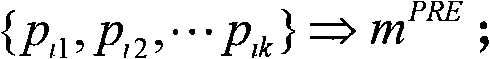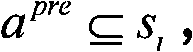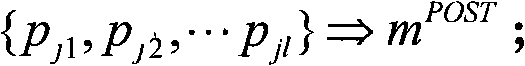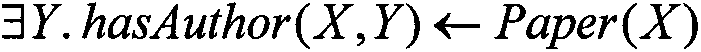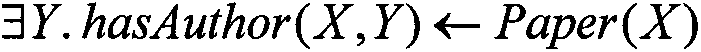Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
30 results about "Datalog" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Datalog is a declarative logic programming language that syntactically is a subset of Prolog. It is often used as a query language for deductive databases. In recent years, Datalog has found new application in data integration, information extraction, networking, program analysis, security, and cloud computing.
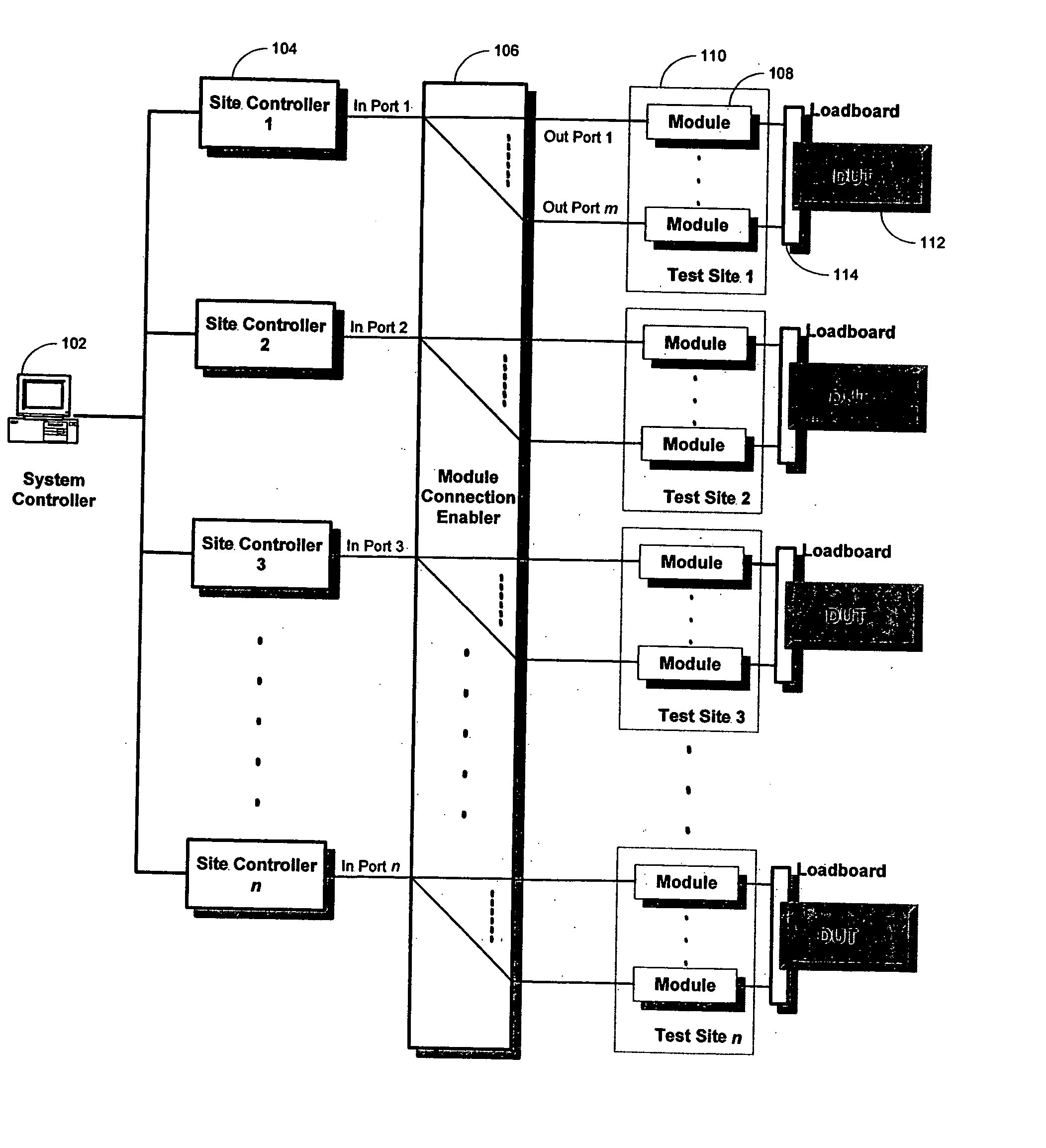
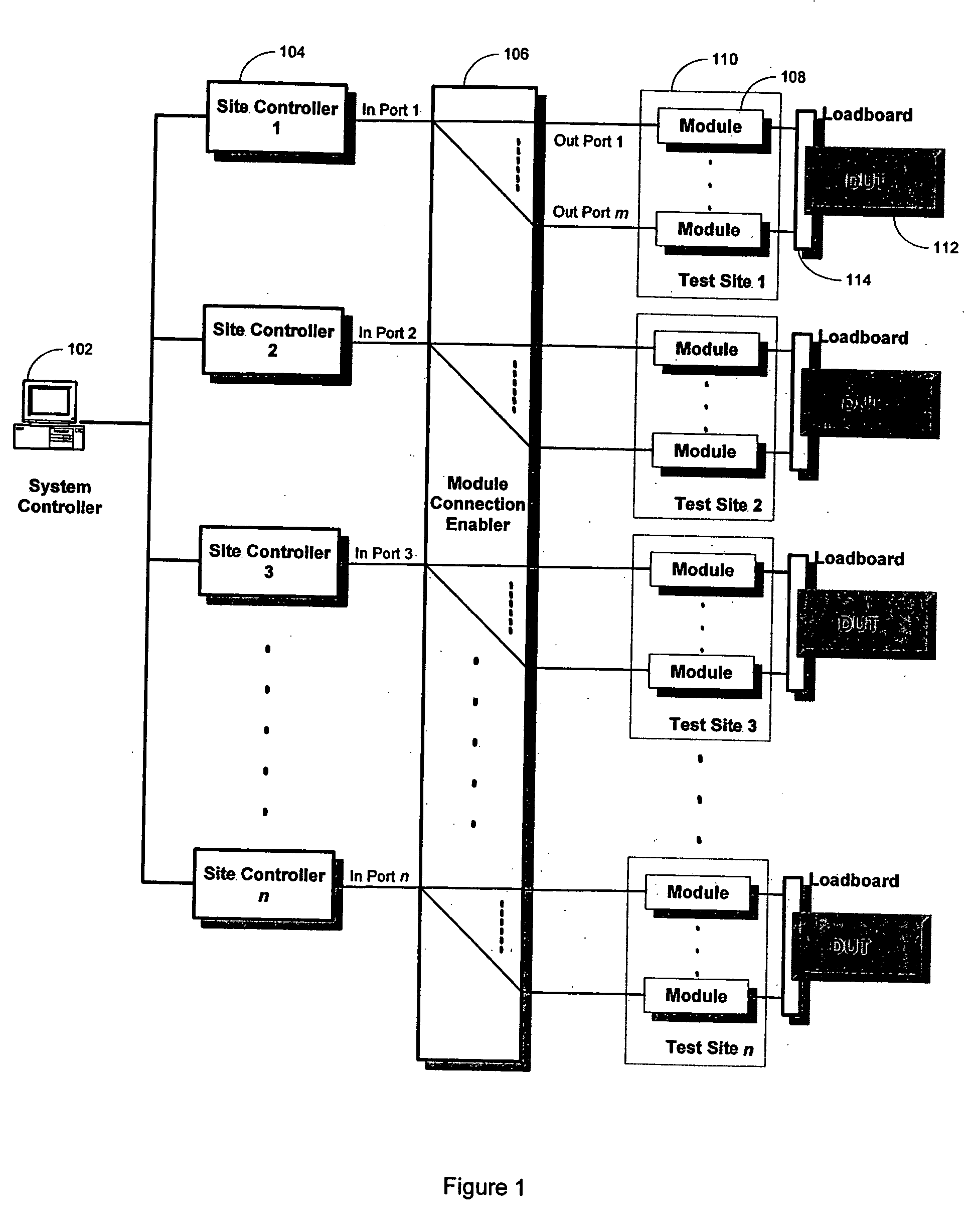
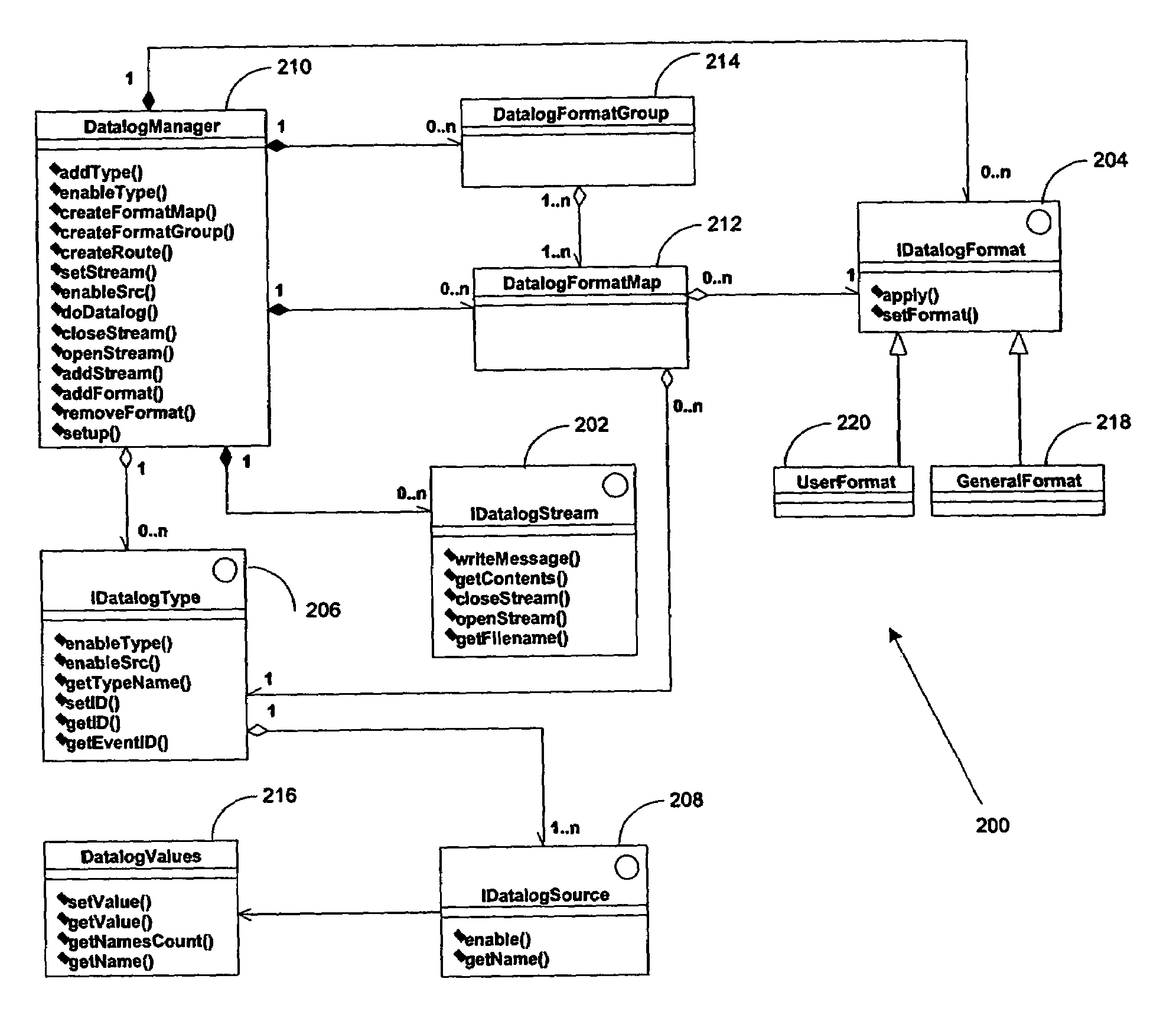
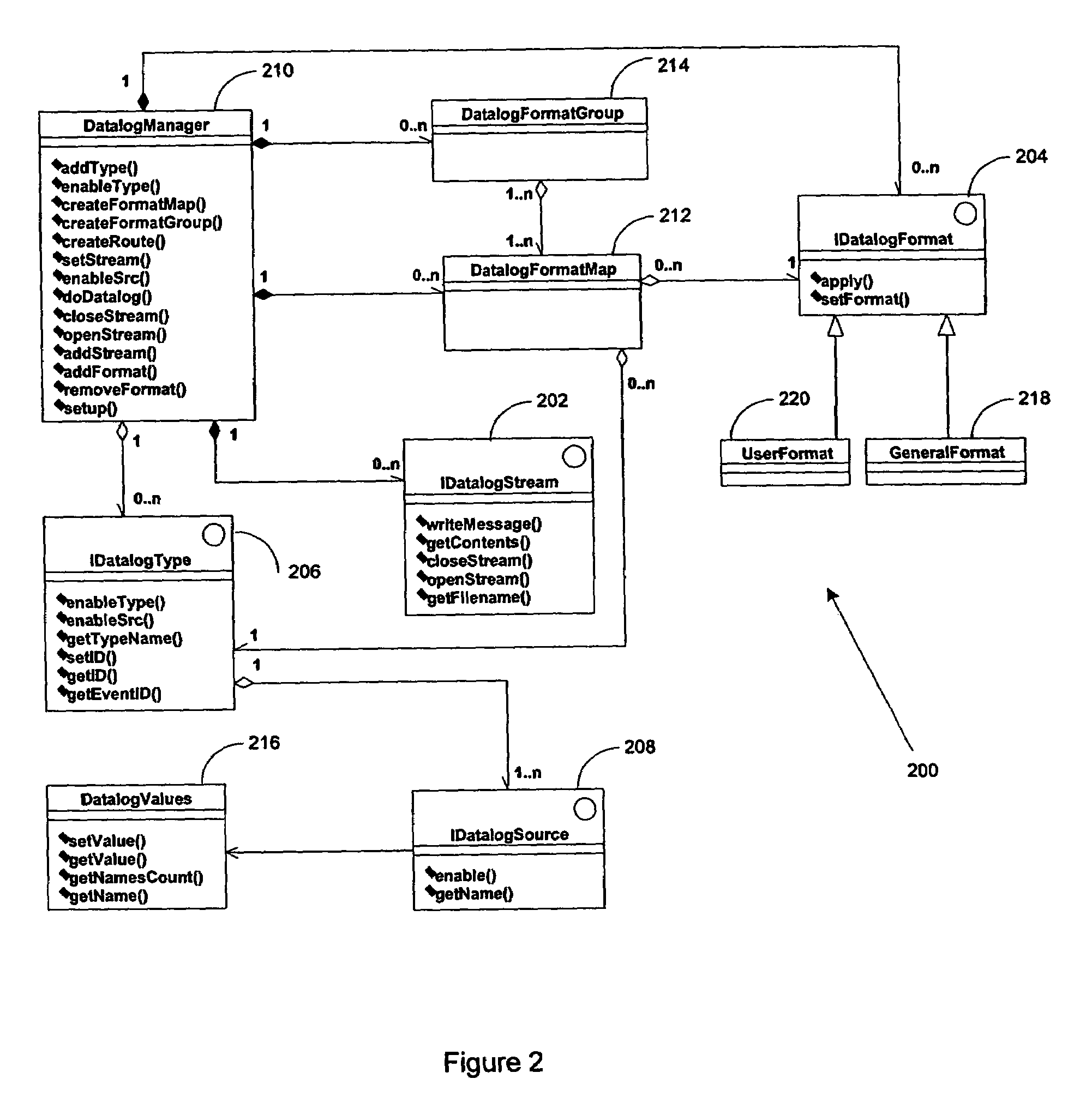
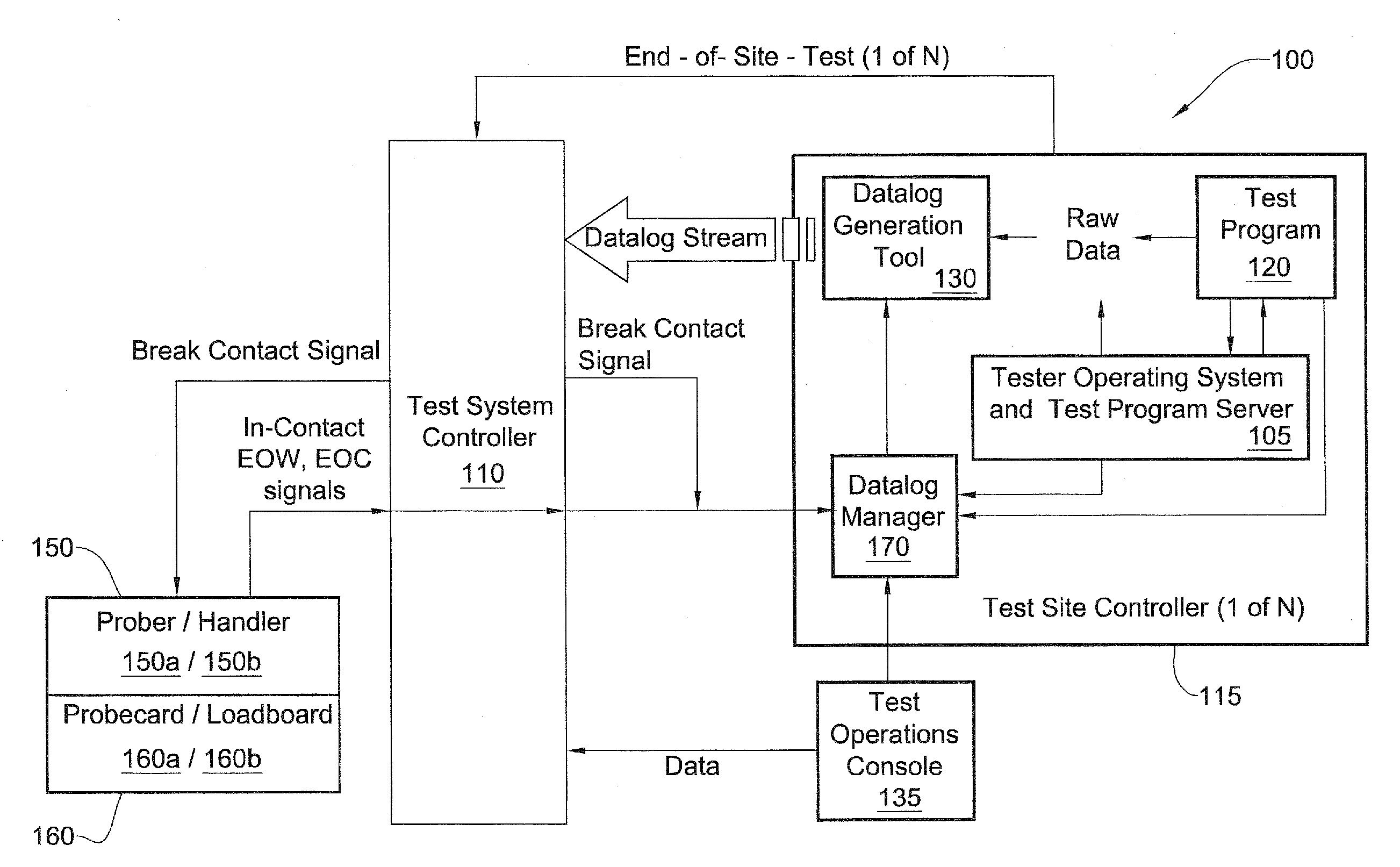
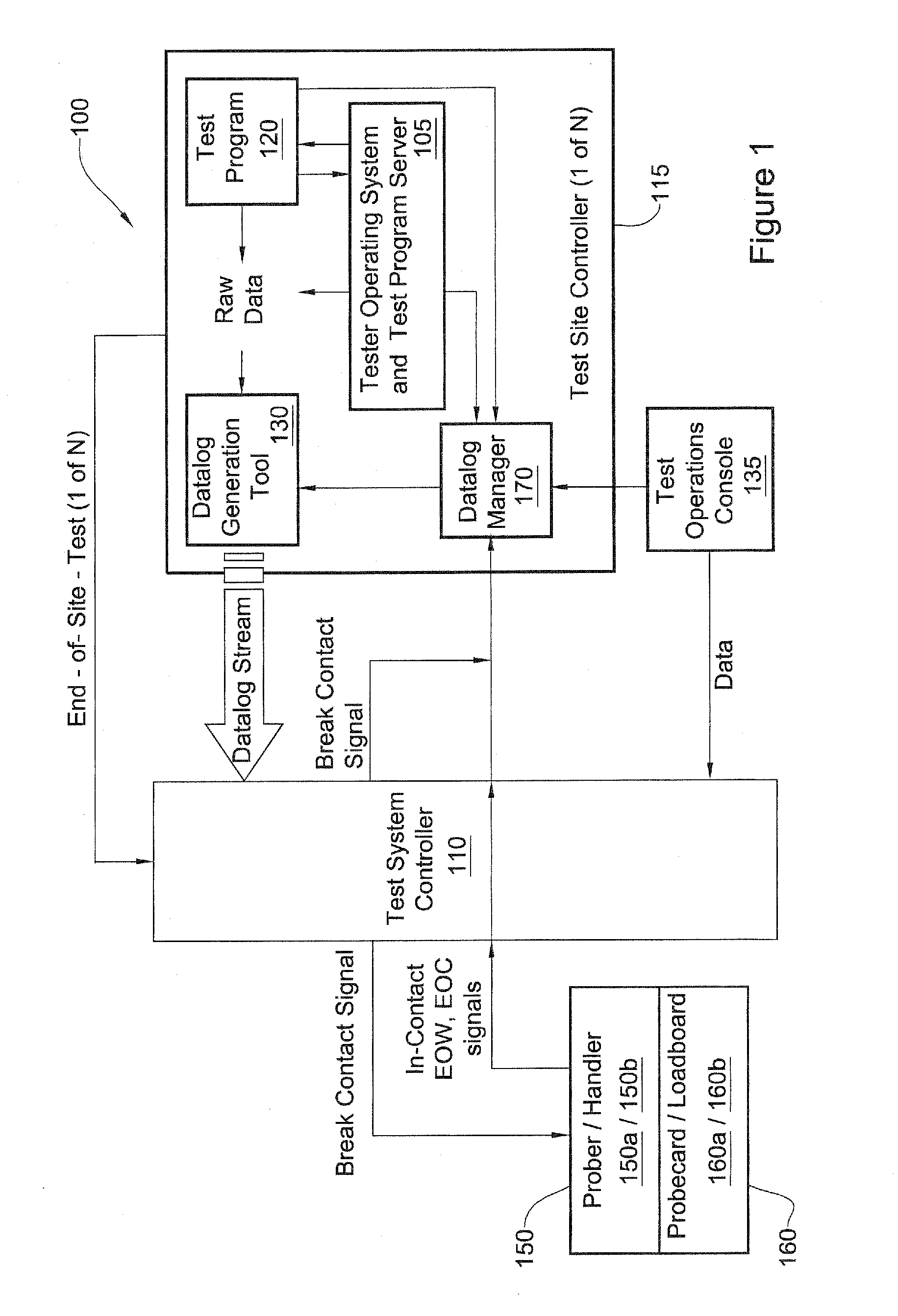
Datalog support in a modular test system
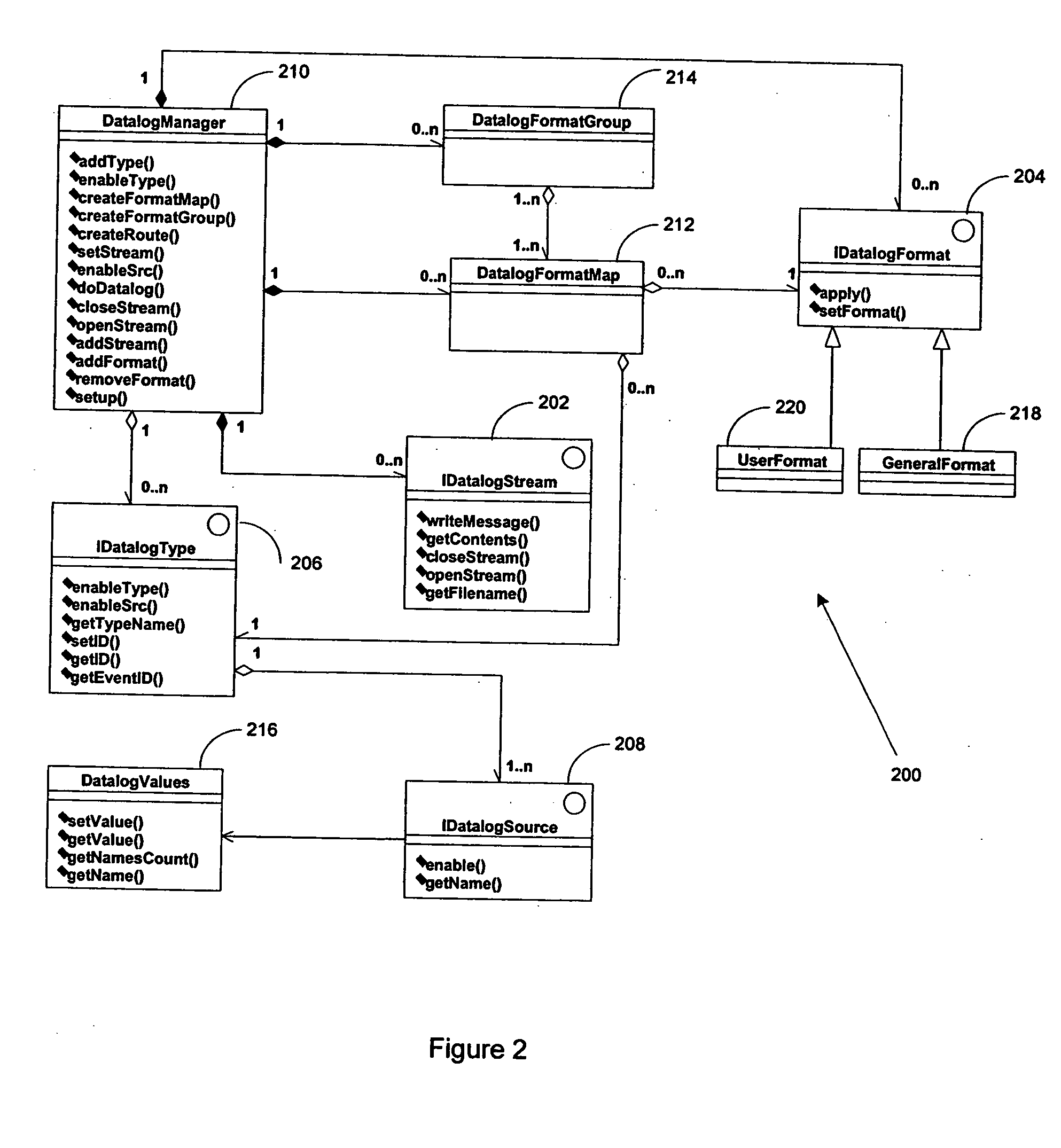
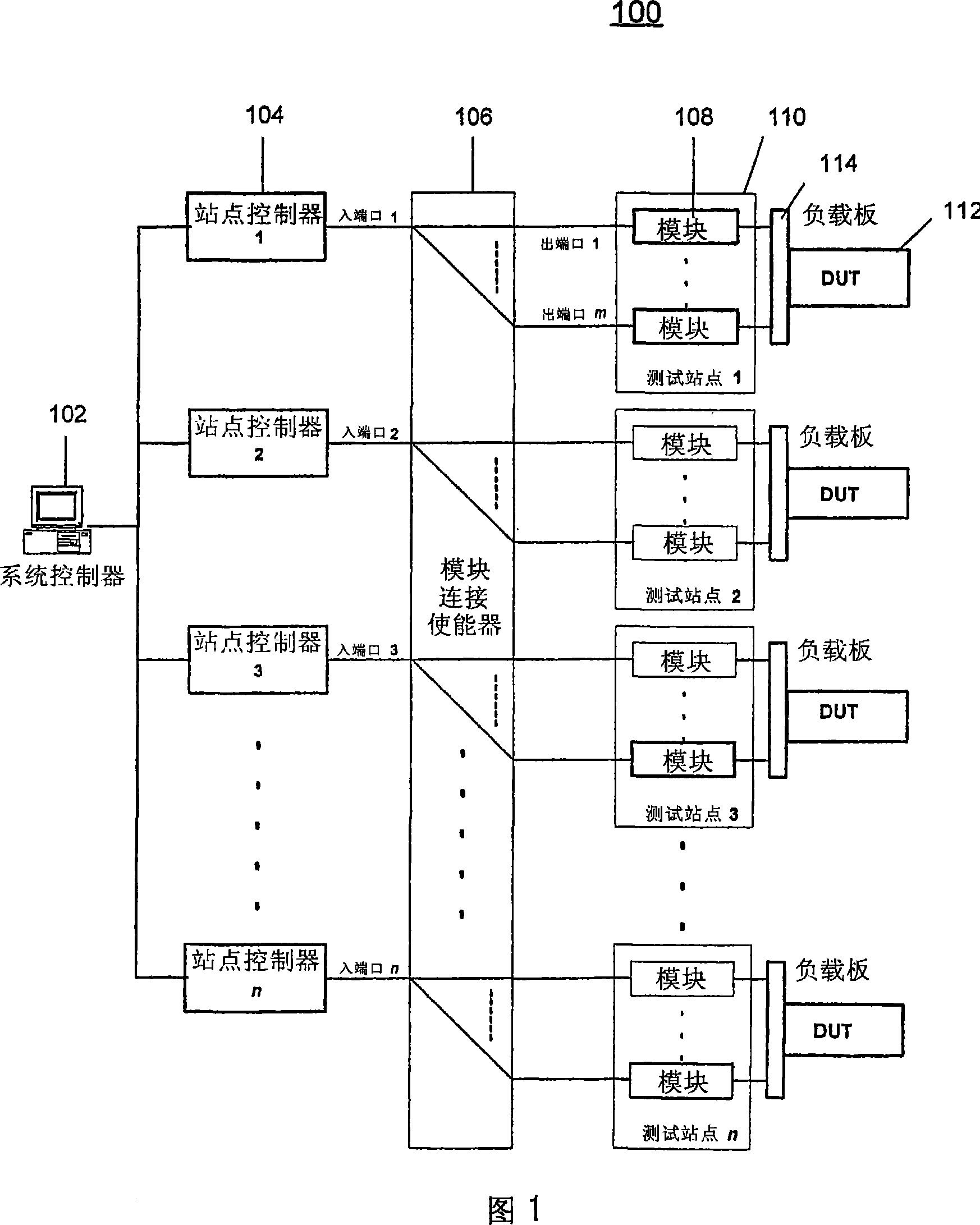
A method for communicating test information from a source to a destination is disclosed. The method includes providing a modular test system, where the modular test system comprises a system controller for controlling at least one site controller, the at least one site controller for controlling at least one test module. The method further includes providing a datalog framework for supporting extension of user-defined datalog formats, providing support classes for supporting user-initiated datalog events, receiving a datalog event requesting for communicating input test information from the source to the destination, configuring output test information based upon the destination, the datalog framework and the support classes, and transferring the output test information to the destination.
Owner:ADVANTEST AMERICA R & D CENT
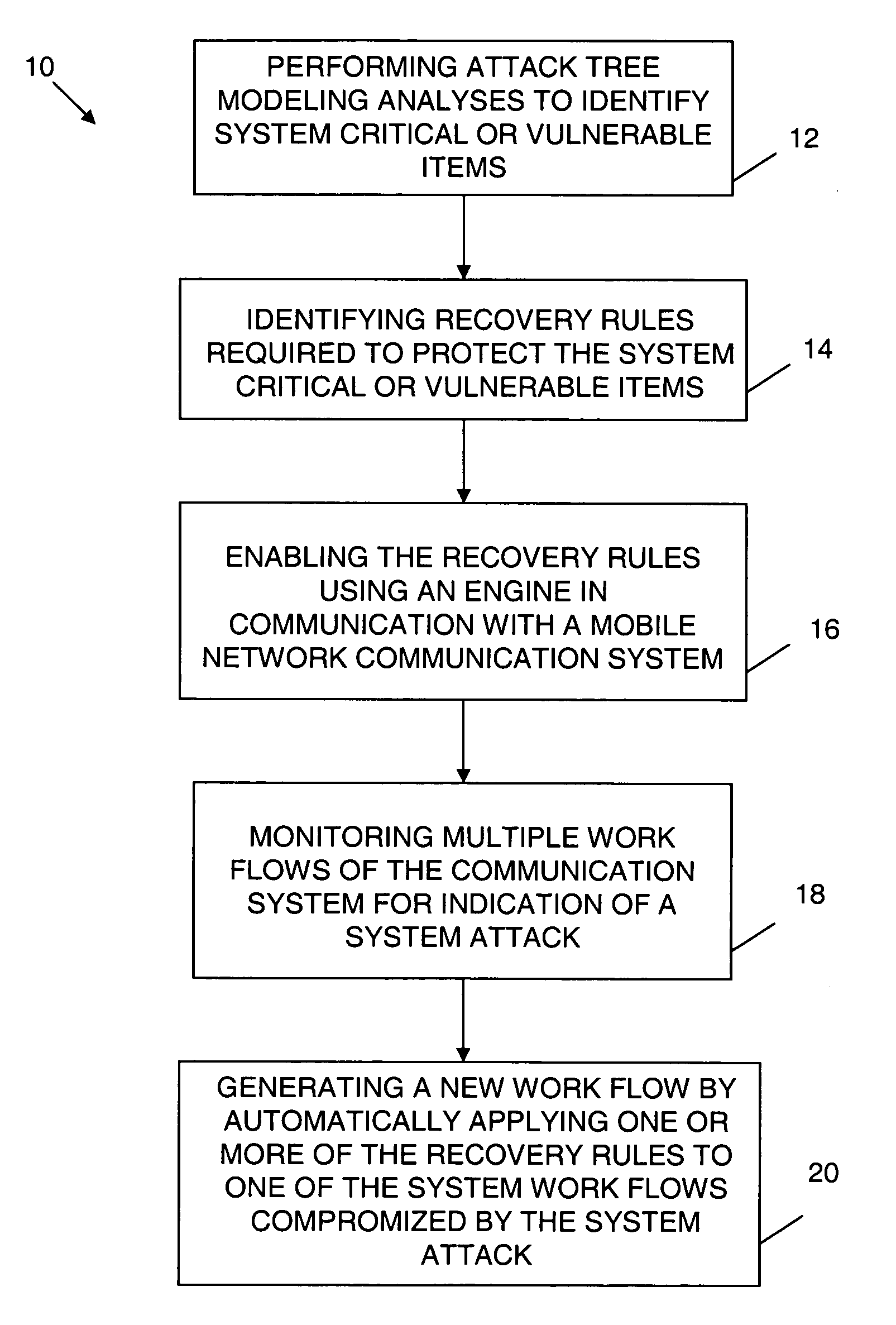
Mobile network dynamic workflow exception handling system
ActiveUS20060259341A1Promote recoveryImprove survivabilityDigital computer detailsResourcesNetwork communicationHandling system
An exception handling system and method are provided for dynamically recovering from a workflow exception occurring in a mobile network communication system. The system has multiple workflows and at least one mission critical item. An attack tree modeling analyses is performed to identify the mission critical item. Another operation includes writing a plurality of forward recovery rules to protect the mission critical item using a transaction datalog fragment of transaction logic. The recovery rules are enabled through an engine in communication with the mobile network communication system. The multiple workflows are monitored for indication of a system attack on any one of the multiple workflows. A new workflow is automatically generated upon detection of the system attack. The exception handling system is overlayed on the mobile network.
Owner:THE BOEING CO
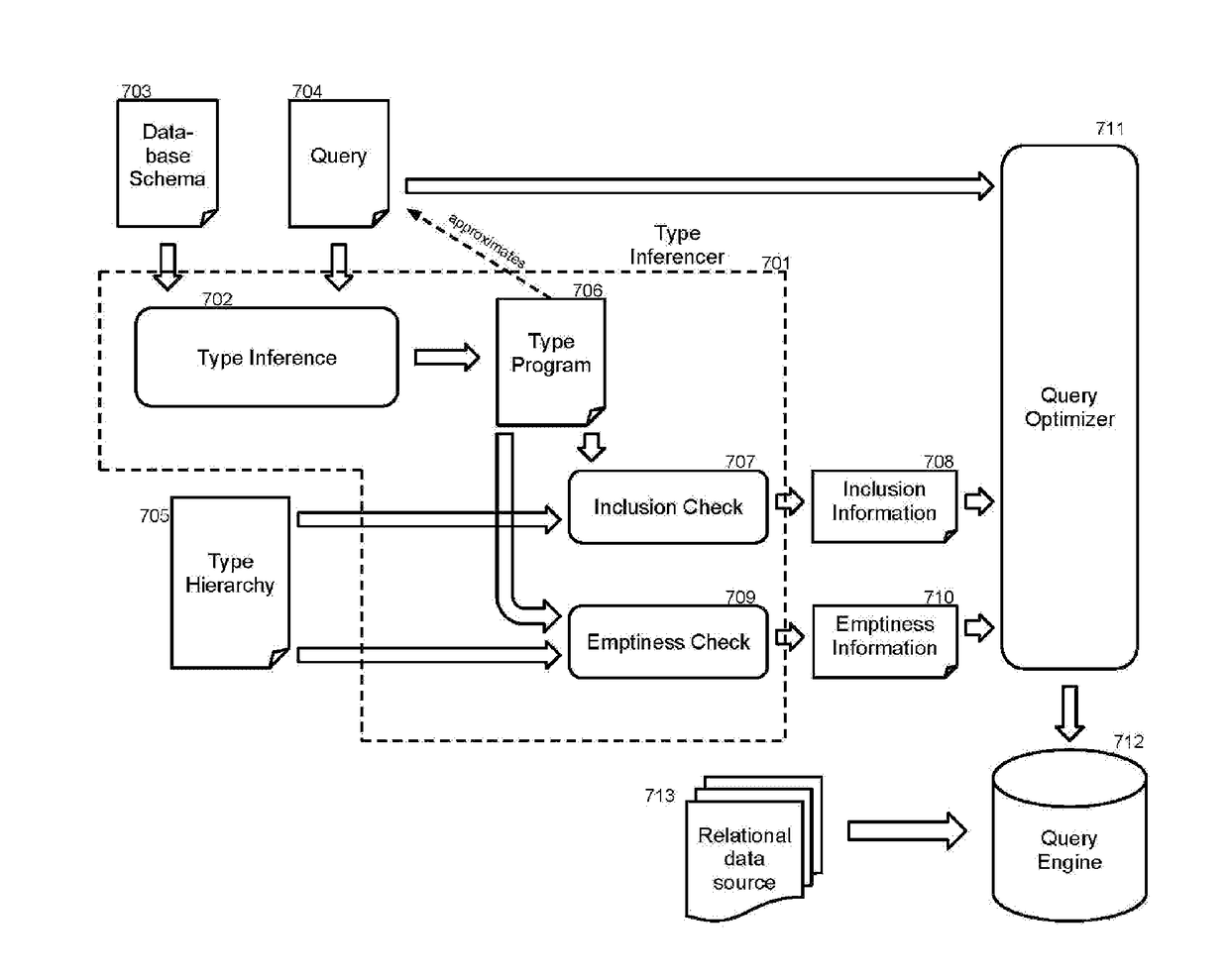
Type inference for datalog with complex type hierarchies
ActiveUS20120016912A1Digital data information retrievalDigital data processing detailsComplex typeDatabase query
What is disclosed are a novel system and method for inferring types of database queries. In one embodiment a program and associated database schema that includes a type hierarchy is accessed. The program includes query operations to a database that contains relations described by a database schema. Types are inferred from definitions in the program by replacing each database relationship in the program by the types in the database schema. A new program is generated with the types that have been inferred with the new program only accessing unary relations in the database. In another embodiment, testing of each of the types that have been inferred is performed for type emptiness. In response to type emptiness being found for a type that have been inferred, a variety of different operations are performing including removing the type, providing a notification regarding the emptiness found for the type, and more.
Owner:MICROSOFT TECH LICENSING LLC
Defect detection method of browser extension
InactiveCN102799524AFully automatedHigh precisionSoftware testing/debuggingSource codeAbstract syntax tree
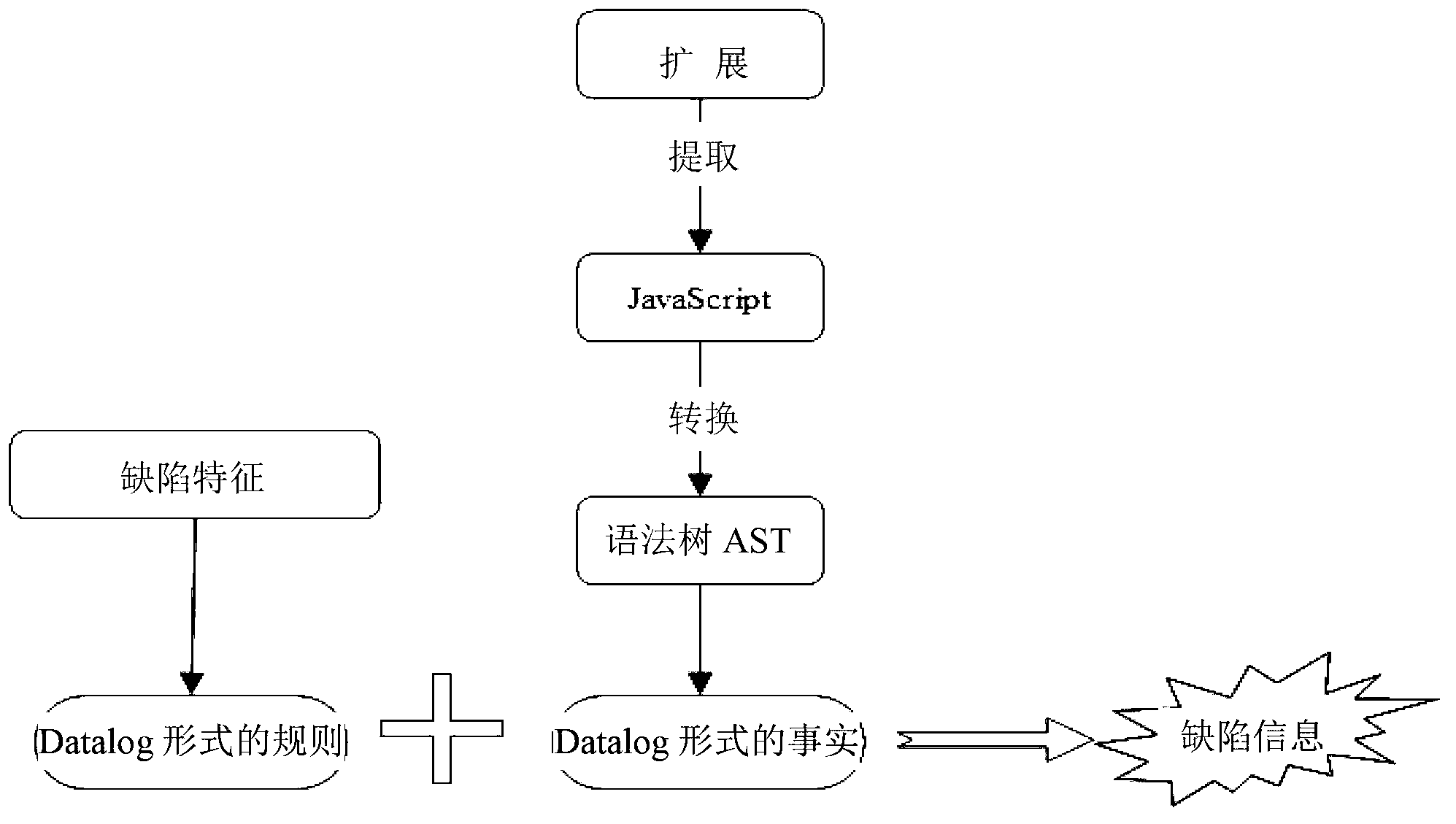
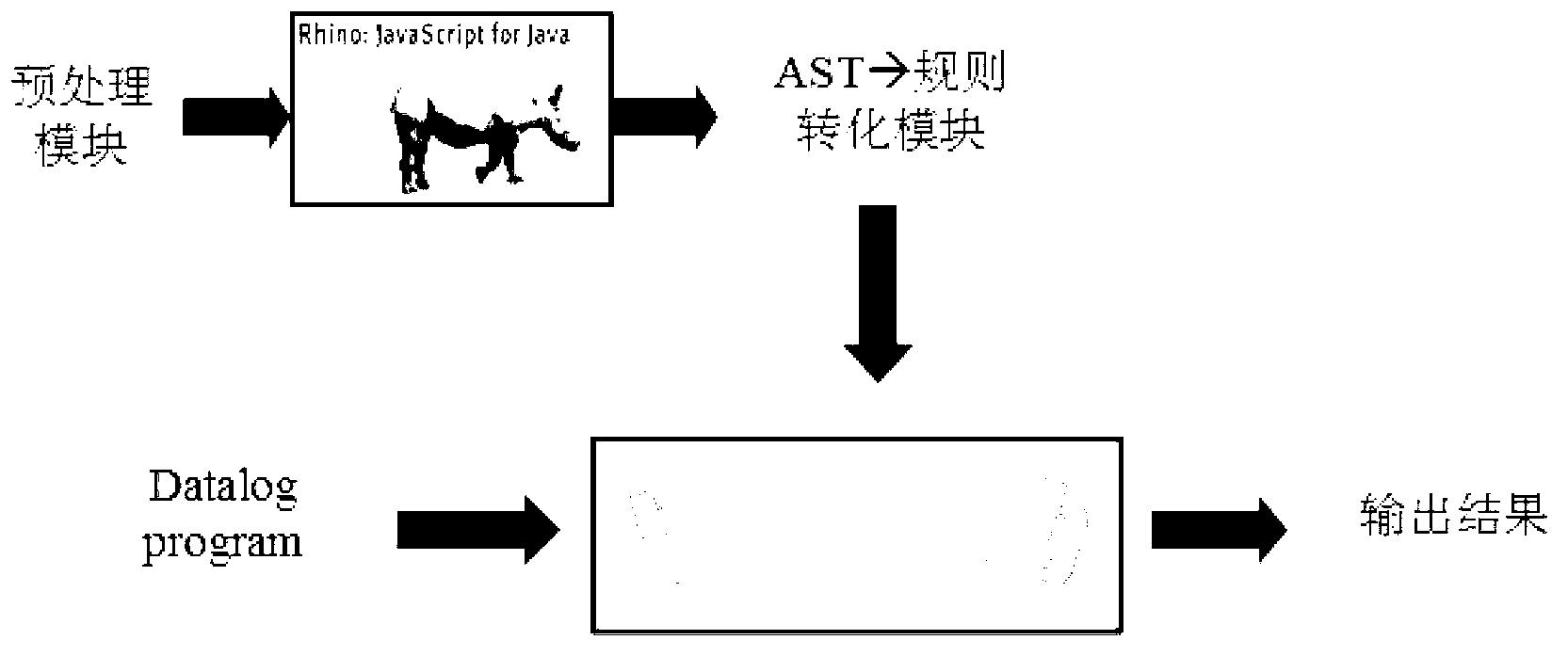
The invention discloses a defect detection method of browser extension. The defect detection method comprises the following steps: (1) converting an extended defect feature into the defect information in a Datalog language format as a rule, constructing a safe defect feature library about the extension by the rule; (2) preprocessing an extension source code, separating a JavaScript code, which describes the extension behavior, from the source code, and converting the JavaScript code into the information in Datalog language format as a fact; (3) changing the JavaScript code into an abstract syntax tree, and converting the JavaScript code into the Datalog language format; and (4) storing the extension information to be detected as a deductive database, carrying out deductive database ratiocination, and finding the part matched with the item of the defect in the safe defect feature library from the extended deductive database so as to realize the detection of the extension. Compared with the prior art, according to the defect detection method of browser extension, the automation of the work of manual review of the browser extension is realized, and precision is improved.
Owner:TIANJIN UNIV
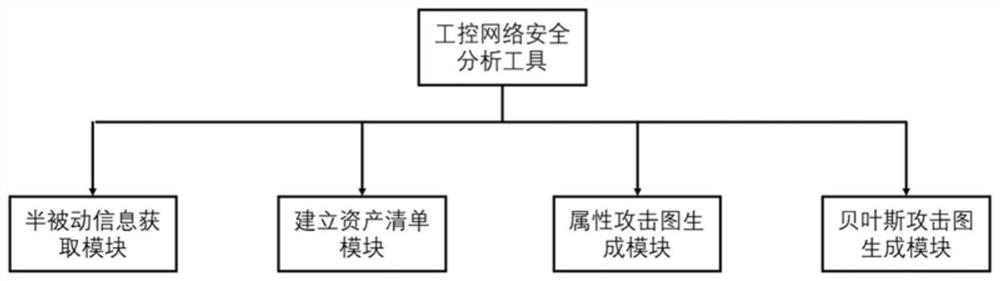
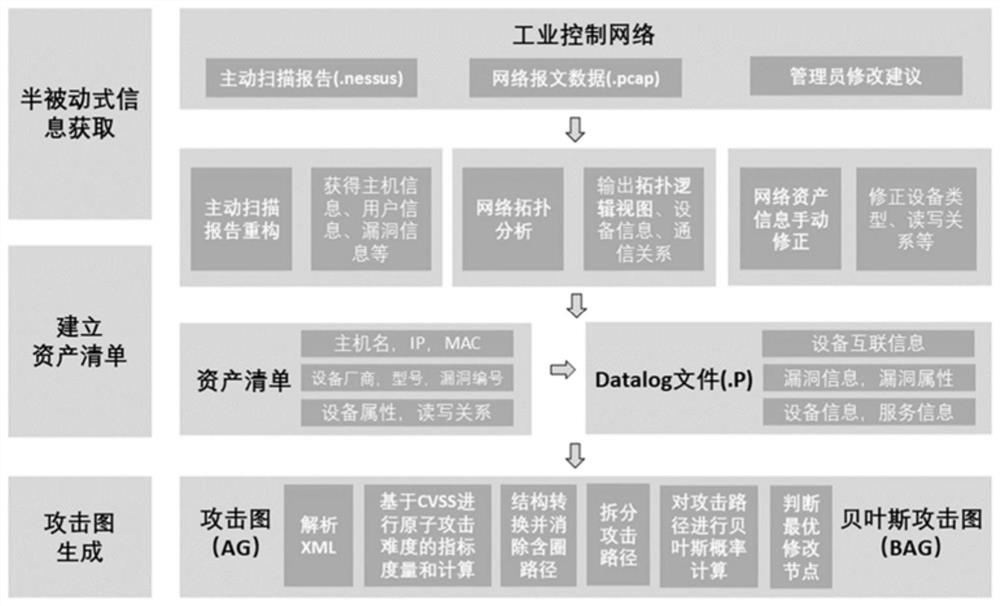
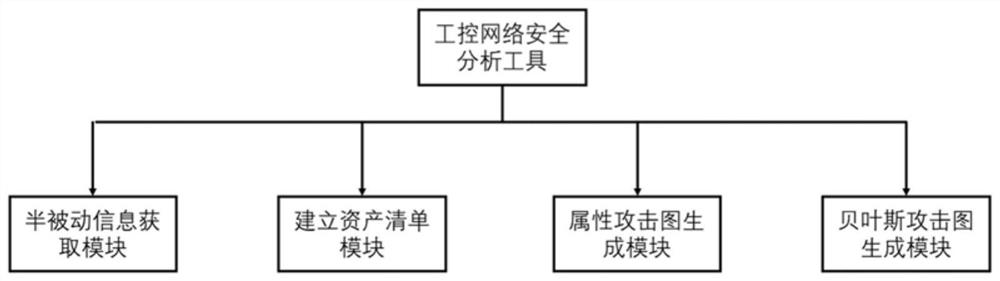
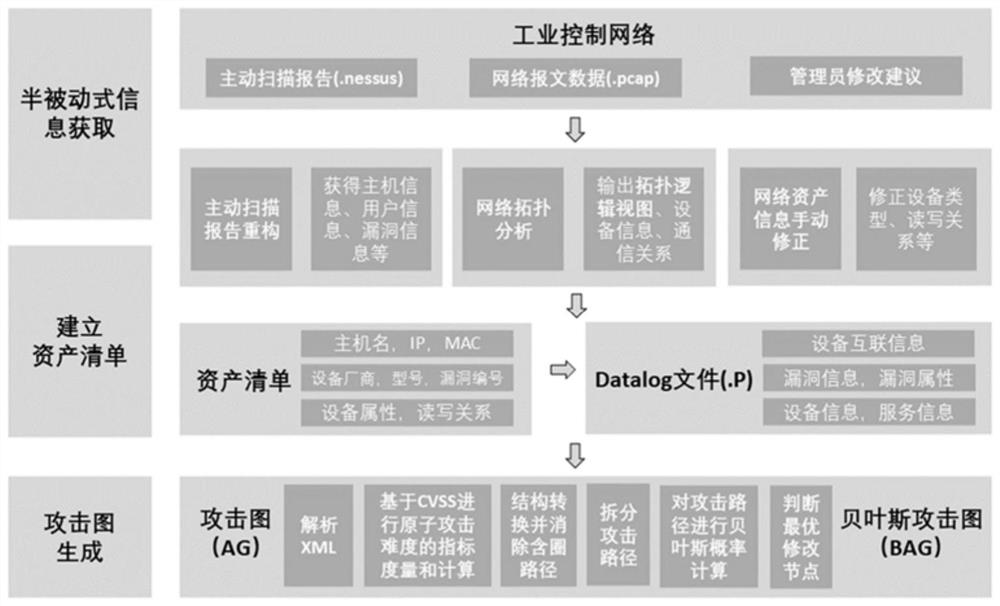
Semi-passive industrial control network security analysis tool and method based on Bayesian attack graph
ActiveCN112653582AReduce occupancyImprove compatibilityData switching networksAttackGraph generation
The invention provides a Bayesian attack graph-based semi-passive industrial control network security analysis tool and a Bayesian attack graph-based semi-passive industrial control network security analysis method, which relate to the technical field of network security, and comprise a semi-passive information acquisition module for acquiring a combination of an active scanning report, network message data and administrator correction suggestions and taking the combination as an input file; an asset list establishing module: establishing an asset list, and generating. P files as input files of the attribute attack graph generation module and the Bayesian attack graph generation module; an attribute attack graph generation module which is used for inputting template network topology information and node information and generating an attack path; and a Bayesian attack graph generation module which is used for comprehensively analyzing the information of the whole network based on the network information and logic rules recorded by the Datalog statement, and finally generating all possible attack graphs. The method has high compatibility for an industrial control network, comprehensively utilizes multiple charts to visually assist network security analysis, and can achieve dynamic analysis and hidden danger prevention and control.
Owner:SHANGHAI JIAO TONG UNIV
Datalog support in a modular test system
A method for communicating test information from a source to a destination is disclosed. The method includes providing a modular test system, where the modular test system comprises a system controller for controlling at least one site controller, the at least one site controller for controlling at least one test module. The method further includes providing a datalog framework for supporting extension of user-defined datalog formats, providing support classes for supporting user-initiated datalog events, receiving a datalog event requesting for communicating input test information from the source to the destination, configuring output test information based upon the destination, the datalog framework and the support classes, and transferring the output test information to the destination.
Owner:ADVANTEST AMERICA R & D CENT
Datalog management in semiconductor testing
Methods, systems and modules for datalog management. In one embodiment, the logging of data is allowed to at least occasionally occur while the handling equipment is preparing device(s) for testing. Additionally or alternatively, in one embodiment with a plurality of test site controllers, after testing has been completed at all test site(s) associated with a particular test site controller the logging of data relating to that test site controller is allowed to at least occasionally occur while testing is continuing at test site(s) associated with other test site controller(s).
Owner:OPTIMAL PLUS
Type inference for datalog with complex type hierarchies
ActiveUS8595213B2Digital data information retrievalDigital data processing detailsComplex typeDatabase schema
What is disclosed are a novel system and method for inferring types of database queries. In one embodiment a program and associated database schema that includes a type hierarchy is accessed. The program includes query operations to a database that contains relations described by a database schema. Types are inferred from definitions in the program by replacing each database relationship in the program by the types in the database schema. A new program is generated with the types that have been inferred with the new program only accessing unary relations in the database. In another embodiment, testing of each of the types that have been inferred is performed for type emptiness. In response to type emptiness being found for a type that have been inferred, a variety of different operations are performing including removing the type, providing a notification regarding the emptiness found for the type, and more.
Owner:MICROSOFT TECH LICENSING LLC
Automatic threat ensuring method facing to network security risk assessment based on first order logic predicate reasoning
The invention discloses an automatic threat ensuring method facing to network security risk assessment based on first order logic predicate reasoning. The method uses a first order logic predicate descriptive language Datalog to formally describe network security state information and attack rule knowledge base information, uses a logic reasoning engine XSB to automatically reason, and analyzes the evidence files in a reasoning result to obtain threat information in a current network system; wherein, the threat information comprises a threat potential attack source, a corresponding loophole and a possible attack action. By adopting the logical reasoning engine, the automatic threat ensuring method can automatically and effectively ensure the attack threat in a large-scale network system, greatly reduce the working pressure of network administrators, and help the network administrators to purposely adopt preventive measures to protect the network system.
Owner:BEIHANG UNIV
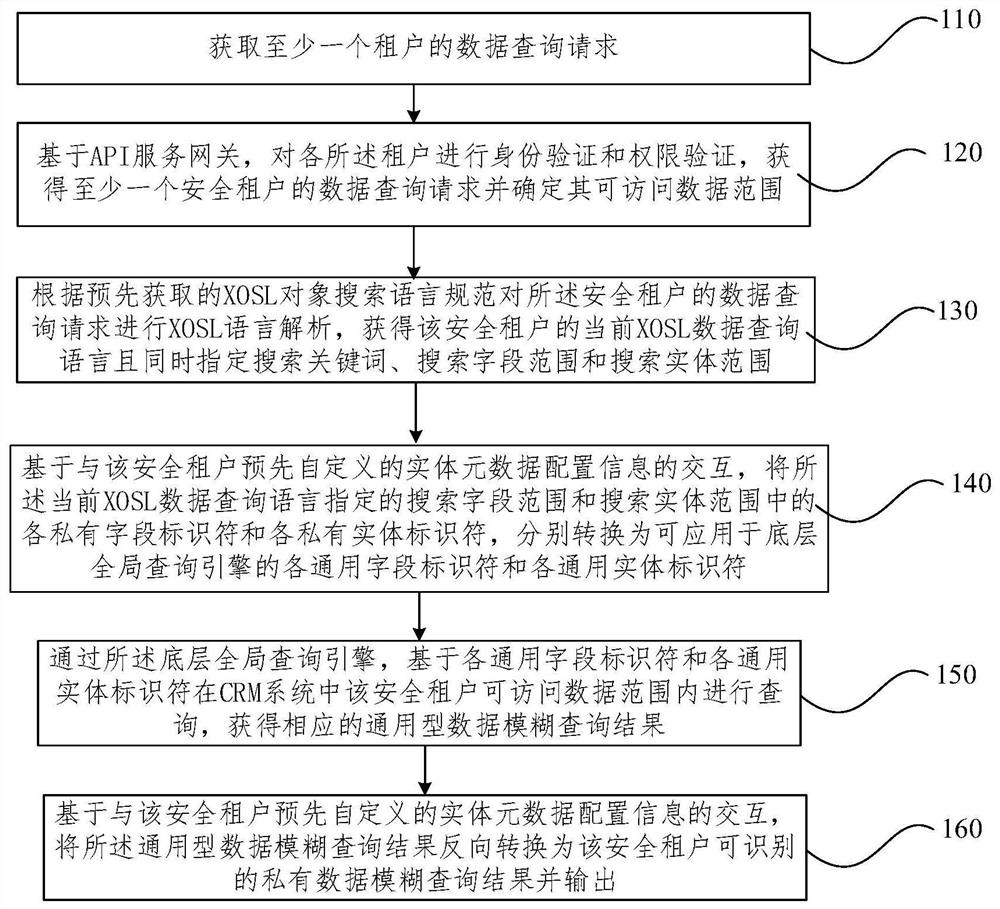
Data fuzzy query method and device for multi-tenant CRM system in SaaS environment
PendingCN113342876ARealize the effect of global data fuzzy queryThe query process is simple, optimized and safeDigital data information retrievalSpecial data processing applicationsData queryDatalog
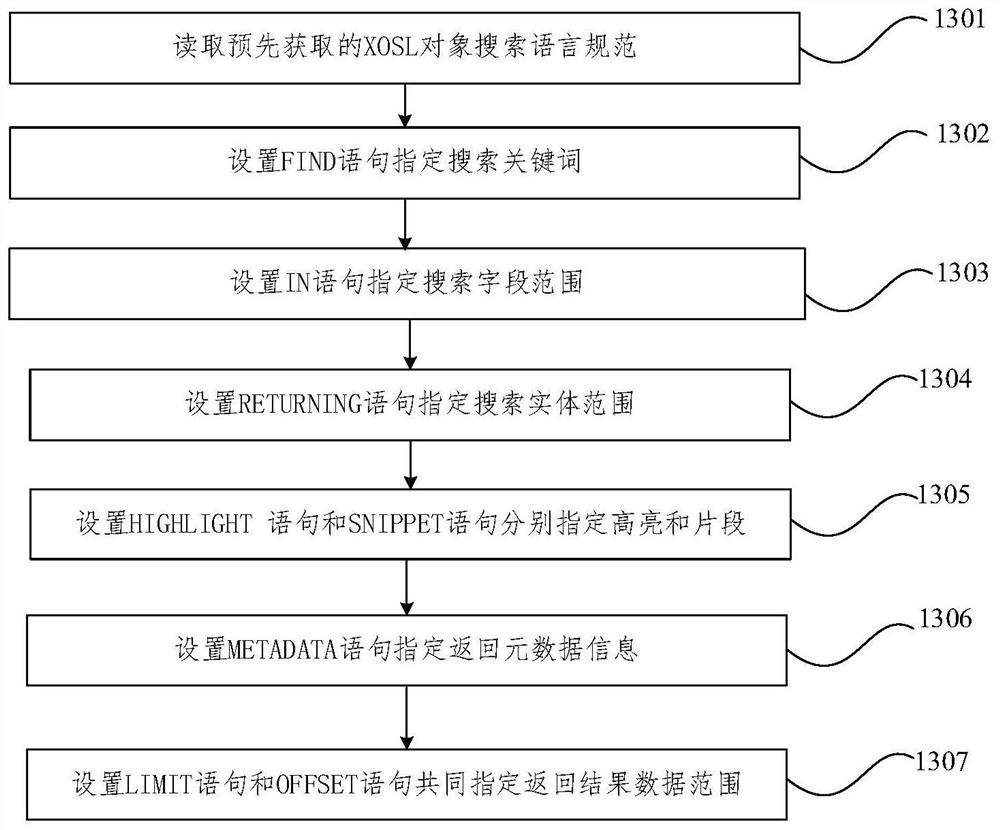
The invention provides a data fuzzy query method and device for a multi-tenant CRM system in a SaaS environment. The method comprises the steps: obtaining a data query request of at least one security tenant; performing language analysis on the query request according to an XOSL object search language specification to obtain a current XOSL data query language of the security tenant; converting each private field identifier and each private entity identifier in search field range and search entity range specified by data query language into each universal field identifier and each universal entity identifier which can be applied to underlying global query engine on the basis of interaction with entity metadata configuration information self-defined by the security tenant in advance; querying through a bottom-layer global query engine to obtain a universal data fuzzy query result; and reversely converting the result into a private data fuzzy query result which can be identified by the security tenant, and outputting the private data fuzzy query result. The method can support global data fuzzy query of multiple fields and multiple entities.
Owner:北京仁科互动网络技术有限公司
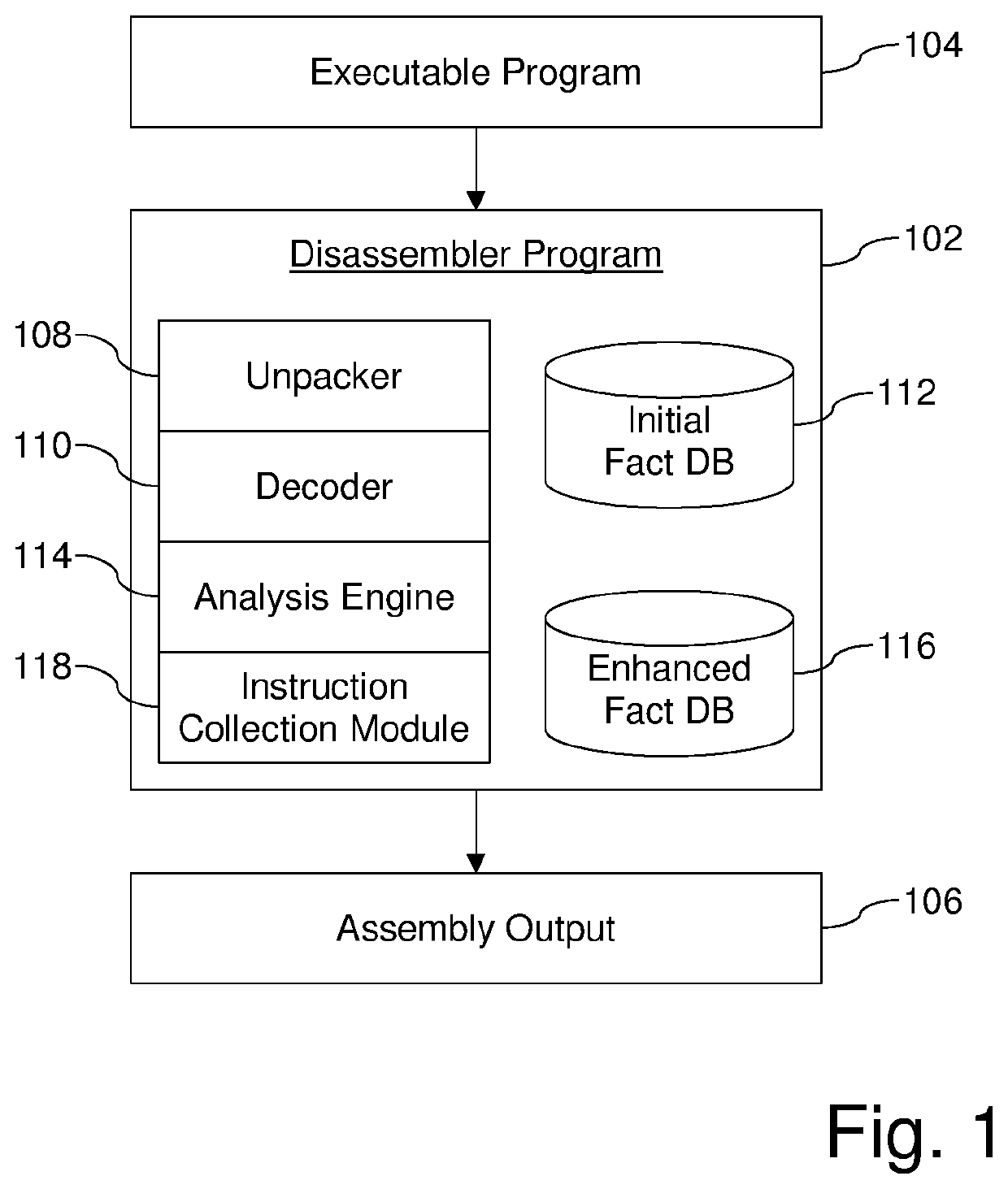
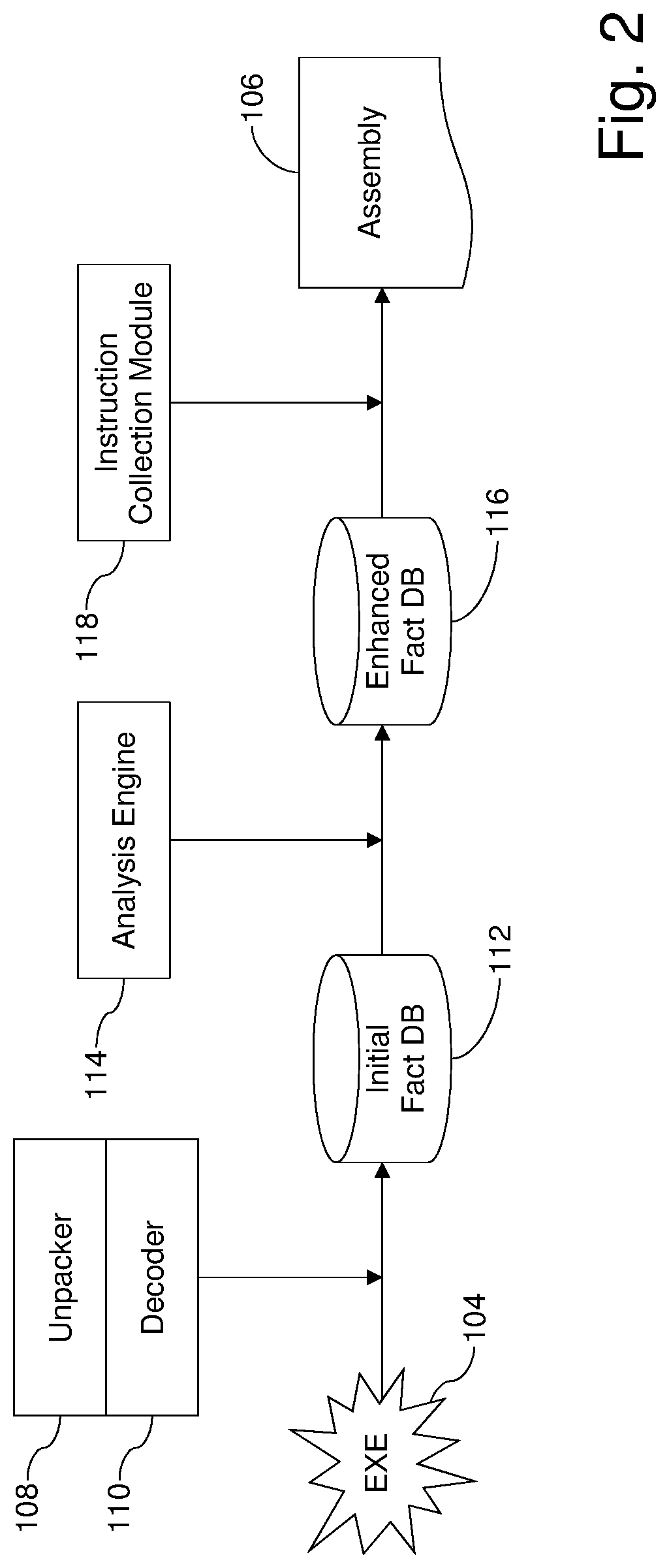
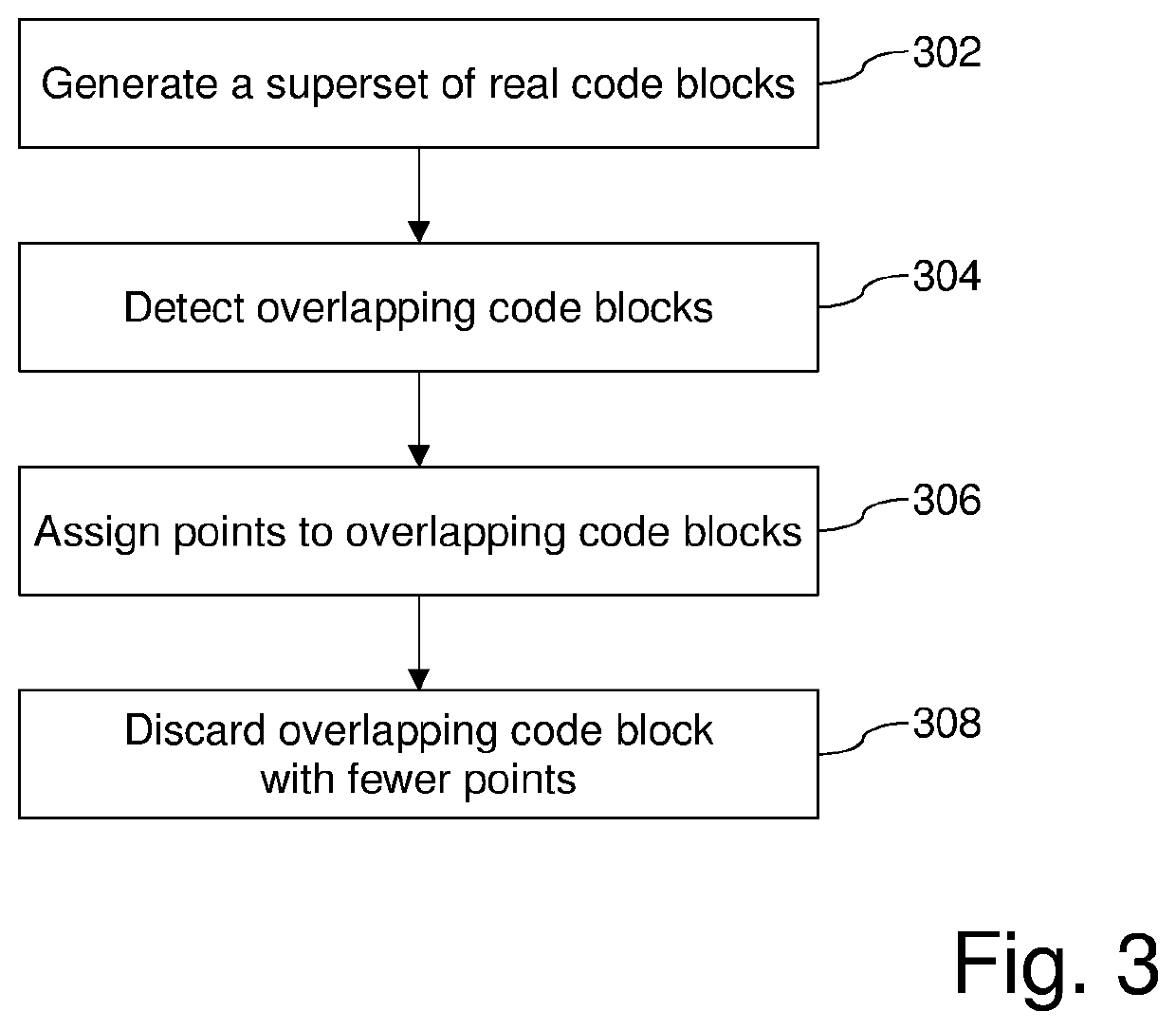
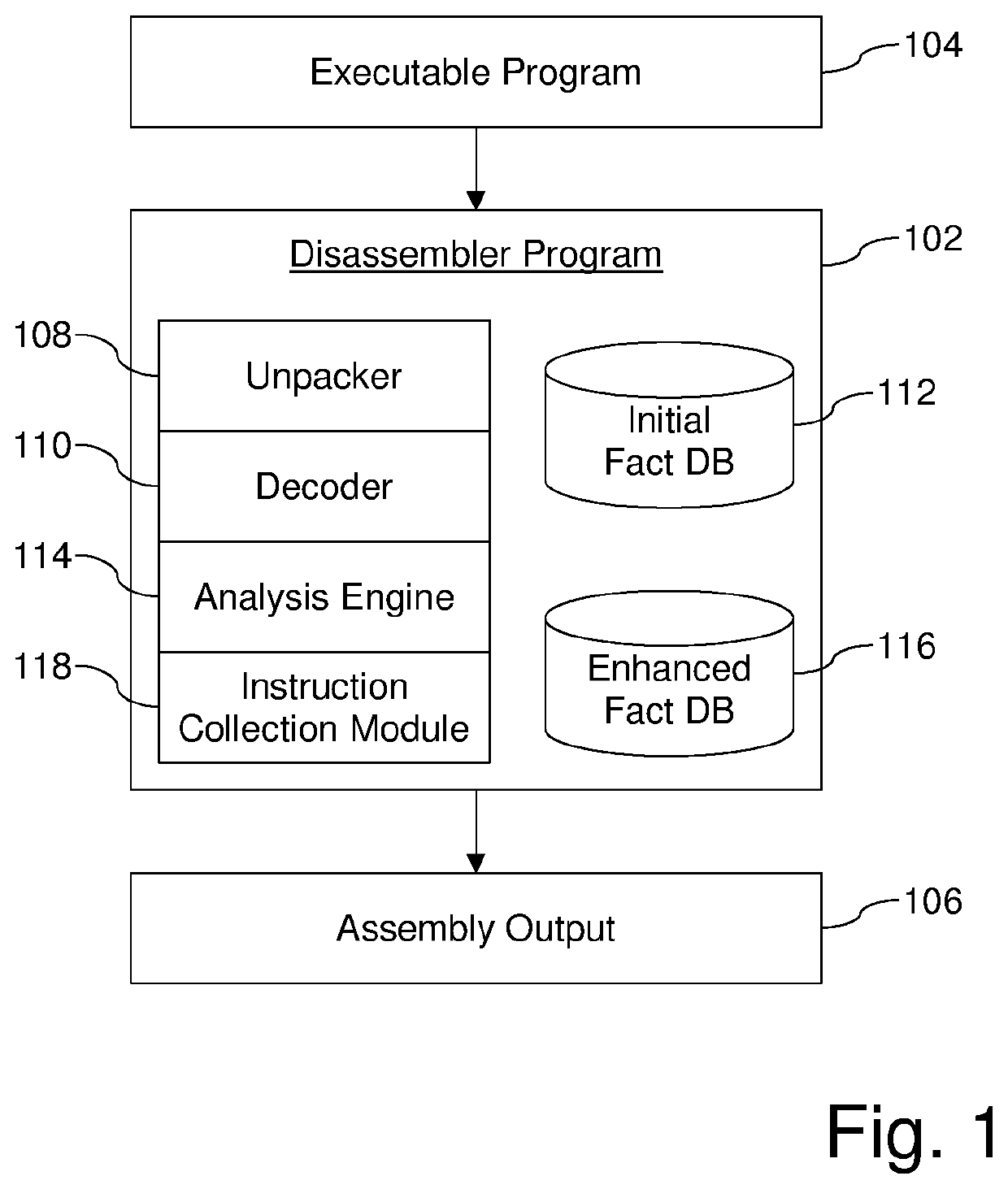
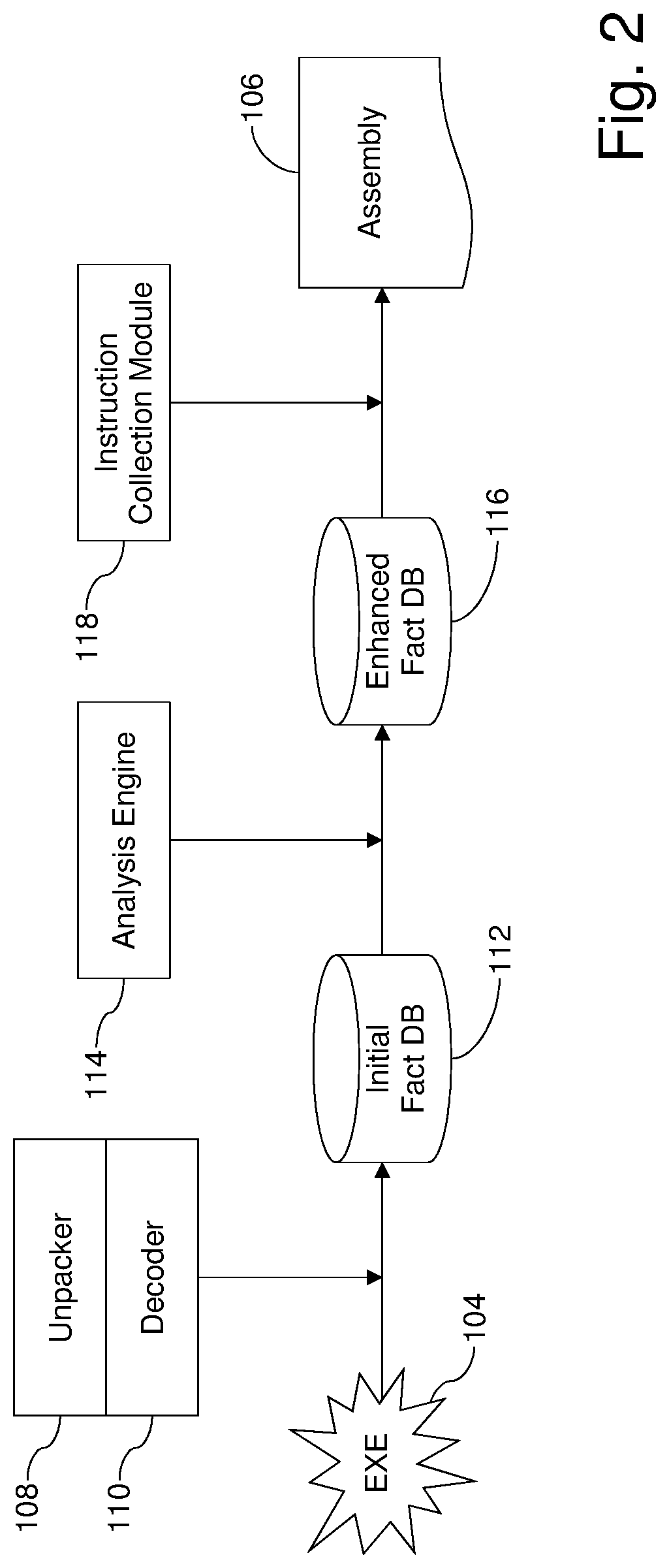
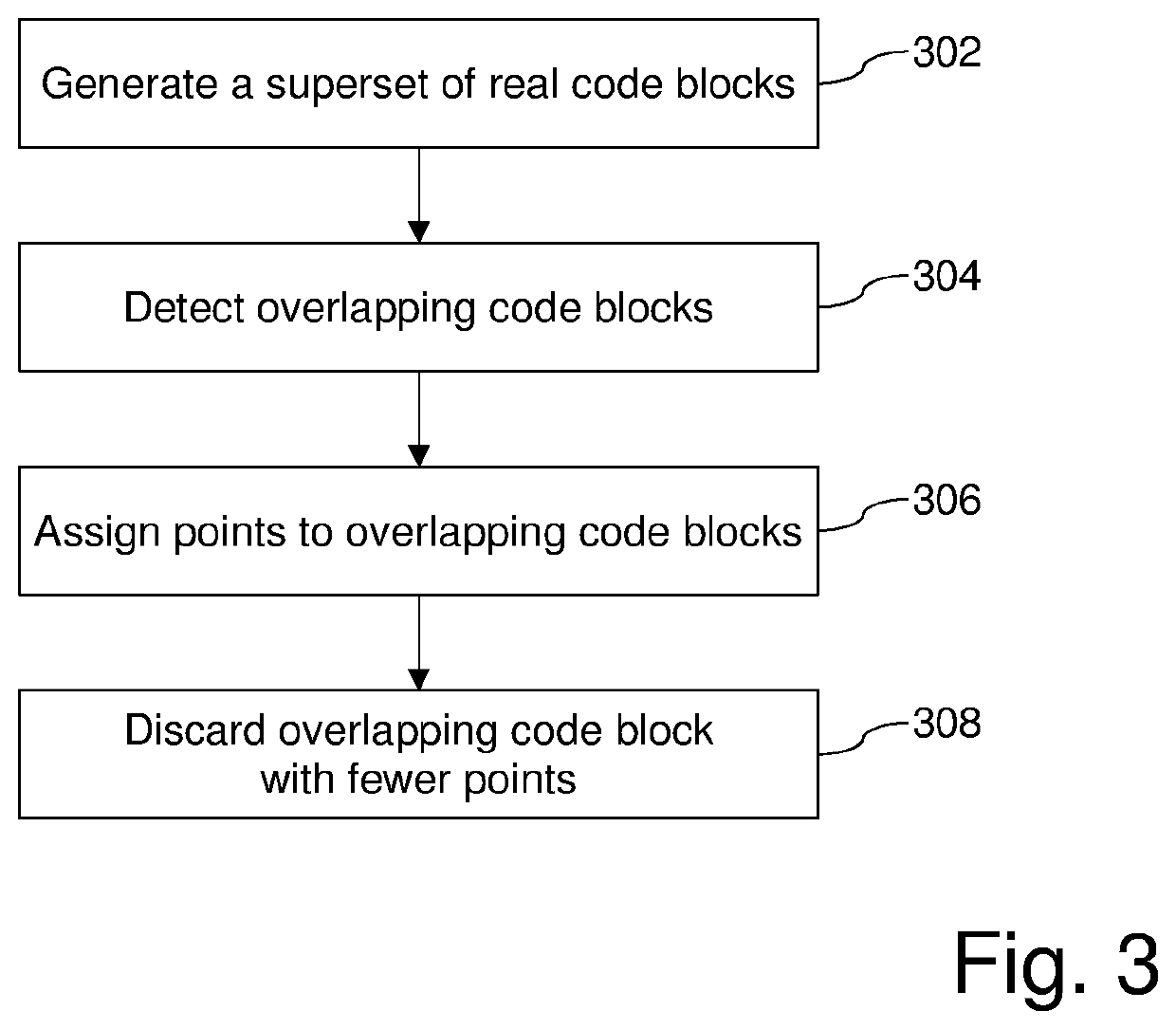
Systems and/or methods for generating reassemblable disassemblies of binaries using declarative logic
Certain example embodiments relate to techniques for generating reassemblable disassemblies of binaries using declarative logic. A declarative logic programming language (e.g., Datalog) is used to compile reverse engineering, binary analysis, and disassembly rules into a format applicable to an executable program, yielding disassembly of that program. Datalog, for example, can be used as a query language for deductive databases, to facilitate this approach. Certain example embodiments thus involve (1) preparation of an executable for Datalog analysis, (2) inference rules and the application of Datalog for program analysis, including the application of Datalog to the domain of binary reverse engineering and analysis, and (3) the collection of assembly code from the results of the Datalog analysis. These rules can include both “hard rules” and “soft rules” or heuristics, even though standard Datalog does not support the latter.
Owner:GRAMMATECH
Type inference for datalog with complex type hierarchies
What is disclosed are a novel system and method for inferring types of database queries. In one embodiment a program and associated database schema that includes a type hierarchy is accessed. The program includes query operations to a database that contains relations described by a database schema. Types are inferred from definitions in the program by replacing each database relationship in the program by the types in the database schema. A new program is generated with the types that have been inferred with the new program only accessing unary relations in the database. In another embodiment, testing of each of the types that have been inferred is performed for type emptiness. In response to type emptiness being found for a type that have been inferred, a variety of different operations are performing including removing the type, providing a notification regarding the emptiness found for the type, and more.
Owner:MICROSOFT TECH LICENSING LLC
Log-structured storage systems
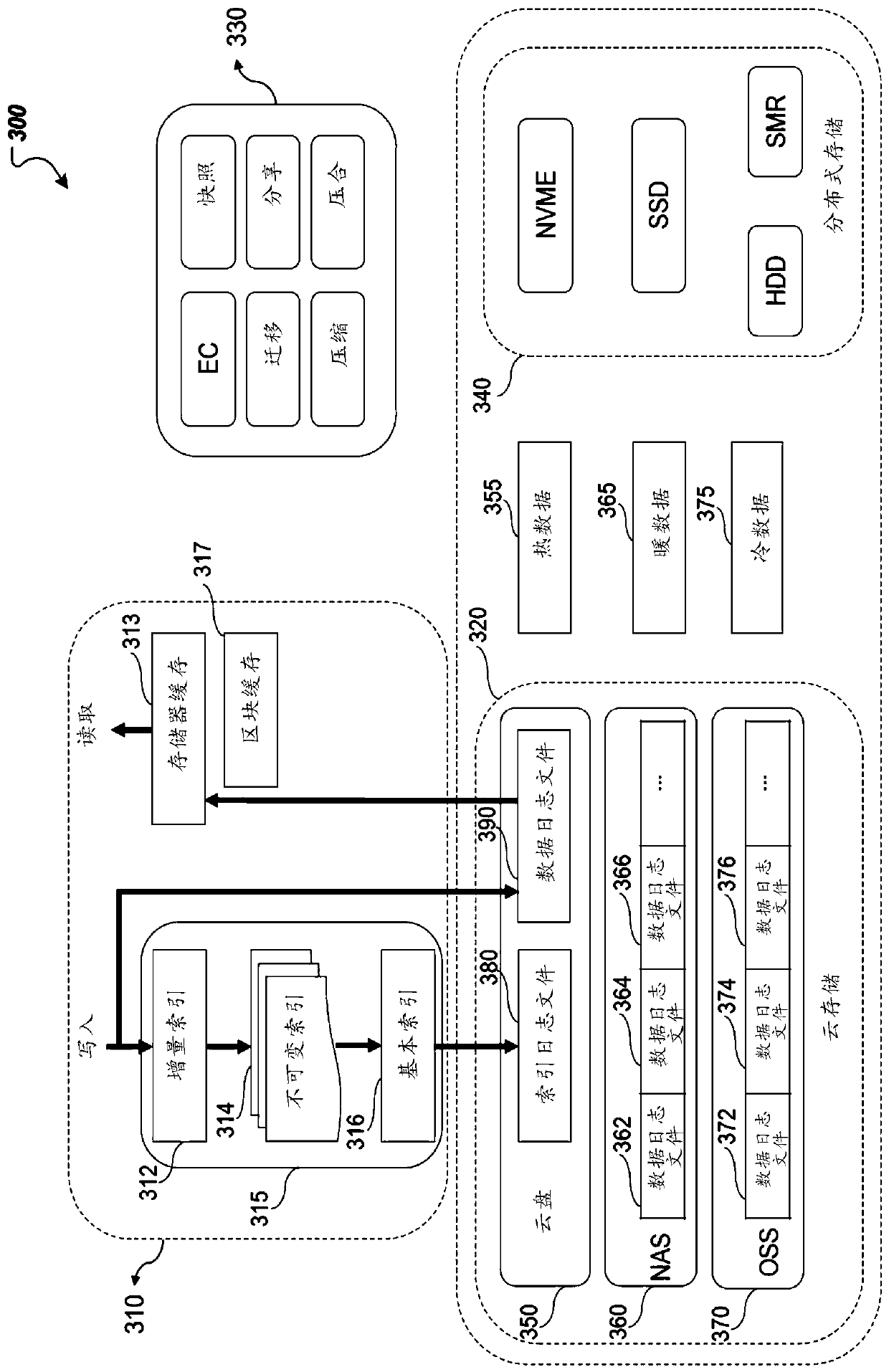
Disclosed herein are methods, systems, and apparatus, including computer programs encoded on computer storage devices, for data processing and storage. One of the methods includes maintaining, by a storage system, a data log file in a source storage device of the storage system. The storage system identifies one or more characteristics of the data log file and one or more characteristics of the source storage device, and determines a migration metric of the data log file based on the one or more characteristics of the data log file and the one or more characteristics of the source storage device. The storage system determines whether to migrate the data log file according to the migration metric. In response to determining to migrate the data log file, the storage system migrates the datalog file from a source location in the source storage device to a destination storage device.
Owner:ADVANCED NEW TECH CO LTD
Datalog support in a modular test system
A method for communicating test information from a source to a destination is disclosed. The method includes providing a modular test system, where the modular test system comprises a system controller for controlling at least one site controller, the at least one site controller for controlling at least one test module. The method further includes providing a datalog framework for supporting extension of user-defined datalog formats, providing support classes for supporting user-initiated datalog events, receiving a datalog event requesting for communicating input test information from the source to the destination, configuring output test information based upon the destination, the datalog framework and the support classes,and transferring the output test information to the destination.
Owner:ADVANTEST CORP
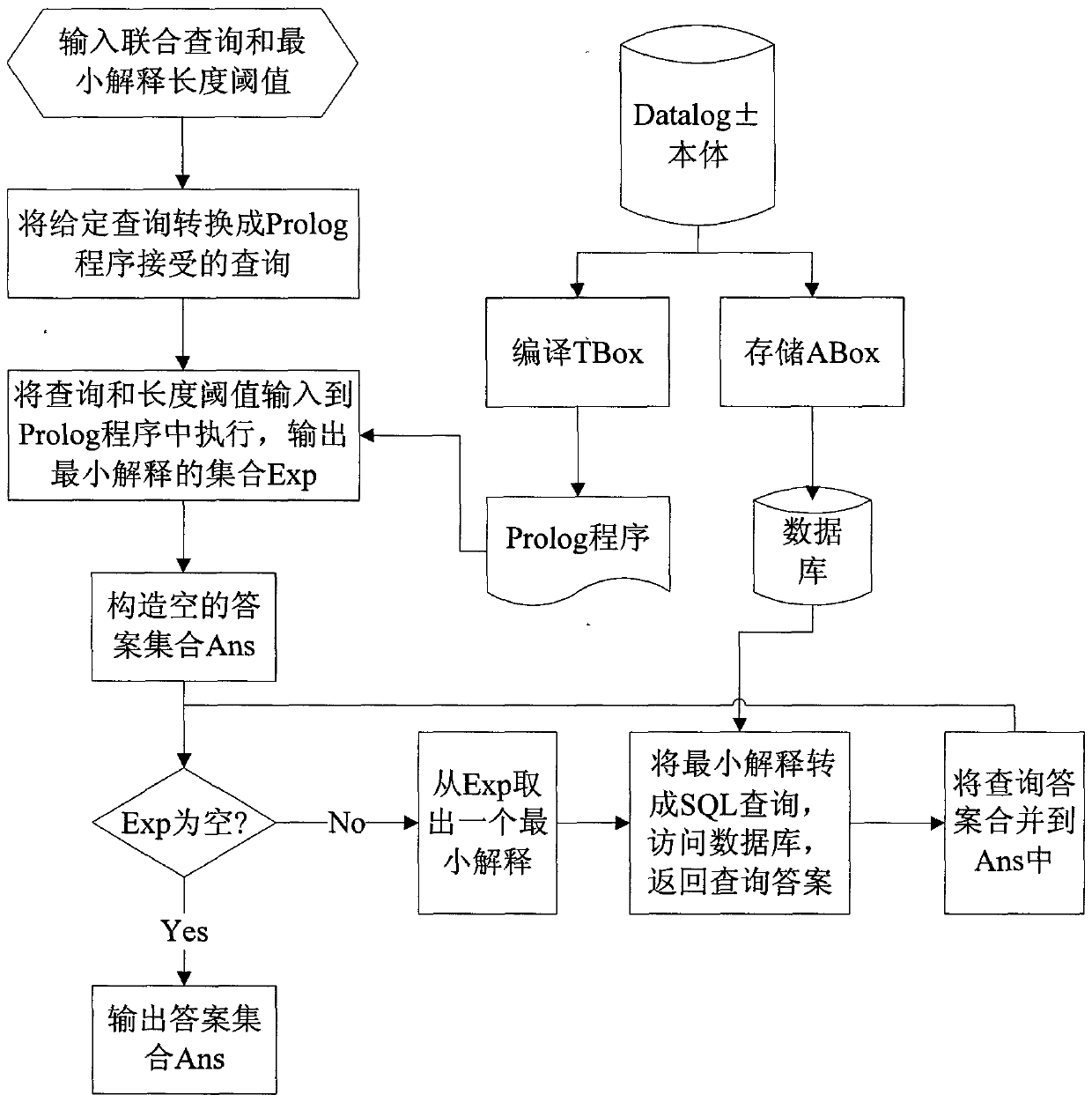
Ontology query inference approximation method based on minimum interpretation
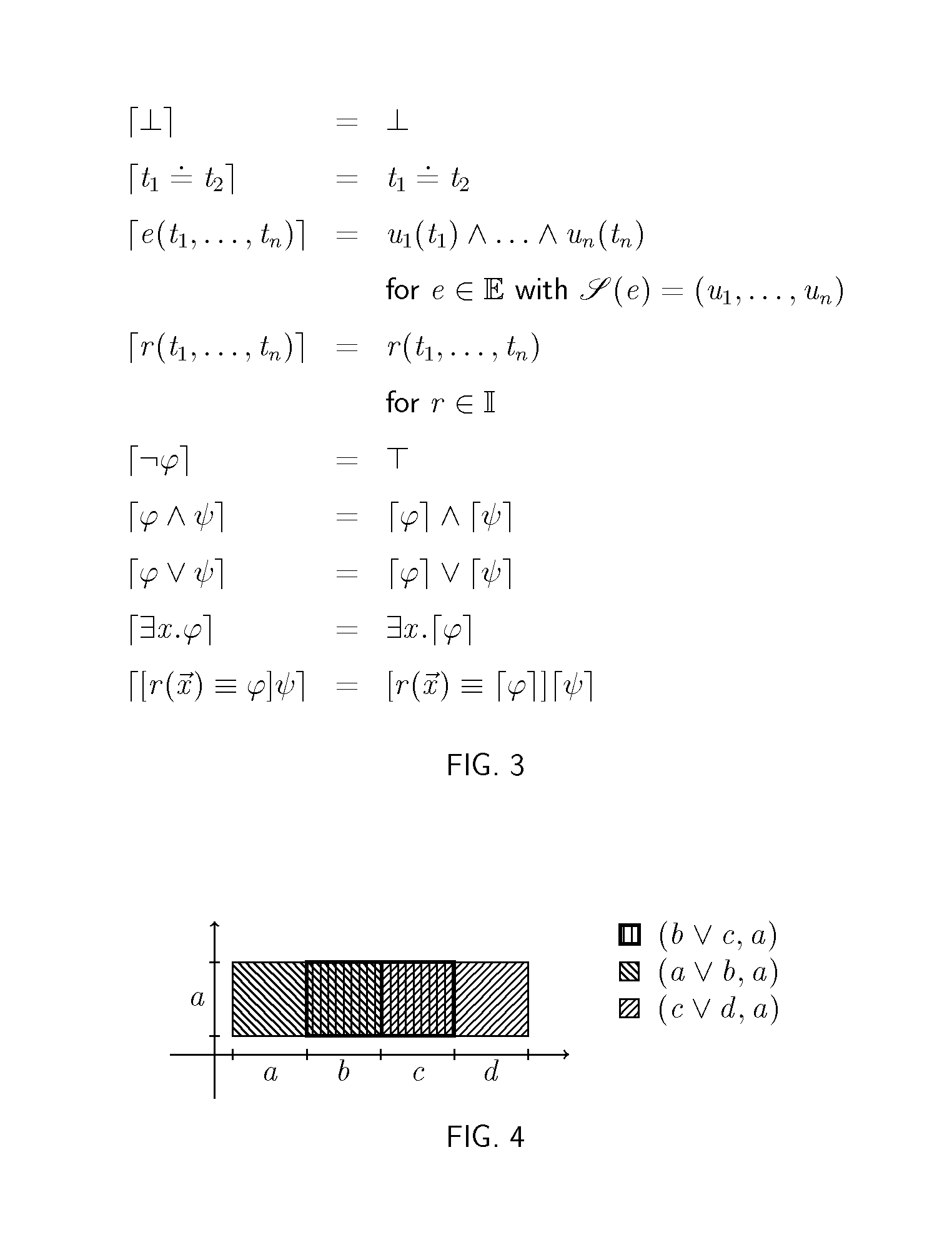
InactiveCN103310024ASolve undecidable problemsSacrifice completenessComplex mathematical operationsConjunctive queryAlgorithm
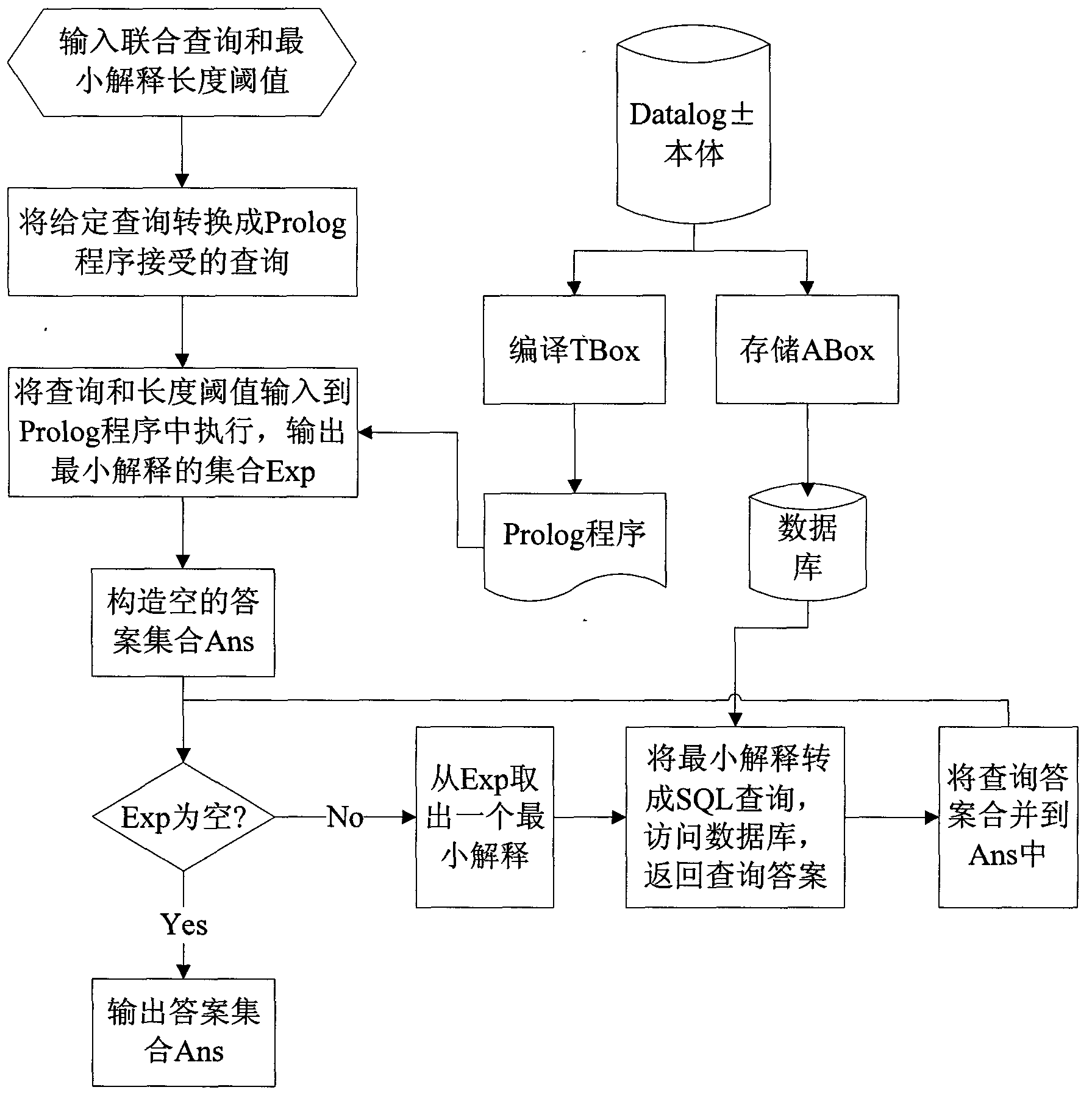
The invention relates to an ontology query inference approximation method based on minimum interpretations and belongs to the field of artificial intelligence. The method is applicable to datalog + / - ontology strong in expression ability and wide in application range, and is characterized in that a query aiming at the datalog + / - ontology is automatically converted into a group of minimum interpretations with lengths not exceeding a threshold value specified by a user, and an ABox part of the datalog + / - ontology is directly accessed via each minimum interpretation so as to obtain respective query result sets. The union set of the query result sets is a subset of original query result sets, and the degree of approximating the original query result sets is controlled by the length threshold value of the minimum interpretations. The key points of the method are as follows: a TBox part of the datalog + / - ontology is automatically compiled into Prolog program capable of receiving a user joint query, and a high-efficiency Prolog system is utilized to automatically calculate all the minimum interpretations with the lengths not exceeding the threshold value specified by the user. The overall data complexity of the method is polynomial time. The method is applicable to various application occasions based on the datalog + / - ontology and supplies an effective information query service to the application occasions.
Owner:杜剑峰
Systems and/or methods for generating reassemblable disassemblies of binaries using declarative logic
ActiveUS10705814B2Decompilation/disassemblyCreation/generation of source codeSoftware engineeringHeuristics
Certain example embodiments relate to techniques for generating reassemblable disassemblies of binaries using declarative logic. A declarative logic programming language (e.g., Datalog) is used to compile reverse engineering, binary analysis, and disassembly rules into a format applicable to an executable program, yielding disassembly of that program. Datalog, for example, can be used as a query language for deductive databases, to facilitate this approach. Certain example embodiments thus involve (1) preparation of an executable for Datalog analysis, (2) inference rules and the application of Datalog for program analysis, including the application of Datalog to the domain of binary reverse engineering and analysis, and (3) the collection of assembly code from the results of the Datalog analysis. These rules can include both “hard rules” and “soft rules” or heuristics, even though standard Datalog does not support the latter.
Owner:GRAMMATECH
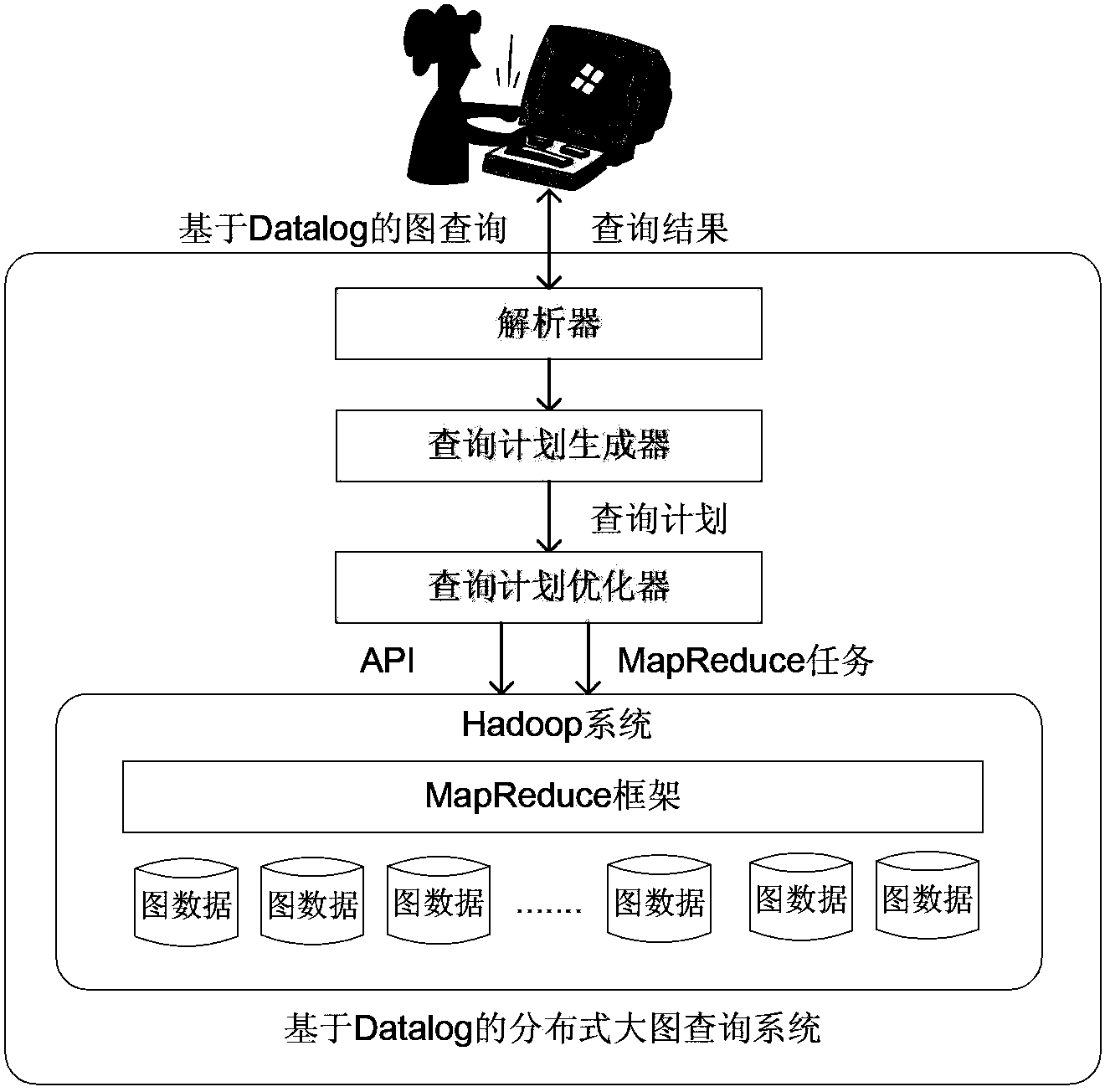
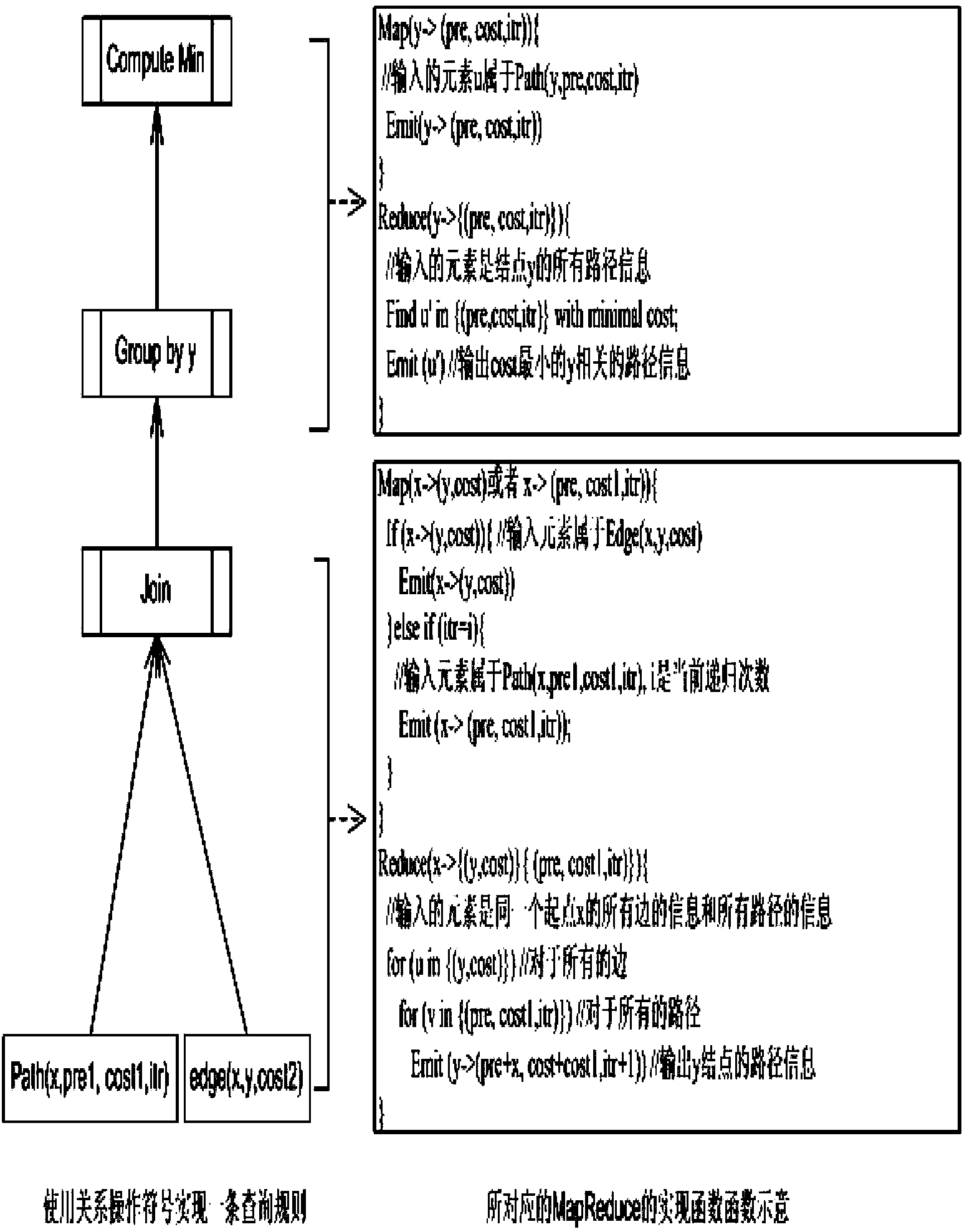
Large-scale graph data query method in distributed environment based on Datalog
InactiveCN102799624BImprove efficiencyOptimize operation functionSpecial data processing applicationsExecution planFunction optimization
Owner:PEKING UNIV
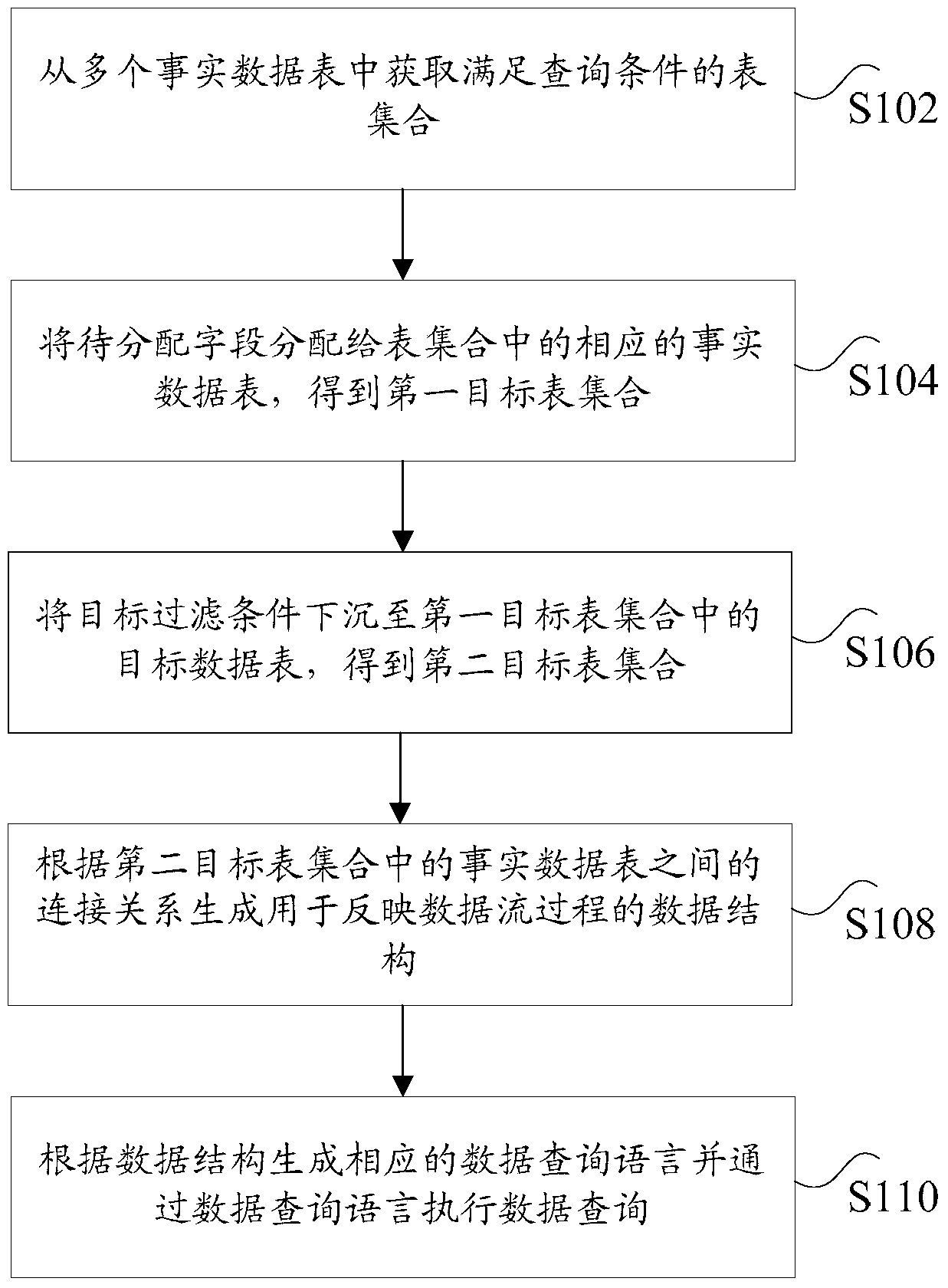
Multi-dimensional data query method and device
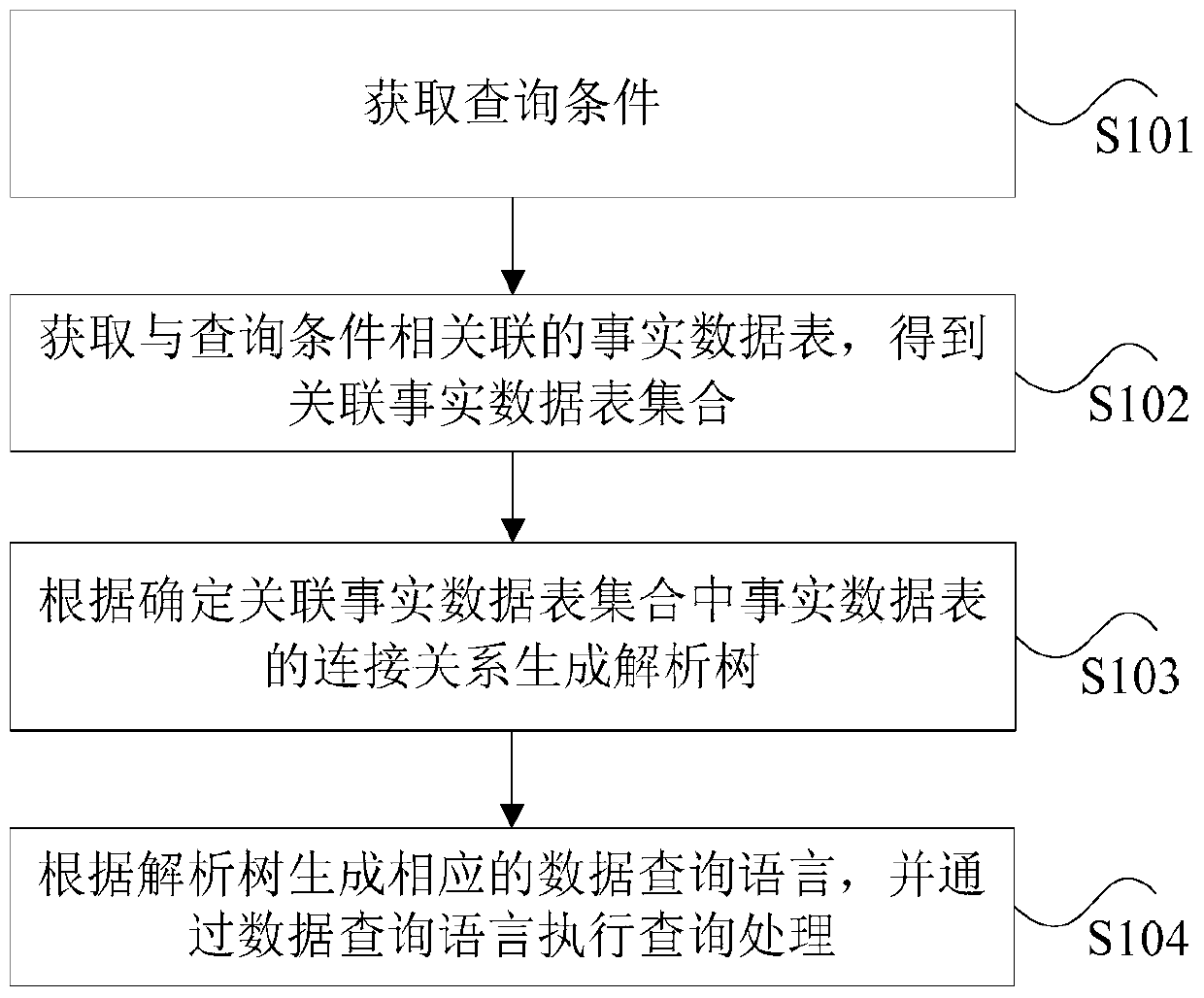
ActiveCN106933909BSolve technical problems with low execution efficiencyMulti-dimensional databasesSpecial data processing applicationsDatasheetData stream
The invention discloses a query method and device for multidimensional data. The method comprises the steps that a table set meeting a query condition is acquired from multiple fact data tables, wherein the query condition comprises a query dimension chain, and the query dimension chain comprises at least one query dimension; to-be-distributed fields are distributed to the corresponding fact data tables in the table set to obtain a first target table set, wherein the to-be-distributed fields are needed column fields acquired from the query condition; a target filtering condition is sunk into a target data table in the first target table set to obtain a second target table set; a data structure used for reflecting a data flow process is generated according to a connection relation between the fact data tables in the second target table set; and a corresponding data query language is generated according to the data structure, and data query is executed through the data query language. Through the query method and device, the technical problem of low execution efficiency of multidimensional data query is solved.
Owner:BEIJING GRIDSUM TECH CO LTD
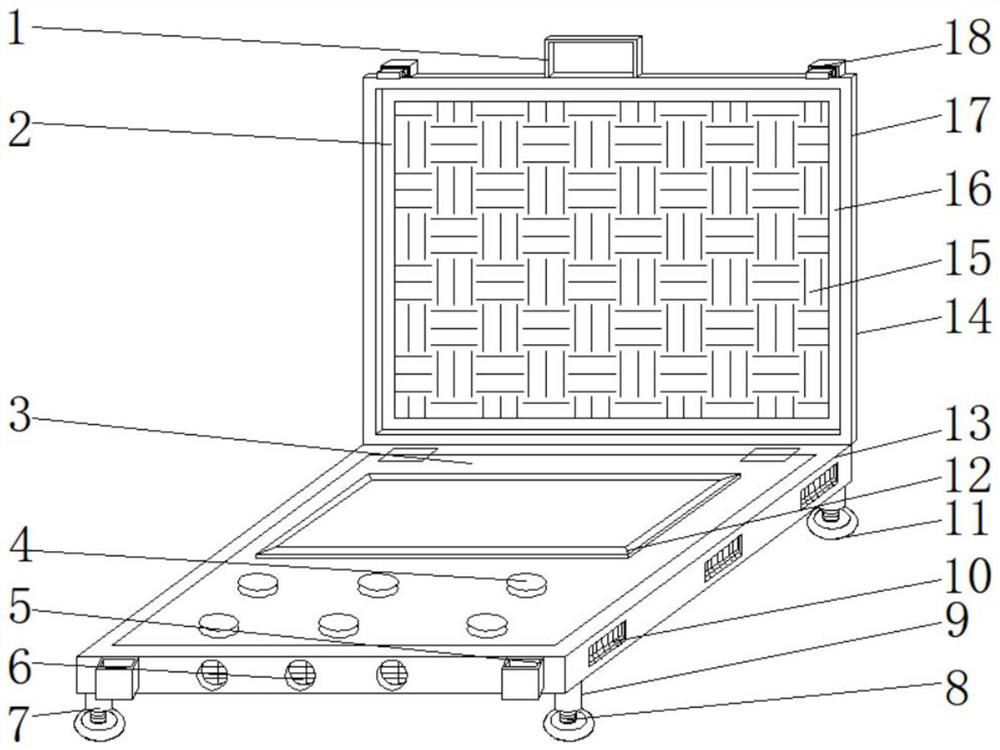
Data retrieval system and data retrieval method
PendingCN113486048AImprove efficiencyAffect progressDigital data information retrievalSpecial data processing applicationsData retrievalData acquisition
The invention discloses a data retrieval system and a data retrieval method. The data retrieval system comprises a shell, adjusting supporting assemblies are arranged at the four corners of the bottom of the shell, a base plate is movably installed on the inner side of the shell through hinges, a touch screen is fixedly installed on the surface of the top of the base plate, and a protective locking assembly is arranged at the top of the shell. Data information to be queried can be directly input through the touch screen, then data query dimension information is converted into query information matched with a data query language through the data collector, the analyzed and converted data is directly transmitted to the processor, and direct matching, calling, comparison and retrieval are carried out through the processor. Through the division of labor and cooperation analysis processing of a plurality of devices, the overall efficiency of retrieval is improved, the retrieval time is shortened, and the situation that the processing and analysis capability is poor, the accuracy has errors, and the query progress and reliability are affected due to the fact that the composition of a single device is large is avoided.
Owner:GUANGXI ELECTRICAL POLYTECHNIC INST
Ontology Query Inference Approximation Method Based on Minimal Explanation
InactiveCN103310024BSolve undecidable problemsSacrifice completenessComplex mathematical operationsConjunctive queryRound complexity
Owner:杜剑峰
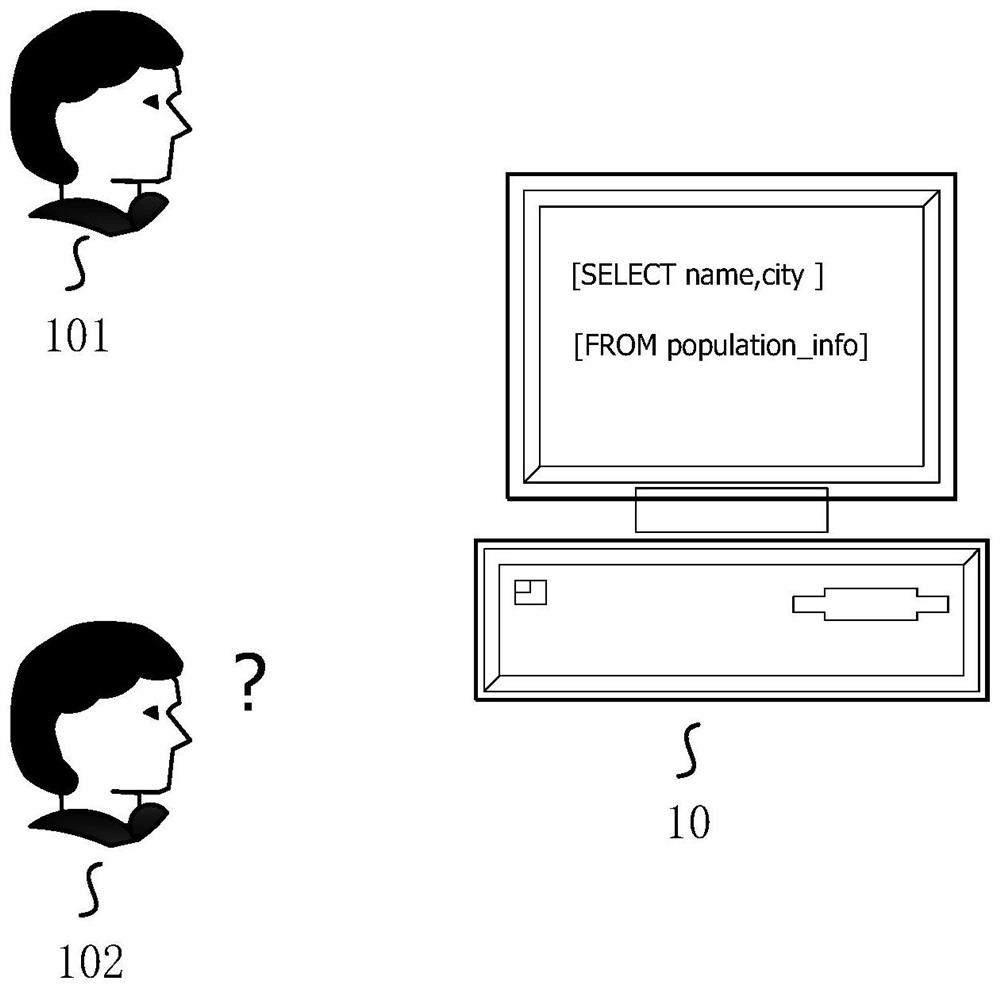
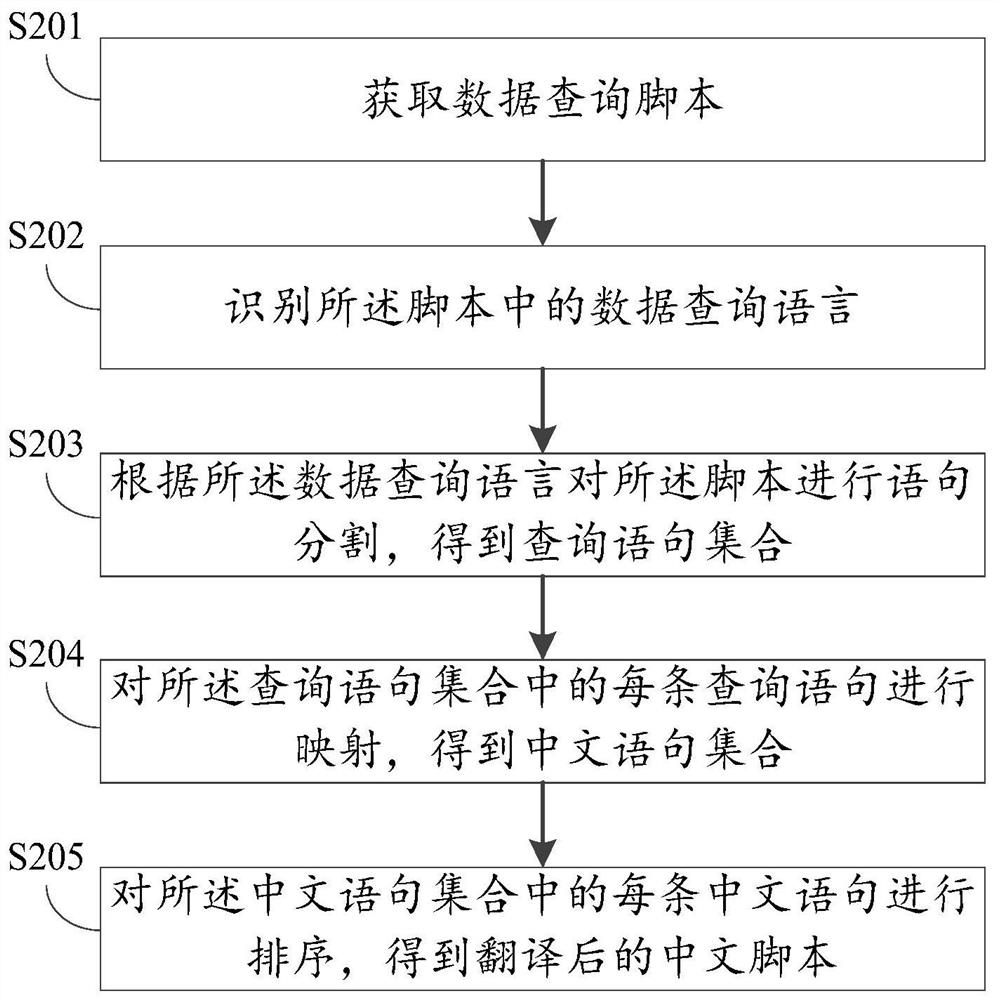
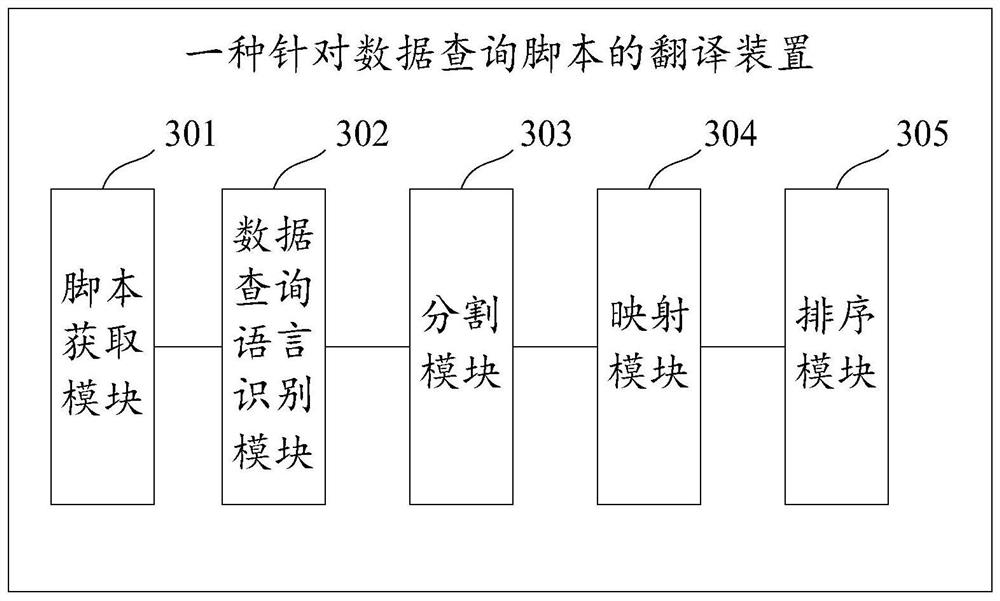
A translation method, device and equipment for data query scripts
ActiveCN109614082BImplement automatic translationImprove translation efficiencyNatural language translationDigital data information retrievalQuery languageData query
The embodiment of this specification discloses a translation method, device and equipment for data query scripts. The scheme includes: obtaining a data query script; identifying the data query language in the script; performing statement segmentation on the script according to the data query language to obtain a query statement set; the query statement set includes dividing the script The obtained query statement; each query statement in the query statement set is mapped to obtain a Chinese statement set; the Chinese statement set includes a Chinese statement corresponding to each query statement; for each query statement in the Chinese statement set The Chinese sentences are sorted to get the translated Chinese script.
Owner:ADVANCED NEW TECH CO LTD
Recording method for test result of integrated circuit mechanical arm
InactiveCN109814019AEasy to analyzeElectronic circuit testingElectrical measurement instrument detailsTested timeEngineering
The invention discloses a recording method for a test result of an integrated circuit mechanical arm. A TrayMap file includes two record parts, the first part comprises integral information of whole Tray disks, a TrayMap file version, a serial number of each Tray disk, batch numbers of products corresponding to the Tray disks, start test time of the Tray disks, end test time of the Tray disks, a serial number of the mechanical arm, a serial number of an operator, called configuration file information, the coordinate range of a TrayMap and Summary information; the invention relates to a TrayMaprecording method. Records comprise test time, test Bin, total test time and the like of all chips of each Tray disk. According to the record file, the test result can be conveniently analyzed, and according to the TrayMap file, a detailed Datalog of each chip generated from a test machine can be traced to the source.
Owner:SINO IC TECH
Automatic mining method and system for misuse vulnerabilities of third-party components of firmware of Internet of Things based on Datalog
PendingCN114722402ASolve efficient mining problemsPracticalDecompilation/disassemblyPlatform integrity maintainanceThird partyCode module
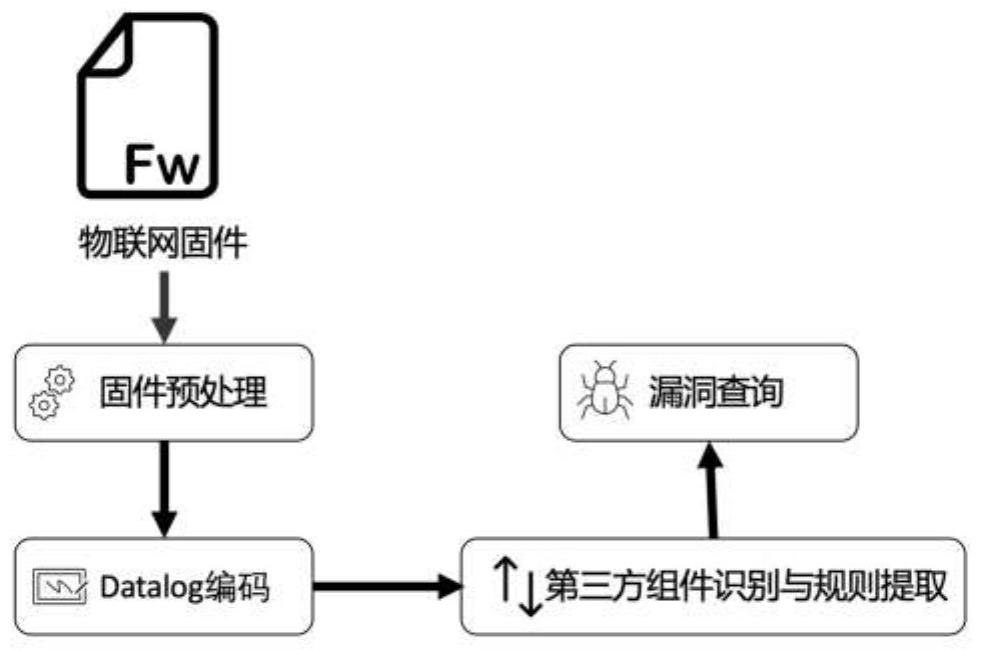
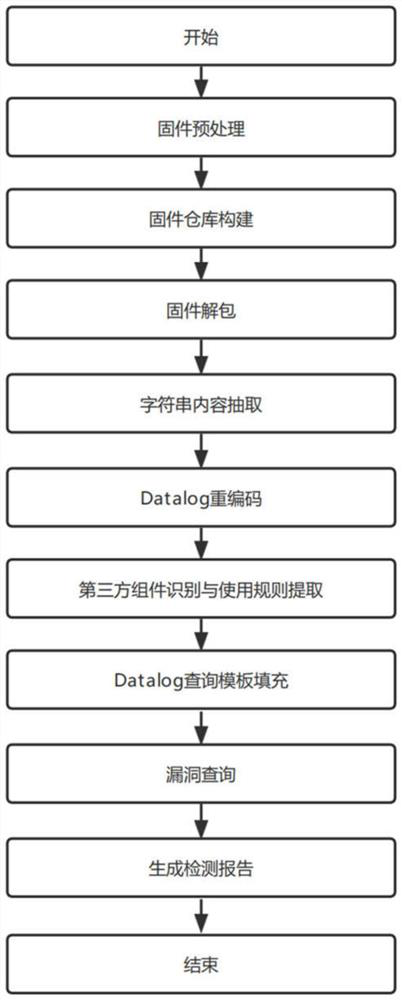
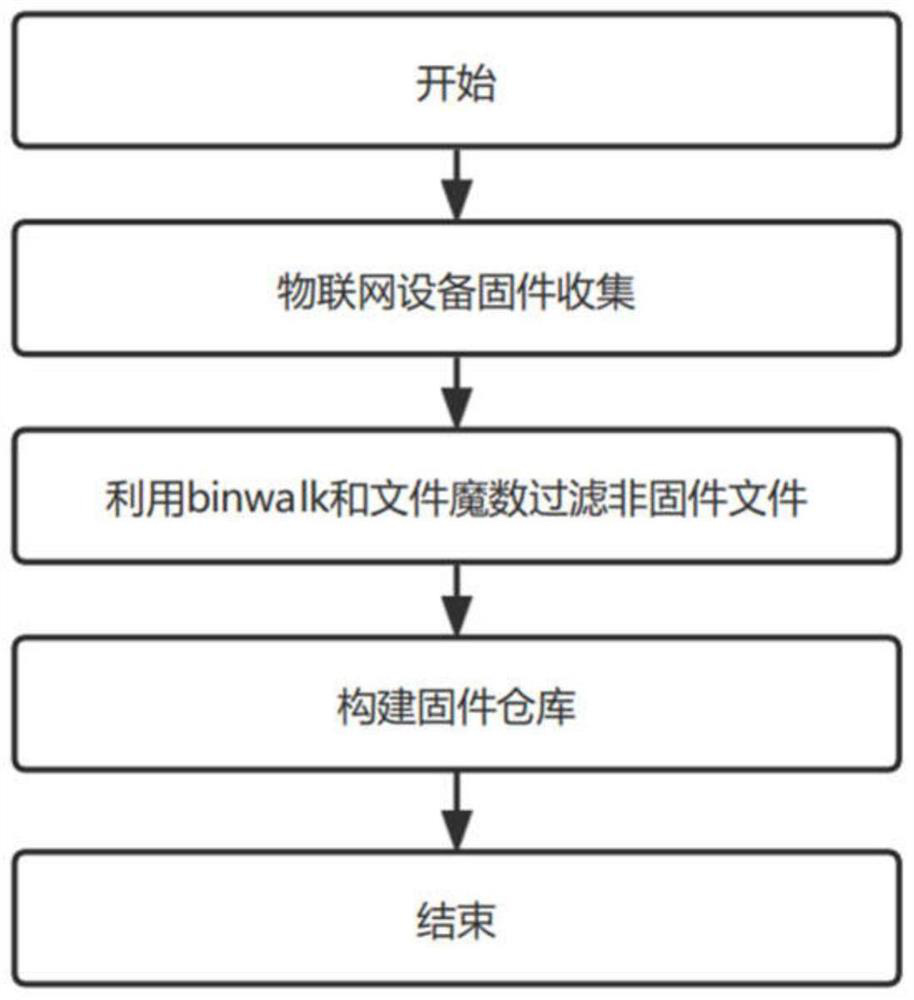
The invention discloses a Datalog-based automatic vulnerability mining method and system for a third-party component of firmware of the Internet of Things, and belongs to the technical field of security of the Internet of Things. The system comprises a firmware preprocessing module for collecting firmware, preprocessing the firmware and storing the firmware into a firmware warehouse; the Datalog coding module is used for extracting files in the firmware and extracting character string contents, and recoding a decompilation result of the binary file by adopting a Datalog coding method; the third-party component identification and rule extraction module is used for identifying a third-party component in the firmware based on regular matching and editing distance and acquiring a related third-party component use rule; and the vulnerability query module is used for performing logical query on the misuse vulnerability of the third-party component in the firmware by utilizing a Datalog query template filled based on the use rule of the third-party component. According to the method, the misuse vulnerability of the third-party component in the firmware of the Internet of Things can be quickly mined with high precision.
Owner:尚蝉(浙江)科技有限公司
Data query method and device
ActiveCN114090627AImprove accuracyAdd supportSpecial data processing applicationsDatabase indexingQuery languageData query
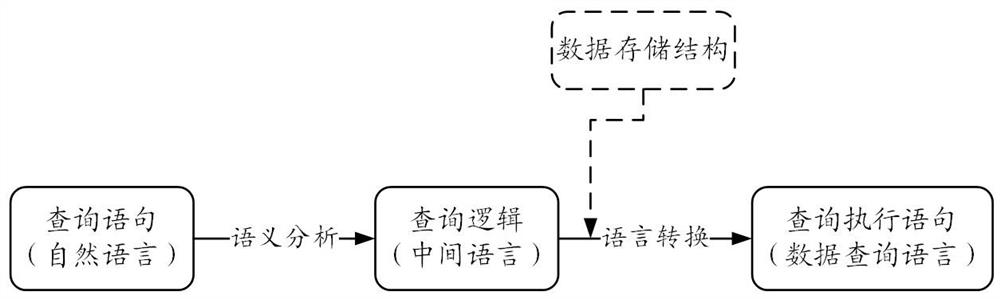
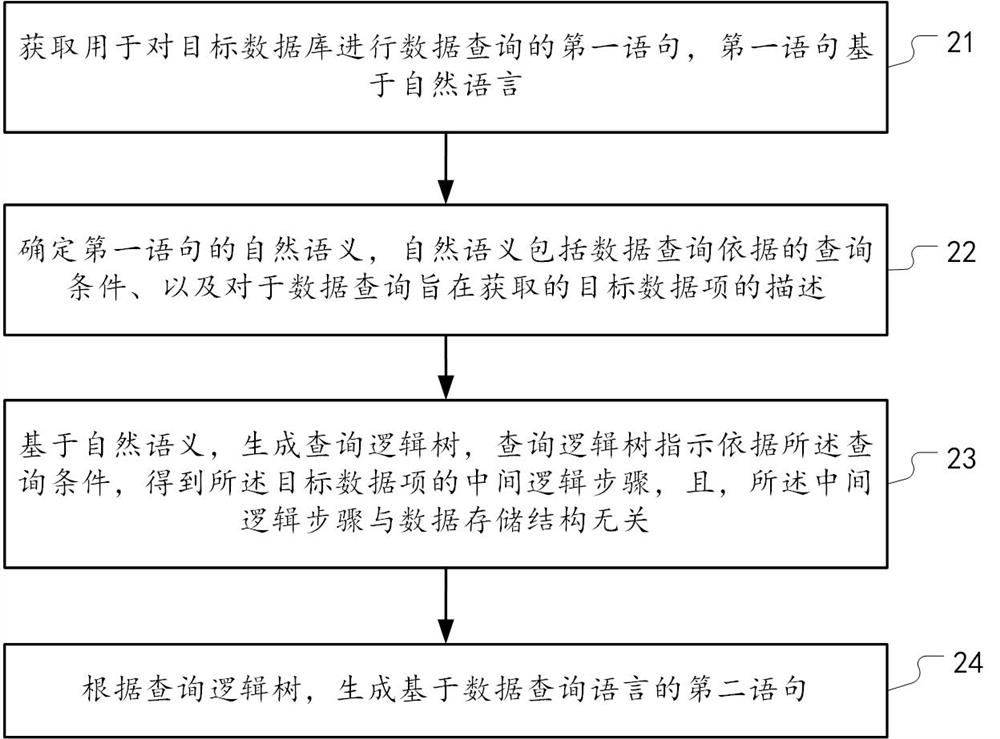
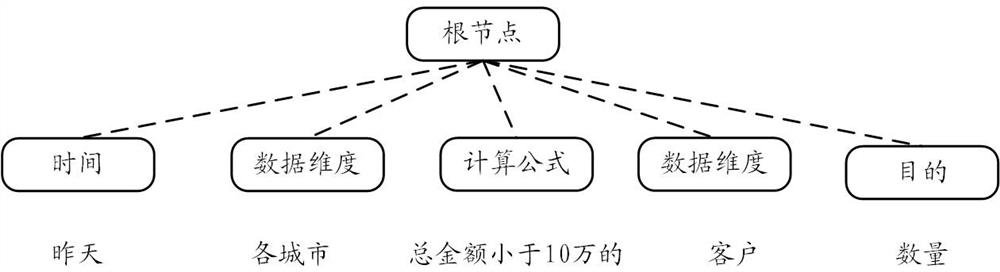
The embodiment of the invention provides a data query method and device. The method comprises the steps of obtaining a first statement used for conducting data query on a data storage system, wherein the first statement is based on a natural language; determining the natural semantics of the first statement, wherein the natural semantics comprises a query condition of a data query basis and description of a target data item to be acquired for the data query; on the basis of natural semantics, generating a query logic tree, wherein the query logic tree indicates that an intermediate logic step of the target data item is obtained according to the query condition, and the intermediate logic step is irrelevant to the data storage structure; and generating a second statement based on the data query language according to the query logic tree.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
A data query method and device
ActiveCN114090627BImprove accuracyAdd supportSpecial data processing applicationsDatabase indexingQuery languageData query
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
A datalog parallel increment maintaining method based on hierarchical counting
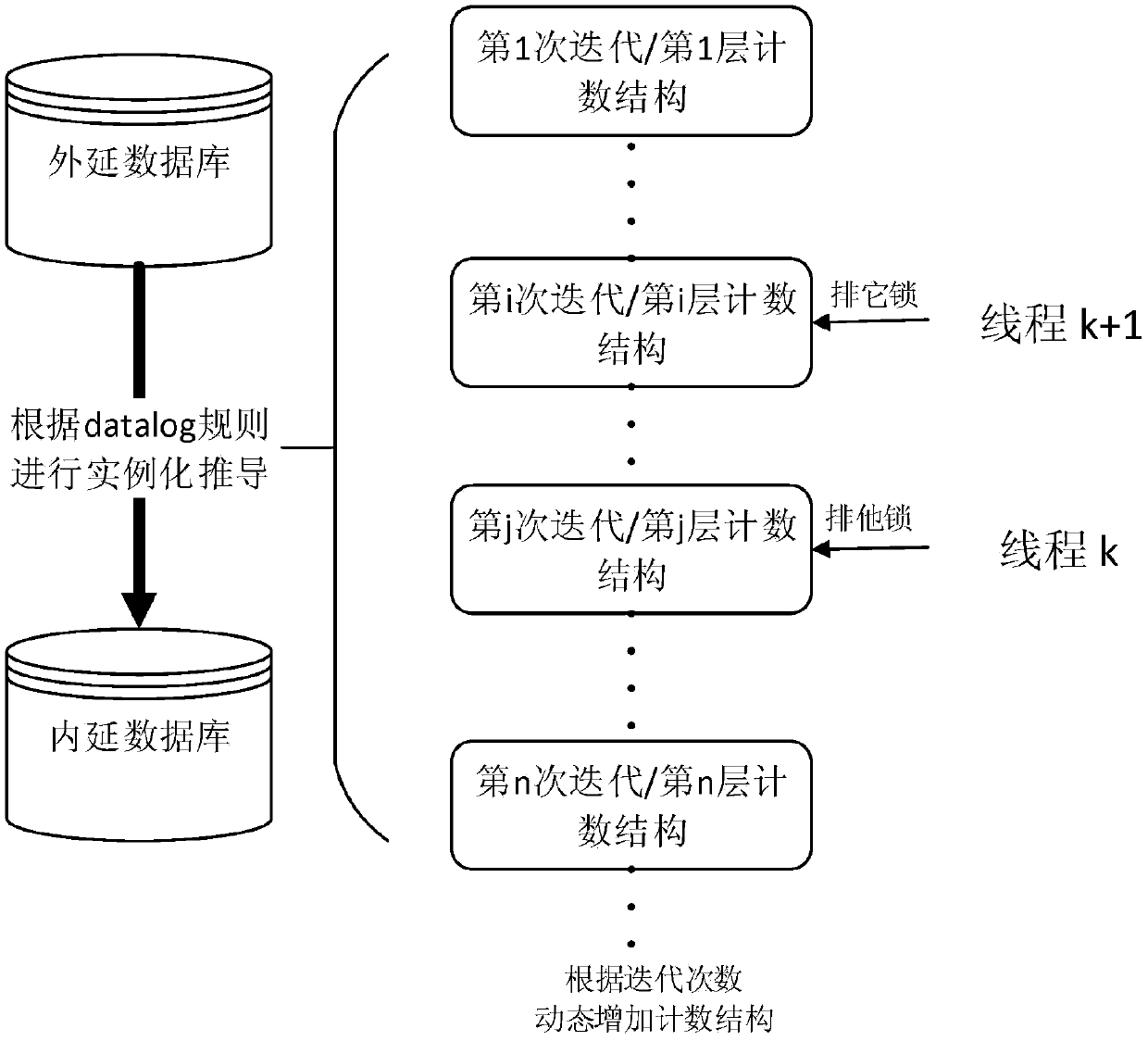
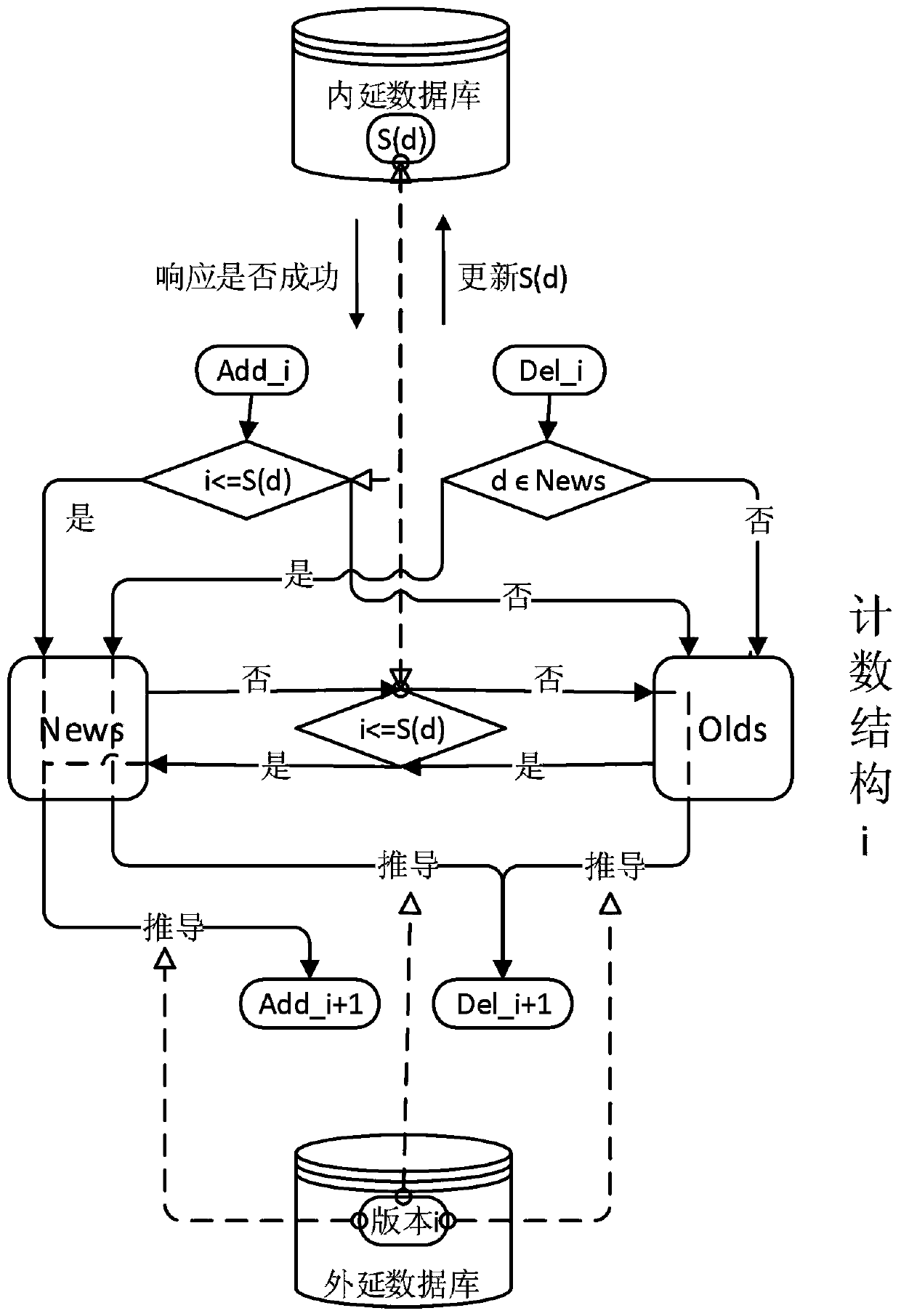
ActiveCN109885579AAccelerate incremental maintenance efficiencyImprove update efficiencyDatabase updatingEnergy efficient computingDatalogComputer science
The invention provides a datalog parallel increment maintaining method based on hierarchical counting, and belongs to the field of knowledge bases. The method comprises the following steps of firstly,layering an instantiation process of datalog, mapping an iterative datalog calculation process into a designed hierarchical structure, and counting each deduced fact in the hierarchical structure incombination with a counting method. In this way, the recursive datalog calculation is converted into a plurality of non-recursive calculations which are connected in series, the defect that a countingmethod cannot be applied to a recursive program is overcome, and the efficient characteristic of the counting method is reserved. The increment triggered by the updating of the epitaxial database ismaintained, and sequentially each level in the process of a counting method is updated. On the basis, an epitaxial data state sequence is further introduced, a small amount of space is utilized, and the different versions of access to an epitaxial database are provided for parallel operation. The method can process a plurality of updating operations at the same time, and greatly improves the instantiation efficiency of the epitaxial database with frequent dynamic changes.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Semi-passive industrial control network security analysis tool and method based on Bayesian attack graph
The invention provides a semi-passive industrial control network security analysis tool and method based on a Bayesian attack graph, and relates to the technical field of network security. The method includes: a semi-passive information acquisition module: acquiring active scanning reports, network message data and management The combination suggested by the staff is corrected and used as an input file; build the asset list module: build the asset list, and generate the .P file as the input file of the attribute attack graph generation module and the Bayesian attack graph generation module; the attribute attack graph generation module: Input template network topology information and node information to generate attack paths; Bayesian attack graph generation module: based on the network information and logic rules recorded by Datalog statements, comprehensively analyze the information of the entire network, and finally generate all possible attack graphs. The invention can have strong compatibility with respect to industrial control networks, and at the same time comprehensively utilize various charts to intuitively assist network security analysis, and can achieve dynamic analysis and hidden danger prevention and control.
Owner:SHANGHAI JIAO TONG UNIV
Multi-dimensional data query method and device
ActiveCN106933906BSolve the problem of low efficiency of multi-dimensional queryMulti-dimensional databasesSpecial data processing applicationsDatasheetData stream
The invention discloses a data multi-dimensional query method and apparatus. The method comprises the steps of obtaining a query condition, wherein the query condition comprises a dimension analysis chain and to-be-queried indexes, and the dimension analysis chain consists of at least one dimension and is used for filtering a plurality of fact data tables; obtaining the fact data tables associated with the query condition, thereby obtaining an associated fact data table set; generating an analytic tree according to connection relationships of the fact data tables in the associated fact data table set, wherein the analytic tree is generated by the query condition and the connection relationships and used for reflecting a data structure of a data flow process; and generating a corresponding data query language according to the analytic tree, and executing query processing through the data query language. Through the method and the apparatus, the problem of relatively low efficiency of data multi-dimensional query is solved.
Owner:BEIJING GRIDSUM TECH CO LTD
AE300 aero-engine data log file analysis method and equipment
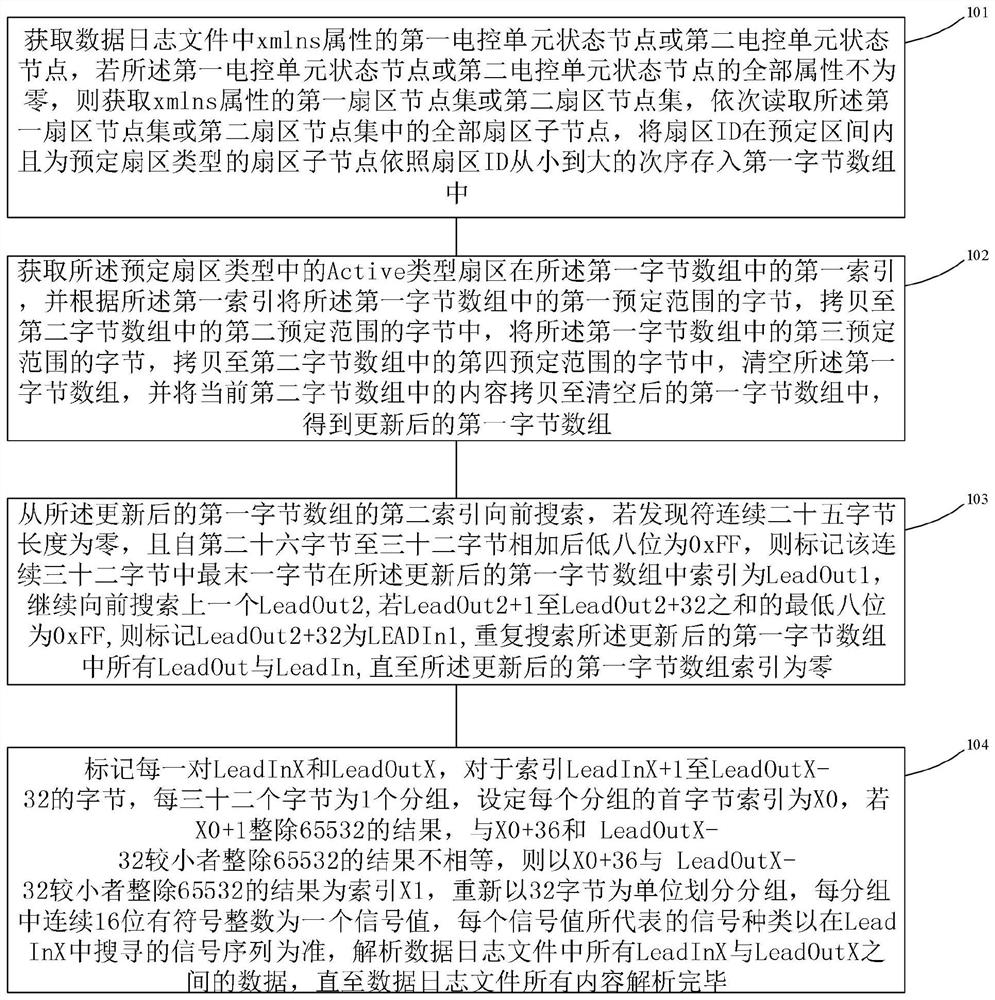
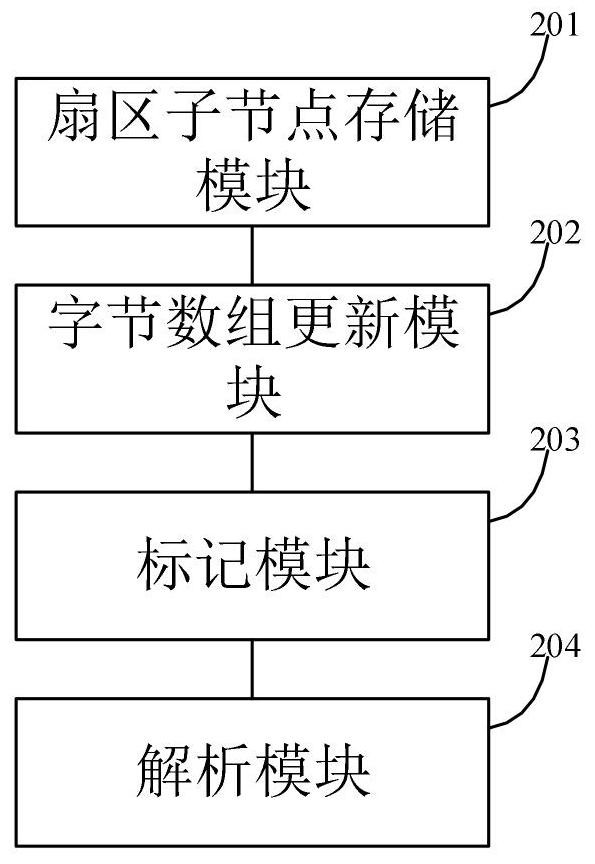
ActiveCN111694989AImplement parsingAchieve complete parsingSemi-structured data indexingSpecial data processing applicationsAlgorithmEngineering
The embodiment of the invention provides an AE300 aero-engine data log file analysis method and equipment. The method comprises the steps of obtaining a first electronic control unit state node or a second electronic control unit state node of xmlns attributes in a data log file; obtaining a first index of an Active type sector in a predetermined sector type in a first byte array; and searching forwards from a second index of the updated first byte array, and if the length of twenty-five consecutive bytes of the discoverer is zero, marking each pair of LeadInX and LeadOutX, and indexing bytesfrom LeadInX + 1 to LeadOutX-32, and the like. According to the AE300 aero-engine data log file analysis method and equipment provided by the embodiment of the invention, complete analysis of the datalog of an AE300 aero-engine can be realized.
Owner:CIVIL AVIATION FLIGHT UNIV OF CHINA
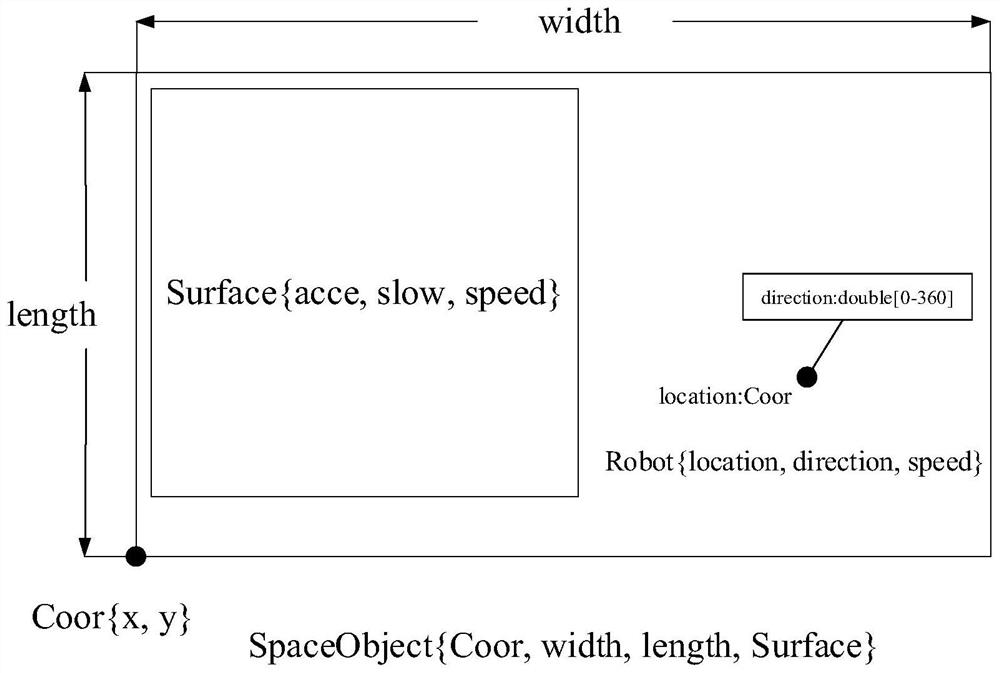
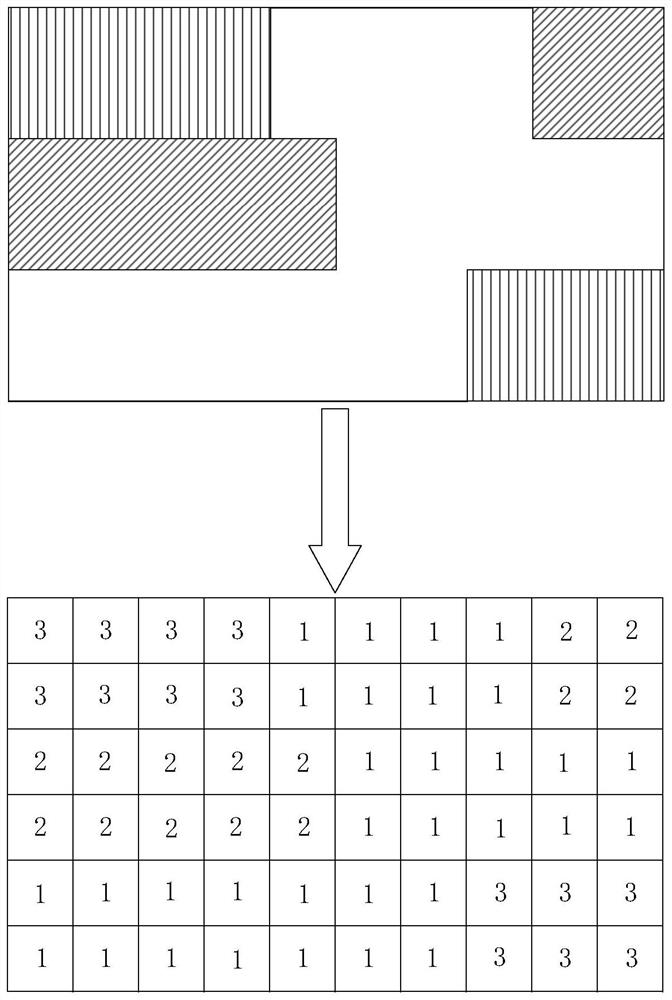
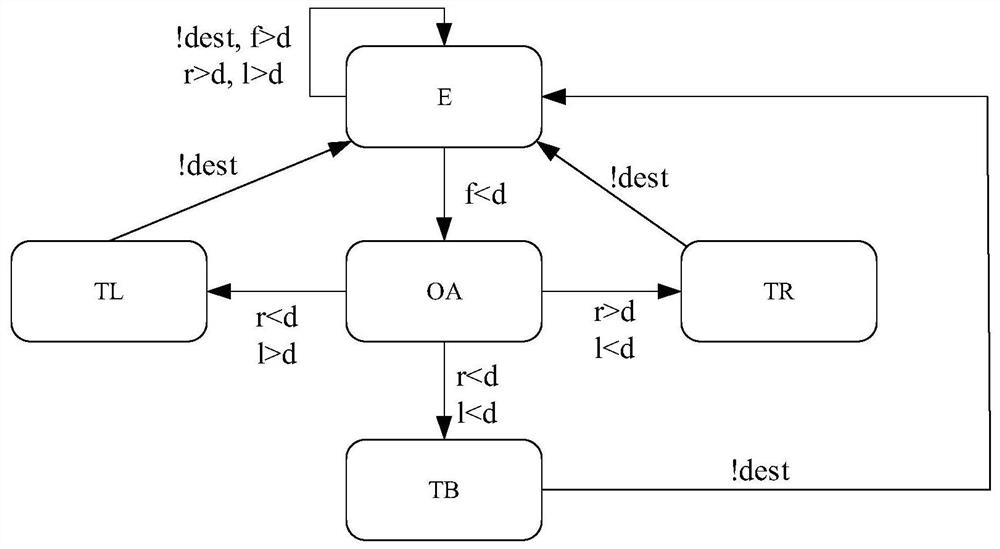
Self-adaptive unmanned trolley simulation method based on Datalog rule
ActiveCN113671851AReduce couplingReduce yardageSimulator controlInternal combustion piston enginesControl theorySelf adaptive
The invention discloses a self-adaptive unmanned vehicle simulation method based on a Datalog rule, and the method comprises the steps: building a dynamically changing self-adaptive unmanned vehicle simulation scene, improving an operation scene through employing a digital matrix and the Datalog rule, and achieving the dynamic updating of the scene; and constructing a state conversion diagram of the operation logic according to the state of the unmanned vehicle and the change of the environmental parameters, performing equivalent translation on the operation logic by using a Datalog rule, and reasoning the state conversion process to realize the operation logic of the self-adaptive unmanned vehicle. According to the method, the dynamic change of the environment and the update of the operation logic are stripped and extracted from the system codes, the independent Datalog rule module is used for deductive reasoning, the self-adaptive process is realized, the system code quantity is greatly reduced, the coupling of the system codes is reduced, the self-adaptive operation logic is more efficient and simpler, and the problems of code rewriting and redeployment caused by dynamic scene updating are avoided.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com