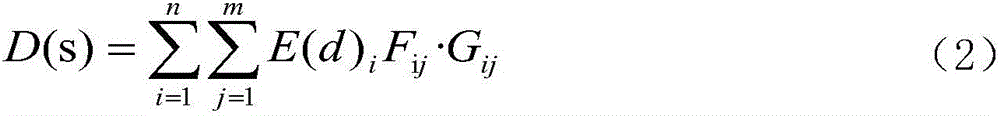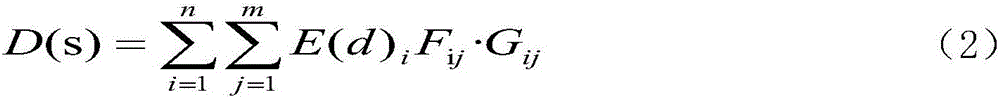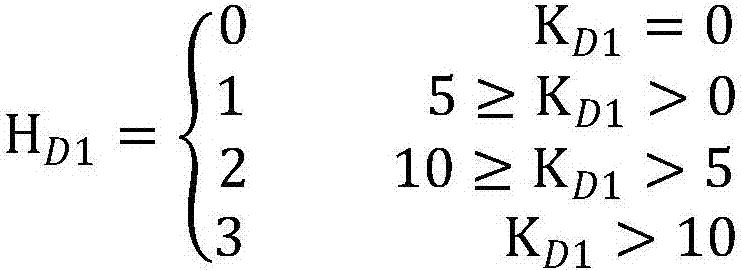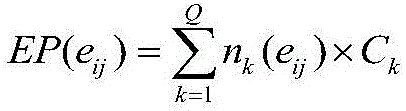Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
234 results about "Vulnerability evaluation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
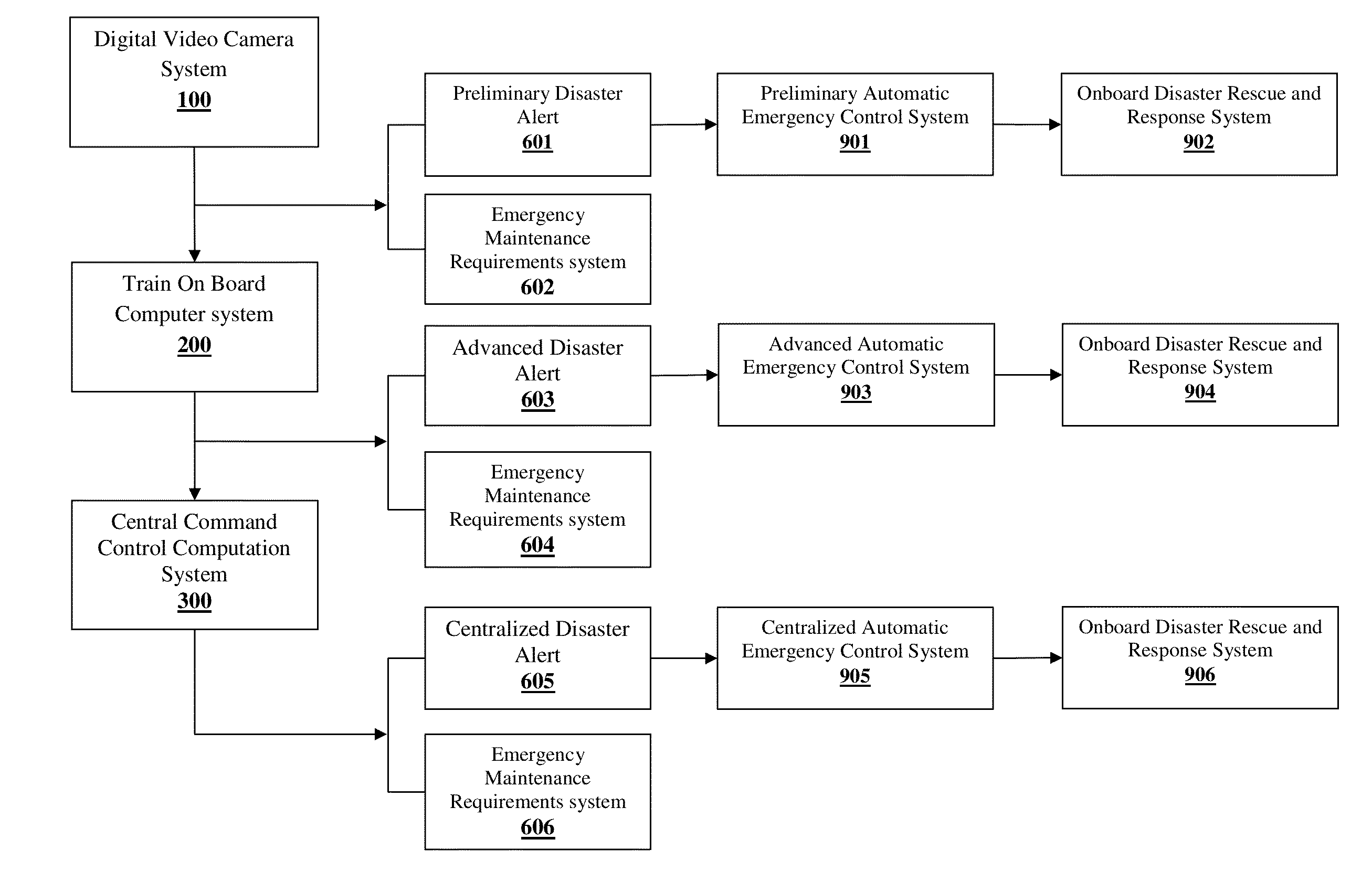
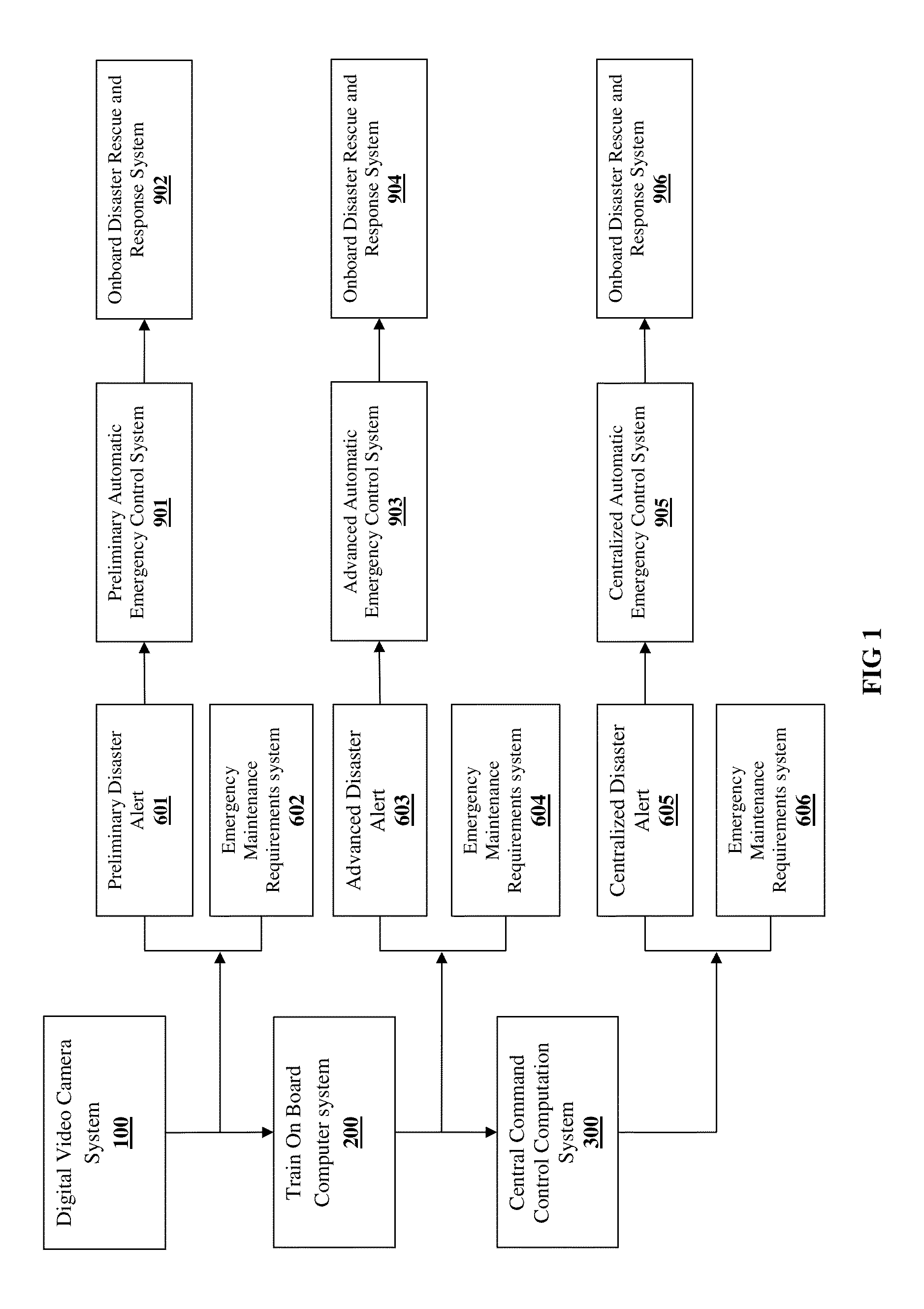
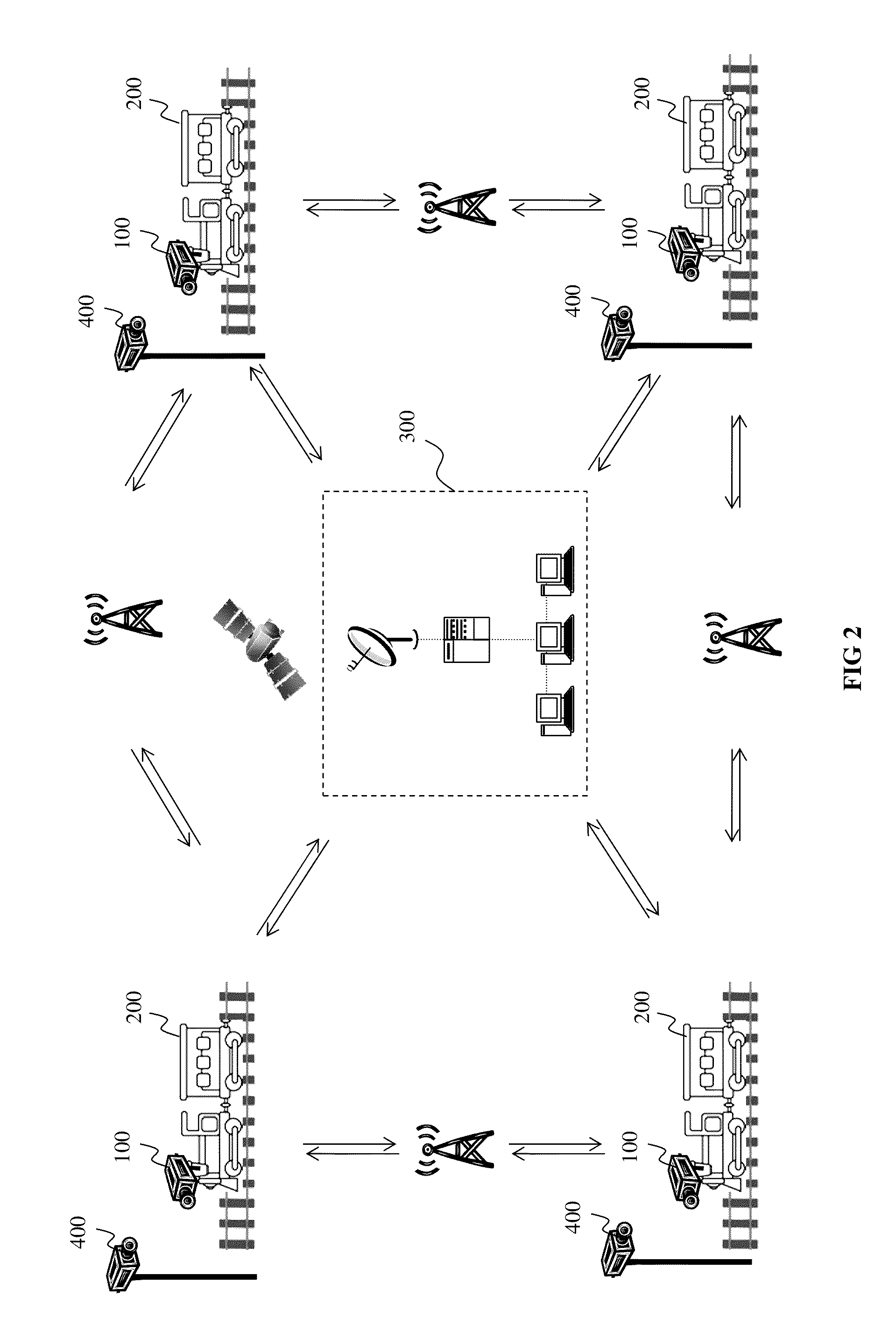
Real time railway disaster vulnerability assessment and rescue guidance system using multi-layered video computational analytics
InactiveUS20150009331A1Minimal damageReduce harmTrack side maintainanceColor television detailsGuidance systemDigital video
The system for real time train disaster vulnerability assessment and rescue guidance using multi layered video computational analytics comprises digital video cameras mounted on train, video cameras mounted at fixed locations on rail route; unmanned aerial monitoring vehicle; train on-broad computer system mounted on train and centralized system centrally located in railway network. The digital video cameras capture video images of railways track and adjacent structure from running train and automatically compute degree of disaster vulnerability from collective analysis of output from all video cameras. In case degree of disaster vulnerability exceeds predetermined threshold value a disaster alert is triggered to take immediate precautionary measures while simultaneously activating On Board Rescue and Response System. In case degree of disaster vulnerability is below predetermined threshold value, the analytics output is transmitted to higher level modules for in-depth advanced analytics by combining real-time train data or real-time geographic and environmental data contributing to a potential disaster.
Owner:VENKASTREETCARAN BALAJI
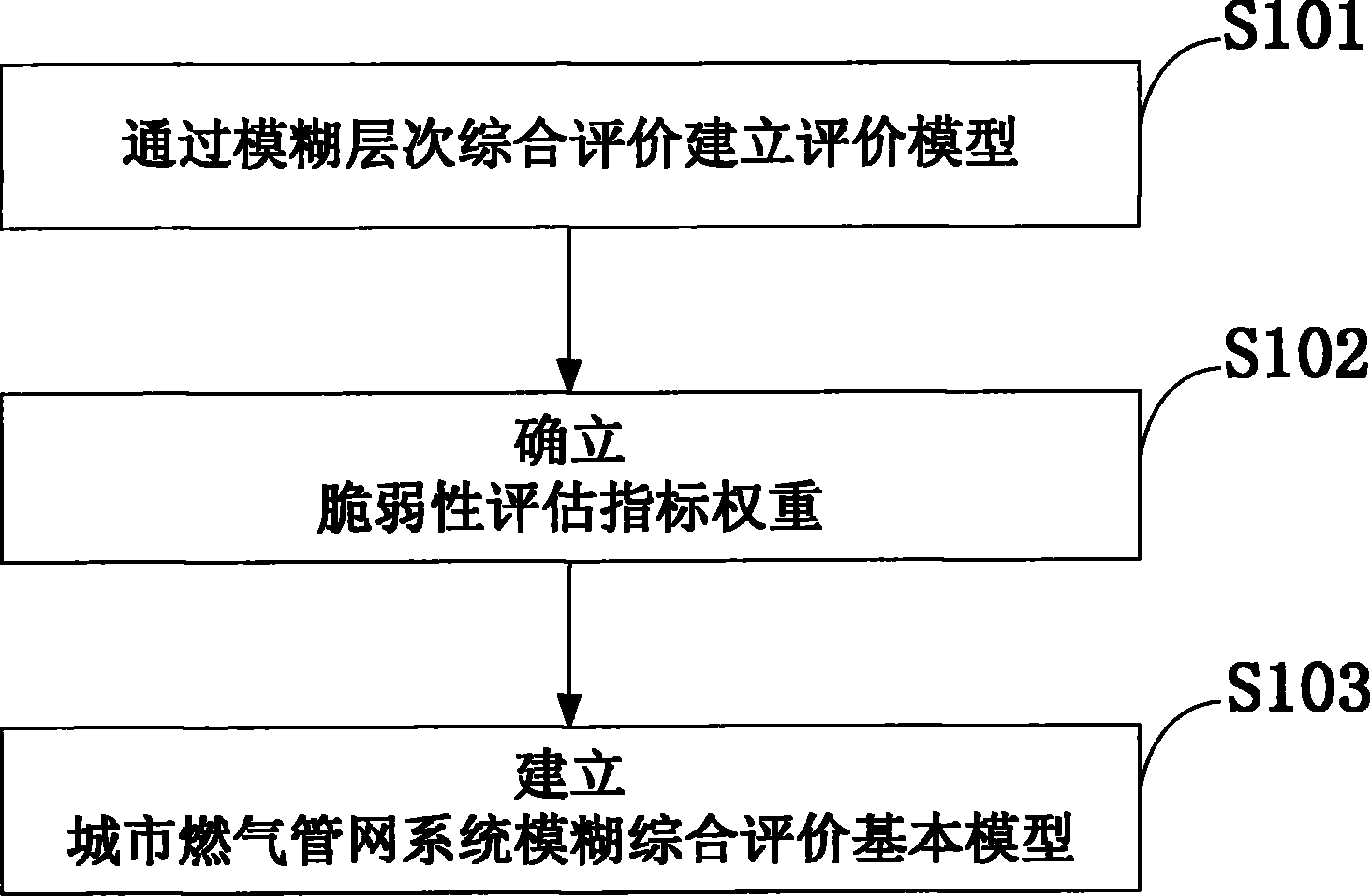
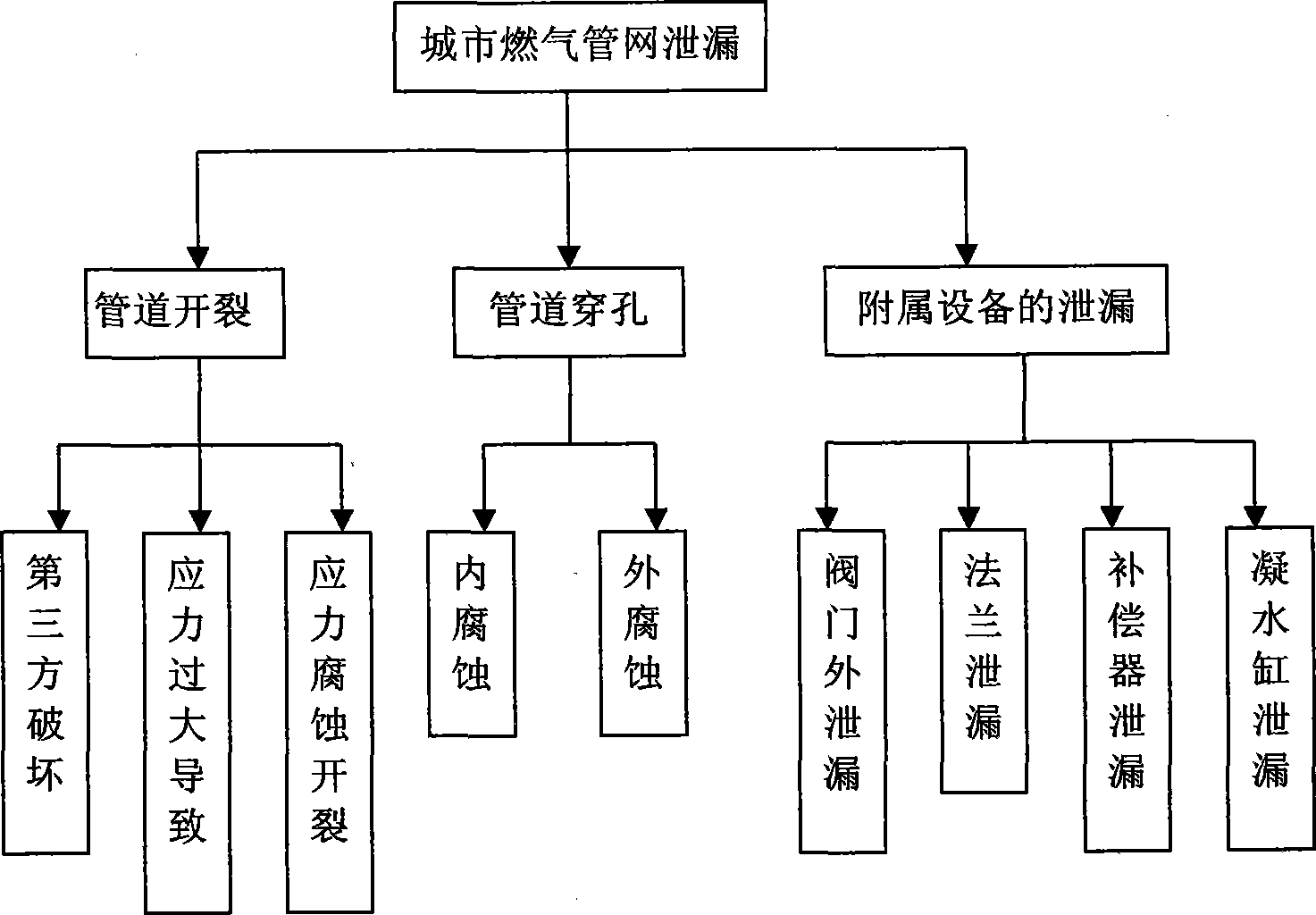
Method for building city gas pipe network vulnerability evaluation model
InactiveCN103413015AImprove the level of management technologyExtended service lifeSpecial data processing applicationsMathematical modelEngineering
The invention discloses a method for building a city gas pipe network vulnerability evaluation model. The method comprises the following steps that an evaluation model is built through fuzzy hierarchy comprehensive evaluation; a vulnerability evaluation index weight is determined; a city gas pipe network system fuzzy comprehensive evaluation basic model is built. As the system vulnerability evaluation and traditional risk evaluation are similar and both need to build evaluation index systems according to evaluation purposes, a proper evaluation method is selected to build an evaluation mathematical model, the model is utilized to conduct system vulnerability calculation and vulnerability grading, the quantitative and qualitative combined system vulnerability evaluation is achieved, and a research result of the city gas vulnerability can lay the foundation for improving the level of a Chinese gas pipeline management technology, prolonging the service life of a city gas pipeline and avoiding or reducing sudden invalidation accidents. With the deepening of the vulnerability research, the vulnerability evaluation is introduced in the filed of research of the science of disasters, the point of view of the safety evaluation is made to be wider, the content of the safety evaluation is made to be fuller, and the evaluation result has more practical value.
Owner:CHONGQING UNIVERSITY OF SCIENCE AND TECHNOLOGY
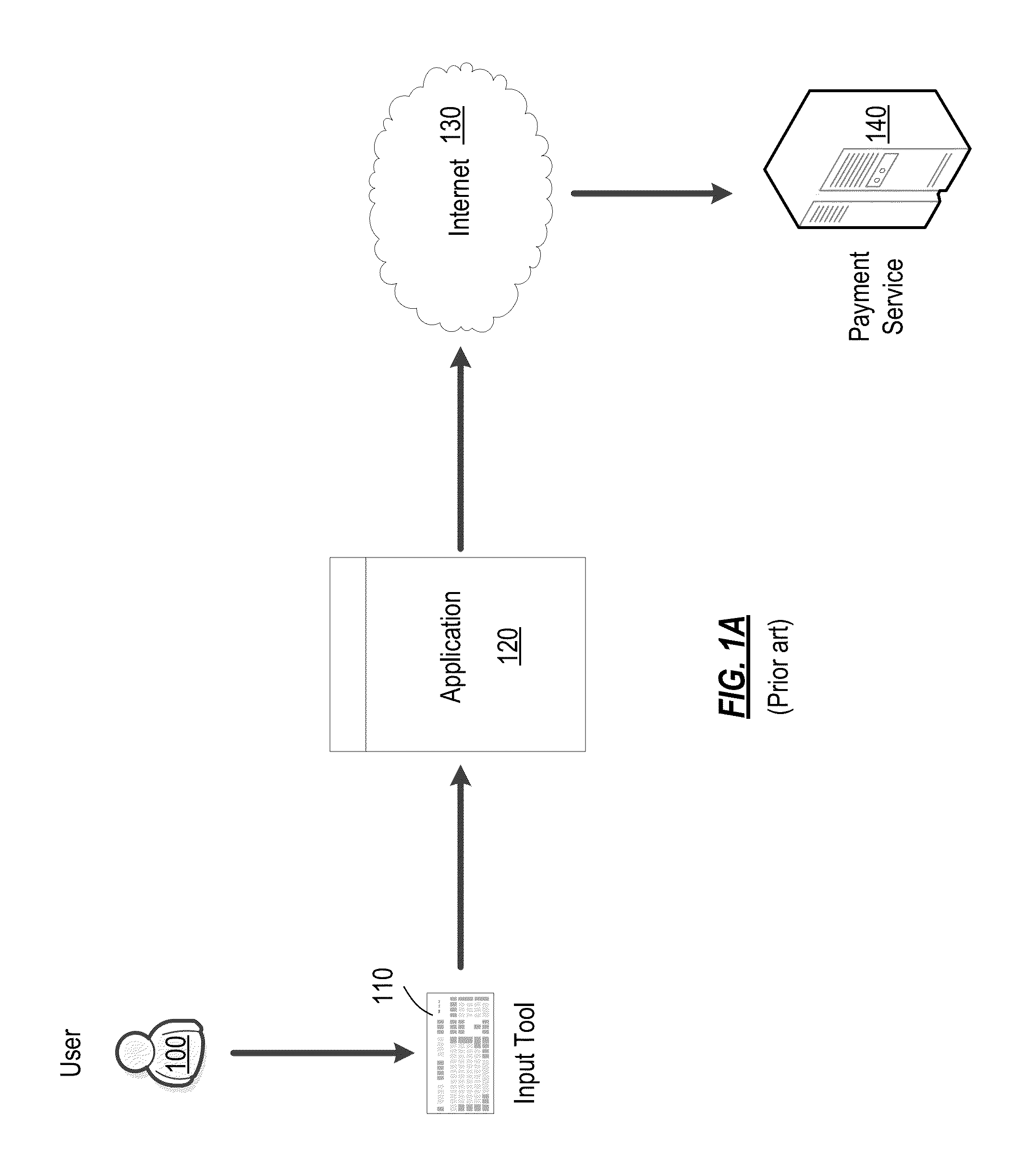
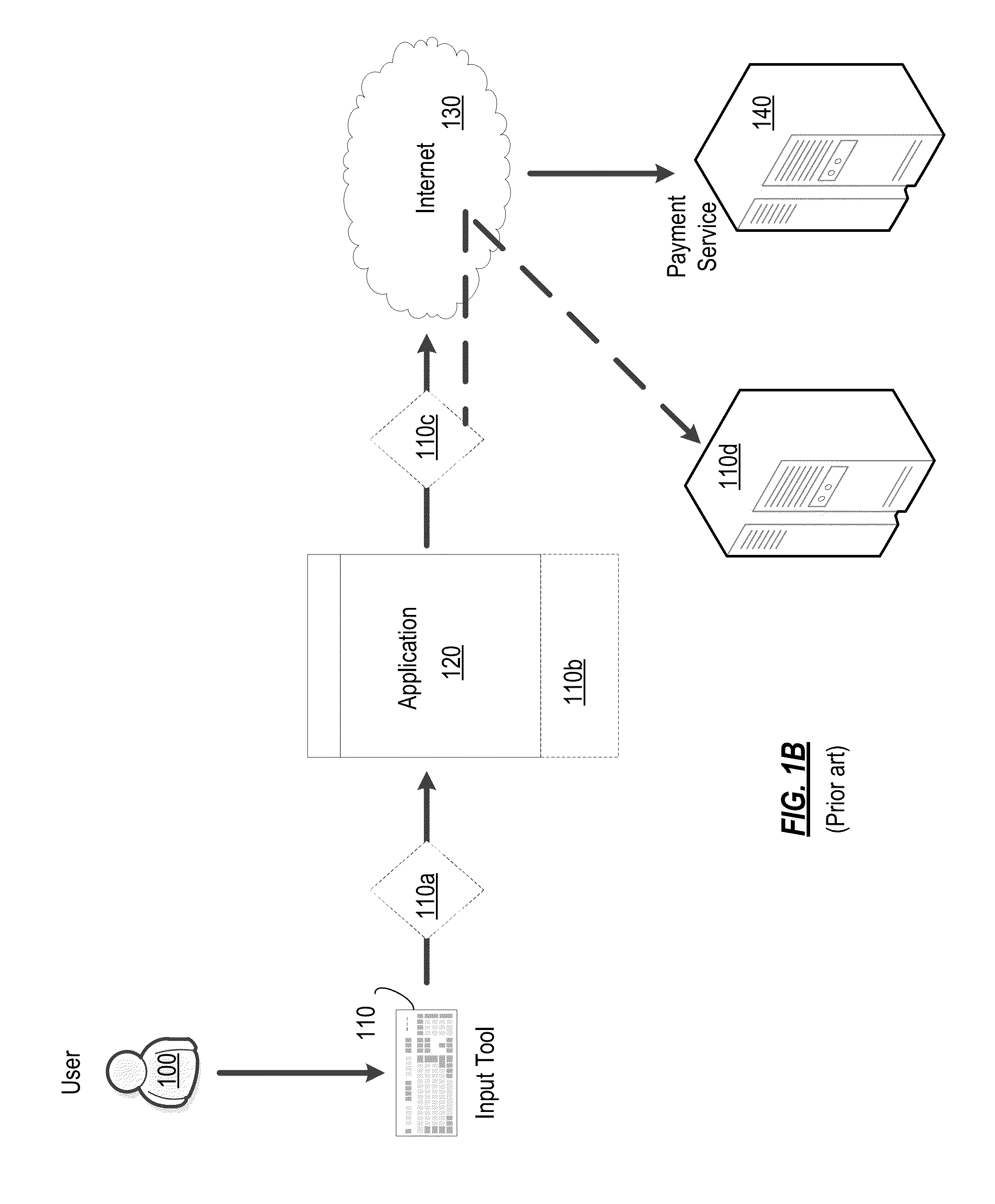
System and method for ensuring safety of online transactions
Online transaction security is improved by detecting a start of an online financial transaction between a user-controlled online transaction application and a remote payment service. A protected data input module, a protected environment module, and a safe data transfer module each provides a corresponding set of protection operations. A risk level of conducting the financial transaction is assessed based on a vulnerability assessment and on present condition of the local computing system. An initial degree of protection for each of the modules is set, and subsequently adjusted based on the risk level.
Owner:AO KASPERSKY LAB
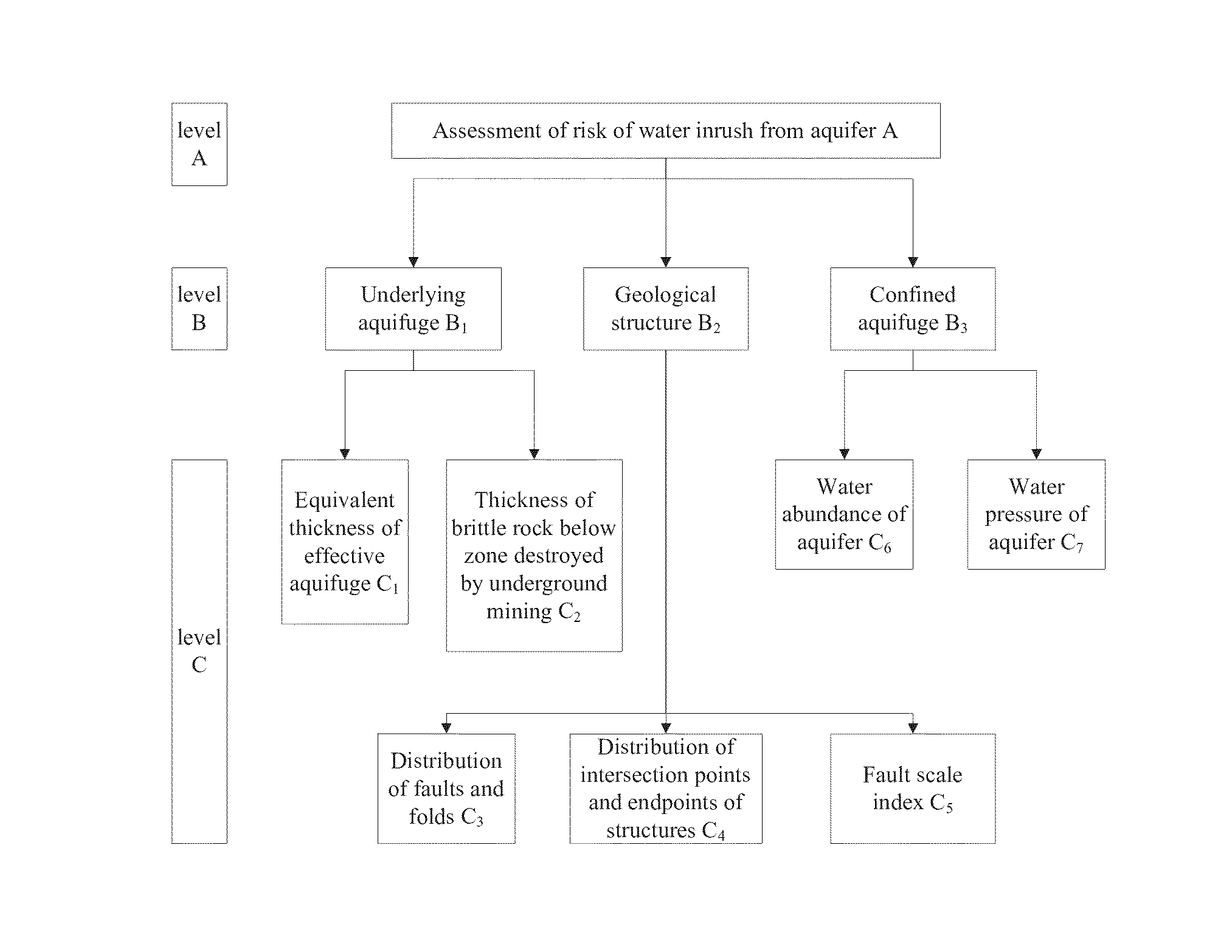
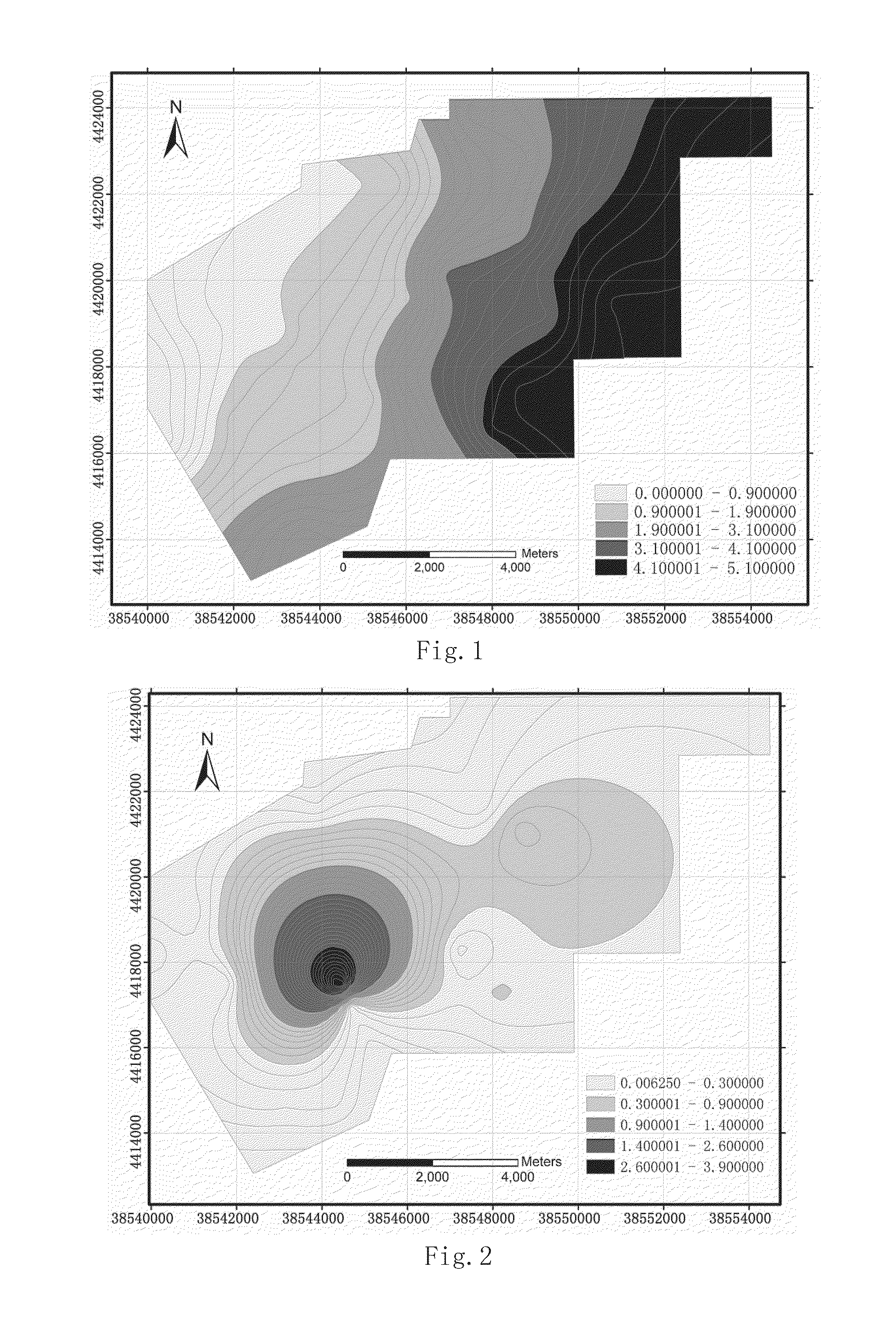
Vulnerability Assessment Method of Water Inrush from Aquifer Underlying Coal Seam
InactiveUS20160070828A1Improve vulnerabilitySolve the real problemMining devicesSeismologySuperimpositionThematic map
A vulnerability assessment method of water inrush from an aquifer underlying coal seam includes steps of: collecting main control factors determined by geological data of a target area to be assessed; quantifying relevant data against the main control factors to form thematic maps; performing normalization processing against attribute data corresponding to the respective thematic maps; establishing databases of normalized attribute data corresponding to the normalized thematic maps by utilizing GIS; determining a weight of each main control factor based on a constant weight model; determining a variable weight of each main control factor based on a zonation variable weight model; performing composite superimposition on the normalized thematic maps of the respective single main control factors, and newly building a topological relation of the relevant data among the attribute databases for performing multi-factor fitting analysis; and establishing a vulnerability assessment model based on the zonation variable weight model.
Owner:CHINA UNIV OF MINING & TECH BEIJNG
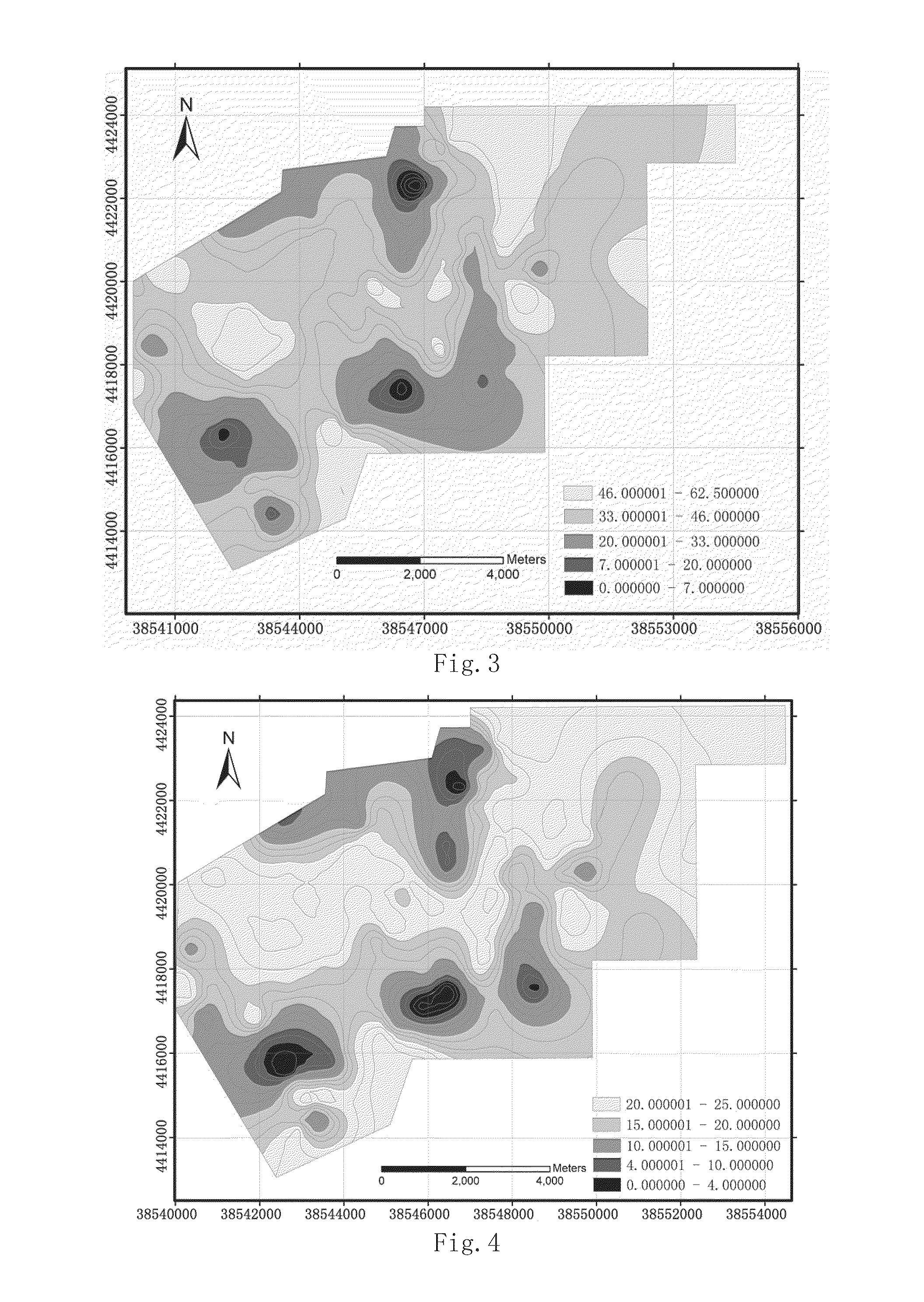
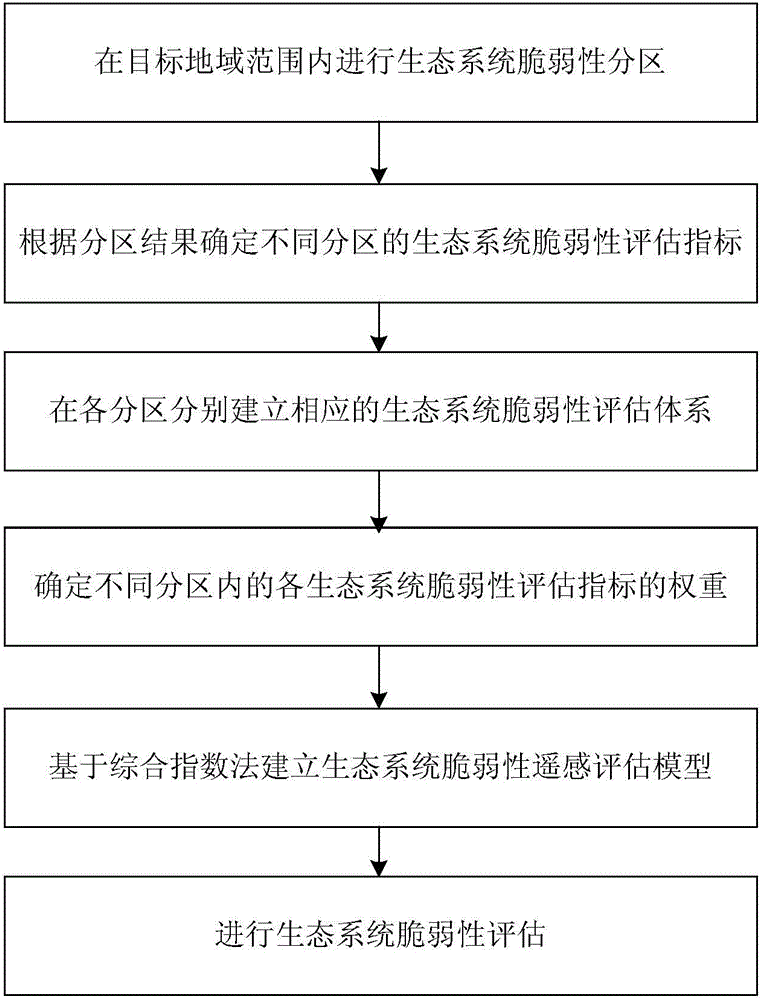
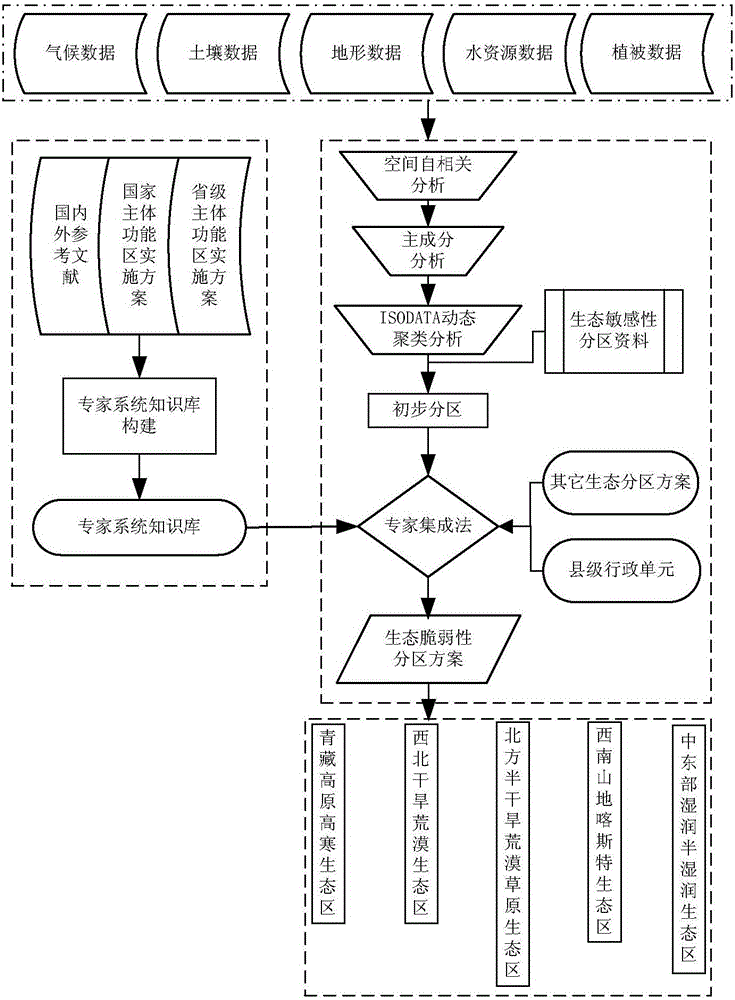
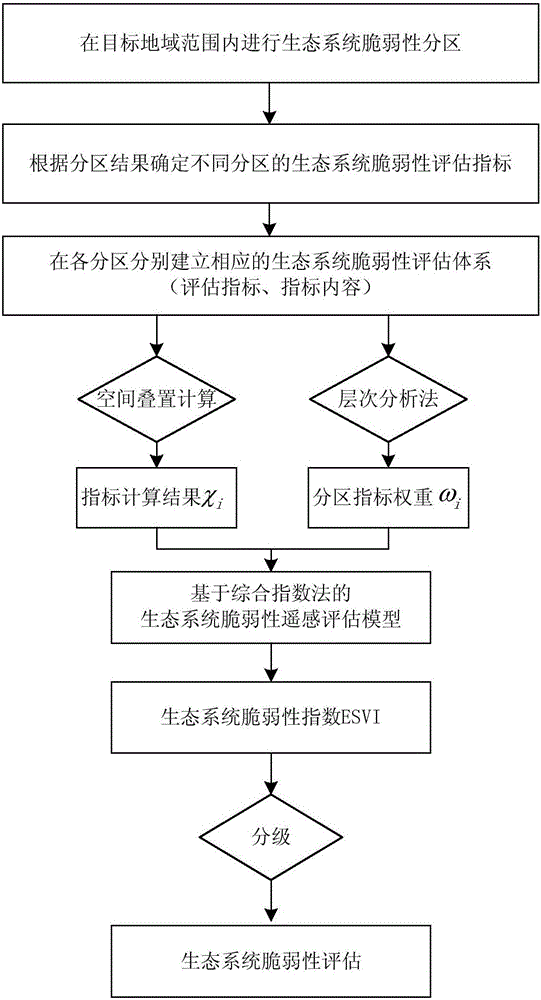
Remote sensing assessment method and system for ecosystem vulnerability
InactiveCN106599601ARealize intelligent remote sensing evaluationEvaluation results are reliableSpecial data processing applicationsInformaticsEcological environmentVulnerability evaluation
The invention relates to a remote sensing assessment method and system for ecosystem vulnerability. The method comprises the steps of performing ecosystem vulnerability zoning in a target area range, determining ecosystem vulnerability assessment indexes of different zones according to the zoning result, establishing a corresponding ecosystem vulnerability assessment system in each zone, determining the weights of the ecosystem vulnerability assessment indexes in the different zones by using a hierarchical analysis method, and establishing an ecosystem vulnerability remote sensing assessment model based on a comprehensive index method to assess the ecosystem vulnerability. According to the method, a reasonable ecological environment zoning scheme is formed in the target area range, and a scientific and normative ecosystem vulnerability assessment system, a weight assignment scheme and an assessment model are respectively constructed according to the ecological environment characteristics of the zones to realize intelligent remote sensing assessment of the ecosystem vulnerability, so that the assessment result is accurate and reliable and repeated operation can be implemented.
Owner:INST OF REMOTE SENSING & DIGITAL EARTH CHINESE ACADEMY OF SCI
Electric power information network vulnerability threat evaluation model establishment method faced to electric power CPS risk evaluation and evaluation system based on the model
ActiveCN105763562AImprove accuracyImprove timelinessPlatform integrity maintainanceTransmissionDistributed structureStructure of Management Information
The invention discloses an electric power information network vulnerability threat evaluation model establishment method faced to electric power CPS risk evaluation and an evaluation system based on the model, the model selects three groups of security vulnerability evaluation factors including vulnerability distribution threat degree, access approach and utilization complexity; an analytic hierarchy process is adopted to establish a vulnerability threat degree evaluation model, and a parameter construction method is provided; on the basis of quantitative evaluation, the evaluation result defines a vulnerability threat level, and the objectivity of quantitative evaluation and visibility of qualitative evaluation are considered; and the system related to the invention comprises a vulnerability detection part and a server part which adopt distributed structure. According to the invention, a vulnerability scanning system and a security area of the electric power information network are combined, an electric power information network vulnerability threat evaluation algorithm based on CVSS and analytic hierarchy process is adopted to perform vulnerability threat evaluation, so that the system can be safer and more accurate for performing vulnerability scanning and safety evaluation on the electric power information network.
Owner:GLOBAL ENERGY INTERCONNECTION RES INST CO LTD +3
Method for evaluating information system risk base on multi-element fusion
InactiveCN101374051AOvercoming ambiguous limitationsEnsure comprehensivenessData switching networksSecuring communicationData acquisitionVulnerability evaluation
The invention discloses an information system risk assessment method based on multi-factor fusion. The method comprises the following steps: the first step: establishing an information system risk assessment system which comprises a risk assessment result library module (12) and further comprises a risk assessment module (2), a security detection data acquisition module (13), an assets investigation module (8), a questionnaire survey module (9), an assessment library module (11) and an assessment template module (7), wherein the assessment template module (7) is connected with the risk assessment module (2); the second step: determining risk assessment factors; the third step: determining the fusion relationship of the risk assessment factors; the fourth step: performing the risk assessment, wherein the risk assessment refers to the asset assessment, the threat assessment, the vulnerability assessment and the risk calculation. The method achieves the effect of centralized analysis and handling of various security detection results, ensures strong applicability of the system and comprehensive factors for risk assessment, establishes the asset-security threat-security frangibility fusion relation, and ensures remarkable causal relationship of the assessment factors.
Owner:706 INST SECOND RES INST OF CHINAAEROSPACE SCI & IND
Assessment method for vulnerability of smart distribution network based on dynamic probability trend
ActiveCN102930175AImprove self-healing abilityData processing applicationsSpecial data processing applicationsRisk theoryVulnerability index
The invention relates to an assessment method for vulnerability of a smart distribution network based on a dynamic probability trend. The assessment method comprises the following steps: adopting a basic function and a random function to form probability distribution for node injection power of the smart distribution network; computing probability distribution for busbar voltage and line power according to Gram-Charlier stage number and semi invariant; utilizing a piecewise function to compute harm severity index caused by voltage, current and power on the smart distribution network; and then computing to output the vulnerability index of the smart distribution network. According to the invention, the method based on risk theory adopts the dynamic probability trend method to access the vulnerability, and enables a self-healing control scheme of the smart distribution network to adapt to change of load and operating environment of the smart distribution network, so that the smart distribution network can operate safely, reliably and economically.
Owner:HOHAI UNIV +2
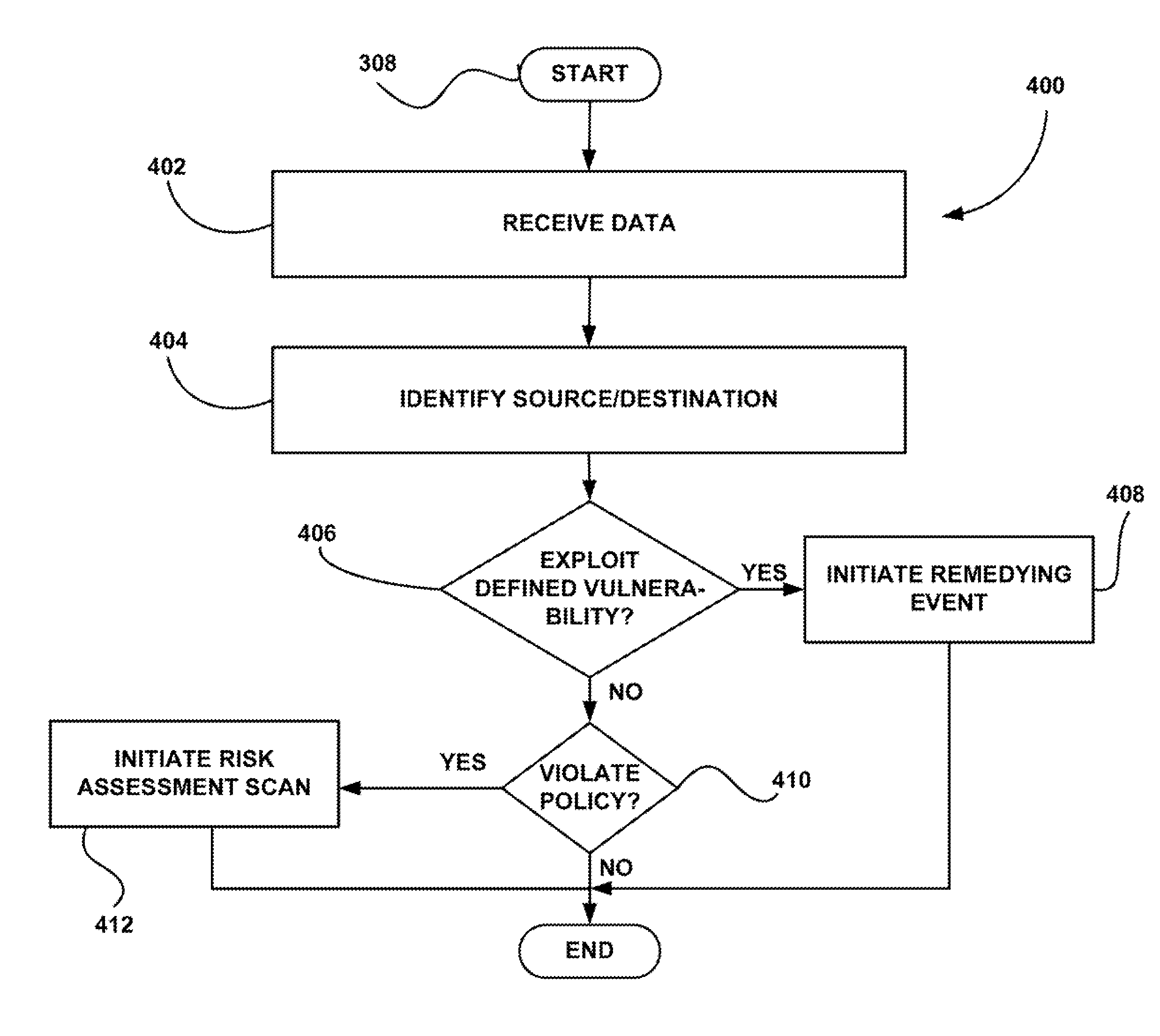
Intrusion detection and vulnerability assessment system, method and computer program product
InactiveUS7779468B1Memory loss protectionError detection/correctionNetwork communicationVulnerability evaluation
A system and associated method / computer program product are provided including an intrusion detection tool for determining whether network communications violate at least one of a plurality of policies. Such policies are defined to detect potential attacks in the network communications. Further included is a vulnerability assessment scanning tool coupled to the intrusion detection tool. The vulnerability assessment scanning tool is adapted for performing a vulnerability assessment scan for identifying vulnerabilities.
Owner:MCAFEE LLC
Intrusion detection and vulnerability assessment system, method and computer program product
InactiveUS7424746B1Memory loss protectionDigital computer detailsNetwork communicationVulnerability evaluation
A system and associated method / computer program product are provided including an intrusion detection tool for determining whether network communications violate at least one of a plurality of policies. Such policies are defined to detect potential attacks in the network communications. Further included is a vulnerability assessment scanning tool coupled to the intrusion detection tool. The vulnerability assessment scanning tool is adapted for performing a vulnerability assessment scan for identifying vulnerabilities.
Owner:MCAFEE LLC
Frangibility assessment method of electric power information physical fusion system
ActiveCN107909276AVulnerability assessmentAnalyze VulnerabilitiesResourcesPhysical spaceVulnerability evaluation
The invention relates to a frangibility assessment method of an electric power information physical fusion system. According to the invention, mutual effects and cascading faults of information and physical space in the electric power information physical fusion system are displayed; and by considering the physical-information virtual connection, effective assessment can be performed on the frangibility of the electric power information physical fusion system and fragile links of the system can be analyzed.
Owner:POWER DISPATCHING CONTROL CENT OF GUANGDONG POWER GRID CO LTD +1
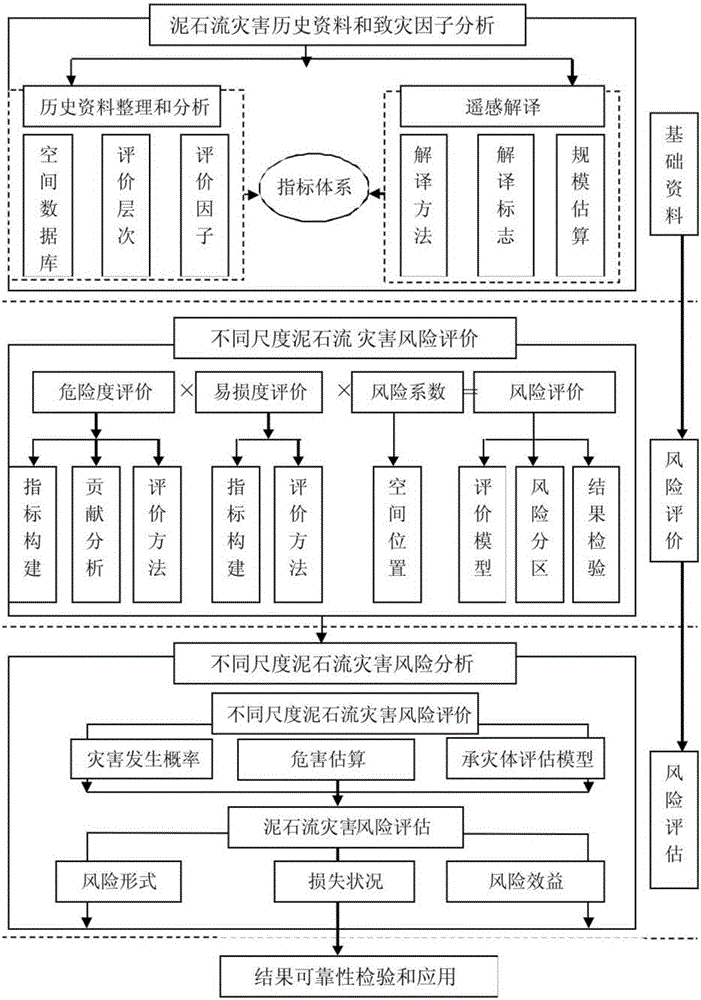
Multi-scale debris flow risk assessment method for earthquake disturbance area
The invention discloses a multi-scale debris flow risk assessment method for an earthquake disturbance area. The method comprises the steps of 1, establishing a spatial database; 2, establishing risk assessment levels and scale demands; 3, establishing risk control and management measure and suggestion demands; and 4, carrying out debris flow risk assessment, comprising four steps of debris flow probability of occurrence assessment, harm assessment, risk evaluation and risk assessment. According to the method, the debris flow dangerousness evaluation, vulnerability evaluation, risk evaluation and risk assessment technical operations for the earthquake disturbance area are stipulated; therefore, the technical basis is provided for carrying out multi-spatial scale risk assessment, control and management work on the debris flows evoked by recent earthquakes or historical earthquakes in the strong earthquake influence area; and the method is applicable to the multi-scale debris flows with scales of 1: 100,000 -1:1000 and the debris flow risk assessment, control and management technical operations for the earthquake disturbance area.
Owner:LANZHOU UNIVERSITY
Method and System For Network Vulnerability Assessment
The present invention relates to a simultaneous system for finding and assessing vulnerabilities in a network, which comprises: A. A mapping unit for: (a) scanning the network, and each time a new element is found, reporting its IP address to a profiling unit; (b) sequentially receiving from the profiling unit profile records of said newly found elements; (c) sequentially extracting tables from those elements which their profile record indicates that they are of the network equipment type; and (d) sequentially reporting to a modeling and simulating unit topology records which include said found IPs, and for those elements being of a network equipment type, said topology records also include said extracted tables; B. A profiling unit for sequentially receiving IP addresses of network elements from the mapping unit, investigating each of said elements, forming a profile record for each of said elements, and sequentially transferring said profile records to both the mapping unit and to a vulnerability assessment unit; C. A vulnerability assessment unit for: (a) sequentially receiving profile records from the profiling unit; (b) determining a list of those vulnerability tests that have to be performed on each element; (c) performing for each element those vulnerability tests that are included in its corresponding list, and determining for each test a passed or failed result; and (d) sequentially reporting to an modeling and simulation unit for each performed test, the IP of the element, the identity code of the element, and the passed or failed result; and D. A modeling and simulation unit for: (a) sequentially receiving topology records from the mapping unit, and each time a topology record is received, adding or subtracting respectively the corresponding element from a model of the network which is maintained at the modeling and simulation unit; (b) sequentially receiving from the vulnerability assessment unit vulnerability test (VT) results; and (c) sequentially analyzing the model currently existing at the modeling and simulation unit for the possibility of exploiting vulnerabilities of the network.
Owner:RAW ANALYSIS
System and method for ensuring safety of online transactions
Online transaction security is improved by detecting a start of an online financial transaction between a user-controlled online transaction application and a remote payment service. A protected data input module, a protected environment module, and a safe data transfer module each provides a corresponding set of protection operations. A risk level of conducting the financial transaction is assessed based on a vulnerability assessment and on present condition of the local computing system. An initial degree of protection for each of the modules is set, and subsequently adjusted based on the risk level.
Owner:AO KASPERSKY LAB
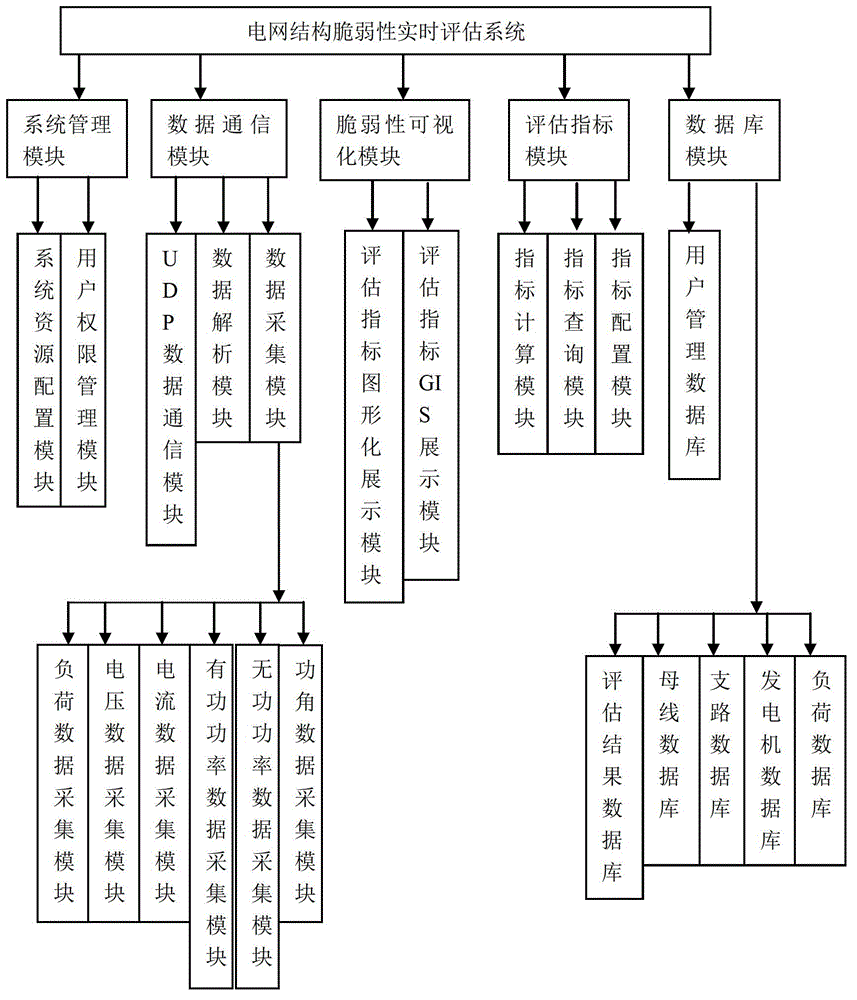
Electric network structure vulnerability real-time evaluation system
InactiveCN103150687ARealize the structureAchieve real-time recordingData processing applicationsState parameterSystems management
The invention relates to an electric network structure vulnerability quantification and visualization display technology and discloses an electric network structure vulnerability real-time evaluation system for carrying out real-time evaluation and analysis on the electric network structure vulnerability. The electric network structure vulnerability real-time evaluation system has the technical scheme that the electric network structure vulnerability real-time evaluation system comprises a system management module, a data communication module, a vulnerability visualization module, an evaluation indicating module and a database module. The electric network structure vulnerability real-time evaluation system is based on the wide area measurement information, the electric network structure vulnerability is evaluated in real time, and the functions of the structure vulnerability evaluation, the real-time display, the real-time recording and the like of operation parameters in an electric network are realized. On one hand, the receiving of dynamic data transmitted by a WAMS (wide area measurement system) is realized, in addition, the dynamic structure and the state information are analyzed, and the real-time recording of the electric network operation state parameter is realized; and on the other hand, the electric network structure vulnerability evaluation and result display is realized, and basis is provided for improving the safe operation of the electric network.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Distributed asset identification and change perception method and system
InactiveCN109327461AIncreased cyber riskImprove accuracyTransmissionResponse treatmentsInformation Harvesting
Owner:广东省信息安全测评中心
System for evaluating adequacy of power supply system
ActiveCN102567650AIncrease contentComprehensive indicatorsData processing applicationsSpecial data processing applicationsChannel powerElectric power system
The invention discloses a system for evaluating adequacy of a power supply system, comprising a generating capacity adequacy evaluating module, a network power supply vulnerability evaluating module and a system unit adequacy evaluating module, wherein the system unit adequacy module specifically comprises a unit power supply capacity adequacy evaluating module, a unit power transmission capacity adequacy evaluating module and a power transmission cross section / channel power transmission capacity adequacy evaluating module. System running personnel can select a certainty criterion or a probability risk criterion as an adequacy evaluating standard according to actual requirements. By adopting the system disclosed by the invention, content and indexes of power supply system adequacy evaluation are enriched, evaluation feasibility and effectiveness can be improved, scientific evidence can be provided for system running planning, and a weak link which exists in the power supply system can be identified.
Owner:GUANGDONG POWER GRID POWER DISPATCHING CONTROL CENT
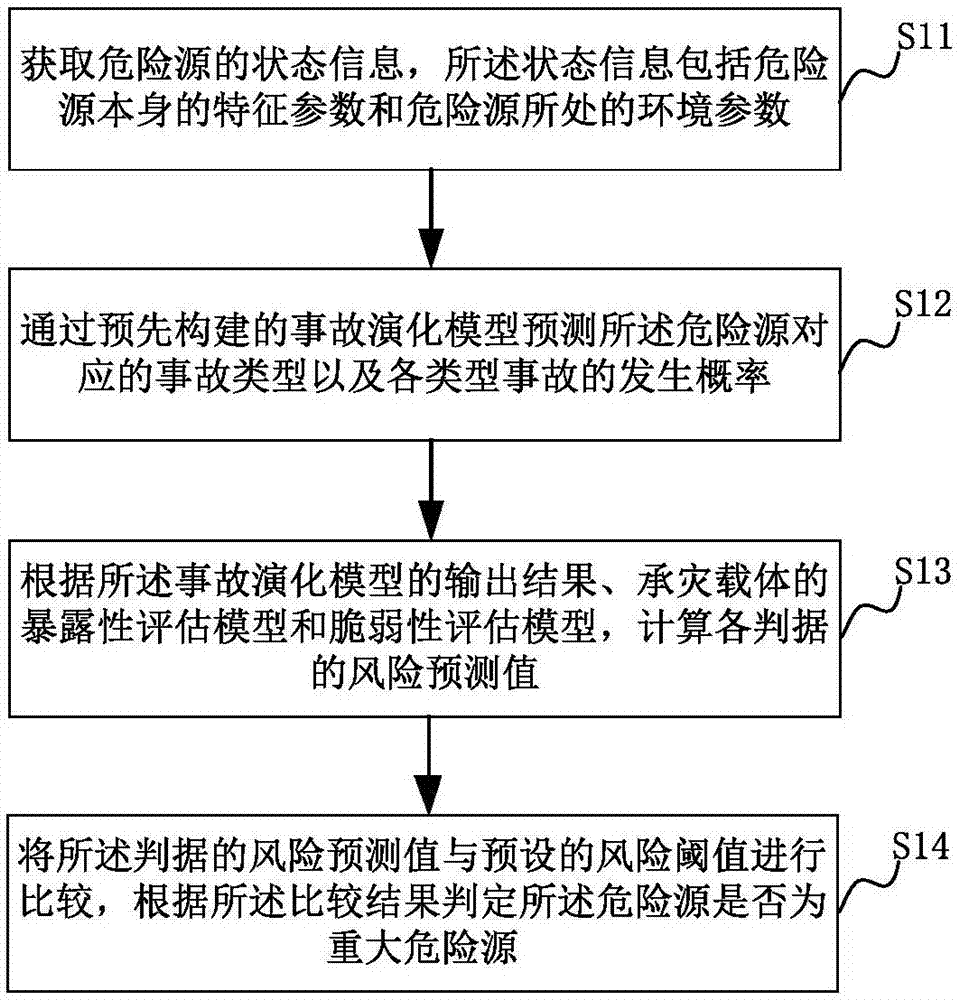
Major hazard recognition method, major hazard recognition system, storage medium and computer device
ActiveCN107169600APrevent major dangerous accidentsForecastingVulnerability evaluationComputer science
The invention relates to a major hazard recognition method, a major hazard recognition system, a storage medium and a computer device. The method comprises steps: the state information of a hazard is acquired; the state information is inputted to a pre-built accident evolution model, and an accident type evolved by the hazard and the happening possibility of each accident type are obtained; according to the preset criterions, a disaster bearing carrier corresponding to the hazard is determined, and an exposure assessment model and a vulnerability assessment model of the disaster bearing carrier are acquired, wherein the number of preset criterions is at least two; the output result of the accident evolution model is read, and according to the output result, the exposure assessment model and the vulnerability assessment model, a risk prediction value corresponding to each criterion is calculated; and the risk prediction value of each preset criterion is compared with a corresponding risk threshold, and according to the comparison result, whether the hazard is a major hazard is judged. Thus, the major hazard can be effectively recognized, and happening of a major accident is prevented.
Owner:INST OF IND TECH GUANGZHOU & CHINESE ACADEMY OF SCI
Multi-dimensional comprehensive index-based power grid vulnerability evaluation method
ActiveCN107193274AGuaranteed uptimeHigh riskProgramme controlElectric testing/monitoringElectric power systemControl system
The present invention relates to a multi-dimensional comprehensive index-based power grid vulnerability evaluation method and belongs to the power system intelligent analysis and control technical field. The multi-dimensional comprehensive index-based power grid vulnerability evaluation method is characterized in that multi-dimensional comprehensive indexes for power grid vulnerability evaluation are built; and power grid vulnerability is evaluated from three aspects, namely, equipment vulnerability evaluation, network vulnerability evaluation and operation vulnerability evaluation. Adjustment and control operation personnel can realize the key monitoring of power grid vulnerable equipment or power grid vulnerable weak links through the visualized power flow diagram of a local dispatching control system, and therefore, the adjustment and control operation personnel can be facilitated to timely process vulnerability factors that may affect the safety of a power grid.
Owner:POWER DISPATCHING CONTROL CENT OF GUANGDONG POWER GRID CO LTD +1
Power communication network vulnerability evaluation and routing optimization method
ActiveCN106789190AImprove accuracyComprehensive performance of the size of the vulnerabilityData switching networksVulnerability factorVulnerability evaluation
The invention relates to a power communication network vulnerability evaluation and routing optimization method, and belongs to the technical field of power communications. The method comprises the following steps: modeling a network topology of a power communication network, and defining the power communication network as a weighted undirected network; establishing a vulnerability evaluation model of a node and a side according to a topology vulnerability factor, a business vulnerability factor and an equipment vulnerability influencing the vulnerability of the node and the side, and evaluating the vulnerability of the power communication network according to the vulnerability evaluation model. The factors influencing the vulnerability of the node and the side are summarized as three factors of topology vulnerability, the business vulnerability and the equipment vulnerability, and a comprehensive vulnerability index is obtained according to the relation of above mentioned three factors, thereby comprehensively displaying the vulnerability size of the node and the side, and improving the vulnerability evaluation accuracy of the power communication network.
Owner:STATE GRID HENAN INFORMATION & TELECOMM CO +1
Network vulnerability evaluation method
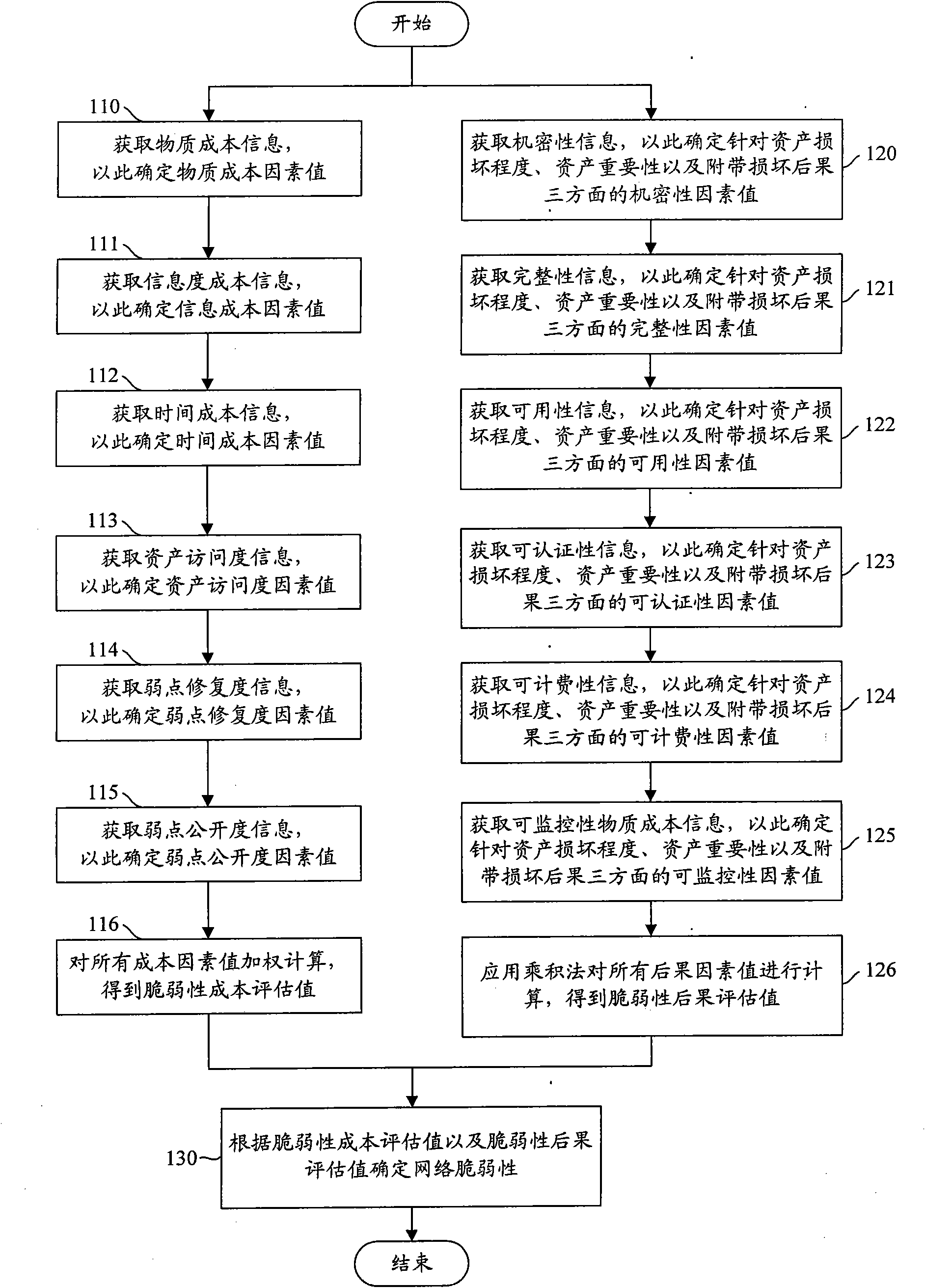
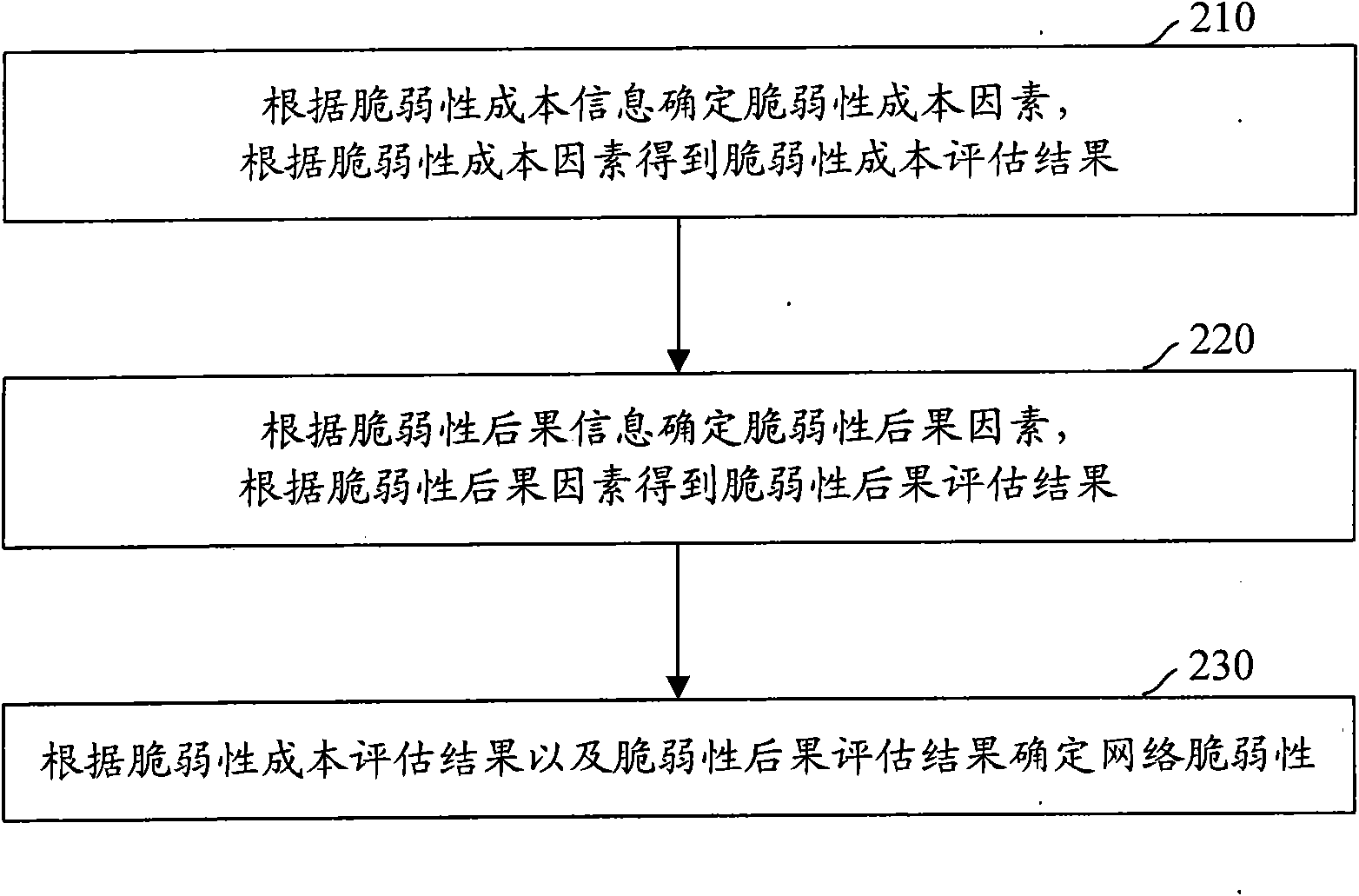
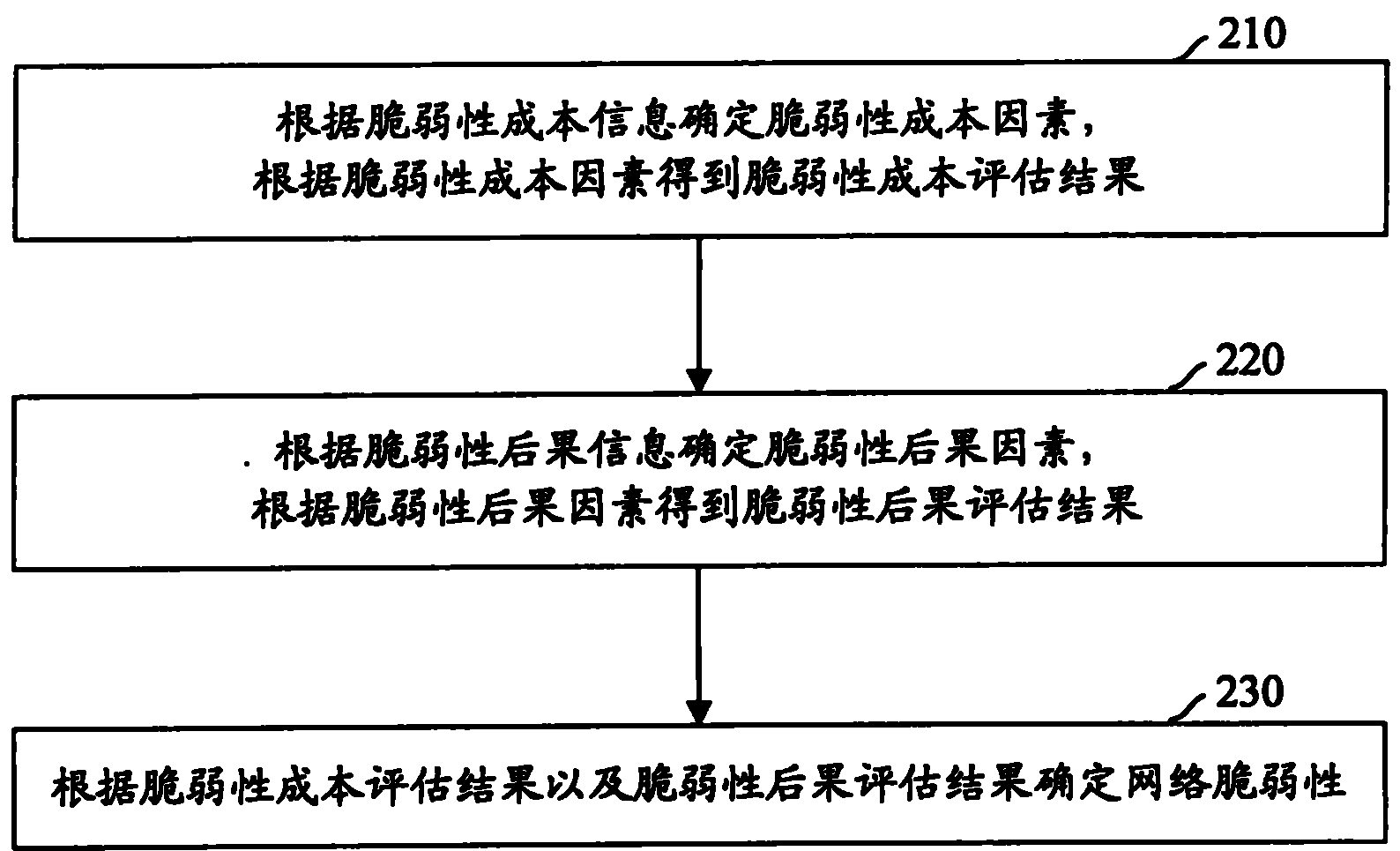
InactiveCN101964730AImprove accuracyAvoid bad consequencesData switching networksCost evaluationEvaluation result
The invention discloses a network vulnerability evaluation method. The method comprises the following steps of: determining vulnerability cost factors according to vulnerability cost information; obtaining a vulnerability evaluation result according to the evaluation cost factors; determining vulnerability consequence factors according to vulnerability consequence information; obtaining a vulnerability consequence evaluation result according to the vulnerability consequence factors; and determining network vulnerability according to the vulnerability cost evaluation result and the vulnerability consequence evaluation result. Therefore, the method of the invention takes the vulnerability cost factors and the vulnerability consequence factors into consideration comprehensively when evaluates the network vulnerability, and enriches and perfects the basis for network vulnerability evaluation in a targeted way, so that the accurate performance of the network vulnerability evaluation is improved obviously. Moreover, the obtained improved network vulnerability evaluation accuracy can provide important reference for network safety management, ensures that corresponding safety measures can be implemented more targeted in a planned manner based on the reference, and avoids a serious result caused by utilizing the network vulnerability.
Owner:BEIJING UNIV OF POSTS & TELECOMM +1
Identification method of vulnerable nodes of distribution network
PendingCN107871216AEffectively identify vulnerable nodesFind vulnerable nodesResourcesRisk theoryRisk evaluation
The invention discloses an identification method of vulnerable nodes of a distribution network. The method includes the following steps: (1) establishing vulnerability evaluation indexes based on complex network theory, and a risk evaluation index based on risk theory; (2) using a hierarchical analysis method to carry out weighted summation on the vulnerability evaluation indexes of the distribution network and comprehensively analyze the vulnerability indexes and the risk index, and establishing a comprehensive estimation index of node vulnerability of the distribution network; (3) acquiringstructure data of the distribution network and a power flow calculation result, and calculating the comprehensive estimation index of the distribution network; and (4) outputting the relatively vulnerable nodes of the distribution network. The comprehensive estimation index has the following advantages that: the complex network theory and the risk theory are adopted, a structure of the distribution network is taken into account, fault risks are taken into account, and the identification problem of the vulnerable nodes in the distribution network is comprehensively solved.
Owner:HUIZHOU POWER SUPPLY BUREAU OF GUANGDONG POWER GRID CO LTD
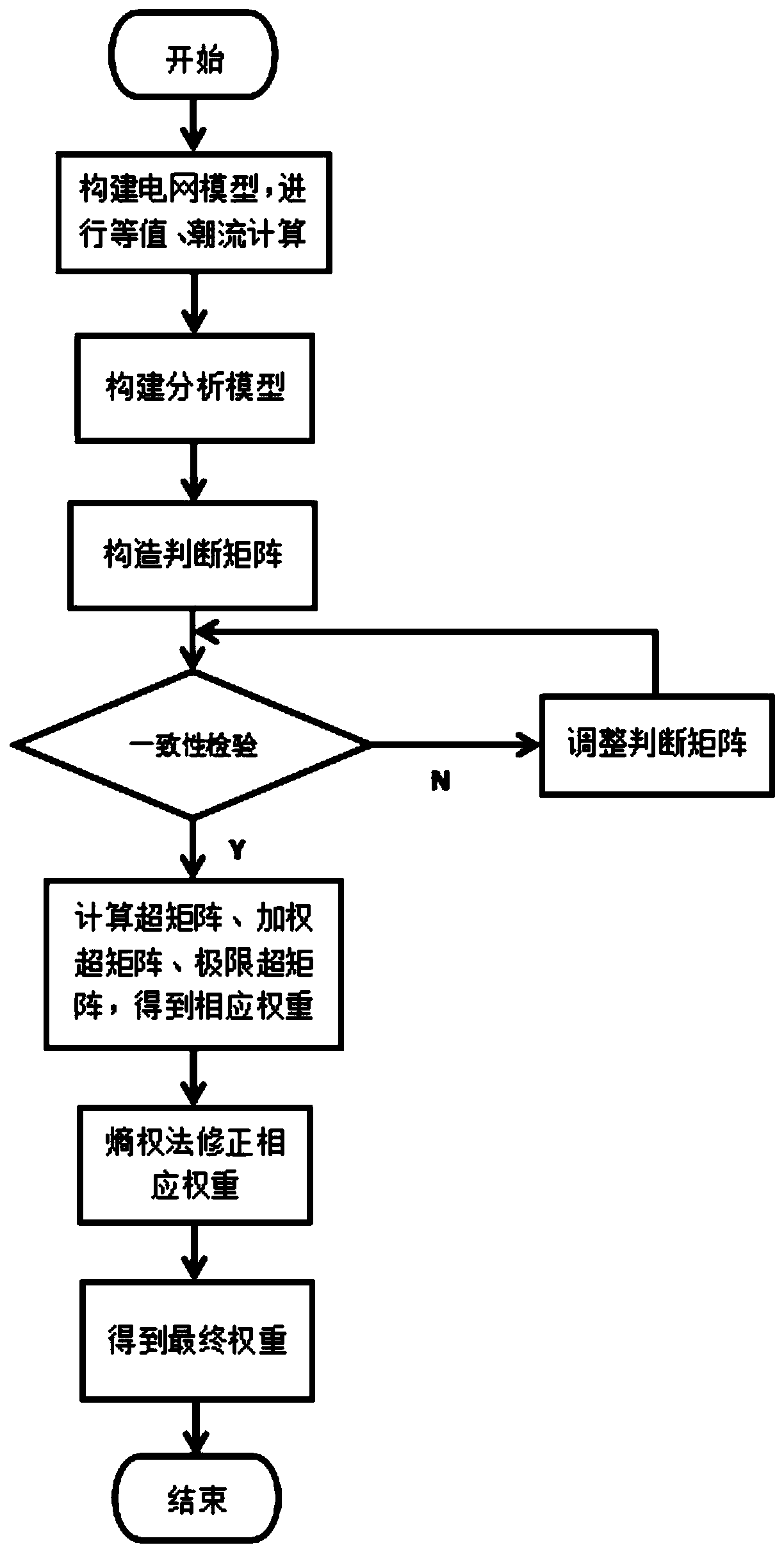
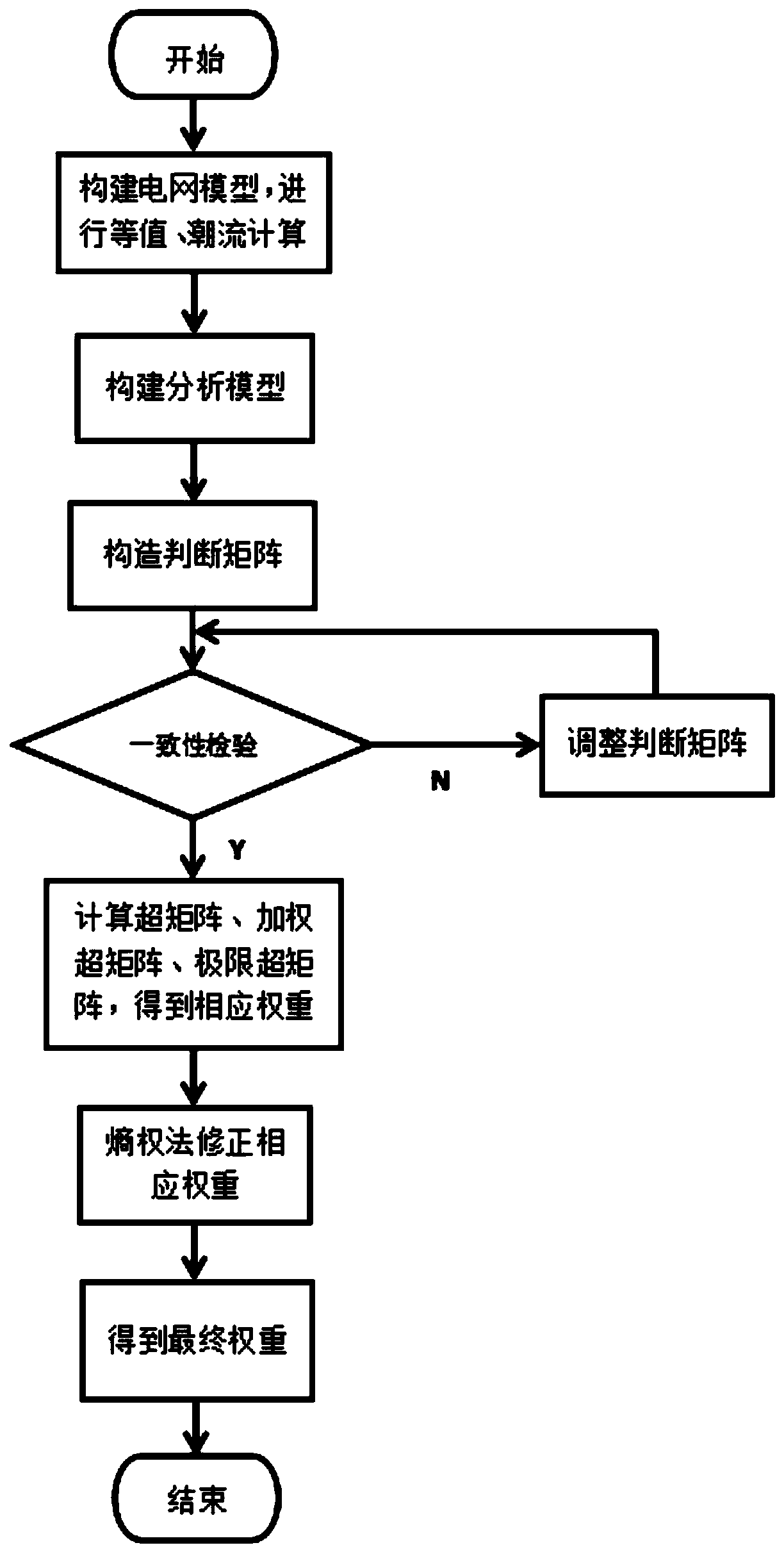
Power grid node comprehensive vulnerability index calculation method based on network analytic hierarchy process
The invention particularly relates to a power grid node comprehensive vulnerability index calculation method based on a network analytic hierarchy process. The method aims to solve the problem that node structure vulnerability and node state vulnerability are not independent, the node structure vulnerability and node state vulnerability are connected with each other, but a common analytic hierarchy process theoretically requires that the node structure vulnerability and node state vulnerability s are independent of each other, in practical application, the evaluation result of the vulnerability is unreasonable; therefore, the method is based on a network analytic hierarchy process, in the aspect of expert decision making, the mutual relation between the node structure vulnerability and thenode state vulnerability assessment result is considered; the obtained weight is more accurate; and on the other hand, an entropy weight method is utilized to reflect an objective weight value to correct the power grid node structure vulnerability and node state vulnerability weight obtained by the network analytic hierarchy process, so that a comprehensive vulnerability evaluation result of eachnode of the power grid is obtained through calculation, and sorting is carried out to judge weak links existing in the power grid. The method can meet the requirement of power grid node comprehensivevulnerability assessment under the large power grid interconnection background.
Owner:YUNNAN POWER GRID
Vulnerability evaluation apparatus, vulnerability evaluation system, and vulnerability evaluation method
InactiveUS20200097663A1Improve quality controlCharacter and pattern recognitionPlatform integrity maintainanceAttackProcessing element
A storage unit of a computer includes: a product configuration information holding unit; a component-vulnerability correspondence holding unit indicating security holes; an asset information holding unit that stores asset values of the respective component of the product; a security countermeasure classification holding unit that stores defense target components for the respective security countermeasures and coefficients of countermeasure effects; and an attack map holding unit that stores attack maps indicating attack paths. A processing unit executes a program, to form: an information collection processing unit; an attack map creation processing unit that creates an attack map for each product; and a vulnerability evaluation processing unit that calculates priority order among countermeasures from threat levels of security holes of the respective components on the basis of the asset values.
Owner:CLARION CO LTD
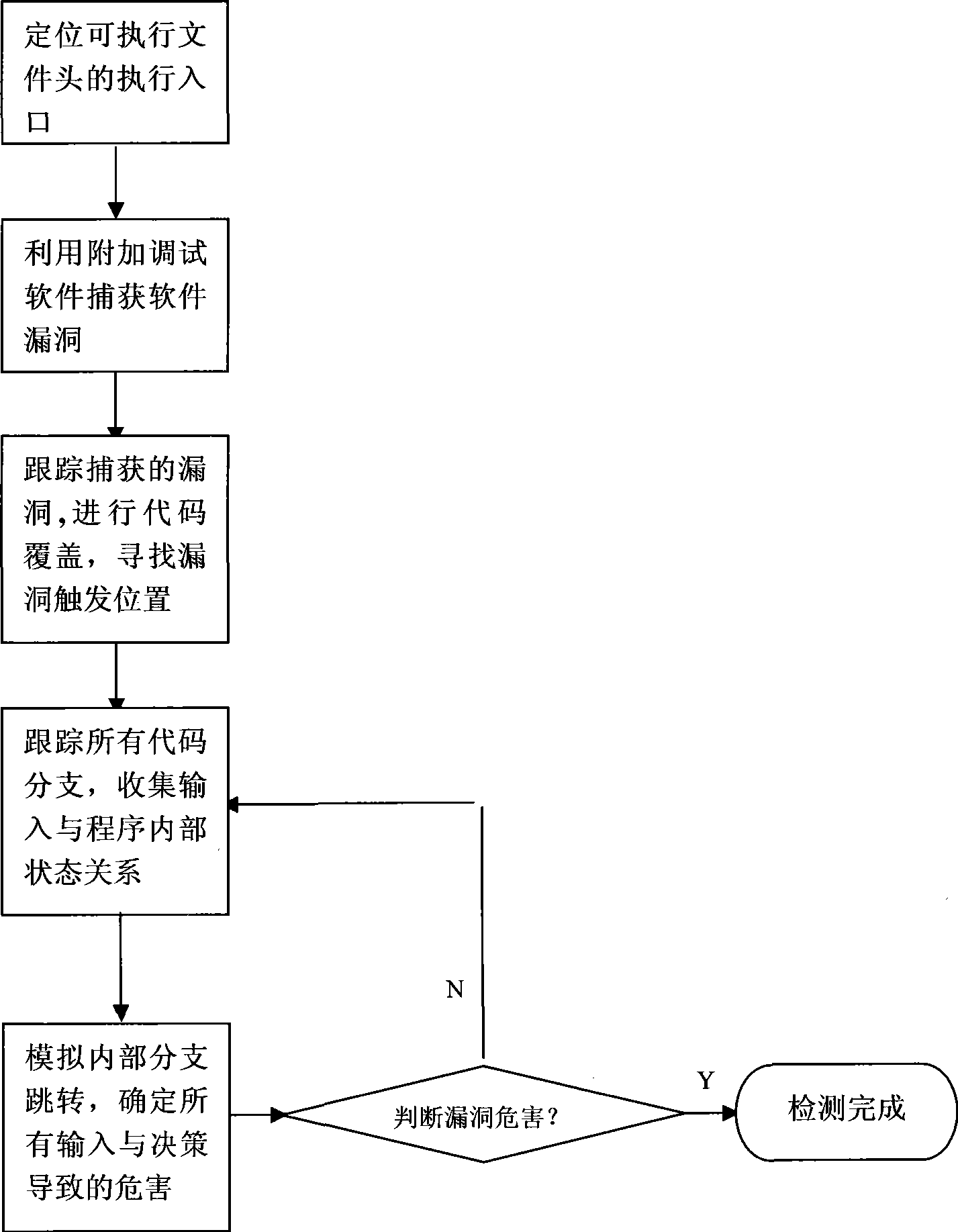
Bug excavation method based on executable code conversed analysis
InactiveCN101482846AMake up for blindnessMake up for one-sidednessSoftware testing/debuggingReverse analysisProgram instruction
The present invention relates to a vulnerability evaluation method which is in the technical field of software engineering and is based on reverse analysis of executable code. Specially, a gray box detecting method is adopted for the PE format document in the Windows system. The vulnerability information of program is captured with debugging software. The alternated data and decision are dynamically analyzed through analyzing the specific code when the program is away from the safety state by the vulnerability and reversely analyzing the program instruction flow and inputting decision information. The inherent and logical vulnerabilities in the program are evaluated. The harm of vulnerability is confirmed thereby obtaining the purpose of detecting vulnerability. The vulnerability evaluation method of the invention has higher detecting efficiency, and can evaluate the logical vulnerability which is likely to be leaked from being detected in the program more successfully.
Owner:SHANGHAI JIAO TONG UNIV
Active distribution network multi-view collaborative vulnerability assessment method considering effects of information system
ActiveCN107220775AComplies with operating conditionsAccurate predictionResourcesPhysical systemIndex system
The invention provides an active distribution network multi-view collaborative vulnerability assessment method considering effects of an information system, which comprises the steps of firstly building a definiteness-randomness topology structure model in allusion to the occurrence randomness of an external disaster of a distribution network; determining the multi-time-scale collaborative influencing information / physical component failure probability under a disaster condition based on system panoramic information; then building an active distribution network function group failure probability model considering effects of the information system; performing assessment on various operating states and grid structures of an active distribution network under a source network load interaction mode, building an active distribution network and information system integrated vulnerability assessment system under the source network load interaction mode, and assessing the collaborative vulnerability between the distribution network structure and the operating stage and between a physical system and the information system at the same time; and finally building a local collaborative vulnerability index system, a regional collaborative vulnerability index system and a global collaborative vulnerability index system on the space scale, and assessing the vulnerability of the active distribution network more comprehensively and more specifically.
Owner:NORTHEASTERN UNIV
Enhanced Real Time Frailty Assessment for Mobile
Some embodiments of the invention provide methods and apparatus for enhanced real time frailty assessment leveraging a mobile or wearable device. In some embodiments, the mobile or wearable device user's gait characteristics are determined in real time, and said information is integrated with additional information comprising the user's balance evaluation and contextual information obtained making use of the mobile or wearable device sensors, in order to deliver an enhanced frailty assessment.
Owner:PRECISE MOBILE TECH LLC
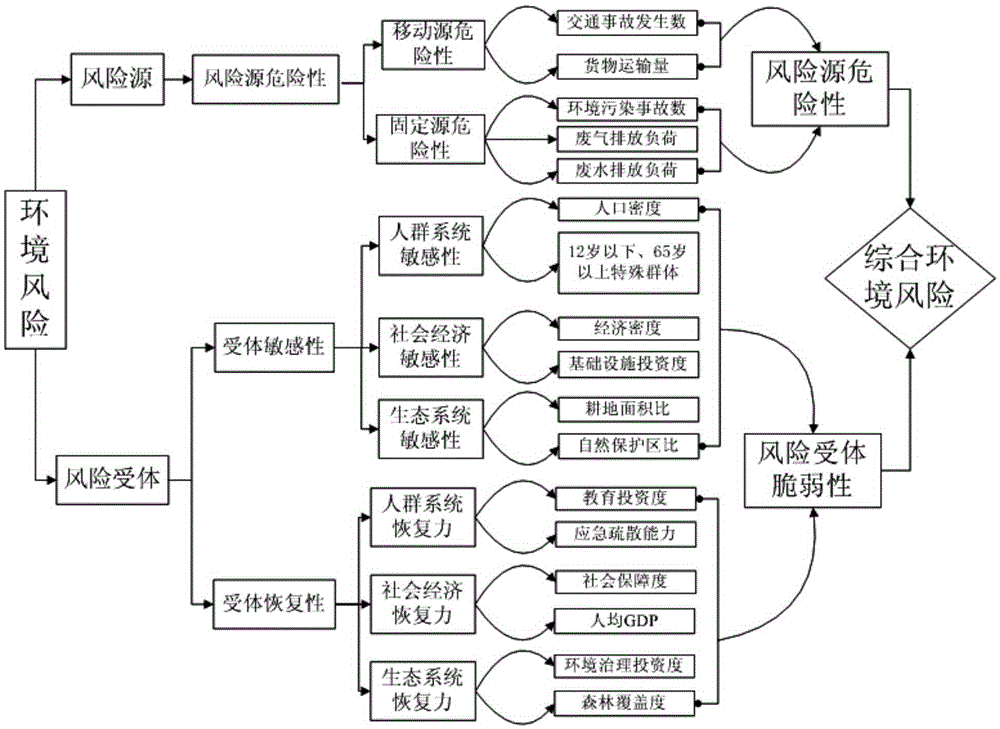
Method for comprehensively evaluating regional abrupt environmental pollution accident risk
The invention discloses a method for comprehensively evaluating a regional abrupt environmental pollution accident risk. The method comprises the following steps: building a multilayer evaluation index system for the regional environmental pollution accident risk; building a risk source dangerousness quantitative model, a receptor sensitivity quantitative model and a restoring force quantitative model by using an objective weighting method, and acquiring risk source dangerousness indexes, receptor sensitivity indexes and restoring force indexes of different study units in a study region; building an environmental risk receptor vulnerability evaluation concept model and a regional abrupt environmental pollution accident comprehensive risk evaluation concept model, and calculating an environmental risk receptor vulnerability index and a regional environmental pollution accident comprehensive risk index according to the concept models, the risk source dangerousness indexes, the receptor sensitivity indexes and the restoring force indexes; and hierarchically clustering comprehensive environmental risk profiles of evaluation units. Through adoption of the method, a scientific theoretical foundation is laid for regional environmental risk comprehensive management, industrial distribution adjustment and optimization, accident emergency and the like. The method has the advantages of high efficiency, low cost, high accuracy and the like.
Owner:HENAN POLYTECHNIC UNIV
Section electric betweenness vulnerability estimation method of power system under wind power grid connection
ActiveCN110034581AVulnerability assessmentAvoiding BlackoutsSingle network parallel feeding arrangementsWind energy generationElectricityElectric power system
The invention discloses a section electric betweenness vulnerability estimation method of a power system under wind power grid connection. The method employs an interval number to describe the fluctuation of a wind power grid-connected power, the section electric betweenness method is proposed, a circuit section electric betweenness and a node section electric betweenness are respectively sequenced according to a possibility degree section sequence method, and a vulnerable circuit and a node in wind power grid connection are identified. By the method, the vulnerable circuit and the node in thewind power grid connection can be effectively and accurately identified; and compared with a traditional power system vulnerability estimation method, the method more conforms to actual running condition of the power system after wind power grid connection and has important guidance significance to prevention of large power failure of a wind power grid-connected power system.
Owner:XIANGTAN UNIV
Pollution risk evaluation method for underground water type drinking water source region
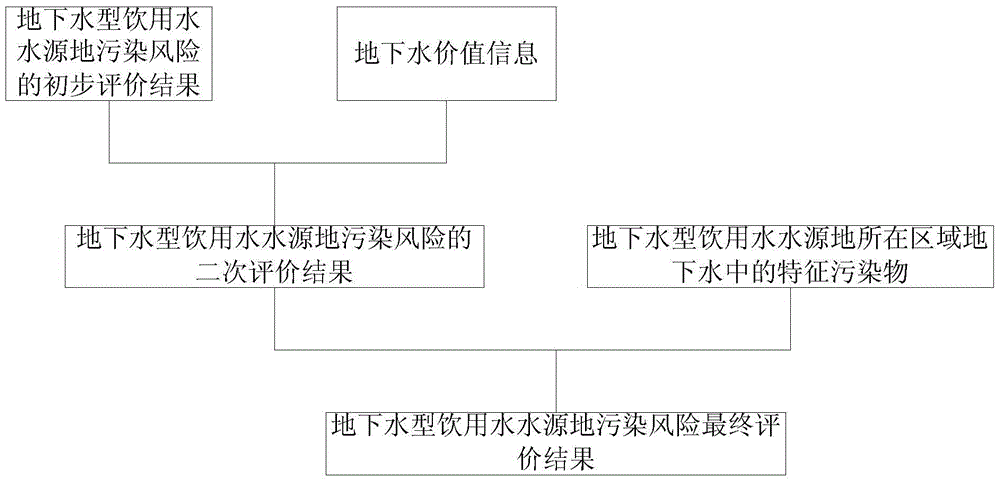
The invention provides a pollution risk evaluation method for an underground water type drinking water source region, wherein the pollution risk of the underground water type drinking water source region can be evaluated at a time aspect and a space aspect. The pollution risk evaluation method comprises the steps of acquiring an underground water inherent vulnerability evaluation result and a pollution source damage grade at an area with the underground water type drinking water source region; combining the underground water inherent vulnerability of the area with the pollution source damage grade, and performing preliminary evaluation on an area pollution risk; combining underground water dynamic change information with an exploitation condition on a preliminary evaluation result, thereby obtaining a water resource region pollution risk evaluation on the exploitation condition; based on the water resource region pollution risk evaluation result on the exploitation condition, combining underground water value information for performing secondary evaluation on the area pollution risk; and performing migration simulation on characteristic pollutants on the exploitation condition of the water source region based on the secondary evaluation result, thereby finishing pollution risk evaluation on the underground water type drinking water source region. The pollution risk evaluation method is suitable for the technical field of environmental science and environment risk.
Owner:BEIJING NORMAL UNIVERSITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com