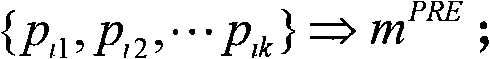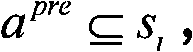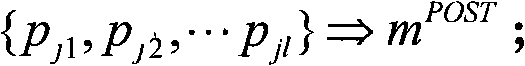Automatic threat ensuring method facing to network security risk assessment based on first order logic predicate reasoning
A network security and risk assessment technology, applied in the field of automated threat determination based on first-order logical predicate reasoning, can solve problems such as complex network topology and difficult to satisfy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0017] The Datalog language is a subset of the Prolog language, which has clear declarative semantics (declarative semantics), which can formally describe network status information and attack rules, etc., and is suitable for analysis related to network attacks; and XSB (XSB is a logic programming and deductive The database system, XSB's official website's English annotation is "XSB is a Logic Programming and Deductive Database system for Unix and Windows") is a reverse reasoning system based on list technology, which can be used to execute Datalog programs, and can give the reasoning target when it is established. all possible reasoning paths. XSB can record all instances of rules that are instantiated and useful to the reasoning goal during the reasoning process, which is the evidence that proves that the reasoning goal is reachable.
[0018] In the present invention, the automated threat determination based on first-order logical predicate reasoning for network security ris...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com