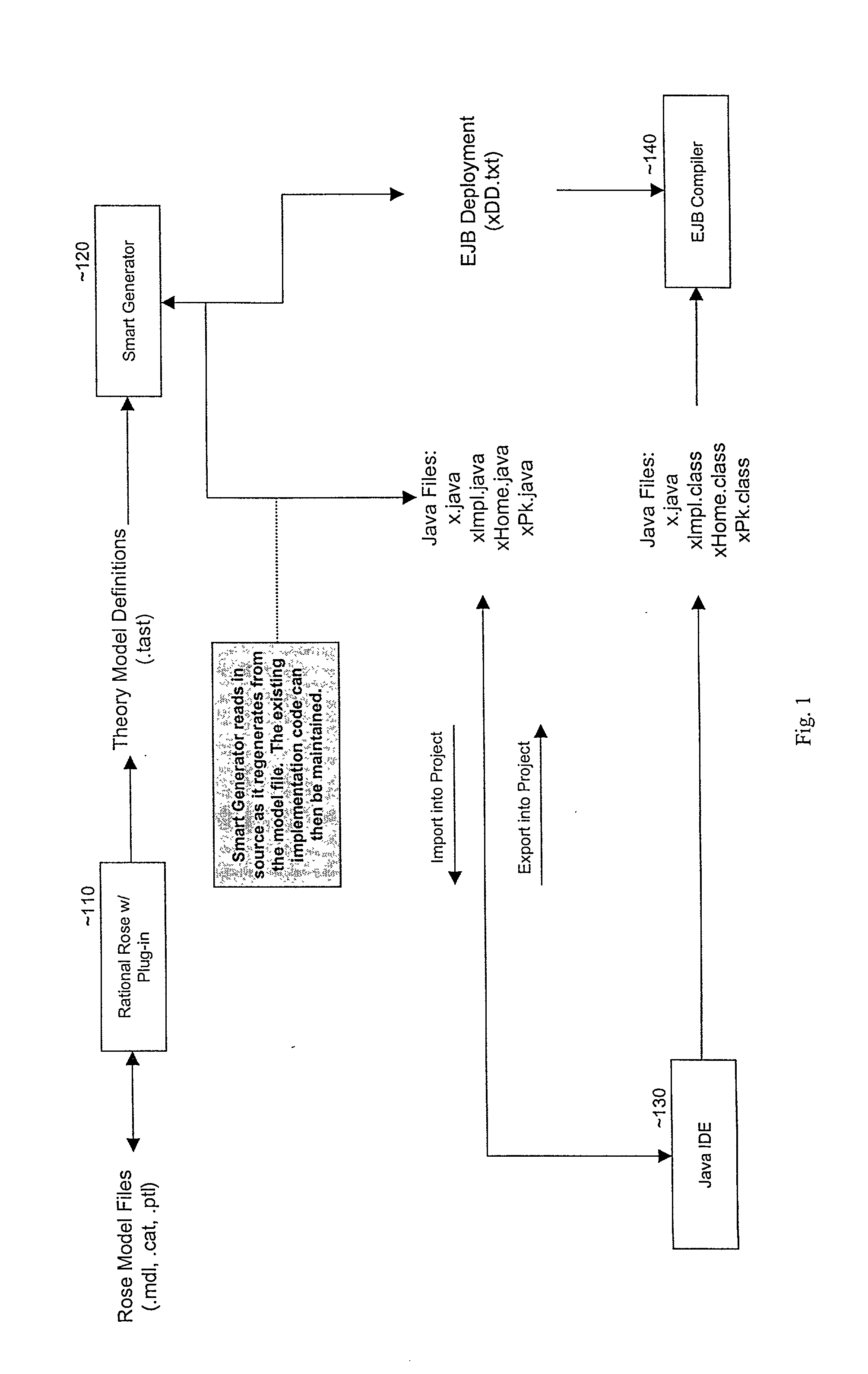
Smart generator
ActiveUS20020147763A1Laborious taskDigital data information retrievalMultiple digital computer combinationsAccess methodDEVS
The Smart Generator of the present invention allows the designer / developer / user to model the EJB components in a natural way without being concerned with implementation-specific details. The developer models the business objects using a UML drawing tool and the Smart Generator creates a set of classes that implements these objects with reference to the Enterprise JavaBeans specification. That is, the Smart Generator automatically create access methods and handling containment of references from the UML diagram.
Owner:ORACLE INT CORP
Tool for graphically defining dialog flows and for establishing operational links between speech applications and hypermedia content in an interactive voice response environment
A computer-implemented graphical design tool allows a developer to graphically author a dialog flow for use in a voice response system and to graphically create an operational link between a hypermedia page and a speech object. The hypermedia page may be a Web site, and the speech object may define a spoken dialog interaction between a person and a machine. Using a drag-and-drop interface, the developer can graphically define a dialog as a sequence of speech objects. The developer can also create a link between a property of any speech object and any field of a Web page, to voice-enable the Web page, or to enable a speech application to access Web site data.
Owner:NUANCE COMM INC
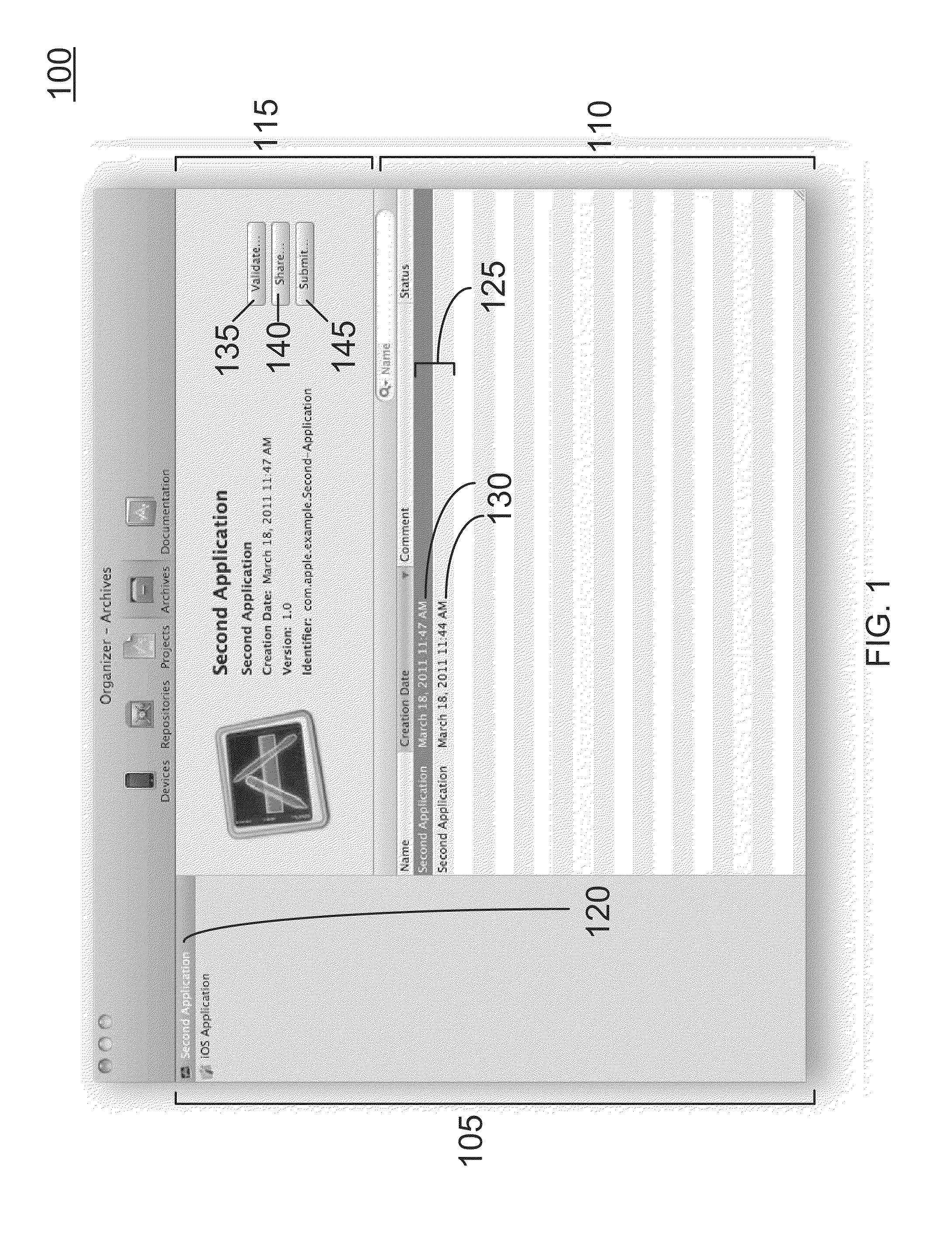
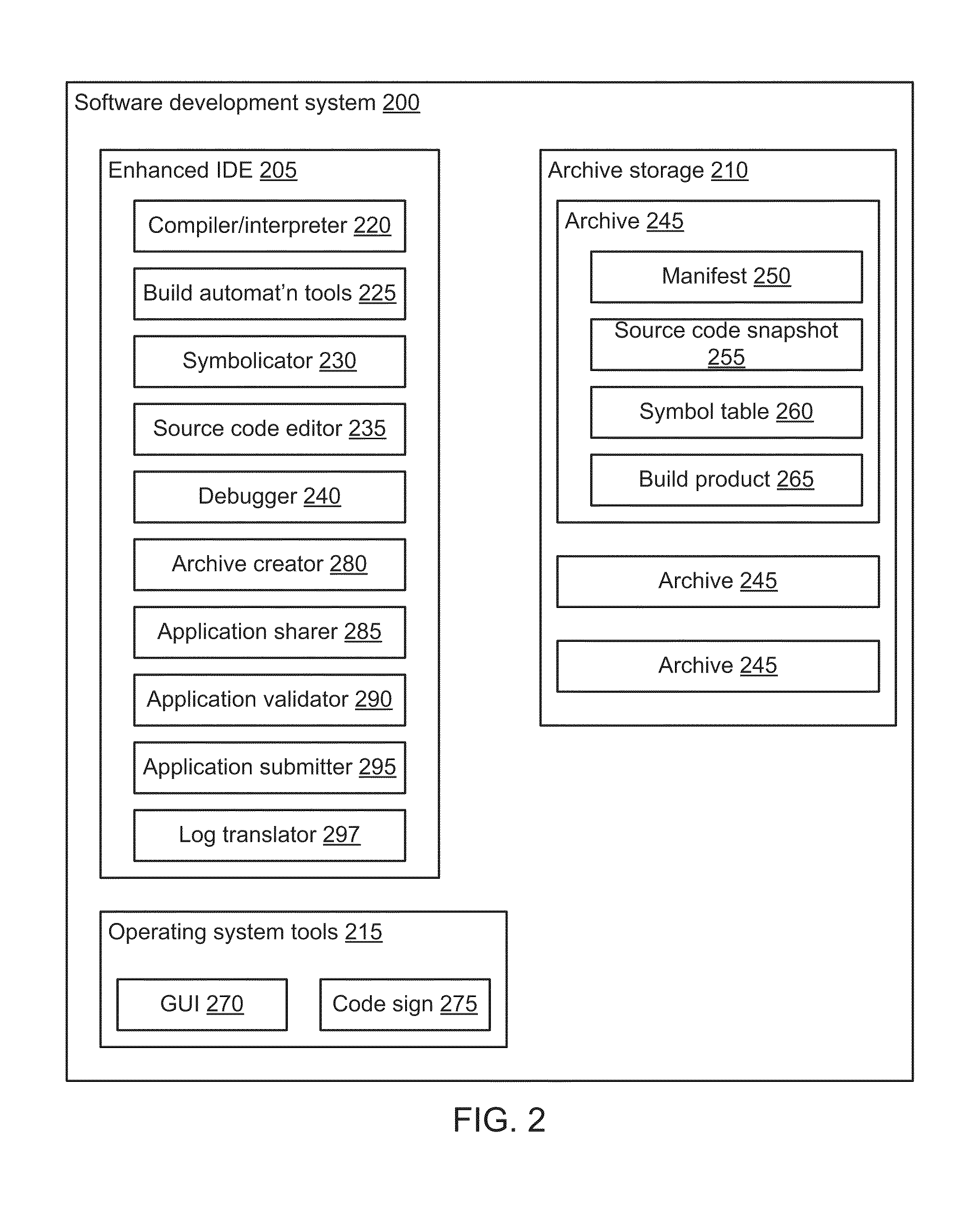
Archiving a Build Product
An enhanced integrated development environment (IDE) is able to archive a build product and / or work with an archived build product in various ways. In one embodiment, a build product archive includes a manifest, a source code snapshot, a symbol table, and a build product. The manifest contains meta-data about the archive. The source code snapshot is a copy of the source code that was used in the build process. The symbol table is a copy of the symbol table that was generated by the build process. The build product is a copy of the build product that was generated by the build process. A developer can use the enhanced IDE to help share a build product with others and / or to understand system logs and reports that describe operation of the build product (e.g., crash logs and memory logs).
Owner:APPLE INC
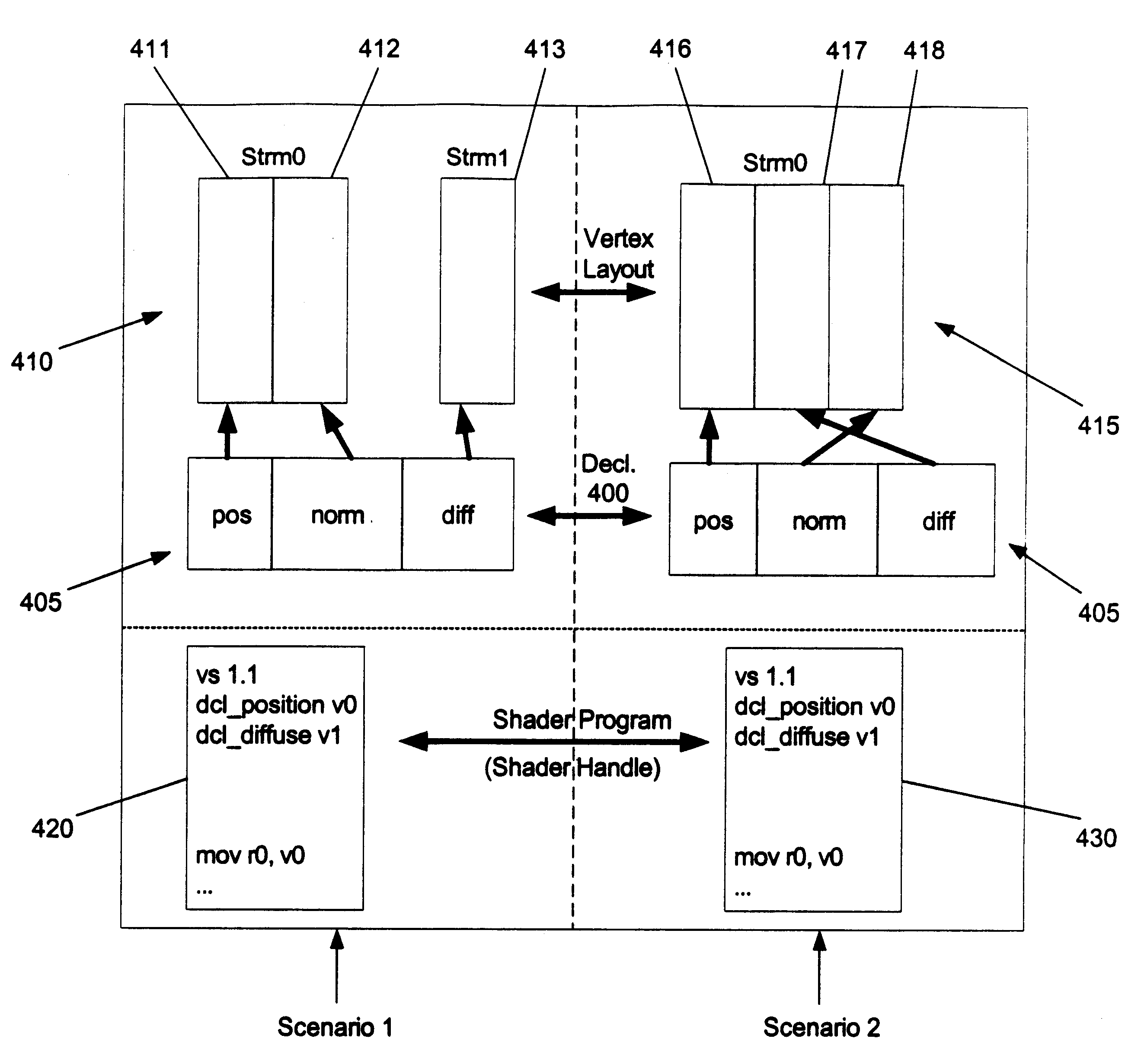
Usage semantics
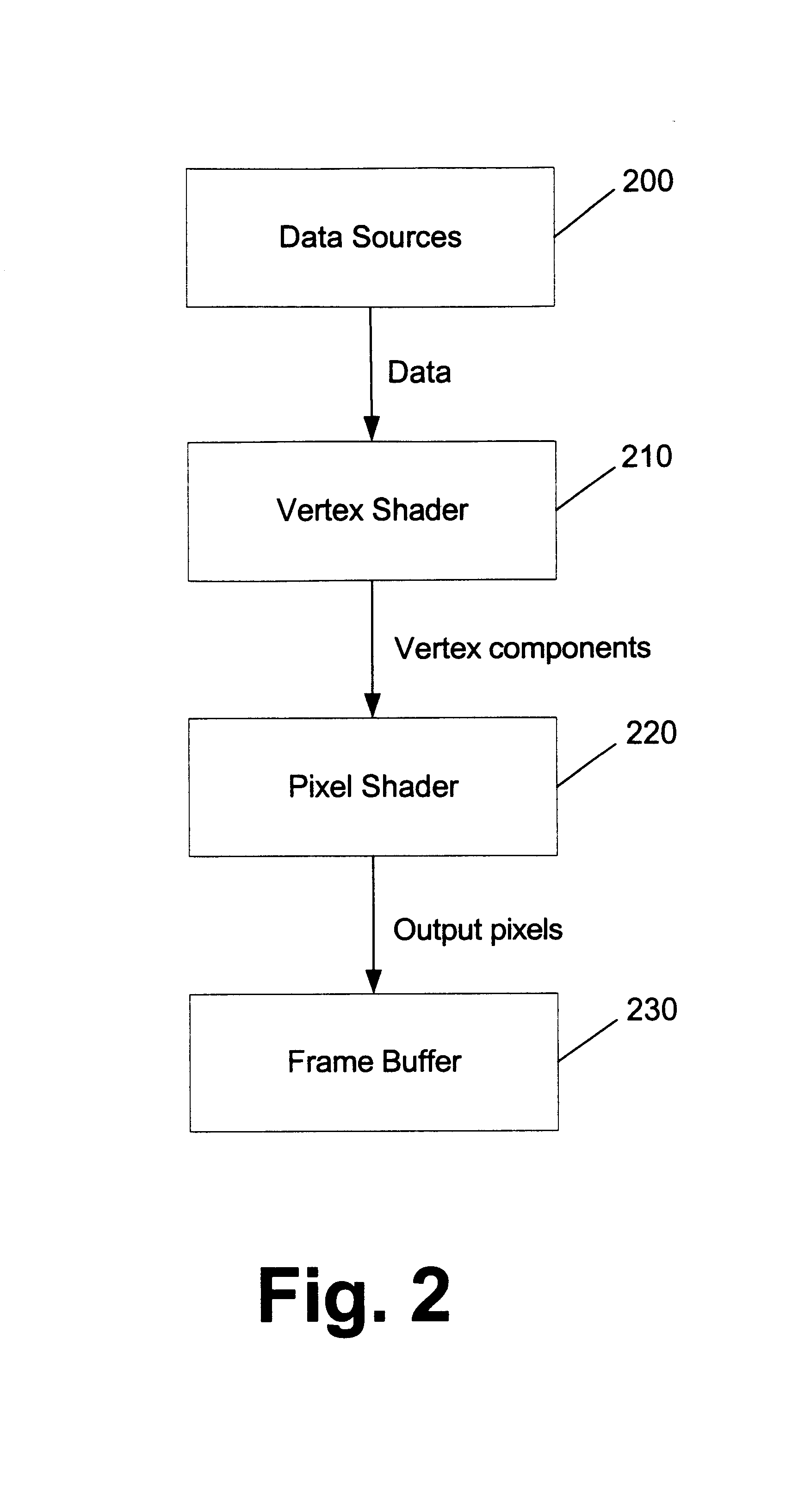
InactiveUS6839062B2Improve the level ofFlexible workflowData processing applicationsImage data processing detailsData streamData set
Usage semantics allow for shaders to be authored independently of the actual vertex data and accordingly enables their reuse. Usage semantics define a feature that binds data between distinct components to allow them to work together. In various embodiments, the components include high level language variables that are bound by an application or by vertex data streams, high level language fragments to enable several fragments to be developed separately and compiled at a later time together to form a single shader, assembly language variables that get bound to vertex data streams, and parameters between vertex and pixel shaders. This allows developers to be able to program the shaders in the assembly and high level language with variables that refer to names rather than registers. By allowing this decoupling of registers from the language, developers can work on the language separately from the vertex data and modify and enhance high level language shaders without having to manually manipulate the registers. This also allows the same shaders to work on different sets of mesh data, allowing the shaders to be reused. Generally, semantics can be used as a data binding protocol between distinct areas of the programmable pipeline to allow for a more flexible workflow.
Owner:MICROSOFT TECH LICENSING LLC
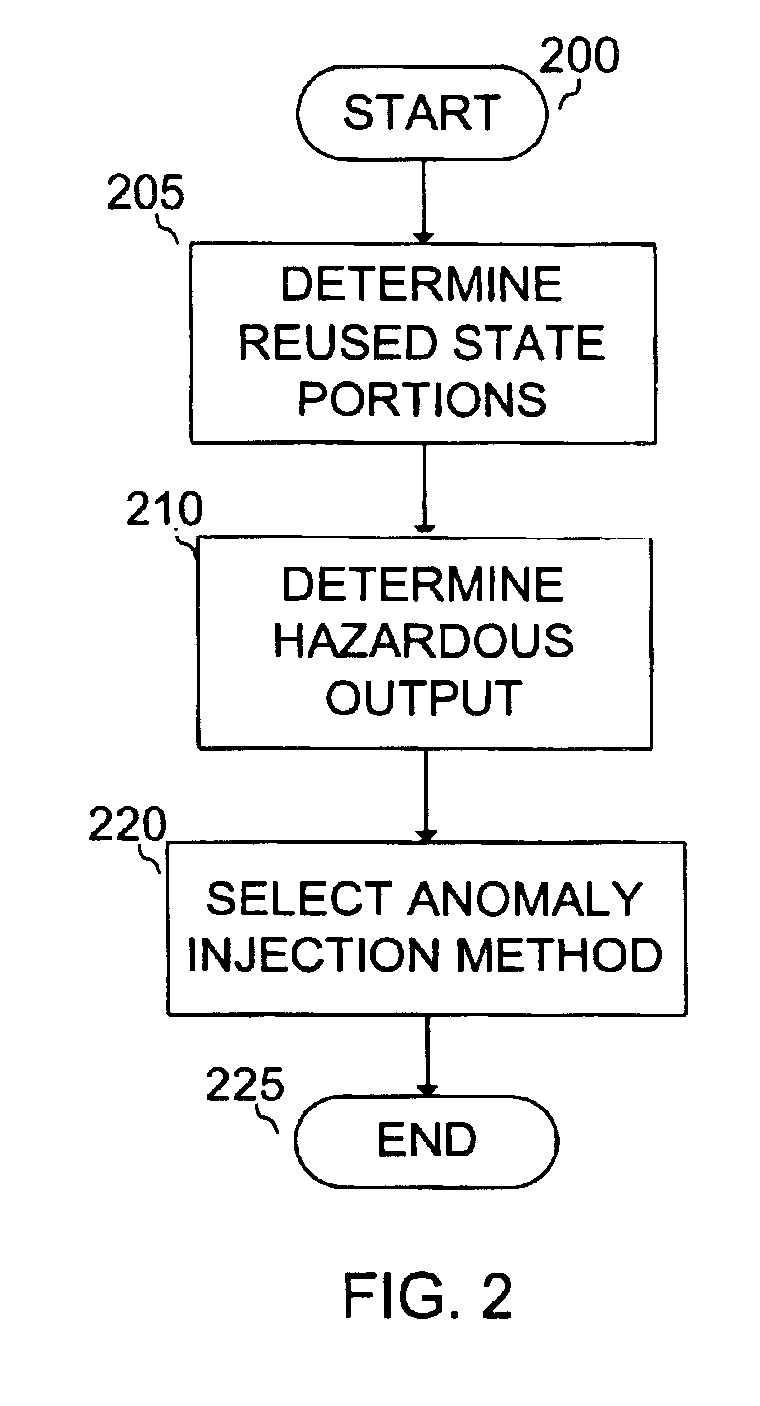
Method for reducing catastrophic failures in continuously operating software systems
InactiveUS7024592B1Accurate operationError detection/correctionSpecific program execution arrangementsSoftware systemProgram planning
A method for assessing how long continuously operating software systems can be expected to remain executing in a safe and / or reliable manner before anomalous conditions will ultimately lead to failure. For safety-critical applications the method can provide a safe upper bound on the time between rebooting. Also disclosed is an empirical technique for determining which portions of the state, if corrupted create the greatest risks to safe and / or reliable continual execution of the software. Armed with this information, developers, testers, and certifiers can create justifiable plans for the frequency with which the software should be rebooted. Further, they can customize and embed internal self-tests into those portions of the state found to have the greatest risks to safe and / or reliable, continual execution of the software. These self-tests can also warn when failures are likely to occur well in advance of the failures, so that the software may be safely rejuvenated to avert undesired or catastrophic conclusions.
Owner:SYNOPSYS INC
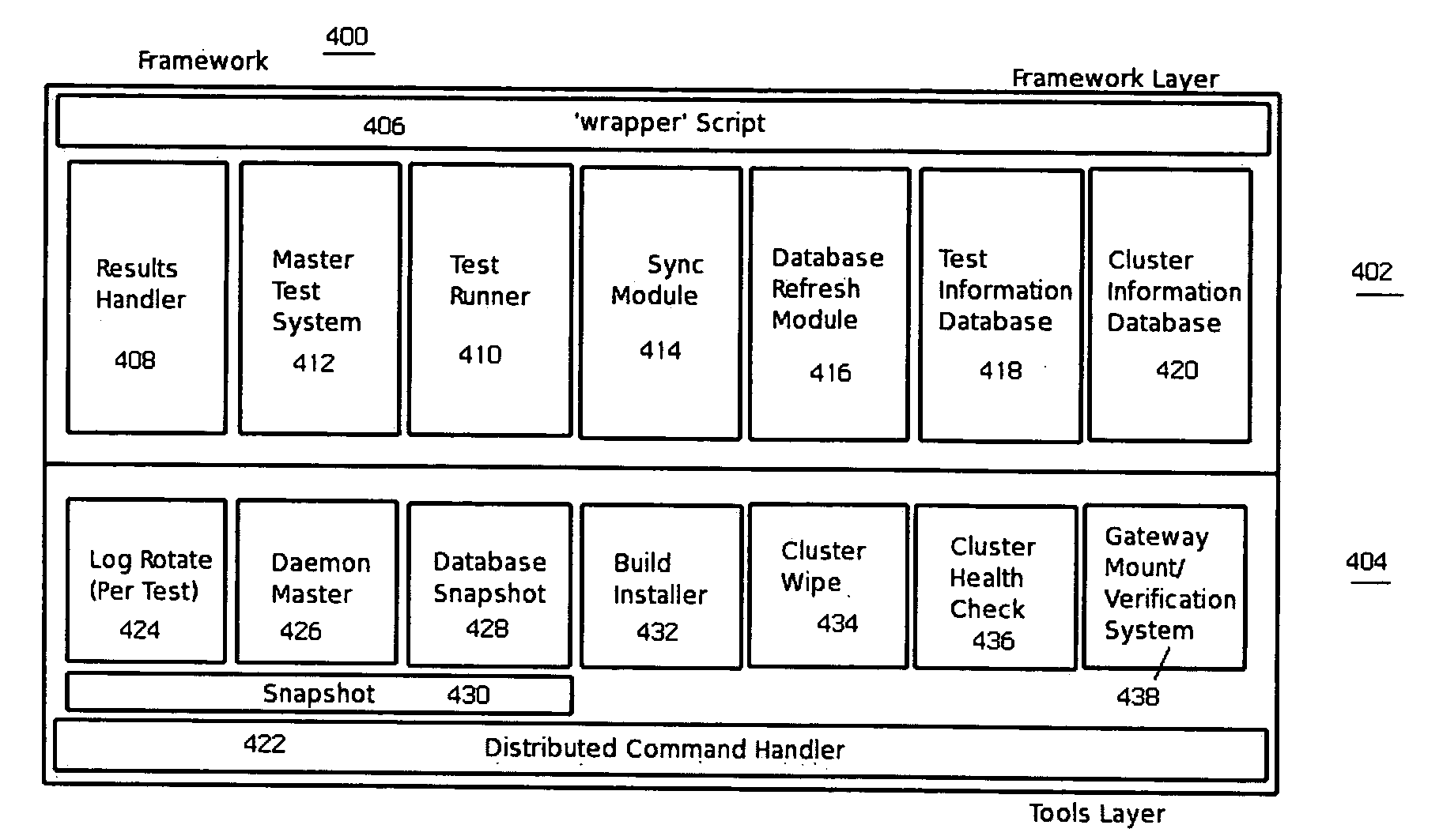
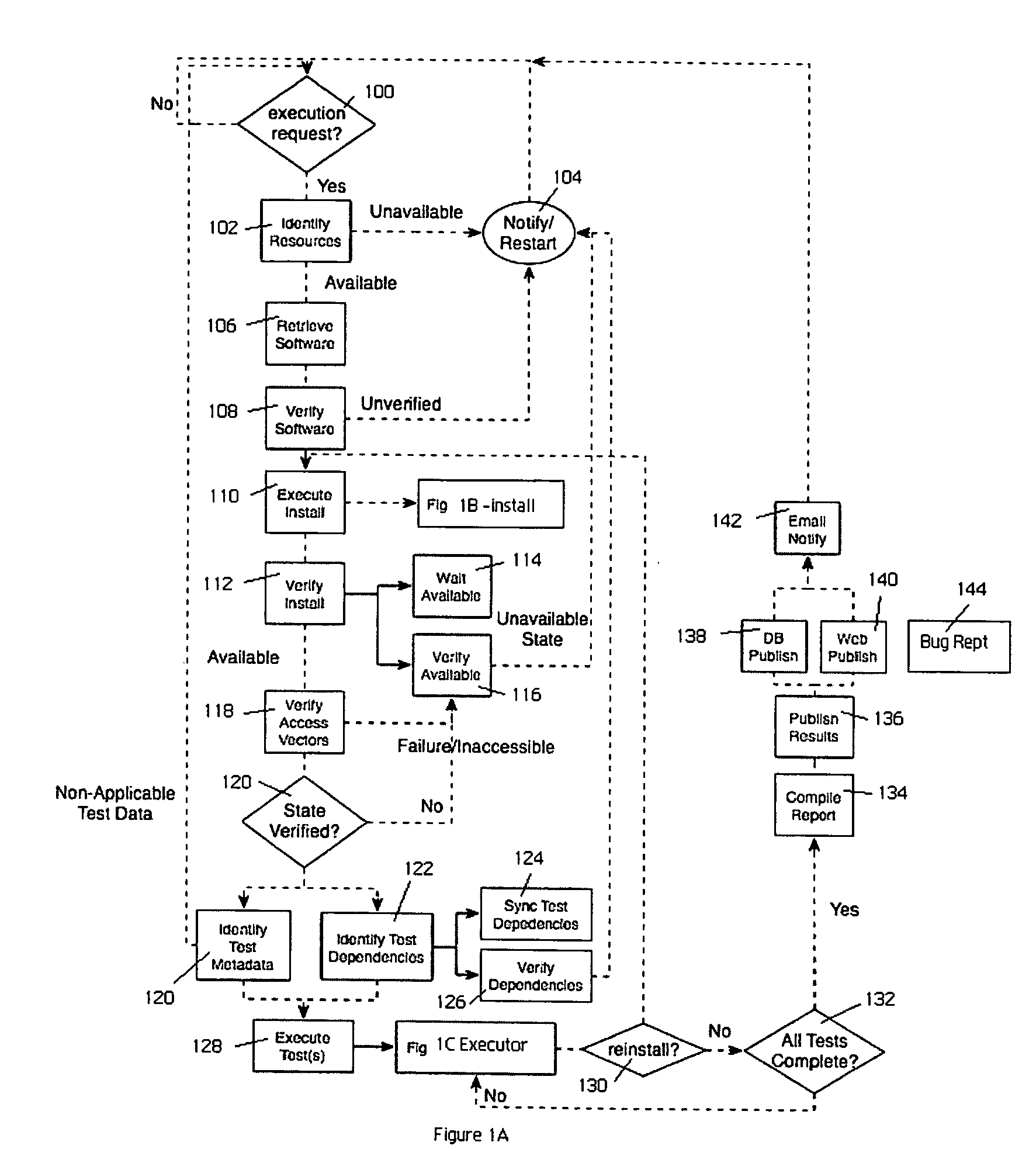
Automated software testing framework
InactiveUS7694181B2Simple and efficientEasy to exportError detection/correctionSpecific program execution arrangementsWeb serviceSystem under test
A generic testing framework to automatically allocate, install and verify a given version of a system under test, to exercise the system against a series of tests in a “hands-off” objective manner, and then to export information about the tests to one or more developer repositories (such as a query-able database, an email list, a developer web server, a source code version control system, a defect tracking system, or the like). The framework does not “care” or concern itself with the particular implementation language of the test as long as the test can issue directives via a command line or configuration file. During the automated testing of a given test suite having multiple tests, and after a particular test is run, the framework preferably generates an “image” of the system under test and makes that information available to developers, even while additional tests in the suite are being carried out. In this manner, the framework preserves the system “state” to facilitate concurrent or after-the-fact debugging. The framework also will re-install and verify a given version of the system between tests, which may be necessary in the event a given test is destructive or otherwise places the system in an unacceptable condition.
Owner:HITACHI DATA SYST CORP
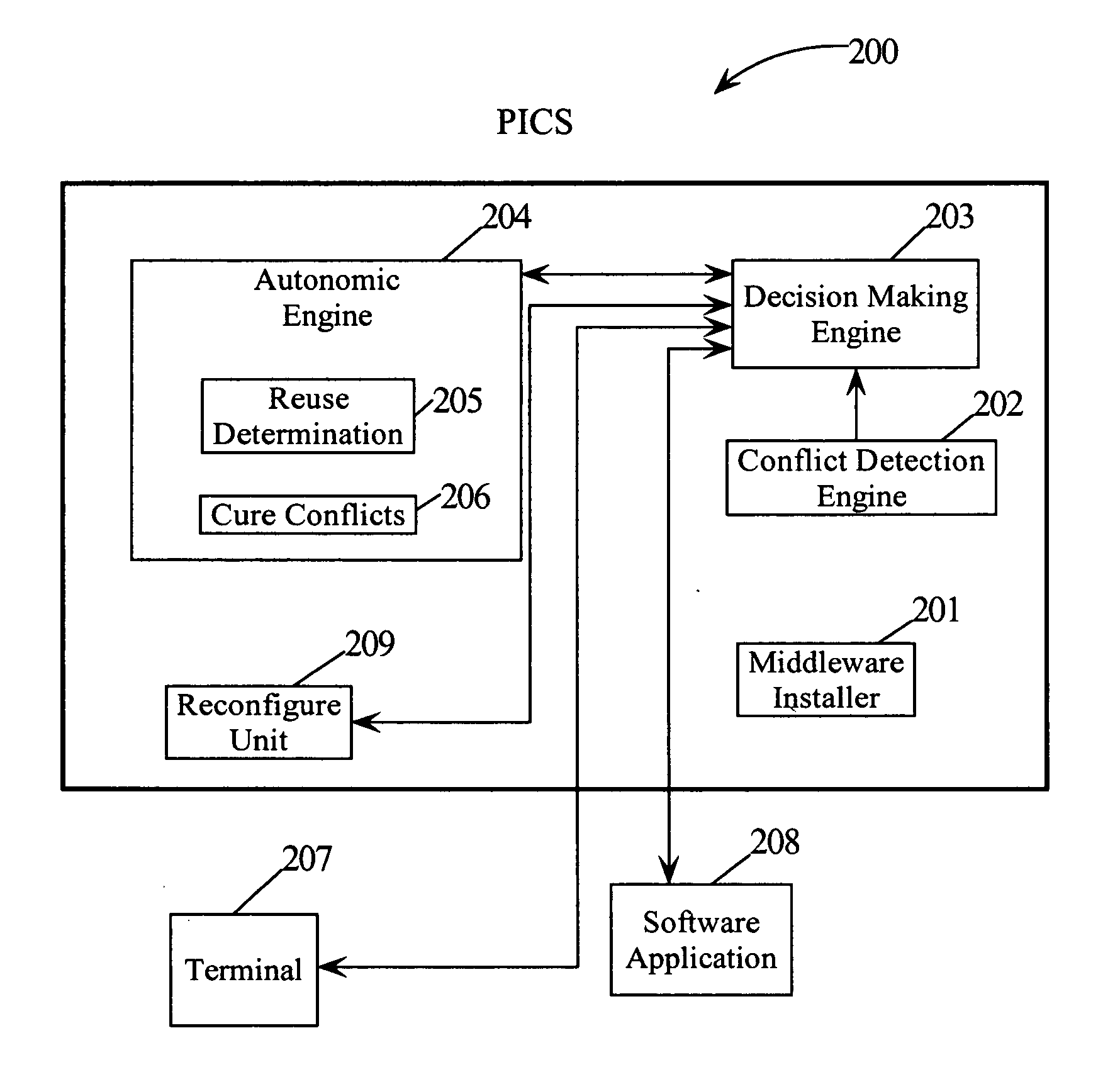
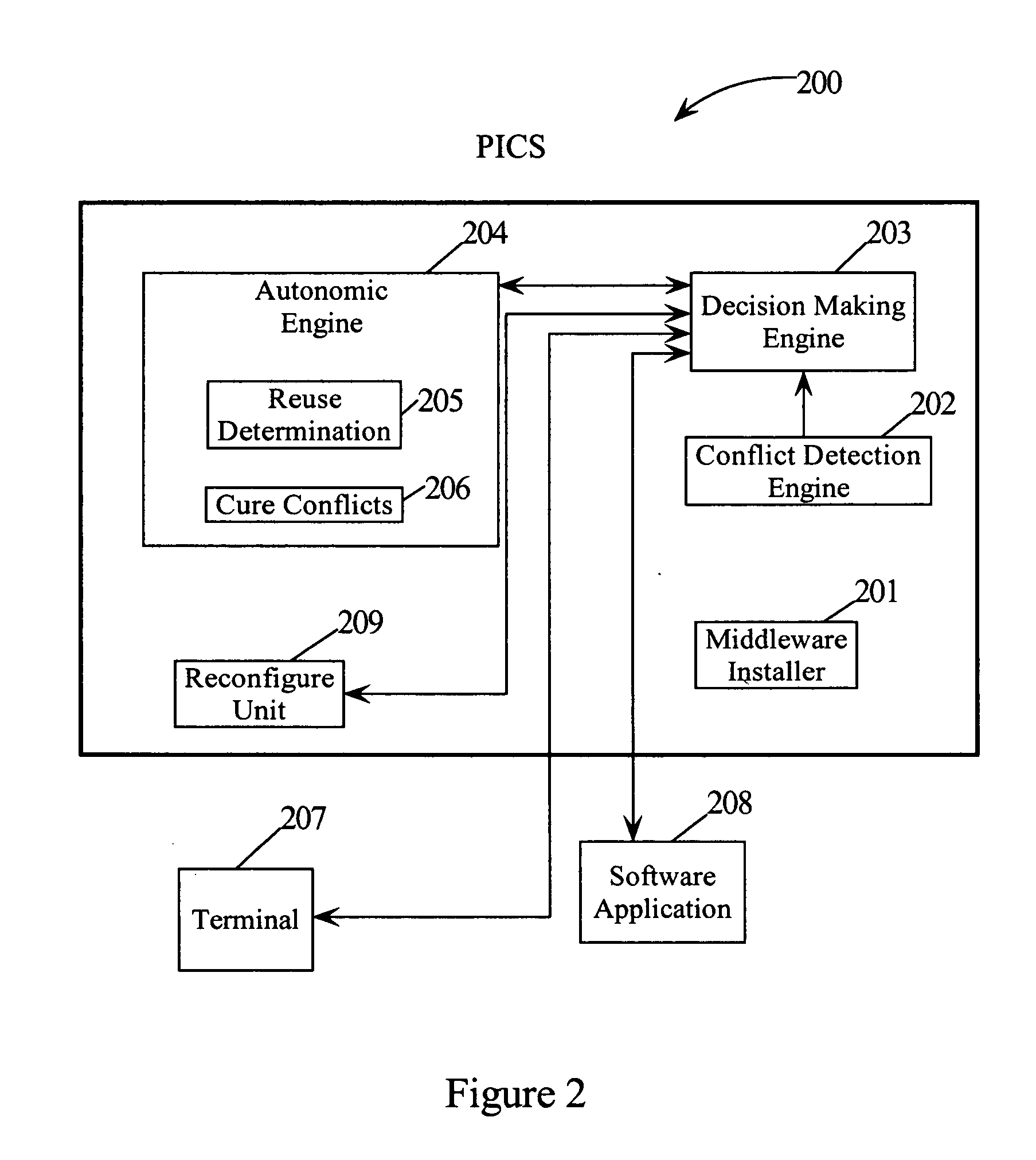
Allowing multiple decisions to be made by multiple decision makers during software installation
A method, computer program product and system for allowing multiple decisions to be made by multiple decision makers during software installation. A developer of an installer program may select the decisions to be made during the installation process. The developer may further designate the decision makers to handle each of these decisions in a configuration file. The configuration file may be compiled into executable code where the executable code may be embedded in the installer program. By the developer designating multiple decision makers to handle multiple decisions, multiple decision makers may now be able to be involved during the software installation process.
Owner:IBM CORP
System and methods for providing a declarative syntax for specifying SOAP-based web services
InactiveUS7055143B2Minimizes code amountSimplify creationSoftware designTransmissionWeb serviceSyntax
Owner:MICROSOFT TECH LICENSING LLC
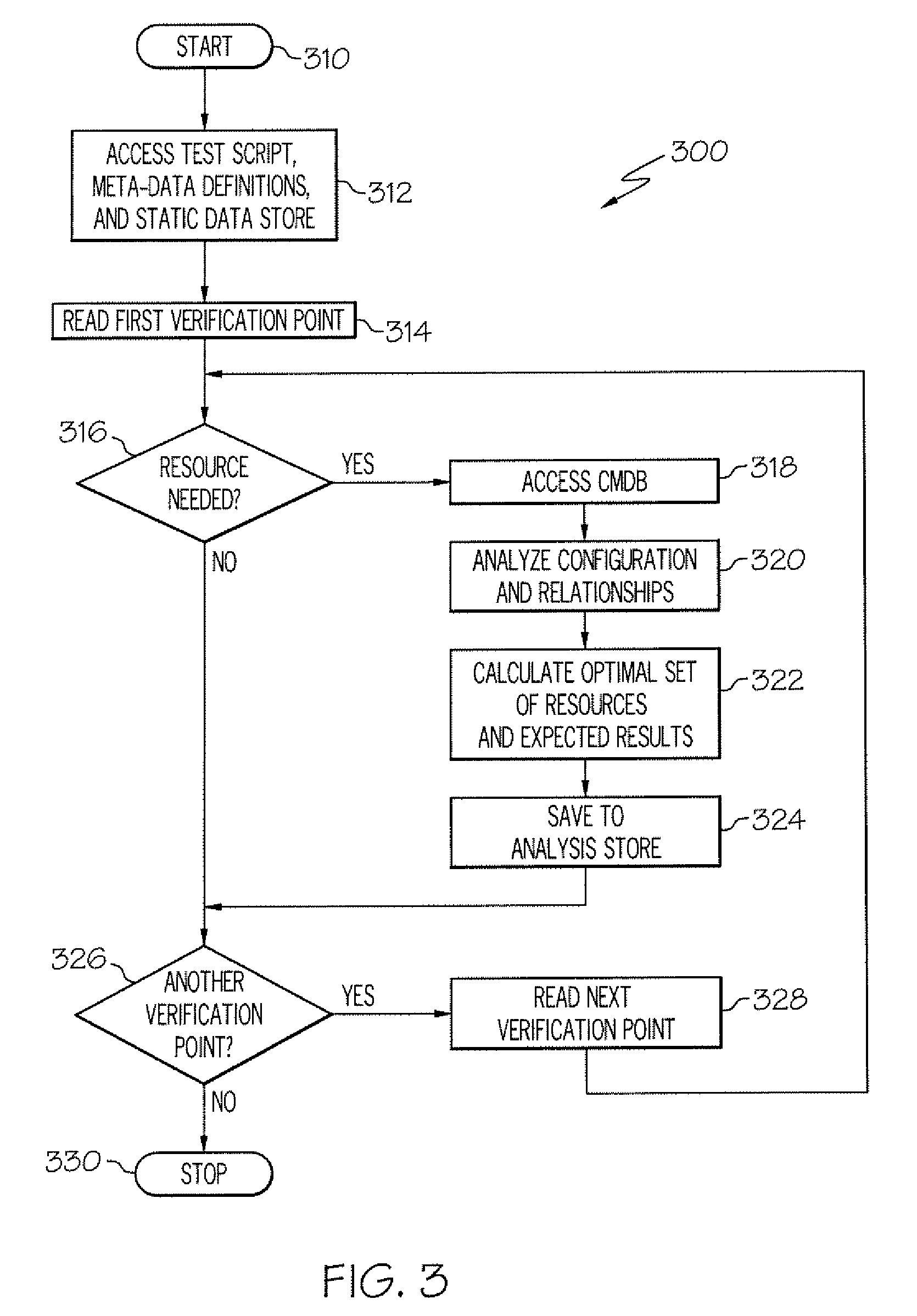
Method and Apparatus for Completing Functional Testing
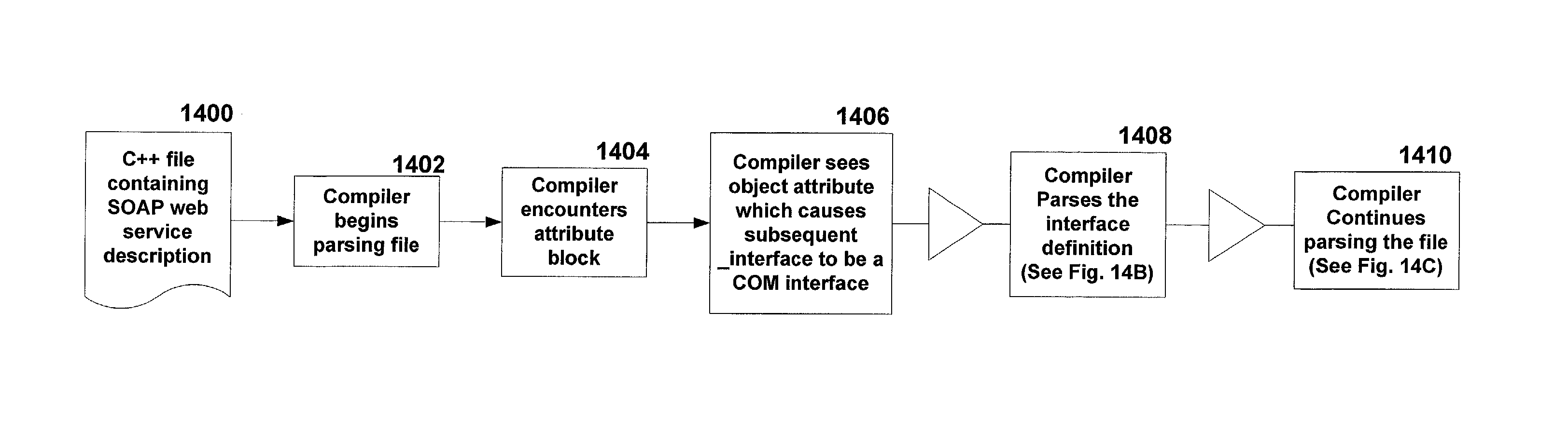
InactiveUS20080276224A1Promote resultsError detection/correctionSoftware maintainance/managementFunctional testingTest script
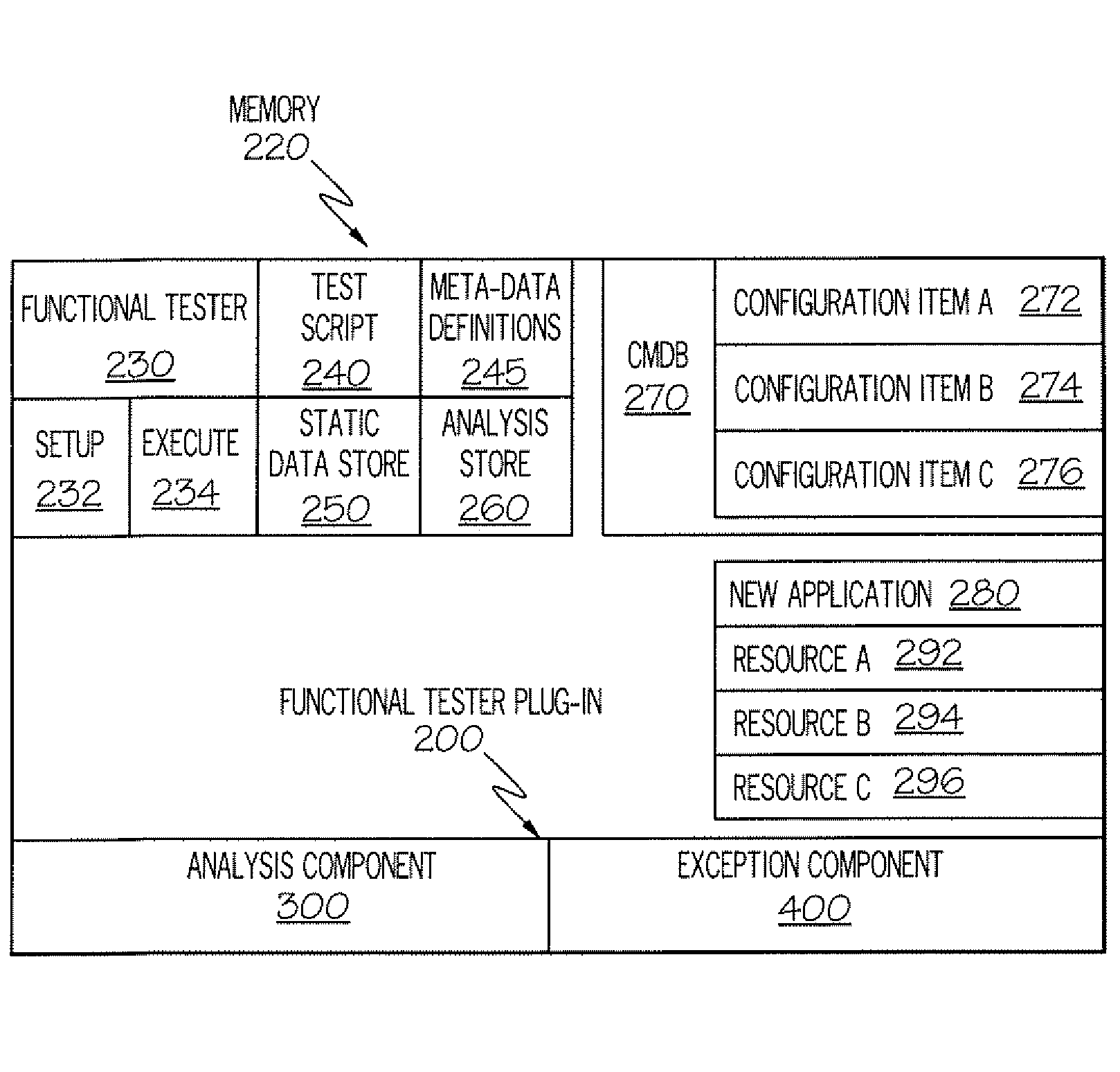
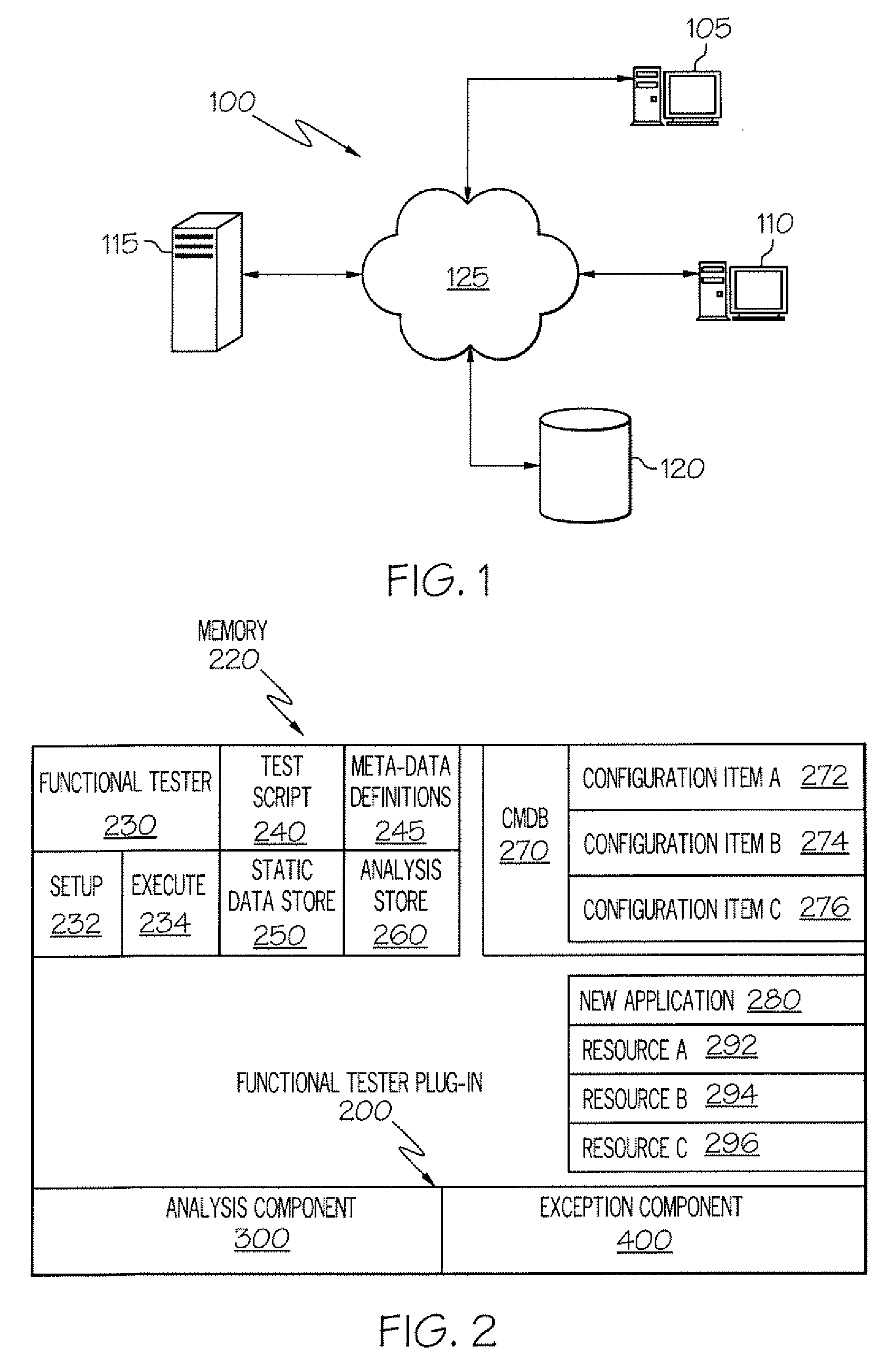
The Functional Tester Plug-in (FTP) extracts information from a data base to enhance automated testing tools to accommodate changes to the computer environment and so that a simulation can be fully executed even if an exception occurs. The FTP accesses the test script and static data store created by a developer using the automated testing tool, wherein the test script and static data store indicate a first resource to be tested at a verification point and a first expected result. The FTP identifies the first resource used by the test script at a first verification point and accesses the data base. The FTP identifies the status and configuration of the first resource in the data base. The FTP calculates and optimal expected result based any changes in the status and configuration of the first resource. The FTP executes the test script using the optimal expected result based any changes in the status and configuration of the first resource.
Owner:IBM CORP
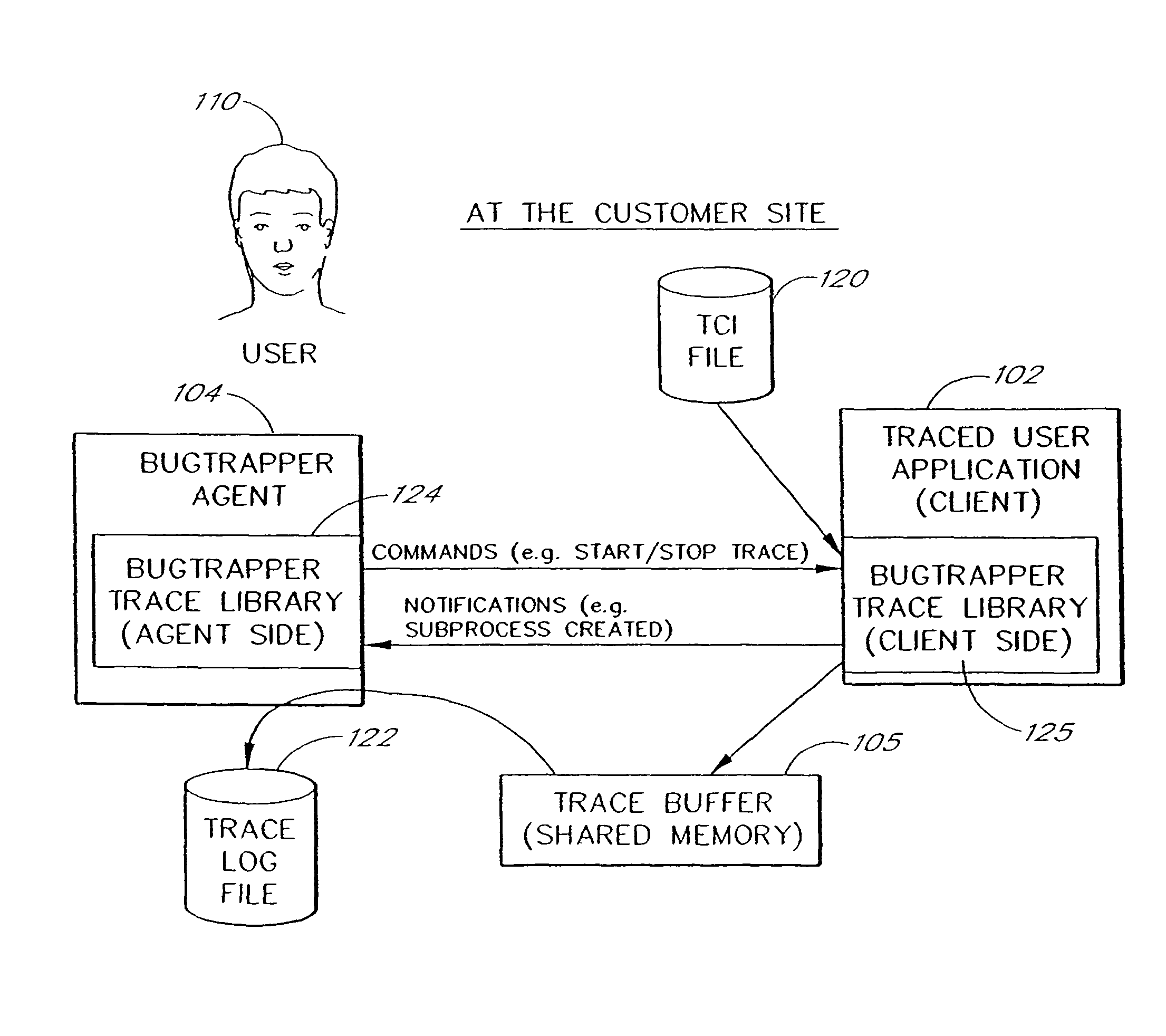
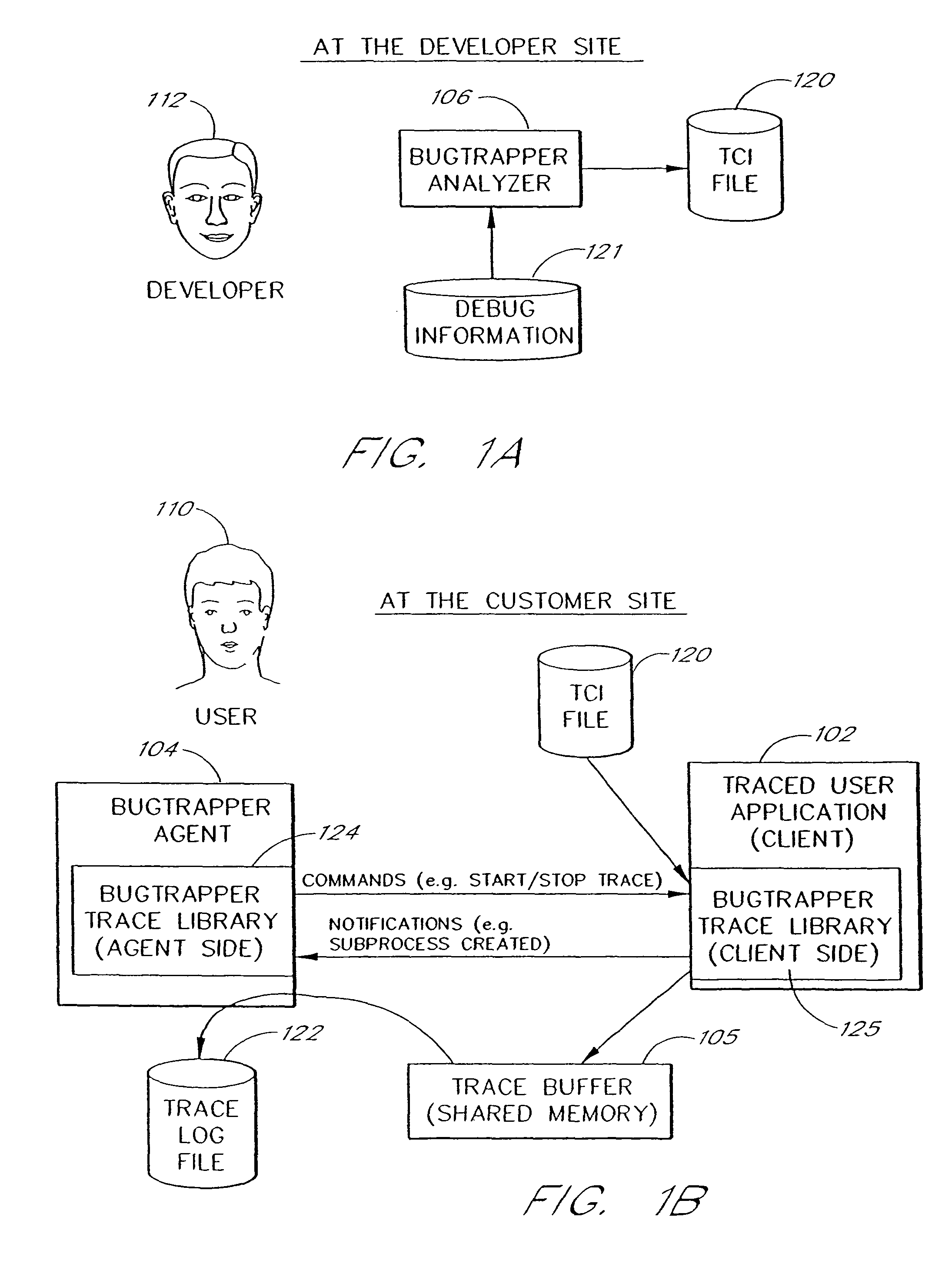
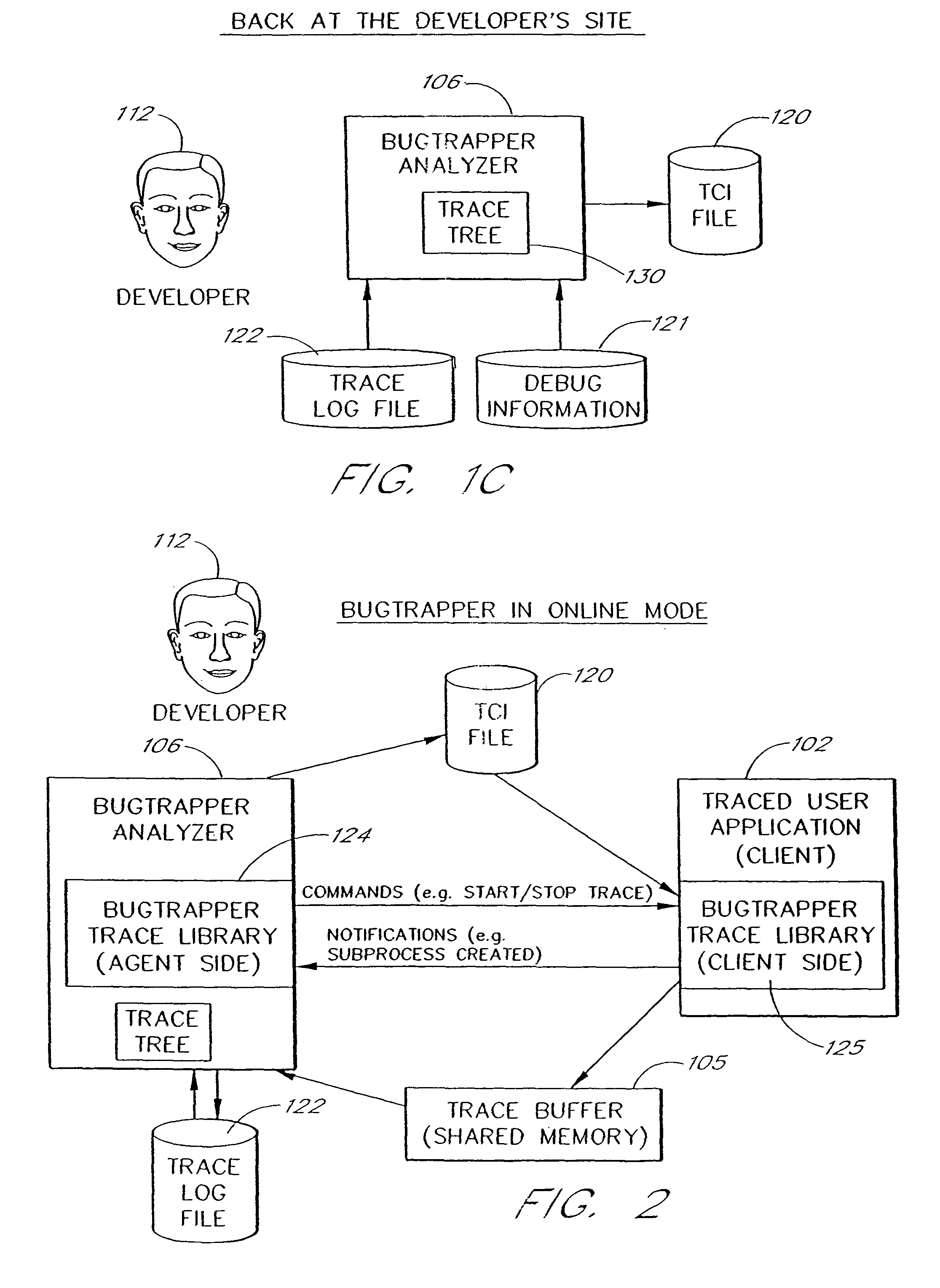
System and method for conditional tracing of computer programs
ActiveUS8312435B2Easy to identifyImprove isolationError detection/correctionSpecific program execution arrangementsSource code fileSoftware system
A software system is disclosed which facilitates the process of tracing the execution paths of a program, called the client. The tracing is performed without requiring modifications to the executable or source code files of the client. Trace data collected during the tracing operation is collected according to instructions in a trace options file. At run time, the tracing library attaches to the memory image of the client. The tracing library is configured to monitor execution of the client and to collect trace data, based on selections in the trace options file. Conditional tracing, through the use of triggers and actions taken in response to the triggers, allows the developer to control the tracing operation. The triggers can be conditional triggers in which the corresponding action is taken only if a conditional expression is satisfied. The system can trace multiple threads and multiple processes. The tracing system provides a remote mode and an online mode. In remote mode, the developer sends the trace control information (which can include triggers and corresponding actions) to a remote user site together with a small executable image called the agent that enables a remote customer, to generate a trace file that represents execution of the client application at the remote site. In online mode, the developer can generate trace options (including triggers and corresponding actions), run and trace the client, and display the trace results in near real-time on the display screen during execution of the client program.
Owner:BMC SOFTWARE ISRAEL LTD
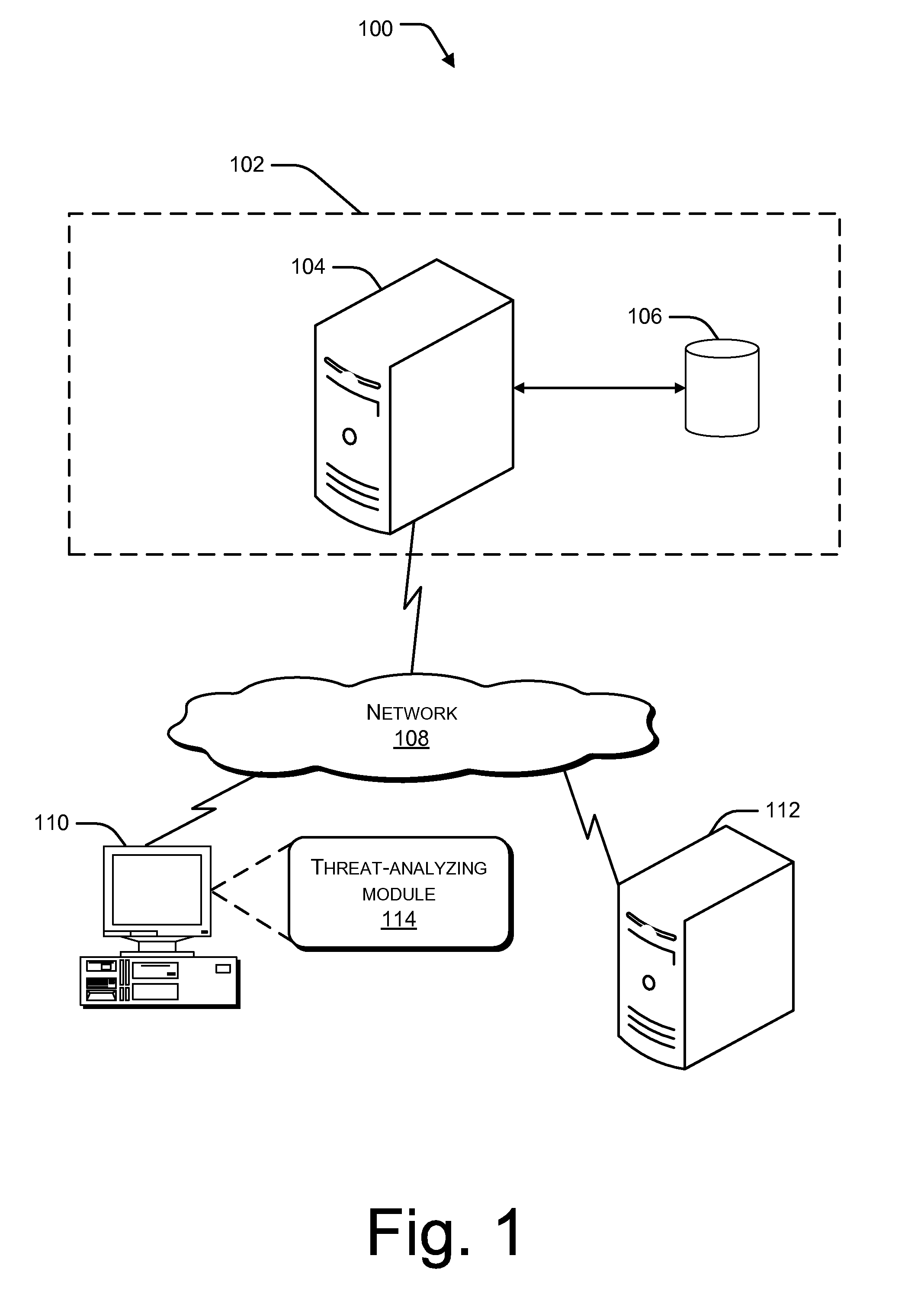
Threat analysis and modeling during a software development lifecycle of a software application
Systems and methods relating to a method for generating a threat analysis and modeling tool are described. In an implementation, aggregate analysis is performed upon applications of an enterprise for complete risk management of the enterprise. The threat analysis model is generated by defining the application, its attributes and the rules related to the application. An application task list is generated from a common task list for the application. Countermeasures for known attacks pertaining to the application are described in the application task list, which allows the developer to reduce the risk of attacks.
Owner:MICROSOFT TECH LICENSING LLC
Run-time instrumentation for object oriented programmed applications
InactiveUS6126330AEasy to changeHardware monitoringSoftware testing/debuggingSoftware engineeringSoftware development
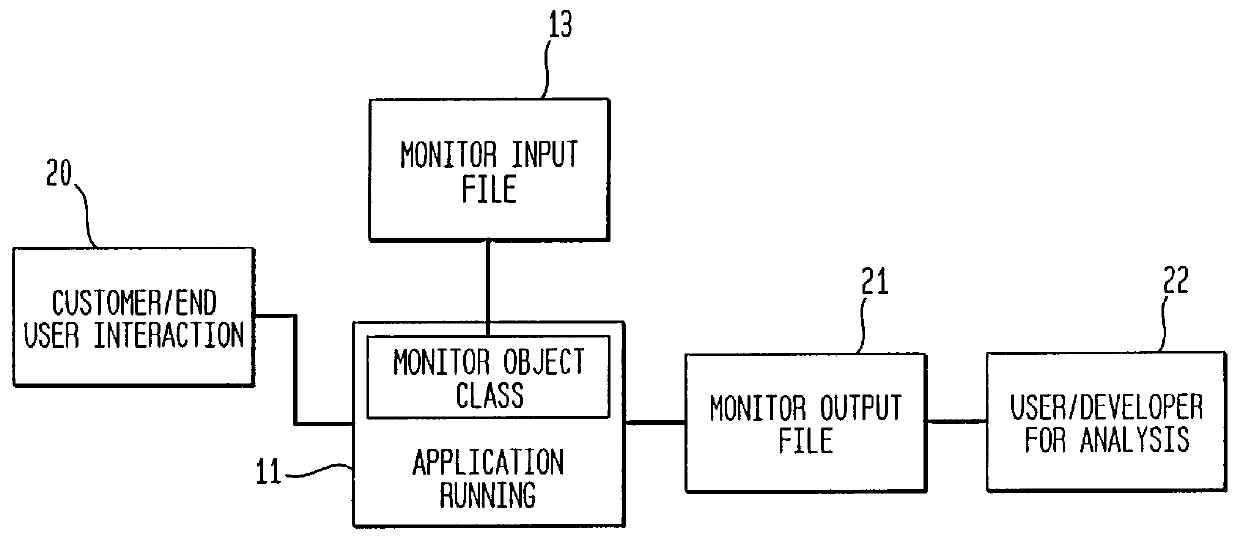
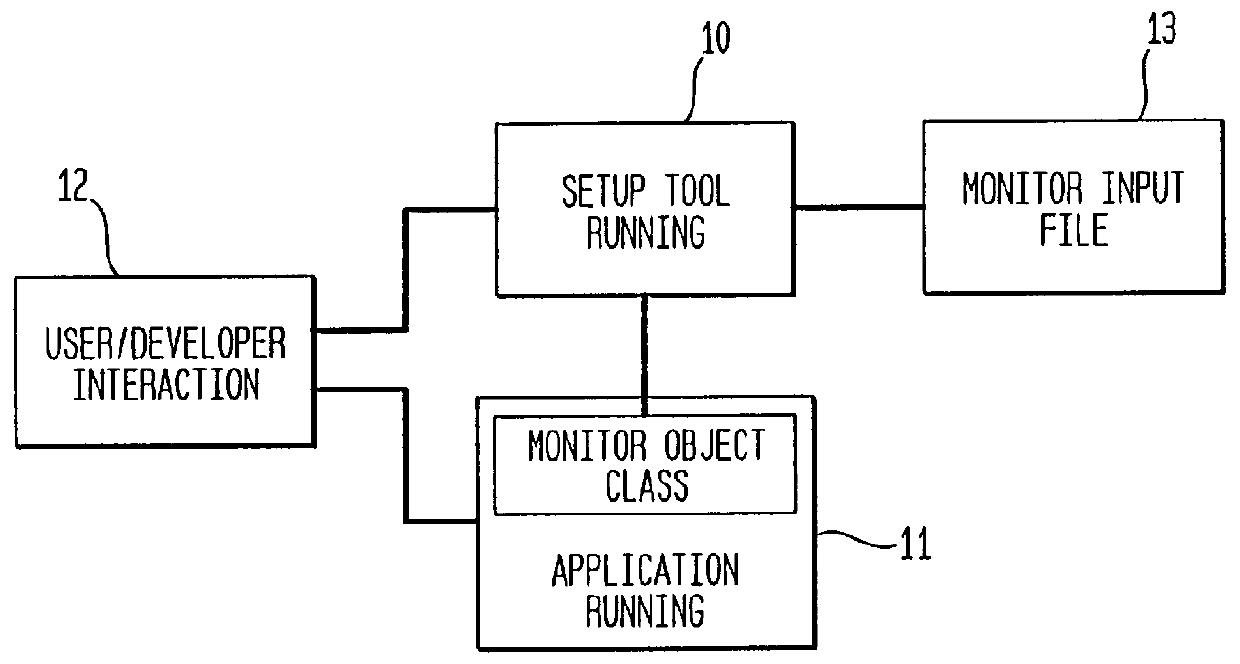
It is desirable for software developers to be able to conveniently obtain feedback from users of applications. It is known for developers and others to use code instrumentation for gathering various types of data relating to applications and their uses. The use of compile time instrumentation may be practical for some situations but it has significant drawbacks when used to provide indications of user interaction with applications. The present invention relates to the use of run time instrumentation for providing feedback from users of object oriented applications where the applications have unique object identifiers and support dynamic data exchange. The invention utilizes a setup software tool to create a monitor input file which indicates which objects of the application should be monitored when a user interacts with them.
Owner:IBM CORP
Systems and methods for software development
InactiveUS7778866B2Without sacrificing qualityQuality improvementDiscounts/incentivesHardware monitoringDesign reviewDesign software
Owner:TOPCODER
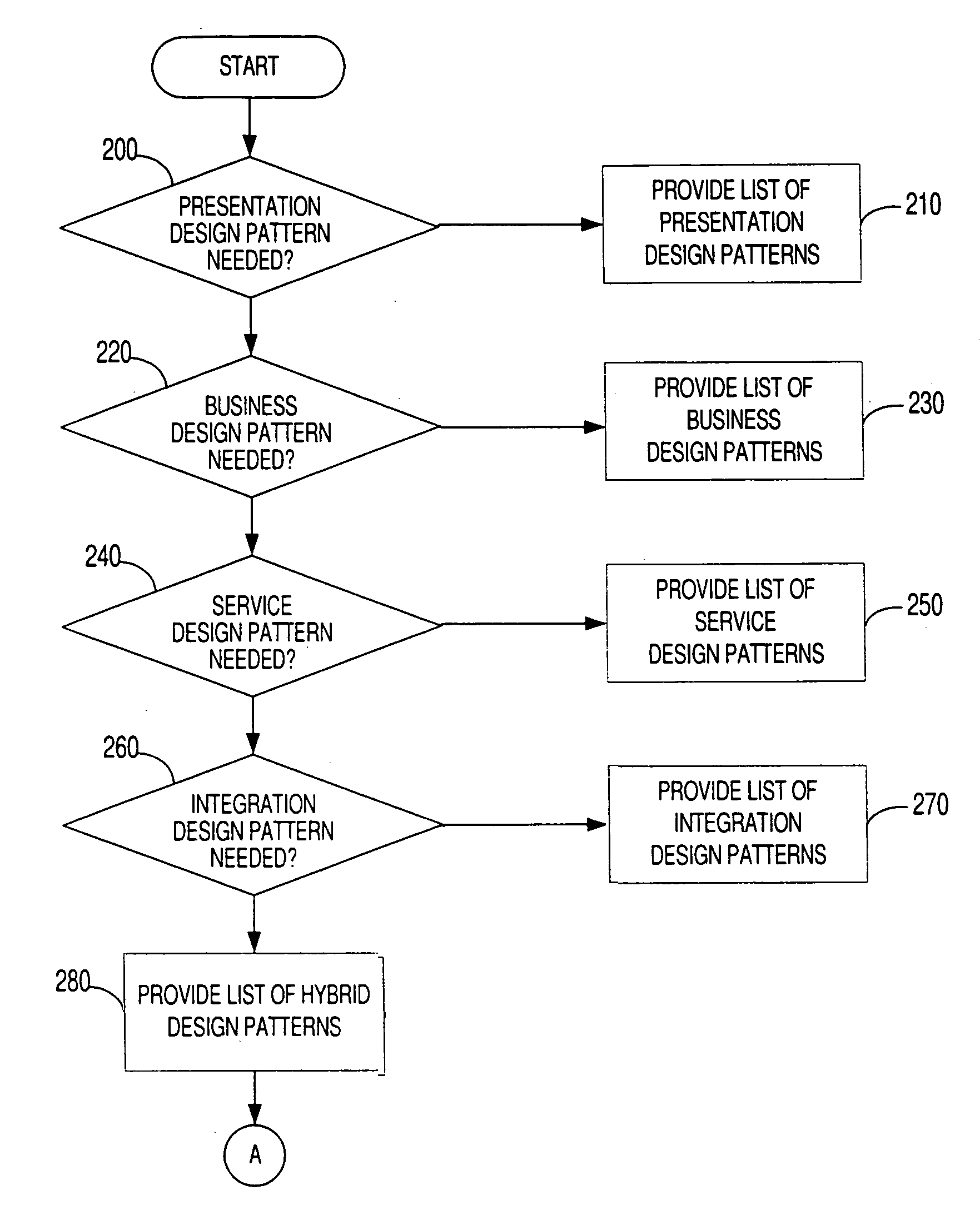
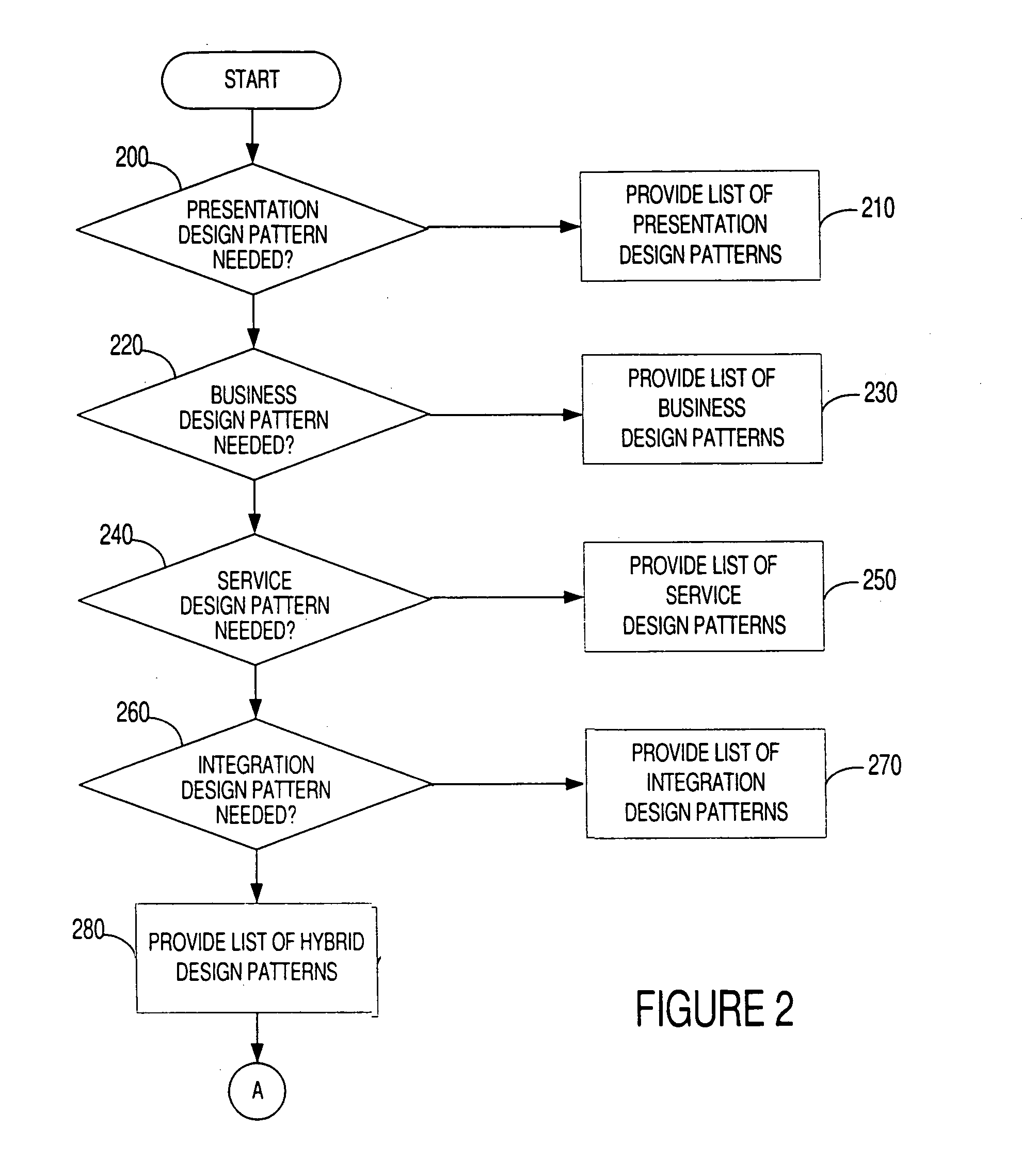
Method and apparatus for developing enterprise applications using design patterns
InactiveUS6993743B2Reducing “ chattiness ”Reduced remote callSoftware designSpecific program execution arrangementsSoftware developmentGood practice
The present invention provides a method and apparatus for developing enterprise applications using design patterns. Over time, different types of enterprise applications have been developed and implemented by various software developers for different purposes. The present invention determines the purpose of the software that is needed by the developer and obtains a design pattern to solve the problem that is in accord with the best practices and patterns derived from these implementations. In turn a developer can rely on the present invention as a tool to develop and implement applications in a three-tier or multi-tier computer architecture.
Owner:ORACLE INT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com