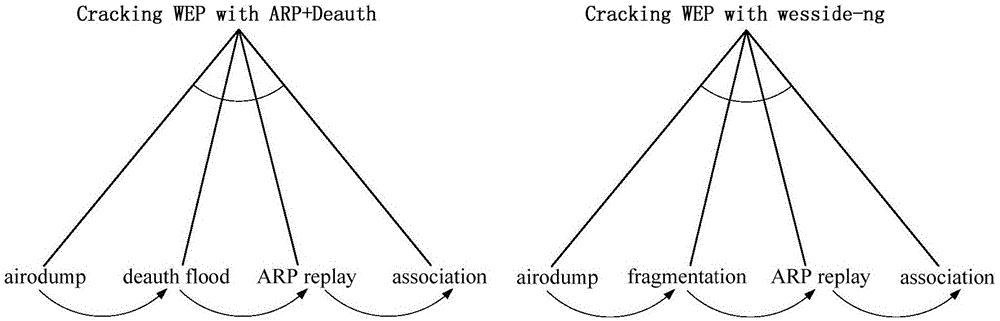
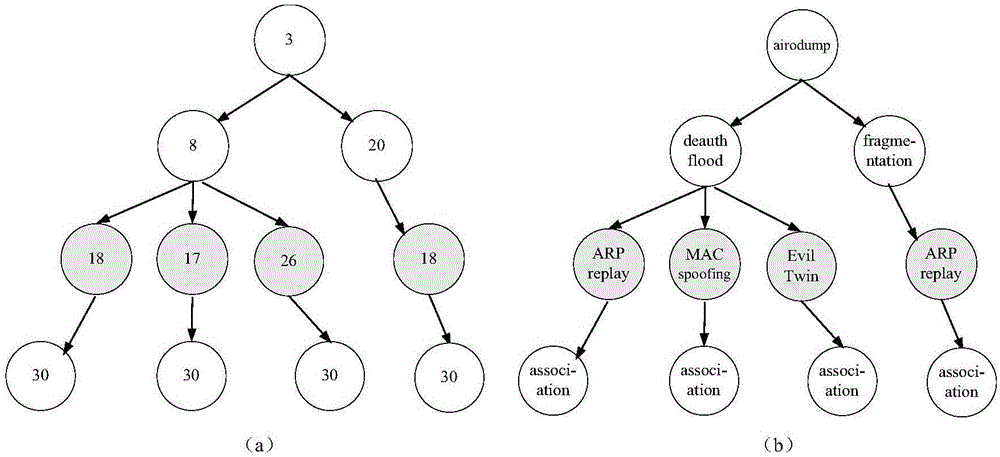
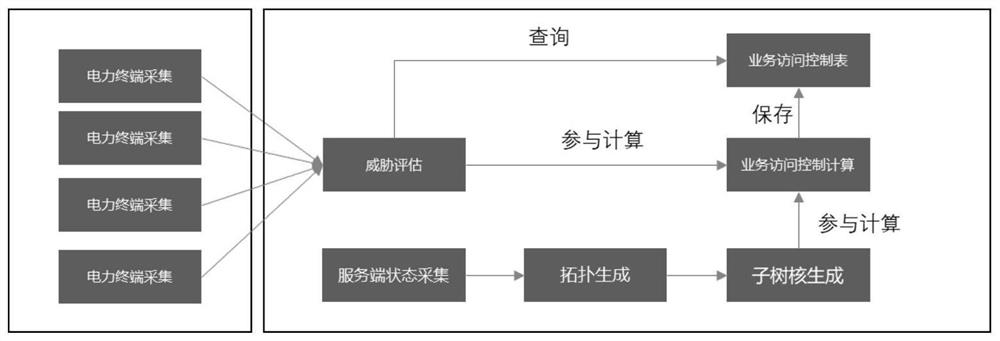
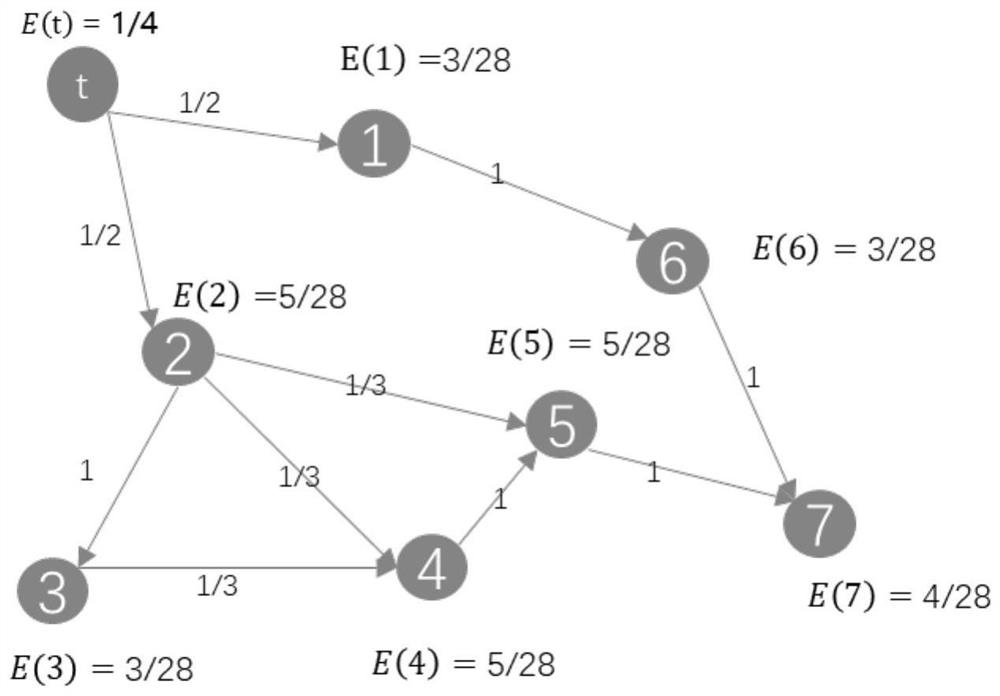
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
57 results about "Attack tree" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
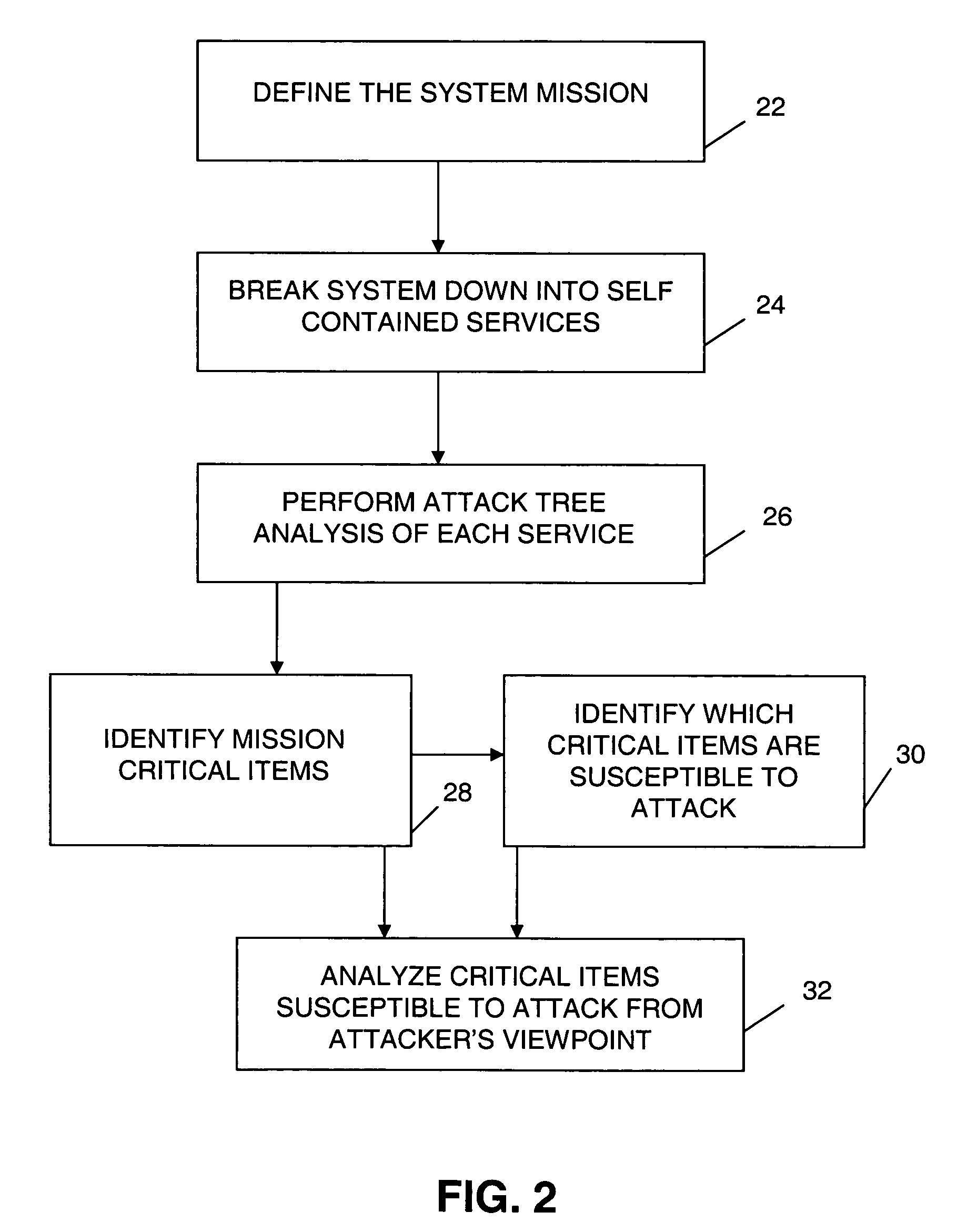
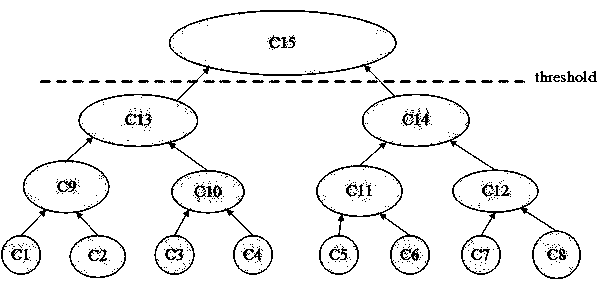
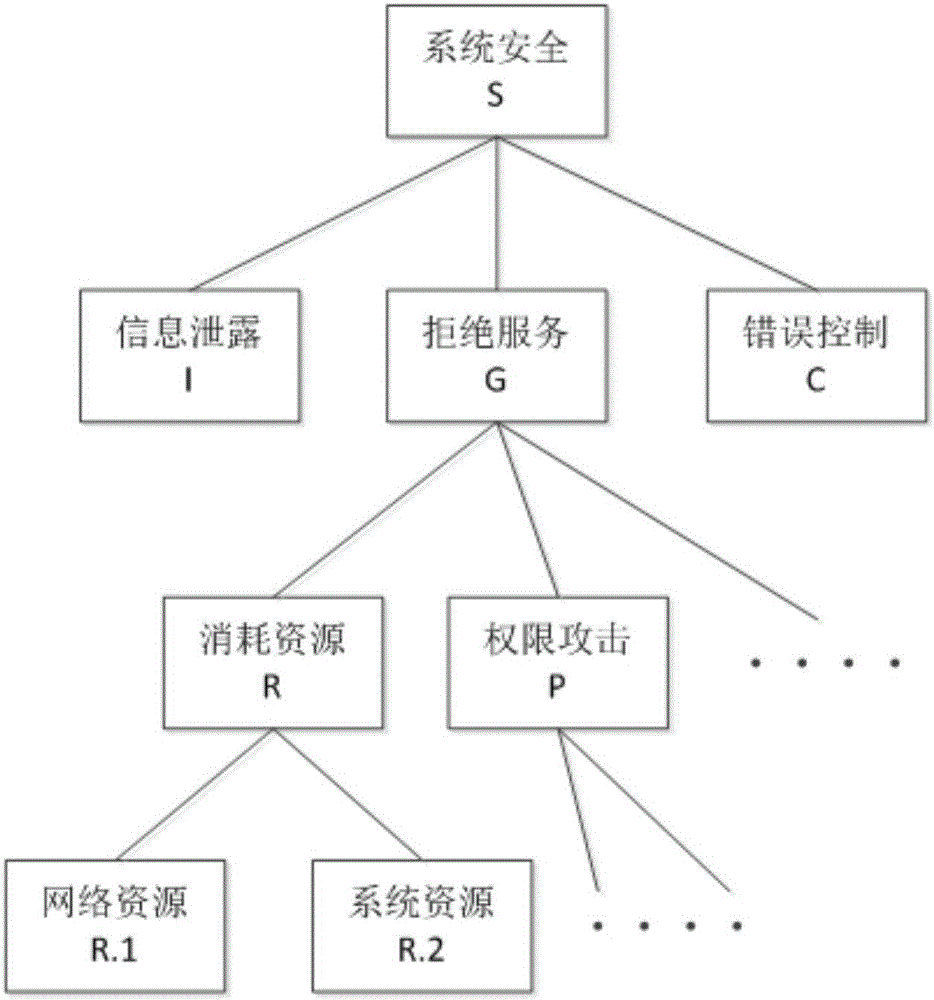
Attack trees are conceptual diagrams showing how an asset, or target, might be attacked. Attack trees have been used in a variety of applications. In the field of information technology, they have been used to describe threats on computer systems and possible attacks to realize those threats. However, their use is not restricted to the analysis of conventional information systems. They are widely used in the fields of defense and aerospace for the analysis of threats against tamper resistant electronics systems (e.g., avionics on military aircraft). Attack trees are increasingly being applied to computer control systems (especially relating to the electric power grid ). Attack trees have also been used to understand threats to physical systems.
System and Method for Distributed Denial of Service Identification and Prevention
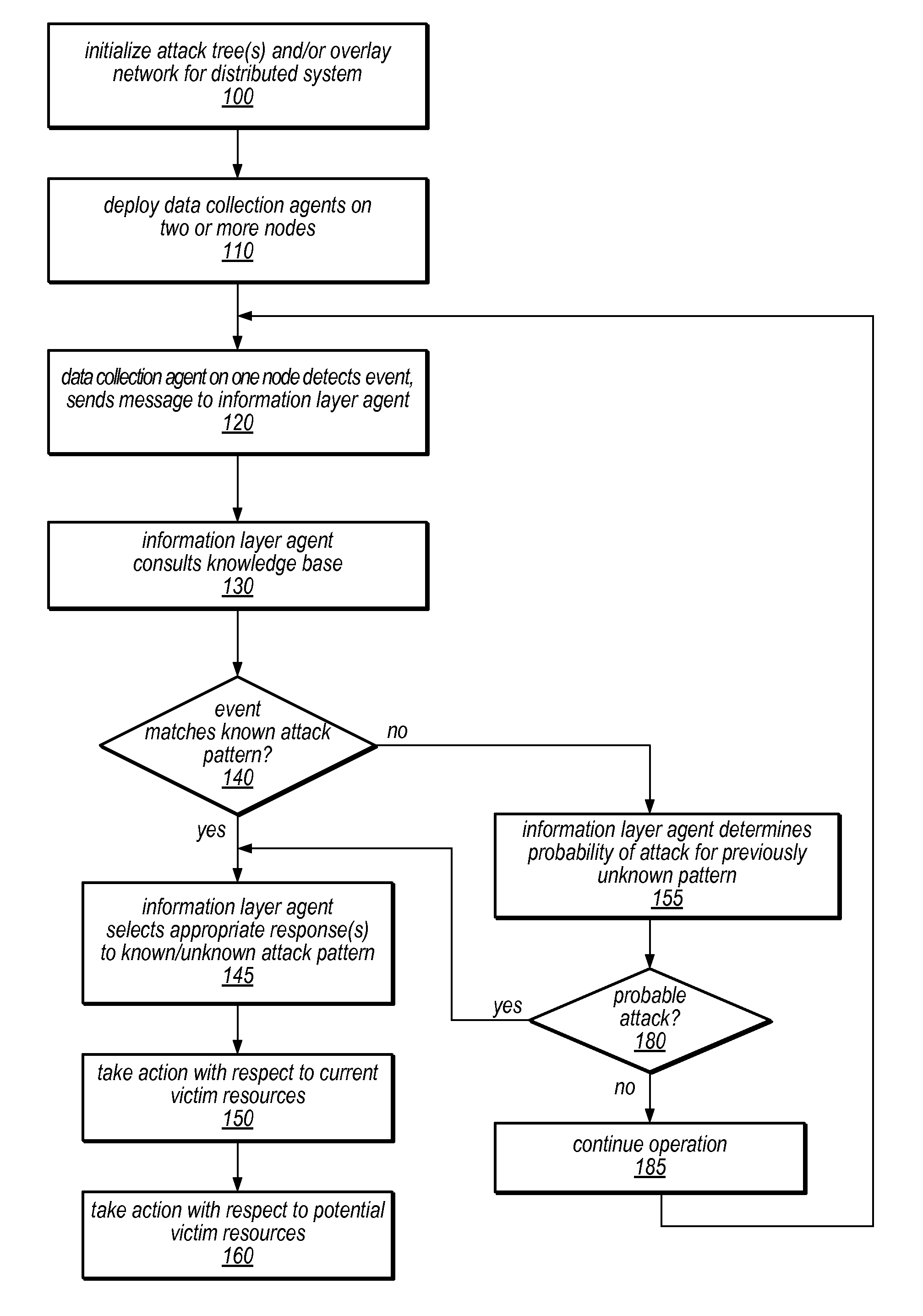
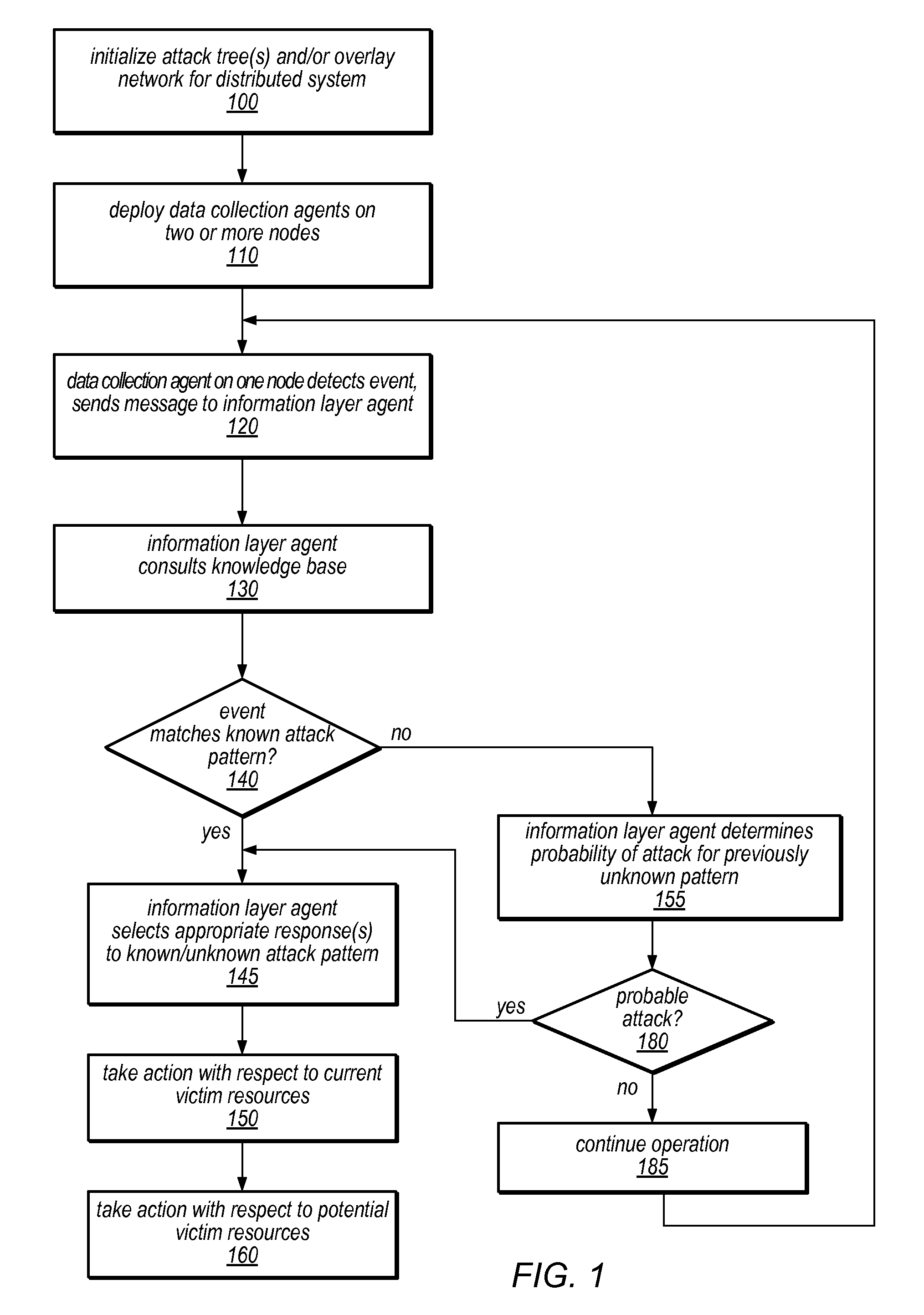
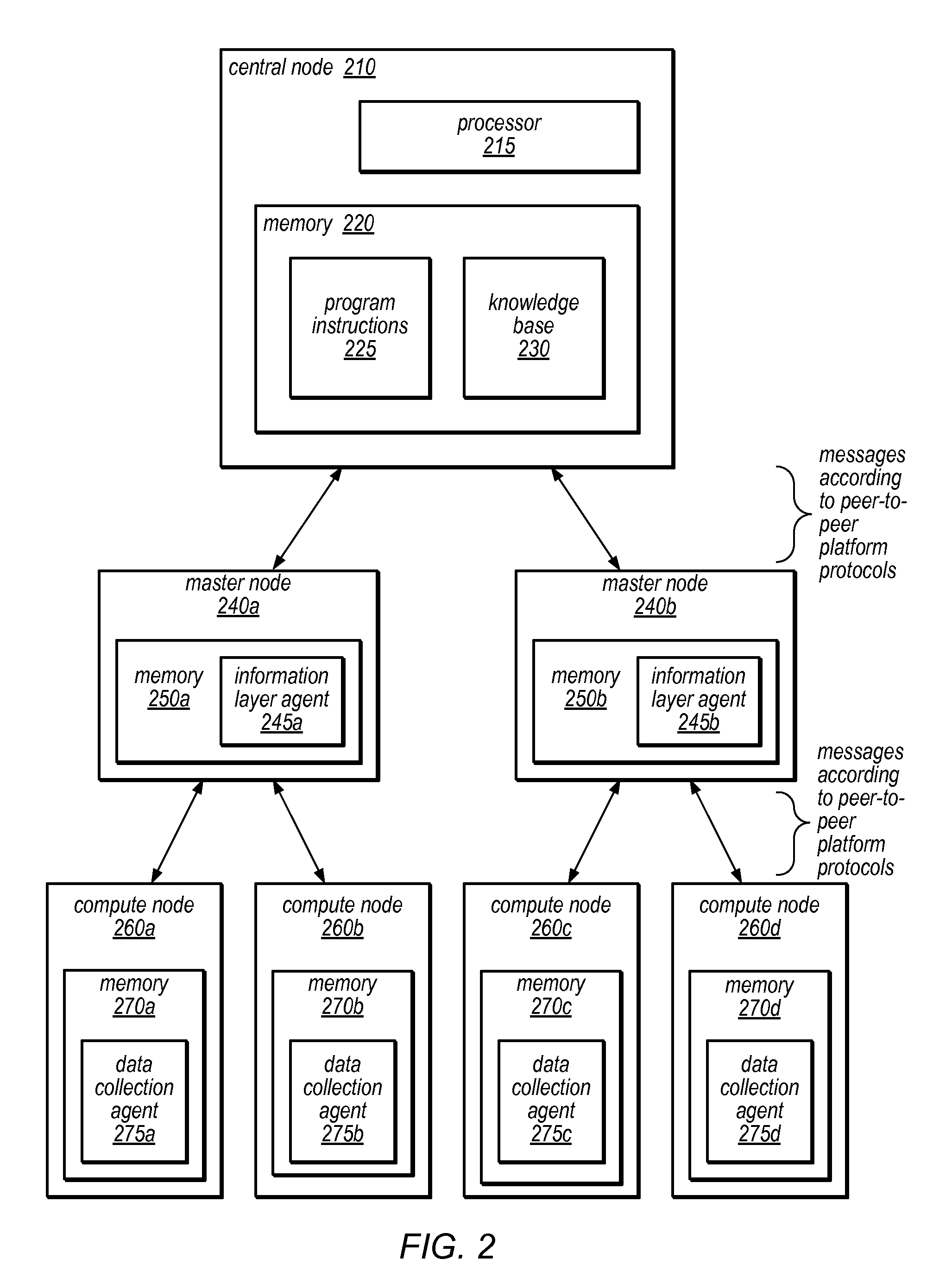
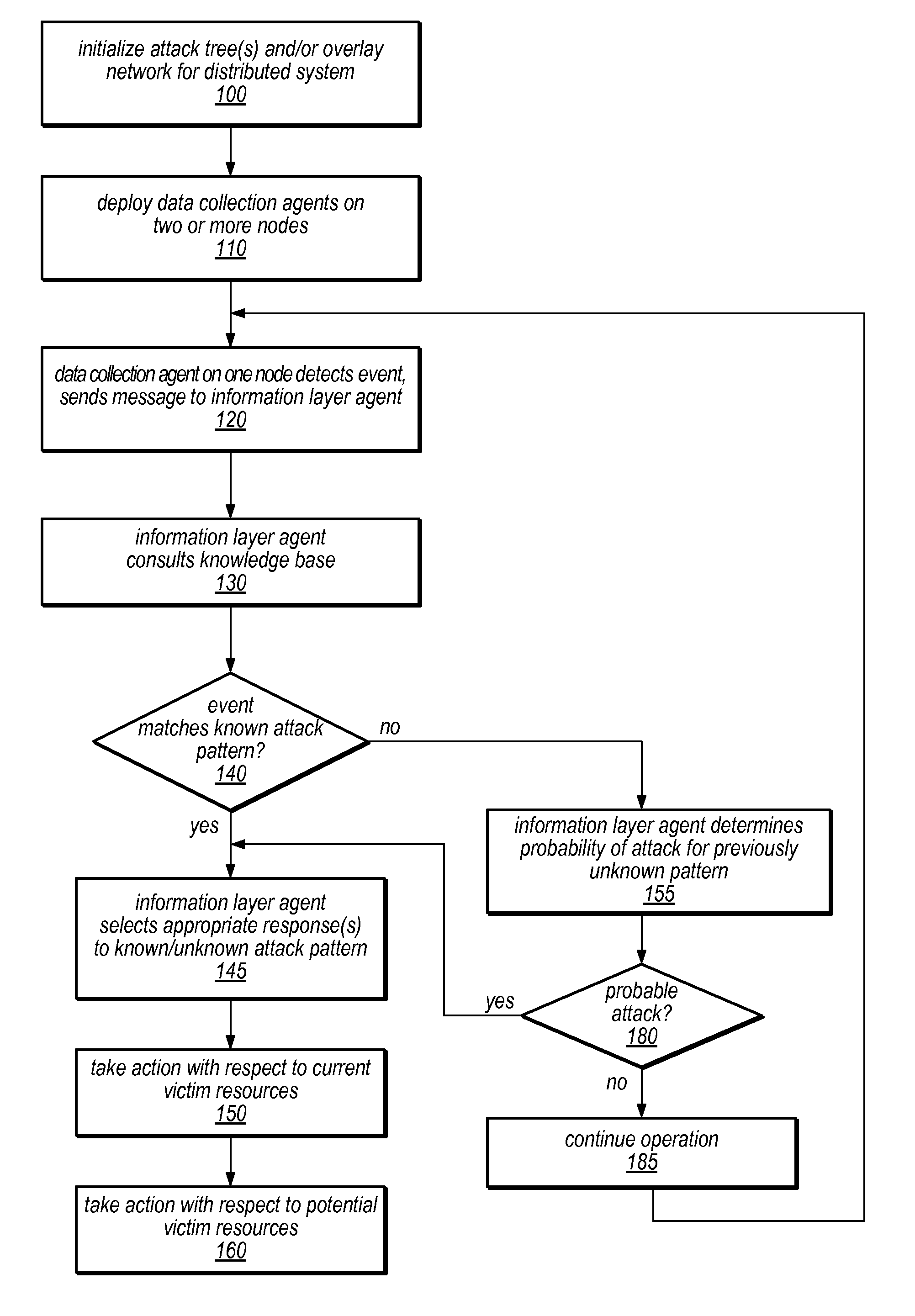
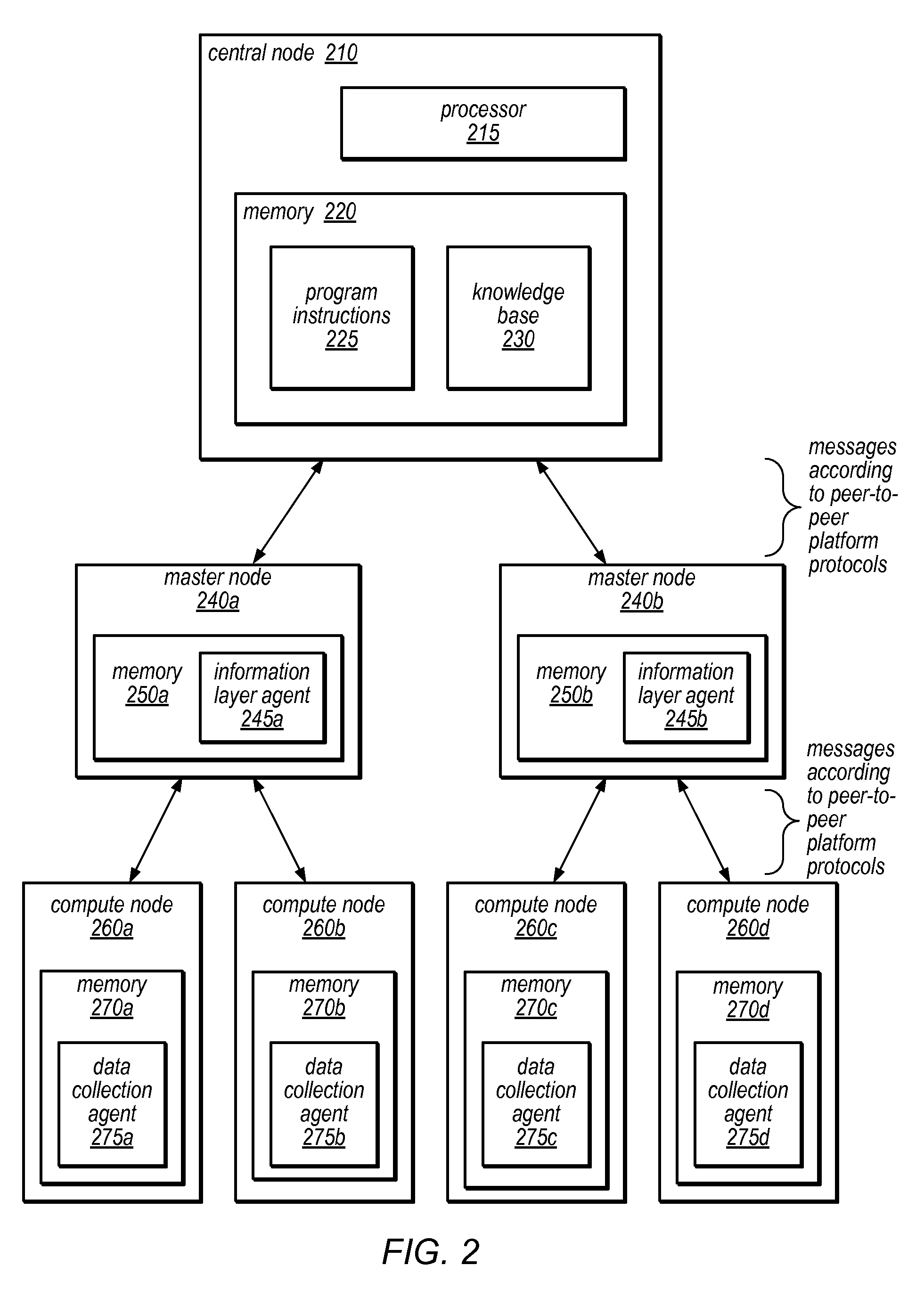
Systems and methods for discovery and classification of denial of service attacks in a distributed computing system may employ local agents on nodes thereof to detect resource-related events. An information later agent may determine if events indicate attacks, perform clustering analysis to determine if they represent known or unknown attack patterns, classify the attacks, and initiate appropriate responses to prevent and / or mitigate the attack, including sending warnings and / or modifying resource pool(s). The information layer agent may consult a knowledge base comprising information associated with known attack patterns, including state-action mappings. An attack tree model and an overlay network (over which detection and / or response messages may be sent) may be constructed for the distributed system. They may be dynamically modified in response to changes in system configuration, state, and / or workload. Reinforcement learning may be applied to the tuning of attack detection and classification techniques and to the identification of appropriate responses.
Owner:ORACLE INT CORP
Network security planning architecture
ActiveUS20050138413A1Expand accessBroaden their knowledgeMemory loss protectionDigital data processing detailsForward chainingAttack tree
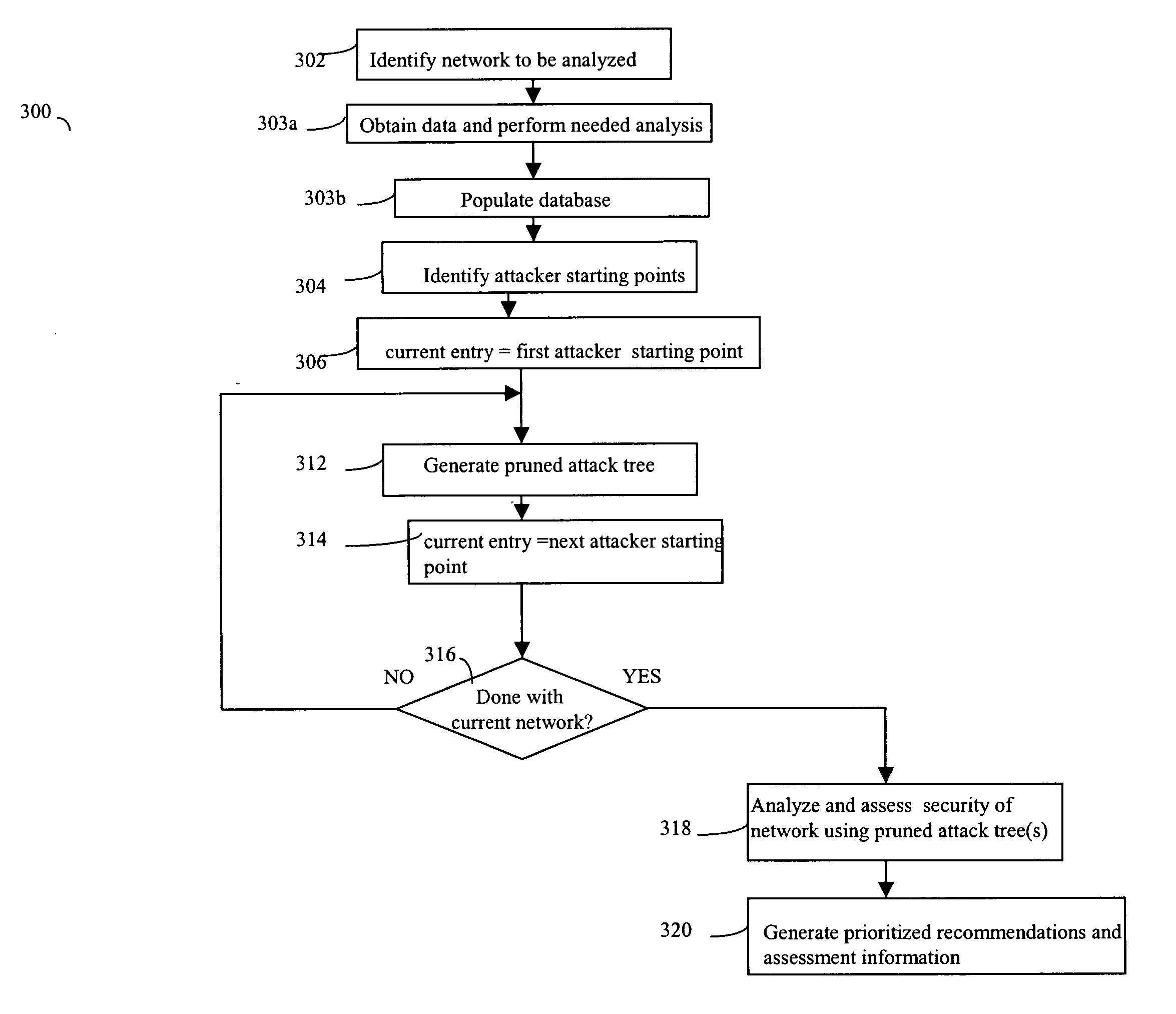
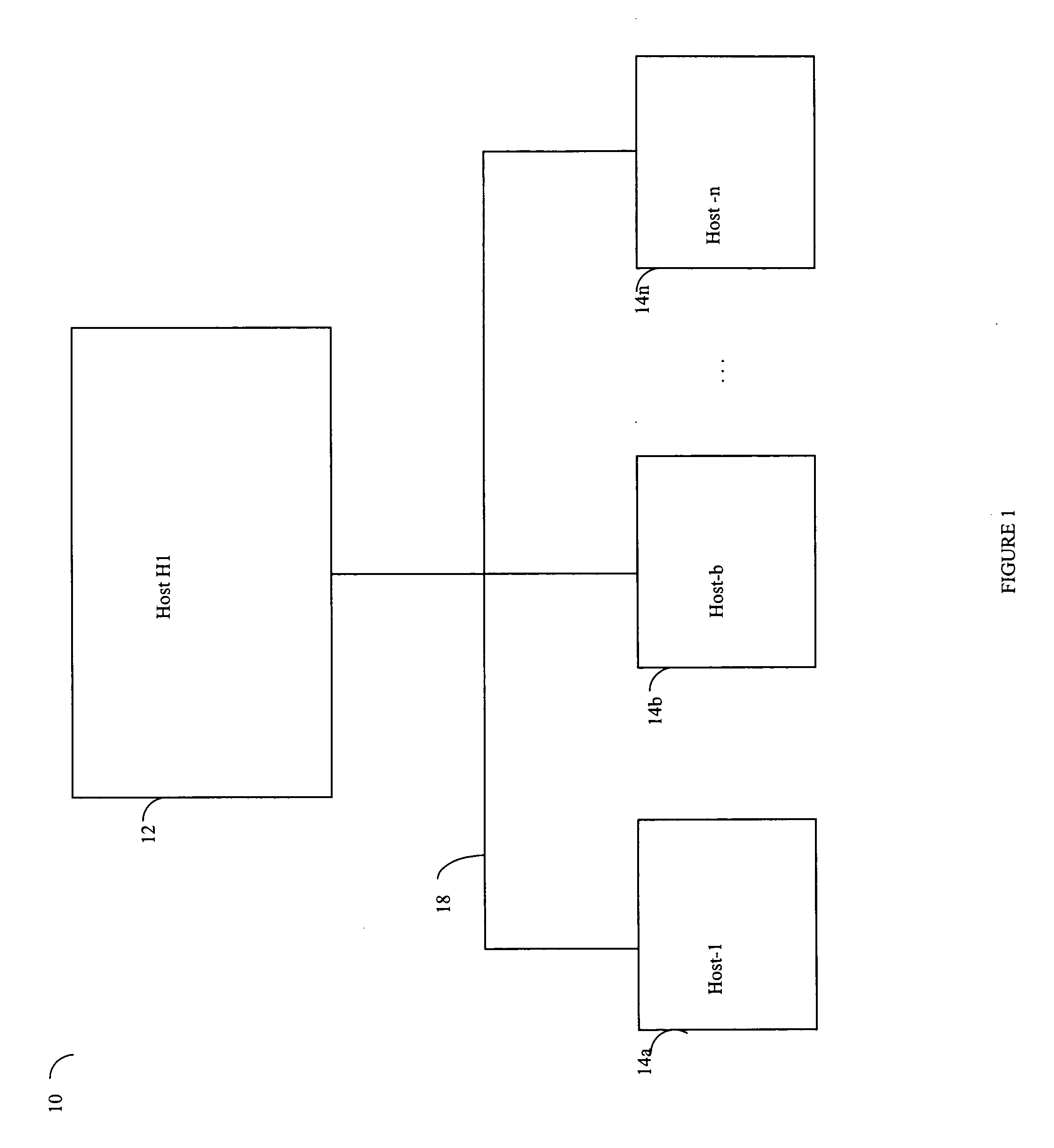
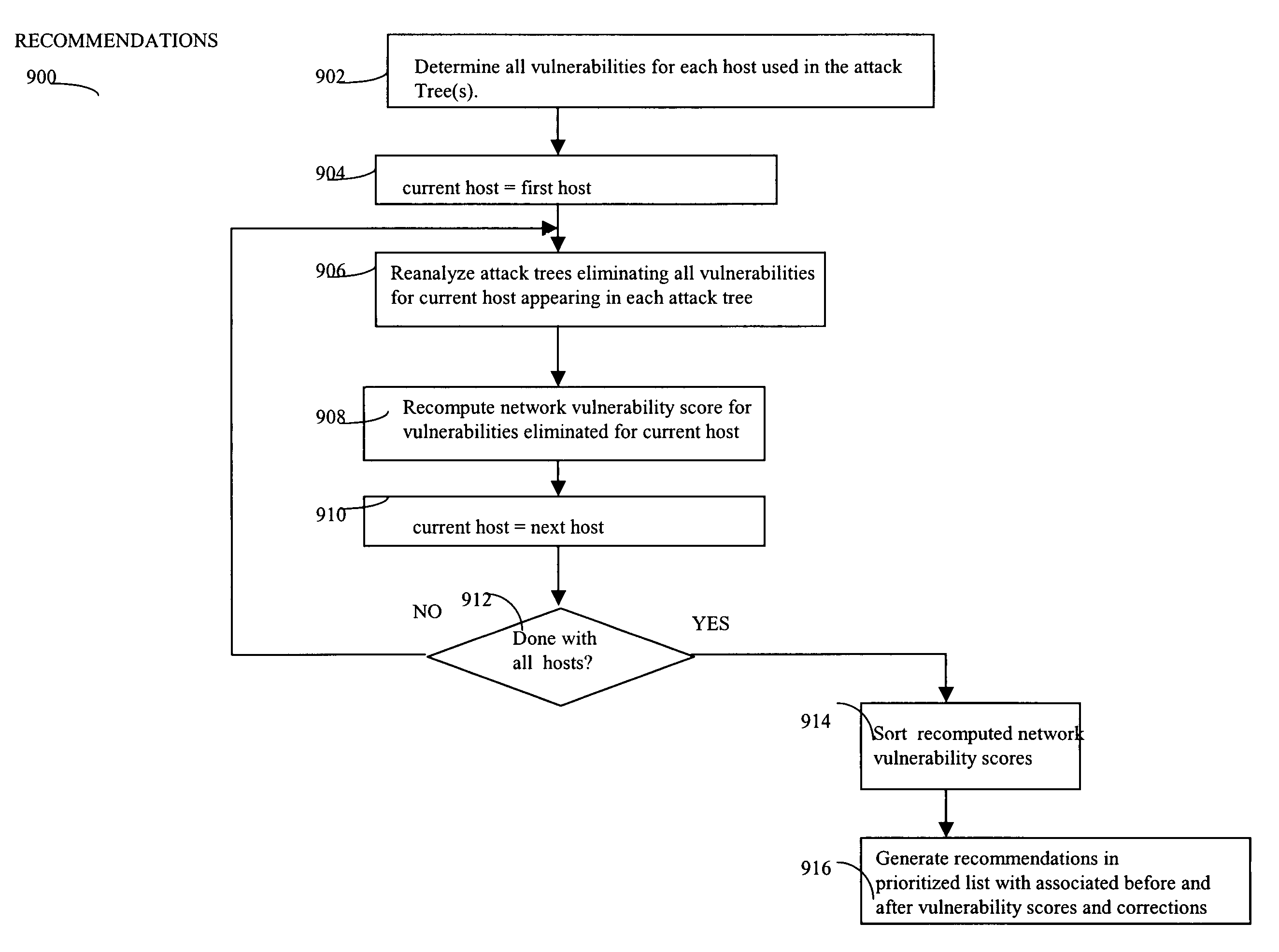
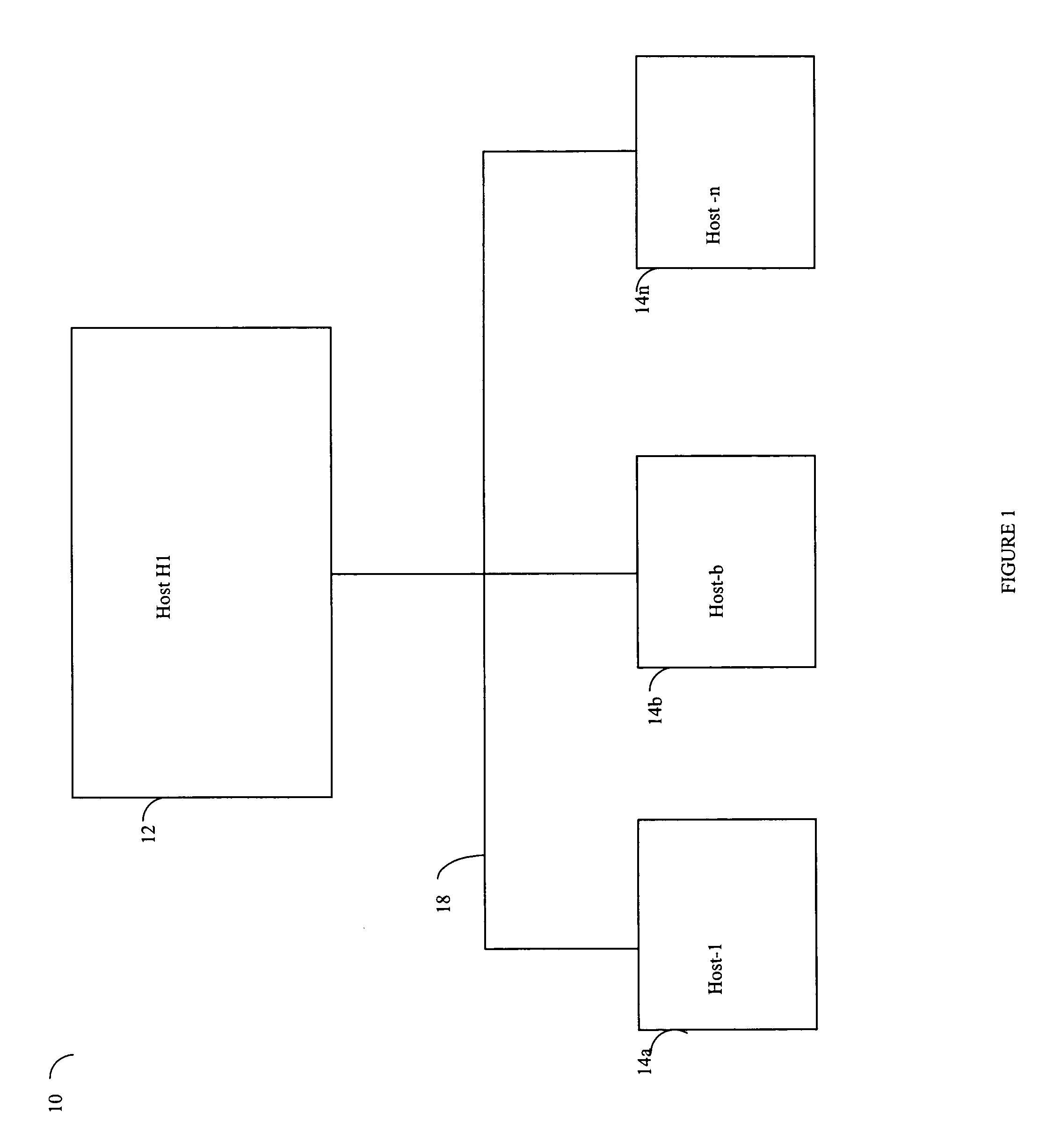
Described are techniques used for assessing the security of a network. Pruned attack trees are generated using a forward chaining, breadth-first technique representing the attack paths of a possible attacker in the network. A vulnerability score is determined for each network and attacker starting point using attack loss values assigned to each host and information extracted from the attack tree(s) concerning compromised hosts. Different hypothetical alternatives may be evaluated to improve security of the network and each alternative may be evaluated by recomputing the network vulnerability score and comparing the recomputed score to the original network vulnerability score. Also disclosed is a method for determining end-to-end connectivity of a network. The resulting end-to-end connectivity information is used in generating the pruned attack tree.
Owner:MASSACHUSETTS INST OF TECH
Network security planning architecture
ActiveUS7194769B2Memory loss protectionUnauthorized memory use protectionForward chainingAttack tree
Described are techniques used for assessing the security of a network. Pruned attack trees are generated using a forward chaining, breadth-first technique representing the attack paths of a possible attacker in the network. A vulnerability score is determined for each network and attacker starting point using attack loss values assigned to each host and information extracted from the attack tree(s) concerning compromised hosts. Different hypothetical alternatives may be evaluated to improve security of the network and each alternative may be evaluated by recomputing the network vulnerability score and comparing the recomputed score to the original network vulnerability score. Also disclosed is a method for determining end-to-end connectivity of a network. The resulting end-to-end connectivity information is used in generating the pruned attack tree.
Owner:MASSACHUSETTS INST OF TECH
System and method for distributed denial of service identification and prevention
Systems and methods for discovery and classification of denial of service attacks in a distributed computing system may employ local agents on nodes thereof to detect resource-related events. An information later agent may determine if events indicate attacks, perform clustering analysis to determine if they represent known or unknown attack patterns, classify the attacks, and initiate appropriate responses to prevent and / or mitigate the attack, including sending warnings and / or modifying resource pool(s). The information layer agent may consult a knowledge base comprising information associated with known attack patterns, including state-action mappings. An attack tree model and an overlay network (over which detection and / or response messages may be sent) may be constructed for the distributed system. They may be dynamically modified in response to changes in system configuration, state, and / or workload. Reinforcement learning may be applied to the tuning of attack detection and classification techniques and to the identification of appropriate responses.
Owner:ORACLE INT CORP
Method, device and system for determining safety event of electric power monitoring system
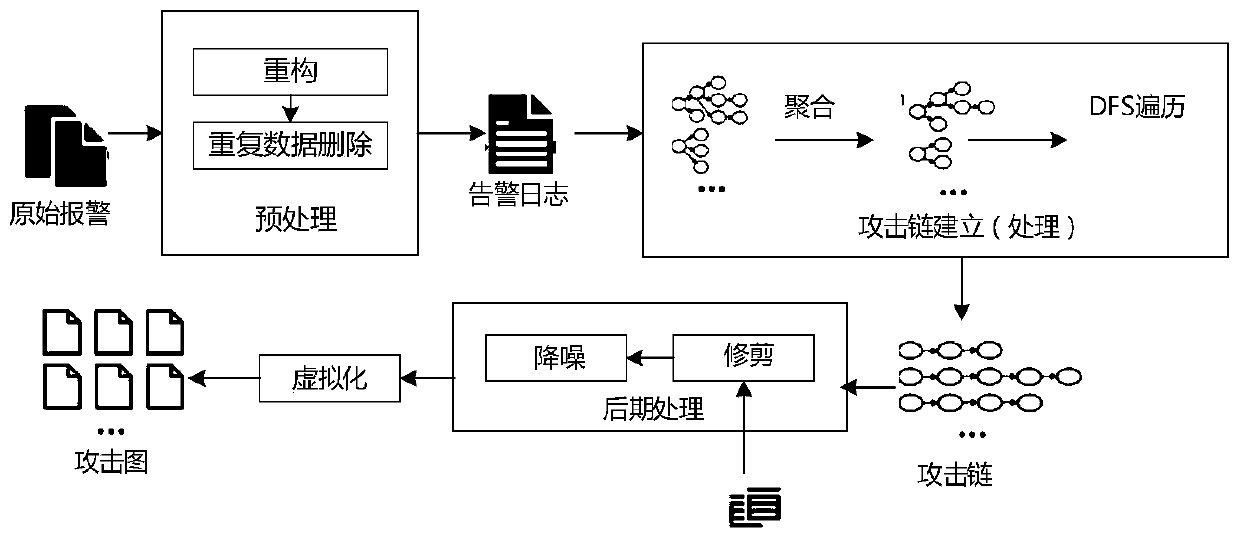
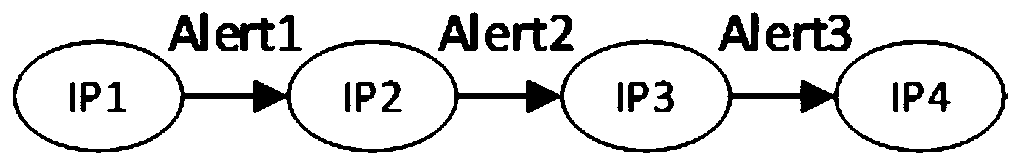
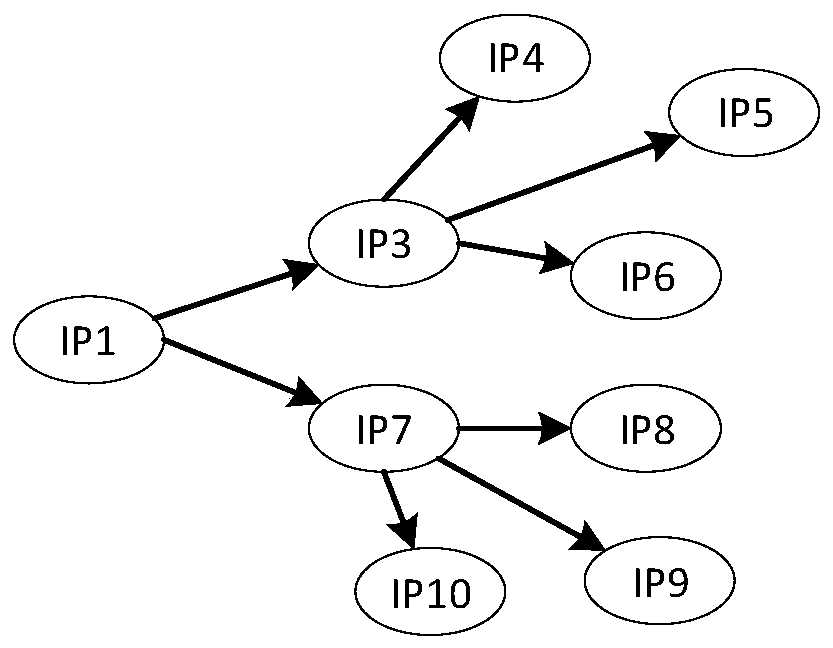
The invention discloses a method, a device and a system for determining a safety event of an electric power monitoring system, and the method comprises the steps: obtaining an alarm log which comprises a plurality of alarm records; performing tree diagram modeling on the alarm logs based on the correlation among the alarm records, and constructing an attack tree; performing aggregation processingon the attack tree to obtain an initial attack chain set; and performing pruning and noise reduction on each initial attack chain in the initial attack chain set to form a final attack chain set, anddetermining a power monitoring system security event. According to the method, the alarm data of the power monitoring system can be automatically and effectively analyzed, the attack event is extracted and presented in a visual mode, a network administrator is helped to know the network security state, a security disposal measure can be conveniently and timely taken, and the security of a network,data, equipment and the like is guaranteed.
Owner:STATE GRID CORP OF CHINA +6
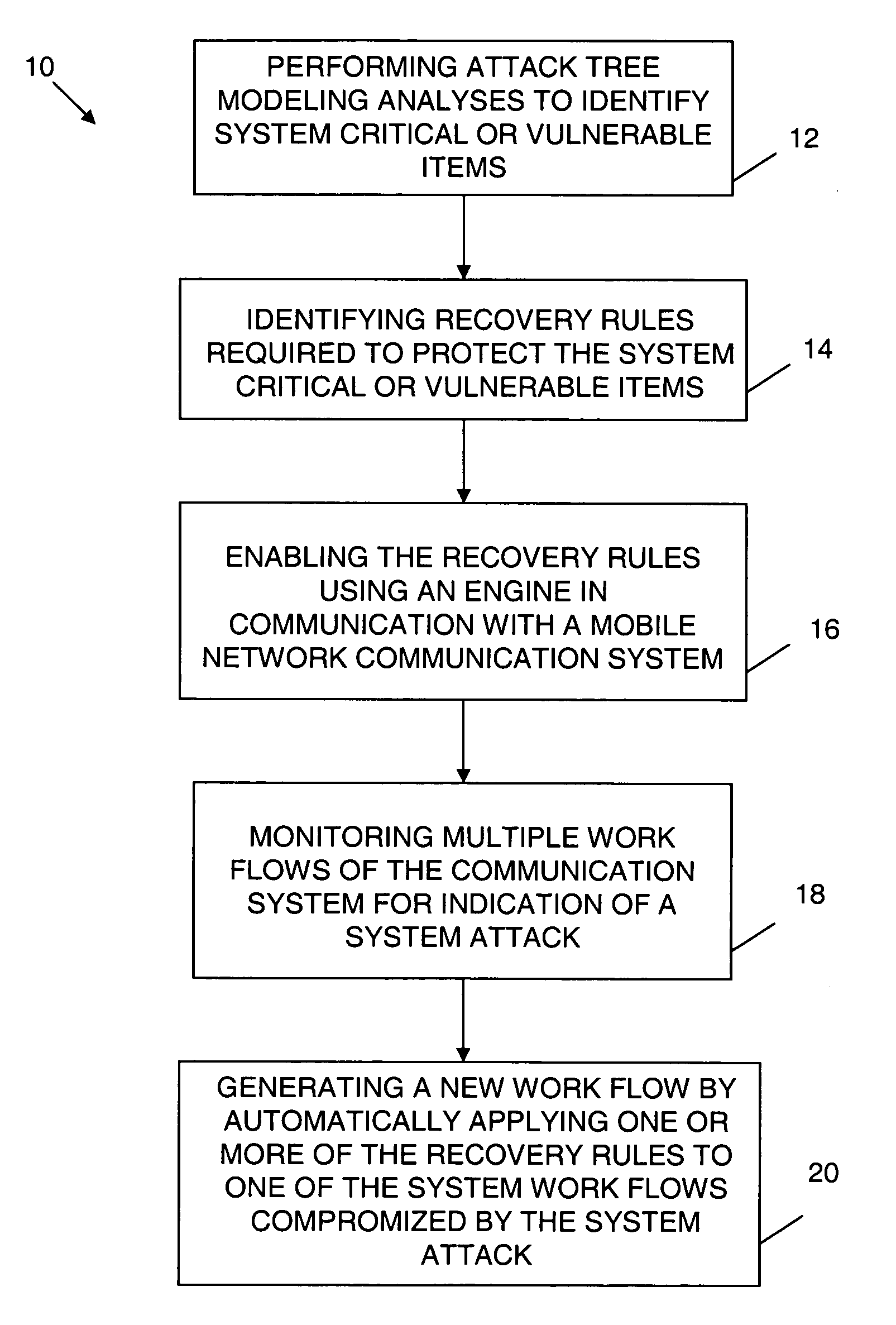
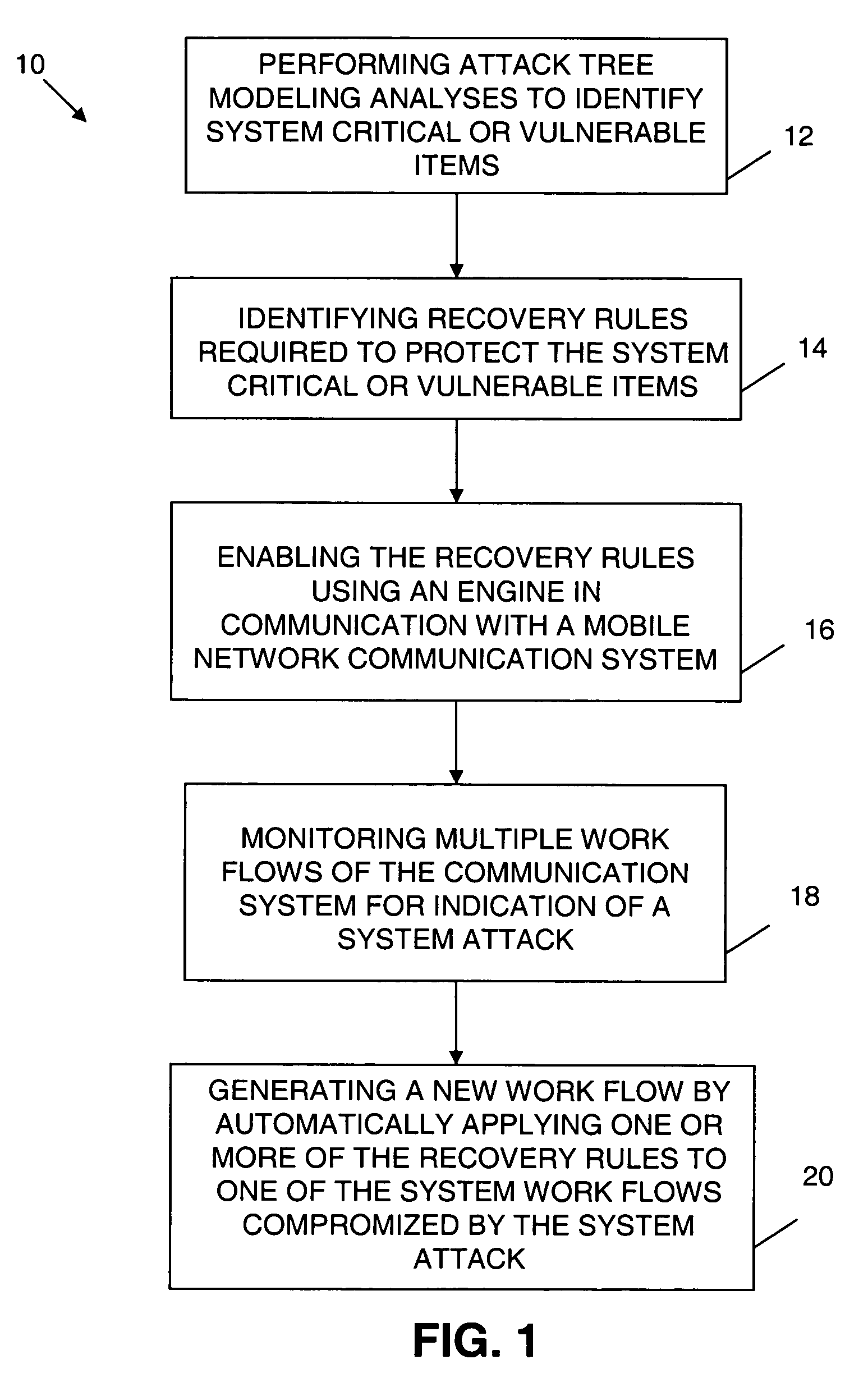
Mobile network dynamic workflow exception handling system
ActiveUS20060259341A1Promote recoveryImprove survivabilityDigital computer detailsResourcesNetwork communicationHandling system
An exception handling system and method are provided for dynamically recovering from a workflow exception occurring in a mobile network communication system. The system has multiple workflows and at least one mission critical item. An attack tree modeling analyses is performed to identify the mission critical item. Another operation includes writing a plurality of forward recovery rules to protect the mission critical item using a transaction datalog fragment of transaction logic. The recovery rules are enabled through an engine in communication with the mobile network communication system. The multiple workflows are monitored for indication of a system attack on any one of the multiple workflows. A new workflow is automatically generated upon detection of the system attack. The exception handling system is overlayed on the mobile network.
Owner:THE BOEING CO
System and method for passive assessment of industrial perimeter security
A computer-implemented method for assessing and managing network security for a network includes retrieving topology data and network traffic data with a processor, where the topology data is indicative of a topology of the network. The method may further include retrieving network flow data from a plurality of network data collectors via the processor, generating an attack tree based on the topology data and the network flow data via the processor, updating a customer model database with the attack tree and the topology data, and outputting a security assessment based on the attack tree and the topology data.
Owner:SIEMENS AG
Attack tree-based intelligent network connection vehicle information security event occurrence probability evaluation method and system
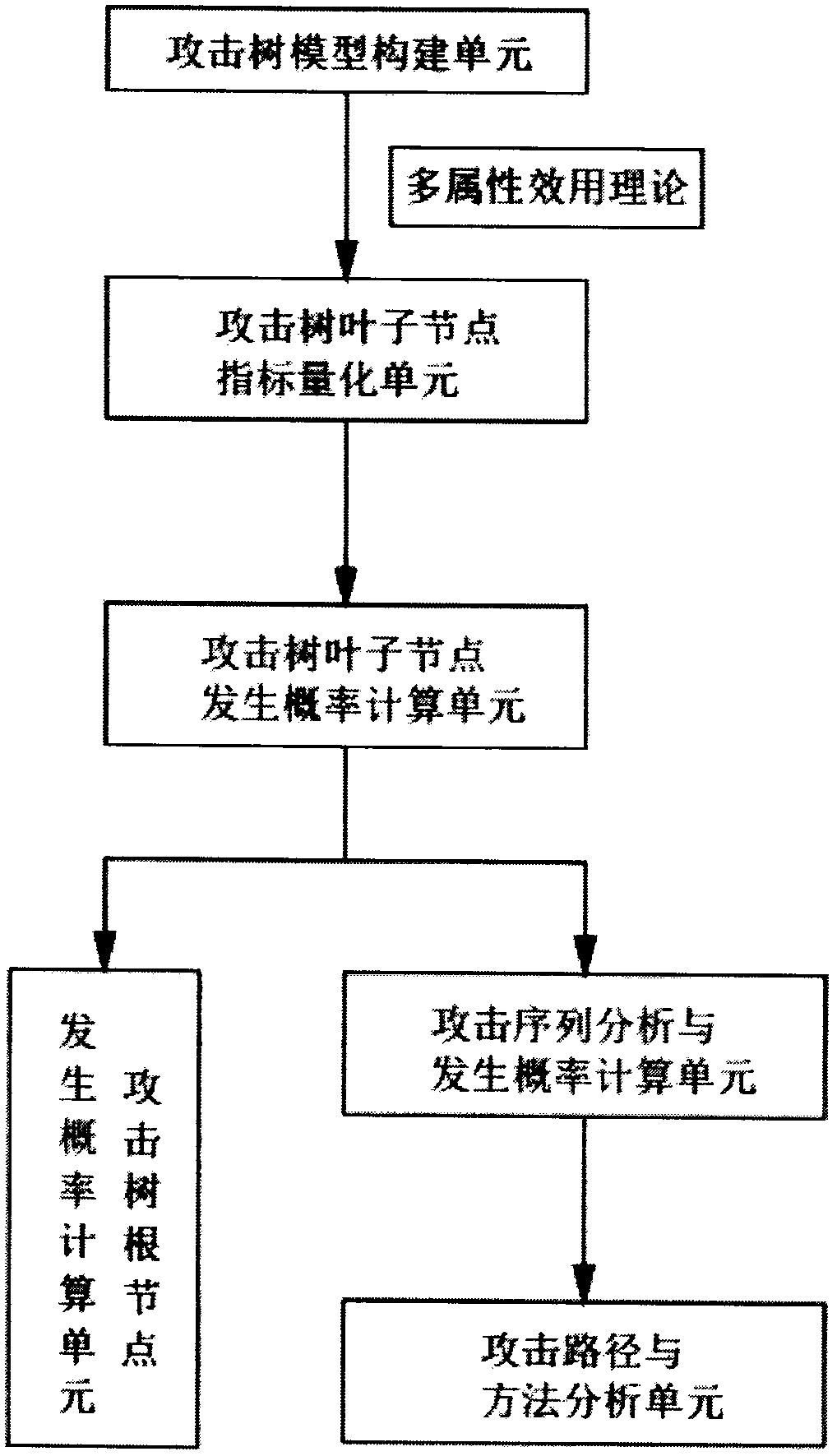
InactiveCN109117637AImprove protectionPlatform integrity maintainanceIntelligent NetworkAnalysis method
The invention discloses an intelligent network connection vehicle information security event occurrence probability evaluation method based on attack tree, in this method, the attack tree analysis method is used to calculate the probability of security events in the intelligent network vehicle information system, the attack sequence of attack tree is analyzed, and the probability of the root nodeand each attack sequence being attacked by information is calculated by using multi-attribute utility theory, which reveals the most risky attack path in the attack tree, so as to determine the attackmode that should be most prevented when the protective measures are made for the system. The method for evaluating the occurrence probability of the information security event adopted by the invention is suitable for evaluating the occurrence probability of the security event of the vehicle service case of the intelligent network connection.
Owner:BEIHANG UNIV
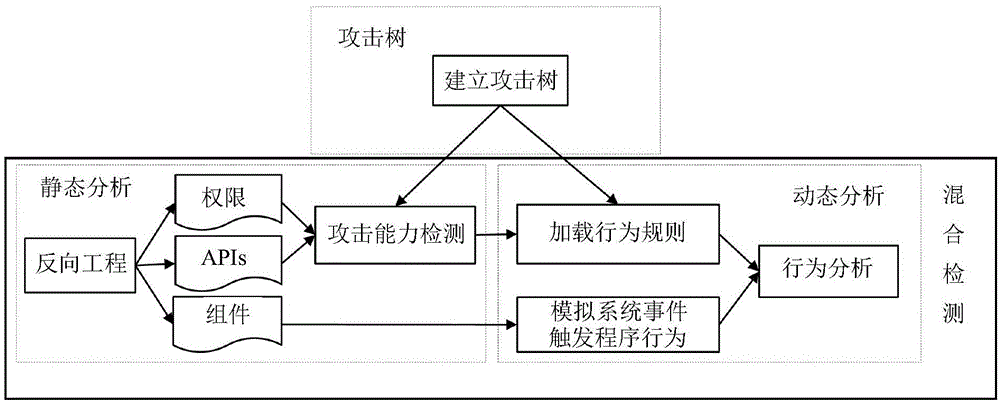
Attack tree model based Android software hybrid detection method
The present invention discloses an attack tree model based Android software hybrid detection method comprising the steps of: using an attack tree model to analyze attack types of various malware, and making a series of dynamic behavior detection rules for each attack path; then, performing hybrid detection including static analysis and dynamic analysis, wherein the static analysis realizes attack ability detection of to-be-tested software, and an analog system event in the dynamic analysis triggers to-be-tested software behaviors of a program; selecting a detecting point during software running by the dynamic analysis according to a result of the attack ability detection of the to-be-tested software, and loading and combining behavior rules; and according to to-be-tested software behaviors of an event trigger program of a component information analog system, forcing the to-be-tested-software to run fully, and performing to-be-tested-software behavior detection according to the behavior rules so as to identify malware. In contrast to the prior art, the attack tree model based Android software hybrid detection method organically combines static analysis and dynamic analysis methods to realize effective detection of malware threatening.
Owner:TIANJIN UNIV
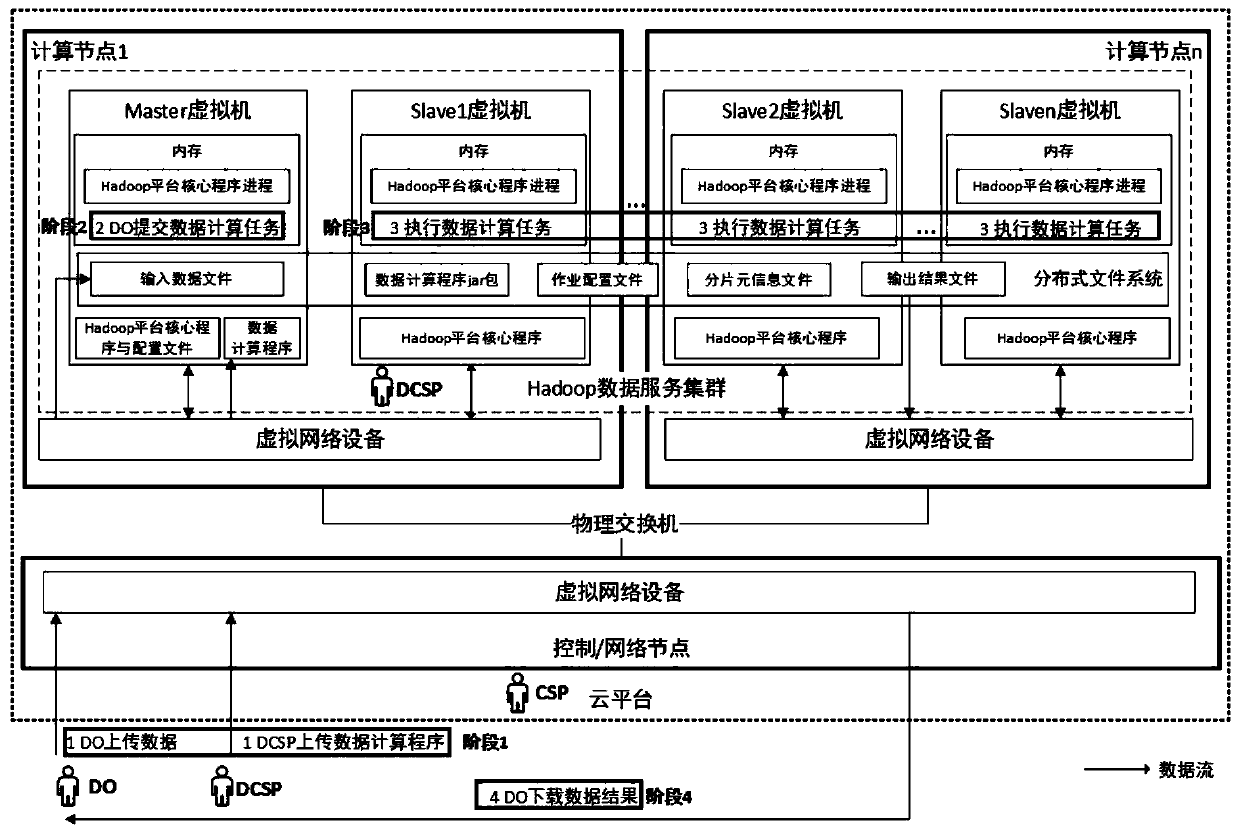
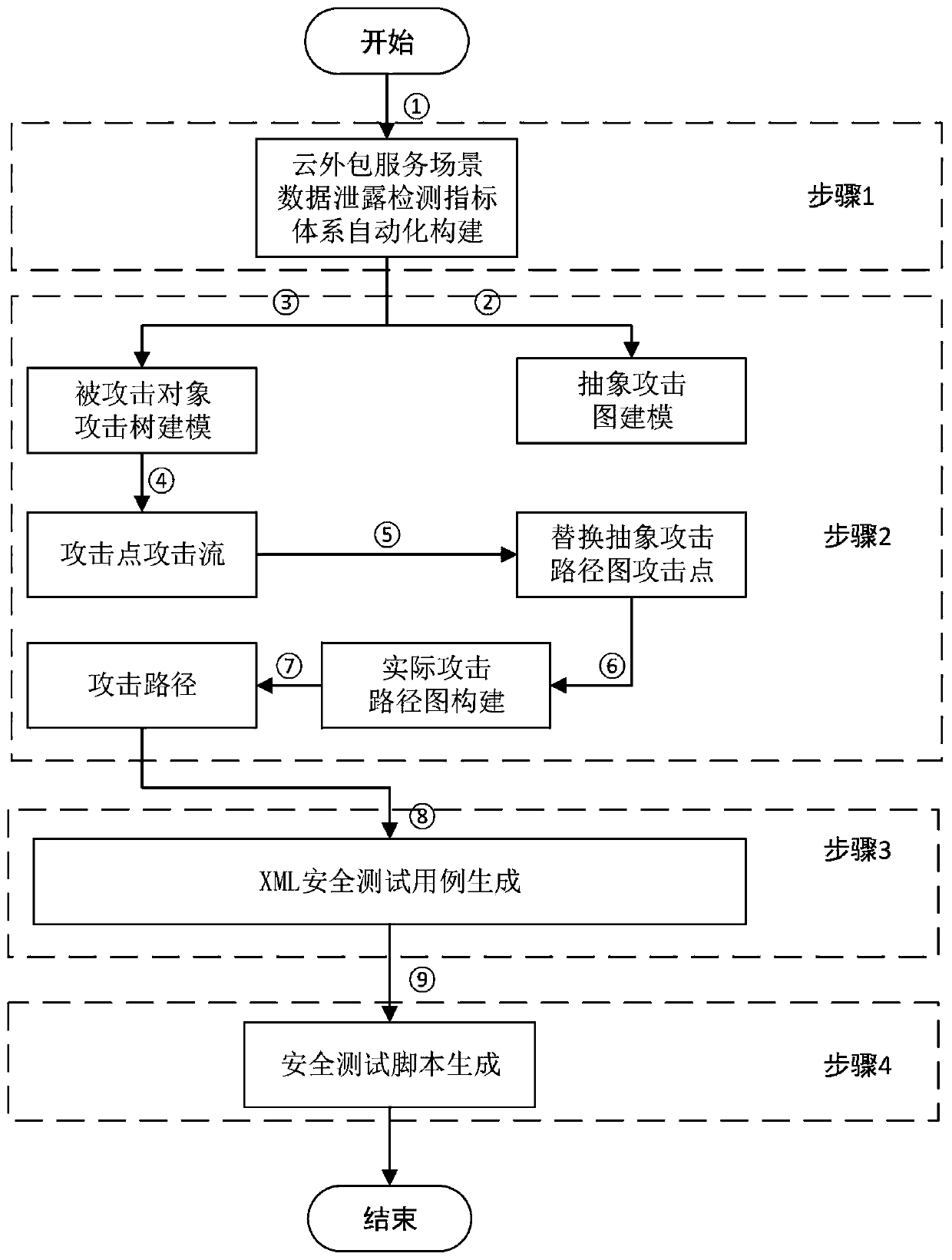
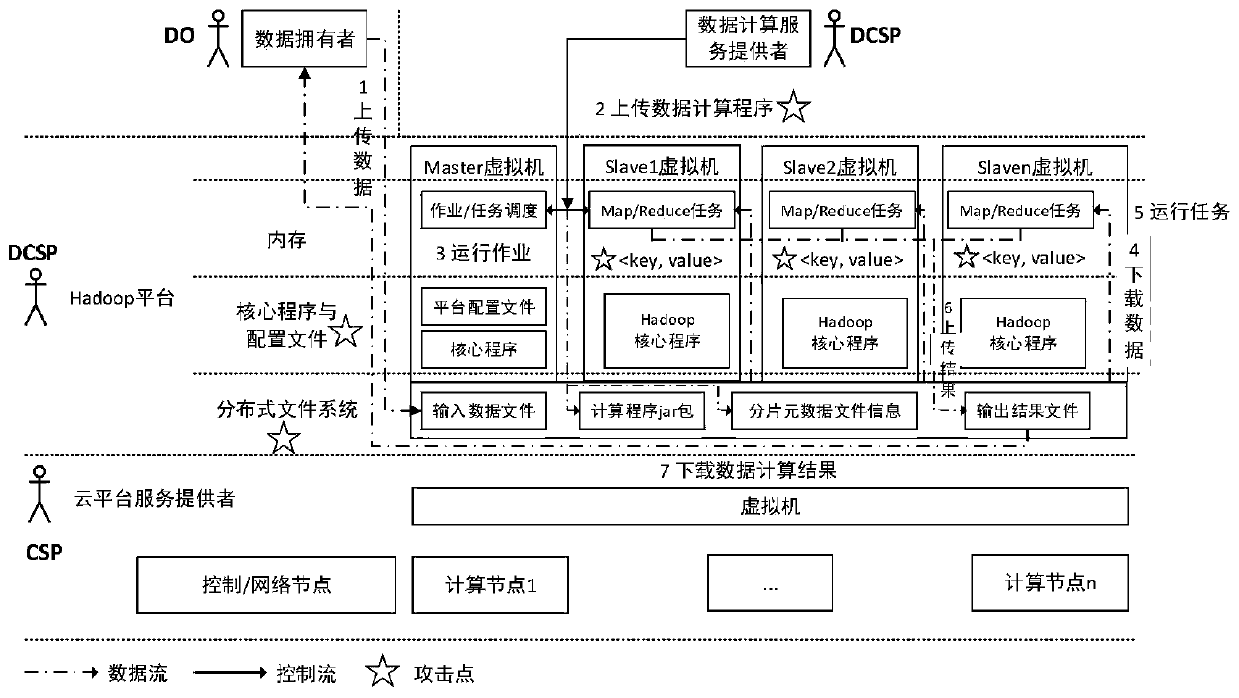
Cloud outsourcing service data leakage safety test case automatic generation method based on attack graph
The invention discloses a cloud outsourcing service data leakage safety test case automatic generation method based on an attack graph, and the method comprises steps of a data leakage detection indexgeneration method covering a cloud outsourcing data service life cycle based on data flow analysis, automatic construction of an attack graph based on the data leakage attack object attack tree model; automatic generation of an XML security test case based on the attack graph and the XML security test description language; automatic generation of a template-based security test script. The data leakage threat covering the cloud outsourcing data service life cycle is analyzed based on the data flow, and a data leakage safety index system under a cloud platform outsourcing data service scene isautomatically constructed; an attack tree and an attack graph are constructed based on the data leakage attack point attack tree model, and the attack detection efficiency is improved; and an executable safety test case script is automatically generated based on the XML safety test description language.
Owner:BEIJING UNIV OF TECH
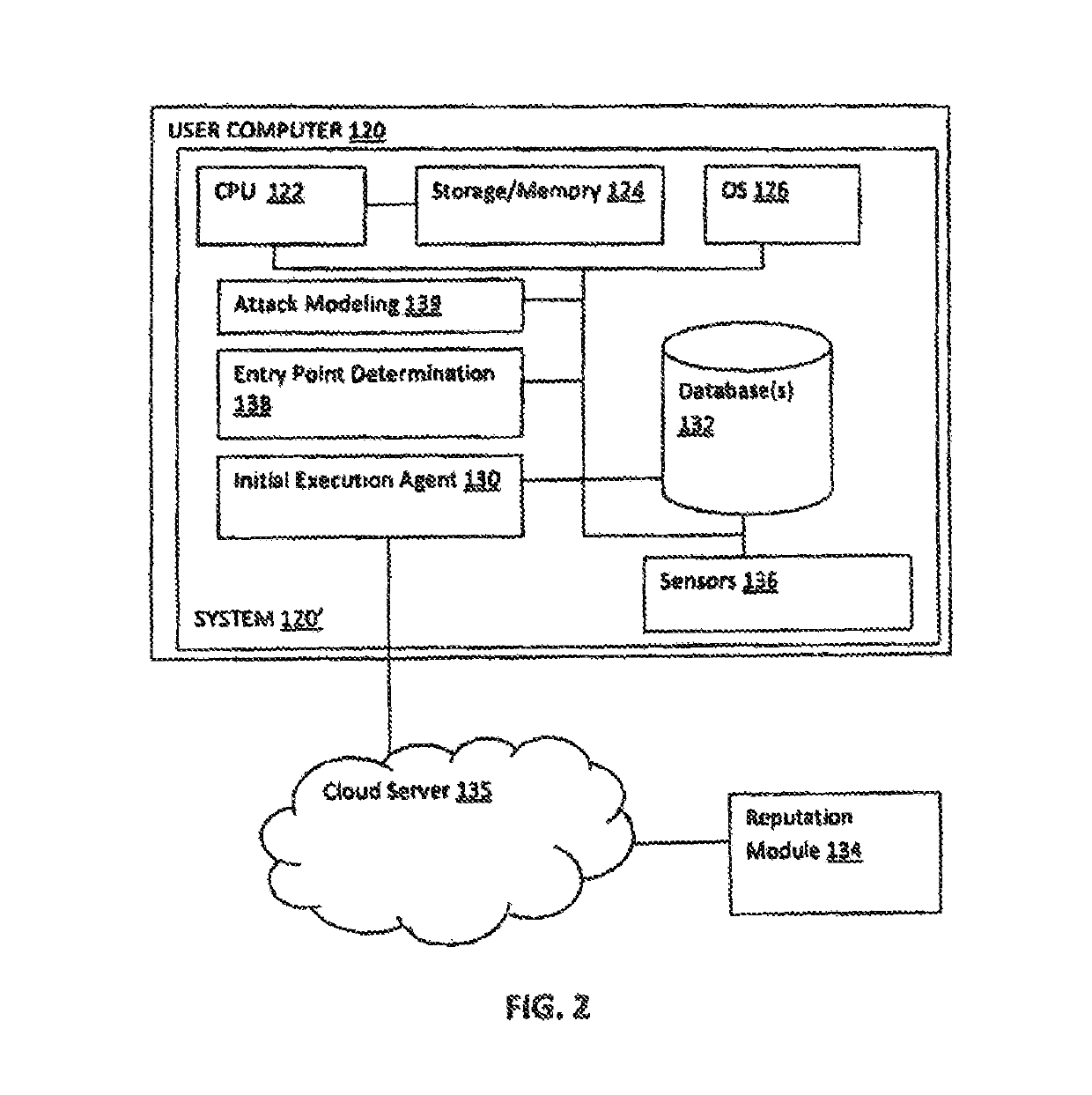
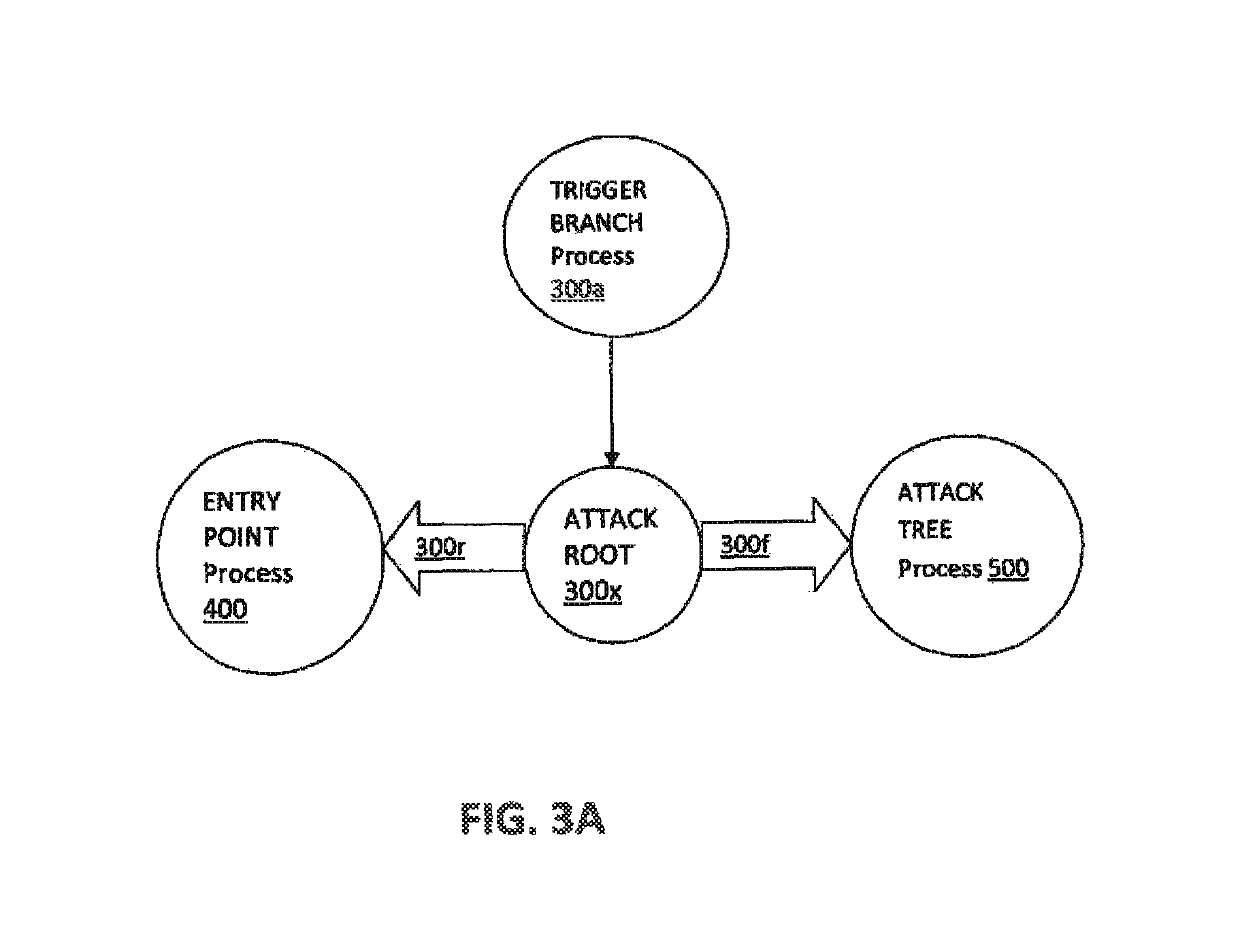
Method and system for modeling all operations and executions of an attack and malicious process entry
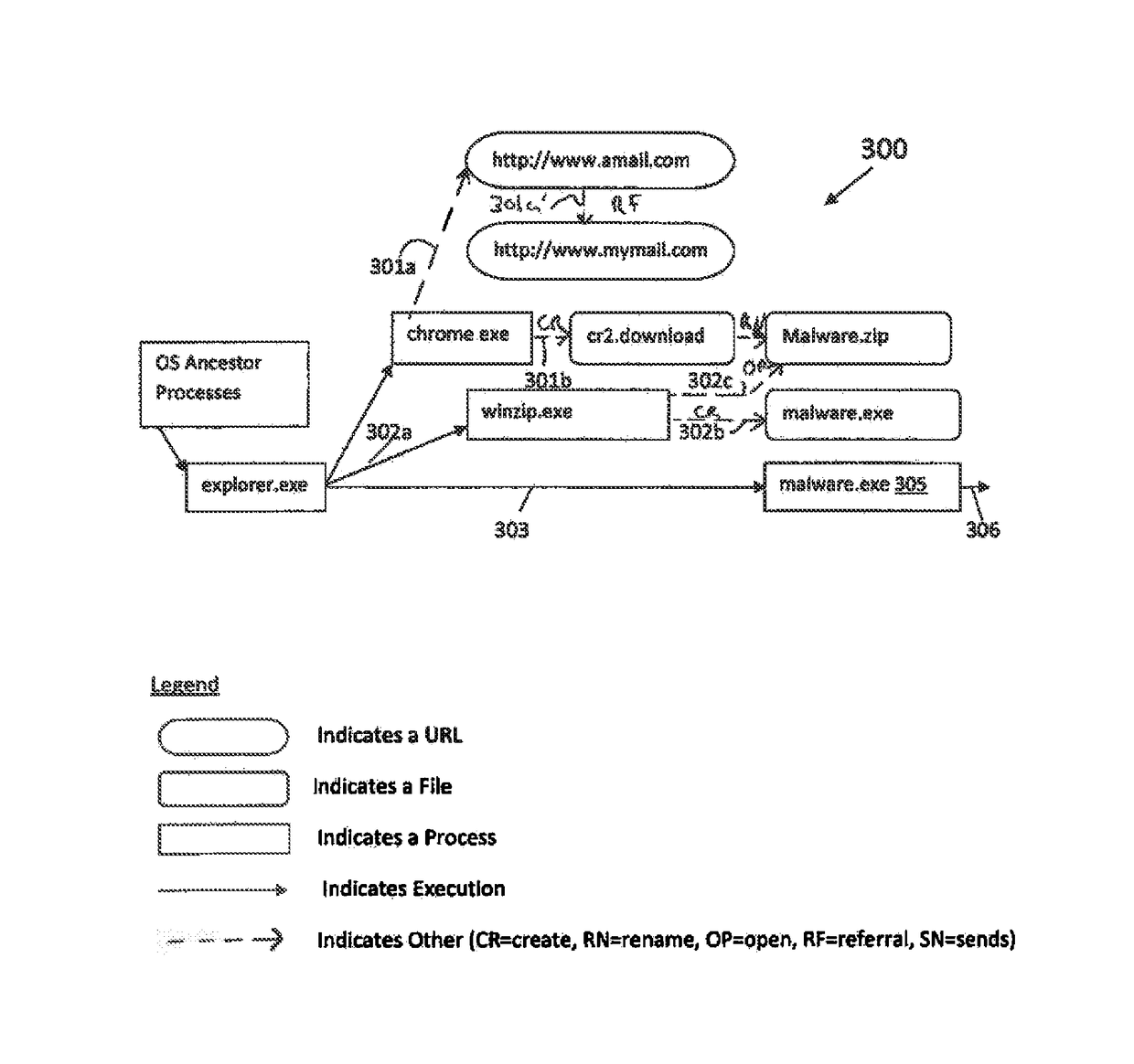
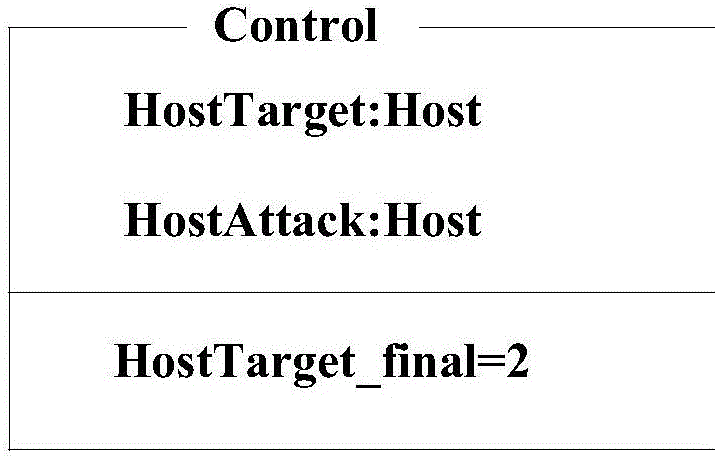
Computerized methods and systems determine an entry point or source of an attack on an endpoint, such as a machine, e.g., a computer, node of a network, system or the like. These computerized methods and systems utilize an attack execution / attack or start root, to build an attack tree, which shows the attack on the end point and the damage caused by the attack, as it propagates through the machine, network, system, or the like.
Owner:CHECK POINT SOFTWARE TECH LTD
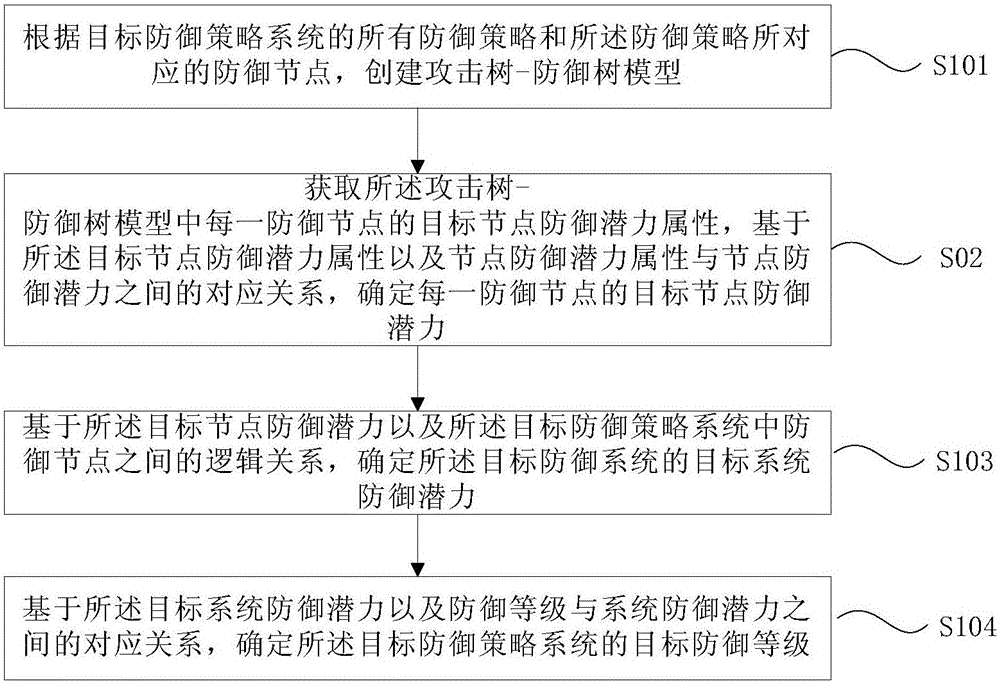
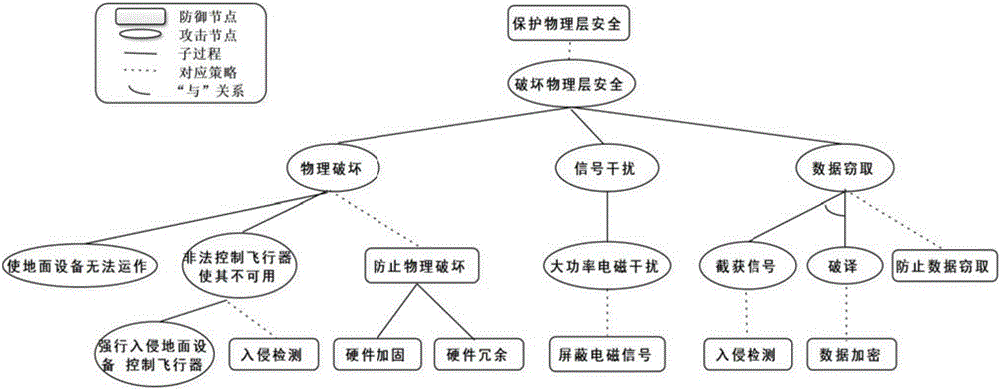
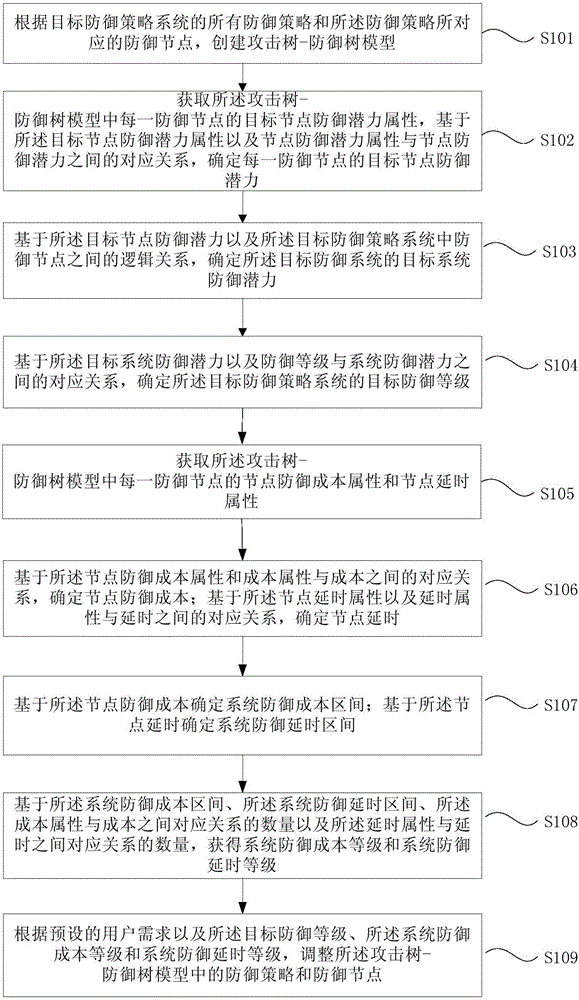
Defense strategy system analysis method and device
The embodiment of the invention provides a defense strategy system analysis method and a defense strategy system analysis device. The method comprises the steps of according to all defense strategies of a target defense strategy system and defense nodes corresponding to the defense strategies, establishing an attack tree-defense tree model; acquiring the target node defense potential attribute of each defense node in the attack-tree-defense tree model, and based on the target node defense potential attribute and correspondence between node defense potential attribute and node defense potential, determining the target node defense potential of each defense node; based on the target node defense potential and a logic relation between the defense nodes in the target defense strategy system, determining the target system defense potential of the target defense system; and based on the target system defense potential and correspondence between a defense class and the system defense potential, determining the target defense class of the target defense strategy system. According to the method, the class of the defense strategy system can be evaluated.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Mobile network dynamic workflow exception handling system
An exception handling system and method are provided for dynamically recovering from a workflow exception occurring in a mobile network communication system. The system has multiple workflows and at least one mission critical item. An attack tree modeling analyses is performed to identify the mission critical item. Another operation includes writing a plurality of forward recovery rules to protect the mission critical item using a transaction datalog fragment of transaction logic. The recovery rules are enabled through an engine in communication with the mobile network communication system. The multiple workflows are monitored for indication of a system attack on any one of the multiple workflows. A new workflow is automatically generated upon detection of the system attack. The exception handling system is overlayed on the mobile network.
Owner:THE BOEING CO
Big data analysis method applied to field of information security
InactiveCN110543761AQuick checkImprove security detection efficiencyDigital data protectionPlatform integrity maintainanceReal time analysisOriginal data
The invention discloses a big data analysis method applied to the field of information security, and belongs to the technical field of information security. The big data analysis method comprises thefollowing steps: S1, establishing a network security database; S2, analyzing network data; S3, carrying out safety management of the data; S4, constructing a safety early warning; and S5, performing alarm processing. The big data analysis method detects whether a security threat occurs in network data analysis by establishing a big data analysis model, wherein the big data analysis model is used for preprocessing acquired data, reorganizing the original data and forming a basic data relation graph through feature extraction and data fusion modes, constructing an attack tree model through the data relation graph so as to speculate the attack behavior of the next step, combining the data statistical characteristics in the attack, designing the data analysis process, method and rule, and deeply mining the preprocessed data by applying the real-time analysis and offline analysis modes, so that the hidden danger information in the data can be detected more quickly, and the security detection efficiency is improved.
Owner:安徽蓝麦通信股份有限公司
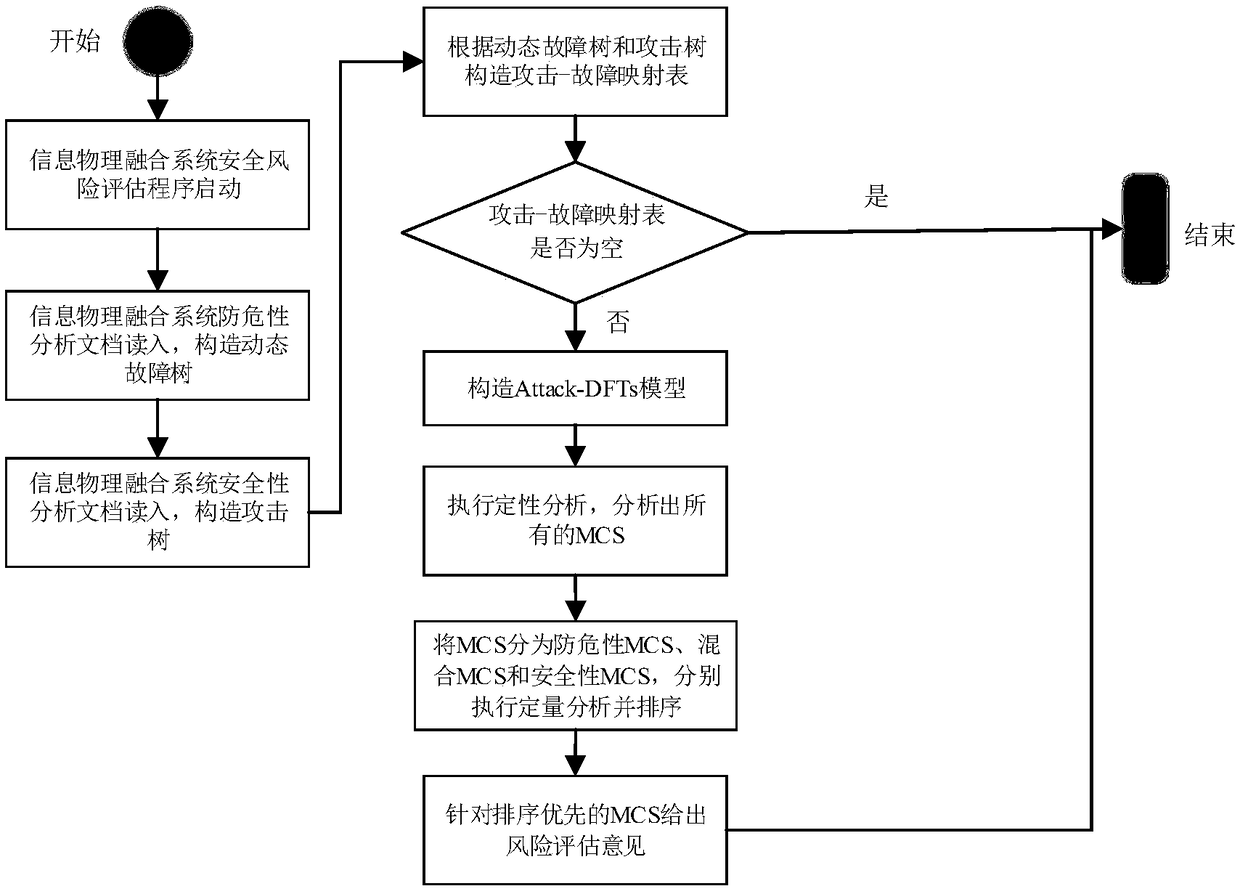
Information physical integration system security risk assessment method
ActiveCN108183897AImplement Security Risk AssessmentAddressing Difficult-to-Assess Security RisksData switching networksPhysical systemNetwork attack
The invention relates to an information physical integration system security risk assessment method, and belongs to the technical field of the information physical integration system. The method comprises the following steps: constructing a dynamic fault tree of an information physical integration system; constructing an attack tree model of the information physical integration system; constructing an attack-fault mapping table; and integrating the dynamic fault tree model and the attack tree model according to the attack-fault mapping table to establish an Attack-DFTs model. The attack-faultis comprehensively assessed, so that the influence on the physical system by the network attack can be accurately estimated through the security risk assessment, thereby giving out improvement suggestions for avoiding the risk.
Owner:NANJING FORESTRY UNIV
TTP automatic extraction and attack team clustering method
The invention relates to a TTP automatic extraction and attack team clustering method. Along with increasingly popularization of advanced persistent threats in the global range, the Internet of Thingsis directly exposed to the Internet due to poor security, so that the Internet of Things becomes an excellent weapon for a hacker organization to initiate APT attacks. Therefore, an attacker can establish a botnet by using the attacked Internet of Things device and initiate an APT attack by using the botnet. The invention provides a framework for observing and predicting attacks of the Internet of Things. The framework aims at automatically extracting technologies, tactics and processes of attackers and mining potential attacker teams behind a large number of attacks. Firstly, related fieldsare extracted from captured Internet of Things honeypot logs; and then, the attack behavior is mapped to an ATT & CK framework to realize TTP automatic extraction. Furthermore, the method generates four feature groups including 18 features including TTP, time, IP and URL, potential attack groups are mined through specific hierarchical clustering, and finally, an attack tree is generated for each attacker cluster so as to better describe team attack behaviors.
Owner:SICHUAN UNIV
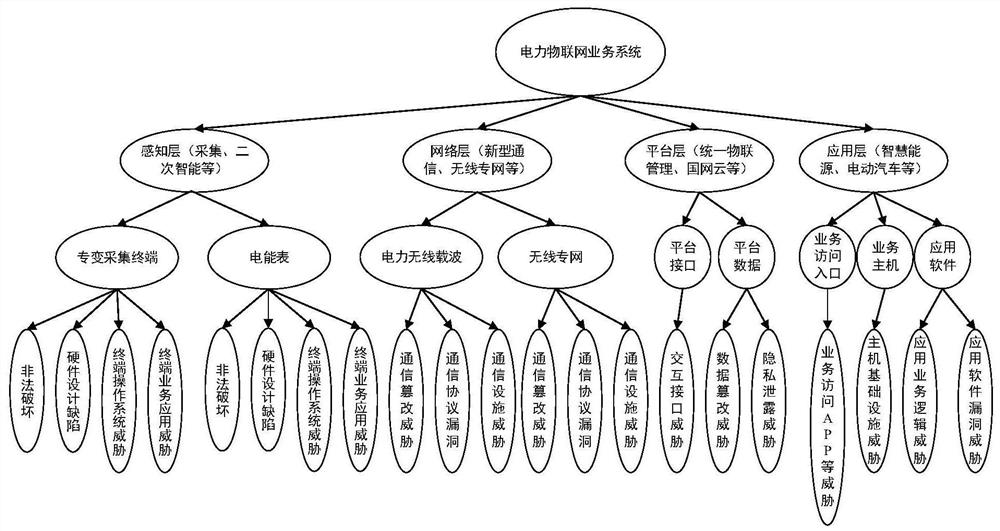
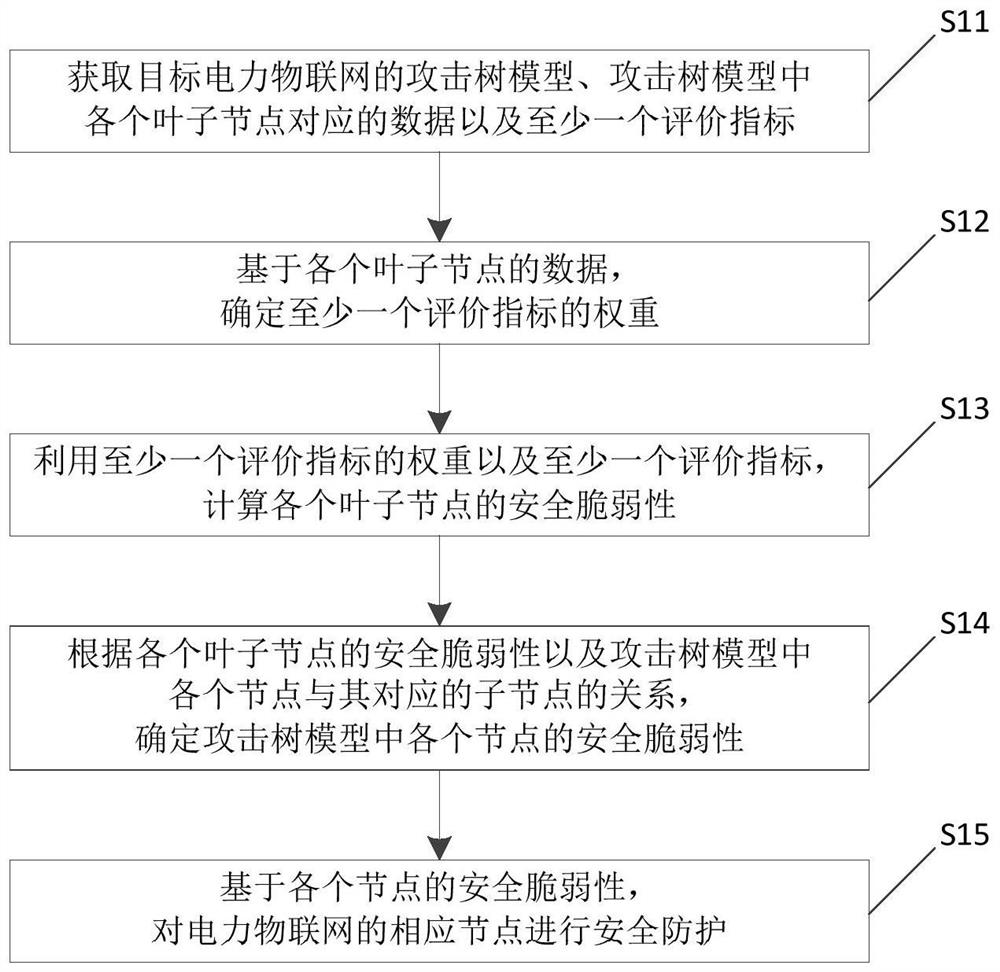
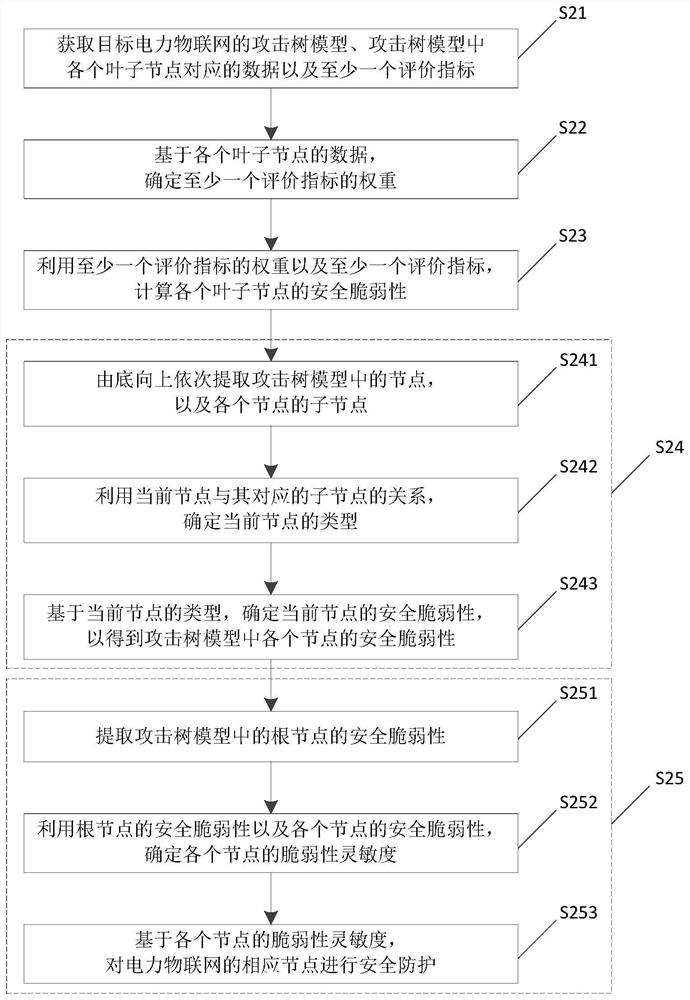
Power Internet of Things security vulnerability evaluation method integrating service security
PendingCN112087445ASecurity Vulnerability AssuranceImprove accuracyResourcesData switching networksVulnerability evaluationAttack tree
The invention relates to the technical field of power internet of things, and particularly relates to a power internet of things security vulnerability evaluation method integrating service security.The method comprises the steps of acquiring an attack tree model of a target power internet of things, data corresponding to each leaf node in the attack tree model and at least one evaluation index;determining the weight of at least one evaluation index based on the data of each leaf node; calculating the security vulnerability of each leaf node by using the weight of the at least one evaluationindex and the at least one evaluation index; determining the security vulnerability of each node in the attack tree model according to the security vulnerability of each leaf node and the relationship between each node in the attack tree model and the corresponding child node; and based on the security vulnerability of each node, performing security protection on the corresponding node of the power Internet of Things. After the security vulnerability of each node is calculated, security protection can be carried out on each node in a targeted manner, so that the security protection accuracy is improved.
Owner:GLOBAL ENERGY INTERCONNECTION RES INST CO LTD +2
ROP (Return-Oriented Program) protection method based on attack tree
InactiveCN105825086AResistantImprove protectionProgram/content distribution protectionControl flowAttack model
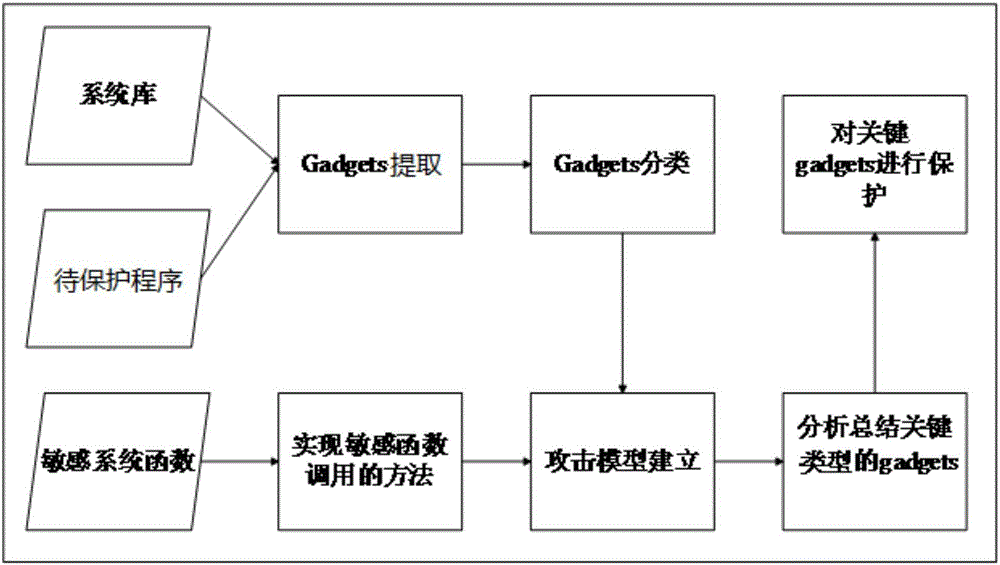
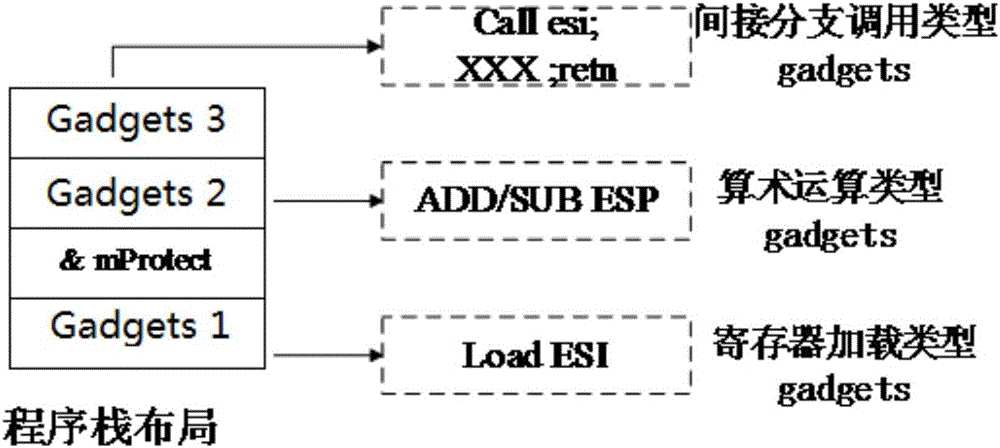
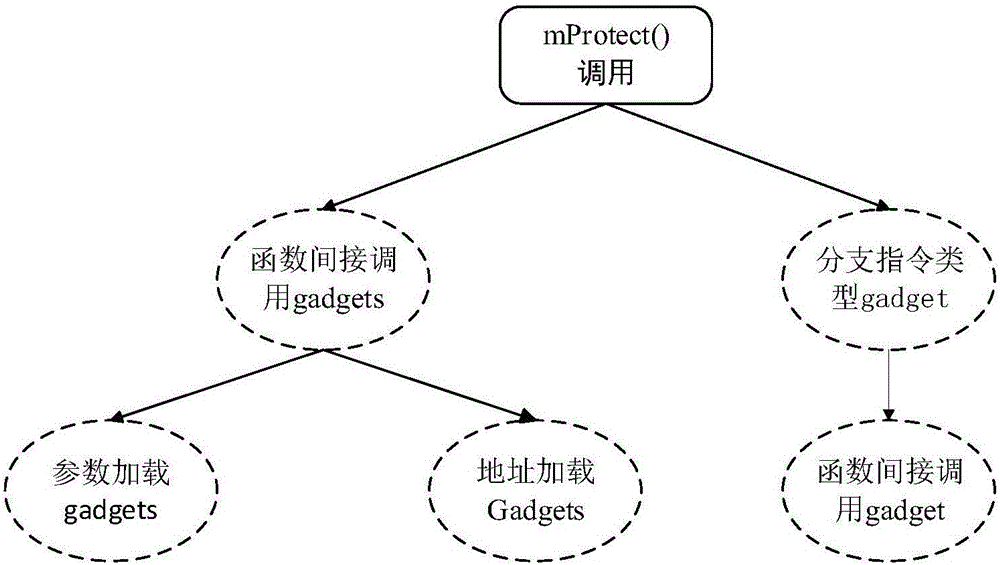
The invention discloses an ROP (Return-Oriented Program) protection method based on an attack tree and belongs to the field of software security of computers. The ROP protection method comprises the following steps: extracting gadgets instruction segments from a program to be protected and a system library file; determining the type of each extracted gadgets instruction segment, and selecting a plurality of sensitive system functions; carrying out attack modeling by utilizing the extracted gadgets instruction segments through a method of constructing the attack tree, and analyzing all attack methods to obtain key gadgets; finally, protecting the key gadgets. The program is protected by utilizing an attack modeling manner, so that the difficulty that an attacker hijacks a control flow is enhanced and the protection efficiency is improved, and finally, the program control flow is safer.
Owner:NORTHWEST UNIV
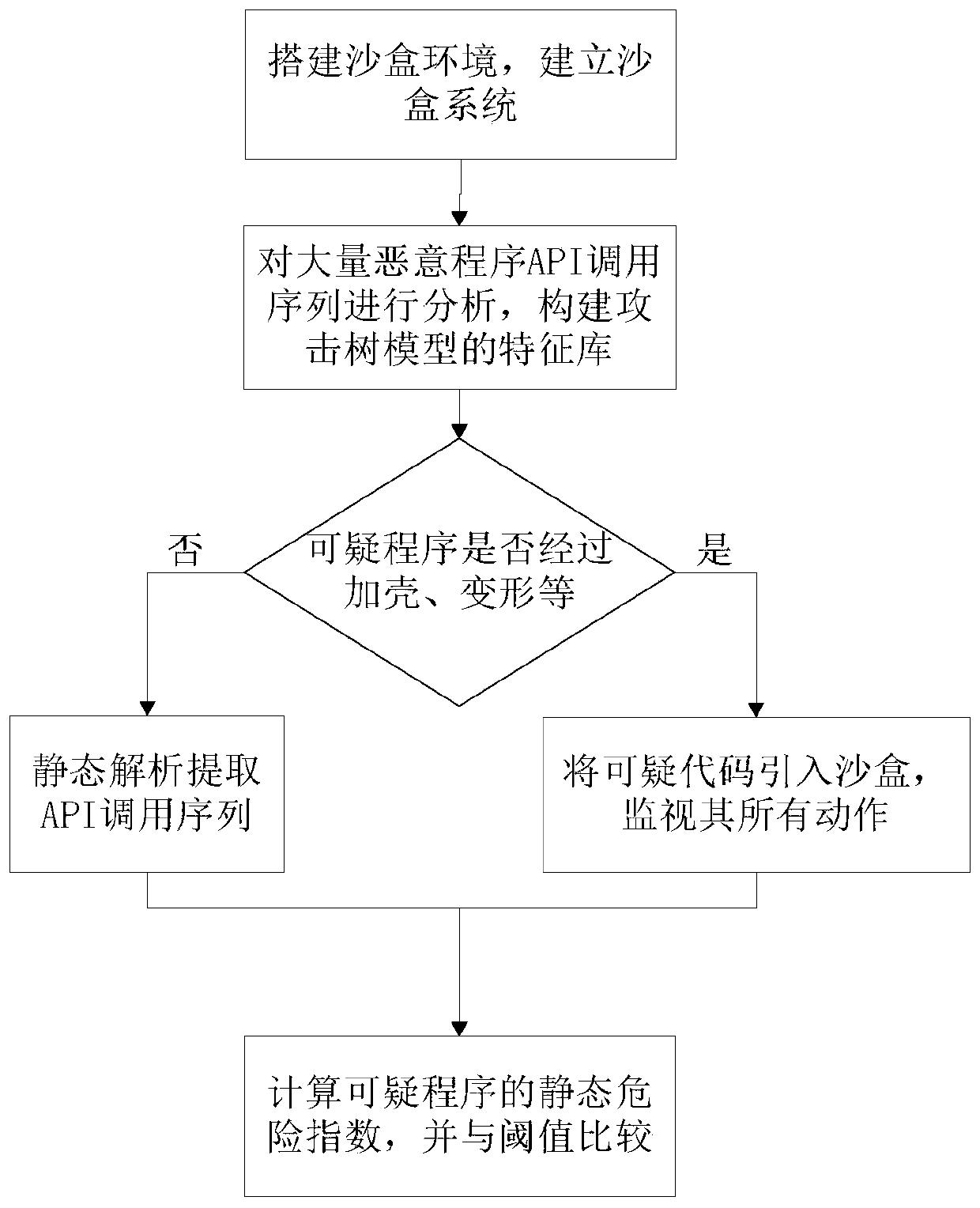
Method for identifying suspicious attack codes based on sandbox dynamic behaviors
ActiveCN110135156AIncreased sensitivityHarm reductionPlatform integrity maintainanceAttack treeBehavior recognition
Owner:ZHEJIANG UNIV OF TECH
Method And System For Modeling All Operations And Executions Of An Attack And Malicious Process Entry
Computerized methods and systems determine an entry point or source of an attack on an endpoint, such as a machine, e.g., a computer, node of a network, system or the like. These computerized methods and systems utilize an attack execution / attack or start root, to build an attack tree, which shows the attack on the end point and the damage caused by the attack, as it propagates through the machine, network, system, or the like.
Owner:CHECK POINT SOFTWARE TECH LTD
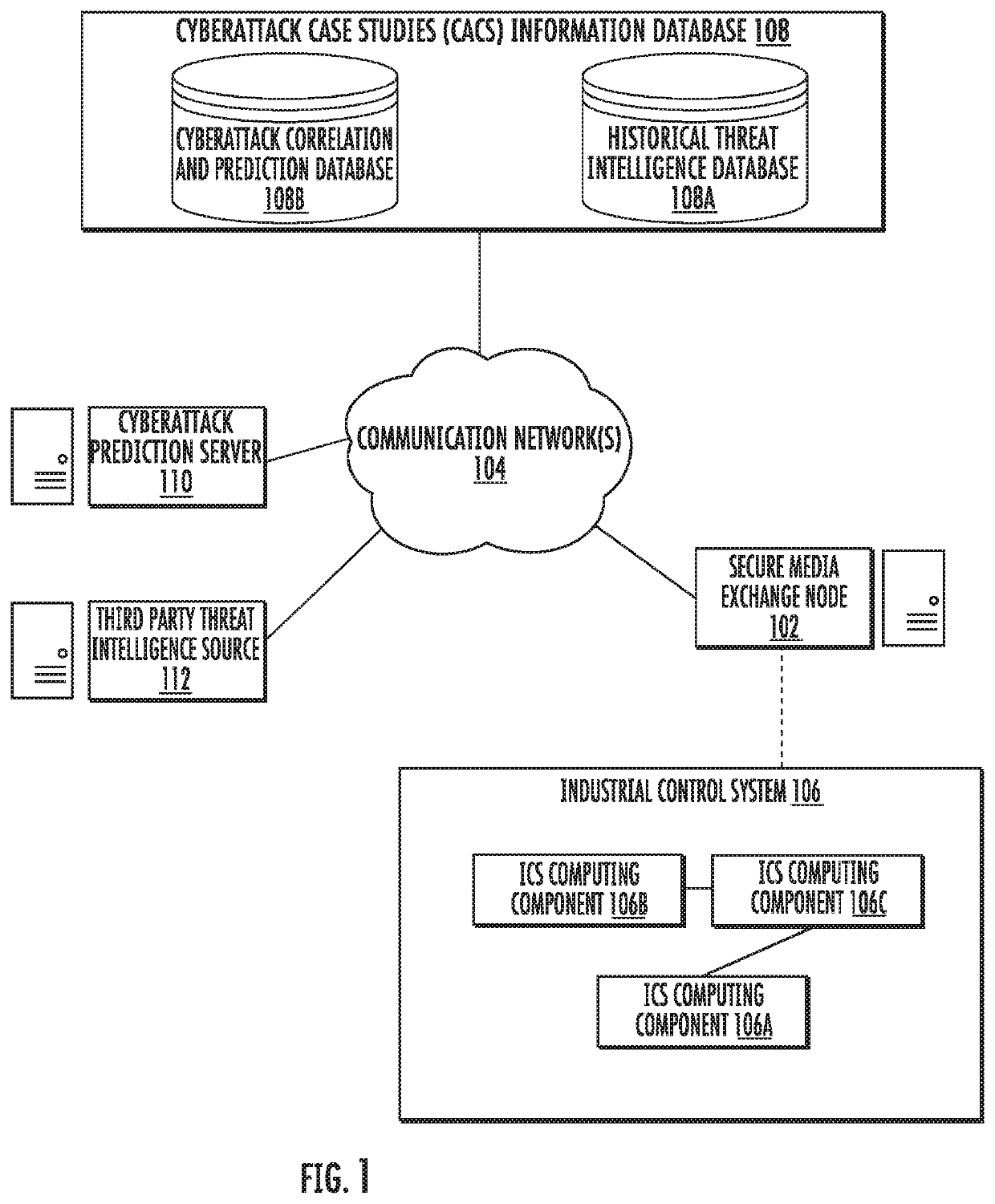
Mapping an attack tree and attack prediction in industrial control and iiot environment using hash data analytics
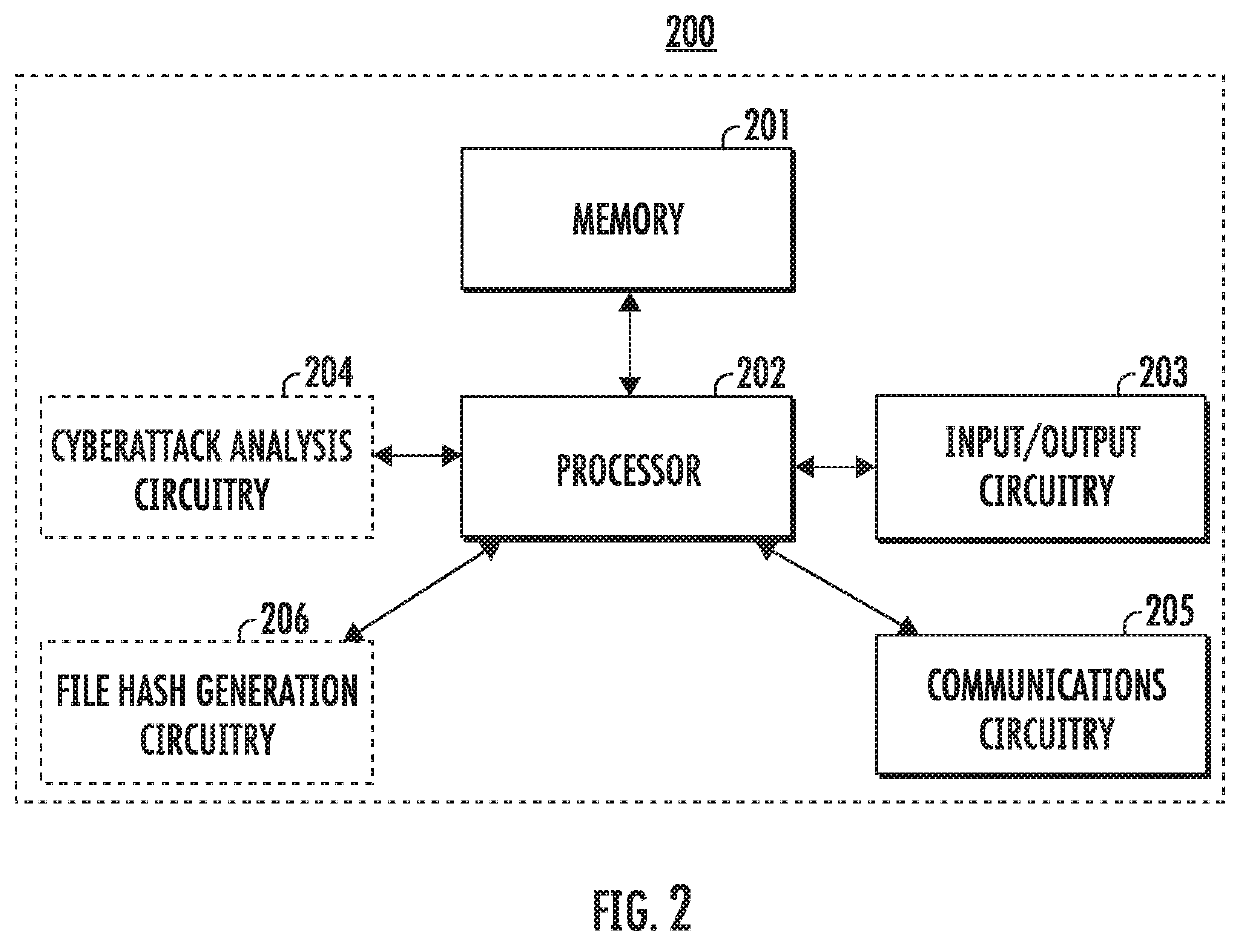
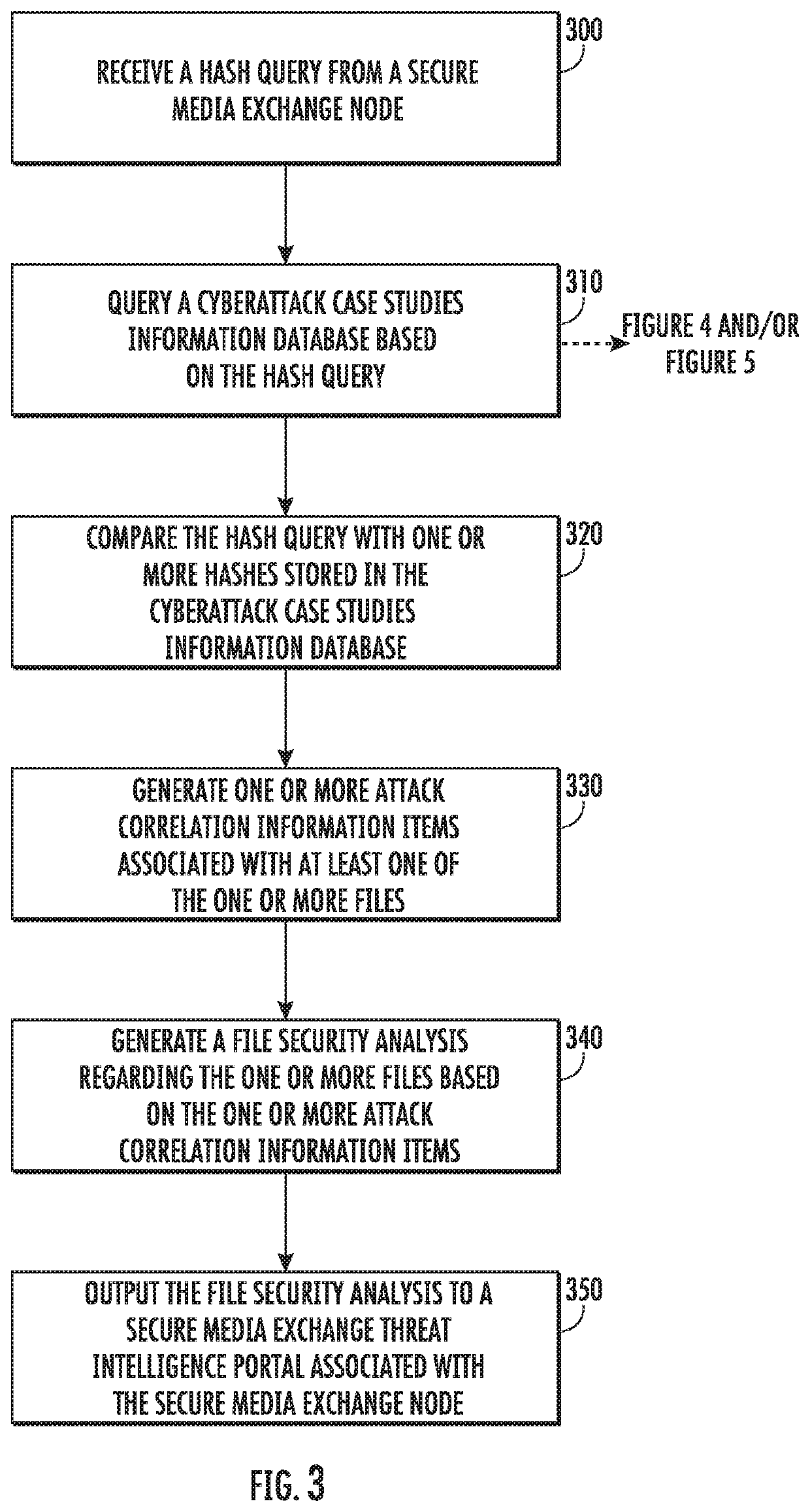
A method, apparatus and computer program product for detecting malicious content and predicting cyberattacks are described herein. In the context of a method, the method receives a hash query comprising a file hash based on one or more files. The method queries a cyberattack case studies information database based on the hash query to generate one or more attack correlation information items associated with at least one of the one or more files. The method also generates and outputs a file security analysis based on the attack correlation information items for authorization of the one or more files.
Owner:HONEYWELL INT INC
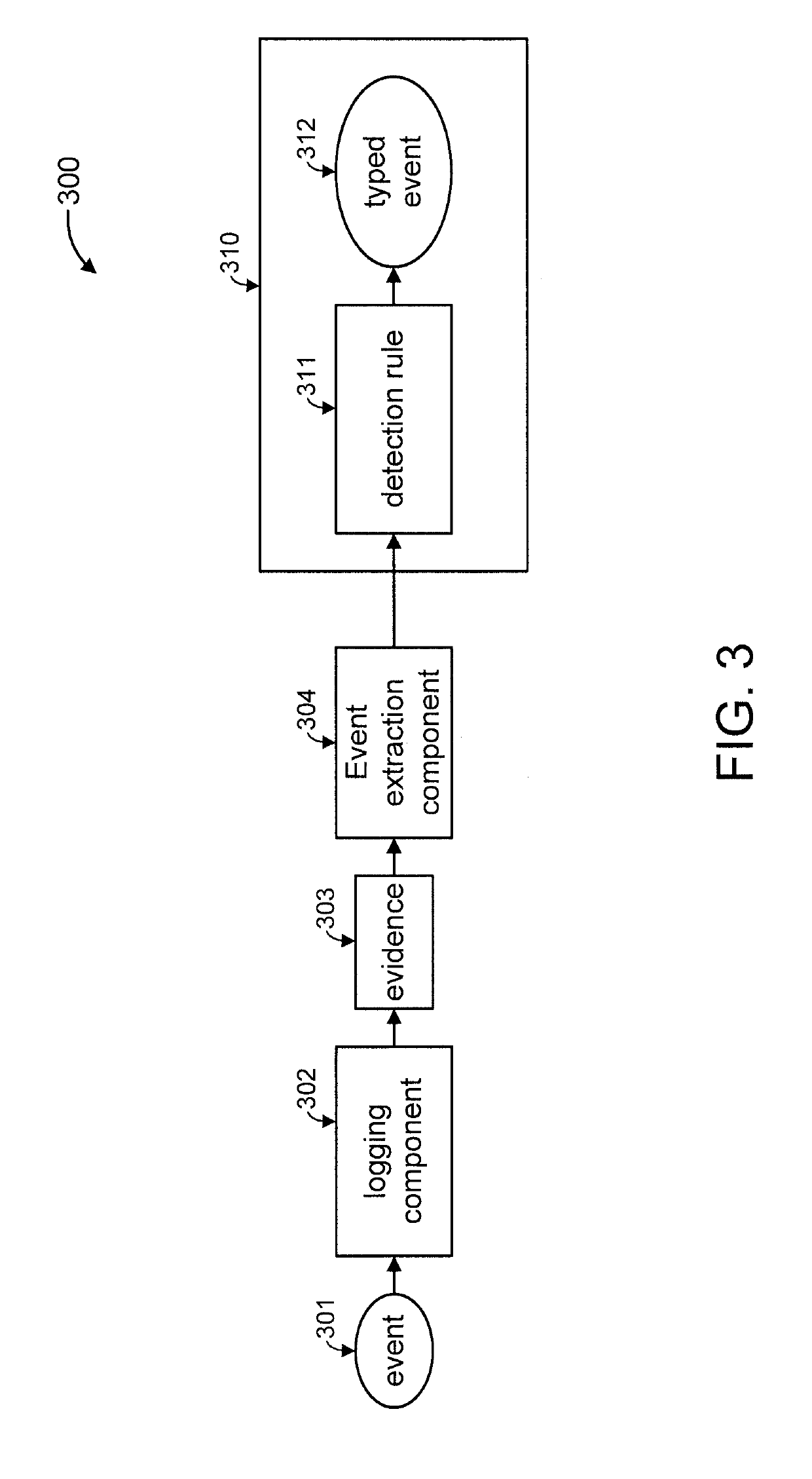
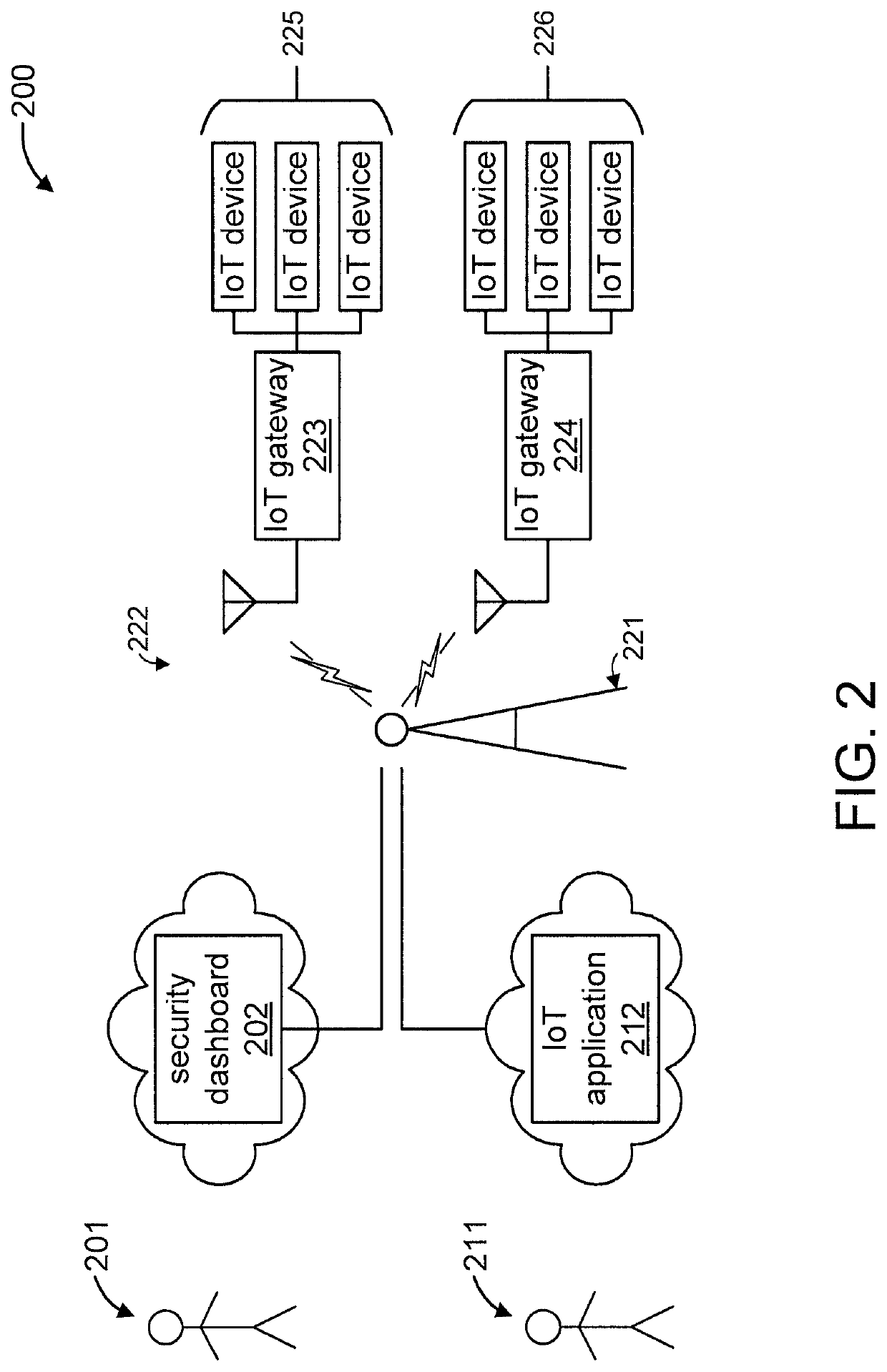
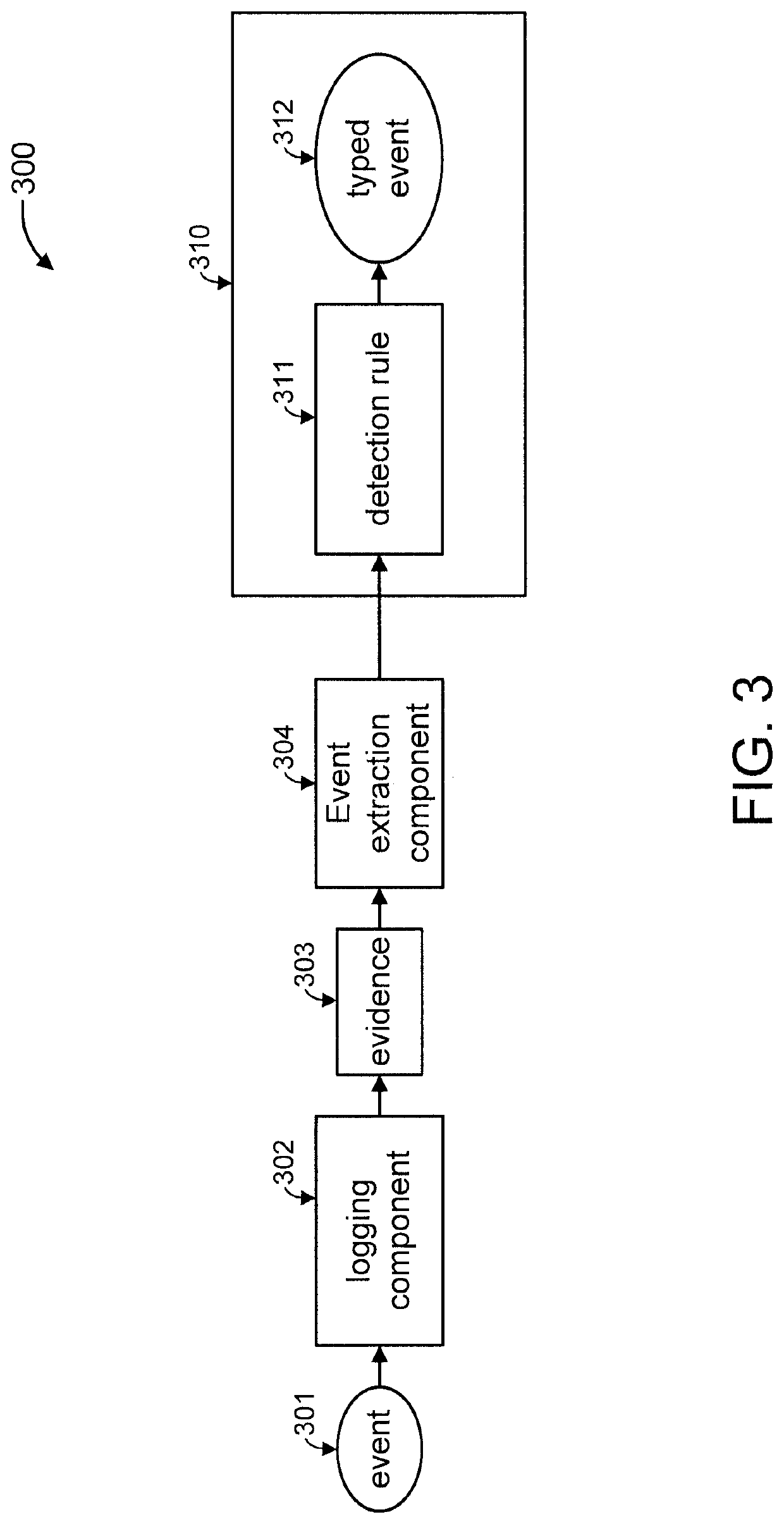
Using attack trees to reduce memory consumption by rule engines
ActiveUS20190129620A1Reduce memory consumptionReduce consumptionInput/output to record carriersPlatform integrity maintainanceConnection typeData mining
A method is provided for reducing memory consumption by a rule engine. The method includes receiving attack trees, each having nodes and edges. Each node represents a security event and is associated with a detection rule for detecting an occurrence thereof. Each edge connects a respective node pair. The method includes assigning a watchpoint to each leaf node. The method includes moving the watchpoint assigned to any leaf node to a next upstream node, responsive to detecting an occurrence of the security event represented by the leaf node. The method includes erasing the watchpoint assigned to all downstream nodes relative to the next upstream node, responsive to the next upstream node being connected to a next downstream node using an edge having an “OR” join type. Only the rules for nodes currently having the watchpoint assigned are loaded into a memory device during runtime, while excluding rules for remaining nodes.
Owner:IBM CORP
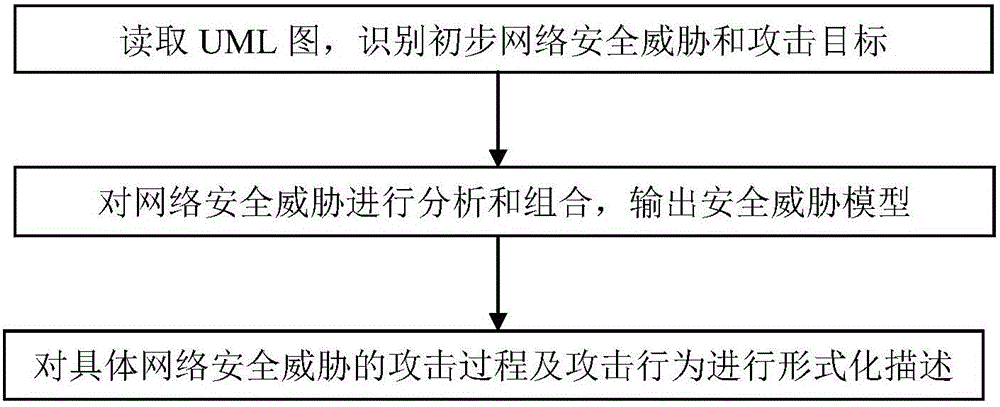
Network security threat evaluation method and system for substation monitoring system
The invention provides a network security threat evaluation method for a substation monitoring system. The method comprises the steps of firstly, reading a UML graph which describes a monitoring system application scene, and identifying primary network security threats and attack objects of the substation monitoring system; then analyzing and combining the network security threats, outputting a monitoring system security threat model, and refining the model into an attack tree; and finally, carrying out formalized description on the attack processes and attack behaviors of the specific network security threats, and outputting the attack processes and attack behaviors in an Object-Z format. Correspondingly, the invention also provides a matched network security threat evaluation system for the substation monitoring system. According to the method provided by the invention, the network security threats of the monitoring system can be described qualitatively, and the network security threats are visual and clear; and the threat attack behaviors are described by use of a formalized mathematical language, and therefore, corresponding defensive measures can be provided.
Owner:NR ELECTRIC CO LTD +1
Prevention and control method of long-horned beetles for macadamia
The invention discloses a prevention and control method of long-horned beetles for macadamia. Aiming at tree trunks attacked by long-horned beetle larvae, adopted are procedures of applying microbialbacterial manure to attacked fruit trees, pruning attacked branches, finding latest bored holes from the attacked parts of the trees and applying insecticide, conducting stem spraying from the trunk root parts to fork parts of the fruit trees, using absorbent cotton balls to block holes of the long-horned beetles, covering the parts, subjected to stem spraying, of the tree trunks with straw ropes,spraying pest-killing and bacteria-killing agent liquid to the tree trunks and root parts of the whole fruit trees, timely removing the attacked trees and dead branches, and meanwhile using phagostimulant to trap the long-horned beetle adults. Comprehensive prevention and control are conducted by combining physical prevention and control with chemical prevention and control, so that the attackingrate of the long-horned beetles is lowered to 0.2% or below, the yield of nuts is obviously increased, and good economic benefit is obtained.
Owner:SOUTH ASIAN TROPICAL AGRI SCI RES INST OF GUANGXI
WLAN multi-step attack intention pre-recognition method
ActiveCN105007262APre-identification implementationData switching networksAlgorithmRecognition algorithm
The invention discloses a WLAN multi-step attack intention pre-recognition method. The method includes three steps: constructing a hierarchical attack tree, generating the shortest prediction sequences and recognizing an attack intention in advance. The first step (1) of constructing a hierarchical attack tree includes constructing a hierarchical attack tree including characteristic nodes, storing wireless multi-step attack modes, describing a hierarchical relation among multi-step attack steps, and increasing the efficiency of attack intention pre-recognition. The second step (2) of generating the shortest prediction sequences includes generating the shortest prediction sequences for all the wireless multi-step attack modes by means of the constructed hierarchical attack tree, and defining the prior degree to evaluate the degree of pre-recognition. The third step (3) of recognizing an attack intention in advance includes designing a multi-step attack pre-recognition algorithm based on the shortest prediction sequences, and finally achieving on-line wireless multi-step attack intention pre-recognition. The beneficial effects of the method are that the wireless multi-step attack intention pre-recognition can be effectively achieved through generation of shortest prediction sequences of wireless multi-step attacks.
Owner:ZHEJIANG UNIV CITY COLLEGE
Security access assessment method and device for power terminal equipment
The invention discloses a security access assessment method and device for power terminal equipment, and the method is used for continuously assessing the credibility and security threat of the terminal equipment in a zero-trust network, and comprises the steps: installing an acquisition probe on the terminal equipment, and collecting the security state of the terminal; constructing a network topological graph based on a network connection relationship of servers on a power business system, and converting the constructed network topological graph into an R-hop weighted attack tree by adopting a WL subtree accounting method; calculating a risk value in a server node R-hop for the accessed terminal equipment, and pruning the weighted attack tree to obtain a final safe and accessible power service system. The method not only considers the security state of the terminal equipment, but also considers the access authority of the terminal equipment at the cloud, the security protection capability of the service system and the like, and finally gives the minimum security service set which can be safely accessed by the terminal.
Owner:STATE GRID ELECTRIC POWER RES INST +3
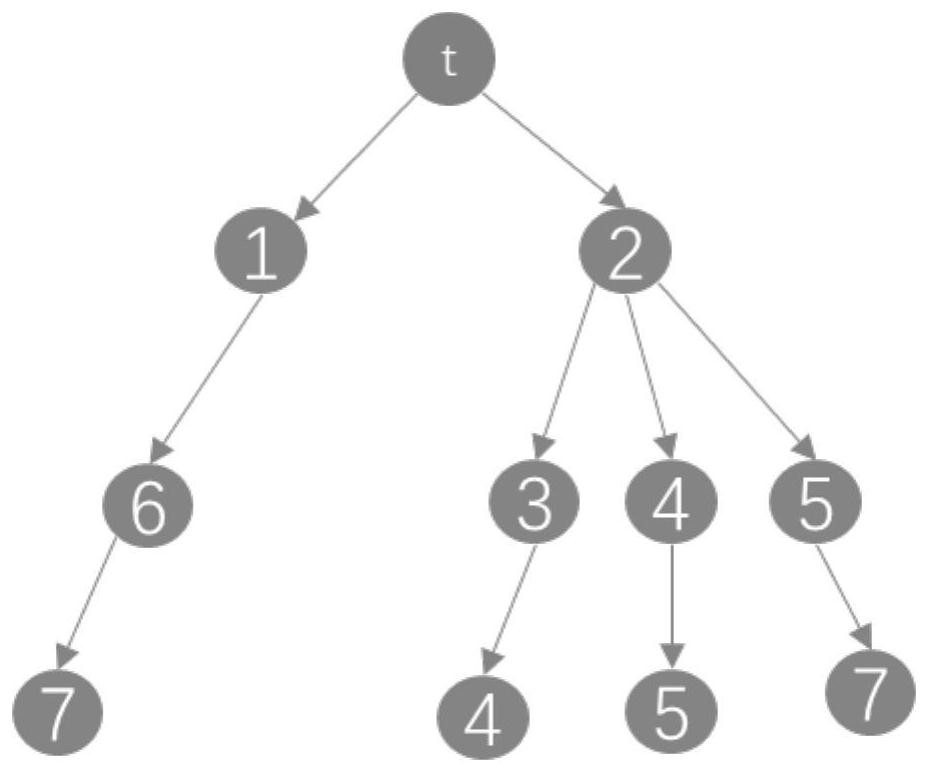
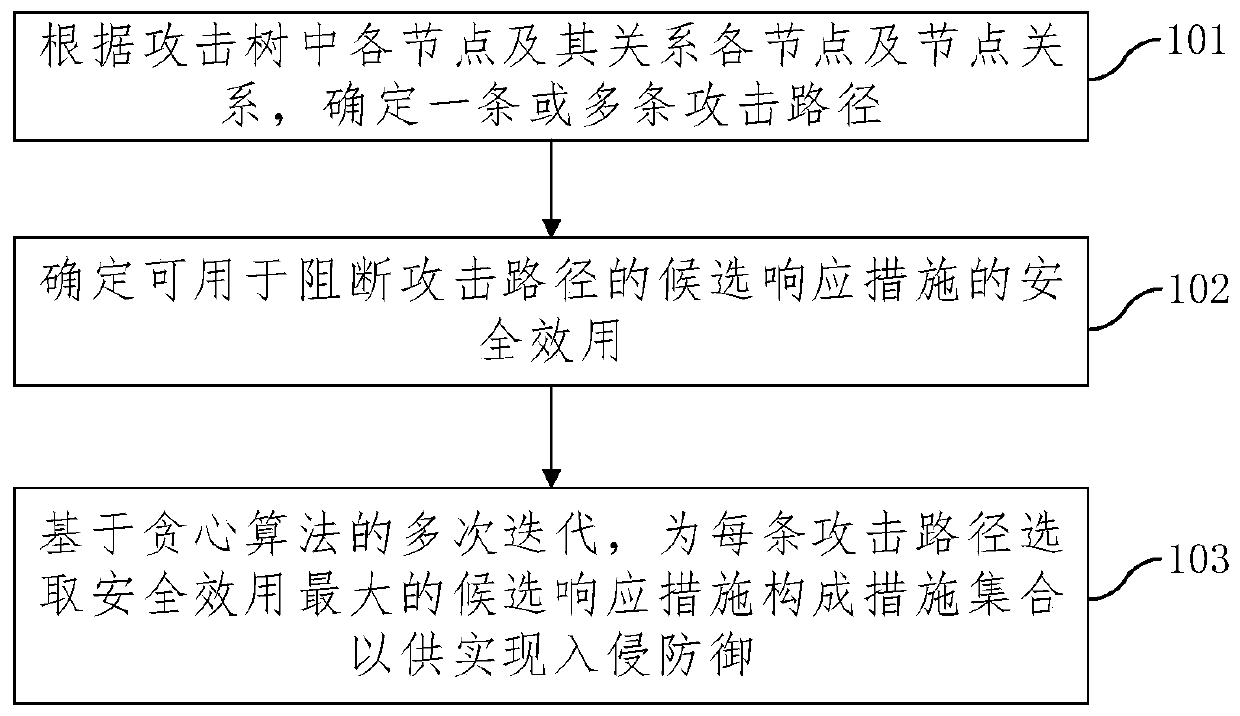
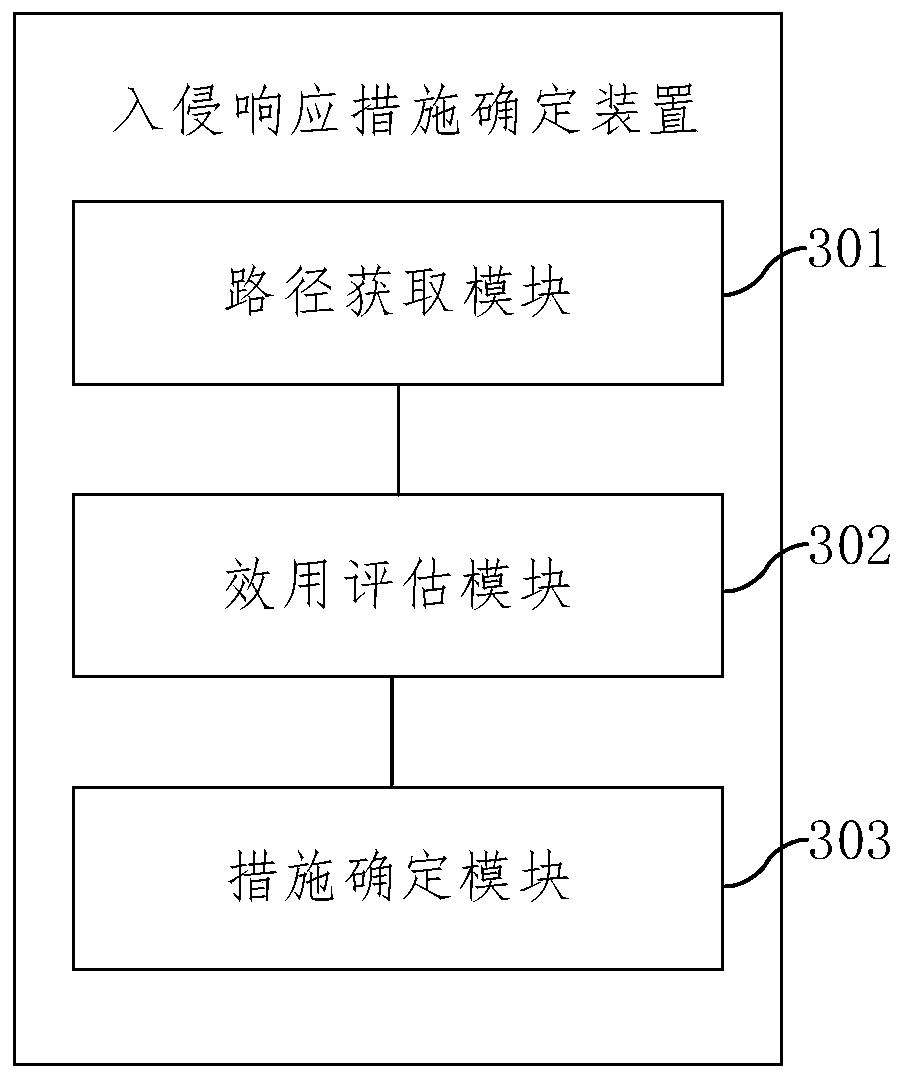
Intrusion response measure determination method and device
InactiveCN110233845AAvoid double countingImplement intrusion preventionTransmissionGreedy algorithmMulti path
The embodiment of the invention provides an intrusion response measure determination method and device, and the method comprises the steps: determining one or more attack paths according to each nodein an attack tree and a node relationship; determining the security utility of candidate response measures which can be used for blocking the attack path; based on multiple iterations of a greedy algorithm, selecting candidate response measures with the maximum security effectiveness for each attack path to form a measure set so as to realize intrusion prevention; wherein in each iteration process, the candidate response measure with the maximum safety effect is selected from the candidate response measures of the attack path to be blocked, the response measure selected this time serves as a deployed measure, and the safety effects of the candidate response measures of the remaining attack path to be blocked are recalculated and used for next iteration selection. According to the method, the overall security effectiveness when a plurality of attack paths are coped can be improved to the maximum extent, and the optimal coping for multi-path attacks is realized.
Owner:INST OF INFORMATION ENG CAS
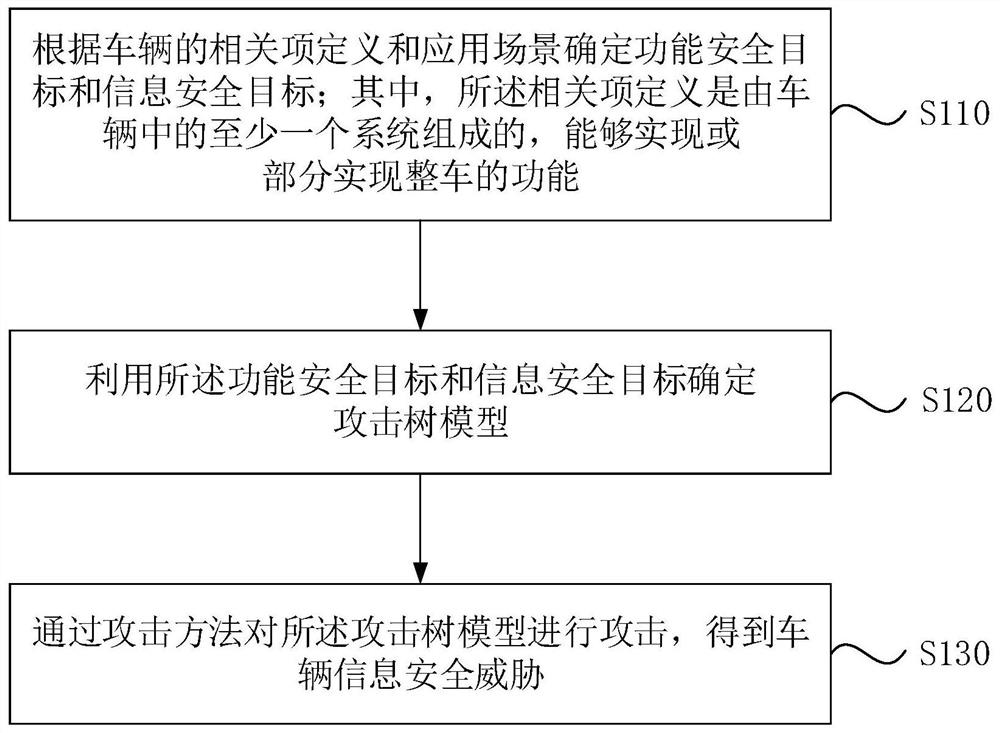
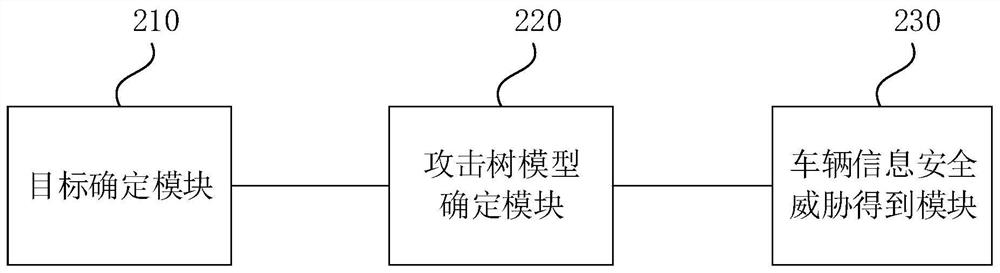
Vehicle information security threat assessment method and device, medium and electronic equipment
ActiveCN113065195AImprove accuracyGeometric CADInternal combustion piston enginesAttackInformation security
The embodiment of the invention discloses a vehicle information security threat assessment method and device, a medium and electronic equipment. The method comprises the following steps: determining a function safety target and an information safety target according to related item definitions and application scenes of a vehicle, wherein the definition of the related items is composed of at least one system in the vehicle, and the functions of the whole vehicle can be achieved or partially achieved; determining an attack tree model by using the function security target and the information security target; and attacking the attack tree model through an attack method to obtain a vehicle information security threat. According to the technical scheme, the information security technology and the function security technology can be fused, the vehicle risk is assessed based on the multi-dimensional attack method, and the accuracy of vehicle security threat assessment is improved.
Owner:CHINA FIRST AUTOMOBILE
Attack path parallel prediction method for power system network
PendingCN114884683AImprove securitySecuring communicationInformation technology support systemPathPingAttack
The invention discloses an attack path parallel prediction method for a power system network, and relates to the field of industrial control system security, and the technical scheme is as follows: (1) assuming an attack target of an attacker: identifying security vulnerabilities existing in SCADA (Supervisory Control And Data Acquisition) which can be utilized by the attacker; (2) identifying possible security vulnerabilities in SCADA and constructing an attack tree; (3) evaluating the safety condition of each leaf node, and calculating the attack success probability of each leaf node; and (4) the attack success probability of each attack path is calculated, and the security of the SCADA system is enhanced.
Owner:国网西藏电力有限公司电力科学研究院
Using attack trees to reduce memory consumption by rule engines
ActiveUS11301134B2Reduce memory consumptionReduce consumptionInput/output to record carriersDigital data protectionComputer networkAttack
A method is provided for reducing memory consumption by a rule engine. The method includes receiving attack trees, each having nodes and edges. Each node represents a security event and is associated with a detection rule for detecting an occurrence thereof. Each edge connects a respective node pair. The method includes assigning a watchpoint to each leaf node. The method includes moving the watchpoint assigned to any leaf node to a next upstream node, responsive to detecting an occurrence of the security event represented by the leaf node. The method includes erasing the watchpoint assigned to all downstream nodes relative to the next upstream node, responsive to the next upstream node being connected to a next downstream node using an edge having an “OR” join type. Only the rules for nodes currently having the watchpoint assigned are loaded into a memory device during runtime, while excluding rules for remaining nodes.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com