Automatic mining method and system for misuse vulnerabilities of third-party components of firmware of Internet of Things based on Datalog
An Internet of Things and component technology, applied in the field of Internet of Things security, can solve problems such as restricting large-scale applications, complex usage rules, and unauthorized attacks, and achieve the effect of improving detection success rate and efficiency, and high-precision mining.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The present invention will be further described in detail below with reference to the accompanying drawings and embodiments. It should be noted that the following embodiments are intended to facilitate the understanding of the present invention, but do not have any limiting effect on it.
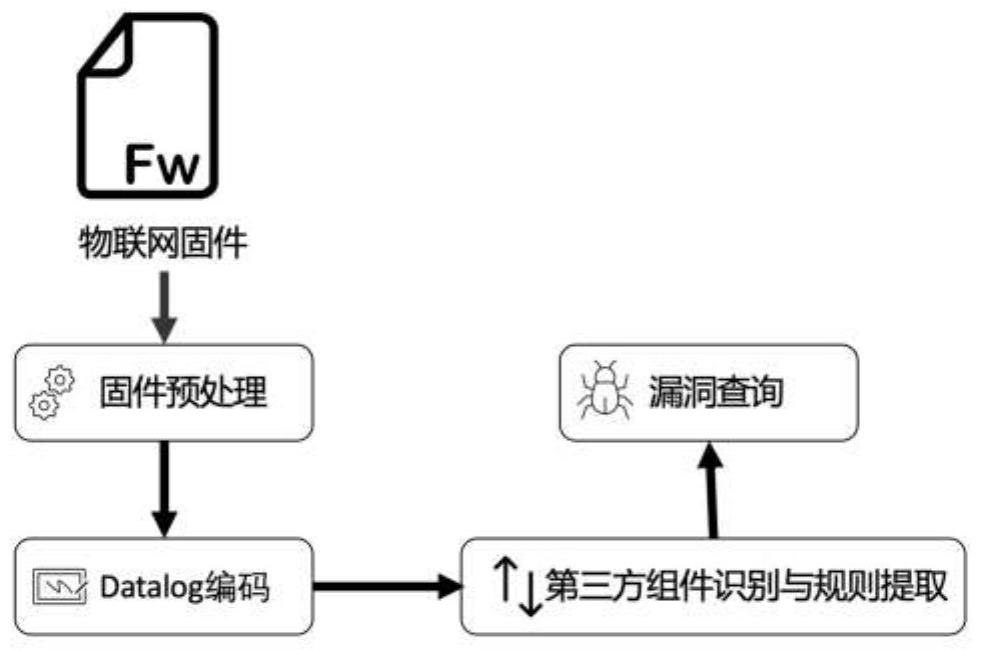
[0030] like figure 1 As shown, the datalog-based IoT firmware third-party component misuse vulnerability automatic mining system of the present invention includes: a firmware preprocessing module, a Datalog encoding module, a third-party component identification and rule extraction module, and a vulnerability query module.
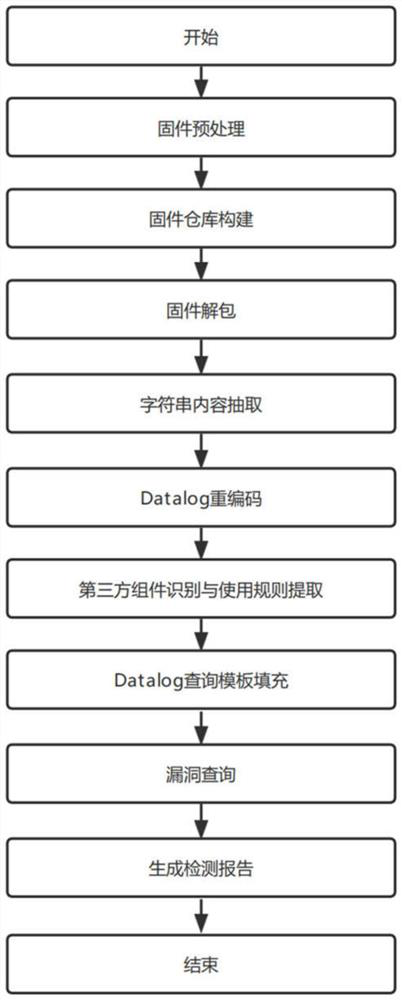
[0031] The workflow of the entire IoT firmware third-party component misuse vulnerability automated mining system is as follows figure 2 shown, including the following steps:
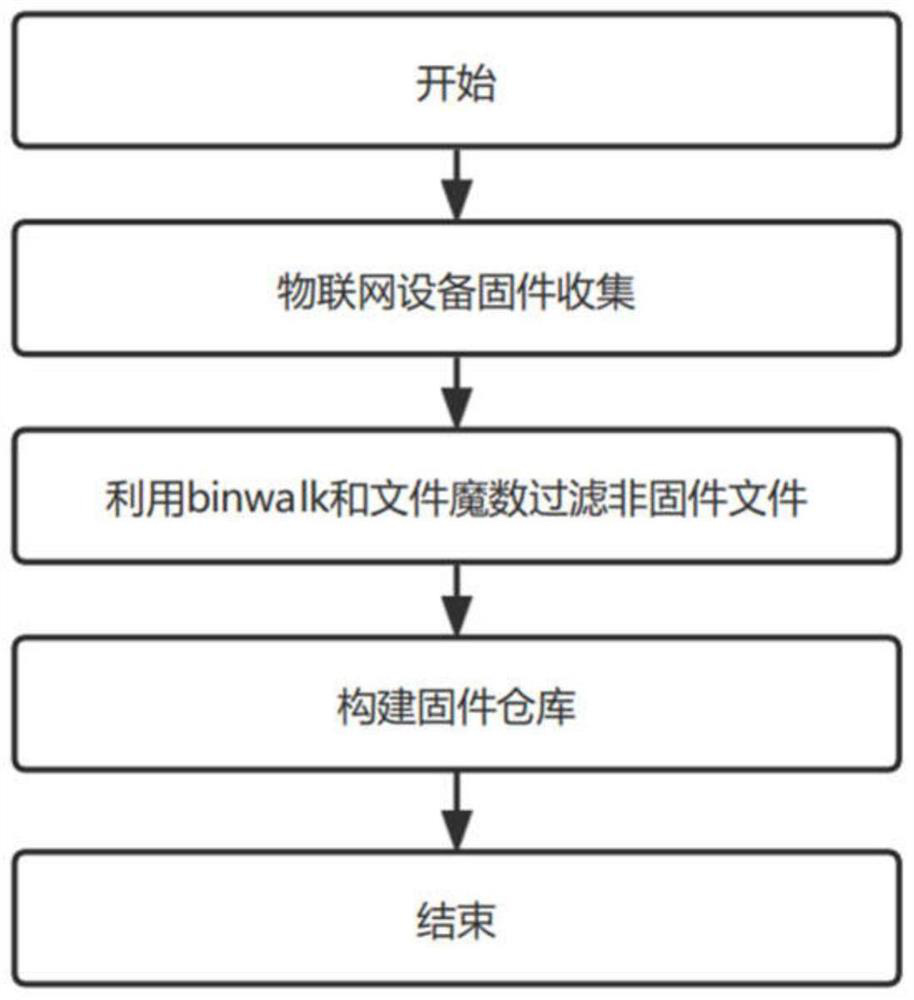
[0032] Step 1: Firmware preprocessing: Collect different types of IoT device firmware from different manufacturers, and preprocess the firmware to be tested. Use binwalk and file magic nu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com