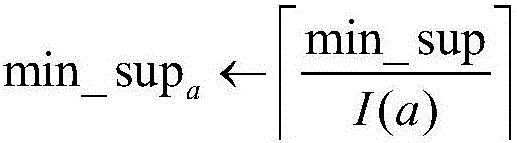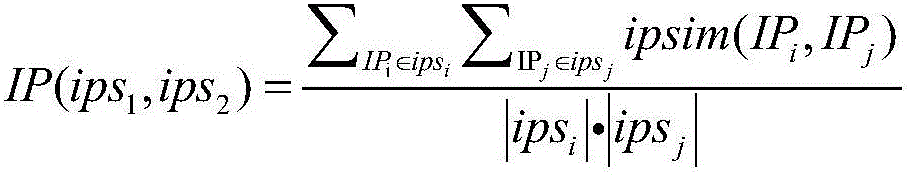Attack mode detection method based on event slide window
A pattern detection and sliding window technology, which is applied in the field of attack pattern detection based on event sliding windows, can solve the lack of comprehensive analysis of log data, the inability to perform collection and analysis tasks well, and the inability to respond to log analysis and security protection in a timely manner, etc. problem, to achieve the effect of improving accuracy and speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
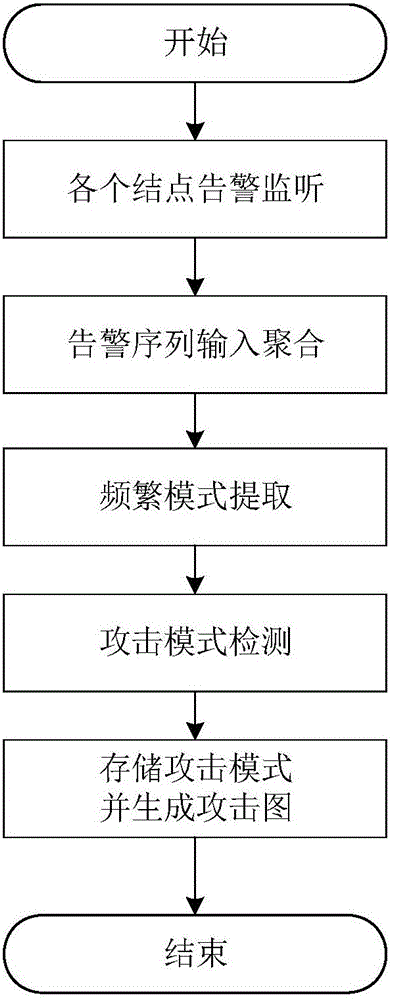
[0021] Such as figure 1 Shown the present invention is based on the attack mode detection method of event sliding window, comprises:
[0022] S1: Alarm aggregation: Since the detection environment is a distributed cluster, and each application corresponds to an alarm source, the collection, preprocessing, and compression are completed during the aggregation process. The steps are:
[0023] S11: By setting agents on different alarm sources, each agent perceives the information generated by the corresponding alarm source, and monitors it according to a certain ratio. If a new alarm is detected, it will be sent to the transmission queue. Use the open source technology of Flume log collection to effectively configure the collection agent source, transmission pipeline and collection settlement.
[0024] S12: Perform information transformation on the generated alarm information, convert it into an alarm log, and then transmit it.
[0025] S13: Normalize the data format of the alar...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com