Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
9481 results about "Testing equipment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
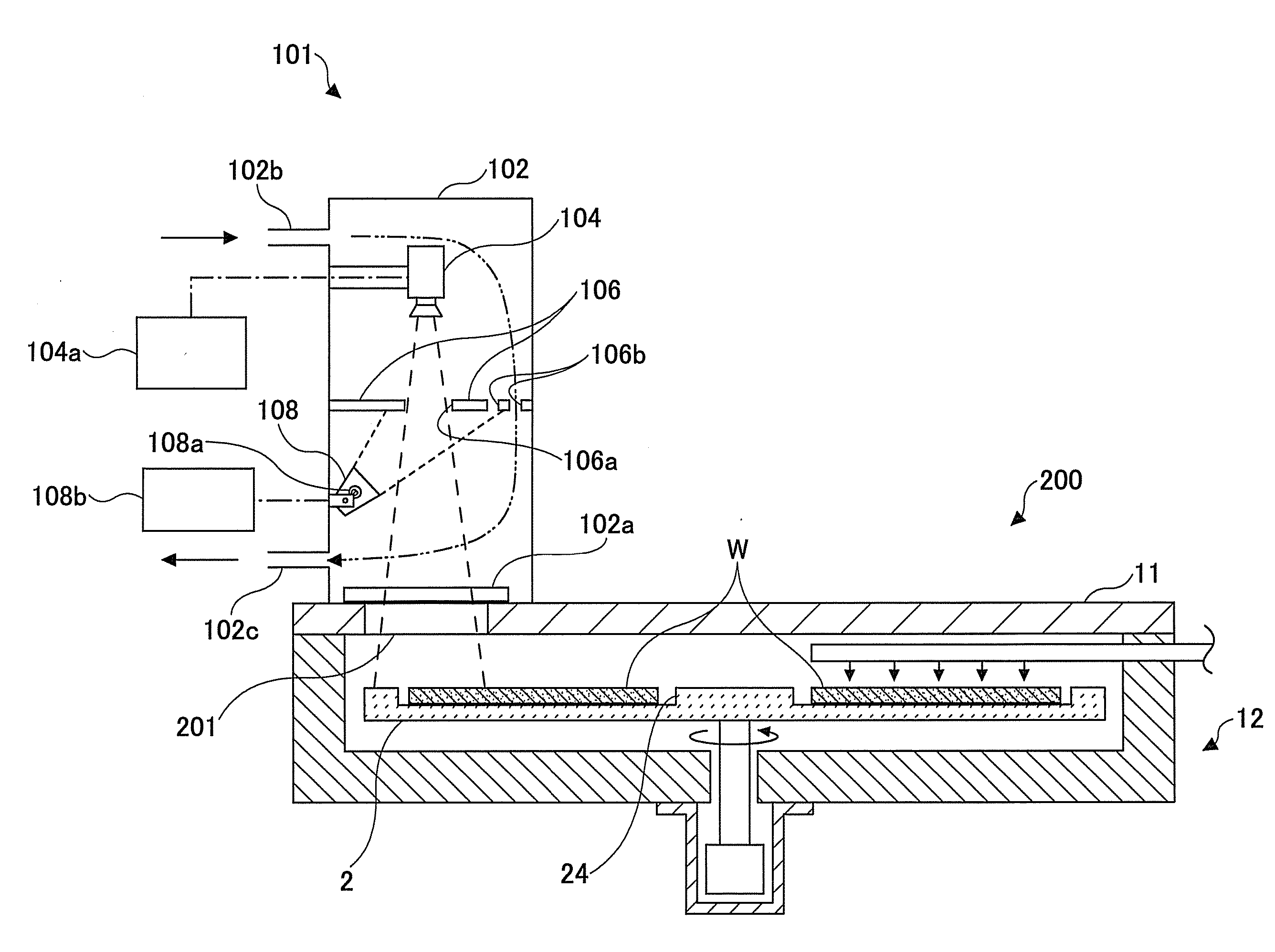
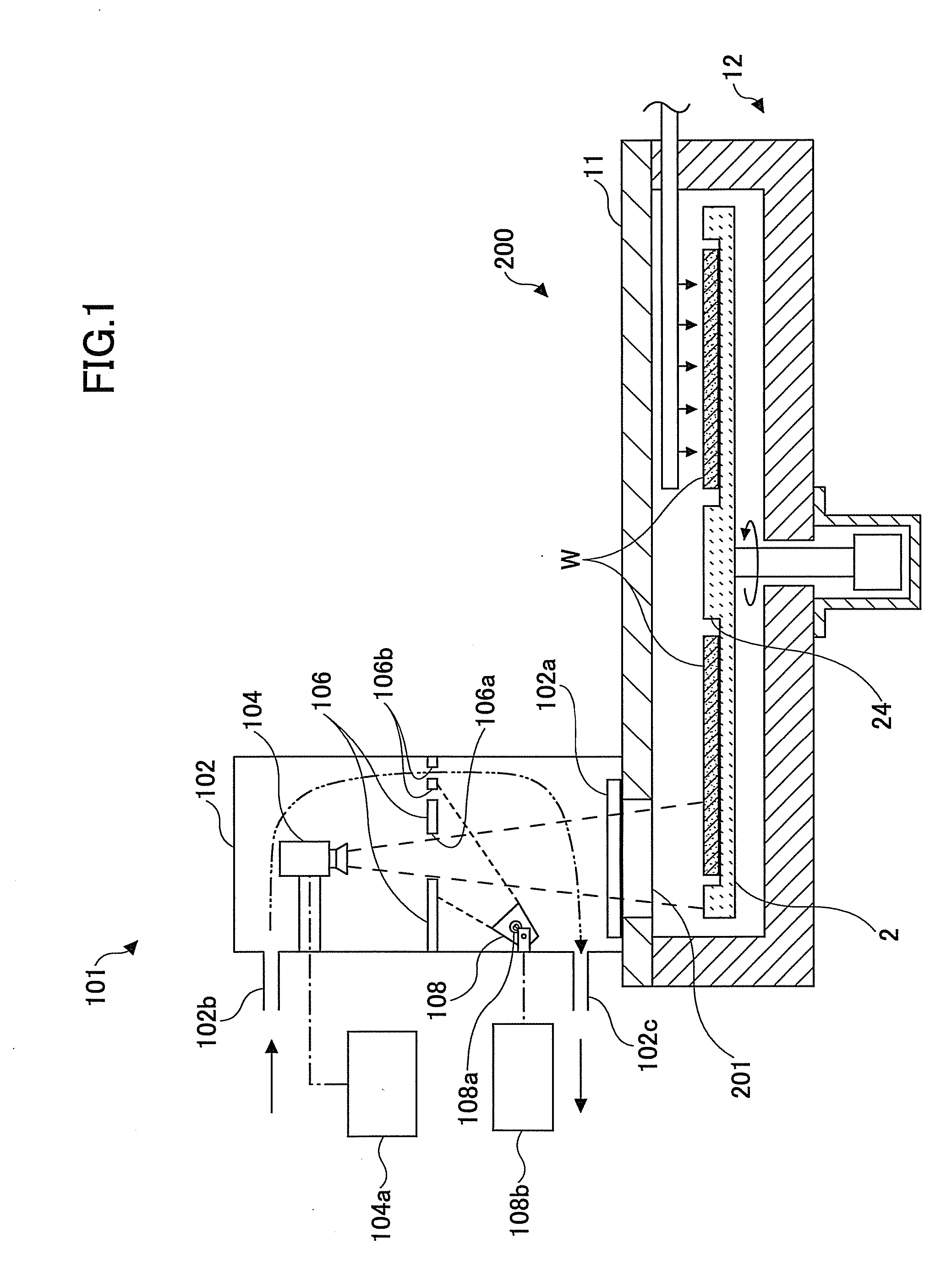
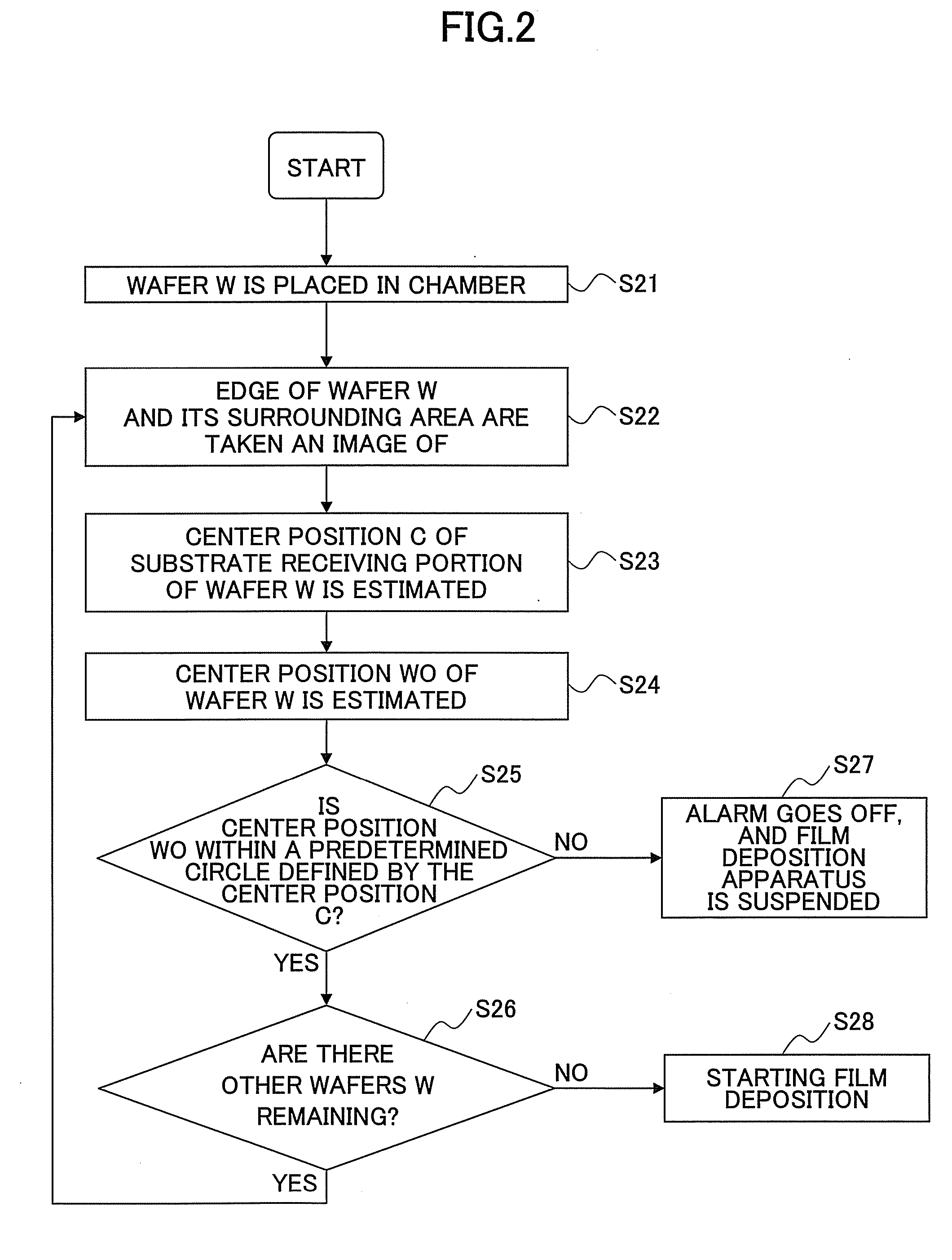
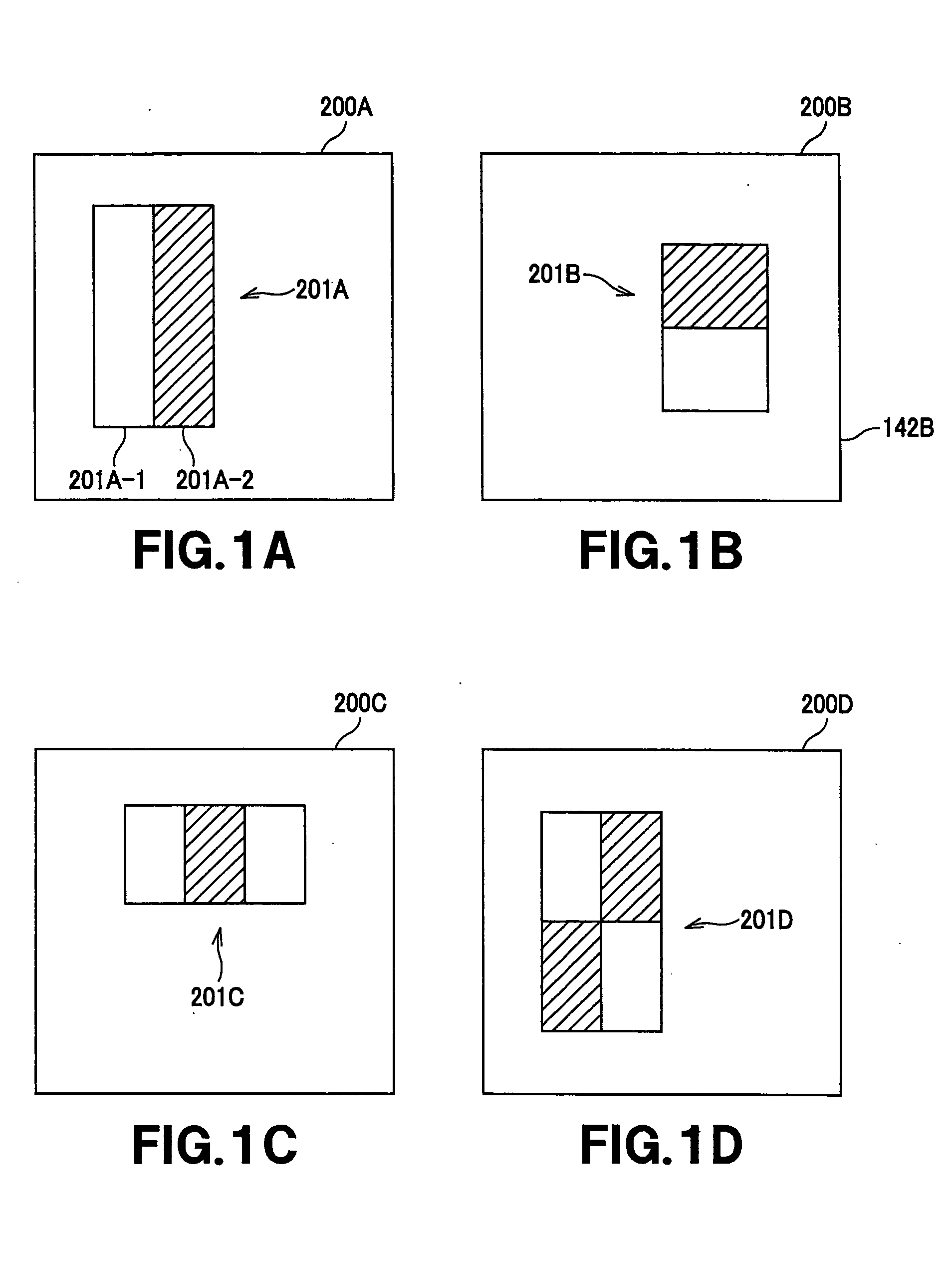
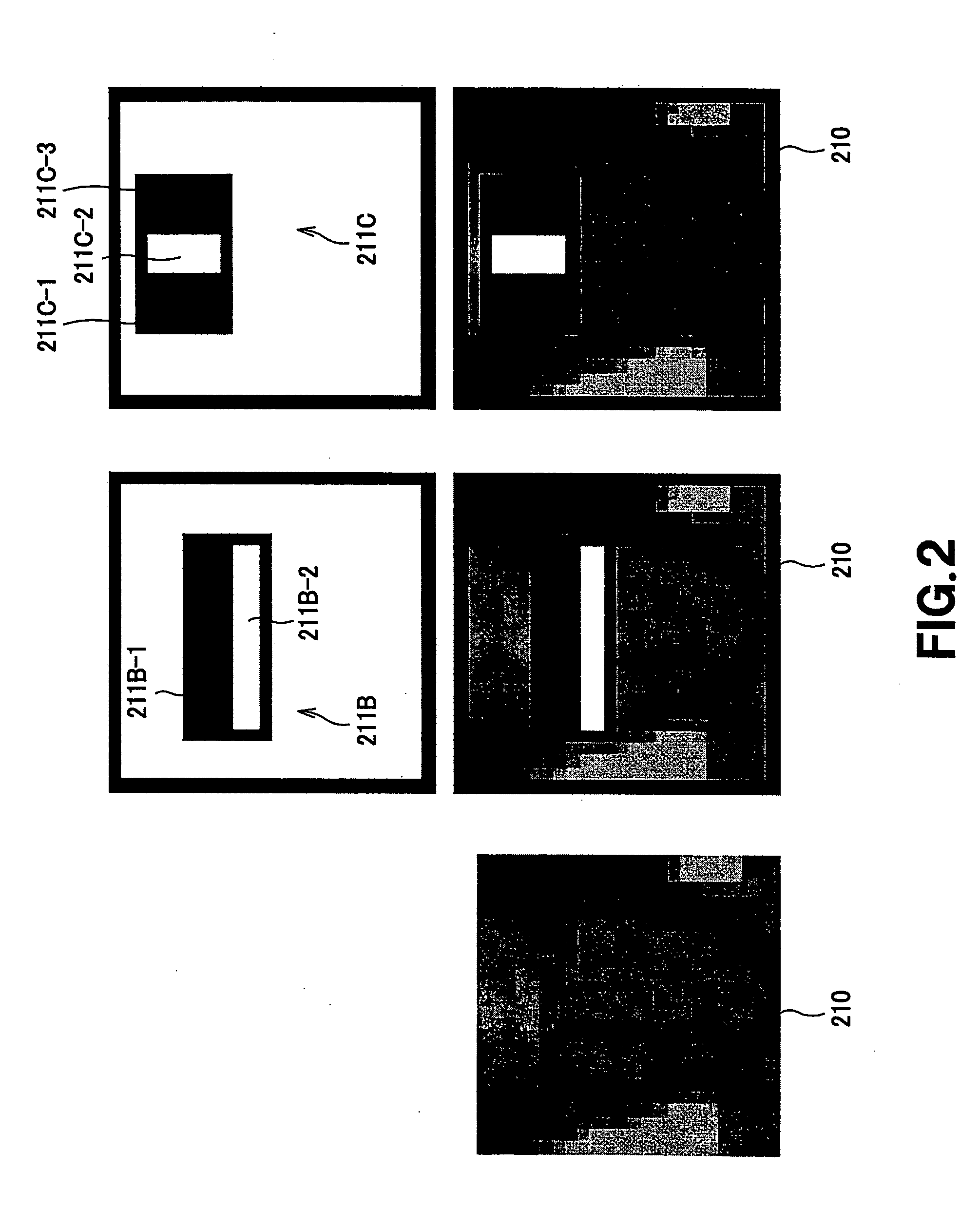
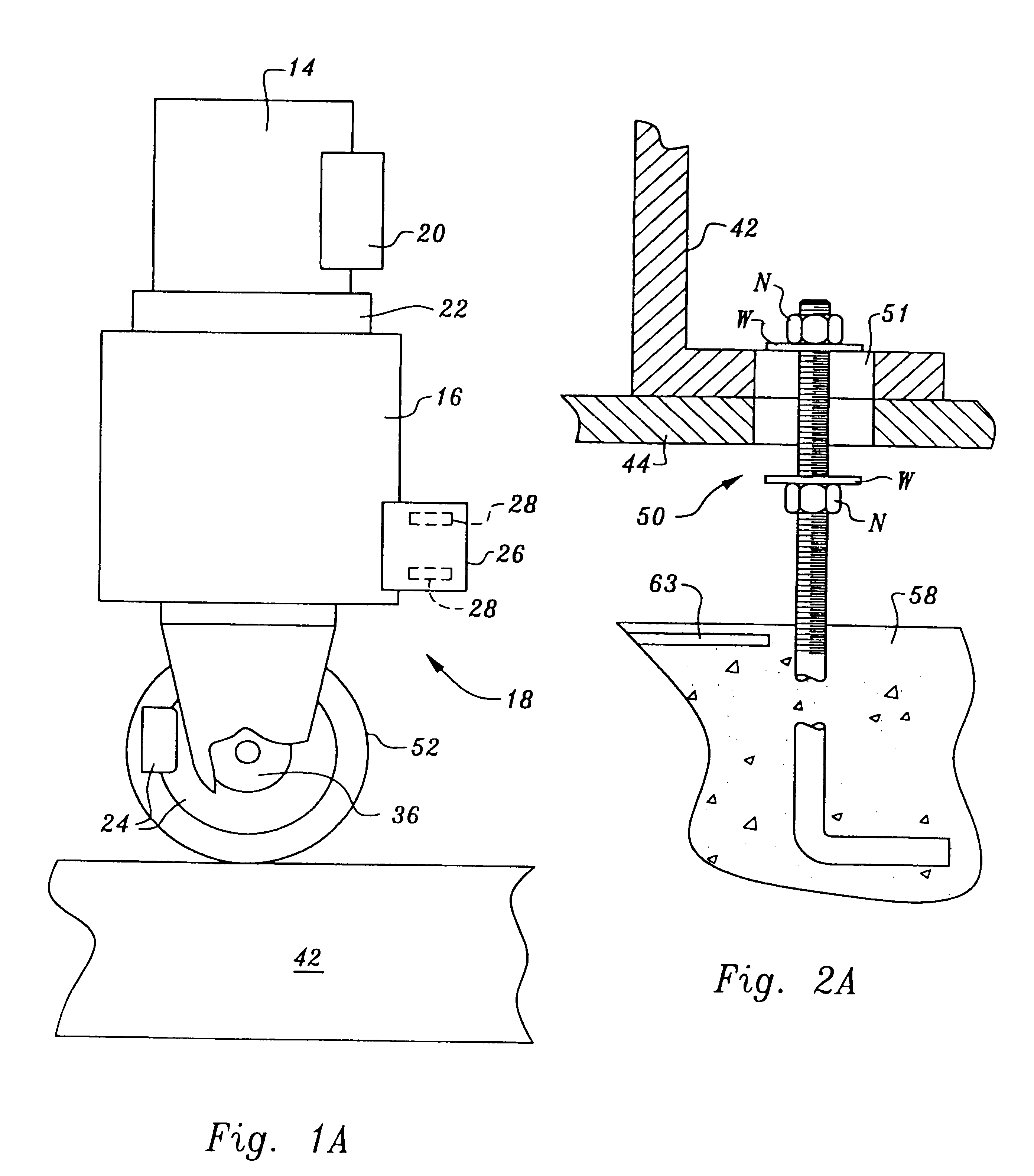
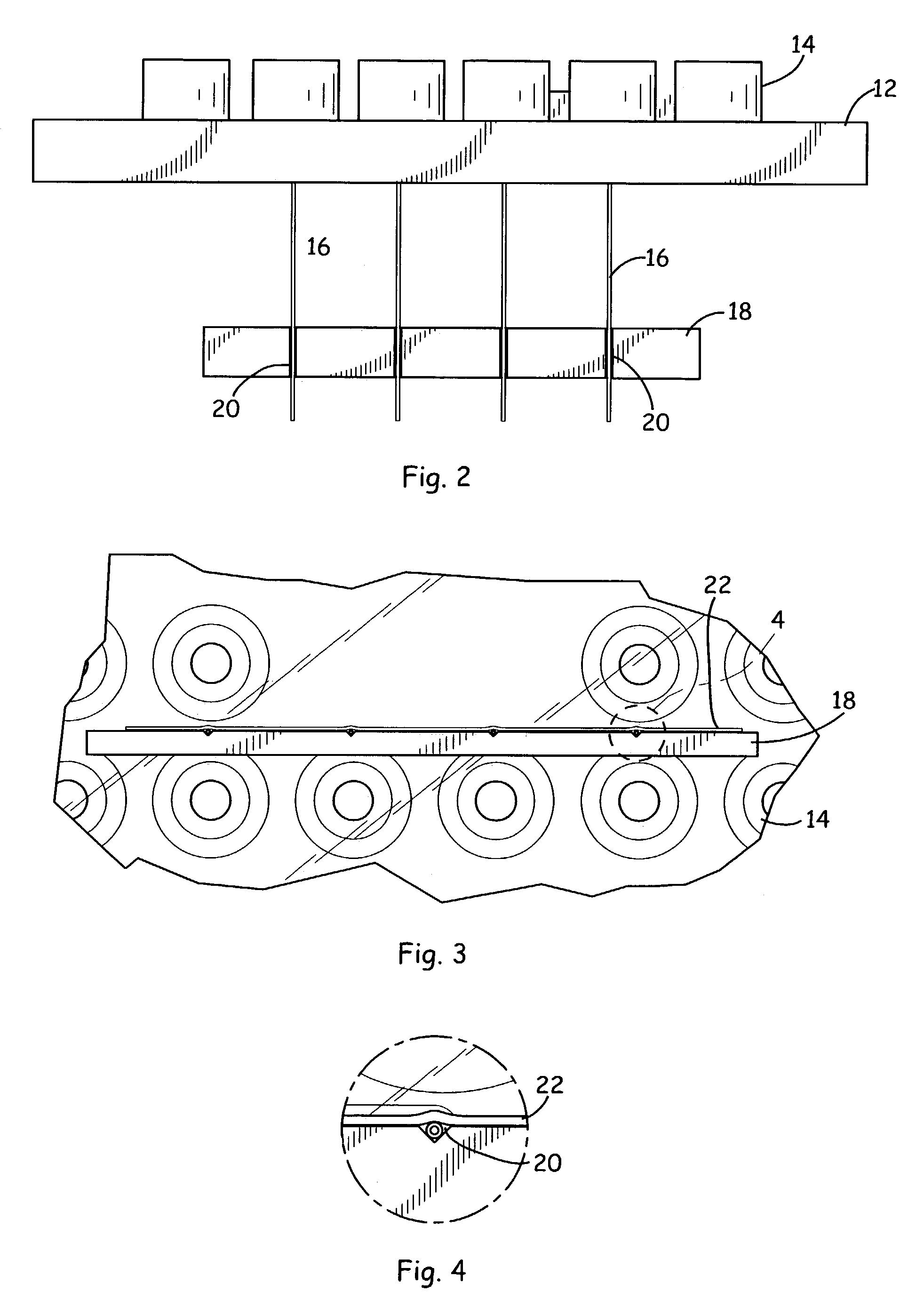
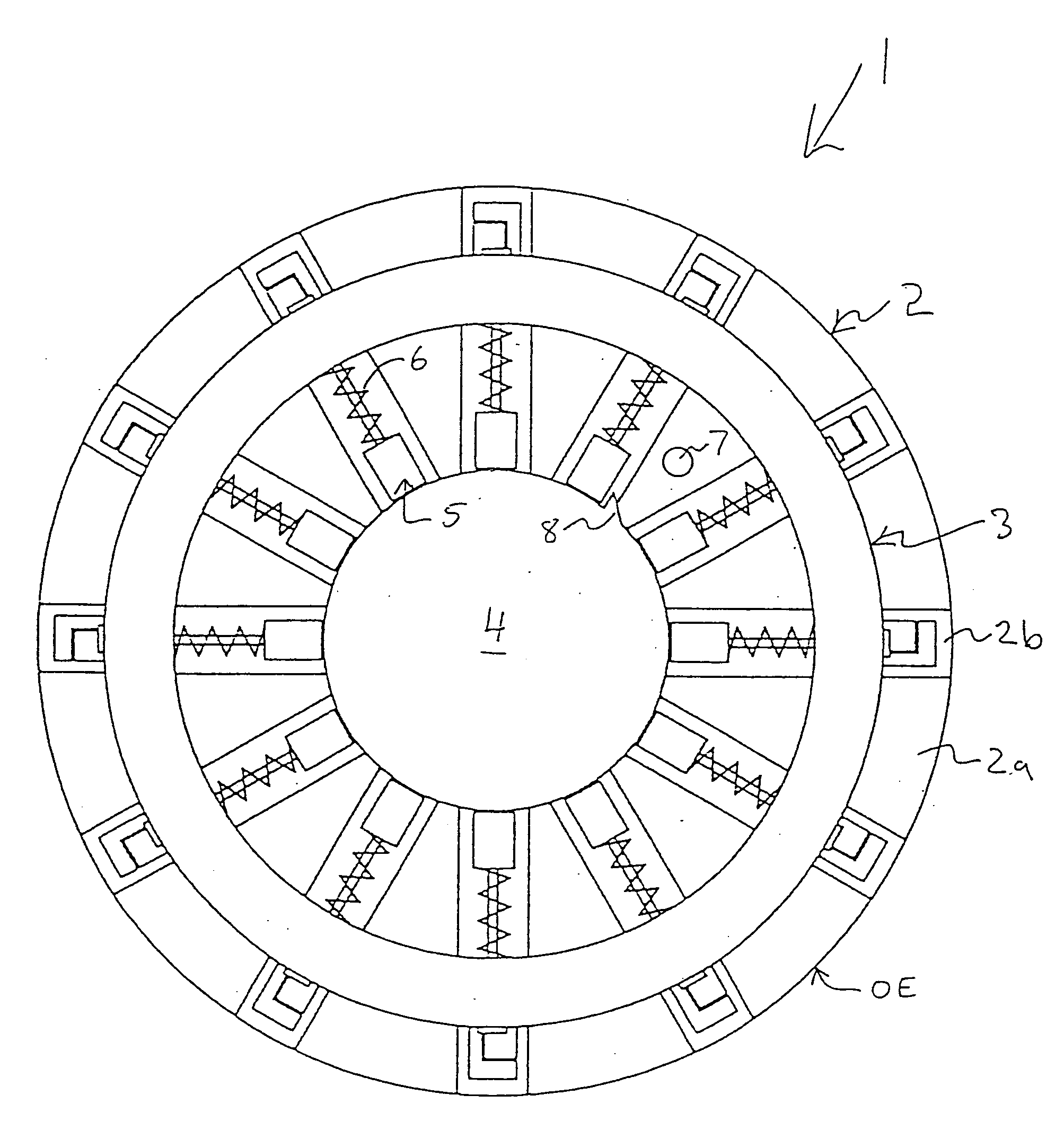
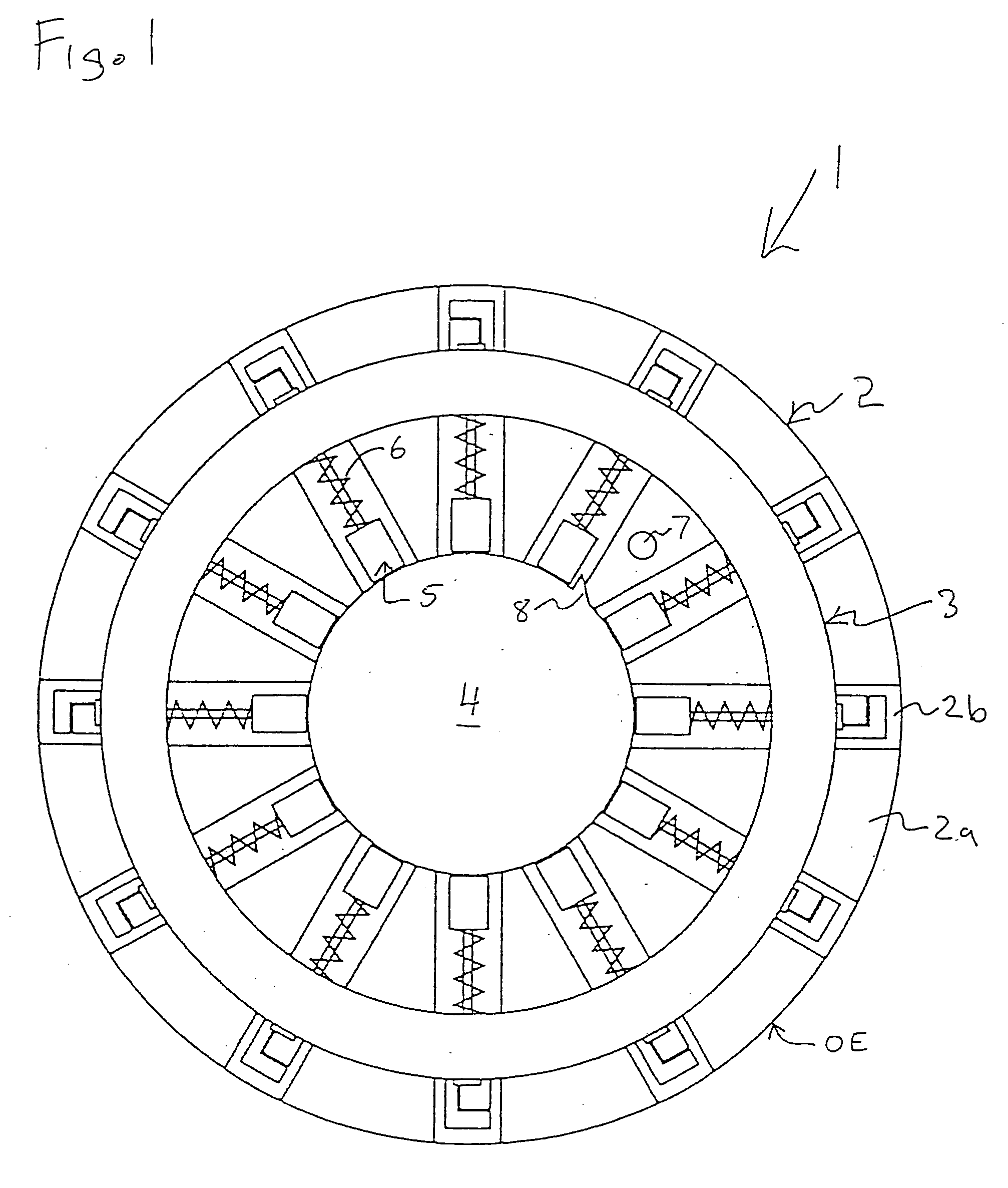
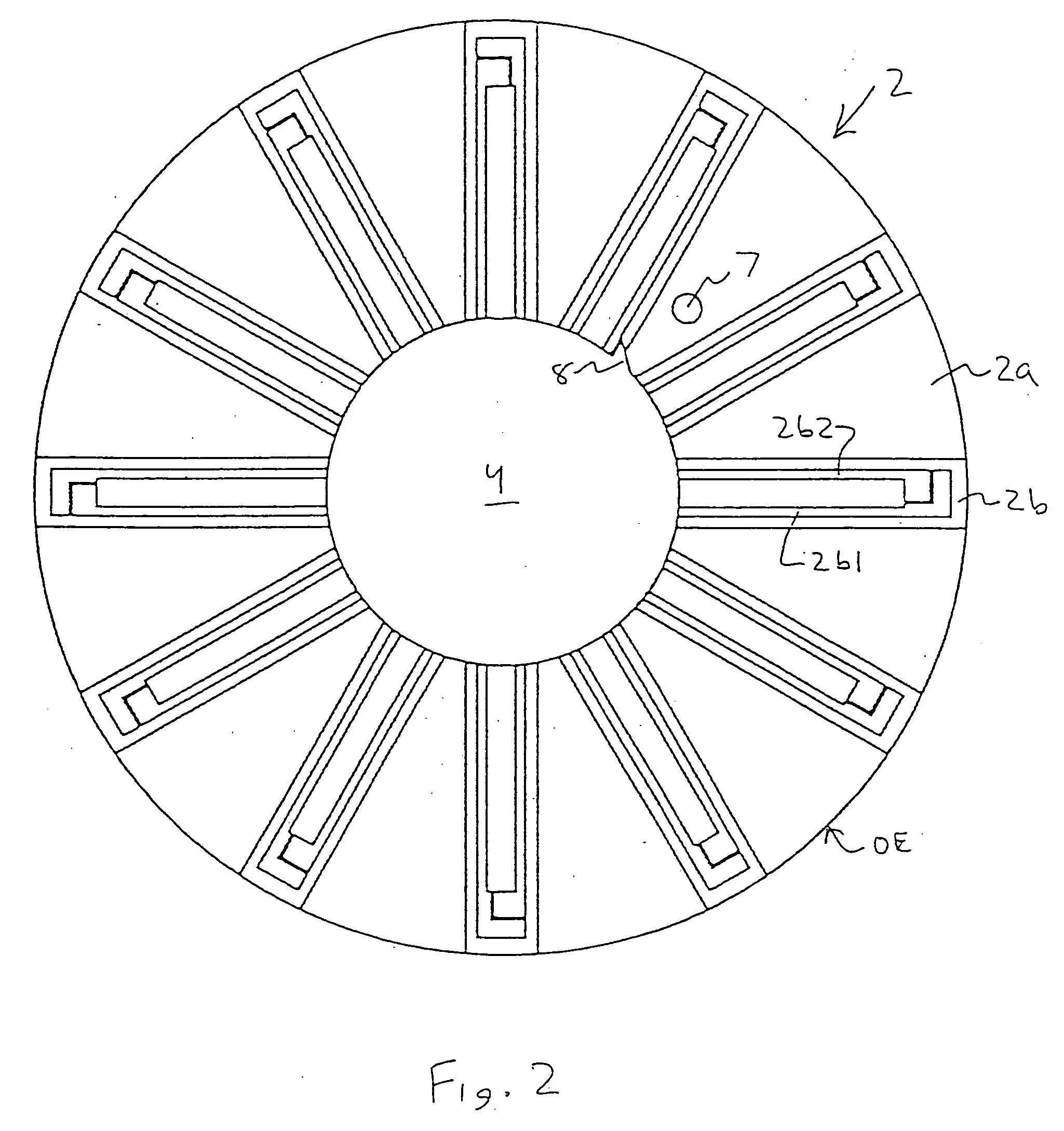
Substrate position detection apparatus, substrate position detection method, film deposition apparatus, film deposition method, and a computer readable storage medium
InactiveUS20100124610A1Reduce detectionLiquid surface applicatorsSemiconductor/solid-state device manufacturingEngineeringField of view
A disclosed substrate position detection apparatus includes an imaging portion configured to take an image of a substrate subject to a position detection; a panel member provided between the imaging portion and the substrate and including a first opening that ensures a field of view for the imaging portion with respect to the substrate, the panel member having a light scattering property; a first illuminating portion configured to illuminate the panel member; and a processing portion capable of determining a position of the substrate in accordance with the image taken through the first opening by the imaging portion.
Owner:TOKYO ELECTRON LTD
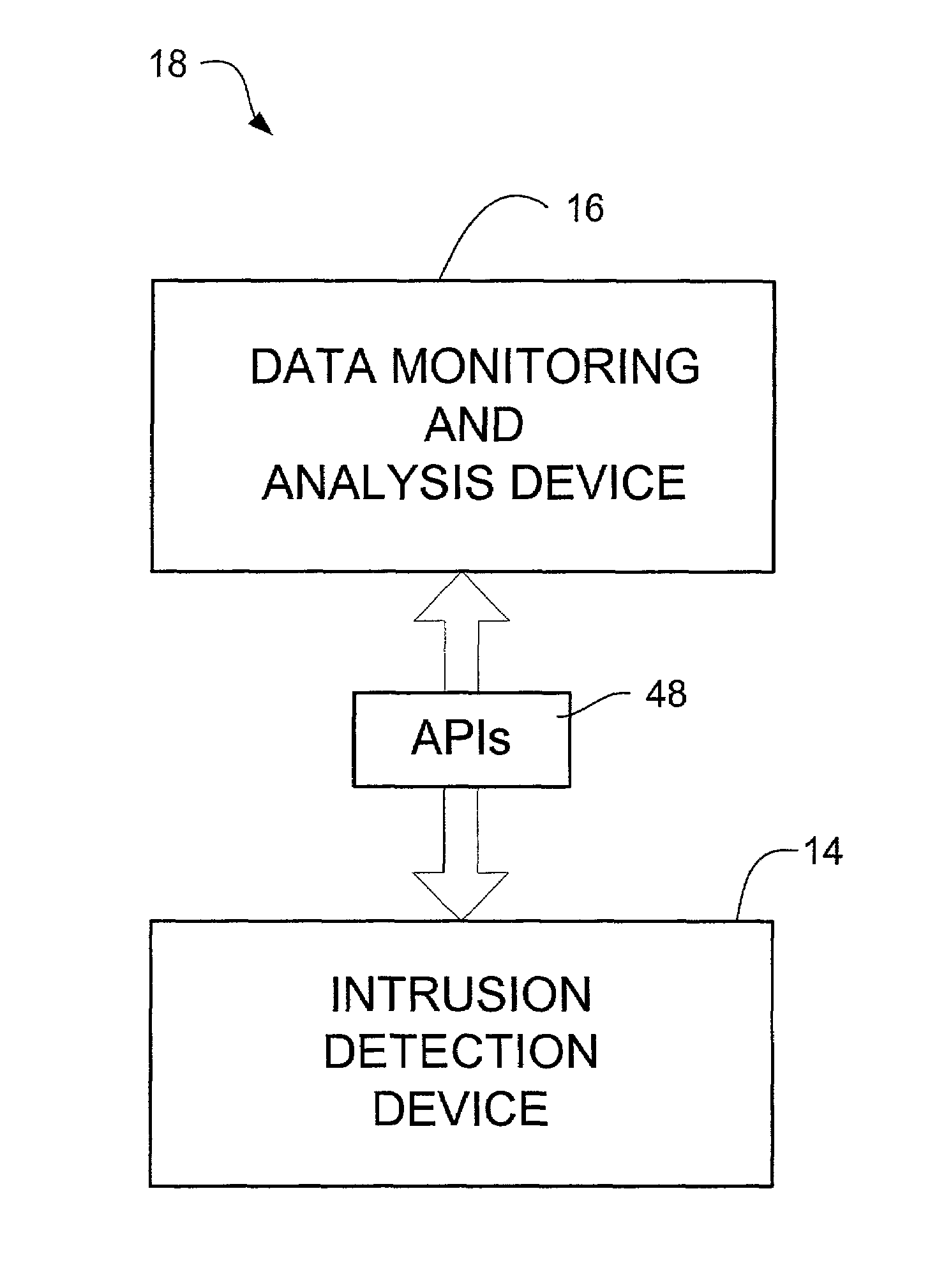
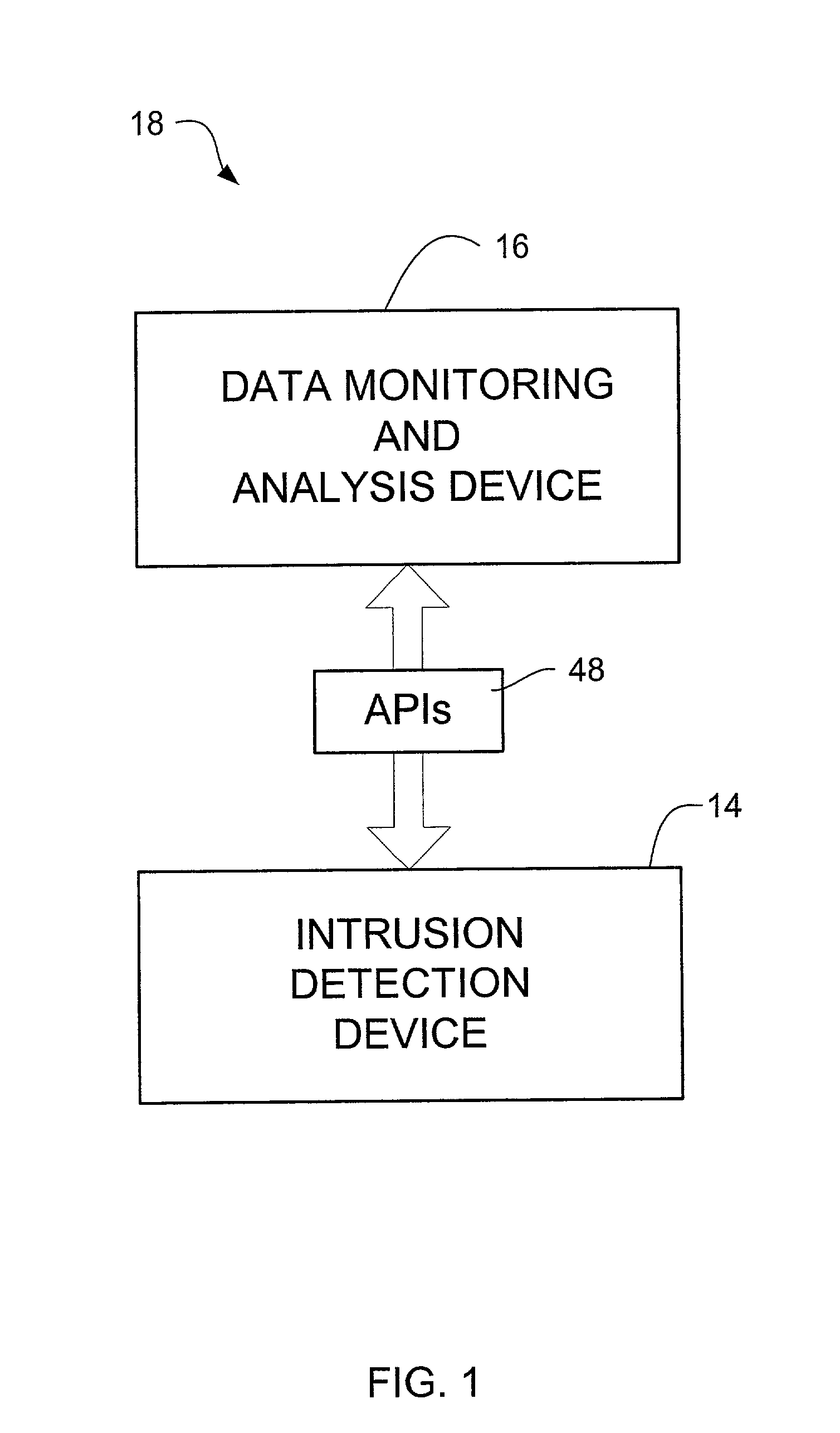
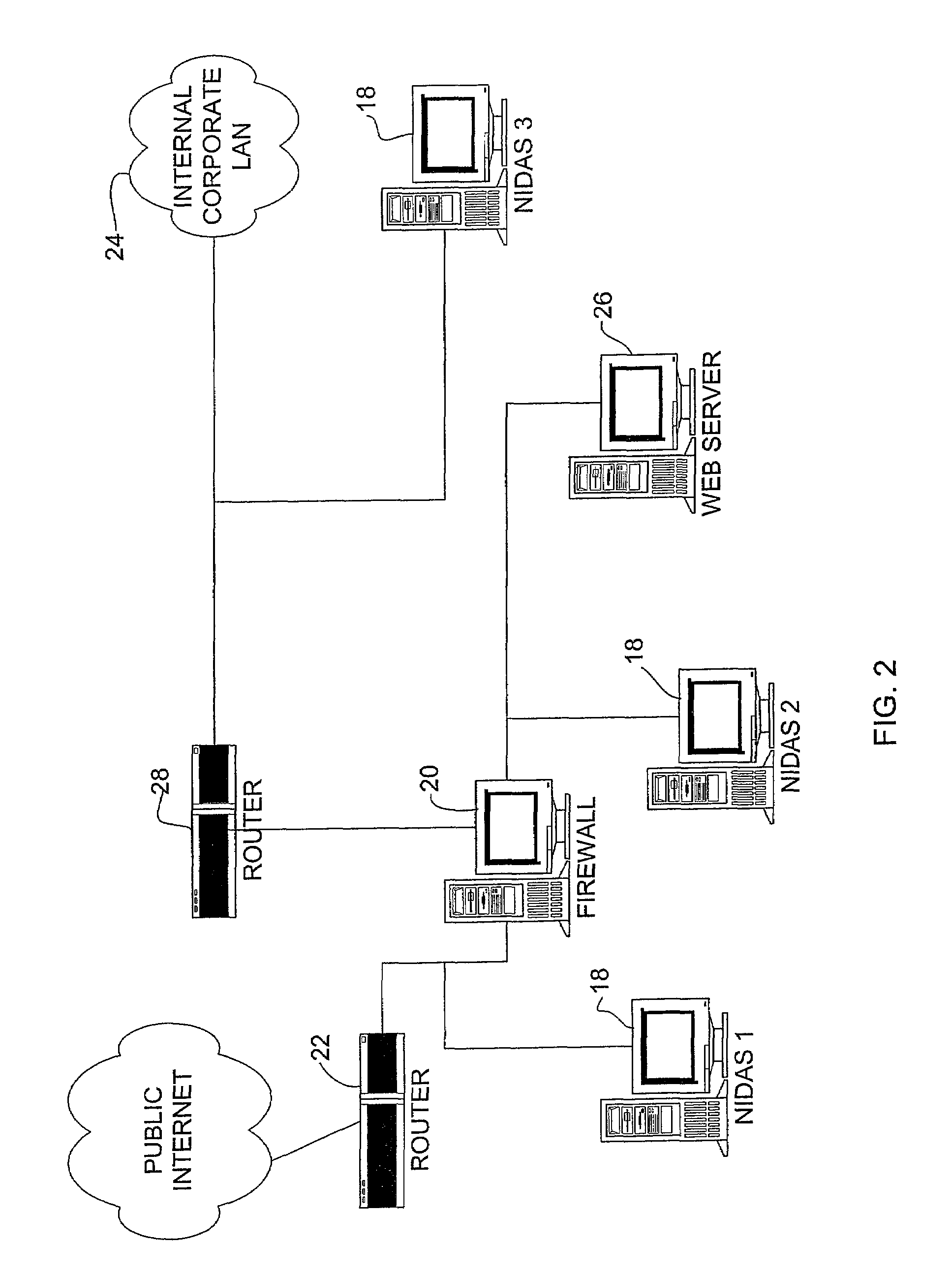
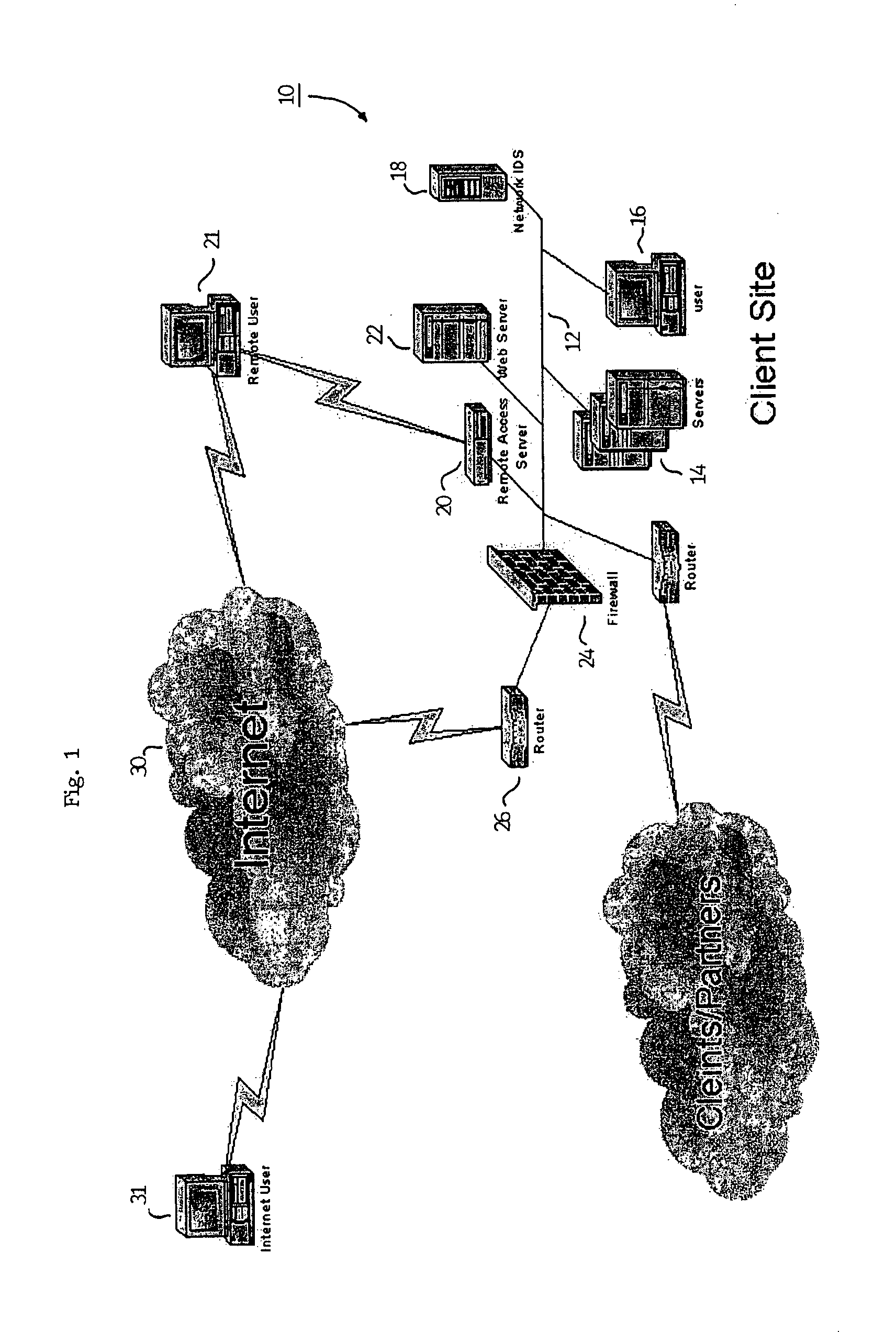
Network intrusion detection and analysis system and method
ActiveUS7493659B1Digital data processing detailsUser identity/authority verificationTraffic capacityData monitoring
An intrusion detection and analysis system and method are disclosed. The system includes a data monitoring device comprising a capture engine operable to capture data passing through the network and configured to monitor network traffic, decode protocols, and analyze received data. The system further includes an intrusion detection device comprising a detection engine operable to perform intrusion detection on data provided by the data monitoring device. Application program interfaces are provided and configured to allow the intrusion detection device access to applications of the data monitoring device to perform intrusion detection. The system also includes memory for storing reference network information used by the intrusion detection device to determine if an intrusion has occurred.
Owner:MCAFEE LLC
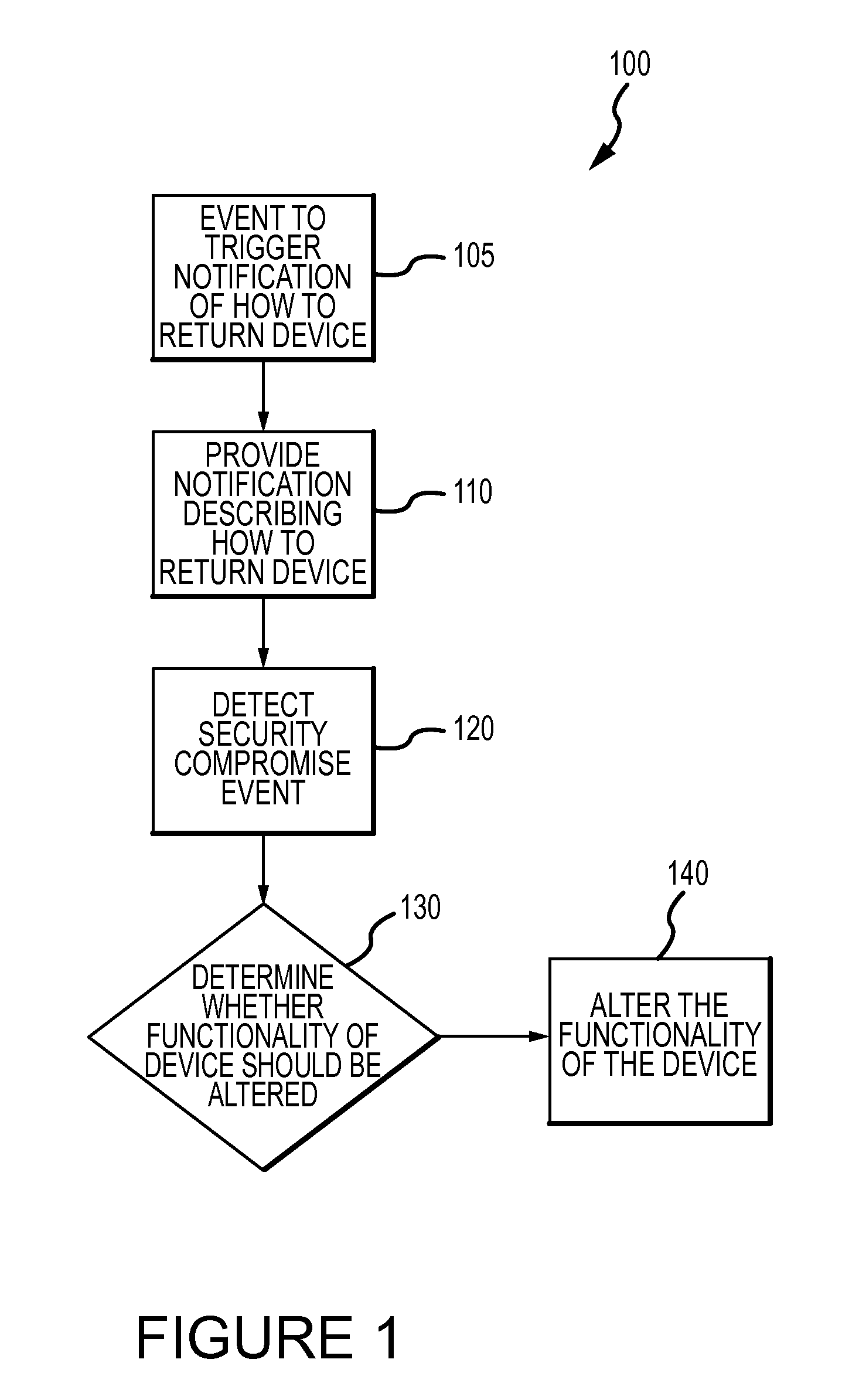
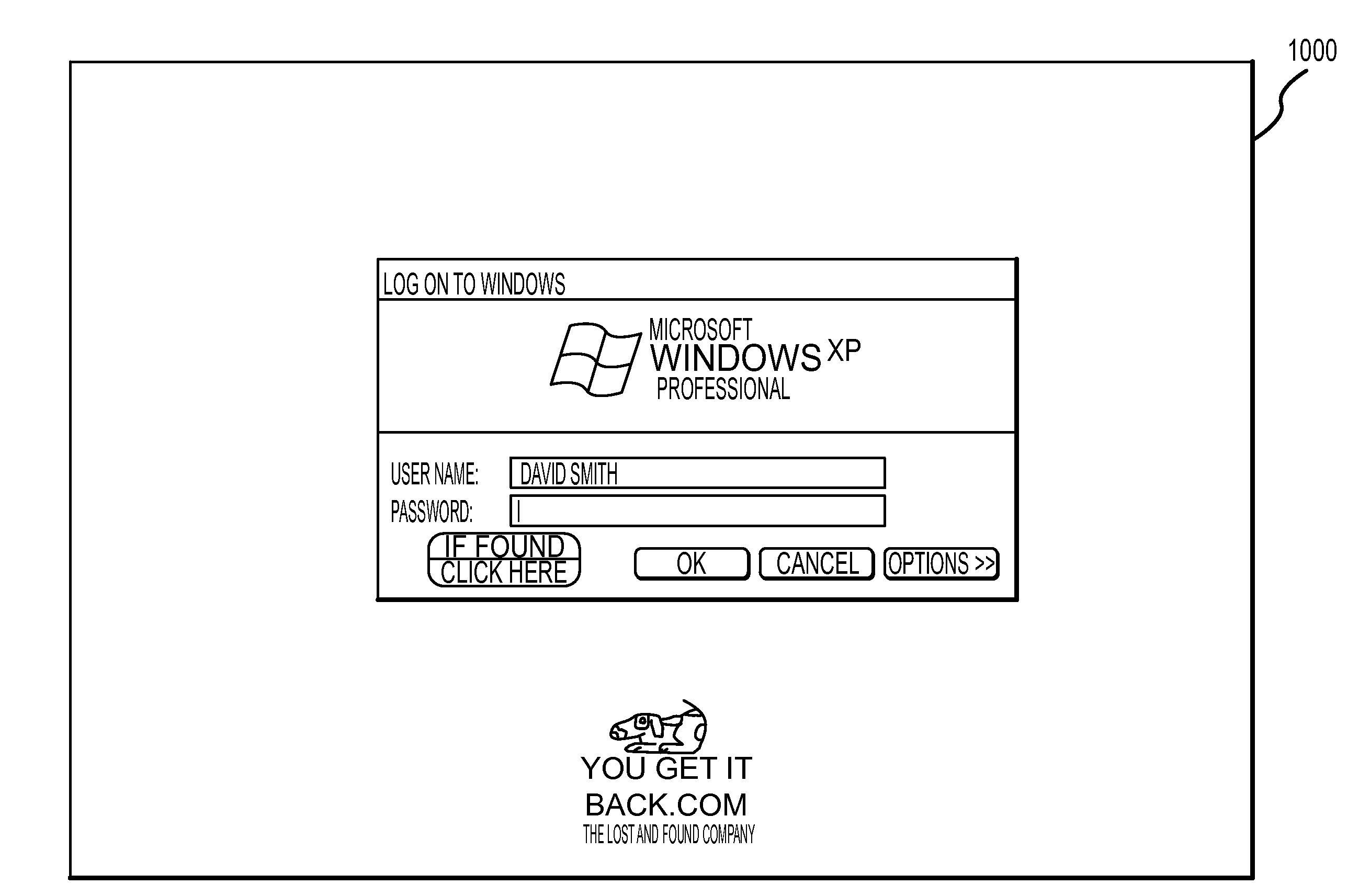
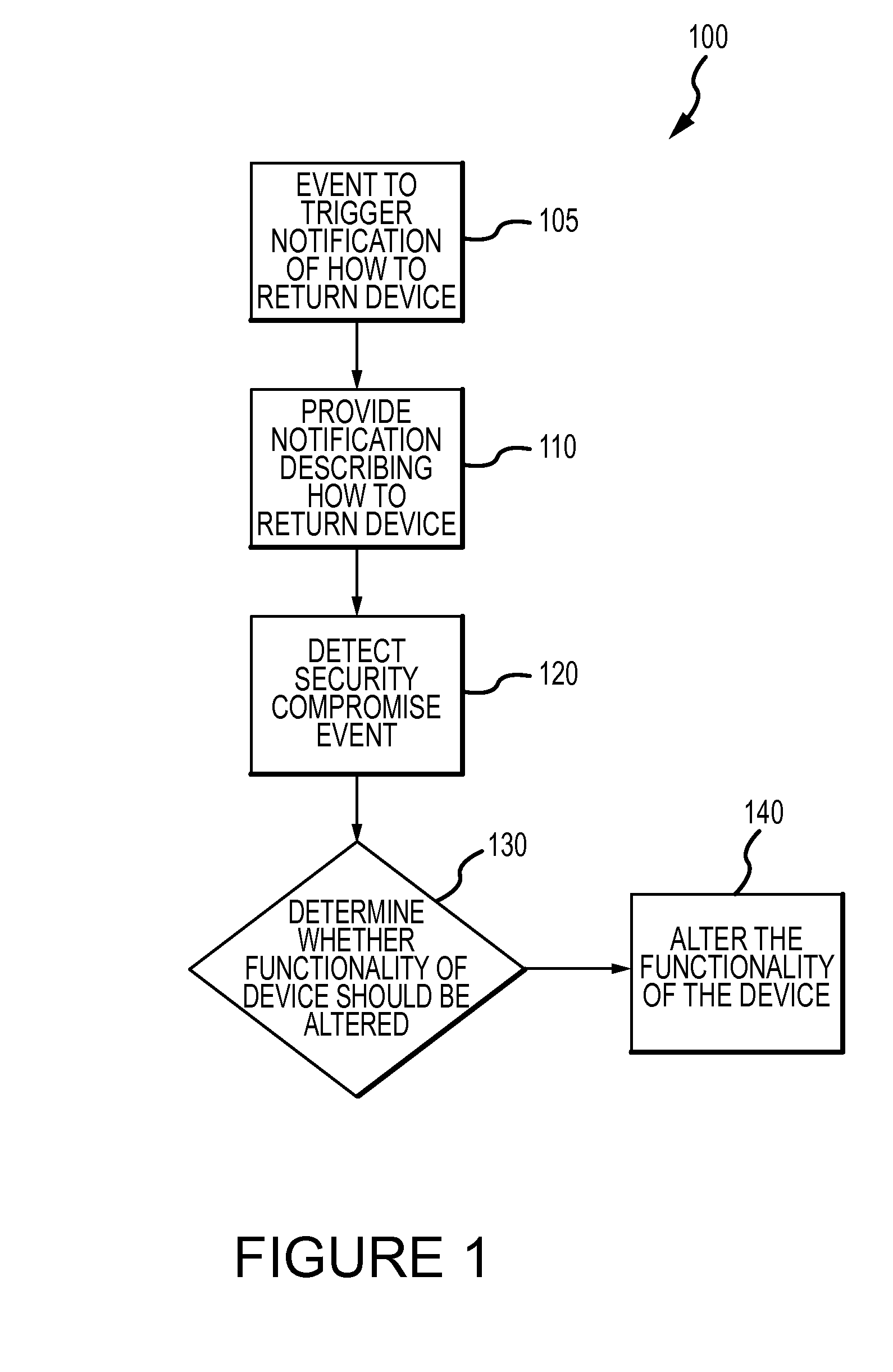
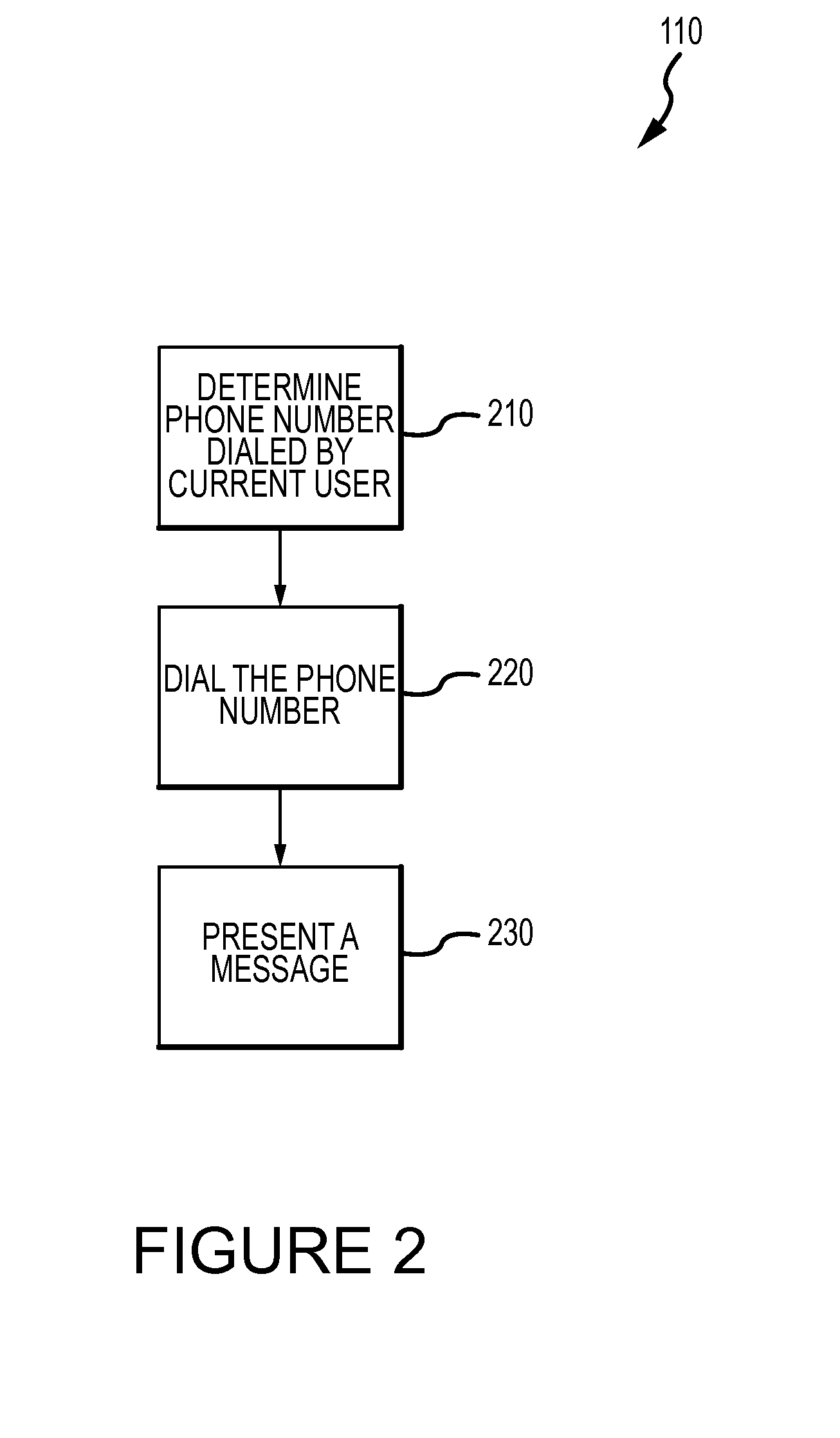
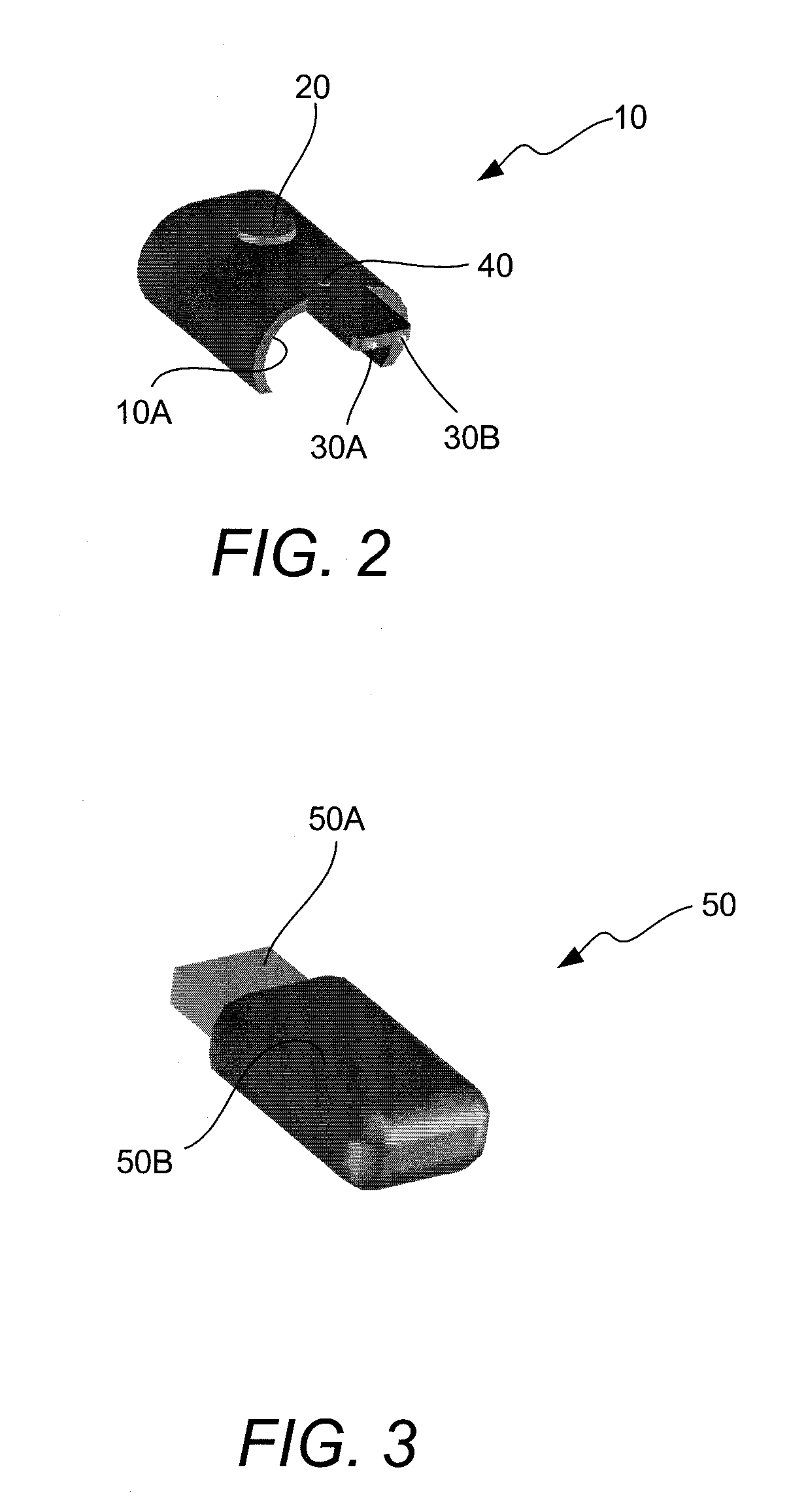
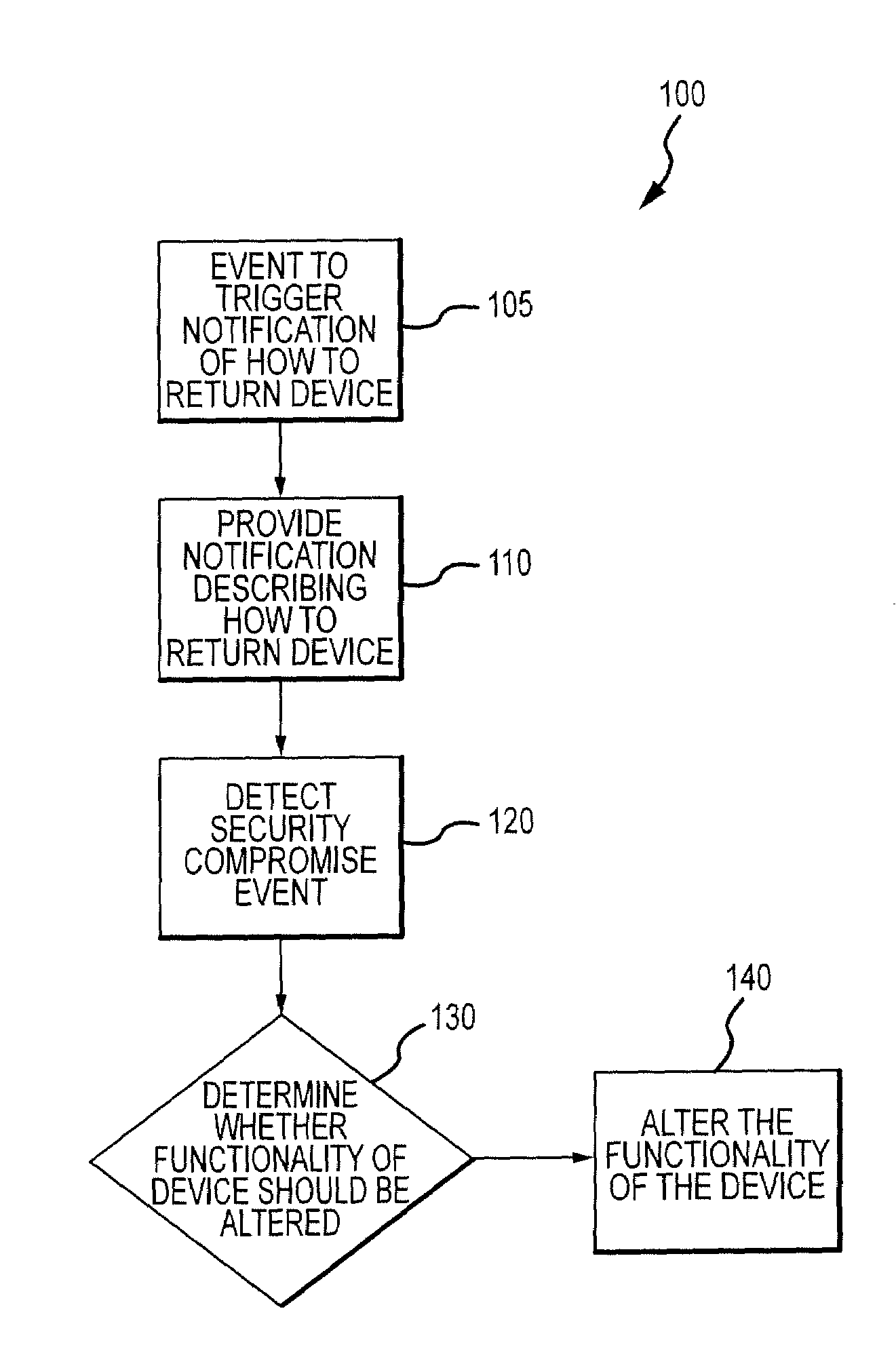
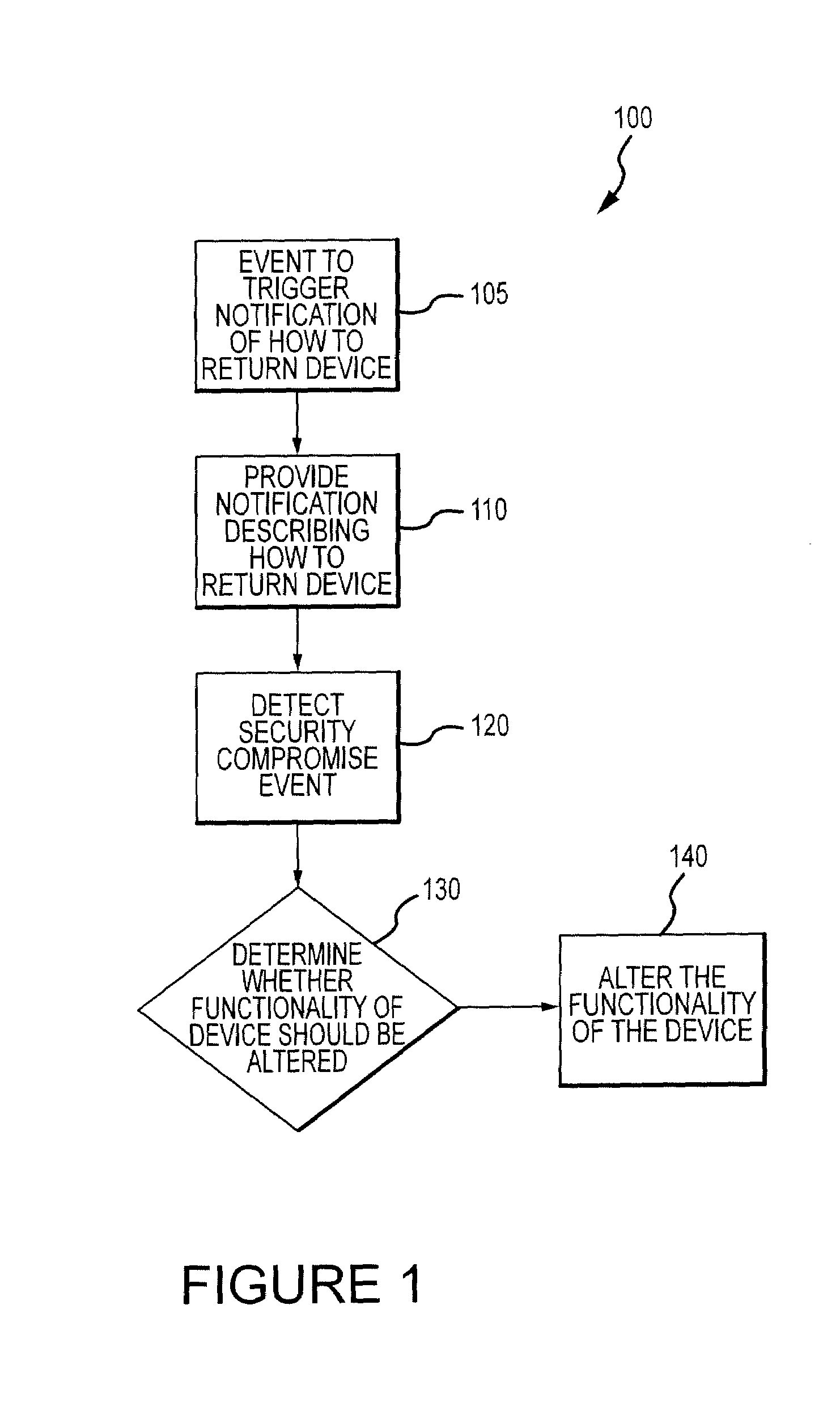
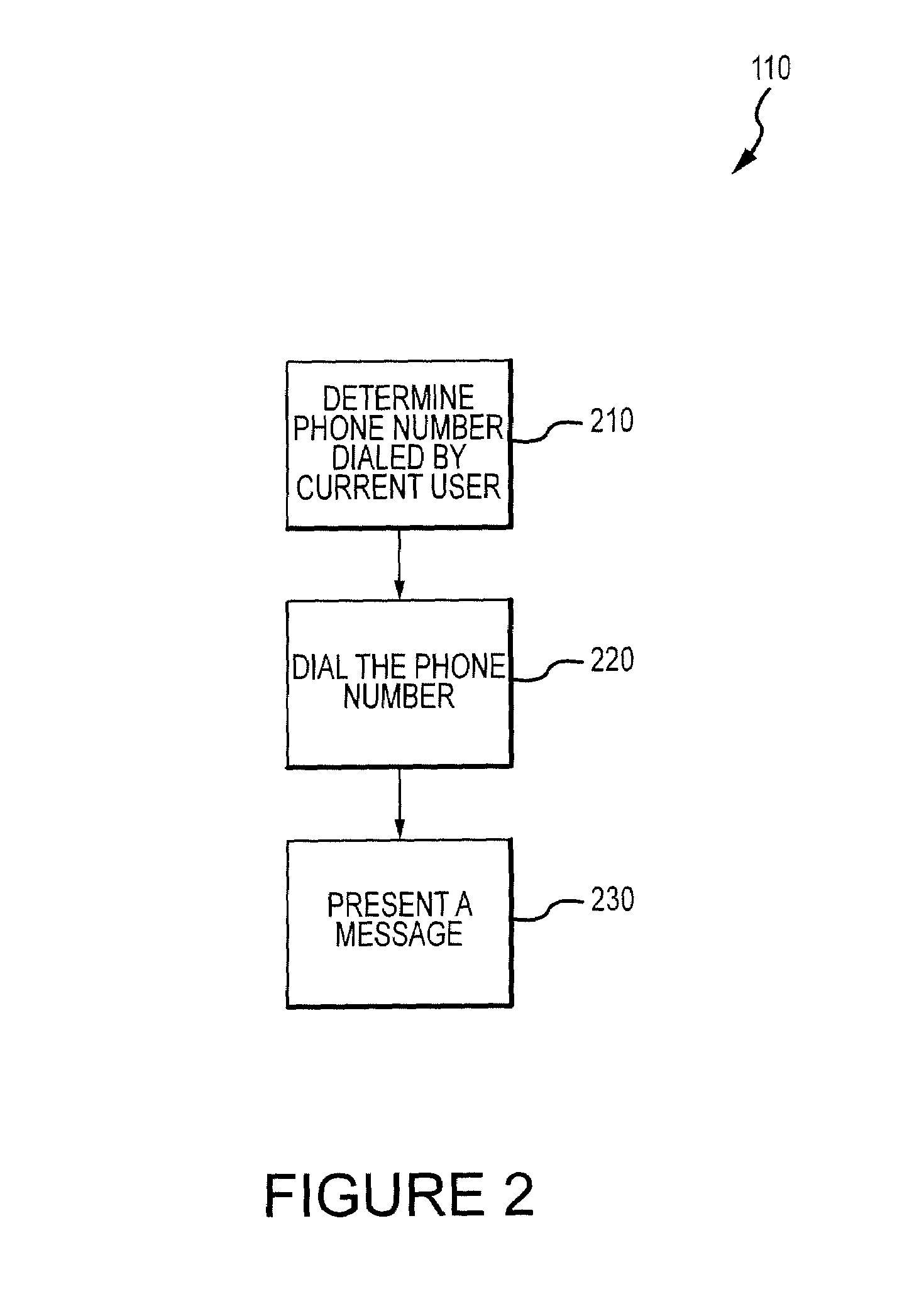
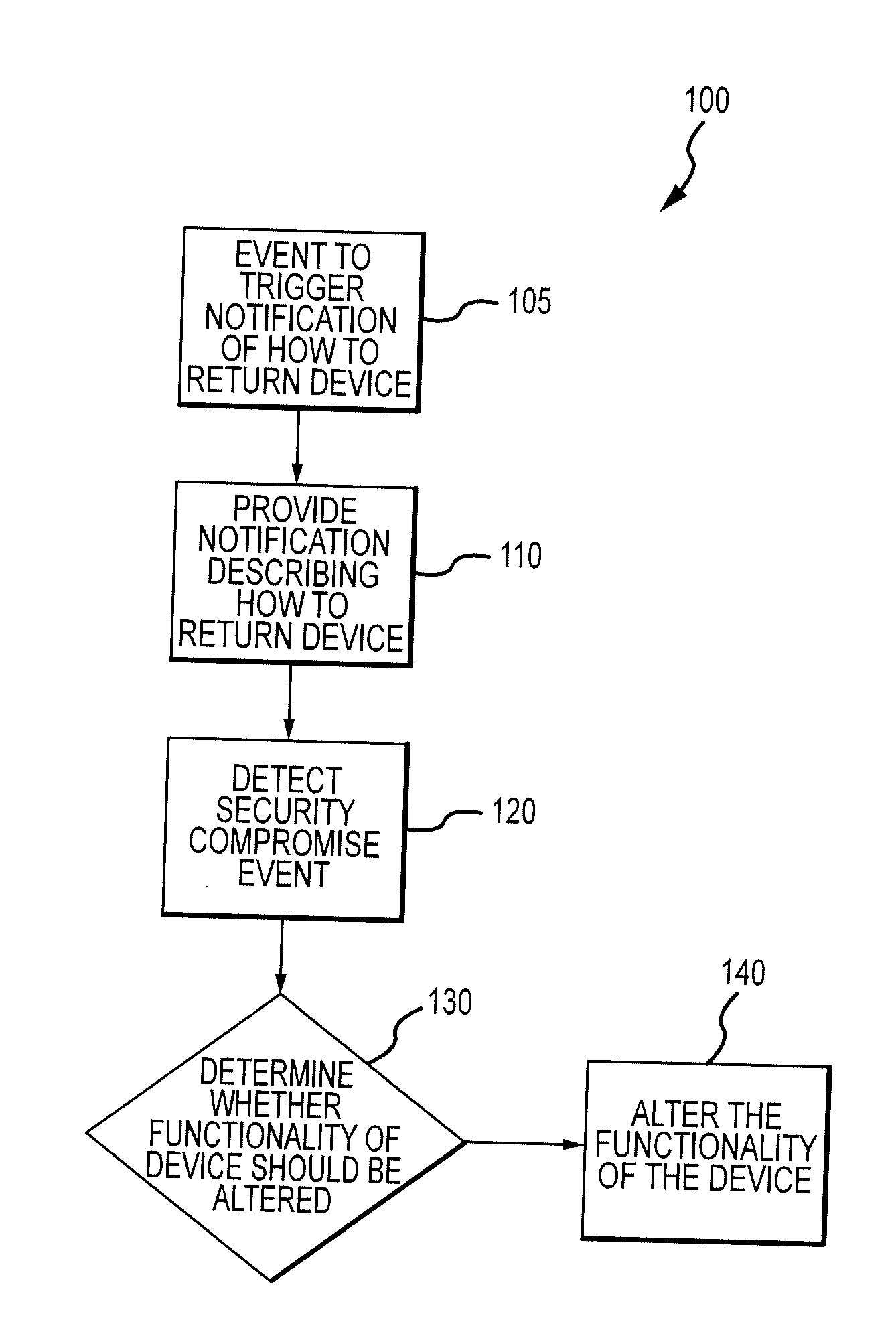
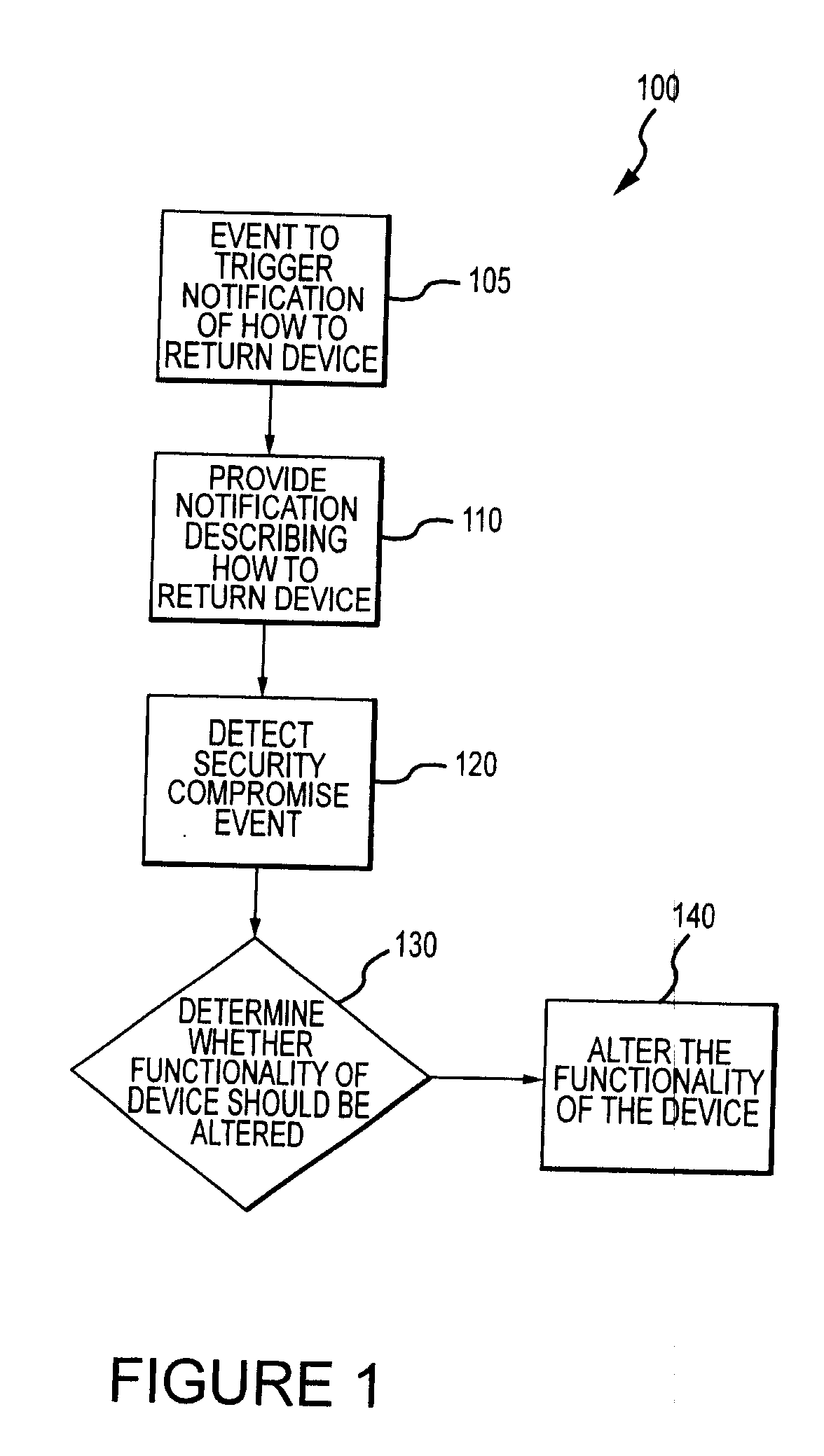
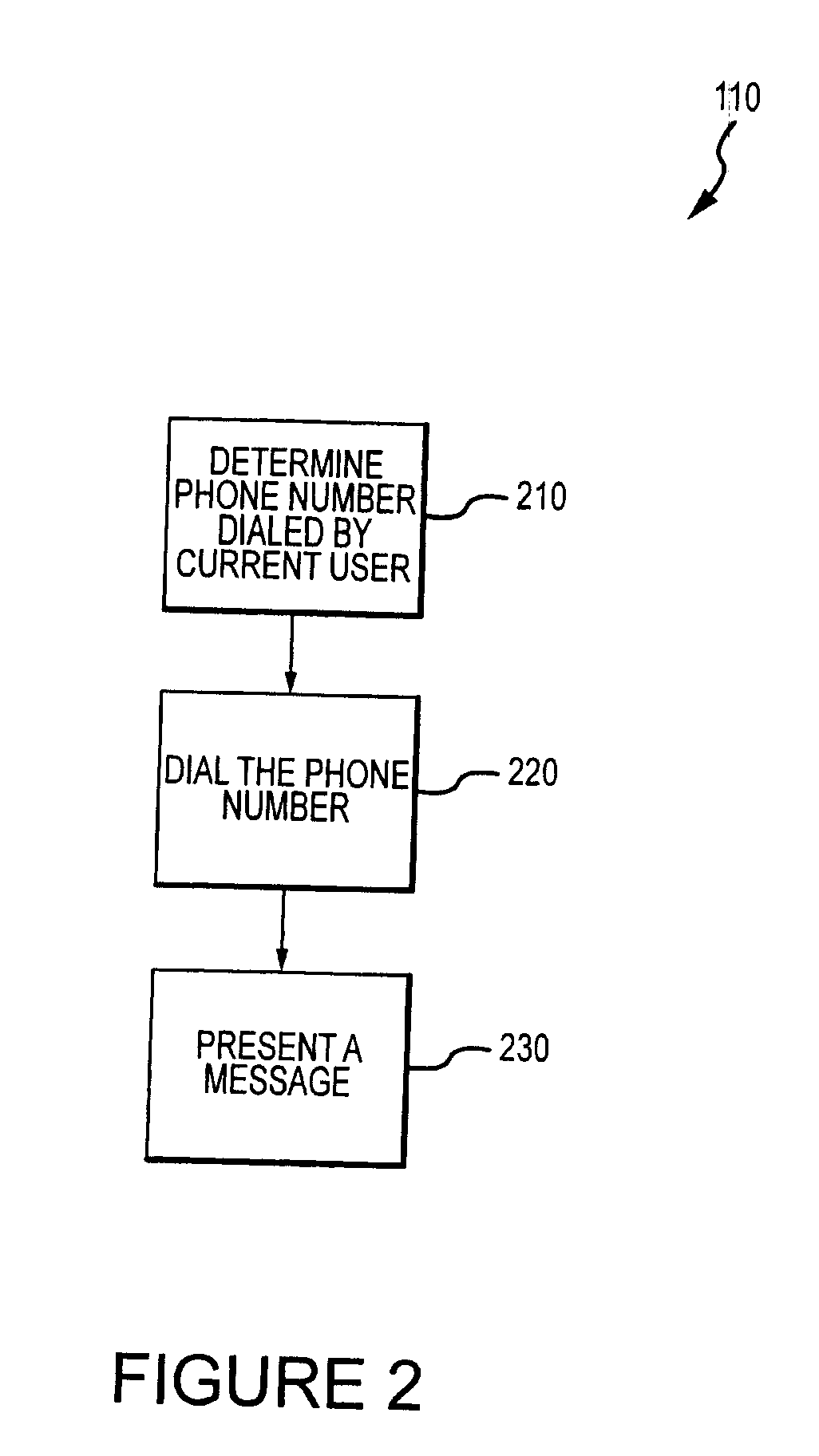
Method for mitigating the unauthorized use of a device
ActiveUS20090253410A1Raise the possibilityIncrease opportunitiesUnauthorised/fraudulent call preventionEavesdropping prevention circuitsDevice MonitorLocal environment
The invention is directed to systems and methods for detecting the loss, theft or unauthorized use of a device and / or altering the functionality of the device in response. In one embodiment, a device monitors its use, its local environment, and / or its operating context to determine that the device is no longer within the control of an authorized user. The device may receive communications or generate an internal signal altering its functionality, such as instructing the device to enter a restricted use mode, a surveillance mode, to provide instructions to return the device and / or to prevent unauthorized use or unauthorized access to data. Additional embodiments also address methods and systems for gathering forensic data regarding an unauthorized user to assist in locating the unauthorized user and / or the device.
Owner:BLANCCO TECH GRP IP OY
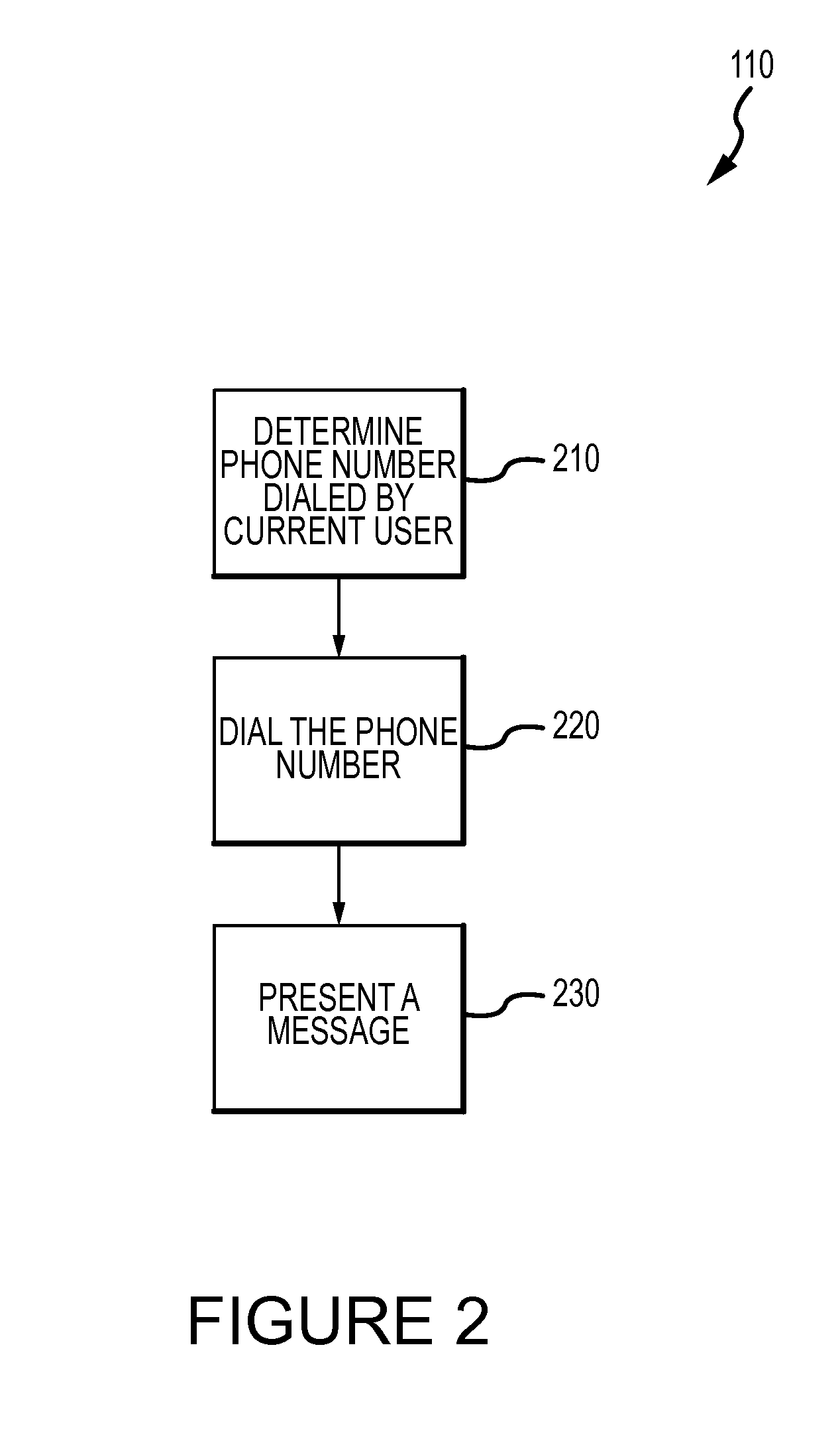
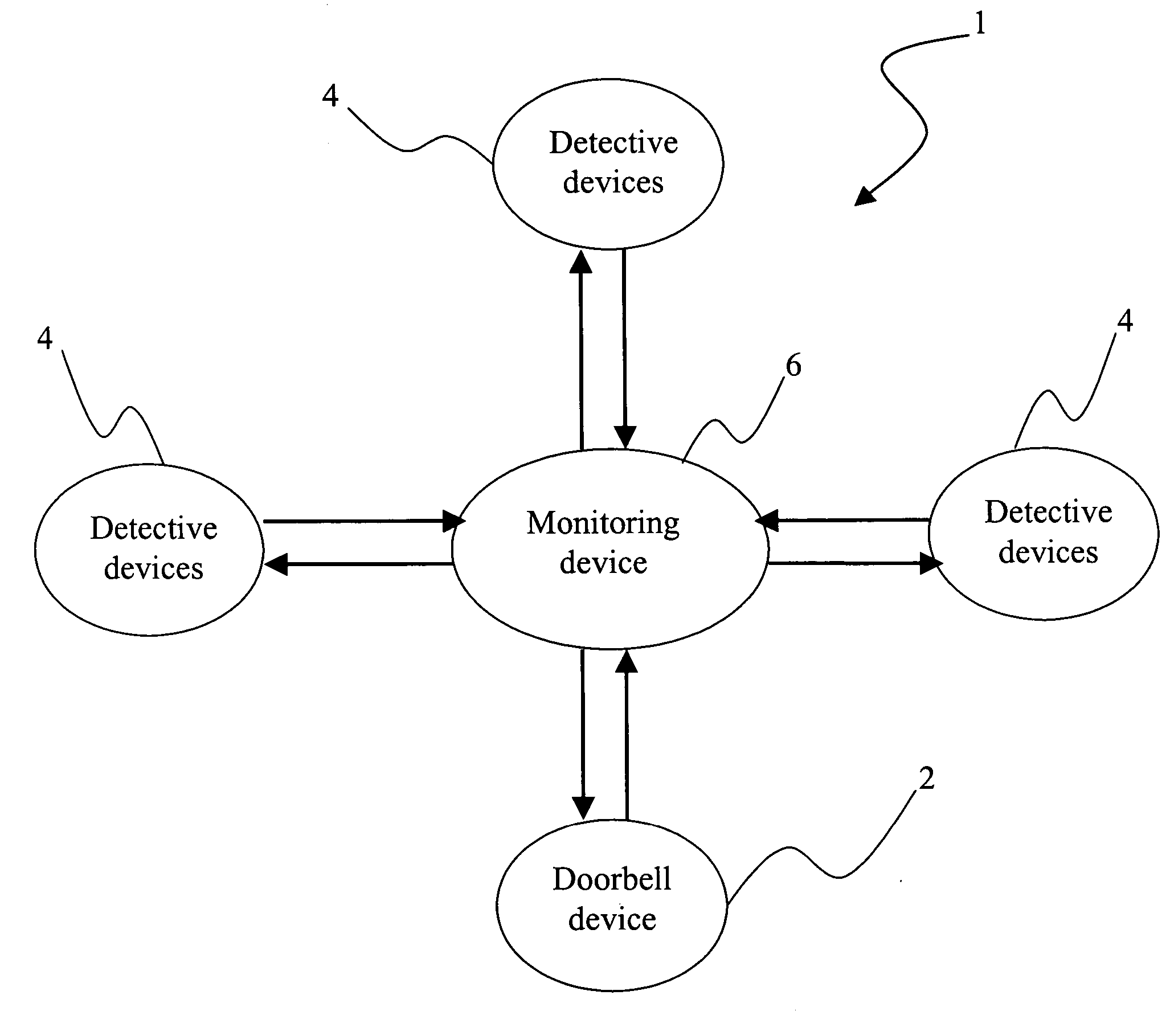
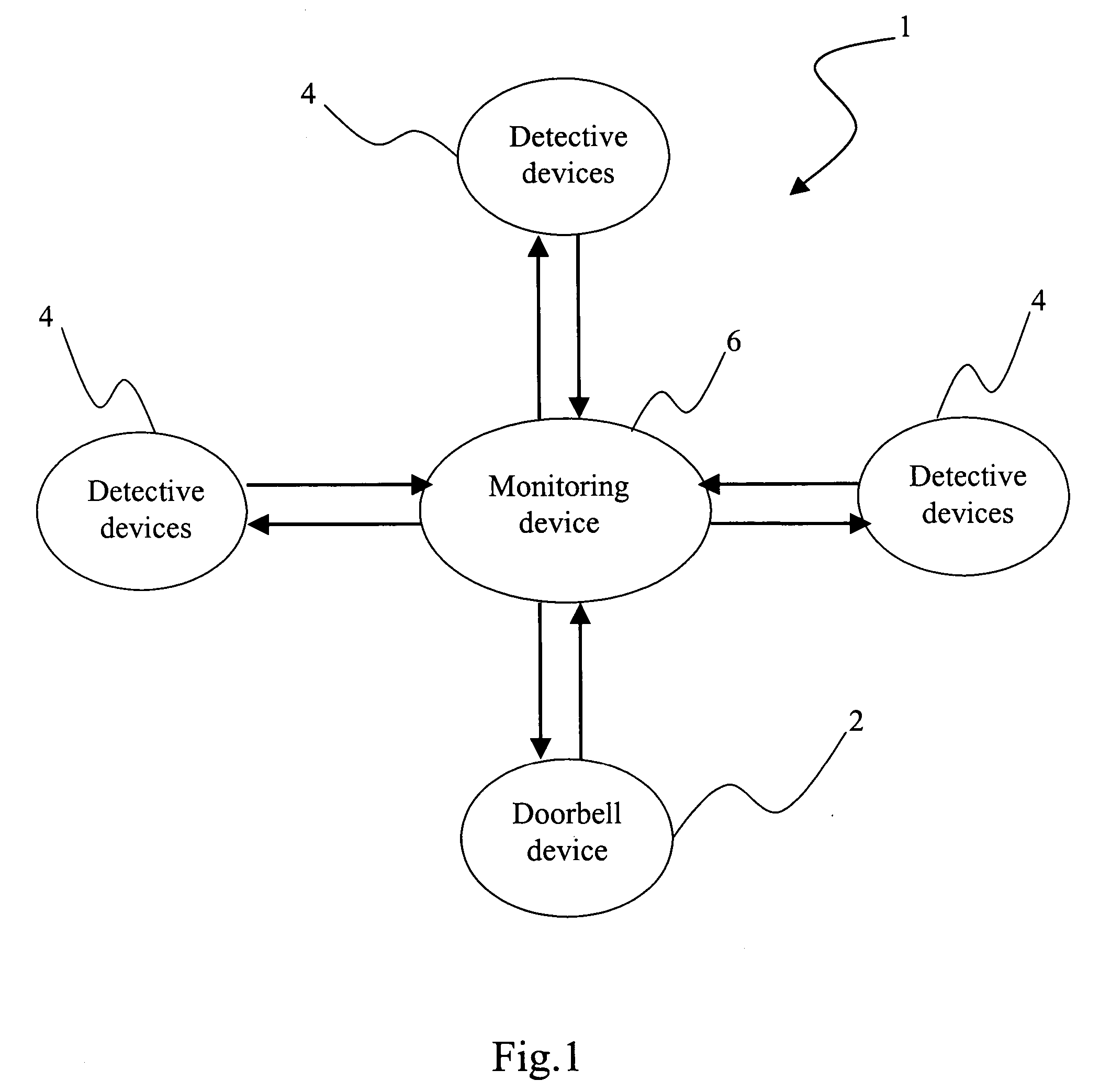
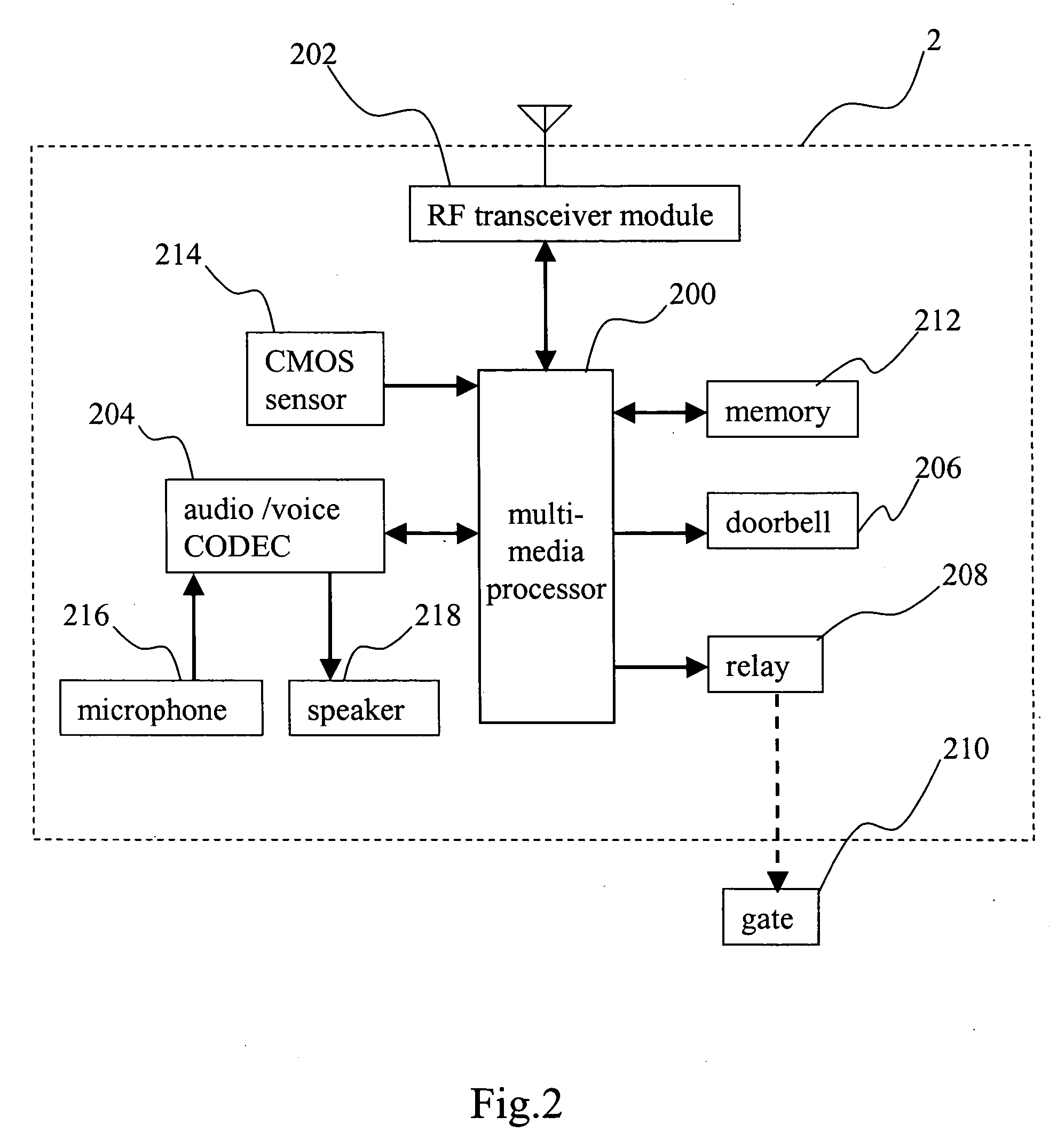
Wireless audio-video doorbell monitoring system
InactiveUS20060139449A1Avoid difficultyEnergy efficient ICTColor television detailsDoorbellTime delays
The present invention pertains to a wireless audio-video doorbell monitoring system, wherein a portable monitoring device administrates a doorbell device and detective devices. After initiation, the monitoring device calls other nearby devices to form a wireless network via a wireless broadcasting way, and then the monitoring device administrates each device to perform the doorbell or detection function. Via the automatic setup and simple operating interface, the present invention enables a general family to be free from a complex operational procedure. In the present invention, the detective device can sense the image and sound of the monitored regions, which is sent to a display panel and a speaker of the monitoring device without a time lag. Accordingly, the present invention provides an instantaneously-displaying and easy-operated wireless audio-video doorbell monitoring system, which is easy installed, automatically set up, highly securing, able to reduce the power consumption efficiently and suitable for a general family usage.
Owner:TRANWO TECH
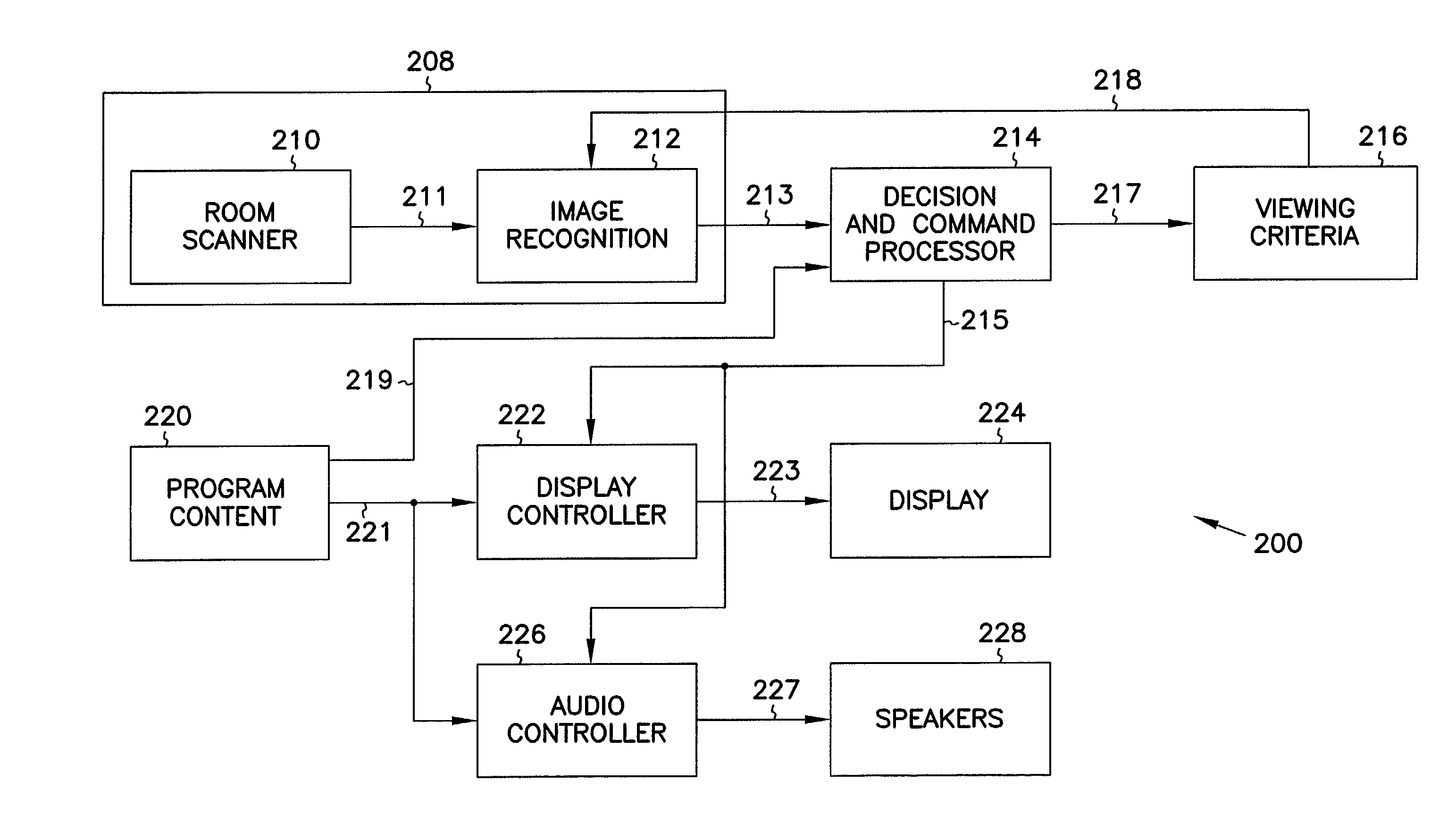
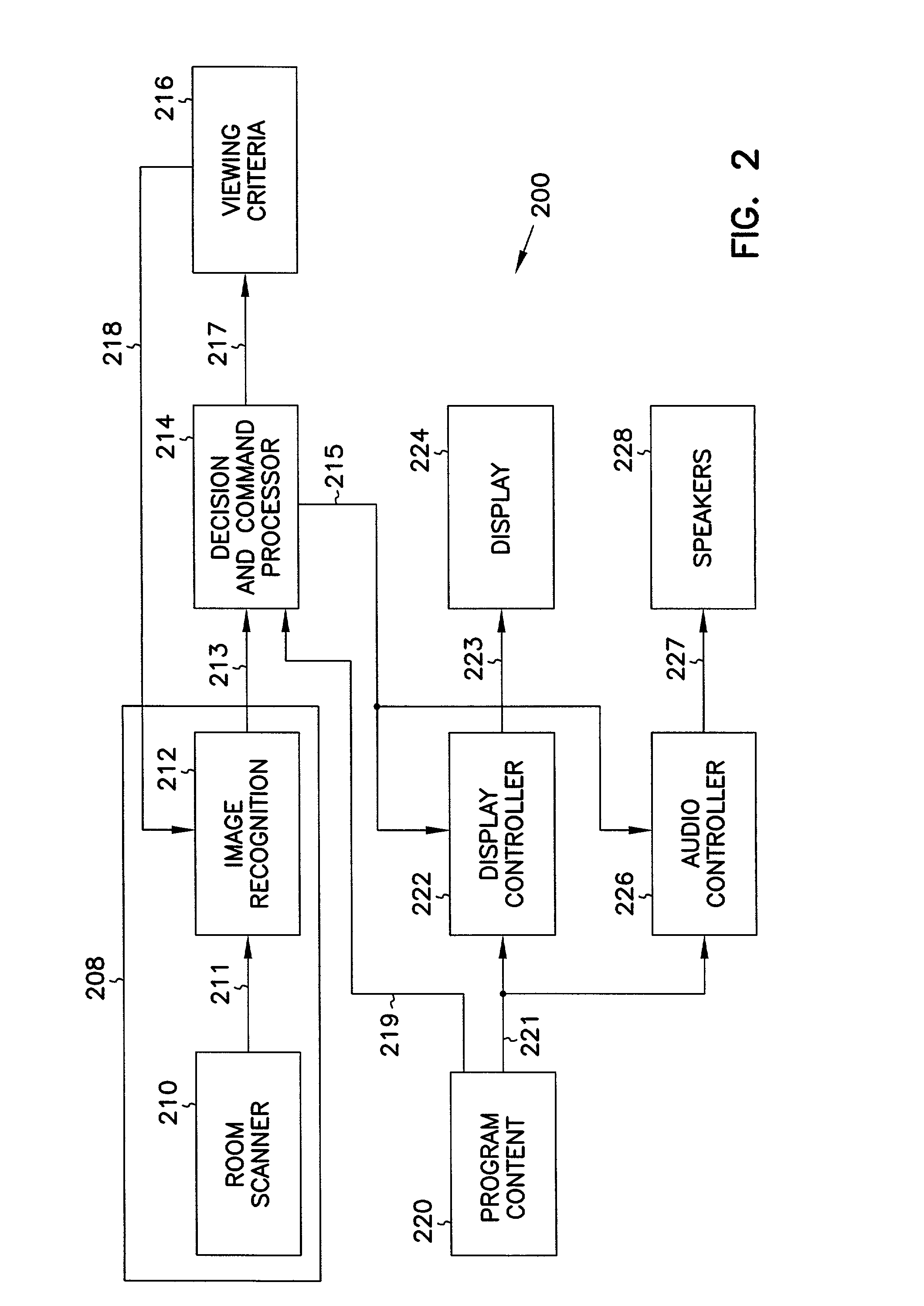
Apparatus and method for user-based control of television content
InactiveUS7134130B1Analogue secracy/subscription systemsBroadcast components for monitoring/identification/recognitionDisplay deviceHuman–computer interaction
An apparatus and method for controlling access to information based on content of the information and user identity. The apparatus includes a video display that displays the information to be viewable by one or more users. A user-recognition input device determines that an additional user is newly present in a given area having access to the display. A blocking device coupled to the user-recognition input device selectively blocks display of the information based on whether the additional user is newly present. In one embodiment, the user-recognition input device includes a video input device, and a feature recognition device operable to distinguish between two or more users based on one or more video features of the users. In another embodiment, the user-recognition input device includes an audio input device, and an audio feature recognition device operable to distinguish when an additional user arrives. In yet another embodiment, the user-recognition input device includes a movement-detection device operable to distinguish when an additional user arrives.
Owner:GATEWAY
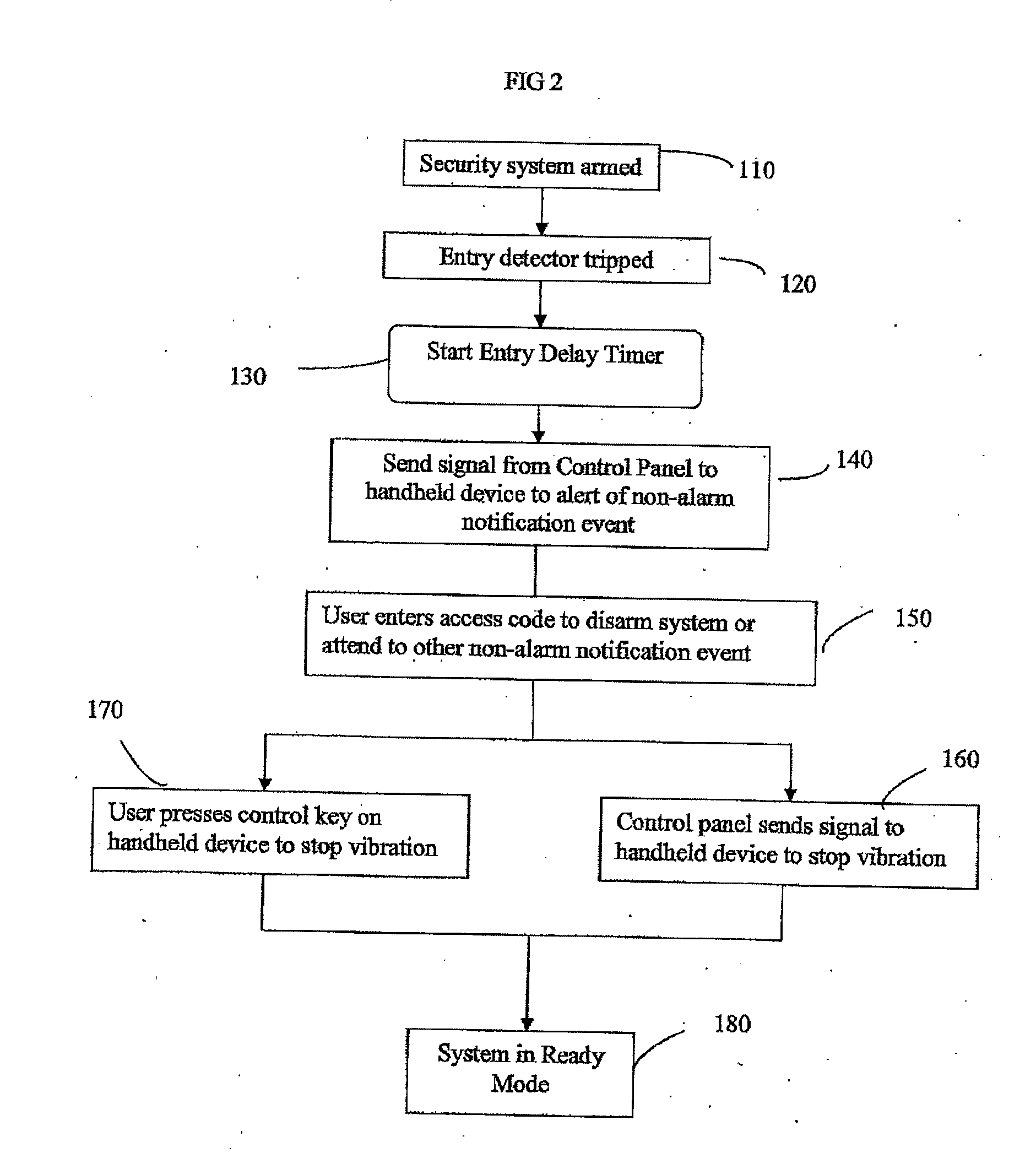
Security system with keyfob alert notification
A system and method are provided for notifying a hearing impaired user of one of a plurality of qualified events via a personal device rather than an audible alert to avoid unnecessary false alarms. The security system includes at least one detection device for monitoring a portion of the premises and a control panel configured to communicate with the at least one detection device. A personal device communicates with the control panel where the personal device is configured to mechanically vibrate upon receipt of a signal from the control panel representing a qualified event associated with the security system.
Owner:TYCO SAFETY PRODS CANADA
Photographing apparatus
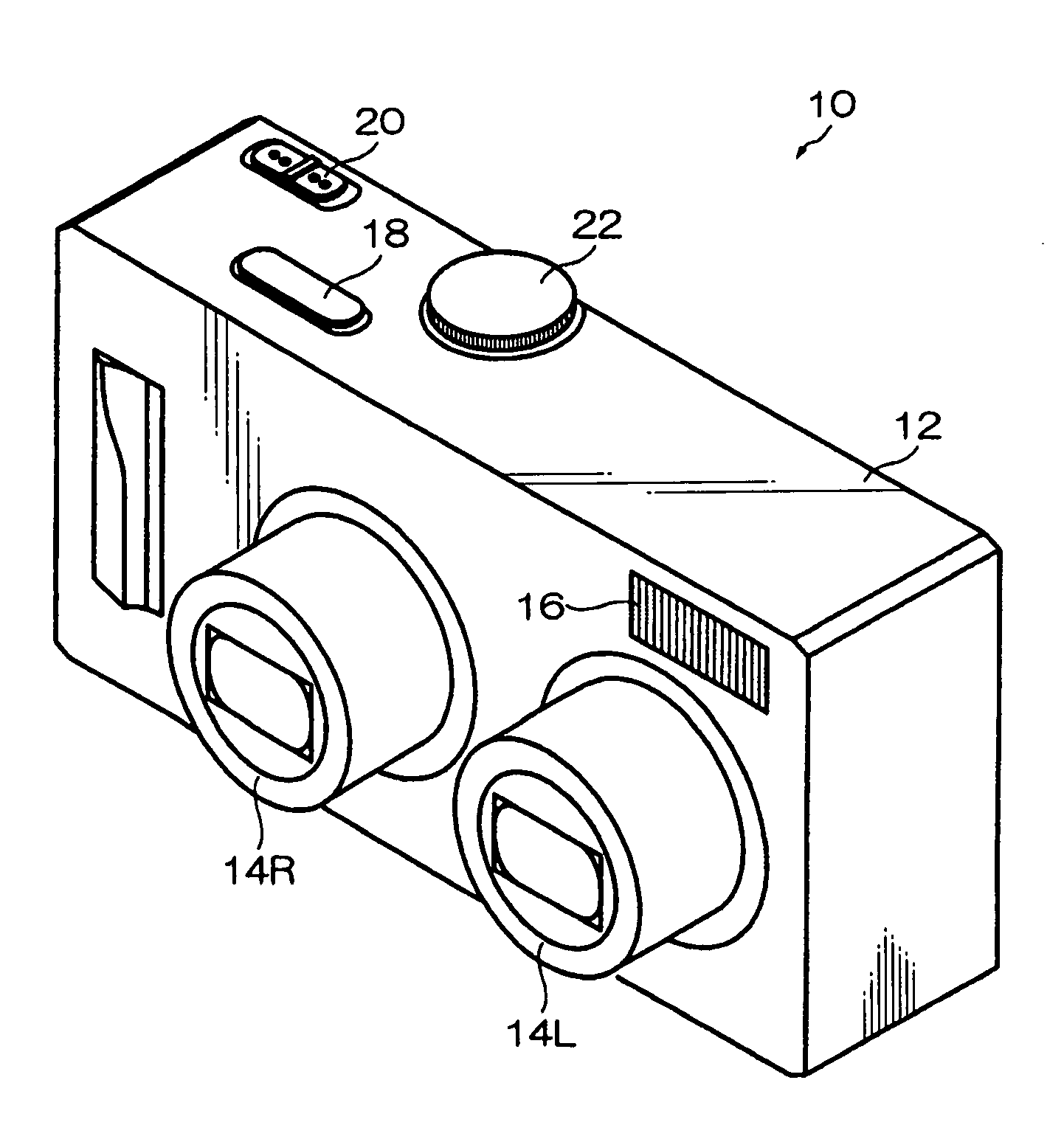
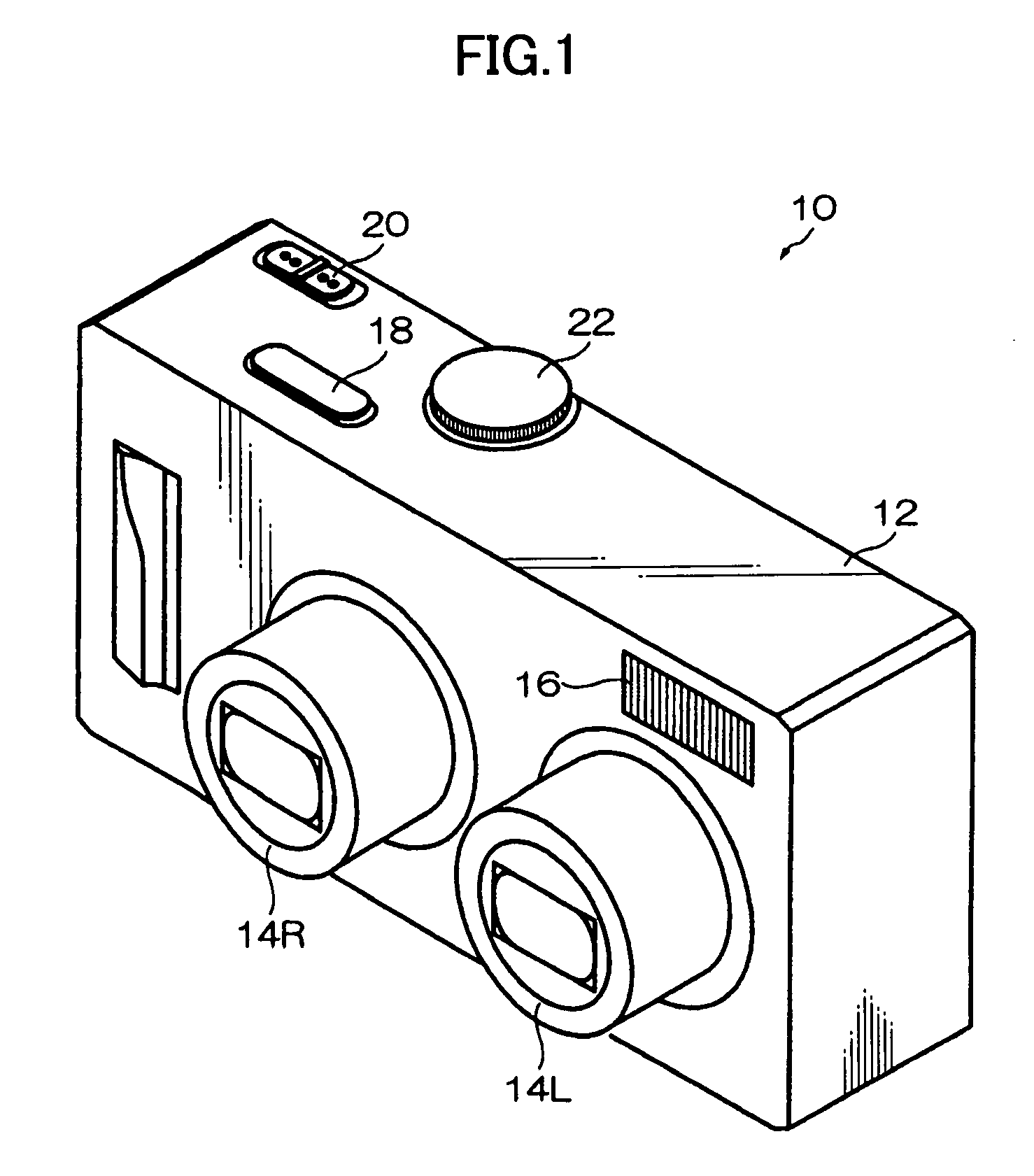
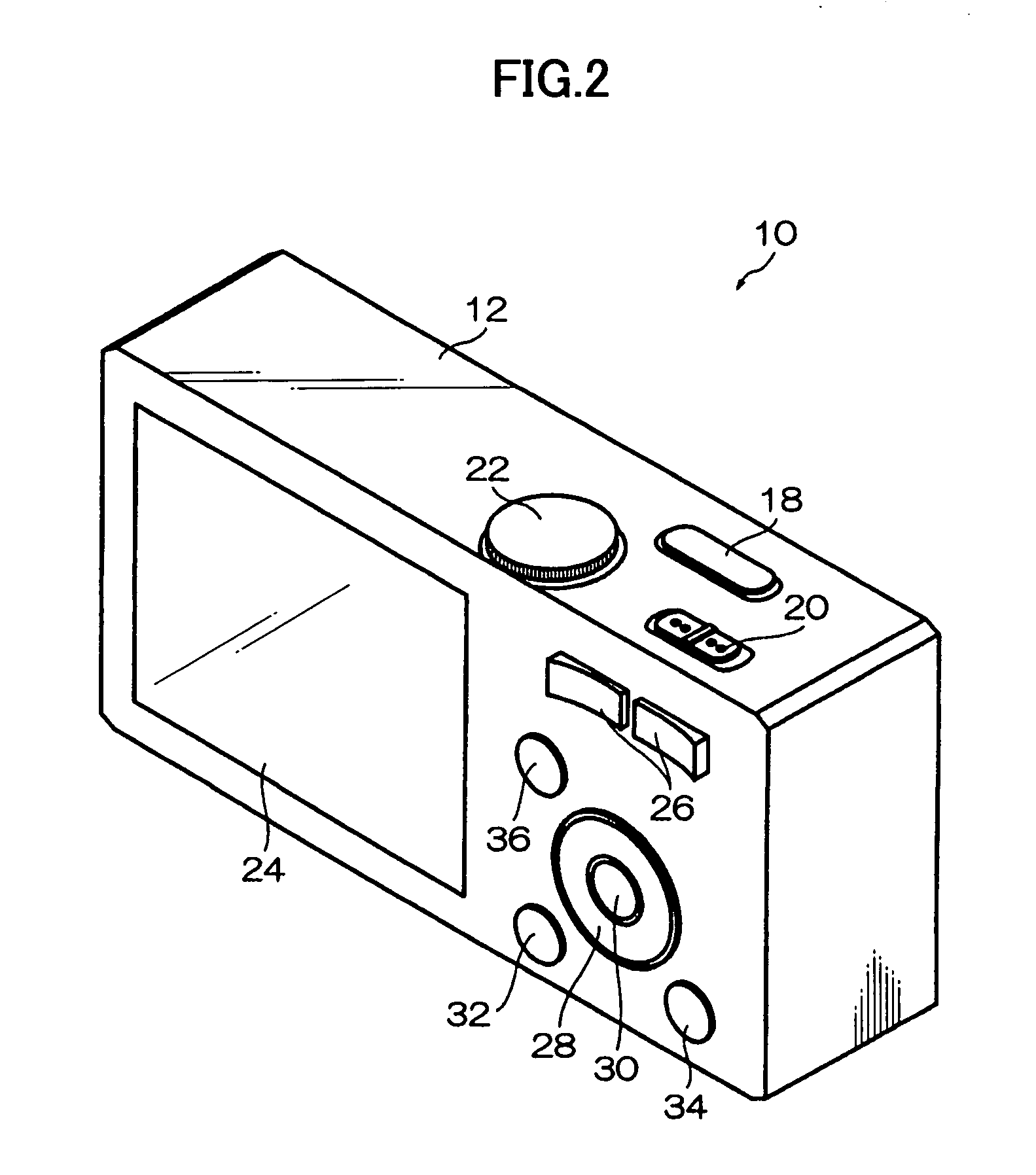
ActiveUS20080131107A1Quality improvementSimply obtainedCharacter and pattern recognitionElectric digital data processingComputer graphics (images)Direction information
Photographing apparatus having a plurality of photographic optical systems, comprises: an attitude detecting device which detects an attitude of the apparatus body; a physical relationship information obtaining device which obtains information on physical relationship among the photographic optical systems setting; and a shooting direction information obtaining device which obtains information on the shooting direction of each of the photographic optical systems. The images photographed by each of the photographic optical systems may be corrected based on information on the attitude of the apparatus body, information on the physical relationship among the photographic optical systems, and information on the shooting direction of each of the photographic optical systems. Thereby it enables to easily correct tilt and the like of the images.
Owner:FUJIFILM CORP
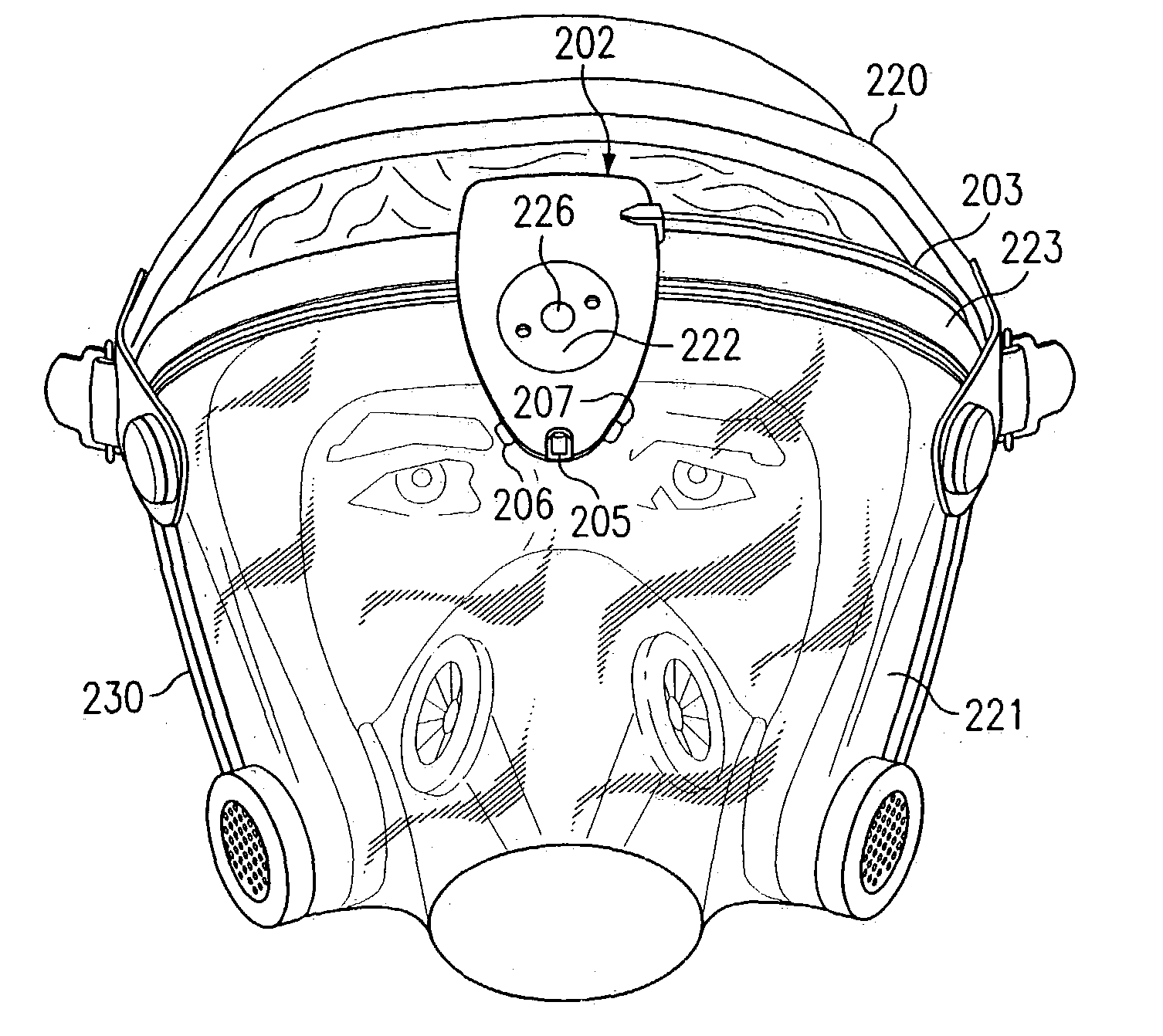
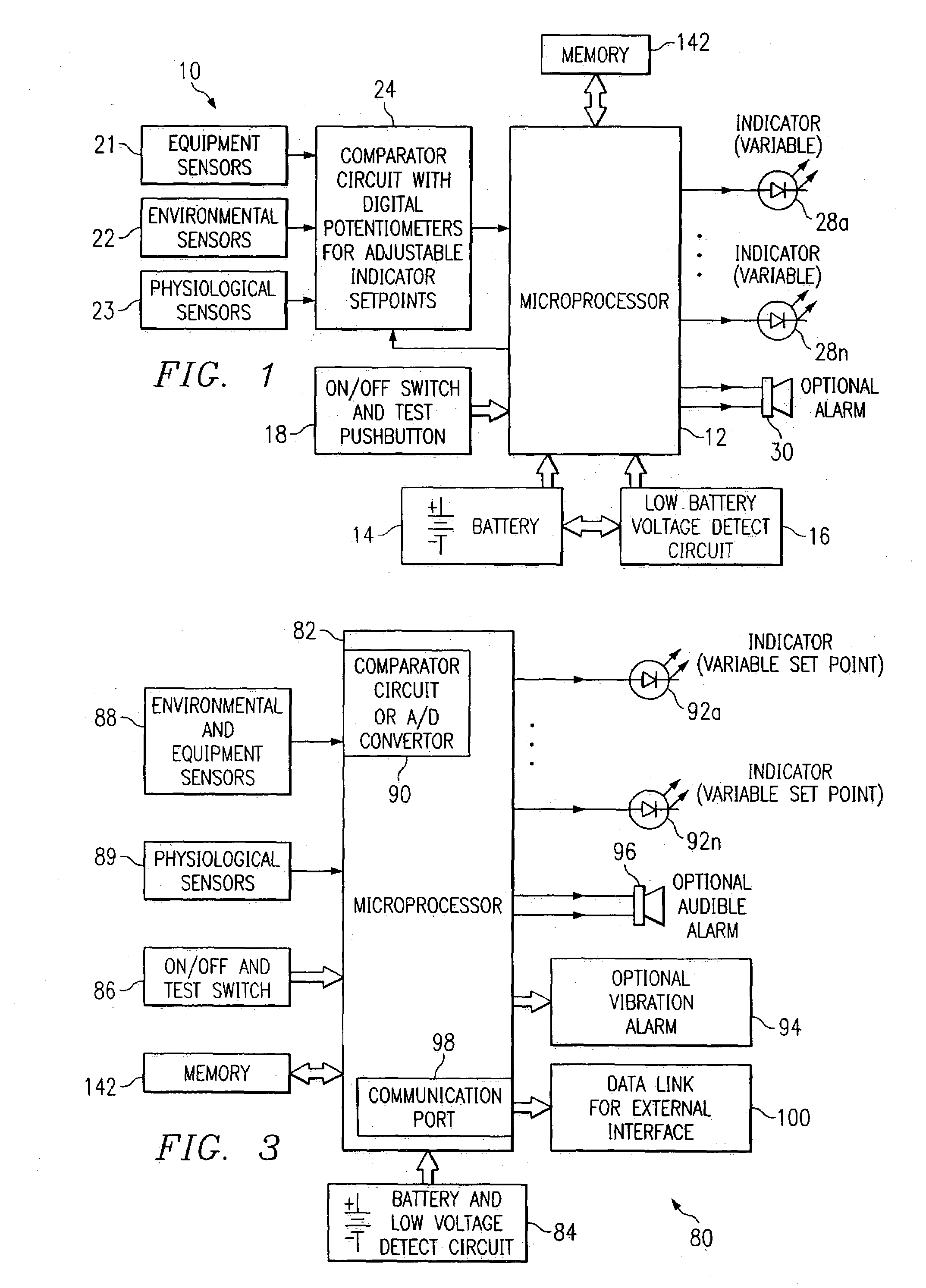
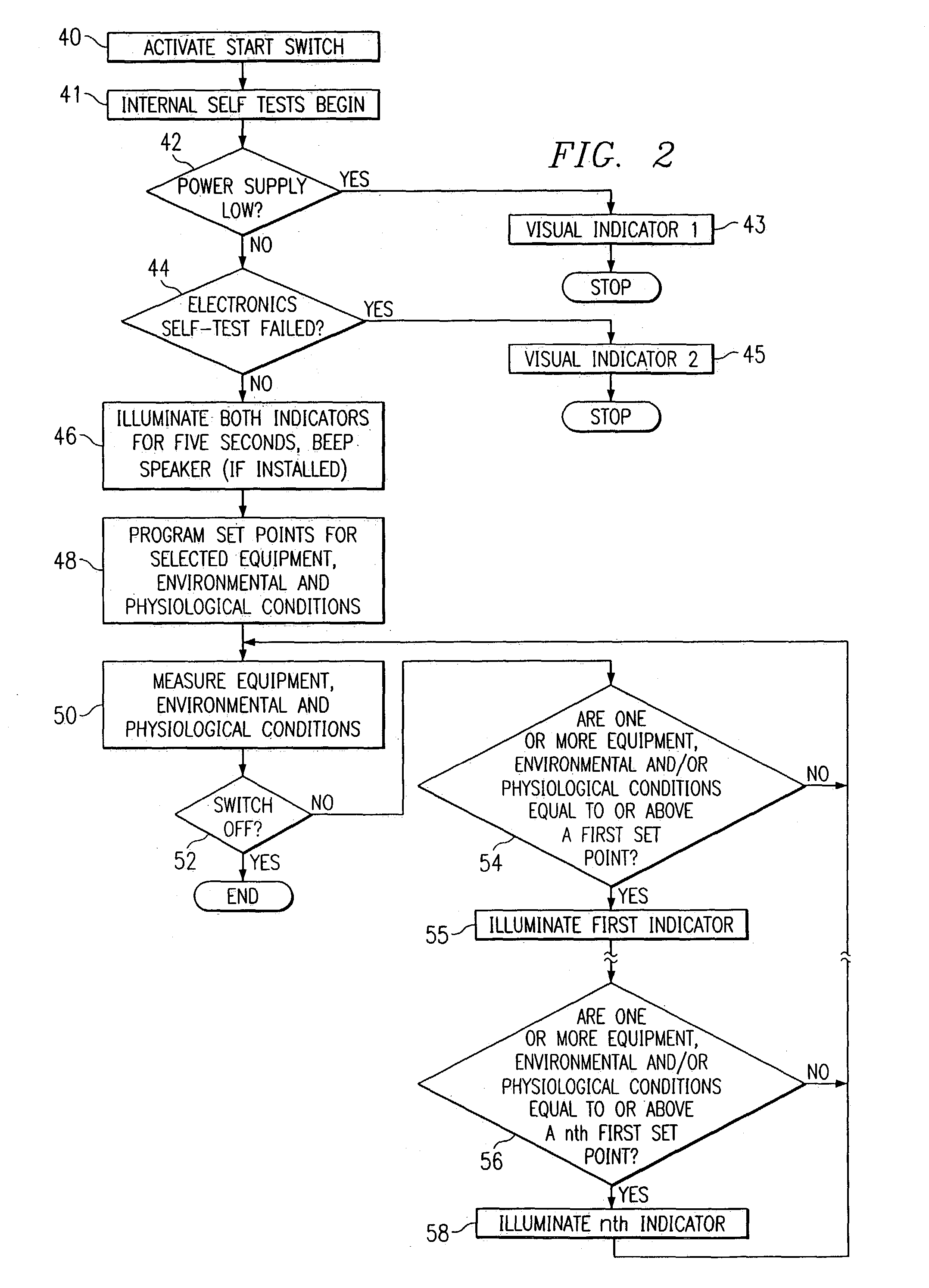
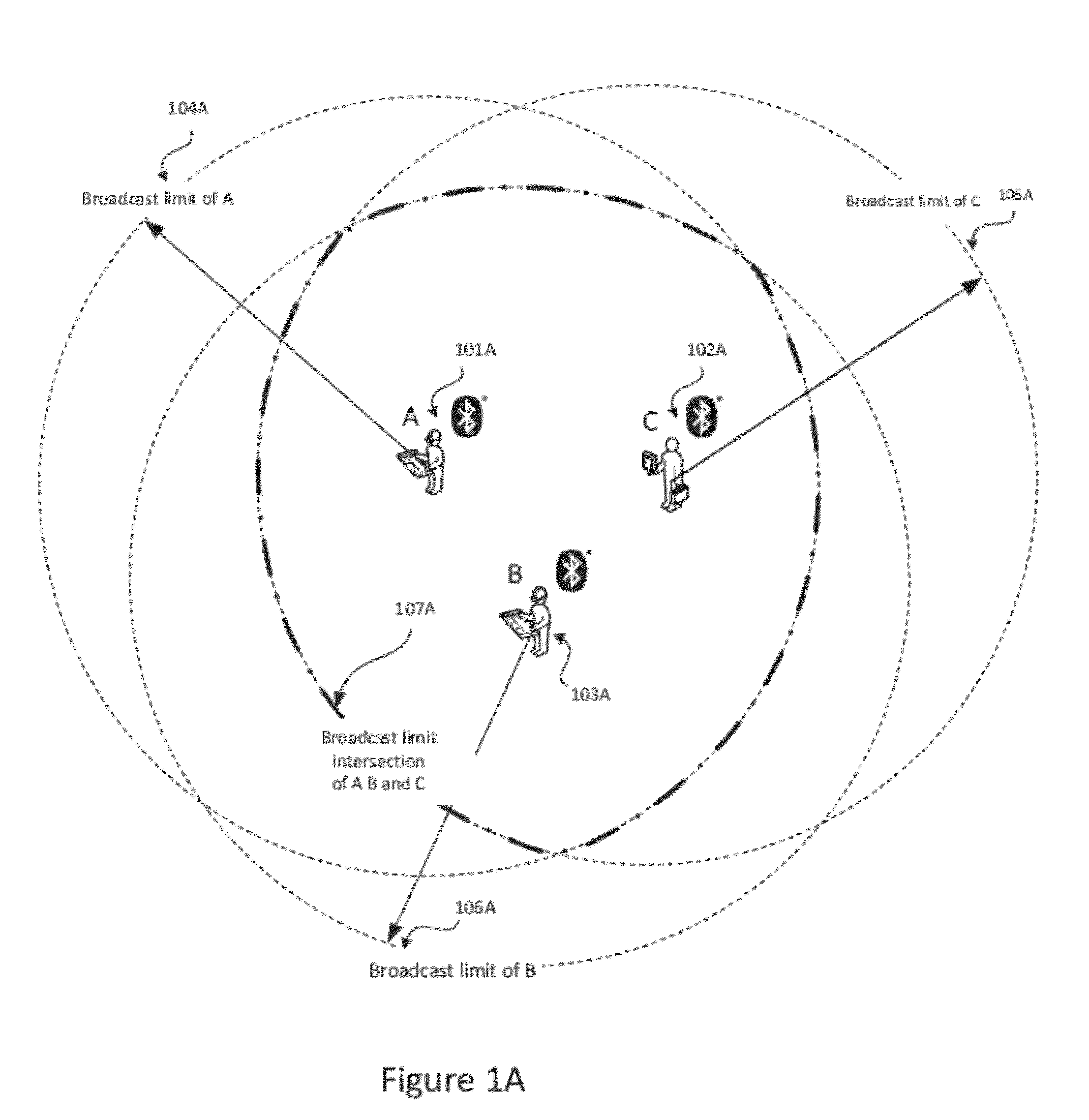
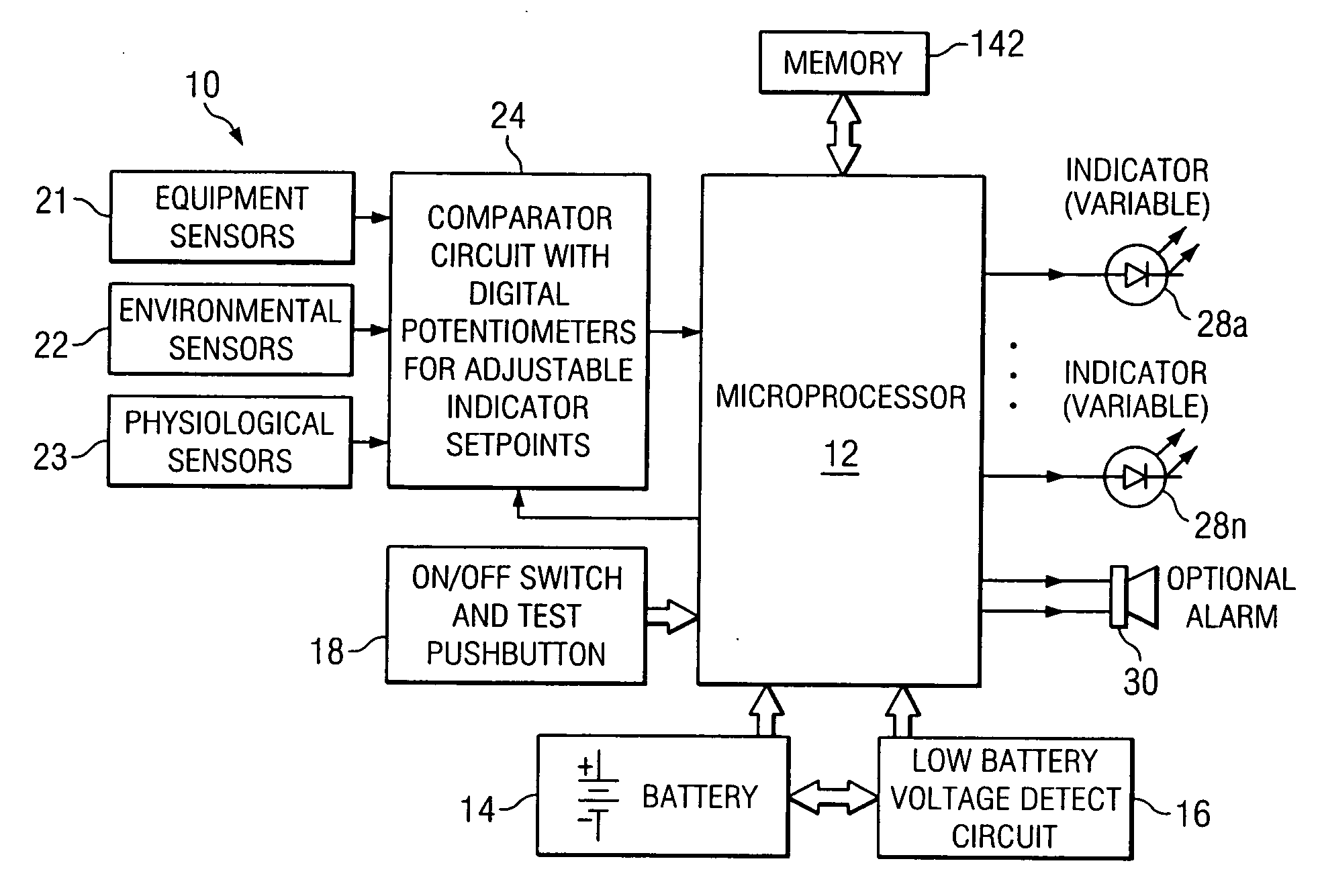
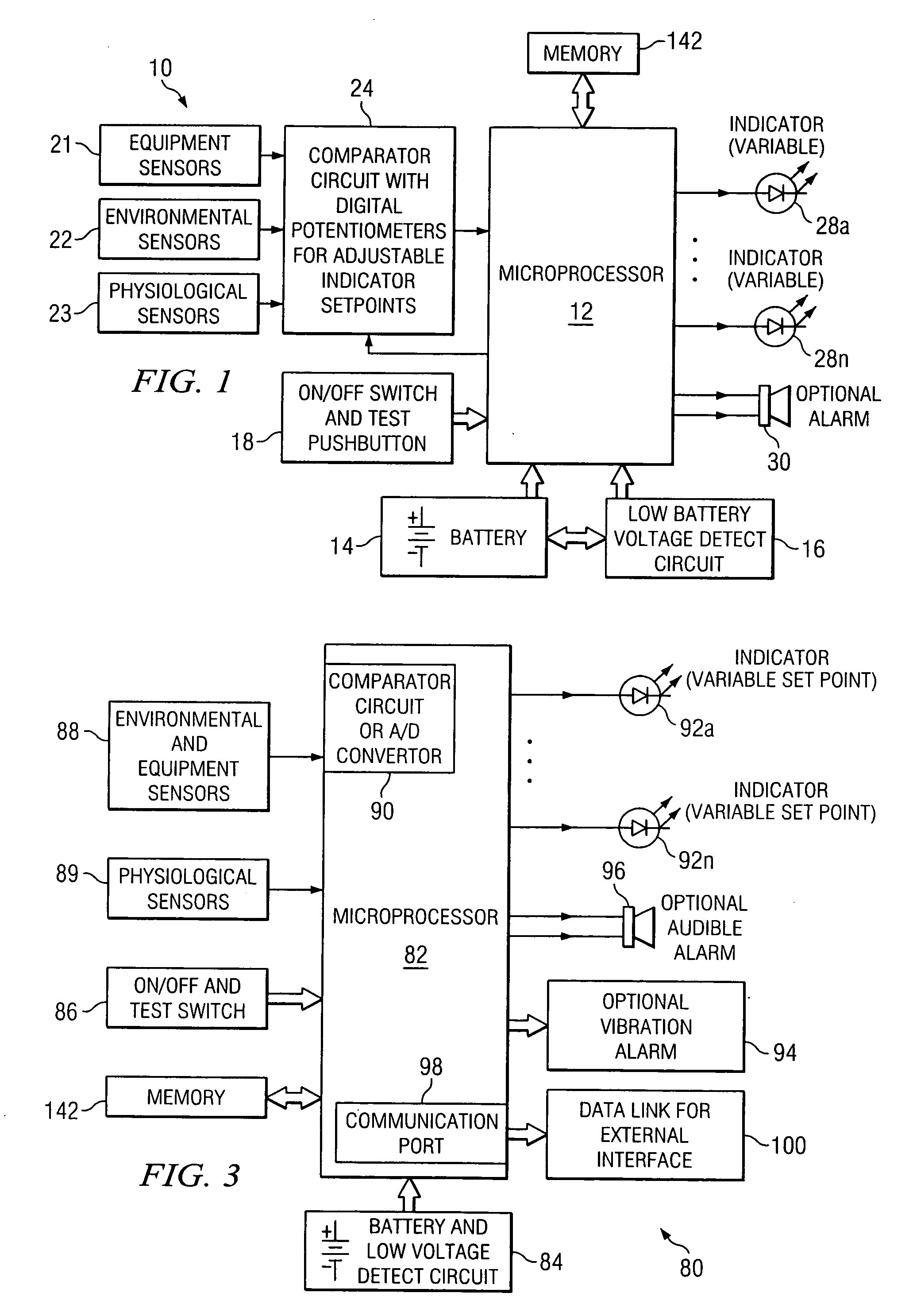
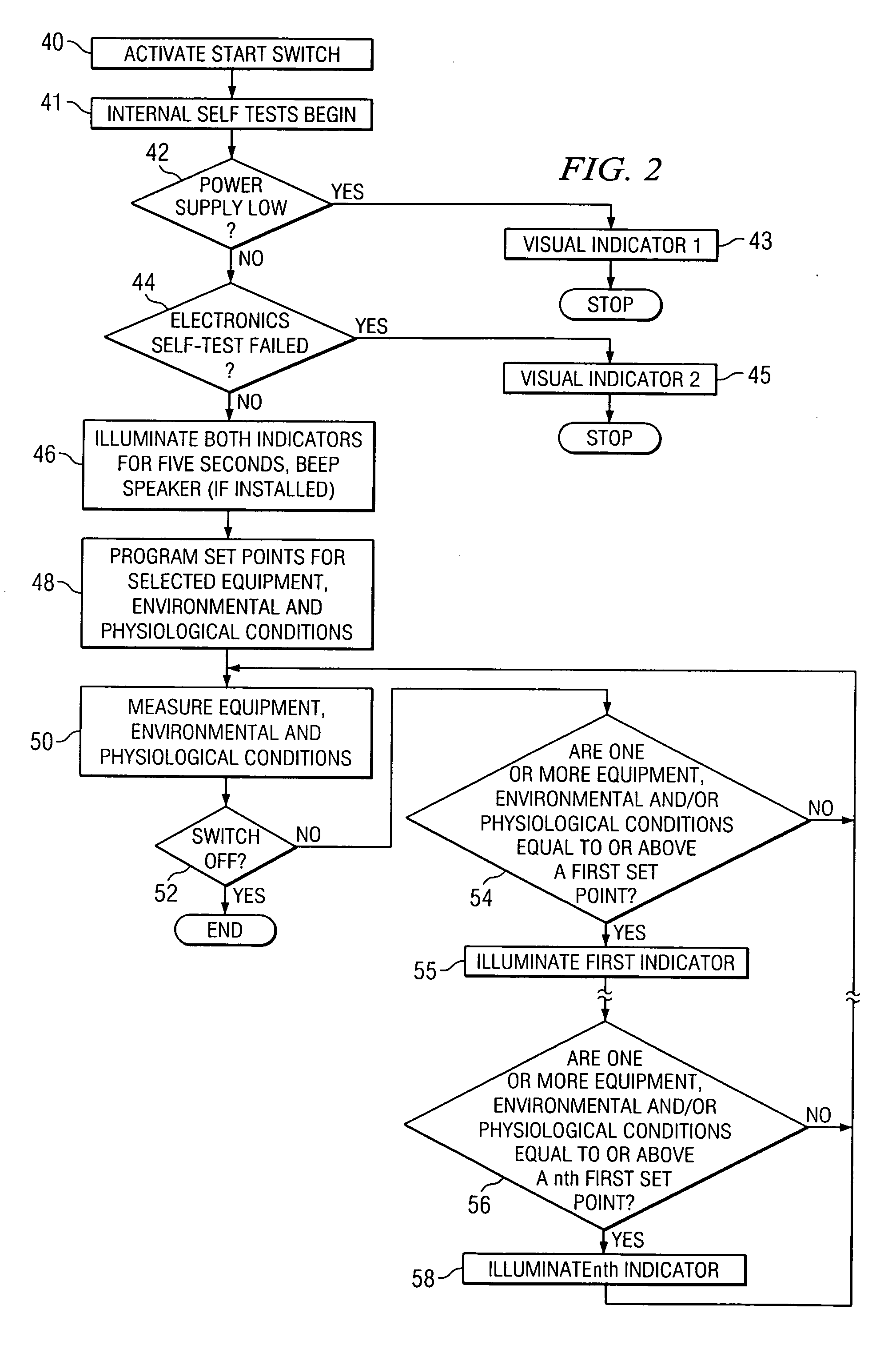
System and method for identifying, monitoring and evaluating equipment, environmental and physiological conditions
InactiveUS6995665B2Reduce in quantityAvoid injuryRespiratorsOperating means/releasing devices for valvesEngineeringHazard potential
A system and method are disclosed for identifying monitoring and evaluating hazardous or potentially hazardous conditions. The system may be worn by safety personnel to detect equipment conditions such as low power supply, environmental conditions such as ambient temperature and / or physiological conditions such as heart rate of a wearer. The system further includes a control unit having electronics operable to communicate signals associated with equipment, environmental and physiological conditions.
Owner:MINE SAFETY APPLIANCES CO
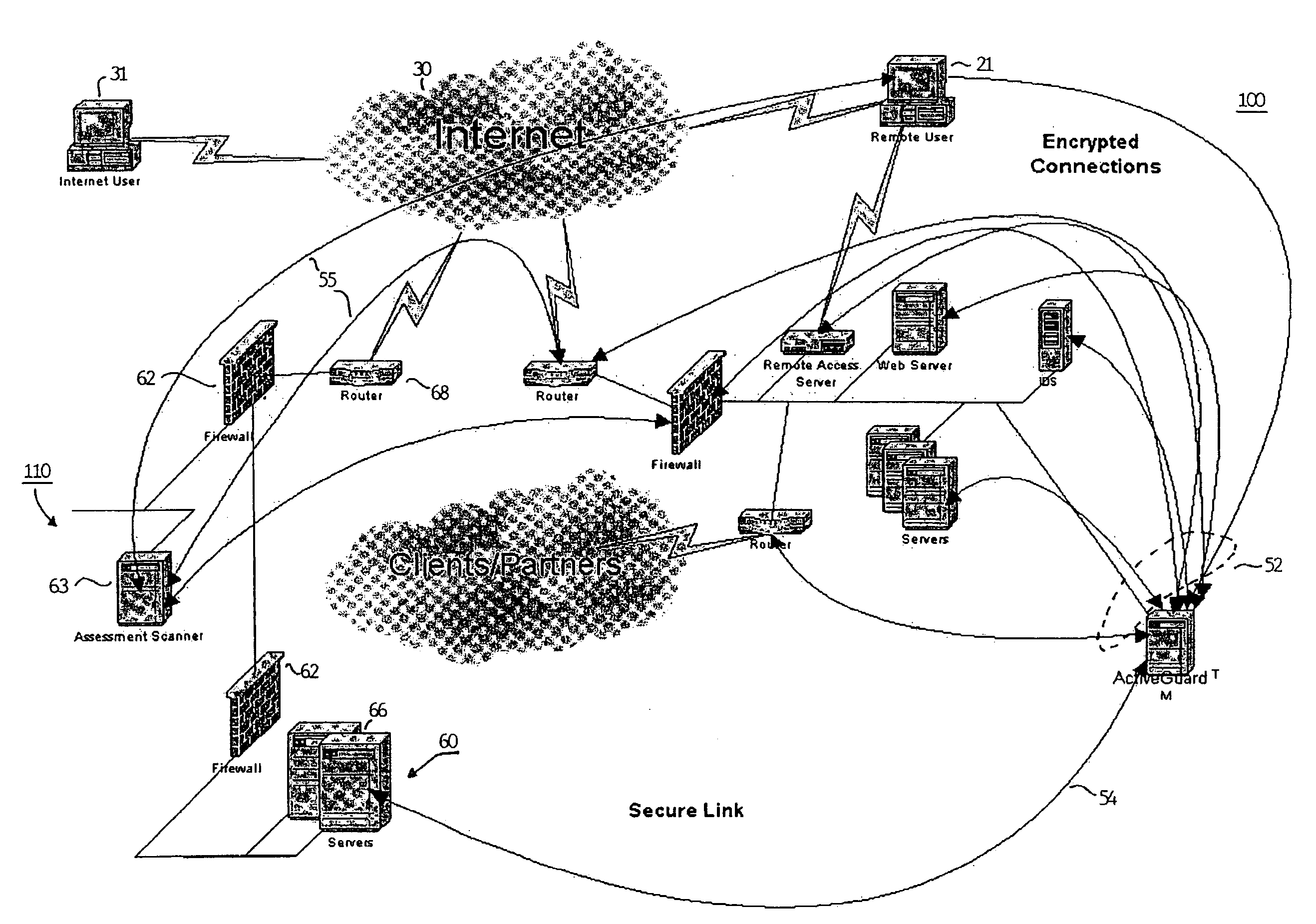
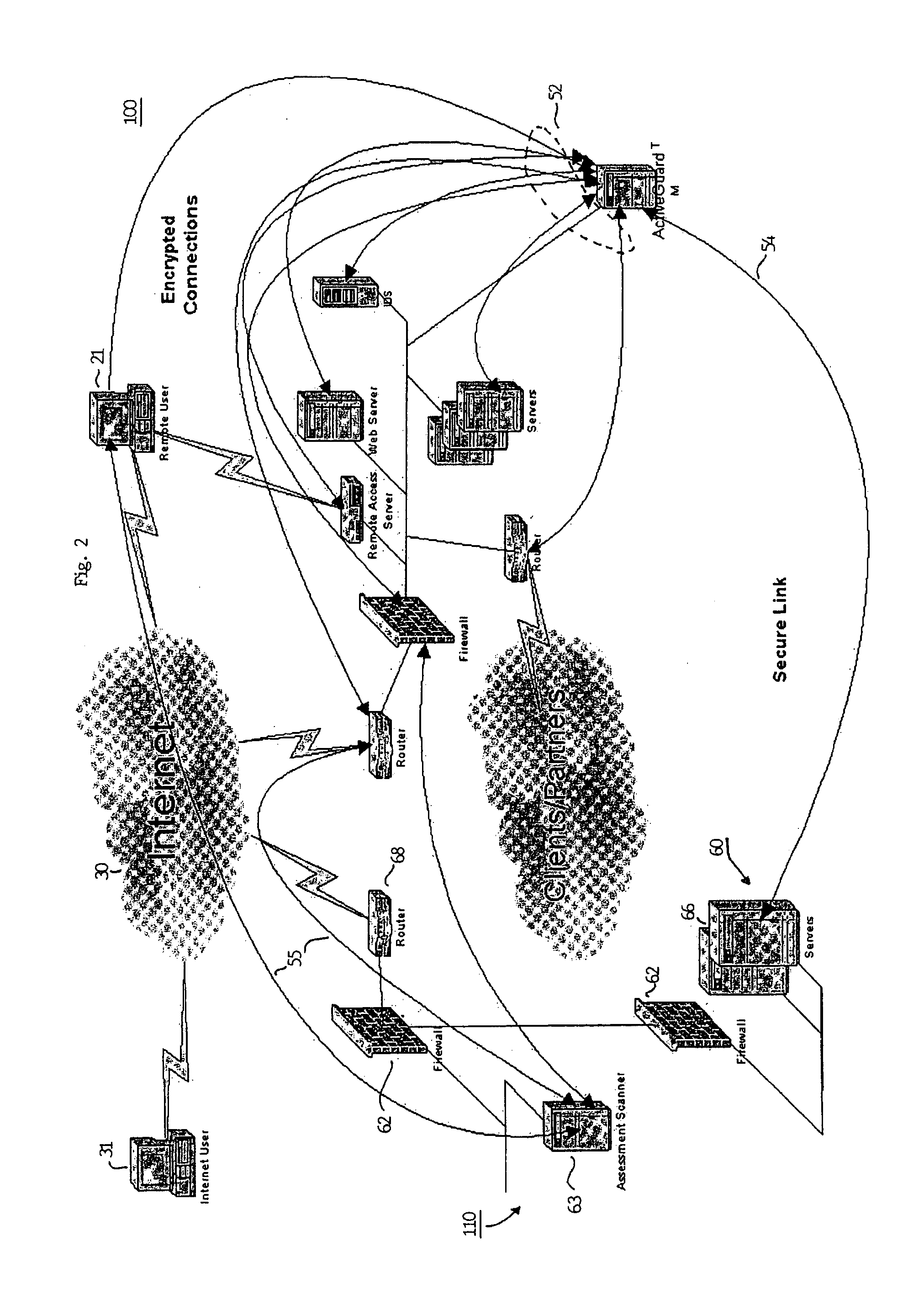
Method and apparatus for verifying the integrity and security of computer networks and implementing counter measures
InactiveUS6988208B2Mitigate or thwart suspected intruder attacks on the target networkMemory loss protectionDigital data processing detailsCountermeasureSecurity system
A method and apparatus for verifying the integrity of devices on a target network. The apparatus has security subsystems and a master security system hierarchically connected to the security subsystems via a secure link. The target network includes various intrusion detection devices, which may be part of the security subsystem. Each intrusion detection device generates a plurality of event messages when an attack on the network is detected. The security subsystem collects these event messages, correlates, and analyzes them, and performs network scanning processes. If certain events warrant additional scrutiny, they are uploaded to the master security system for review.
Owner:SICORTEX
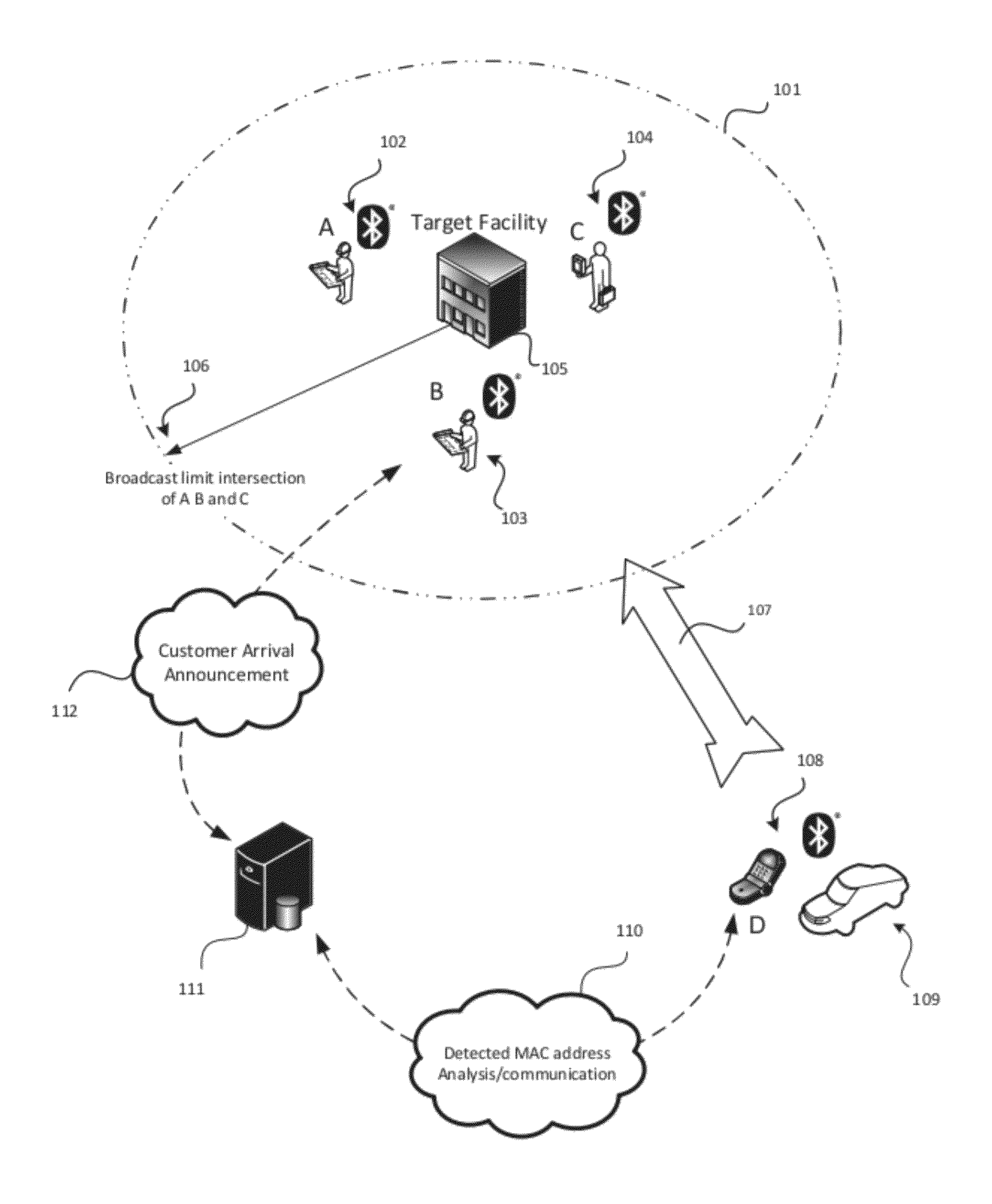
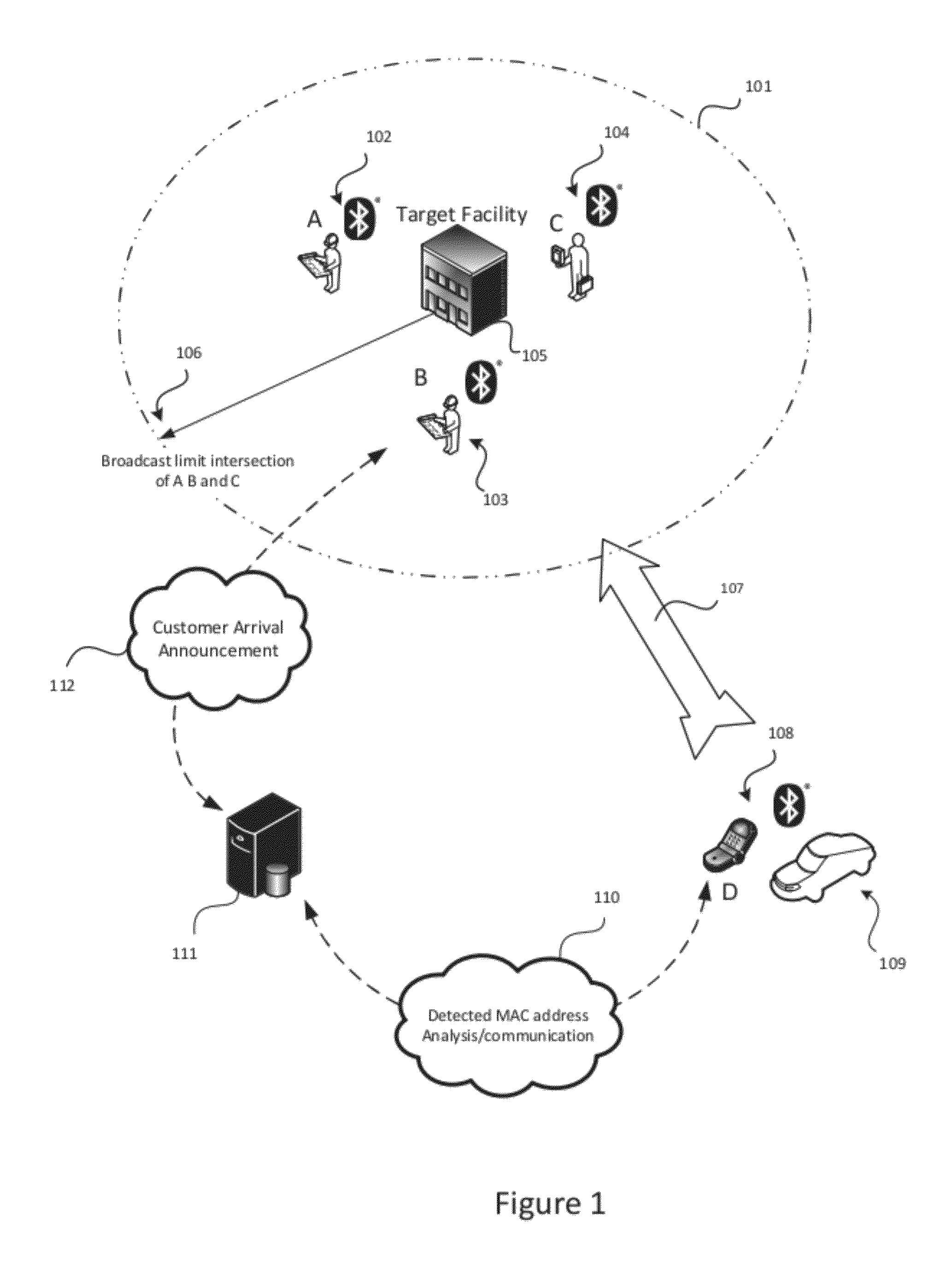
System and Method for Proximity Detection
InactiveUS20120235865A1Improving the accuracy of the confidence computationImprove accuracyDirection finders using radio wavesSpecial service for subscribersFault toleranceConfidence interval
The present invention is for a system and method for determining the proximity of a mobile device to a location without the use of a satellite based or other location awareness system, nor a stationary beacon of any kind Instead, the mobile device monitors radio frequency broadcast identification codes from nearby mobile devices, and determines if the set of detected identification codes is sufficiently similar to a weighted set of identification codes attributed to specified location. If the calculation of similarity meets the confidence conditions of the system, notification is made that the customer or visitor has arrived. The invention utilizes a combination of confidence interval computation, machine learning, and fault tolerance mechanisms to optimize the success of correctly detecting that the device is near the relevant location.
Owner:KAARYA
Equipment and method for identifying, monitoring and evaluating equipment, environmental and physiological conditions
InactiveUS20060125623A1Reduce in quantityChemical protectionHeat protectionEngineeringHazard potential
A system and method are disclosed for identifying monitoring and evaluating hazardous or potentially hazardous conditions. The system may be worn by safety personnel to detect equipment conditions such as low power supply, environmental conditions such as ambient temperature and / or physiological conditions such as heart rate of a wearer. The system may further include a control unit having electronics operable to communicate signals associated with equipment, environmental and physiological conditions.
Owner:MINE SAFETY APPLIANCES CO
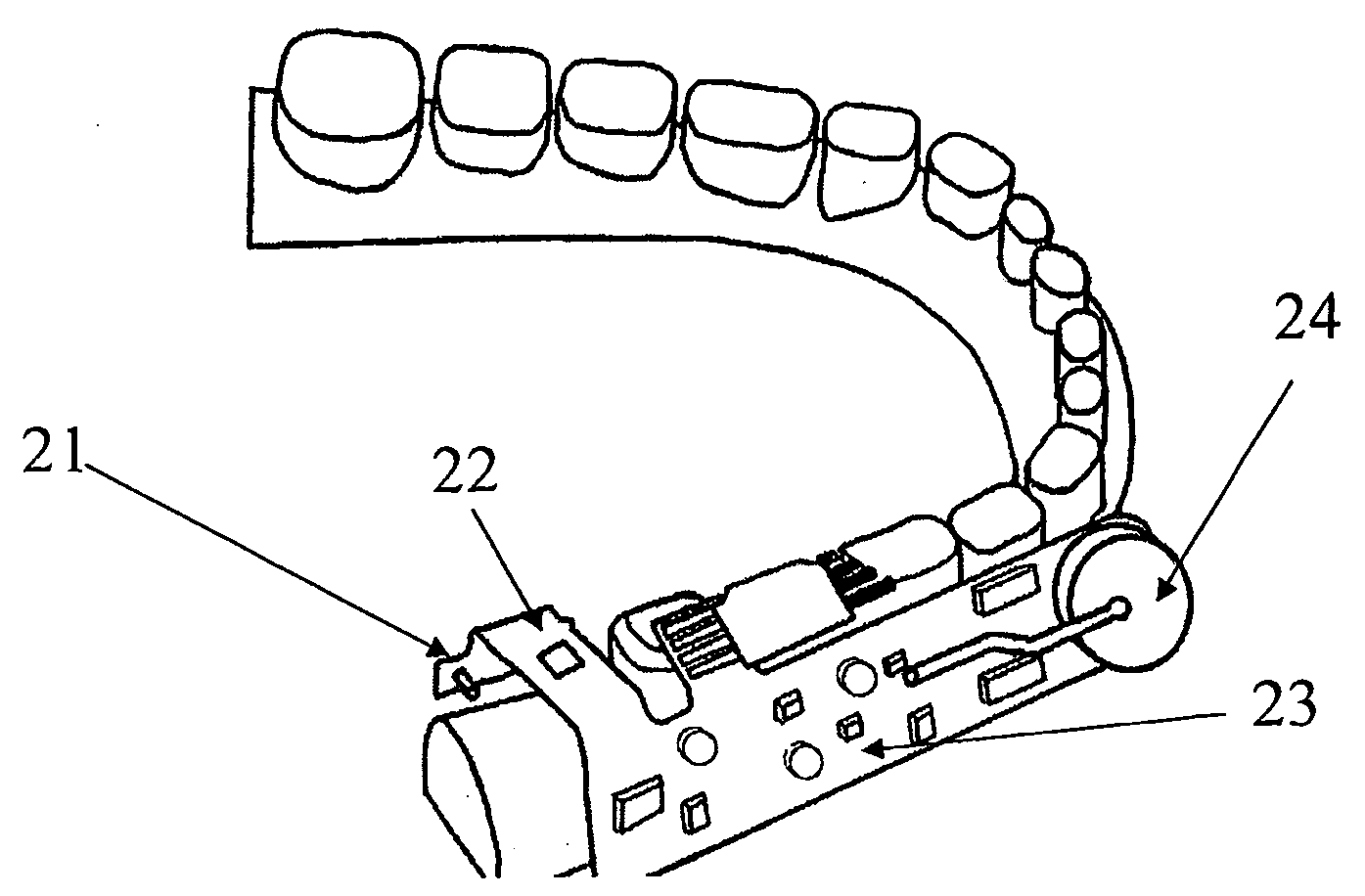
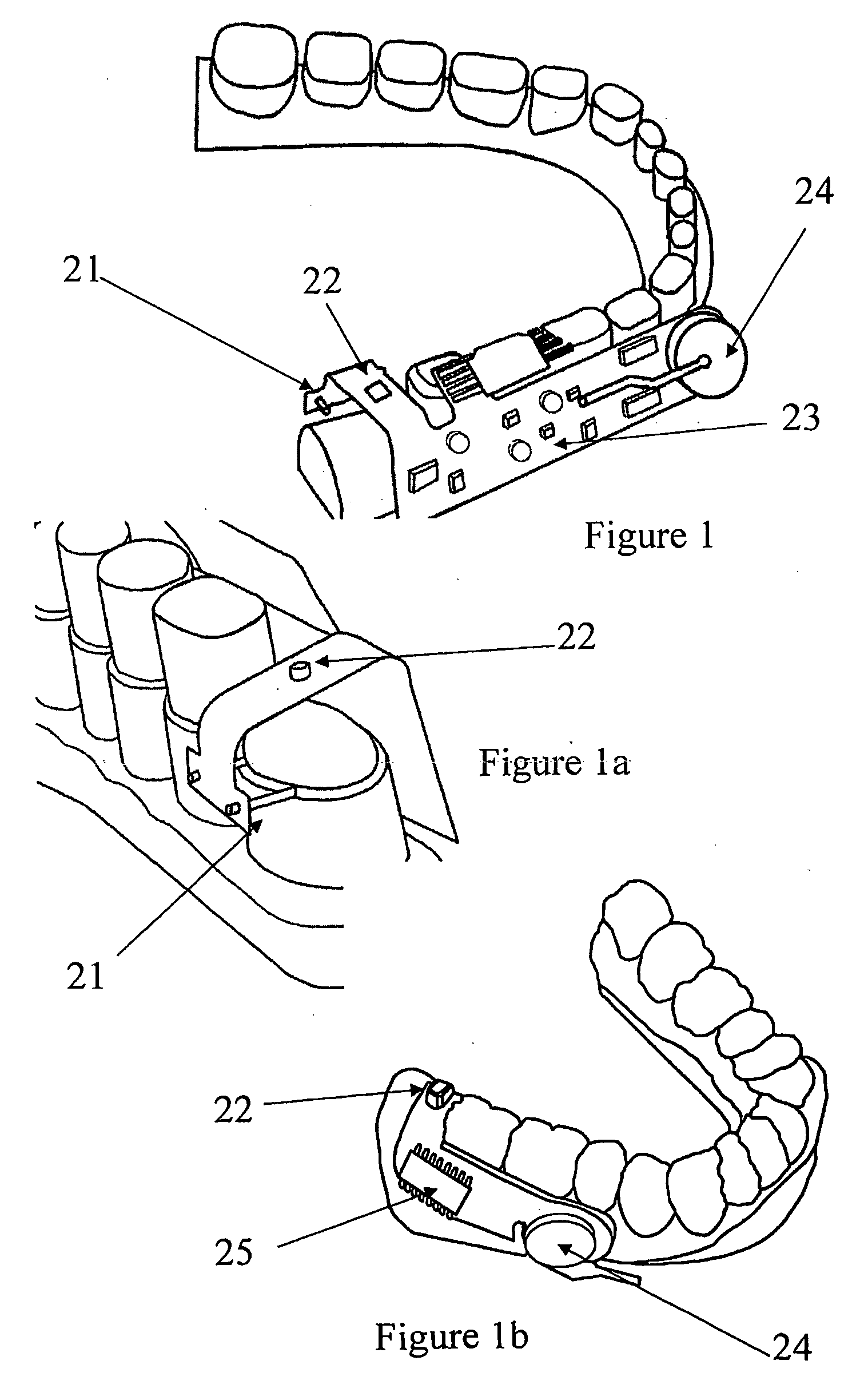
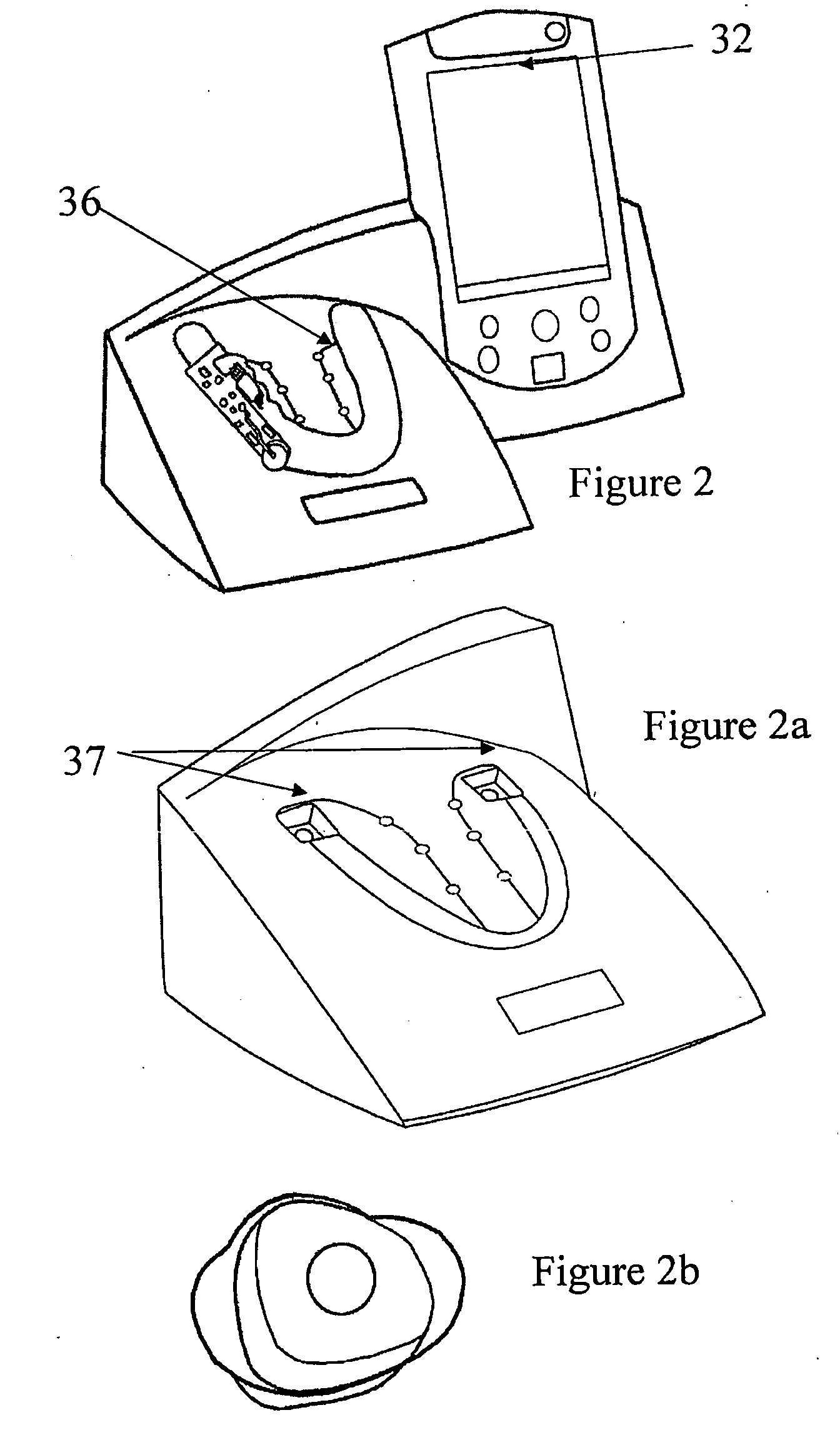
Manufacturing methods, testing methods, and testers for intra-oral electronically embedded devices
InactiveUS20090210032A1Minimize power consumptionLow power saving modeHead electrodesSnoring preventionDrying mouthWhole body
The invention is directed to manufacturing and testing methods of electronic intraoral devices for diagnose, monitor and treat local and systemic diseases and conditions for humans and animals. More specifically, the current invention deals with manufacturing techniques, testing methods and a testing apparatus of mainly three types of intra-oral devices: (a) electro-stimulators for various applications such as treatment of dry mouth by stimulating saliva secretion, apnea, sleeping disorders, eating disorders (obesity, anorexia, etc.) dysphagia and others, (b) drug delivery devices; and (c) bio-sensing and monitoring devices. The common parts or the devices are: (1) art electronic module embedded in the device: (2) or a power source being embedded in the device; (3) the devices (or part of them) being placed in the oral cavity.
Owner:BEISKI BEN ZION +1
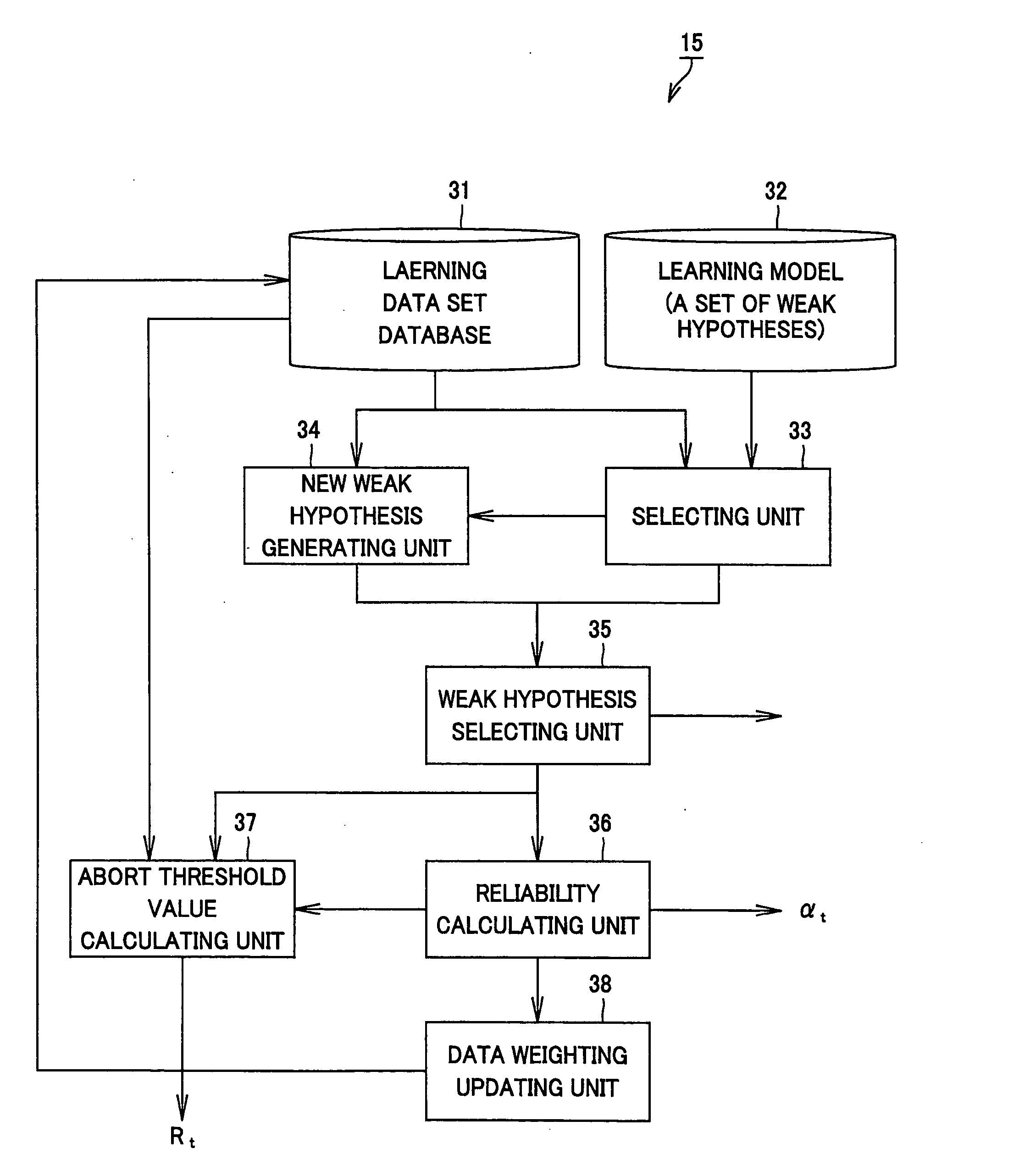
Weak hypothesis generation apparatus and method, learning apparatus and method, detection apparatus and method, facial expression learning apparatus and method, facial expression recognition apparatus and method, and robot apparatus
ActiveUS20050102246A1Lower performance requirementsIncrease speedImage analysisDigital computer detailsFace detectionHypothesis
A facial expression recognition system that uses a face detection apparatus realizing efficient learning and high-speed detection processing based on ensemble learning when detecting an area representing a detection target and that is robust against shifts of face position included in images and capable of highly accurate expression recognition, and a learning method for the system, are provided. When learning data to be used by the face detection apparatus by Adaboost, processing to select high-performance weak hypotheses from all weak hypotheses, then generate new weak hypotheses from these high-performance weak hypotheses on the basis of statistical characteristics, and select one weak hypothesis having the highest discrimination performance from these weak hypotheses, is repeated to sequentially generate a weak hypothesis, and a final hypothesis is thus acquired. In detection, using an abort threshold value that has been learned in advance, whether provided data can be obviously judged as a non-face is determined every time one weak hypothesis outputs the result of discrimination. If it can be judged so, processing is aborted. A predetermined Gabor filter is selected from the detected face image by an Adaboost technique, and a support vector for only a feature quantity extracted by the selected filter is learned, thus performing expression recognition.
Owner:SAN DIEGO UNIV OF CALIFORNIA +1
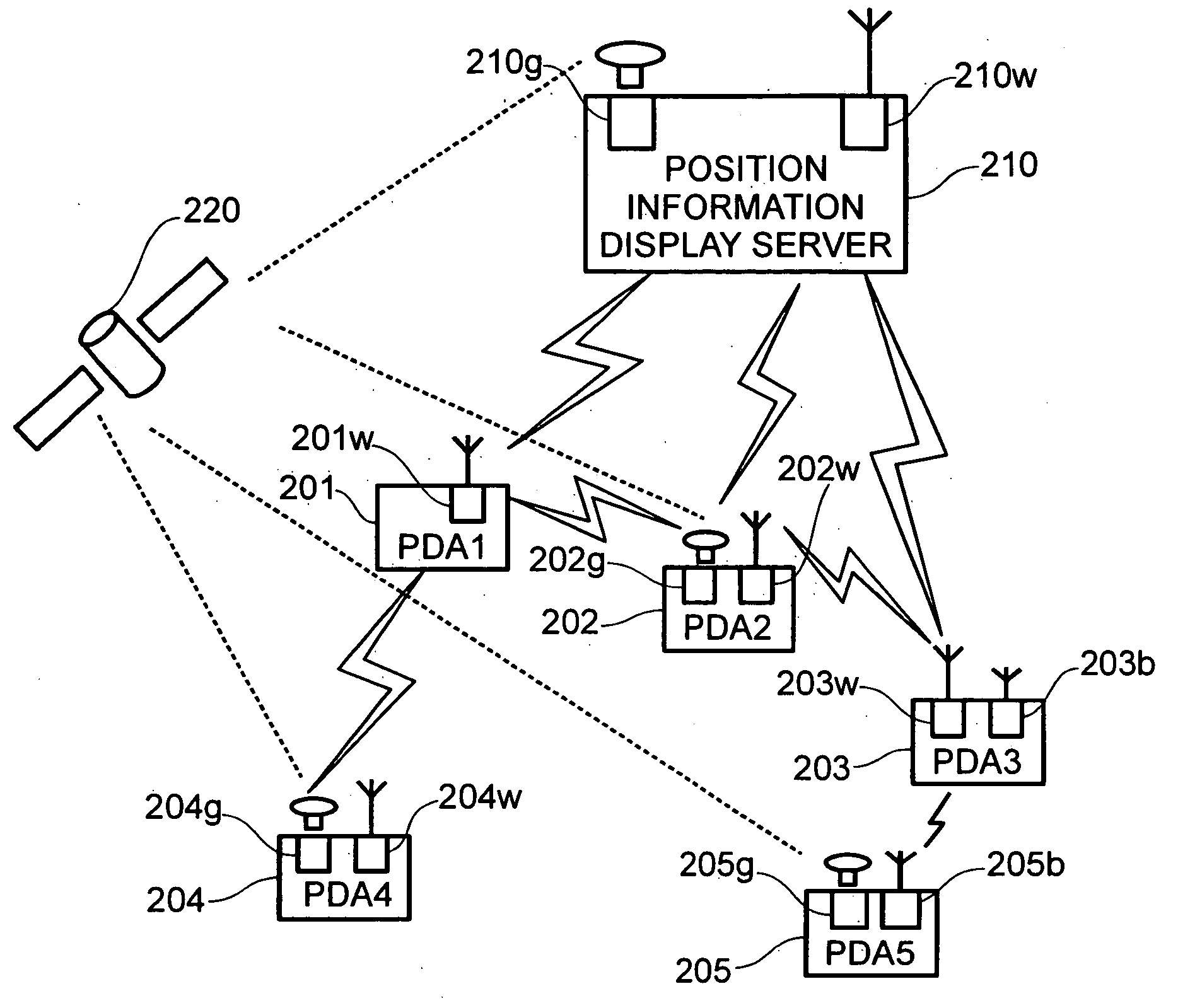
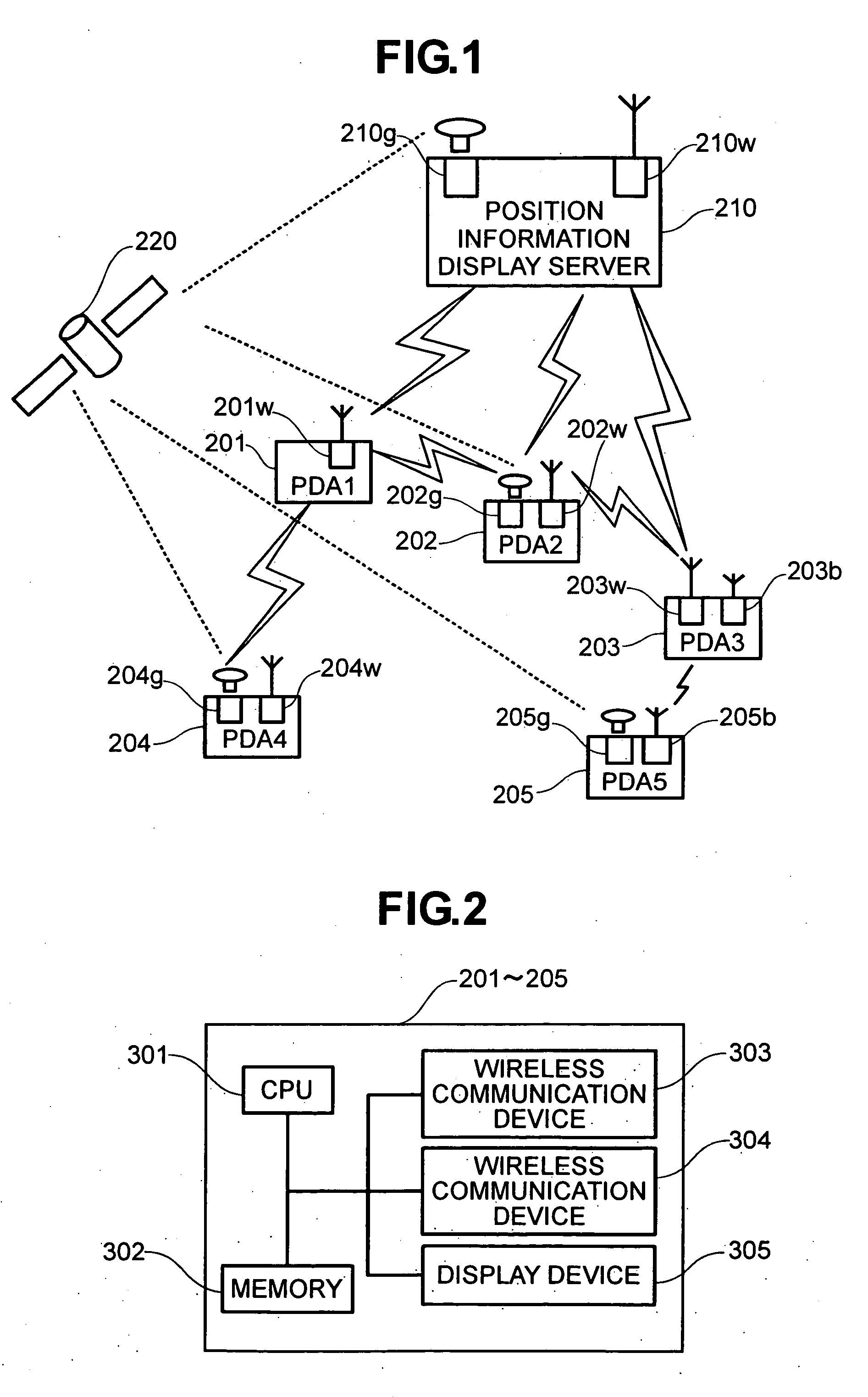
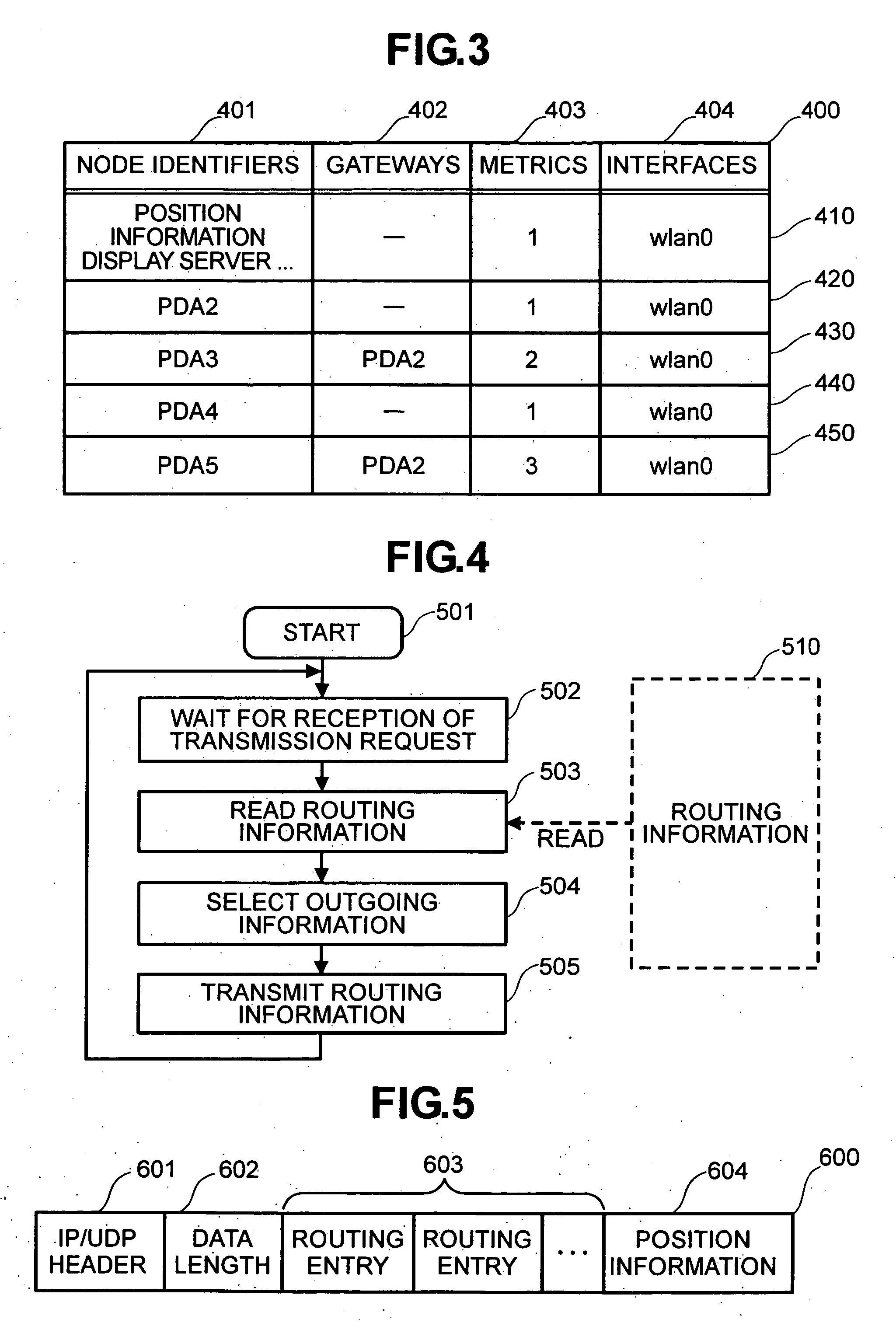
Method for managing position information about nodes connected to a network
InactiveUS20050003832A1Increase costLarge service areaNetwork topologiesPosition fixationSelf-organizing networkReal-time computing
Owner:HITACHI LTD
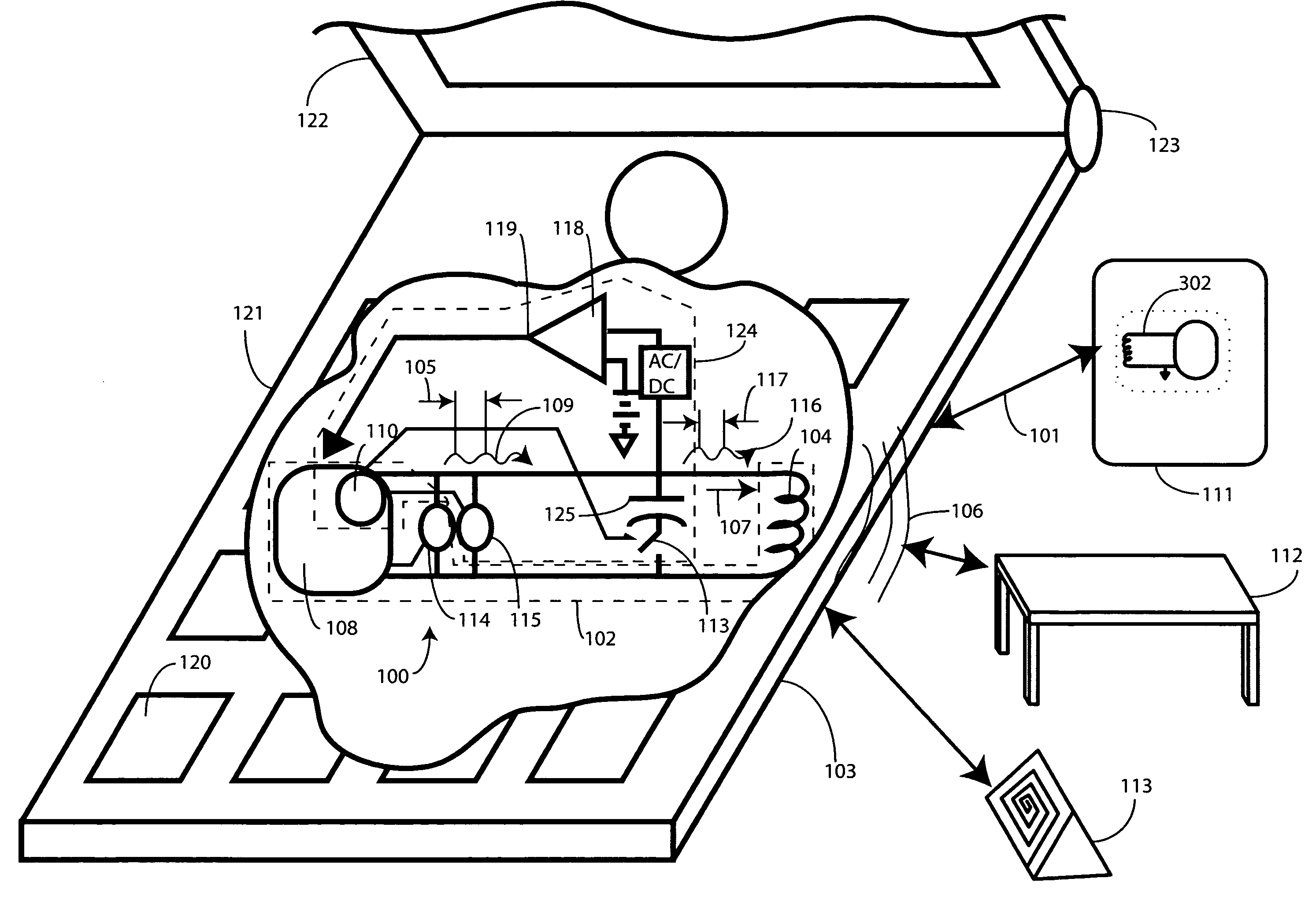
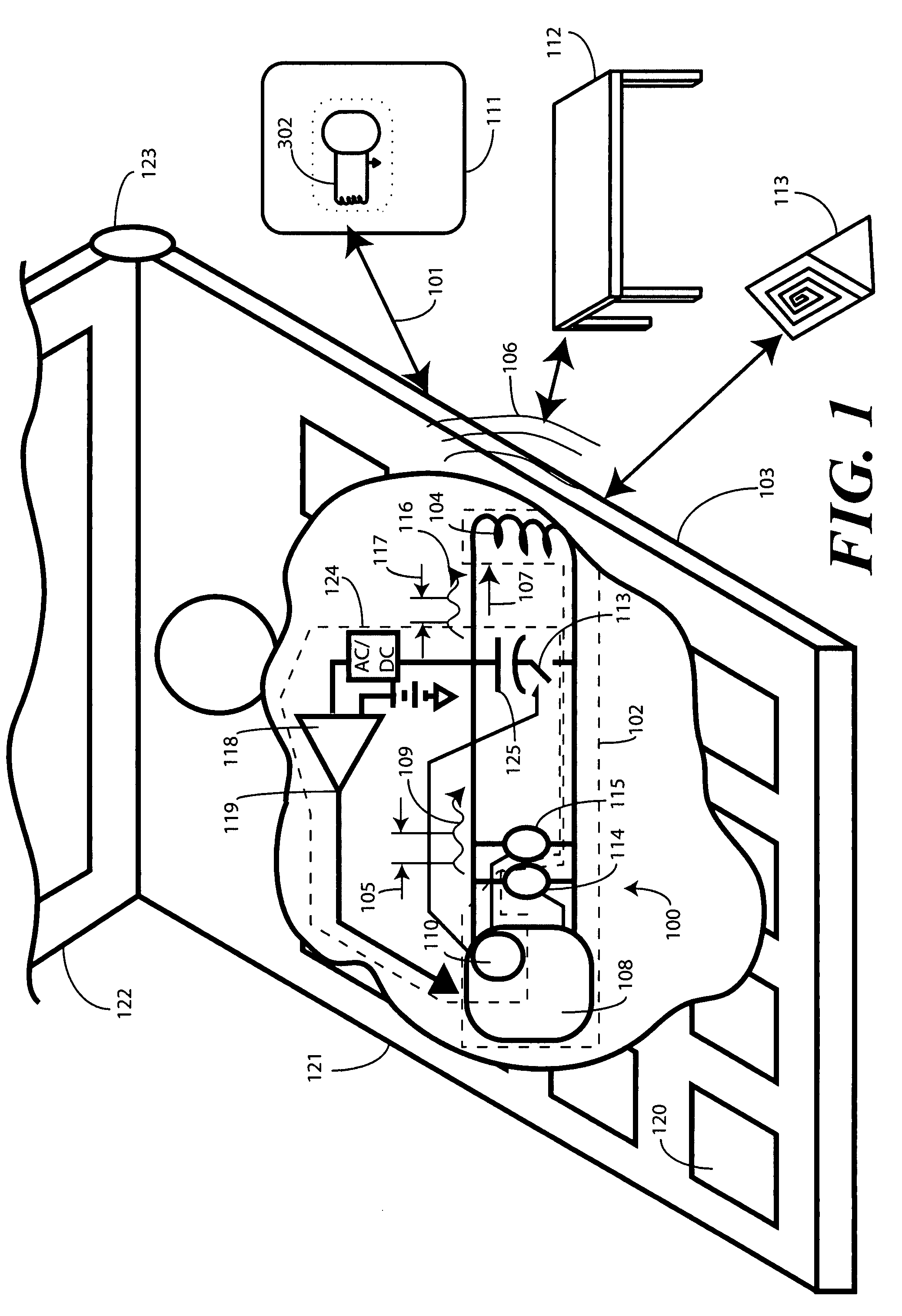
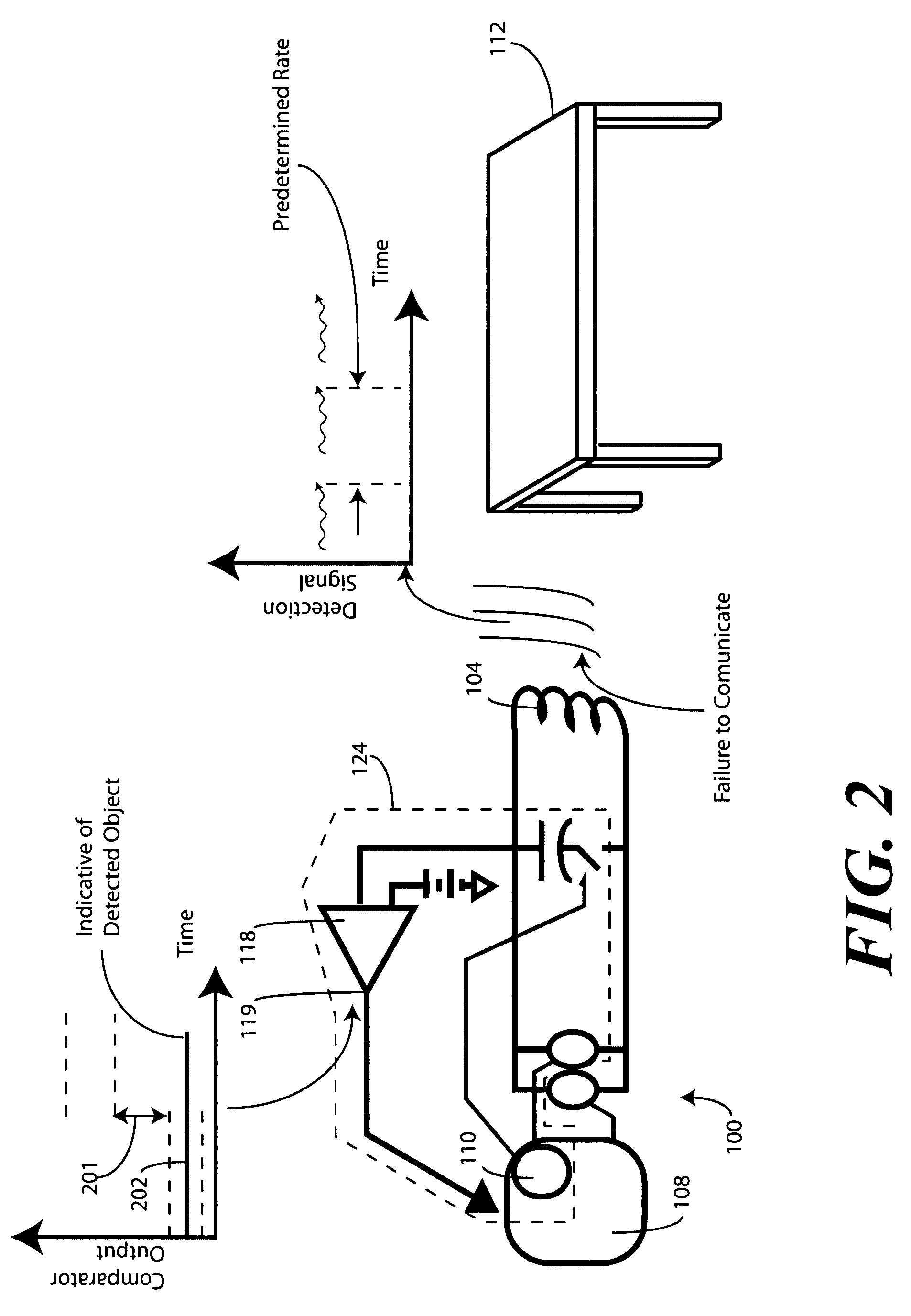
Detection apparatus and method for near field communication devices
A near-field communication circuit (100), such as a radio frequency identification circuit, includes a communication coil (104) and a communication circuit (108) configured to transmit data (109) through the communication coil (104). When the communication circuit (108) is in an idle mode, probing circuitry (124) is configured to detect the presence of a magnetically conductive object within close proximity of a communication coil (104). In one embodiment, a control circuit (110) selectively couples a capacitance (125) in parallel with the communication coil (104). The control circuit (110) then applies a probing signal (116) to the communication coil (104). A comparator (118) monitors a secondary parameter of the communication coil (104), such as inductance or impedance. When a magnetically conductive object is detected, the communication circuit (108) transitions to a communication state and attempts to communicate with the object.
Owner:GOOGLE TECH HLDG LLC
System for monitoring the unauthorized use of a device
ActiveUS20090247122A1Raise the possibilityIncrease opportunitiesUnauthorised/fraudulent call preventionEavesdropping prevention circuitsDevice MonitorLocal environment
The invention is directed to systems and methods for detecting the loss, theft or unauthorized use of a device and / or altering the functionality of the device in response. In one embodiment, a device monitors its use, its local environment, and / or its operating context to determine that the device is no longer within the control of an authorized user. The device may receive communications or generate an internal signal altering its functionality, such as instructing the device to enter a restricted use mode, a surveillance mode, to provide instructions to return the device and / or to prevent unauthorized use or unauthorized access to data. Additional embodiments also address methods and systems for gathering forensic data regarding an unauthorized user to assist in locating the unauthorized user and / or the device.
Owner:BLANCCO TECH GRP IP OY
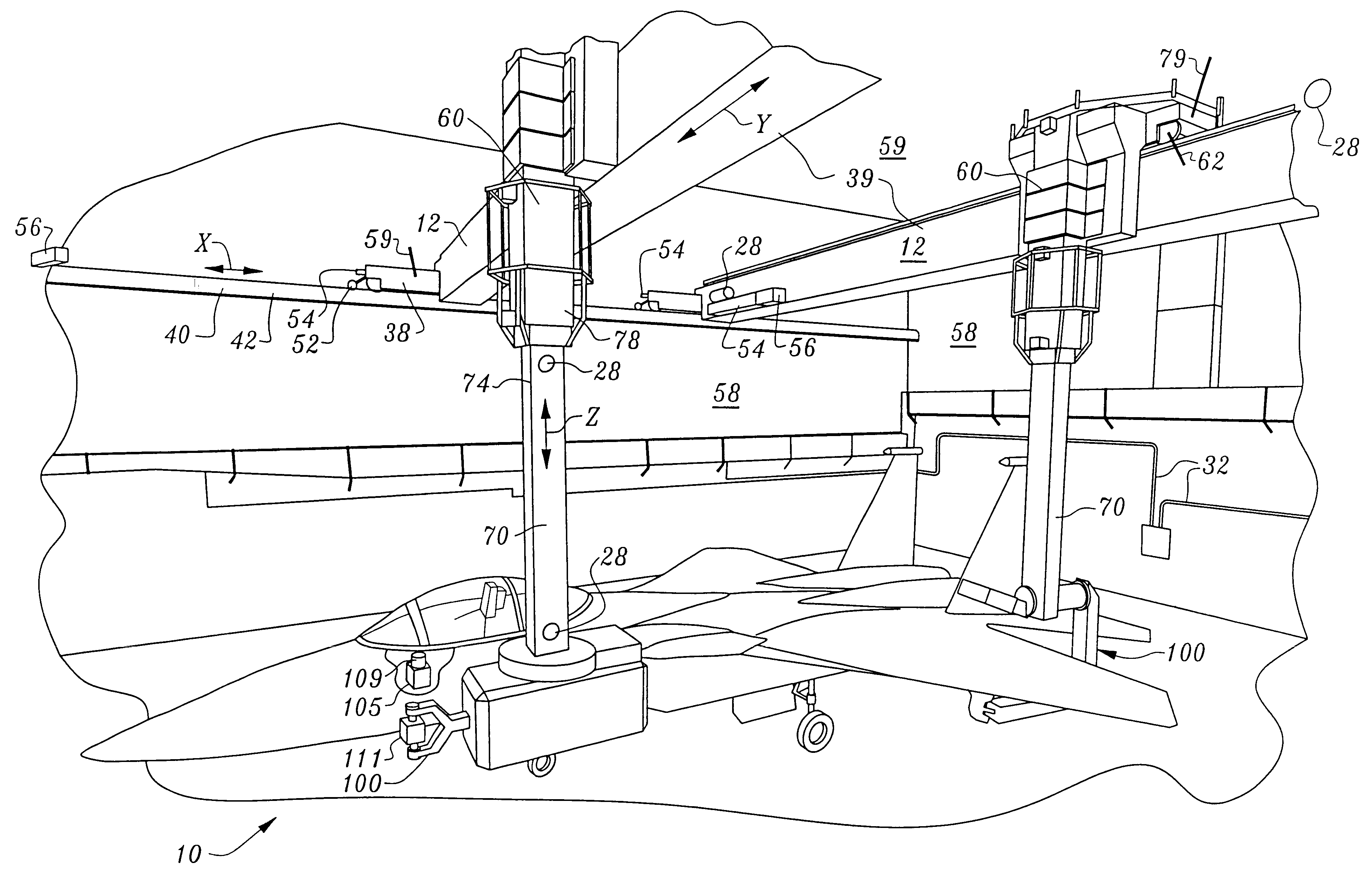
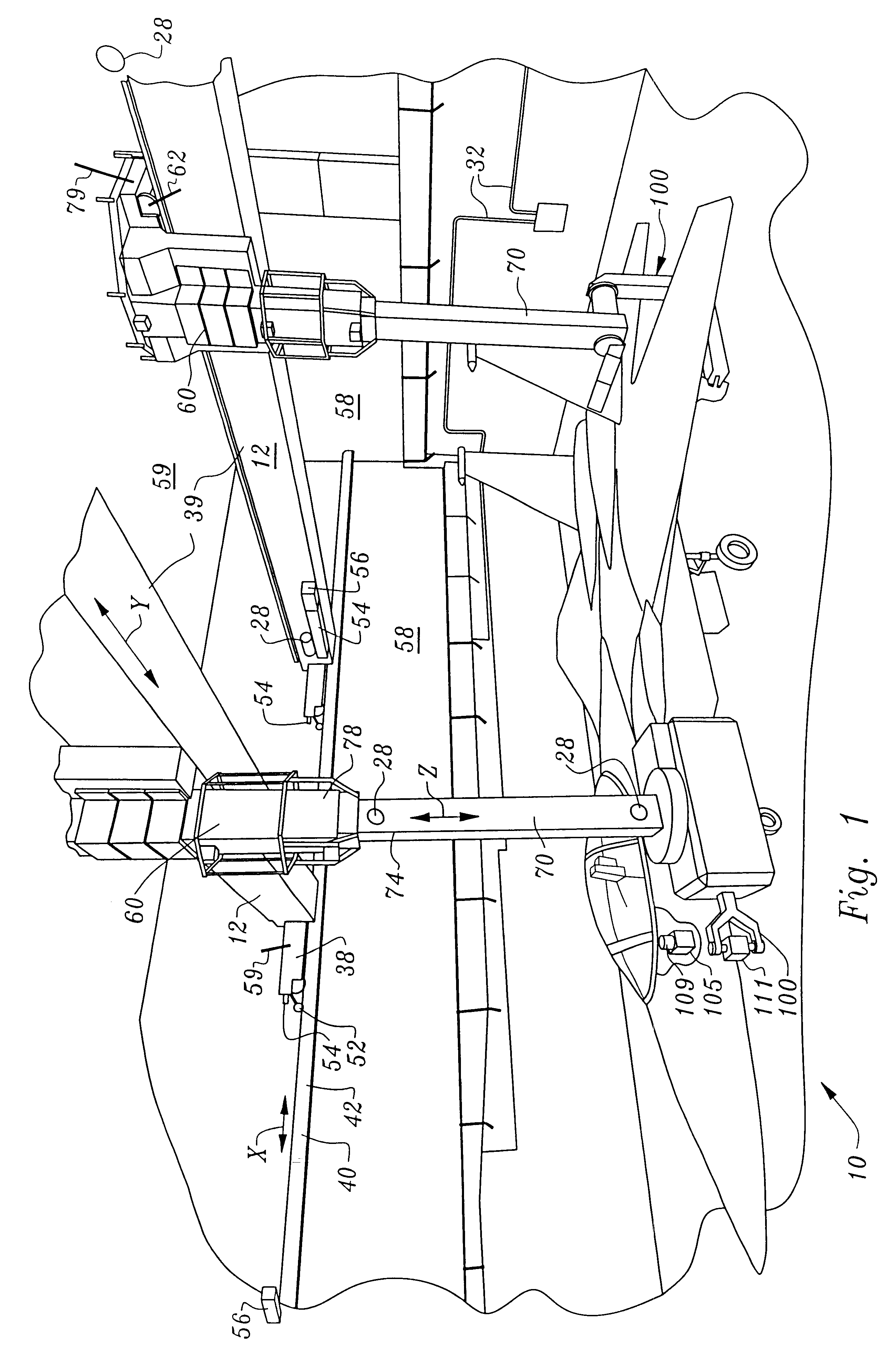
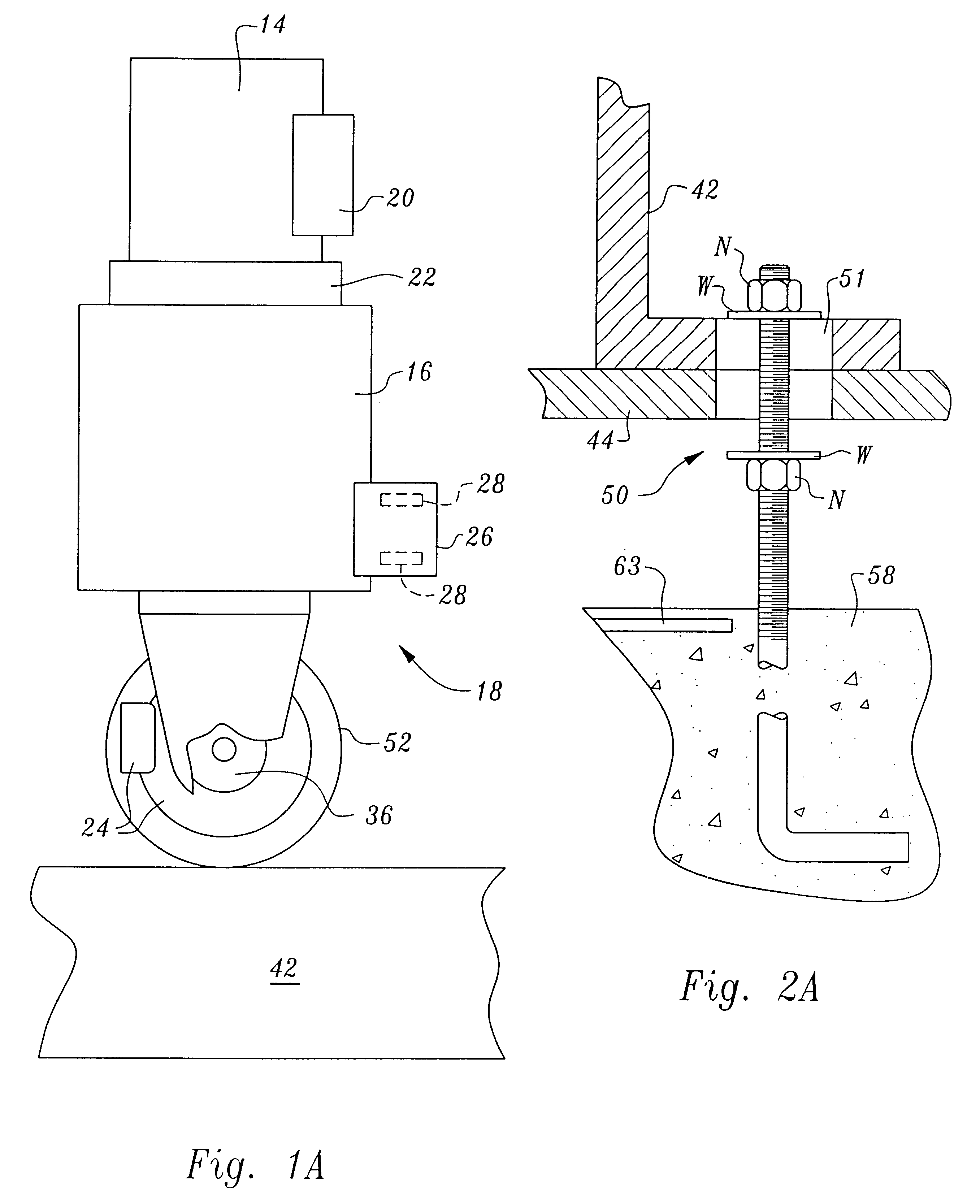
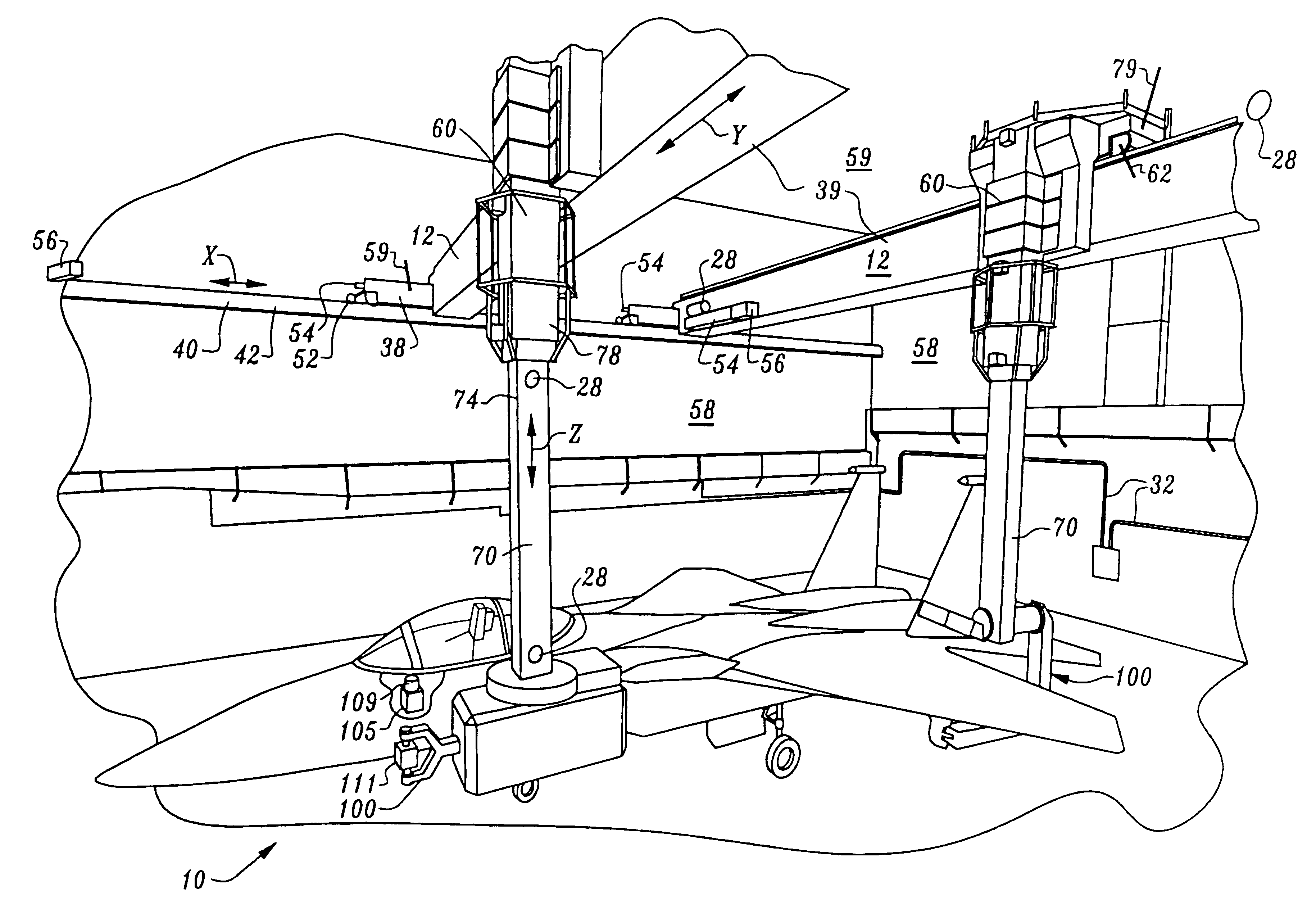
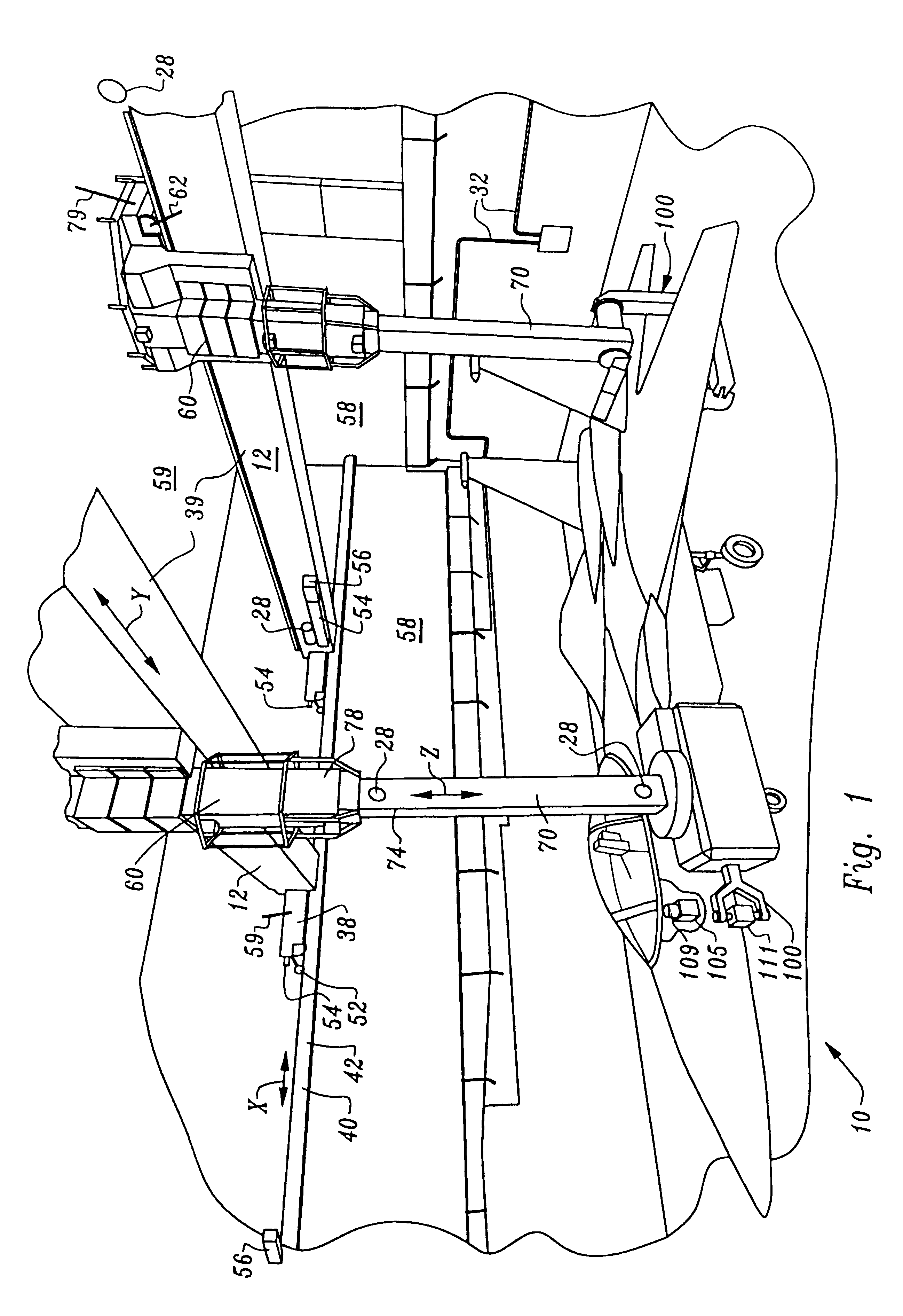
Non-destructive inspection, testing and evaluation systems for intact aircraft and components and method therefore
InactiveUS6637266B1Accurate predictionEasy to useVibration measurement in solidsAnalysing solids using sonic/ultrasonic/infrasonic wavesRadiographic ExamNon destructive
Owner:FROOM DOUGLAS ALLEN
Non-destructive inspection, testing and evaluation system for intact aircraft and components and method therefore
InactiveUS6378387B1Accurate predictionEasy to useProcessing detected response signalDigital computer detailsRadiographic ExamNon destructive
A non-destructive inspection, testing and evaluation system and process is provided for the review of aircraft components. The system provides for a structure configured to contain an inspection and testing apparatus and the aircraft components under inspection. The structure is lined with shielding to attenuate the emission of radiation to the outside of the structure and has corbels therein to support the components that constitute the inspection and testing apparatus. The inspection and testing apparatus is coupled to the structure, resulting in the formation of a gantry for supporting a carriage and a mast is mounted on the carriage. The inspection and testing equipment is mounted on the mast which forms, in part, at least one radiographic inspection robot capable of precise positioning over large ranges of motion. The carriage is coupled to the mast for supporting and allowing translation of the equipment mounted on the mast. The mast is configured to provide yaw movement to the equipment.
Owner:AEROBOTICS
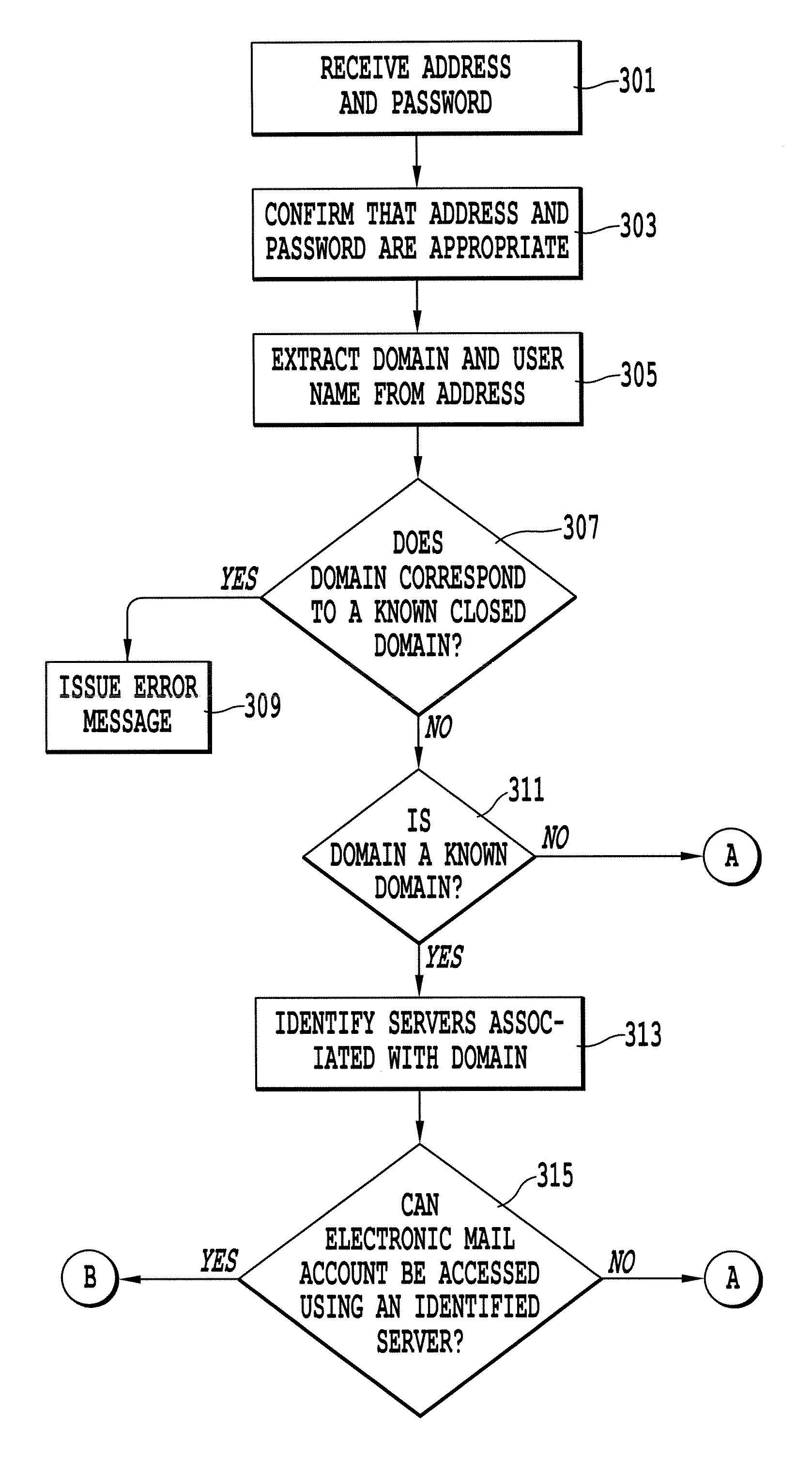
Method and system for determining information to access an electronic mail account
ActiveUS7284045B1Multiple digital computer combinationsData switching networksPasswordWorld Wide Web
An automatic detection device and method for determining the access data necessary to access an existing electronic mail account. Further, the automatic detection device and method can determine whether an electronic mail account can be accessed according to a specific electronic mail protocol. With the detection device and method, the user provides the password and address for an existing electronic mail account. From this information, the automatic detection device and method determines the user name and the server name for the server hosting the electronic mail account. The device and method then employs the user name, server name and password to determine whether the electronic mail account can be accessed according to a particular electronic mail protocol, such as the post office protocol, and, if possible, to access the electronic mail account.
Owner:MALIKIE INNOVATIONS LTD
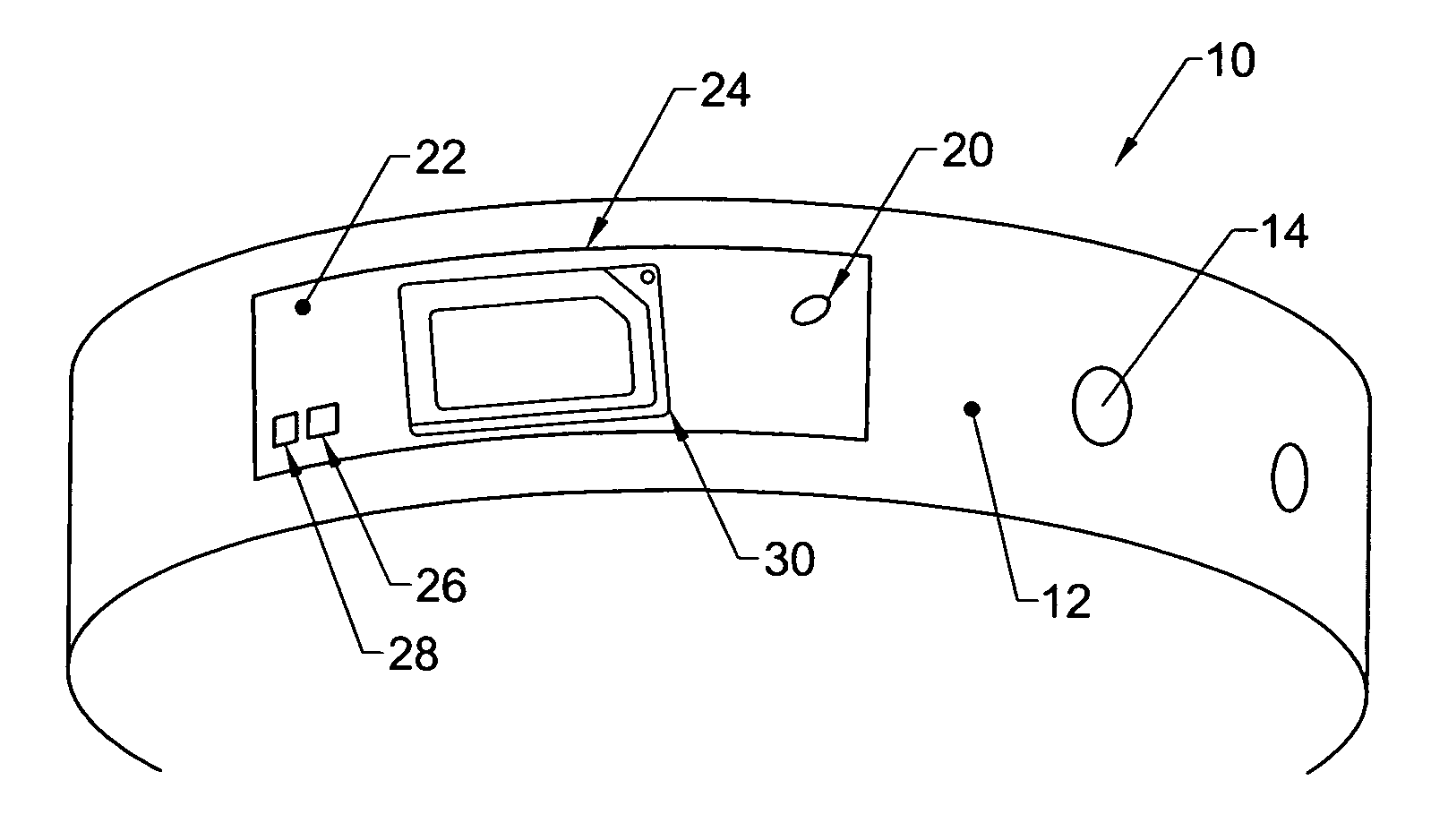
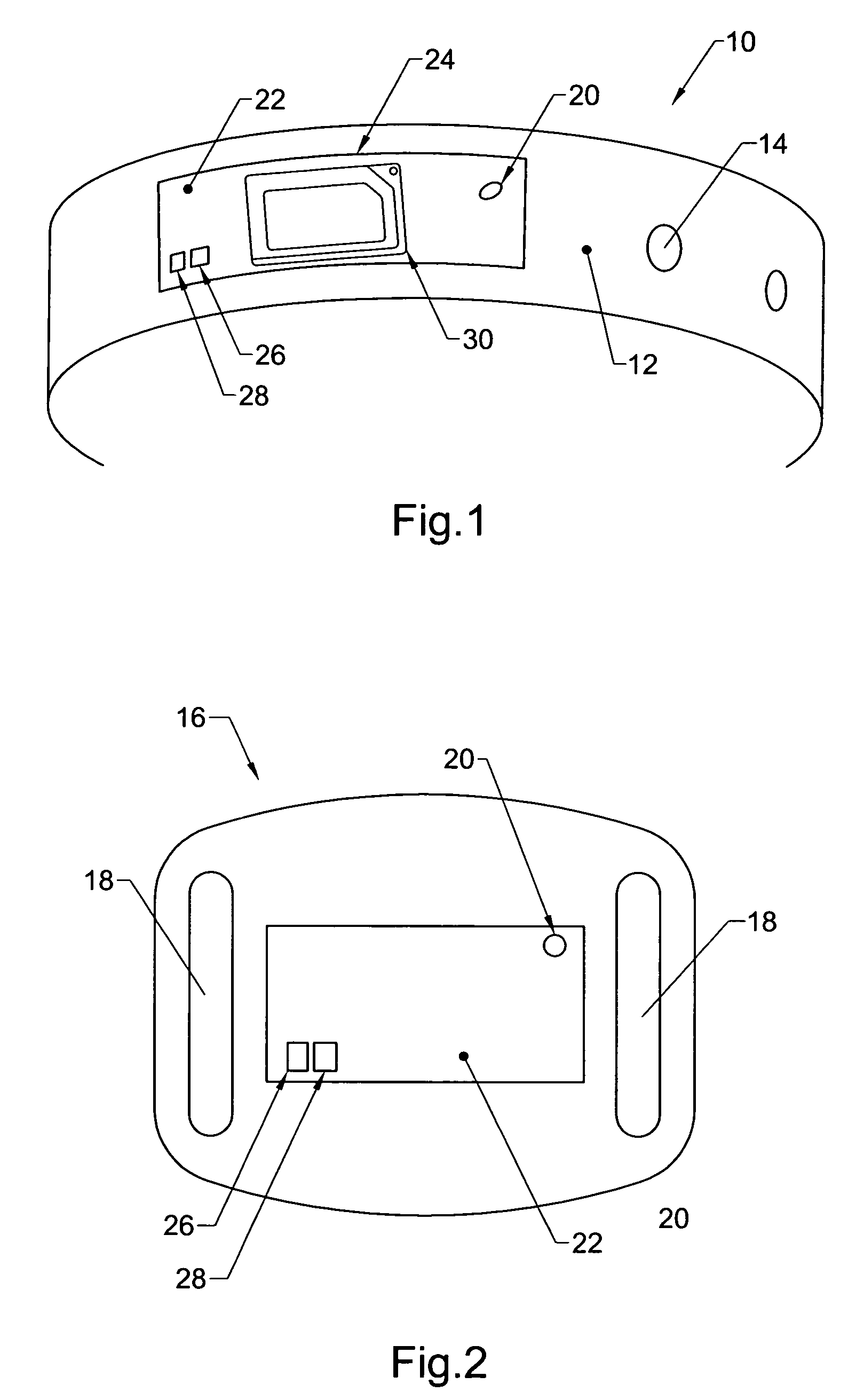
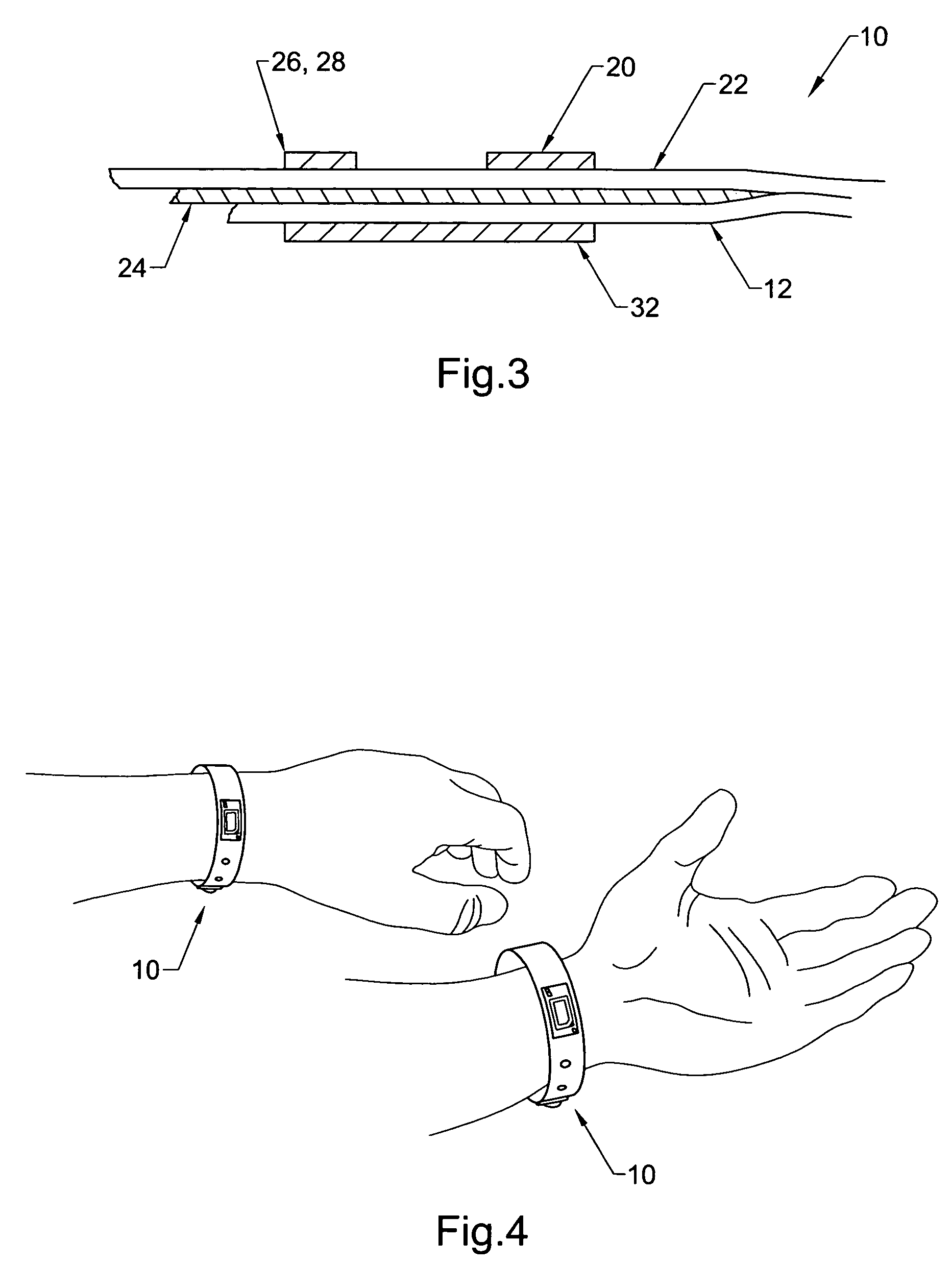
Physical condition or environmental threat detection appliance system
InactiveUS7188767B2Converting sensor ouput using wave/particle radiationMeasurement arrangements for variableEngineeringRadio frequency
A system includes one or more devices for providing information about a physical condition or environmental hazard. Each device includes a sensor physically associated with the user for detecting a predetermined environmental hazard and / or a physical condition of the user. The device is usually in the form of a wristband patch or tag attached to the user. The one or more sensors are adapted to detect predetermined chemicals, biological organisms, radiation or user blood pressure, heart rate, temperature, oxygen level, glucose level, skin condition, or biological and chemical changes of the user. An electronic circuit communicates with the sensor and includes an alarm for notifying the user or a third party of elevated environmental hazards or abnormal physical conditions of the user. Typically, the electronic circuit includes a transmitter, such as a radio frequency transmitter, for conveying information obtained from the sensor and electronic circuitry to a third party.
Owner:PRECISION DYNAMICS CORPORATION
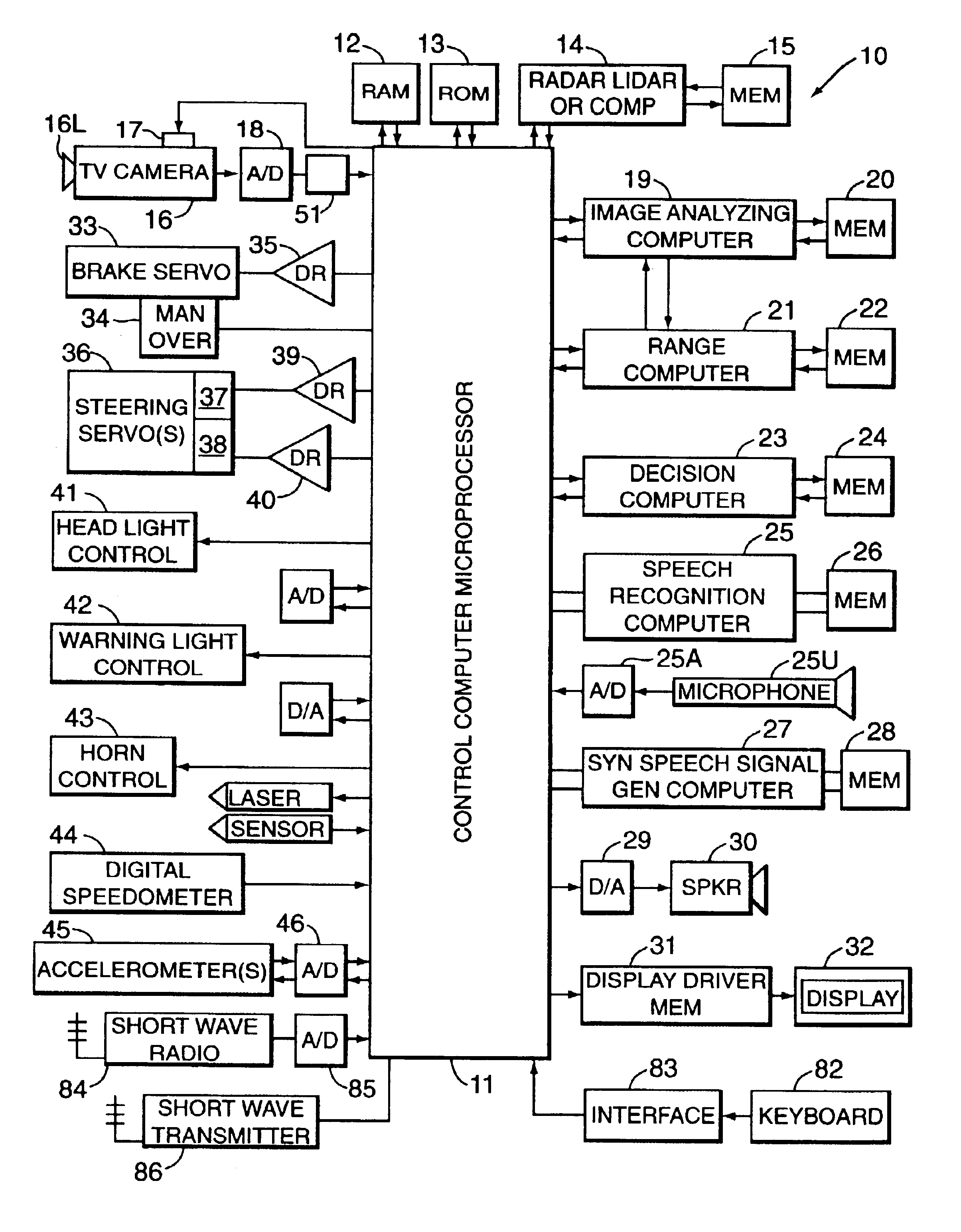
Motor vehicle warning and control system and method
InactiveUS6906639B2Hazardous conditionReduce chanceRegistering/indicating working of vehiclesAnti-collision systemsDriver/operatorMotor vehicle part
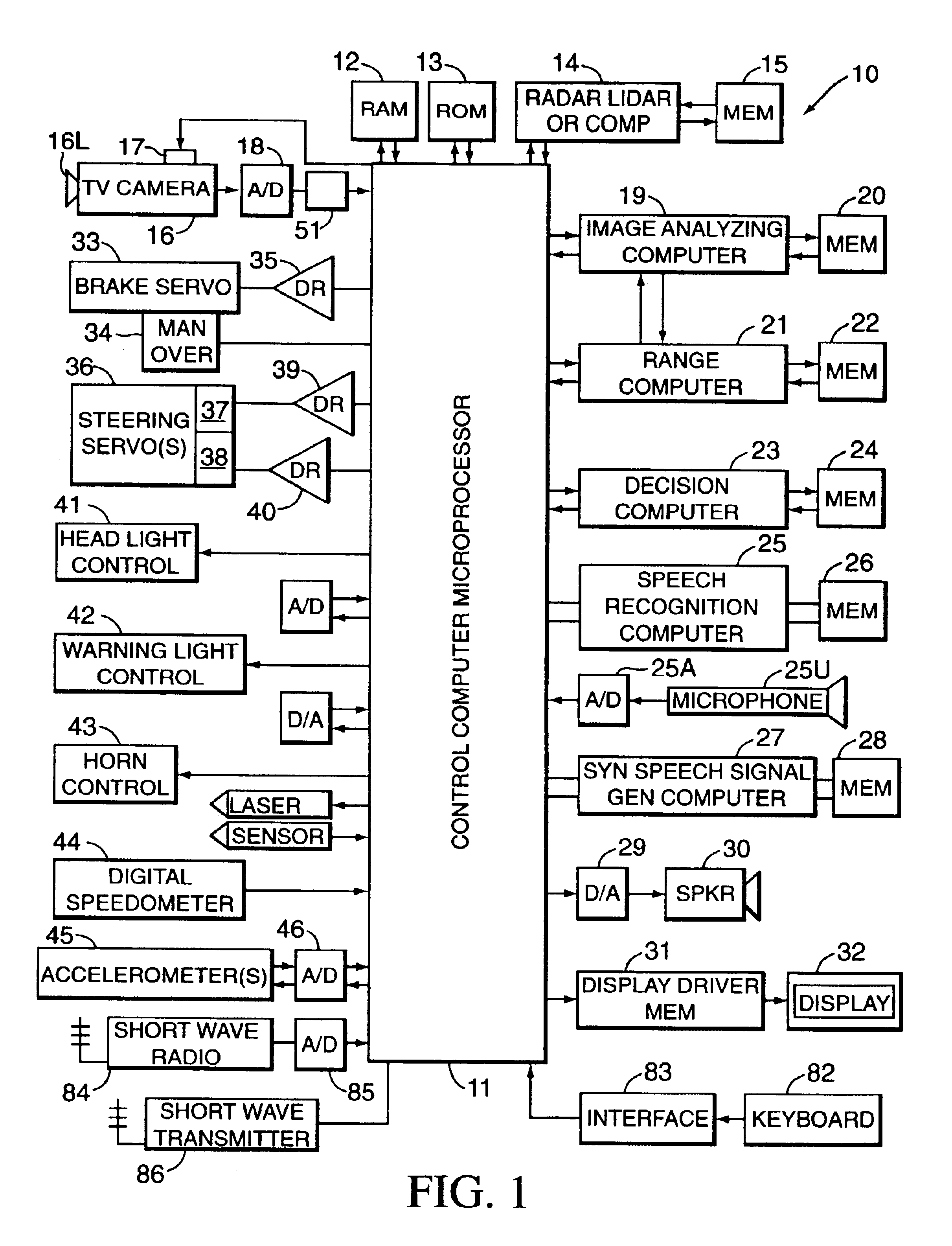
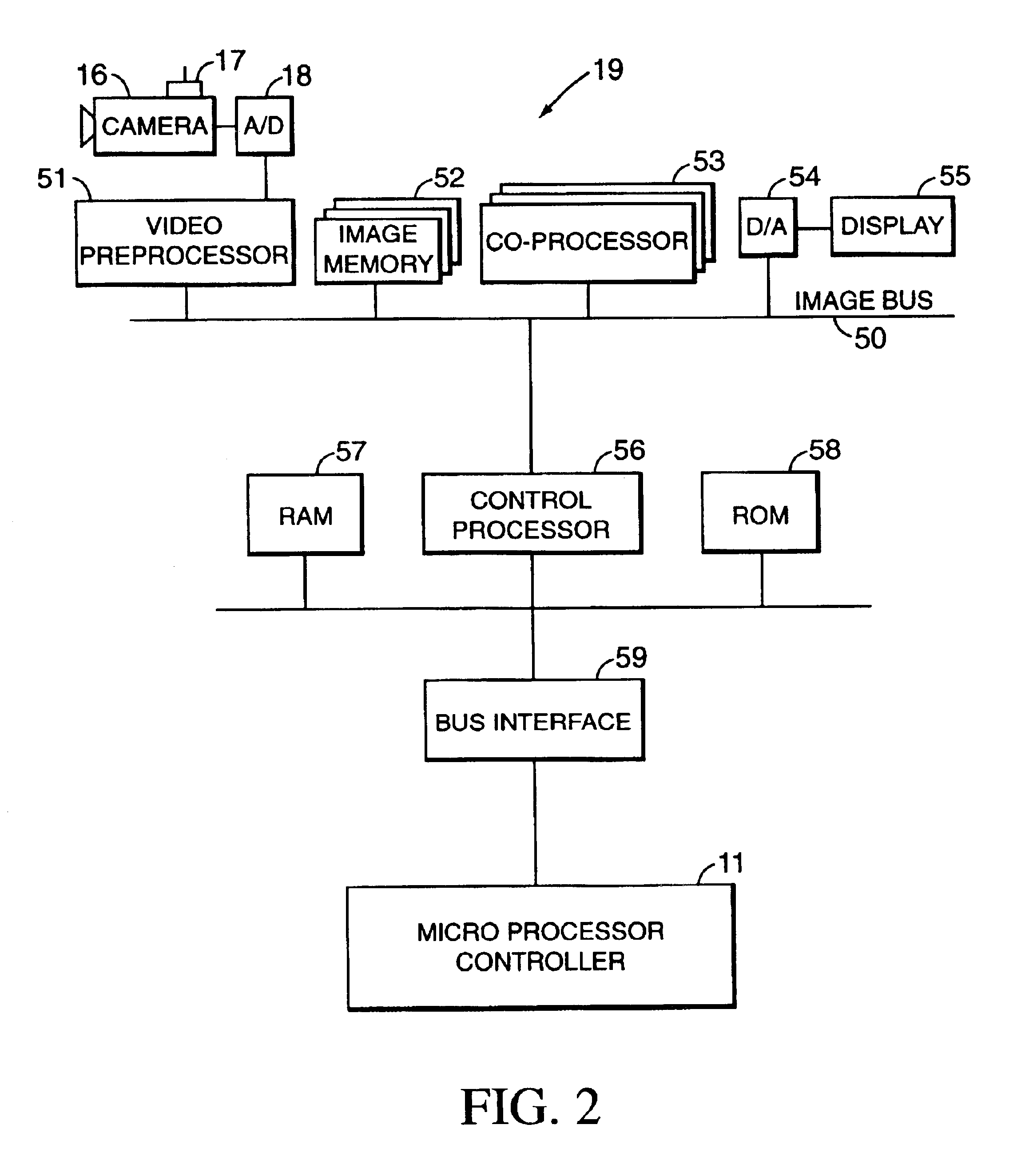
A system and method assists the driver of a motor vehicle in preventing accidents or minimizing the effects of same. In one form, a television camera or other ranging device is mounted on a vehicle and scans the roadway ahead of the vehicle as the vehicle travels. Continuously generated video picture signals output by the camera are electronically processed and analyzed by a fuzzy-logic-based image analyzing computer mounted in the controlled vehicle, which generates control signals and applies them to control the operation of the accelerator, brake, and steering system of the vehicle in a coordinated way to attempt to avoid or lessen the effects of a collision. In a particular form, the decision computer may select the evasive action taken from a number of choices, depending on whether and where the detection device senses other vehicles and obstacles. Warning signals may also be generated.
Owner:LEMELSON JEROME H +2
Probe device having a clip-on wireless system for extending probe tip functionality
InactiveUS20090212938A1Function increaseElectrical testingMeasurement leads/probesTelecommunications linkWireless transceiver
A probe device is provided that has a clip-on wireless device attached thereto for communicating over a wireless communication link with test equipment having a wireless transceiver attached thereto. The clip-on wireless device may have one or more components that provide additional functionality to the probe device over that which is currently available on most probe devices. Such components may include, for example, run / stop buttons, activity indicators, “headlight” LEDs, etc
Owner:AGILENT TECH INC
Method for mitigating the unauthorized use of a device
ActiveUS20090253408A1Raise the possibilityIncrease opportunitiesUnauthorised/fraudulent call preventionEavesdropping prevention circuitsDevice MonitorLocal environment
The invention is directed to systems and methods for detecting the loss, theft or unauthorized use of a device and / or altering the functionality of the device in response. In one embodiment, a device monitors its use, its local environment, and / or its operating context to determine that the device is no longer within the control of an authorized user. The device may receive communications or generate an internal signal altering its functionality, such as instructing the device to enter a restricted use mode, a surveillance mode, to provide instructions to return the device and / or to prevent unauthorized use or unauthorized access to data. Additional embodiments also address methods and systems for gathering forensic data regarding an unauthorized user to assist in locating the unauthorized user and / or the device.
Owner:BLANCCO TECH GRP IP OY
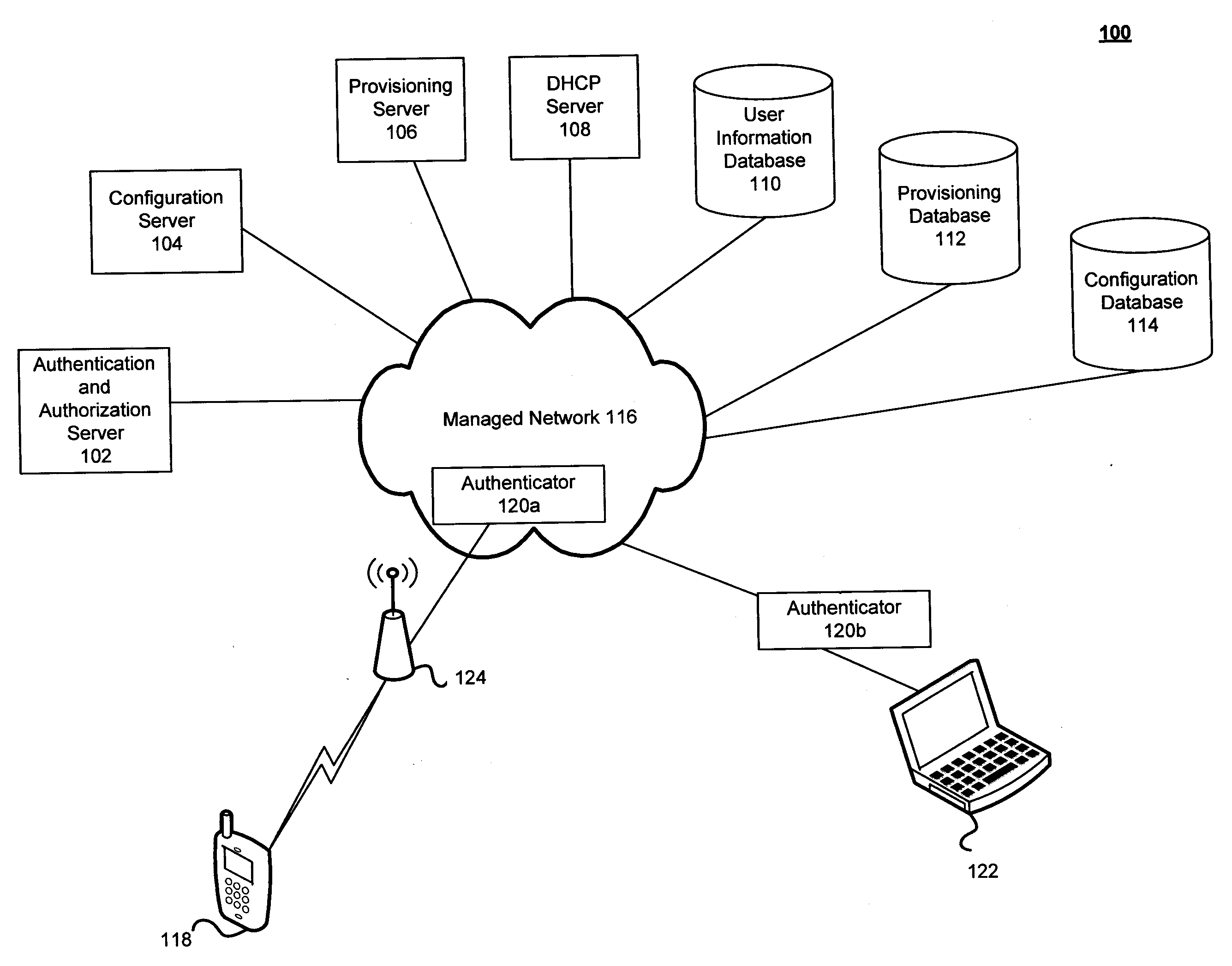
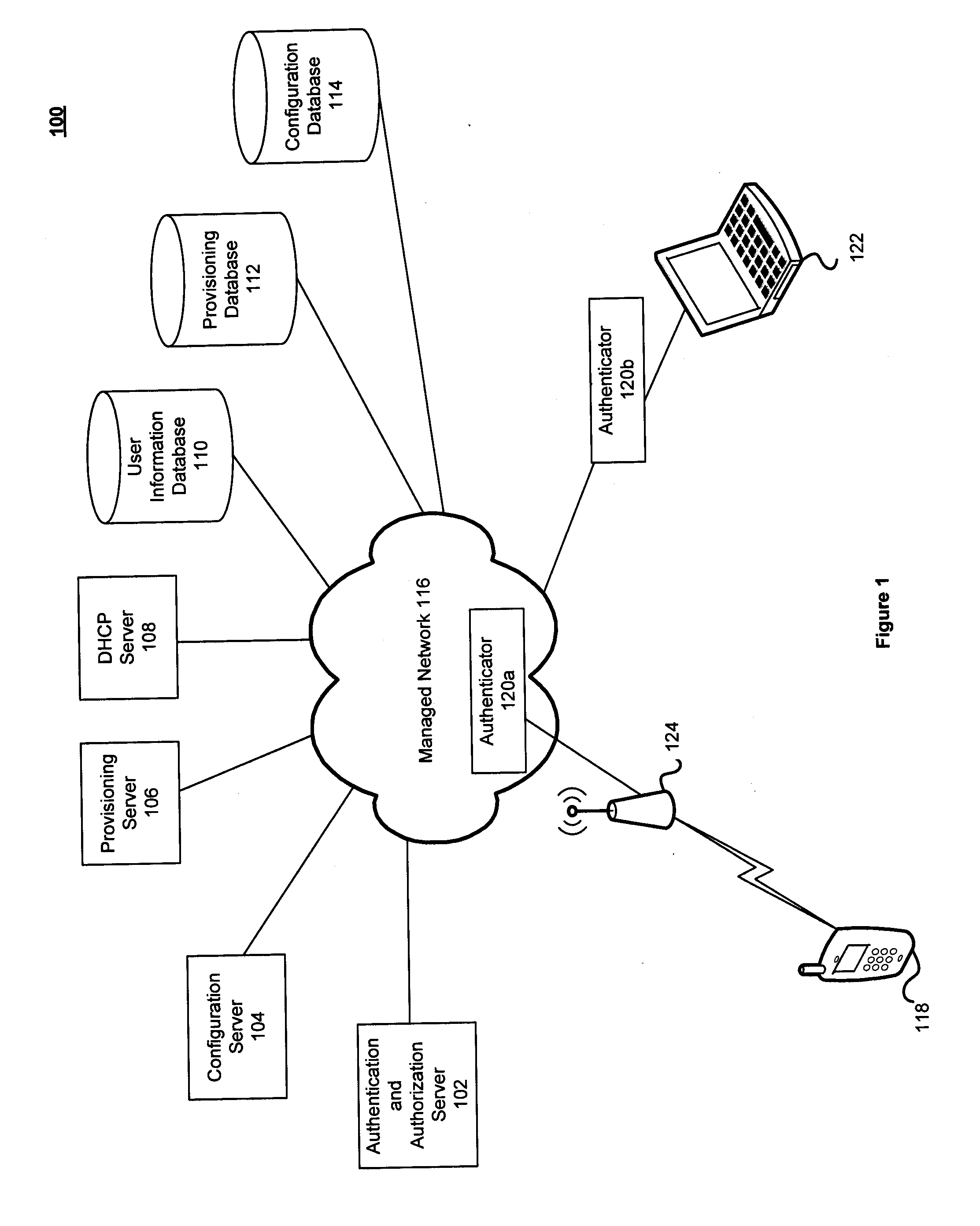
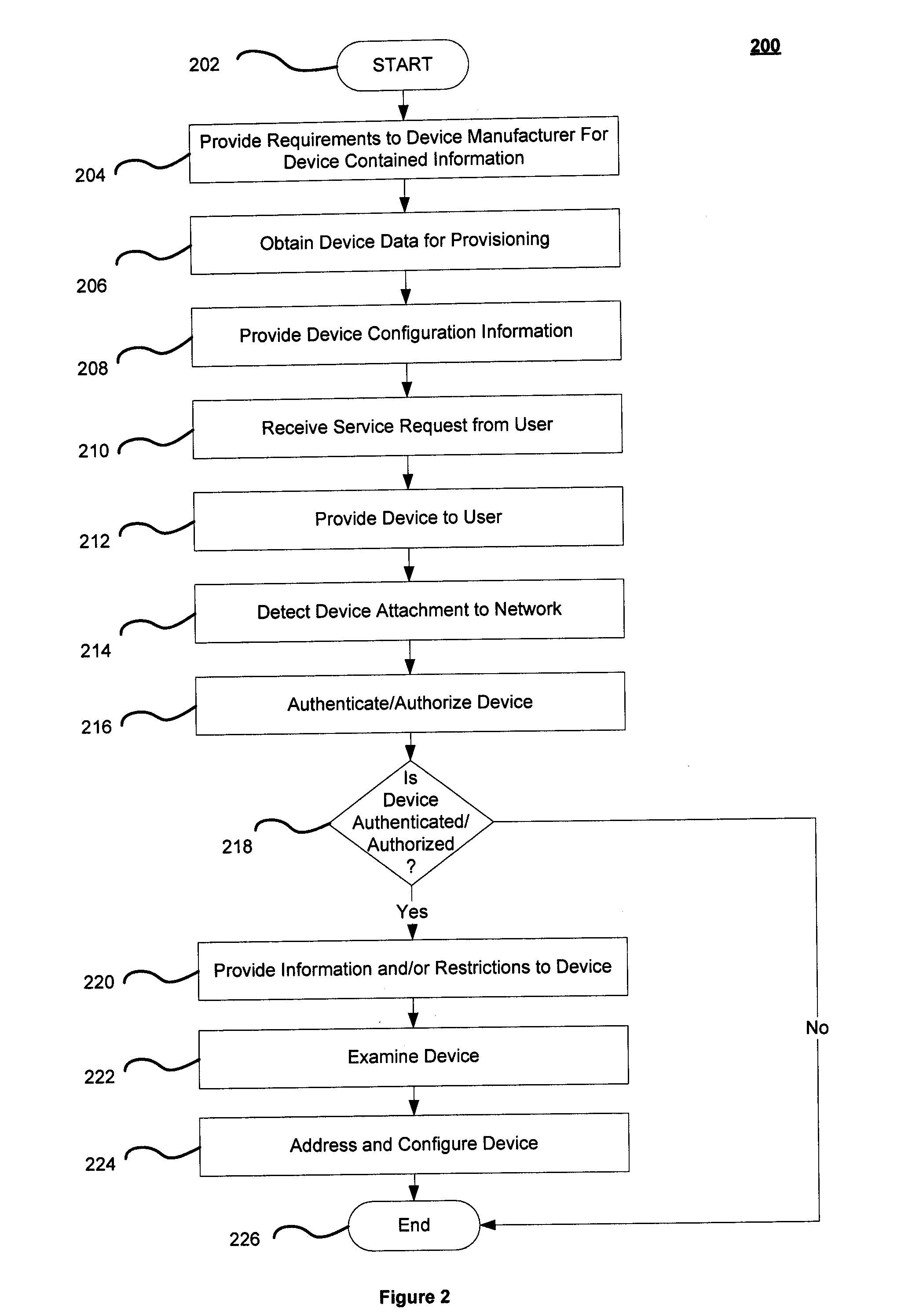
System and Method for Secure Configuration of Network Attached Devices
ActiveUS20090132682A1Digital computer detailsElectric digital data processingNetwork addressTesting equipment
A system and method for supplying, to a provider of the device, requirements for information to be stored on a device, obtaining device data for provisioning the device on a network, storing device configuration information on storage associated with the network, receiving a service request from a user of the device, detecting attachment of the device to the network, authenticating the device utilizing a device identifier and shared credentials to enable the device to be configured without storing a network address for configuration in the device, providing network information to the device, and providing configuration information to the device.
Owner:VERIZON PATENT & LICENSING INC
Generating a three-dimensional model using a portable electronic device recording
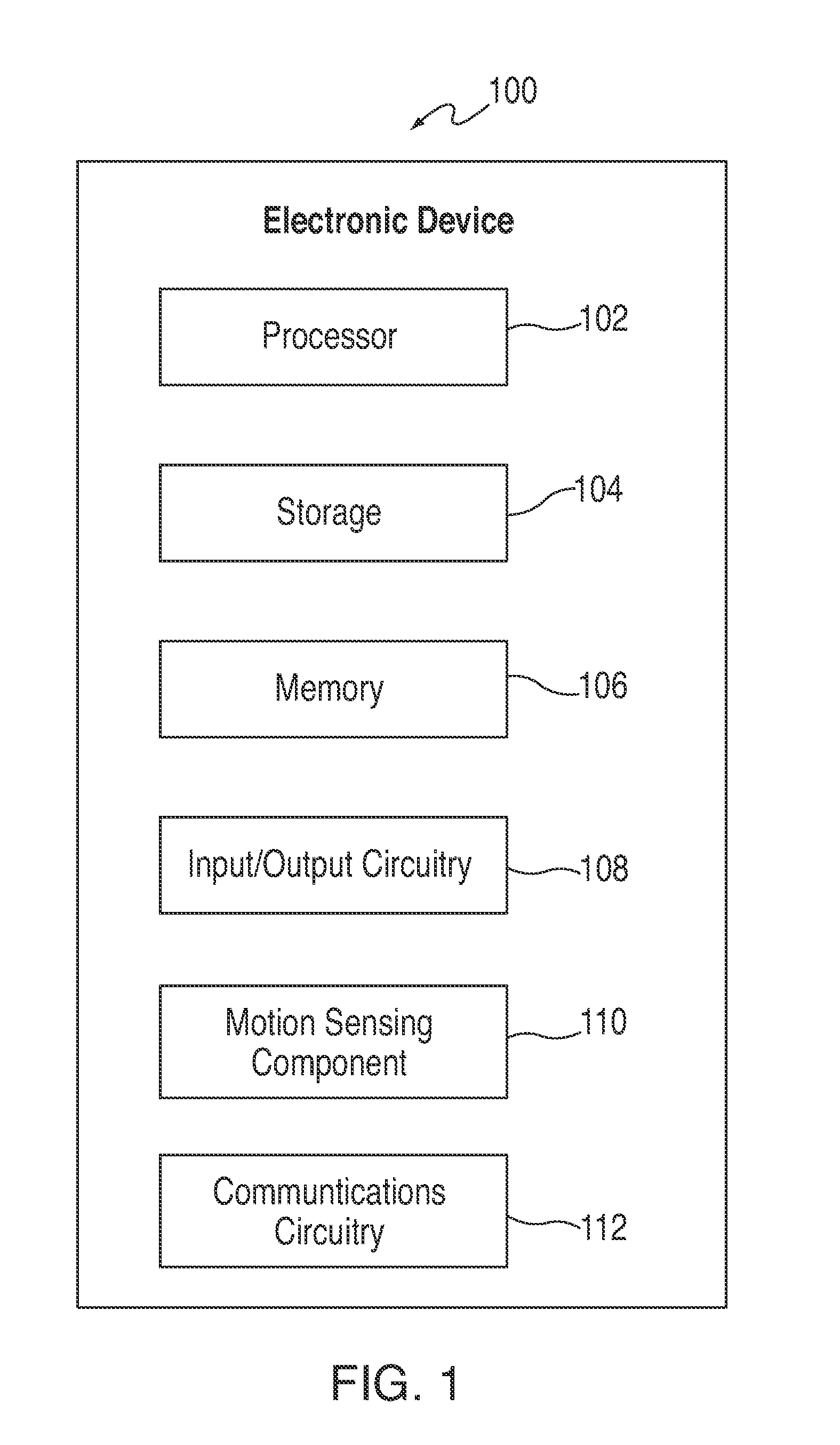
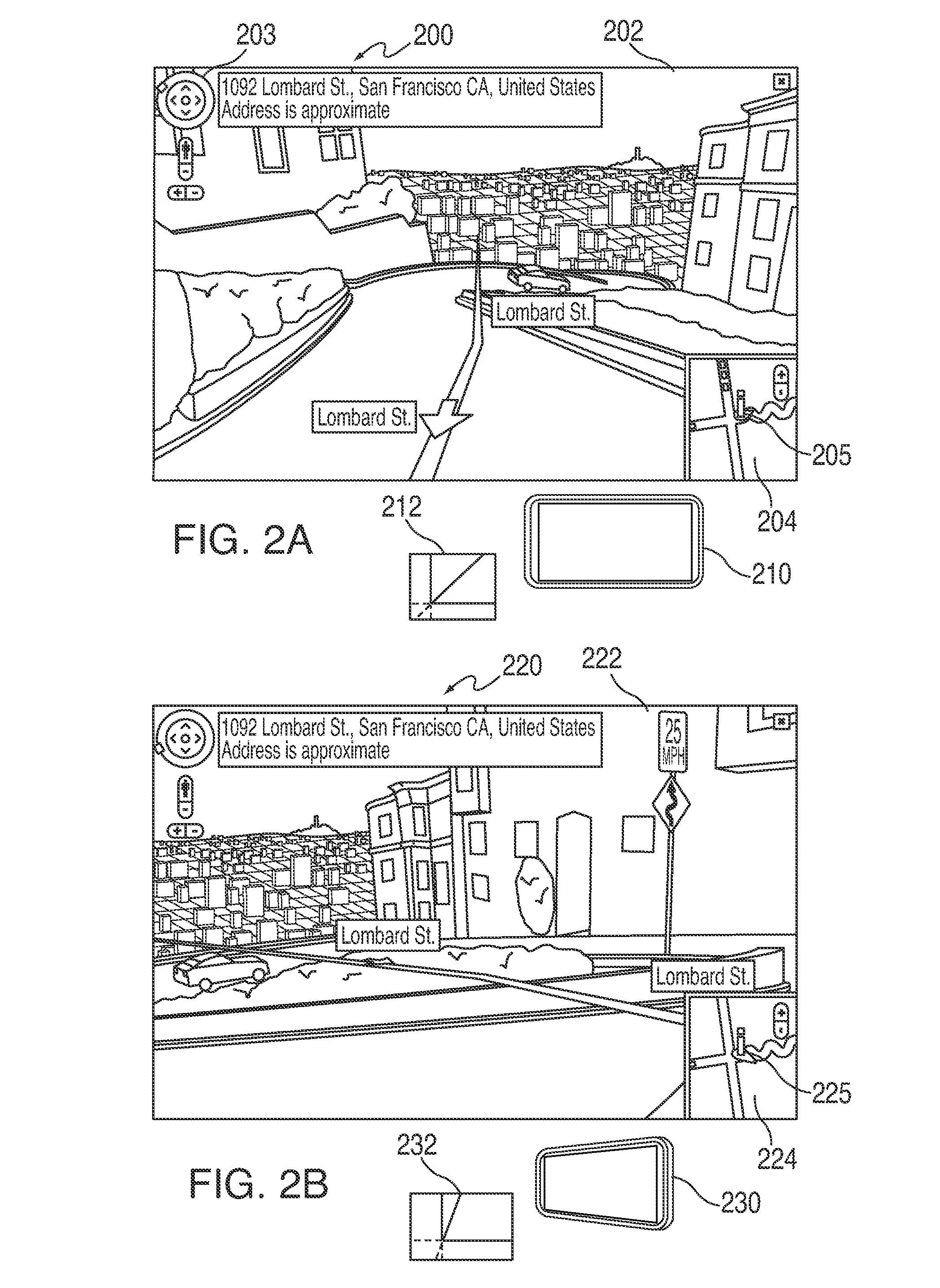
ActiveUS20100188503A1Navigational calculation instrumentsColor television detailsMotion sensingDimensional modeling
Systems and methods are providing for navigating a three-dimensional model using deterministic movement of an electronic device. An electronic device can load and provide an initial display of a three dimensional model (e.g., of an environment or of an object). As the user moves the electronic device, motion sensing components, positioning circuitry, and other components can detect the device movement and adjust the displayed portion of the three-dimensional model to reflect the movement of the device. By walking with the device in the user's real environment, a user can virtually navigate a representation of a three-dimensional environment. In some embodiments, a user can record an object or environment using an electronic device, and tag the recorded images or video with movement information describing the movement of the device during the recording. The recorded information can then be processed with the movement information to generate a three-dimensional model of the recorded environment or object.
Owner:APPLE INC
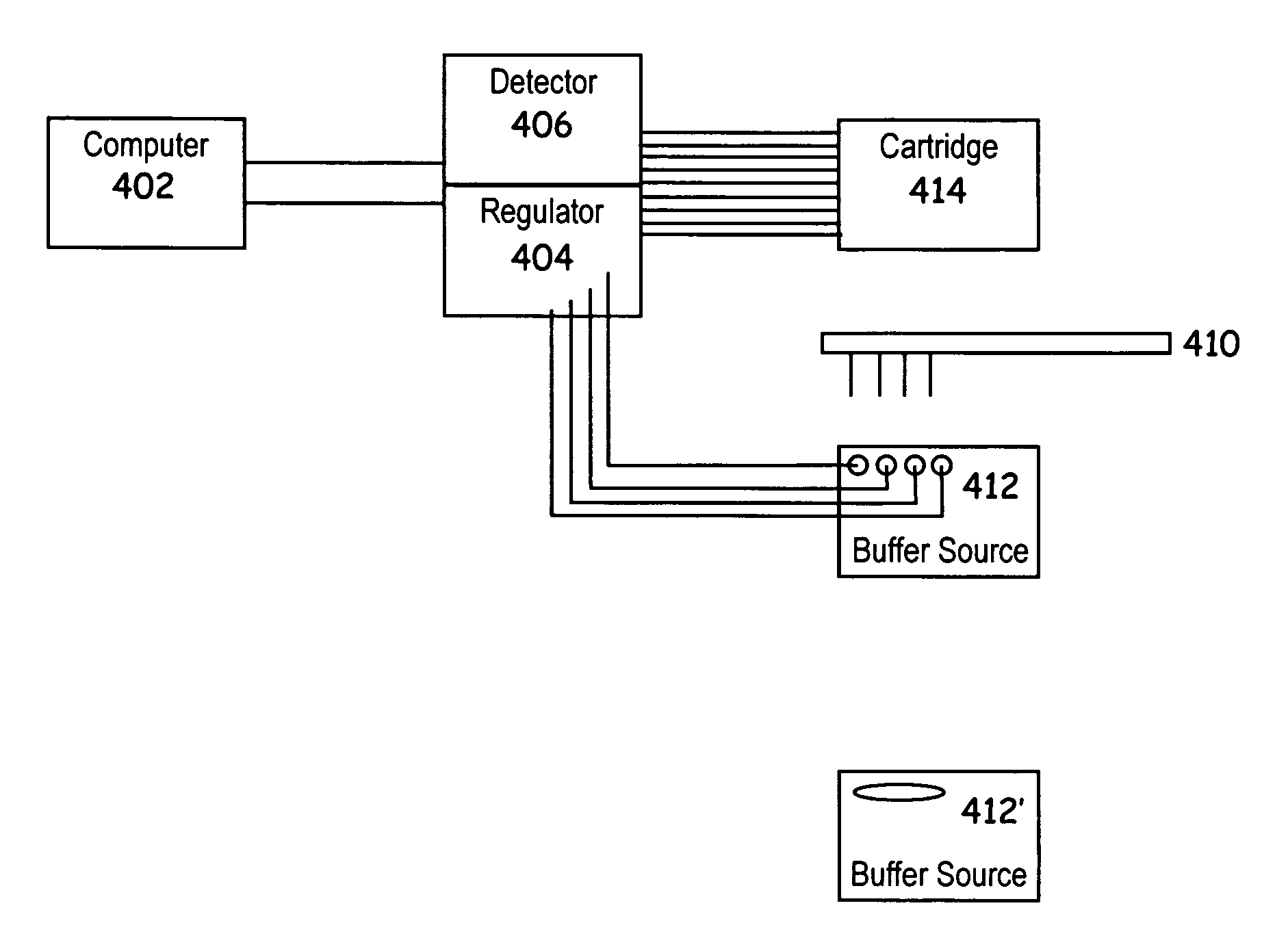
Voltage/current testing equipment for microfluidic devices
The present invention provides novel methods and devices for testing / verifying the configuration of one or more microfluidic elements in a microfluidic device. In particular the methods and devices of the invention are useful in testing for blockages or the presence of air bubbles in microfluidic elements. For example, a method for verifying the proper function of a microfluidic device is disclosed, which device comprises at least first, second and third fluidic openings, which fluidic openings are fluidly coupled to at least first, second and third microscale channel elements, respectively, the method comprising flowing an electrically conductive buffer through the first, second and third microscale channel elements; setting a known applied voltage potential (or current) between the first and second fluidic openings; setting a current in the third microscale channel element to be approximately zero; detecting a resulting voltage at the third fluidic opening; and, comparing the detected voltage at the third fluidic opening with a calculated target voltage expected at the third fluidic opening to determine whether there is a fault or problem (e.g., air bubble) in at least one of the first and second microscale channel elements. The above method can be repeated one or more times for the other fluidic openings in the microfluidic device to determine whether there is a fault in any one or more microscale elements of the device.
Owner:CAPLIPER LIFE SCI INC
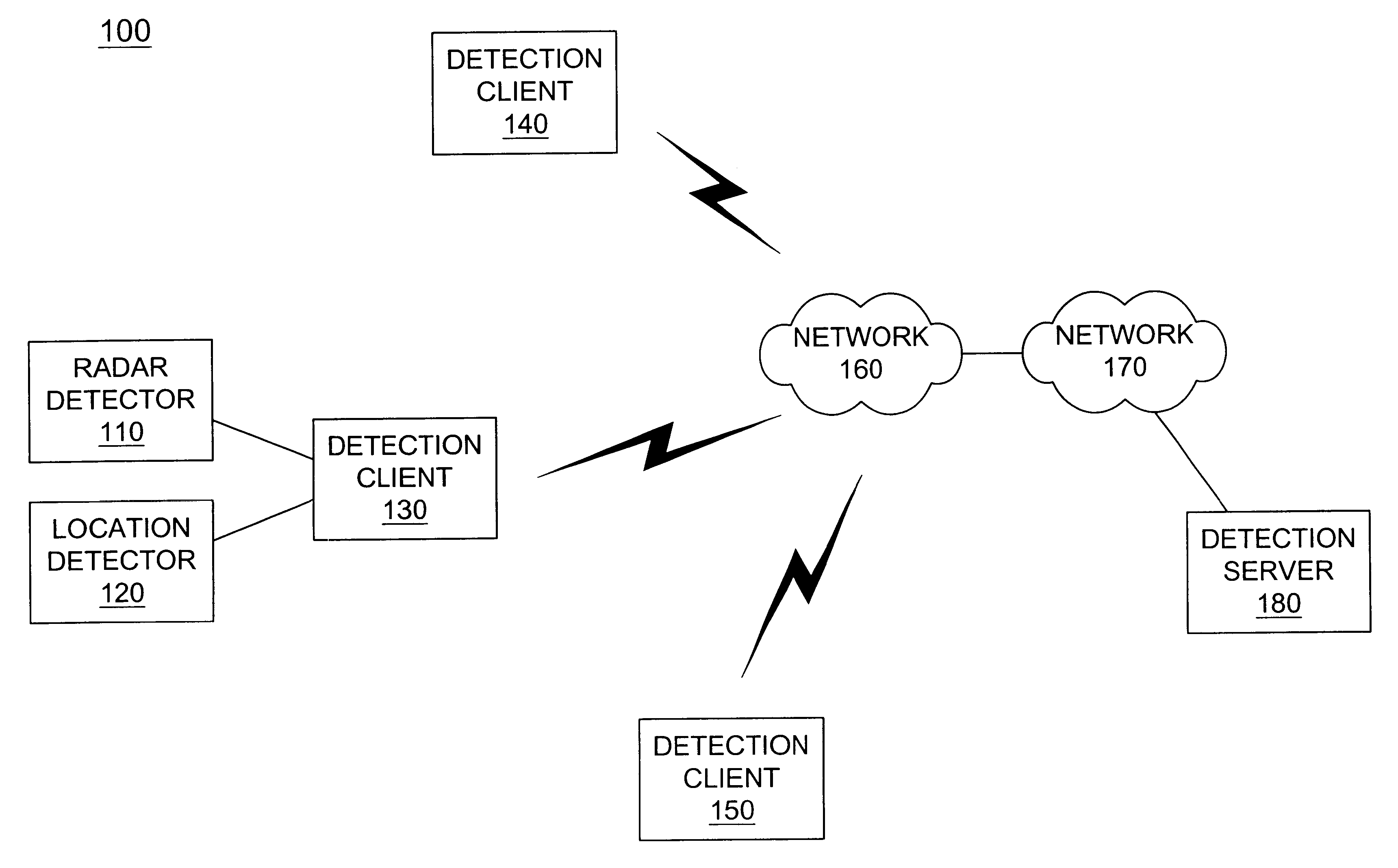
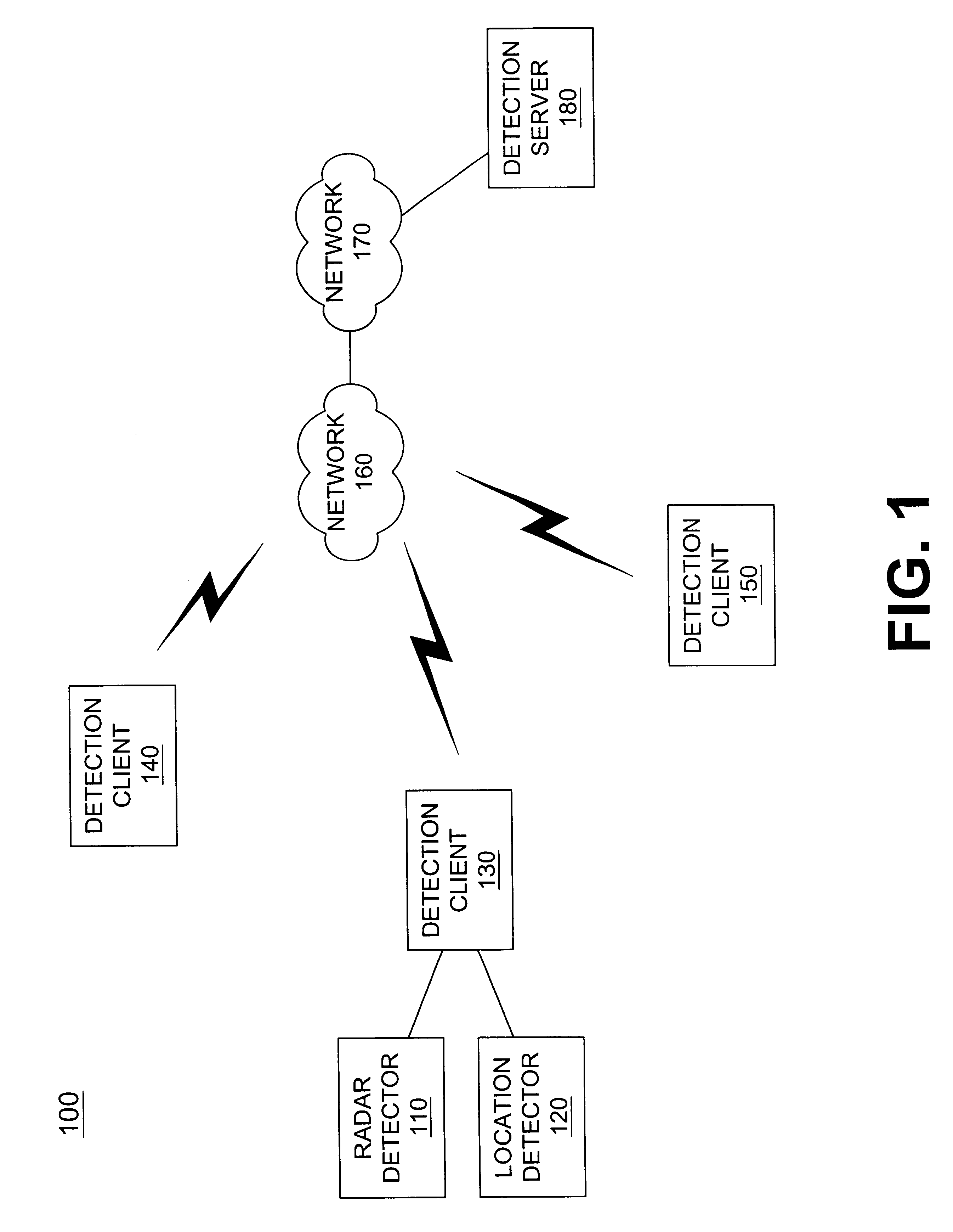
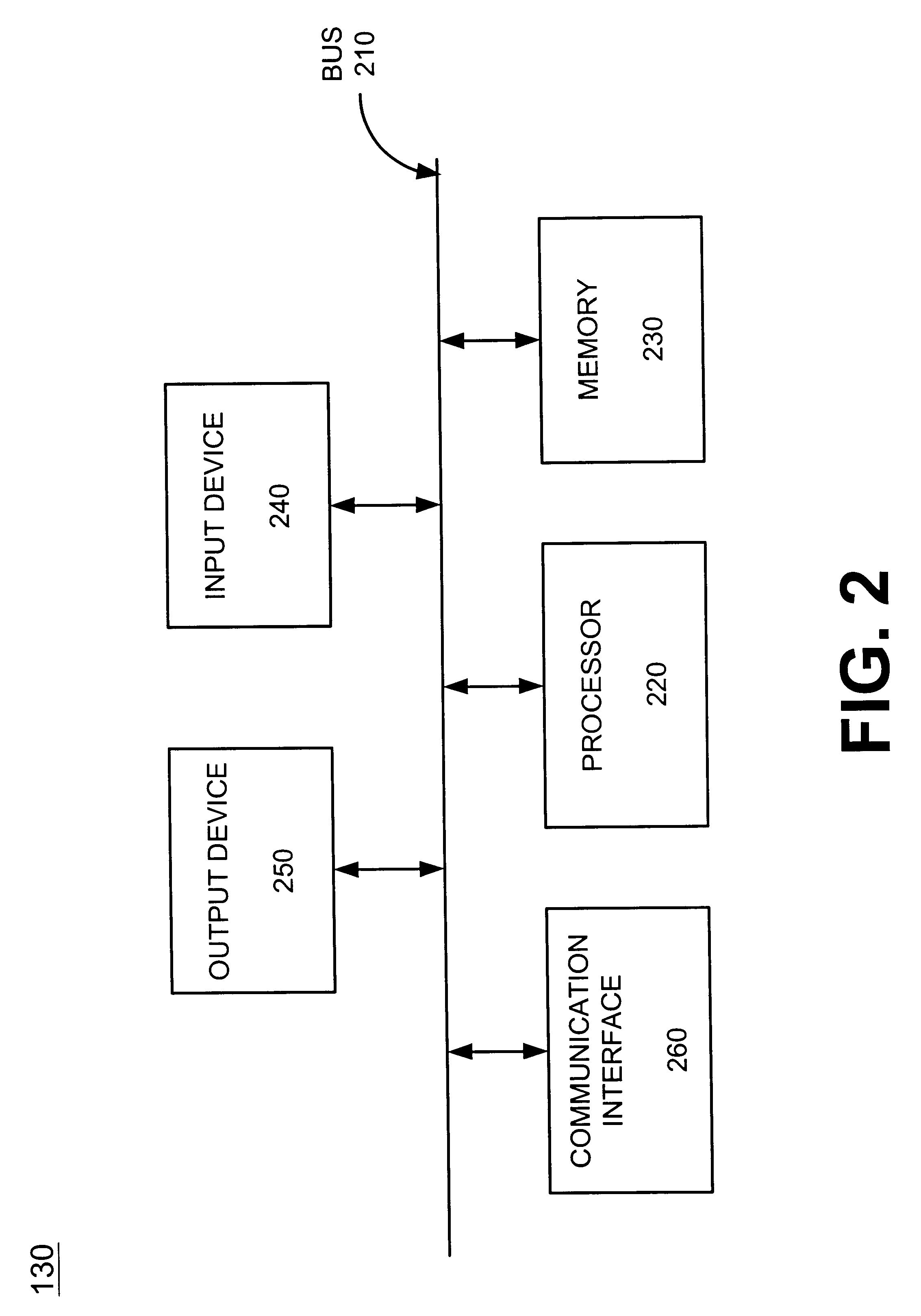
Systems and methods for networking radar detectors
Systems and methods for networking detection devices associated with police activity are provided in a network that includes at least one server (180) and a number of client devices (130-150). Each of the client devices (130-150) transmits its location information to the server for storage. When a client device (130) receives detection information relating to radar activity, a police sighting or other police activity, that client device transmits the detection information to the server (180). The server (180) may then transmit the detection information to other client devices (140,150).
Owner:BBN TECHNOLOGIES CORP
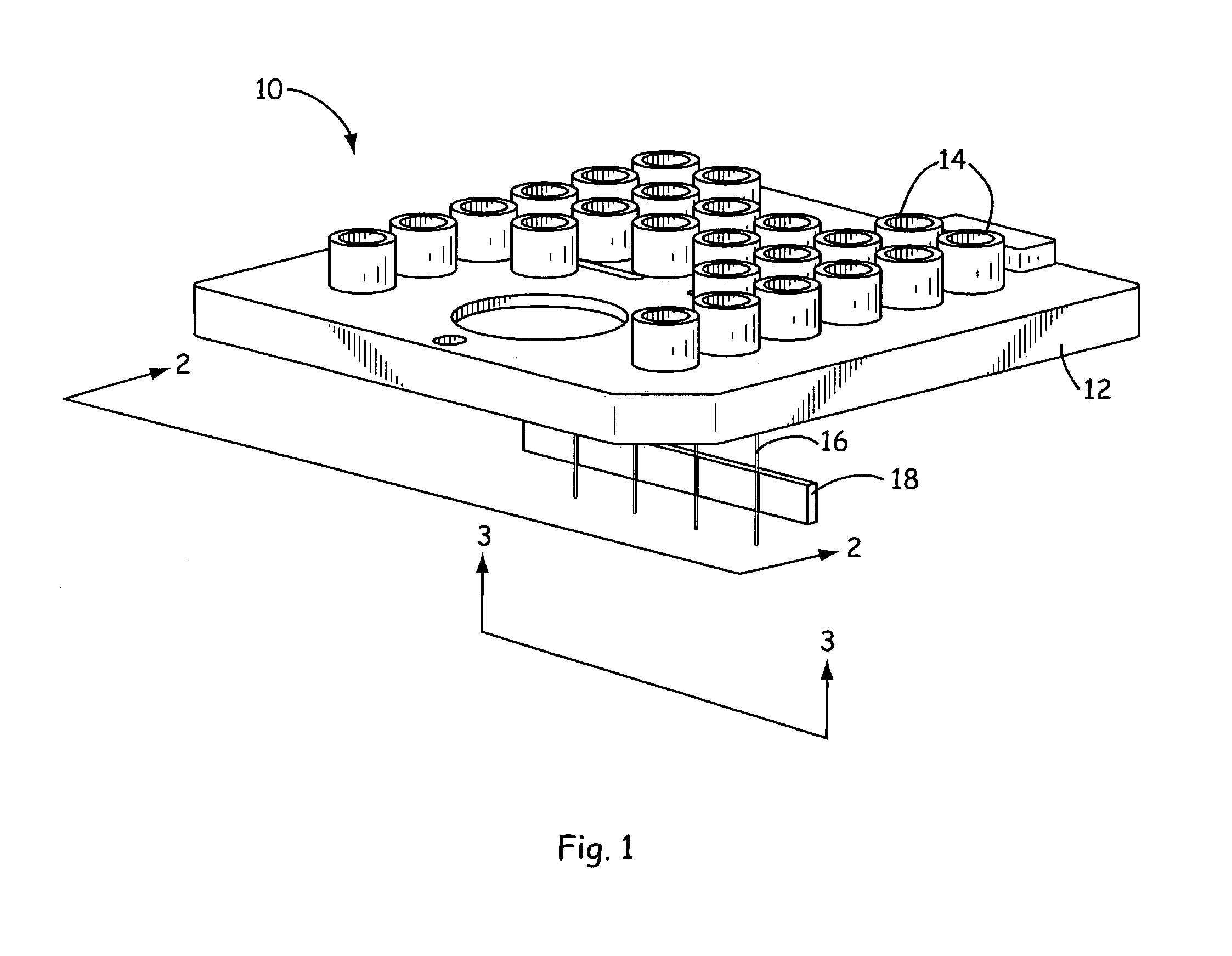
Cartridge with lancets and testing device using the cartridge
Cartridge for a testing device and method of testing using the testing device with the cartridge. The cartridge includes a plurality of lancet needles and a mechanism allowing the cartridge to be mounted to the testing device. The method provides for puncturing a surface of skin using the testing device by arranging the testing device adjacent against a user's skin, triggering the testing device so that one of the plurality of lancet needles is caused to penetrate the user's skin, and rotating the cartridge to another position. This Abstract is not intended to define the invention disclosed in the specification, nor intended to limit the scope of the invention in any way.
Owner:STAT MEDICAL DEVICES
System for monitoring the unauthorized use of a device
ActiveUS20090249460A1Raise the possibilityIncrease opportunitiesError detection/correctionVolume/mass flow measurementDevice MonitorLocal environment
The invention is directed to systems and methods for detecting the loss, theft or unauthorized use of a device and / or altering the functionality of the device in response. In one embodiment, a device monitors its use, its local environment, and / or its operating context to determine that the device is no longer within the control of an authorized user. The device may receive communications or generate an internal signal altering its functionality, such as instructing the device to enter a restricted use mode, a surveillance mode, to provide instructions to return the device and / or to prevent unauthorized use or unauthorized access to data. Additional embodiments also address methods and systems for gathering forensic data regarding an unauthorized user to assist in locating the unauthorized user and / or the device.
Owner:BLANCCO TECH GRP IP OY
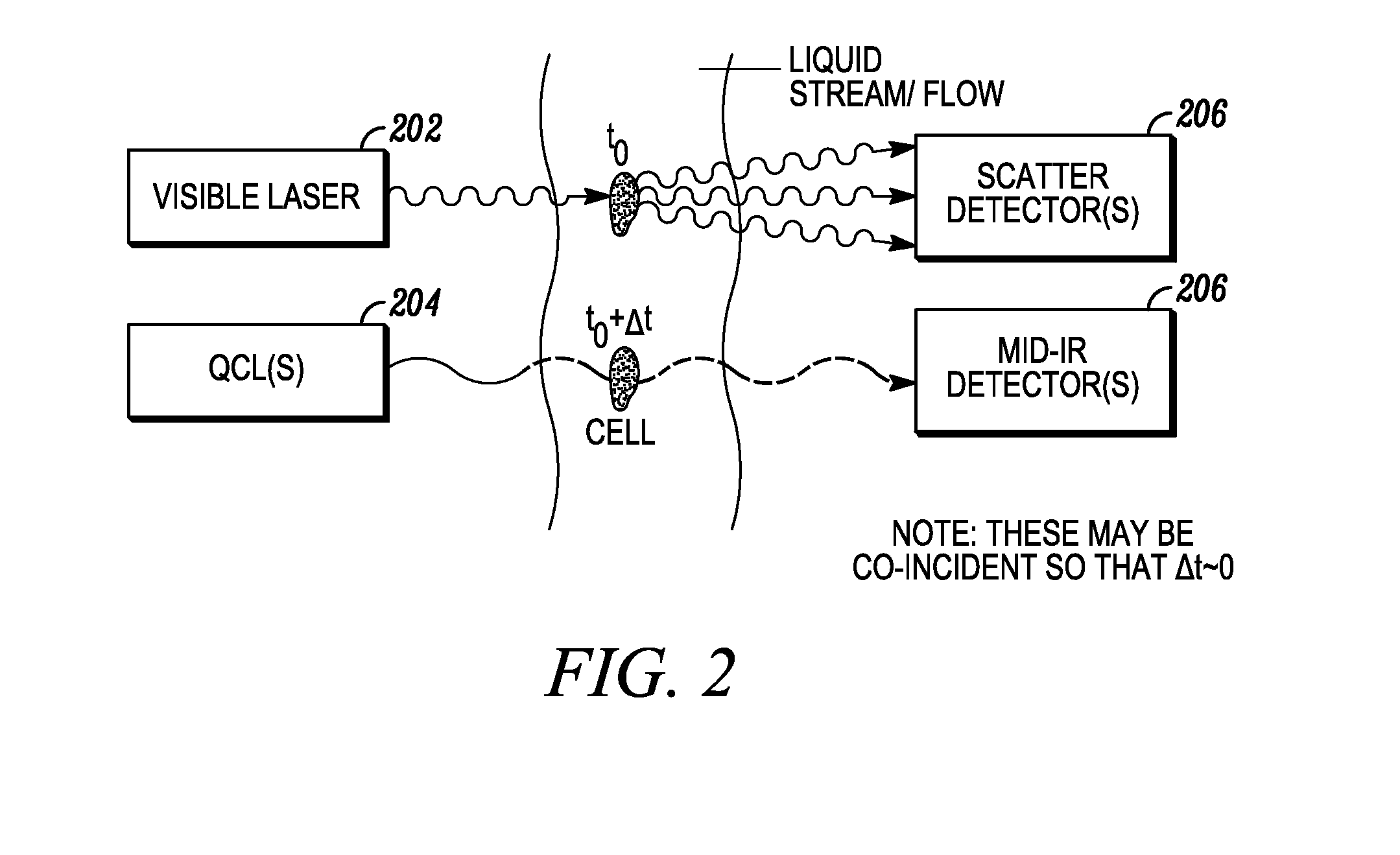
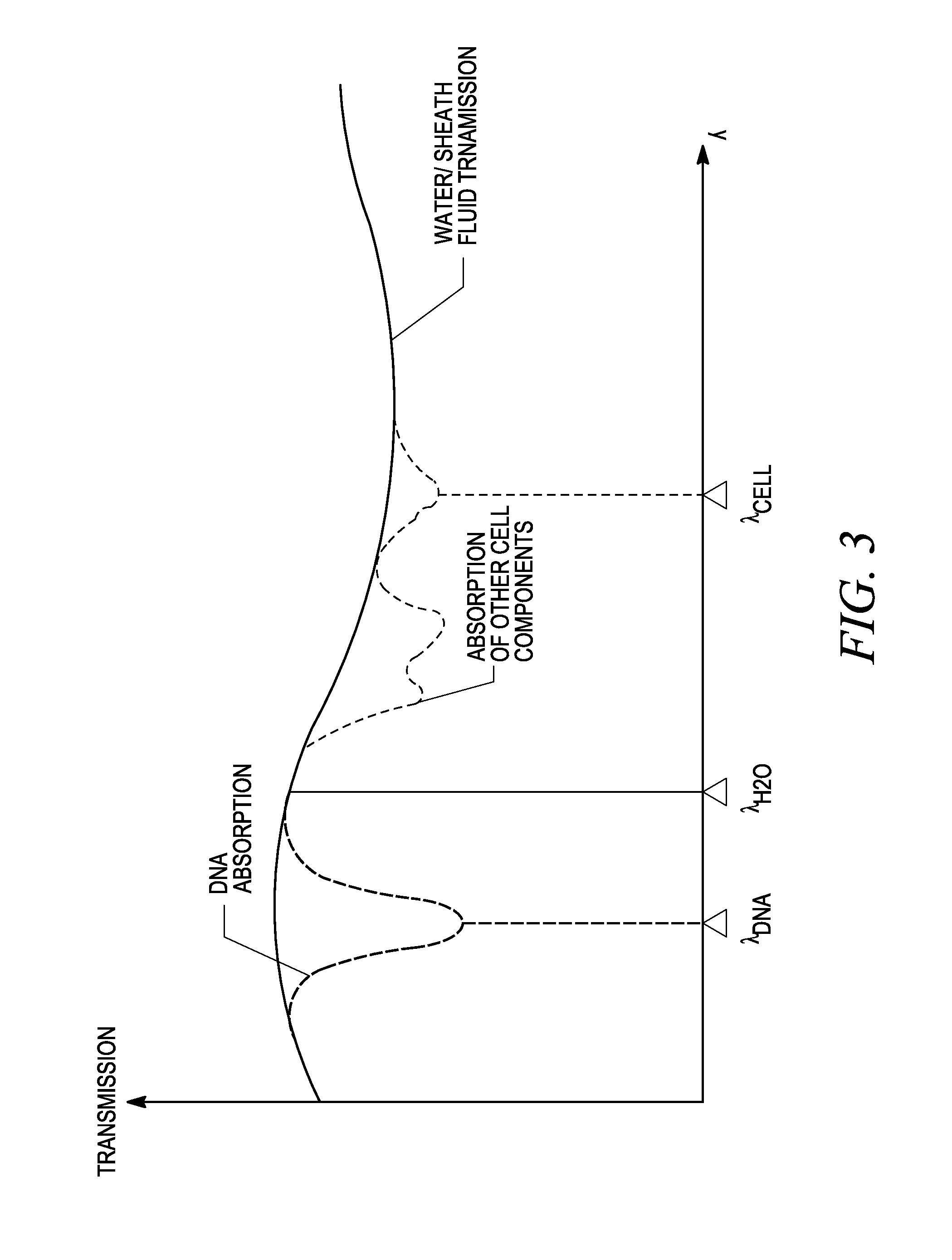
Cytometry system with quantum cascade laser source, acoustic detector, and micro-fluidic cell handling system configured for inspection of individual cells
InactiveUS20120225475A1Bioreactor/fermenter combinationsBiological substance pretreatmentsAnalyteCell handling
This disclosure concerns a cytometry system including a handling system that presents single cells to at least one quantum cascade laser (QCL) source. The QCL laser source is configured to deliver light to a cell within the cells in order to induce resonant mid-IR vibrational absorption by one or more analytes, leading to local heating that results in thermal expansion and an associated shockwave. An acoustic detection facility that detects the shockwave emitted by the single cell.
Owner:1087 SYST
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com