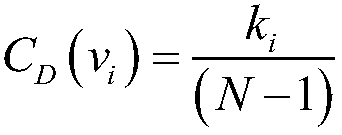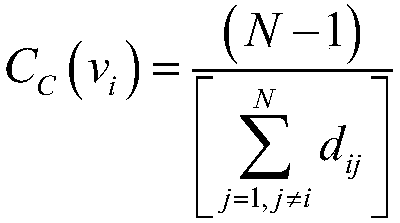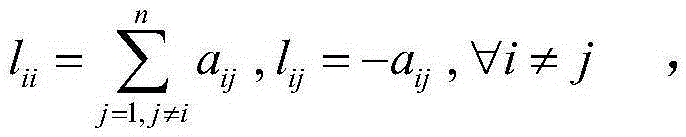Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
99results about How to "Addressing Vulnerability" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
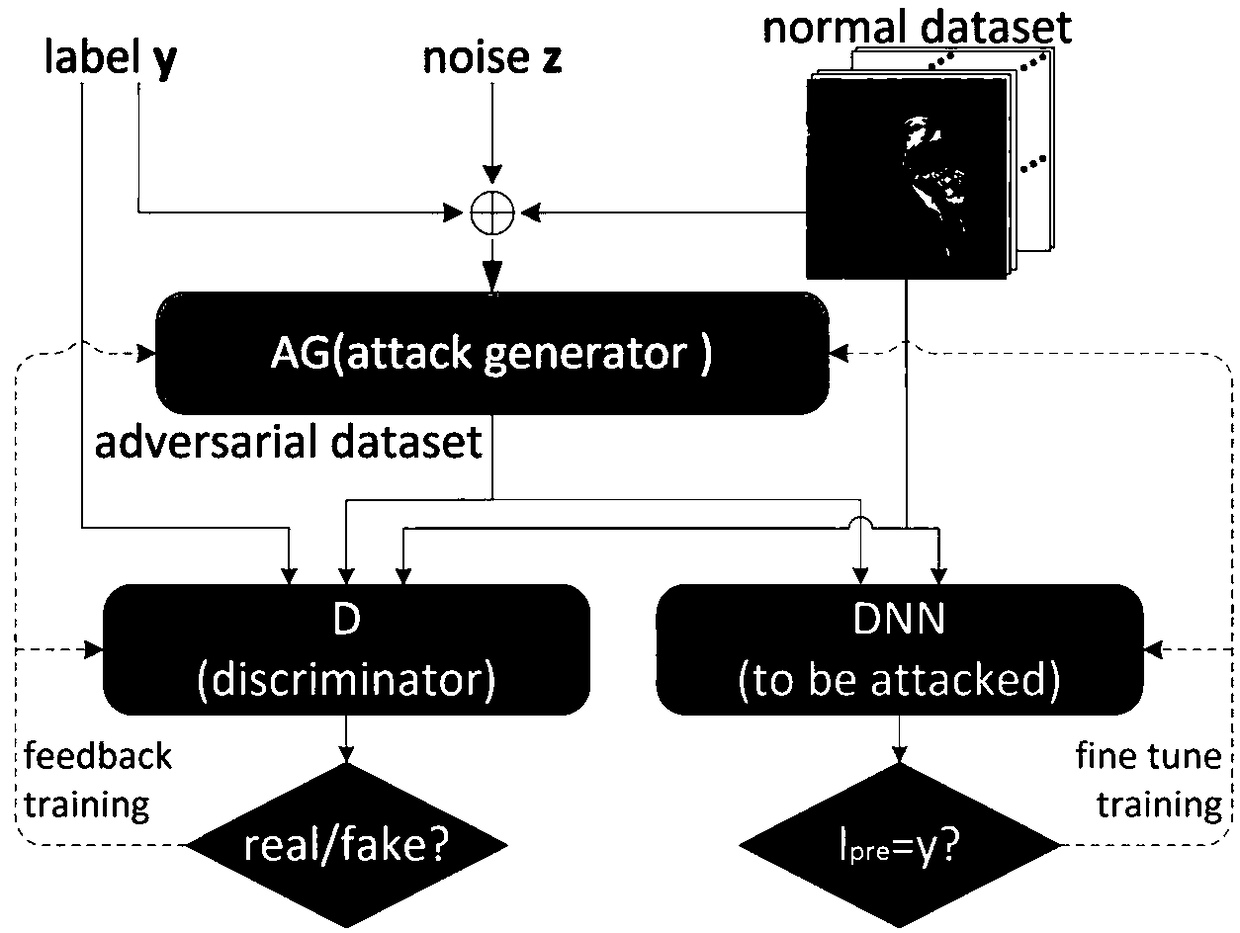
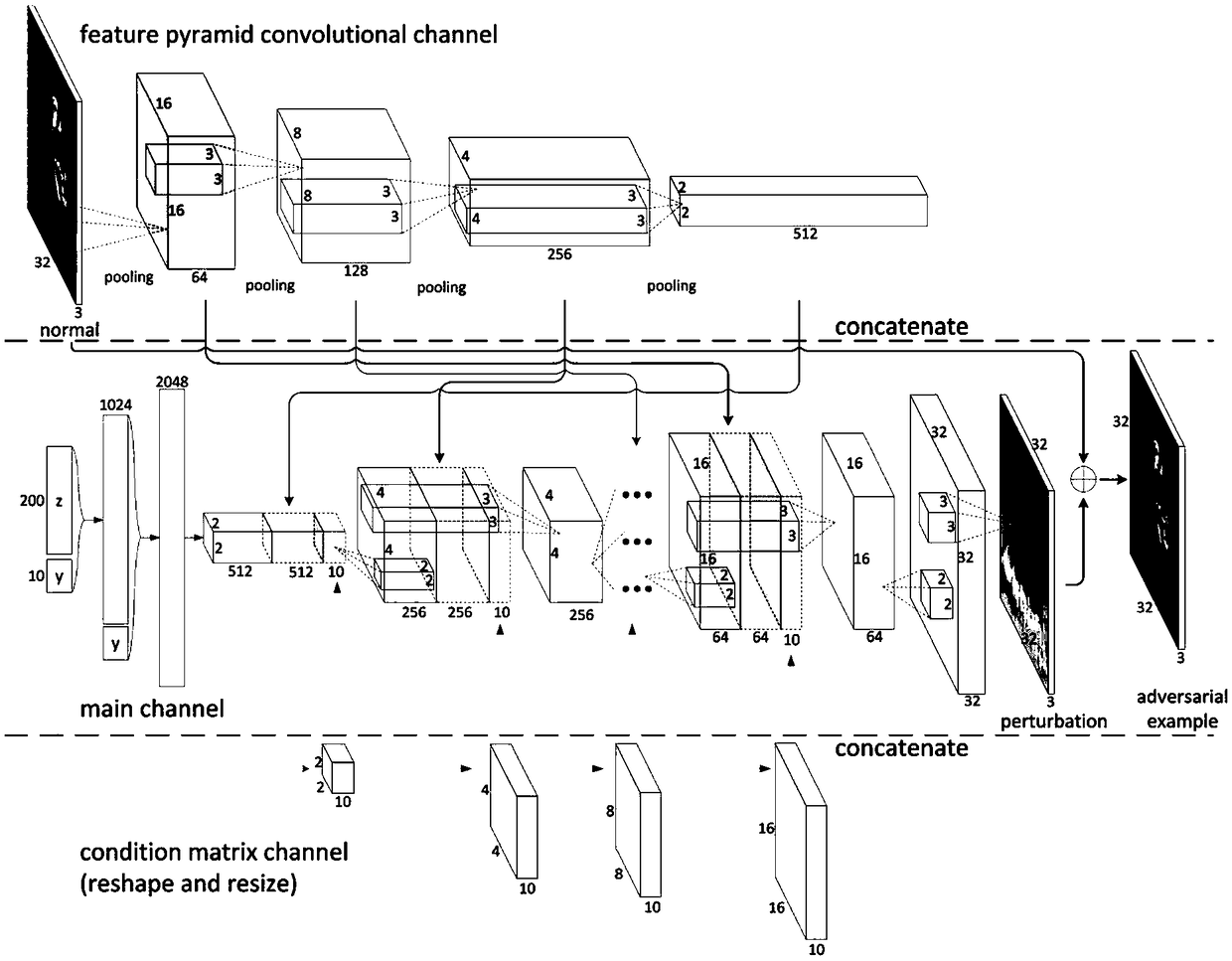
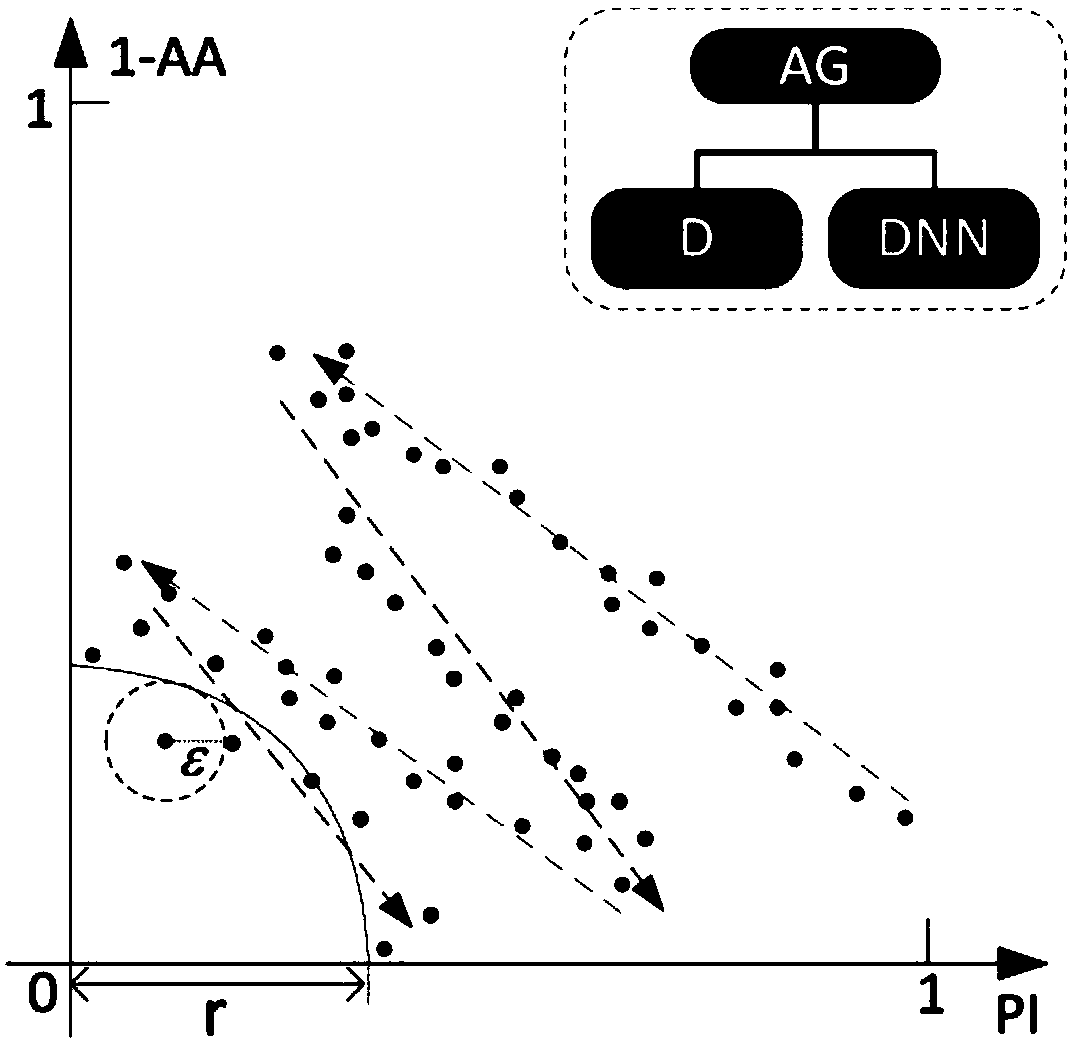
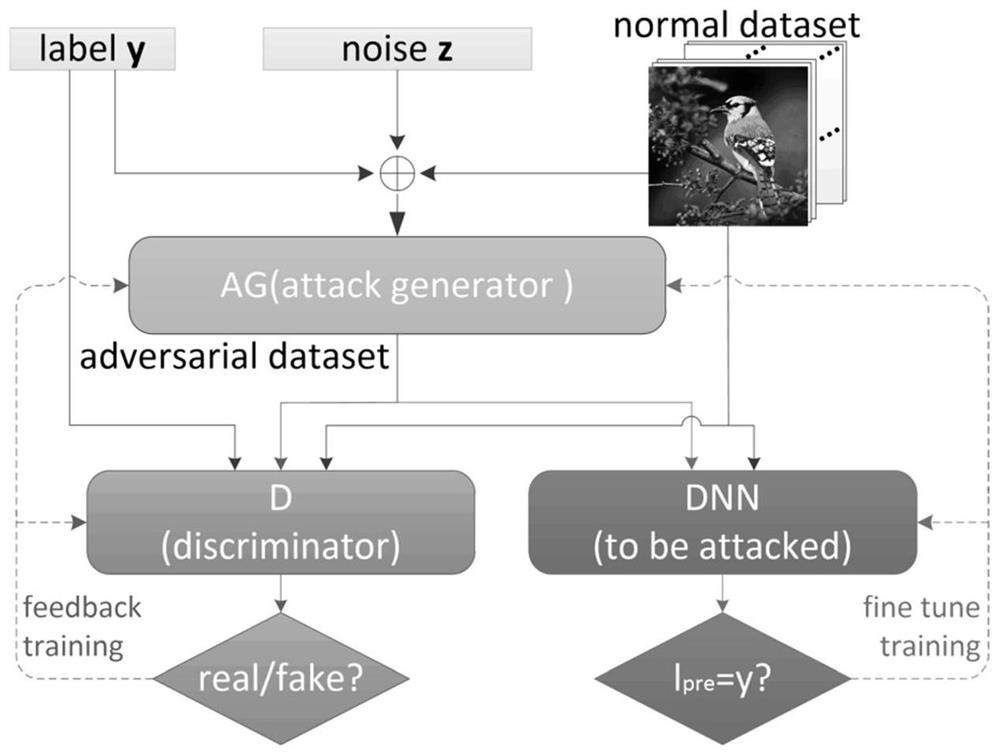
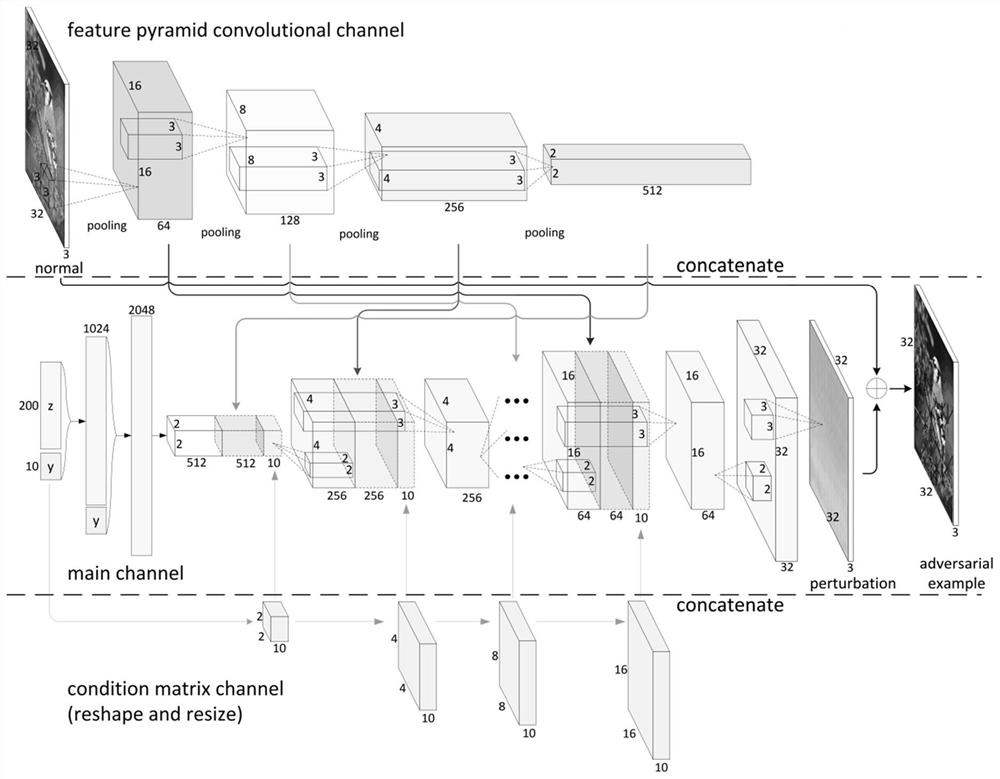
A deep learning classification method with the function of defending against sample attack
ActiveCN109460814AReduce disturbanceImprove attack abilityNeural architecturesData setClassification methods
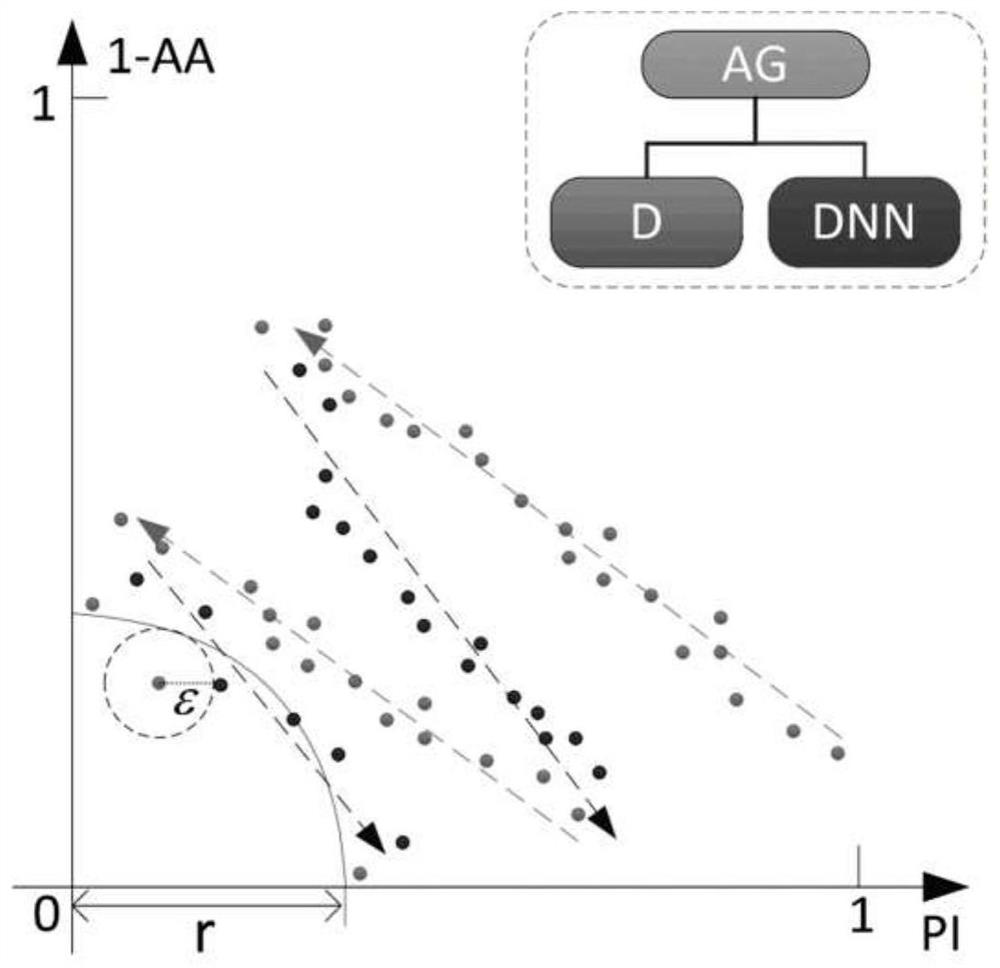
The invention discloses a depth learning classification method with the function of defending against sample attack, The device for realizing the classification method comprises: an attack generationmodel AG, a confrontation sample discrimination model D and a classification model DNN. The specific methods are as follows: (1) training the DNN by using a normal data set, the classification accuracy is higher than a preset value, and the training of the DNN is stopped; (2) Alternatively training the parameters of AG and D until AG-D realizes Nash equilibrium; (3) The parameters of AG and DNN were alternately trained until AG-DNN realizes Nash equilibrium; 4) judging whether that discrimination model D and the classification model DNN of the antagonism sample reach the Pareto optimality, ifso, the DNN training is complete and the step 5 is executed; otherwise, the step 2) is returned; (5) Inputting the samples to be classified into the trained classification model DNN to obtain the classification result. The invention can effectively solve the vulnerability of the classification model when confronted with the confrontation sample in the actual classification application, and improvethe robustness of the model performance.
Owner:ZHEJIANG UNIV OF TECH
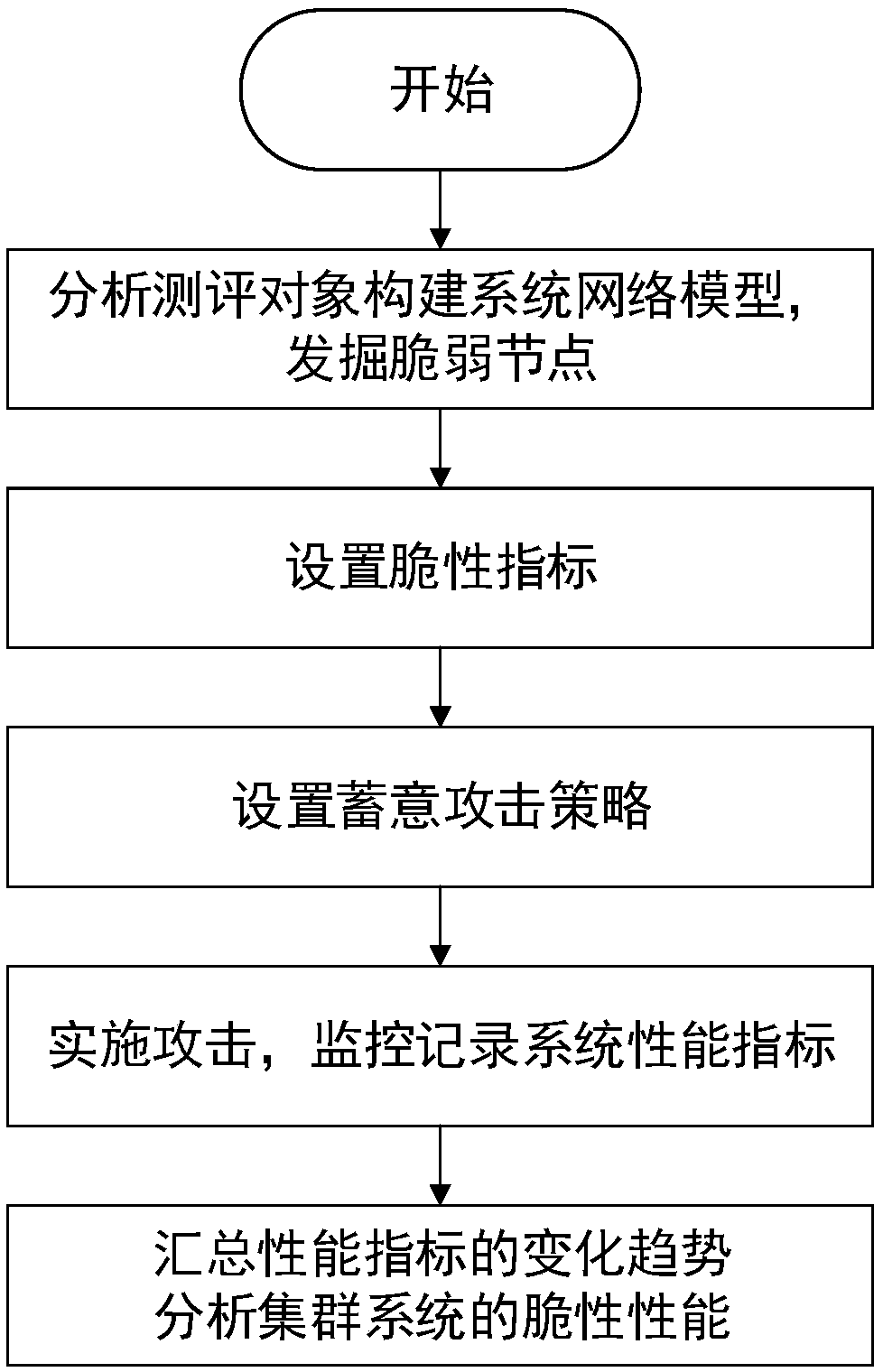
Brittleness evaluation method for cluster system based on complex network
ActiveCN108768745AAddressing VulnerabilitySolve the problem that cannot be analyzed quantitatively wellData switching networksComplex networkNetwork model
The invention provides a brittleness evaluation method for a cluster system based on a complex network. The method mainly includes the following steps: step A, analyzing an evaluation object to builda system network model, and exploring vulnerable nodes; step B, setting a brittleness index; step C, setting an intentional attack strategy; step D, implementing attacks, and monitoring and recordingsystem performance indexes; and step E, summarizing the variation trend of the performance indexes, and analyzing the brittleness performance of cluster system. According to the scheme of the invention, on the premise of considering various complex characteristics of the cluster system, the evaluation method provided by the invention is adopted to search the vulnerable nodes for the cluster system, and then the intentional attacks are carried out for the vulnerable nodes, the brittleness index provided by the invention is adopted to perform brittleness quantitative analysis and brittleness trend analysis on the attacked cluster system, so that system designers can be facilitated to discover the vulnerable nodes of the system and can perform optimization and improvement for the vulnerable nodes and a network structure according to an evaluation result, and thus the brittleness performance of the system can be improved.
Owner:BEIHANG UNIV
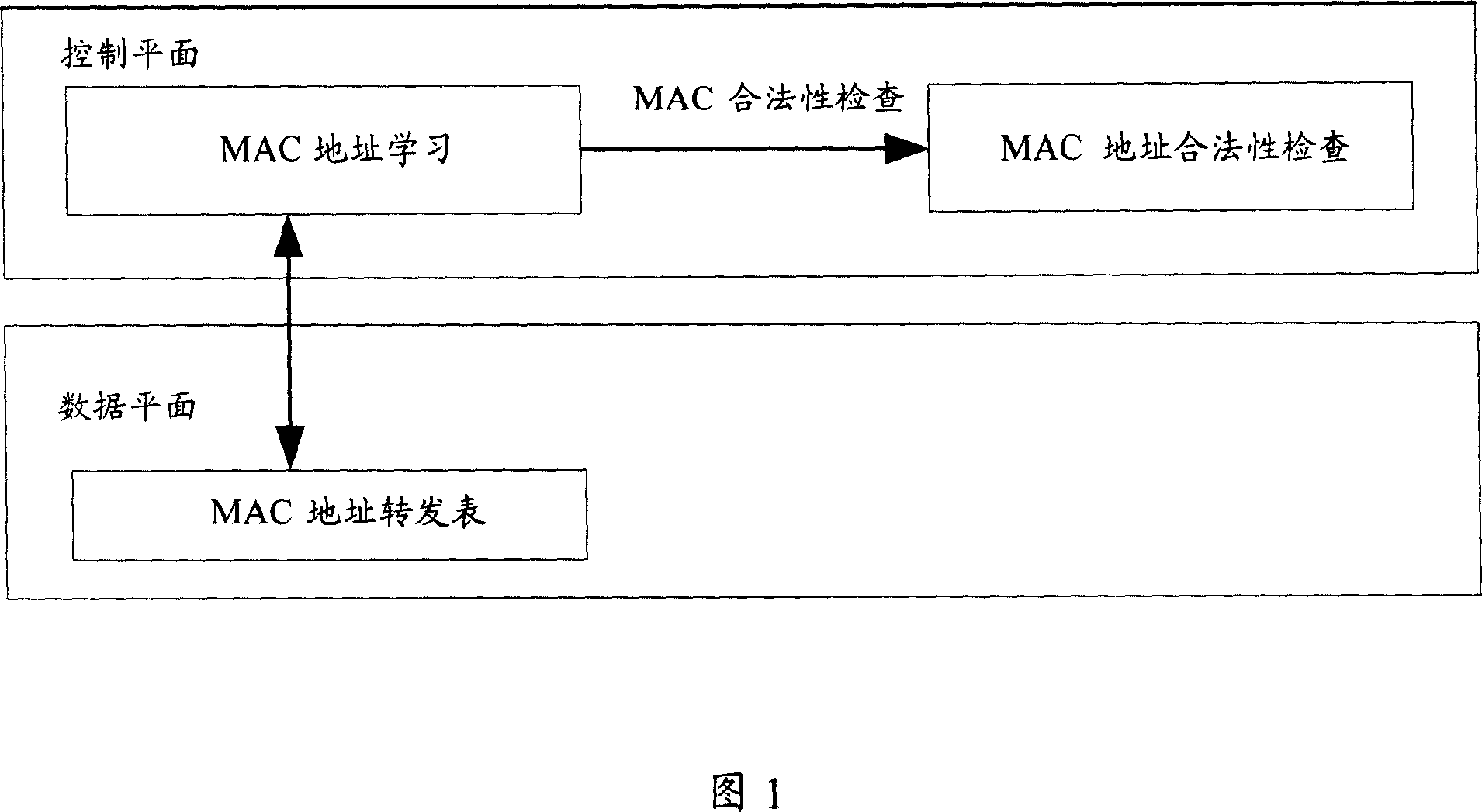
Method for preventing disturbance of medium accessing control address table on access equipment
ActiveCN101098291AEnsure correct forwardingEliminate MAC address table disturbanceNetworks interconnectionMedia access controlRouting control plane
The invention discloses a method for avoiding interference of medium access control address list on access device, comprising that an exchange chip in data plane closes the MAC address study at network port, a MAC address study module exchanges the MAC address study function of the exchange chip, the MAC address study module and a MAC address legality check module filter illegal MAC address study to build a legal MAC address list, a control plane sets studied a new legal MAC address list into the exchange chip, and starts an aging process, when aged, deletes the MAC address of the exchange chip. Since the exchange chip uses static MAC address, the invention converts the dangerous MAC address study function of exchange chip into safe MAC address study of control plane, to avoid MAC address list interference caused by source MAC attack.
Owner:ZTE CORP
Identification method of vulnerable nodes of distribution network
PendingCN107871216AEffectively identify vulnerable nodesFind vulnerable nodesResourcesRisk theoryRisk evaluation
The invention discloses an identification method of vulnerable nodes of a distribution network. The method includes the following steps: (1) establishing vulnerability evaluation indexes based on complex network theory, and a risk evaluation index based on risk theory; (2) using a hierarchical analysis method to carry out weighted summation on the vulnerability evaluation indexes of the distribution network and comprehensively analyze the vulnerability indexes and the risk index, and establishing a comprehensive estimation index of node vulnerability of the distribution network; (3) acquiringstructure data of the distribution network and a power flow calculation result, and calculating the comprehensive estimation index of the distribution network; and (4) outputting the relatively vulnerable nodes of the distribution network. The comprehensive estimation index has the following advantages that: the complex network theory and the risk theory are adopted, a structure of the distribution network is taken into account, fault risks are taken into account, and the identification problem of the vulnerable nodes in the distribution network is comprehensively solved.
Owner:HUIZHOU POWER SUPPLY BUREAU OF GUANGDONG POWER GRID CO LTD
Economic dispatching method with robust collaborative consistency
ActiveCN105429185AEmbodies the characteristics of decentralized optimizationAddress overdependenceSingle network parallel feeding arrangementsComputer scienceGenerative power
The invention discloses an economic dispatching method with robust collaborative consistency. The method comprises the following specific steps: determining a laplacian matrix L; obtaining a total power P<D>, and initializing power generating powers of various units and calculating power deviations; correcting the laplacian matrix L in real time; calculating a consistency gain function c(k); updating a virtual consistency variable of a leader and a follower; calculating real consistency variables of various units; solving the power generating powers P<Gi> of the units; determining power deviations [delta]P and judging whether a power error margin P<error> is met or not; and if so, ending iteration and outputting an optimization result. According to the economic dispatching method, the problem that a traditional CCA algorithm excessively depends on an ideal communication network is solved; the economic dispatching method has robustness on transmission delay and noise interference; the vulnerability that a traditional CCA algorithm cuts off the units from a key position of a communication topology is solved; and plug and play characteristics of the units are considered.
Owner:SOUTH CHINA UNIV OF TECH
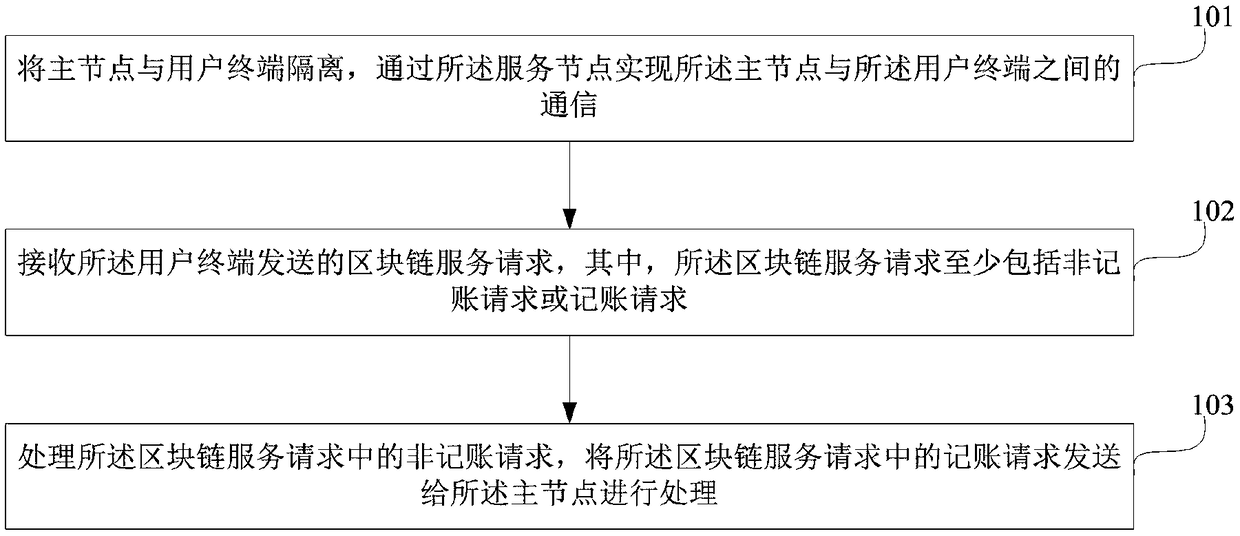
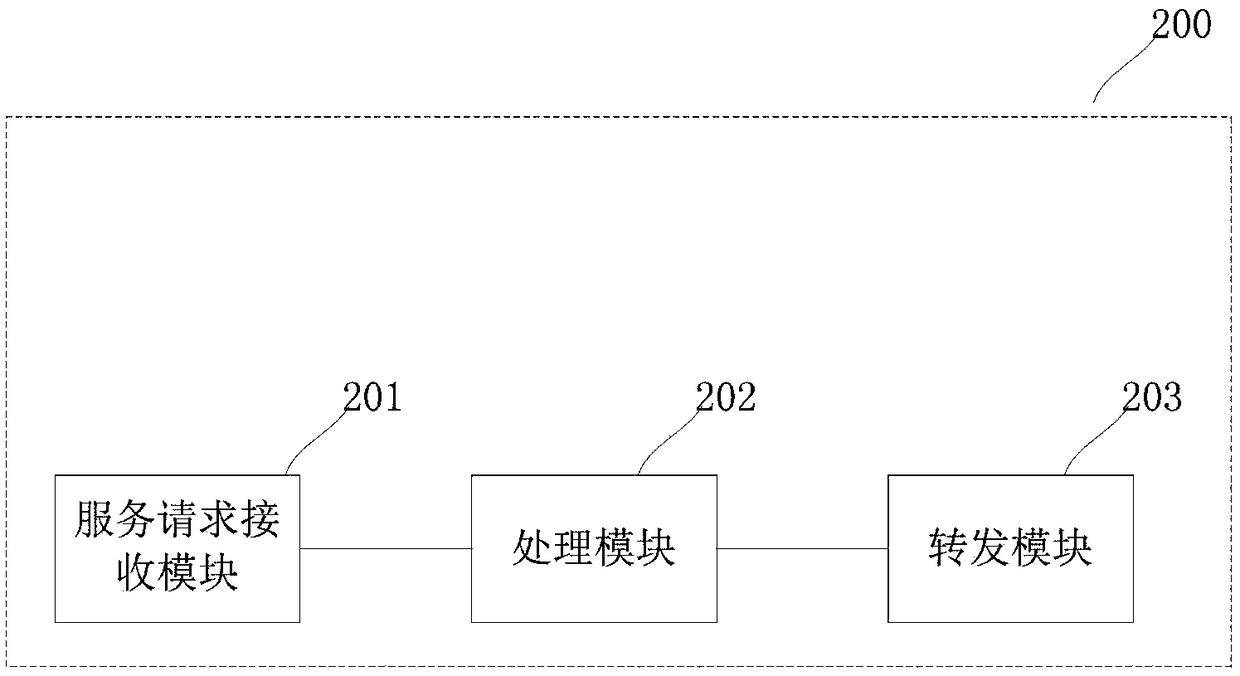
Blockchain secure communication method and system, and service node
ActiveCN109451036AAddressing VulnerabilityHigh speedFinanceTransmissionCommunications securityBlockchain
The invention relates to the technical field of blockchain security, and in particular to a blockchain secure communication method and system, and a service node. The method comprises the following steps: isolating a master node from a user terminal; receiving a blockchain service request sent by the user terminal, wherein the blockchain service request at least comprises a non-accounting requestor an accounting request; processing the non-accounting request in the blockchain service request, and sending the accounting request in the blockchain service request to the master node for processing. By adoption of the method and system, and the service node provided by the embodiment of the invention, the problem that the master node in a blockchain network is easily attacked can be solved, and the communication security of the master node in the network is improved.
Owner:北京创世智链信息技术研究院
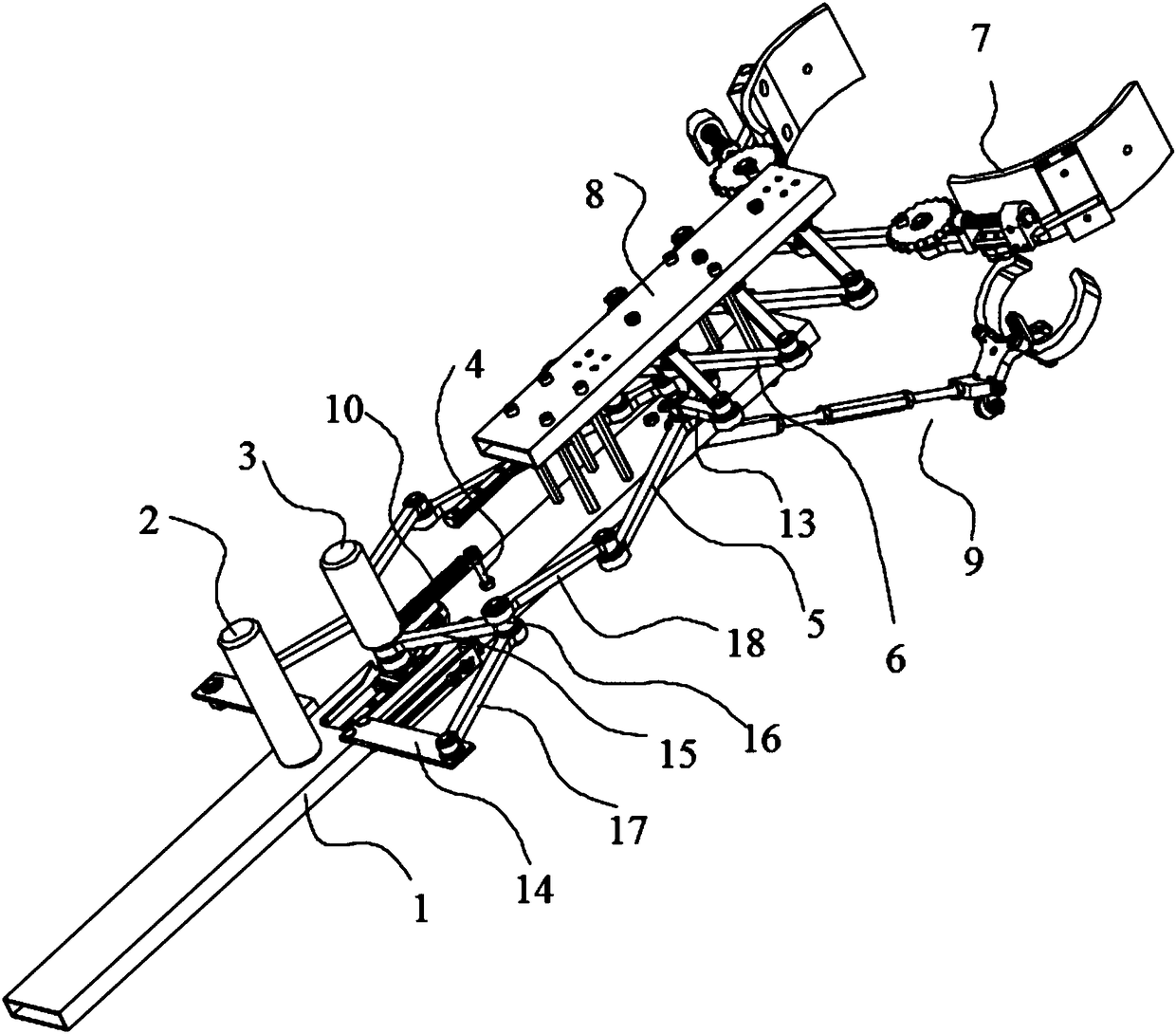
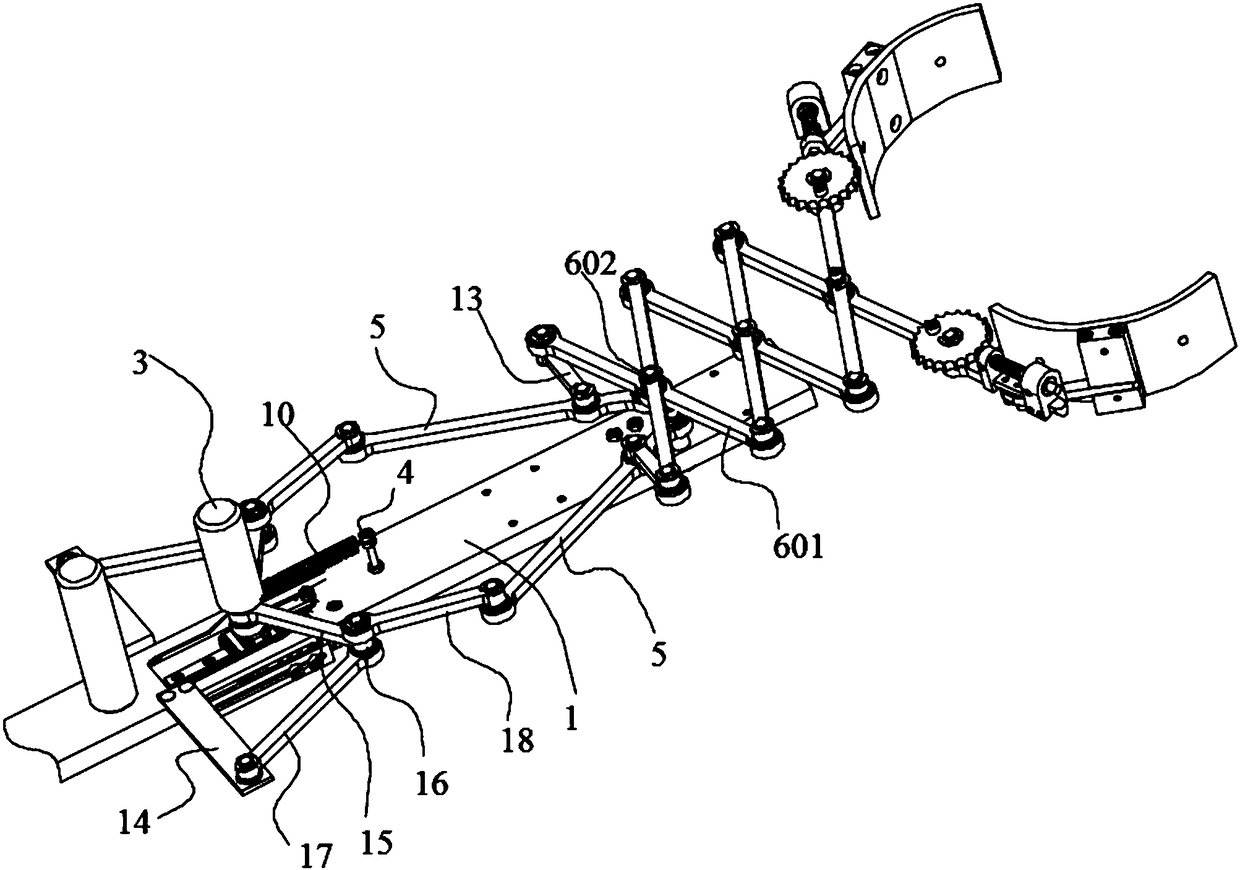
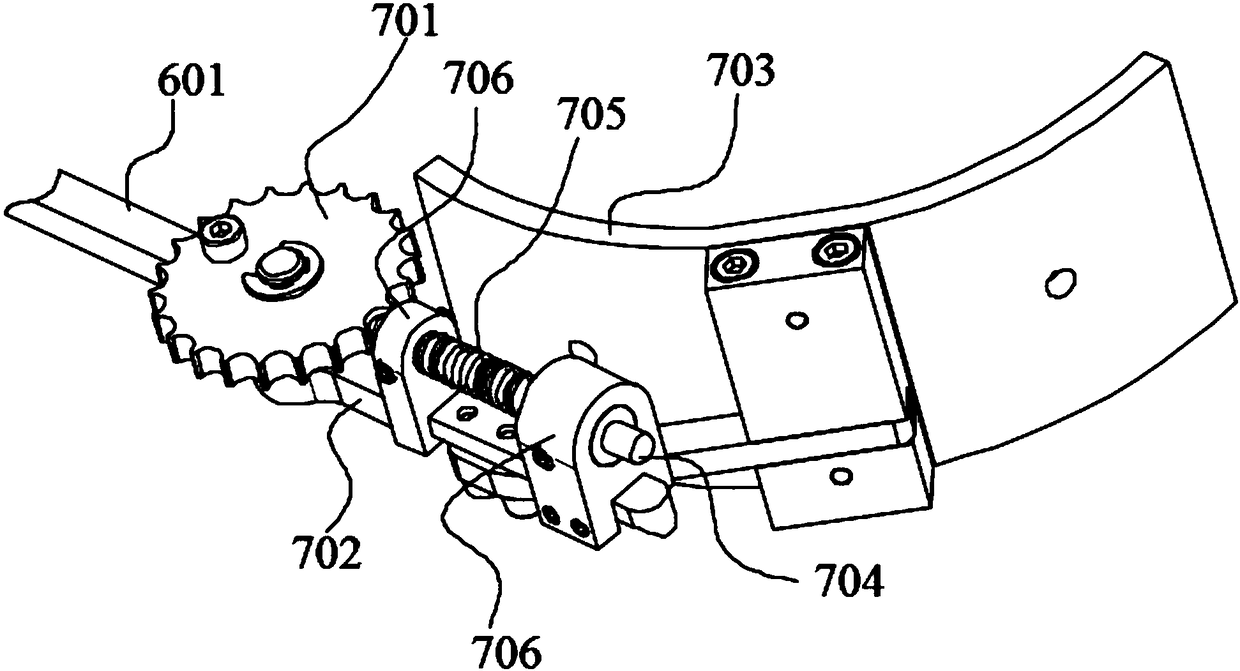
Wearable scissor-fork type pineapple one-step picking auxiliary arm
The invention discloses a wearable scissor-fork type pineapple one-step picking auxiliary arm. The auxiliary arm comprises a bottom plate, a hand-held column, a hand-pulled column, two scissor-fork oscillating bars, a scissor-fork mechanism and two mechanical claws, wherein the hand-pulled column is arranged on the bottom plate through a guiding rail-sliding block structure, one end of each scissor-fork oscillating bar is arranged on the bottom plate through a pin shaft, the other end of the corresponding scissor-fork oscillating bar is connected to the hand-pulled column through a link mechanism, a first-stage intermediate pin shaft of the scissor-fork mechanism is fixedly arranged on the bottom plate, end portions of first-stage two scissor-fork rods of the scissor-fork mechanism are respectively hinged with the middle portions of the scissor-fork oscillating bars through first connecting rods, and the mechanical claws are respectively fixedly arranged at the last-stage end portion of the scissor-fork mechanism; when a user pulls the hand-pulled column backward, the hand-pulled column drives the scissor-fork oscillating bars to rotate around end portion pin shafts of the scissor-fork oscillating bars inward through the link mechanism, the rotation of the scissor-fork oscillating bars drives the scissor-fork mechanism to elongate through the first connecting rods and simultaneously drives the mechanical claws to stretch forward and clamp the pineapple. The wearable scissor-fork type pineapple one-step picking auxiliary arm has the advantages that the structure is simple, manual pineapple picking can be assisted, and the labor intensity is reduced.
Owner:WUHAN UNIV OF TECH
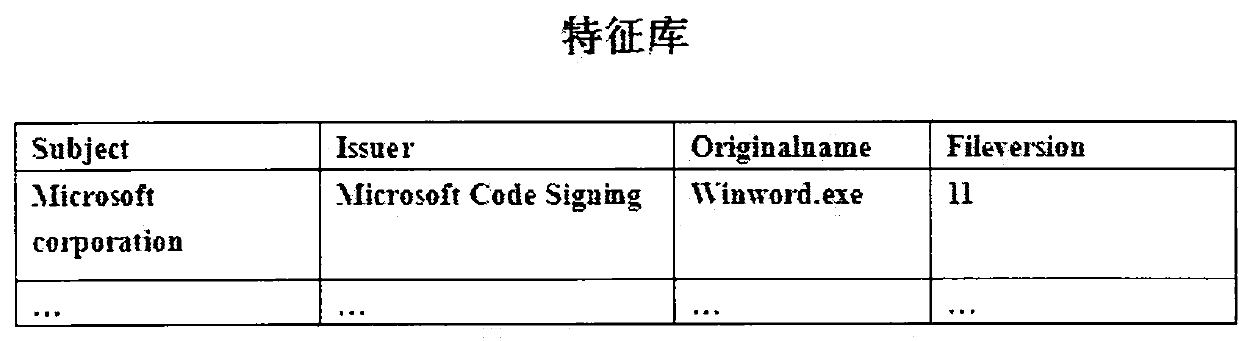
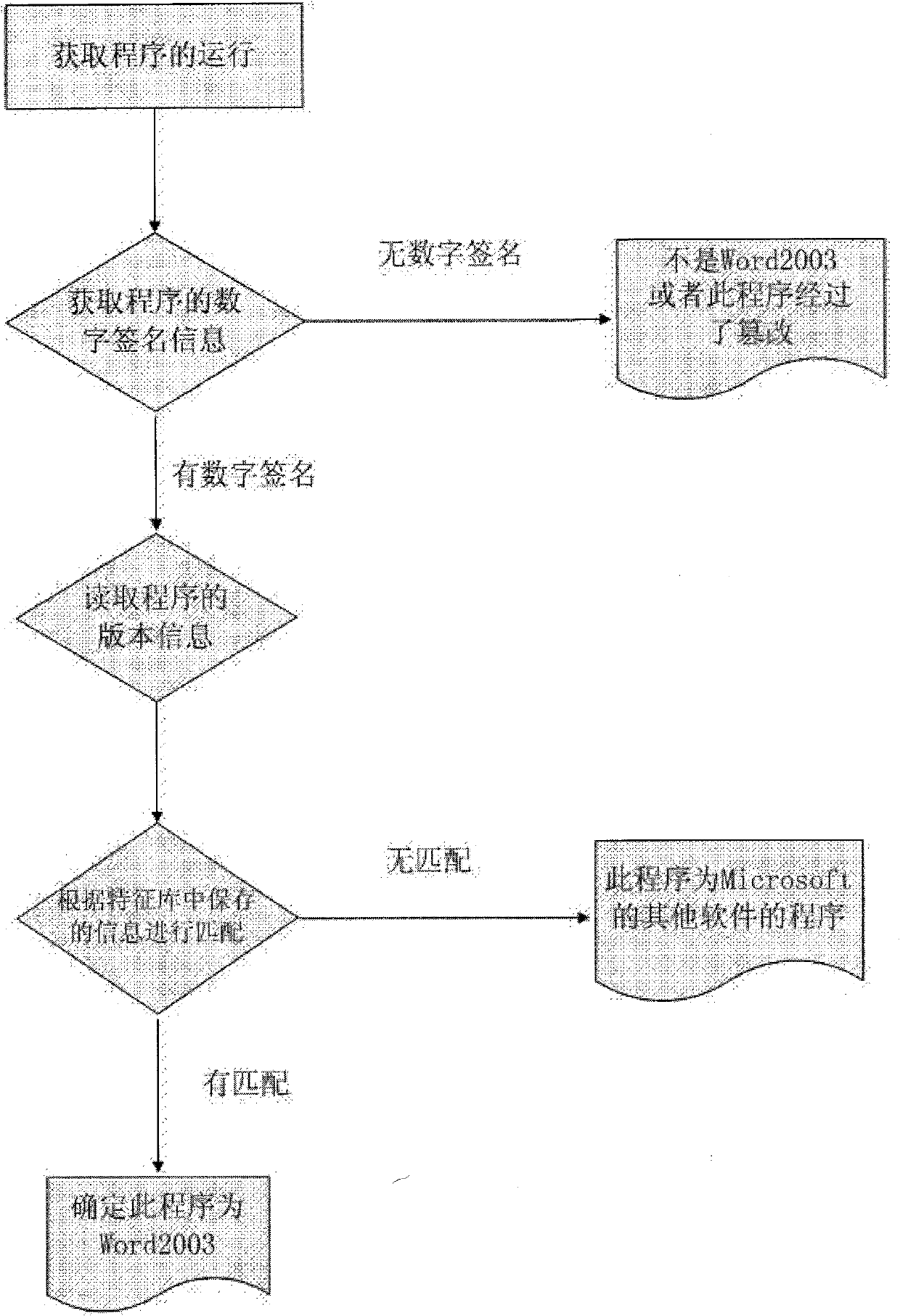
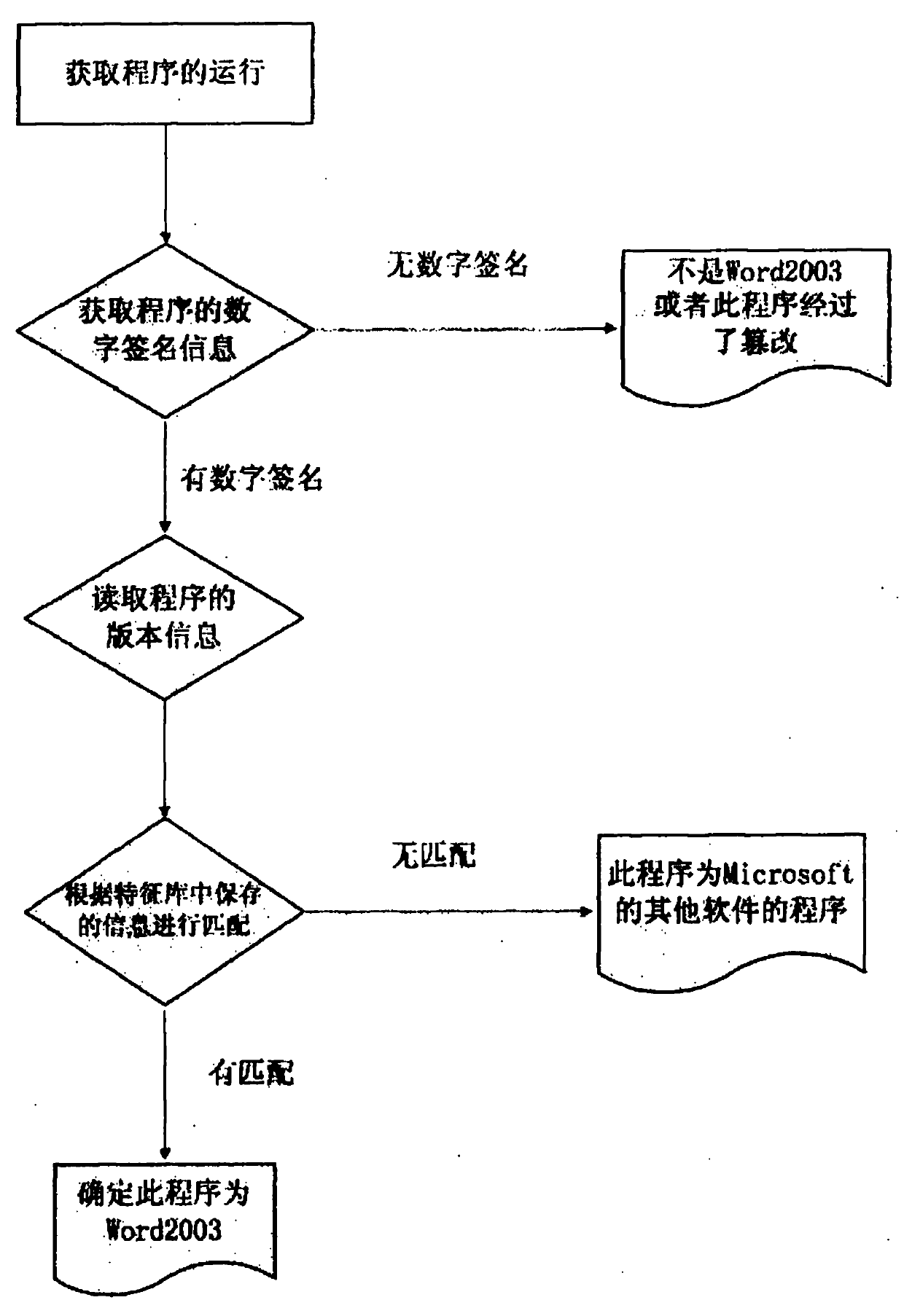
Method for using digital signature to detect falsification possibility of software
InactiveCN102024120AAddressing VulnerabilityAddress maintenance complexitiesPlatform integrity maintainancePlaintextDigital signature
The invention relates to a method for detecting whether an application program is tampered or not. The principle that a digital signature can not be modified is utilized, and whether a program is tampered or not can be further determined by reading digital signature information contained in software and comparing the read digital signature information with the information which is saved in a feature library in advance. The method is mainly used for the field of computer information security. By adopting the method, the defect that a user maliciously forges a program the name and version information of which are same with the those of a controlled program, and then further utilizes the forged program to outtrick the protection of transparent encryption software so as to directly read a plaintext and further export the plaintext can be effectively prevented. Simultaneously, by adopting the method, the version number of the program can be firstly judged so as to make different settings according to different versions.
Owner:无锡安腾软件开发有限公司
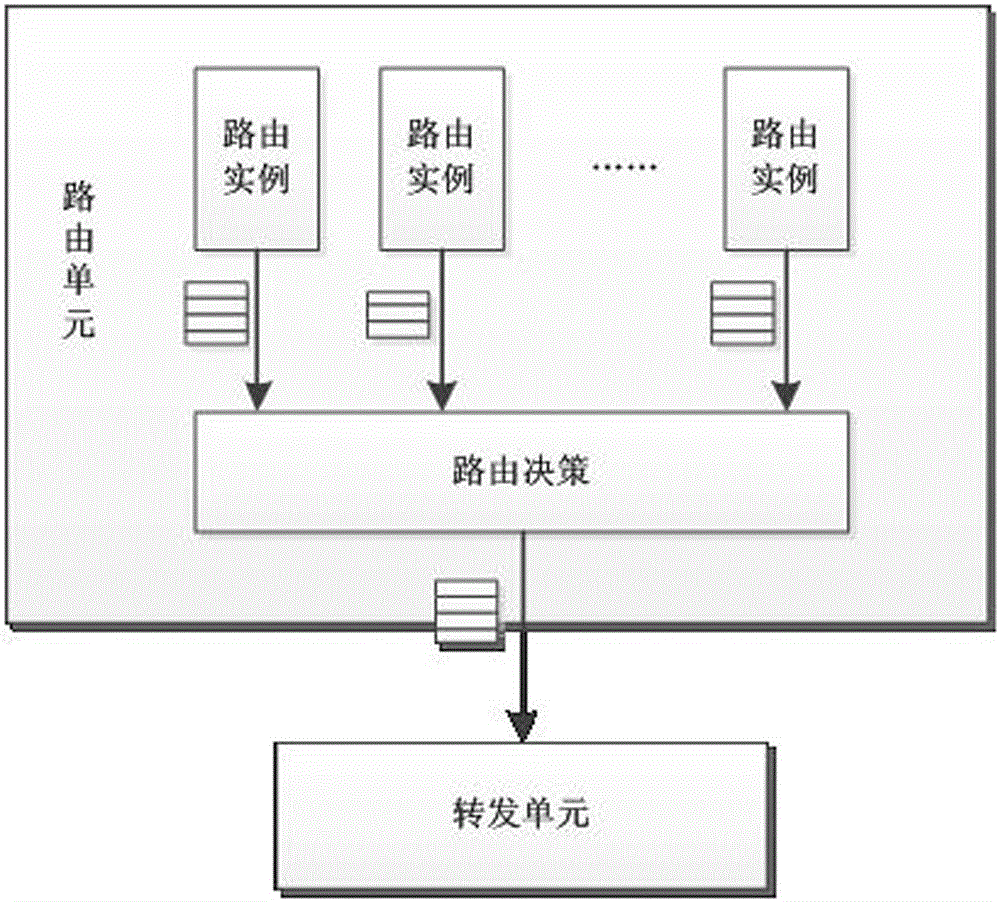
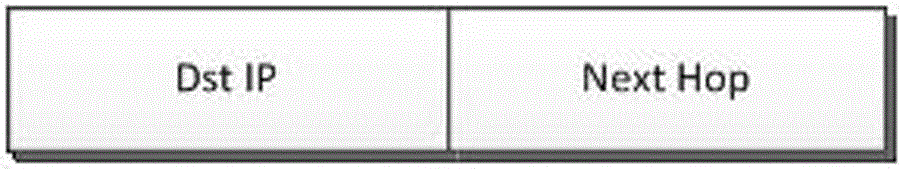
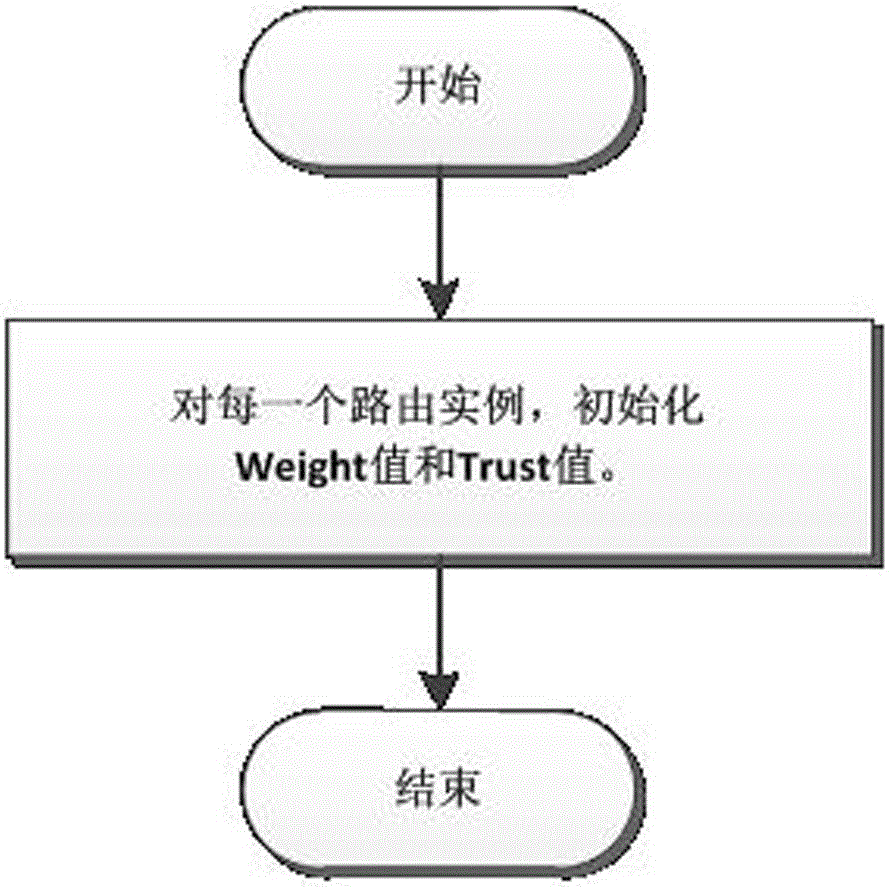
Mimicry routing decision method of multi-instance routing unit
ActiveCN105072036ANo static properties changedAvoid safety hazardsData switching networksRouting decisionRouting table
The invention discloses a mimicry routing decision method of a multi-instance routing unit, and overcomes the problem that a safety demand of a network space is very rigorous in the prior art. The mimicry routing decision method comprises the a step (1) that a routing decision module maintains routing table items, which are issued by routing instances, for the routing instances, a step (2) that, for each routing table item, credibility of each routing table item is calculated according to the number of the same table items and credibility of the routing instances to which the same table items belong, a step (3) that the routing table item having the same destination address and highest credibility is taken as a final routing table item obtained through a decision, and the final routing table item is converted into a forwarding table item and then is issued to a forwarding unit, a step (4) for operation which is used to delete the routing table items and which is issued by the routing instances, the routing decision module executes corresponding deleting operation firstly, and a step (5) that, if a problem occurs in a certain path of routing instance, the step (5) is turned to the step (4), and all the routing table items issued by the routing instance are correspondingly deleted. The technology has the high ability to resist a network risk.
Owner:SHANGHAI REDNEURONS +1
Catalyst for secondary reversible air electrode and preparation method thereof
ActiveCN102658185AHigh purityEvenly dispersedPhysical/chemical process catalystsCell electrodesPtru catalystElectrical battery
The invention relates to a catalyst for a secondary reversible air electrode and a preparation method thereof, in particular to a load type perovskite type catalyst for the secondary reversible air electrode. The chemical formula of the catalyst is LaxCa (1-x) CoO3 / TiC or LaxCa (1-x) CoO3 / TiN, wherein 0.5<=x<=0.7, and the loading quantity of LaxCa (1-x) CoO3 is 5wt%-80wt%. The catalyst is capable of resolving the problem that structure of a carbon material is easy to damage when the carbon material serves as a carrier, simultaneously improves circulation performance of a battery, is simple in preparation method, adopts a direct heating method without adding other materials, is high in purity, is evenly dispersed on the carrier, and is capable of well improving catalyst effect and suitable for industrial production.
Owner:紫石能源有限公司
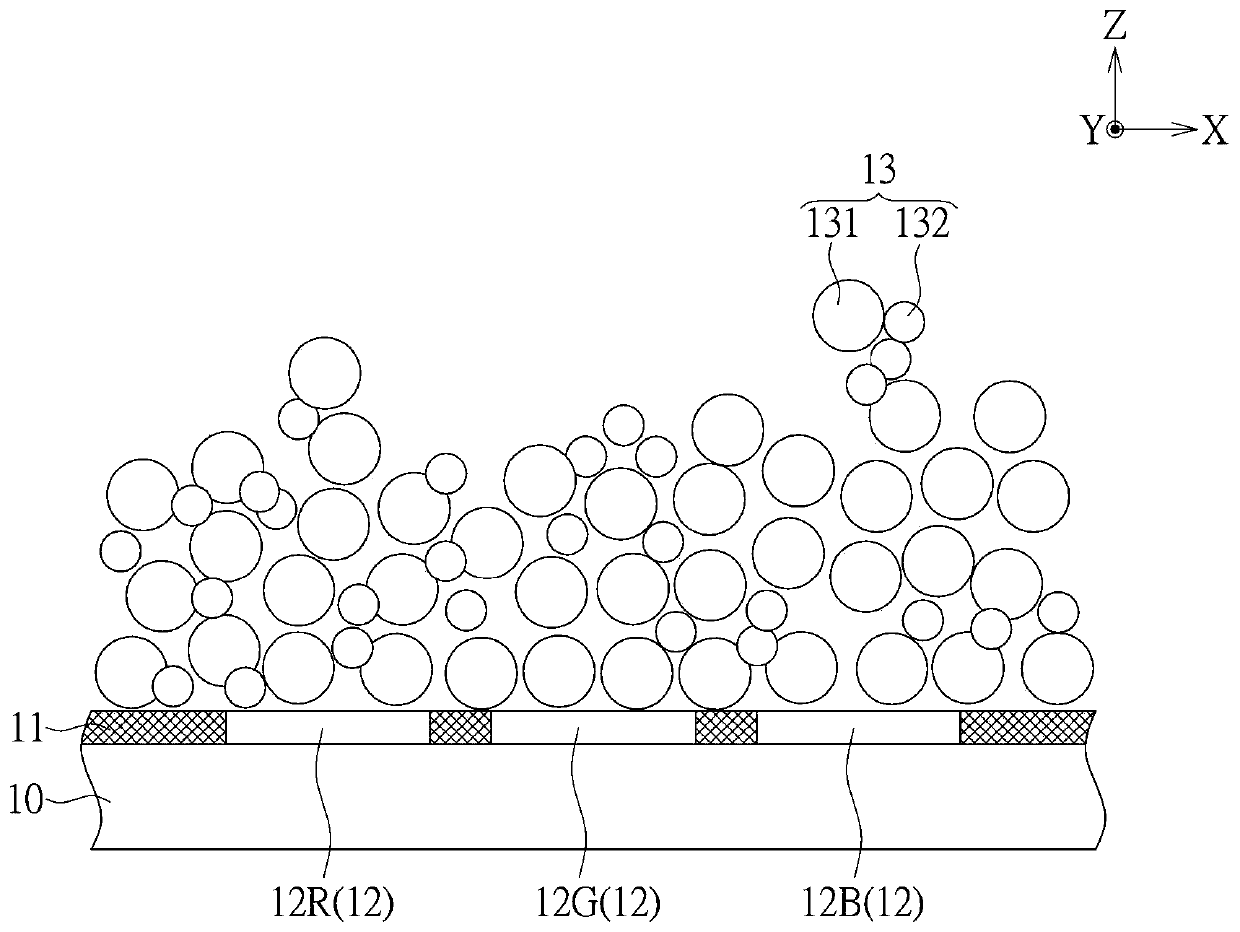
Display panel and manufacturing method thereof
ActiveCN109830186AAddressing VulnerabilitySolve the defectsSolid-state devicesIdentification meansProtection layerComputer science
The invention discloses a display panel and a manufacturing method thereof. The display panel comprises a substrate, a plurality of pixel units, a color conversion layer, a protection layer and a shading layer. The color conversion layer is on the substrate. The protection layer covers the color conversion layer and comprises a plurality of patterned protection units, wherein each patterned protection unit corresponds to one pixel unit. The light shielding layer is located in a gap formed between the patterned protection units.
Owner:AU OPTRONICS CORP
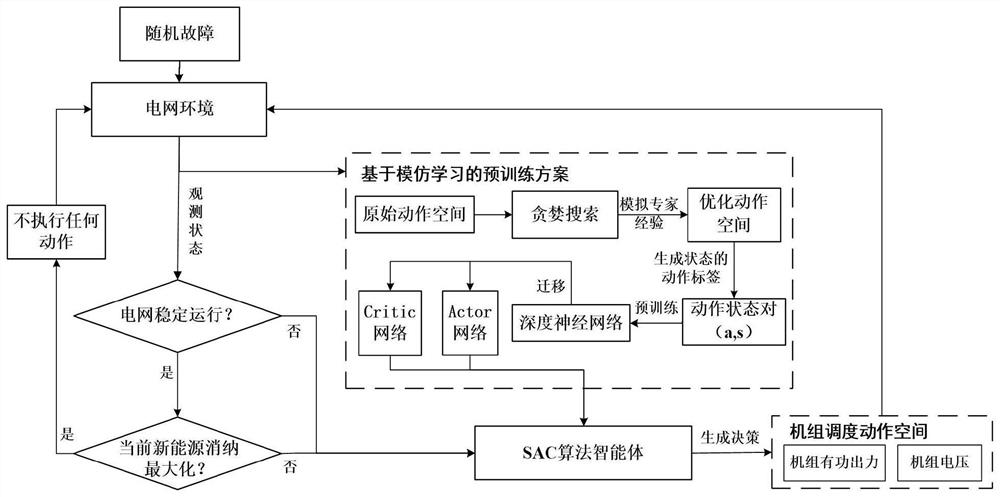
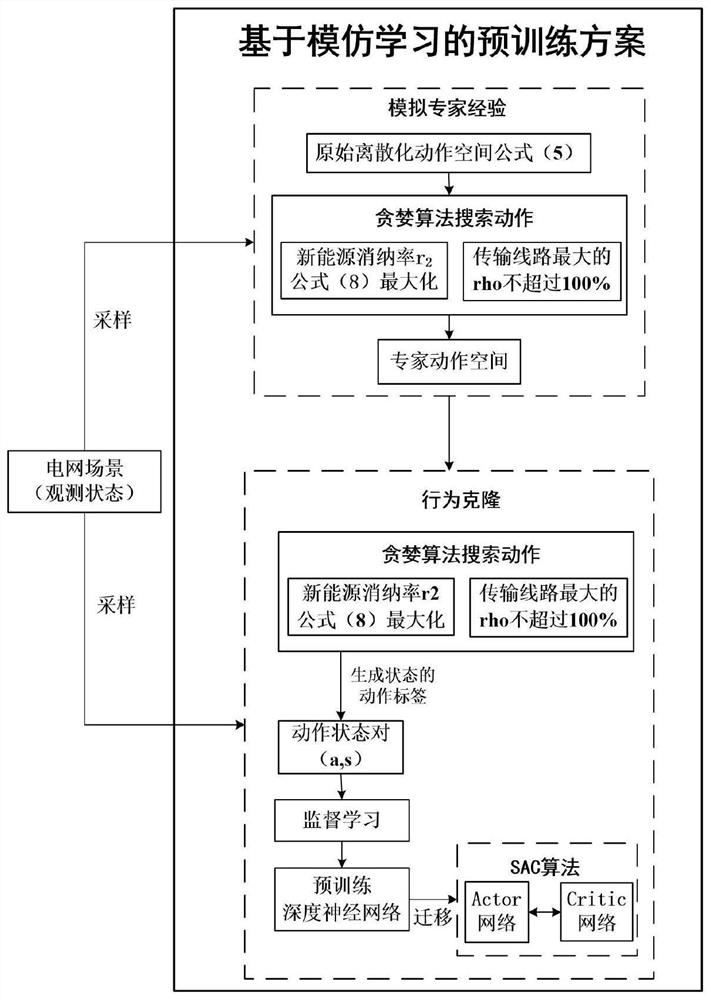
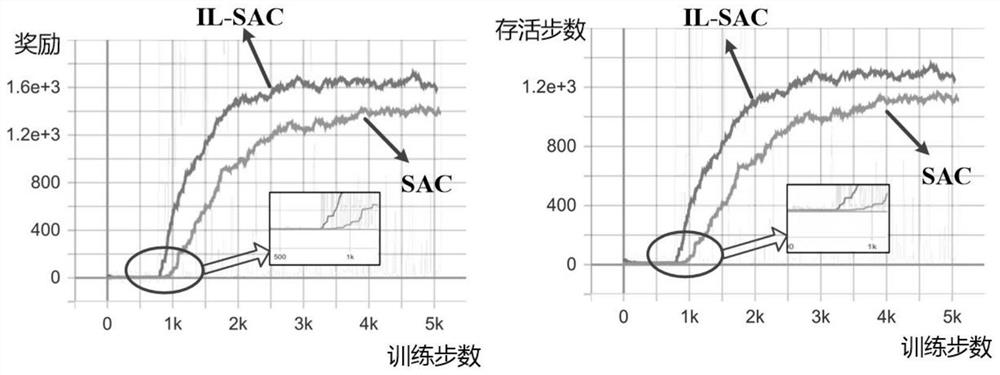
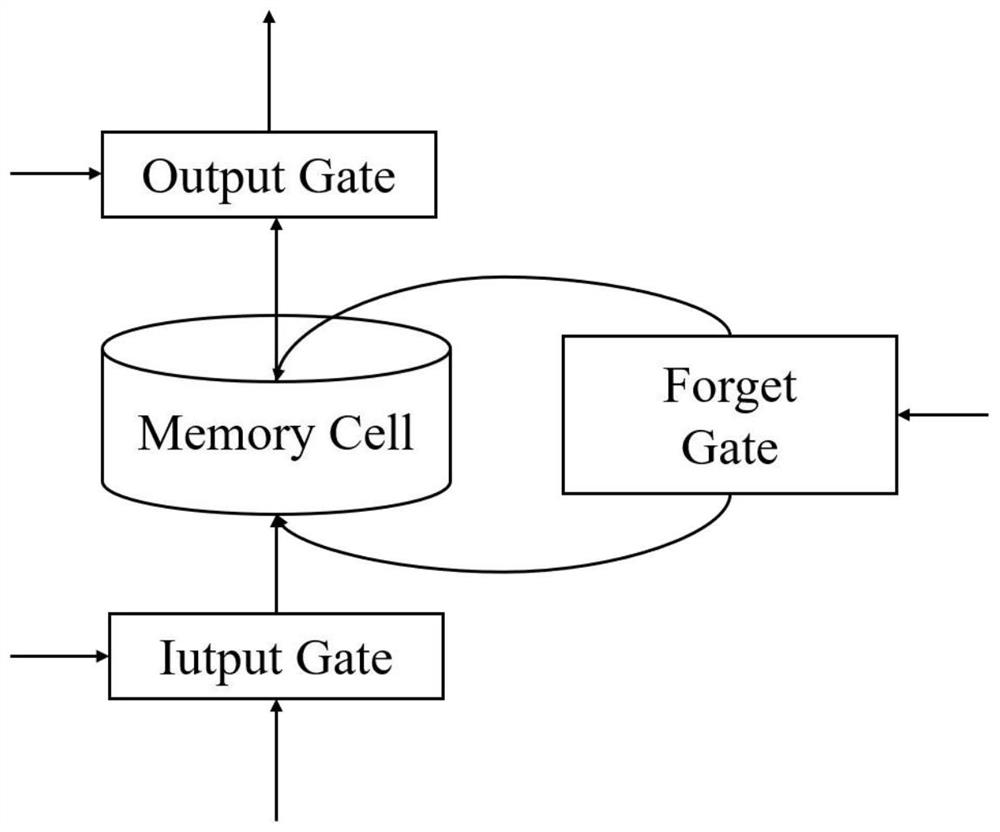
Power grid real-time adaptive decision-making method based on deep reinforcement learning
PendingCN114217524AGuarantee maximum consumptionInnovativeSystems intergating technologiesNeural learning methodsElectric power systemPower grid
The invention relates to a power grid real-time adaptive decision-making method based on deep reinforcement learning. The method comprises the following steps: step 1, modeling a novel power system unit adaptive scheduling problem as a Markov decision-making process; 2, researching the basic principle of an SAC algorithm, and solving a strategy enabling the accumulated reward value of the MDP model in the step 1 to be maximum; step 3, designing a neural network pre-training scheme based on behavior cloning in the IL, simulating expert experience, optimizing an original action space, proposing an IL-SAC algorithm, training a corresponding power grid optimization scheduling agent based on the IL-SAC algorithm and 105 real power grid scene data, and performing optimization scheduling on the power grid. During testing, the intelligent agent can output a real-time decision scheme in response to different power grid scene data, and intelligent regulation and control of a novel power grid system are realized. The power grid dispatching strategy can be output in real time.
Owner:ELECTRIC POWER SCI & RES INST OF STATE GRID TIANJIN ELECTRIC POWER CO +2
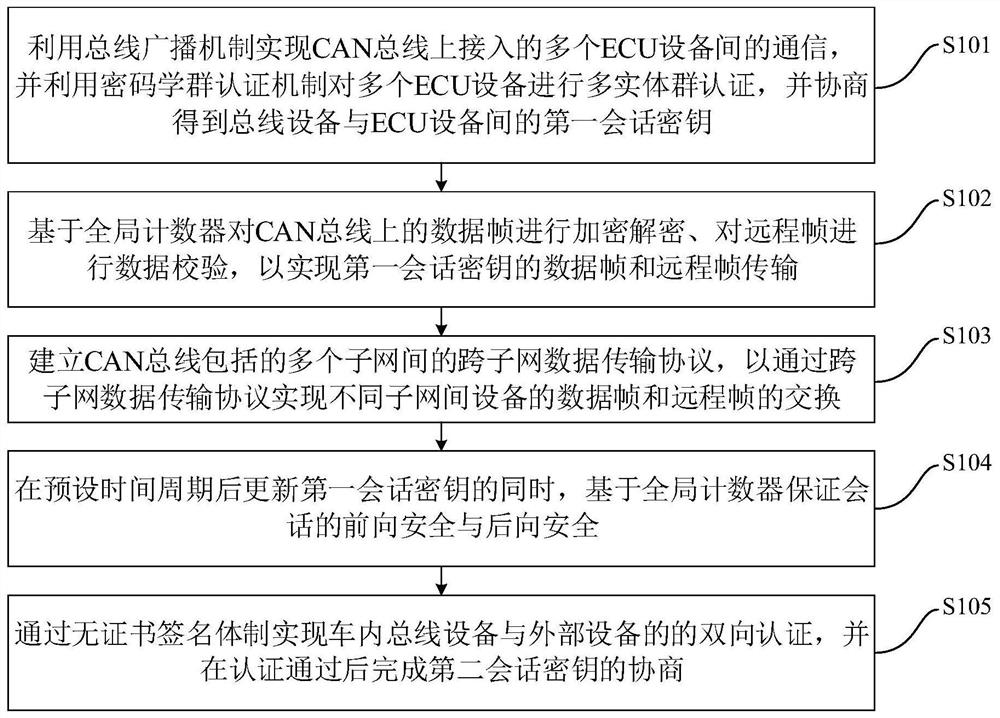
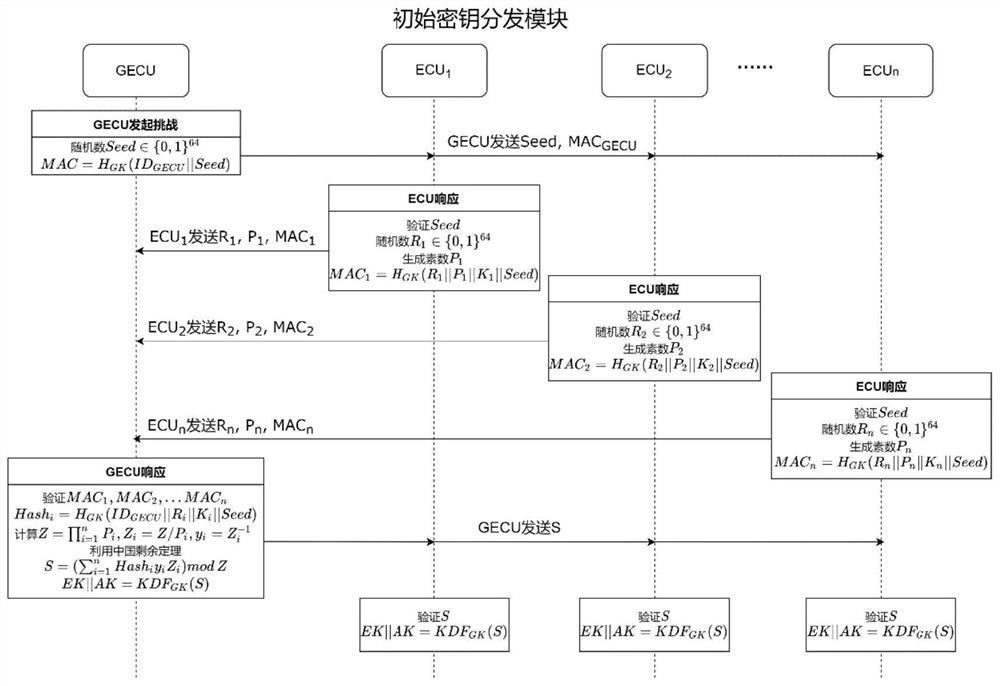
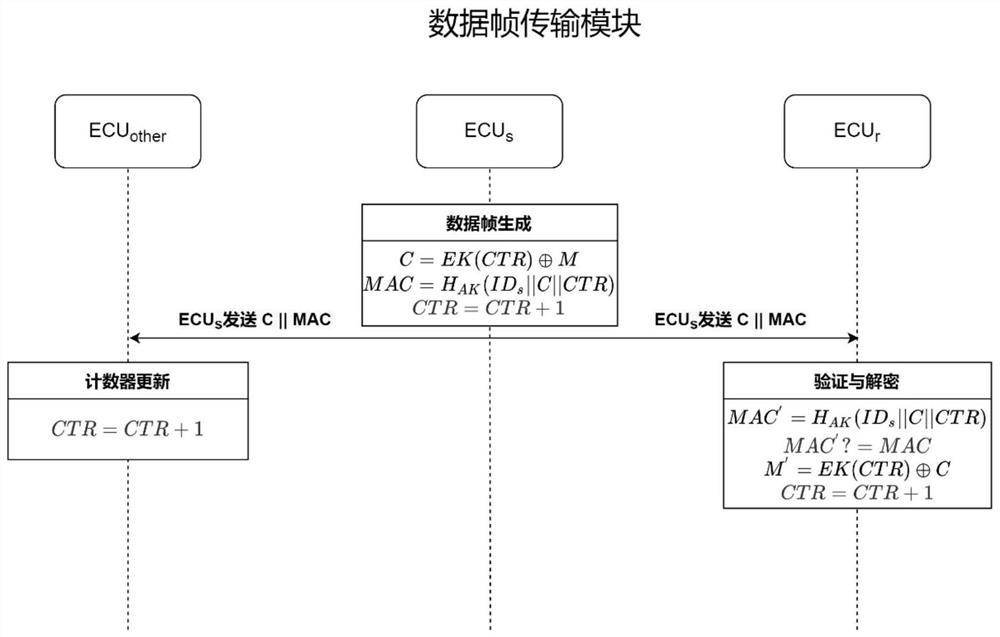
Extensible CAN bus safety communication method and device for large-scale in-vehicle network
ActiveCN113132098AReduce overheadAddressing VulnerabilityKey distribution for secure communicationUser identity/authority verificationArea networkConfidentiality
The invention discloses an extensible CAN (Controller Area Network) bus safety communication method and device for a large-scale in-vehicle network, and the method covers the safety scenes of initial key distribution, key updating, data confidentiality and integrity protection, external equipment access and the like in a bus. A broadcasting mechanism and a cryptographic group authentication mechanism of the bus are properly utilized, so that the communication process in the initial key distribution stage is effectively simplified, the lightweight design of key initialization is realized, and good expandability is achieved for the increasing number of equipment on the CAN bus; the vulnerability of a data encryption communication face to a delay attack is solved by using a global counter; a cross-subnet data transmission module is introduced to solve the defect that the encrypted message cannot be transmitted in a cross-network manner; in addition, an authentication process for external equipment access is designed based on a certificateless signature mechanism without bilinear pairing, dependence on a public key infrastructure mechanism is eliminated, communication overhead is reduced, complex bilinear pairing operation is avoided, and the real-time requirement is met.
Owner:BEIHANG UNIV
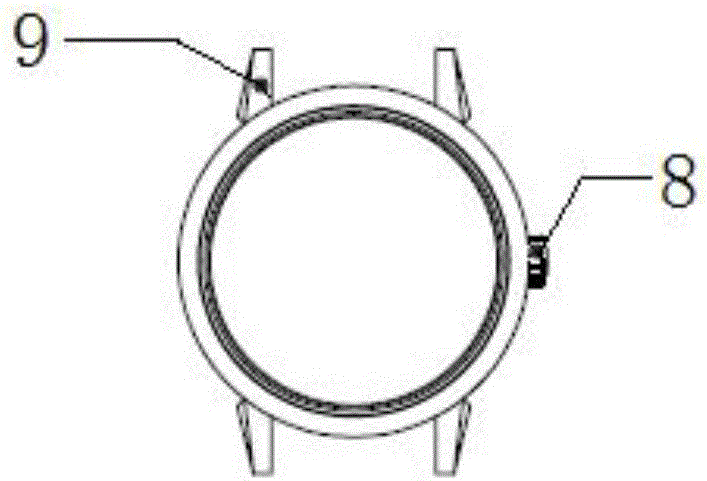
Pure-gold watchcase and manufacturing method thereof, and dial plate comprising same
The invention relates to a pure-gold watchcase manufacturing method, comprising raw material melting, rough blank forming, stamping treatment and cutting treatment. The invention also relates to a pure-gold watchcase obtained by the above method, and a dial plate comprising the pure-gold watchcase. The dial plate also comprises an inner container, a movement, a graduated disk, a watch glass, a watch crown and an ear part. The inner container comprises an inner container body and a fixed part. The pure-gold watchcase is wrapped at the outer wall of the inner container. The movement is arranged inside the inner container. The graduated disk is arranged on the top surface of the movement in a covering manner. The watch glass is disposed at an opening of the inner container in a covering manner. With the gold content higher than nine hundred and ninety per one thousand, the pure-gold watchcase achieves good machining performance, allows surface treatment, has high strength and hardness and is adapted to normal knock and collision when used. The rejection rate in the pure-gold watchcase manufacturing process is low, and the production efficiency is high. The dial plate comprising the pure-gold watchcase has good waterproofness, and the strength of an outer shell of the dial plate is further enhanced, so the service lifetime of the dial plate is prolonged.
Owner:JUNSON SHENZHEN CHUANJINDAIYIN TECH CO LTD
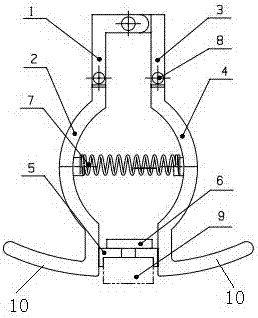
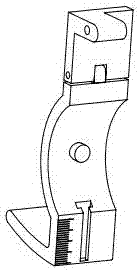
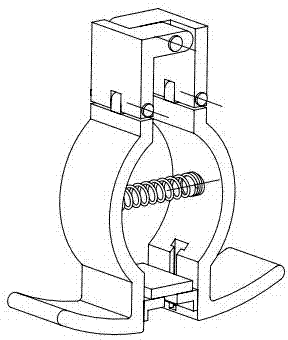
Adjustable metallographic sample clamp
An adjustable metallographic sample clamp comprises an upper left clamping board (1), a lower left clamping board (2), an upper right clamping board (3) and a lower right clamping board (4); the lower left clamping board (2) and the upper left clamping board (1) are connected through a rivet (8); the lower right clamping board (4) and the upper right clamping board (3) are connected through a rivet (8); the upper left clamping board (1) and the upper right clamping board (3) are connected through a rivet (8); a tension spring (7) is arranged between the lower left clamping board (2) and the lower right clamping board (4); an adjusting board (5) is installed on the lower left clamping board (2) and the lower right clamping board (4) through a T-type groove and can move up and down in the T-type groove; a pressure board (6) is arranged on the adjusting board (5); and force of fingers is evenly transmitted to the adjusting board (5) through the pressure board (6), so that the surface of a sample is stressed evenly. The adjustable metallographic sample clamp is simple in structure, convenient to operate, easy to adjust, high in work efficiency and low in cost.
Owner:南通海泰科特精密材料有限公司
Control method and control system for intelligent lamp
ActiveCN110891352AAddressing VulnerabilityAvoid damageElectrical apparatusEnergy saving control techniquesInformation controlControl system
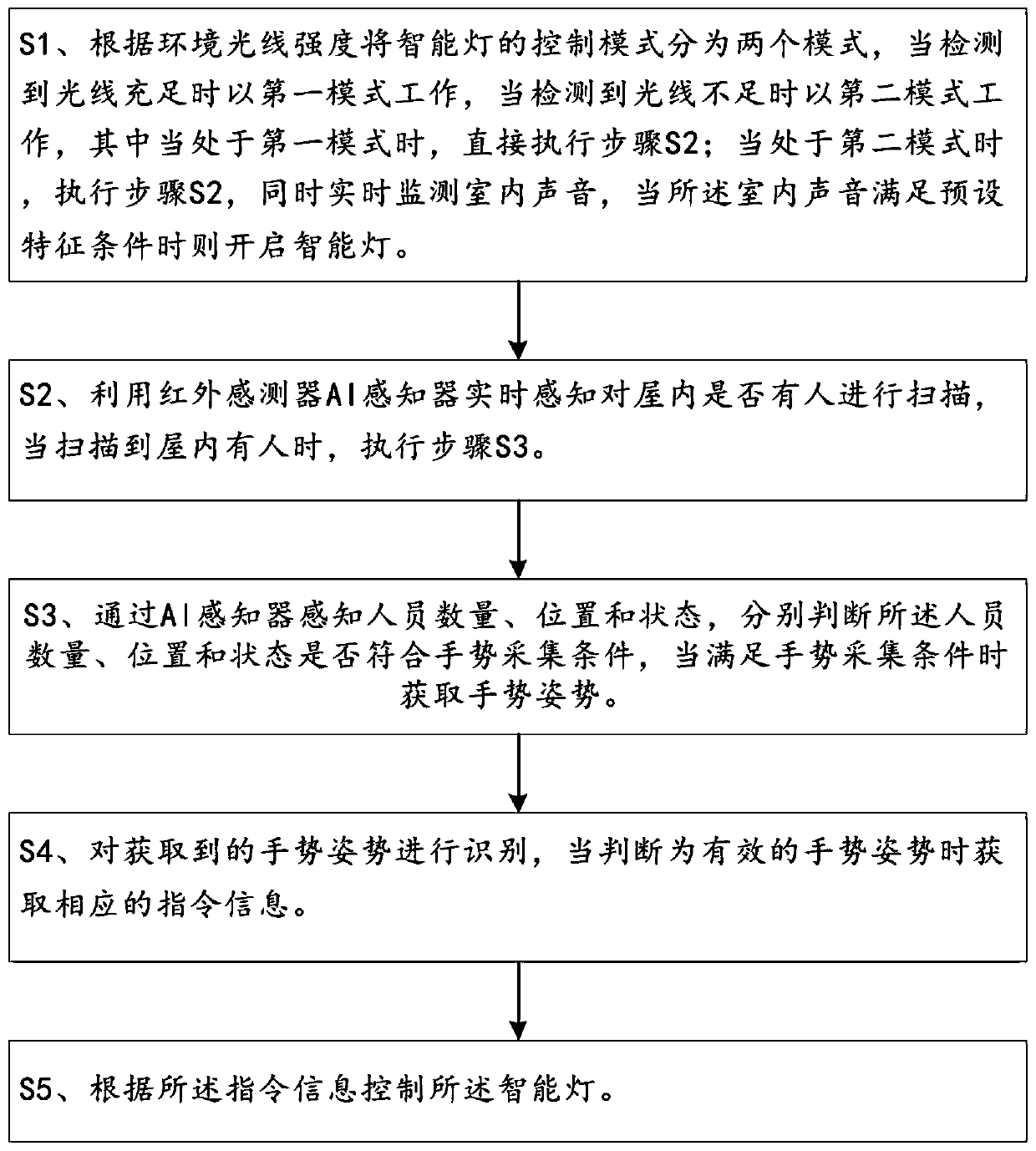
The invention provides a control method of an intelligent lamp, which comprises the following steps: S1, dividing a control mode of the intelligent lamp into two modes according to ambient light intensity, working in a first mode when sufficient light is detected, working in a second mode when insufficient light is detected, and executing a step S2 when the intelligent lamp is in the first mode; in the second mode, executing the step S2, monitoring the indoor sound in real time, and turning on the intelligent lamp when the indoor sound meets a preset characteristic condition; S2, an AI sensoris used for sensing whether a person exists in a room or not in real time, and when it is scanned that the person exists in the room, the step S3 is executed; S3, sensing the number, the positions andthe states of the persons through an AI sensor, judging whether the number, the positions and the states of the persons meet gesture collection conditions or not, and obtaining gesture postures whenthe gesture collection conditions are met; S4, recognizing the acquired gesture and posture, and acquiring corresponding instruction information when the gesture and posture are judged to be effective; and S5, controlling the intelligent lamp according to the instruction information.
Owner:GREE ELECTRIC APPLIANCES INC +1
Digital certificate processing method and device
ActiveCN108737111AAddressing VulnerabilitiesUniqueUser identity/authority verificationDomain nameComputer security
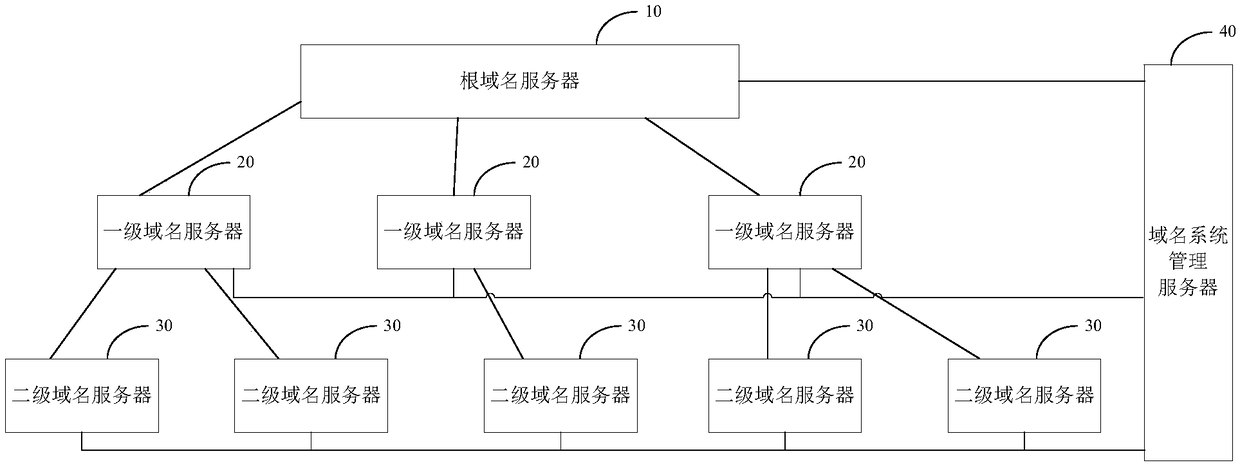
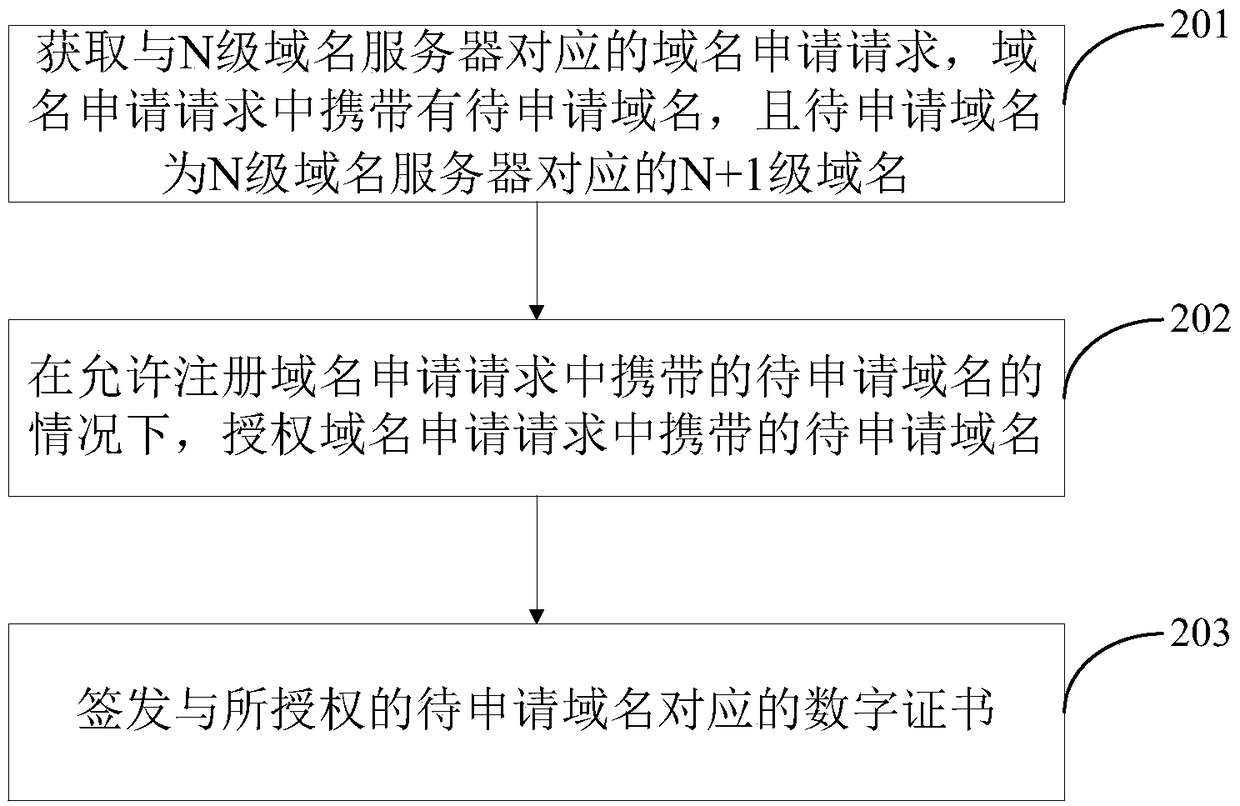
The invention provides a digital certificate processing method and device. After a domain name application request carrying a to-be-applied domain name is acquired, the to-be-applied domain name carried in the domain name application request is authorized if the to-be-applied domain name carried in the domain name application request is allowed to be registered, a digital certificate correspondingto the authorized to-be-applied domain name is singed and issued, and therefore an N-stage domain name server can be not only be a domain name administrator but also be a novel CA mechanism for signing and issuing the digital certificate corresponding to the domain name. That is to say, for any stage of domain name server, the domain name server only can sign and issue the digital certificate corresponding to the next-stage domain name administrated by the domain name server, therefore, the power that various stages of domain name servers sign and issue the digital certificates is limited, and the problem that the domain name serves are prone to be attacked due to the fact that the power is too large is solved; and in addition, the digital certificate corresponding to the domain name under each stage of domain name server is related to the root domain name server, trust anchors corresponding to the various stages of domain name servers are all root domain name digital certificates ofthe root domain name servers, and then the uniqueness of the trust anchors is achieved.
Owner:CHINA INTERNET NETWORK INFORMATION CENTER
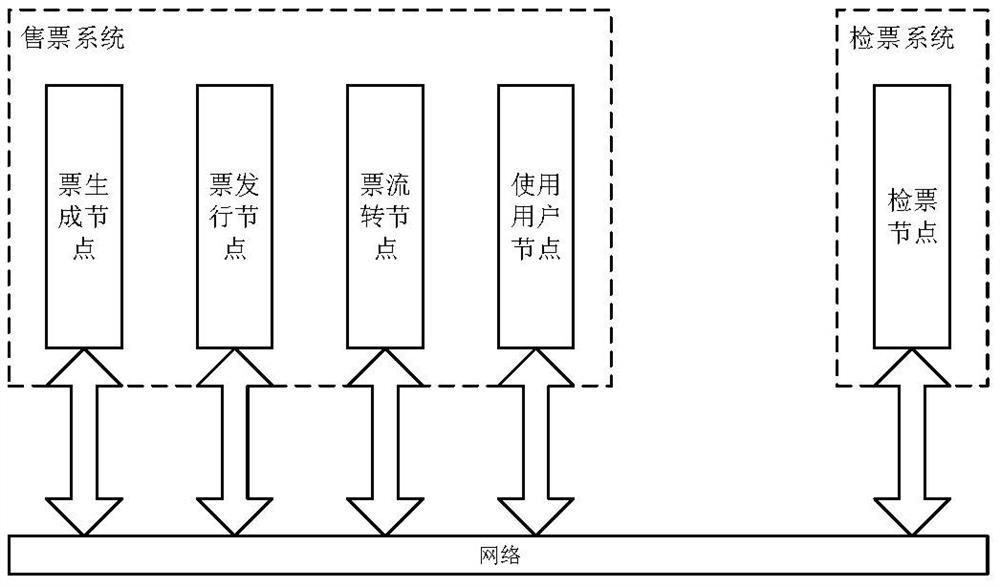
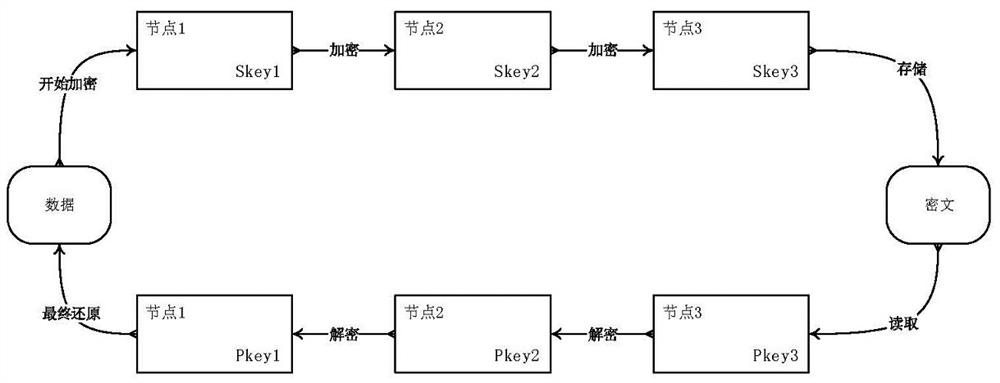
Offline ticket anti-counterfeiting method based on distributed account book principle
PendingCN112926974ALow transaction data and communication loadFast transactionTicket-issuing apparatusPayment protocolsKey leakageTamper resistance
The invention discloses an offline ticket anti-counterfeiting method based on a distributed account book principle. The offline ticket anti-counterfeiting method comprises the following steps that ticket system nodes are divided into a ticket (ticket number) generation node, an issuing node, a transfer node, a user node and a ticket checking node; ticket system transactions are divided into ticket generation transactions, issuing transactions, circulation transactions, pre-check transactions, ticket checking transactions, pre-refunding transactions and ticket refunding transactions, wherein each node has own secret keys (including a public key and a private key), and each transaction of the system needs to be encrypted by multiple nodes; when a ticket selling system sells a ticket, multiple parties are taken from transaction nodes for encryption and common certification, each node encrypts data by using a private key according to a specified sequence, and finally a ciphertext is formed and stored. When a ticket checking system checks the ticket, decryption is carried out by utilizing the public key of the corresponding node in the transaction of the ticketing system according to an opposite sequence. A multi-party authentication mechanism is provided, so that a decentralized mutual trust effect is achieved, tampering resistance is improved, and secret key leakage of any party is insufficient to cause counterfeiting of transaction data.
Owner:GLOBALTOUR GROUP LTD
A deep learning classification method with the function of defending against adversarial sample attacks
The invention discloses a deep learning classification method with the function of defending against adversarial sample attacks. The device for realizing the classification method includes: an attack generation model AG, an adversarial sample discrimination model D, and a classification model DNN. The specific methods are as follows: (1) Normal use The data set trains DNN, and the classification accuracy is greater than the preset value, and the training of DNN is stopped; (2) Alternately train the parameters of AG and D until AG‑D achieves Nash equilibrium; (3) Alternately train the parameters of AG and DNN until AG-DNN realizes Nash equilibrium; (4) judge whether the adversarial example discrimination model D and the classification model DNN reach Pareto optimality, if yes, DNN training is completed, and step (5) is performed; otherwise, return to step (2); ( 5) Input the sample to be classified into the trained classification model DNN to obtain the classification result. The invention can effectively solve the vulnerability of the classification model in the face of confrontation samples in practical classification applications, and improve the robustness of the model performance.
Owner:ZHEJIANG UNIV OF TECH
Sample plate marking and pricking-pressing device and use method of sample plate marking and pricking-pressing device
ActiveCN104907357AQuality assuranceAddressing VulnerabilityMetal working apparatusBrute forceWorkload
The invention discloses a sample plate marking and pricking-pressing device and a method used by the sample plate marking and pricking-pressing device. An end head support arm and a support arm are arranged on a base; a power hammer is arranged on the end head support arm; the power hammer penetrates through a limiting groove in a baffle for limiting; a centrifuge support arm is arranged at the lower part of a rod of the power hammer and is used for controlling and driving the power hammer. By using the device, the technical problems that a worker easily gets hurt, the processing quality can not be ensured, and the working efficiency is low as the manual processing is adopted in the prior art can be solved. By using the device and the method, the original manual pricking-pressing operation by the worker can be completely replaced; in the whole process, the manual pricking-pressing with brute force is avoided, the workload is reduced, the danger coefficient during work is reduced, the phenomenon of arm ache caused by vibration when the pricking-pressing is carried out by adopting a hammer is eliminated, the working efficiency is improved and simultaneously the workpiece processing quality is ensured.
Owner:SHENYANG AIRCRAFT CORP
Information fraud prevention method based on user historical data
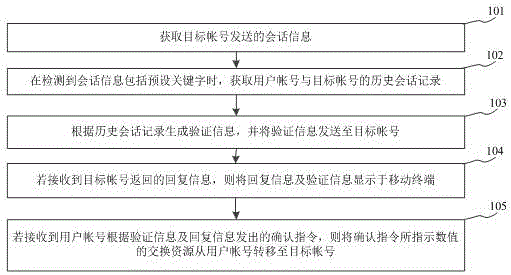
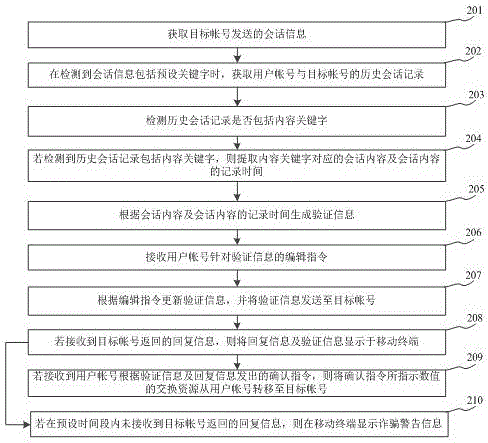
InactiveCN105763428APrevent fraudGuarantee property securityData switching networksProtocol authorisationInternet privacyNumeric Value
The invention relates to an information fraud prevention method based on user historical data, and belongs to the technical field of computer. The method comprises the steps: session information sent by a target account is acquired; when the session information comprising a preset keyword is detected, a historical session record of a user account and the target account is acquired; verification information is generated according to the historical session record, and the verification information is sent to the target account; if a reply message returned by the target account is received, the reply message and the verification information are displayed on a mobile terminal; and if a confirmation instruction is sent by the user account according to the verification information and reply message, exchanging resources indicated by numbers of the confirmation instruction are moved from the user account to the target account. According to the invention, the session information including sensitive keywords is detected, the verification information randomly is generated according to the historical session record of the user account and the target account, so as to prevent the user from fraud, the user property security is not easy to be infringed, and the user property security can be guaranteed.
Owner:徐亚萍
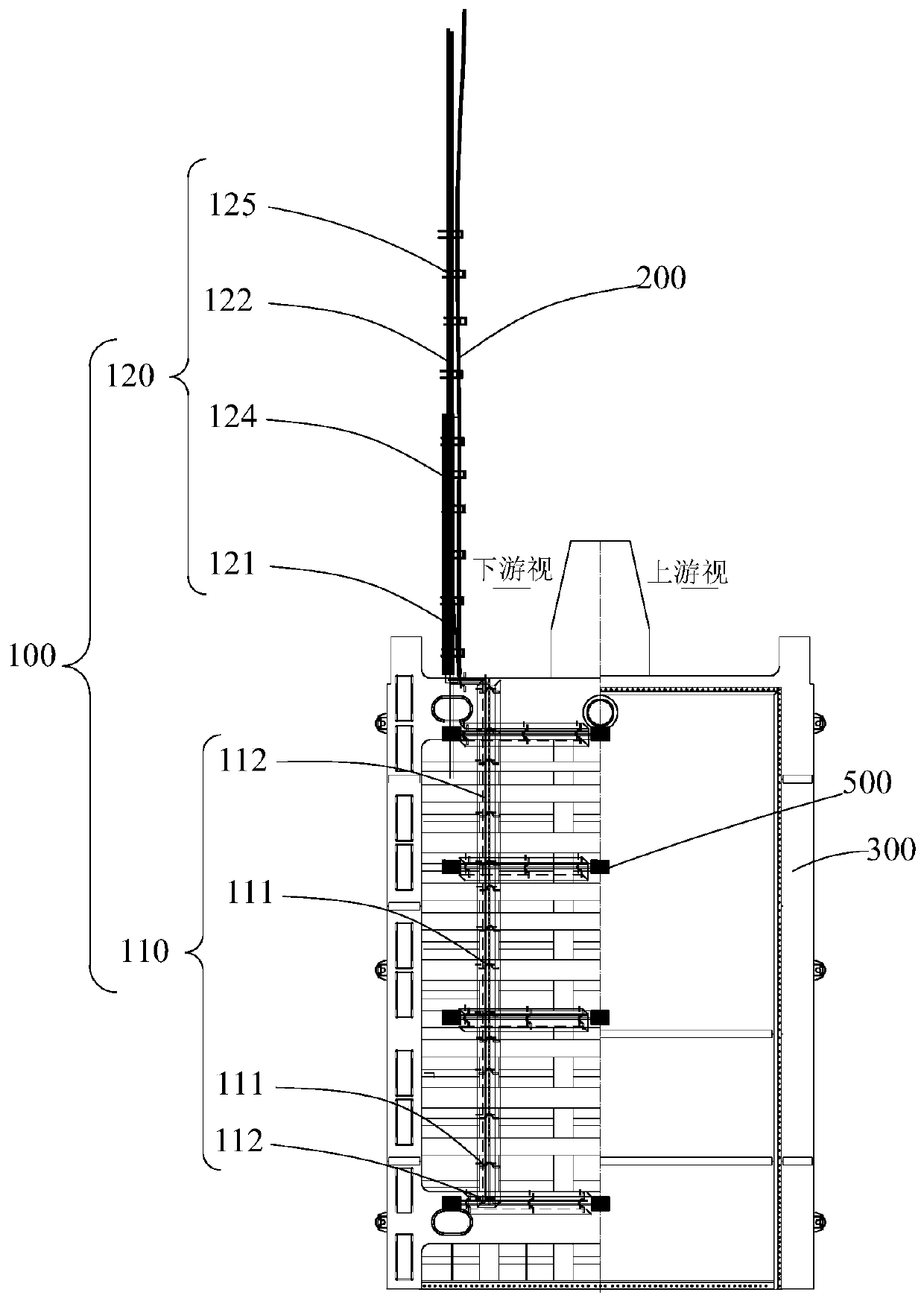
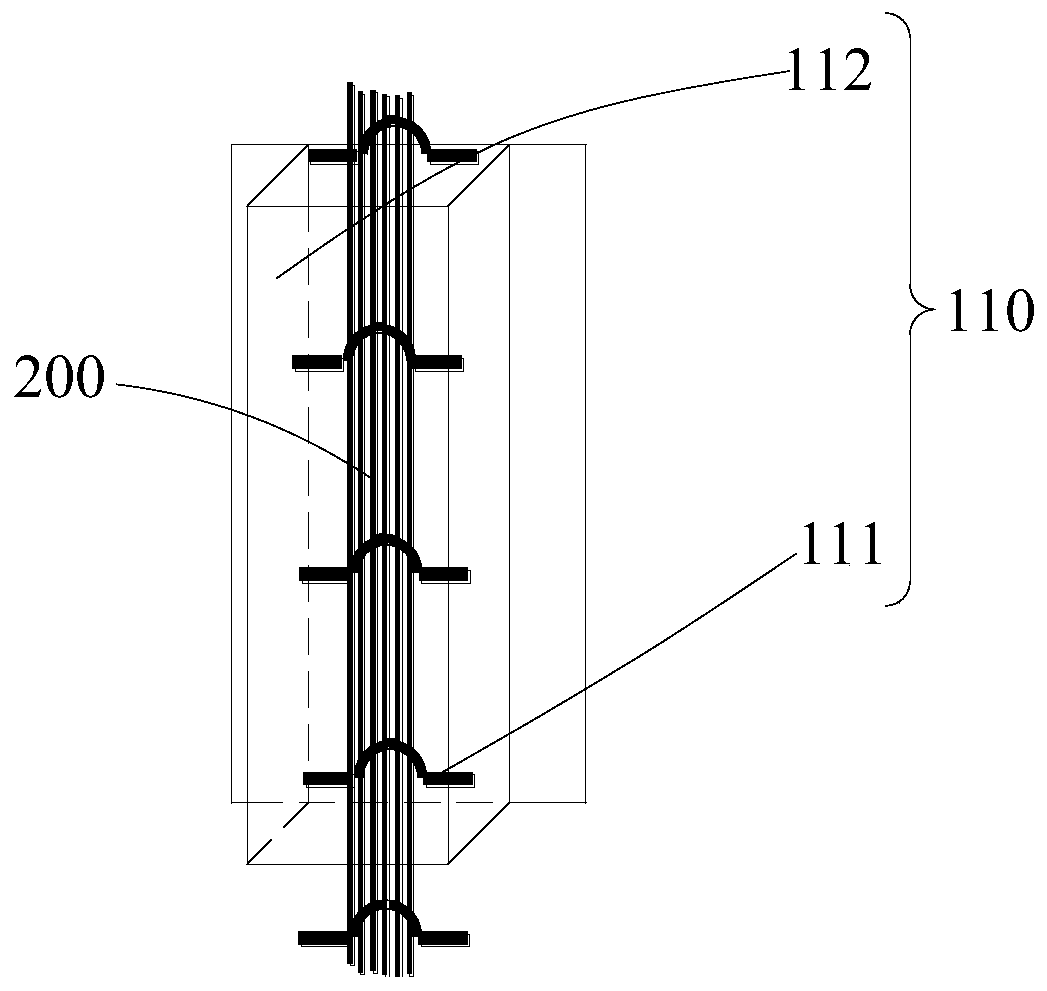
High-water-head bulkhead gate vibration monitoring system, cable protective device and arrangement method
PendingCN110086138ARealize reliable protectionGuaranteed to be intactVibration measurement in solidsCable arrangements between relatively-moving partsWire ropeFlat panel
The invention provides a high-water-head bulkhead gate vibration monitoring system, a cable protective device and an arrangement method. The cable protective device comprises a gate body vibration monitoring cable protective assembly and a gate well monitoring cable protective assembly; the gate body vibration monitoring cable protective assembly comprises a first fixation part and a protective plate, the first fixation part fixes a monitoring cable to a measured gate, and the protective plate covers the monitoring cable, and is fixed to the measured gate; and the gate well monitoring cable protective assembly comprises a support member, a wire rope and an elevating member, and the support member is arranged in the top of the measured gate. The wire rope is connected with the support member and the elevating member. The elevating member is arranged in the top of the gate well, and is used to drive the wire rope and monitoring cable on the measured gate to rise and fall synchronous withthe measured gate. Thus, gate vibration monitoring cable is protected reliably, the monitoring cable is kept in good condition in the process that the measured gate is opened / closed in dynamic water,and safe reliable operation of the high-water-head bulkhead gate system and a sluicing building is ensured.
Owner:CHINA INST OF WATER RESOURCES & HYDROPOWER RES
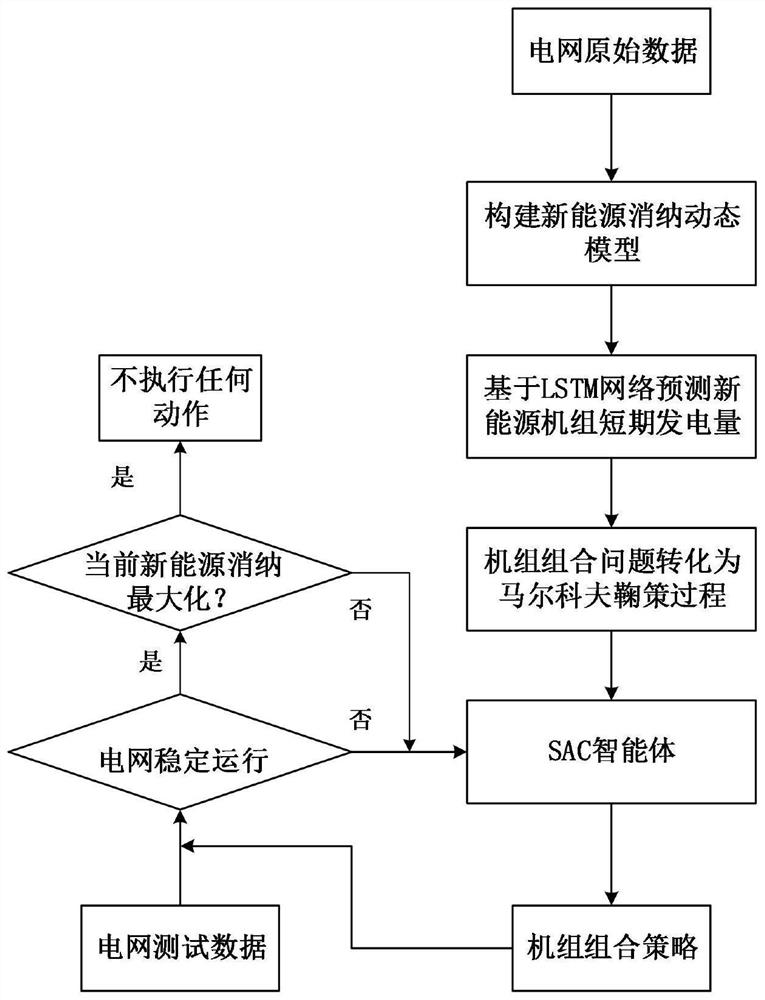
Unit commitment optimization method considering new energy consumption
PendingCN114204546AEfficient use ofImprove grid connection efficiencyGeneration forecast in ac networkSingle network parallel feeding arrangementsNew energyElectric power system
The invention relates to a unit commitment optimization method considering new energy consumption. The method comprises the following steps: step 1, constructing a day-ahead new energy consumption dynamic evaluation model; step 2, predicting the short-term generating capacity of the new energy unit based on an LSTM neural network, including preprocessing historical data and completing prediction of the generating capacity of the new energy unit by using the LSTM neural network; step 3, converting a unit commitment problem into a Markov decision process, including design of a power grid state st, an action at, a reward value Rt and a transfer function; and step 4, according to the historical operation data characteristics of the power grid, intelligent agent construction is completed based on a parameter adaptive neural network, an intelligent agent is trained, and a unit output plan meeting a new energy consumption target is obtained. According to the invention, the stability of a novel power system taking new energy as a main body can be improved, efficient utilization of clean energy is realized, and consumption of the new energy is completed on the premise of reliable operation of a power grid.
Owner:ELECTRIC POWER SCI & RES INST OF STATE GRID TIANJIN ELECTRIC POWER CO +2
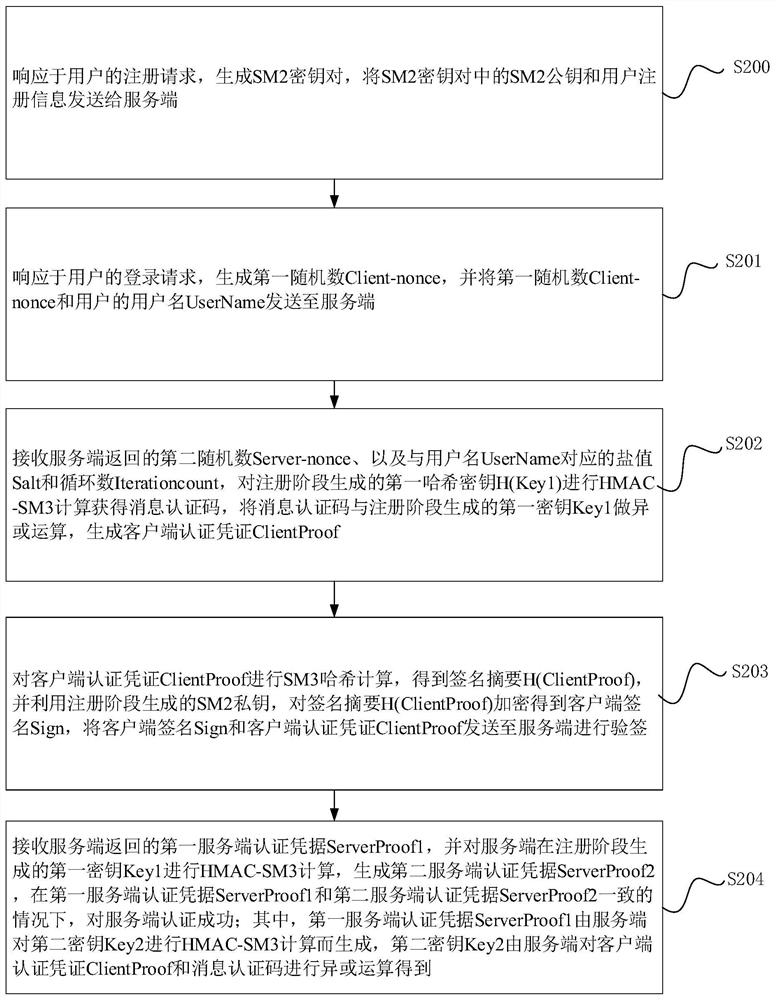
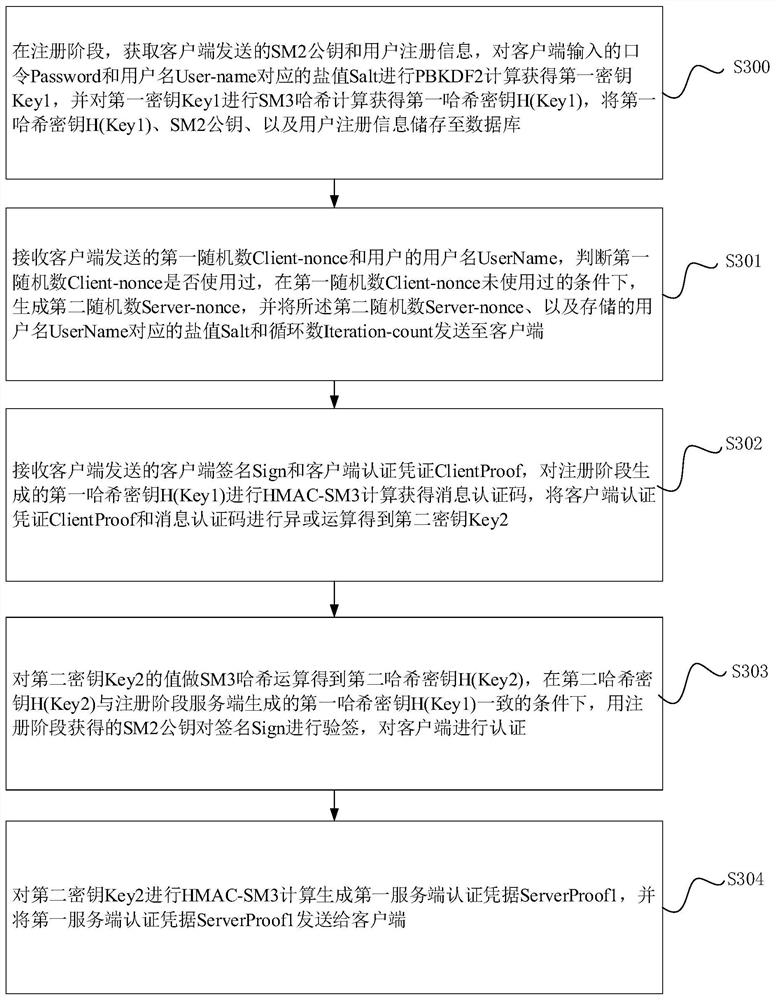
Password authentication method and system, electronic device and storage medium
InactiveCN113556321AEnsure safetyPurpose and benefits are concise and easy to understandKey distribution for secure communicationEncryption apparatus with shift registers/memoriesInternet privacyEngineering
The invention relates to a password authentication method and system, an electronic device and a storage medium, and the method comprises the steps: generating a first random number in response to a login request of a user; receiving a second random number, a salt value and a cycle number returned by the server, and generating a client authentication certificate; obtaining a signature abstract and a client signature based on the client authentication credential, and sending the client signature and the client authentication credential to a server for signature verification; and receiving a first server authentication certificate returned by the server, performing HMAC-SM3 calculation on a first key generated by the server in a registration stage, generating a second server authentication certificate, and authenticating the server successfully under the condition that the first server authentication certificate is consistent with the second server authentication certificate. Through the password authentication method and device, the problem that the password is easily attacked and leaked in a password authentication process in the prior art is solved, and password security authentication is realized.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Intelligent industrial decentralized information storage node communication network system and method
PendingCN111404994AAddressing Vulnerability to AttacksSolve high cost problemsUser identity/authority verificationIndustrial InternetIndustrial communication
The invention discloses an intelligent industrial decentralized information storage node communication network system and method, and relates to the technical field of intelligent industrial systems.The system comprises an administrator terminal, an industrial equipment terminal, a general control computer, an industrial network platform, an industrial data collection module and a communication interaction module. According to the invention, the decentralization technology is applied to the field of intelligent industry, a strict identity verification mechanism is established without depending on a central verification server, more reliable identity verification support is provided for intelligent industrial equipment, and the problem of high cost consumption of industrial Internet of Things equipment caused by a centralization server in the prior art is effectively solved. According to the invention, based on the decentralization technology, equipment in the field of intelligent industry is enabled to carry out security interaction, tamper resistance is realized, each distributed industrial communication node has public key information of all nodes with the same content, and theproblem that a centralized server is easily attacked in the traditional technology is effectively solved.
Owner:北斗(天津)科学技术应用研究院(有限合伙)
Preschool education drawing board
InactiveCN109849583ANot easy to wearAddressing VulnerabilityOther artistic work equipmentsState of artEngineering
The invention discloses a preschool education drawing board. The preschool education drawing board structurally comprises a framework, a drawing board, a supporting block and a protection device. Theprotection device is arranged, so that a protection cover can be packaged along the periphery of the drawing board and buckled and fixed by a buckling shell and a buckle which are arranged on the outer surface of the right end of the drawing board, and then fixing pieces are in threaded connection with four corners of the drawing board through screws, so that the outer surface of the protection cover is protected and does not wear easily. A plastic protection sleeve arranged on the outer surface of the framework also plays a certain protection role. A rubber pad arranged at the bottom end of the framework prevents the framework from moving in the using process and affecting drawing. The problem that protective measures are not provided for spaces between the drawing board and the frameworkafter the drawing board is placed on the framework, and therefore children can easily get hurt during use is solved.
Owner:天津星博翼教育科技有限公司
Safe twist-open cap
The invention discloses a safe twist-open cap. The safe twist-open cap comprises a cap top and a cylindrical cap wall formed by downward extending of the outer edge of the cap top, wherein two convex rings which are parallel to each other and surround the cap wall are arranged at the lower part of the cap wall; an annular groove is formed in a position between the two convex rings; a plurality of U-shaped slits are formed in the groove bottom of the annular groove along the circumferential direction of the cap wall; the cap wall at the upper side of the U-shaped slits inclines inwards to form punching openings penetrating through the cap wall; the cap wall between adjacent punching openings form bridges; the cap wall below the punching openings form anti-theft rings; and the anti-theft rings are connected with the cap wall above the punching openings through the bridges. The safe twist-open cap effectively solves the problem that an operator is prone to hurt in the uncapping process of a twist-open cap in the prior art, the safety of the twist-open cap in the uncapping process is greatly improved, and the practical value is high.
Owner:YIWU EASY OPEN END INDAL CORP
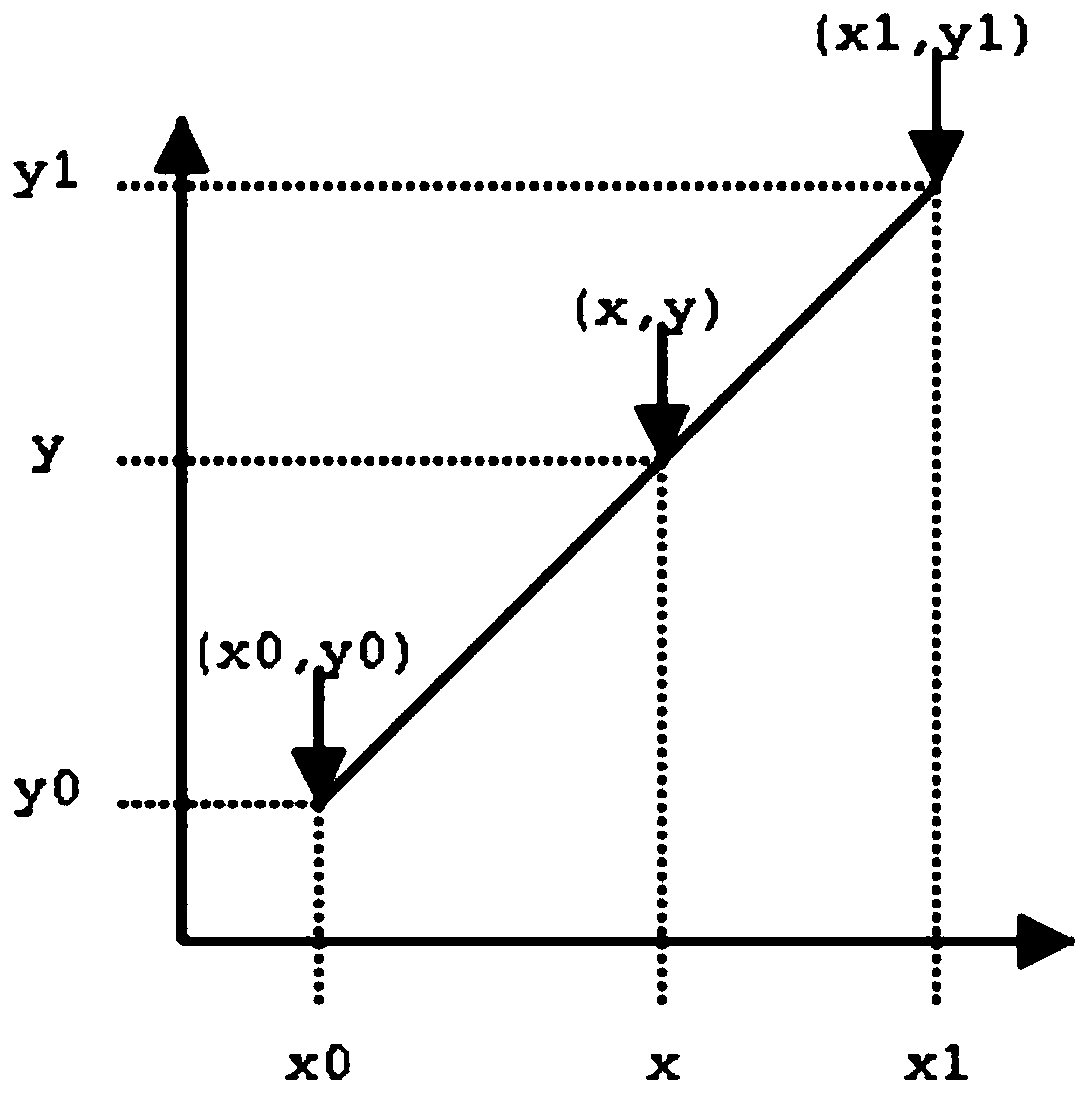
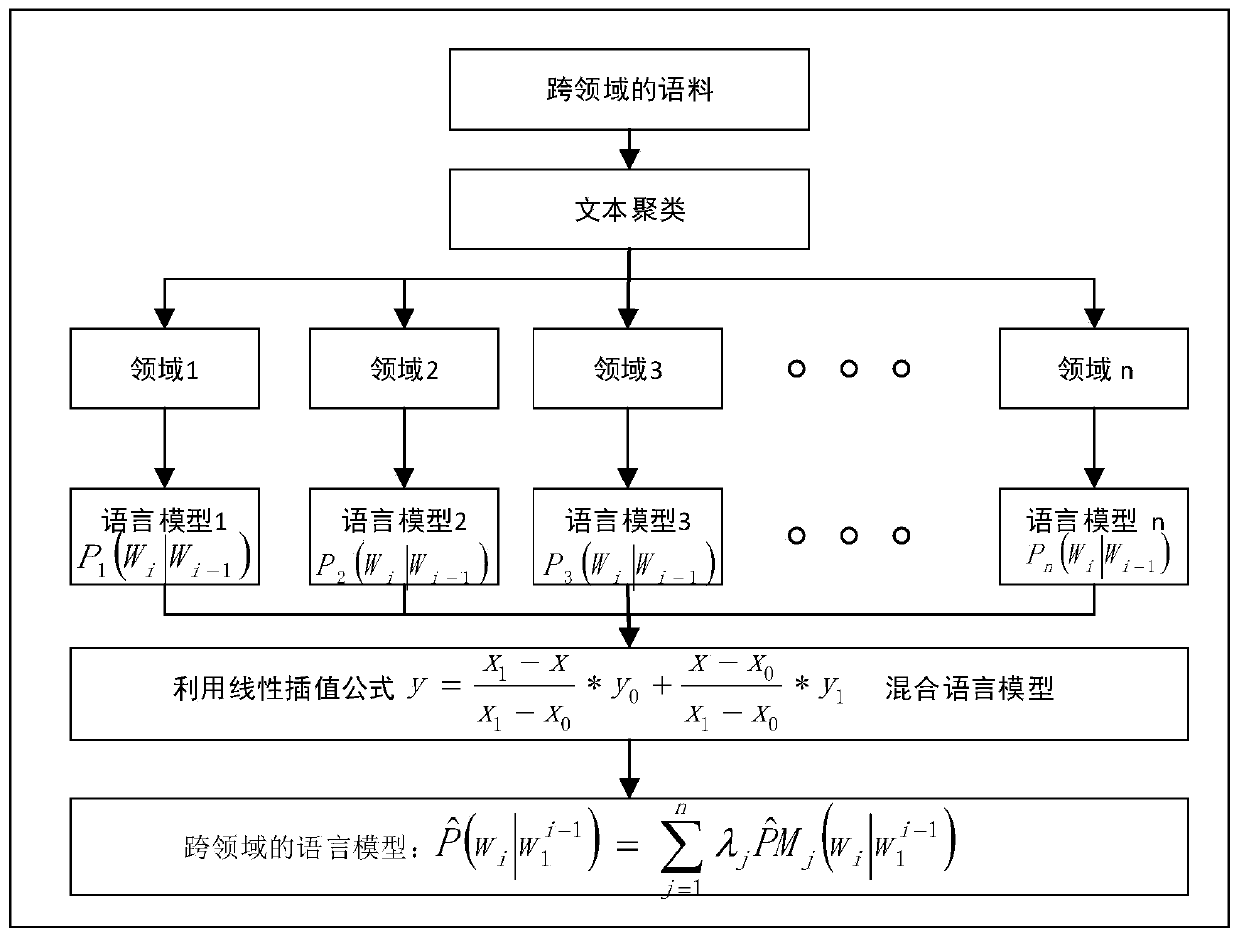
Cross-domain language model training method and device, electronic equipment and storage medium
ActiveCN111143518AAddressing VulnerabilityImprove performance indicatorsText database queryingSpecial data processing applicationsEngineeringPerplexity
The invention provides a cross-domain language model training method and device, electronic equipment and a storage medium. The method comprises the steps of obtaining corpus training sets of multipledomains; training a plurality of language models based on the corpus training sets of the plurality of fields to obtain respective outputs of the plurality of language models, the plurality of language models being in one-to-one correspondence with the corpus training sets of the plurality of fields; and according to respective outputs of the plurality of language models and preset interpolationcoefficients of the plurality of language models, interpolating the plurality of language models to obtain a cross-domain language model. According to the cross-domain language model training method provided by the invention, language models in multiple domains are mixed into one model through a language model mixing method based on linear interpolation, so that the cross-domain vulnerability of the language model is effectively solved, the performance index of the language model is improved, and the confusion degree of the language model is reduced.
Owner:北京明朝万达科技股份有限公司
Sealant material, manufacturing method of sealant material, display panel and manufacturing method of display panel
PendingCN108949080AAddressing VulnerabilityEster polymer adhesivesEpoxy resin adhesivesEngineeringSealant
The invention provides a sealant material, a manufacturing method of the sealant material, a display panel and a manufacturing method of the display panel and belongs to the technical field of display. The problem that poor display is caused due to damage of the sealant in the conventional display panel can be at least partially solved. The sealant material disclosed by the invention comprises a sealant body material, wherein a micro shell coated repair agent monomer and a catalyst capable of enabling the repair agent monomer to polymerize are distributed in the sealant body material.
Owner:BOE TECH GRP CO LTD +1
Intelligent household electrical appliance configuration network access method, device and system
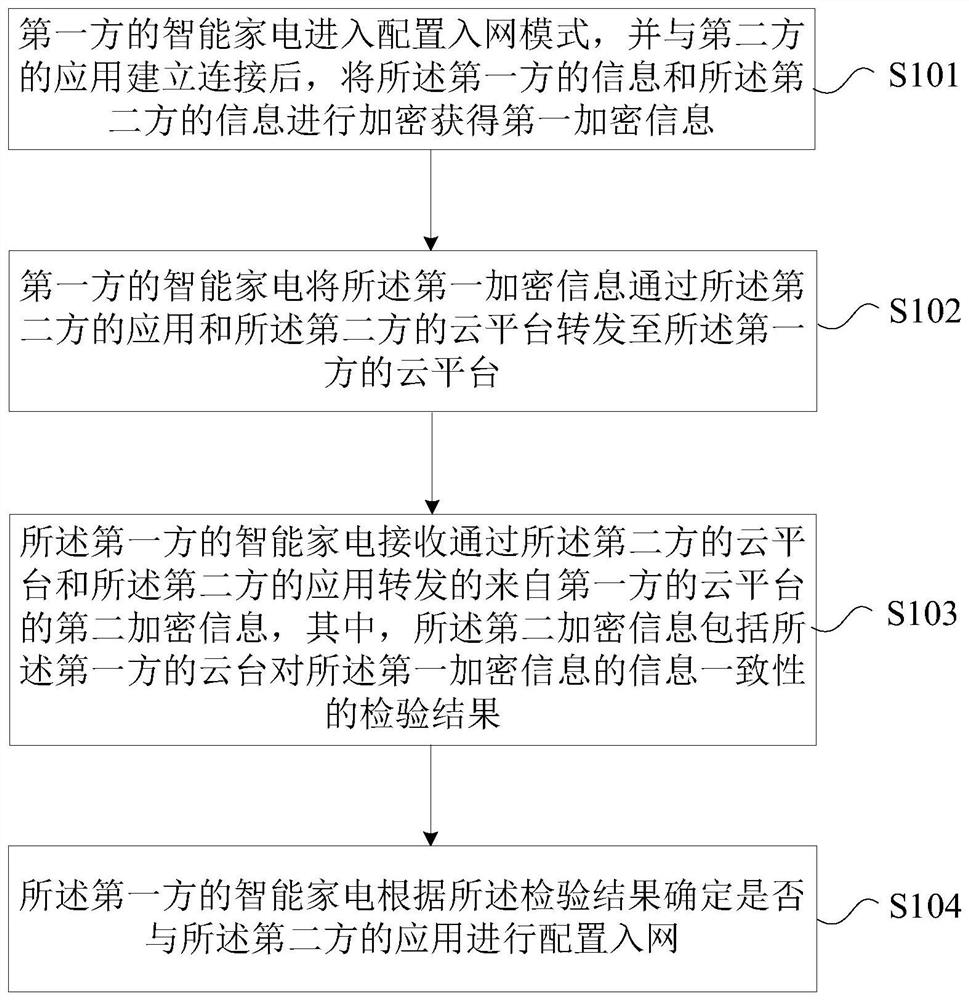
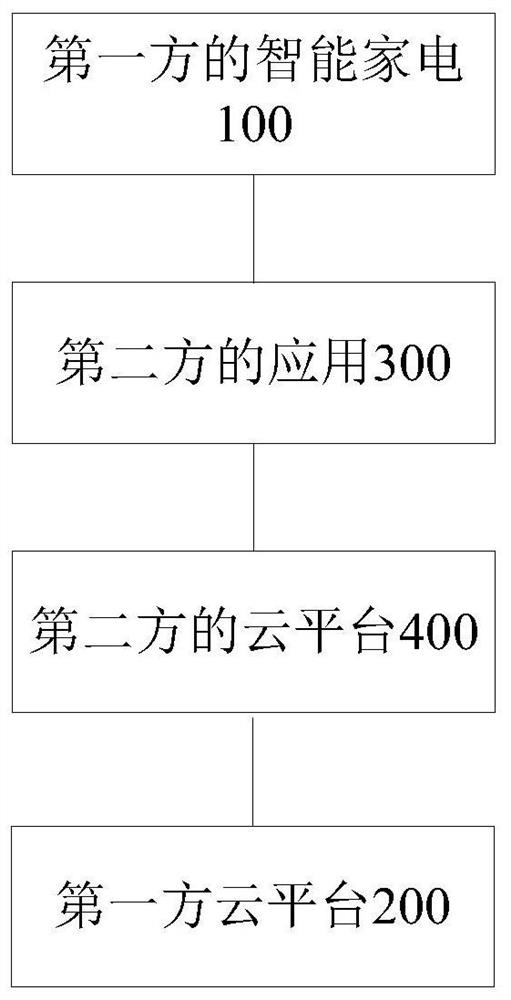
PendingCN111885595AAddressing VulnerabilityEnsure safetyAssess restrictionNetwork topologiesEngineeringWireless lan
The embodiment of the invention provides an intelligent household electrical appliance configuration network access method, device and system, and the method comprises the steps that an intelligent household electrical appliance of a first side enters a configuration network access mode, builds a connection with an application of a second side, and encrypts the information of the first side and the information of the second side to obtain first encryption information; the intelligent household electrical appliance of the first party forwards the first encrypted information to the cloud platform of the first party through the application of the second party and the cloud platform of the second party; the intelligent household electrical appliance of the first party receives second encryption information forwarded by the cloud platform of the second party and the application of the second party from the cloud platform of the first party; and the intelligent household electrical applianceof the first party determines whether to perform configuration network access with the application of the second party according to the check result. According to the invention, the problem that thehousehold electrical appliance is easy to be attacked when being configured to access the wireless local area network in the intelligent household electrical appliance interconnection and intercommunication technology is solved, and the effect of ensuring the security of the household electrical appliance and the household electrical appliance manufacturer cloud platform in the network configuration process is achieved.
Owner:HAIER YOUJIA INTELLIGENT TECH (BEIJING) CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com