Identification method of vulnerable nodes of distribution network
An identification method and technology of distribution network, applied in the direction of instruments, data processing applications, resources, etc., can solve problems such as no longer applicable, increasing failure occurrence, weak links in distribution network, etc., to achieve accurate and reasonable, accurate High, effectiveness in addressing vulnerability issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
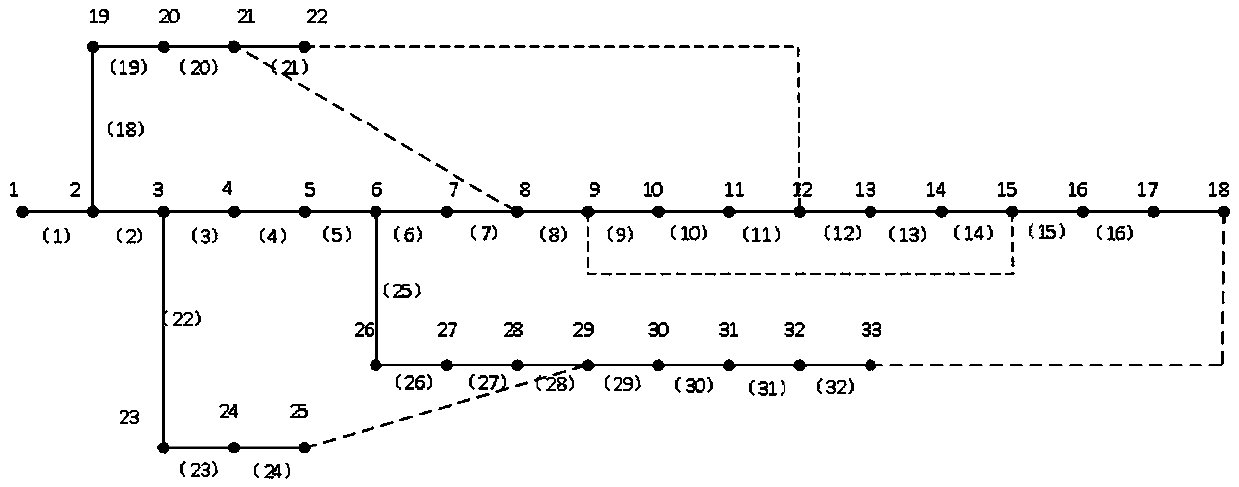
[0045] The accompanying drawings are for illustrative purposes only, and should not be construed as limitations on this patent; in order to better illustrate this embodiment, certain components in the accompanying drawings will be omitted, enlarged or reduced, and do not represent the size of the actual product; for those skilled in the art It is understandable that some well-known structures and descriptions thereof may be omitted in the drawings. The positional relationship described in the drawings is for illustrative purposes only, and should not be construed as a limitation on this patent.
[0046] Such as figure 1 As shown, a method for identifying vulnerable nodes in a distribution network includes the following steps:
[0047] Step 1, establishing distribution network node indicators, specifically including:
[0048] Step 101, establishing vulnerability assessment indicators based on complex network theory;
[0049] Step 102, establishing risk assessment indicators ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com