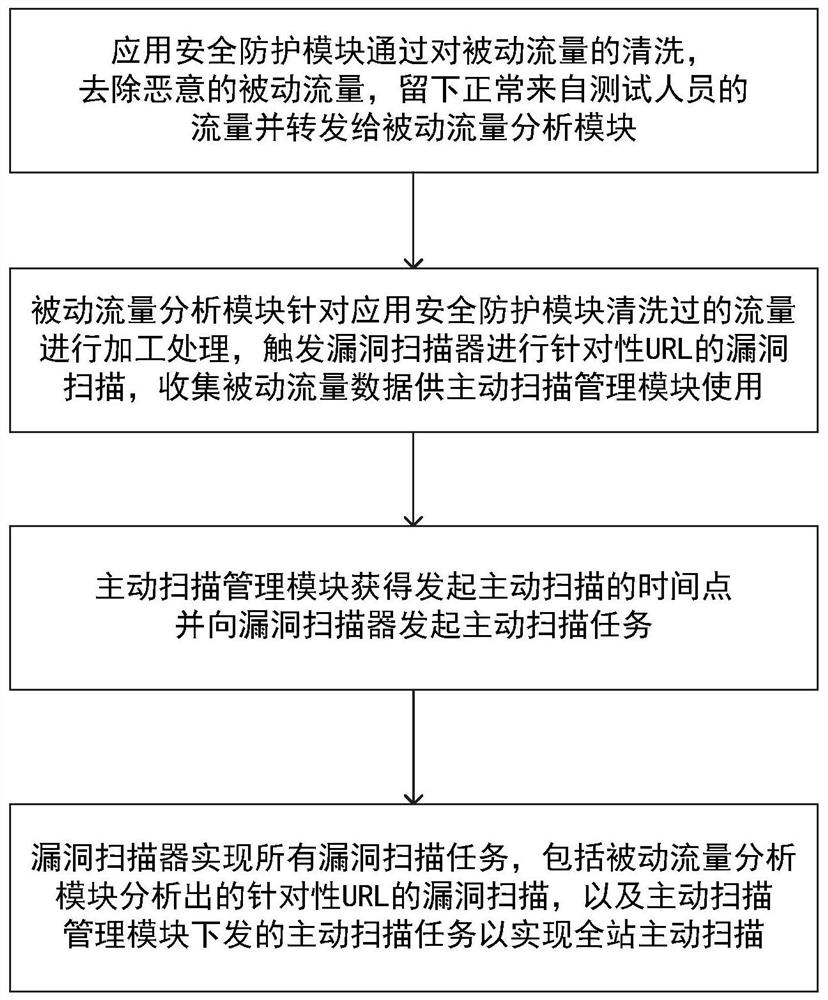
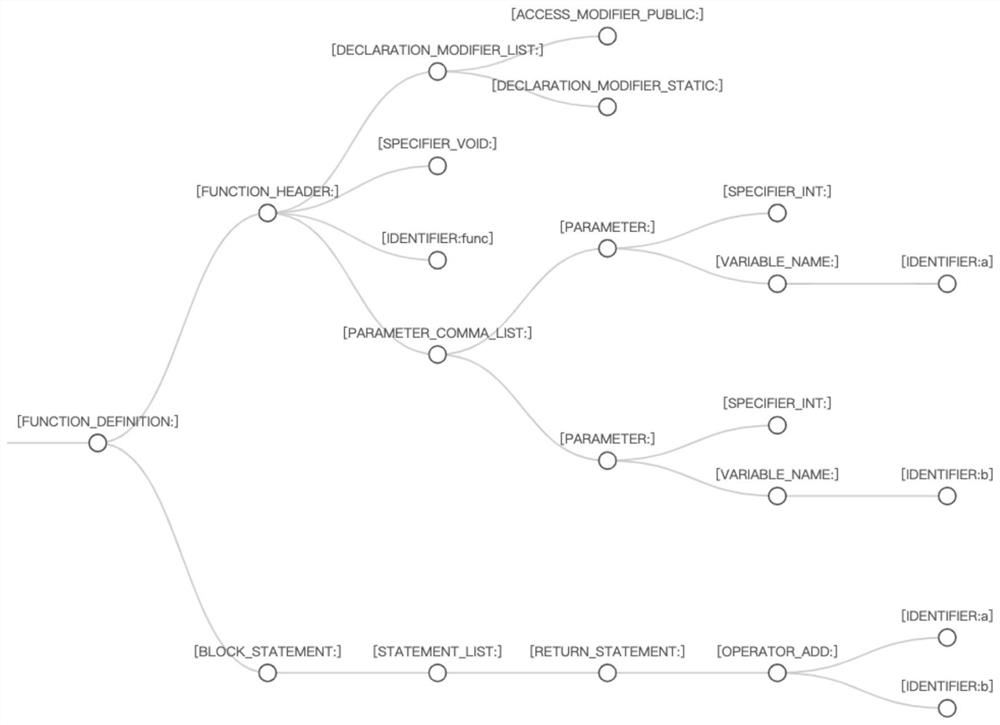
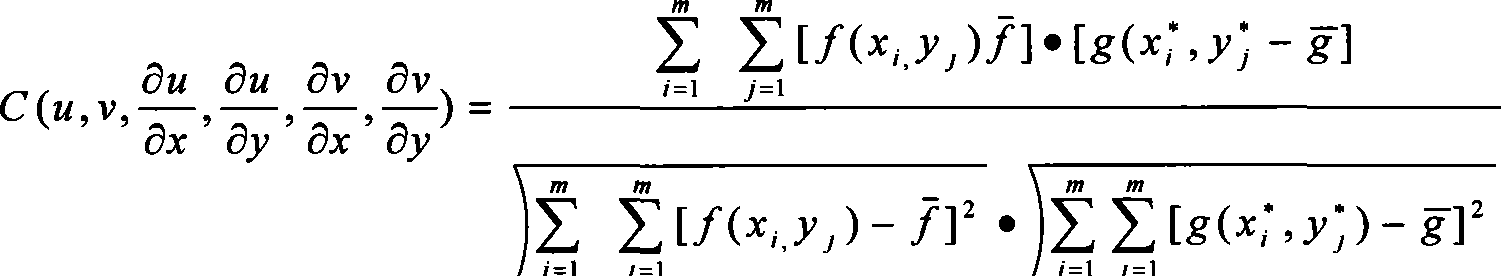Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
61results about How to "Improve security detection efficiency" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
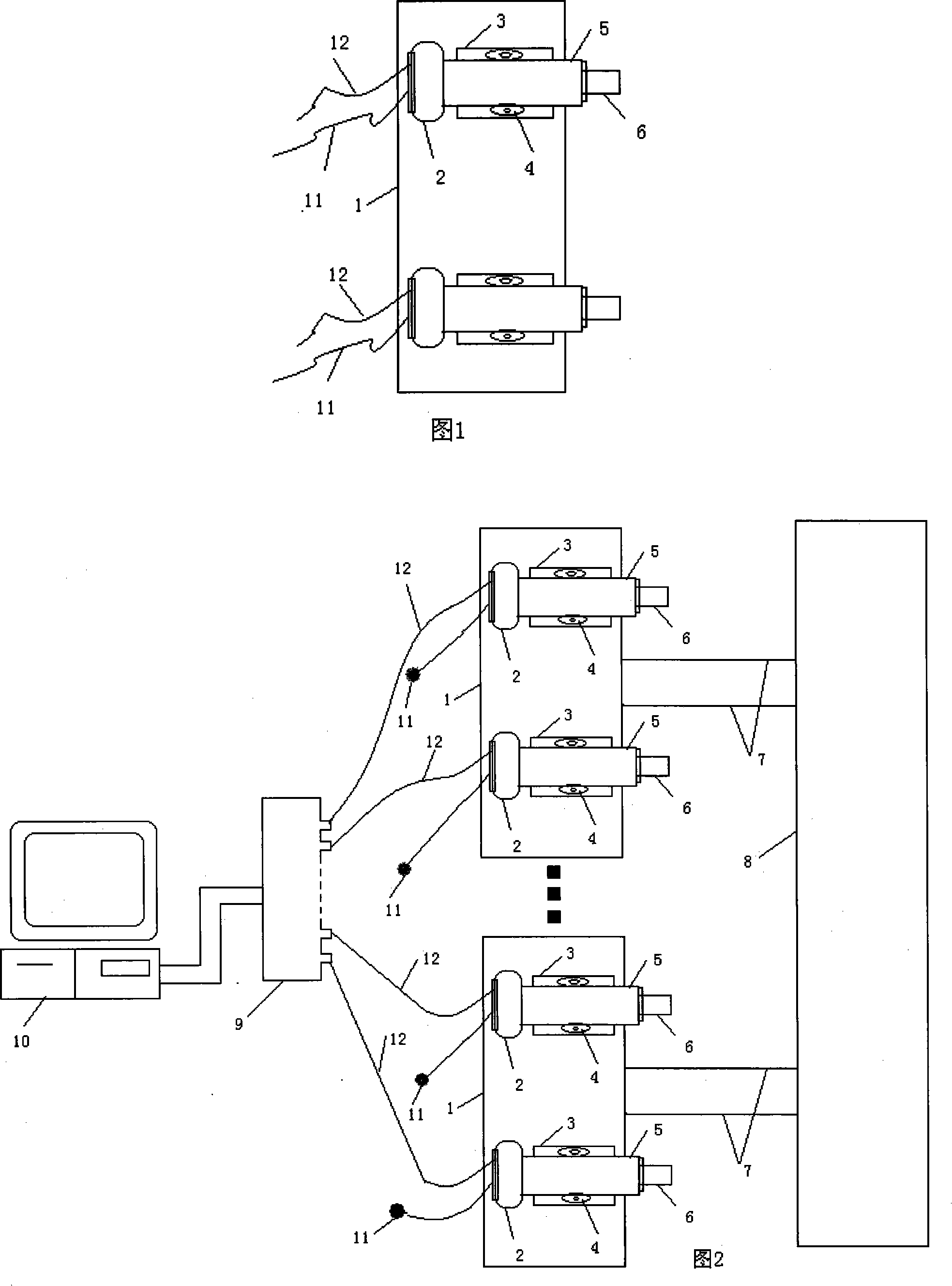
Double microscopic digital speckle strain measurement method
InactiveCN101182989AShort detection cycleLow resource consumptionUsing optical meansEconomic benefitsEngineering
The invention provides a digital double-micro speckle measuring method for strain. The invention relates to the measuring method for the stress and the strain of a structure, in particular to the measuring method for the stain with application of the photoelectron technology. The CCD with a micro-lens is arranged on a fixed platform while two CCDs serve as a group in the invention; when in measuring, a speckle field is manufactured on the surface of the measured object and the speckle images of the measured object in the scale distance between two points before and after being loaded are collected by the double-CCD synchronously and then are operated by the related processing software after being transmitted into a PC machine, at last, the mechanics parameter of the measured object can be obtained. The invention has short detection period, low consumption of resources, low detection cost, good economic benefit, easy interpretation and convenient and wide application. Meanwhile, the method can be used for detecting and evaluating the safety performance of other large buildings, such as houses, large dams, etc.
Owner:KUNMING UNIV OF SCI & TECH
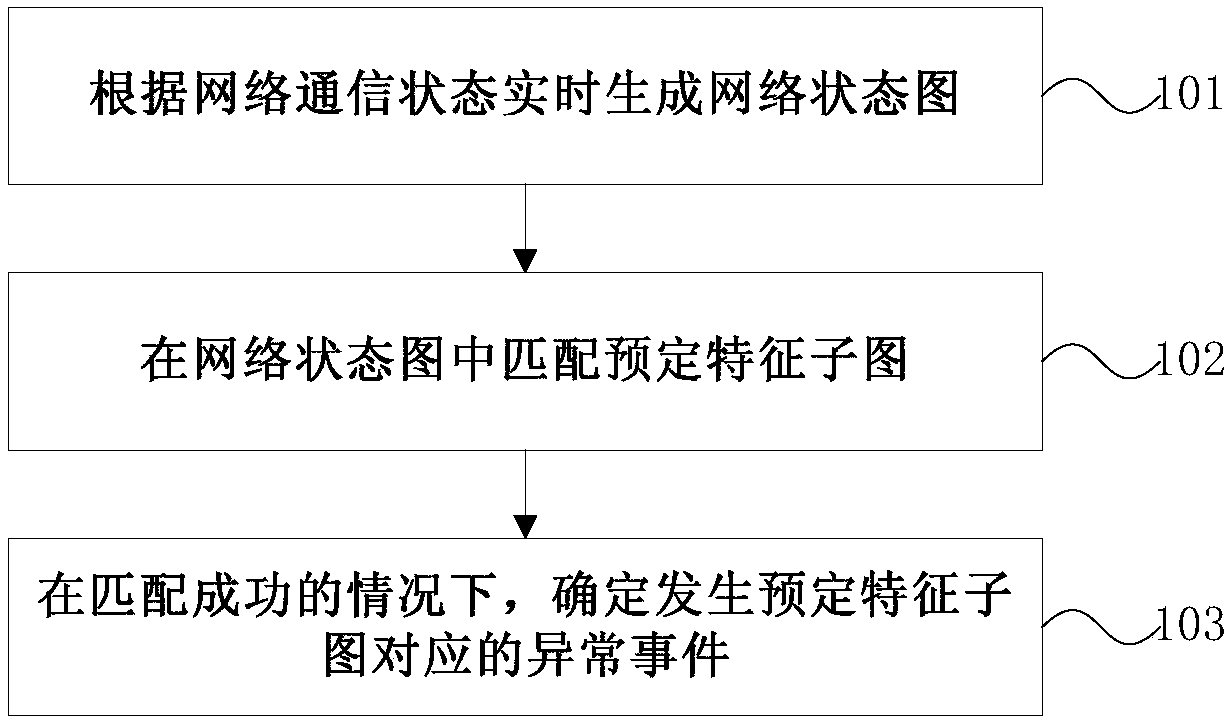
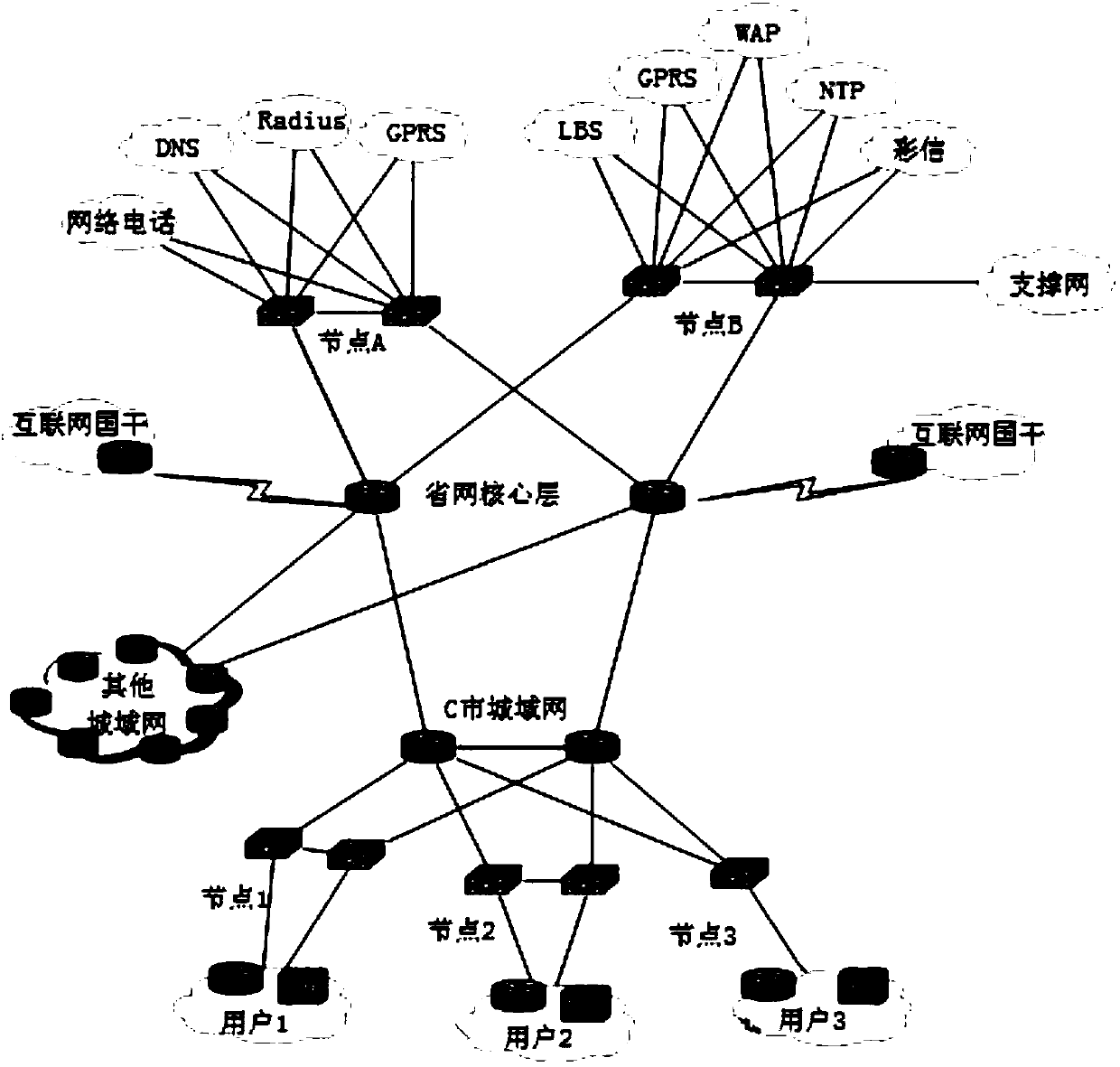
Network security detecting method and device
ActiveCN107666468AImprove security detection efficiencyTransmissionNetwork communicationState diagram
The invention discloses a network security detecting method and device and relates to the field of big data. The network security detecting method includes generating a network state diagram in real time according network communication states; matching a predetermined feature sub diagram in the network state diagram, wherein the predetermined feature sub diagram is a state diagram when errors of the network communication states occur; determining abnormal events corresponding to the predetermined feature sub diagram when the matching goes successfully. According to the invention, the sub diagram corresponding to abnormal states can be searched in the network state diagram generated in real time by adopting an image matching method and whether an abnormal state occurs in the network can bedetermined. Compared with a traditional keyword based search method, the diagram matching technology is more suitable for complex-mode search on data having high relevance, so that network security detection efficiency can be improved greatly.
Owner:CHINA TELECOM CORP LTD
Safety testing method, device, computer device and storage medium
ActiveCN108256322AImprove security detection efficiencyPlatform integrity maintainanceSafety testingComputer science
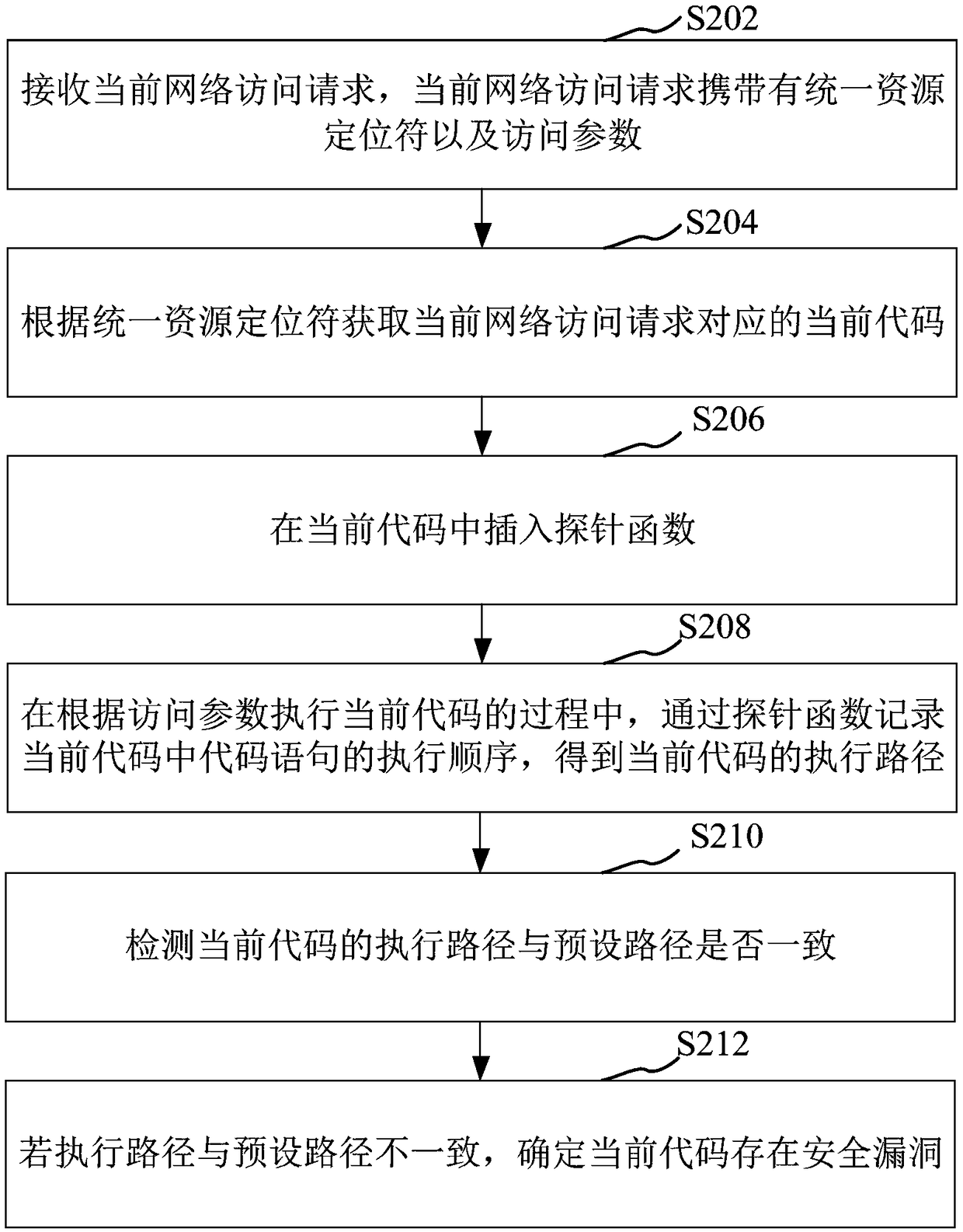
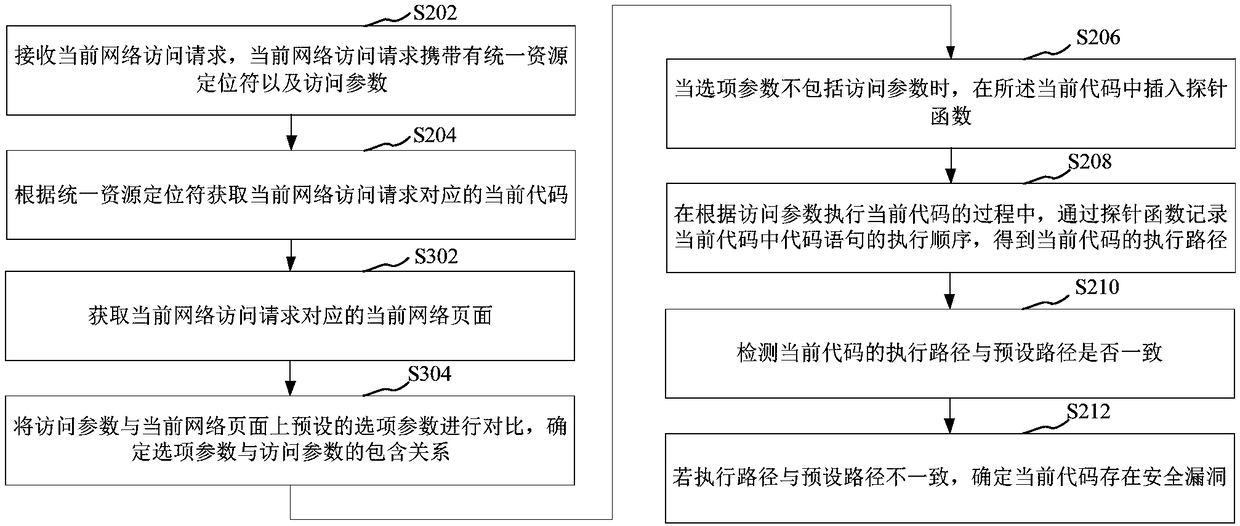
The application relates to a safety testing method, a safety testing device, a computer device and a storage medium. The method includes steps of receiving a current network access request, wherein the current network access request carries with a uniform resource positioning symbol and an access parameter; according to the uniform resource positioning symbol, acquiring a current code corresponding to the current network access request; inserting a probe function in the current code; when the current code is executed according to the access parameter, recording the executing order of a code sentence in the current code through the probe function, and acquiring the executing path of the current code; detecting if the executing path of the current code is consistent with the preset path; ifthe executing path is inconsistent to the preset path, confirming the safety flaw existed in the current code. By adopting the method, the detecting efficiency can be improved.
Owner:PING AN TECH (SHENZHEN) CO LTD
Link security detection method and client
InactiveCN105530218AImprove security detection efficiencyImprove experiencePlatform integrity maintainanceTransmissionNetwork dataProtocol for Carrying Authentication for Network Access
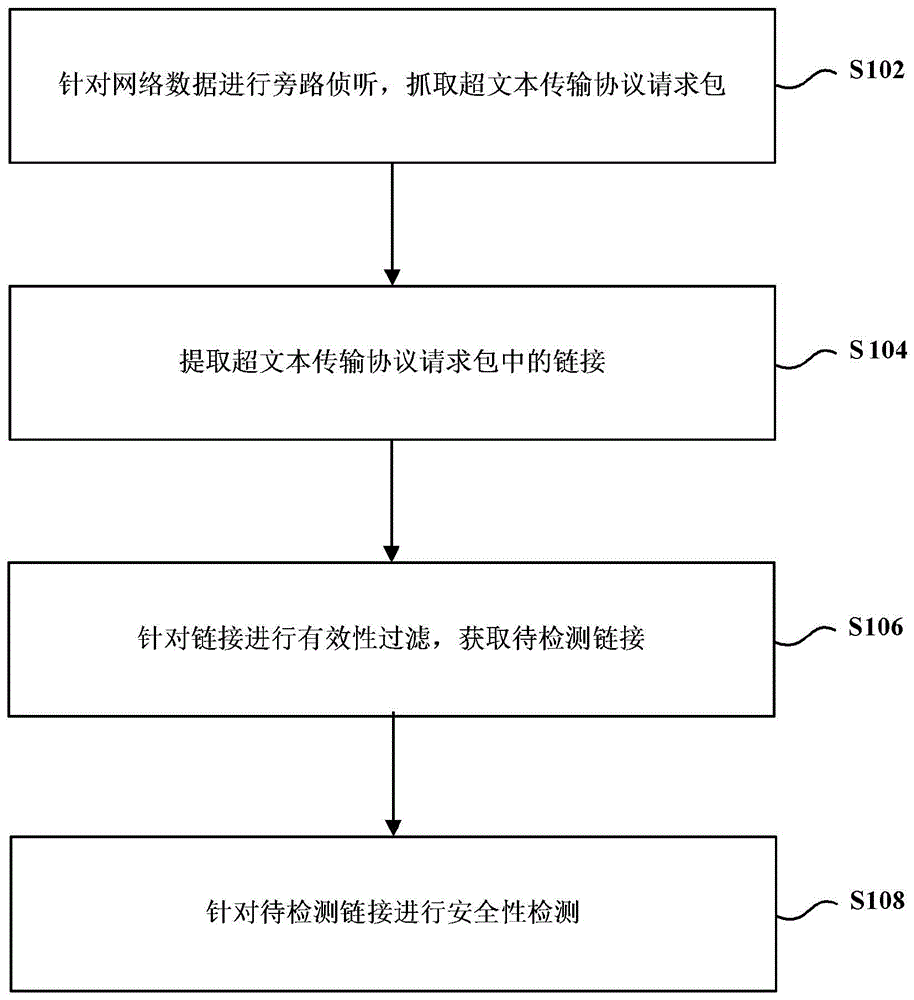
The invention provides a link security detection method and a client. The method comprises steps: bypass interception is carried out for network data, and a hypertext transfer protocol request packet is grabbed; the link in the hypertext transfer protocol request packet is extracted; effective filtering is carried out on the link to acquire a to-be-detected link; and security detection is carried out on the to-be-detected link. In the embodiment of the invention, after the link is acquired, effective filtering is firstly carried out on the link, security detection is then carried out on the acquired to-be-detected link, the real-time performance of the security detection is improved, the security detection efficiency is greatly enhanced, the network security is ensured more reasonably, and the user experience is enhanced.
Owner:BEIJING QIANXIN TECH
Website security detection system and method based on full flow
ActiveCN112003864AImprove securityIncrease coveragePlatform integrity maintainanceTransmissionWeb siteWeb development
The invention discloses a website security detection system and method based on full flow, which can more comprehensively cover the security test of a fast iterative WEB project, can discover newly added vulnerabilities of the system in time and can improve the security of a WEB system. The technical scheme is as follows: according to the system and the method provided by the invention, the problem of insufficient security detection vulnerability coverage rate frequently encountered by an Internet company in a WEB development process is taken as a starting point, safety scanning is carried outby combining active scanning and passive scanning latitudes, and active flow and passive flow of a website are covered, so that newly-added vulnerabilities of the system are discovered in time, and the safety of the WEB system is improved.
Owner:SHANGHAI JUSHUITAN NETWORK TECH CO LTD +1
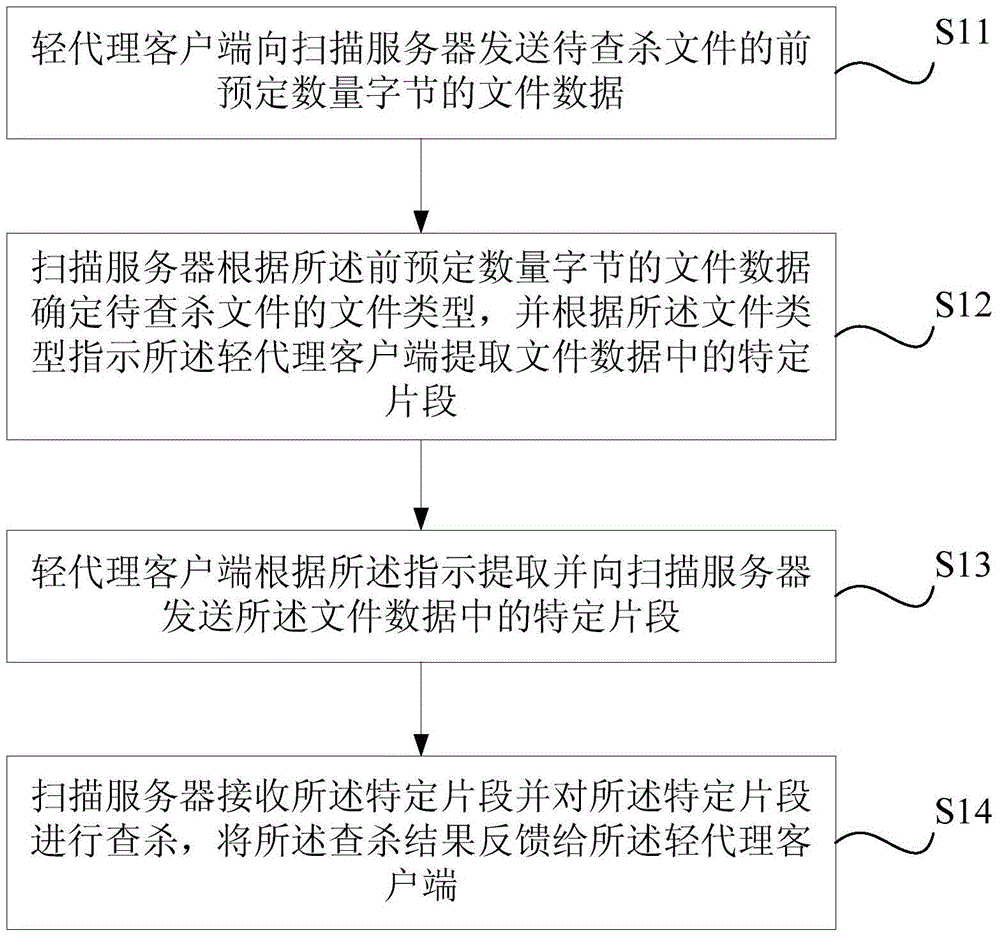
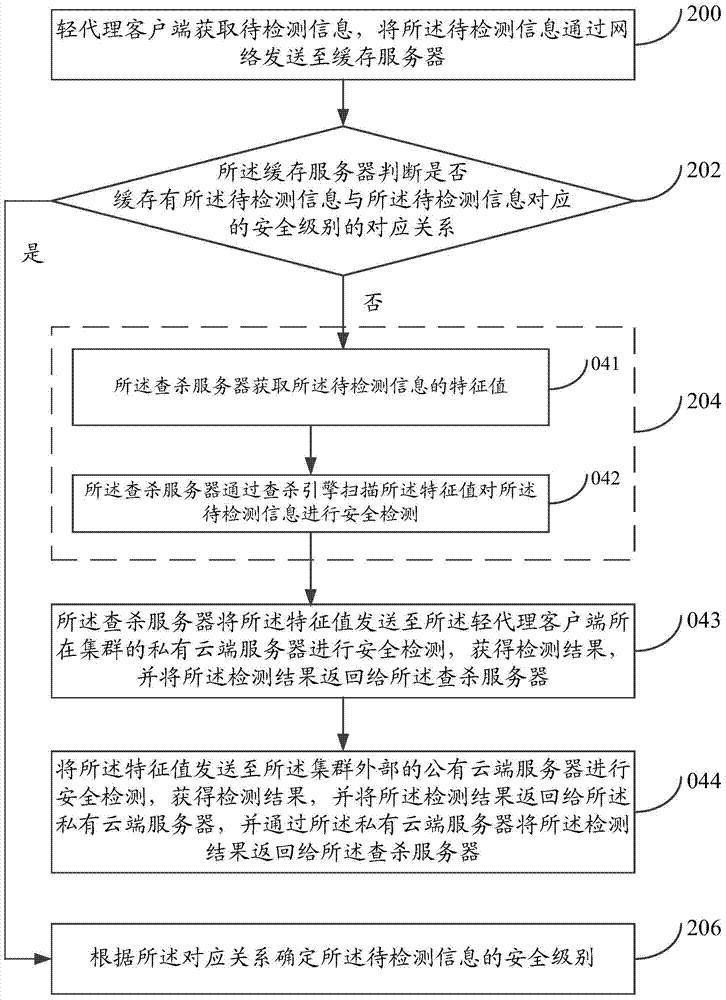
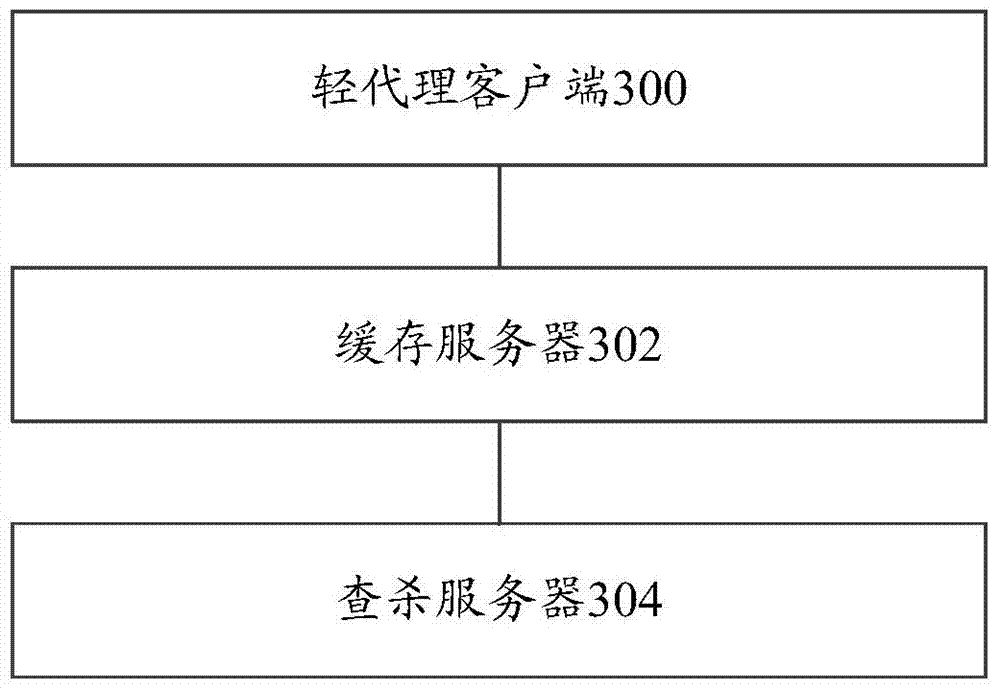
System and method for detecting file in virtual environment
InactiveCN104598818ARealize detectionReduce resource usagePlatform integrity maintainanceSoftware simulation/interpretation/emulationVirtualizationClient-side
The invention relates to a system and a method for detecting a file in a virtual environment. The method comprises the steps of sending file data with a front preset number of bytes of a to-be-searched and killed file to a scanning server by a light agent client, wherein the light agent client is arranged in a virtual machine; determining the file type of the to-be-searched and killed file according to the file data with the front preset number of bytes, and indicating the light agent client to extract a specific fragment in the file data according to the file type; extracting and sending the specific fragment in the file data to the scanning server according to the indication by the light agent client; receiving the specific fragment by the scanning server, searching and killing the specific fragment, and feeding back a searching and killing result to the light agent client. According to the technical scheme, file detection in the virtual environment can be rapidly and efficiently realized, the safety detection efficiency is increased, and the resource occupation rate of a physical computer is reduced.
Owner:BEIJING QIANXIN TECH
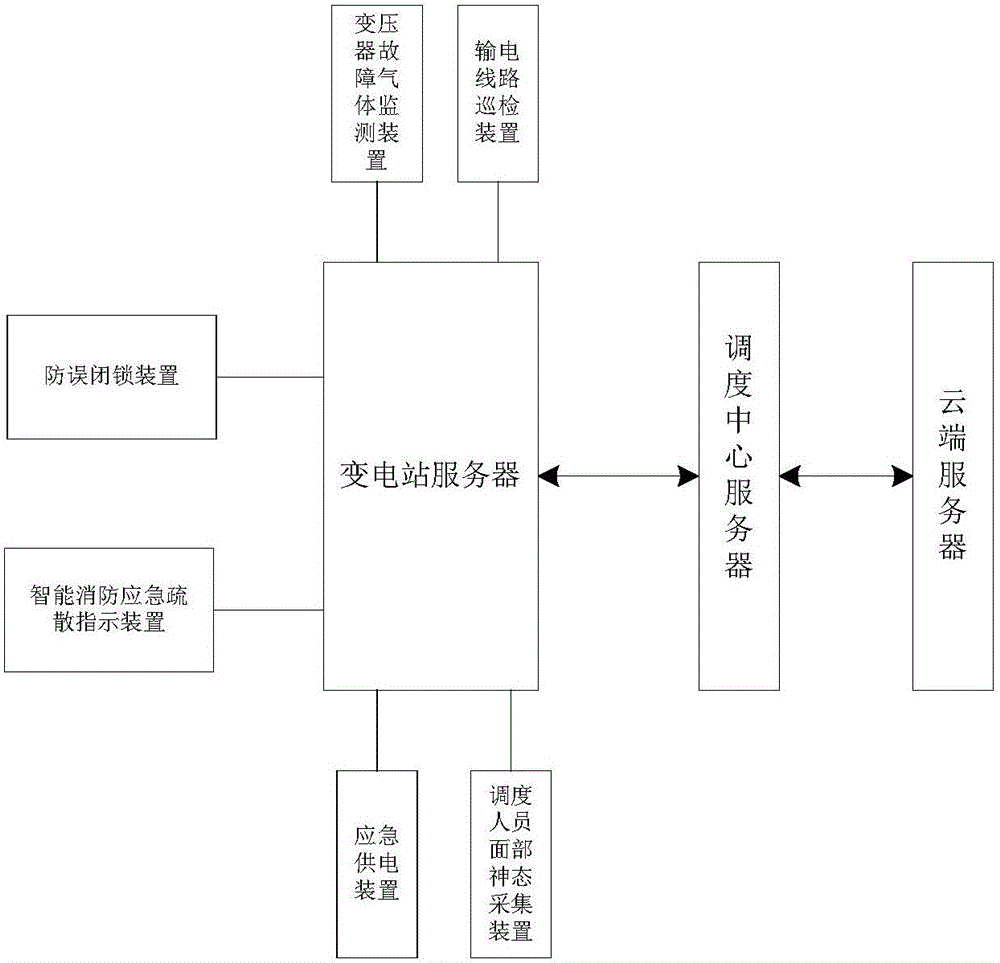
Grid dispatching monitoring early warning system and method
ActiveCN105958653ARun fastImprove resource utilizationCircuit arrangementsMaterial analysis by optical meansPower gridReal-time computing
The invention discloses a grid dispatching monitoring early warning system and method. The system comprises a dispatching center server, the dispatching center server communicates with a server in each substation and also communicates with a cloud server, and the cloud server is used for generating a grid dispatching instruction from the received information based on a task dispatching algorithm of IGA and feeding back the generated grid dispatching instruction to the server of each substation by the dispatching center server to control the operation of the substation.
Owner:国网山东省电力公司招远市供电公司
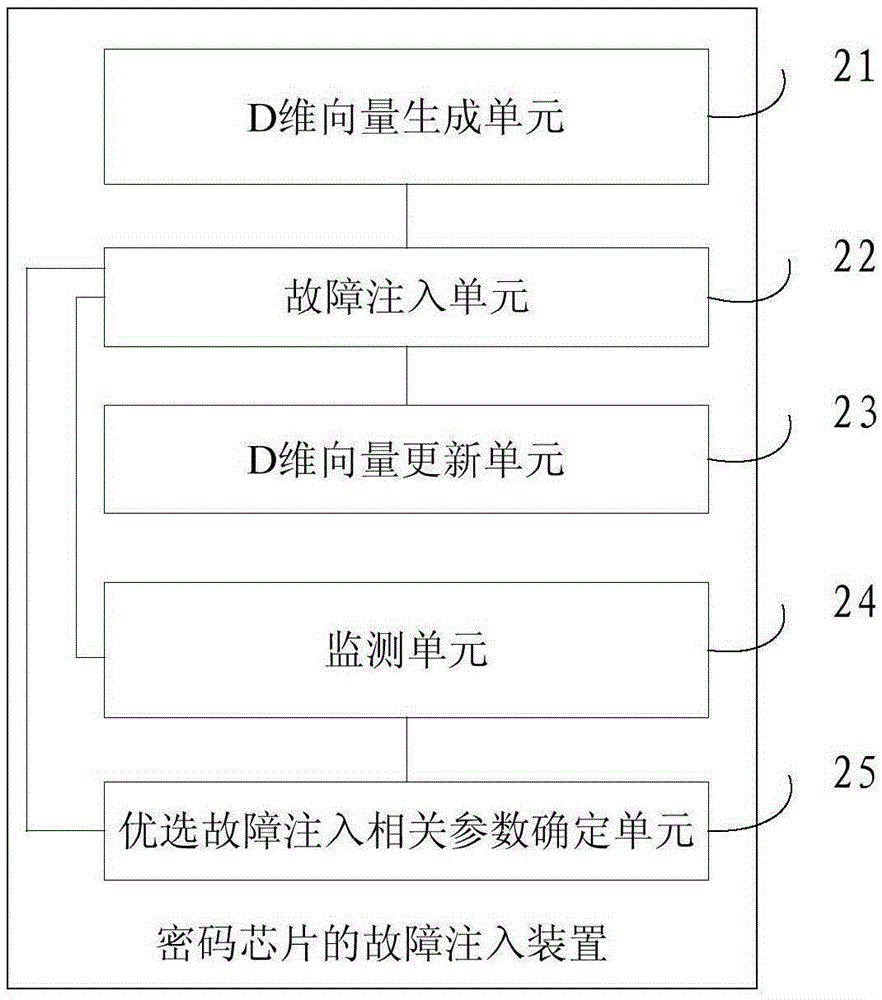
Fault injection method and fault injection device for password chips
The invention provides a fault injection method and a fault injection device for password chips, and relates to the technical field of password chips. The method comprises the steps as follows: randomly selecting multiple fault injection related parameter particles from a fault injection related parameter set; injecting a fault to a password chip according to D fault injection related parameters in each D-dimension vector; updating each dimension of fault injection related parameter in each D-dimension vector using a speed parameter; injecting a fault to the password chip again after updating; monitoring the frequency of effective error output for fault injection of the password chip according to each D-dimension vector; and executing the steps repeatedly until the frequency corresponding to a first D-dimension vector of the D-dimension vectors is greater than or equal to a preset threshold, and determining the D fault injection related parameters in the first D-dimension vector as preferred fault injection related parameters. According to the invention, the problem that selection of the required parameters from the parameter set by means of exhaustion is inefficient and results in slow password chip detection is avoided.
Owner:CHINA ACADEMY OF INFORMATION & COMM
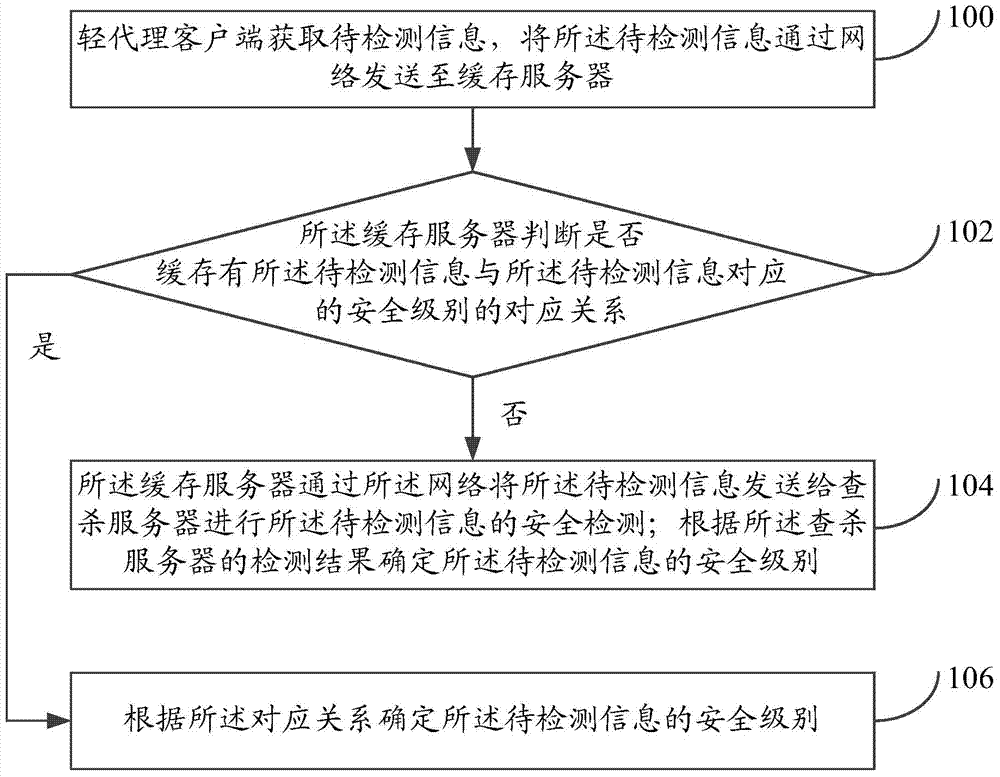
Virtual safety detecting method and system
ActiveCN104504330AIncrease resource usageImprove security detection efficiencyPlatform integrity maintainanceProgram controlVirtualizationCache server
The invention provides a virtual safety detecting method and a virtual safety detecting system. The method comprises the following steps that a light agent client acquires to-be-detected information and sends the to-be-detected information to a cache server through a network; the cache server judges whether corresponding relation between the to-be-detected information and a corresponding safety level of to-be-detected information exists or not; if the corresponding relation between the to-be-detected information and the corresponding safety level of to-be-detected information does not exist, the cache server sends the to-be-detected information to a checking server through the network to perform safety detection on the to-be-detected information; according to the detecting result of the checking server, the safety level of the to-be-detected information is determined; if the to-be-detected information and the corresponding safety level of to-be-detected information exists, according to the corresponding relation, the safety level of the to-be-detected information is determined, wherein the light agent client is installed in a virtual machine. The efficiency of safety detection is improved, and the resource occupation rate of a physical machine is reduced.
Owner:BEIJING QIANXIN TECH
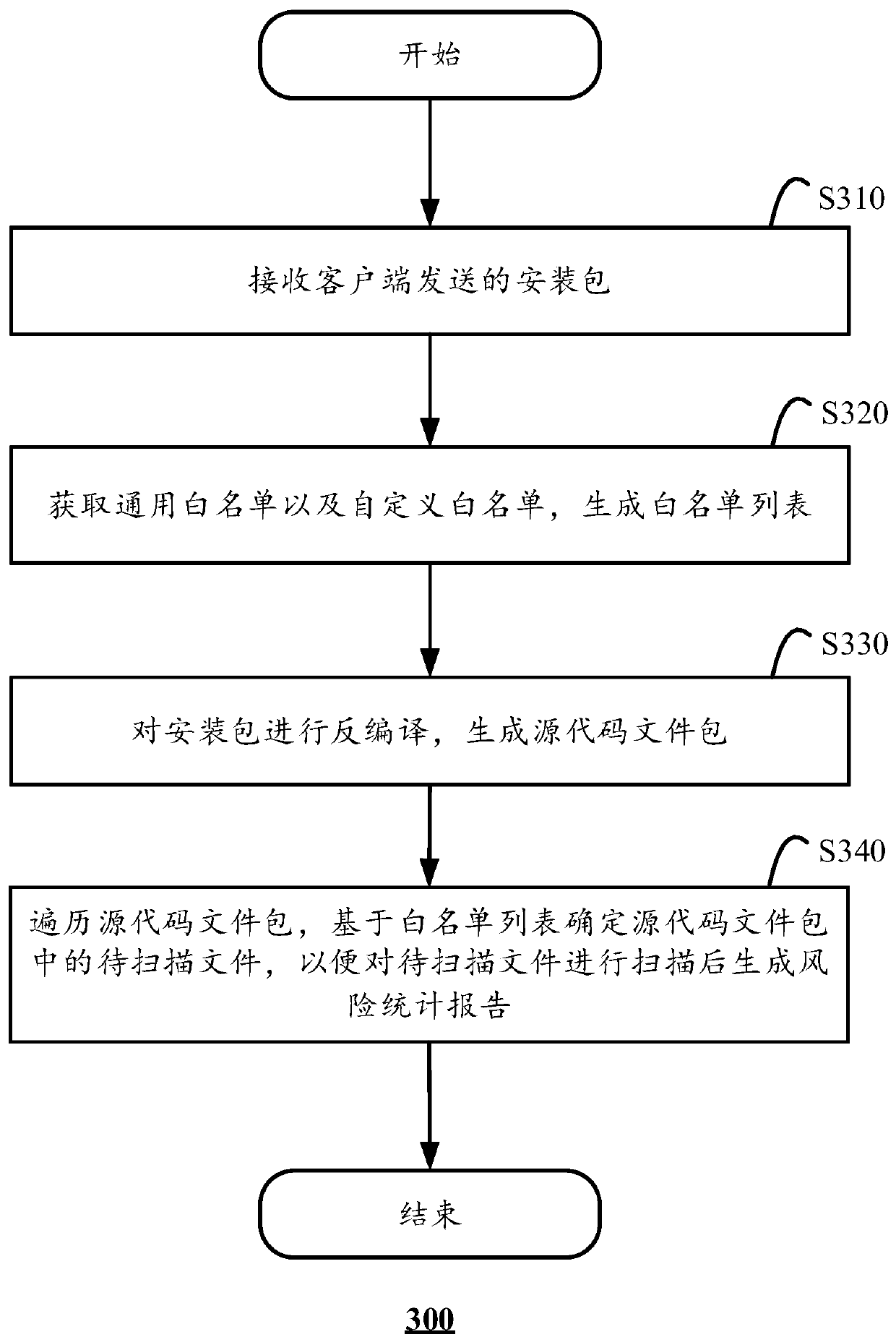
Safety detection method and safety detection system
ActiveCN110826068AMeticulous and comprehensive testingGuaranteed reliabilityPlatform integrity maintainanceSource code fileSoftware engineering
The invention discloses a security detection method, which is executed in computing equipment and comprises the following steps: receiving an installation package sent by a current client; obtaining ageneral white list and a custom white list, and generating a white list; decompiling the installation package to generate a source code file package; and traversing the source code file package, anddetermining a to-be-scanned file in the source code file package based on the white list so as to generate a risk statistics report after the to-be-scanned file is scanned. The invention further discloses a corresponding safety detection system. The security detection method provided by the invention is beneficial to improving the security detection efficiency of the installation package and greatly reducing the false alarm rate.
Owner:海南车智易通信息技术有限公司
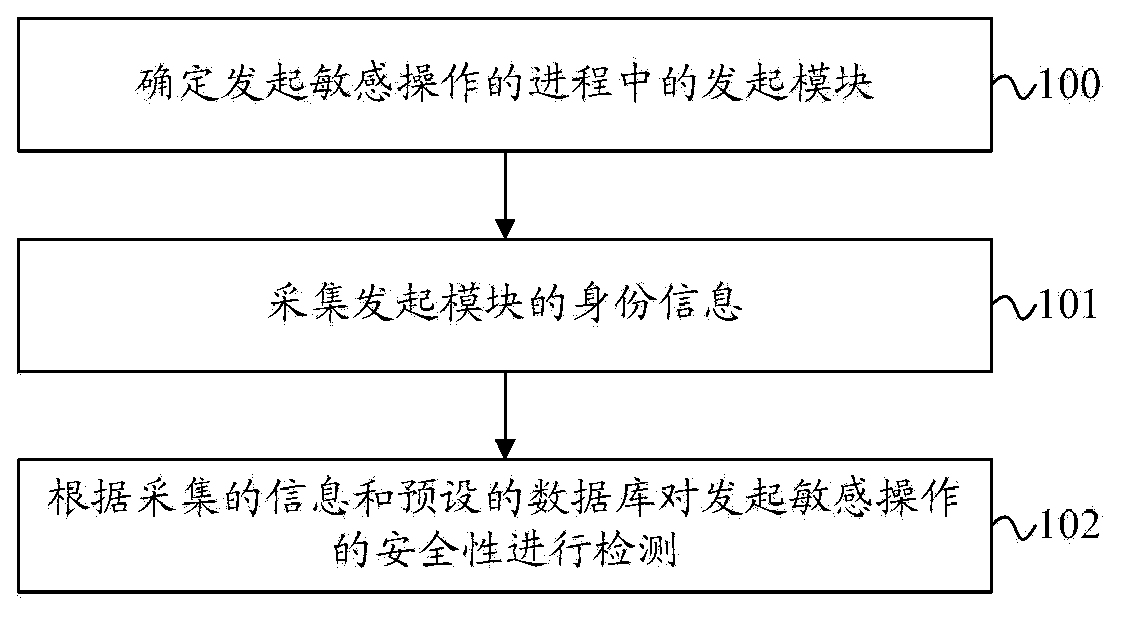
Safety detection method and device
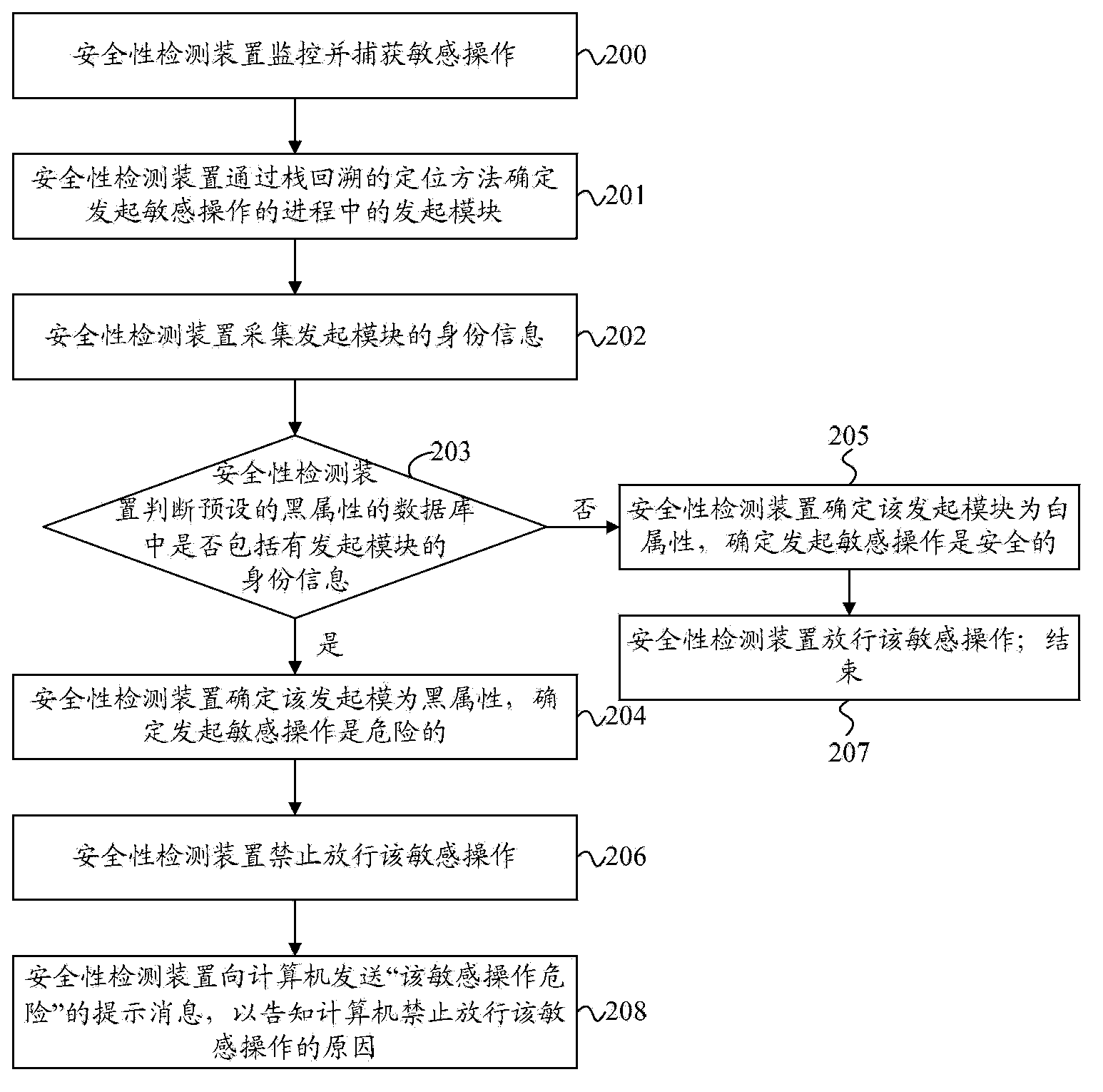
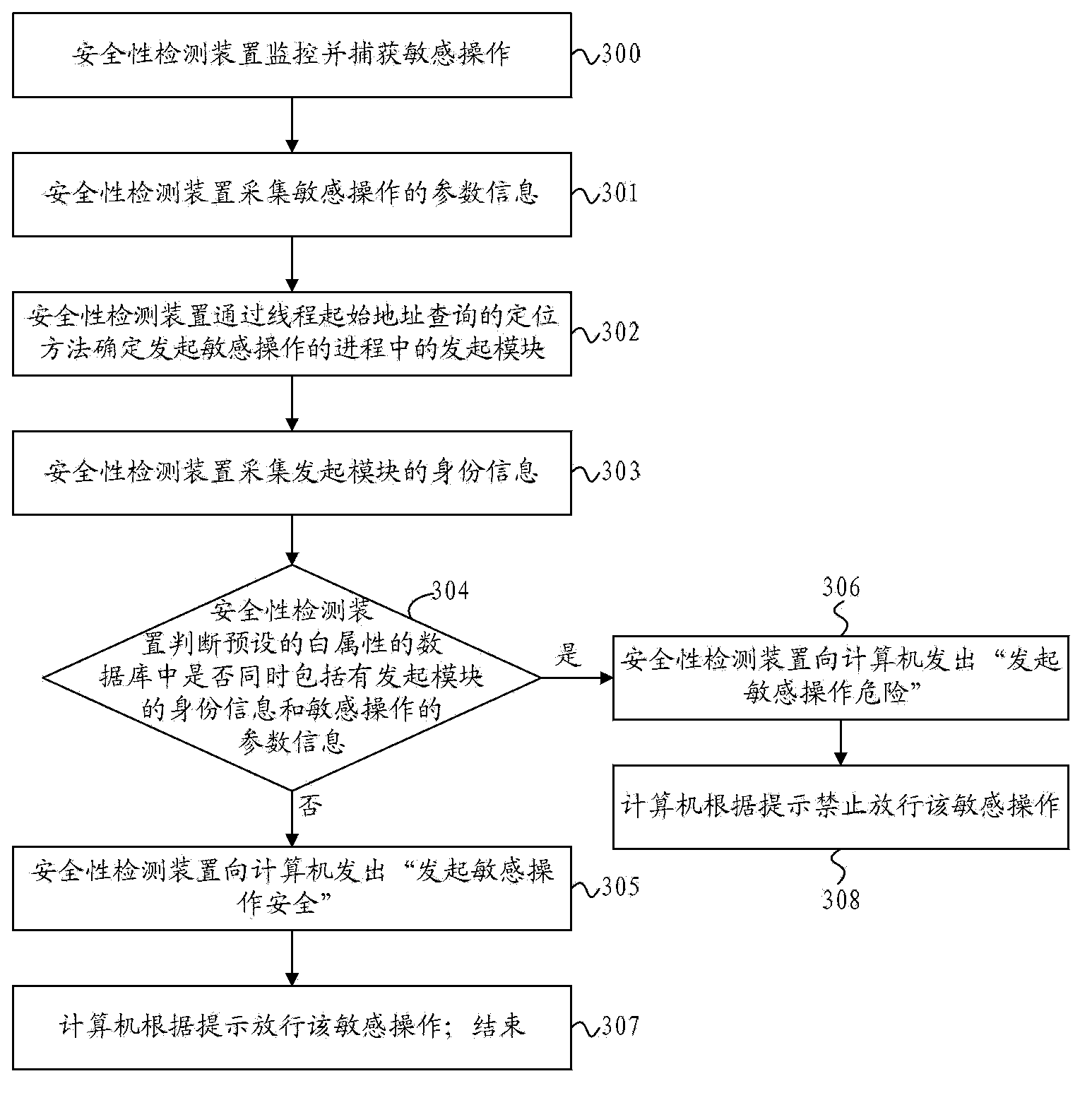
ActiveCN103679035AImprove securityImprove stabilityPlatform integrity maintainanceGranularityComputerized system
The invention discloses a safety detection method and device and belongs to the technical field of computer safety. The safety detection method comprises the steps that a launching module which launches sensitive operation in a process is determined, the identity information of the launching module is acquired, and the safety of the launched sensitive operation is detected according to the acquired information and a preset database. Compared with the prior art, the safety detection method and device have the advantages that the detection granularity is fine, and the safety and the stability of a computer system can be effectively improved; due to the fact that the safety of the launched sensitive operation is detected according to the identity information of the launching module and the preset database, the problem that the situation that a launching module with a black property launches sensitive operation by hijacking the progress of a launching module with a white property can not be detected can be effectively solved, as a result, the safety detecting efficiency can be effectively improved, and the safety and the stability of the computer system are guaranteed.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
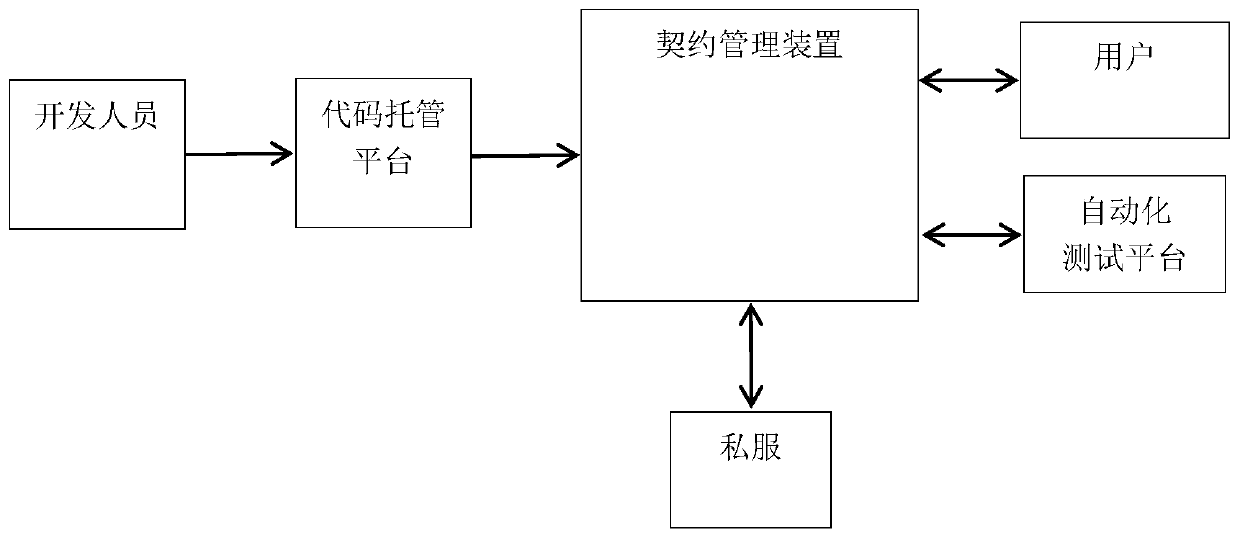
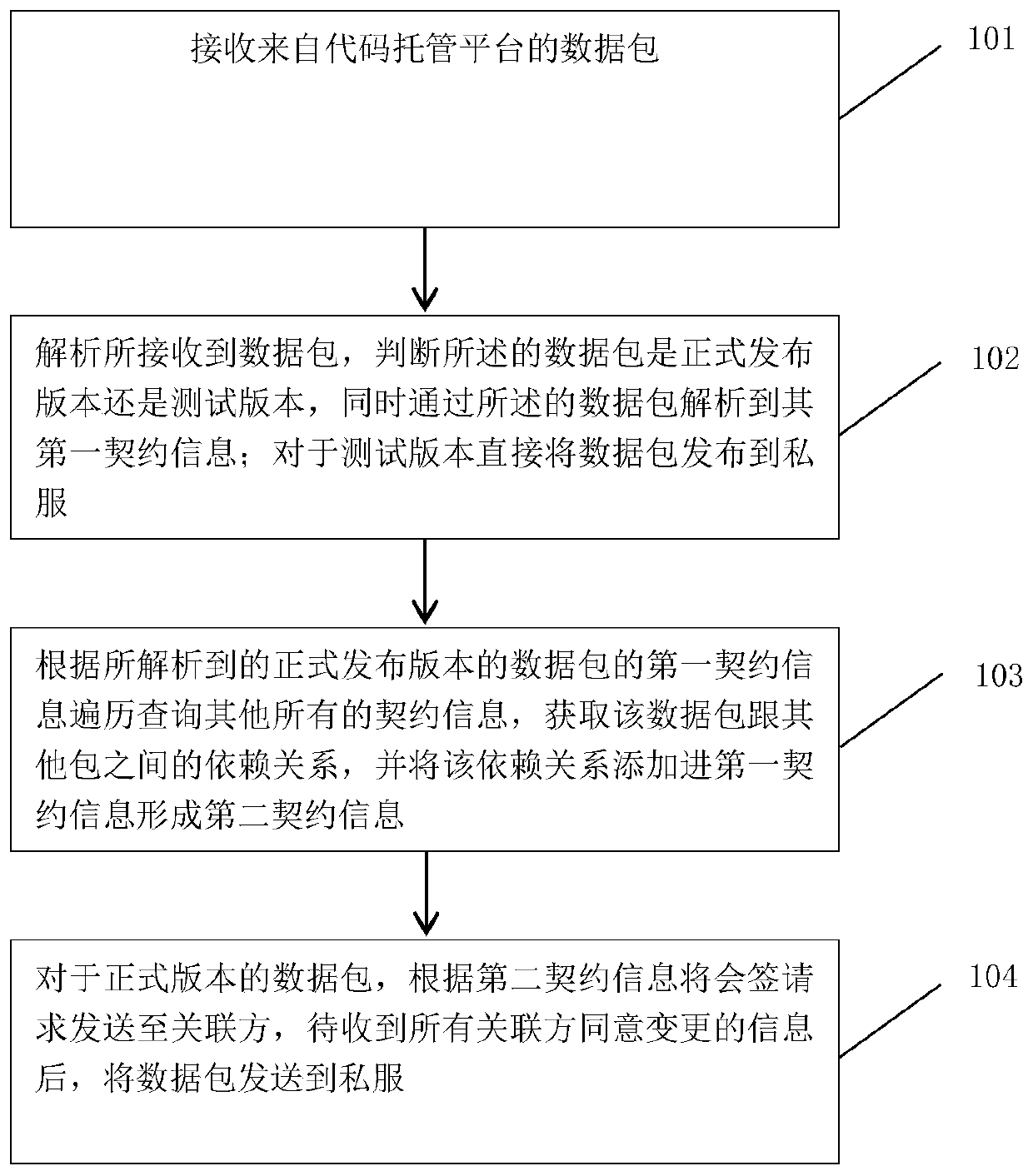
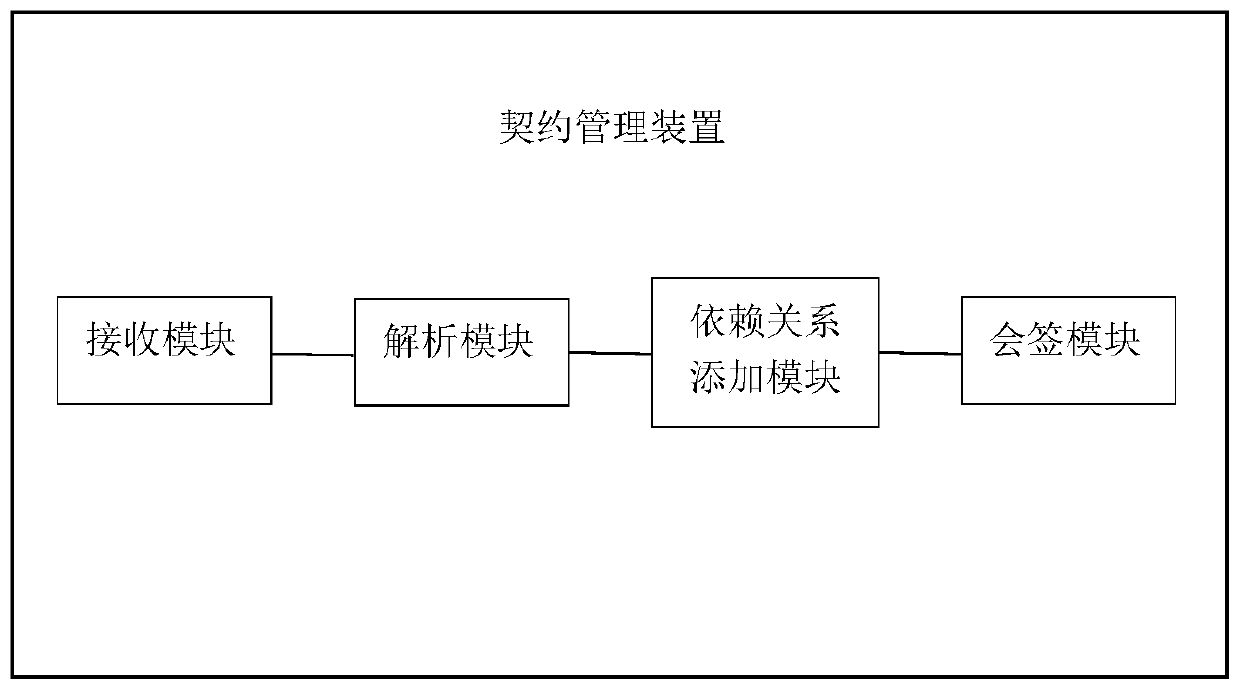
Distributed architecture-oriented micro-service contract management method and device, computer equipment and readable storage medium
PendingCN111176660AImprove management efficiencyImprove security detection efficiencyFinanceVersion controlData packDistributed structure
The invention discloses a distributed architecture-oriented micro-service contract management method and a device, computer equipment and a readable storage medium. The method comprises the steps of receiving a data packet from a code hosting platform; analyzing the received data packet, judging whether the data packet is a formal release version or a test version, and analyzing first contract information of the data packet through the data packet; directly publishing the data packet to a private server for the test version; traversing and querying all other contract information according to the analyzed first contract information of the formally published version of the data packet, obtaining a dependency relationship between the data packet and other packets, and adding the dependency relationship into the first contract information to form second contract information; and for the data packet of the formal version, sending the countersigning request to the associated parties according to the second contract information, and sending the data packet to the private server after receiving the information that all the associated parties agree to change.
Owner:CITIC AIBANK CORPORATION LIMITED
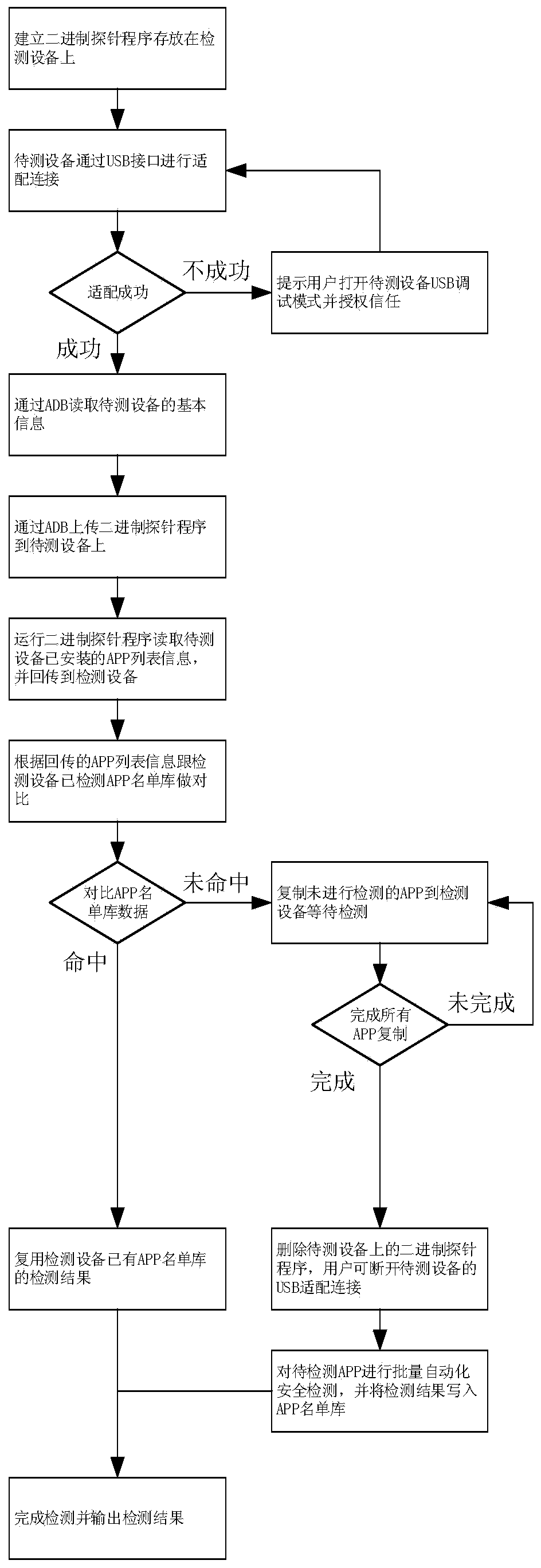
Method for detecting APP vulnerabilities of Android equipment based on probe mechanism
InactiveCN110826072AGuaranteed Accuracy and ReliabilityImprove efficiencyPlatform integrity maintainanceComputer securityTesting equipment
The invention provides a method for detecting APP vulnerabilities of Android equipment based on a probe mechanism, which comprises the following steps: step 1, acquiring list information of APPs installed in equipment to be detected based on a binary probe program installed in the equipment to be detected; and 2, comparing the returned APP list information with data of a detected APP list libraryof the detection equipment by the detection equipment to obtain a detection result. According to the method and the system, APP vulnerability security detection for testing the Android equipment terminal can be automatically completed, and the detection report is generated, so that a user can know the health condition of APP software installed in the Android equipment terminal, and potential security threats of the Android equipment terminal can be discovered in advance.
Owner:深圳市云钜天成信息技术有限公司
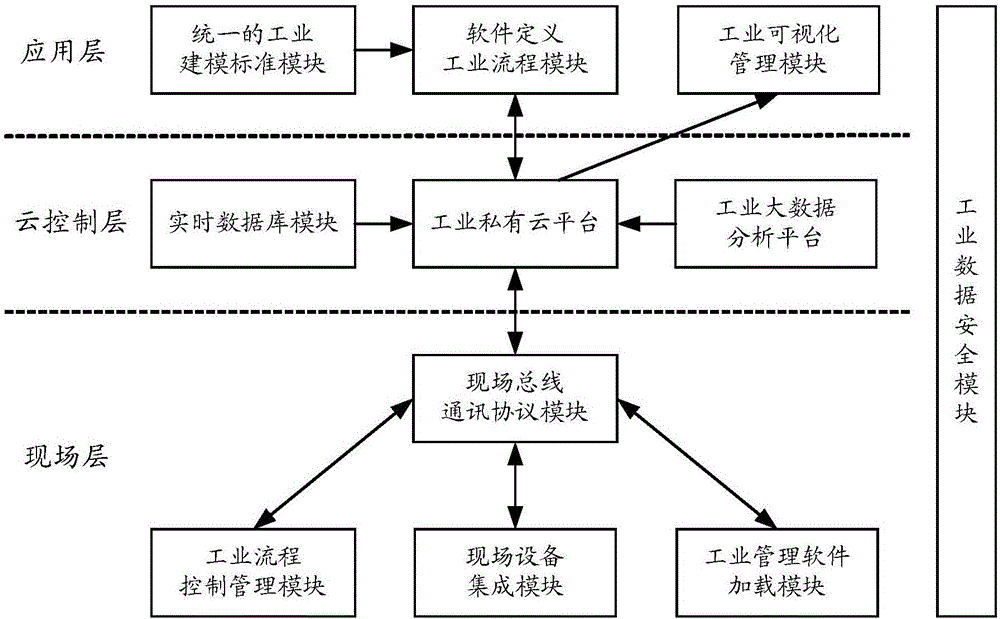
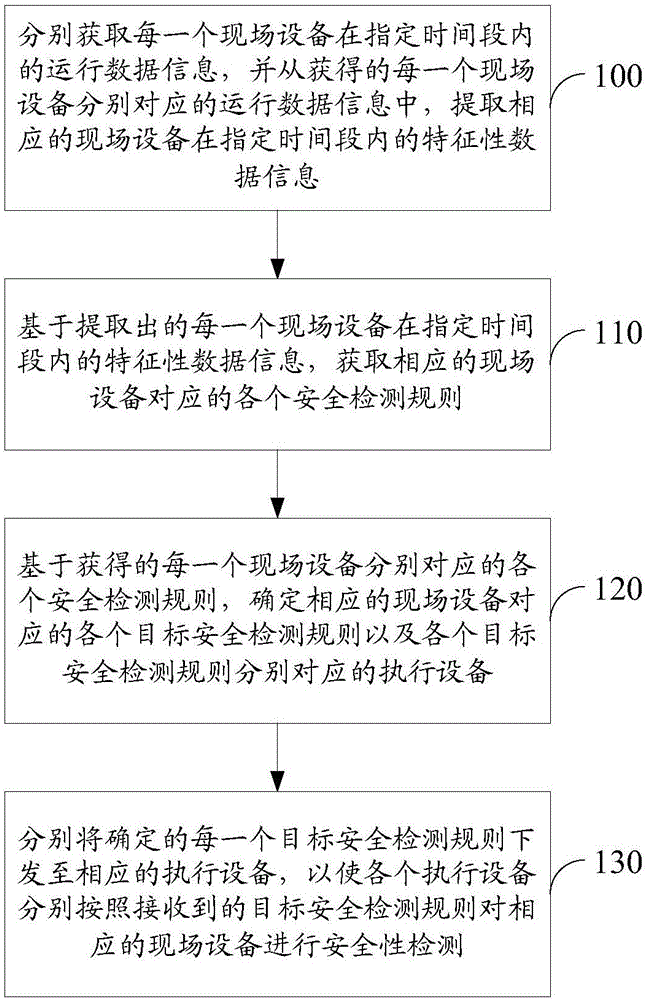
Safety detecting method and safety detecting device based on industrial Internet operation system
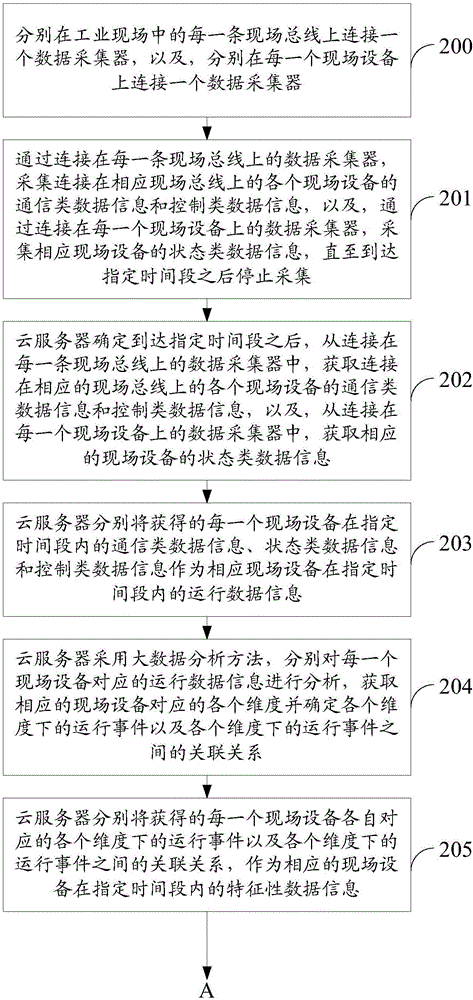
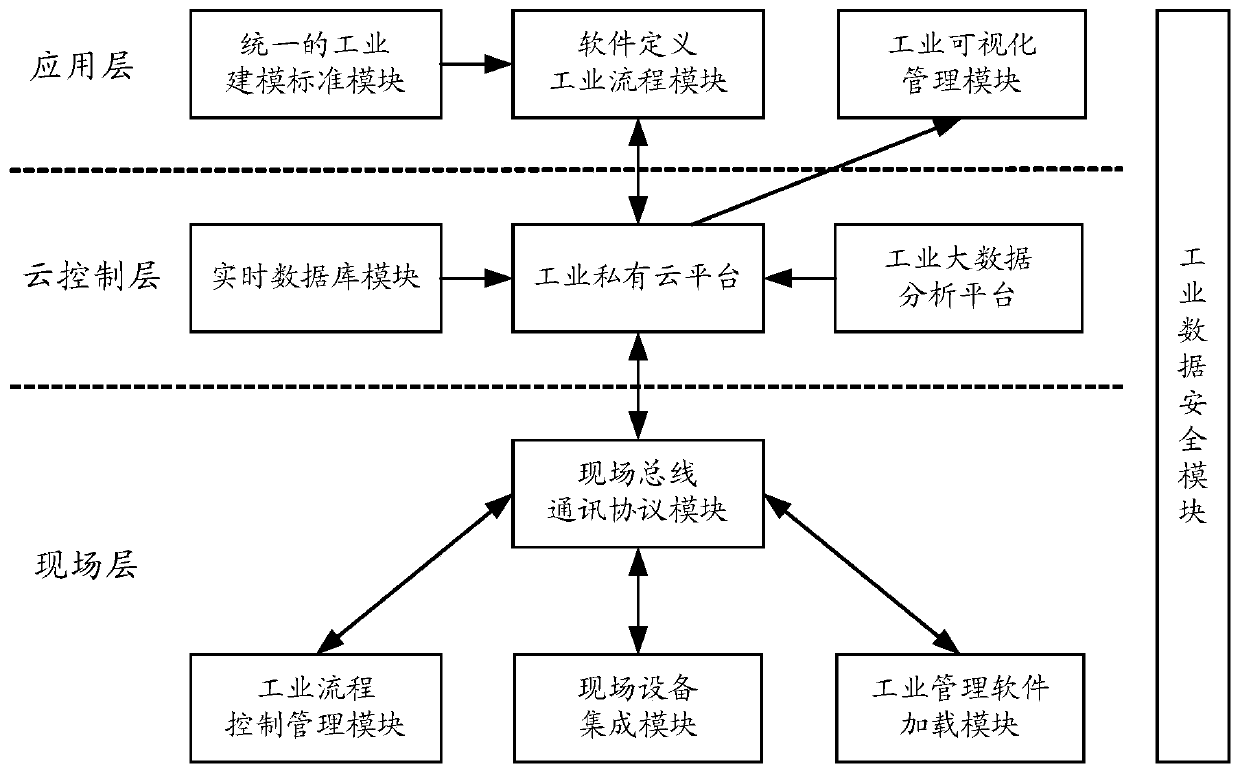
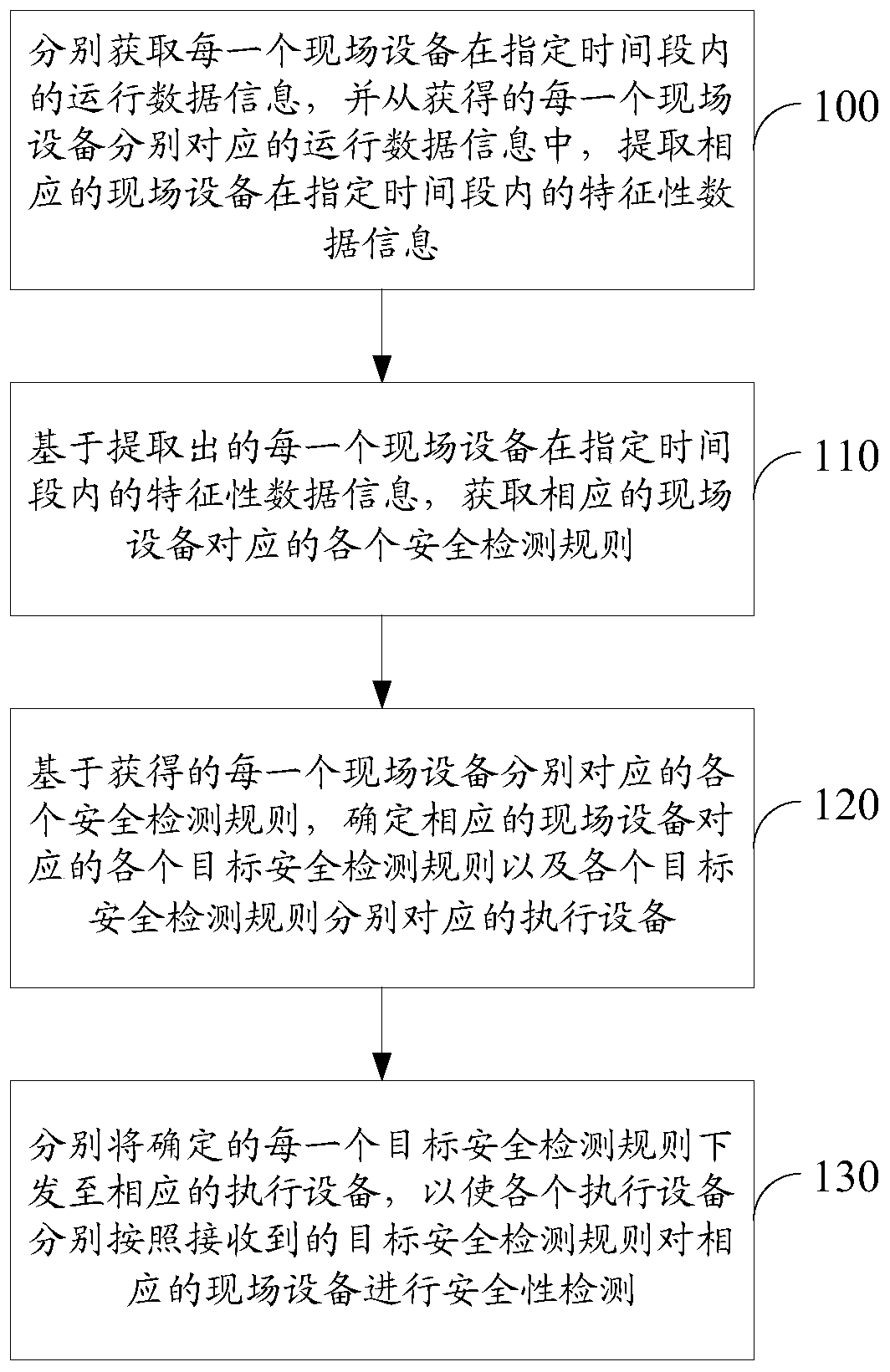
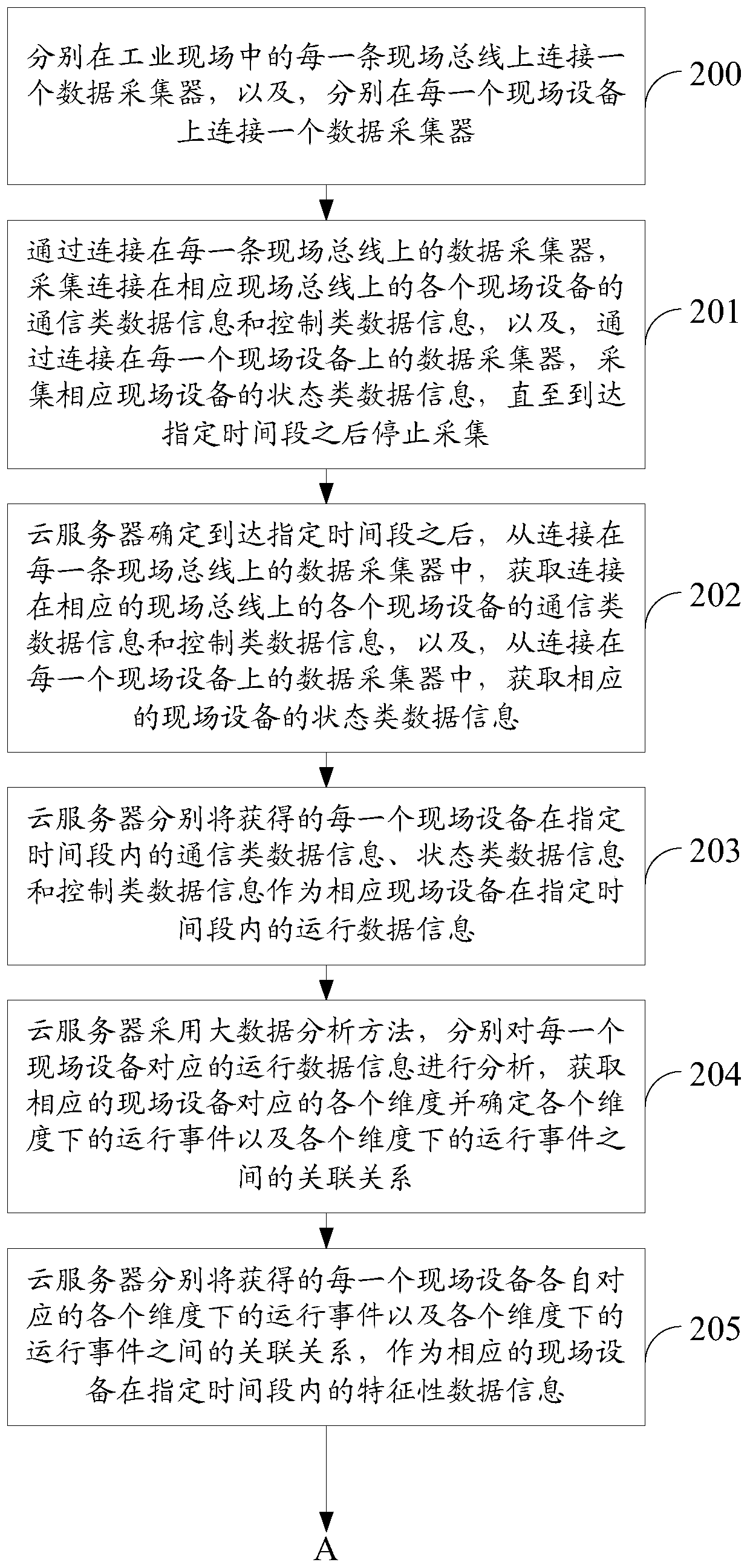
ActiveCN106685990ARealize all-round detectionAvoid the problem of poor regulatory flexibilityProgramme controlData processing applicationsOperational systemData information
The invention relates to the technical field of industrial Internet, and particularly to a safety detecting method and a safety detecting device based on an industrial Internet operation system. The method and the device are used for settling problems of relatively low industrial field safety and high field equipment controlling difficulty in prior art. The safety detecting method is advantageous in that based on various, heterogeneous and disperse operation data information which are acquired by a real-time database in the industrial field and a big data analysis mode of an industrial big data analysis platform, each safety detecting rule which corresponds with each set of field equipment is acquired; furthermore the safety detecting rule which corresponds with each set of field equipment is selected and forwarded to corresponding executing equipment, thereby realizing safety detection on each set of field equipment and ensuring controllability for safety of the industrial field. Based on a big data analysis manner, a full process which comprises industrial data acquisition, data analysis, data storage, data mining, data optimization and data safety is realized so that industrial field of each set of field equipment can operate in a reliable working environment.
Owner:KYLAND TECH CO LTD
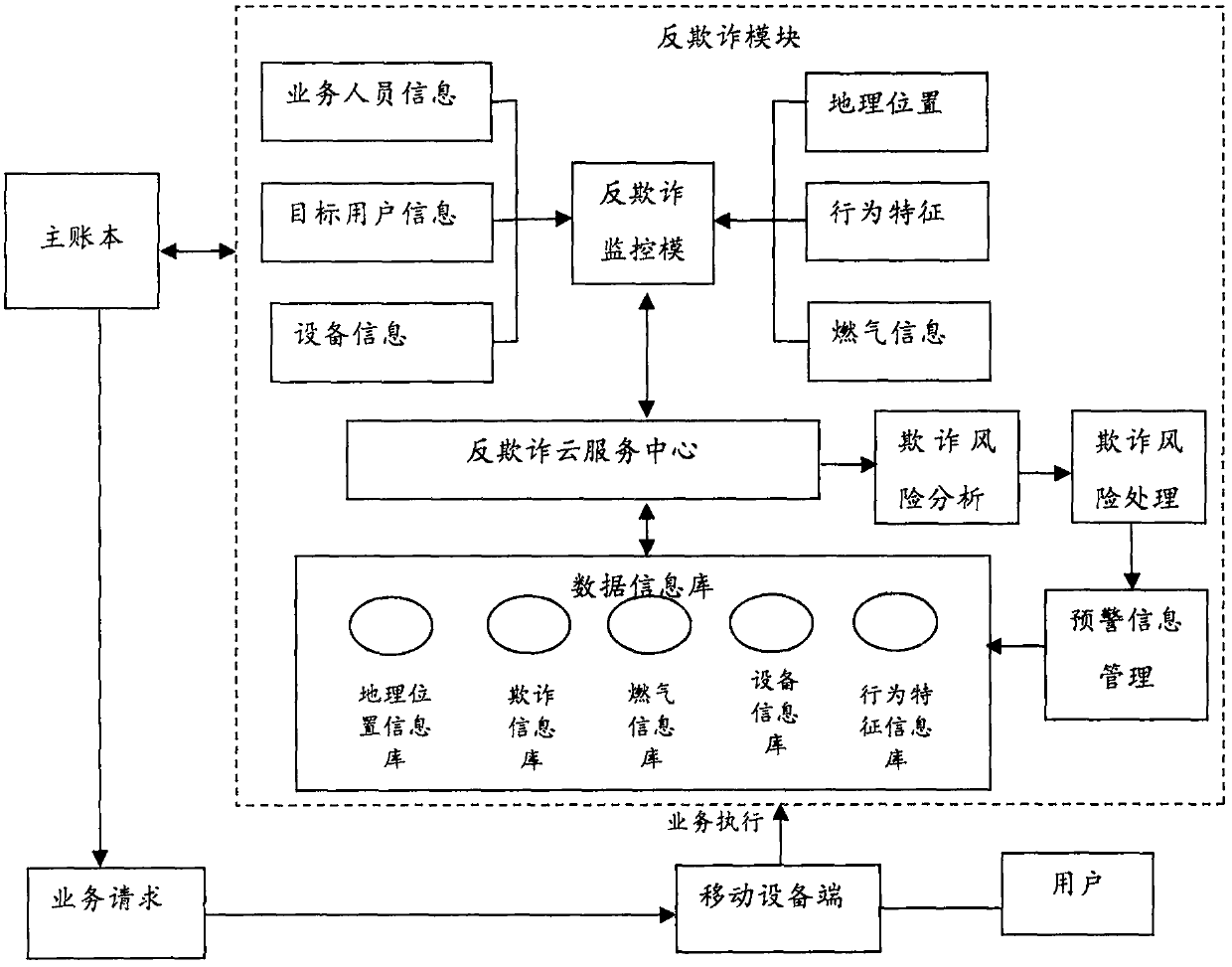
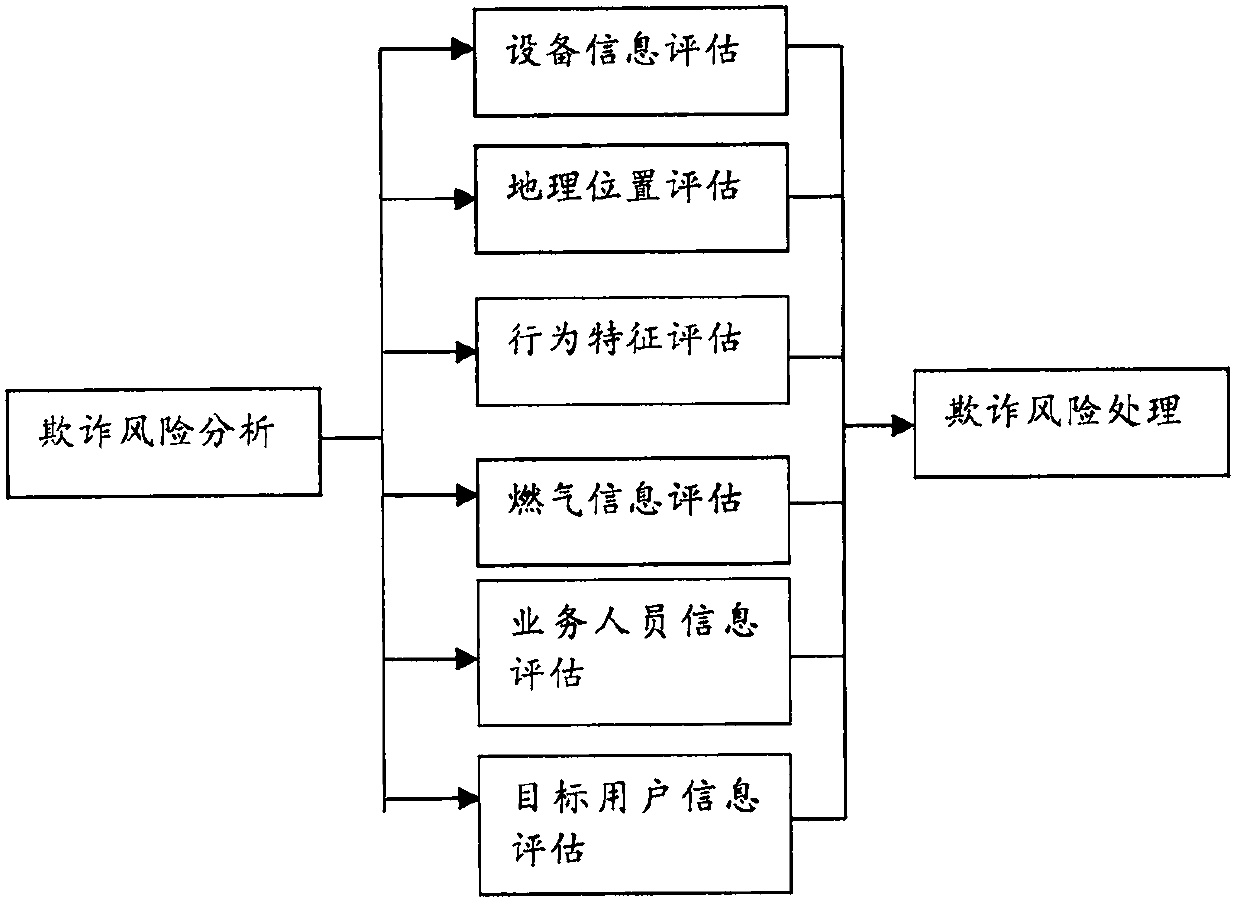
Anti-fraud system and method for account book based on Internet of Things (IoT)
The invention discloses an anti-fraud system for an account book based on the Internet of Things (IoT). The system comprises a main account book module, a mobile equipment terminal, a user terminal, and an anti-fraud module, wherein the main account book module is used for storing the latest updated business information, so that data support can be provided for business execution; the mobile equipment terminal is connected with the main account book module, and comprises a remote meter reading device which can send a business execution request to the main account book module, download a meterreading request from the main account book module and execute meter reading; the user terminal comprises a gas meter with a signal transceiving module, and the signal transceiving module can receive arequest signal transmitted by the remote meter reading device and send gas consumption conditions of a user to the remote meter reading device; and the anti-fraud module is connected with the mobileequipment terminal and the main account book module, and carries out anti-fraud processing according to the business execution request of the mobile equipment terminal, so that monitoring and anti-fraud analysis can be carried out on a business execution process. The anti-fraud system for the account book provided by the invention has the advantages that the meter reading by the mobile equipment terminal can be achieved, and anti-fraud evaluation on gas information can be carried out, so that high completeness and safety of the account book are guaranteed.
Owner:北京泛融科技有限公司
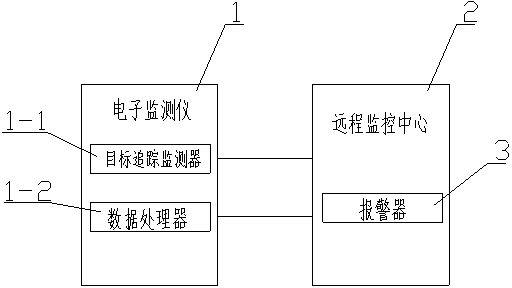
Cloud computing-based food safety testing system
InactiveCN104076129AReduce workloadImprove security detection efficiencyTesting foodFood safetyData treatment
The invention relates to the technical field of a testing system, and in particular relates to a cloud computing-based food safety testing system which comprises an electronic monitor and a remote monitoring center, wherein the electronic monitor comprises a target tracking monitor and a data processor; signals monitored by the target tracking monitor and the data processor are sent into the remote monitoring center. The cloud computing-based food safety testing system is capable of monitoring the food safety from a long distance.
Owner:刘瑞
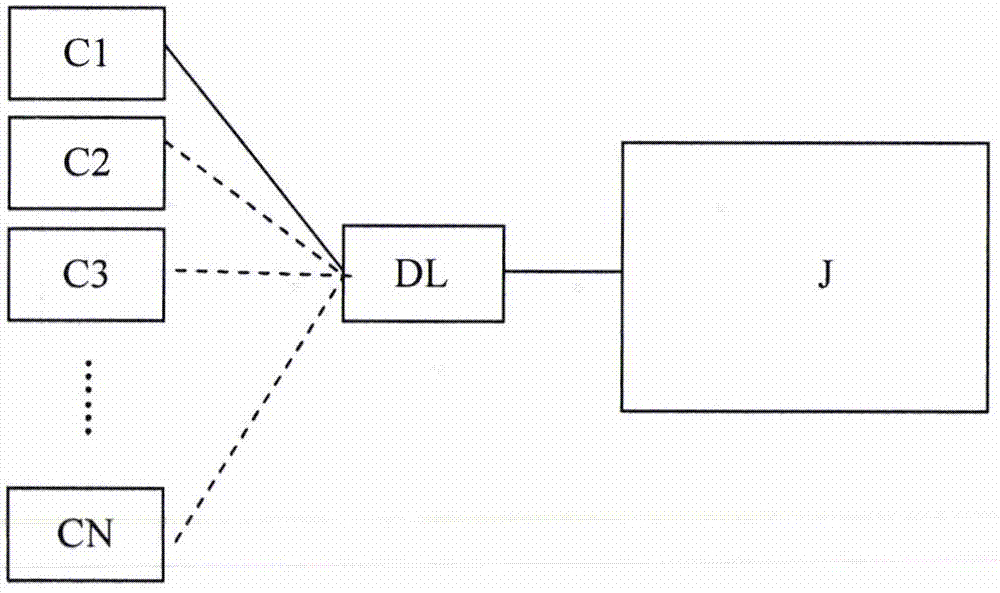
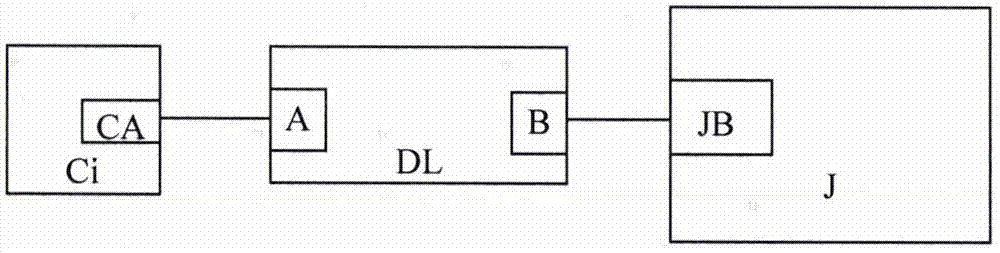
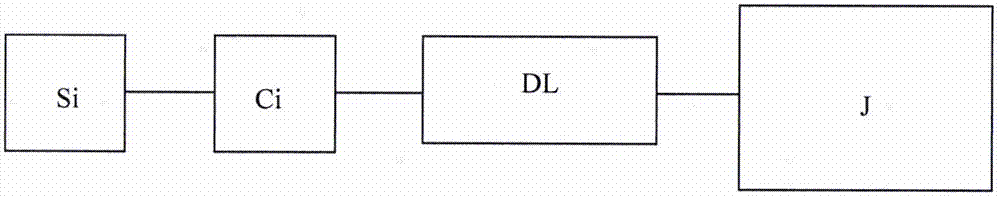
Technological safety testing system for power distribution socket
InactiveCN106872810AImprove security detection efficiencySolve the matching and docking problemElectrical testingSafety testingTest object
The invention provides technological safety testing device which is composed of a plurality of specialized adaption plugs C1, C2, ..., CN, a double-end adaption cable DL and specialized technological safety detecting equipment J. The technological safety testing device has advantages of settling a problem of matching connection between a tested object and testing equipment, improving speed and safety in a testing operation, furthermore preventing a problem of tedious technological safety testing process in carrying and using a plurality of sets of testing equipment, and further improving technological safety testing efficiency of the power distribution socket.
Owner:中国人民解放军91550部队第210所
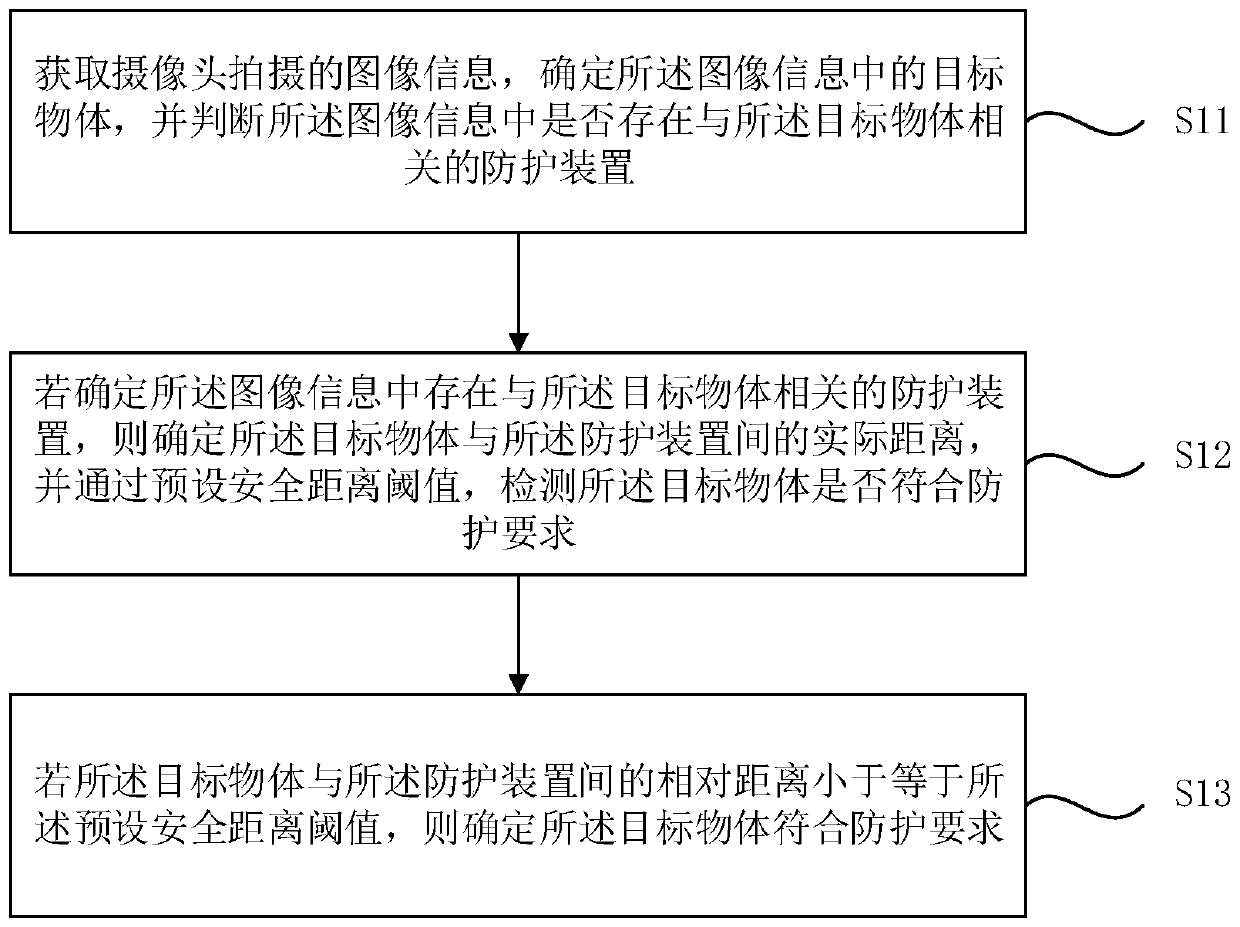
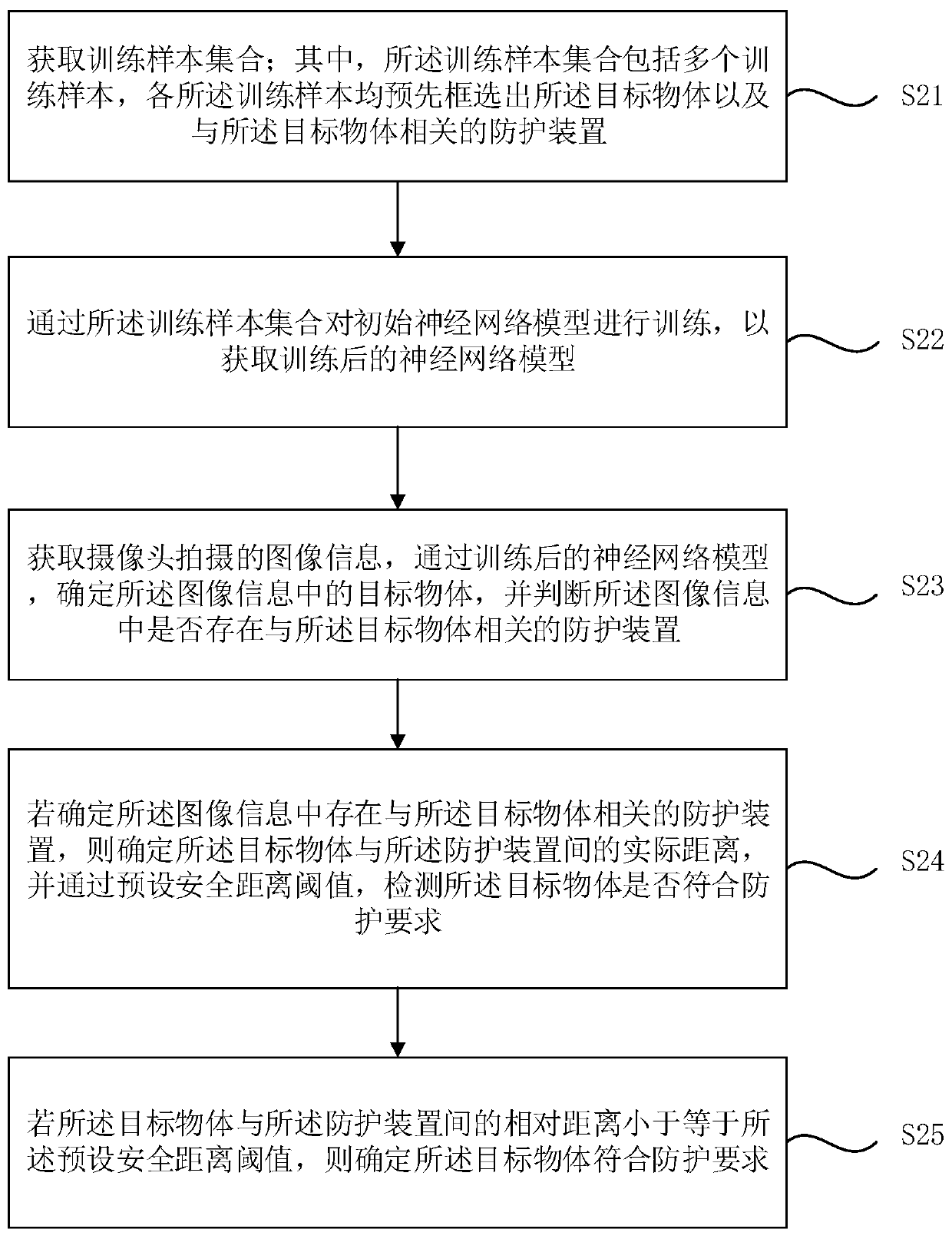
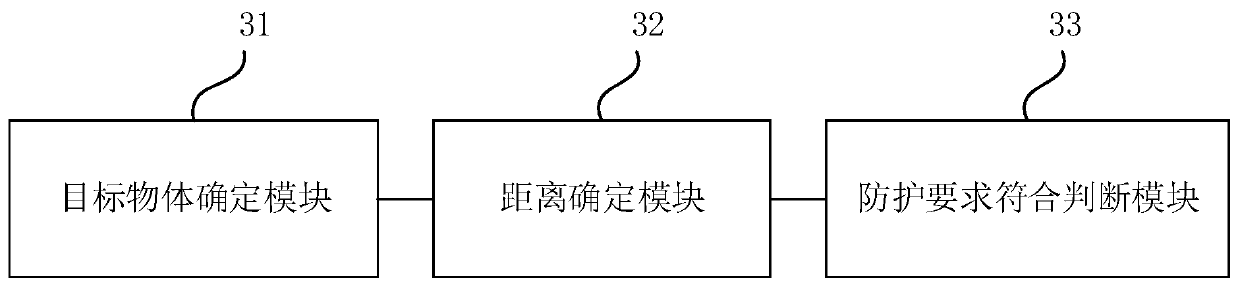
Target object protection detection method and device, equipment and storage medium
PendingCN111091104ASave labor cost and time costImprove security detection efficiencyCharacter and pattern recognitionPetrol stationReal-time computing
The embodiment of the invention discloses a protection detection method and device for a target object, equipment and a storage medium. The method comprises the steps that image information shot by acamera is acquired, a target object in the image information is determined, and whether a protection device related to the target object exists in the image information or not is judged; if it is determined that the protection device related to the target object exists in the image information, the actual distance between the target object and the protection device is determined, and whether the target object meets the protection requirement or not is detected through a preset safe distance threshold value; If the relative distance between the target object and the protection device is smallerthan or equal to the preset safety distance threshold, determining that the target object meets the protection requirement. According to the technical scheme provided by the embodiment of the invention, the automatic safety protection detection of the oiling machine is realized, the labor cost and the time cost are reduced, the safety detection efficiency of a gas station is improved, and the detection error rate is reduced.
Owner:HEBEI UNIV OF TECH
Method for detecting systemic pesticide dimethoate residue
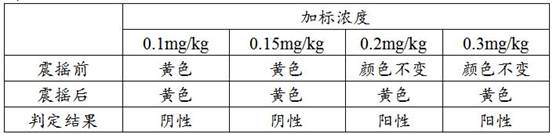
ActiveCN113884486AImprove detection sensitivityObvious phenomenonMaterial analysis by observing effect on chemical indicatorPreparing sample for investigationEnvironmental chemistryEther
The invention discloses a method for detecting systemic pesticide dimethoate residue. The method comprises the following steps: step a, crushing a sample to be detected to obtain a first sample; step b, adding a sodium salt solution and chloroform into the first sample, performing centrifugal treatment until the solution is obviously layered, and taking a chloroform phase solution to obtain a first sample solution; step c, blow-drying the first sample liquid to obtain a first substance to be detected; step d, adding diethylamine into the first substance to be detected, redissolving, adding an oxidizing agent, adjusting the temperature to 80 DEG C, standing to obtain a second sample solution, and blow-drying to obtain a second substance to be detected; step e, adding an ether organic solvent into the second substance to be detected, redissolving, slowly adding a buffer solution, adding an acetylcholin esterase reagent, and standing; step f, adding a substrate and a color developing agent, standing for 3 minutes, observing the color change of a lower layer after the solution is layered, shaking, standing, and observing the color change of the lower layer after the solution is layered; and step g, judging a result.
Owner:广东江门中医药职业学院
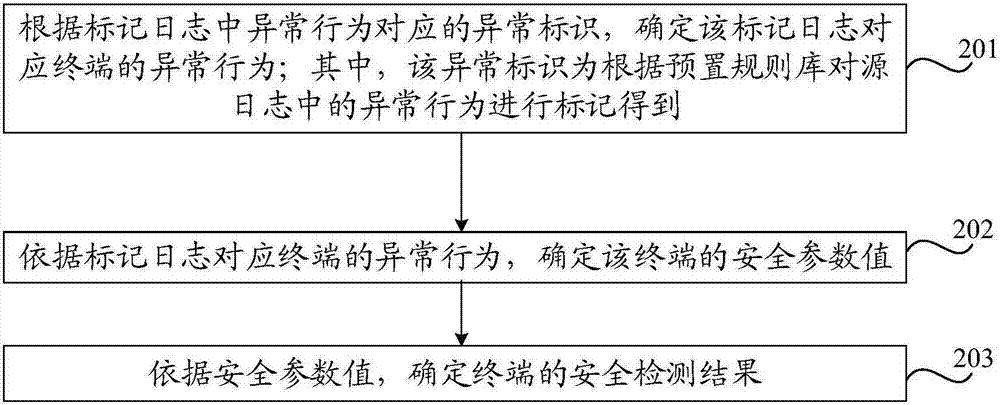
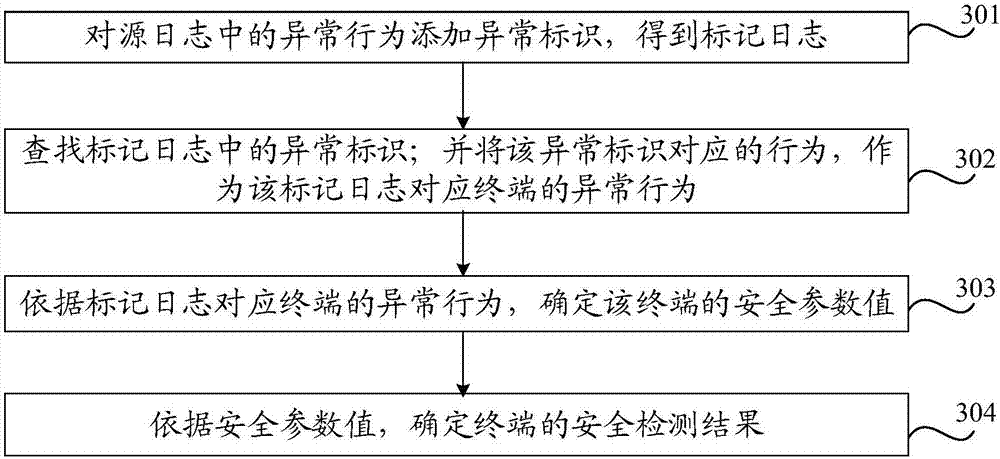
Security detection method and device
InactiveCN107124419AImprove security detection efficiencyReduce operating costsTransmissionInternet privacySecurity parameter
The embodiment of the invention provides a security detection method and device. The method specifically comprises the steps of determining abnormal behaviors of terminals corresponding to marked logs according to abnormal identifiers corresponding to the abnormal behaviors in the marked logs; determining security parameter values of the terminals according to the abnormal behaviors of the terminals corresponding to the marked logs; and determining security detection results of the terminals according to the security parameter values. According to the embodiment of the invention, the operation costs for artificially analyzing the logs can be reduced, the terminal security detection efficiency can be improved, and the terminal security detection flexibility and application range can be improved.
Owner:BEIJING QIANXIN TECH
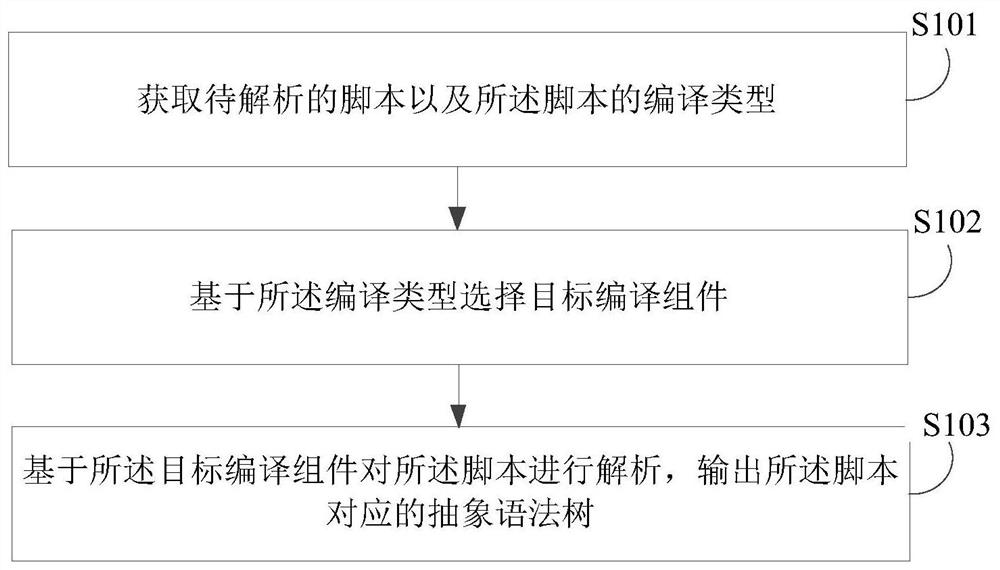
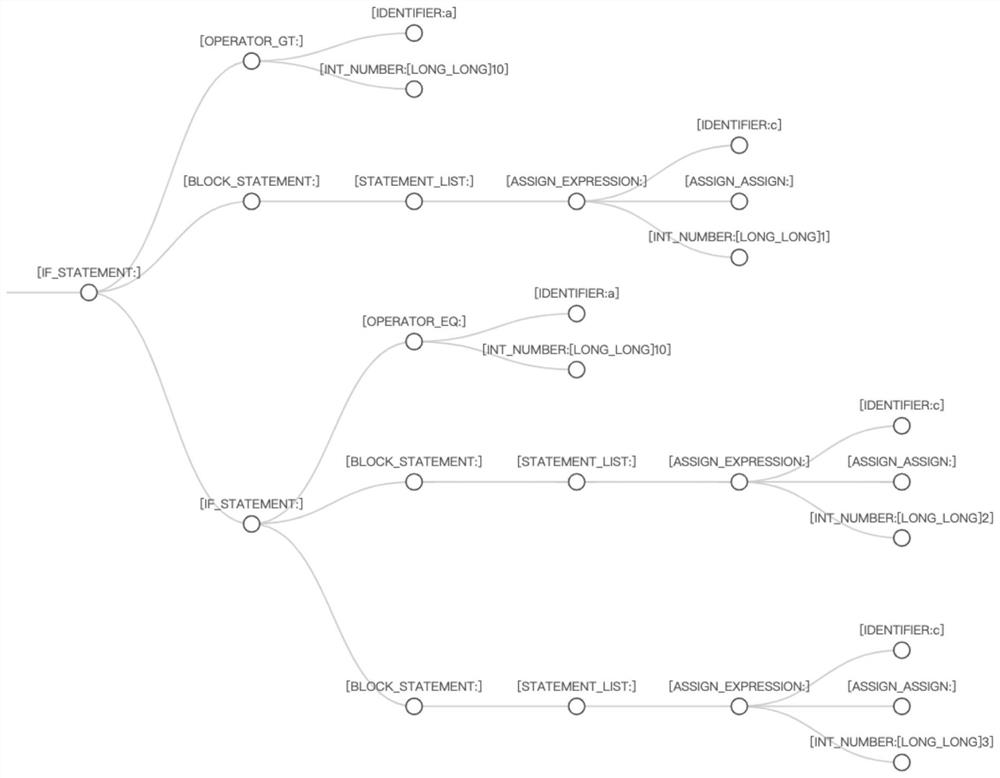
Analyzing method of abstract syntax tree and computer program product
PendingCN114443041AImprove efficiencyImprove accuracyCode compilationTheoretical computer scienceSoftware engineering
Embodiments of the invention disclose an abstract syntax tree analysis method and a computer program product. The method comprises the steps of obtaining a script to be analyzed and a compiling type of the script; selecting a target compiling component based on the compiling type; analyzing the script based on the target compiling component, and outputting an abstract syntax tree corresponding to the script; wherein the structure types of the abstract syntax trees output by the target compiling components corresponding to different compiling types are the same. According to the technical scheme, scripts written by various languages can be normalized into abstract syntax trees of the same type, and the adaptation efficiency and accuracy of the scripts can be improved.
Owner:ALIBABA CLOUD COMPUTING LTD
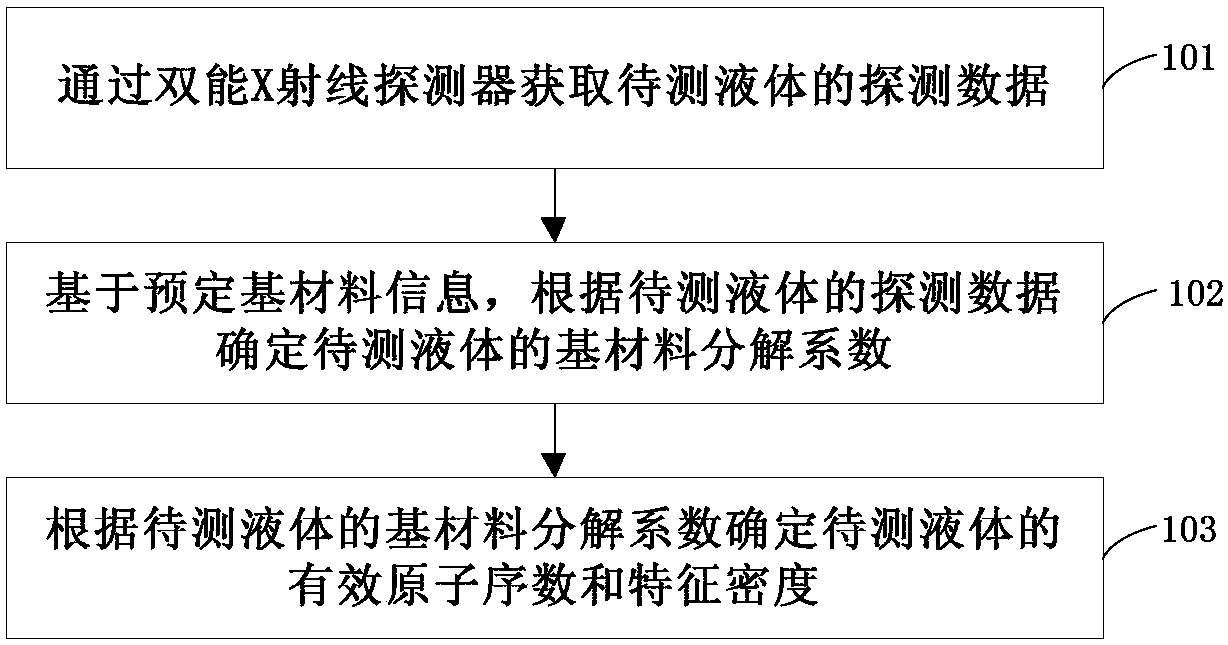
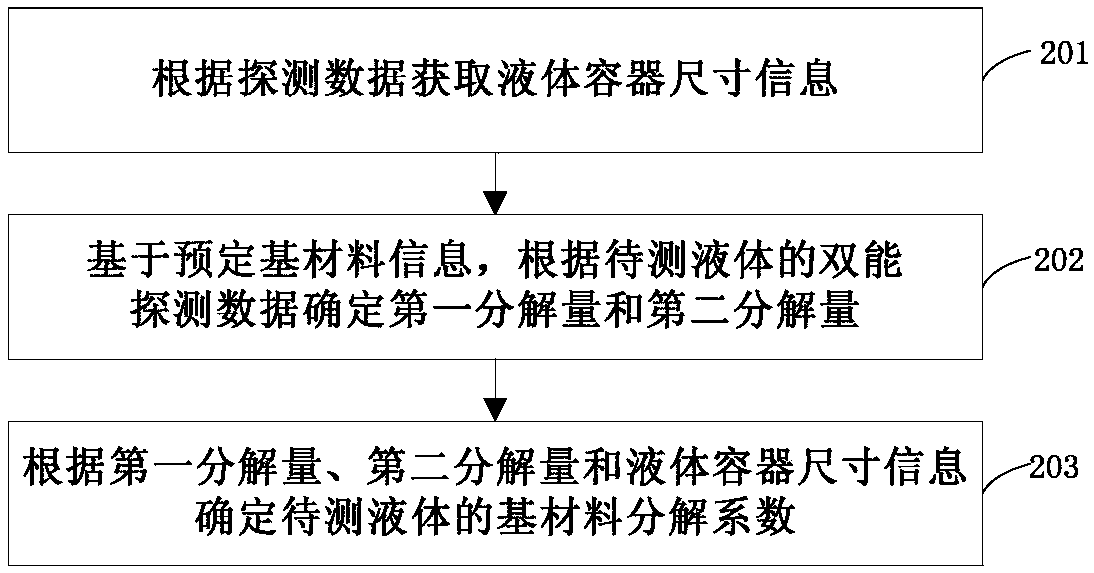
Liquid detecting method and device and security inspection equipment
ActiveCN108267464ARealize identificationImprove security detection efficiencyMaterial weighingMaterial analysis by transmitting radiationDual energyComputer science
The invention provides a liquid detecting method and device and security inspection equipment, and relates to the field of security inspection. The liquid detecting method comprises the following steps: acquiring detecting data of liquid to be detected through a dual-energy X-ray detector; determining a base material decomposition coefficient of the liquid to be detected according to the detectingdata of the liquid to be detected on the basis of preset base material information; and determining an effective atomic number and feature density of the liquid to be detected according to the base material decomposition coefficient of the liquid to be detected. By the method, the base material decomposition coefficient of the liquid to be detected can be obtained by ray detecting data acquired by the dual-energy detector on the basis of the preset base material information, the effective atomic number and feature density of the liquid to be detected according to the base material decomposition coefficient, and thus, the liquid is recognized. Because the dual-energy X-ray detector is high in efficiency and large in detecting range, recognition of liquid in a plurality of containers can berealized simultaneously, the detecting time is shortened, and efficiency of safe detection of liquid is improved.
Owner:CINTS CO LTD
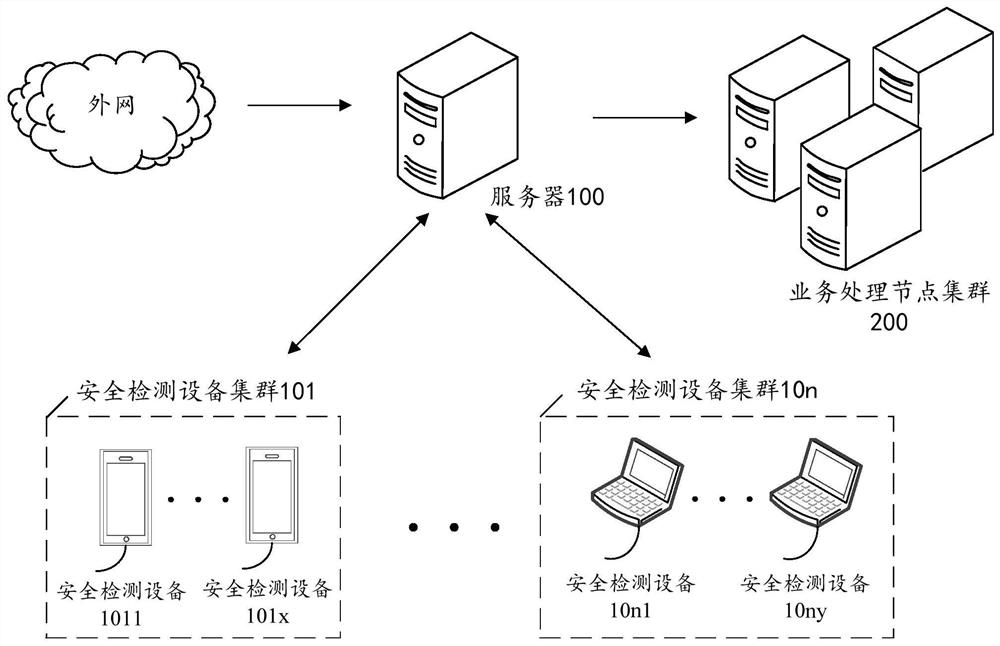
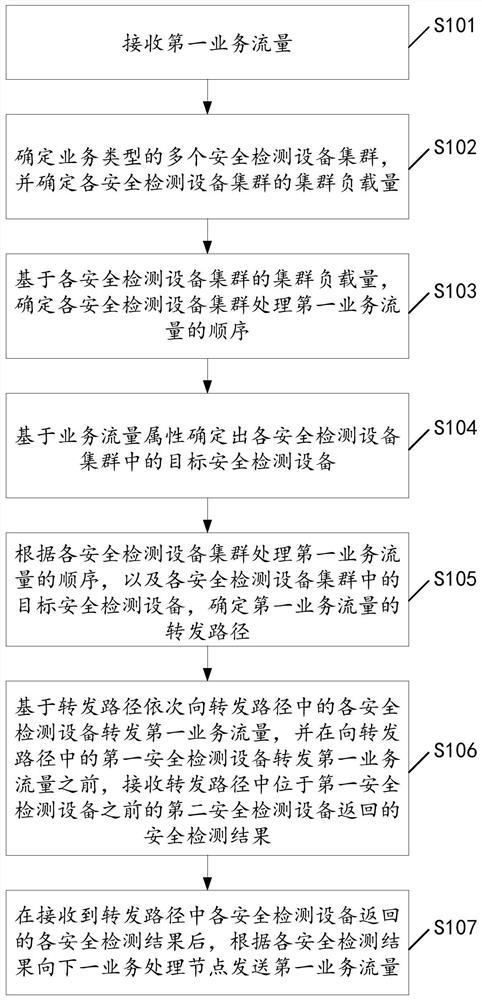
Service flow detection method and device, server and storage medium
ActiveCN113452691AImprove security detection efficiencyData switching networksService flowEngineering
The invention discloses a service flow detection method and device, a server and a storage medium, and the method comprises the steps: determining a plurality of safety detection equipment clusters of a service type based on the service type carried by a first service flow, and carrying out the detection of the service flow based on the cluster load of each safety detection equipment cluster, determining a sequence of processing the first service traffic by each security detection device cluster, determining a target security detection device in each security detection device cluster based on the service traffic attribute, further determining a forwarding path of the first service traffic, and forwarding the first service traffic to each security detection device in the forwarding path in sequence based on the forwarding path, and after security detection results returned by the security detection devices are received, sending the first service flow to the service processing node. By adopting the method and the device, the security detection equipment through which the service flow needs to pass can be flexibly selected, so that the security detection efficiency of the service flow is improved.
Owner:WEIKUN (SHANGHAI) TECH SERVICE CO LTD
Nanometer immune-magnetic bead, and preparation method thereof and kit thereof
ActiveCN104096548ASimple preparation processGood repeatabilityMaterial nanotechnologyOther chemical processesMagnetic beadFood safety
The invention discloses a nanometer immune-magnetic bead, and preparation method and a kit thereof. The method comprises the following steps: 1, injecting an iron source and stabilizer mixed liquid into an alkaline solution in an inert atmosphere to obtain magnetic nano-particles, wherein a volume ratio of the alkaline solution to the mixed liquid is 1:(8-10), and a molar ratio of the iron source to the stabilizer to an alkaline substance in the alkaline solution is 1:(5-10):(10-14); and 2, modifying the surfaces of the magnetic nano-particles surface with an antibody having specific immune activity. The preparation method of the nanometer immune-magnetic bead has a simple preparation process and good repeatability. The kit constructed on the basis of the nanometer immune-magnetic bead has the characteristics of good dispersion stability in a target detection liquid, fast magnetic response, strong specificity, high sensitivity and high target capture rate, and has a certain promotion effect on the improvement of the food safety detection efficiency.
Owner:THE NAT CENT FOR NANOSCI & TECH NCNST OF CHINA
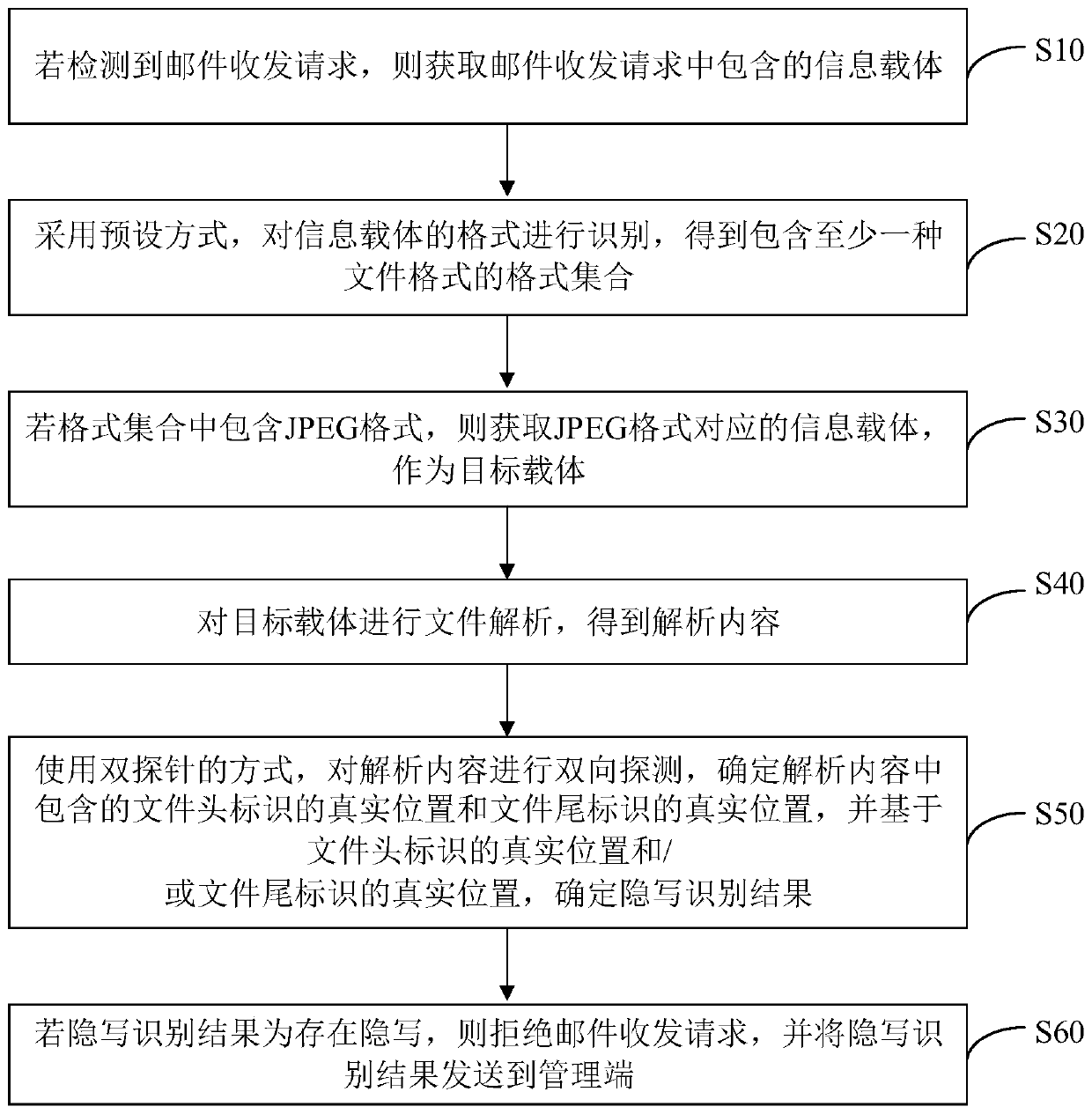
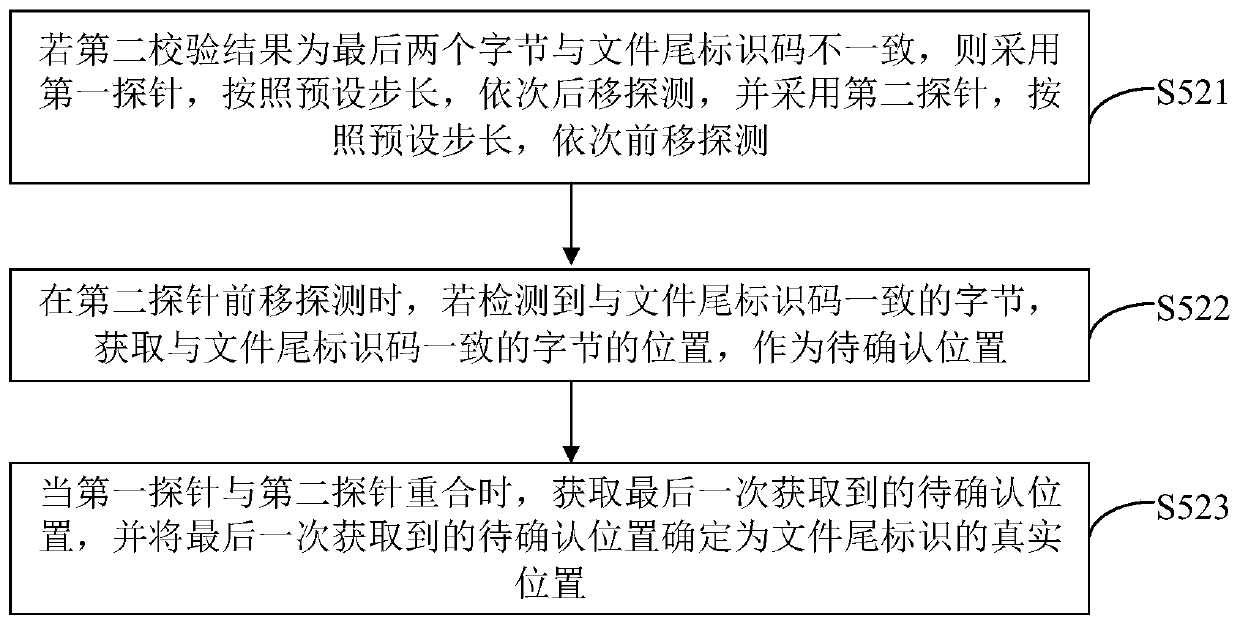
Mail security check method and device, computer equipment and storage medium
ActiveCN111049724AImprove security detection efficiencyStrong targetingData switching networksComputer networkJPEG
The invention discloses a mail security check method and device, computer equipment and a storage medium. The method comprises the following steps of: when a mail receiving and sending request is detected, obtaining an information carrier contained in the mail receiving and sending request, identifying the format of the information carrier; if a JPEG format exists, acquiring an information carriercorresponding to the JPEG format as a target carrier, and analyzing the target carrier to obtain parsed content; through a dual-probe mode, carrying out bidirectional detection on the parsed contentto determine real positions of a file header identifier and a file tail identifier contained in the parsed content; based on the real positions, determining steganography recognition results; and whenthe steganography recognition result shows that steganography exists, refusing the mail receiving and sending request, and sending the steganography recognition result to the management end. Whethersteganography exists or not is judged by obtaining the real positions of the file header identifier and / or the file tail identifier, so that pertinence is high, rapid steganography recognition is achieved, and the safety detection efficiency in the mail receiving and sending process is improved.
Owner:CHINA PING AN PROPERTY INSURANCE CO LTD
Ion exchange membrane fluid food quality detection method
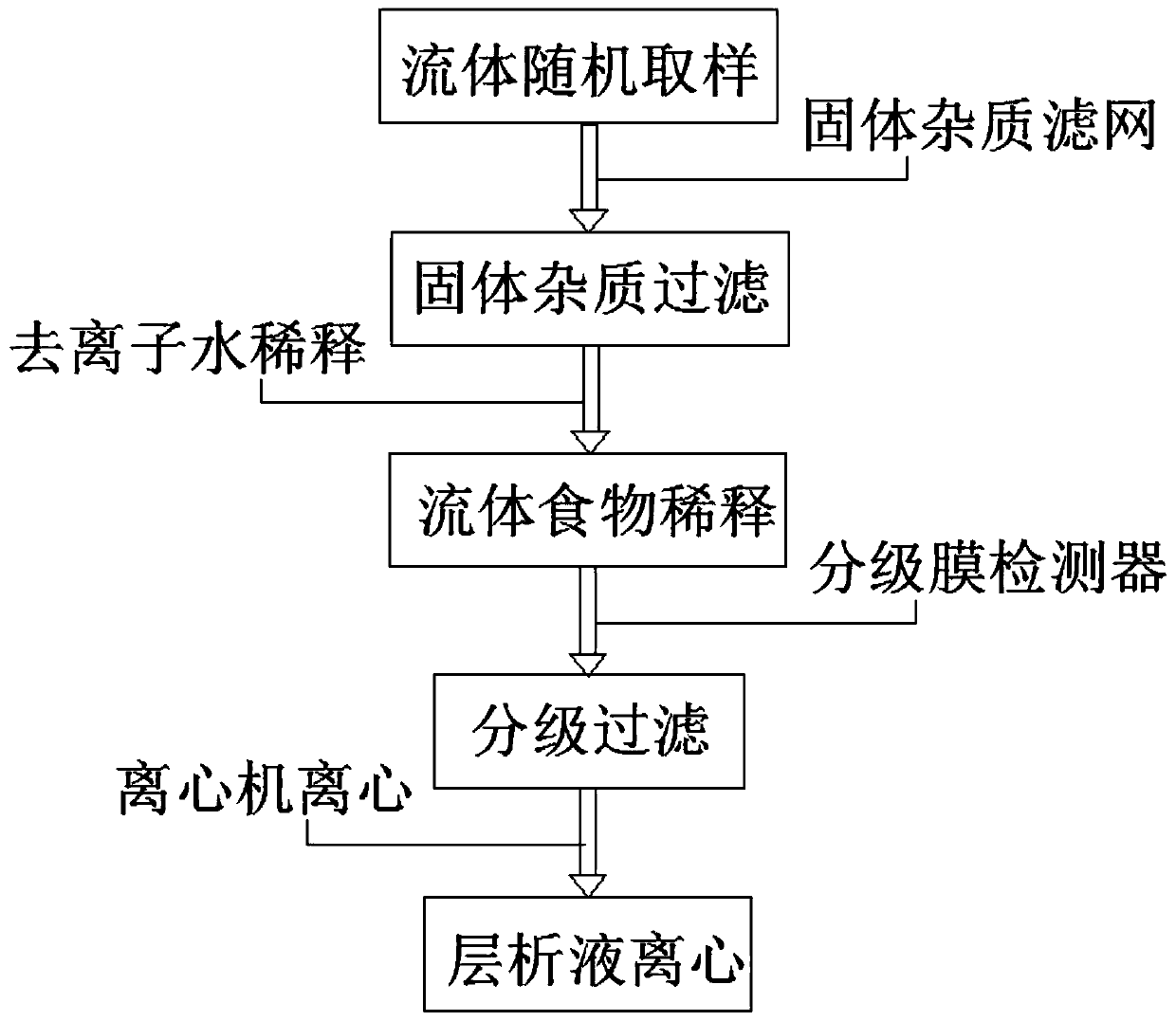
InactiveCN109856263AQuick checkImprove security detection efficiencyComponent separationPreparing sample for investigationFood safetyFiltration
The invention discloses an ion exchange membrane fluid food quality detection method and belongs to the field of food quality detection technologies. The ion exchange membrane fluid food quality detection method includes the following steps of: fluid random sampling; solid impurity filtration; fluid food dilution; classified filtration; and chromatographic solution centrifugation: diluted fluid food which has been subjected to chromatography is centrifugated through a centrifuge, sectioned sampling is performed, a supernatant is taken so as to be subjected to component analysis and detection;and therefore, the rapid detection of fluid food can be realized, the complex process of the detection process of the fluid food can be simplified, the detection efficiency of food safety can be improved, a variety of heavy metals and harmful elements that threaten food safety can be detected in a detection process, some metal ions can be filtered out, and the impact of mutual interference betweenmetal ions on food safety detection can be decreased.
Owner:商文辉
Smart contract security detection method and system, equipment, terminal and application
PendingCN113626826AReduce cumbersomeImprove efficiencyDatabase distribution/replicationPlatform integrity maintainanceGraph modelGraph Node
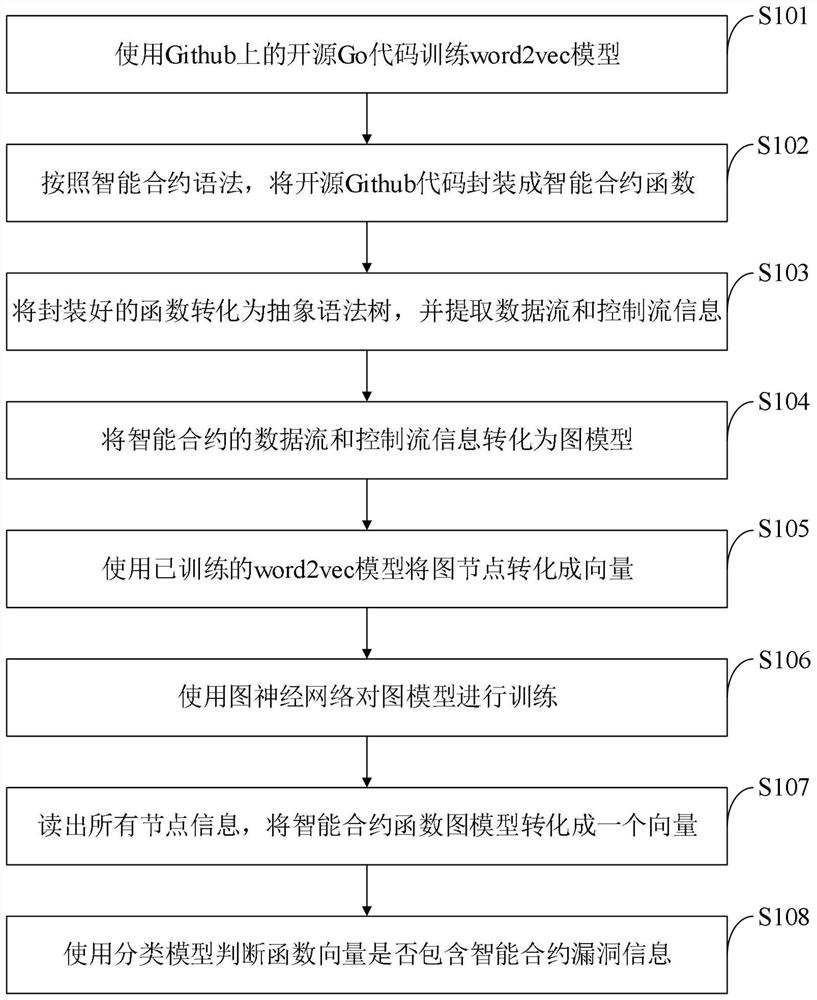
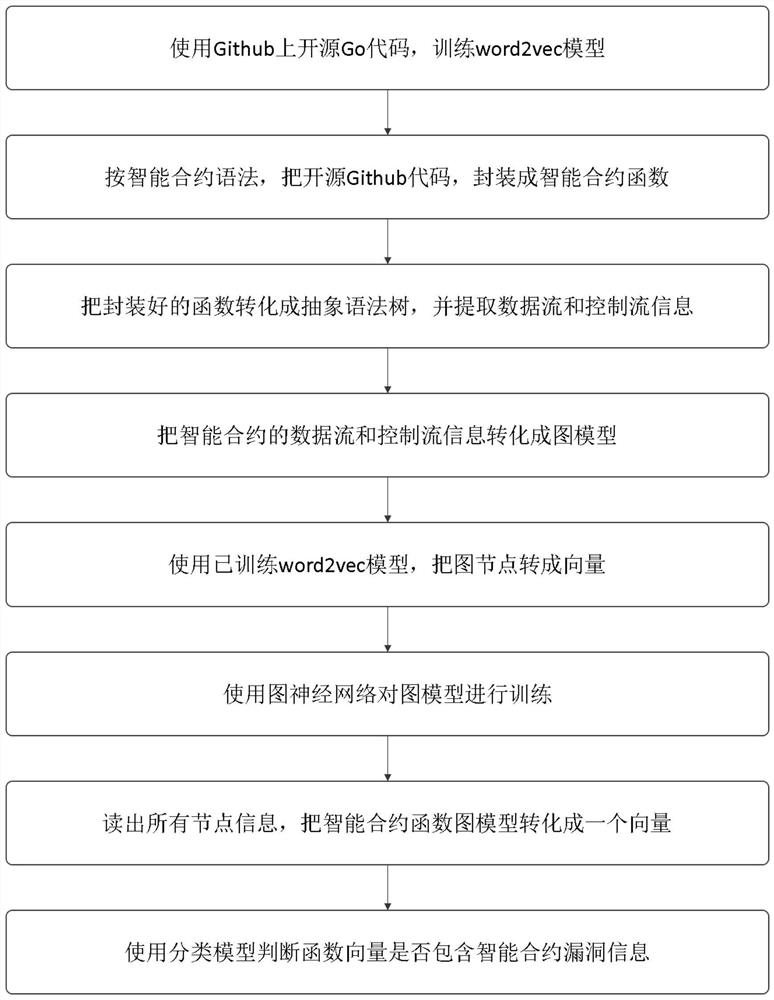
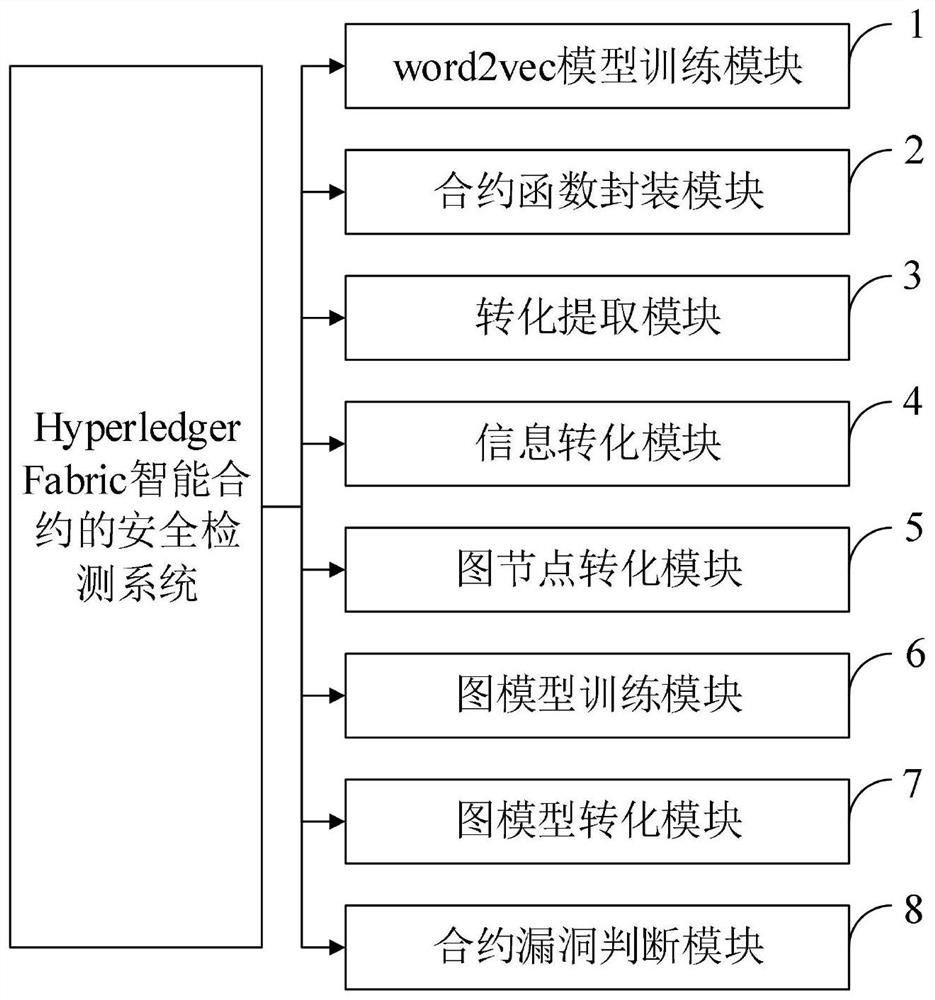
The invention belongs to the technical field of block chain security, and discloses a smart contract security detection method and system, equipment, a terminal and application, the smart contract security detection method comprises the following steps: using an open source code to train a word2vec model; packaging the open source code into an intelligent contract function according to an intelligent contract grammar; converting the packaged function into an abstract syntax tree, and extracting data flow and control flow information; converting data flow and control flow information of the smart contract into a graph model; using a trained word2vec model to convert the graph nodes into vectors; training the graph model by using a graph neural network; reading all node information, and converting the intelligent contract function graph model into vectors; and judging whether the function vector contains the intelligent contract vulnerability information or not by using the classification model. According to the invention, the security detection efficiency of the smart contract is improved, and a good effect is achieved.
Owner:XIDIAN UNIV
High-flux multi-card food safety detection equipment sample injection device
PendingCN112684124AImprove efficiencyReduce instrument investmentTesting foodElectric machineryComputer hardware
The invention discloses a high-flux multi-card food safety detection equipment sample injection device which comprises a sample injection turntable and a sample injection tray in sliding fit with a host; the sample injection turntable is rotatably connected with the sample injection tray through a rotating shaft; a stepping motor capable of driving the sample injection turntable to rotate is arranged on the sample injection tray; a plurality of alignment grooves are formed in the top surface of the sample injection turntable; alignment bulges in one-to-one correspondence with the alignment grooves are arranged on the bottom surface of the sample injection turntable, and and the alignment bulges can be clamped with the corresponding alignment grooves; a photoelectric controller is further arranged on the sample injection tray, a light blocking plate is fixedly arranged on the bottom surface of the sample injection turntable, and the light blocking plate can block the photoelectric controller when the sample injection turntable rotates; and the photoelectric controller and the stepping motor are electrically connected with a program control module respectively. The high-flux multi-card food safety detection equipment sample injection device has the advantage that the food safety detection efficiency is improved.
Owner:LIUJIAOTI TECH TIANJIN
Food-borne pathogenic bacterium classification method
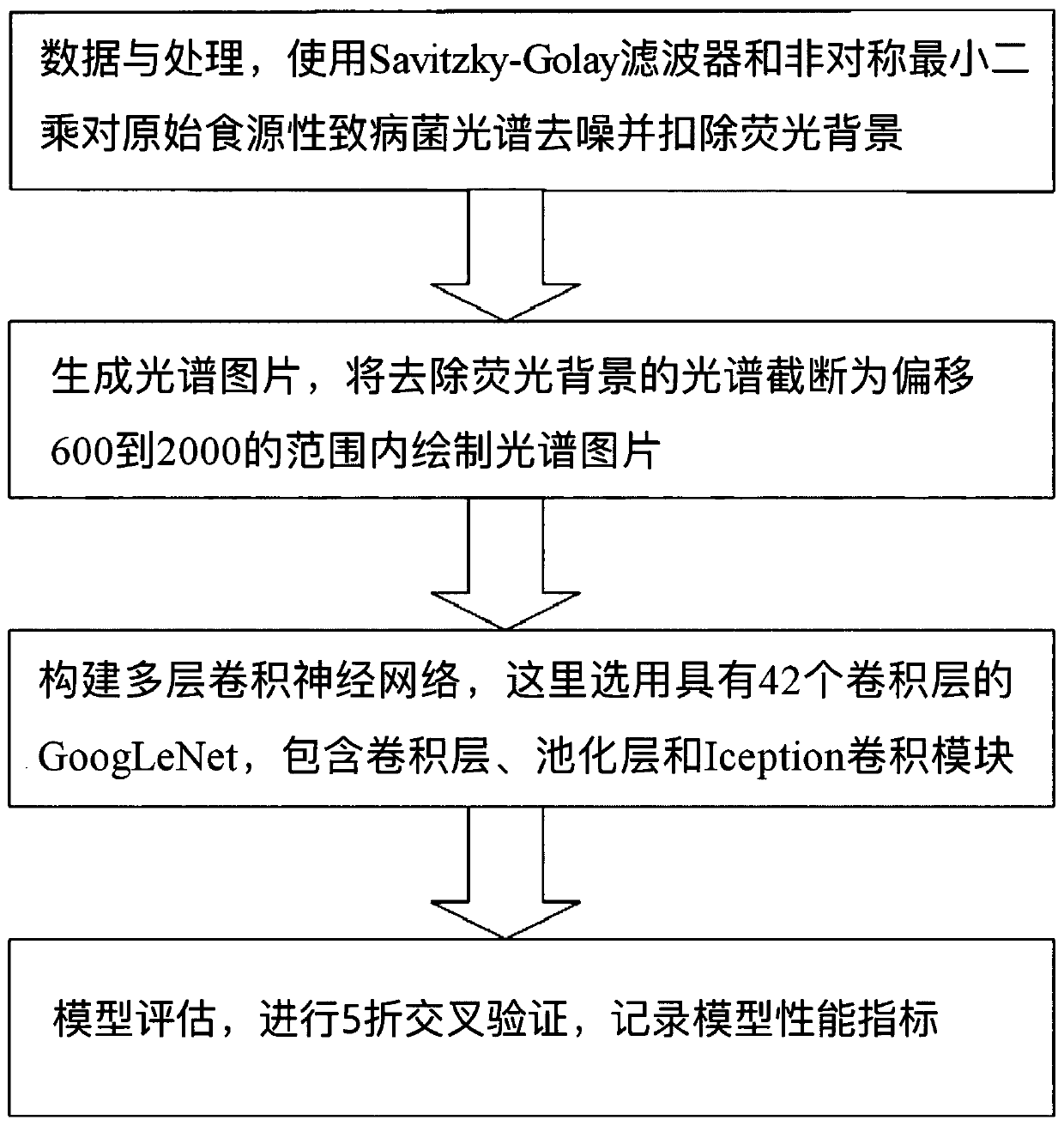
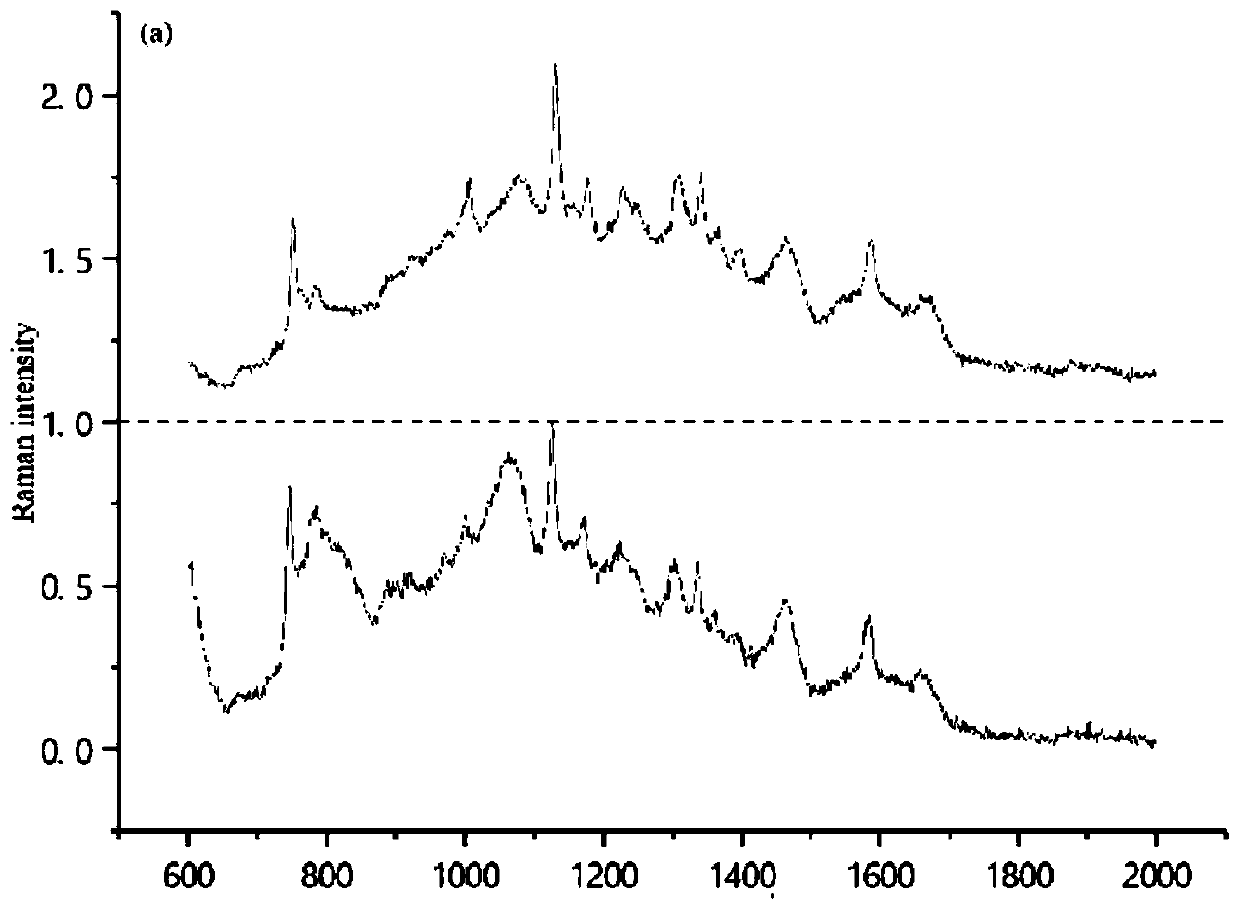
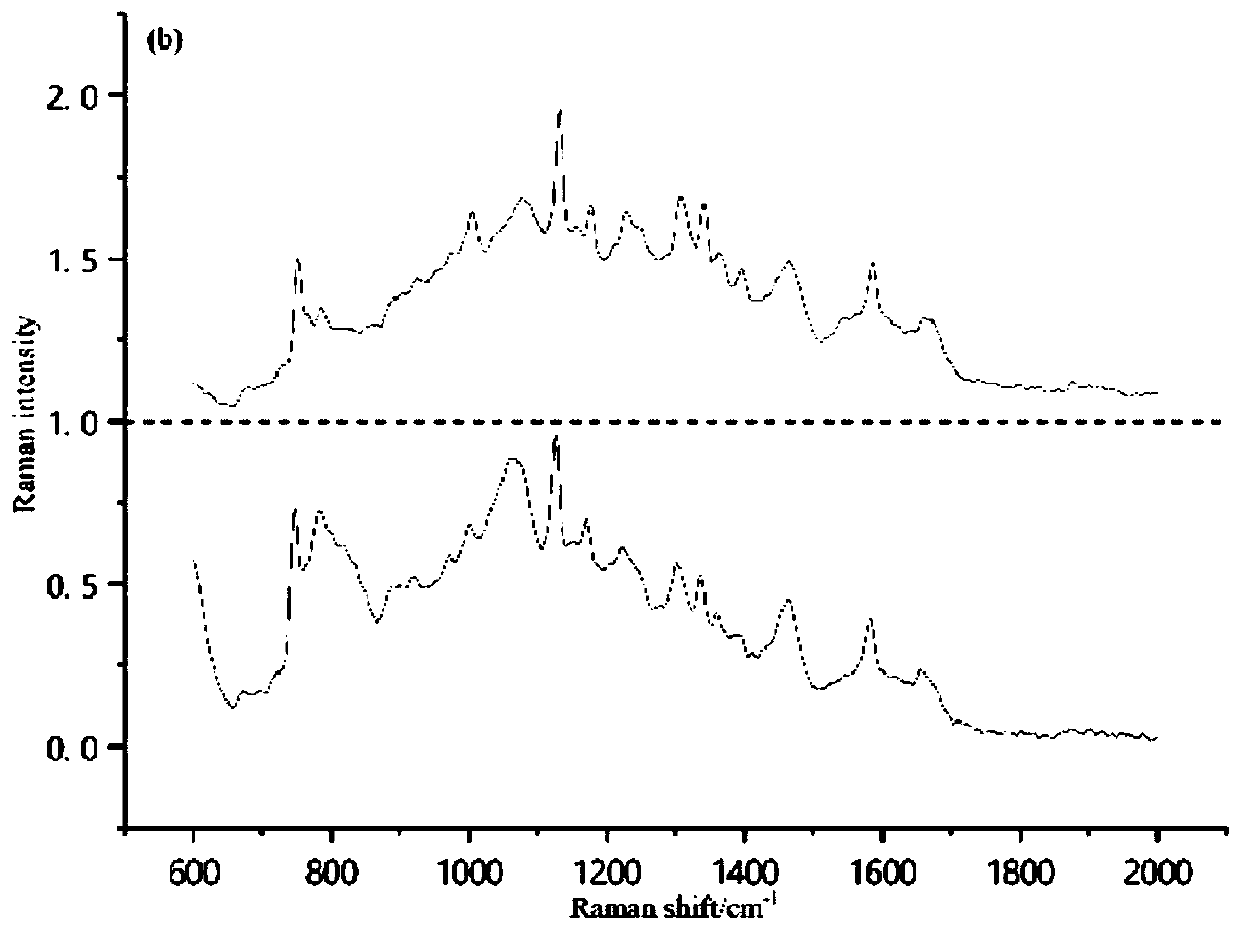
PendingCN110245713AImprove accuracyImprove security detection efficiencyCharacter and pattern recognitionNeural architecturesFood borneFood safety
The invention discloses a food-borne pathogenic bacterium classification method. The method comprises the steps of constructing a convolutional neural network and carrying out k-fold cross validation for model evaluation. The method based on the convolutional neural network is used, and the accuracy of food-borne pathogenic bacterium spectral classification is improved through structural configuration and optimization of the convolutional neural network. The technical problem mainly solved by the invention is to realize automation of spectral data classification of the food-borne pathogenic bacteria by modeling the convolutional neural network, provide reference for food safety practitioners and improve the food safety detection efficiency.
Owner:SHANGHAI INST OF TECH
A security detection method and device based on an industrial Internet operating system
ActiveCN106685990BRealize all-round detectionAvoid the problem of poor regulatory flexibilityProgramme controlData processing applicationsOperational systemData information
The present invention relates to the technical field of industrial Internet, in particular to a security detection method and device based on an industrial Internet operating system, which is used to solve the problems in the prior art that the security of the industrial site is poor and the field equipment is difficult to control. The method is: based on the diverse, heterogeneous, and dispersed operating data information in the industrial site collected by the real-time database and the big data analysis method of the industrial big data analysis platform, each safety detection rule corresponding to each field device is obtained, and each Each safety detection rule corresponding to a field device is selected and sent to the corresponding execution device to realize the safety detection of each field device and ensure the controllability of industrial field safety. Based on the big data analysis method, realize The whole process from industrial data collection, analysis, storage to data mining, data optimization, and data security is realized, so that the industrial cloud and every field device can run in a trusted working environment.
Owner:KYLAND TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com