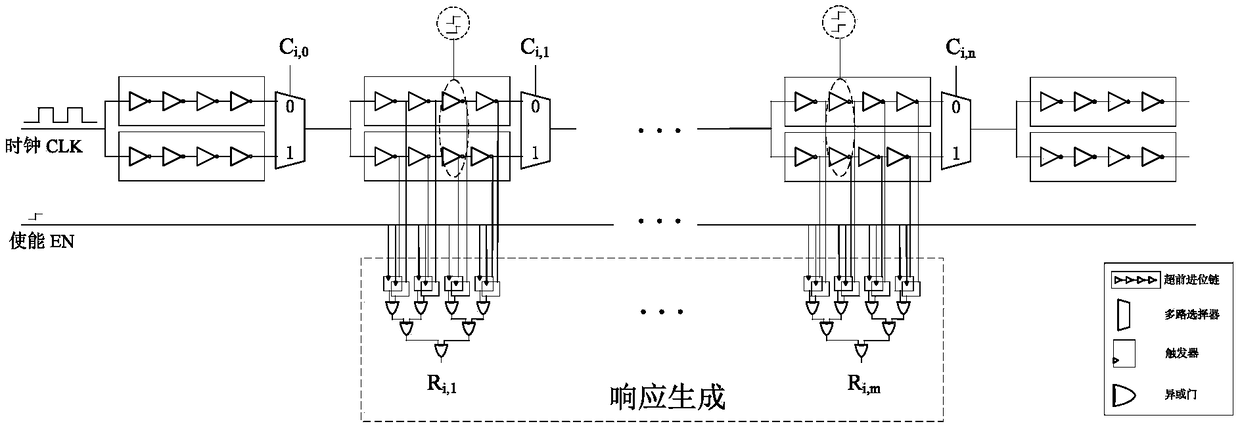
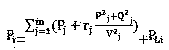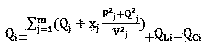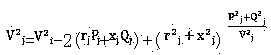Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
70 results about "Forward chaining" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Forward chaining (or forward reasoning) is one of the two main methods of reasoning when using an inference engine and can be described logically as repeated application of modus ponens. Forward chaining is a popular implementation strategy for expert systems, business and production rule systems. The opposite of forward chaining is backward chaining.
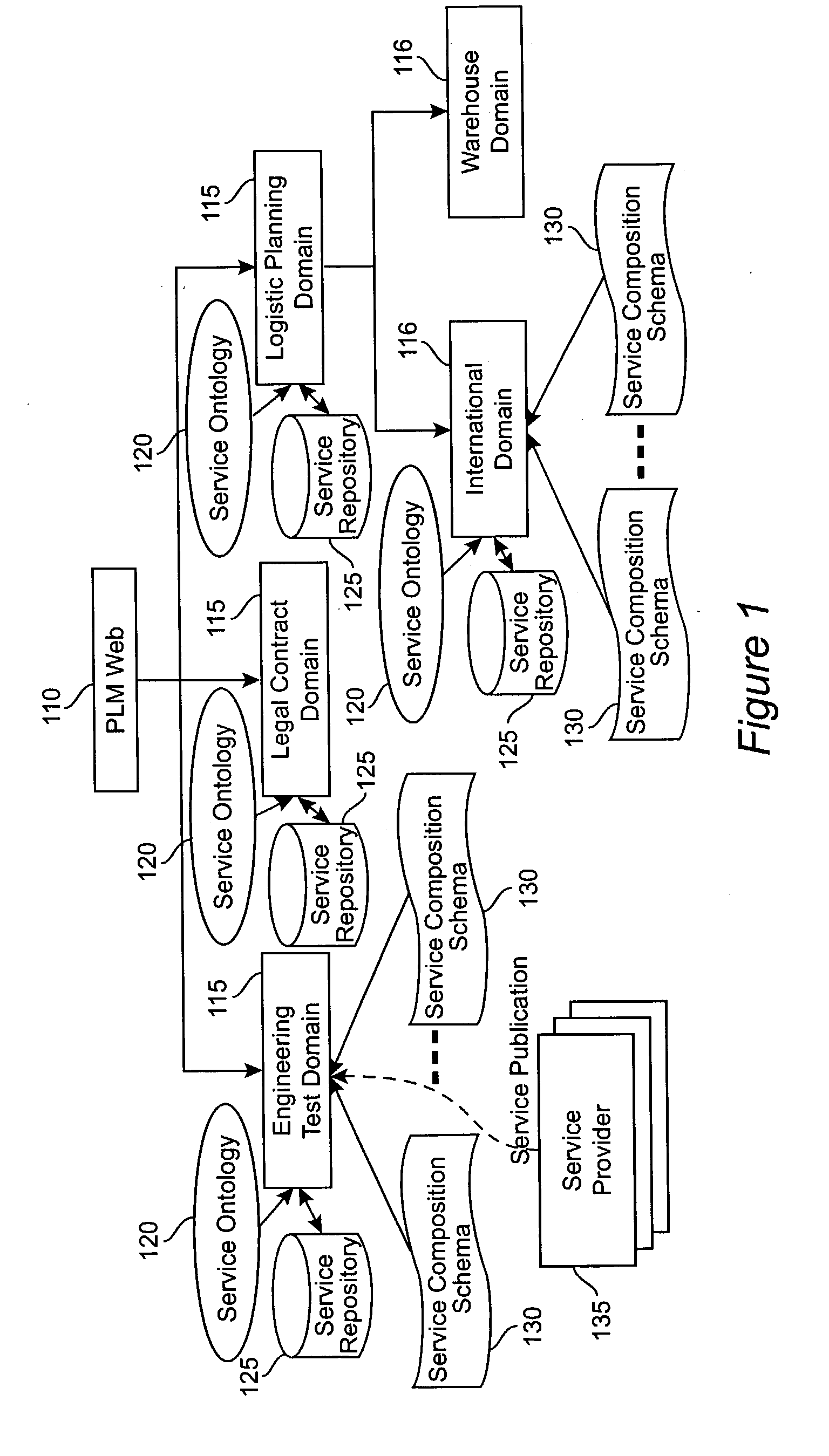
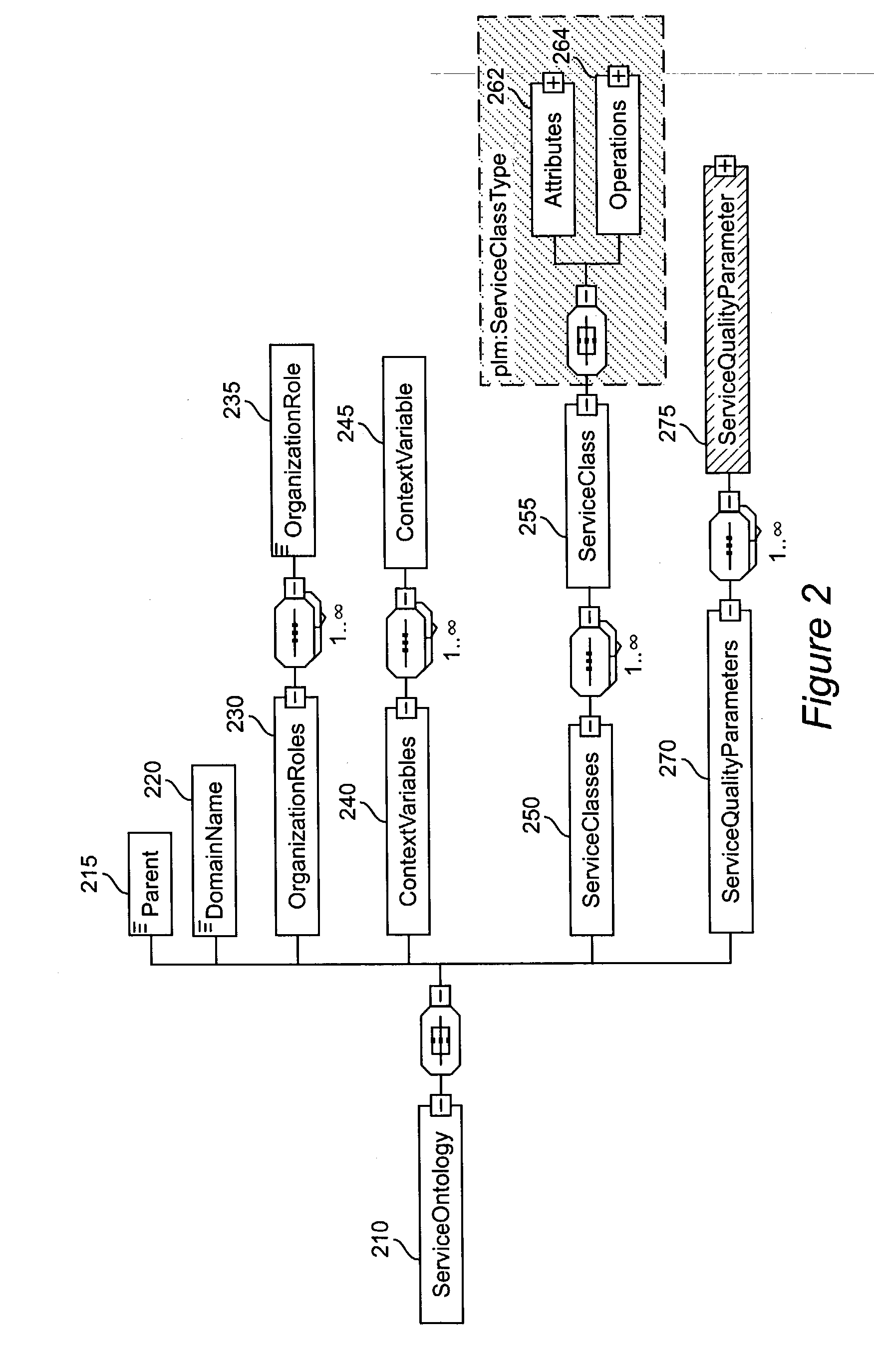
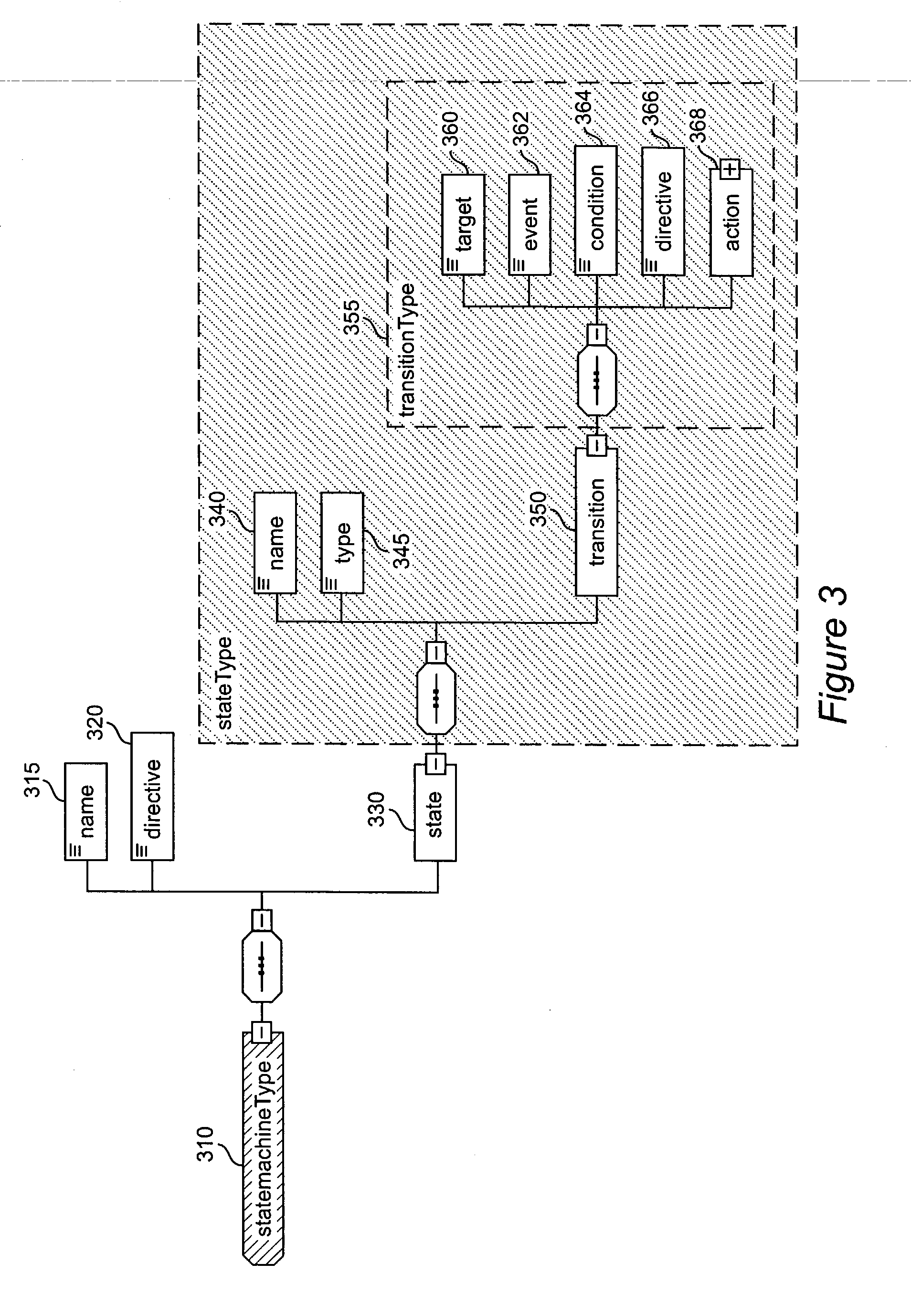
Method and apparatus for product lifecycle management in a distributed environment enabled by dynamic business process composition and execution by rule inference
InactiveUS20040162741A1Detect and resolve conflictOffice automationResourcesDistributed servicesNetwork topology
A system and method for supporting Product Lifecycle Management over a distributed service network topology that connects a hierarchy of functional domains, each domain having a service ontology and one or more service composition schemas defined by the service ontology. Each service composition schema models a business process in its domain. Descriptions of services provided to each domain are published to a service repository by providers of the services, in conformity with one of the service composition schemas. There is a business process proxy provided by the service provider for each service description, which encapsulates for public access the internal processes of the service provider. The invention makes use of an event messaging protocol that enables service collaboration and ad-hoc workflow composition. Each business process is implemented by an ad-hoc workflow comprised of one or more tasks connected by one or more business rules. For each business process there is a business flow manager that dynamically composes ad-hoc workflow prior to execution and dynamically modifies the ad-hoc workflow as the business process executes. The business flow manager uses backward-chain inferencing and then forward-chain inferencing to generate the ad-hoc workflows, based on user identification of a target task. The business flow manager is able to stop execution of the workflow and regenerate a workflow for remaining tasks in response to events received over the network from service providers, and is also able to detect conflicts in the workflows at composition time and at execution time.
Owner:IBM CORP
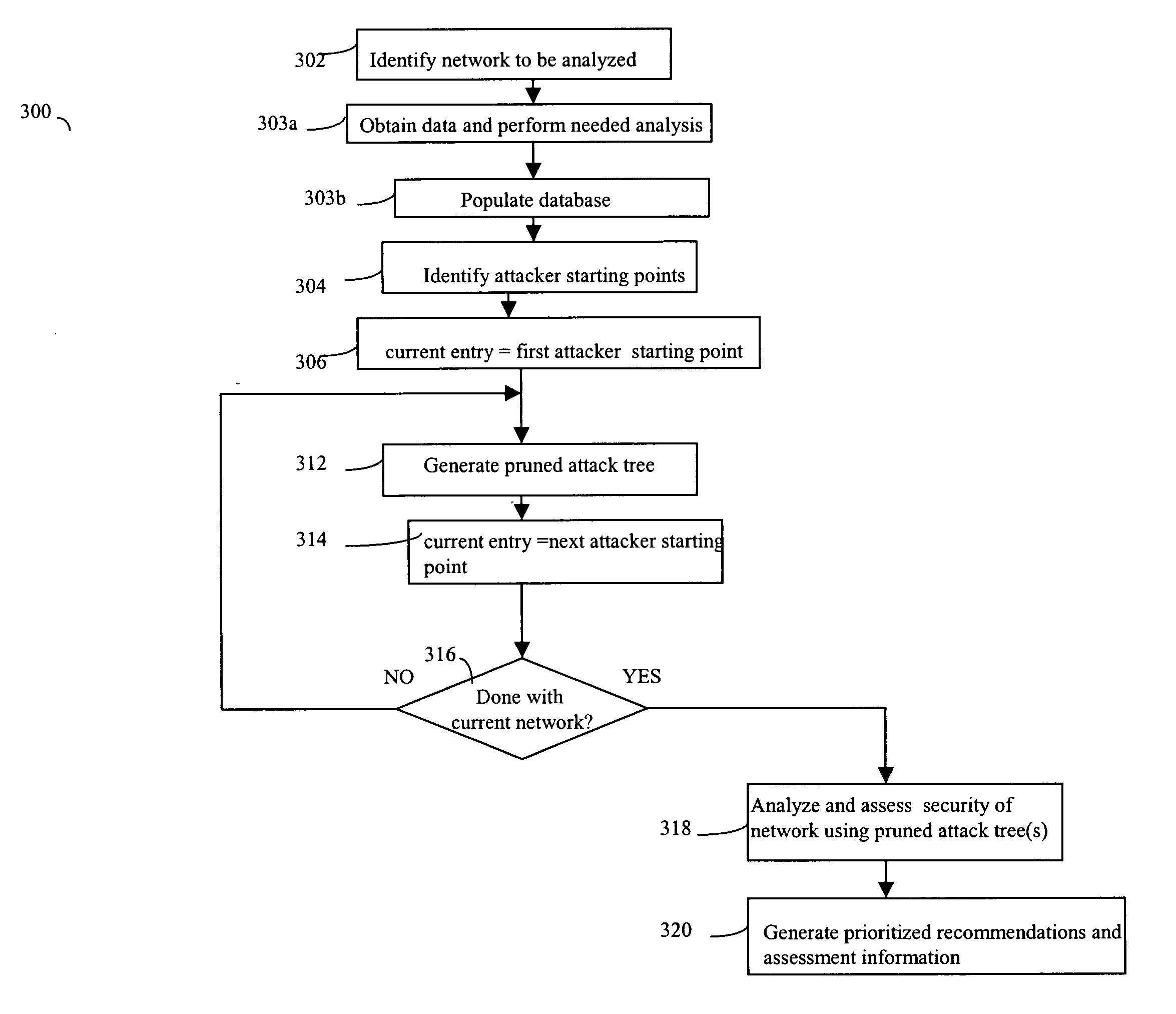
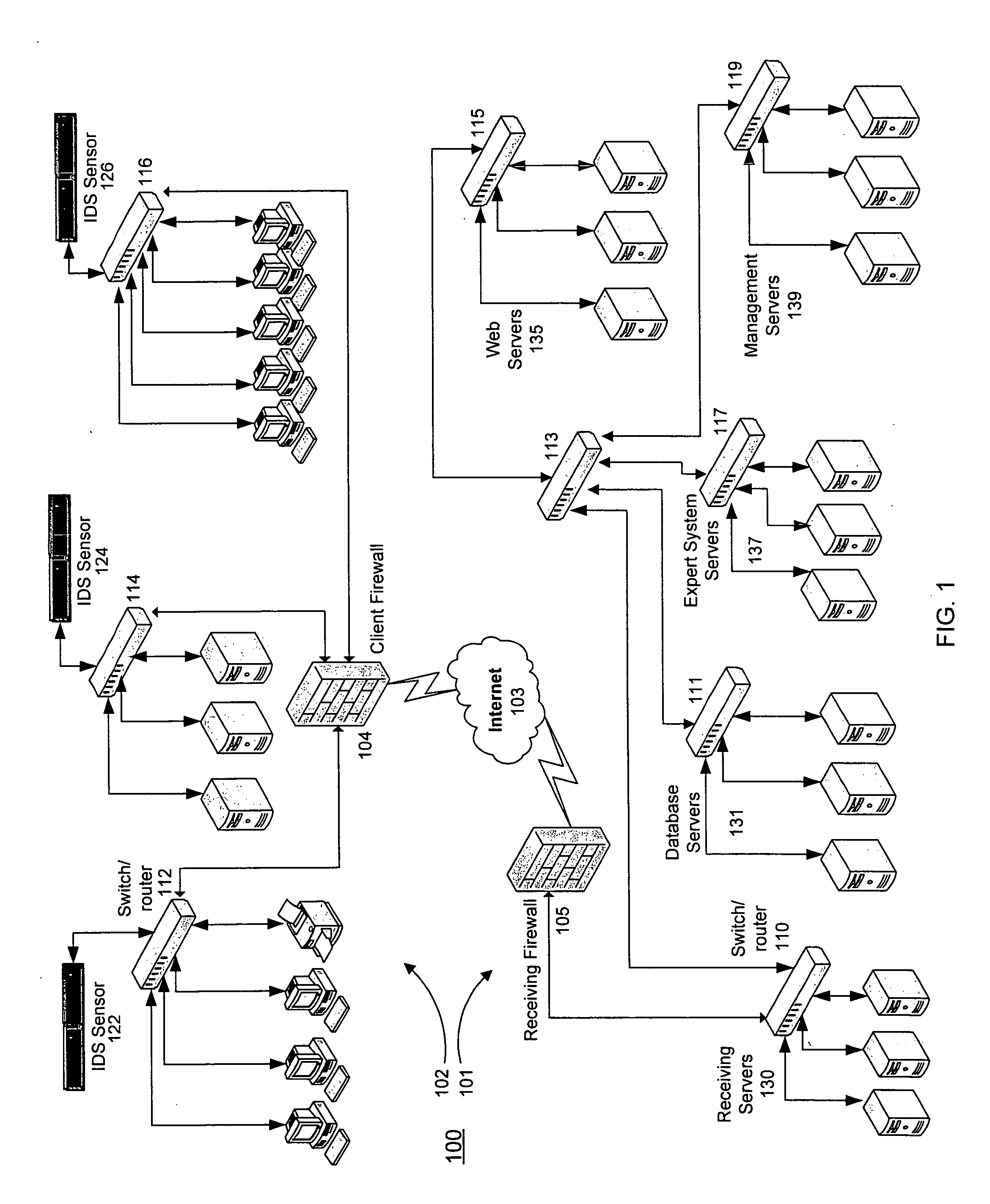
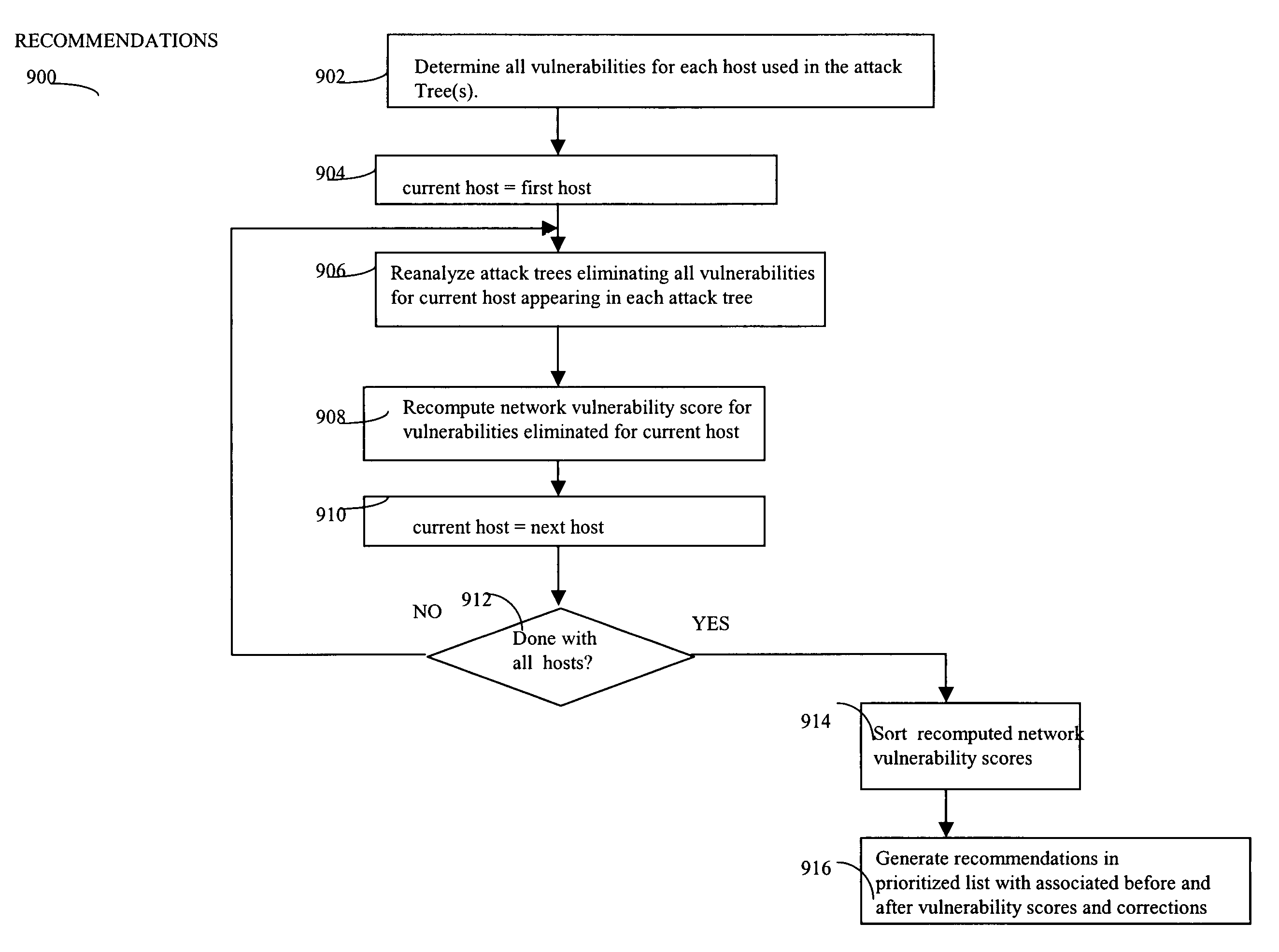
Network security planning architecture
ActiveUS20050138413A1Expand accessBroaden their knowledgeMemory loss protectionDigital data processing detailsForward chainingAttack tree
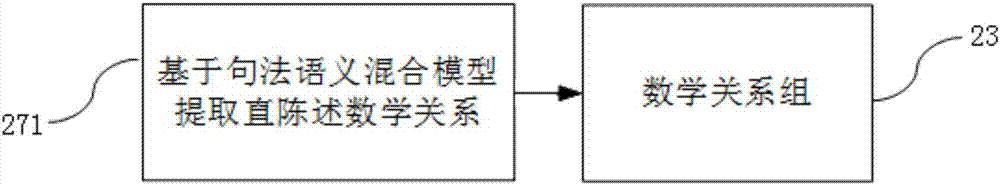
Described are techniques used for assessing the security of a network. Pruned attack trees are generated using a forward chaining, breadth-first technique representing the attack paths of a possible attacker in the network. A vulnerability score is determined for each network and attacker starting point using attack loss values assigned to each host and information extracted from the attack tree(s) concerning compromised hosts. Different hypothetical alternatives may be evaluated to improve security of the network and each alternative may be evaluated by recomputing the network vulnerability score and comparing the recomputed score to the original network vulnerability score. Also disclosed is a method for determining end-to-end connectivity of a network. The resulting end-to-end connectivity information is used in generating the pruned attack tree.
Owner:MASSACHUSETTS INST OF TECH
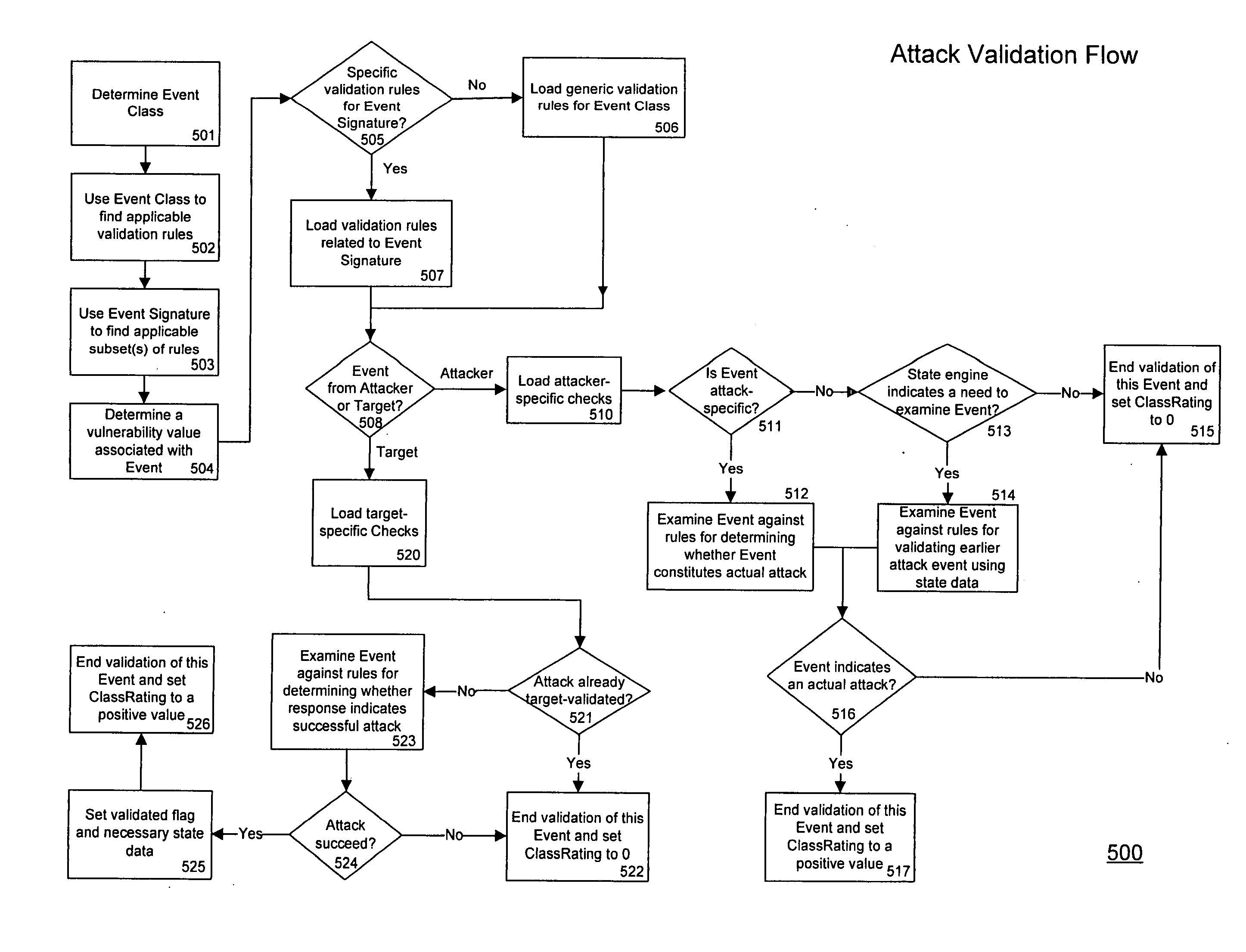
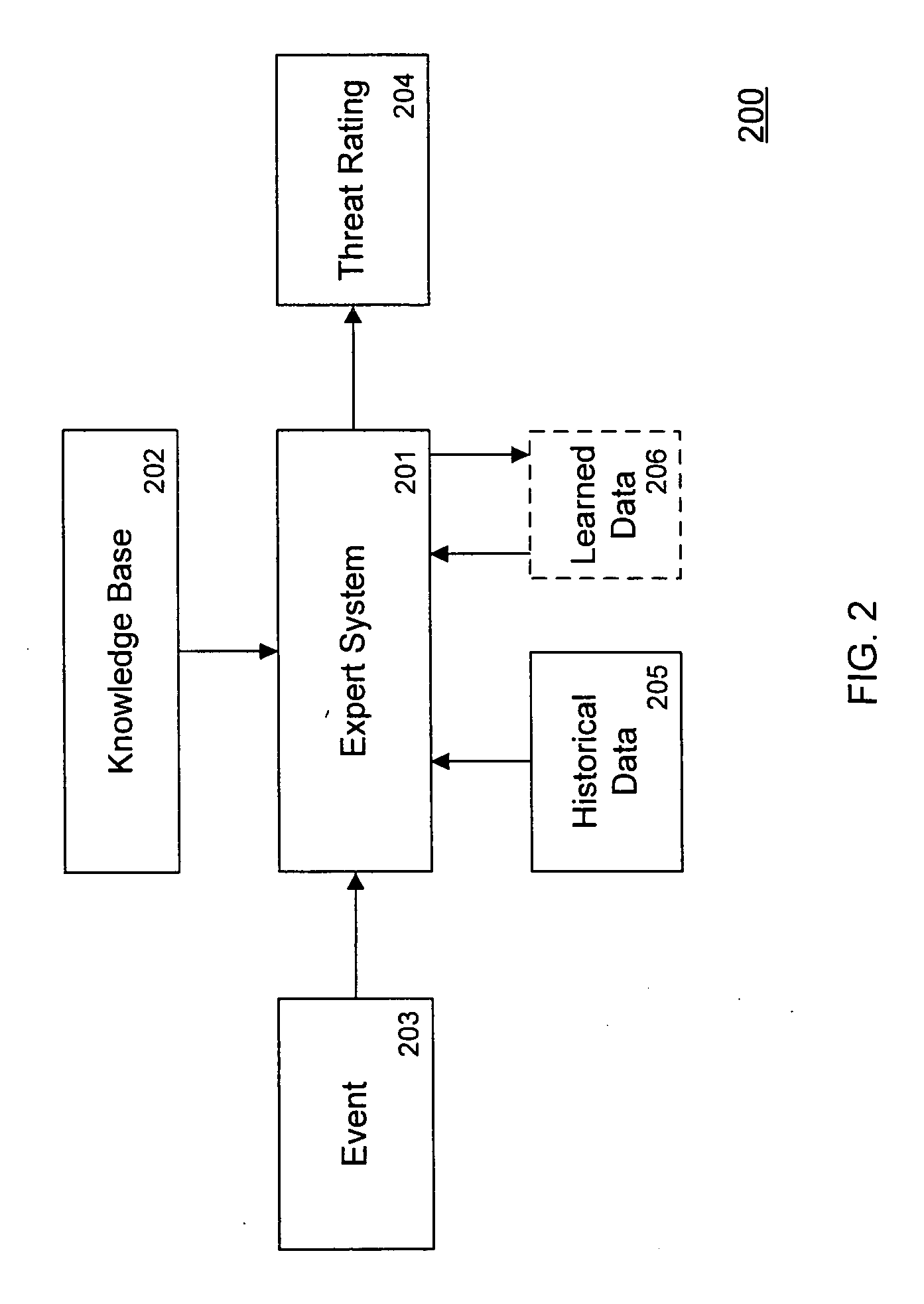
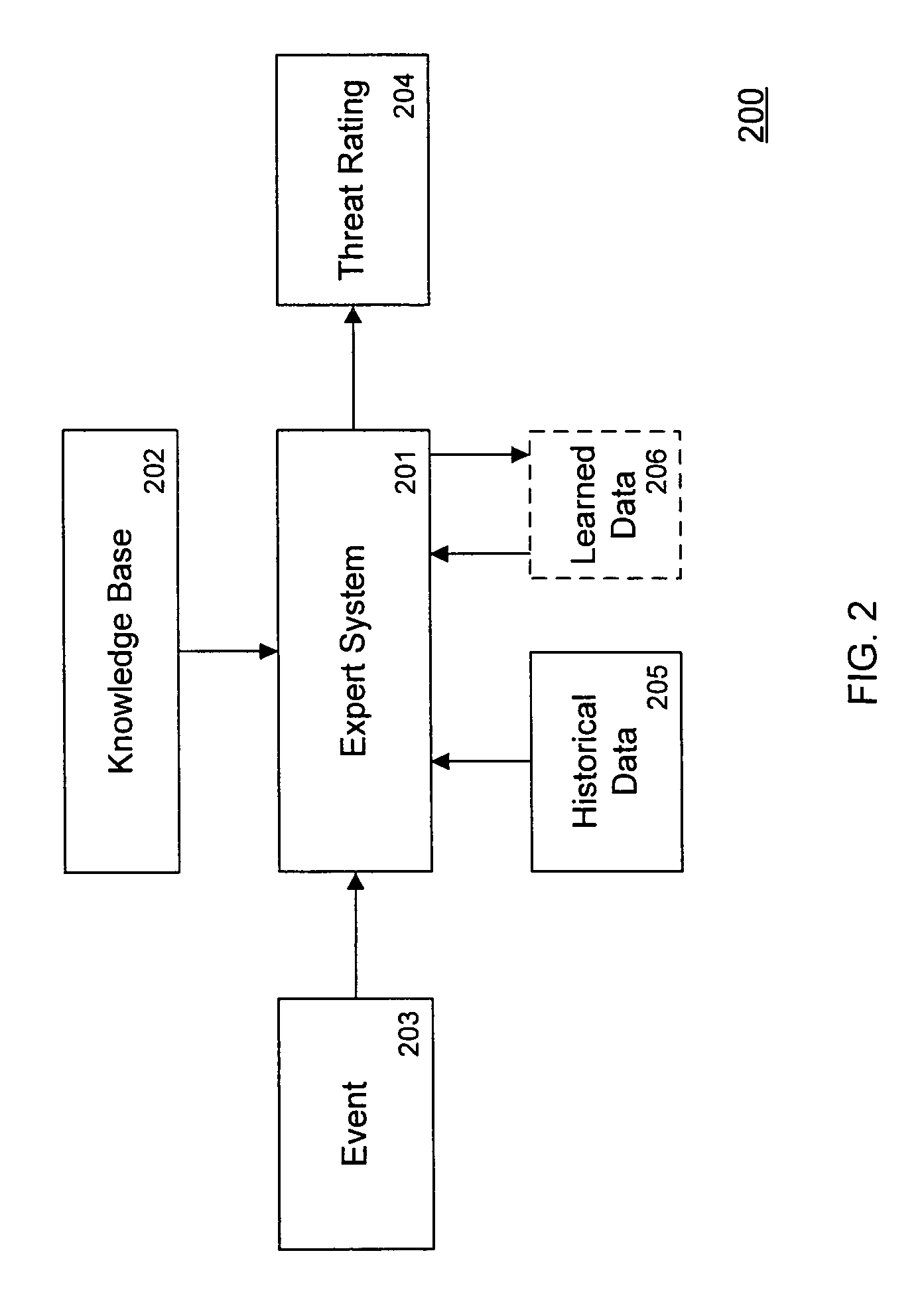
Threat scoring system and method for intrusion detection security networks
ActiveUS20070169194A1Rapid deploymentAutomate quicklyMemory loss protectionError detection/correctionTriage CodeSecurity expert
Embodiments of the invention provide a security expert system (SES) that automates intrusion detection analysis and threat discovery that can use fuzzy logic and forward-chaining inference engines to approximate human reasoning process. Embodiments of the SES can analyze incoming security events and generate a threat rating that indicates the likelihood of an event or a series of events being a threat. In one embodiment, the threat rating is determined based on an attacker rating, a target rating, a valid rating, and, optionally, a negative rating. In one embodiment, the threat rating may be affected by a validation flag. The SES can analyze the criticality of assets and calibrate / recalibrate the severity of an attack accordingly to allow for triage. The asset criticality can have a user-defined value. This ability allows the SES to protect and defend critical network resources in a discriminating and selective manner if necessary (e.g., many attacks).
Owner:ALERT LOGIC
Threat scoring system and method for intrusion detection security networks
ActiveUS7594270B2Rapid deploymentAutomate quicklyMemory loss protectionError detection/correctionTriageSecurity expert
Owner:ALERT LOGIC
Network security planning architecture
ActiveUS7194769B2Memory loss protectionUnauthorized memory use protectionForward chainingAttack tree
Described are techniques used for assessing the security of a network. Pruned attack trees are generated using a forward chaining, breadth-first technique representing the attack paths of a possible attacker in the network. A vulnerability score is determined for each network and attacker starting point using attack loss values assigned to each host and information extracted from the attack tree(s) concerning compromised hosts. Different hypothetical alternatives may be evaluated to improve security of the network and each alternative may be evaluated by recomputing the network vulnerability score and comparing the recomputed score to the original network vulnerability score. Also disclosed is a method for determining end-to-end connectivity of a network. The resulting end-to-end connectivity information is used in generating the pruned attack tree.
Owner:MASSACHUSETTS INST OF TECH
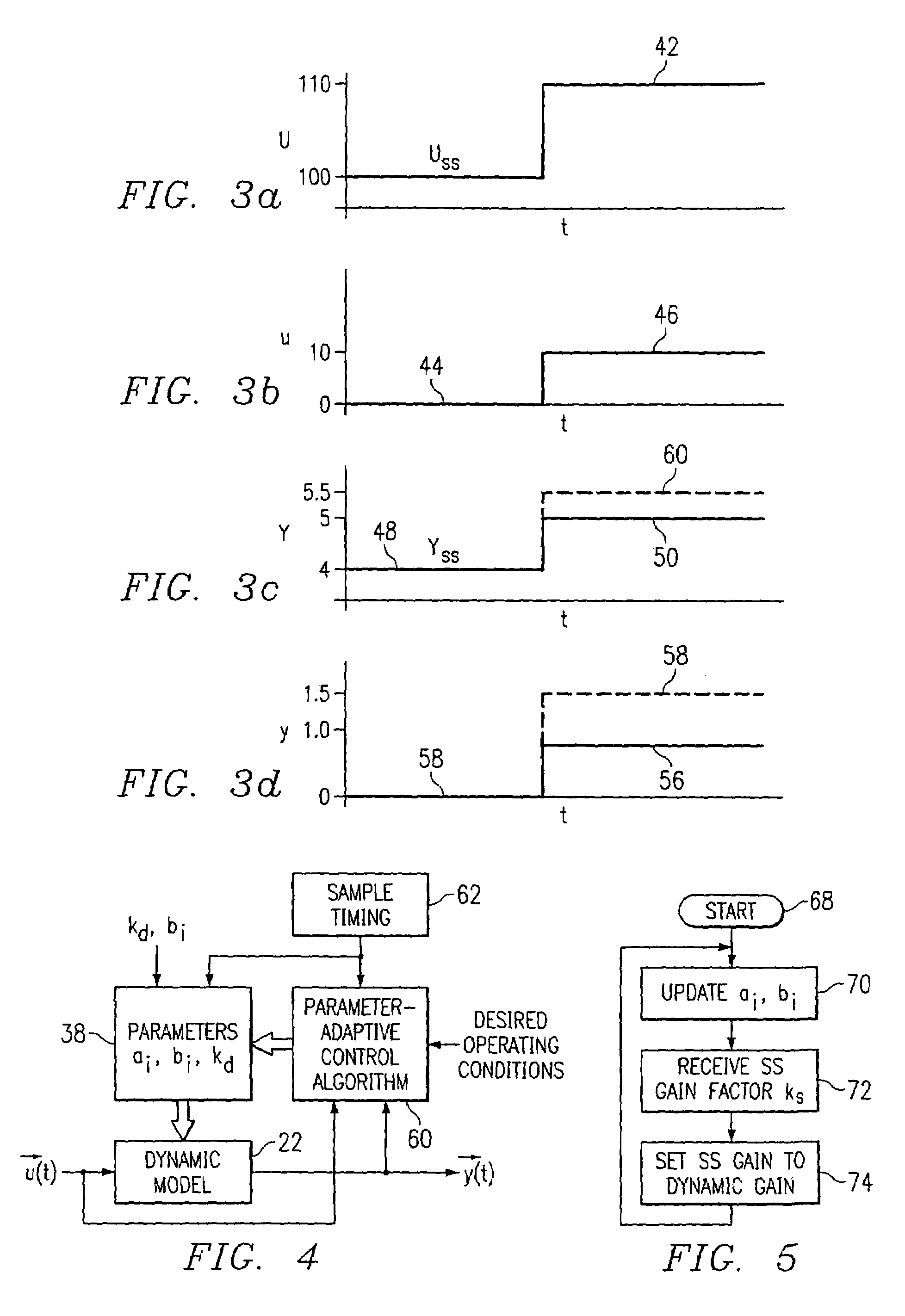
Kiln control and upset recovery using a model predictive control in series with forward chaining
InactiveUS7149590B2Simulator controlComputation using non-denominational number representationPredictive controllerControl theory
A method for controlling a non-linear process includes the steps of first providing a controller that is operable to receive inputs representing measured variables of the process and predicting on an output of the controller predicted control values for manipulatible variables that control the process. An expert system is provided that models the actions of an operator of the process over an operating region of the process that represents a set of rules for actions to be taken by an operator upon the occurrence of predetermined conditions in the operation of the process. The operation of the controller is modified with the expert system when one of the predetermined conditions exists.
Owner:ROCKWELL AUTOMATION TECH
Driving an Interactive Decision Service From a Forward-Chaining Rule Engine
InactiveUS20150142703A1Natural language data processingKnowledge representationMultiple criteriaData mining
Disclosed techniques include generating a plurality of questions, each question based upon one or more conditions of a plurality of conditions, wherein the plurality of conditions are generated a plurality of business rules associated with a forward changing rule engine; identifying, as a side effect of evaluating the plurality of business rules for outcome data, missing information corresponding to the plurality of questions; and selecting, for presentation to a user, a first question of the plurality of questions to elicit the missing information from the user.
Owner:IBM CORP
Parallel computer network and method for telecommunications network simulation to route calls and continuously estimate call billing in real time
InactiveUS6614893B1Use minimizedPower maximizationMultiplex system selection arrangementsInterconnection arrangementsTelecommunications networkAnalog computer
A telecommunications call routing and billing computer system includes a telecommunications network including a junction point including a call routing switching device, and including two call routing links meeting at the junction point and in communication with each other through the call routing switching device; and a call routing simulation network including a junction point simulation computer located at the junction point and in communication with the call routing switching device and the two call routing links. A method of placing a call through such a telecommunications network includes the steps of: placing one junction point simulation computer at each telecommunications network call junction point; for each call placed with the telecommunications network, plotting a call routing vector through the simulation network with forward chaining through the junction point simulation computers; and sending routing vector information back through the simulation network with rearward chaining to direct the call along a parallel routing vector through the telecommunications network. The method preferably includes the additional steps of: monitoring buffer levels of telecommunications network junction point computers with the simulation computer at each junction point; and using the buffer level information to shunt calls from telecommunications network junction point computers having smaller buffers to those having larger buffers.
Owner:PAIZ RICHARD S
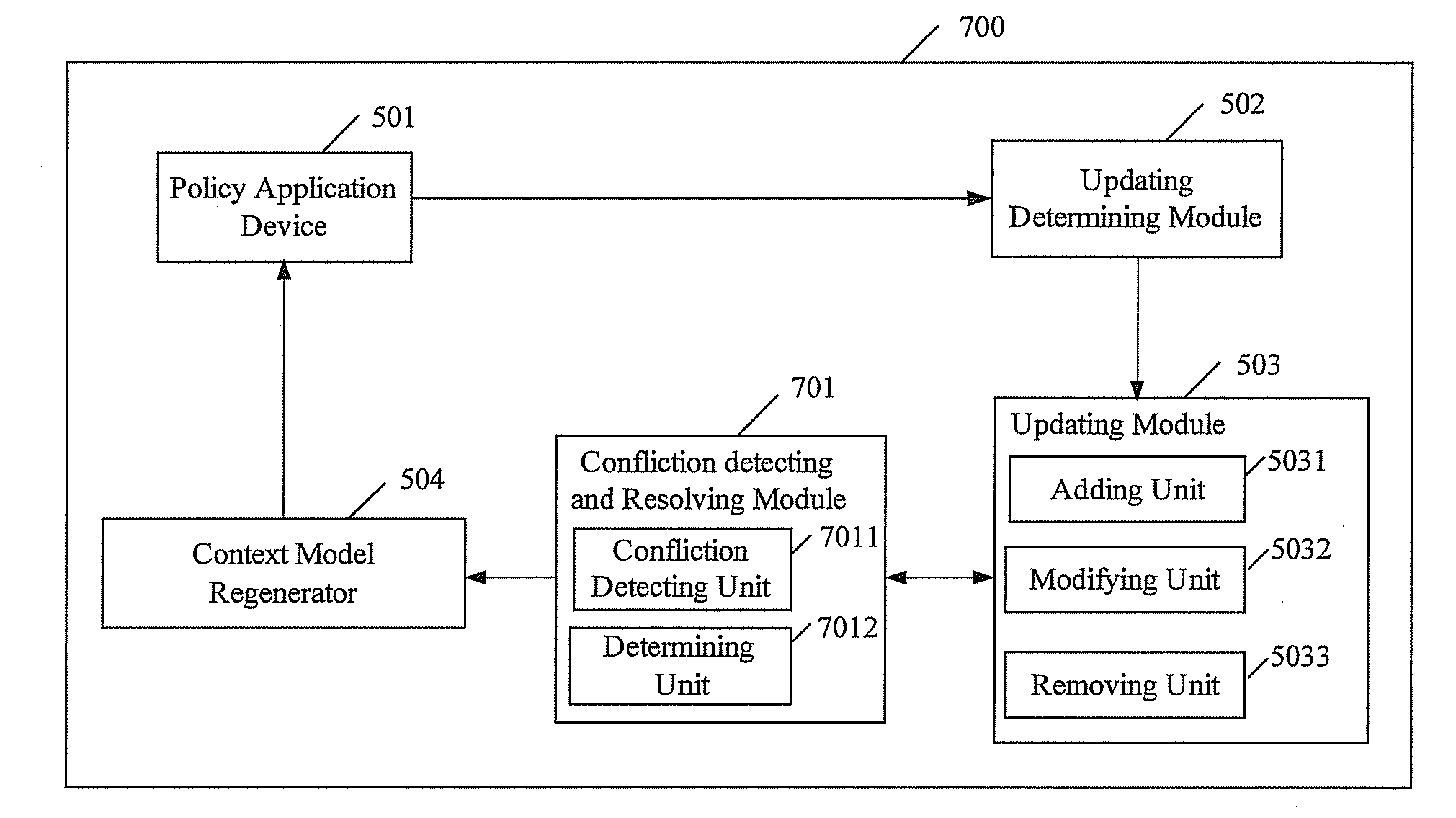
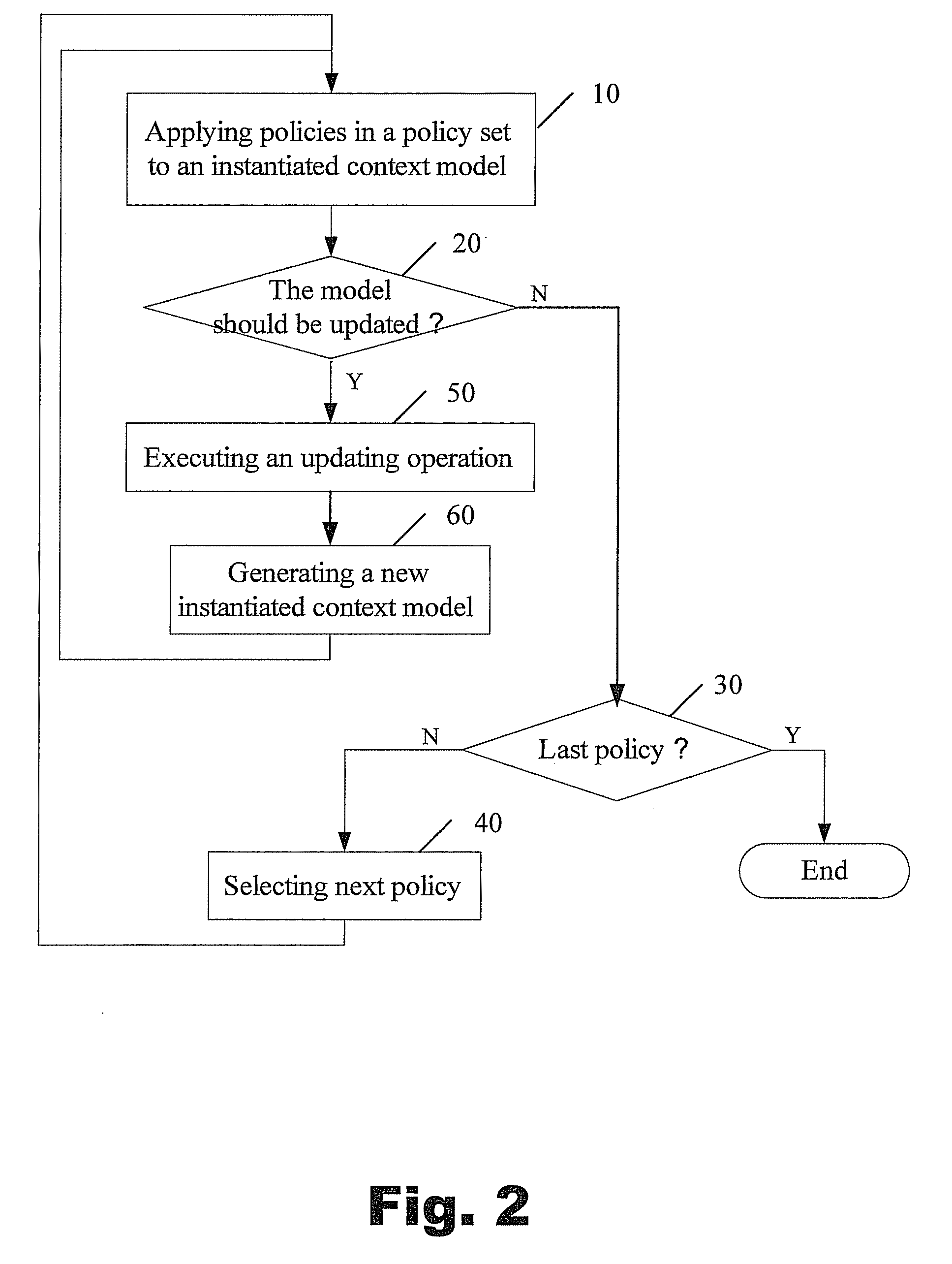
Enforcing context model based policies with forward chaining
A method for enforcing a number of context model based policies with forward chaining comprising applying a policy set including a plurality of policies to an instantiated context model which includes a set of referenced instance documents in XML format, determining whether the instantiated context model should be updated, if the instantiated context model should be updated, executing an updating operation, re-generating a new instantiated context model according to the updated instance documents and the instantiated context model, and applying the policy set to the new instantiated context model, and wherein the policies include a condition part and an action part.
Owner:IBM CORP
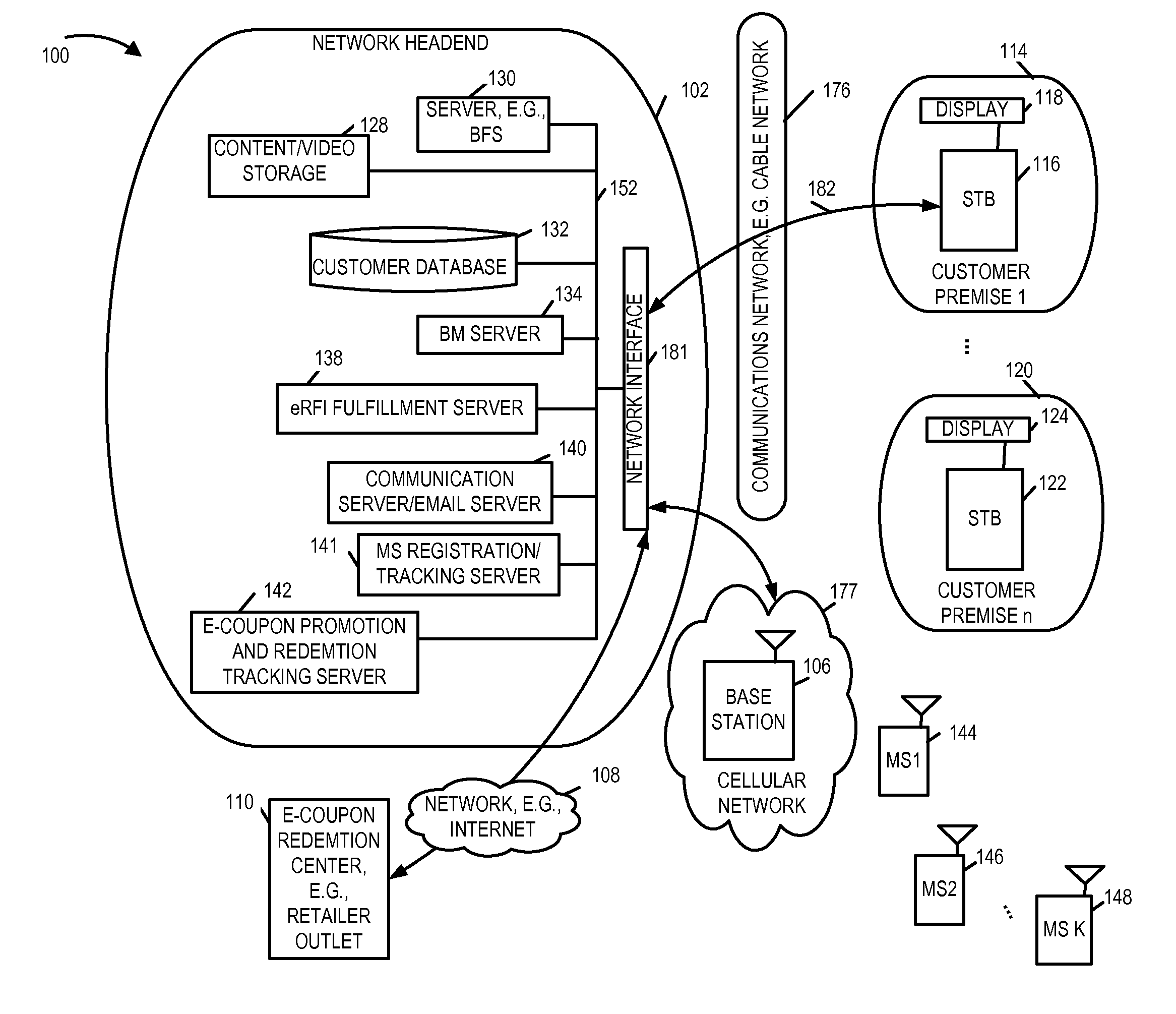
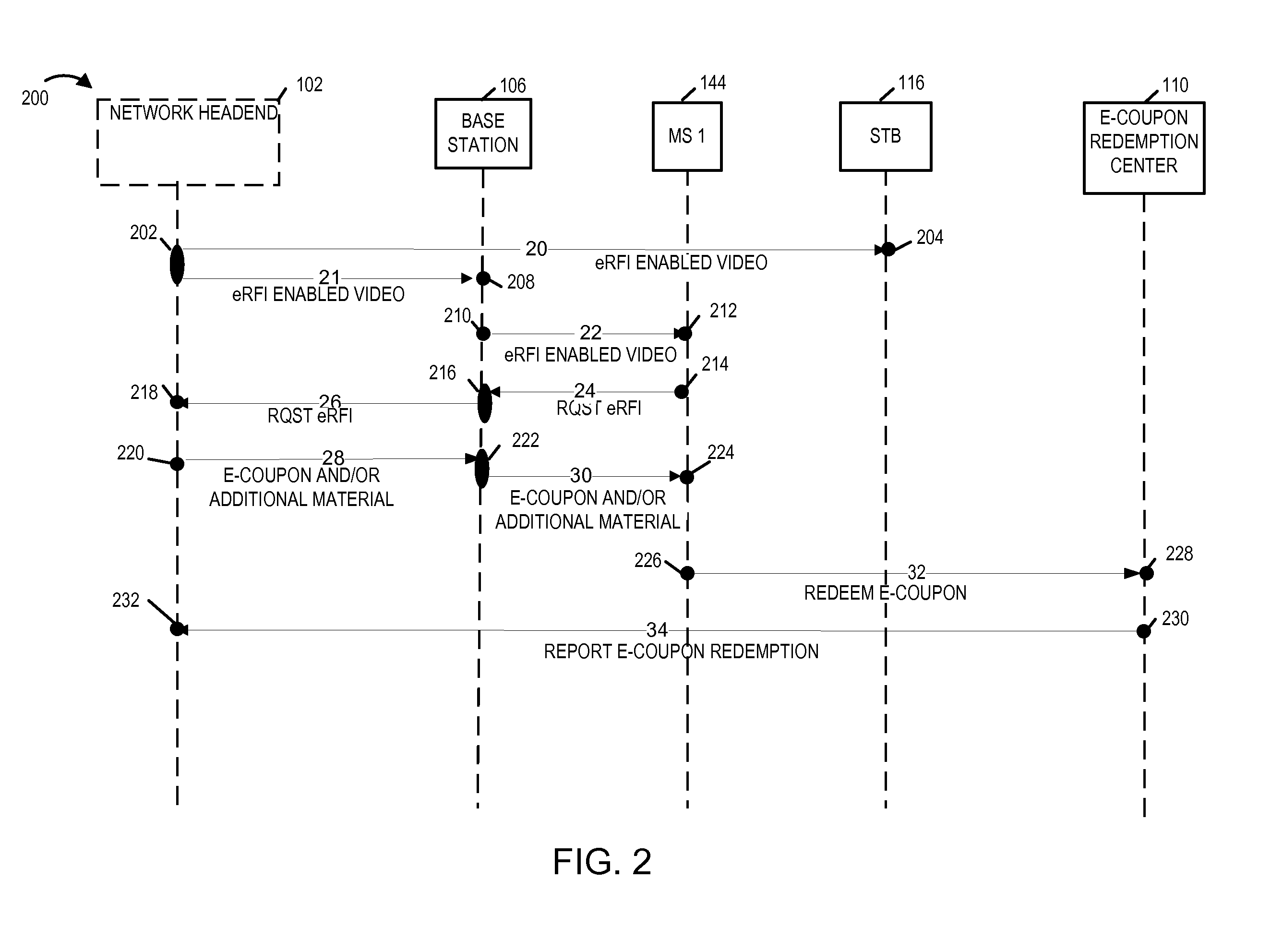
Methods and apparatus for supporting electronic requests for information and promotions on multiple device platforms in an integrated manner
Methods and apparatus for supporting electronic promotions and electronic requests for information, e.g., in an integrated manner, on multiple platforms including, e.g., cable network systems, cell phones, etc., are described. Rewards and / or benefits are tracked in a centralized manner and a subscriber is allowed to accumulate rewards and benefits in a single account irrespective of which device or platform was used to initiate an eRFI and / or to act upon a promotion. The methods and apparatus of the present invention allow a cable service provider which supports eRFI on set top boxes to use the same eRFI server to provide responses to eRFI requests received from devices, e.g., cell phones and / or E-mail devices corresponding to a service subscriber, to forward electronic promotion information and to reward users in a forwarding chain for redemptions of coupons included in forwarded promotion information. Forwarded promotion information securely identifies each device / user in the forwarding chain.
Owner:TIME WARNER CABLE ENTERPRISES LLC
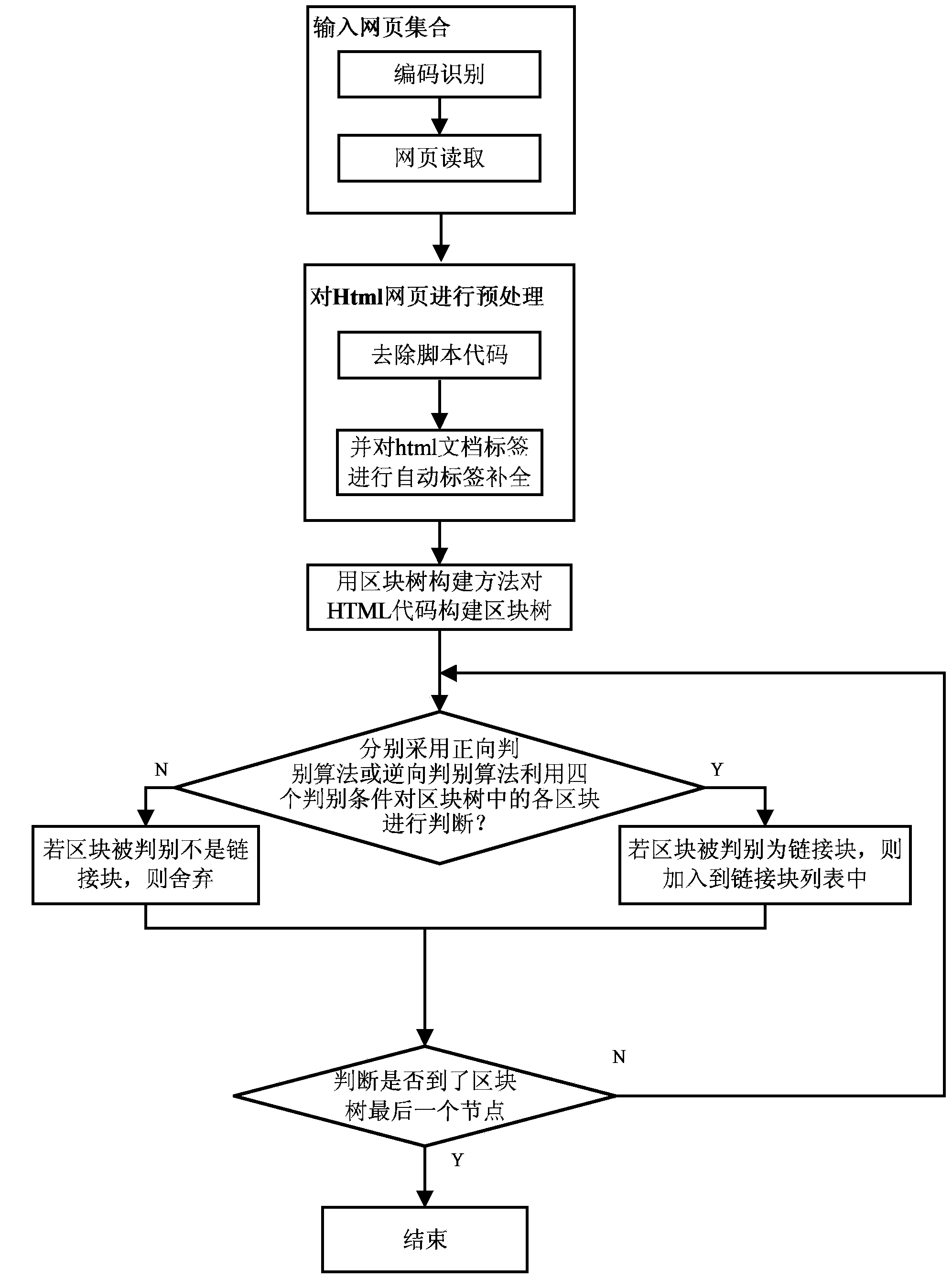
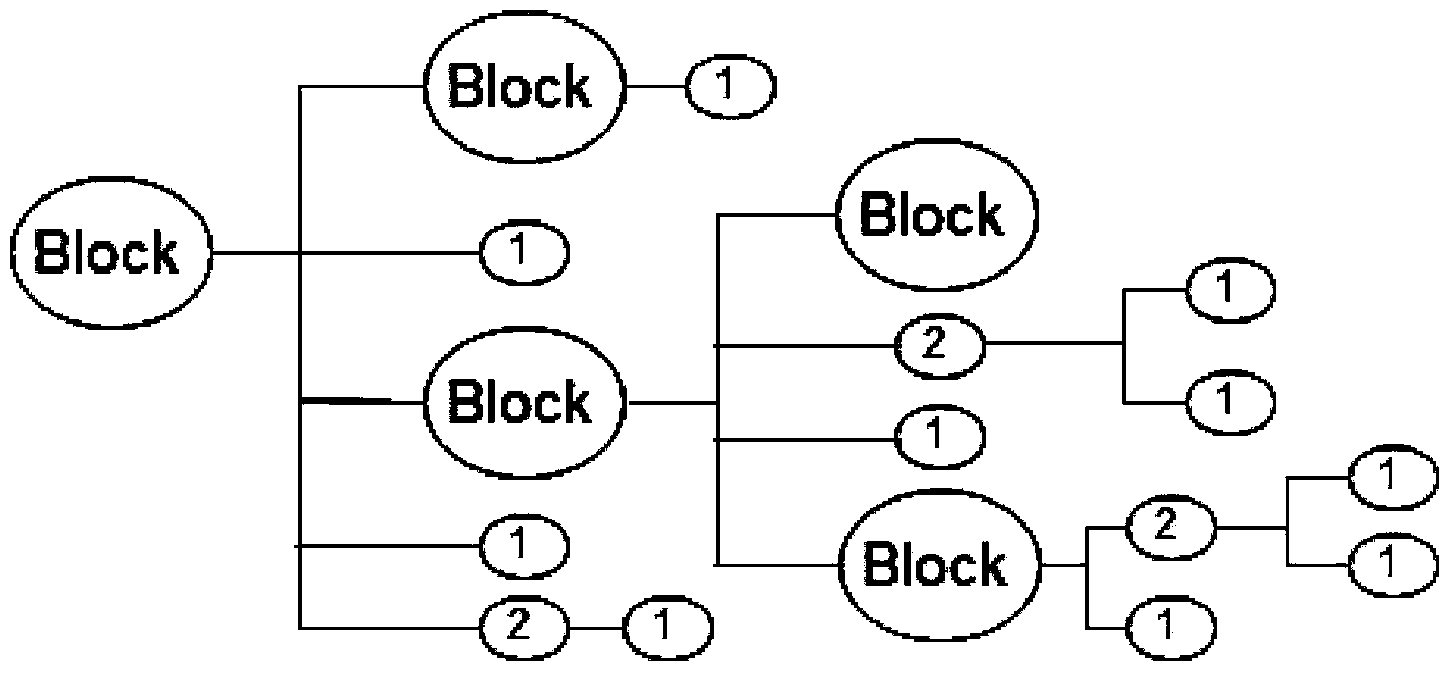
Recognition method for Web page link blocks based on block tree
ActiveCN103927397ALarge granularitySmall particle sizeSpecial data processing applicationsGranularityBasic block
The invention provides a recognition method for Web page link blocks based on a block tree. On the basis of the recognition method, link block distinguishing and estimating indexes are provided, and meanwhile two basic block traversing and distinguishing algorithms including a forward link block distinguishing method and a backward link block distinguishing method are provided; the forward distinguishing method is high in recognition speed and can be used for analysis of indexing type Web pages and text extraction and application, and the granularity of link blocks is large; the backward distinguishing method can control the granularity, quantity and scale of the link blocks easily and flexibly, ensures refinement and integrity of the link blocks and finally achieves comprehensiveness of covering Web page link with the link blocks. The method not only can be used in places with the fine-granularity requirement for the link blocks, but also can be used in places of page denoising, text extracting, automatic template generating through text abstracting and others; the provided block tree serves as the basis of Web page analysis and processing and can be widely applied to Web data preprocessing, data mining and other fields in combination with the two provided traversing and distinguishing methods.
Owner:湖北云服科技有限公司
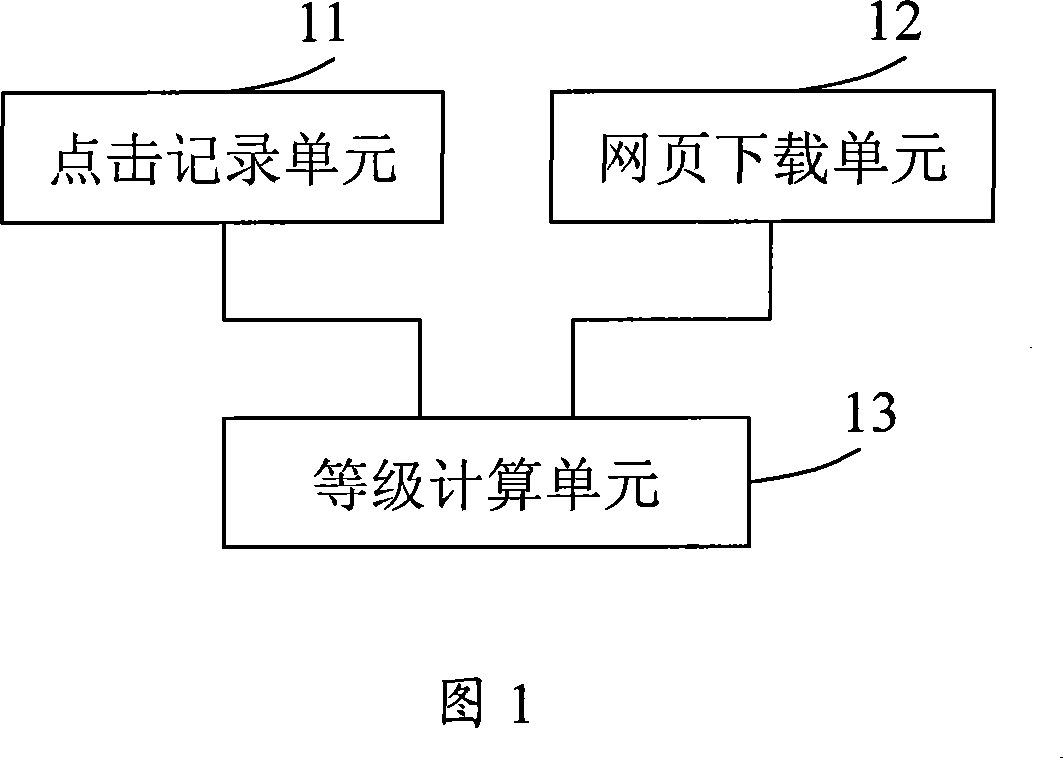
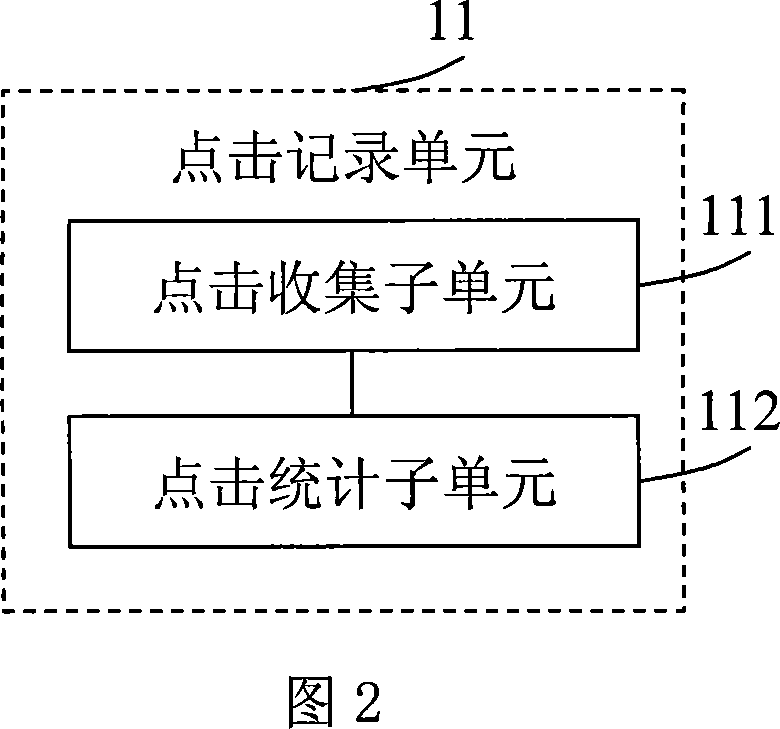
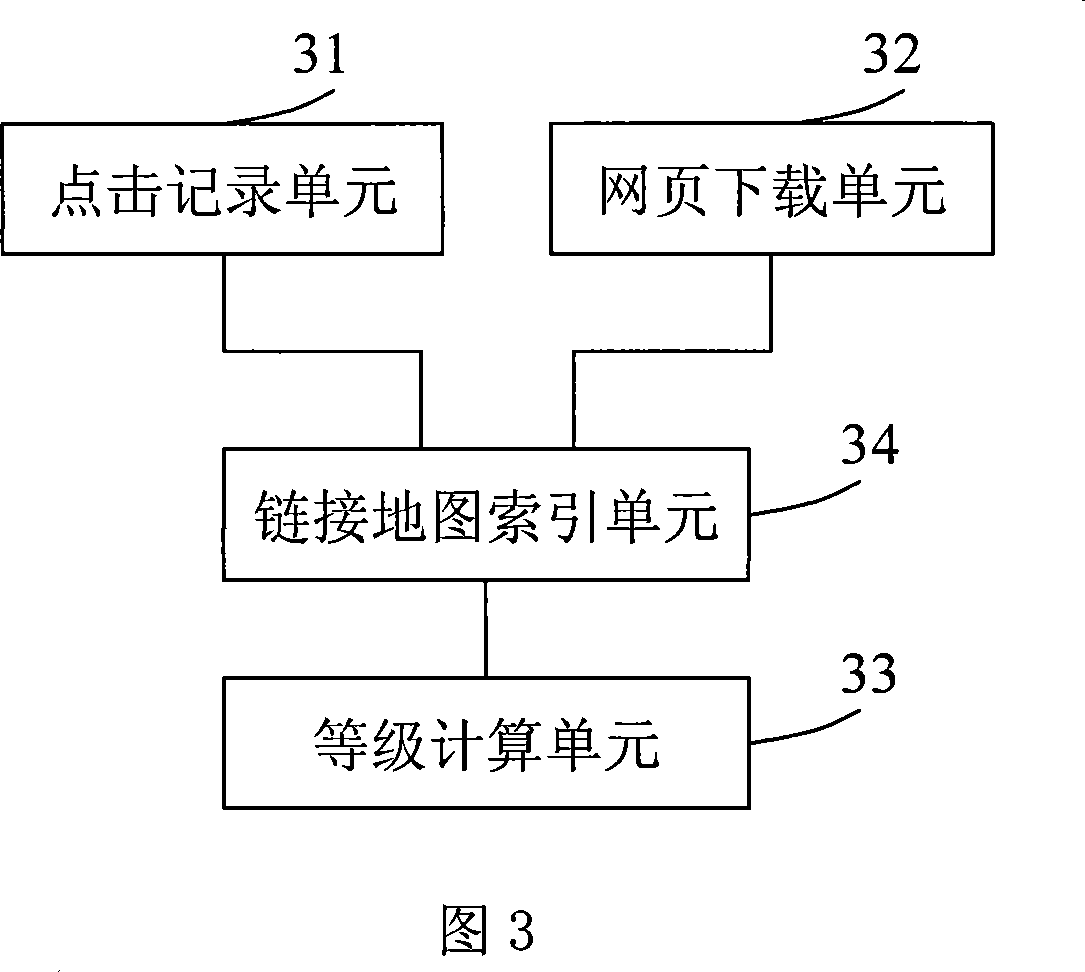
Web page importance evaluation method and system
ActiveCN101079062AThe importance value is reasonableSpecial data processing applicationsRelationship - FatherWeb page
The invention discloses a method of evaluating the web page importance, which comprises the following steps: (a) generating link map which includes a plurality of the corresponding web page nodes and every link corresponding the every webpage; (b) achieving and recording the hitting operation of the node in the link map by the terminal; (c) proceeding iterative computation of the general important value of every node according to the hit record of the link map and node in the link map. The invention also discloses a system of evaluating the web page importance. The invention distributes the general important value of the father node to the general important value of every son node and makes the general important value of the web page more rational by counting the probability of forward link in the hitting web page when the terminal browses the web page.
Owner:SHENZHEN SHI JI GUANG SU INFORMATION TECH
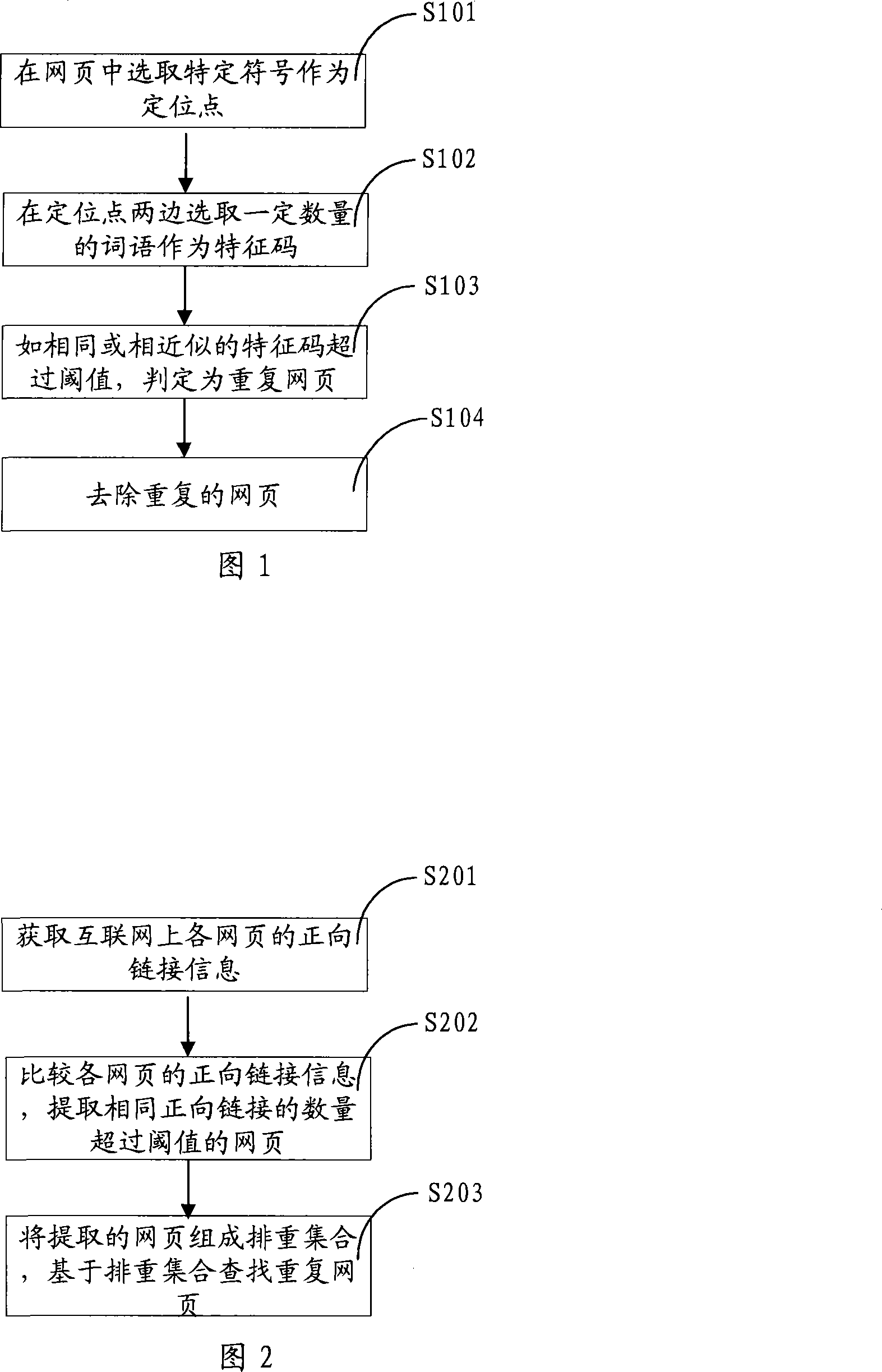
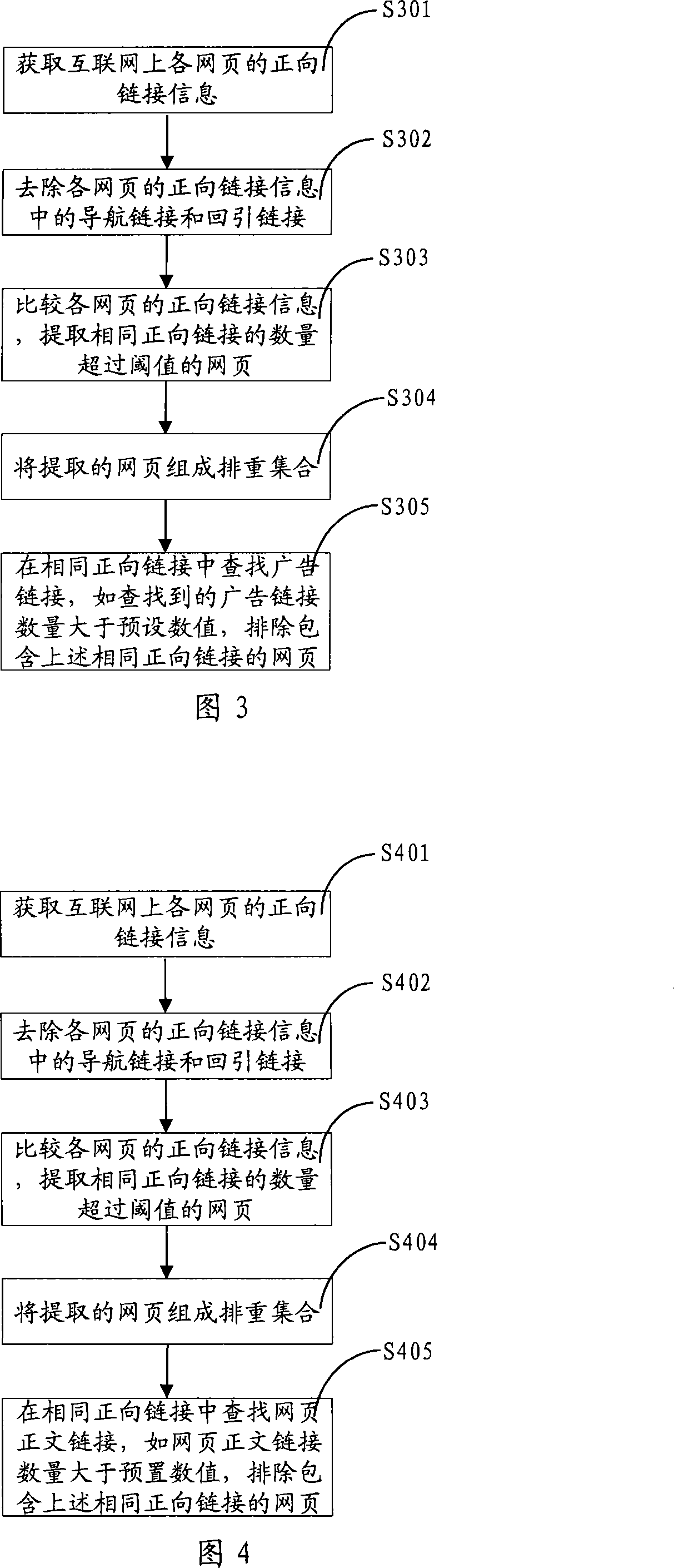
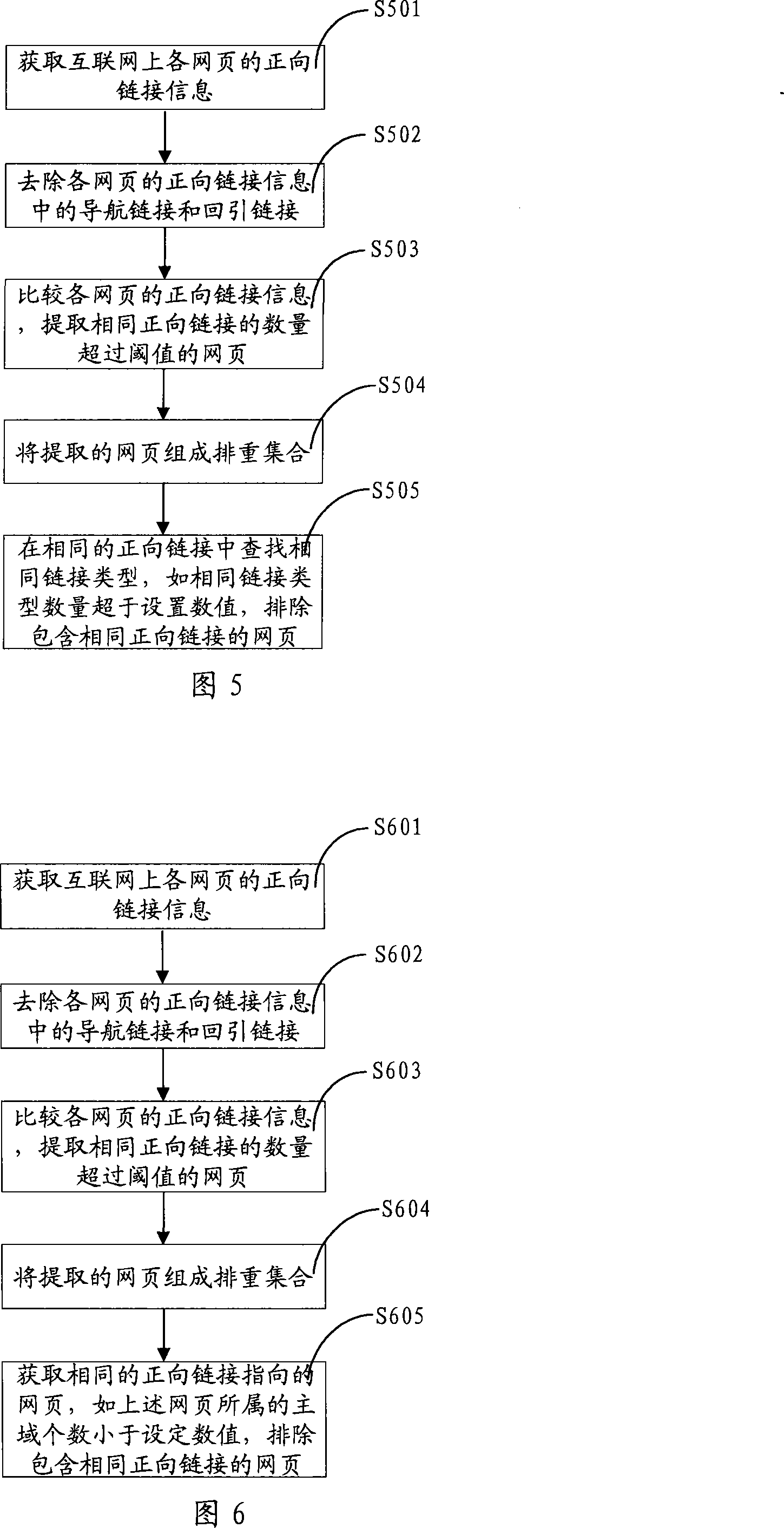
Method and system for arranging web page again
ActiveCN101226533AEasy to identifyEasy extractionSpecial data processing applicationsThe InternetWeb page
The invention relates to a method to detect duplicate web pages, which comprises: obtaining forward links information of each web page on the internet and removing guidance links and back-leading links in the forward links information of each web page, comparing the forward links information of each web page and extracting the web pages whose number of same forward links is over a threshold value, forming a duplicate web pages set by the extracted web pages and eliminating duplicate web pages based on the duplicate web pages set. The method of the invention can compute scores of web pages which contain the same forward links according to properties of the same forward links and excludes web pages whose scores differences are within a certain value. The method of the invention also computes quality values of web pages and keeps the web pages whose quality values are larger than a set threshold value and then computes web pages signatures and excludes the web pages whose similarity degrees of signatures are over a threshold value. Simultaneously, the invention also discloses a duplicate web pages detection system and solves problems of low efficiency of the prior art, and has higher efficiency, precision and accuracy.
Owner:SHENZHEN SHI JI GUANG SU INFORMATION TECH
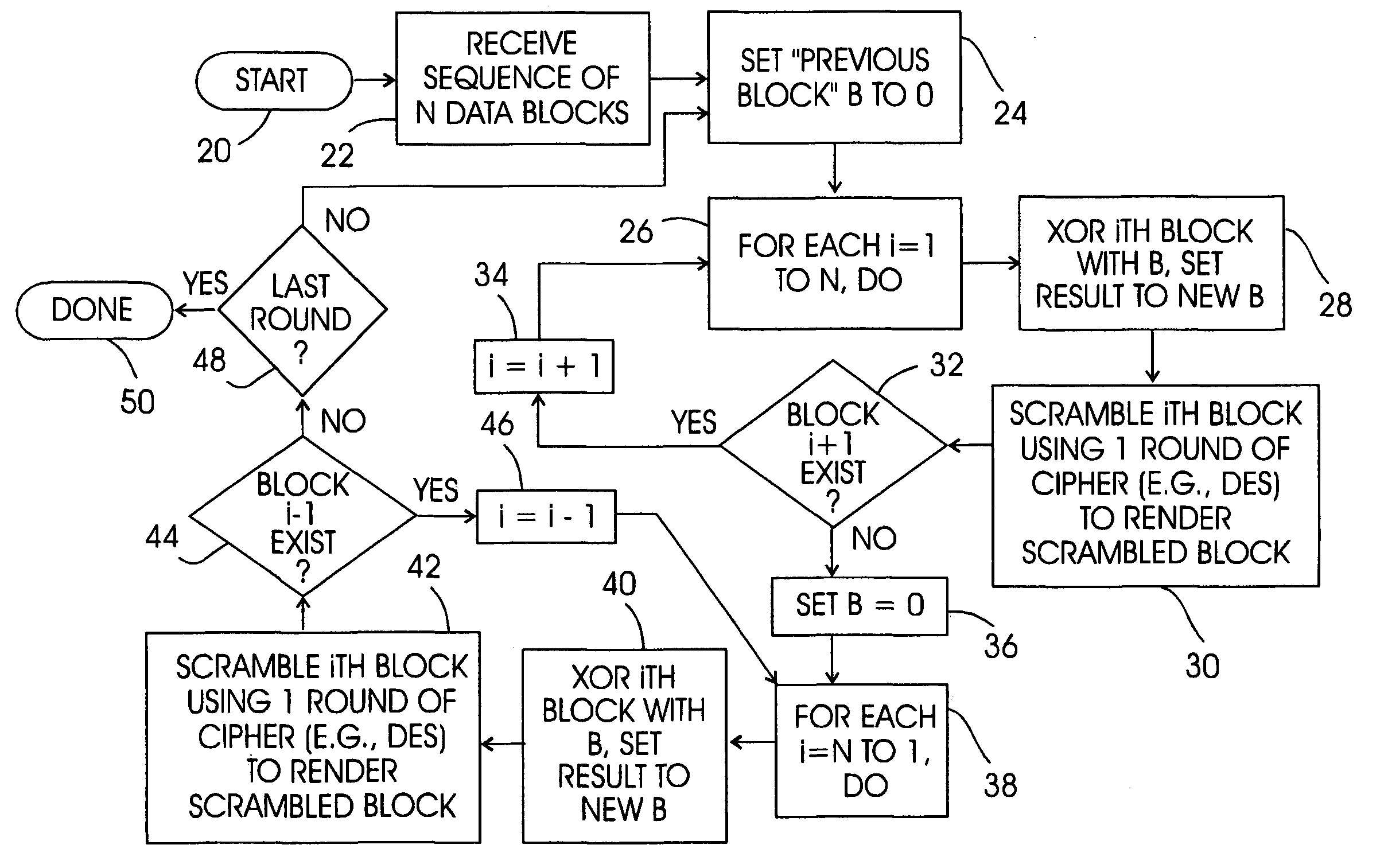
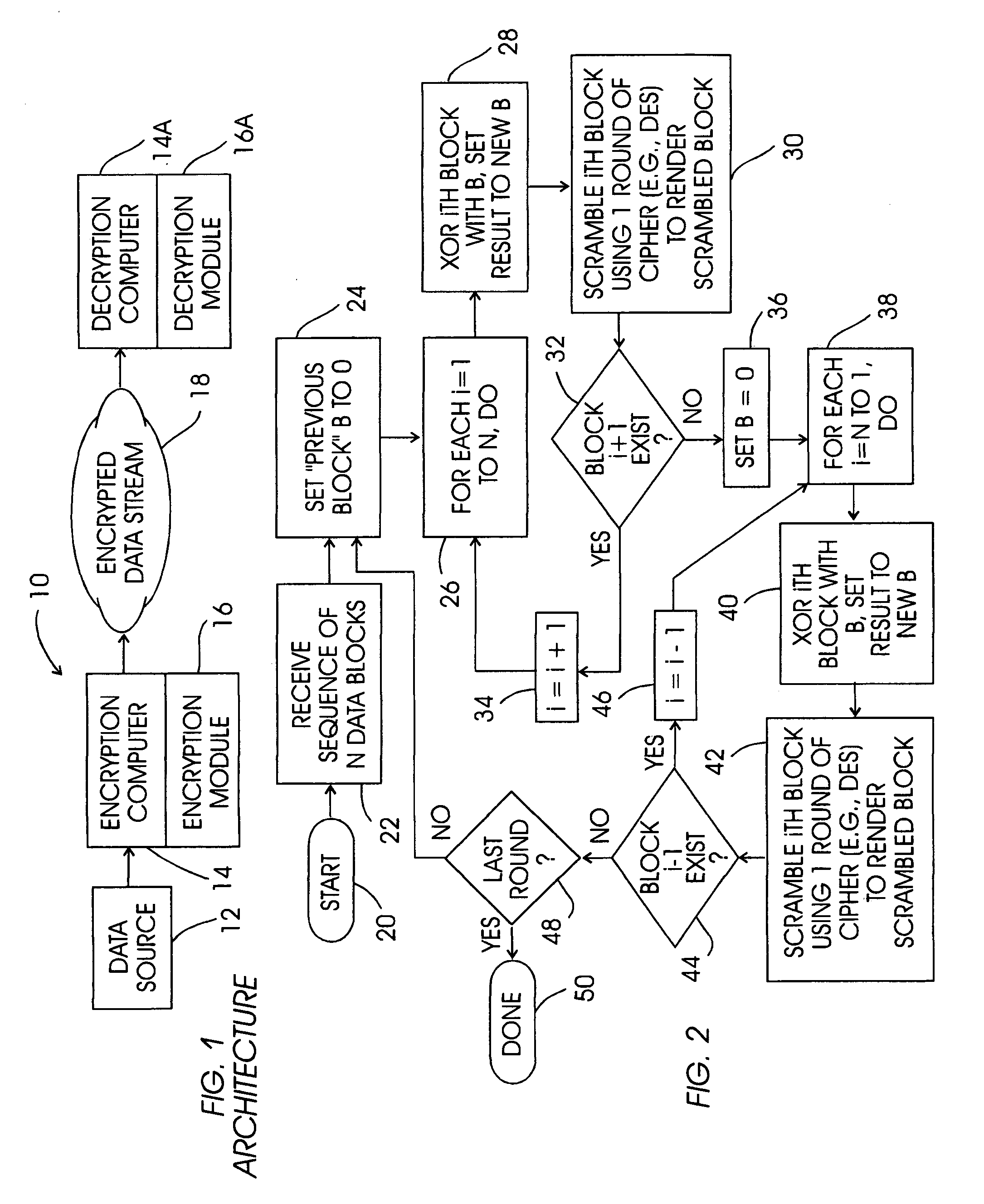
Fault intolerant cipher chaining
InactiveUS6952477B1Encryption apparatus with shift registers/memoriesDigital data processing detailsAlgorithmParallel computing
A method and system for producing, e.g., tamper-resistant software such that the software is fault intolerant, thereby complicating hacking attacks, includes undertaking several iterations of forward plain text chaining and backward plain text chaining through the blocks. Essentially, during forward chaining a block is scrambles using a single round of an appropriate algorithm such as DES, and then it is XORed with the plain text of the next block. The result of the XOR is then scrambled, and then XORed with the plain text of the next block, and so on. At the end of the stream, the process is repeated in reverse, from last block to first. The cycles are repeated for the desired number of rounds, e.g., 16.
Owner:IBM CORP
Rules based data processing system and method
Systems, methods and mediums are described for processing rules and associated bags of facts generated by an application in communication with a processing engine, database and rule engine that process the bags of facts in view of the rules and generate one or more rule-dependent responses to the application which performs one or more work flows based on the responses. The rule engine may apply forward-chaining, backward-chaining or a combination of forward-chaining and backward-chaining to process the rules and facts. Numerous novel applications that work in conjunction with the processing engine, database and rule engine are also described.
Owner:VIDITECK
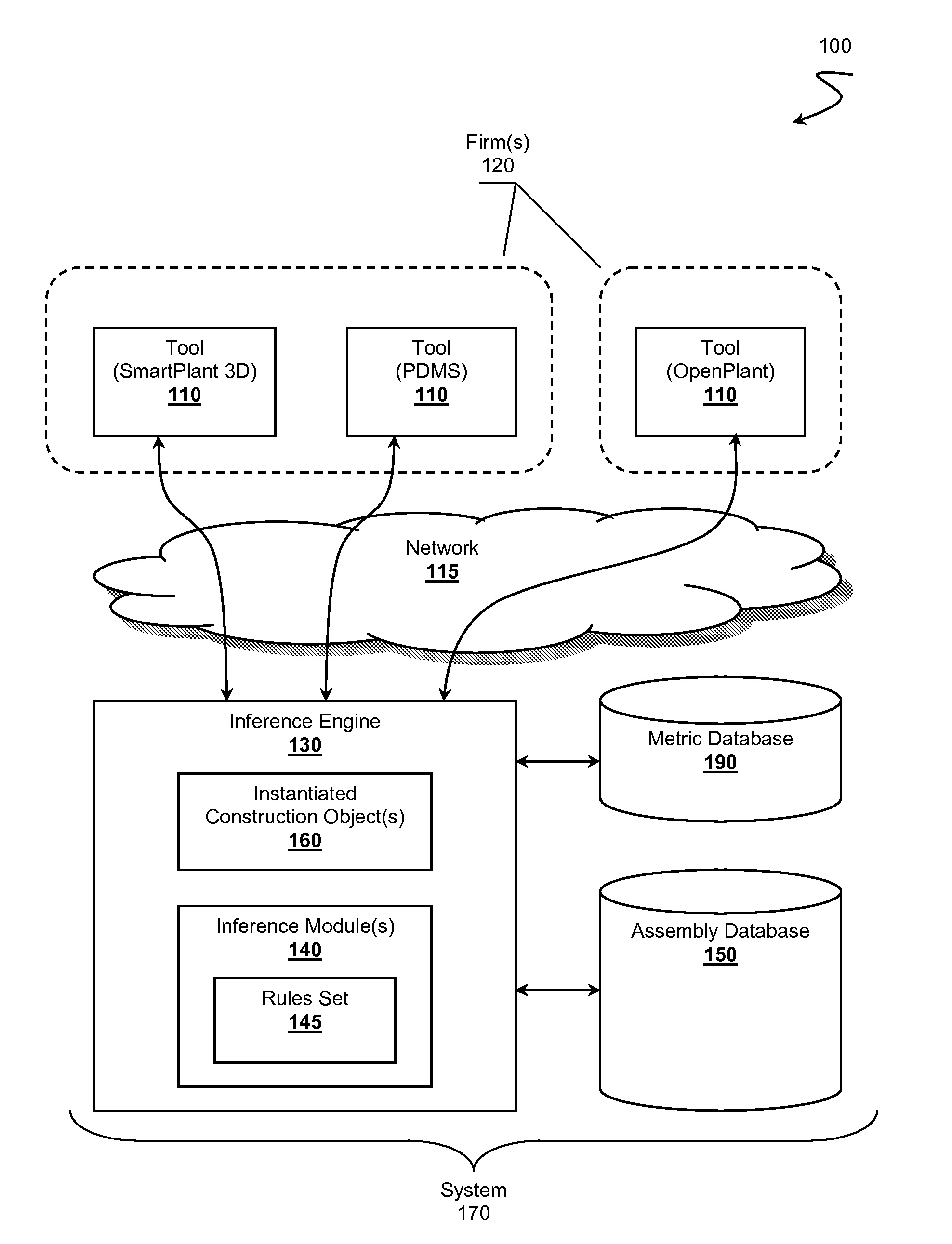
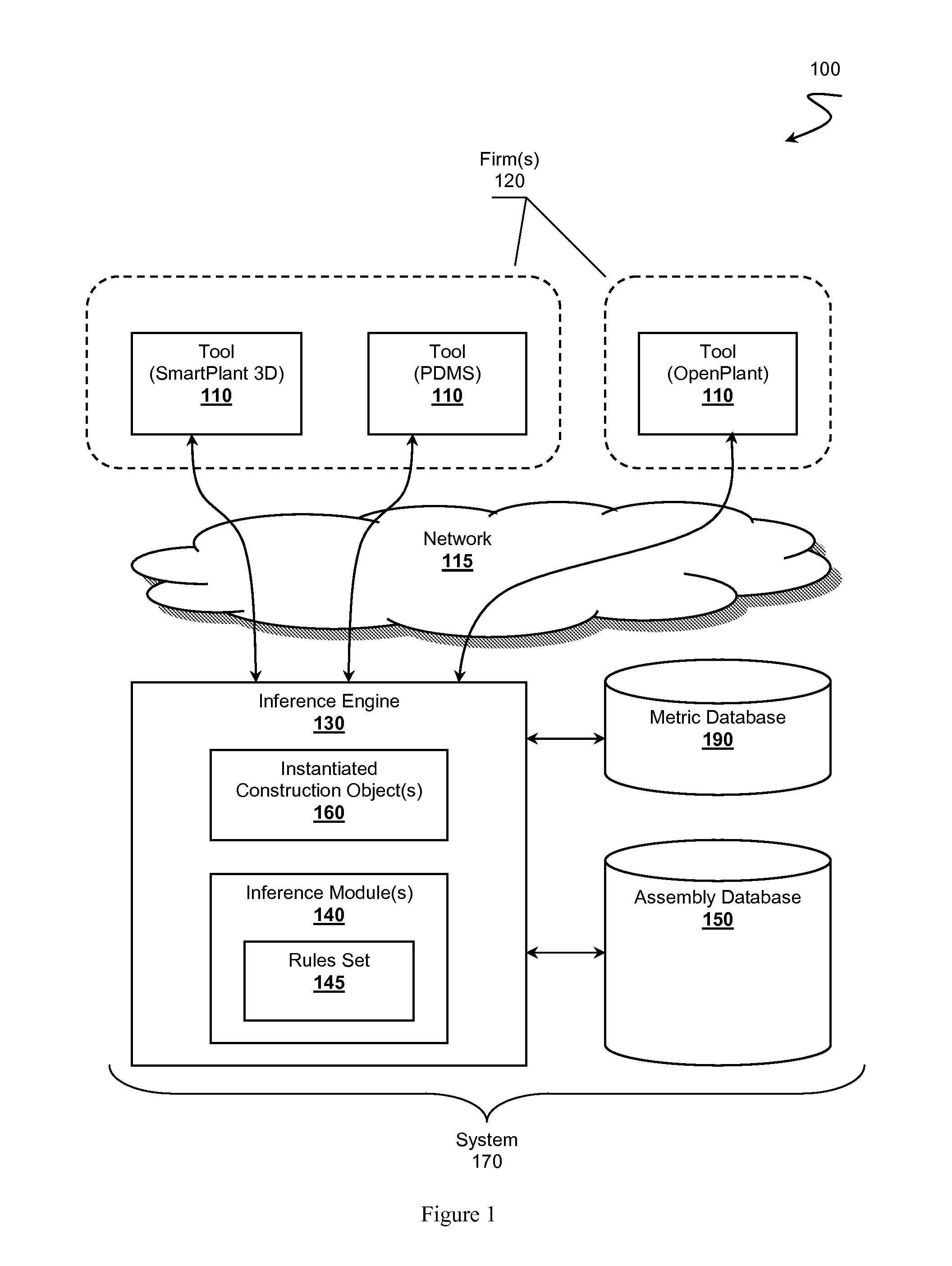
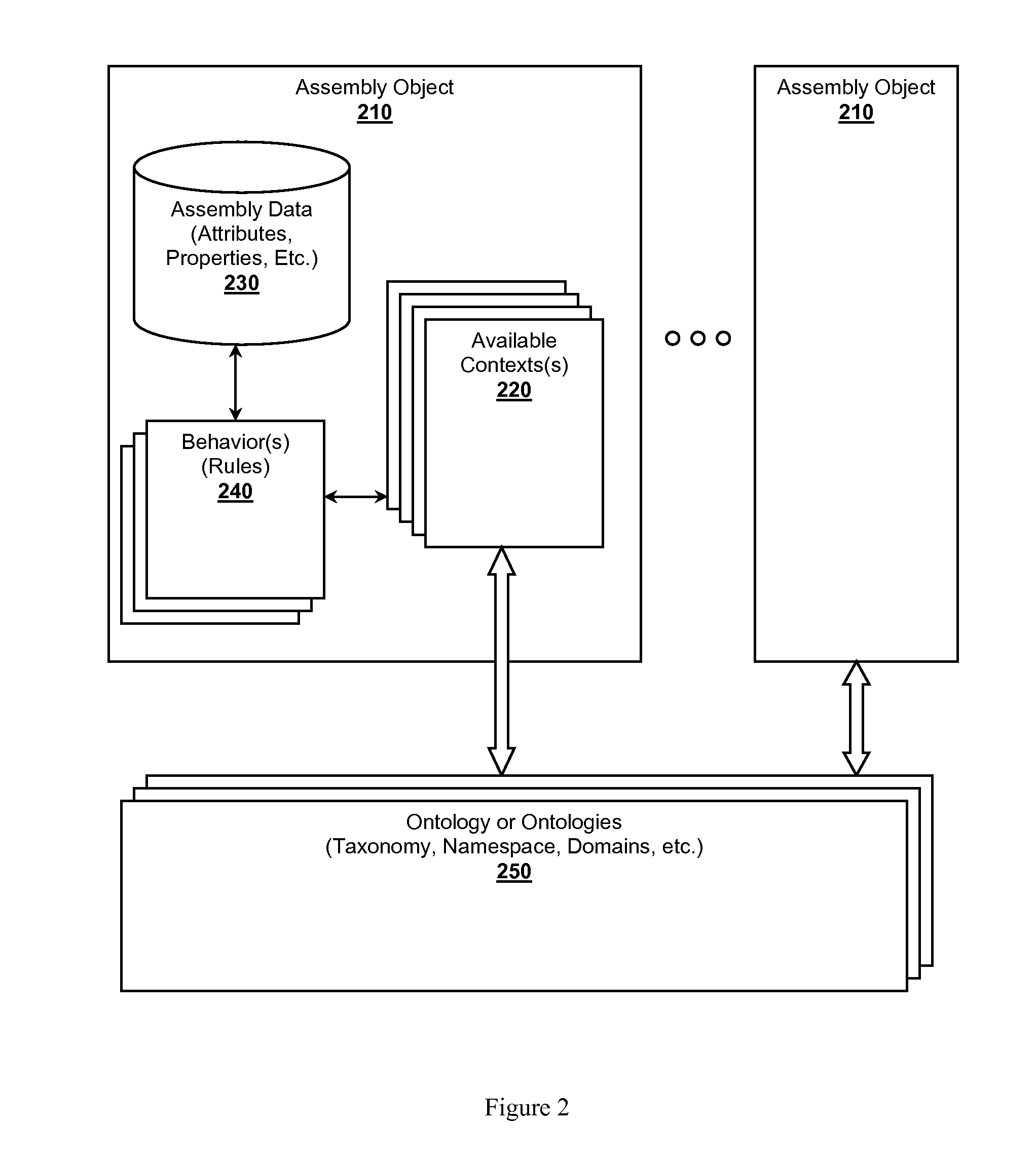
Intelligent Plant Development Library Environment
InactiveUS20120072386A1OptimizationGeometric CADKnowledge representationAbductive reasoningCable tray
An intelligent plant development library environment is presented. Contemplated environments comprise an EPC knowledge system capable of incorporating know-how of one or more construction firms in the form of assembly objects. Assembly objects represent construction components (e.g., bolts, cable trays, pipes, processing units, deliverables, etc.) that can be incorporated into a plant design. Assembly objects are stored in an assembly database and include available contexts considered relevant to the assembly objects. An inference engine is utilized to derive a specified context related to a plant design from one or more design tools. The inference engine applies rule sets to infer which assembly objects to instantiate as construction objects. The inference engine can further configure the design tools to incorporate the instantiated construction objects into a plant construction project model. Example rule sets include forward chaining rules, backward chaining rules, case-based reasoning rules, inductive reasoning rules, or abductive reasoning rules.
Owner:FLUOR TECH CORP
Electric distribution network reactive-voltage three-level coordination control method
ActiveCN103746388AGuaranteed forward-lookingReduce economic pressureReactive power adjustment/elimination/compensationReactive power compensationThree levelDistribution transformer
The invention discloses an electric distribution network reactive-voltage three-level coordination control method, which comprises the following steps: (1) creating data input by self structure duplication, (2) performing forward chaining, (3) performing back substitution, (4) performing astringency judgment, (5) returning a result to a caller. The method has the advantages that 1) layered control over equipment according to the installation position and the control range of the equipment; 2) the variation trend of the operating state of a power grid is judge in advance according to short-run and super short-run load predicting technologies, the perspectiveness of adjustment tactics is ensured, the adjustment times of the equipment are reduced, and invalid actions are avoided; 3) the current situation that adjustment equipment of the electric distribution network is deficient is solved by classified coordination control, the adjustment potence of the adjustment equipment is fully exerted, and the economic pressure for investing and constructing the distribution network is reduced; 4) the method can adapt to multiple conventional and unconventional adjustment equipment, such as a subdivided capacitor, a distribution transformer tap, a line voltage regulator, a line capacitor, SVG, SVC and TSF.
Owner:南京软核科技有限公司
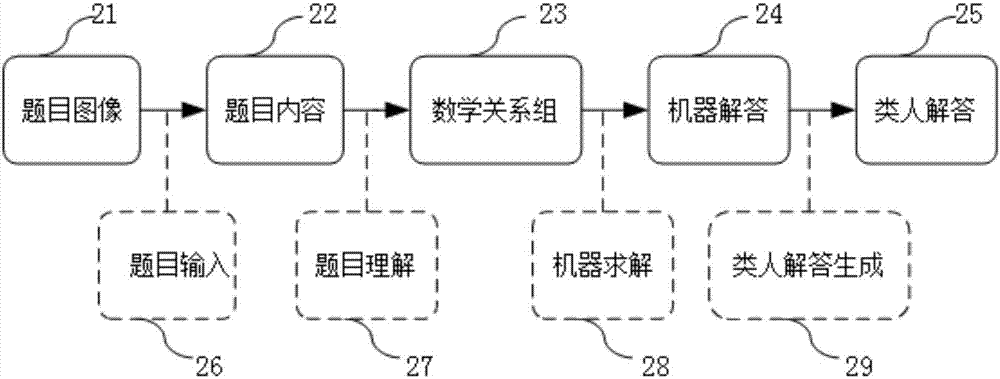
Automatic plane geometry proof question answering method and system
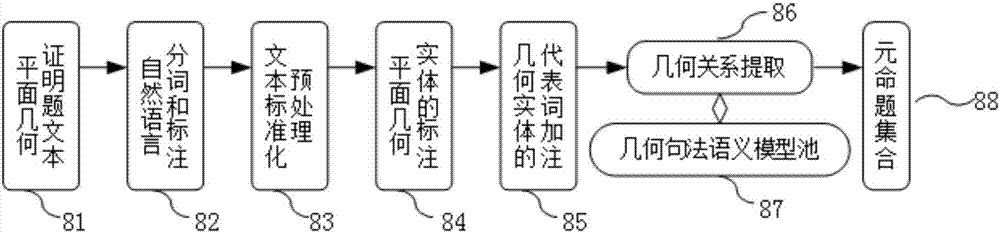
InactiveCN107423287AHigh degree of automationData processing applicationsSemantic analysisPart of speechAlgorithm
The invention discloses an automatic plane geometry proof question answering method and system. The method comprises the following steps of: question input; question understanding: carrying out word segmentation and part-of-speech labelling on a recognized plane geometry proof question text, segmenting a question into n simple clauses and standardizing the clauses; labelling all the geometric entity words in the clauses; expressing each geometric element word as a binary group and expressing each geometric relationship word as a binary group; extracting geometric relationship by adoptions of a syntax-semantic model and forming a binary geometric proposition set by all the geometric relationships; machine solution: reasoning the binary geometric question set to obtain a geometric evidence chain of the question; and quasi-man answer generation: carrying out continuous search through a forward chain according to the evidence chain and a known condition until a conclusion is deduced, so as to generate quasi-man expression. Compared with existing plane geometry proof systems, the method and system are capable of greatly improving the automation degree of answer systems.
Owner:HUAZHONG NORMAL UNIV
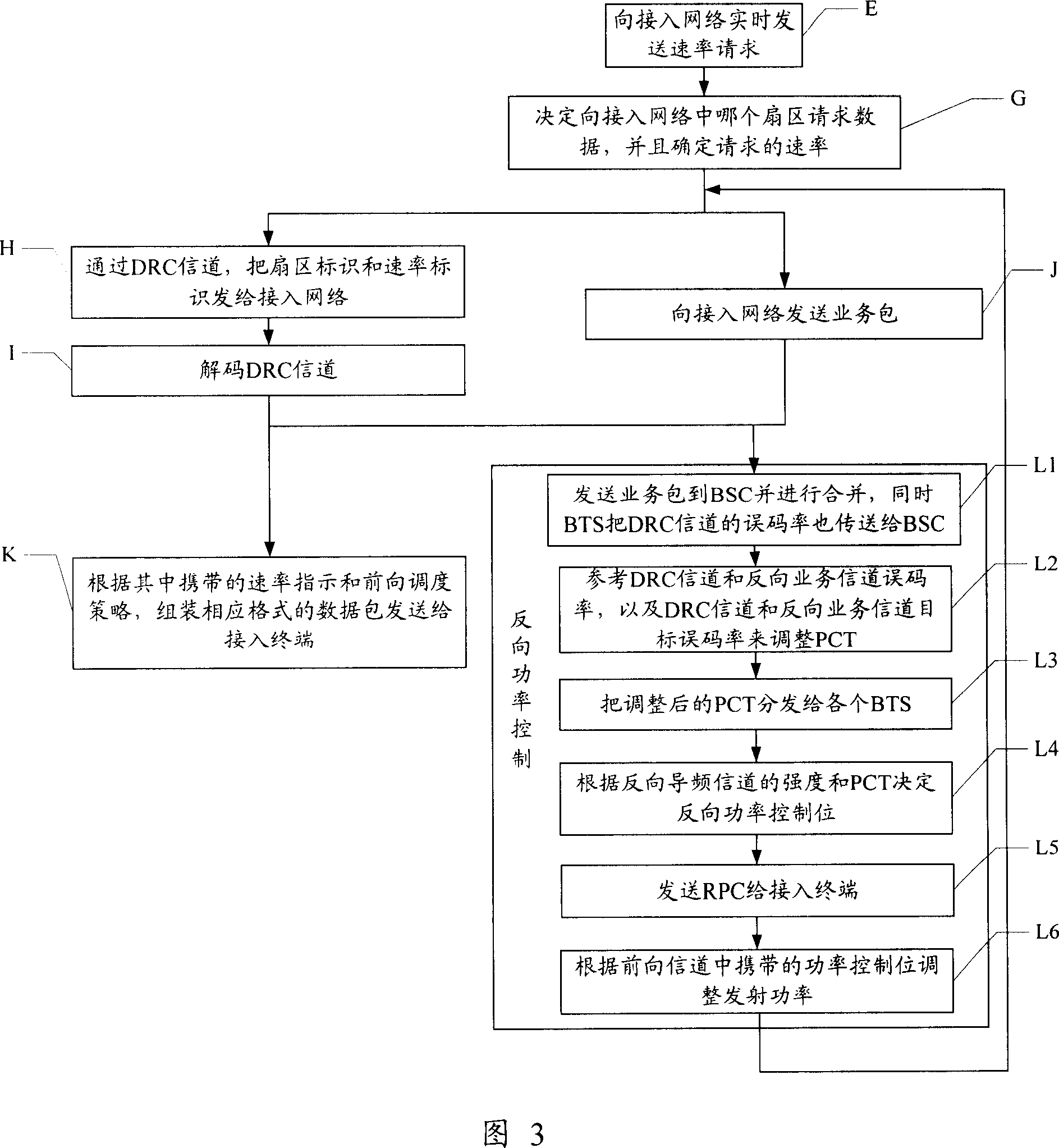
Power control method in communication method and its system
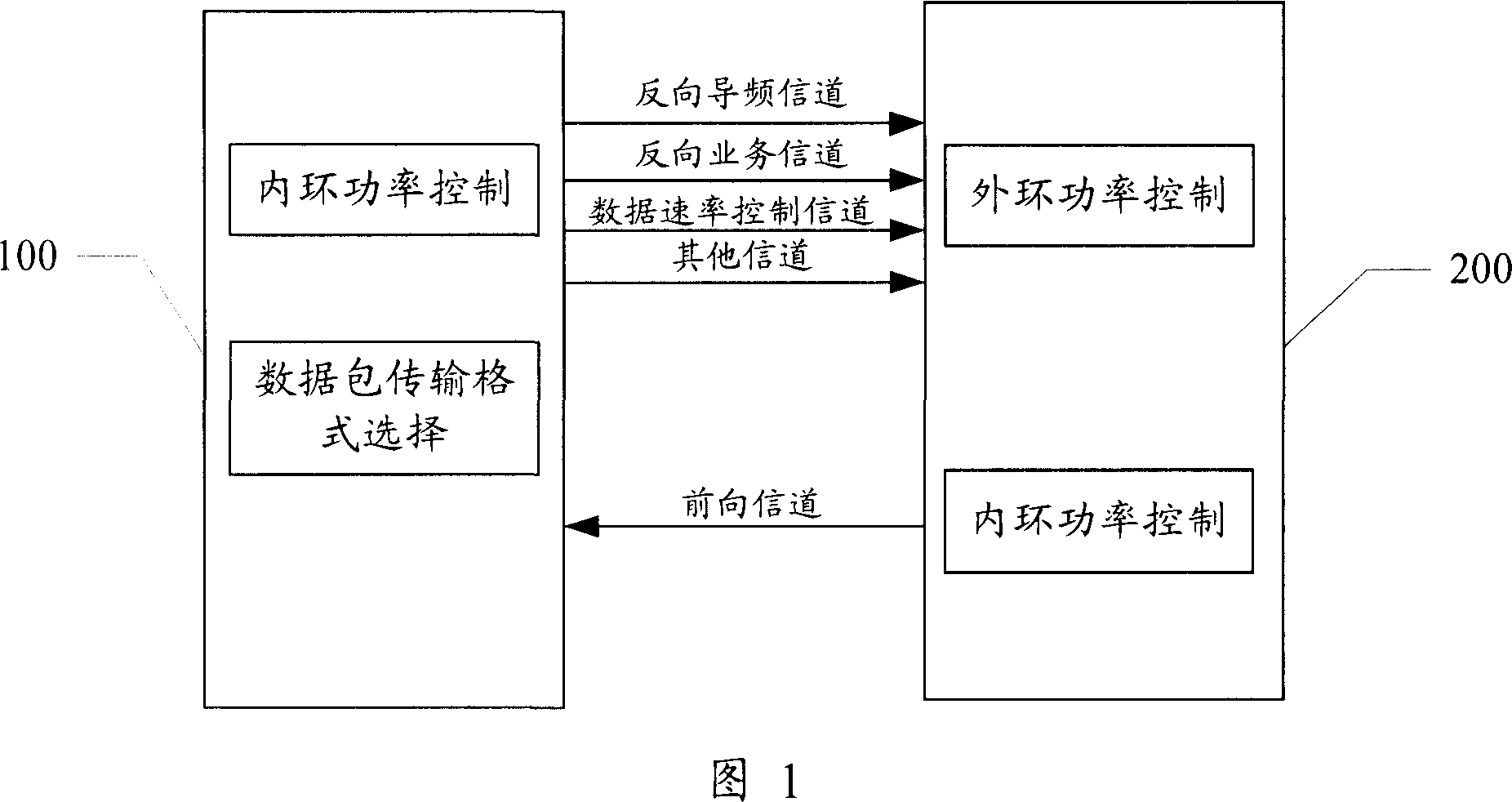
ActiveCN1968037AIncrease transmit powerImprove throughputPower managementTransmission control/equalisingCommunications systemInner loop
The invention relates to a power control method in communication system, wherein it comprises that: obtaining the error code rate of data speed control channel and the error pack rate of reverse service channel; comparing said error code rate, error pack rate, and target error code rate and error pack rate, while any one of target rates is higher, improving the power control threshold value; based on said threshold value, processing inner loop power control. The invention adjusts the access terminal emission power, to confirm the quality of DRC channel; therefore, the service area can install relative data pack via the speed requested by access terminal, to hold high forward chain throughout.
Owner:XFUSION DIGITAL TECH CO LTD
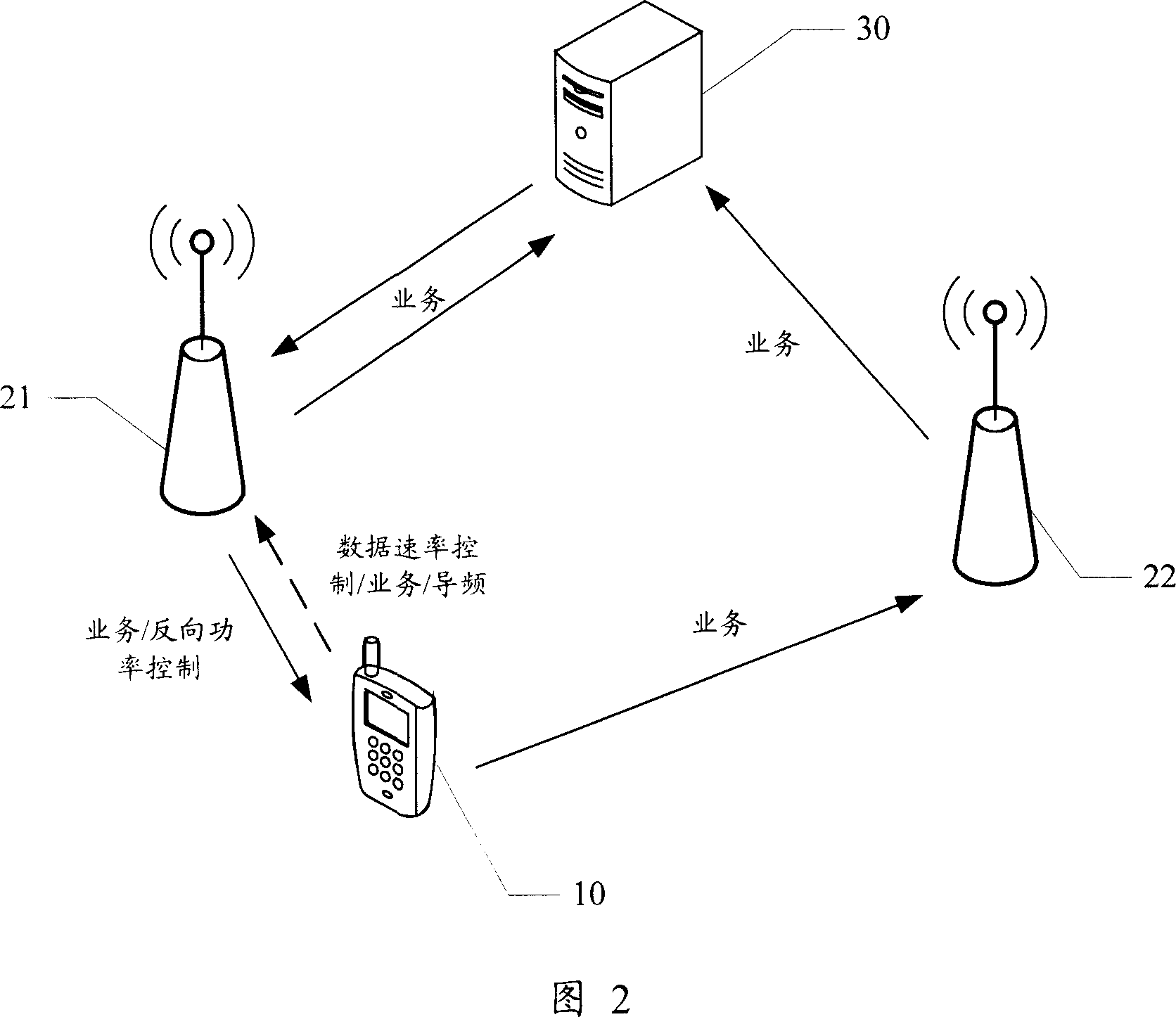
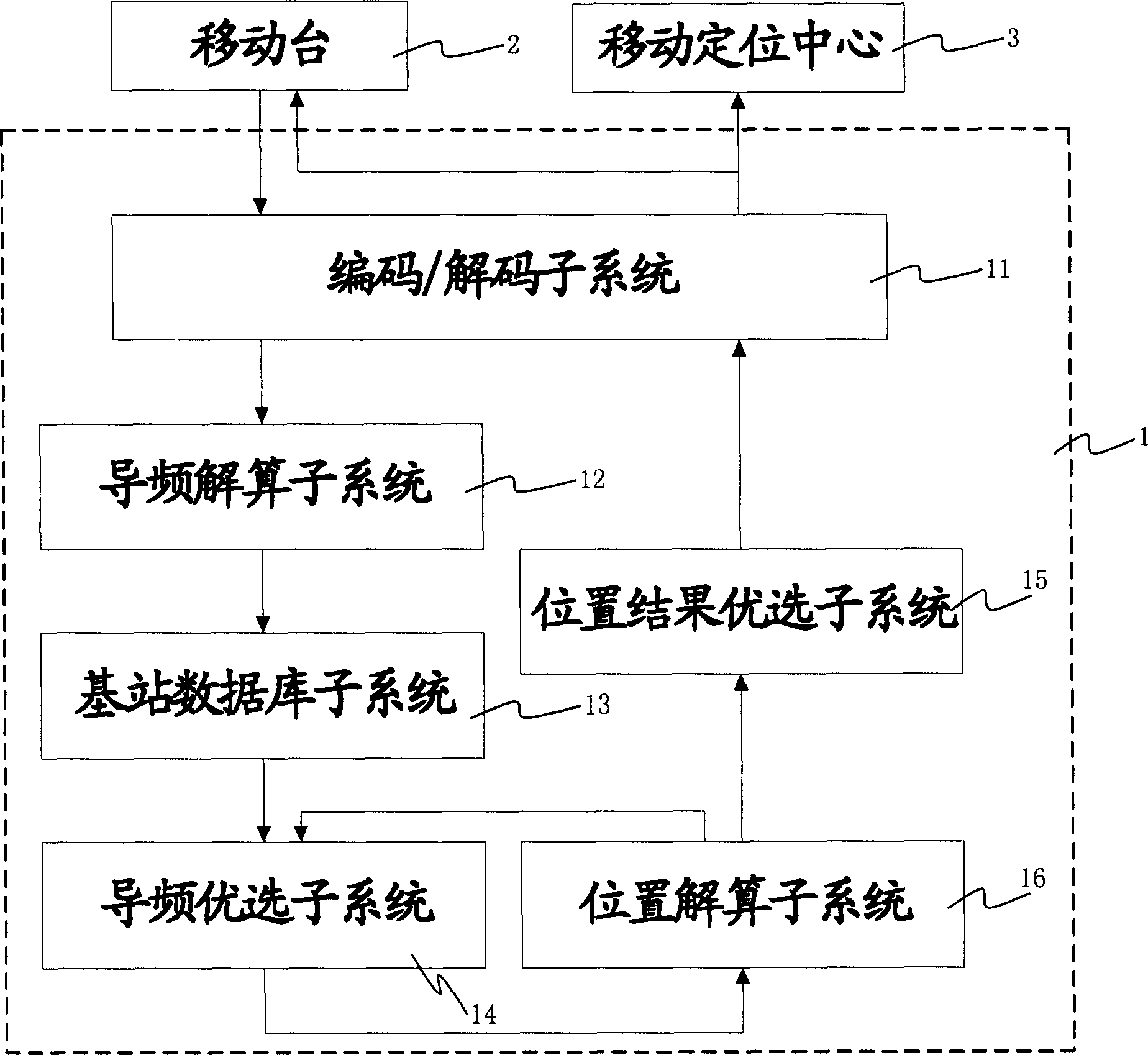
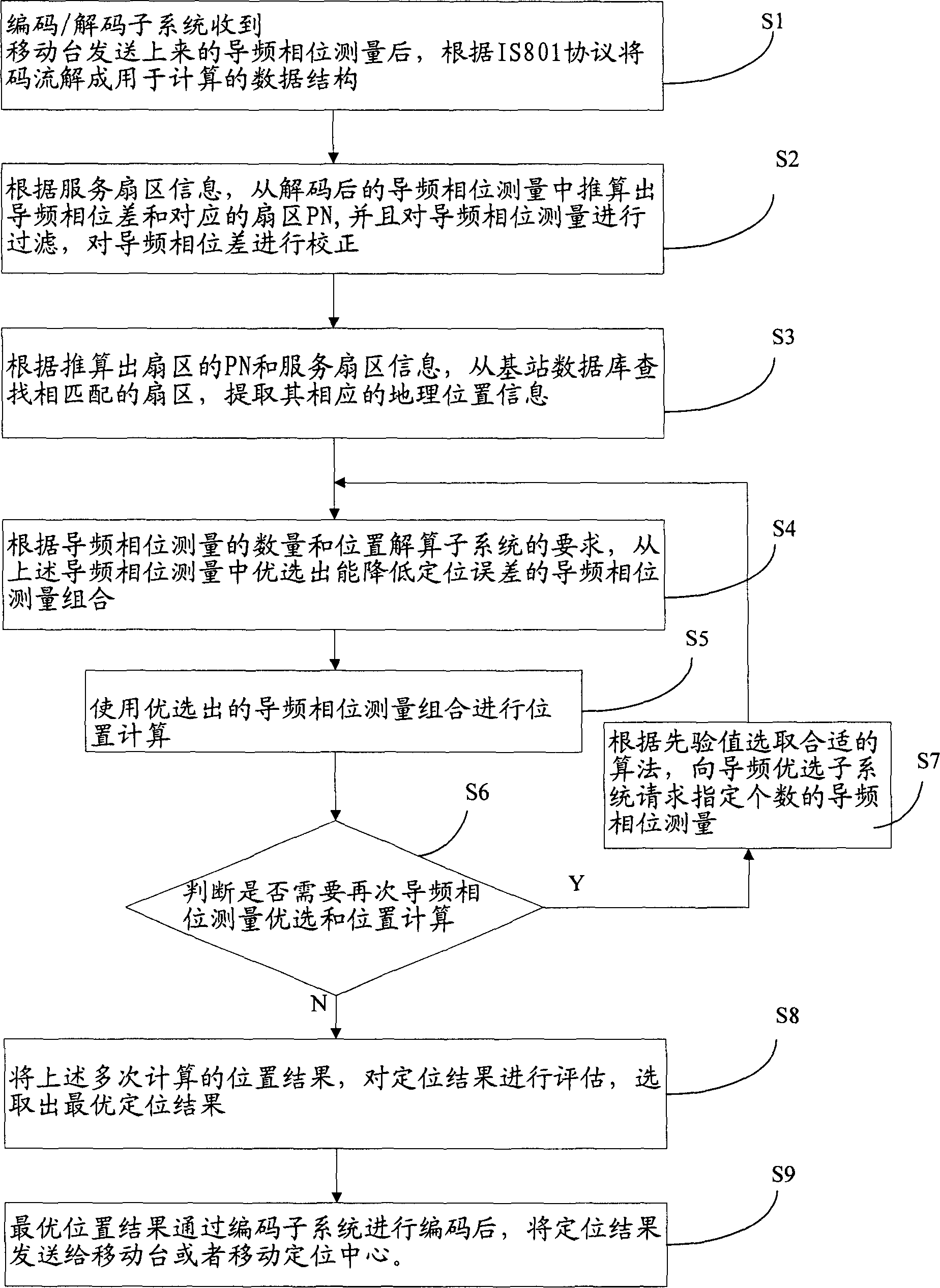
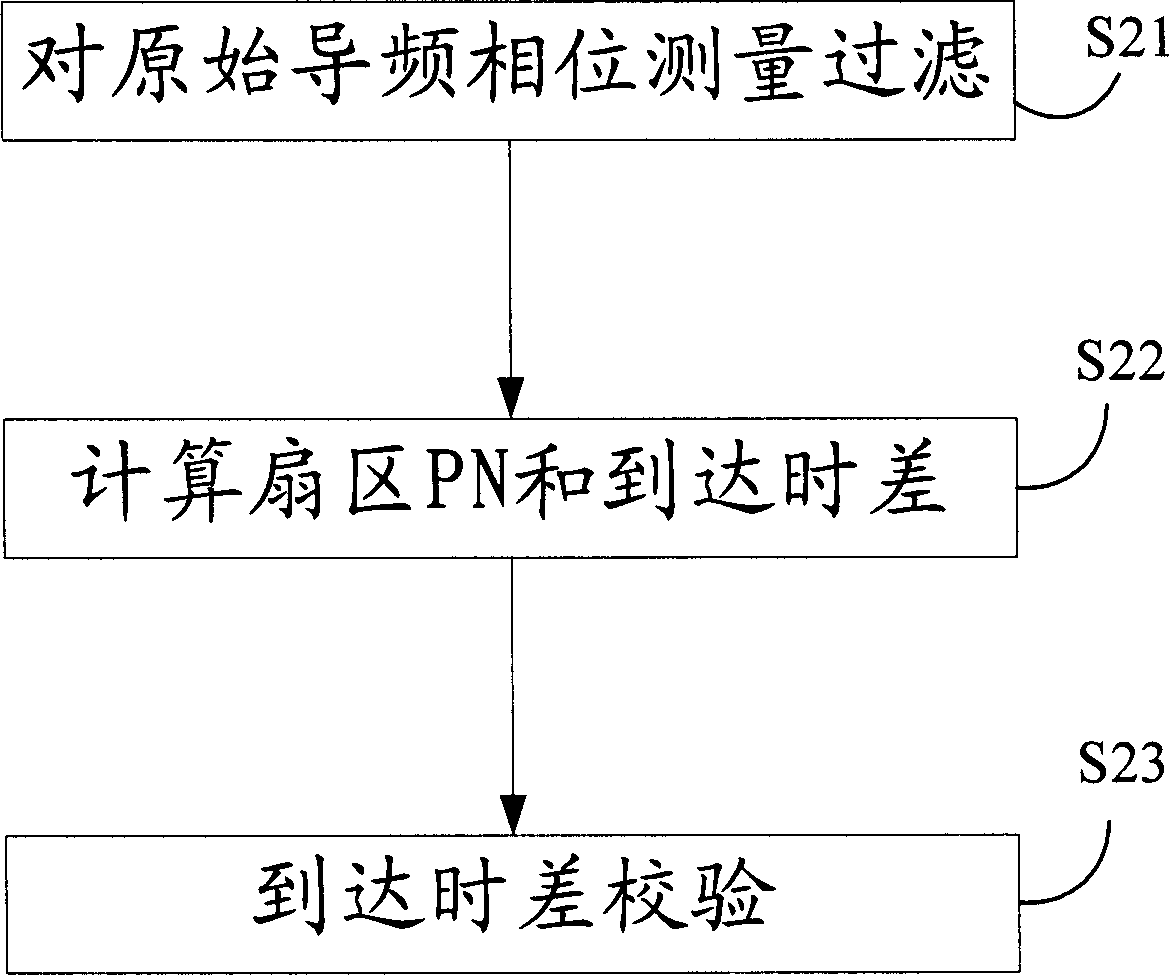
Method and system for calculating position based on triangle positioning of forwarding chain in high rank
InactiveCN1797026AGood effectPosition fixationWireless communicationCode division multiple accessPhase difference
The invention discloses a position calculating method and system based on high grade forward link triangular location, for CDMA mobile communication network, firstly decoding a code flow transmitted by a mobile station, screening pilot frequency phase measurement and calculating a pilot frequency phase difference between each non-reference sector and the reference sector, then preferring the pilot frequency phase measurement and calculating positions, preferring one of the multi-location results, and finally encoding the preferred location result to the mobile station. The system has locating accuracy able to achieve an ideal effect. The test shows that the locating error can be within 100 m, a relatively ideal effect in the present wireless environment and the AFLT-based location technique.
Owner:ZTE CORP
A configurable physically non-clonable function circuit based on delay chain
ActiveCN109460681ASave resourcesLower unit costInternal/peripheral component protectionOn boardFpga chip
The invention provides a configurable physical non-clone function circuit based on delay chain, which comprises a signal control module, an excitation generation module and at least one delay multi-excitation unit. The delay multi-excitation unit comprises a delay chain; The clock source in the circuit is generated by multiplying the clock of FPGA chip on board and controlled by signal control module. The delay chain is composed of inverting blocks which are configured by the carry-forward chain in series. The random difference of the response of different inverting blocks to the signal is extracted to generate the excitation response pair. The circuit uses fewer resources than other delay-type physical non-clonable function circuits under the condition of generating the same bit sequenceby adjusting the configuration signal of the excitation generation module, thus greatly reducing the unit cost.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Network configuration method, ring network system and node
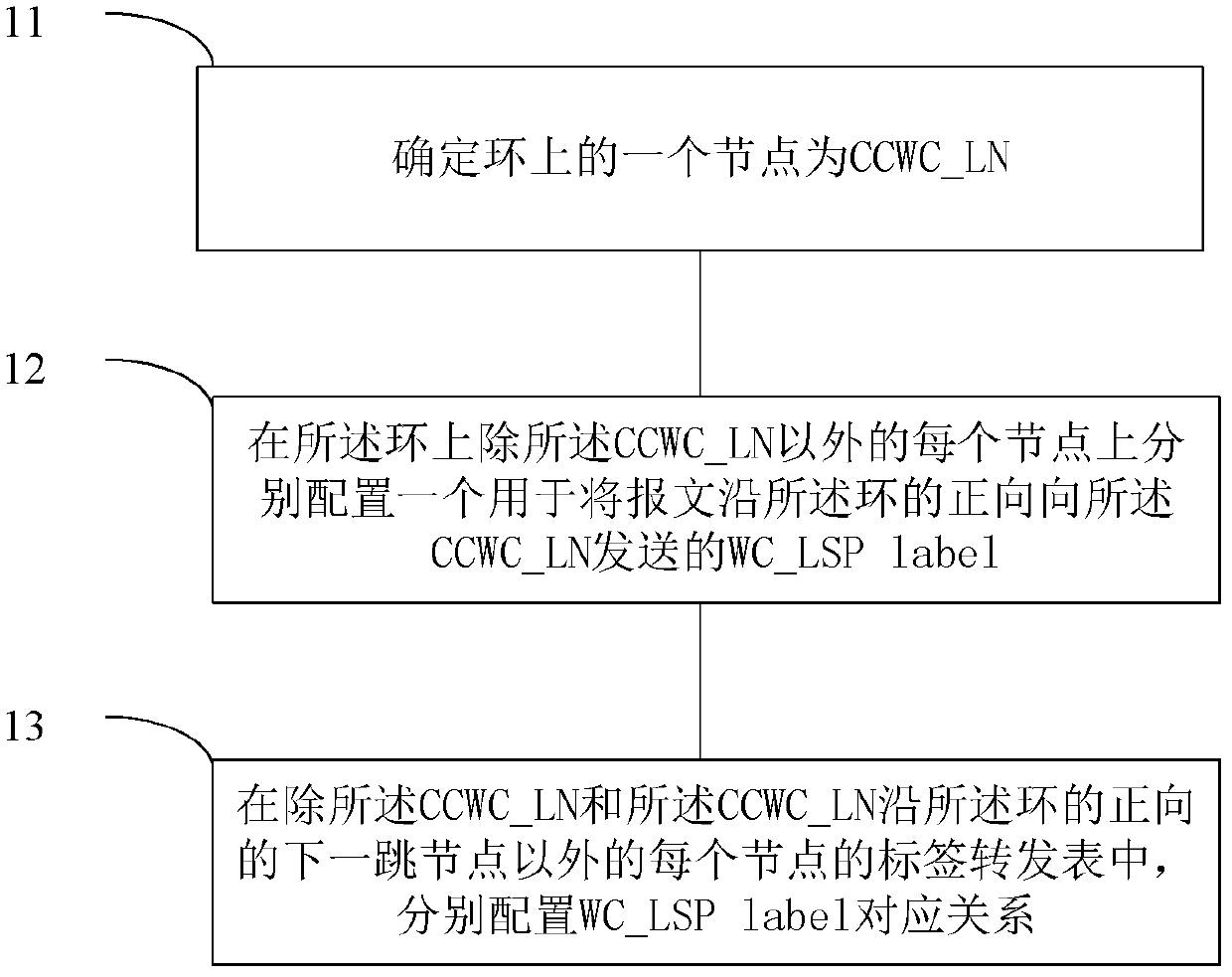
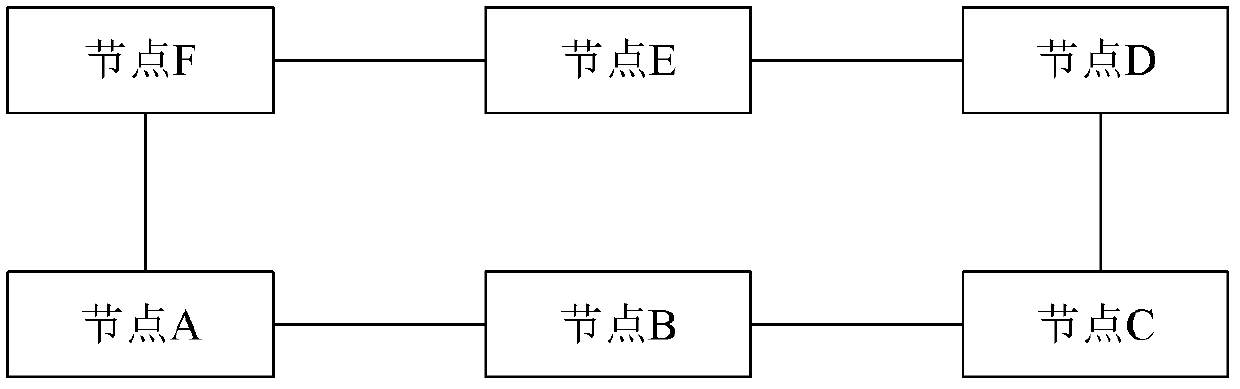
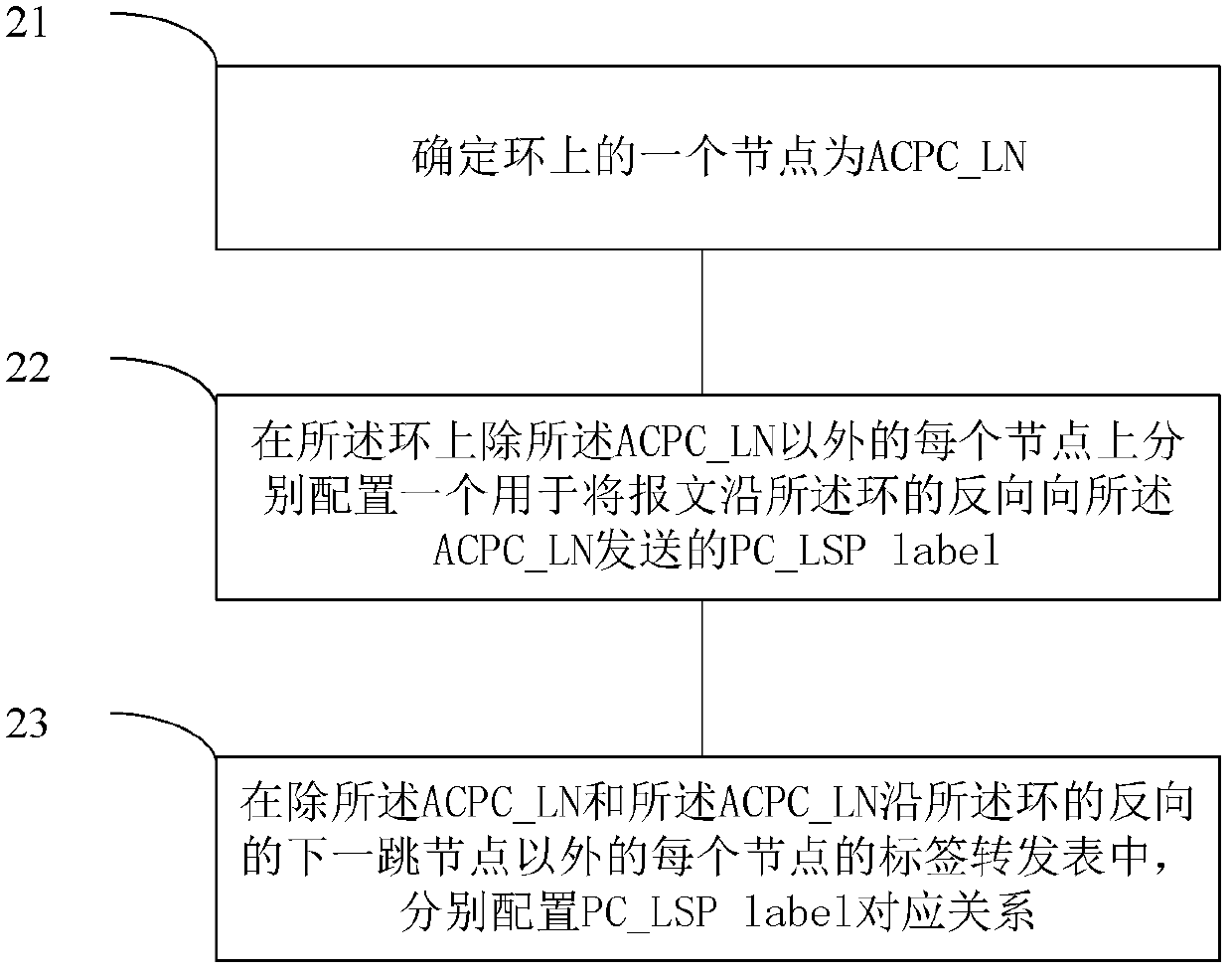
The invention relates to a network configuration method, a ring network system and a node. A network is applied to a ring comprising n nodes, wherein n is not less than 2, n is a natural number, and the network is characterized in that each node on the ring is taken as a lower ring node CCWC-LN of a forward chain-shaped working channel, and the forward chain-shaped working channel is respectivelyestablished for each CCWC-LN. The invention has one advantage that as each node on the ring is taken as the lower ring node (CCWC-LN) of the forward chain-shaped working channel, the forward chain-shaped working channel is respectively established for each CCWC-LN, and services on the ring are packaged with WC-LSP (working channel-label switched path) labels during forwarding and can reach the lower ring nodes through the corresponding forward chain-shaped working channels. Therefore, the nodes on the ring do not perform forwarding according to each service, thereby greatly reducing the processing burden.
Owner:HUAWEI TECH CO LTD
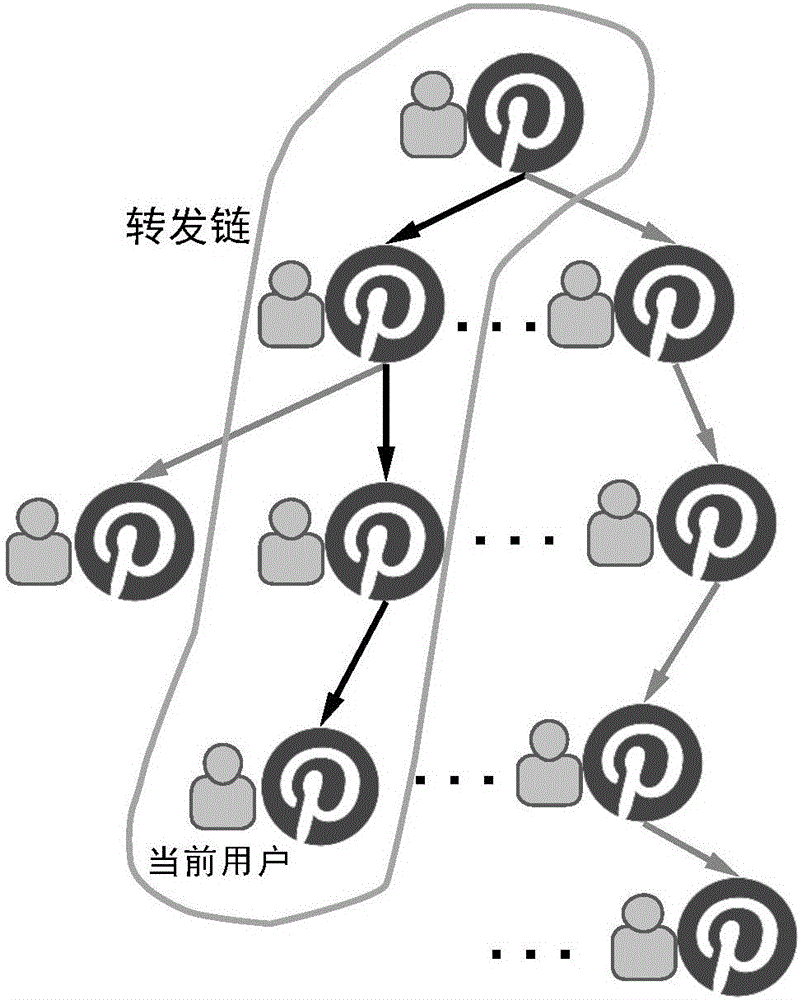
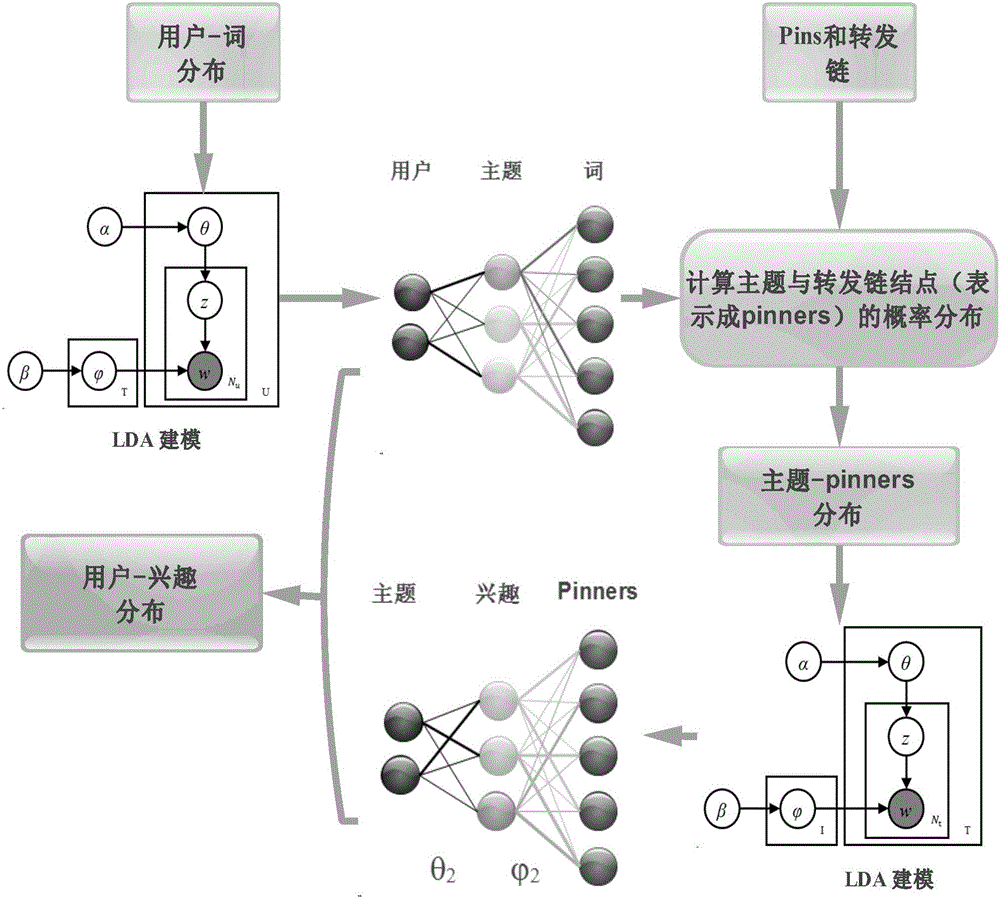
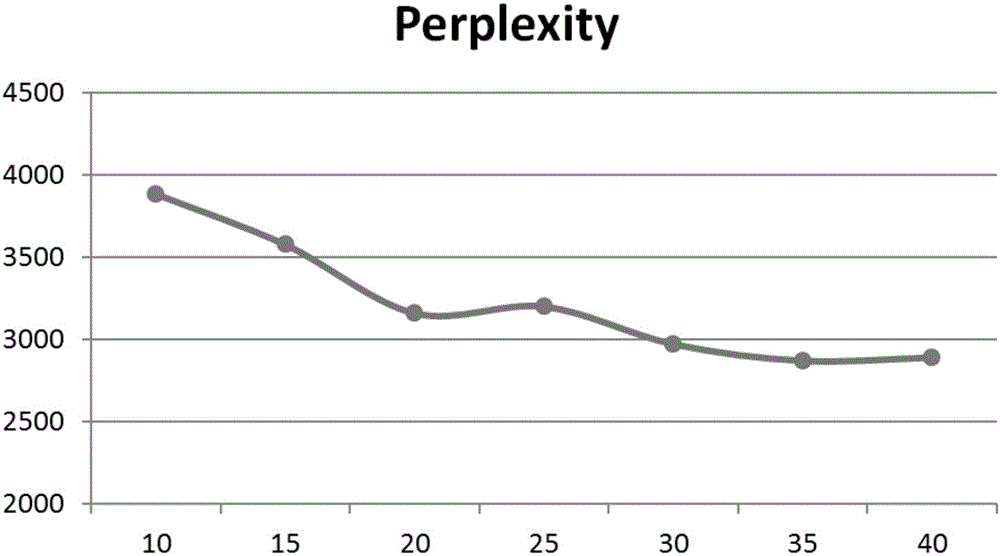
Method for user portrait extraction based on multilayer latent variable model
InactiveCN105869058AData processing applicationsText processingJensen–Shannon divergenceLatent Dirichlet allocation
The invention relates to a method for user portrait extraction based on a multilayer latent variable model and relates to the field of data mining and recommendation systems. A user portrait is extracted according to a social curation network, and the method for user portrait extraction based on the multilayer latent variable model is provided according to data of two modes including text description information of collected entries and user behaviors on a forward chain. A latent Dirichlet allocation (LDA) model is introduced to the text description information to obtain user's latent subject distribution, and subject interest distribution is obtained based on the user's latent subject distribution; and users' interest distribution is obtained in combination with the user's latent subject distribution and the subject interest distribution. A users' social community is found based on the multilayer latent variable model, and user recommendation results are obtained in combination with Jensen-Shannon divergence ascending sort. According to the method, the users' social community is found by utilization of information of the two different modes including the user text description information and the user behaviors on the forward chain, and user recommendation is achieved.
Owner:BEIJING UNIV OF TECH
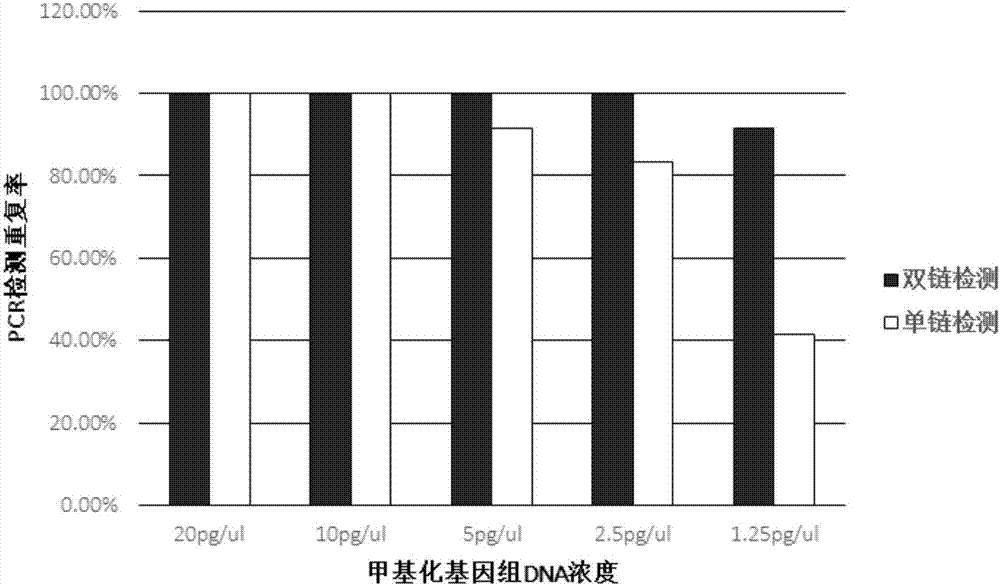
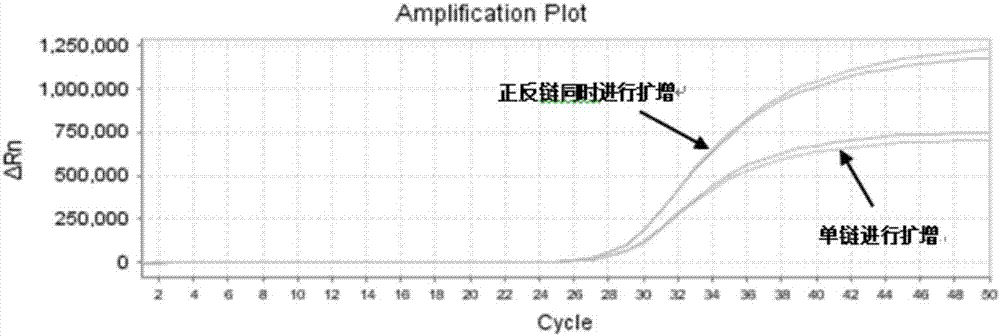
Primer and probe used for detecting gene methylation, and sampling method and kit thereof
InactiveCN107164524AEasy to operateShort experiment timeMicrobiological testing/measurementDNA/RNA fragmentationDNA methylationForward primer
The invention provides a primer and a probe used for detecting gene methylation, and a sampling method and a kit thereof. The primer comprises a specific methylation forward chain primer and a specific methylation reverse chain primer; the specific forward chain primer comprises a forward chain forward primer and a forward chain reverse primer, and the specific methylation reverse chain primer comprises a reverse chain forward primer and a reverse chain reverse primer; the probe comprises a specific methylation forward chain probe and a specific methylation reverse chain probe; and the primer also comprises a forward chain non-methylation blocking primer and a reverse chain non-methylation blocking primer. The primer, the probe, the sampling method and the kit have the advantages of high specificity, high sensitivity, small pollution, simplicity and fastness in operation, safety, good accuracy and good repeatability of a detection result, and effective improvement of the gene methylation detection condition, and are suitable for clinic use.
Owner:SHENZHEN YOU SHENGKANG BIOSCI CO LTD
Bicycle Derailer Chain Driver
A manually controlled chain driver apparatus for a bicycle drive chain derailer providing necessary forward chain movement less power transmission to bicycle pedals for derailer operation during stopping and coasting instances when pedaling motion has ceased or is not possible.
Owner:HAMED HAZEM NIHAD
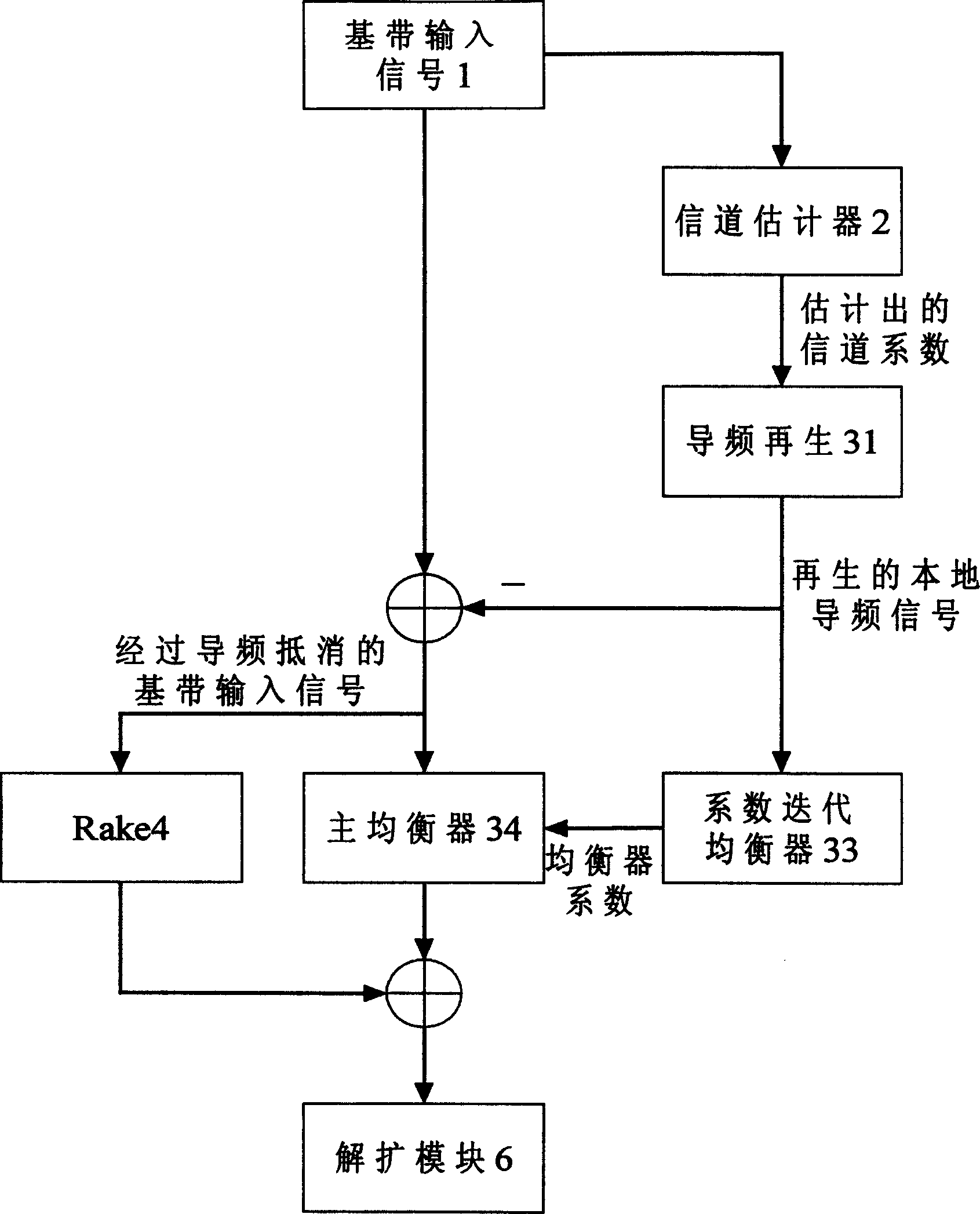
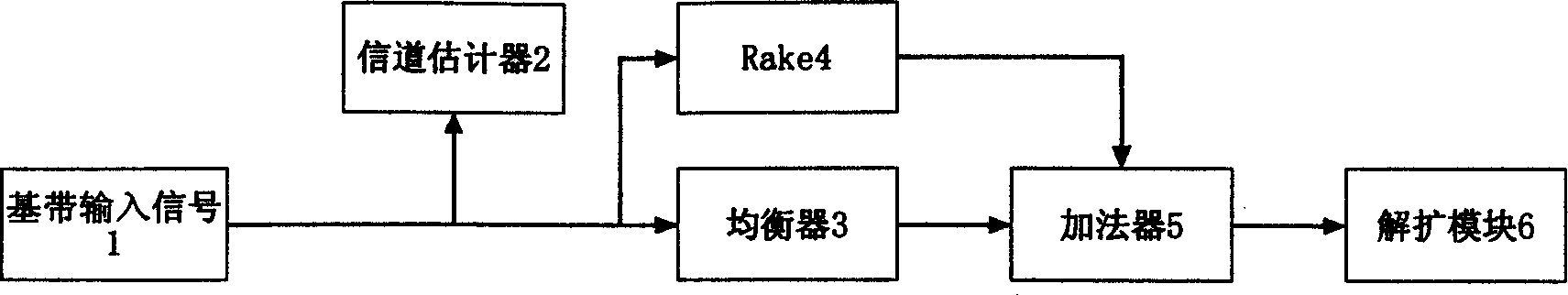
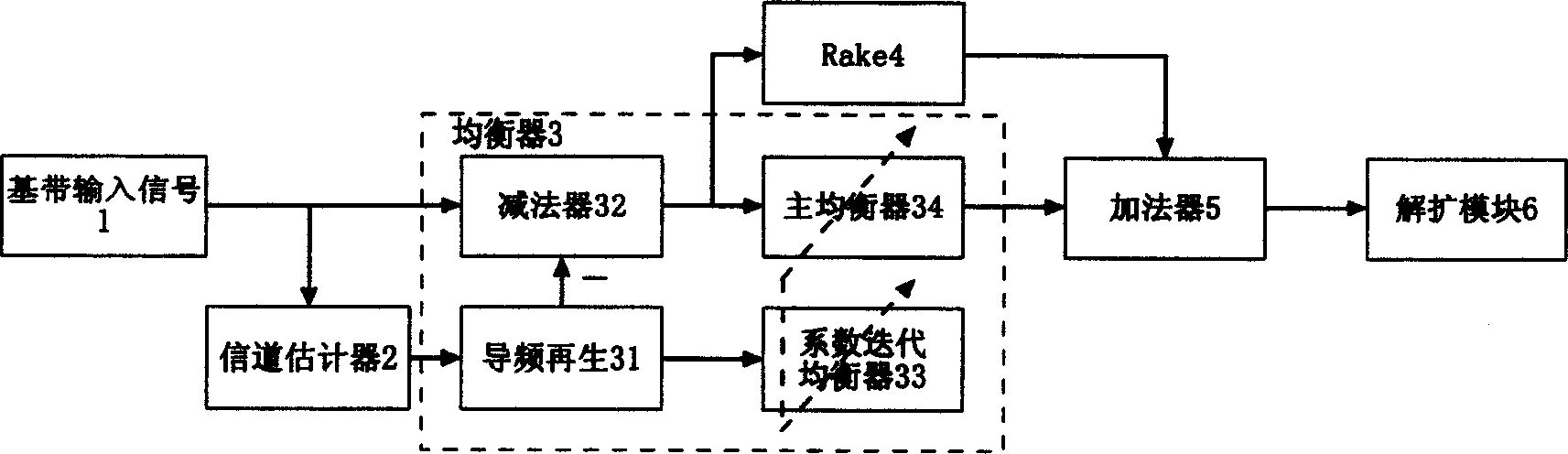
Parallelling receiving method by chip balancer and rake receiver
InactiveCN1585300AImprove performanceImprove robustnessSpatial transmit diversityComputation complexityCommunications system
A parallel reception of a chip balancer and a Rake receiver is used for CDMA frequency extending communication system. It is achieved by: using channel estimator to reforming guide signals for training coefficient iterative balancer, and a primary balancer linked with the former and used for basic band signals. The output of the primary balancer and the output of the Rake are synthesized at a certain ratio to be fed a demodulating and expending module. It is a chip stage of CDMA forward chain receiver with good performance, and with low working robust and calculation complication.
Owner:SOUTHEAST UNIV +1
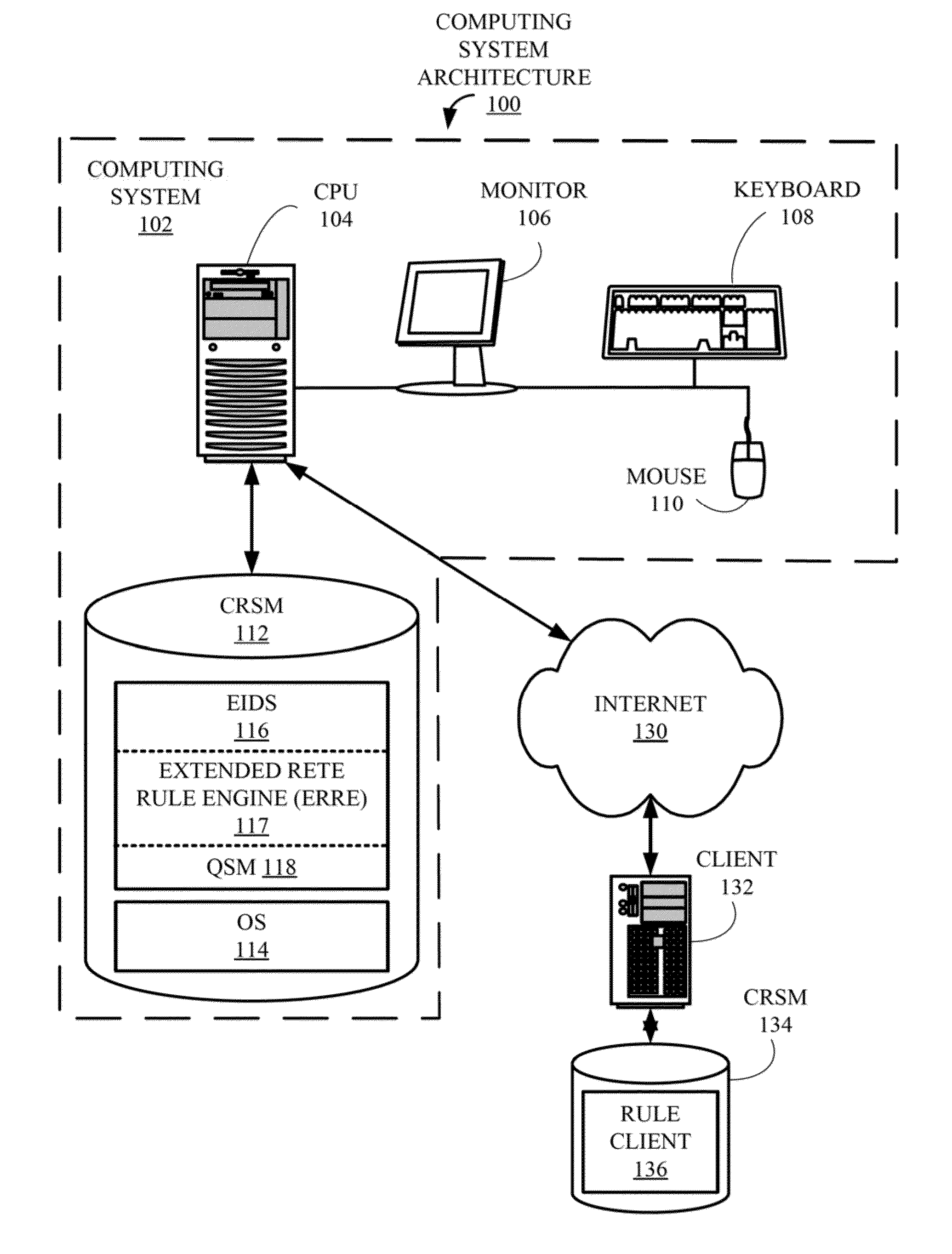
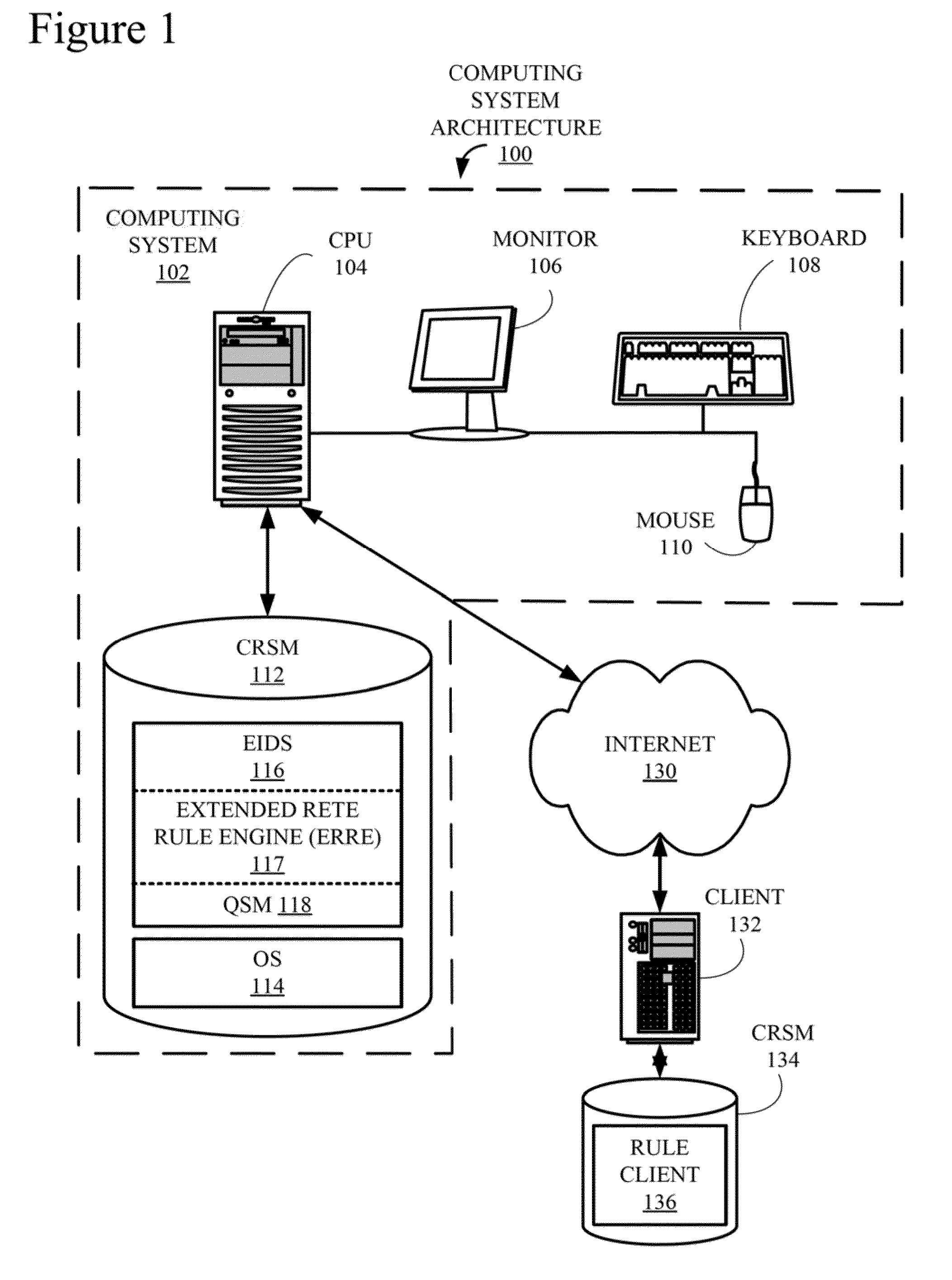
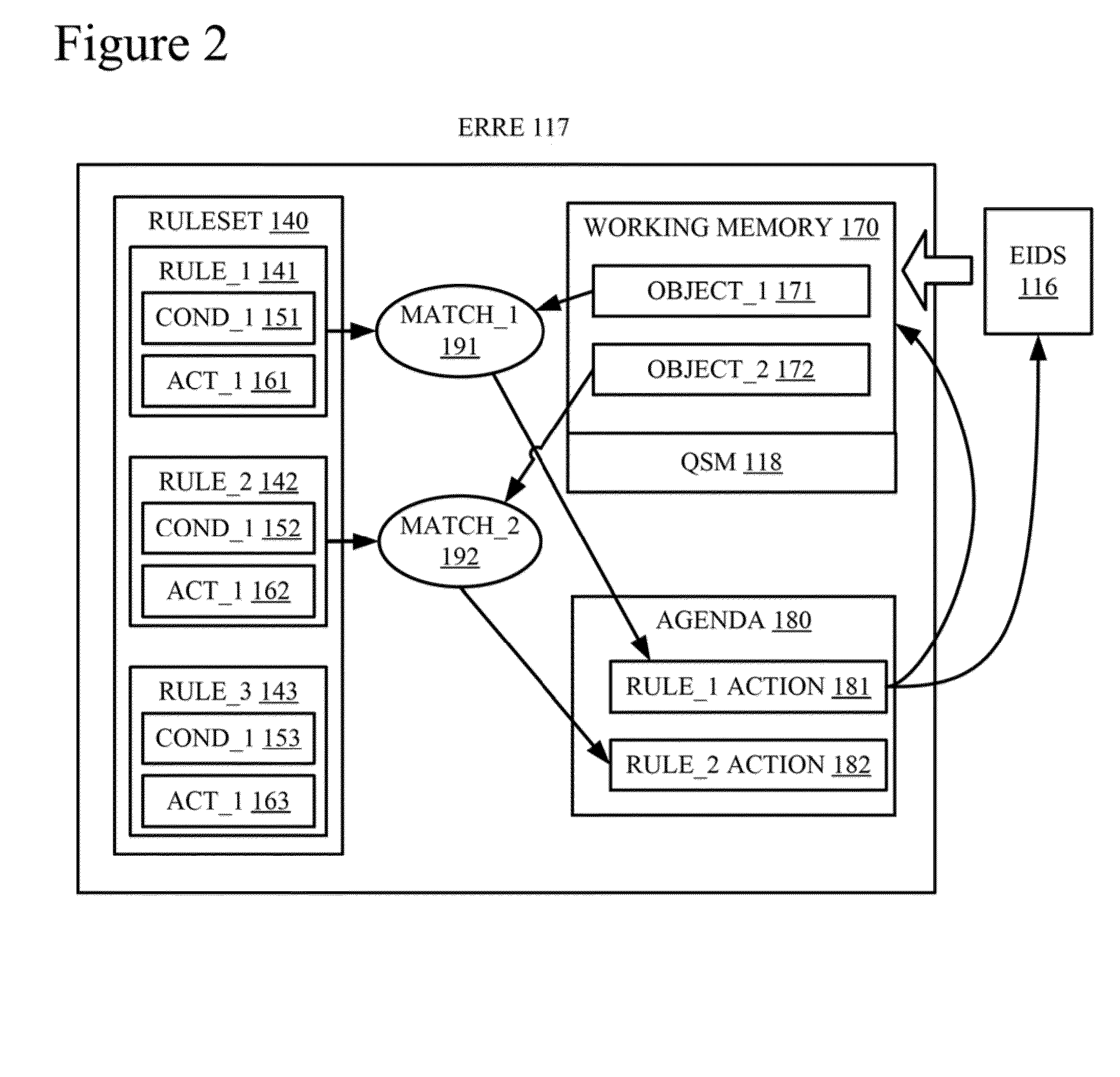
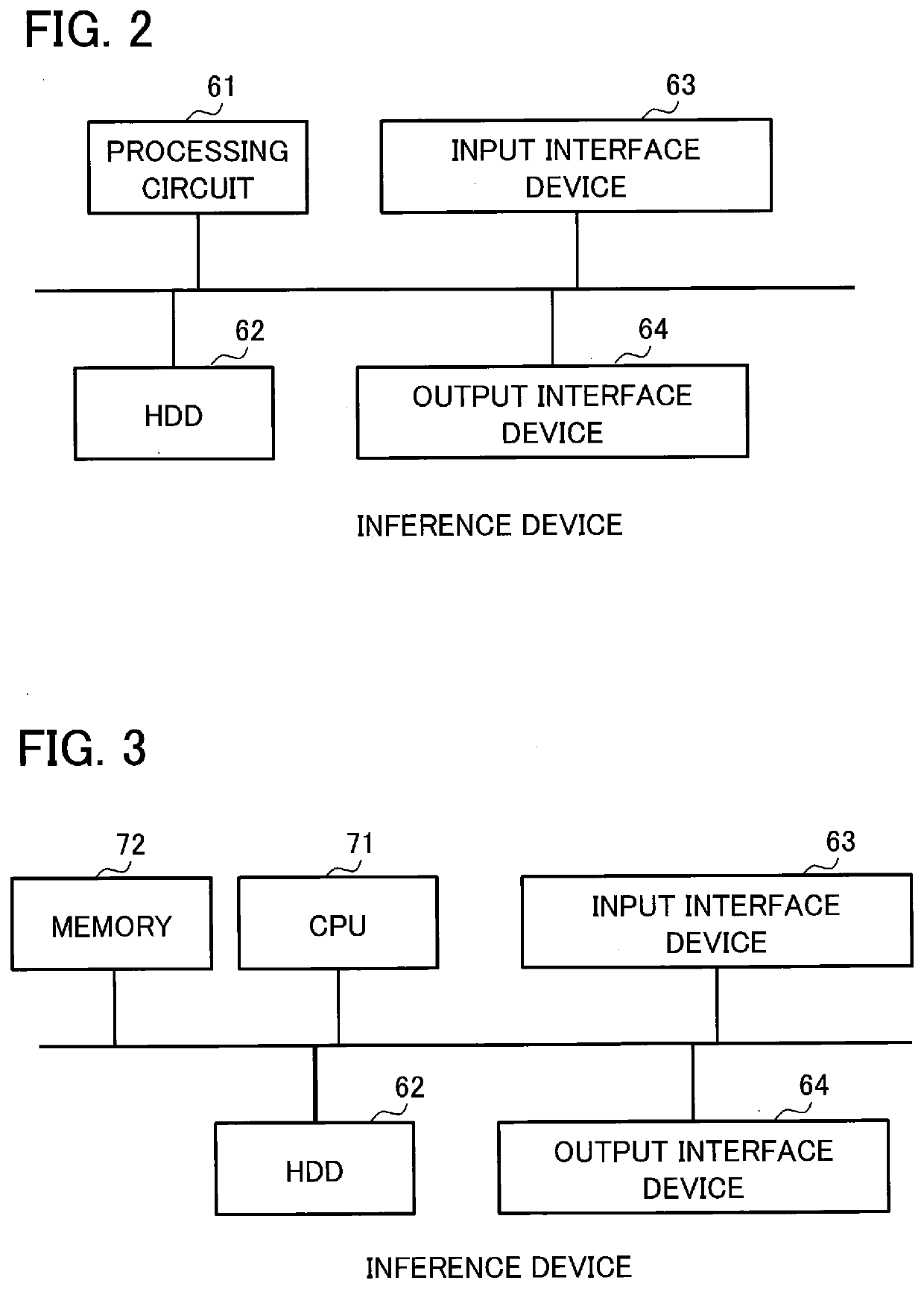
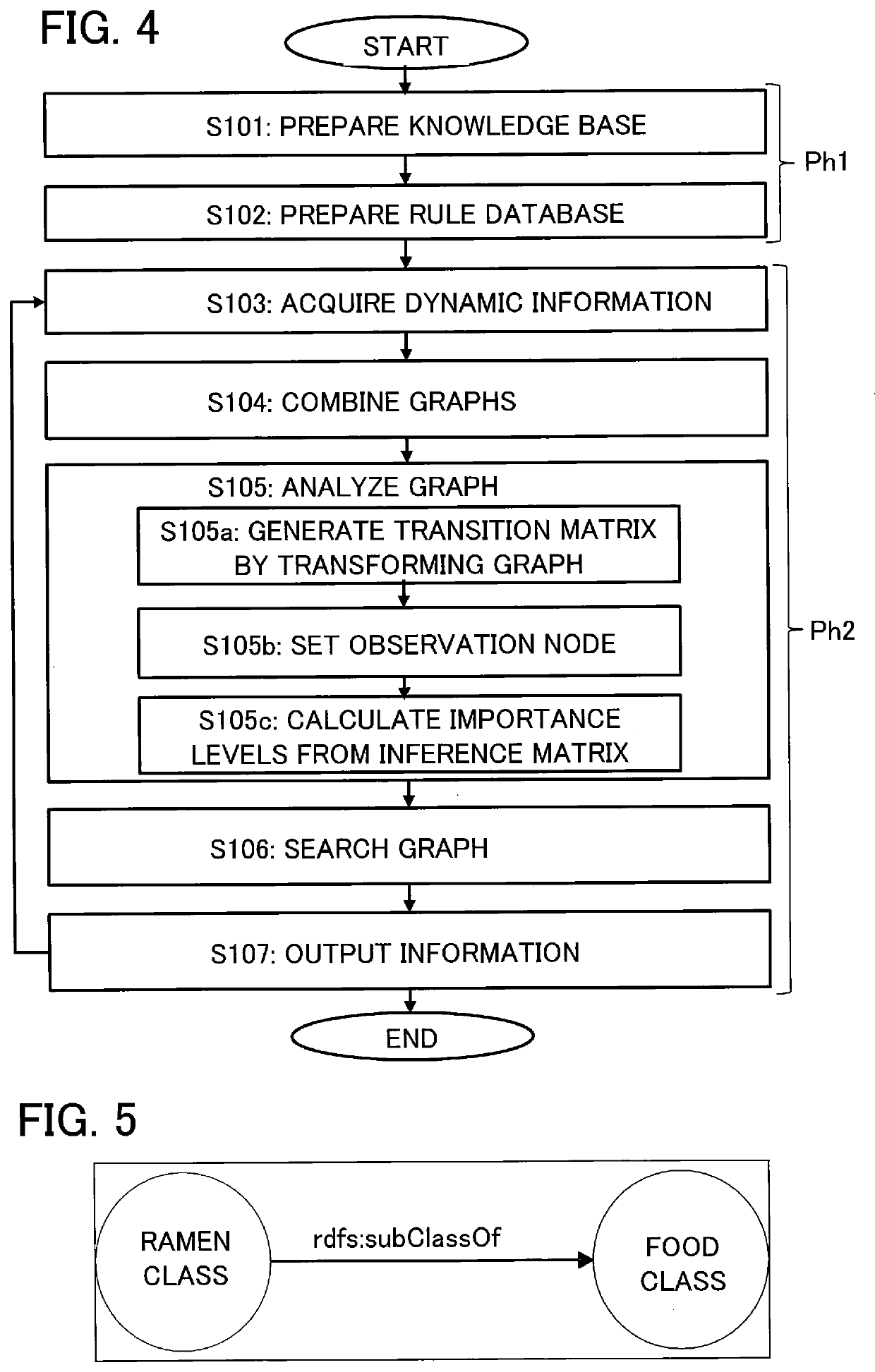
Inference device, inference method, and inference program
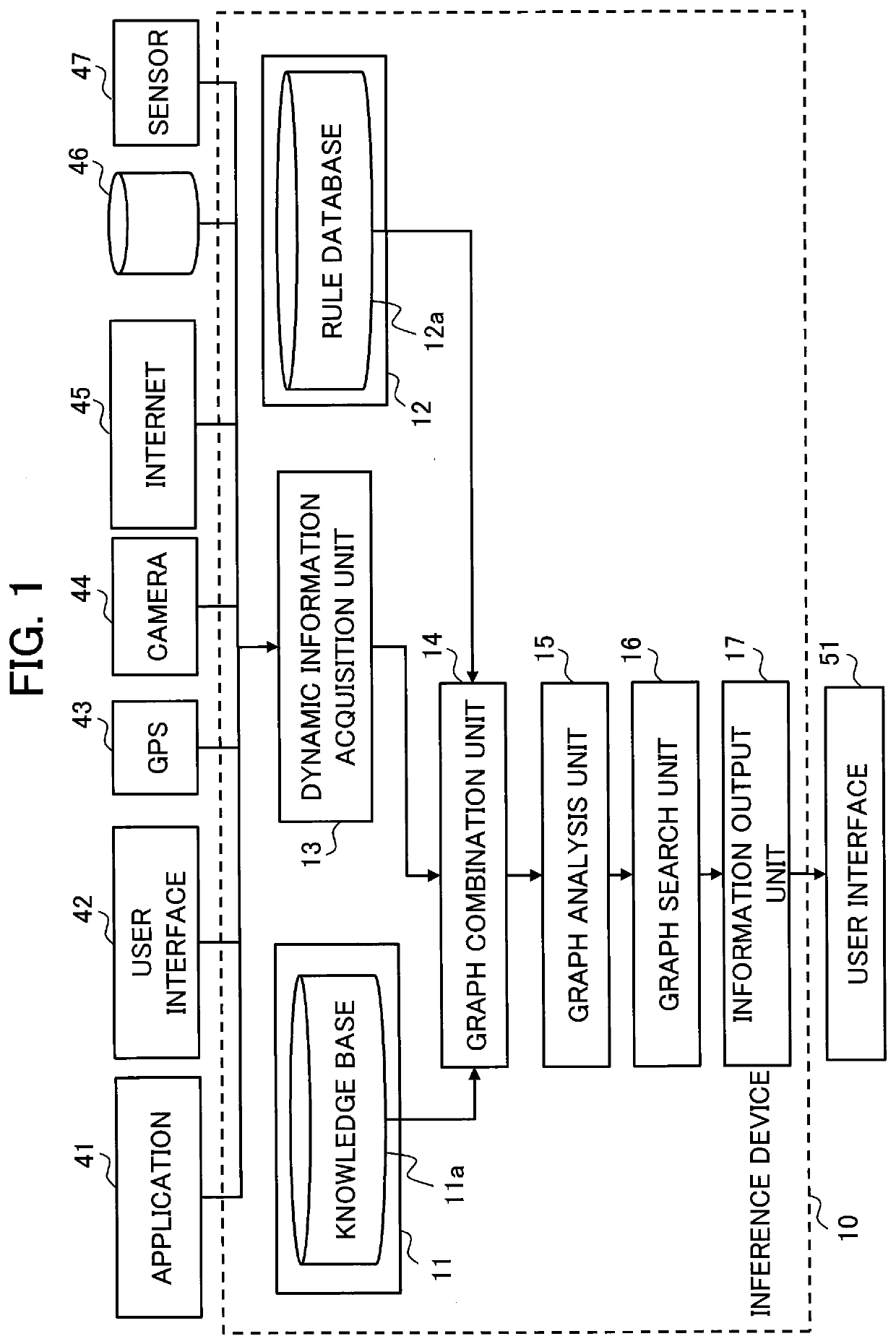
PendingUS20210166141A1Suitable resultOther databases indexingKnowledge representationAlgorithmTheoretical computer science
An inference device includes processing circuitry to generate integrated information by combining items of information respectively belonging to domains different from each other included in dynamically changing external information by means of forward chaining by using knowledge information including information regarding a human's condition and information regarding a human's action and provided from a knowledge base and an inference rule provided from a rule database. Each of the items of information respectively belonging to domains different from each other is information that can be represented as a directed graph including a node and an edge. The integrated information is an integrated graph. The processing circuitry calculates an importance level of a node as a component of the integrated graph from a probability of arriving at the node in a stationary state reached by performing a random walk on the integrated graph or by using an algorithm of PageRank.
Owner:MITSUBISHI ELECTRIC CORP
Eliminating method for tempered seamless steel pipe residual stress and adopted bi-directional chain type cooling bed
PendingCN108396130AGood effectGuaranteed straightnessFurnace typesProcess efficiency improvementChain typeStress relief
The invention provides an eliminating method for tempered seamless steel pipe residual stress and an adopted bi-directional chain type cooling bed. A straightening working procedure is adopted beforetempering, and the straightness accuracy of a steel pipe before tempering is ensured; the bi-directional chain type cooling bed with the gradient is adopted, the steel pipe is constantly rotated in the cooling process after being tempered, the straightness accuracy of the steel pipe in the cooling process after tempering is ensured, and therefore it is ensured that the steel pipe is not subjectedto stress relief annealing after being tempered and residual stress does not exceed 3% of the specified minimum yield strength while the straightness accuracy reaches 1 mm / m or below. The gradient ofa bed boy of the bi-directional chain type cooling bed is 2-5 degrees, the bed body is provided with the lower front portion and the higher rear portion and formed by alternately arranging multiple forward chains and multiple reverse chains at intervals, the forward direction of the forward chains is the same as the movement direction of the seamless steel pipe, and the forward direction of the reverse chains is opposite to the movement direction of the seamless steel pipe. By means of the eliminating method, the technical effect of achieving straightness and low residual stress simultaneouslyis achieved, the working procedure of stress relief annealing is omitted, the production cost is reduced, and the surface quality of the steel pipe is improved.
Owner:DAYE SPECIAL STEEL CO LTD
Bi-directional drag grader
A bi-directional drag grader comprising a rigid overhead support, attachable to a self propelled machine using a common receiver hitch or directly attached, a substantially rectangular rigid and collapsible frame, the frame having a leading edge and trailing edge with attachable blades, the blades having a planer sections along the length and inclined with respect to each other, the frame and support are operatively attached by forward and rearward chain lengths. Runners with stops are attached across the frame to support and position weights and prevent bending of the blades or frame while encountering loads in use. The frame and blades further comprise a design to use alternate configurations of cutting blades. The grader is configured so that the forward chains are in tension and the rearward chains are relaxed when the vehicle moves forward and vice-versa. This configuration allows for bi-directional operation.
Owner:GENDRON ROBERT J
Wire rod protection chain
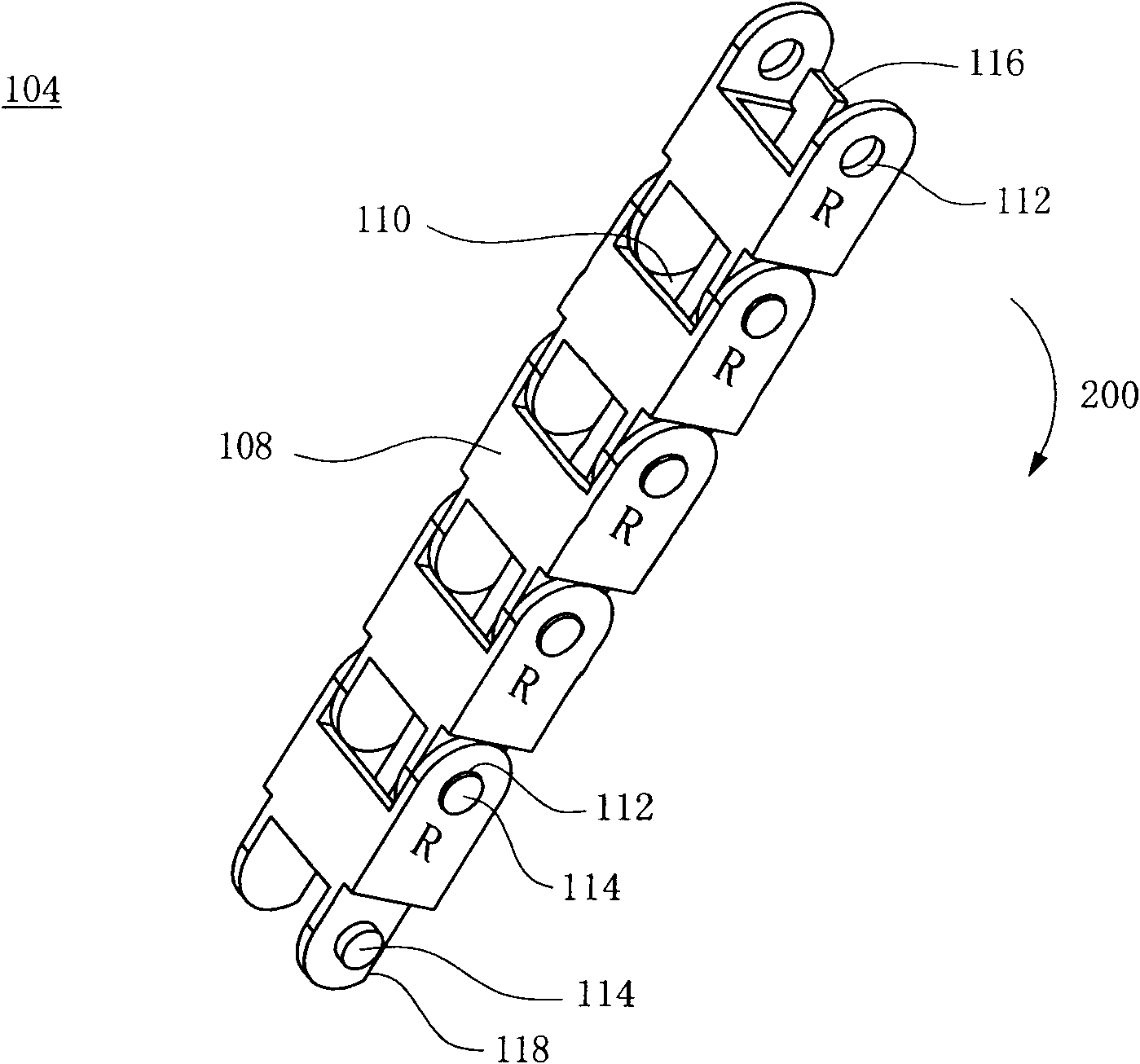
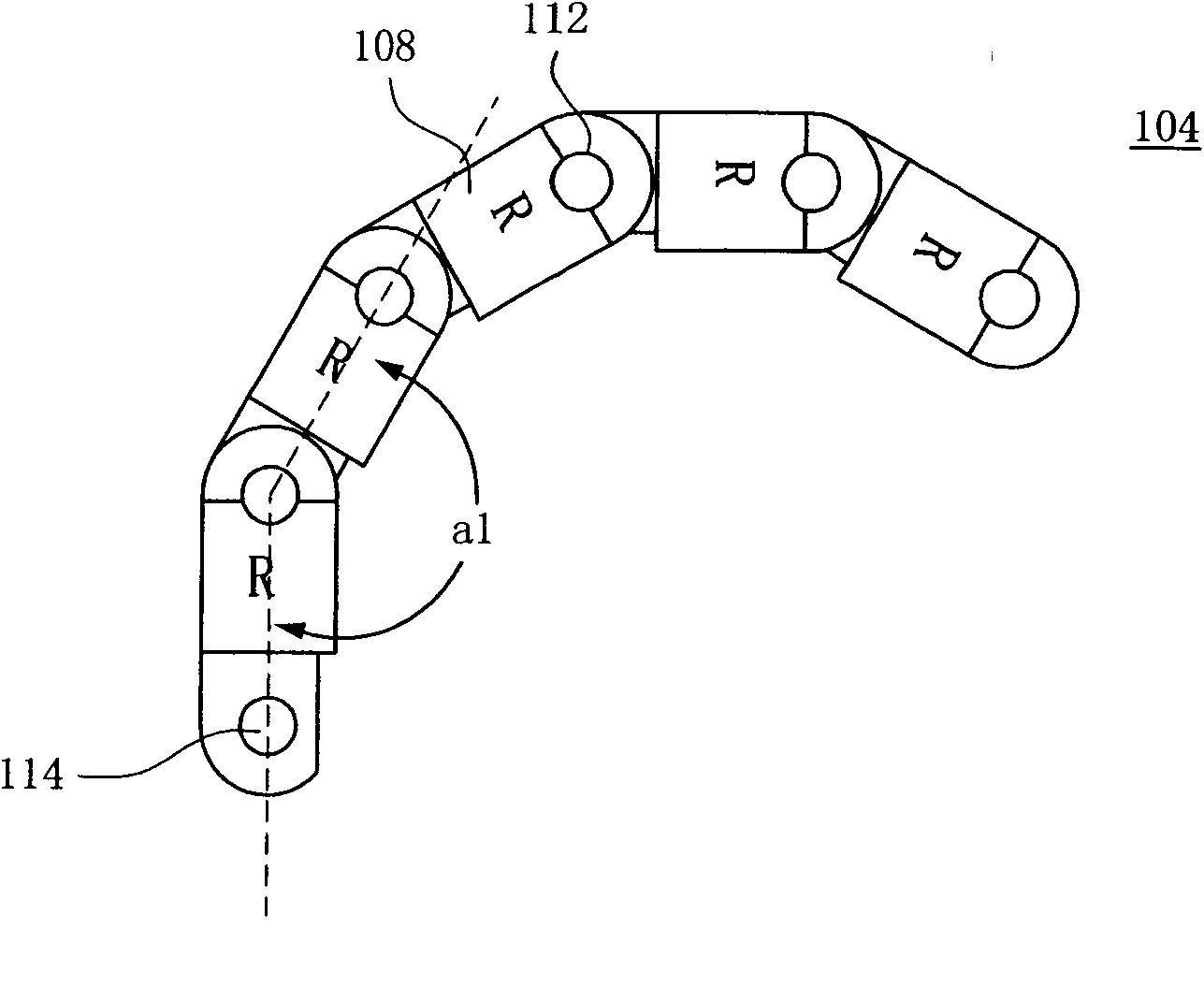
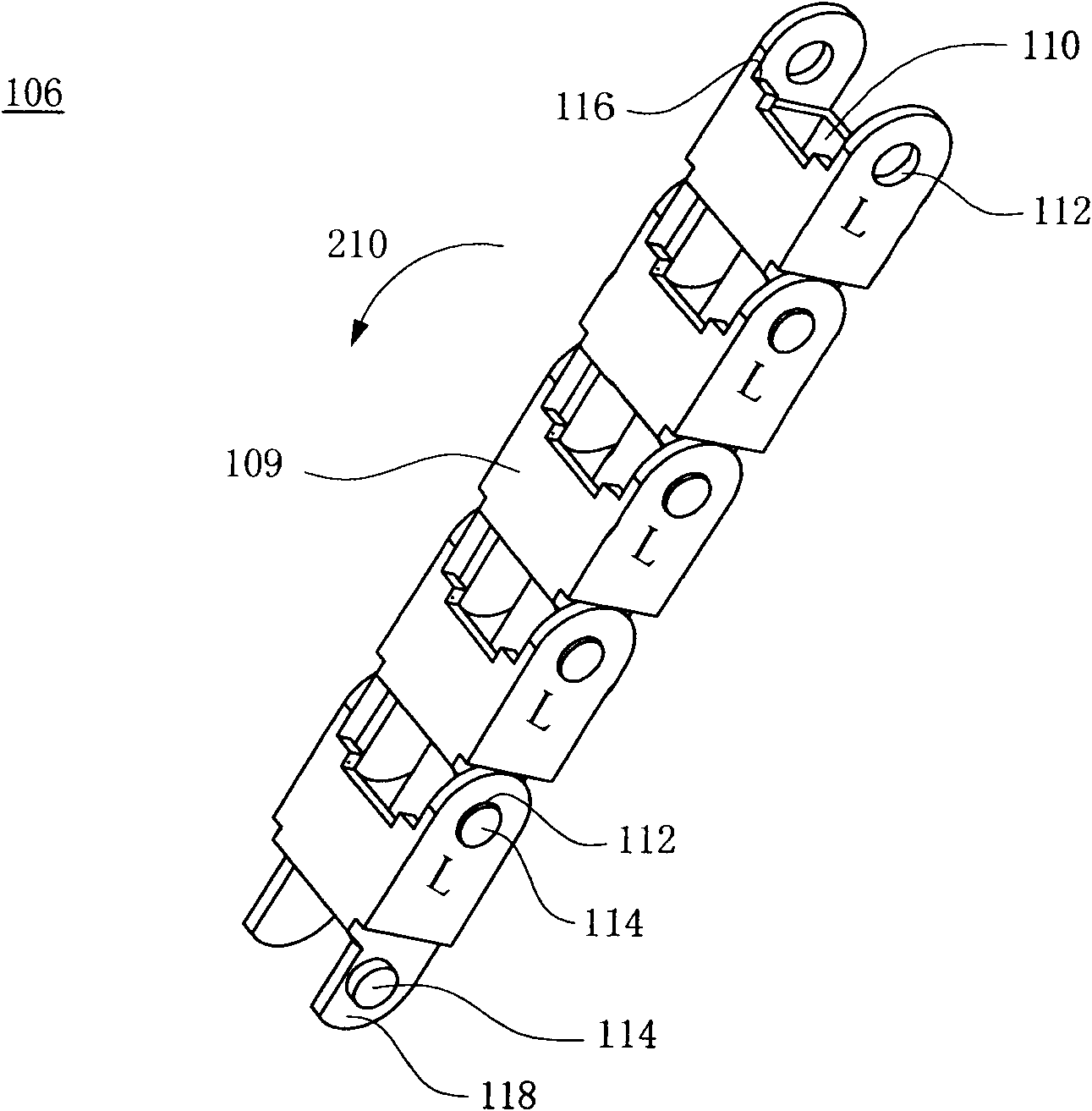
InactiveCN101677180ARestricted degrees of freedomAvoid getting stuckHauling chainsHoisting chainsWire rodForward chaining
The invention relates to a wire rod protection chain comprising forward sections and reverse sections which are staggered and interlinked. In the invention, each forward section is provided with a plurality of forward chain single bodies which are interlinked, wherein every two interlinked forward chain single bodies form an included angle limited within 0-180 degrees; and each reverse section isprovided with a plurality of reverse chain single bodies which are interlinked, wherein every two interlinked reverse chain single bodies form an included angle limited within 180-360 degrees, so thatthe wire rod protection chain can be folded in a zigzag manner.
Owner:INVENTEC CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com