Method, device and system for determining safety event of electric power monitoring system
A technology for system security and power monitoring, applied in electrical components, transmission systems, digital transmission systems, etc., can solve problems that are difficult to apply directly, and achieve the effect of reducing redundancy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
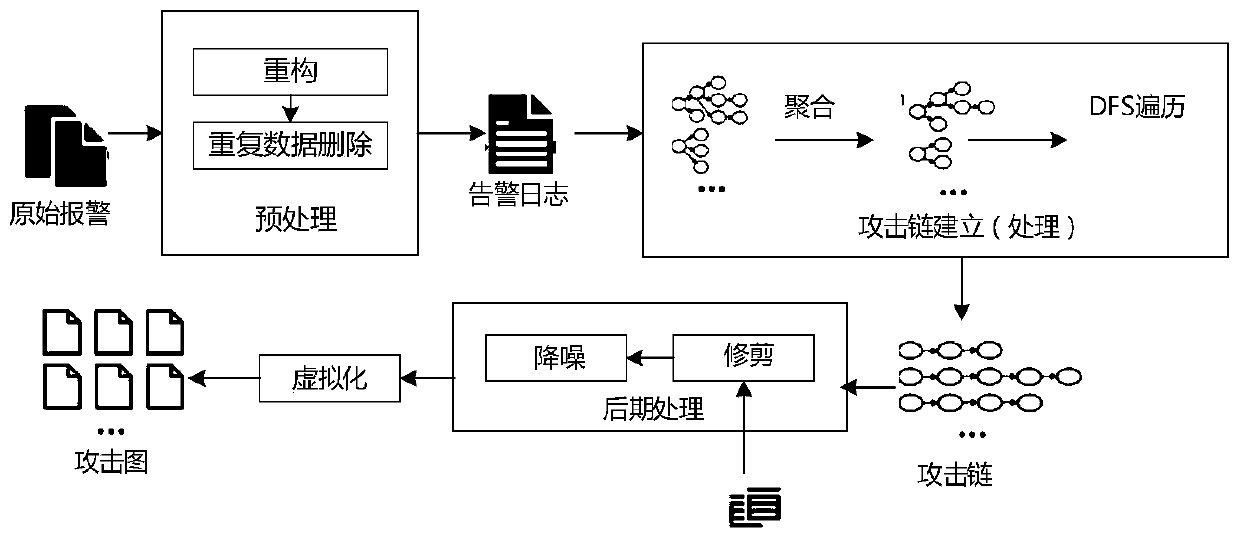
[0055] Such as figure 1 Shown is the flow chart of the method for determining the security event of the power monitoring system in the embodiment of the present invention. The input is the original alarm of the power monitoring system. After preprocessing, an analyzable alarm log is formed, and then sent to the attack chain initial construction module to undergo aggregation and The attack chain is formed after traversal, but the attack chain at this time still contains a large number of unreasonable events, so it needs to be pruned and reduced by the post-processing module to form the final attack chain. Finally, in order to make the result more intuitive, we introduced Visualize, draw the interconnected attack chains into an attack graph, and the final output is an attack graph.
[0056] Specifically, the method for determining a security event of a power monitoring system in an embodiment of the present invention includes the following steps:
[0057] Step (1) Obtain an alarm log...
Embodiment 2
[0111] Based on the same inventive concept as Embodiment 1, an embodiment of the present invention provides a device for determining a security event of a power monitoring system, including:
[0112] The obtaining module is used to obtain the alarm log, and the alarm log contains several alarm records;
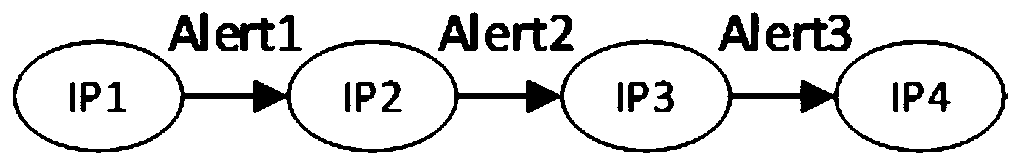
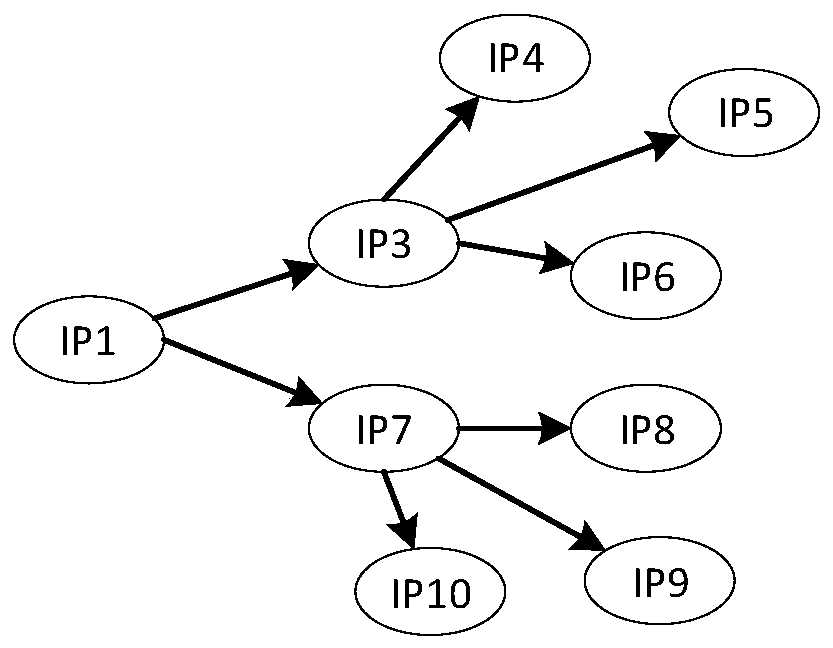
[0113] The modeling module is used to model the tree diagram of the alarm log based on the correlation between each alarm record to obtain the attack tree;
[0114] The aggregation processing module is used to obtain an initial attack chain set after performing aggregation processing on the attack tree;
[0115] The pruning module is used to prune each initial attack chain in the initial attack chain set to form a final attack chain set, and determine the security event of the power monitoring system.
[0116] The rest are the same as in Example 1.
Embodiment 3
[0118] Based on the same inventive concept as the embodiment 1, the embodiment of the present invention provides a system for determining a security event of a power monitoring system, which is characterized in that it includes:
[0119] A processor suitable for implementing instructions; and
[0120] The storage device is adapted to store a plurality of instructions, and the instructions are adapted to be loaded by a processor and execute the steps described in any one of Embodiment 1.
[0121] Those skilled in the art should understand that the embodiments of the present application can be provided as methods, systems, or computer program products. Therefore, this application may adopt the form of a complete hardware embodiment, a complete software embodiment, or an embodiment combining software and hardware. Moreover, this application may adopt the form of a computer program product implemented on one or more computer-usable storage media (including but not limited to disk storag...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com