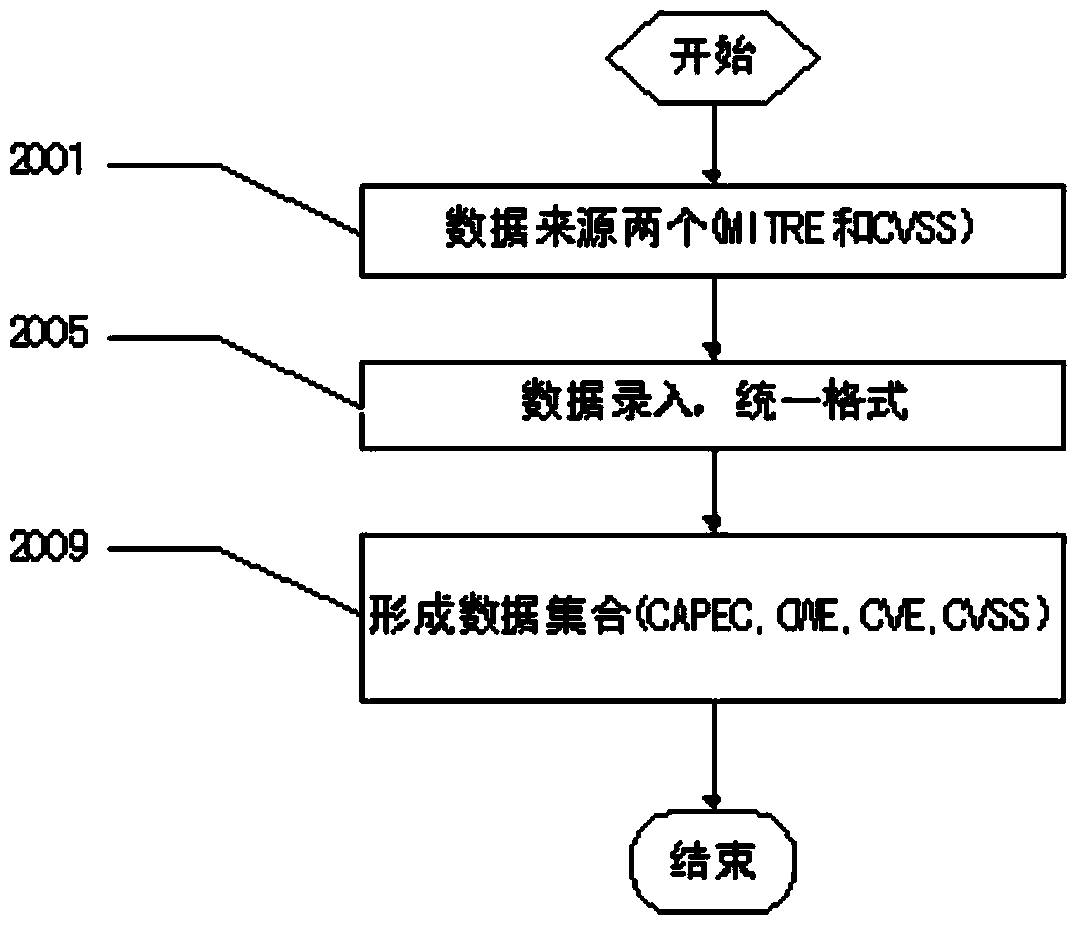
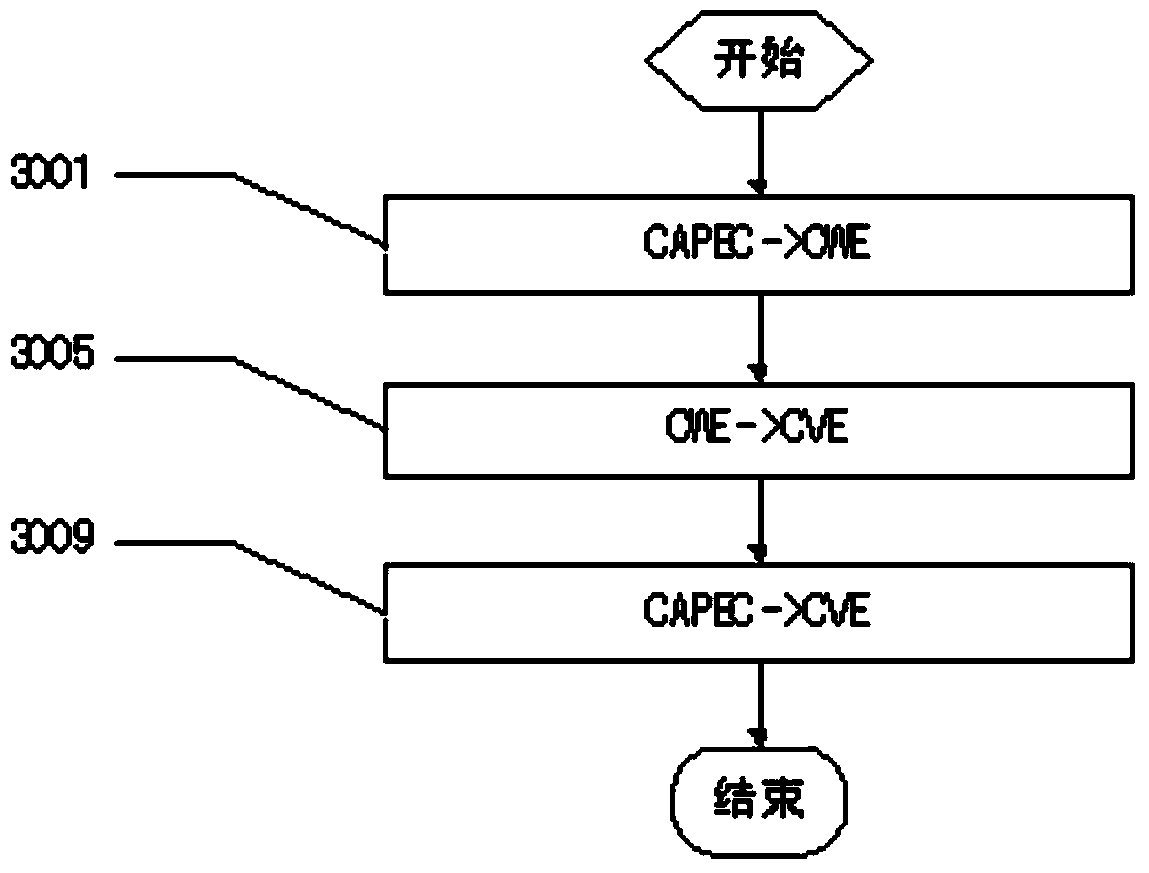
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
134 results about "Attack patterns" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer science, attack patterns are a group of rigorous methods for finding bugs or errors in code related to computer security. Attack patterns are often used for testing purposes and are very important for ensuring that potential vulnerabilities are prevented. The attack patterns themselves can be used to highlight areas which need to be considered for security hardening in a software application. They also provide, either physically or in reference, the common solution pattern for preventing the attack. Such a practice can be termed defensive coding patterns.
System and Method for Distributed Denial of Service Identification and Prevention
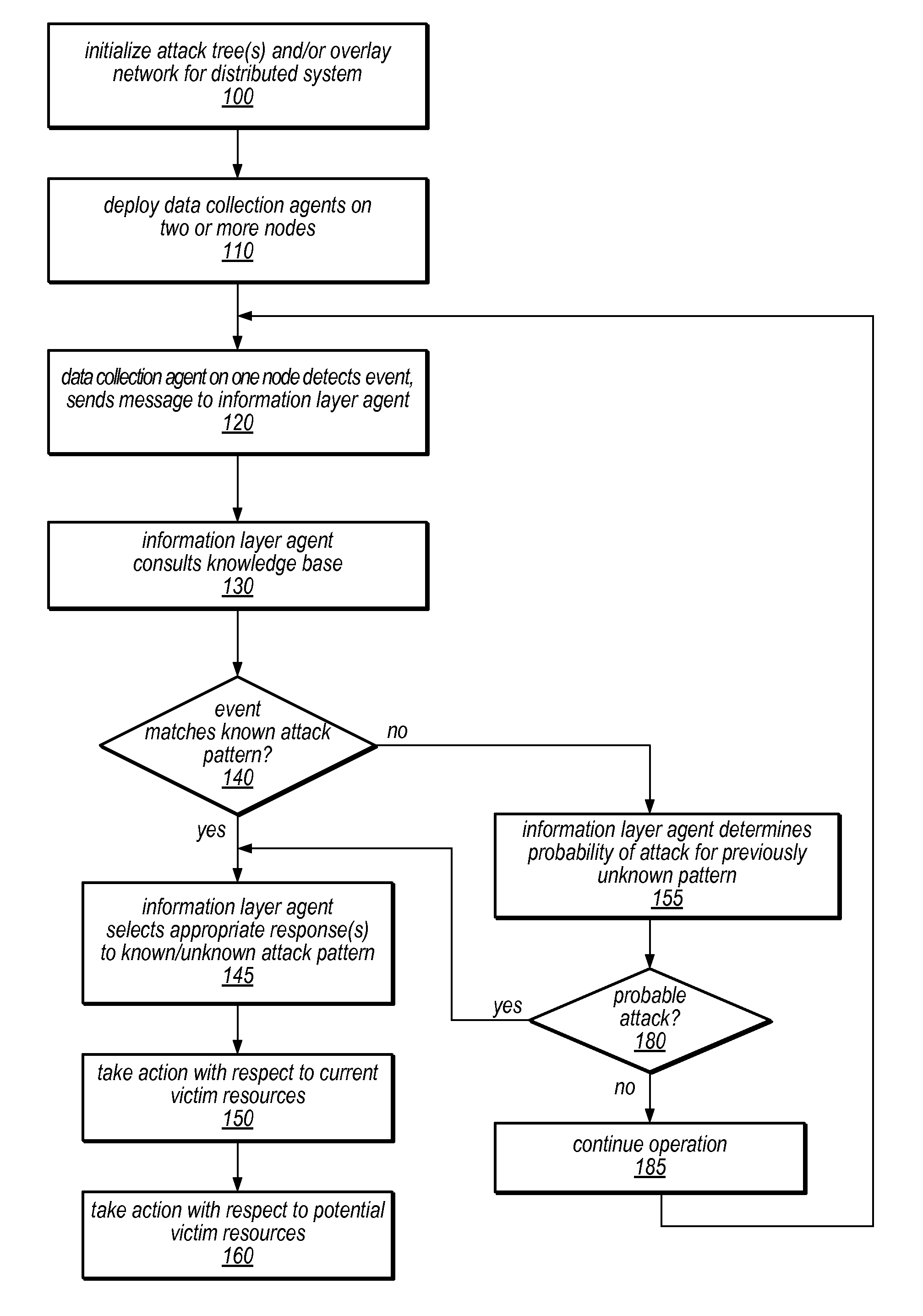
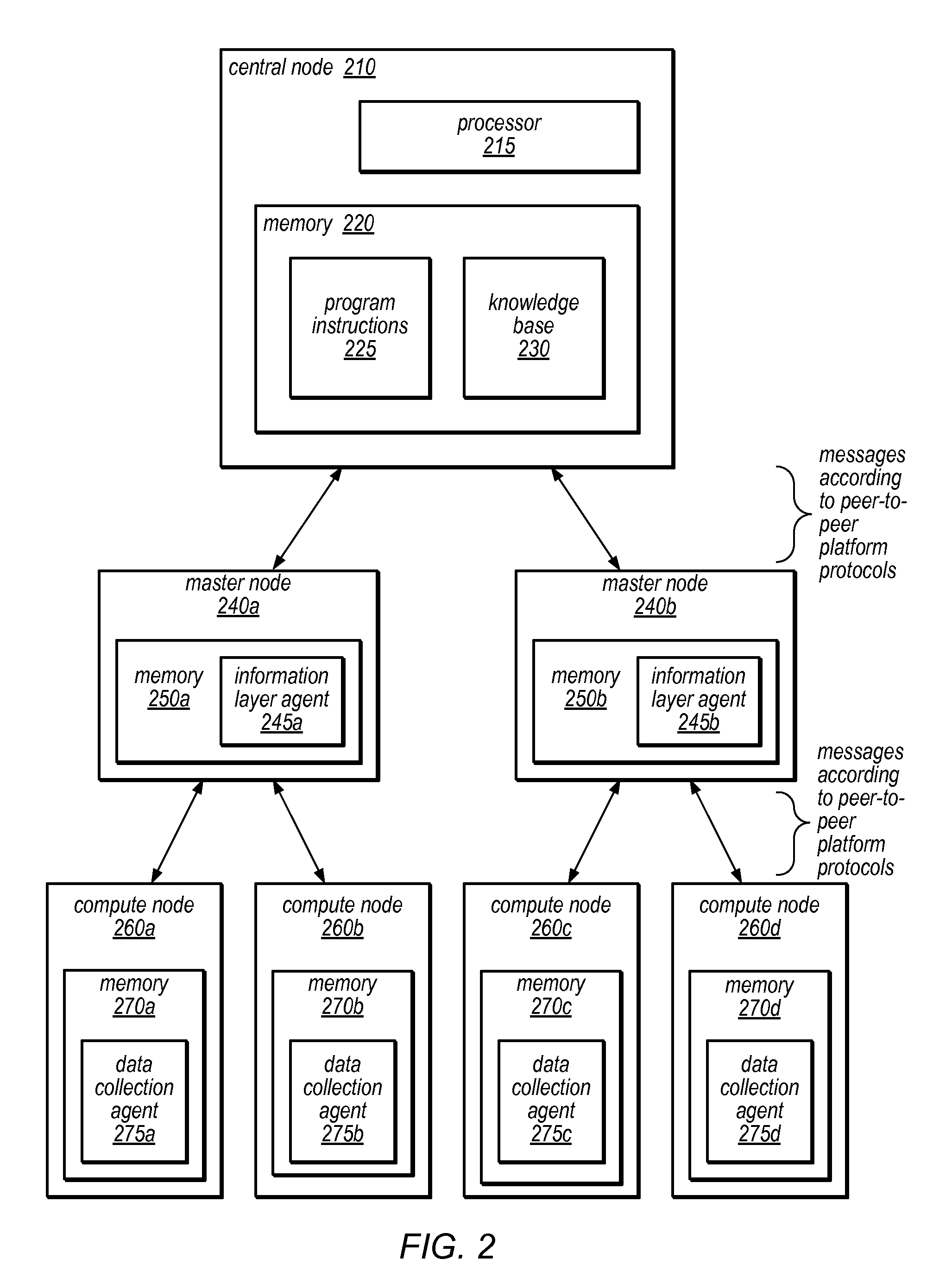
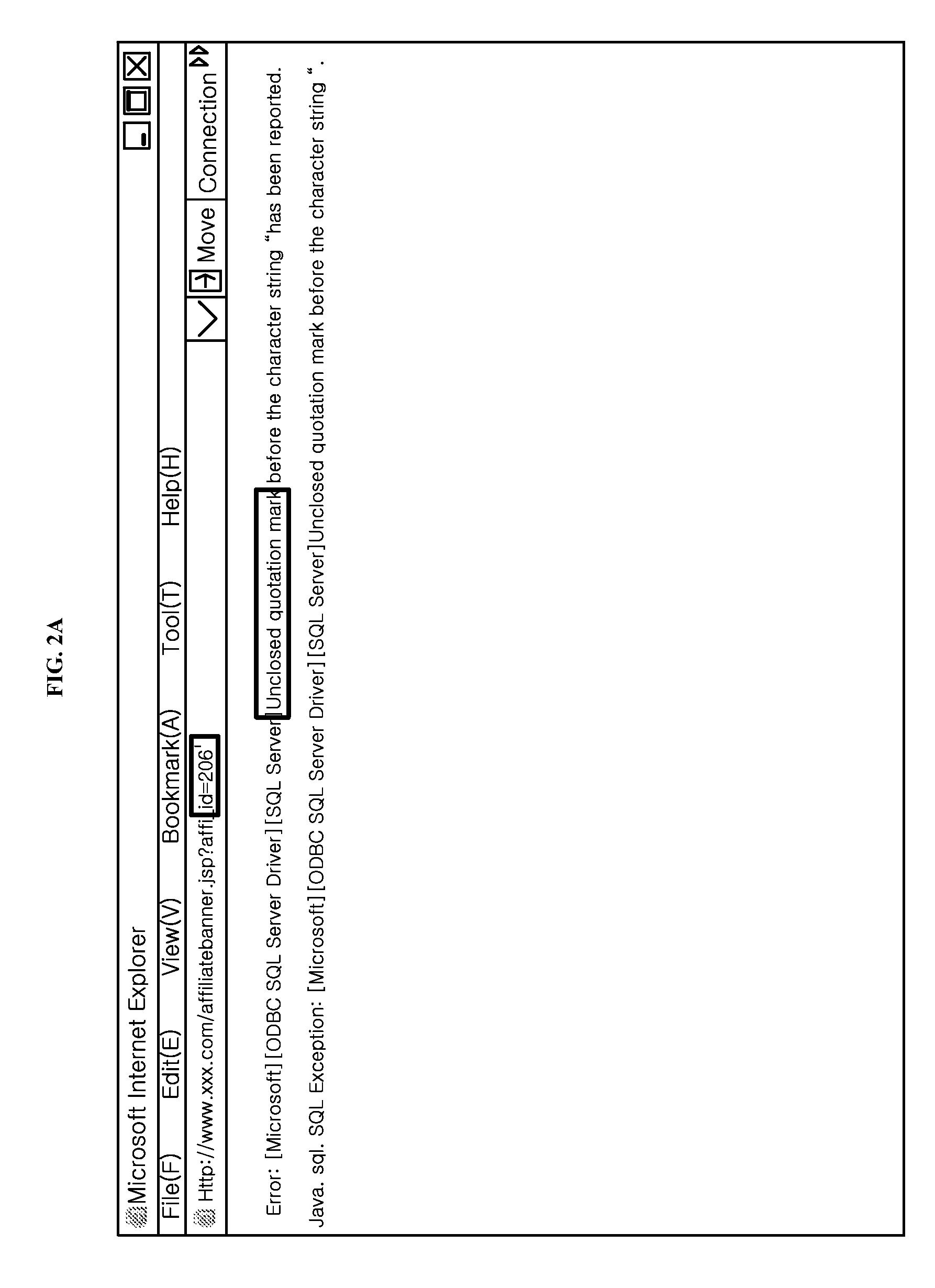
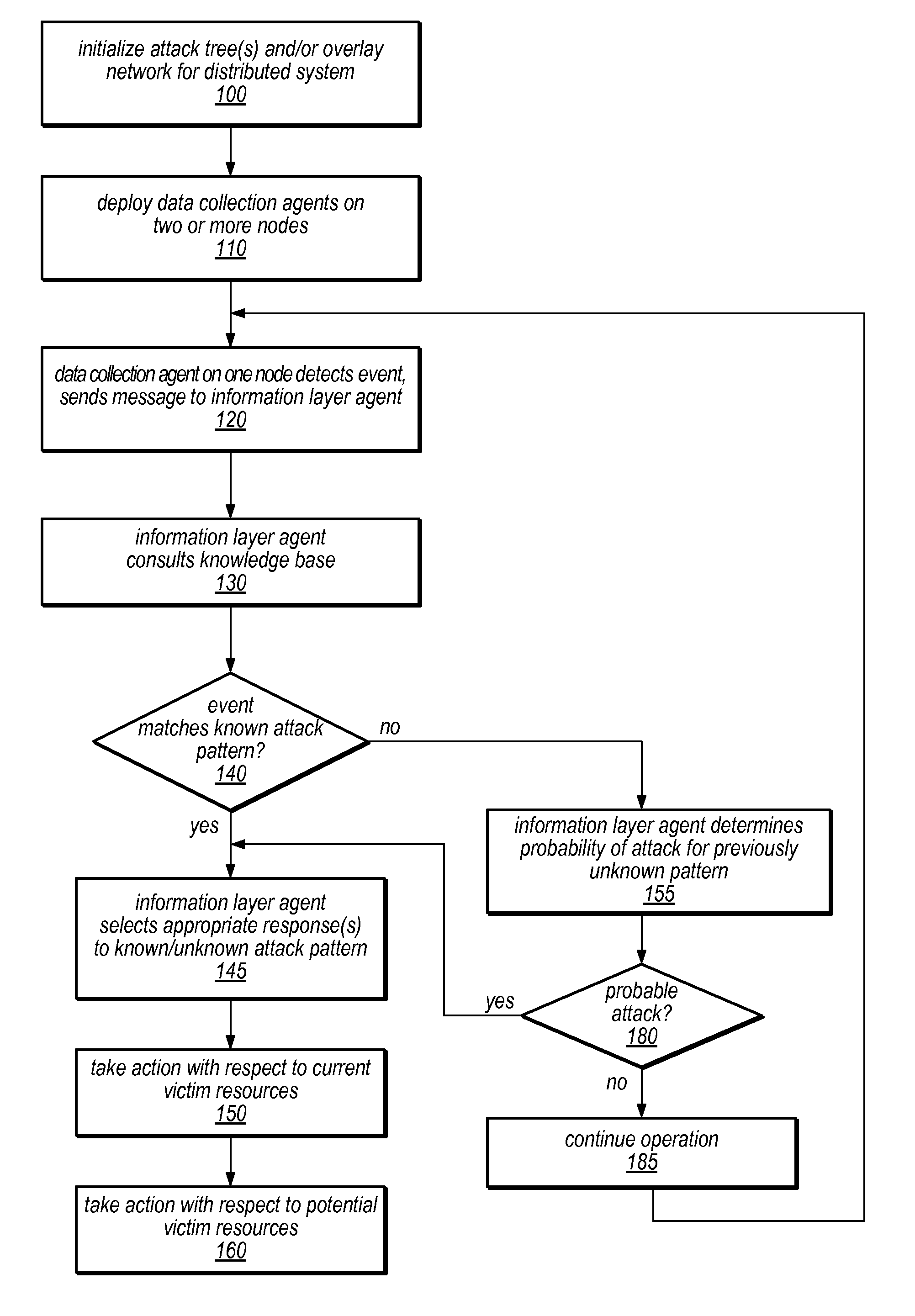
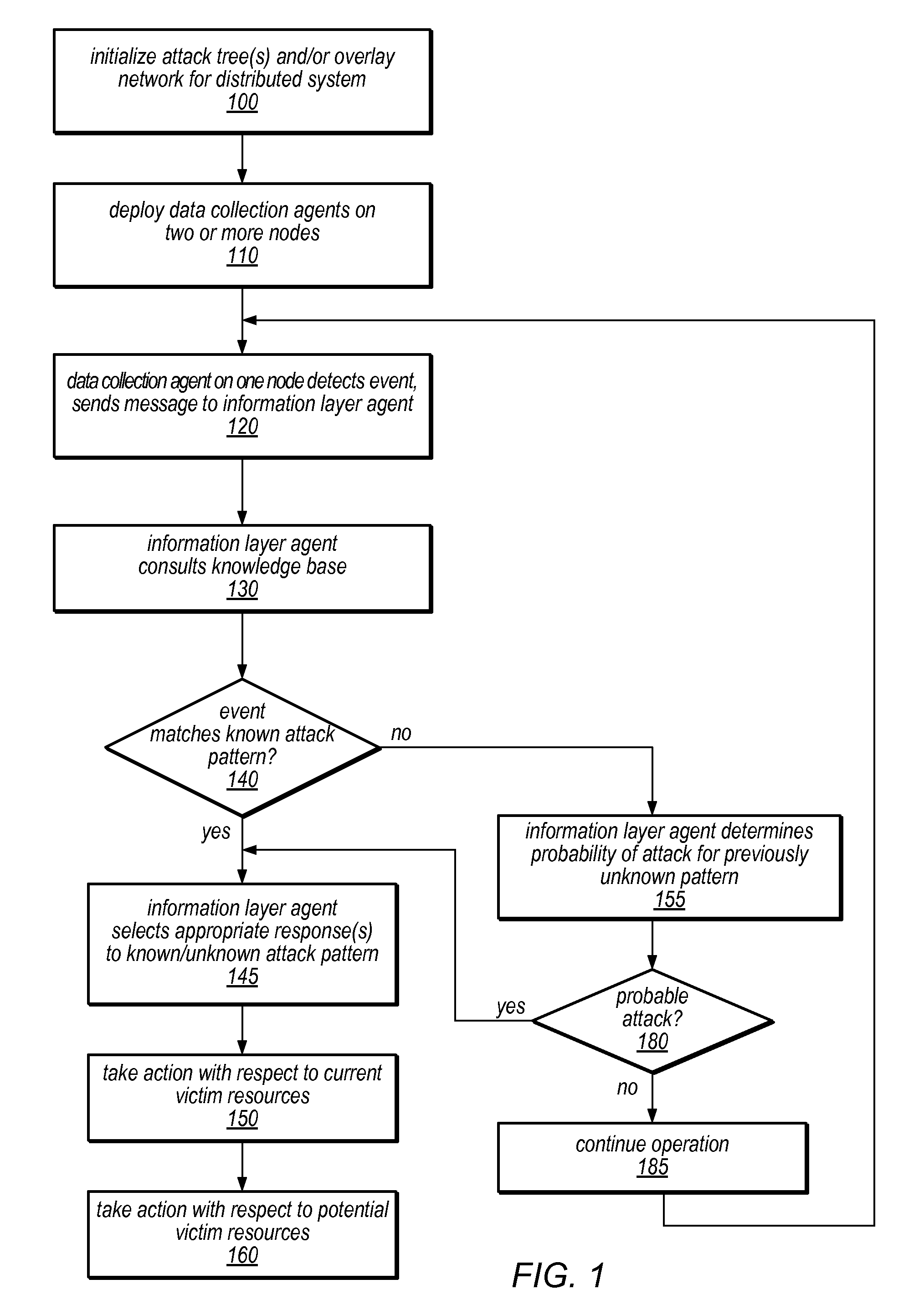
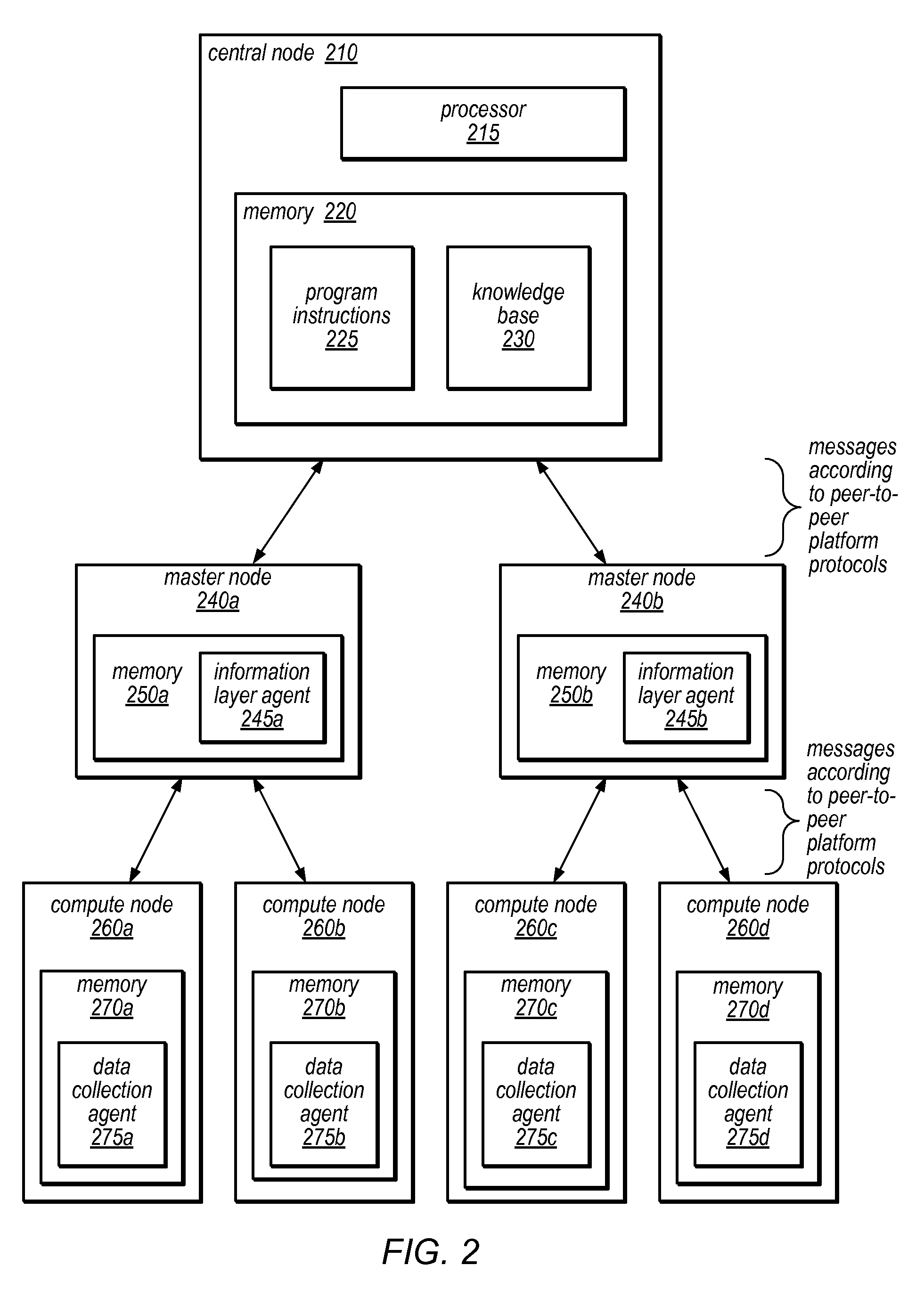
Systems and methods for discovery and classification of denial of service attacks in a distributed computing system may employ local agents on nodes thereof to detect resource-related events. An information later agent may determine if events indicate attacks, perform clustering analysis to determine if they represent known or unknown attack patterns, classify the attacks, and initiate appropriate responses to prevent and / or mitigate the attack, including sending warnings and / or modifying resource pool(s). The information layer agent may consult a knowledge base comprising information associated with known attack patterns, including state-action mappings. An attack tree model and an overlay network (over which detection and / or response messages may be sent) may be constructed for the distributed system. They may be dynamically modified in response to changes in system configuration, state, and / or workload. Reinforcement learning may be applied to the tuning of attack detection and classification techniques and to the identification of appropriate responses.
Owner:ORACLE INT CORP
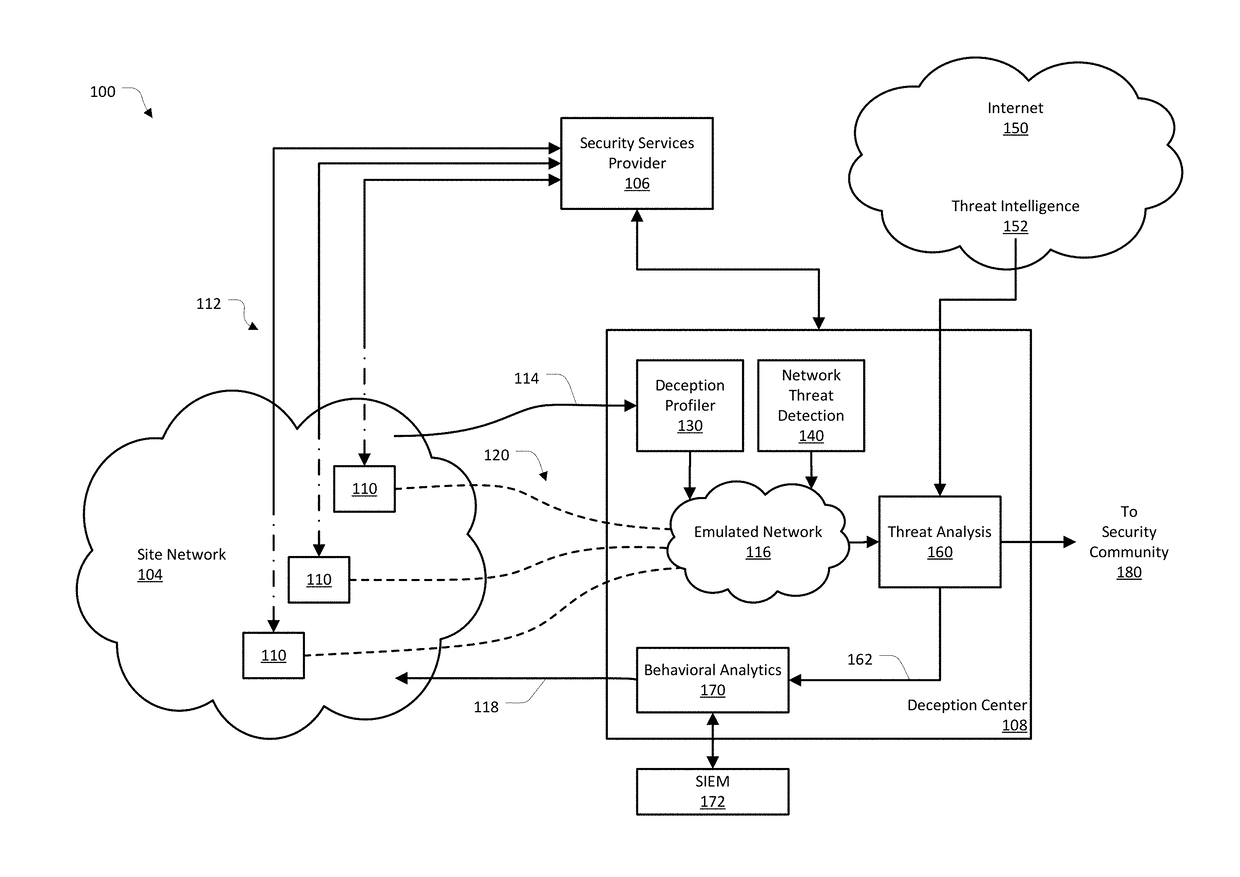
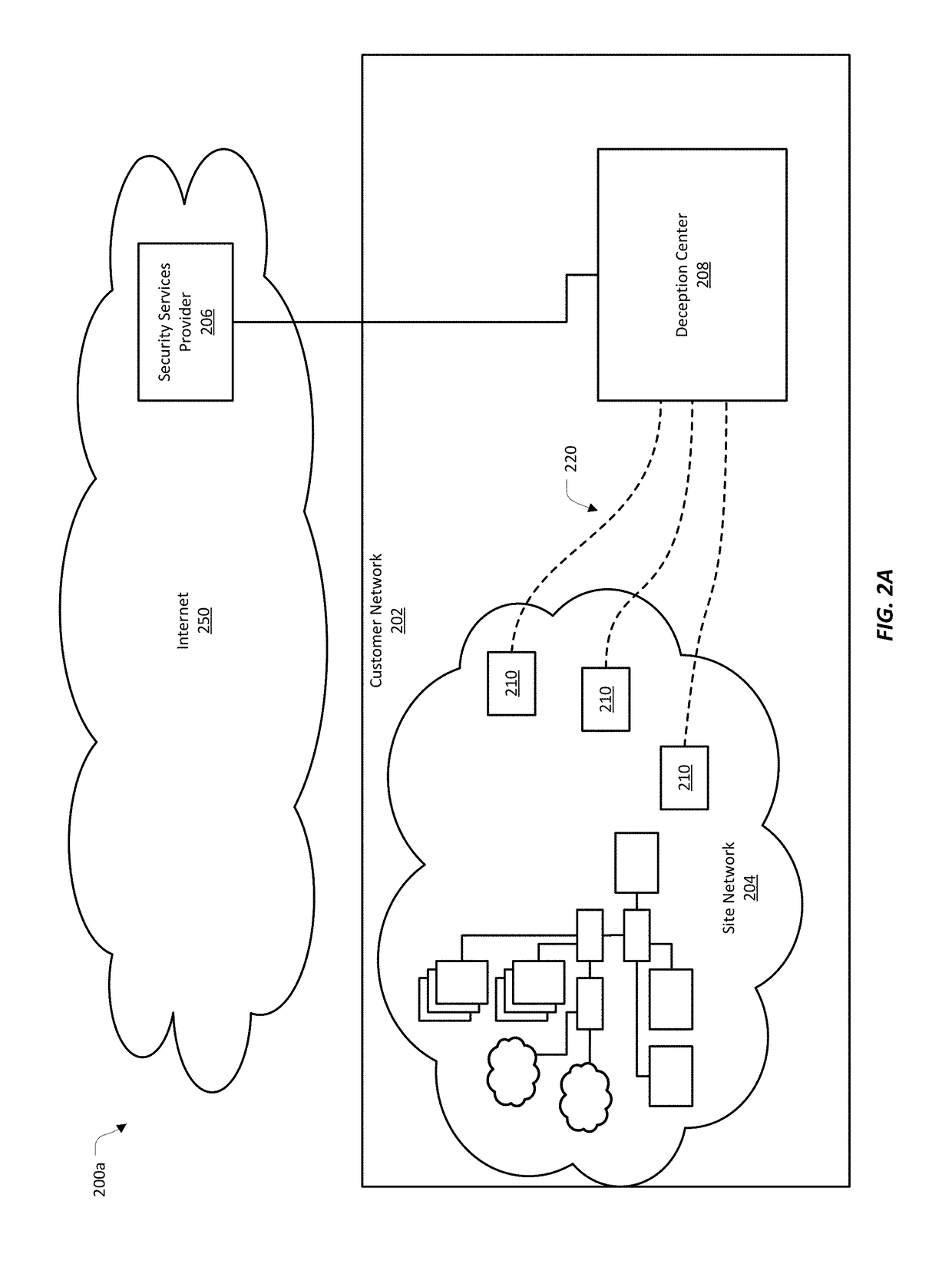
Detecting security threats by combining deception mechanisms and data science
Provided are systems, methods, and computer-program products for a network device, configured to use data science techniques to manage the deployment of deception mechanisms in a network, where the deception mechanisms can attract and detect threats to the network. In various implementations, the network device can receive network data. The network data can include data produced by an interaction with a deception mechanism. The deception mechanism can be part of the security of the network. An interaction can include a potential threat to the network. The network device can further be configured to analyze the network data using a data science engine, including identifying a pattern of network behavior. The network device can further generate an attack pattern that includes the behavior of the potential threat. The network device can further use the attack pattern to modify deception mechanisms on the network.
Owner:ACALVIO TECH
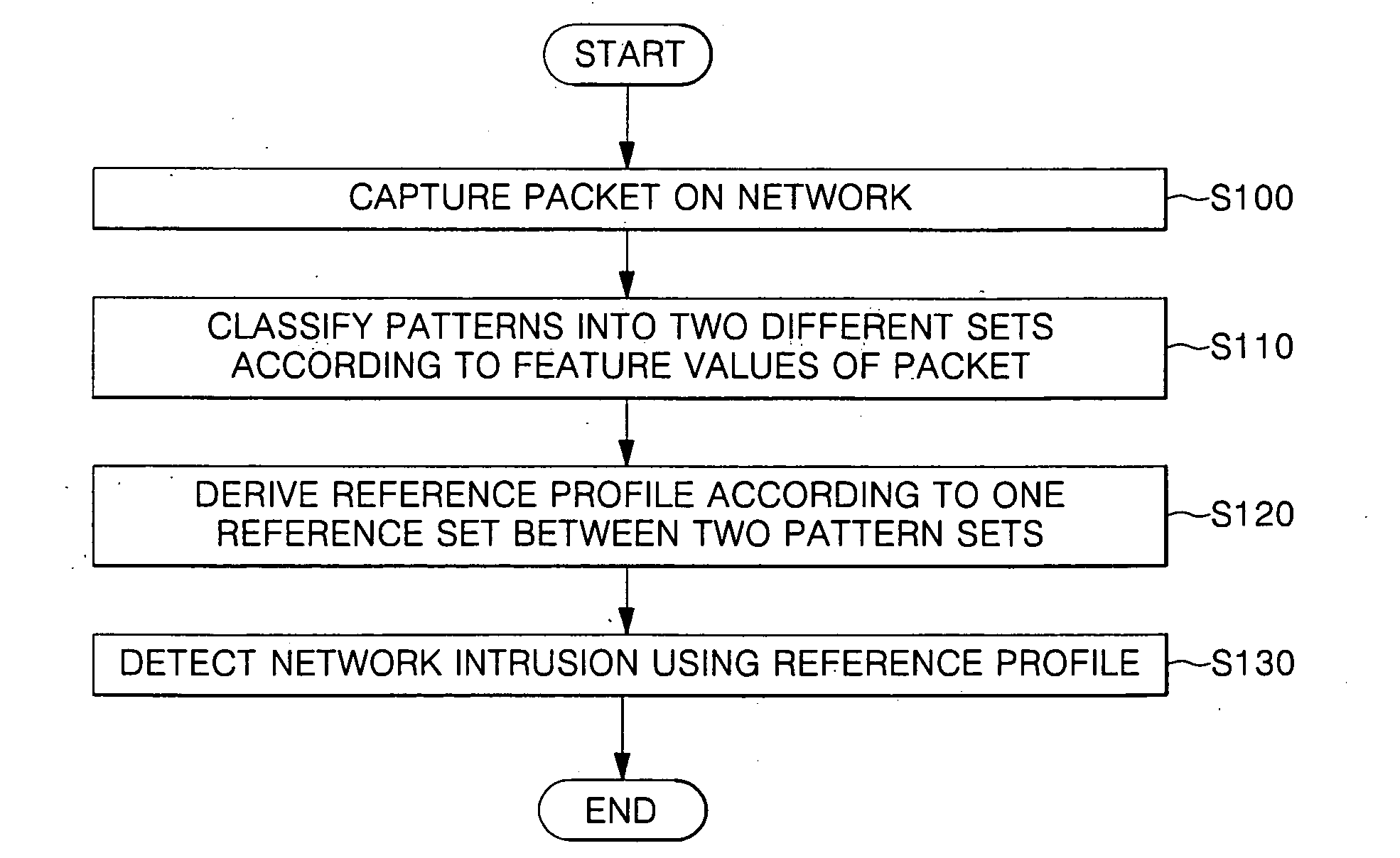
System and method for detecting network intrusion
InactiveUS20070150954A1Efficient detectionMemory loss protectionData taking preventionReal-time computingAttack patterns
In a system and method for detecting network intrusion, the system comprises: a packet capturer which captures at least one packet on a network; a preprocessor which provides feature values dependent on features of each packet captured by the packet capturer; and a learning engine for classifying patterns dependent on the feature values provided by the preprocessor into two different pattern sets, and for selecting one pattern set having more elements from the pattern sets as a reference set so as to detect network intrusion. The network intrusion detection system and method do not depend on historical data according to known attack patterns, and thus not only detect a changed attack pattern but also efficiently detect network intrusion.
Owner:SAMSUNG ELECTRONICS CO LTD
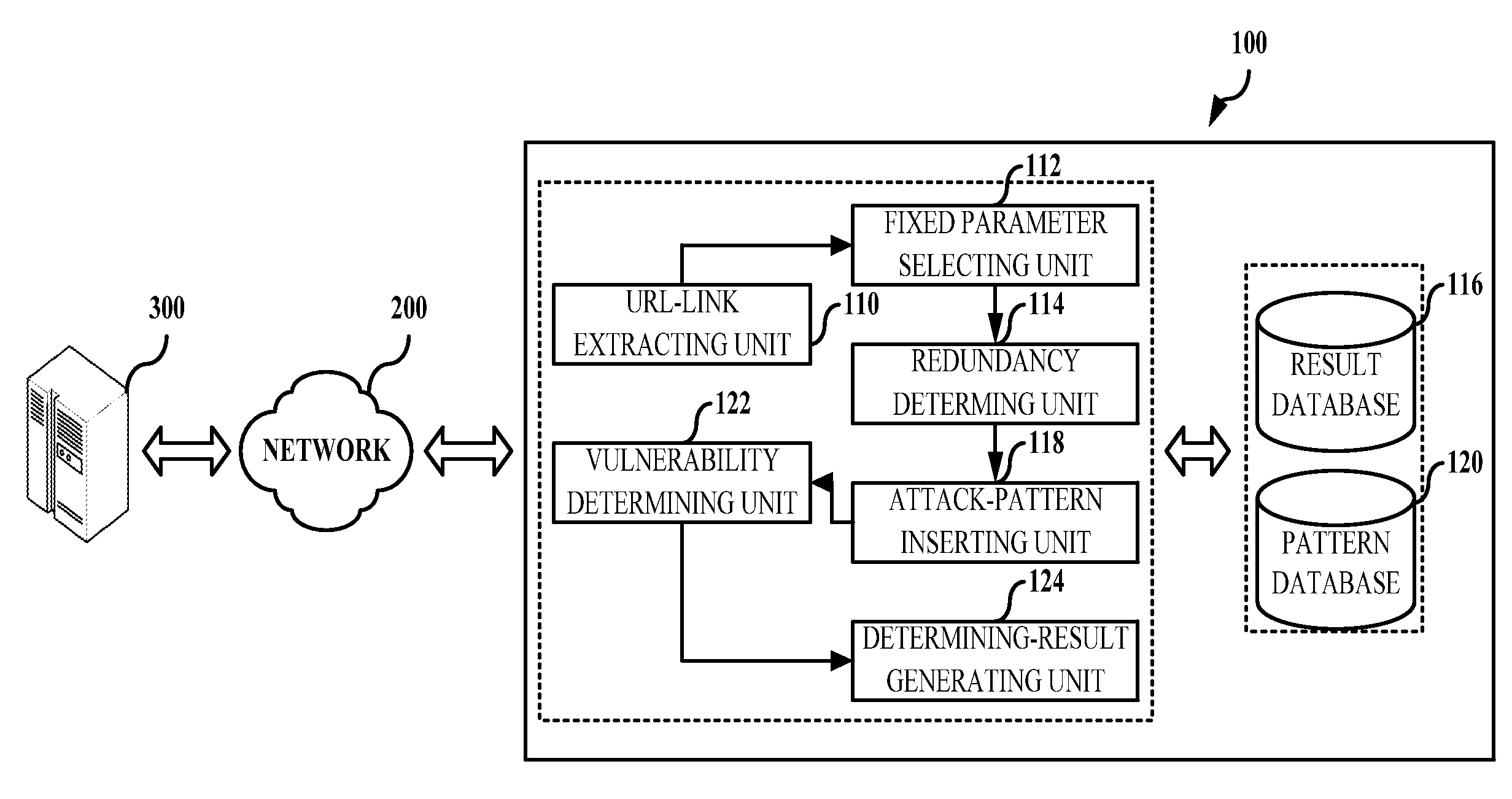
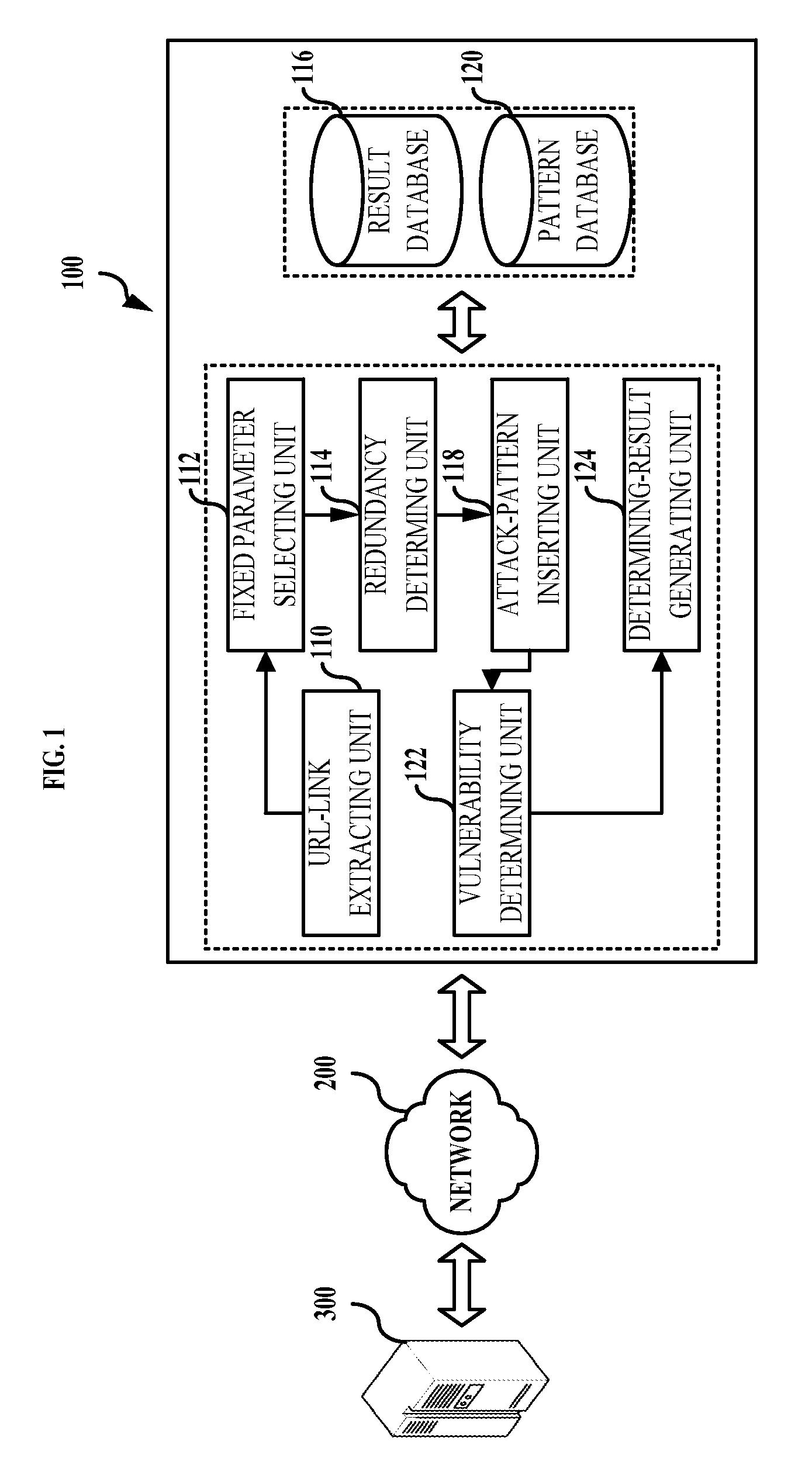
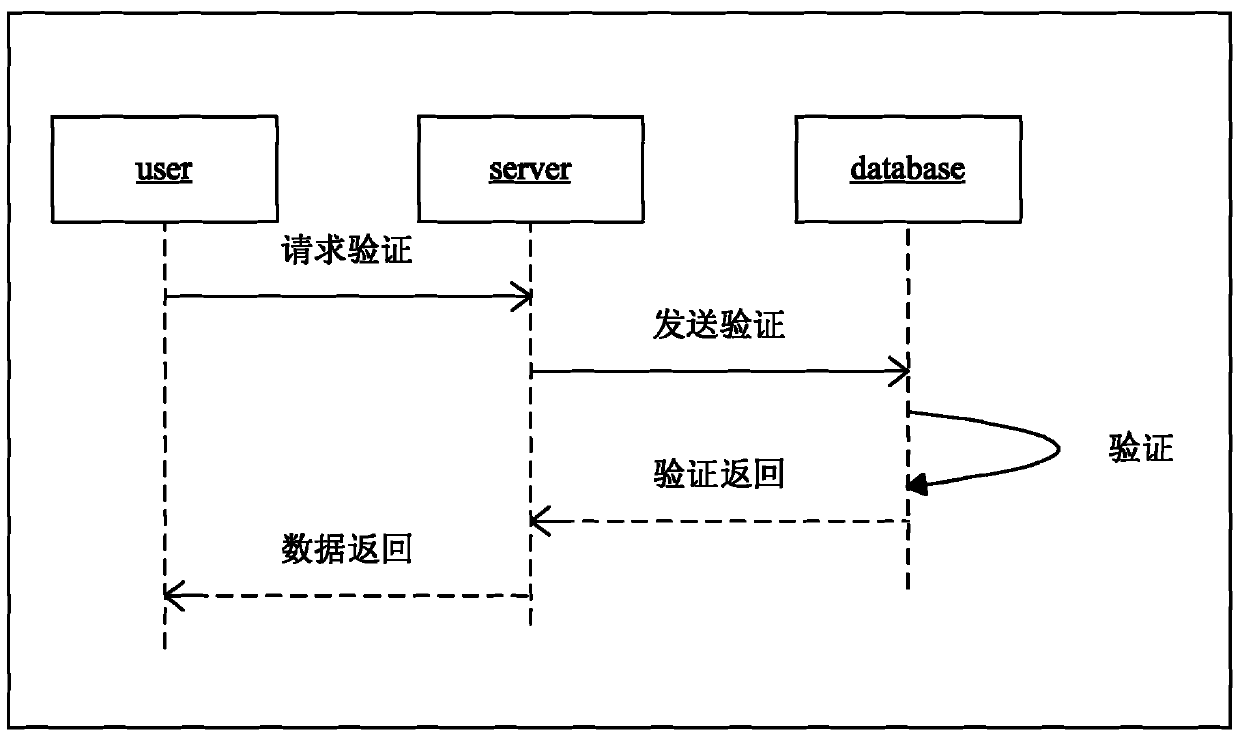
Method and system of determining vulnerability of web application
Owner:NAVER CLOUD CORP
System and method for distributed denial of service identification and prevention
Systems and methods for discovery and classification of denial of service attacks in a distributed computing system may employ local agents on nodes thereof to detect resource-related events. An information later agent may determine if events indicate attacks, perform clustering analysis to determine if they represent known or unknown attack patterns, classify the attacks, and initiate appropriate responses to prevent and / or mitigate the attack, including sending warnings and / or modifying resource pool(s). The information layer agent may consult a knowledge base comprising information associated with known attack patterns, including state-action mappings. An attack tree model and an overlay network (over which detection and / or response messages may be sent) may be constructed for the distributed system. They may be dynamically modified in response to changes in system configuration, state, and / or workload. Reinforcement learning may be applied to the tuning of attack detection and classification techniques and to the identification of appropriate responses.
Owner:ORACLE INT CORP
DoS/DDoS attack detecting and filtering method based on light-weight intrusion detection
The invention discloses a DoS / DDoS attack detecting and filtering method based on light-weight intrusion detection. The problem that intrusion detection accuracy still needs to be improved in the prior art is solved through the method. The method includes the steps of 1, flow early warning based on a time window; 2, abnormal flow characteristic processing; 3, rapid attack detection based on rule matching; 4, excavation and detection of attacks of unknown types; 5, attack filtering based on an IP list. Compared with the prior art, through the combination of the light-weight intrusion detection technology with characteristic selection, the problem that an original DoS / DDoS attack detection method based on classification detection is poor in instantaneity is basically solved; through the combination of online incremental learning and characteristic selection, the problems existing in detection of attacks of unknown types are solved, wherein pre-built attack modes of the attacks are not matched.
Owner:THE PLA INFORMATION ENG UNIV
Method and apparatus for pattern matching based on packet reassembly
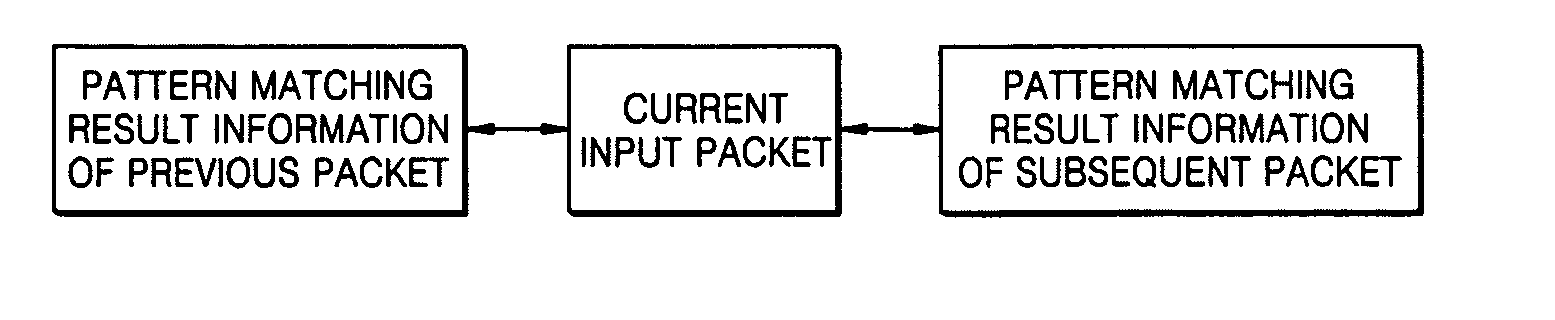
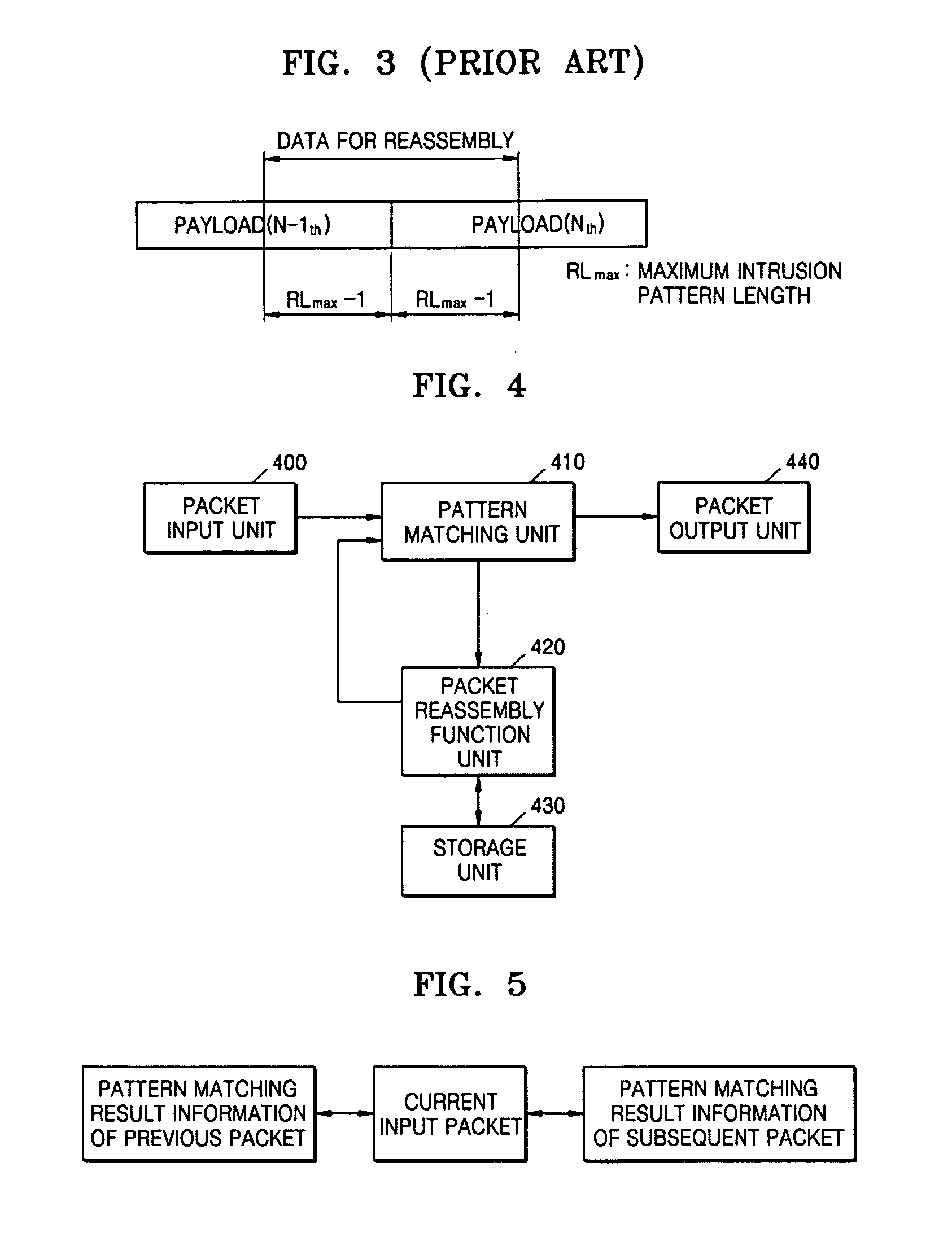
InactiveUS20060198375A1Overcome limitationsEfficient use of resourcesError preventionFrequency-division multiplex detailsPattern matchingSerial code
A method and apparatus for pattern matching using packet reassembly are provided. The pattern matching method using packet reassembly includes: extracting serial information in relation to a current input packet; determining whether or not pattern matching result information in relation to one or more previous packets and / or subsequent packets on the basis of the serial number of the current input packet is already stored; loading the pattern matching result information in relation to the previous packets and / or subsequent packets; and reassembling the loaded pattern matching result information in relation to the previous packets and / or subsequent packets and the current input packet and performing pattern matching with attack patterns which are already stored. Accordingly, by using packet reassembly, a method and apparatus for pattern matching capable of reducing memory usage without lowering the speed can be provided
Owner:ELECTRONICS & TELECOMM RES INST
Coating of a discrete selective surface of an article
A method for restoring or enhancing an environmental resistant coating of a coating total thickness within a coating design thickness range on a metal substrate of an article includes the application of a restoring or enhancing metal to at least one discrete local surface area. Then at least the discrete local surface area is coated with an environmental resistant coating. For use of the method to restore a coating on an article which has experienced service operation and the discrete surface area includes an undesirable amount of oxidation / corrosion products, the oxidation / corrosion products first are removed from an outer portion of the coating while retaining a coating present at the discrete surface areas and retaining the entire coating on surface areas adjacent the discrete surface areas. Then the restoration metal is applied. For use of the method to enhance an existing coating, at least one discrete surface area is selected based on an oxidation / corrosion attack pattern identified from similar articles which experienced service operation in apparatus of a design for which the article is intended. Then the enhancing metal is applied to the selected area.
Owner:GENERAL ELECTRIC CO
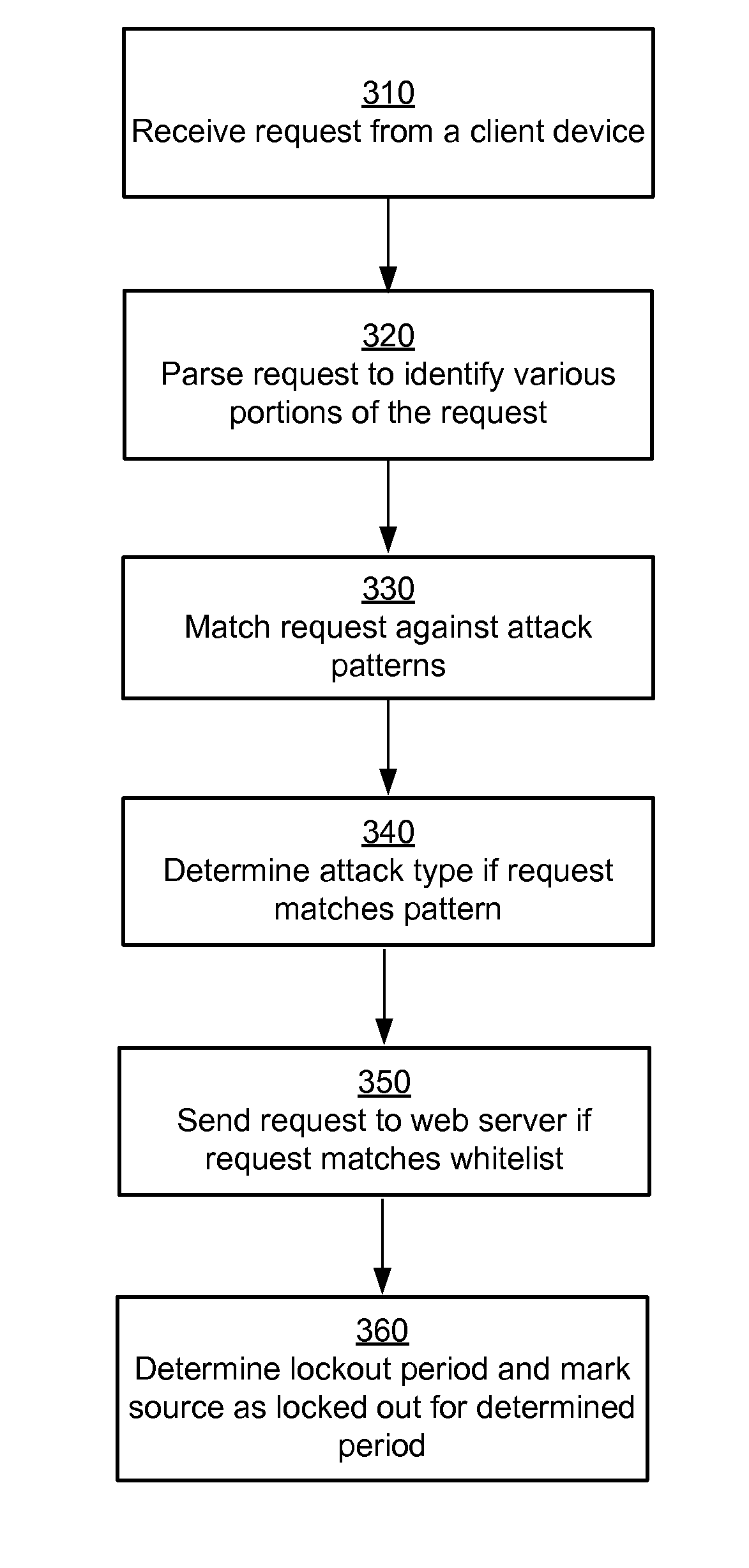
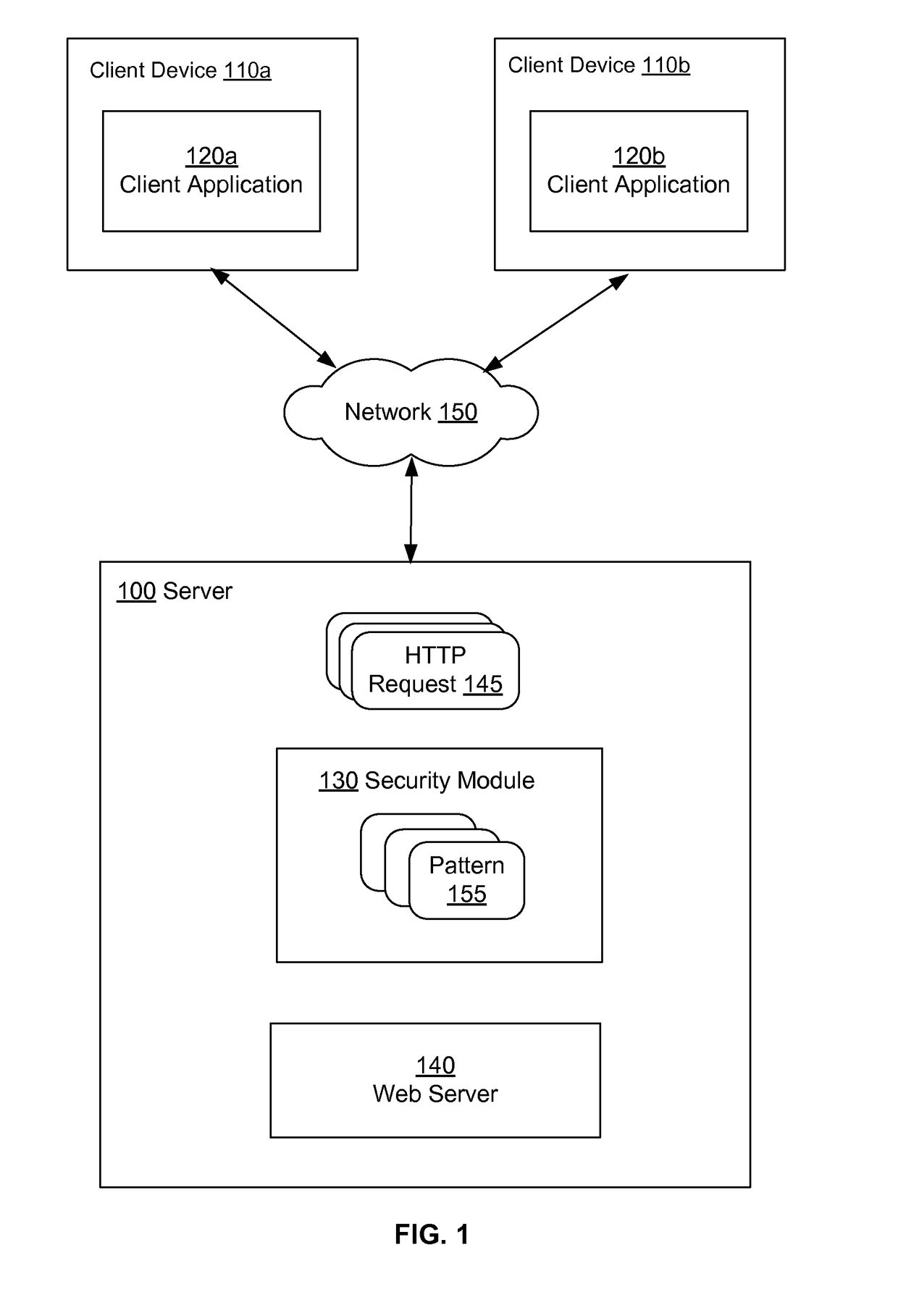
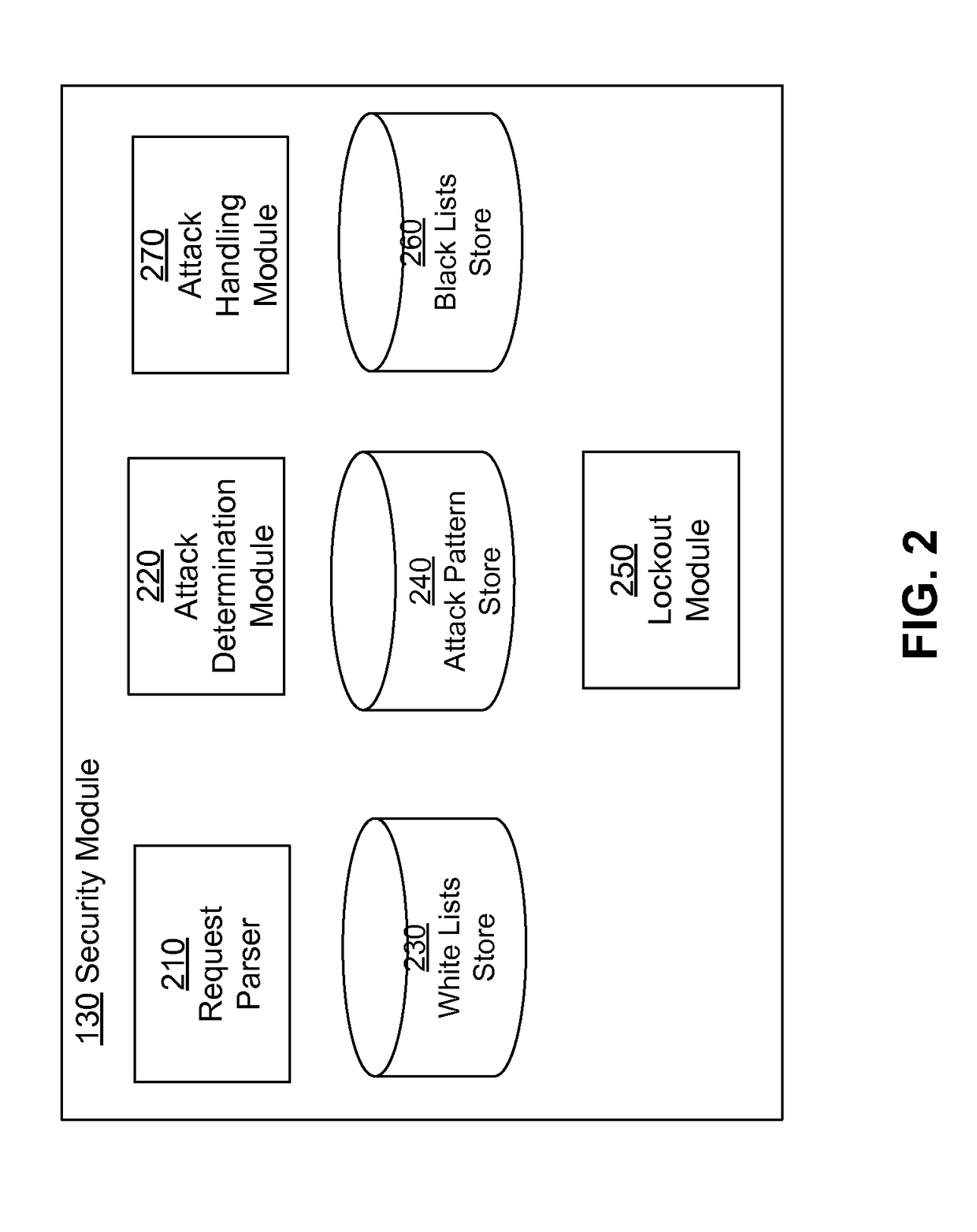
Identifying Attack Patterns in Requests Received by Web Applications
A system and a method are disclosed for determining malicious web requests. The system processes incoming web requests to determine whether a request matches predetermined patterns of suspicious requests. The systems stores associations between patterns of suspicious requests, parts of the web request where each pattern occurs, and attack type associated with the pattern. If the system determines that an incoming web request matches a pattern of a suspicious request, the system determines whether to forward the request to the web server for processing or to hold the request. The system locks out a source of request for a period of time if the source sends requests that match certain attack patterns.
Owner:SALESFORCE COM INC
Cognitive radio space-frequency two-dimensional anti-hostility jamming method based on deep reinforcement learning
InactiveCN106961684AImprove communication efficiencyFast learningMachine learningNeural learning methodsAnti jammingNerve network
The invention discloses a cognitive radio space-frequency two-dimensional anti-hostility jamming method based on deep reinforcement learning. A cognitive radio secondary user observes an access state of a cognitive radio primary user and a signal to jamming ratio of a wireless signal under a state of unknowing a jammer attack mode and a wireless channel environment, and decides whether to leave the located interfered region or select an appropriate frequency point to send the signal by use of a deep reinforcement learning mechanism. A deep convolutional nerve network and Q learning are combined, the Q learning is used for learning an optimal anti-jamming strategy in a wireless dynamic game, and an observation state and acquired benefit are input into the deep convolutional nerve network as a training set to accelerate the learning speed. By use of the deep reinforcement learning mechanism, the communication efficiency for competing hostility jammer by the cognitive radio under a wireless network environment scene in dynamic change is improved. A problem that the learning speed is fast reduced since an artificial nerve network needs to firstly classify the data in the training process and the Q learning algorithm is large in dimension in a state set and an action set can be overcome.
Owner:XIAMEN UNIV
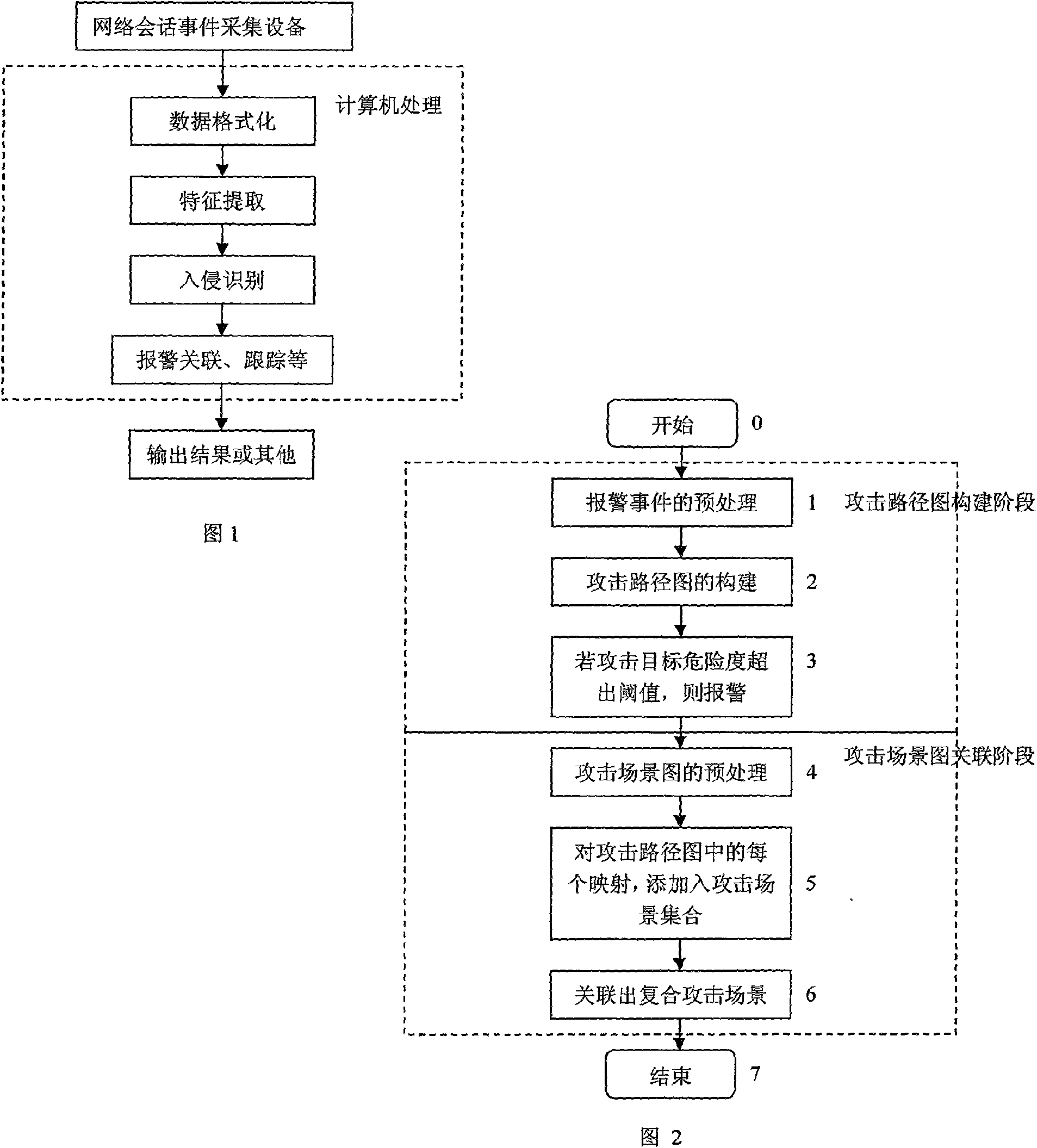
Building method of combined attack correlation and attack scene modelling on the basis of attack mode
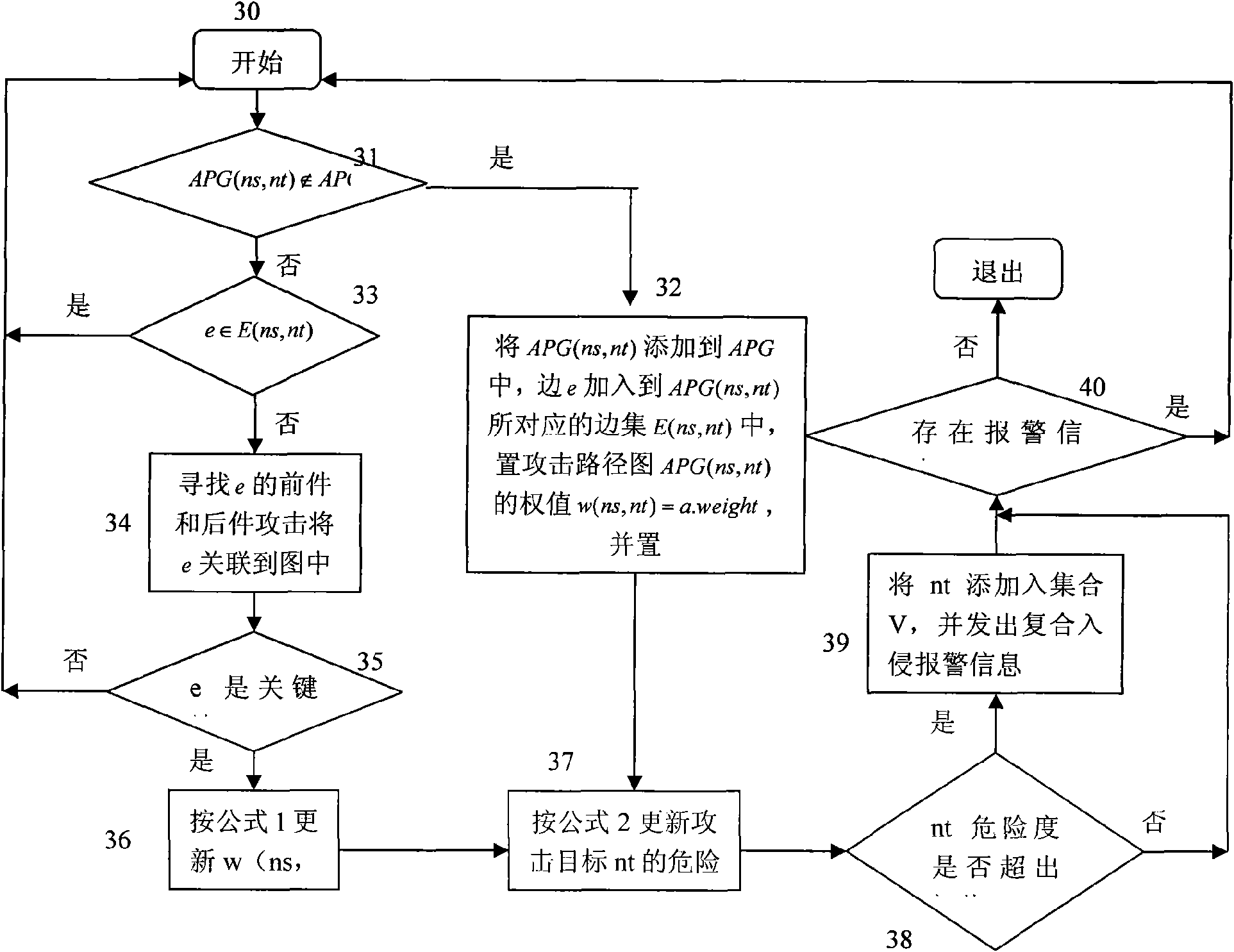
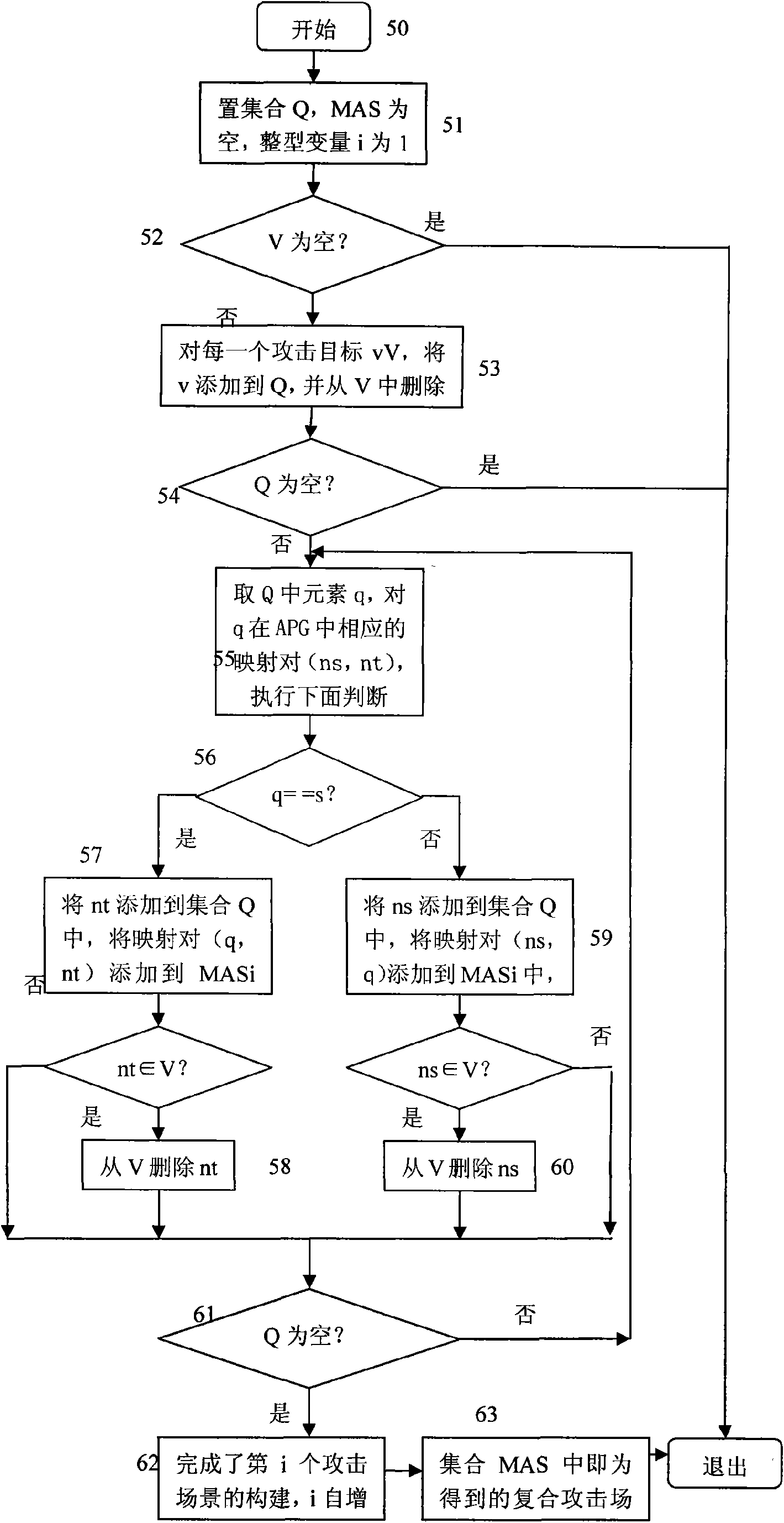
InactiveCN101599855AImprove predictive performanceImprove accuracyData switching networksCorrelation analysisAttack patterns
The invention discloses a building method of combined attack correlation and attack scene modelling on the basis of an attack mode, comprising the following steps: 1) the stage of building an attack path map: 11) warning information is treated primarily; 12) a relevant attack path map is built to the pre-treated warning information ; 13) the risk degree of an attack target is calculated, if the risk degree is larger than a preset threshold value, warning information is sent out; 14) the stage is finished. 2) the correlation stage of attack scene map: 21) the attack scene map is treated primarily; 22) each mapping in an attack path map assembly is added into an attack scene map assembly; 23) a combined attack scene map is correlated; 24) the stage is finished. The building method of combined attack correlation and attack scene modelling on the basis of an attack mode of the invention improves the correlation analysis precision rate of warning time under the condition of keeping simple calculation, so that correlation analysis and prediction performance of an intrusion detection system can be improved.
Owner:NANJING UNIV
Network safety warning system based on cluster and relavance
InactiveCN1588880AVersatileImprove performanceData switching networksSpecial data processing applicationsProcess moduleComputer module
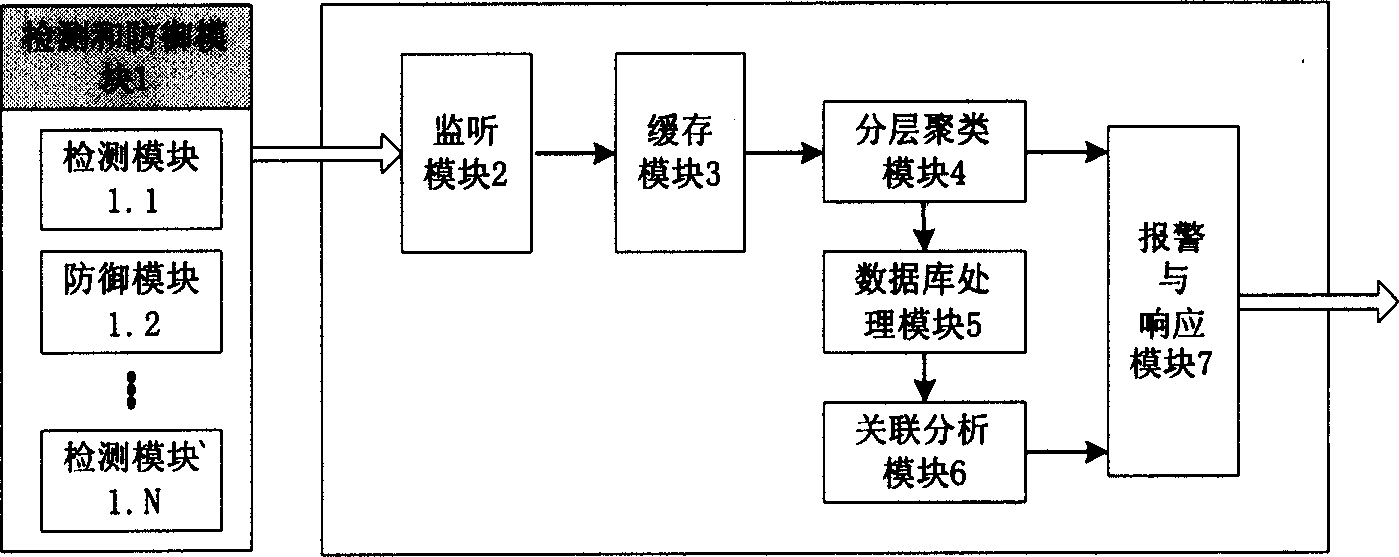
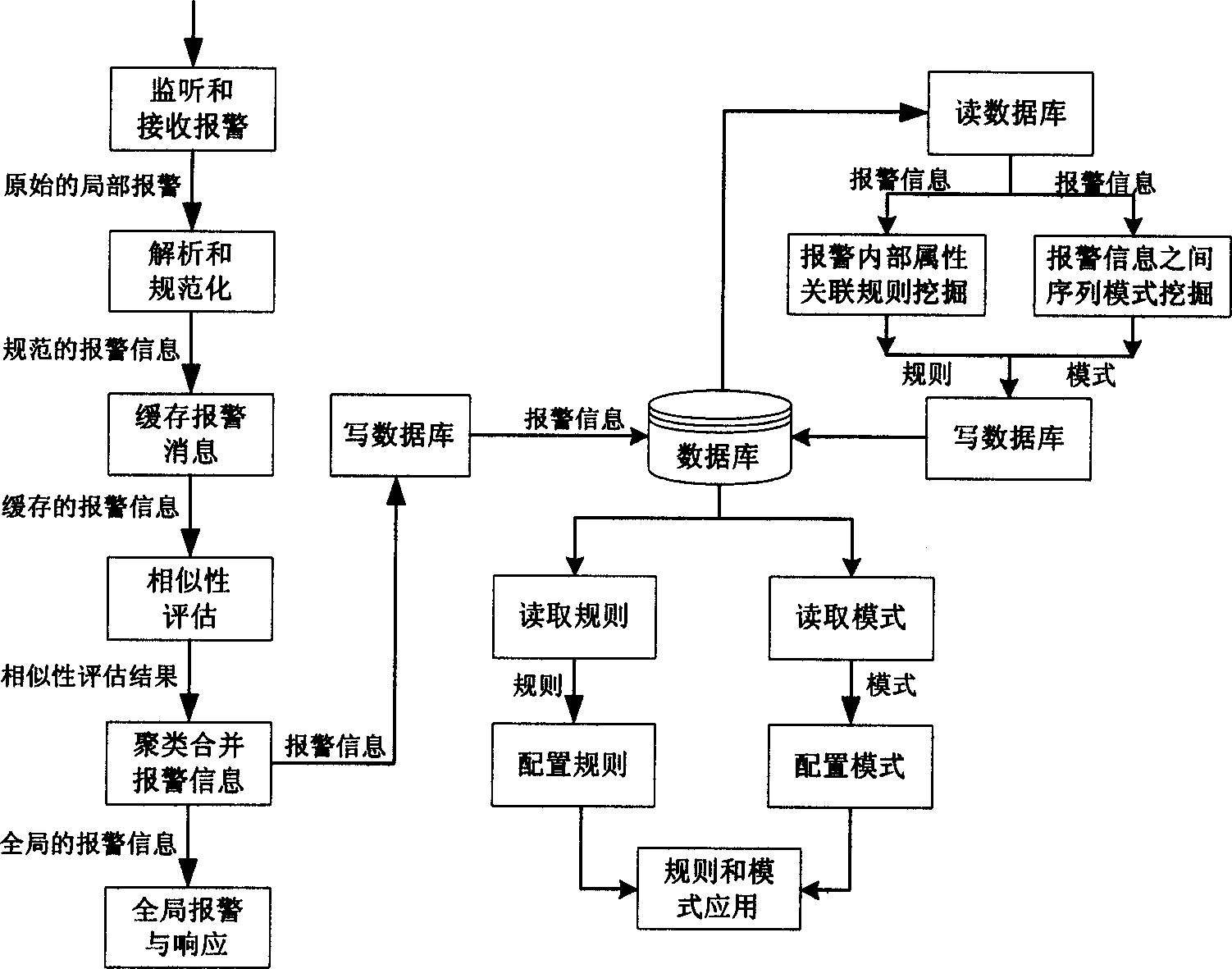
This invention relates to an system based on alarming cluster and associated network safety including a monitor module, a buffer memory module, a hierachi clustering module, a database process module, an associated analysis module and an alarm and response module integrated on the upper control stand. The hierachi clustering module can reduce the same or similar redundant alarm information, so as to reduce its transmission volume or extra loads and reduce process burden of network managers who can be even more clear about the attack behavior and configurated safety strategy.
Owner:HUAZHONG UNIV OF SCI & TECH
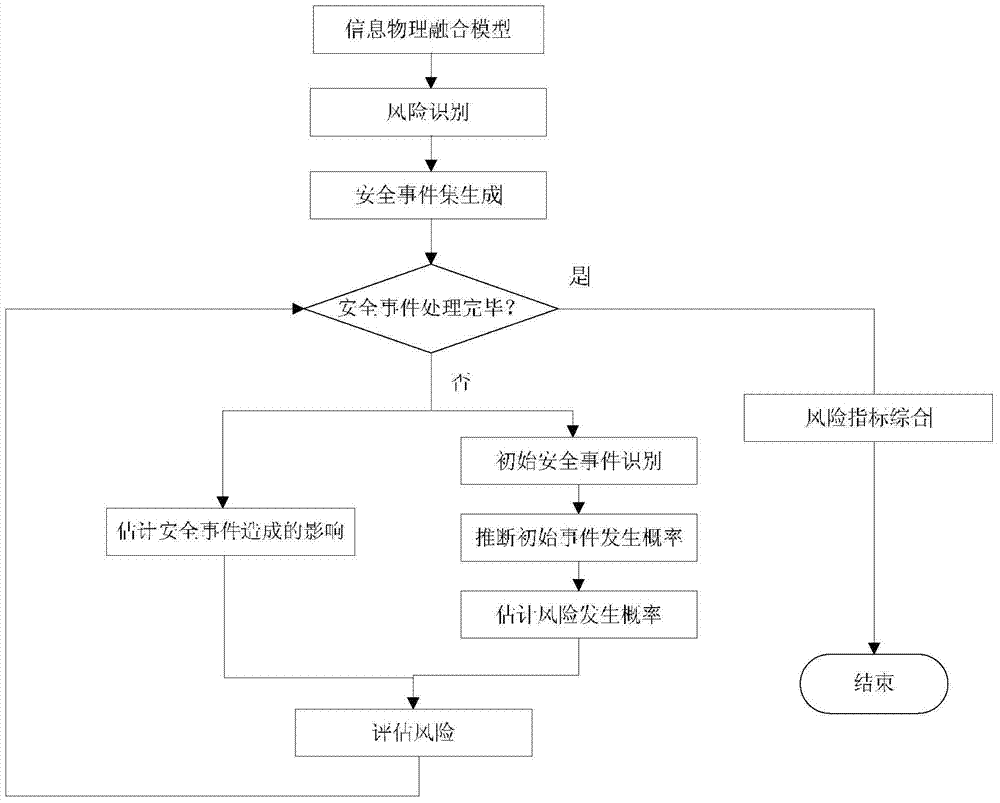
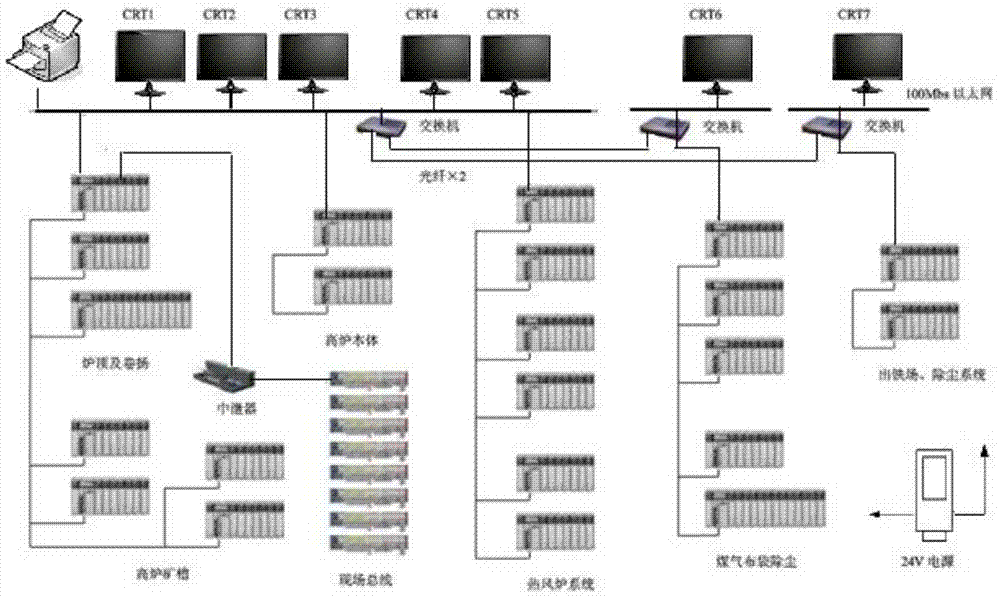
Information security risk assessment method oriented to typical metallurgy process control system
InactiveCN104331072AGuaranteed safe operationLow costElectric testing/monitoringProbabilistic methodRisk indicator
The invention provides an information security risk assessment method oriented to a typical metallurgy process control system and belongs to the technical field of industrial control system information security. The system robustness under different attack modes and policies is analyzed by establishing an attack model under the typical scenes of the metallurgy process, and therefore, the security risk assessment on the typical metallurgy process control system in different attack modes and a failure mode can be realized. Based on the risk theory, the method is used for performing the security risk assessment by use of a random probability algorithm by defining the metallurgy process control system as a physical information fusion system; from the two aspects of the occurrence probability and the influence of attack sources or failure sources, a security assessment method based on risk indexes is developed. Quantitative estimation is performed based on risk indexes; a security incident set is created based on the established physical information fusion model and attack model, and then the security incident set is combined with the calculated robustness assessment indexes for the quantitative estimation, and therefore, the weak security links in the control system can be located conveniently.
Owner:AUTOMATION RES & DESIGN INST OF METALLURGICAL IND
Information security event automatic association and rapid response method and system based on big data analysis
ActiveCN105847029AEliminate false positivesHigh precisionData switching networksResponse methodCorrelation analysis
The invention discloses an information security event automatic association and rapid response method and system based on big data analysis. The method and the system comprise an offline association module, an online association module, an element alarm comparison module, an element alarm priority module, an element alarm clustering module, an attack mode discovering module and an alarm response system / work order module. Through adoption of the method and the system, alarms reported by a security device are aggregated into element alarms for correlation analysis by using a big data technique, thus generating multiple element alarms. Element alarm priority analysis is carried out after alarm correlation analysis is carried out; alarm priorities corresponding to element alarms are distributed; an alarm response system informs related personnel and the delegates related personnel to check and repair faults according to the alarm level priorities; the alarm response time is remarkably shortened; and misinformation generated by information security devices such as IDS (Intrusion Detection Systems) is eliminated.
Owner:NANJING LIANCHENG TECH DEV
Attack mode detection method based on event slide window
ActiveCN106375339AGood lifting effectExcavate accuratelyPlatform integrity maintainanceTransmissionSlide windowSequence pattern
The invention relates to an attack mode detection method based on an event slide window. The method comprises the steps of S1, normalizing, integrating, compressing and preprocessing warning information, and aggregating the warning information with approximate attribute similarity into super warning; S2, carrying out protocol on frequent items, thereby obtaining frequent correlation sequence patterns according to a causal correlation matrix; S3, for the new frequent correlation sequence patterns at each time and warning pairs of the frequent correlation sequence patterns with different attributes, carrying out weight average on the participating attributes; and S4, generating an attack pattern graph consistent with invasion characteristics. According to the method, attack patterns existing in warning logs can be mined efficiently and accurately, new invasion access behaviors can be identified or intercepted rapidly, and the accuracy and speed of mining the attack patterns in the massive and seemingly meaningless warning logs can be greatly improved.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
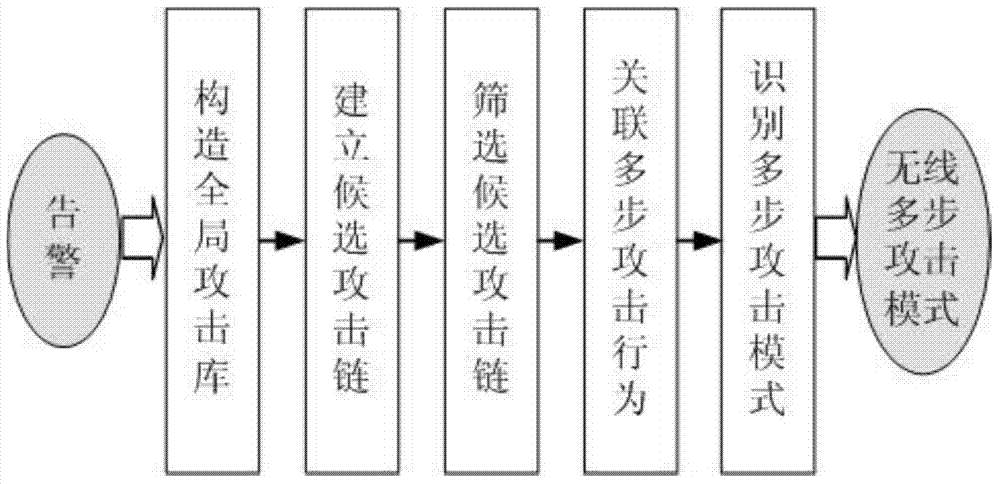
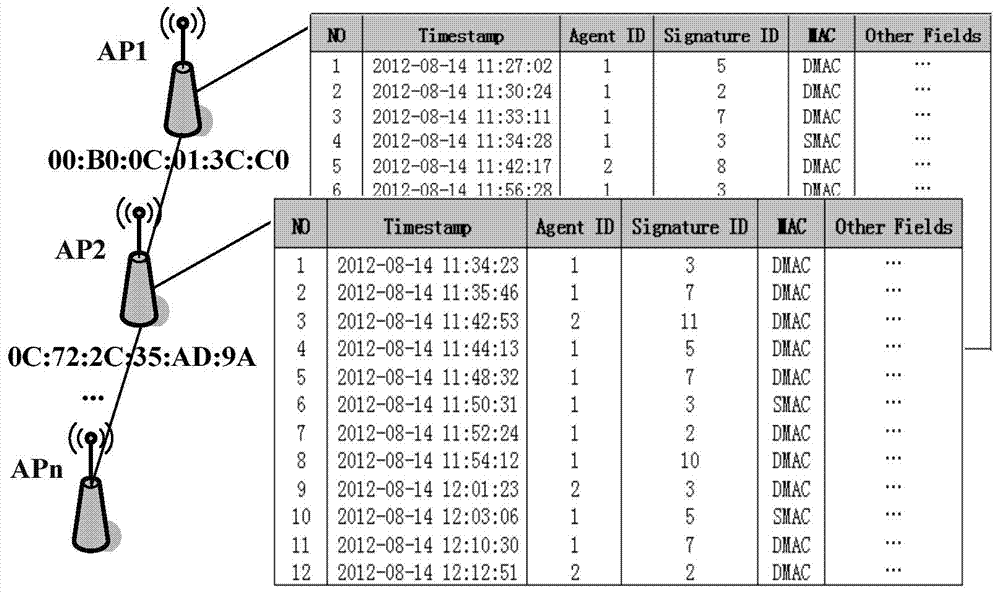
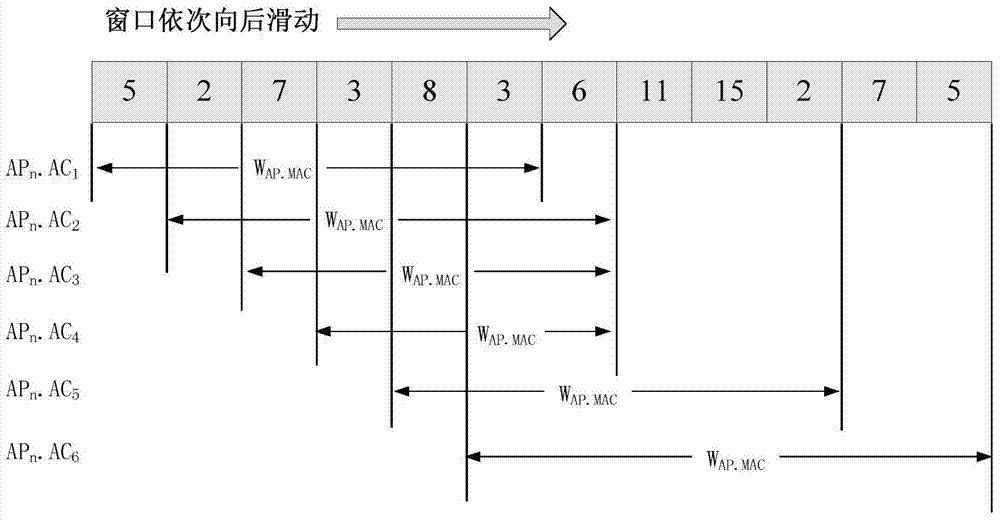
Wireless multi-step attack mode excavation method for WLAN
The invention discloses a wireless multi-step attack mode excavation method for WLAN. The method comprises the following steps of: 1, building a global attack library, consisting of: classifying wireless alarm according to different AP information in a WLAN environment and BSSID information of the AP, and building the global attack library based on the AP according to attributes of occurrence time; 2, building candidate attack links; 3, screening the candidate attack links; 4, correlating a multi-step attack behavior; 5, identifying a multi-step attack mode, consisting of: computing the correlation between adjacent attacks in the attack link, deleting the attack link with the correlation lower than a predetermined correlation threshold, and finally identifying the wireless multi-step attack mode. The wireless multi-step attack mode excavation method for WLAN has the advantages of being applicable to actual attack scenes of WLAN, and capable of effectively excavating the wireless multi-step attack mode and providing bases for the pre-identification of the multi-step attack intention.
Owner:ZHEJIANG UNIV CITY COLLEGE
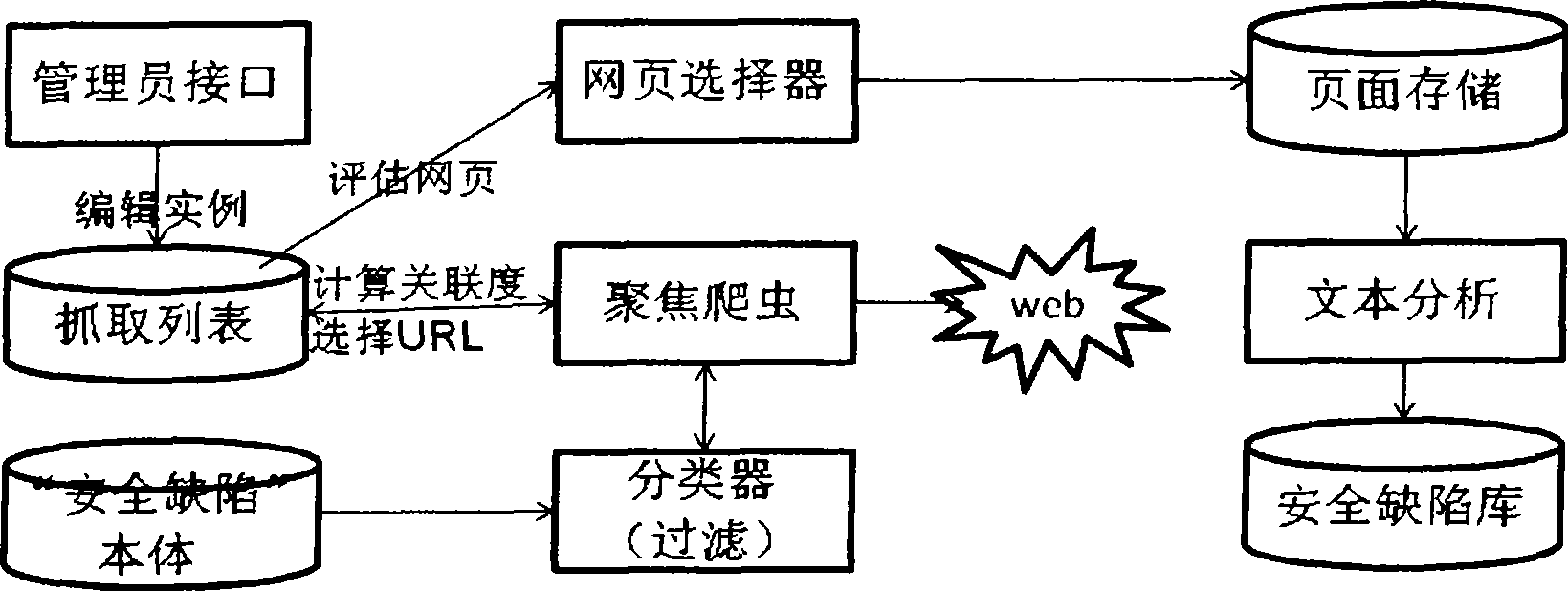
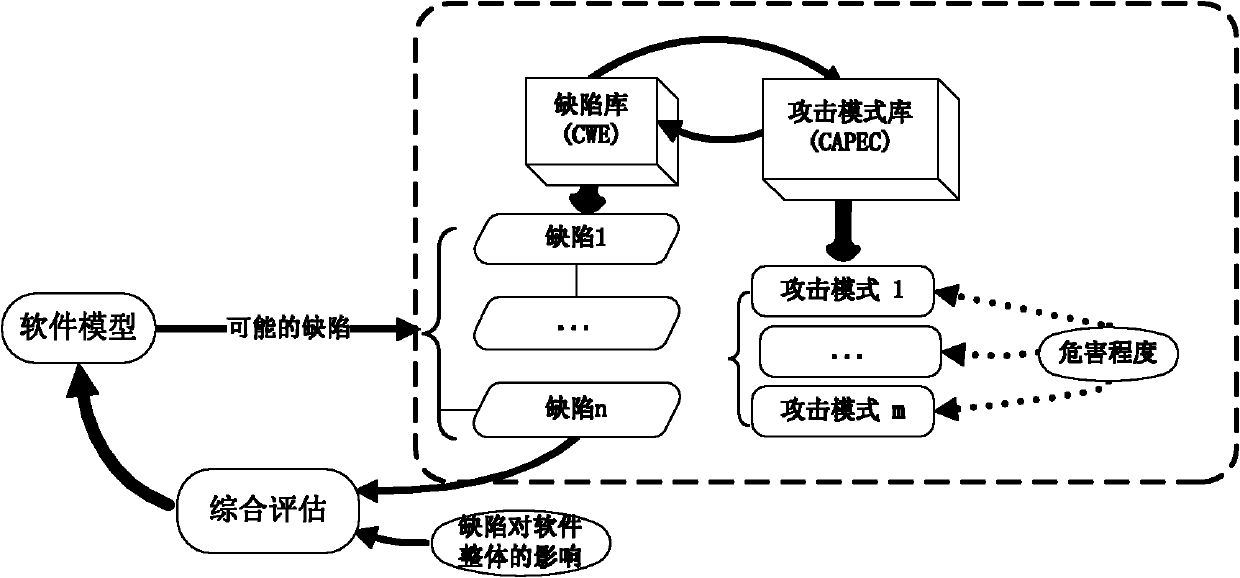
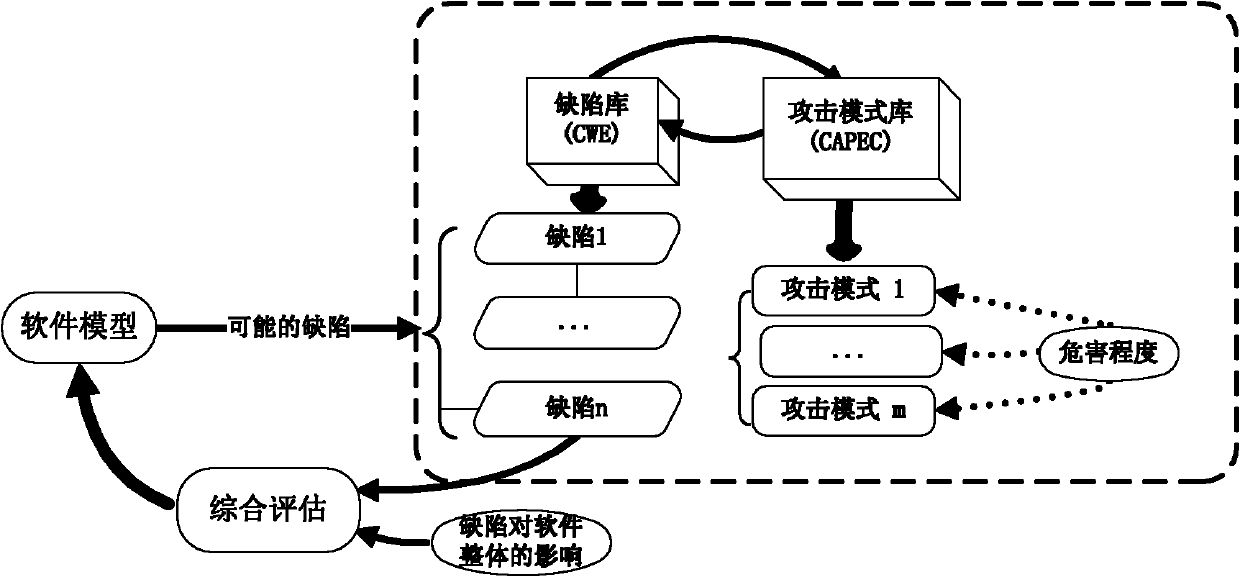
Software safety defect library system based on attack mode and management method thereof
ActiveCN101452469AQuality improvementReduced security flawsDigital data protectionSpecial data processing applicationsManagement unitSubject matter
The invention discloses a software security defect database system based on an attack mode, which comprises a construction unit of a security defect database, a management unit of the security defect database, and a security defect body. The software security defect database system is characterized in that the construction unit of the security defect database comprises the steps of establishing a mapping from the attack mode to a software defect structure, establishing a mapping from the attack mode to a security defect and a mapping from the security defect to a corresponding alleviation proposal, and constructing the two mappings into a unified model; and the management unit of the security defect database comprises a security defect information acquisition module and a security defect information classification module, wherein information acquisition is based on WEB subject mining technology, and defect classification is based on body technology. The software security defect database system simultaneously combines external attack mode analysis and a security-oriented software development cycle to construct a security defect database model, so as to reduce security defects of software products and improve the quality of software, thereby the software security defect database system meets different demands on software security defect examples in different stages and can be used for supporting the data service of the security defect model.
Owner:江苏永达电力电信安装工程有限公司
Key generation and distribution method for wireless communication system
ActiveCN107196920AImplement two-factor authenticationTransmissionCommunications securityCommunications system
The invention relates to the technical field of communication security, and more particularly to a key generation and distribution method for a wireless communication system. The key generation and distribution method comprises the steps that: a terminal and an access point generate physical layer keys based on wireless communication channel features of the two parties; an authentication center generates authentication data and a non-access-layer key by means of a root key associated with identity of the terminal and an access-layer authentication key; the terminal authenticates the access point and the authentication center by utilizing the root key, the access-layer authentication key and the received authentication data of the authentication center; the authentication center authenticates the terminal by utilizing the root key, the access-layer authentication key and received terminal authentication data; the terminal and the access point each generates a secondary access-layer encryption and integrity protection key; and the terminal and the access point can update a primary access-layer key and the access-layer authentication key synchronously at any time, and realizes updating and continuous authentication of the access-layer keys. The key generation and distribution method utilizes the uniqueness, reciprocity and time-varying property of the wireless channel, generates the physical layer keys at the terminal and the access point separately, introduces the physical layer keys into the access-layer keys and the authentication keys, realizes dual authentication of identity and path, and can prevent the attack pattern of acquiring the access-layer keys from a non-access layer.
Owner:THE PLA INFORMATION ENG UNIV
Random Petri net-based network security risk analysis method
InactiveCN102130906AImprove analytical performanceSolving the unknown attack patterns in hard-to-find systemsData switching networksSecurity analysisPetri net
The invention discloses a random Petri net-based network security risk analysis method, which comprises the following steps of: acquiring related attributes of a network topology structure and property; acquiring and saving threat information and frangibility information of the property; constructing a risk analysis model; simplifying the risk analysis model; acquiring user index information which is needed to be calculated; performing index quantitative analysis and calculation, and the like. The system risk associated analysis in a general information system environment is provided, the problems that the conventional security analysis tool is difficult to discover an unknown attack mode or security hole in the system, cannot perform global security analysis on the system and the like are solved, the comprehensive network risk analysis capacity is greatly improved, and the security of a network information system is effectively guaranteed.
Owner:INFORMATION SECURITY METASOFT BEIJING
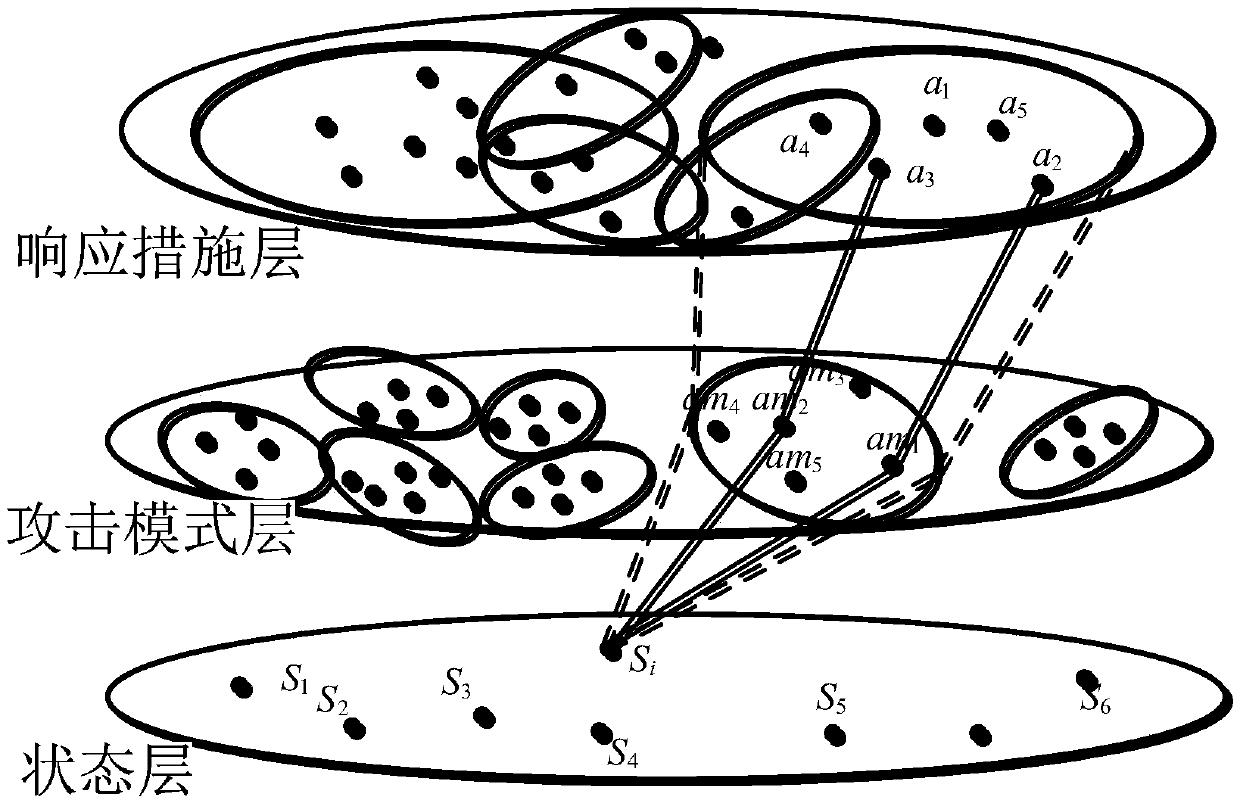
Automatic intrusion response decision making method based on Q-learning
InactiveCN108809979AImprove accuracyImprove real-time performanceComputing modelsTransmissionDecision takingInformation security
The invention belongs to the technical field of information security, and particularly relates to an automatic intrusion response decision making method based on Q-learning. The method comprises the following steps: scanning system vulnerability, constructing an attack graph, and establishing a network state layer, an attack pattern matching layer and a response measure layer according to the attack graph; establishing a mapping relationship among the network state layer, the attack pattern matching layer and the response measure layer; receiving an intrusion alarm from a network defense device, and mapping the intrusion alarm to a corresponding network state; selecting a defense action according to the mapping relationship, and notifying the system of the result; performing online learning by using the execution result of the defense action, and updating the mapping relationship between the attack pattern matching layer and the response measure layer; and returning to the step of mapping the intrusion alarm to the corresponding network state, and performing automatic response decision marking and online learning, until a defender terminates the defense. By adoption of the automatic intrusion response decision making method based on Q-learning provided by the invention, evaluation of multiple response purposes of the strategy can be achieved, the demand of multiple response purposes can be met, the instantaneity and accuracy of the intrusion detection are improved, the network resource consumption is reduced, and the overall performance of the system is improved.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
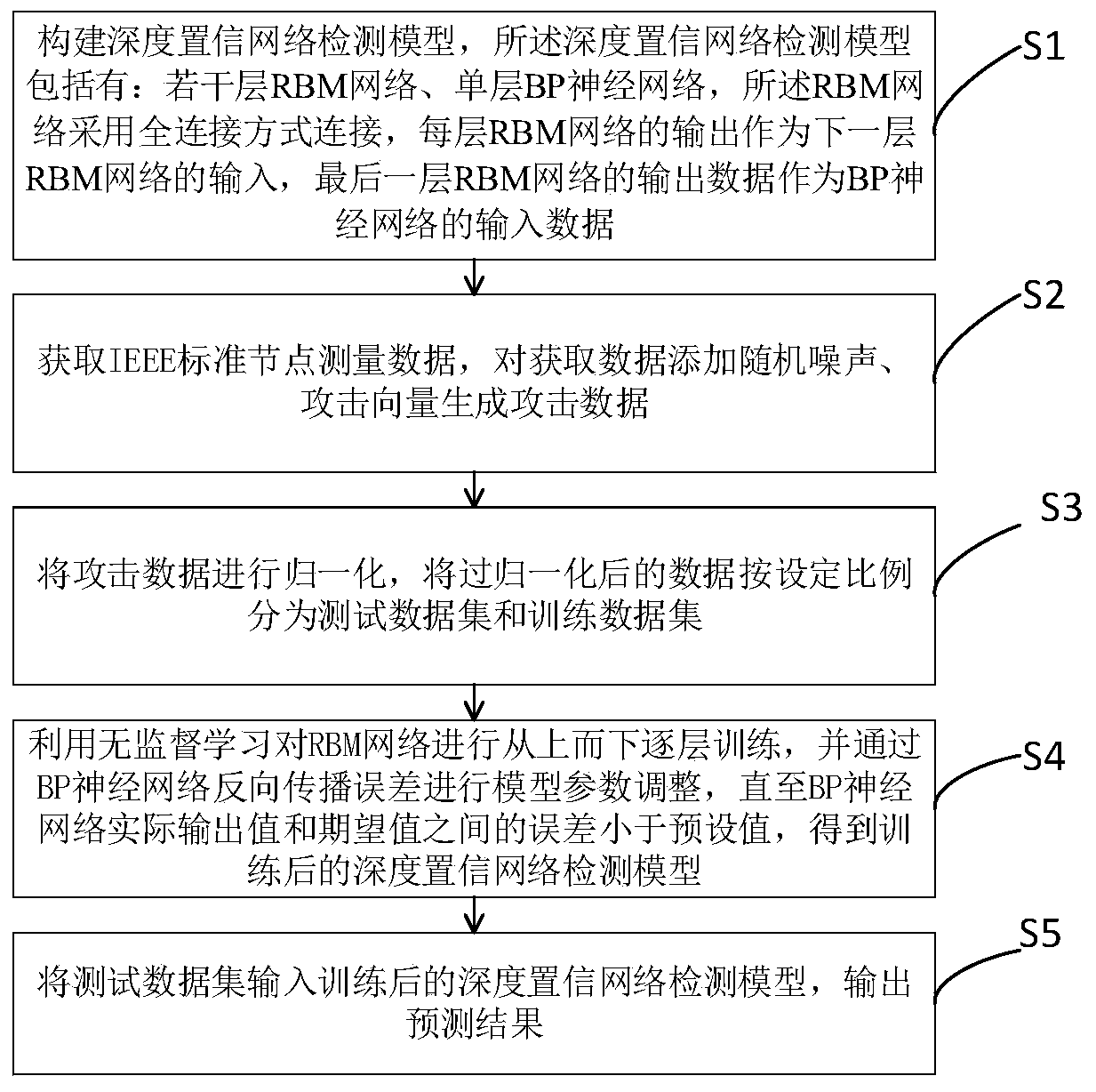
Power grid virtual data injection attack detection method based on deep belief network
PendingCN110889111AAvoid dependenceRealize detectionData processing applicationsCharacter and pattern recognitionDeep belief networkData set
The invention discloses a power grid virtual data injection attack detection method based on a deep belief network, and the method comprises the steps: S1, building a deep belief network detection model which comprises a plurality of layers of RBM networks and a single-layer BP neural network, wherein the RBM networks is connected in a full connection mode; S2, acquiring IEEE standard node measurement data, and adding random noise and attack vectors to the acquired data to generate attack data; s3, dividing the normalized attack data into a test data set and a training data set according to aset proportion; s4, training the RBM network layer by layer from top to bottom by using unsupervised learning, and performing model parameter adjustment through BP neural network back propagation errors to obtain a trained deep belief network detection model; and S5, inputting the test data set into the trained deep belief network detection model, and outputting a prediction result. According to the invention, the dependence of the traditional detection method on the detection threshold is overcome, and the detection of various attack modes is realized.
Owner:GUANGDONG UNIV OF TECH
Mobile terminal to detect network attack and method thereof
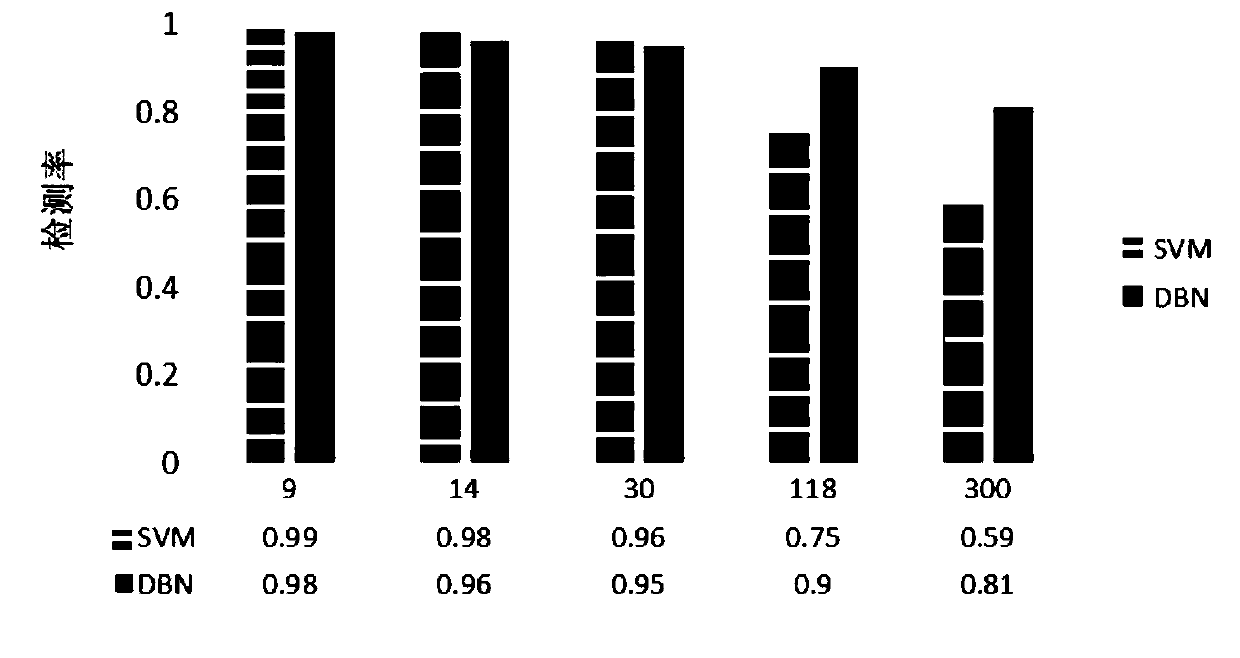
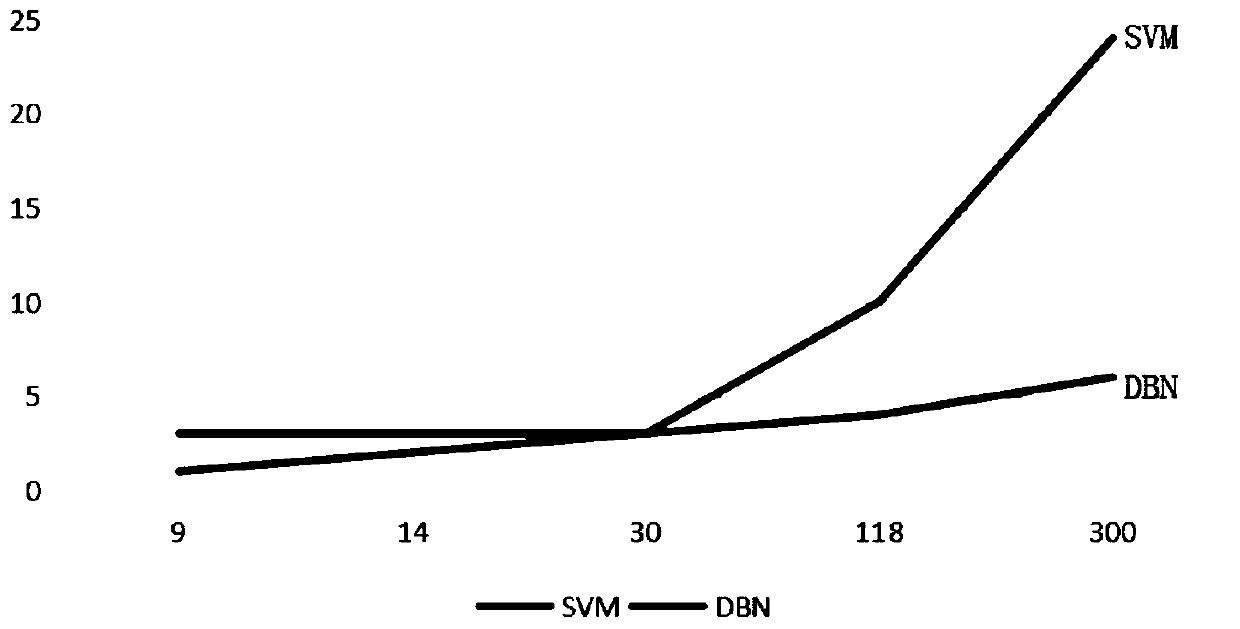
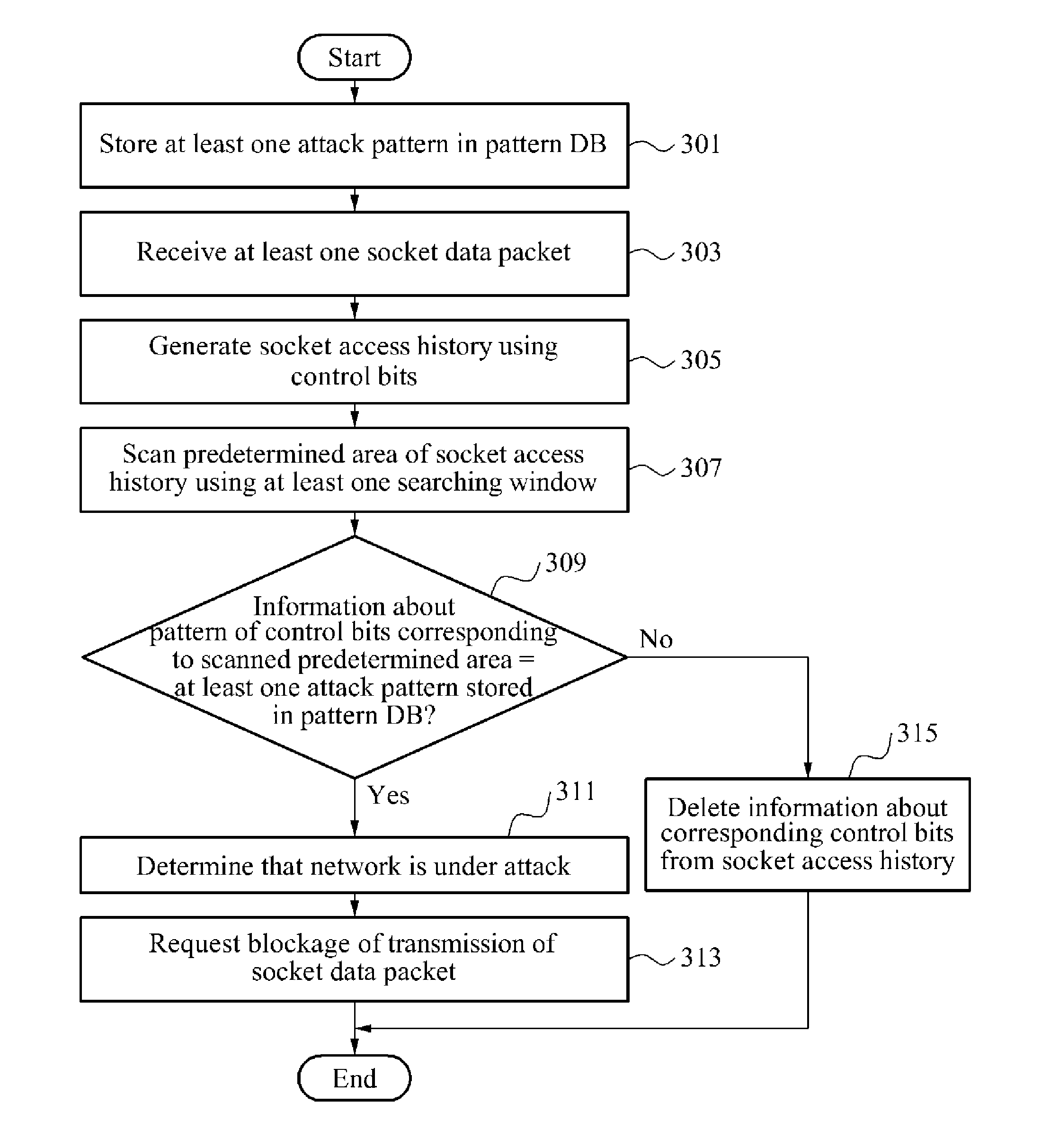
InactiveUS20130227687A1Memory loss protectionData taking preventionCommunication interfaceAccess history
A method for detecting a network attack in a wireless terminal, including storing, in a pattern database (DB), information about an attack pattern that is determined using a plurality of control bits indicating a type of a socket data packet, receiving a socket data packet of a target selected to be accessed through a wireless communication interface identifying the at least one socket data packet received, and generating a socket access history by extracting the plurality of control bits indicating the type of the socket data packet using the at least one socket data packet identified, and determining whether a network is under attack, using the pattern DB and the socket access history.
Owner:PANTECH CO LTD
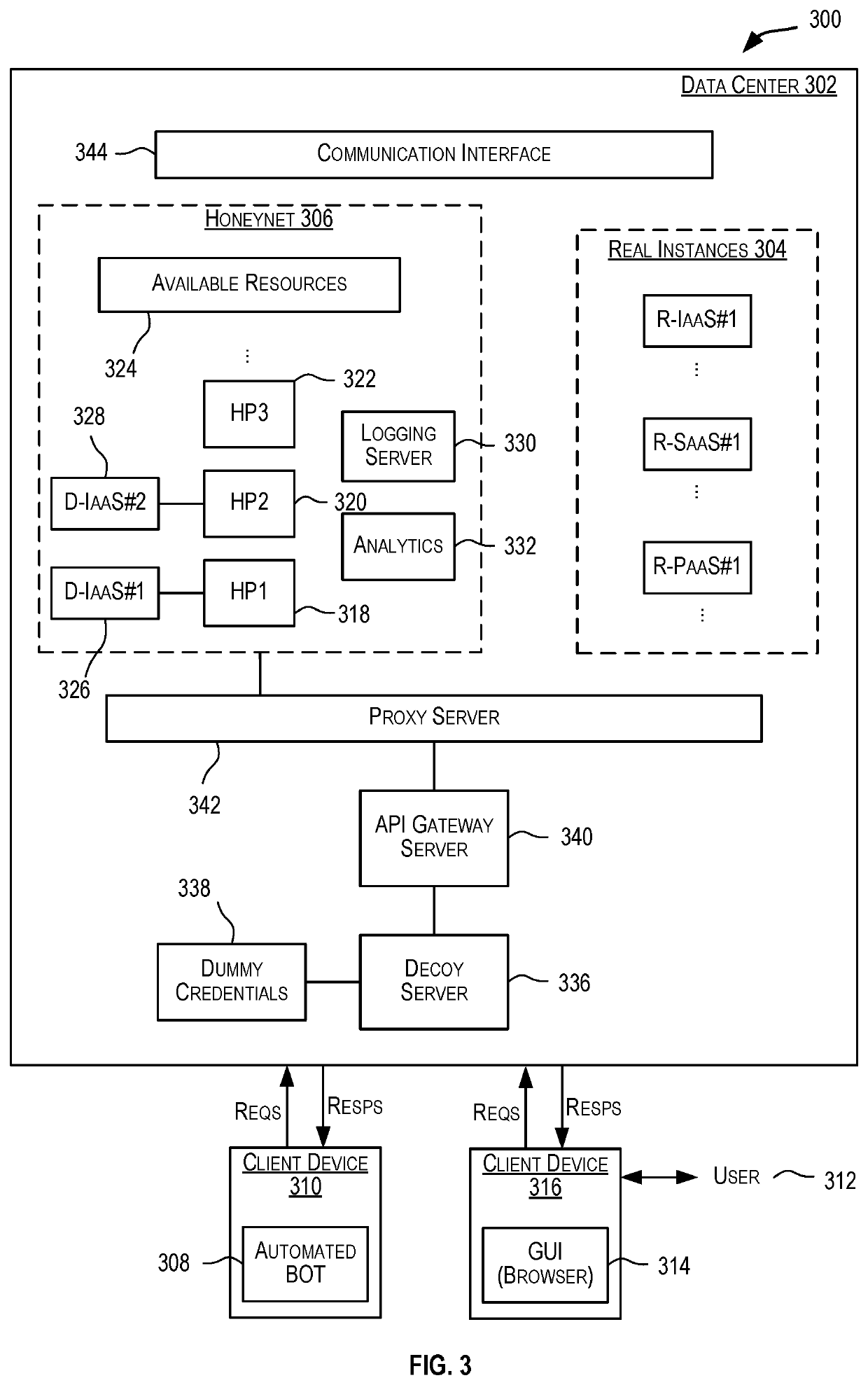
Honeypots for infrastructure-as-a-service security
Techniques for using honeypots to lure attackers and gather data about attackers and attack patterns on Infrastructure-as-a-Service (IaaS) instances. The gathered data may then be analyzed and used to proactively prevent such attacks.
Owner:ORACLE INT CORP
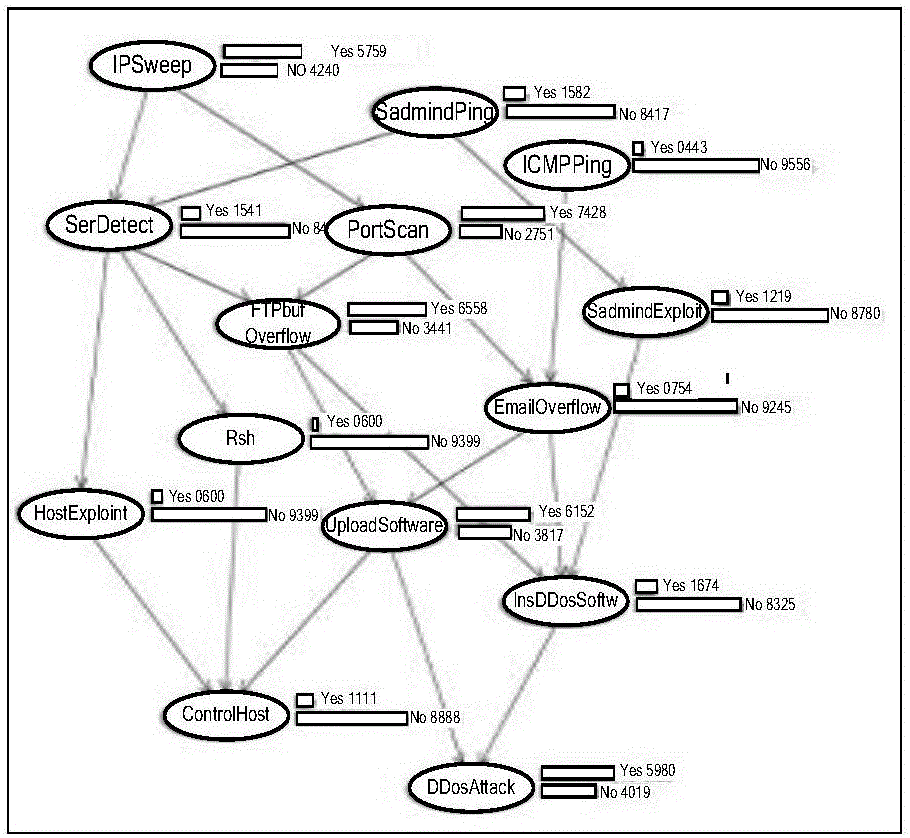
Multi-step attack prediction method based on cause-and-effect Byesian network
ActiveCN106411921AImprove attack prediction capabilitiesOptimized multi-step attack prediction methodTransmissionSerial patternNetwork attack
The invention relates to a multi-step attack prediction method based on a cause-and-effect Byesian network. First of all, a multi-step attack mode in an attack scene sample is mined by use of a frequent mode, the multi-step attack mode is depicted through a cause-and-effect Byesian network mode, based on this, a probability of future attacks is calculated through attack evidence, and thus next-step attack behaviors of network multi-step attacks and attack intensions of attackers can be predicted. According to the invention, a multi-step attack prediction method of manually constructing a network attack structure graph is optimized, the multi-step attack mode is mined automatically based on a frequent sequence mode, by means of the cause-and-effect Byesian network mode, the attack mode is depicted, network parameters are learnt, next-step attacks and the attack attentions are predicted, the attack prediction capability for unknown changing multi-step attack modes is improved, next-step attack means and a final attack attention of the multi-step attacks can be rapidly and accurately predicted, and the method has great realistic significance for safeguarding network and computer information security.
Owner:THE PLA INFORMATION ENG UNIV
Software defect based method for quantificationally estimating software credibility
InactiveCN101819617ALow costEvaluate trusted performancePlatform integrity maintainanceSoftware engineeringQuantitative assessment
The invention belongs to the field of software security and relates to a software defect based method for quantificationally estimating software credibility. The method comprises steps of: classifying each defect according to a credible definition; confirming attack modes probably existed in each defect; confirming corresponding threaten degree levels of the attack modes in high and low damage degrees by analyzing the damage degree caused by the involved attack modes; selecting corresponding threaten degree with the maximum quantitative degree as the defect damage degree of the defect in each probably existed attack mode of each defect; confirming the level of an impact factor of each defect to the whole software according to the influence degree of each defect to the software; and for some kinds of defects, confirming the credibility metric of the defects according to a credibility metric formula. The method enables a developer to more clearly understand the security problem their software products face and improves the weakness of the product again till the effect is satisfied.
Owner:TIANJIN UNIV
Method and system of determining vulnerability of web application
Owner:NAVER CLOUD CORP
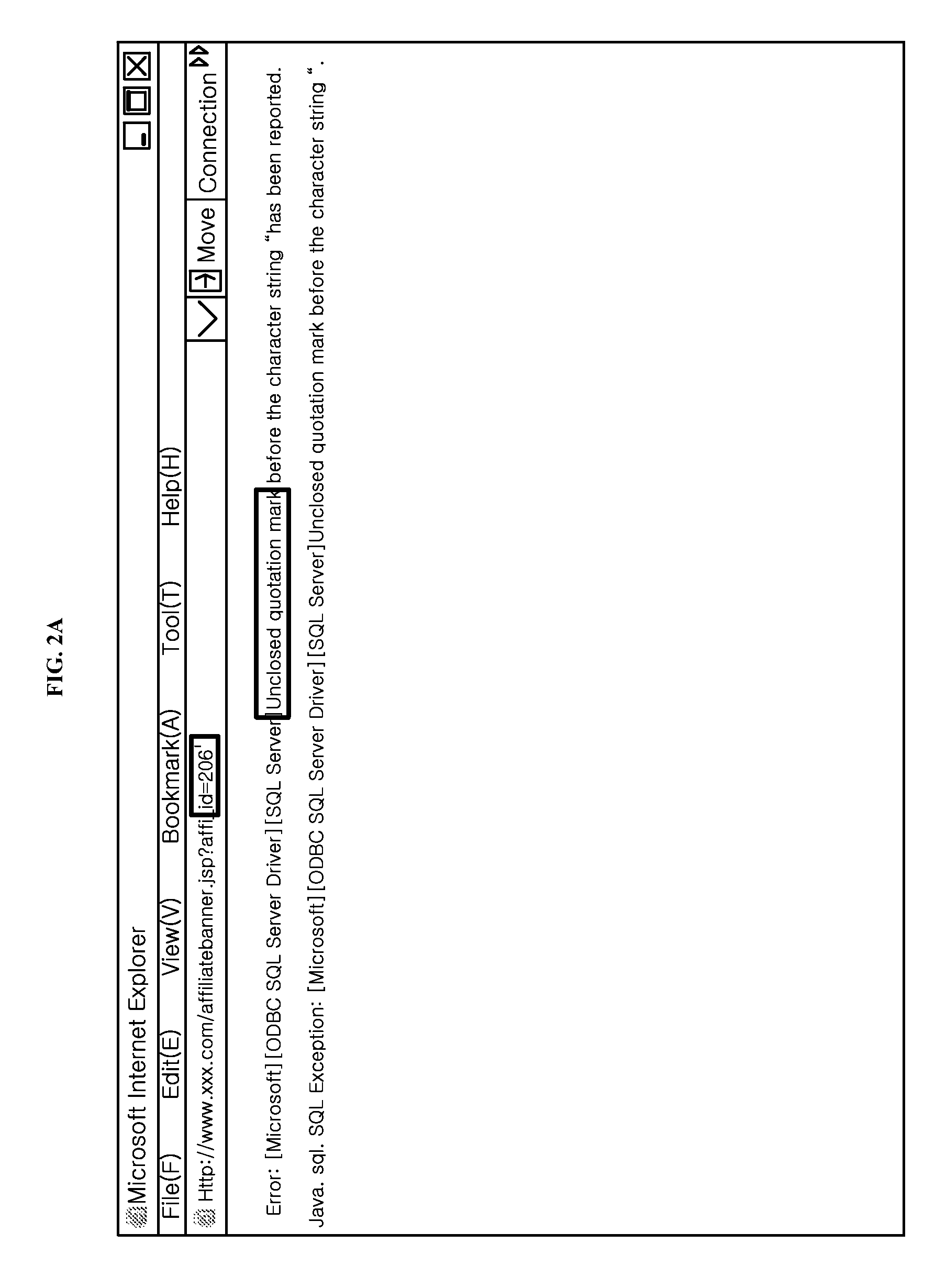
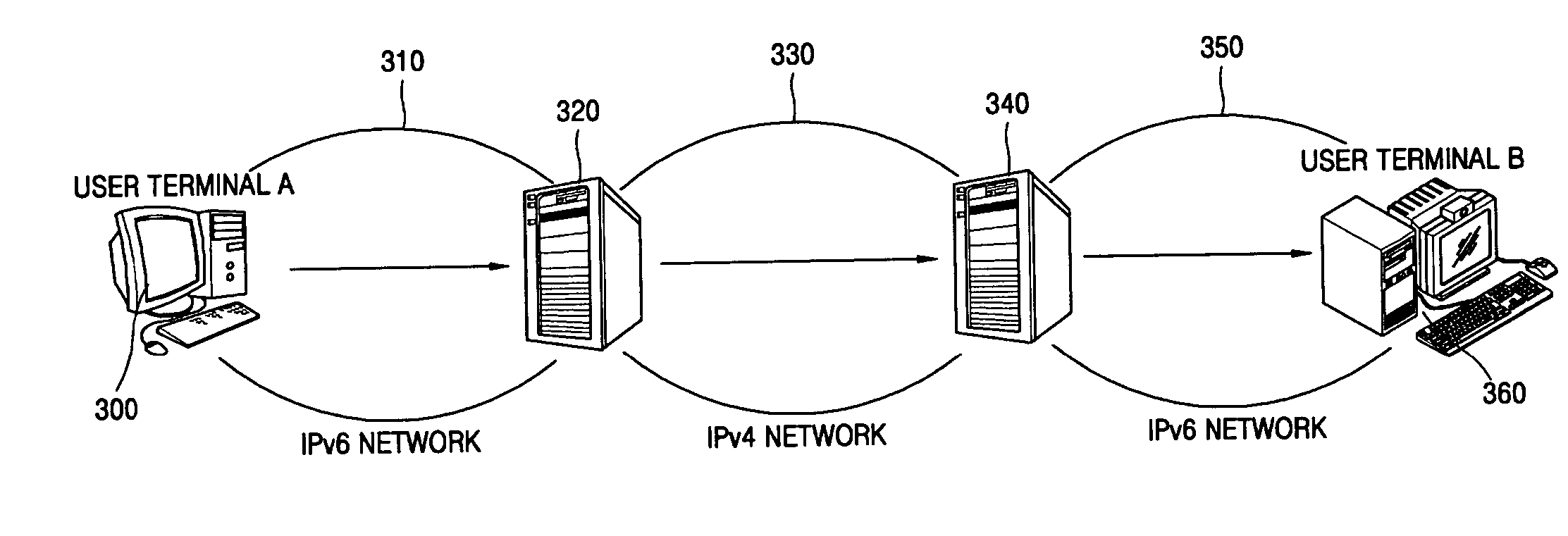
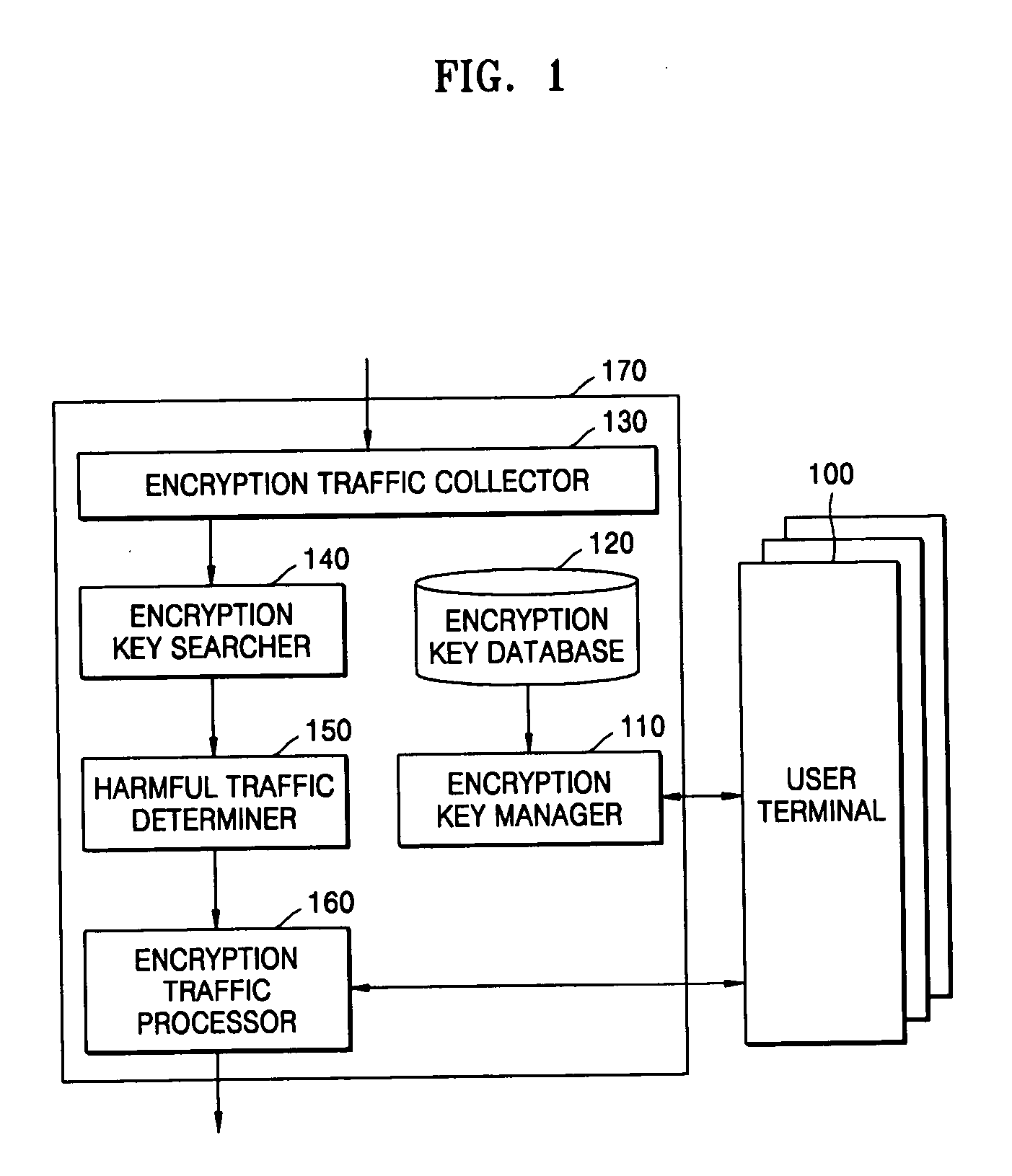
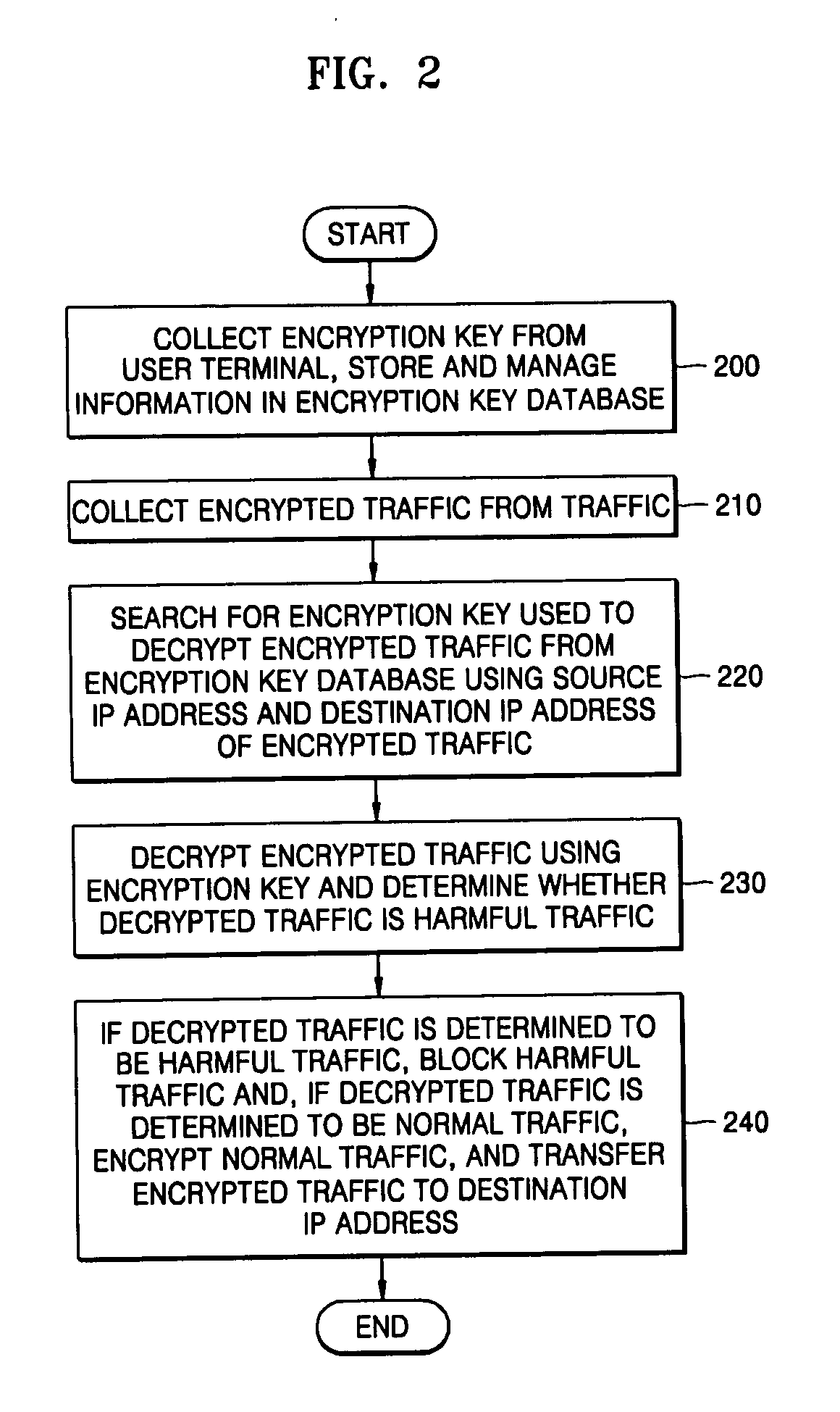
System and method for coping with encrypted harmful traffic in hybrid IPv4/IPv6 networks
InactiveUS20060137011A1Key distribution for secure communicationMemory loss protectionMix networkIp address
Provided are a system and method for coping with encrypted harmful traffic in hybrid IPv4 / IPv6 networks. The system includes: an encryption key manager collecting encryption key information from a user terminal connected to the hybrid IPv4 / IPv6 networks, and storing and managing the information in an encryption key database; an encryption traffic collector collecting encrypted traffic from traffic in the hybrid IPv4 / IPv6 networks; an encryption key searcher searching for an encryption key used to decrypt the encrypted traffic from the encryption key database using a source IP address and a destination IP address of the encrypted traffic; a harmful traffic determiner decrypting the encrypted traffic using the encryption key and determining whether the decrypted traffic is harmful traffic; and an encryption traffic processor, if the decrypted traffic is determined to be harmful traffic, blocking the harmful traffic and, if the decrypted traffic is determined to be normal traffic, encrypting the normal traffic, and transferring the encrypted traffic to a user terminal corresponding to the destination IP address, thereby detecting and blocking an attack pattern using the encrypted harmful traffic in hybrid IPv4 / IPv6 networks which cannot be detected by a conventional firewall system and more effectively protecting the networks.
Owner:ELECTRONICS & TELECOMM RES INST
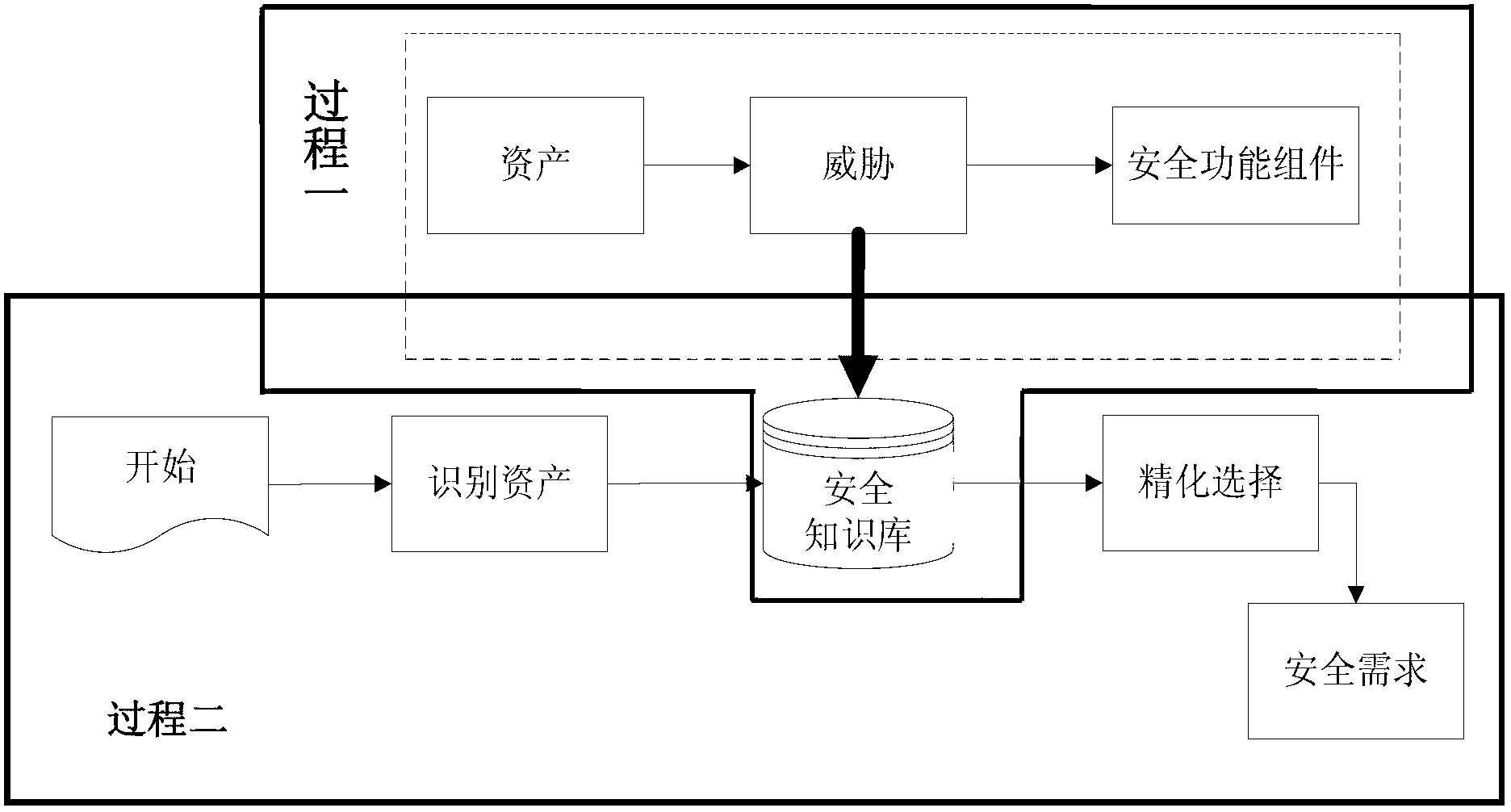
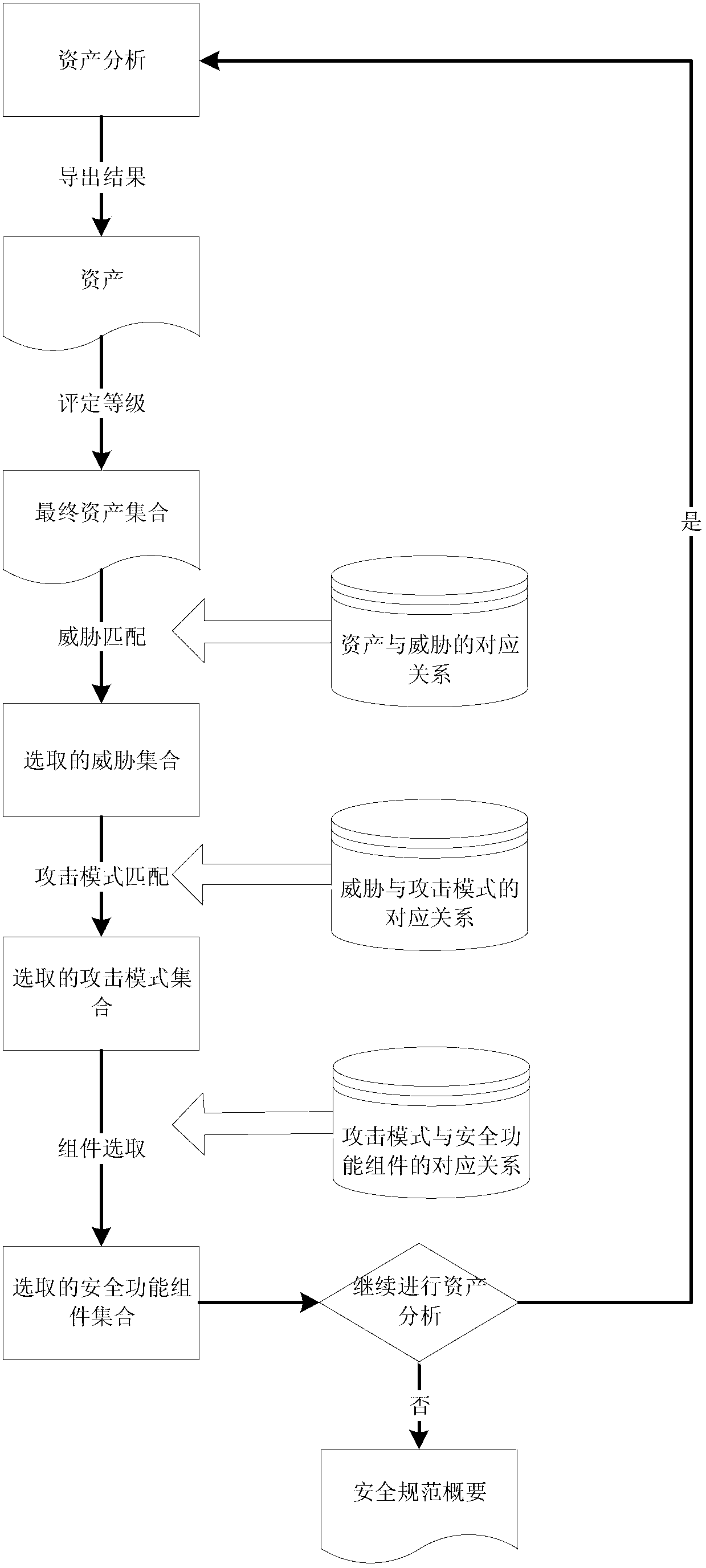
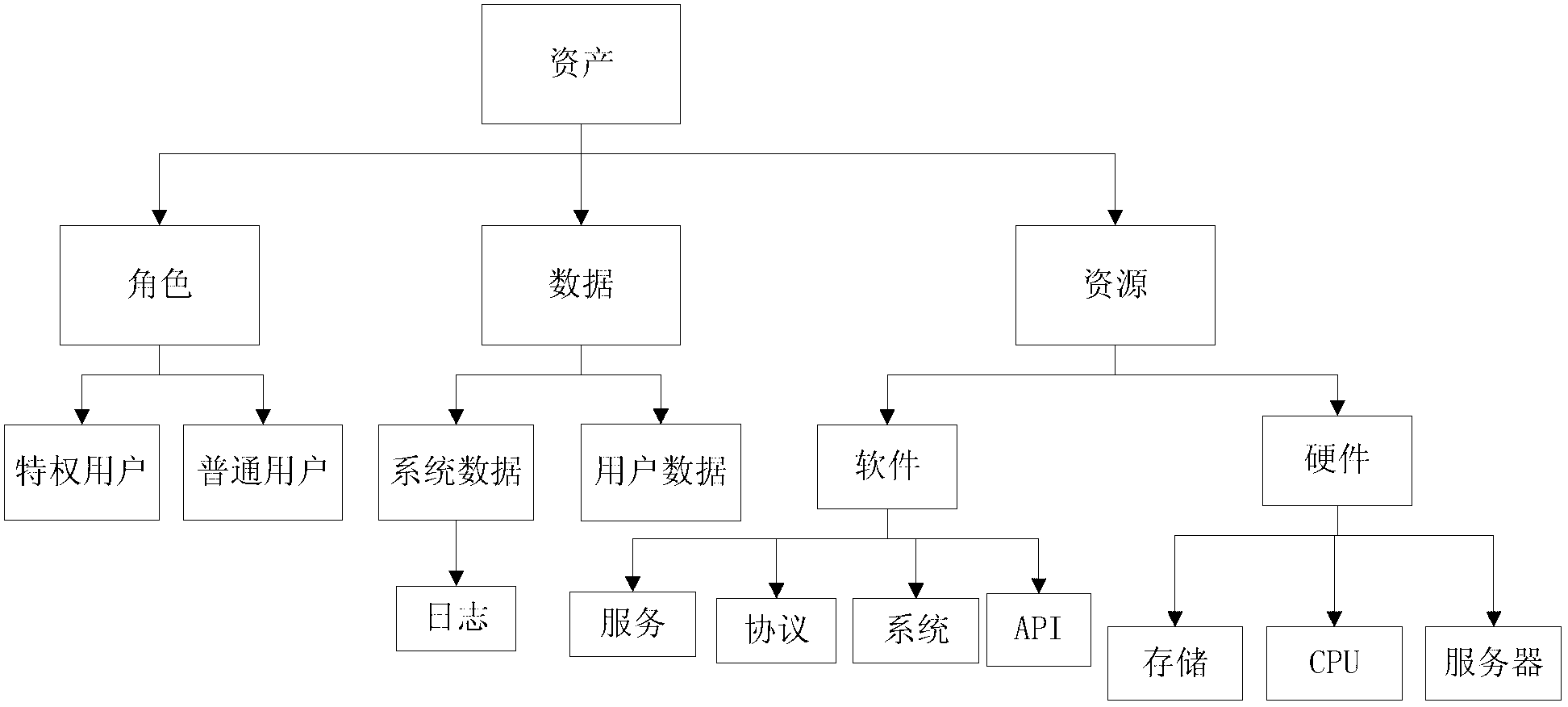
System-asset-based software security requirement analysis method
InactiveCN102799834AImprove development efficiencyImprove securityComputer security arrangementsRequirements analysisSystem development
The invention discloses a system-asset-based software security requirement analysis method. The method comprises the following steps of: 1, establishing the corresponding relation between system asset categories and security functional components, and the corresponding relation between assets and threats which may appear among the security functional components, constructing a security knowledge library, classifying system assets, threats and attack modes, and establishing the corresponding relation so as to ensure that the corresponding security components can be determined from the system assets; and 2, acquiring the corresponding security functional components in the security knowledge library aiming at the concrete system development according to the system assets determined by requirement personnel, performing refined selection by security requirement analysts in consideration of concrete technologies and security policies, and describing the finally selected security functional components into a security profile specification. Compared with the prior art, the method has the advantages that requirement analysts who have inadequate security knowledge can quickly perform security requirement analysis, the difficulty of the analysis of security functional requirements is effectively reduced, and the development cost of security requirements is reduced.
Owner:TIANJIN UNIV
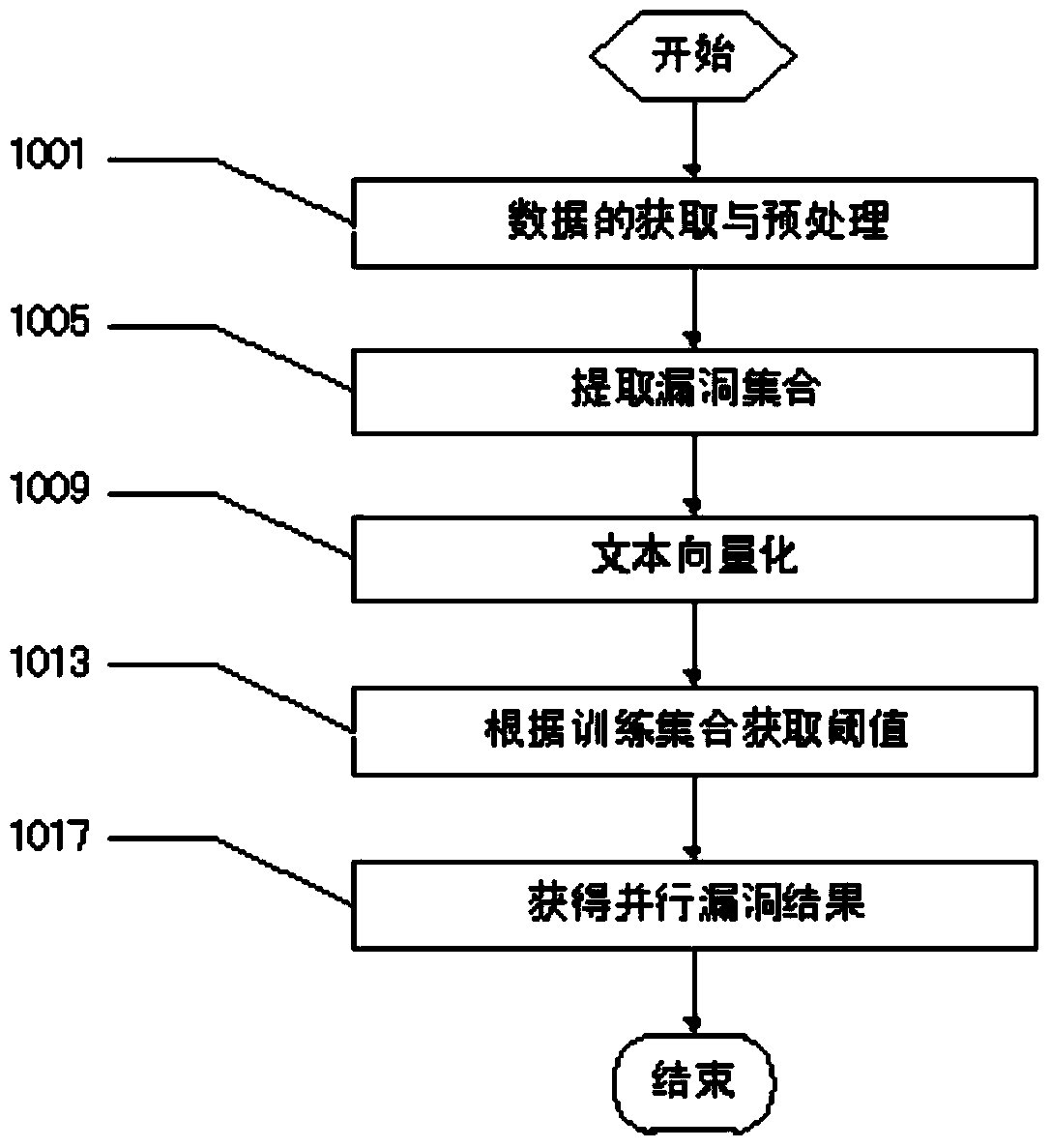
Parallel vulnerability mining method based on open source library and text mining
ActiveCN104166680AImprove intelligenceImprove automationComputer security arrangementsSpecial data processing applicationsInformation repositoryText mining
The invention relates to a parallel vulnerability mining method based on an open source library and test mining, and belongs to the technical field of computer information safety. The parallel vulnerability mining method comprises the steps that vulnerability data are obtained from the open source library and pre-processed, a vulnerability set is extracted, text vectorization is conducted, the threshold is calculated and parallel vulnerabilities are discovered. The parallel vulnerability mining method has the advantages that on the basis of the open source library, relevant vulnerability information in the same attack mode is extracted, and therefore potential parallel relationships between the vulnerabilities can be analyzed conveniently; text description information of the vulnerabilities are vectorized, and therefore a computer system can conduct intelligent processing on vulnerability recording data conveniently; the method differs from query on the basis of keyword matching in that the similarity between the vulnerabilities is studied according to the threshold obtained through a training set; the parallel relationships between the vulnerabilities can be calculated, so that when it is found that one vulnerability is utilized, the other parallel vulnerabilities are made up rapidly, therefore, the vulnerability of a whole network is made up, the defense capacity is enhanced and great significance for information safety is achieved.
Owner:CHINA INFORMATION TECH SECURITY EVALUATION CENT
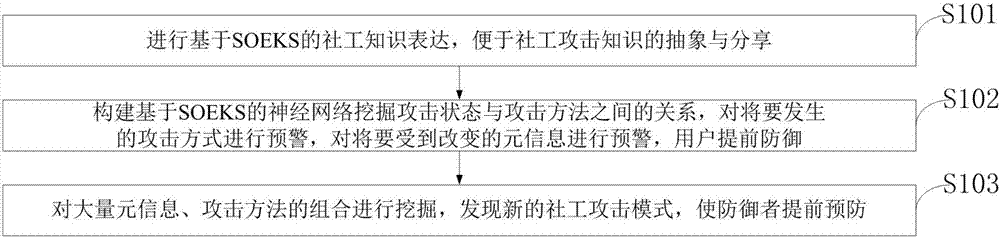
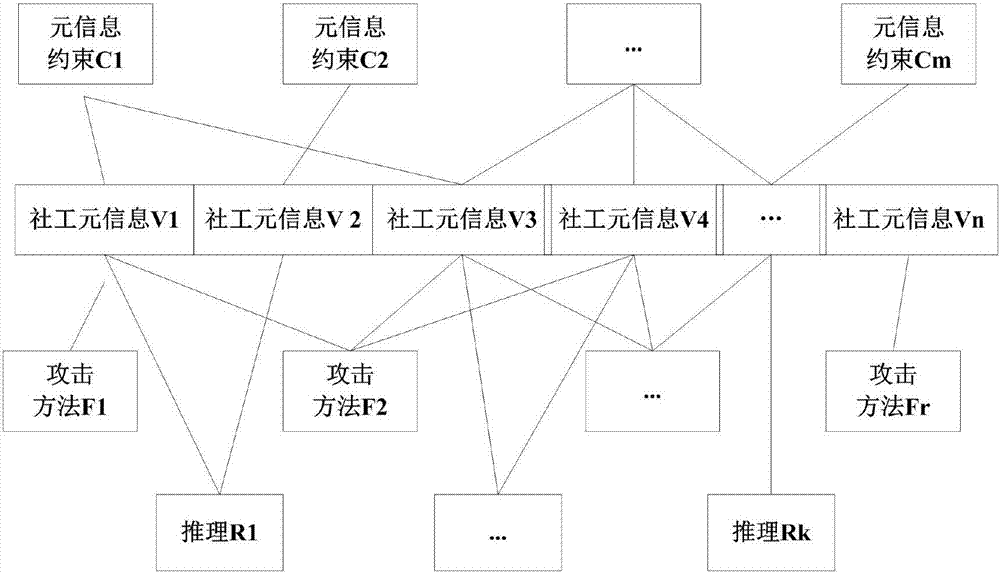
Social worker attack knowledge representation and excavation method based on SOEKS
ActiveCN107220541AEasy to shareReduce dependenceData processing applicationsPlatform integrity maintainanceNerve networkInternet privacy
The invention belongs to the technical field of network space security and discloses a social worker attack knowledge representation and excavation method based on an SOEKS. The method includes the steps that social worker knowledge representation based on the SOEKS is designed, and the social worker attack knowledge can be abstracted and shared; the relationship between neutral network excavation attack states and attack methods based on the SOEKS is established, an attack about to occur is subjected to early warning, meta-information about to be changed is subjected to early warning, and a user is reminded of defense in advance; combinations of a large quantity of meta-information and attack methods are excavated, and a new social worker attack mode is discovered. Social worker attacks are subjected to abstract knowledge representation for the first time; abstract social worker attack information based on the SOEKS is conveniently shared and subjected to experience accumulation; through mode excavation of the relationship between the social worker attack states and attack methods, attack steps can be predicted, defense weak links can be disclosed, existing defense is theoretically guided, and dependence on experience is reduced.
Owner:CHENGDU UNIV OF INFORMATION TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com