User identity authentication method suitable for transparent computing system and system configuration method
A user identity authentication and transparent computing technology, which is applied in the configuration field of transparent computing systems, can solve problems such as inability to identify user identities in real time, user data leakage, etc., and achieve the effects of improving user experience, expanding the scope of application, and facilitating investigation and positioning
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
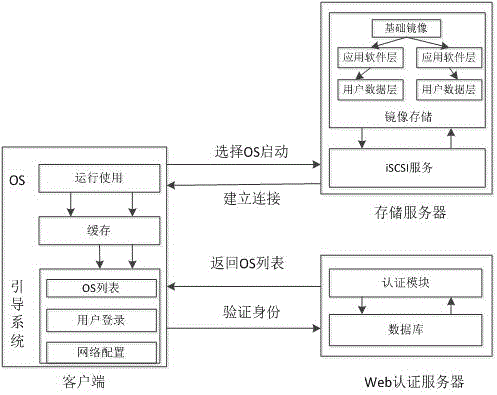
[0039] figure 1 Shows the overall structural block diagram of the transparent computing system of this embodiment, the client hardware platform is a mobile tablet with x86 architecture, and its hard disk is pre-burned with a network boot program NBP (a network boot program written according to an open source project); the server side includes Two parts: the authentication server responsible for user rights information management (that is, the Web authentication server) and the storage server responsible for user operating system image storage. The storage server needs to be configured with iSCSI service and DHCP service, and the web authentication server needs to be configured with MySQL service and Tomcat service (see Example 3).
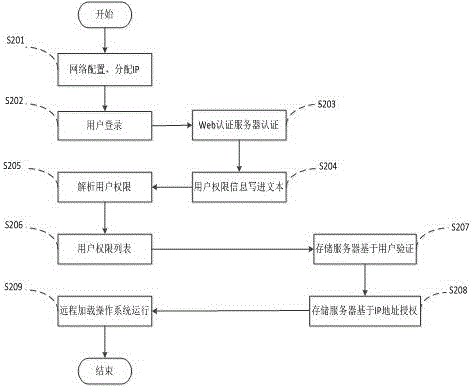
[0040] see figure 2 , the user identity authentication method applicable to the transparent computing system of this embodiment includes the following steps:
[0041] S201: The client is powered on and logged in, and first performs network confi...
Embodiment 2
[0052] see Figure 5 , the user identity authentication method applicable to the transparent computing system of this embodiment includes the following steps:
[0053] When the user boots up and logs in, the following authentication steps are performed:
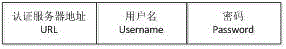
[0054] S1: The client sends a login request packet to the authentication server, the login request information (see image 3 ) including the authentication server address, username and password.
[0055] S2: The authentication server queries the background database, obtains the operating system permission list that the user can start, writes text information and sends it to the client, and the text information (see Figure 4 ) includes the user ID, OS number, OS name, and terminator.
[0056] S3: The user selects the operating system to be remotely loaded through the client, and initiates a remote loading request to the storage server. The loading request information includes the user name, password, storage server address...
Embodiment 3
[0062] see Figure 6 , using the system configuration method of the transparent computing system of the user identity authentication method of embodiment 1 or embodiment 2, comprising the following steps:
[0063] 1) Add network configuration and user authentication policy codes to the bootloader NBP source code, and recompile to generate the NBP bootloader;
[0064] 2) Erase the main boot partition MBR in BIOS mode on the client's hard disk, and burn the compiled NBP boot program to the original main boot partition MBR location;
[0065] 3) Configure the MySQL and Tomcat services of the authentication server, and deploy the identity authentication background program on the Tomcat of the Web authentication server;
[0066] 4) Configure the iSCSI service of the storage server, bind the user operating system image to the user name and password, modify the access rights of the operating system image, and set the IP address that can be accessed;
[0067] 5) Modify the configurat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com