Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
437 results about "Server authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
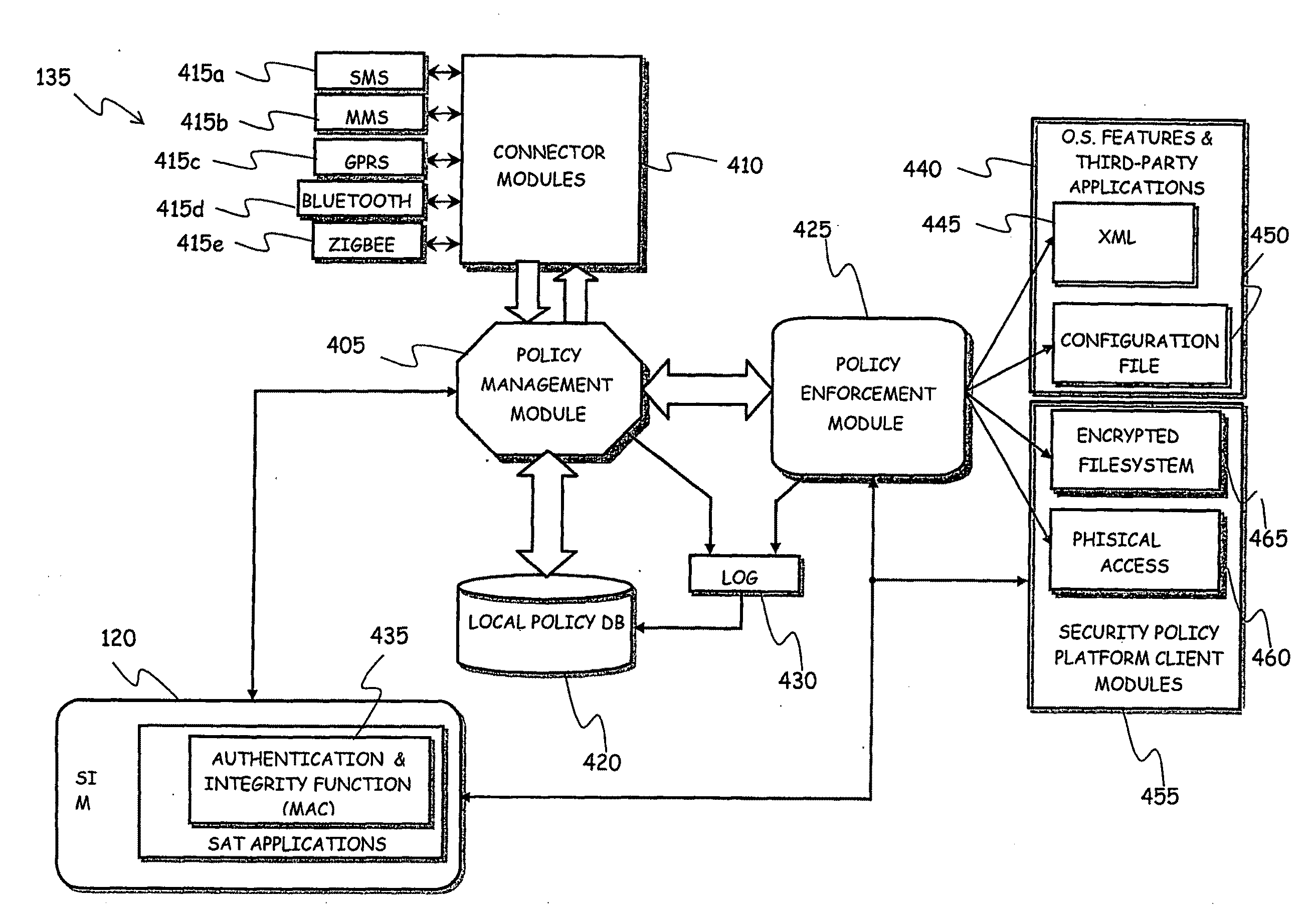
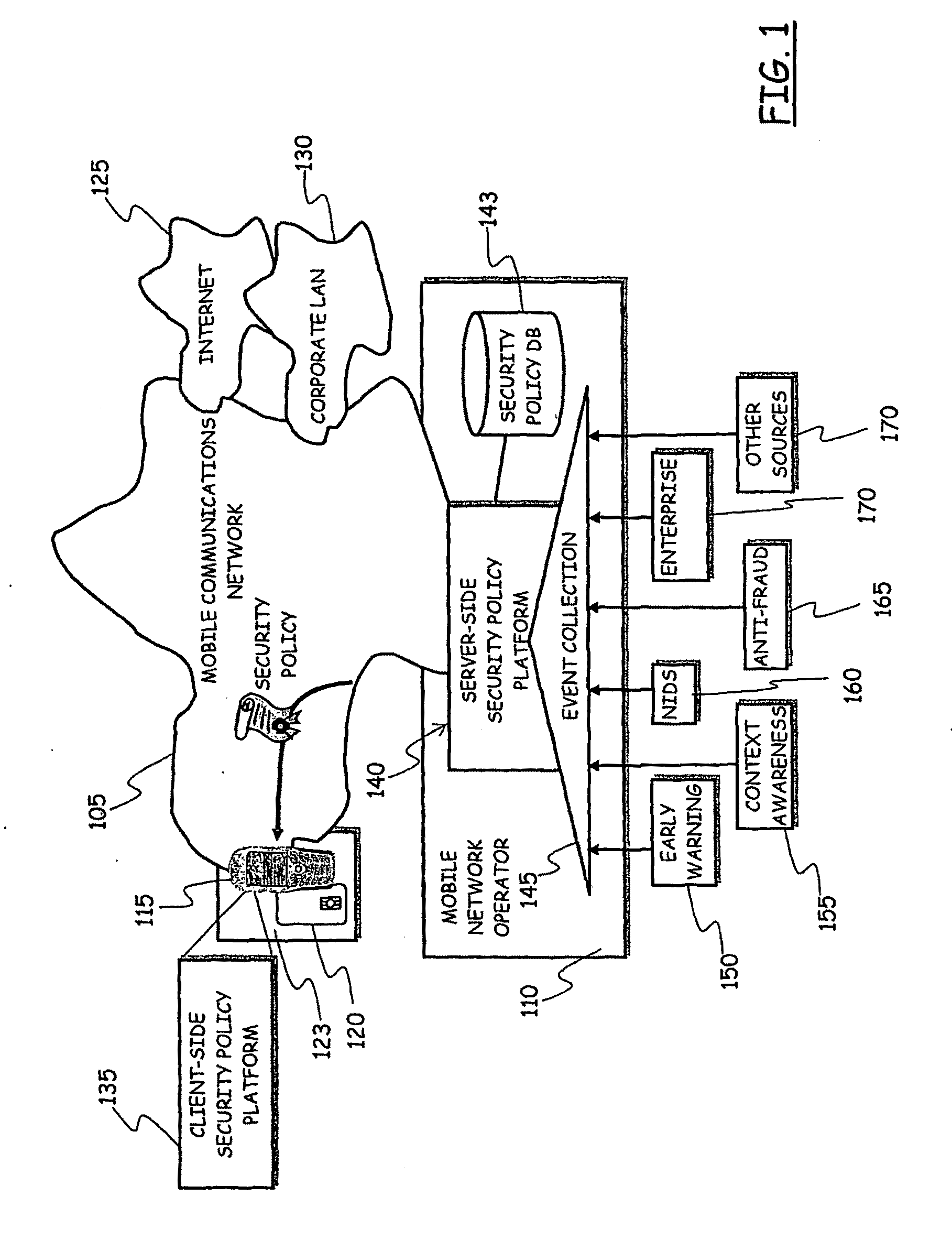
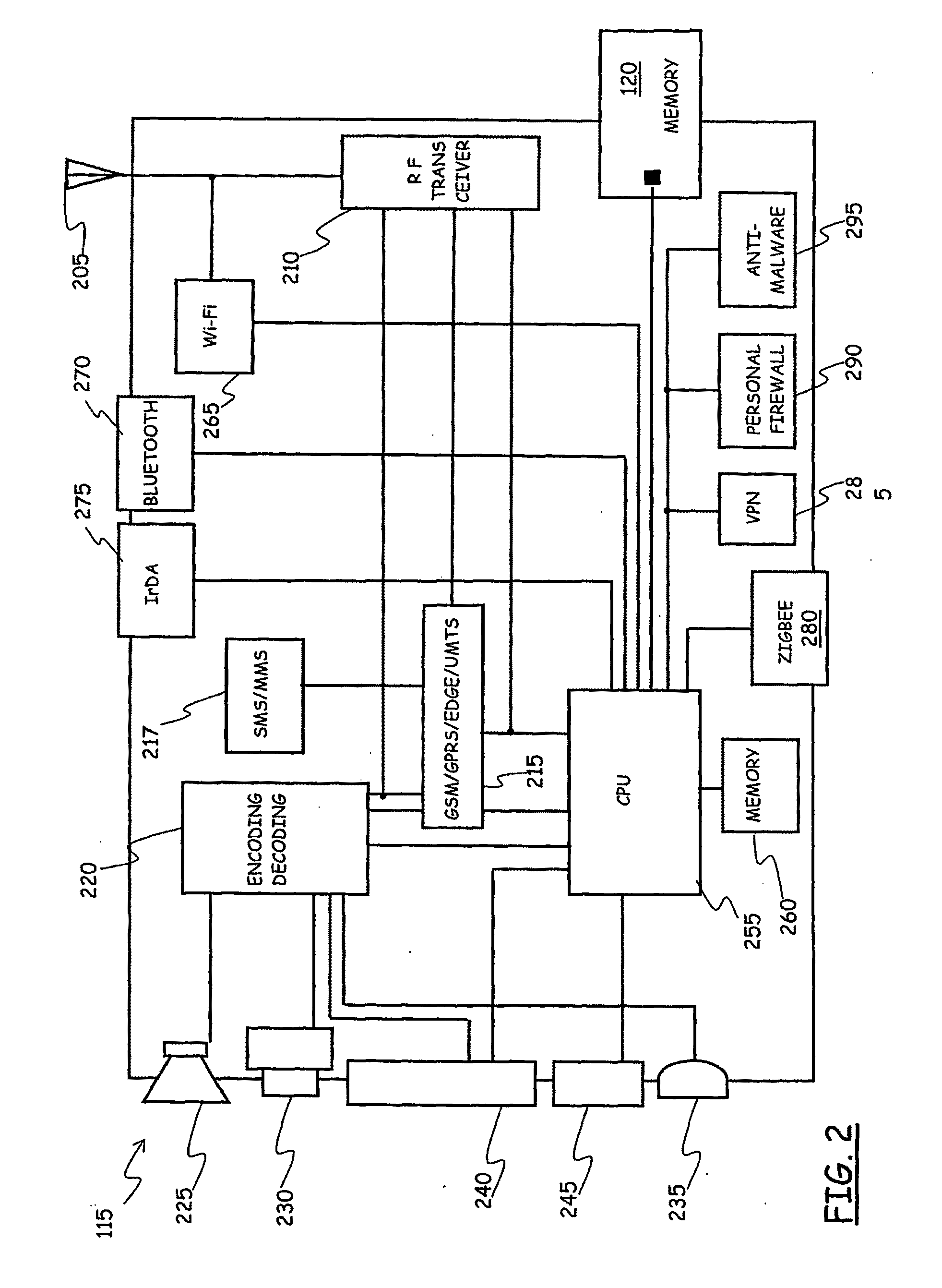
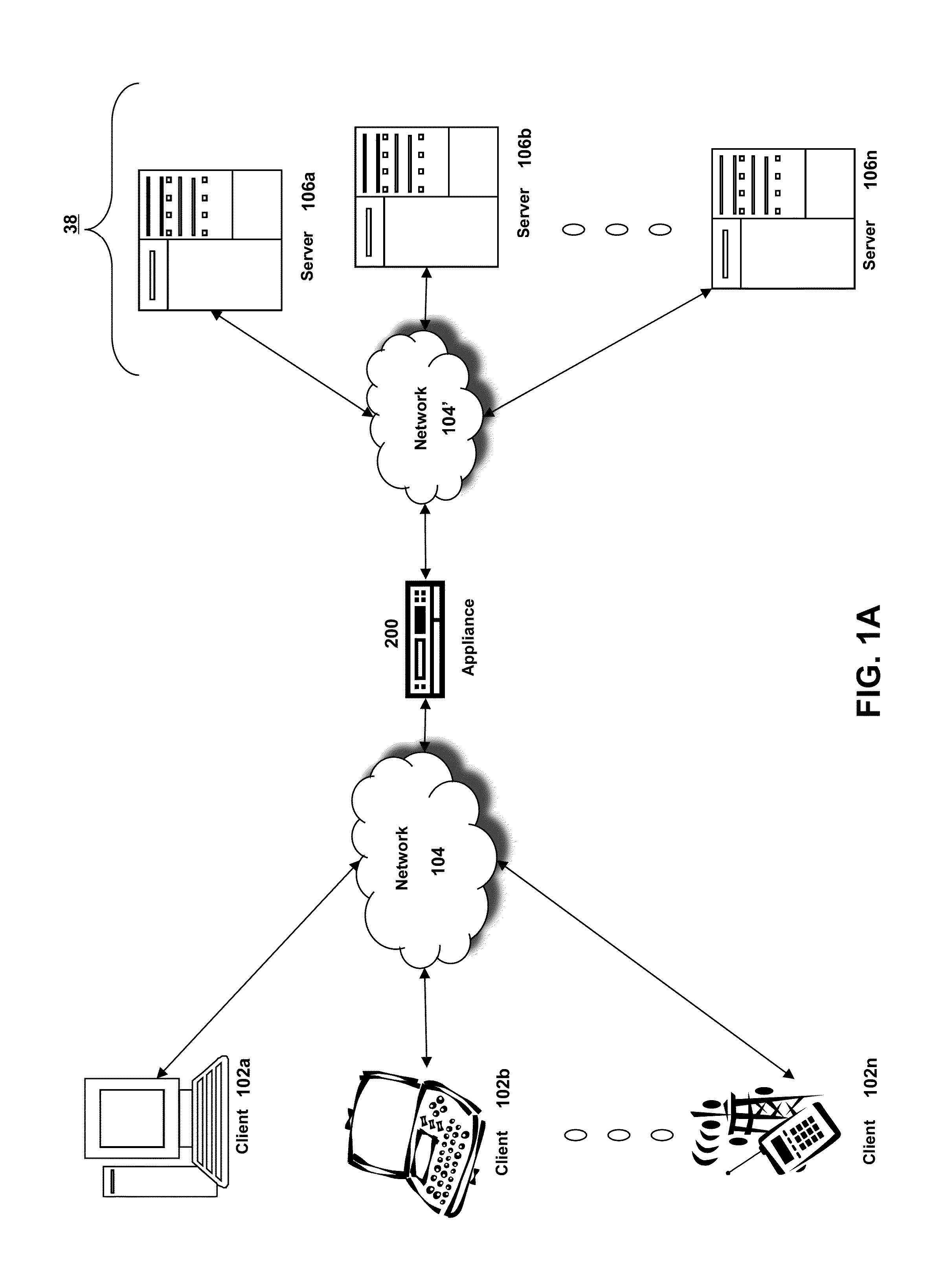
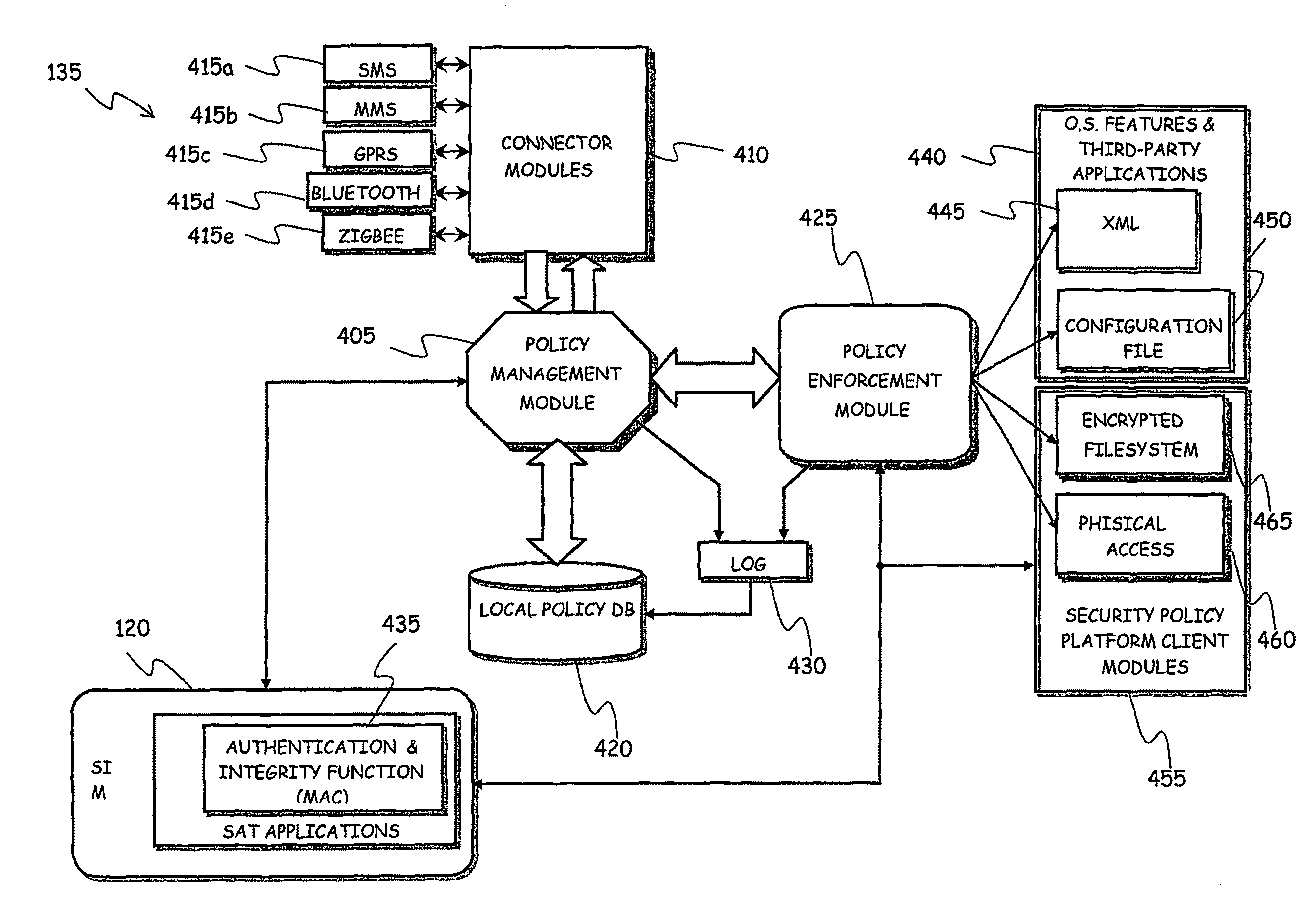
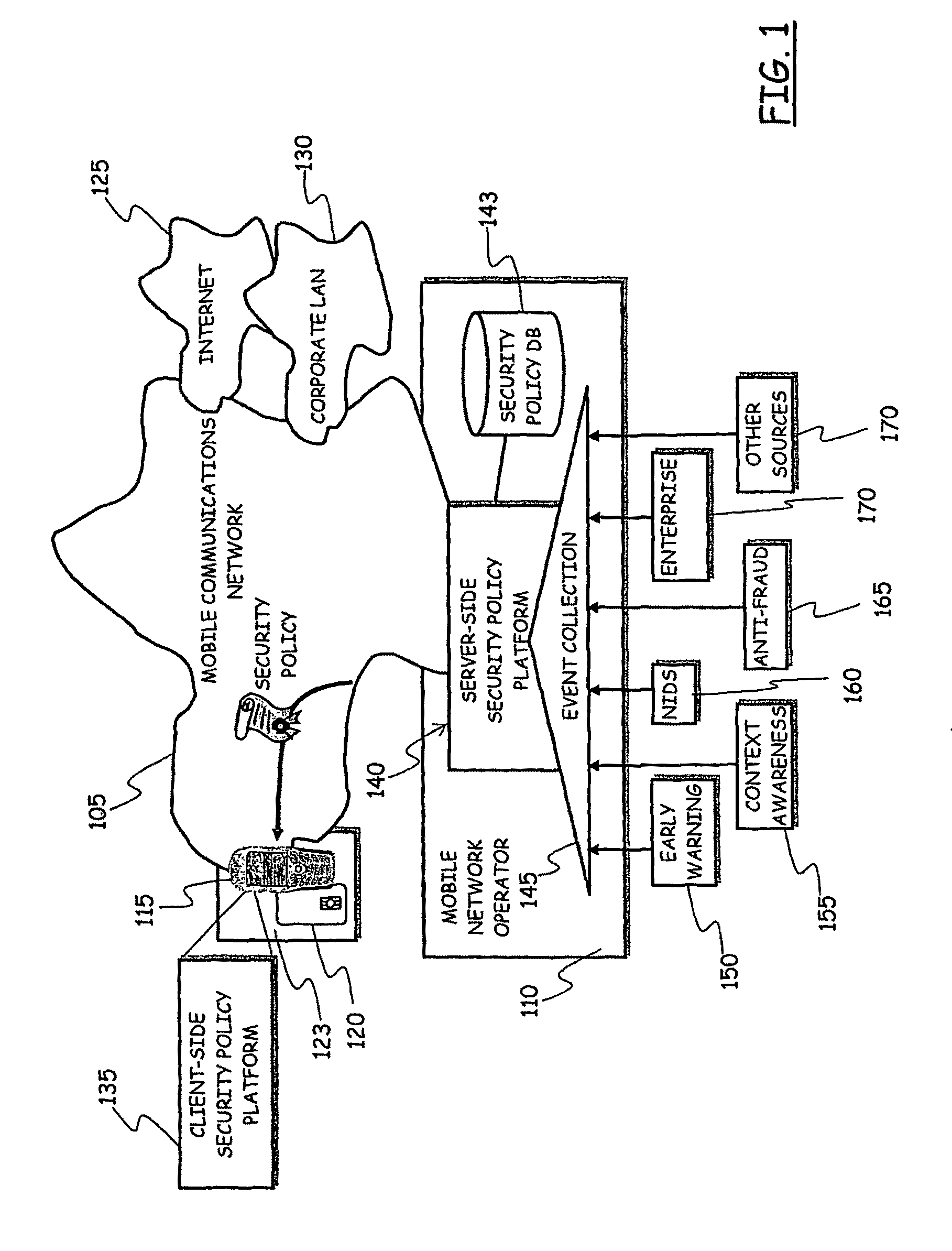
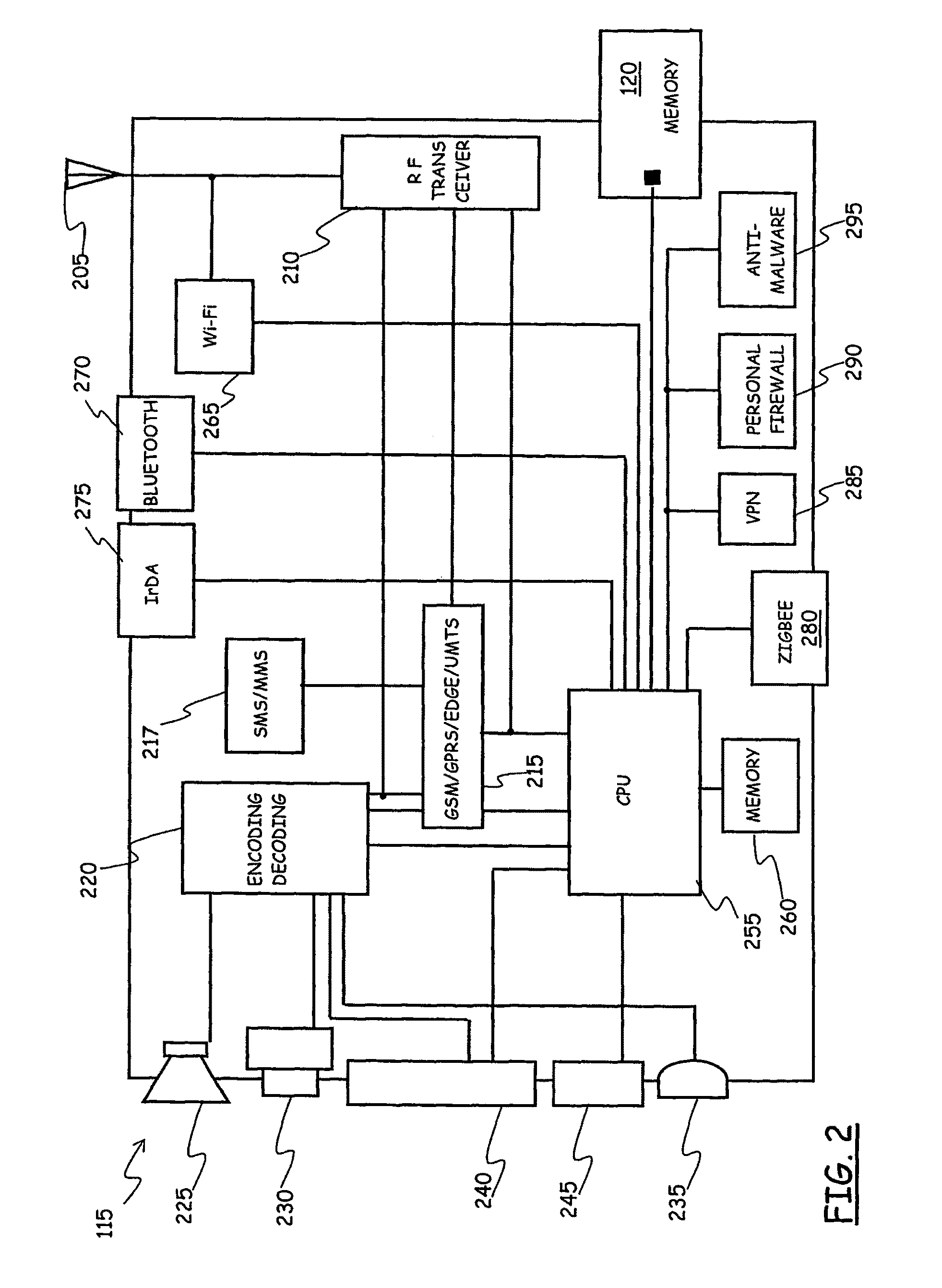
System for Enforcing Security Policies on Mobile Communications Devices
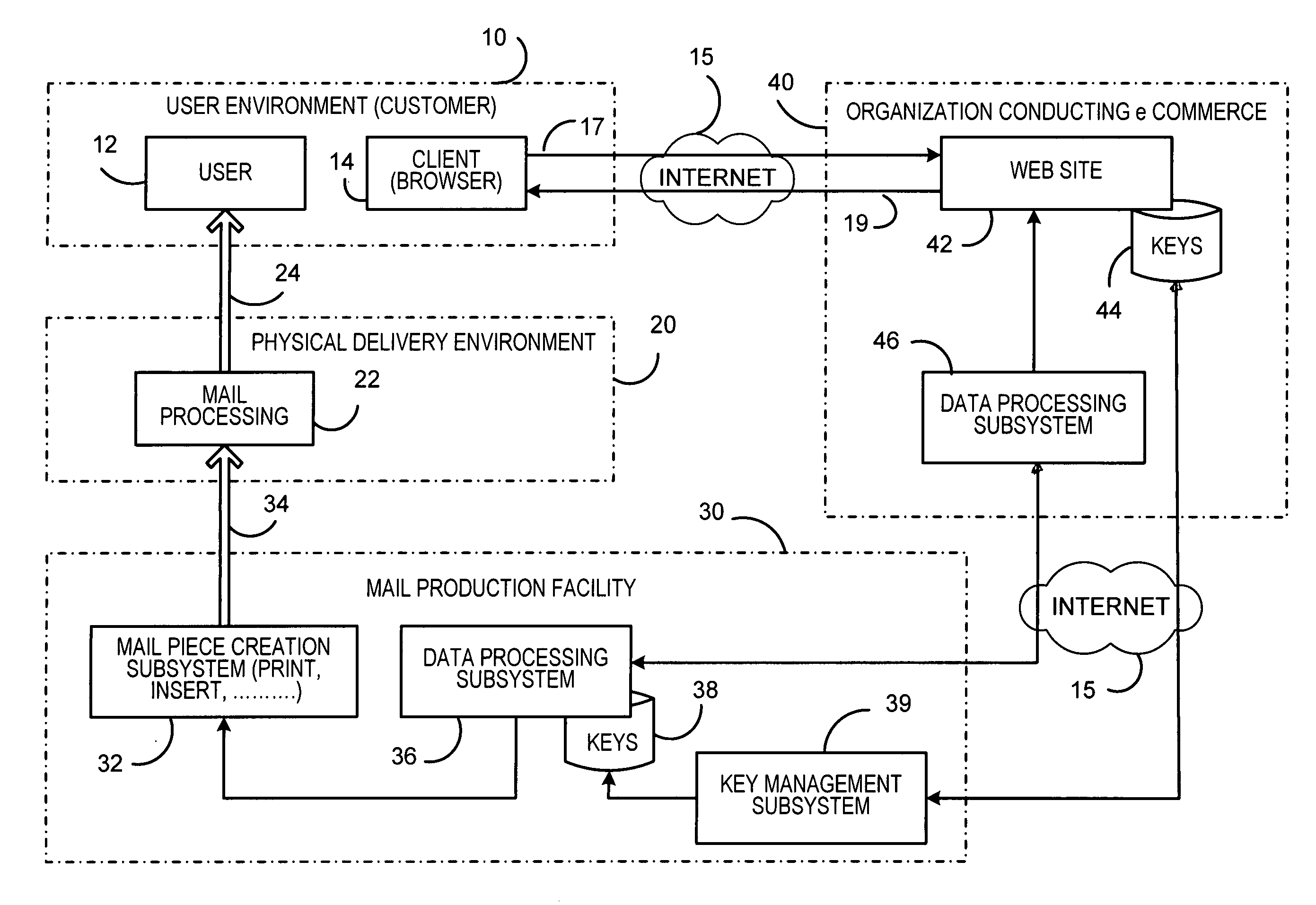
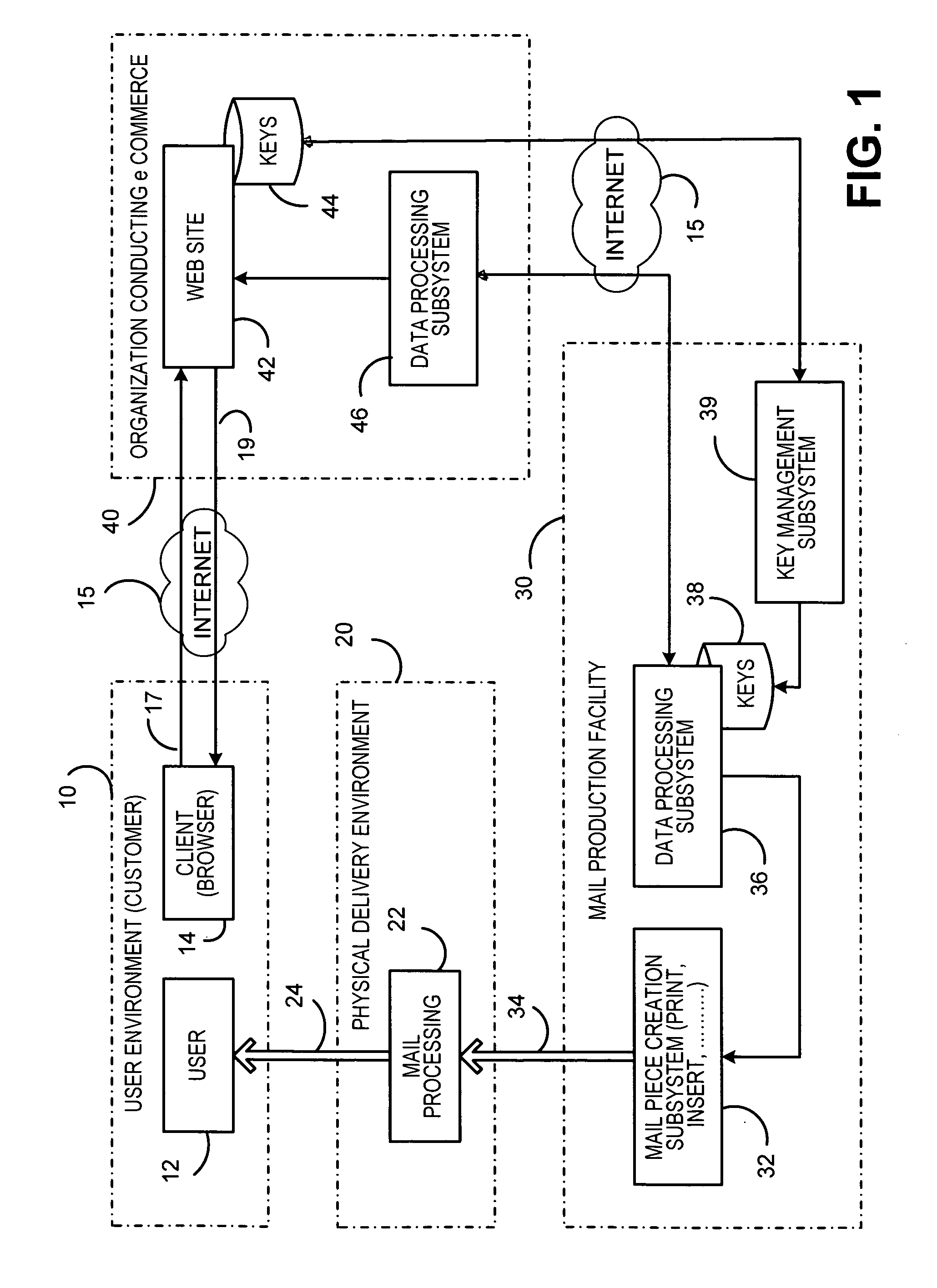
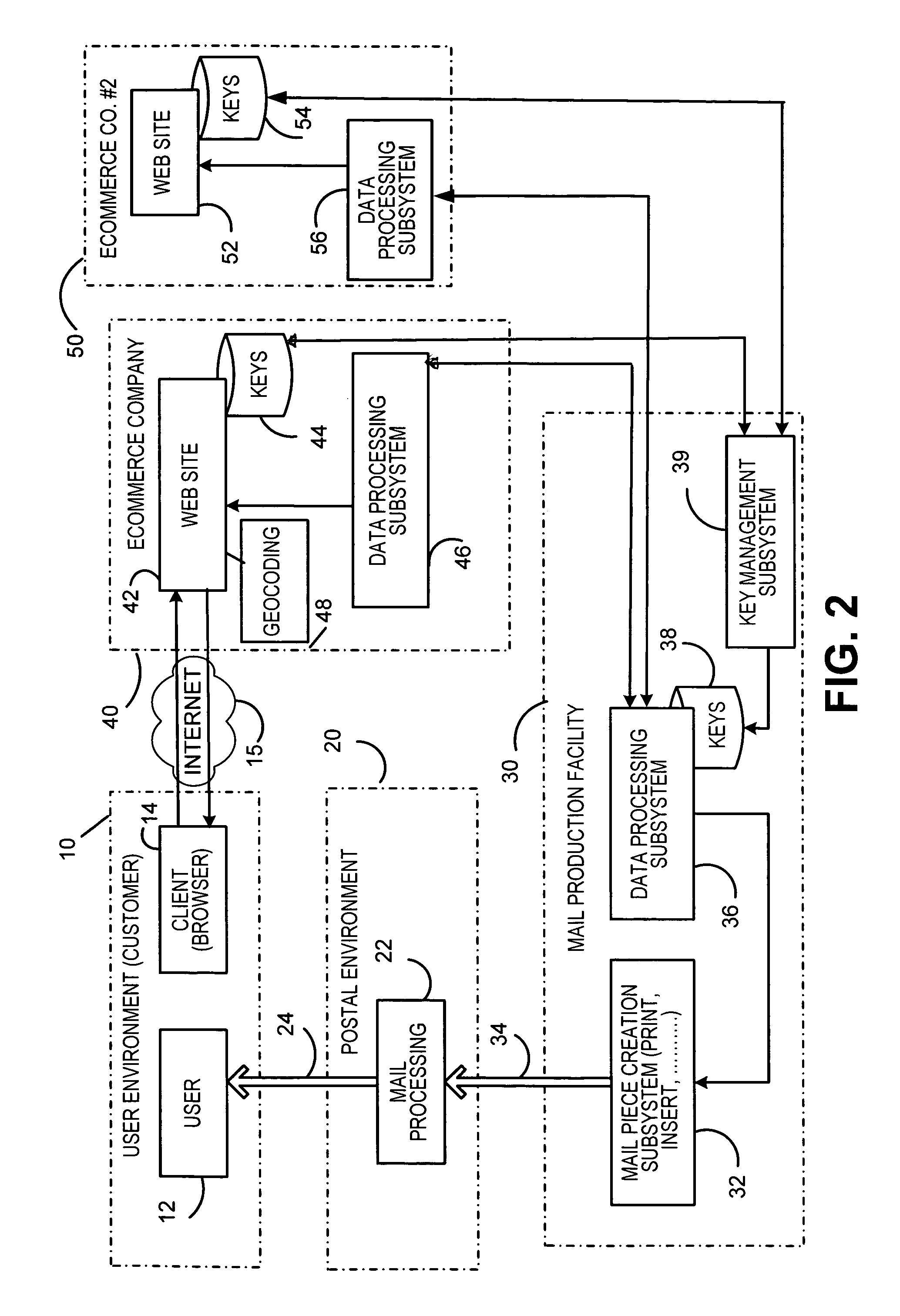
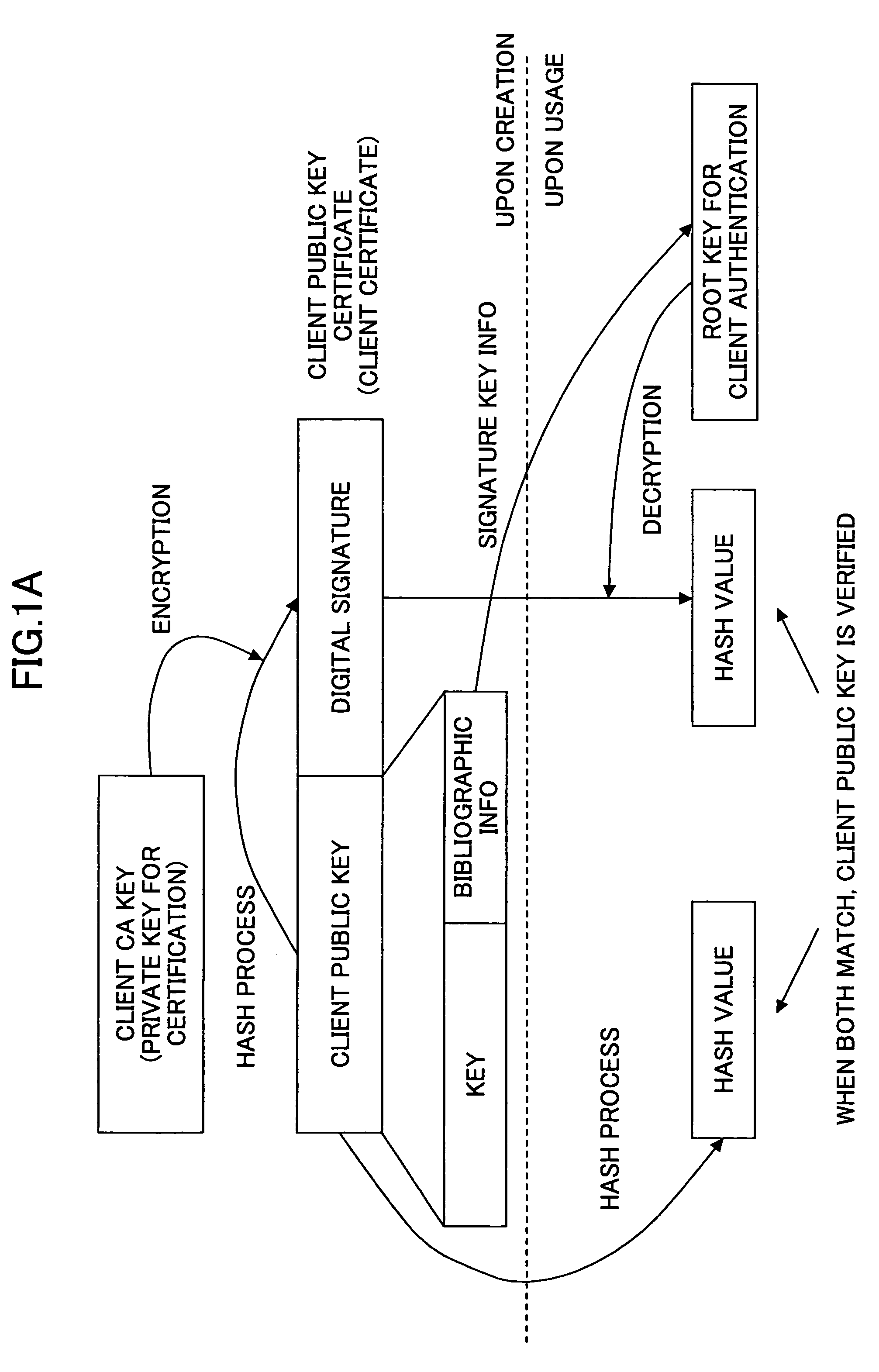
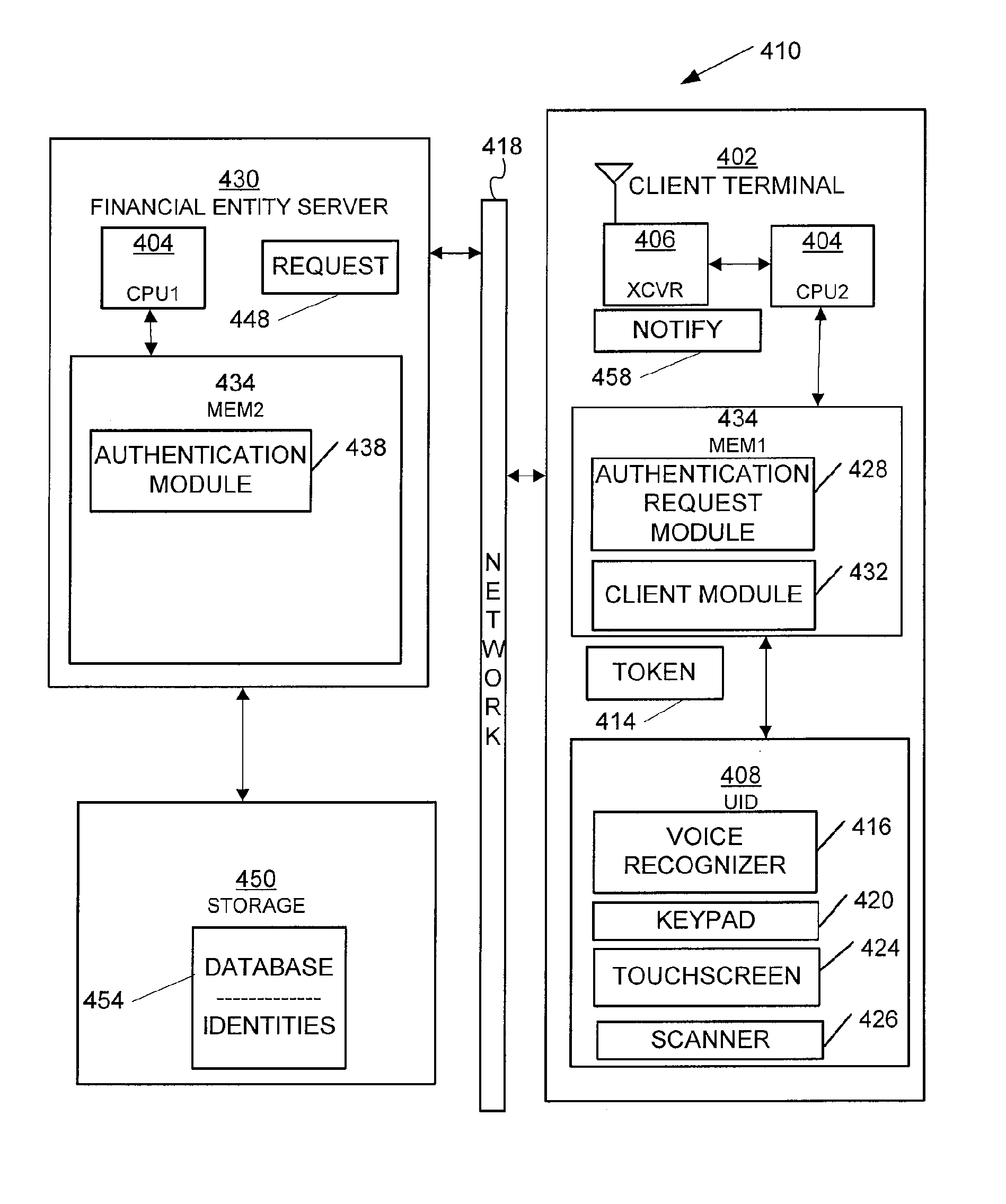
A system for enforcing security policies on mobile communications devices is adapted to be used in a mobile communications network in operative association with a subscriber identity module. The system having a client-server architecture includes a server operated by a mobile communications network operator and a client resident on a mobile communications device on which security policies are to be enforced. The server is adapted to determine security policies to be applied on said mobile communications device, and to send thereto a security policy to be applied. The client is adapted to receive the security policy to be applied from the server, and to apply the received security policy. The server includes a server authentication function adapted to authenticate the security policy to be sent to the mobile communications device; the client is further adapted to assess authenticity of the security policy received from the server by exploiting a client authentication function resident on the subscriber identity module.
Owner:TELECOM ITALIA SPA
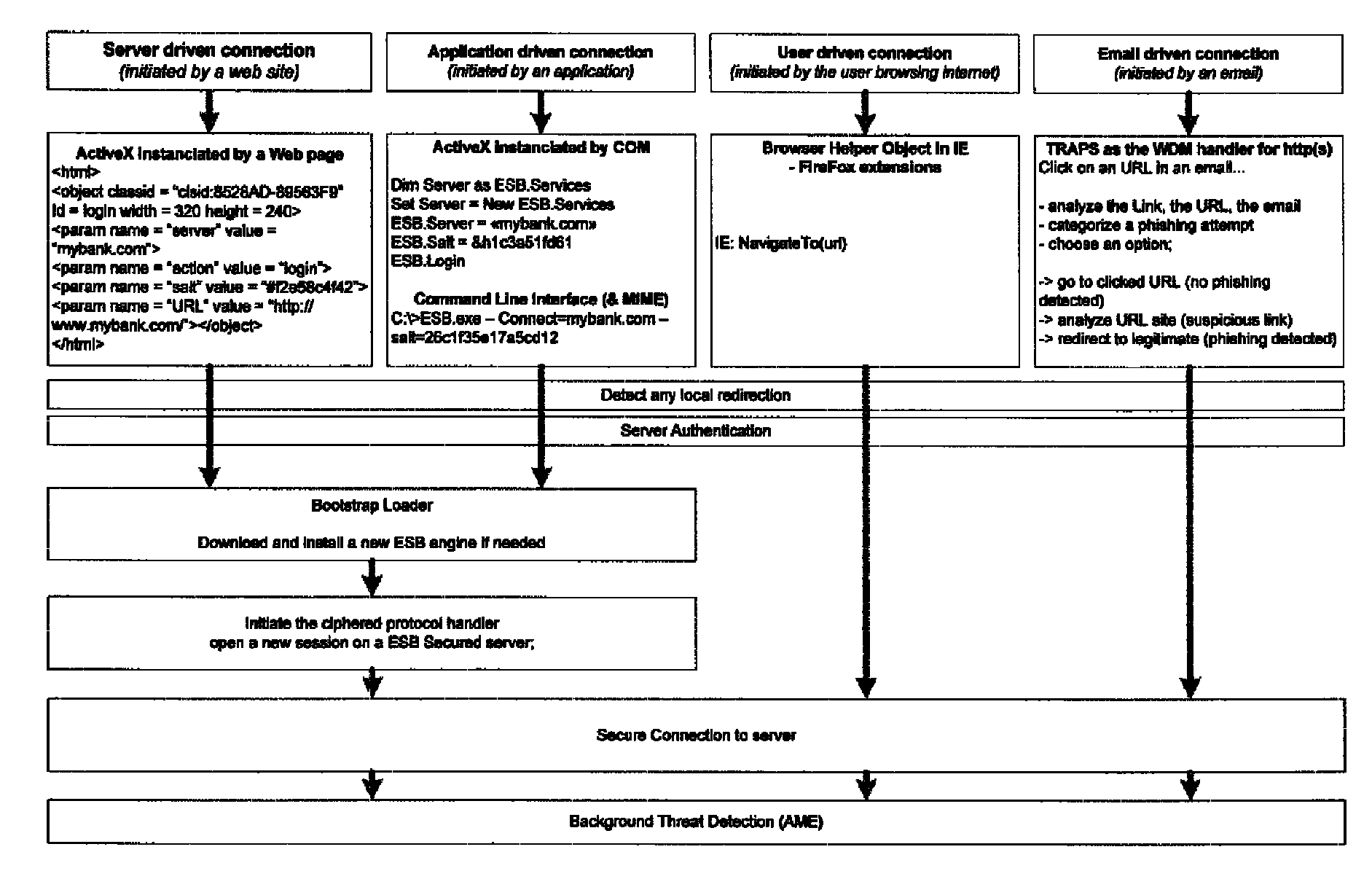
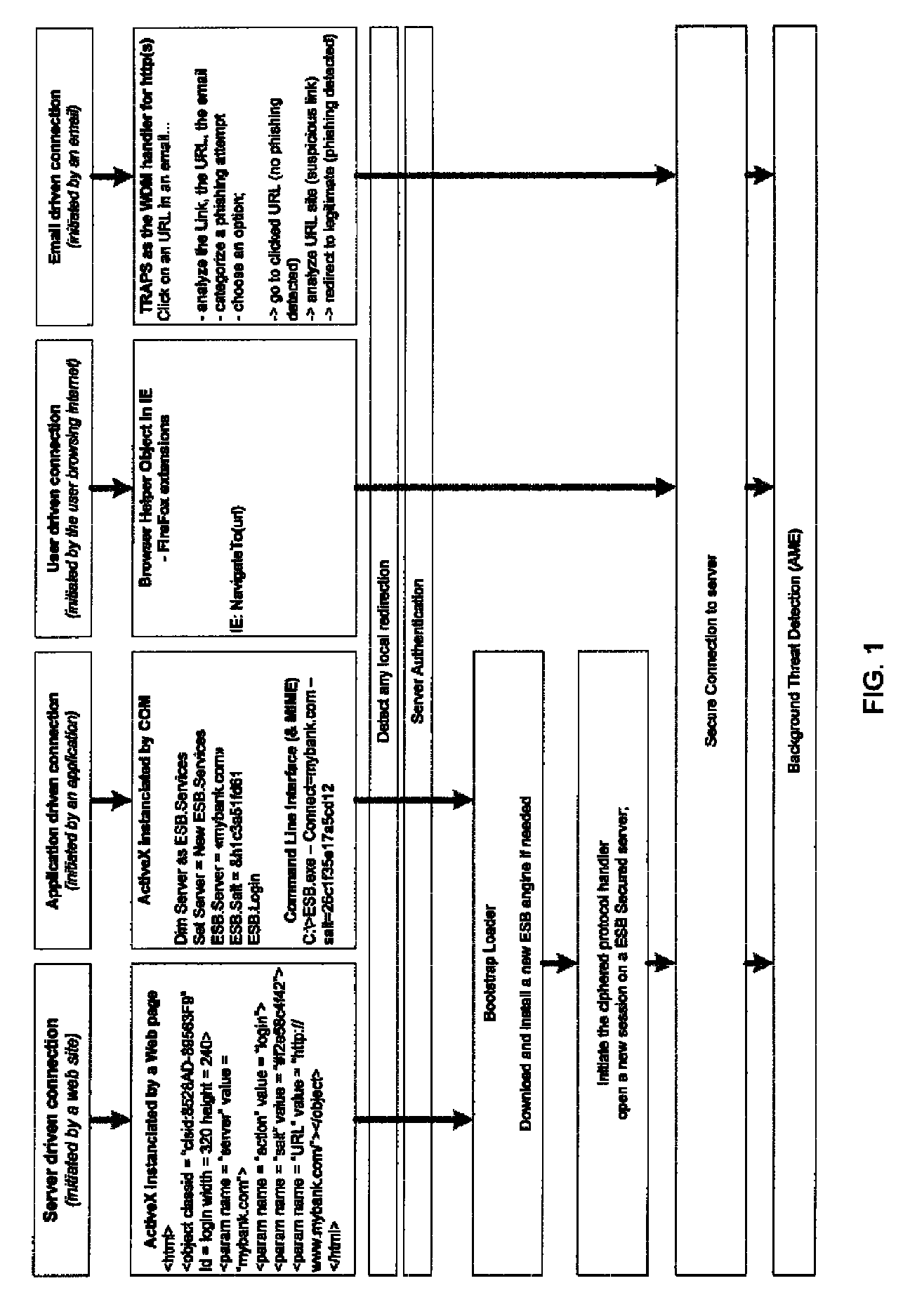
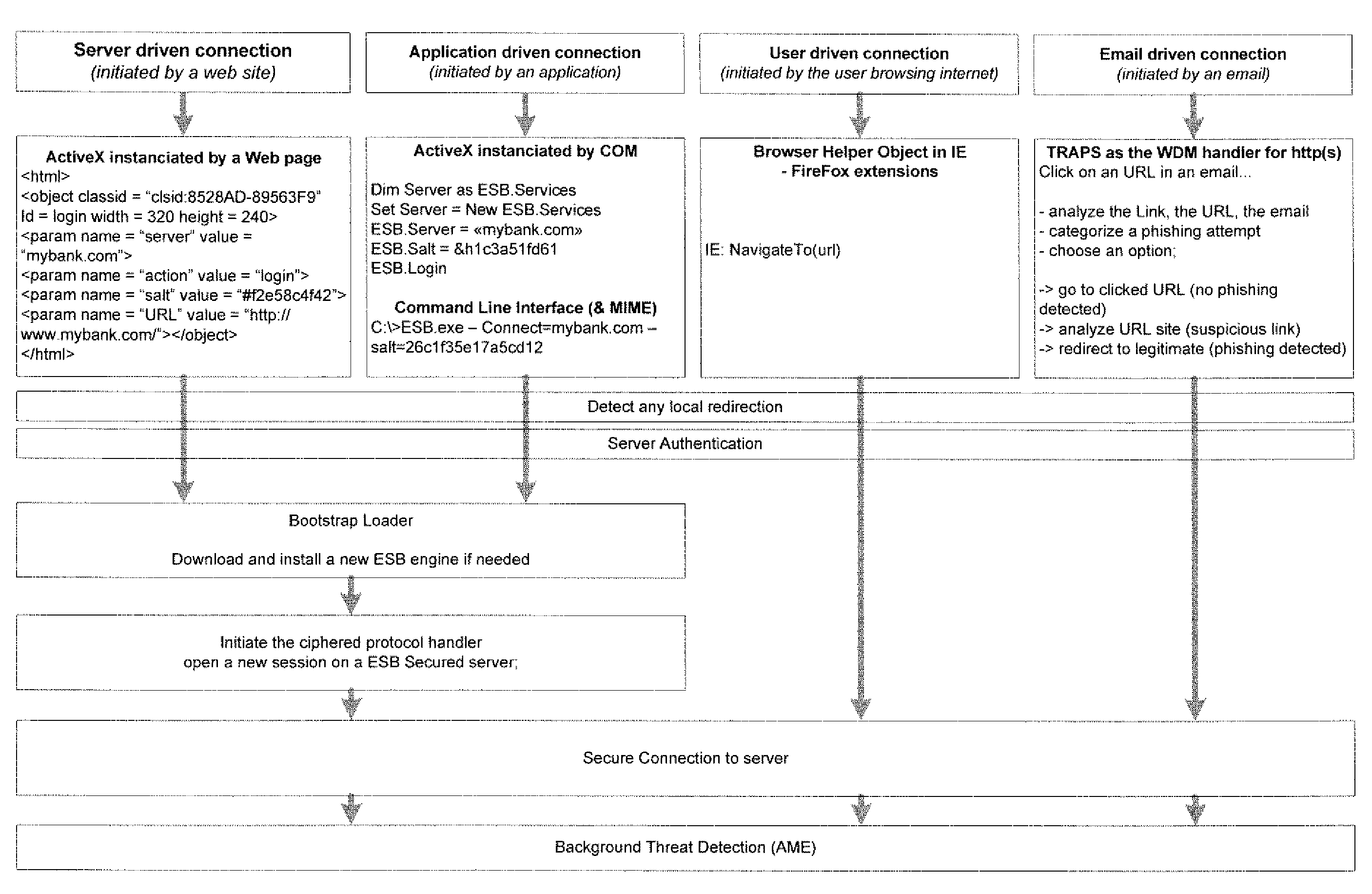
System and method for authentication, data transfer, and protection against phishing
ActiveUS8578166B2Key distribution for secure communicationDigital data processing detailsElectronic communicationStructure of Management Information
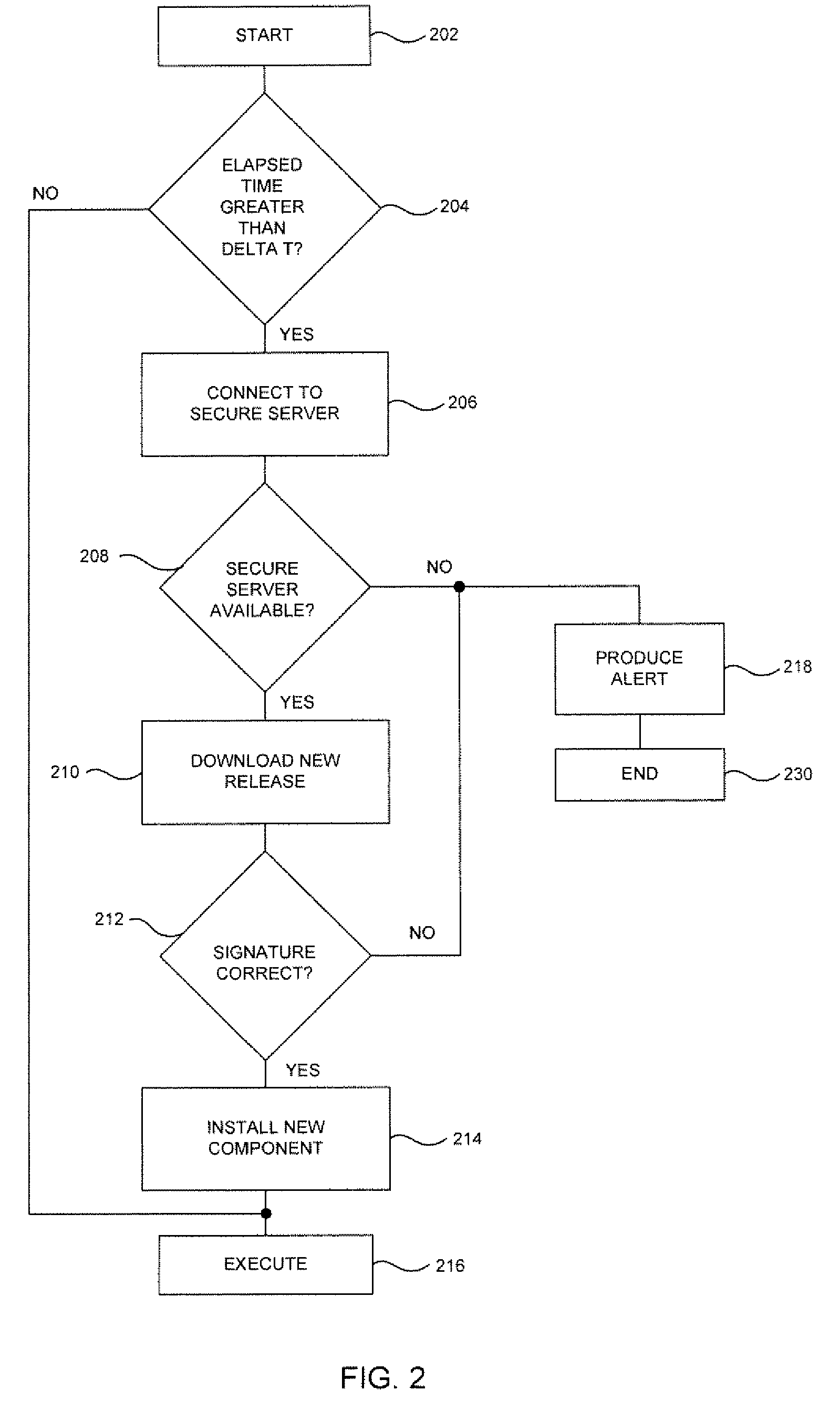
Methods and systems for secure electronic data communication over public communication networks. A secure data communication component may be utilized to implement a communication protocol. New versions of the data communication component may be generated, with each version containing a different communication protocol. Source code of the data communication component may be modified using a polymorph engine to create a functionally-equivalent component having a different code structure. An anti-phishing component may intercept a link in an electronic communication activated by a user, analyze the link and the electronic communication, determine a phishing risk to the user posed by the link, and direct the user to a location indicated by the link or redirect the user to a valid location. A server authentication component may detect and prevent DNS attacks, injections, and defacing activities.
Owner:MORGAMON
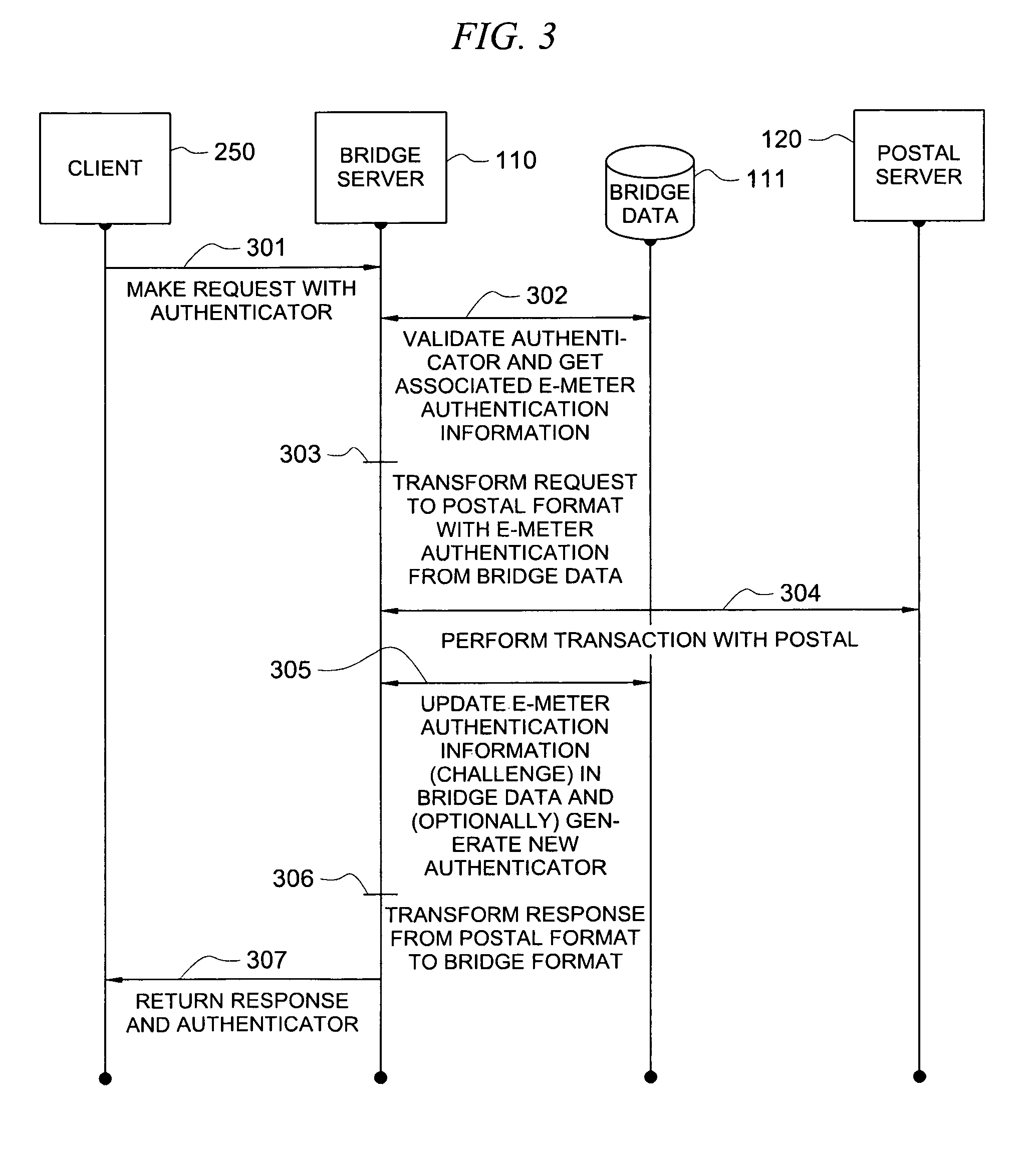
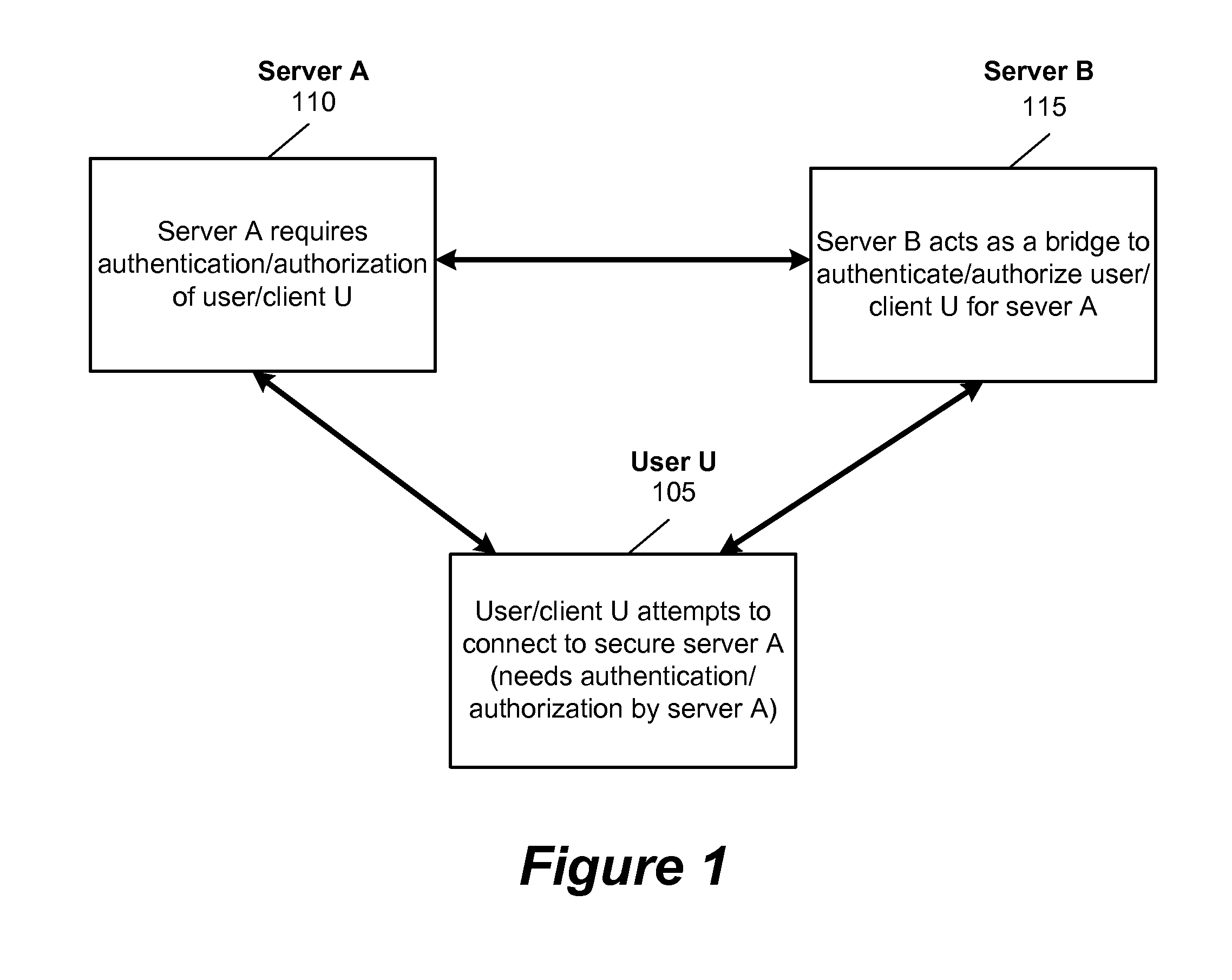
Secure application bridge server
ActiveUS8046823B1Easy to implementConvenient to accommodateDigital data processing detailsComputer security arrangementsApplication serverCryptographic protocol
Systems and methods are provided which implement a bridge server to provide user access to one or more secure applications. A bridge server of embodiments is disposed between a user and a secure application and invokes bridge server security protocols with respect to the user and secure application security protocols with respect to the secure application. In operation according to embodiments, client applications will link into a bridge server, the user will be authenticated by the bridge server, and a valid user will be correlated to an account of the secure application by the bridge server. Bridge servers of embodiments facilitate providing features with respect to secure application user access unavailable using the secure application security protocols.
Owner:AUCTANE INC
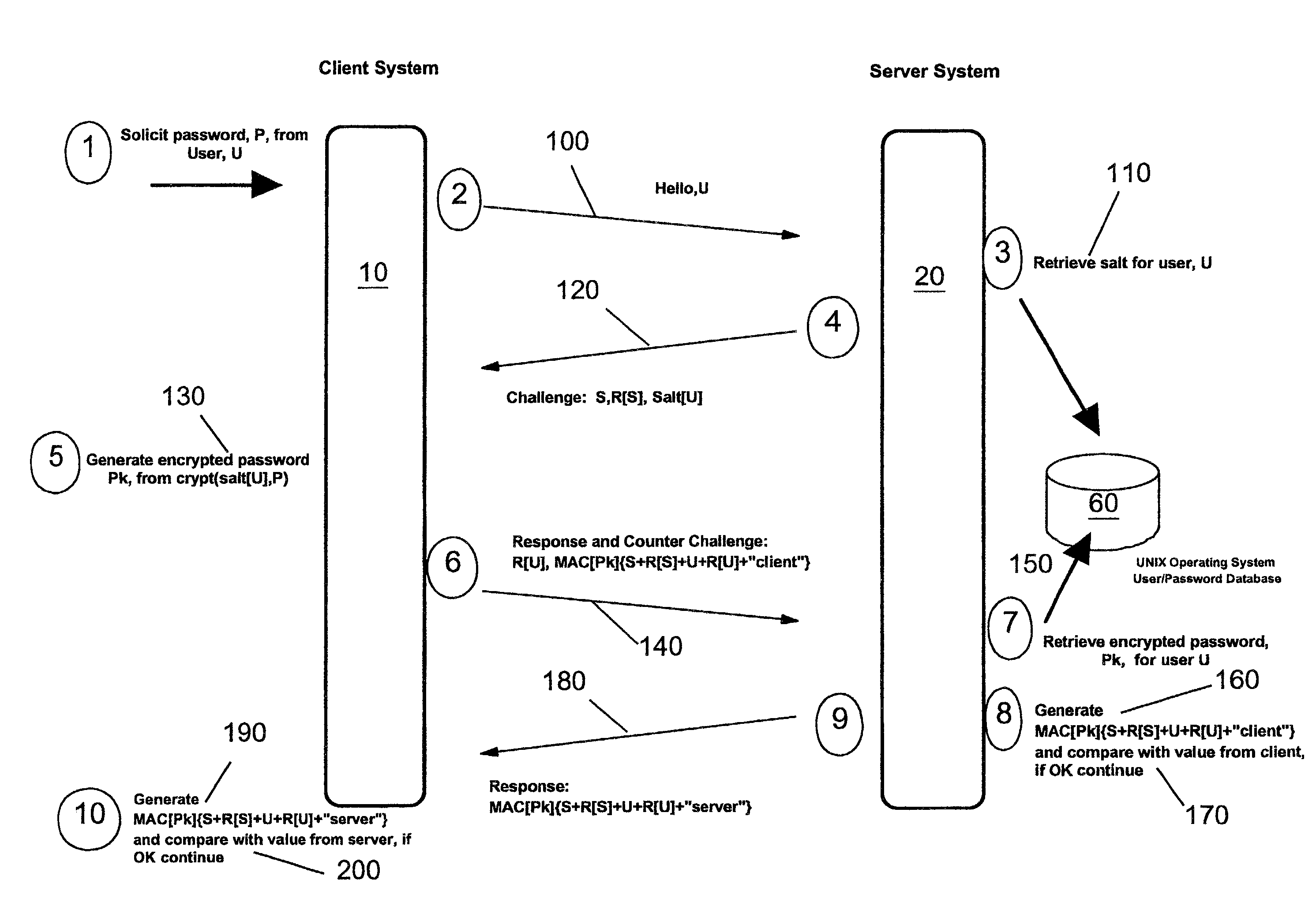
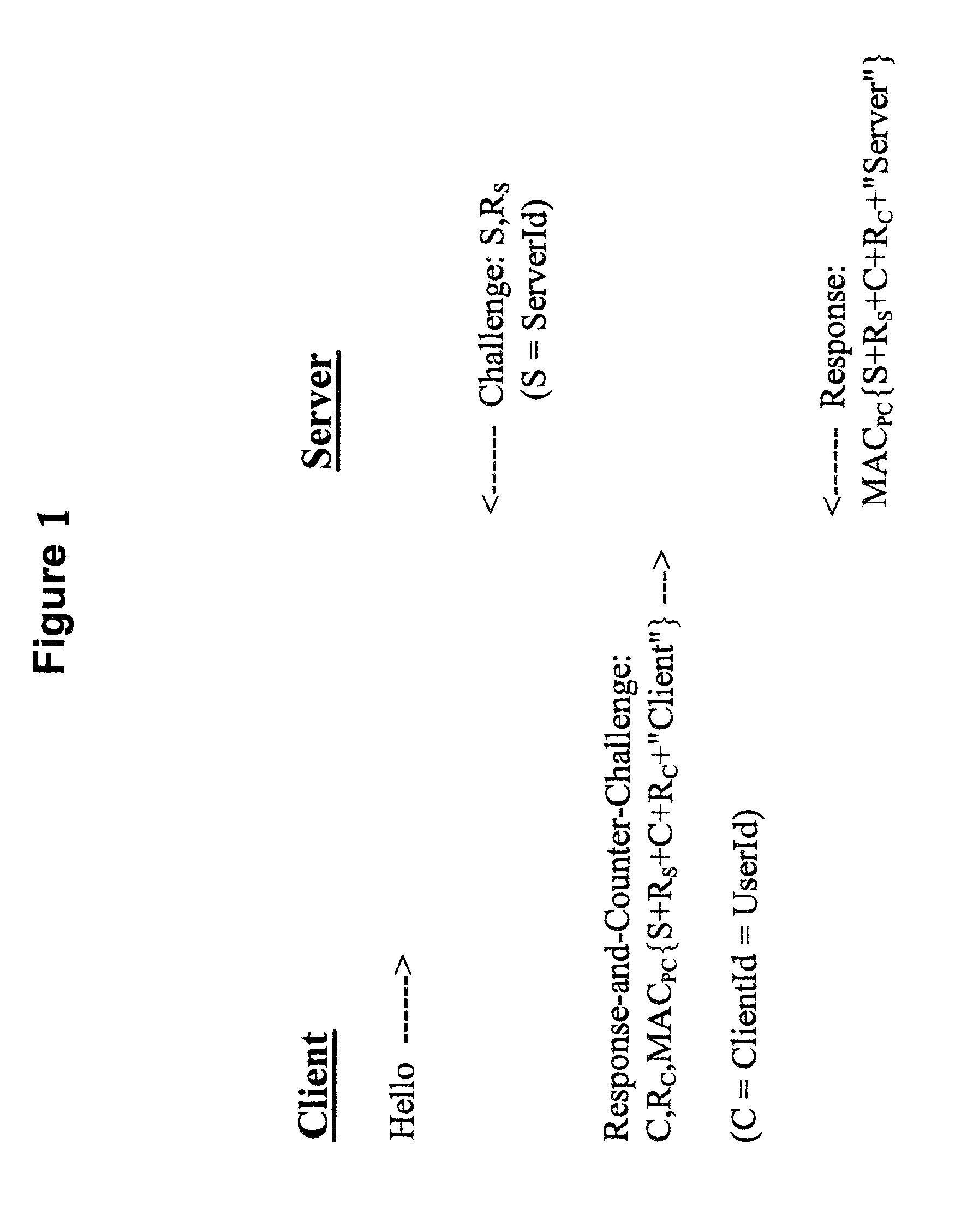
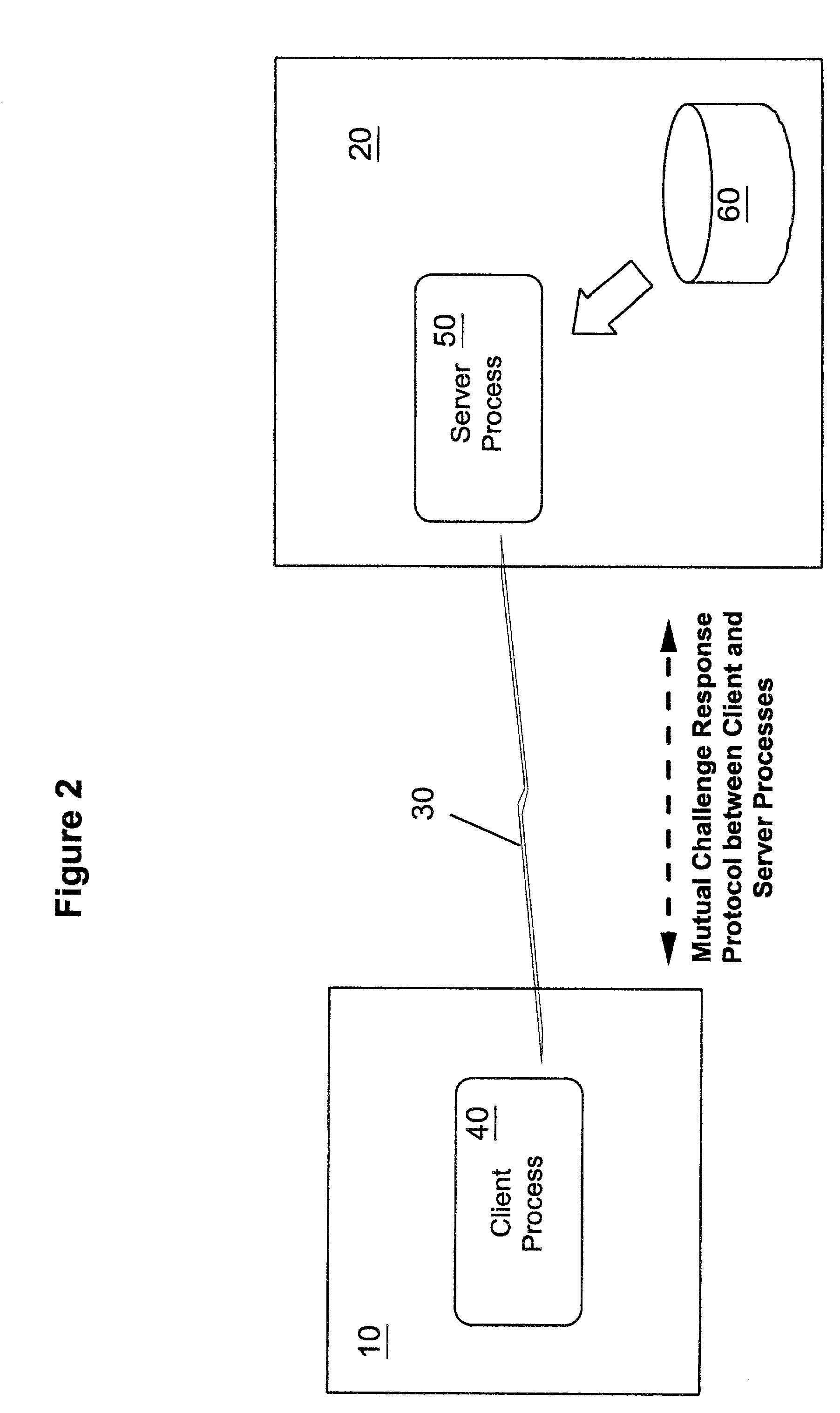
Methods, apparatus and computer programs performing a mutual challenge-response authentication protocol using operating system capabilities
InactiveUS20030093680A1Avoids security exposureMeet growth requirementsKey distribution for secure communicationDigital data processing detailsOperational systemCrypt
A client-server authentication method for use where a server process has access to a repository storing cipher-protected client passwords. The method includes applying the same cipher function to the client's copy of its password as was previously applied to generate the stored cipher-protected client passwords. This ensures that both the client and server have access to an equivalent cipher-protected client password-providing a shared secret for driving a mutual challenge-response authentication protocol without having to convert the password into cleartext at the server. The invention can be implemented without significant additional software infrastructure in a UNIX environment. Client passwords are typically stored in the UNIX password repository under the protection of the crypt( ) function applied to the combination of the password and a random number (a "salt'). By sending the salt to the client system together with the server's initial challenge of the authentication protocol, a process at the client is able to apply the crypt( ) function to the client password with the same salt such that the client and server have a shared secret for use as, or to generate, a common session key for the authentication.
Owner:IBM CORP
System and method for authentication, data transfer, and protection against phishing
ActiveUS20090077383A1Key distribution for secure communicationDigital data processing detailsElectronic communicationPhishing
Methods and systems for secure electronic data communication over public communication networks. A secure data communication component may be utilized to implement a communication protocol. New versions of the data communication component may be generated, with each version containing a different communication protocol. Source code of the data communication component may be modified using a polymorph engine to create a functionally-equivalent component having a different code structure. An anti-phishing component may intercept a link in an electronic communication activated by a user, analyze the link and the electronic communication, determine a phishing risk to the user posed by the link, and direct the user to a location indicated by the link or redirect the user to a valid location. A server authentication component may detect and prevent DNS attacks, injections, and defacing activities.
Owner:MORGAMON
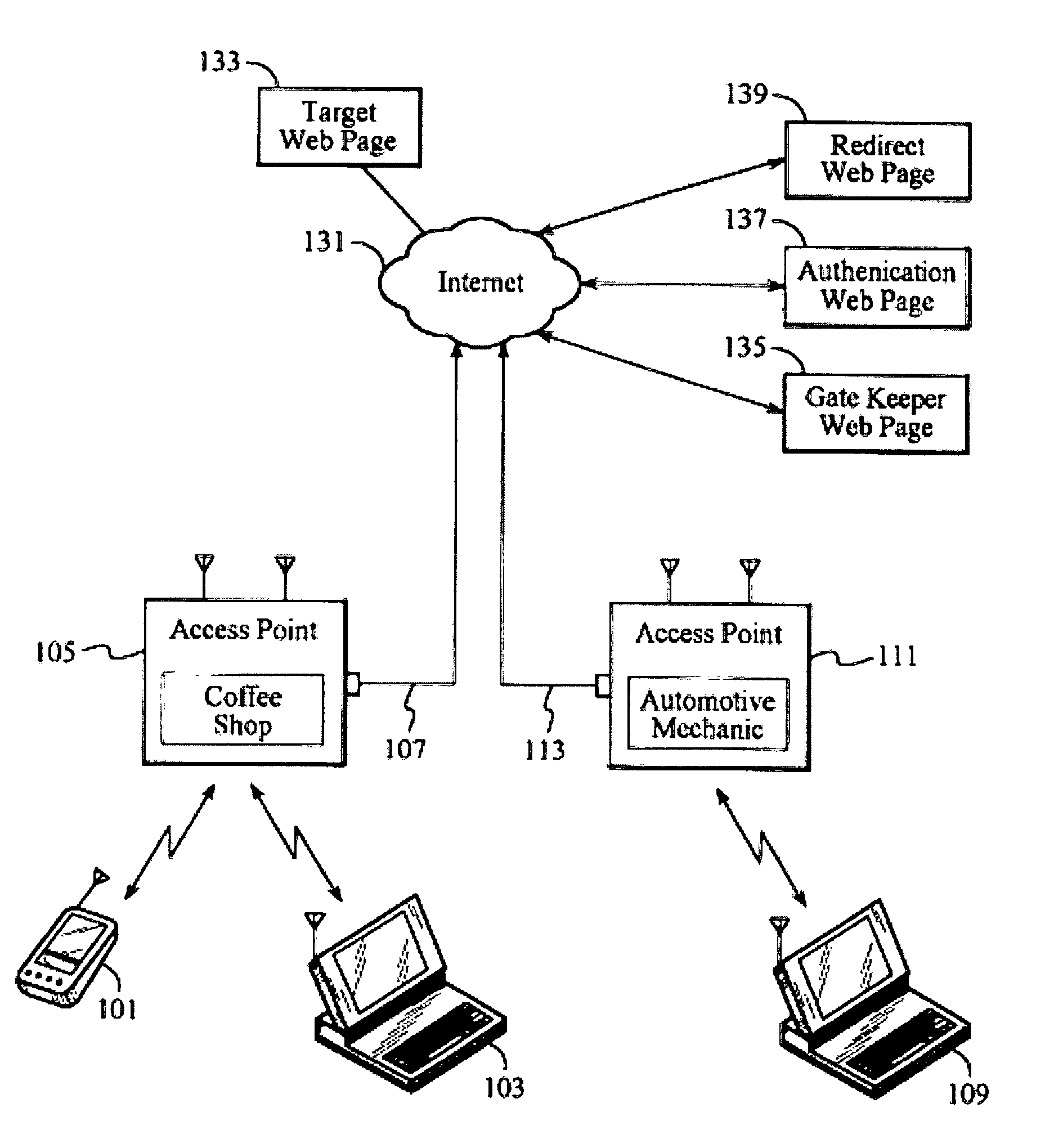
System for distributed network authentication and access control
InactiveUS7185360B1Facilitate wireless accessEasy accessError preventionFrequency-division multiplex detailsWeb authenticationGate-keeper
A user gains access to a private network by connecting to a network, either through a hardwired or wireless connection, and then initiates an Internet access request targeting any website. If the user is not already authorized for Internet access, then the user is sent to a first predetermined website that points the user to an authentication server accessible via the Internet. The authentication server sends the user an HTTP form pages requesting authentication information. When the user responds, a network monitoring device within the private network alters the form page to include the user's hardware address and an encoded ID based on the network's location. The authentication server forwards this data to a gate keeper server, which authenticates the new user and transmits an unblock message along with another encoded ID based on the network's location and the user's hardware address.
Owner:HEREUARE COMMUNICATIOINS
Secure internet applications with mobile code
InactiveUS6907530B2Easy accessUser identity/authority verificationUnauthorized memory use protectionThe InternetMobile code
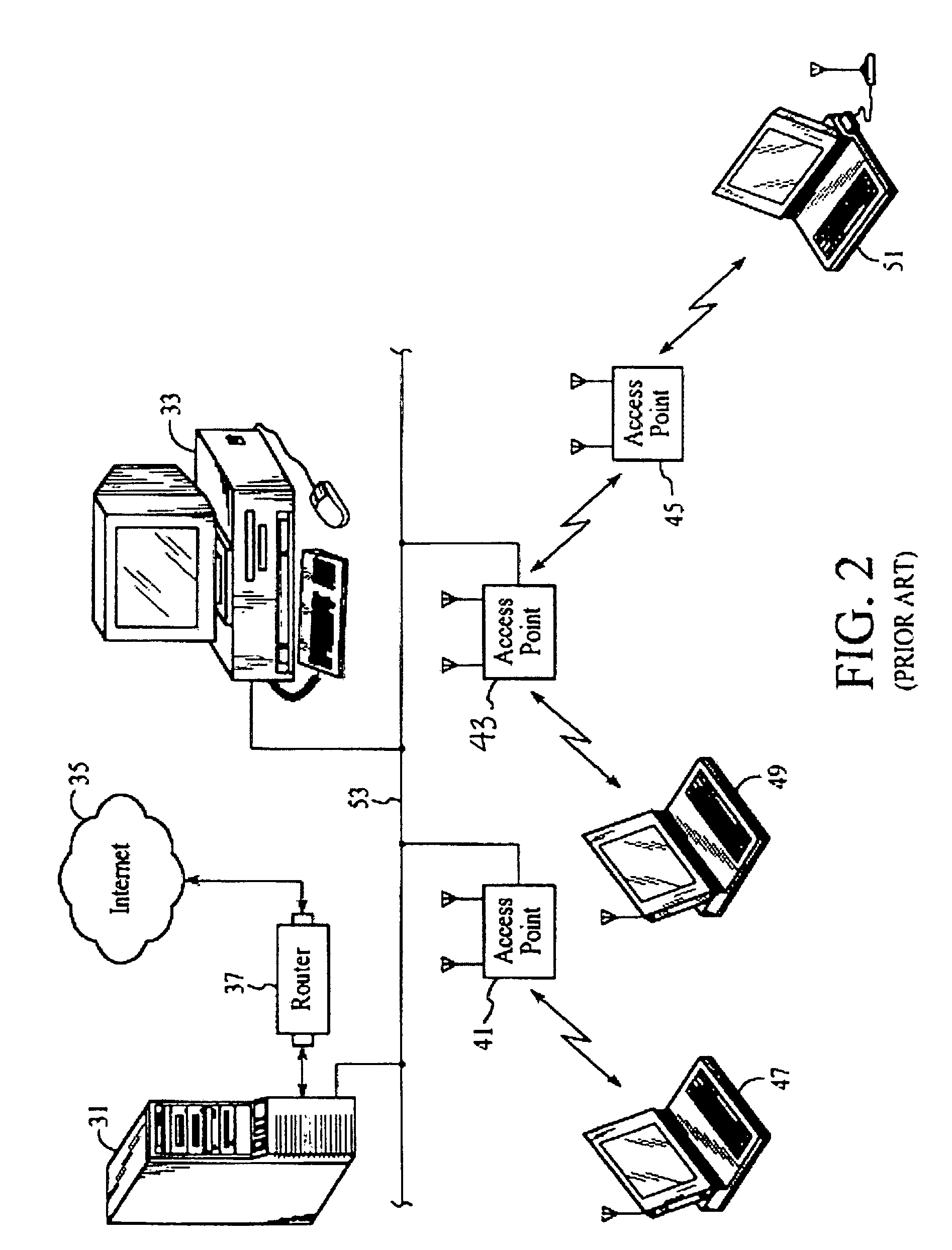
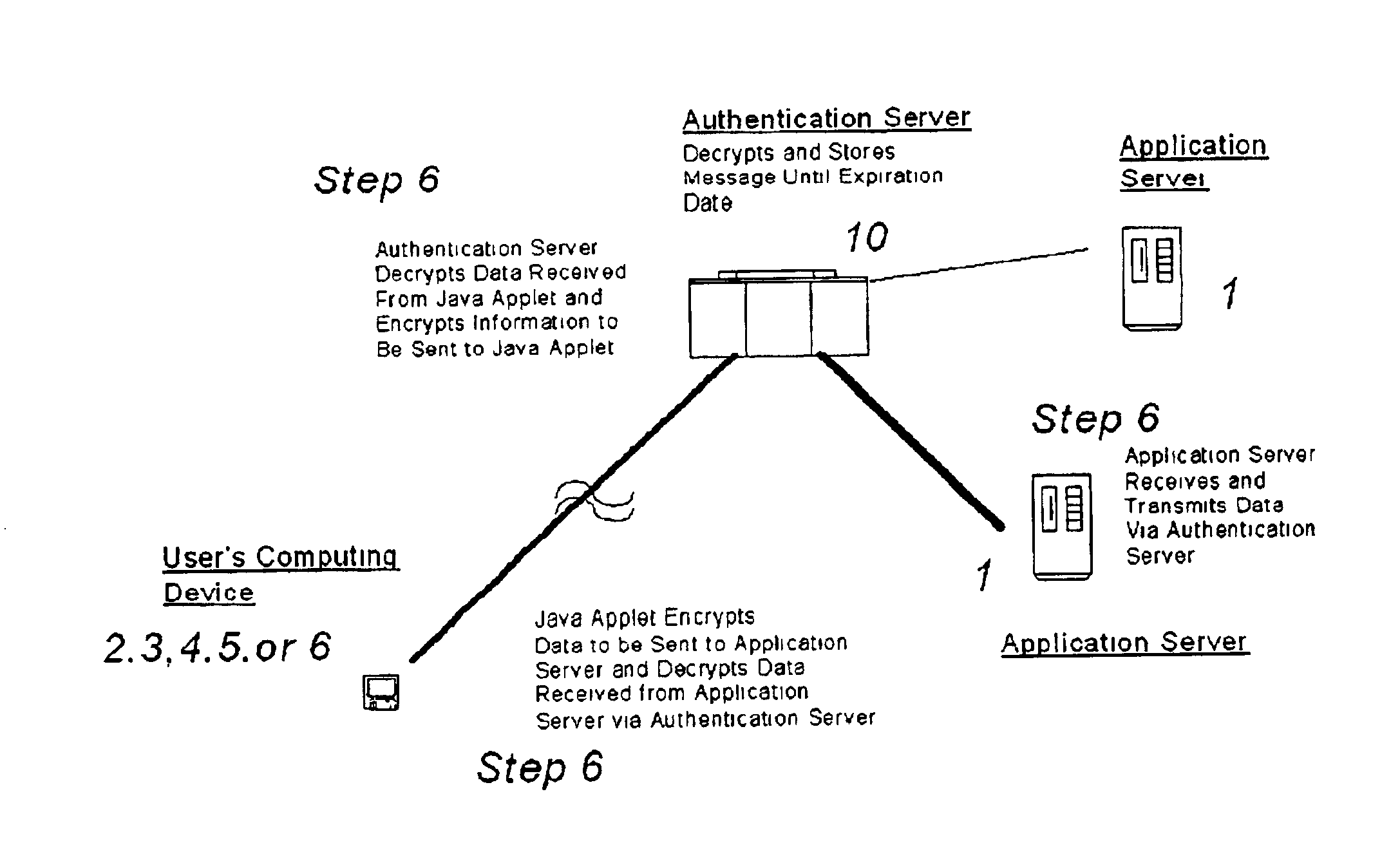
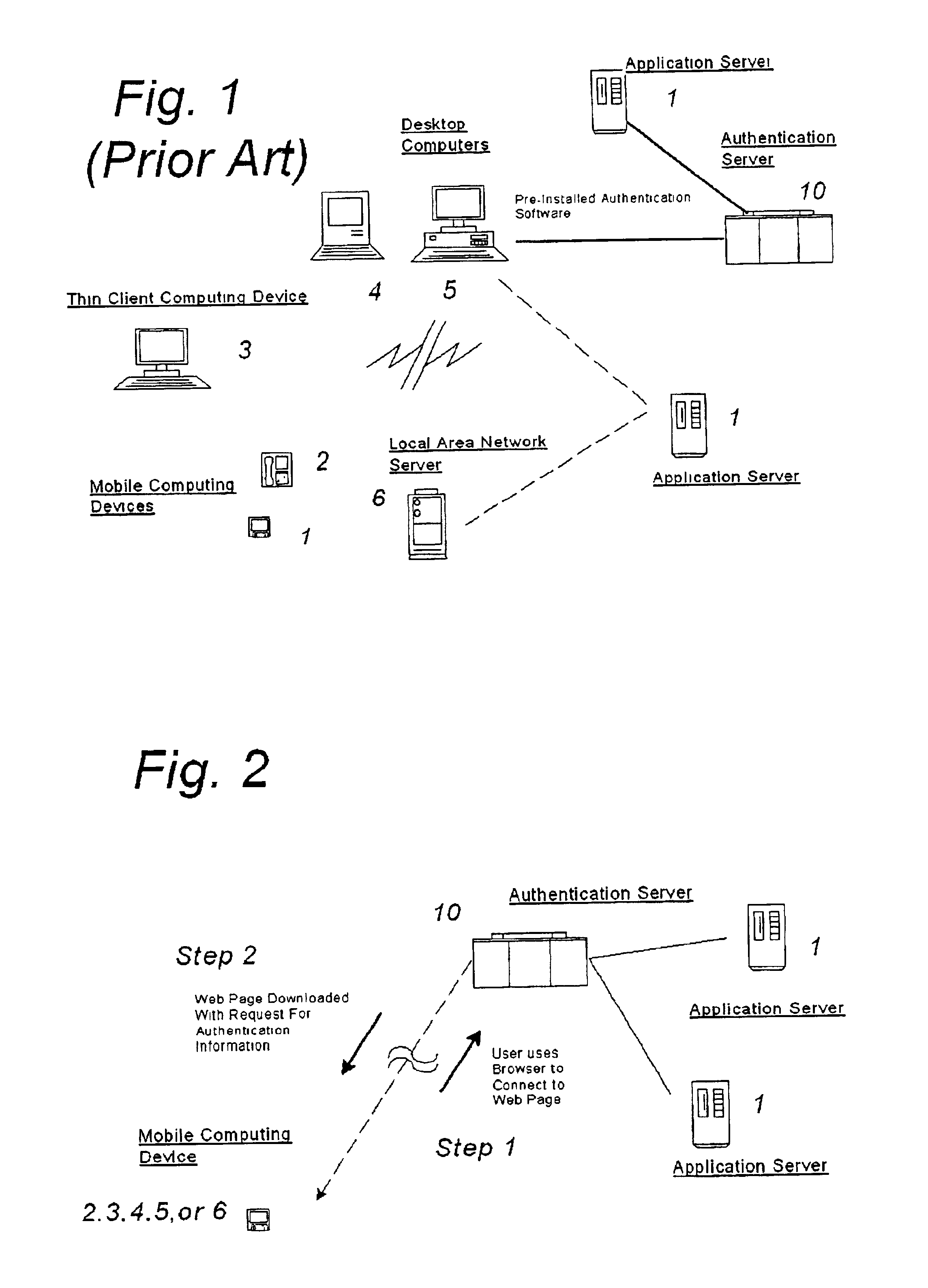
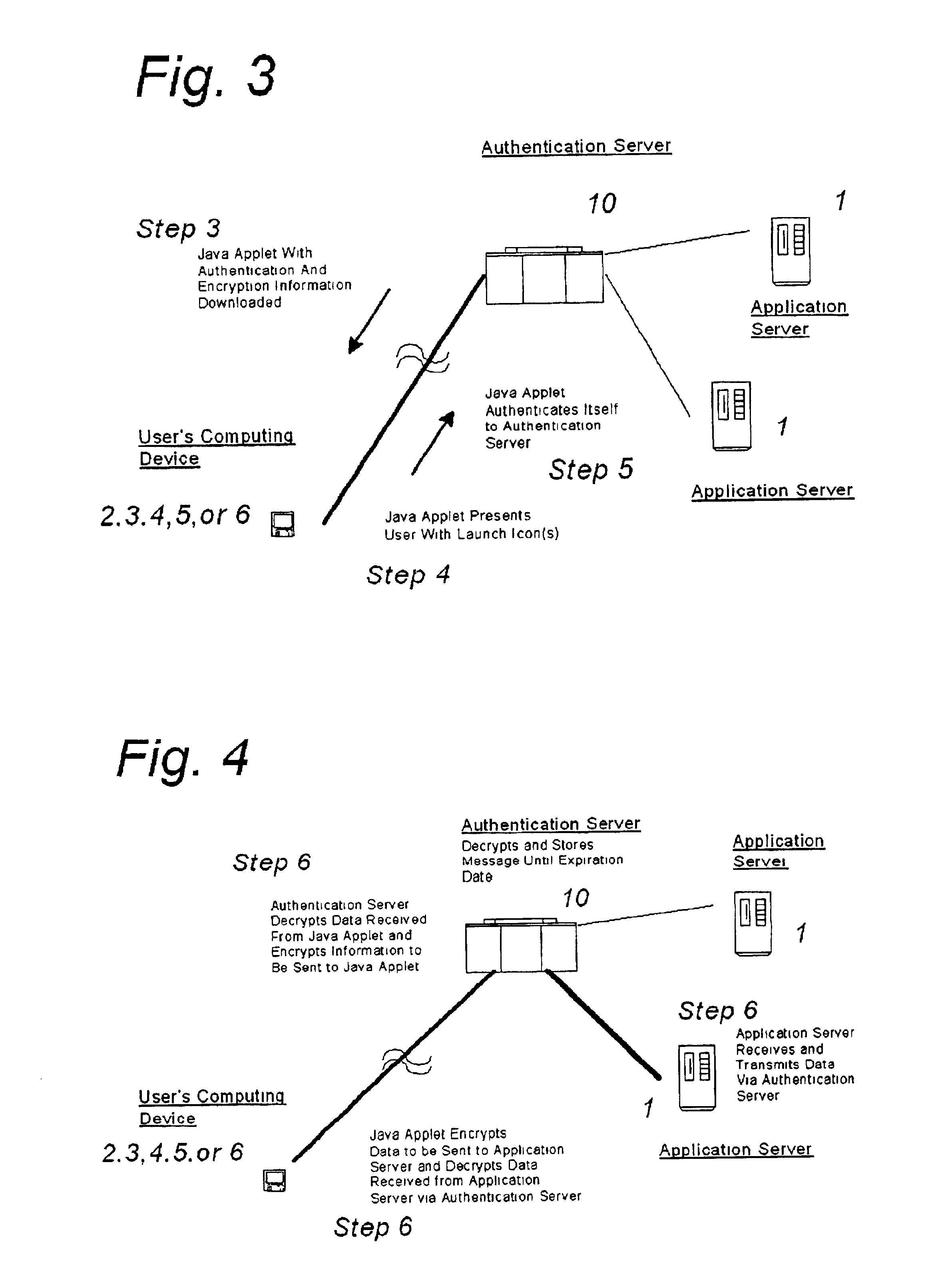
A system and method for securing pathways to a remote application server involves a gateway or authentication server, and a mobile code authentication and encryption client available for download from the gateway or authentication server. Upon connection of a user's computing device to the authentication server over the open network, the authentication server requests authentication information, such as a password, from the user, and upon authentication of the user by the authentication server, the authentication server downloads the mobile code authentication and encryption client to the user's computing device. The authentication and encryption client then authenticates itself to authentication server, after which a secure communications channel between the user's computing device and the authentication server is opened, the secure communications channel permitting transfer of data between the user's computing device and an application server. The system and method do not require pre-installation or any certificates or other authentication and encryption software on the user's computing device, enabling the system and method to be used with thin-client and mobile computing devices, as well as with conventional computers.
Owner:SSL SERVICES
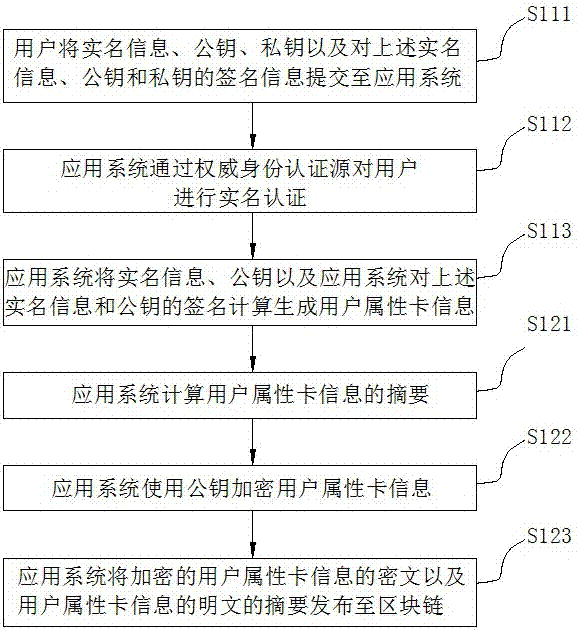
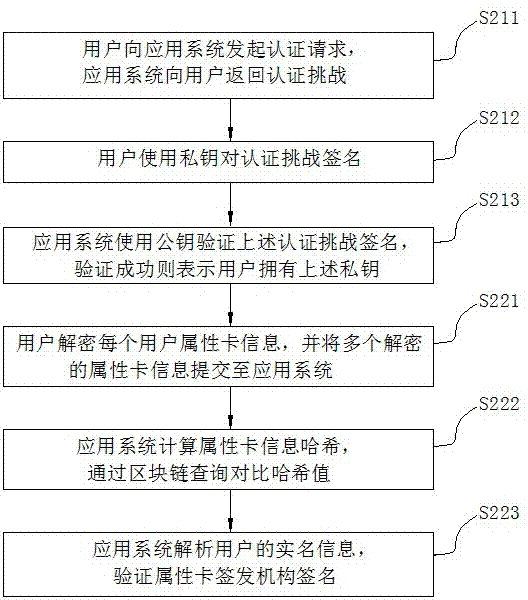
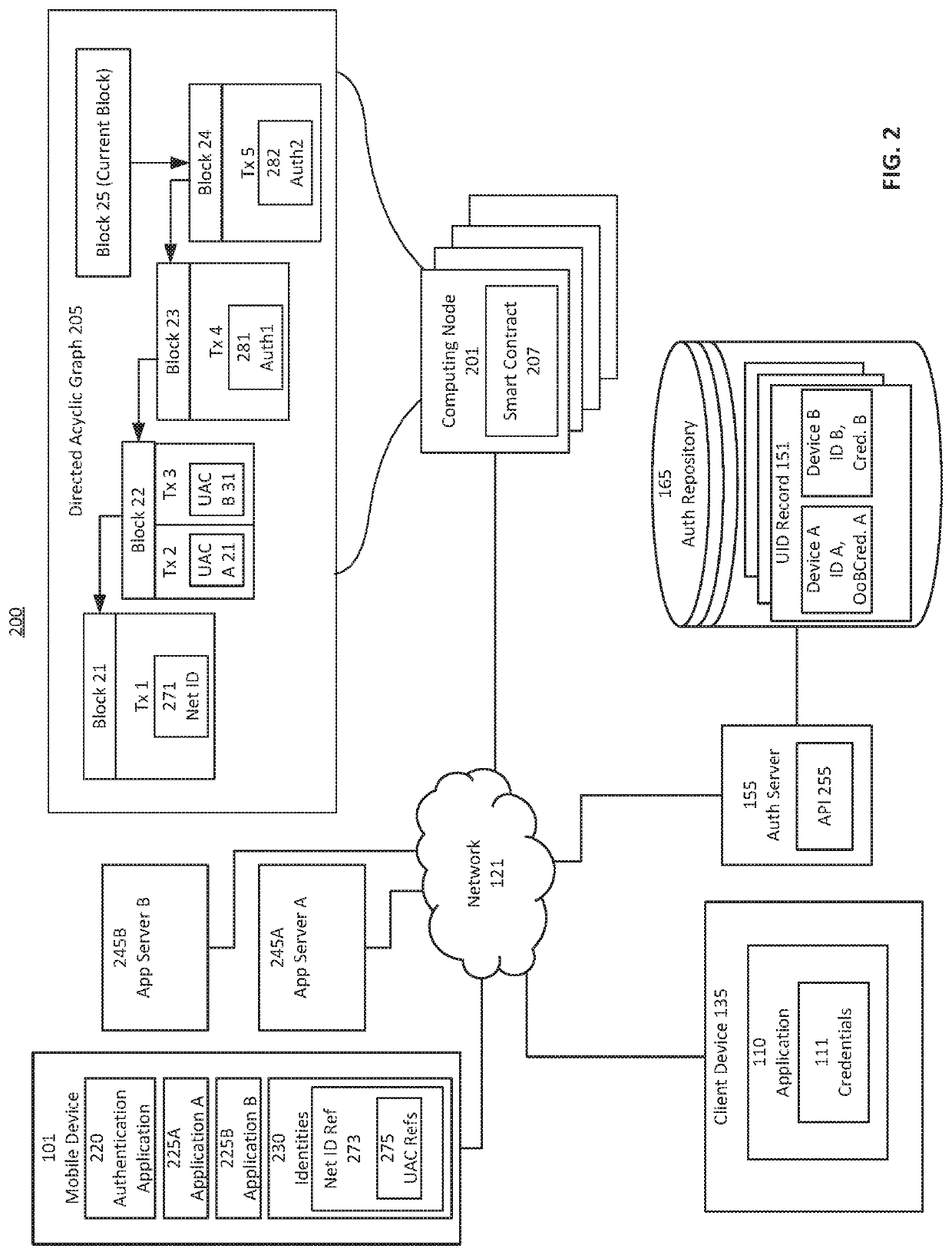
Multi-party trusted identity authentication method and system based on block chain
ActiveCN107196966AEnsure authenticityClear and unambiguous identityKey distribution for secure communicationMultiple keys/algorithms usageApplication serverThe Internet
The invention discloses a multi-party trusted identity authentication method and system based on a block chain, and belongs to the field of Internet identity authentication. The technical problem to be solved is to realize identity authentication of a user in a plurality of application systems based on the block chain, securely store the user information in the identity authentication process through the block chain and really and completely verify the user identity. The method comprises the following steps: an application system generates user attribute card information according to a received registration request, encrypts the user attribute card information and issues the user attribute card information to the block chain, wherein a plurality of application systems are provided, and the encrypted user attribute card information corresponding to each application system is stored in the block chain; each application system verifies the user identity based on the block chain. The system structurally comprises a block chain network, a client authentication module configured in a client and an application server authentication module configured in the application system. By adoption of the multi-party trusted identity authentication method and system, the real name information of the user is stored in the block chain securely and reliably, and the identity authentication of the user is implemented really and completely through the block chain.
Owner:北京信任度科技有限公司
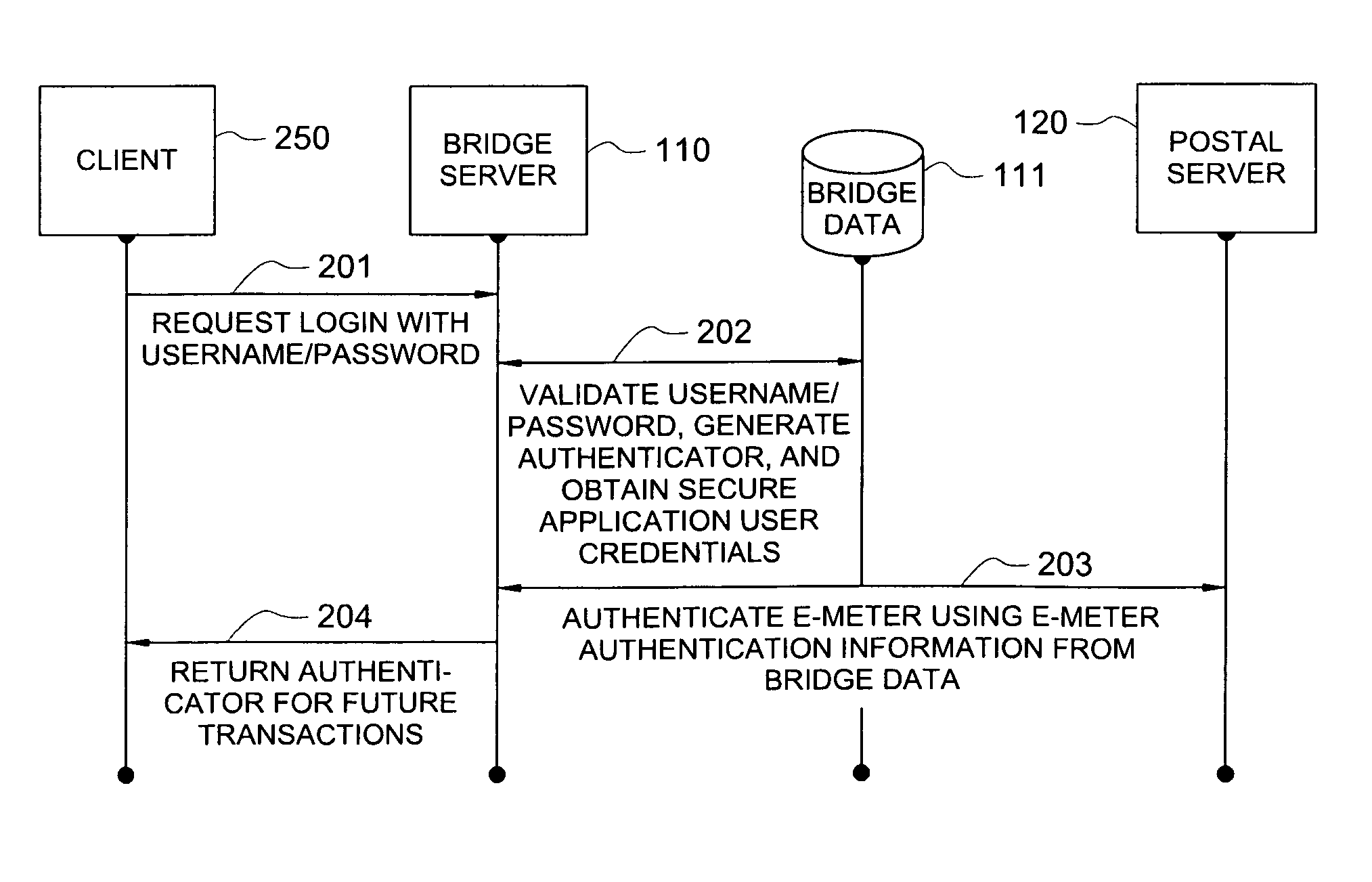
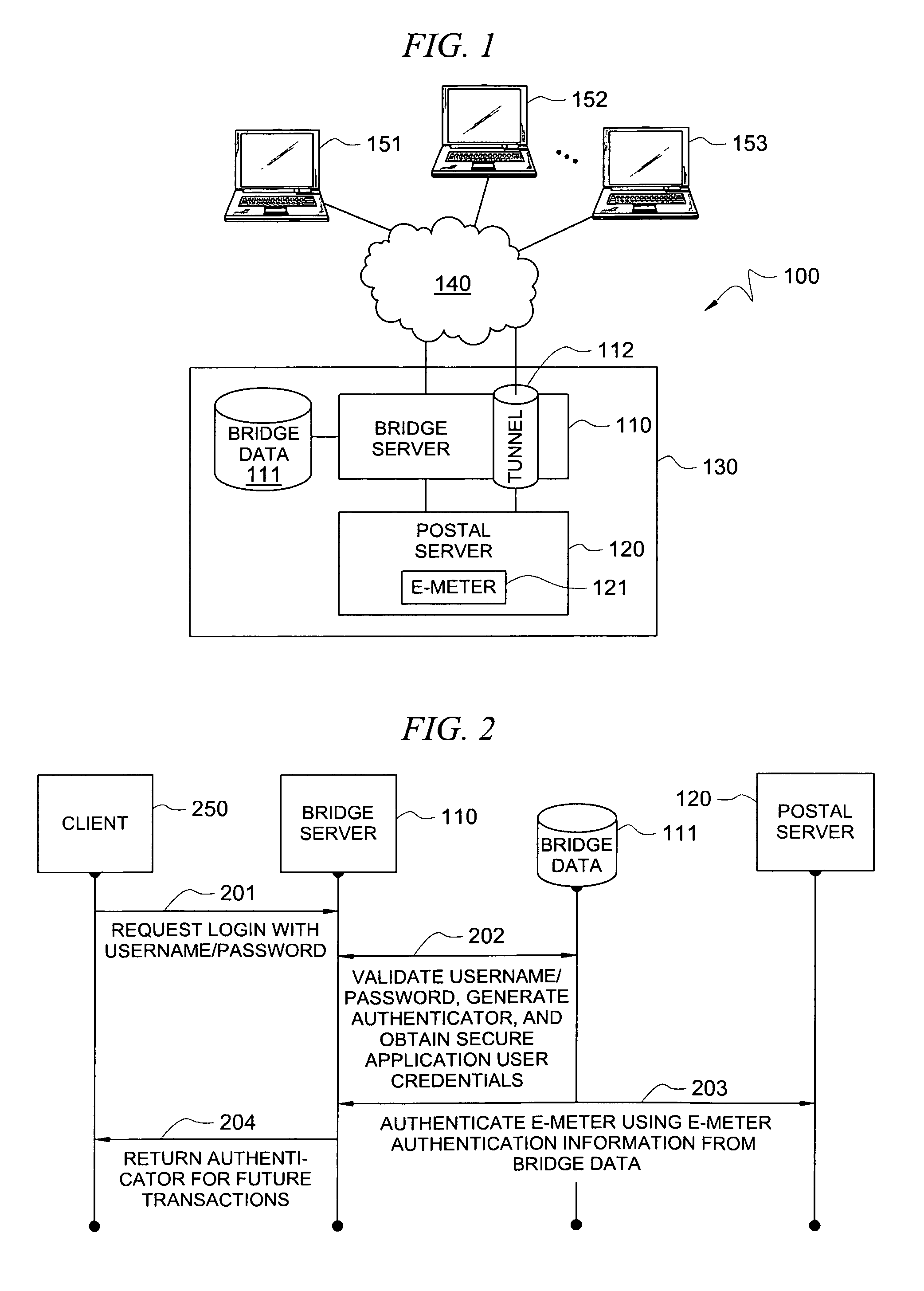
Method and system for improved security
ActiveUS20120144464A1Low costEasy to useDigital data processing detailsUser identity/authority verificationCredit cardPassword
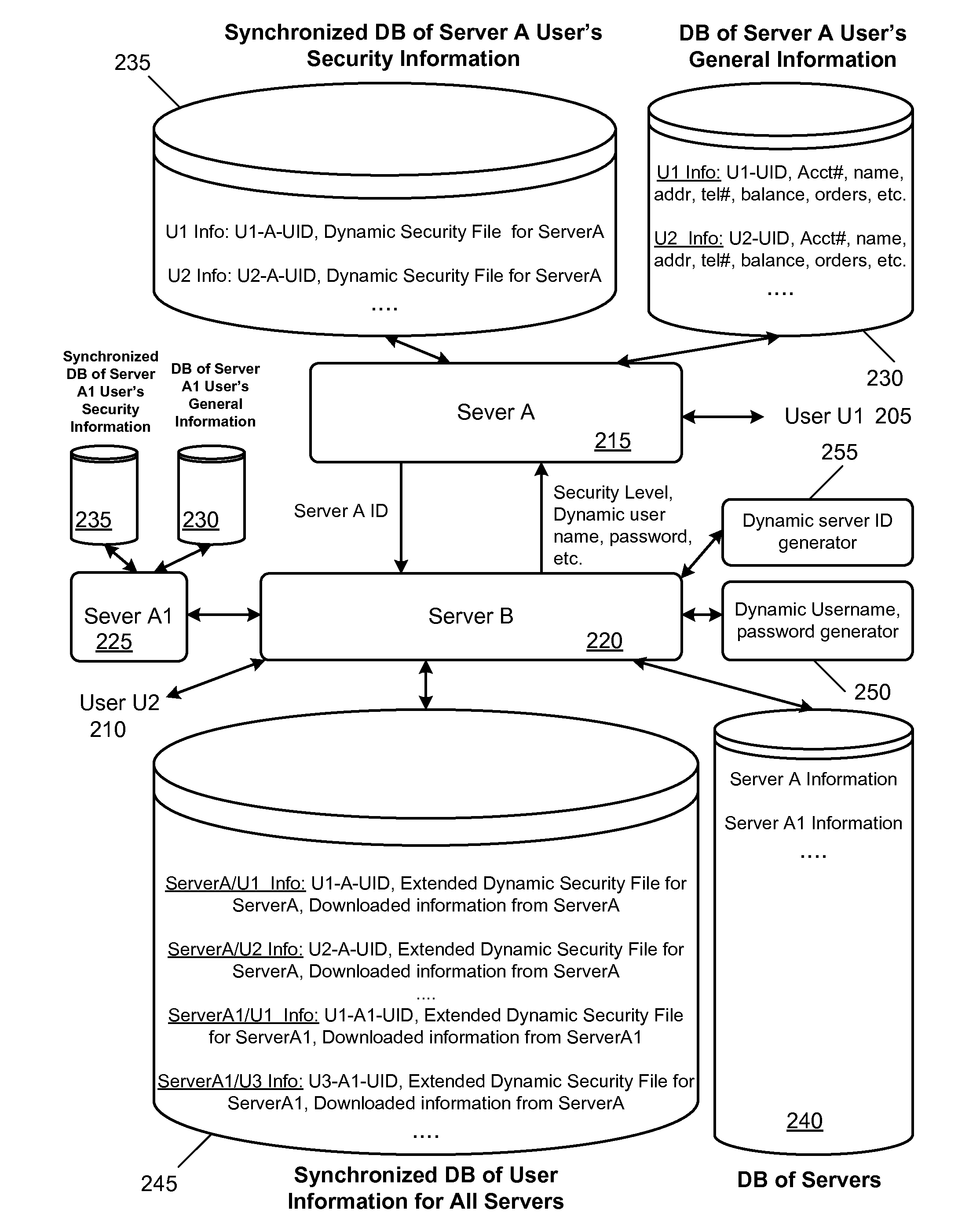
An improved authentication method and system is provided where a user securely accesses a variety of target servers for online email, online banking, credit card purchases, ecommerce, brokerage services, corporate databases, and online content (movies, music and software). The method involves a bridge server performing authentication tasks that allow a user to access a server or a group of servers with multiple security levels. The method eliminates the need for the user to remember multiple usernames / passwords for each target server. The method also allows one bridge server and one set of security devices to be used to authenticate the user for multiple servers, thereby reducing security costs and increasing user convenience. A location-based password-ID generating device is also described for secure location-based access.
Owner:STRIPE INC
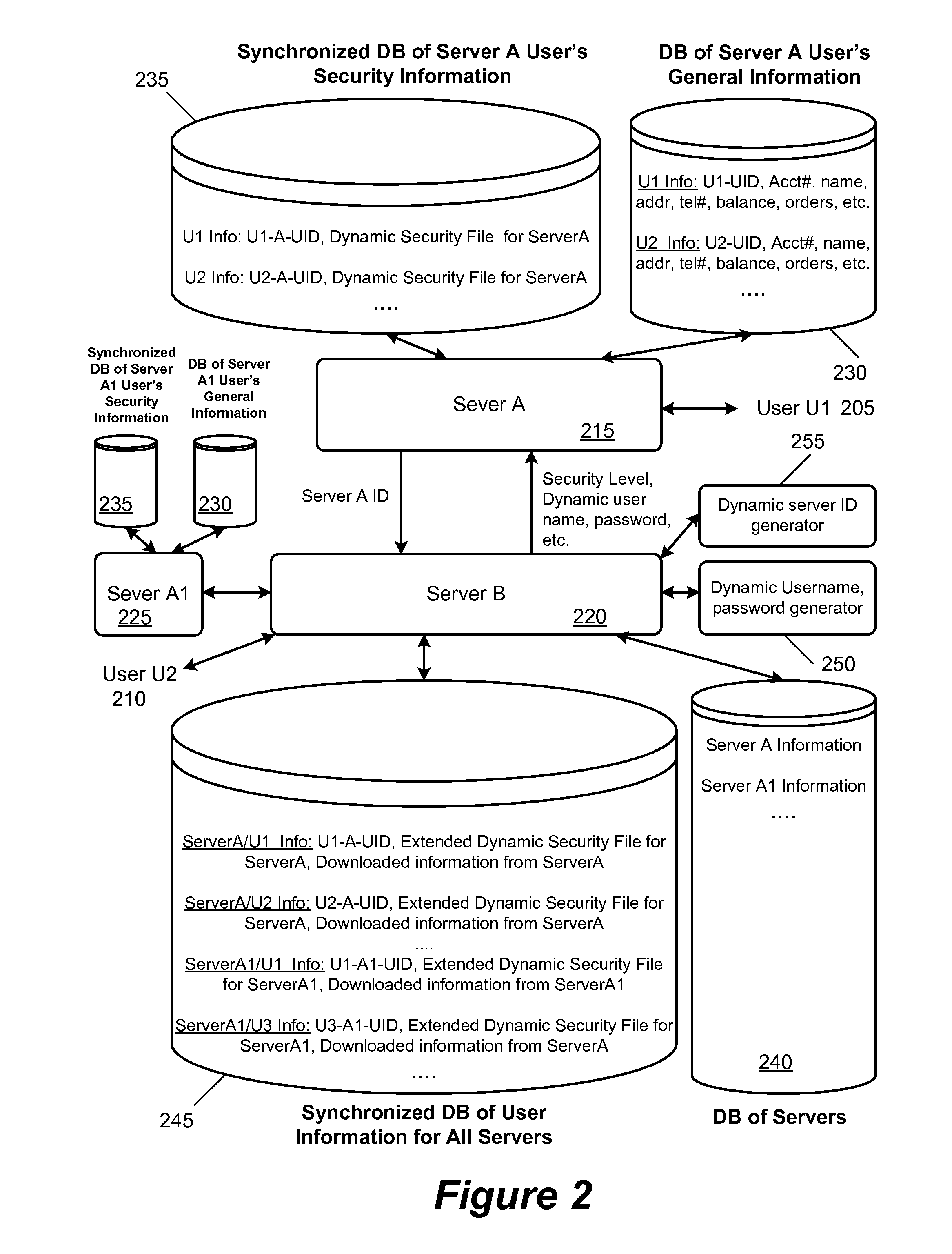
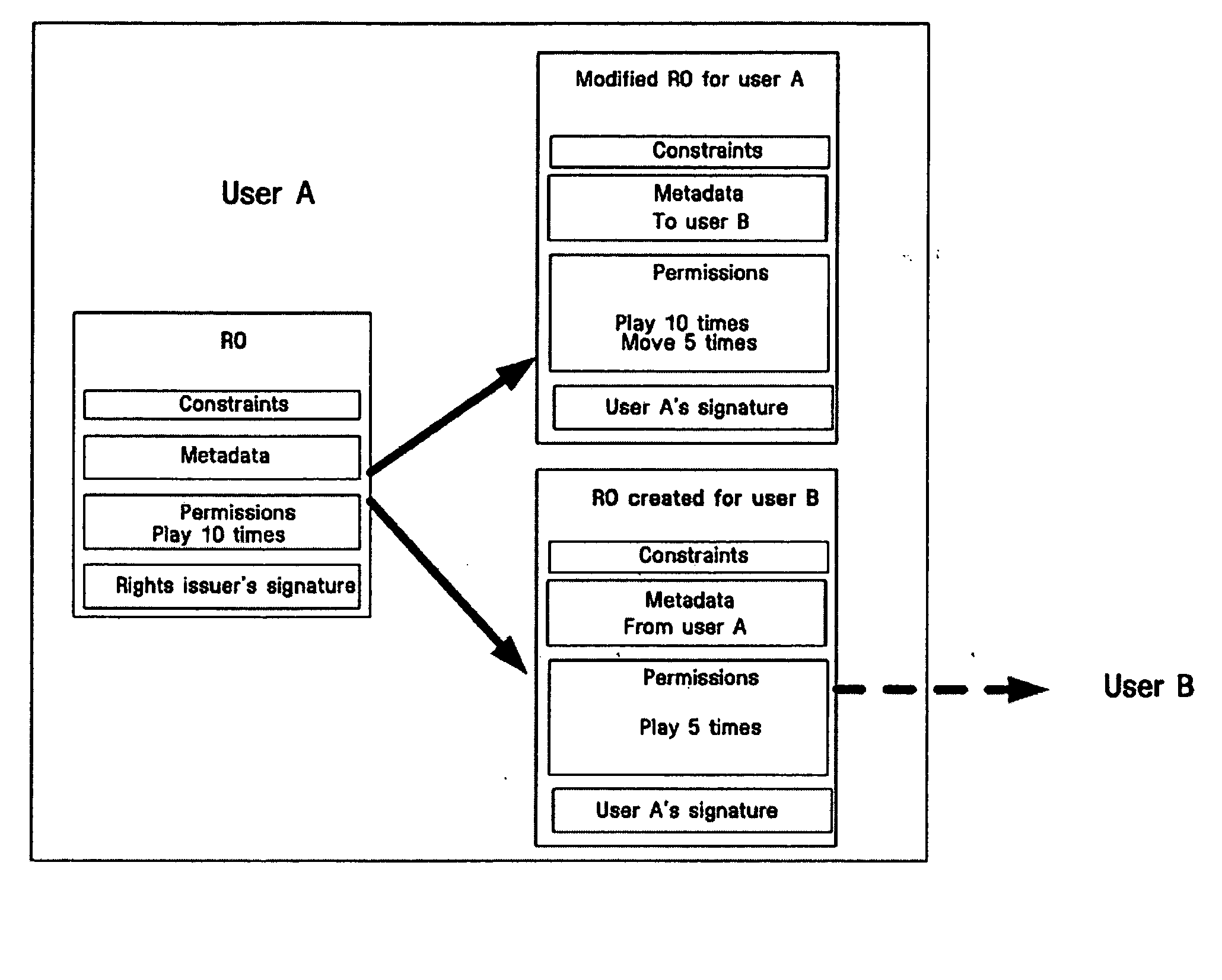
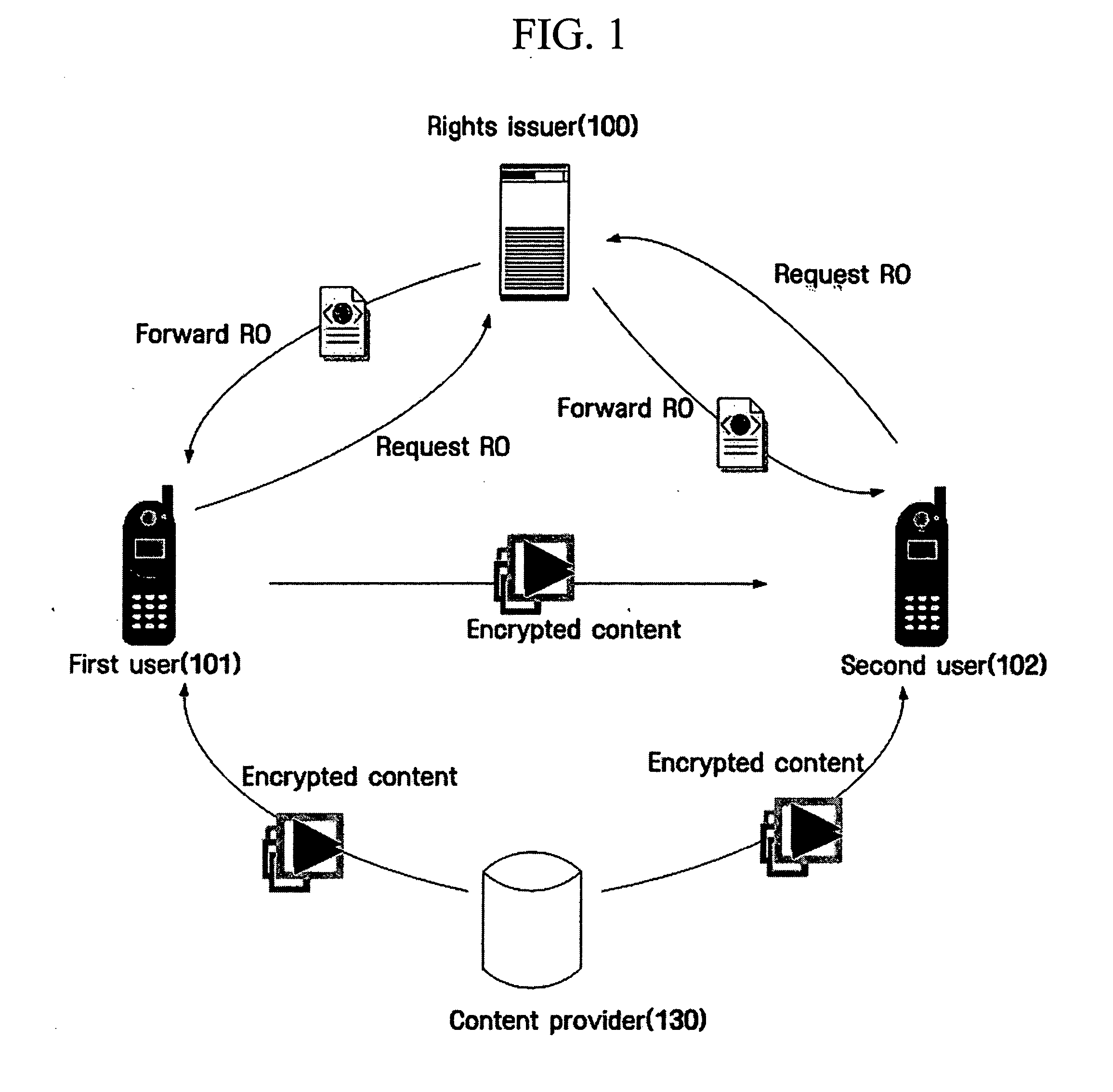
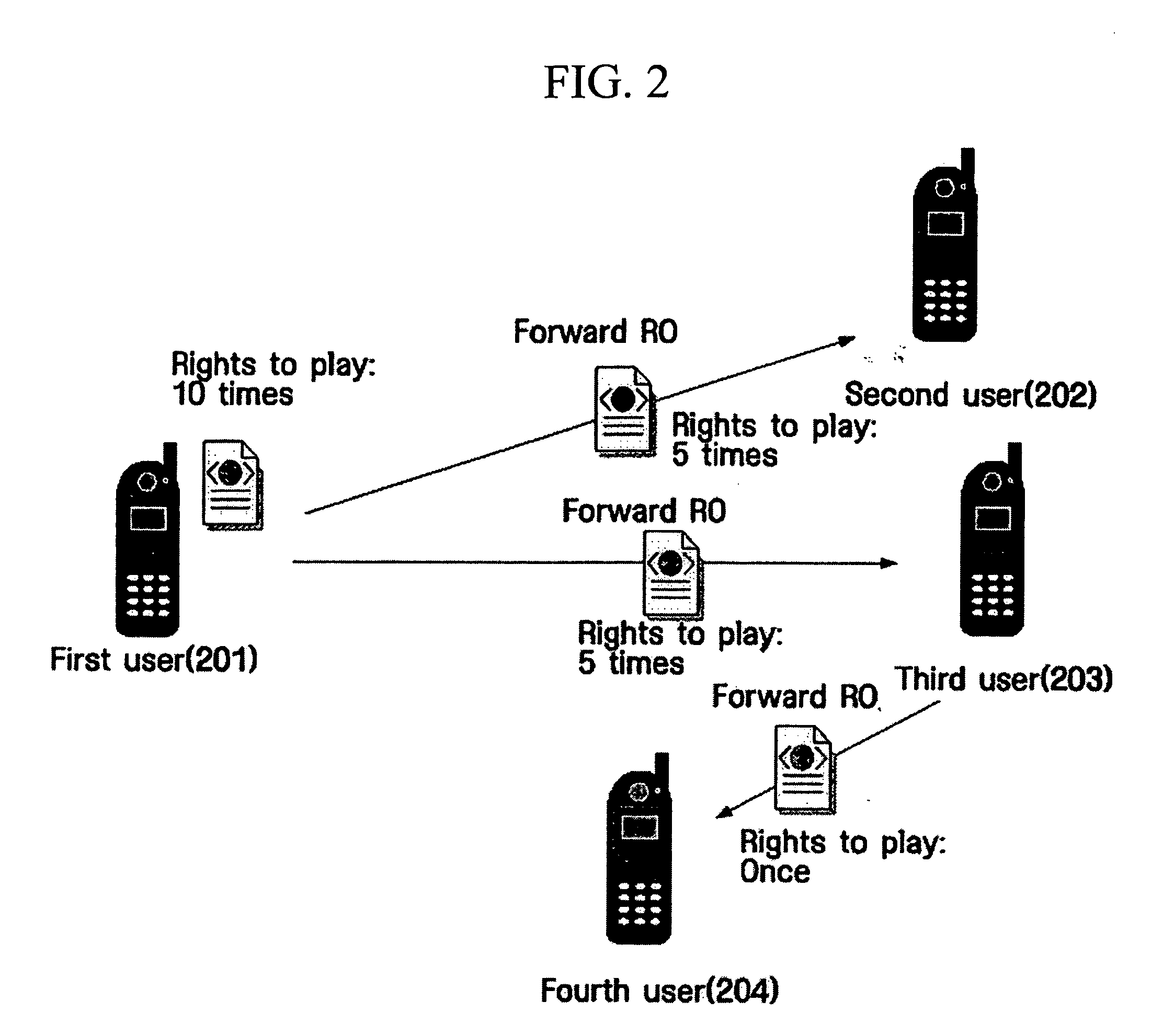
Method for sharing rights objects between users
InactiveUS20050044361A1Promote recoveryReduce processing loadAnalogue secracy/subscription systemsDigital data protectionServer authenticationWorld Wide Web
Provided is a method for delivering all or part of a rights object (RO) of a user associated with the content to other users. The method includes creating a rights object to be transmitted to a second user within a limit of the rights object held by the first user, and forwarding the created rights object to the second user. The method allows each user to share its own RO with other users within the limit of the RO without server authentication.
Owner:SAMSUNG ELECTRONICS CO LTD
Enhanced network server authentication using a physical out-of-band channel
InactiveUS20080091618A1Improve trustDigital data authenticationElectronic credentialsElectronic communicationE-commerce
Systems and methods for increasing user trust by authenticating an electronic commerce server over an electronic communications channel using information received through an out-of-band communication in a physical communications channel are described. In one configuration, a paper bill is sent to a user by physical mail delivery and it includes challenge and response data used to authenticate the electronic commerce server over the electronic communications channel.
Owner:PITNEY BOWES INC
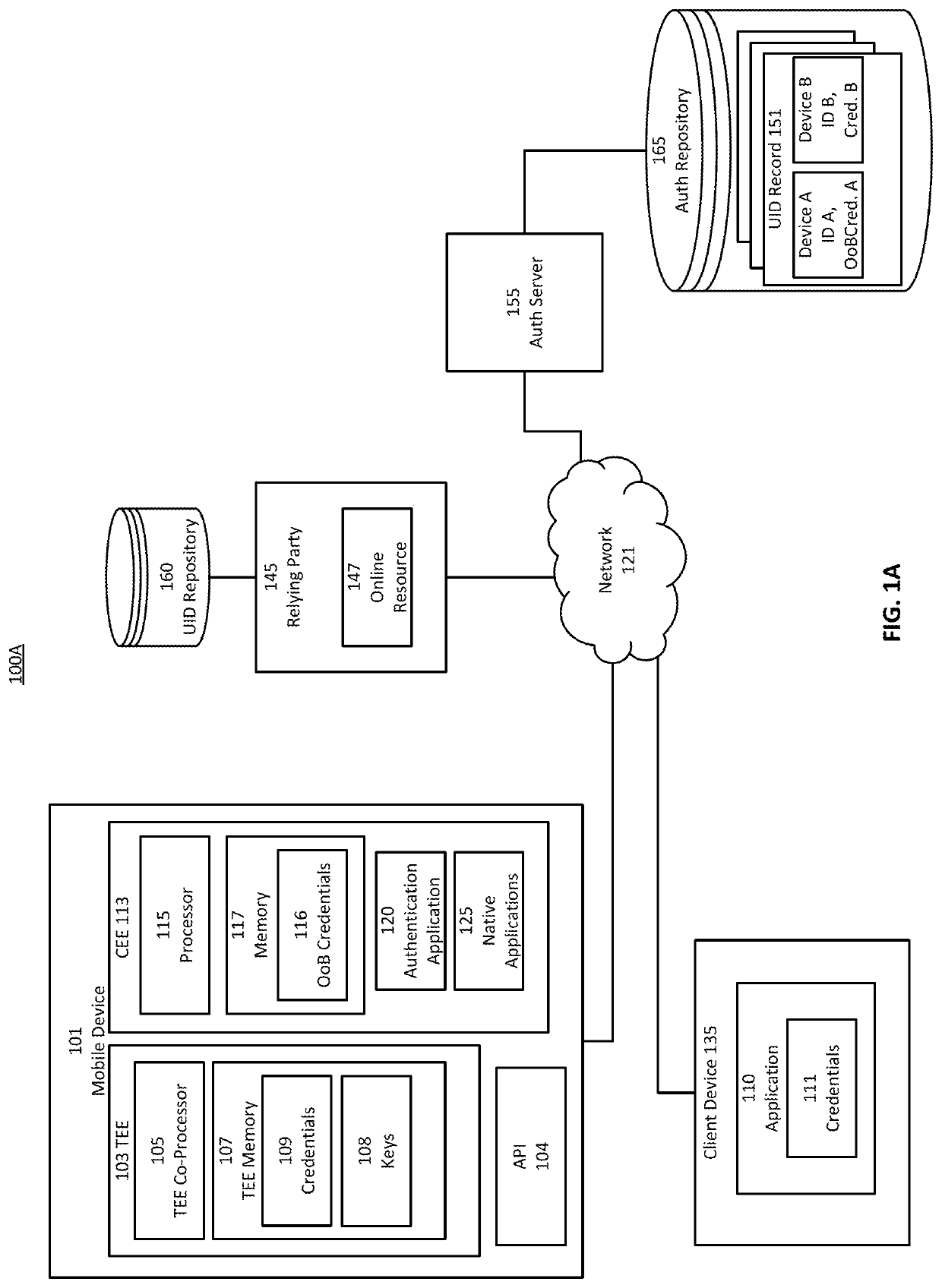
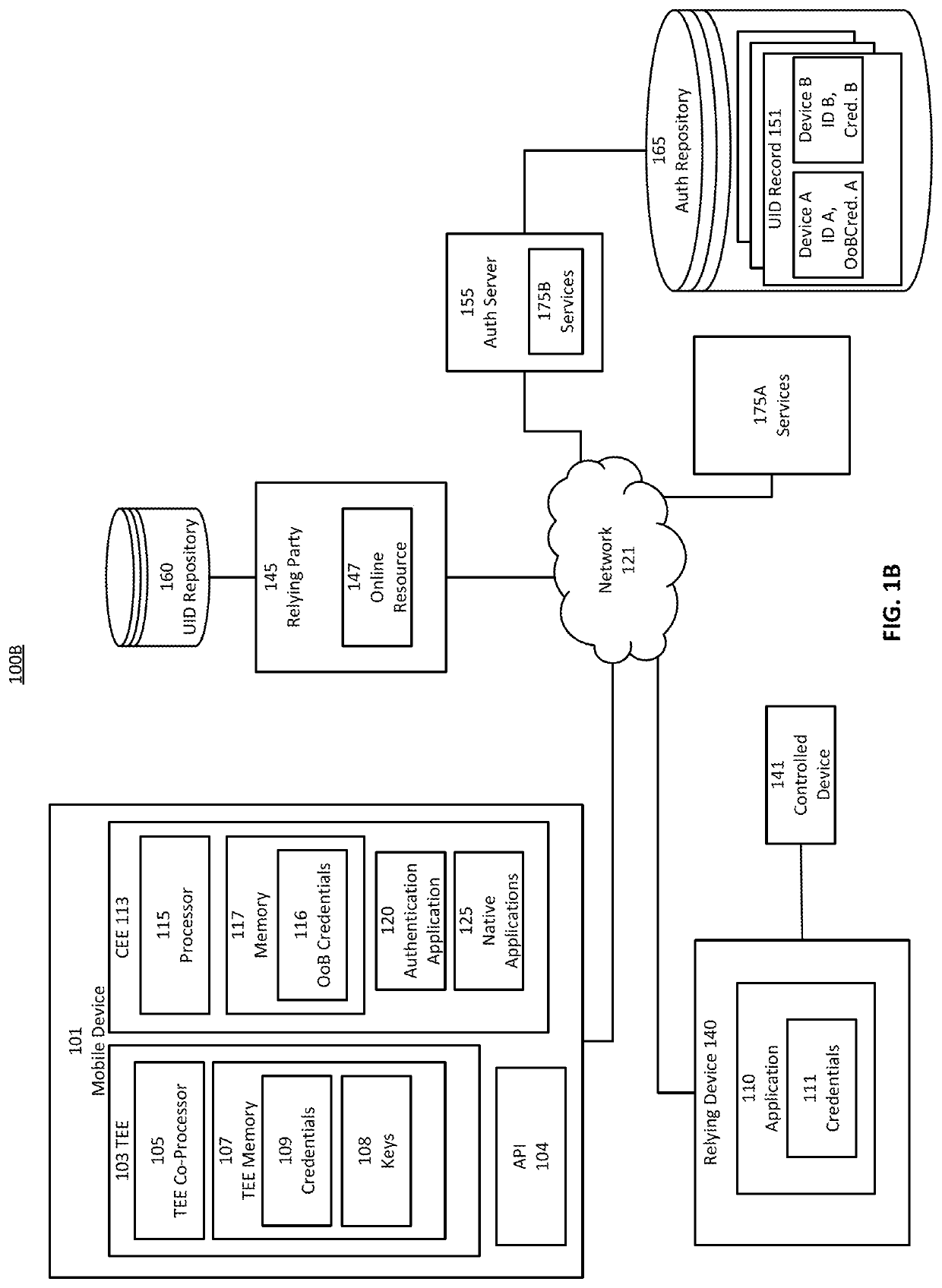
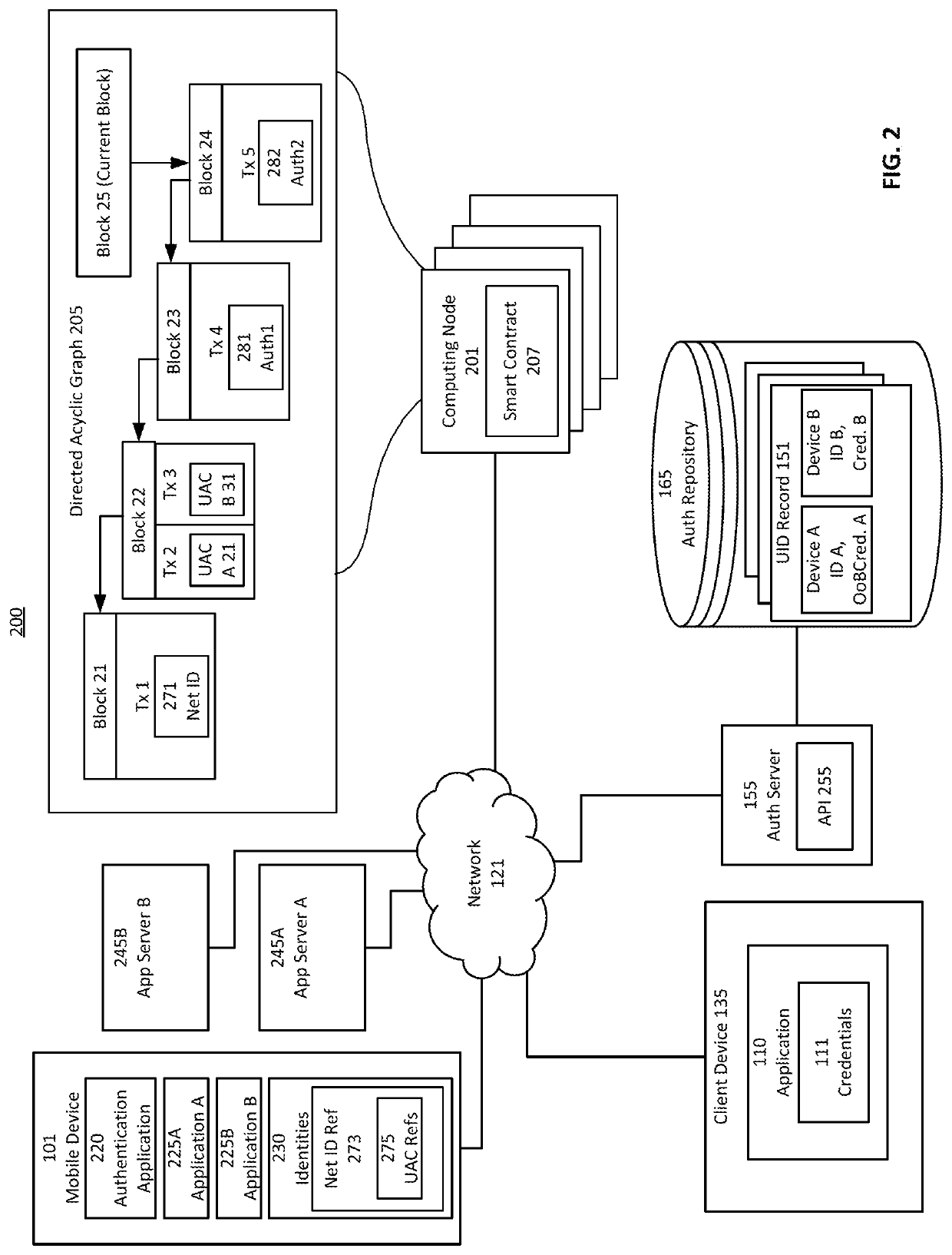
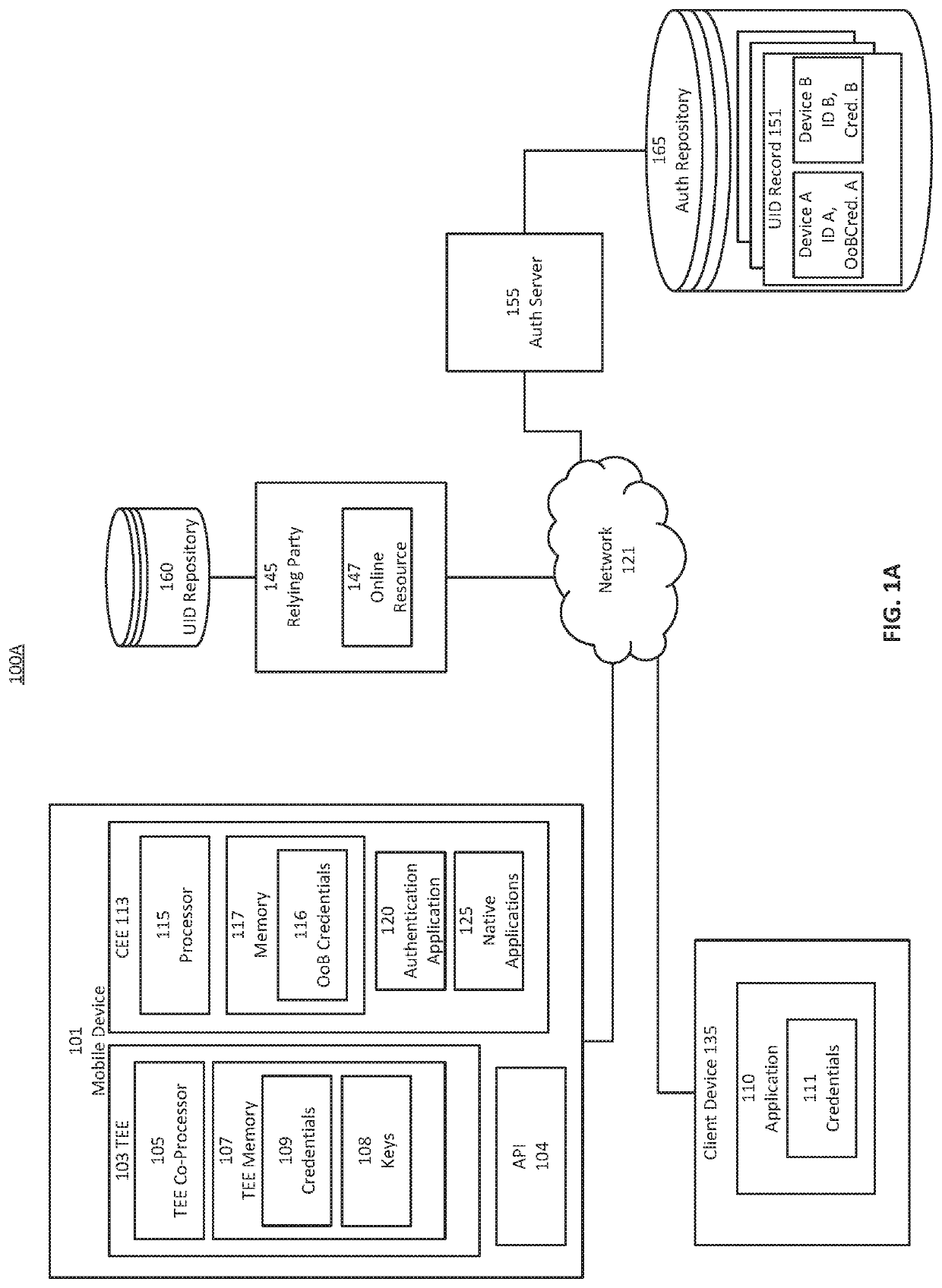
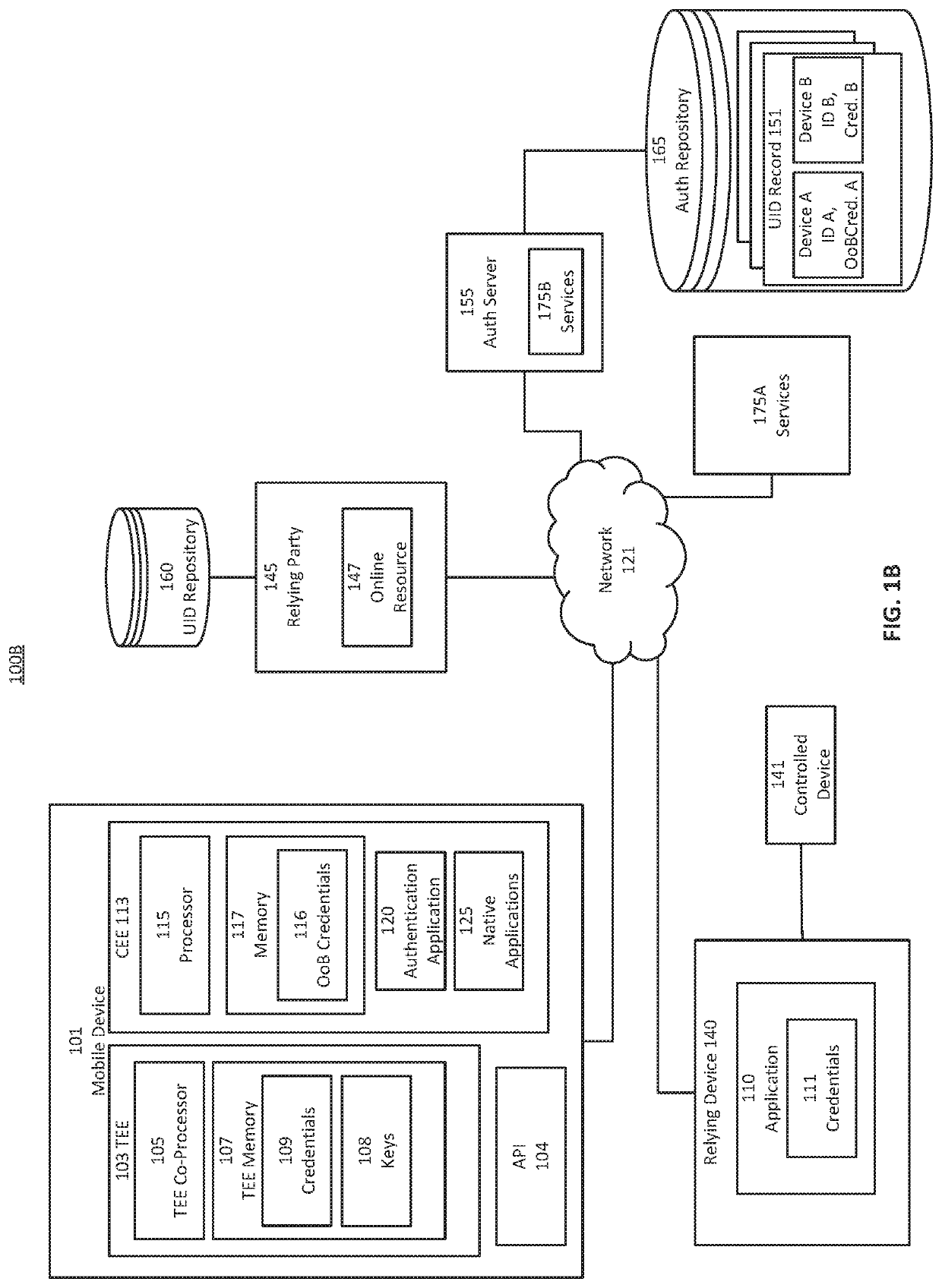
Secure mobile initiated authentications to web-services
Provided is a process for mobile-initiated authentications to web services. Credential values of the user are established within a trusted execution environment of the mobile device and representations are transmitted to a server. The user of the mobile device may authenticate with the mobile device to the server, which may convey access to a web-based service from a relying device. The server may pass credentials corresponding to the web-service received from the mobile device and verified to permit user access to the web-service to the relying device. The relying device presents credentials to the web-service to login, authenticate, or otherwise obtain user-level permission for the user on the relying device. The user of the mobile device may authenticate with the mobile device to the server, and may initiate the authentication process from the mobile device, without inputting credentials corresponding to the web-service on the relying device.
Owner:HYPR CORP
Secure mobile initiated authentication
Provided is a process that establishes representations and permits users to login to a relying device to which a mobile device has registered. Credential values of the user are established within a trusted execution environment of the mobile device and representations of those credentials are transmitted to a server. The user of the mobile device may authenticate with the mobile device to the server, which may permit user access to the relying device via secure session. The user of the mobile device may authenticate with the mobile device to the server, which may permit user access by causing the mobile device to obtain a value by which the relying device may be accessed. The user of the mobile device may authenticate with the mobile device based on a policy received from the server to obtain a value by which the relying device may be accessed.
Owner:HYPR CORP
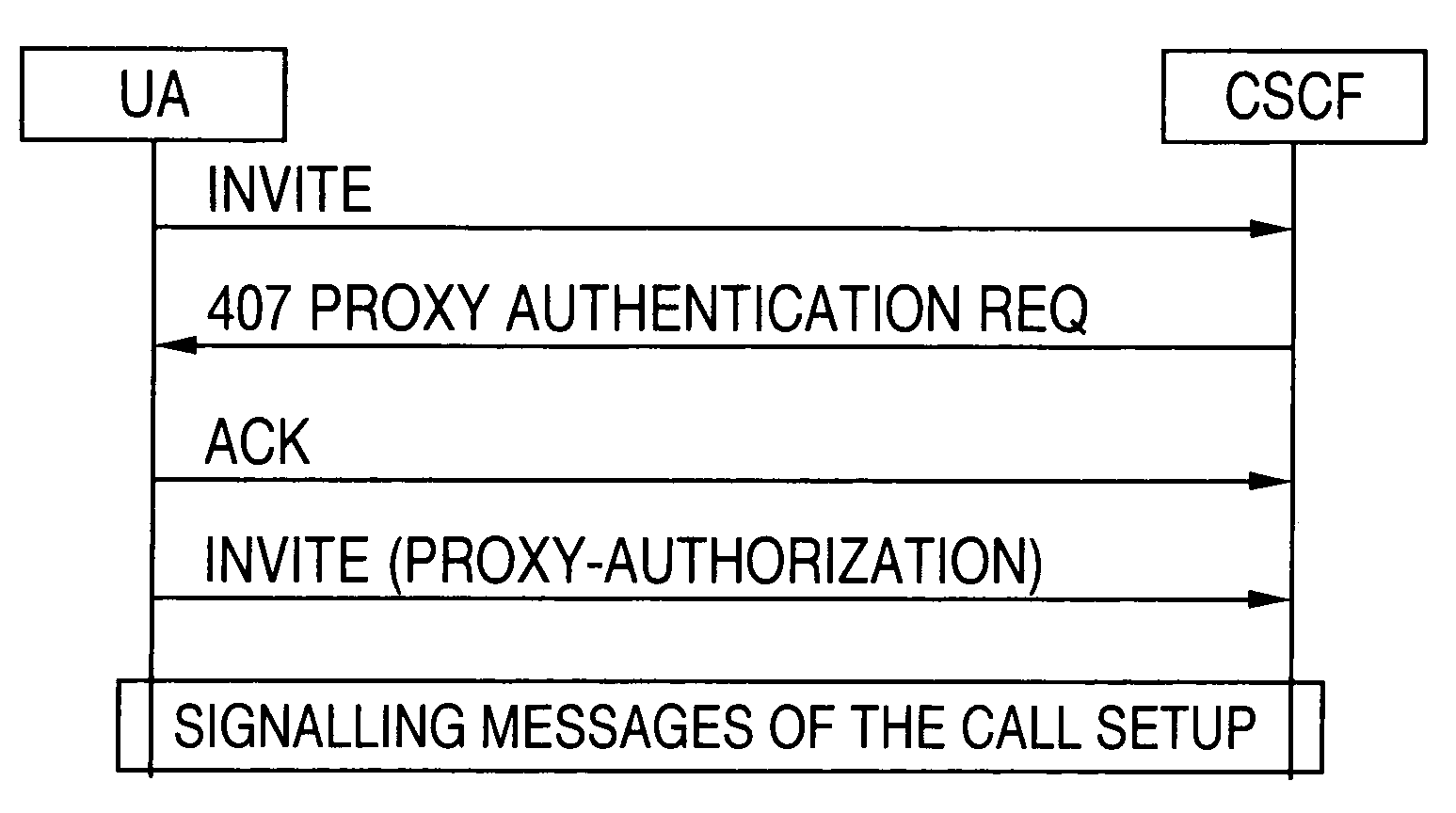
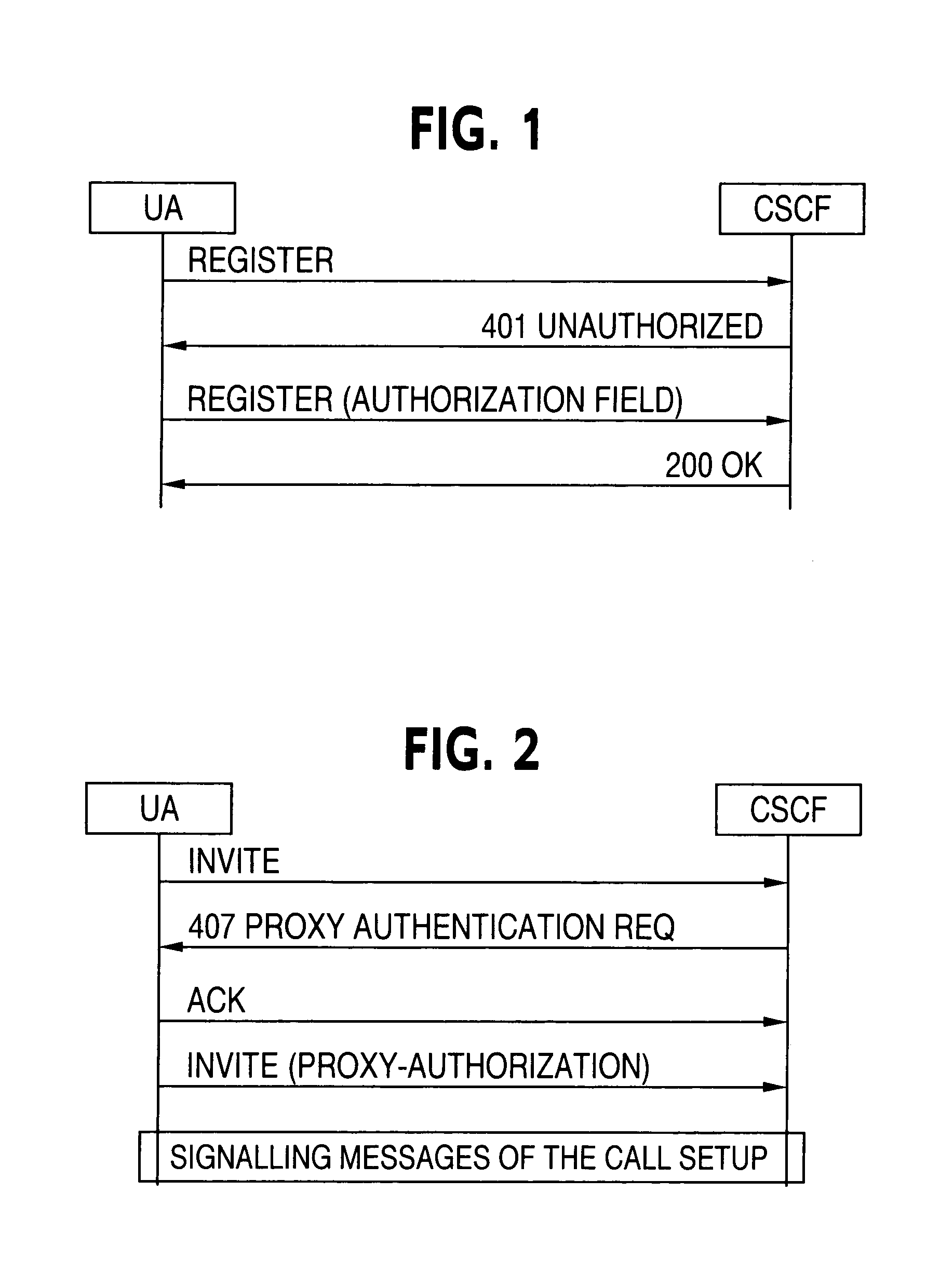
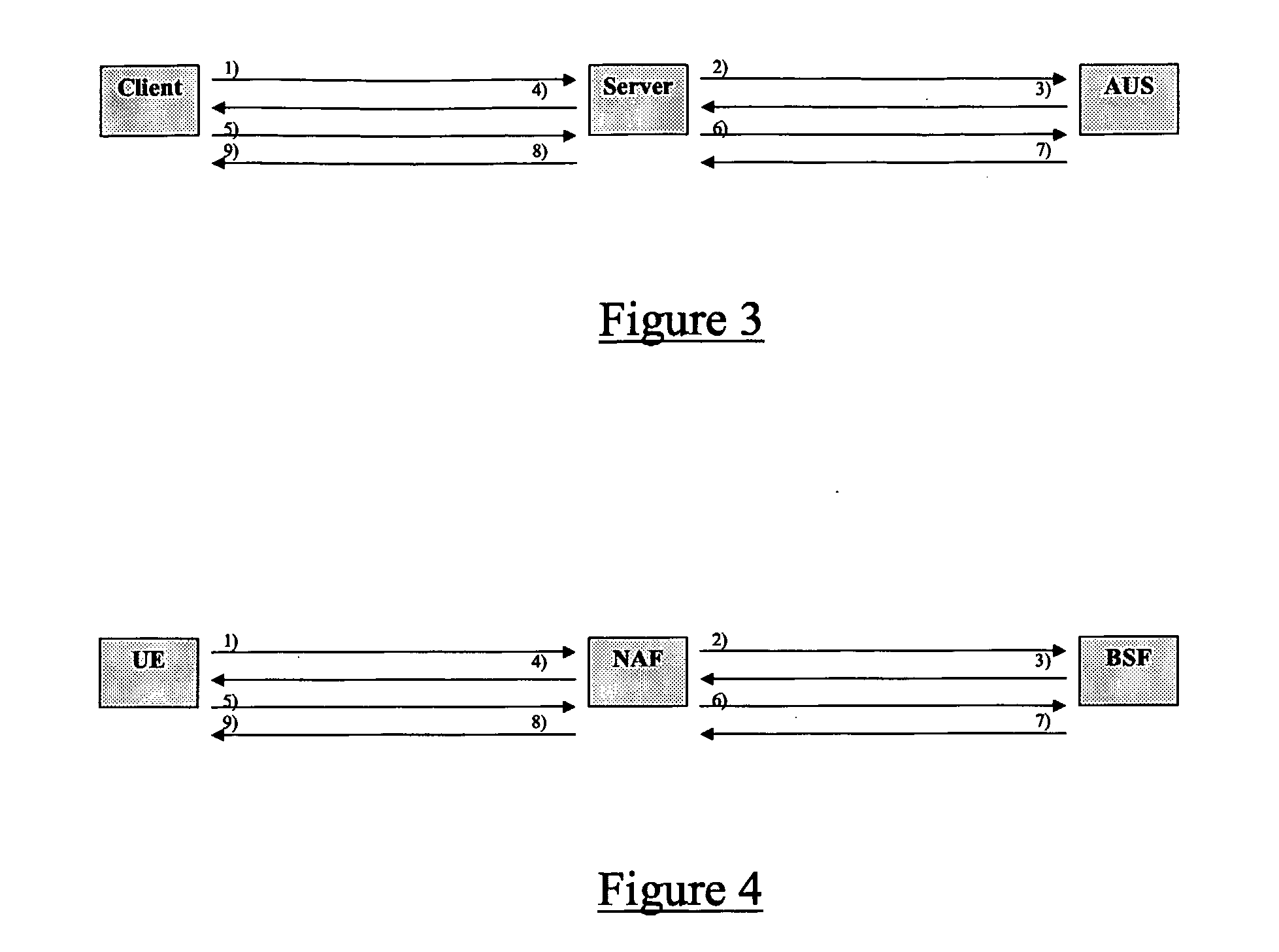
Techniques for performing UMTS (universal mobile telecommunications system) authentication using SIP (session initiation protocol) messages
InactiveUS7024688B1Digital data processing detailsUser identity/authority verificationSession Initiation ProtocolServer authentication
A technique for authenticating a user to a server using SIP messages includes forwarding an SIP request from the user agent to the server. The server then forwards a request for authentication to the user agent in response to the invite request, the request for authentication including information that the authentication will be performed using a UMTS AKA mechanism. The user agent then forwards and authentication response to the server in accordance with the UMTS AKA mechanism and the server then performs the appropriate actions to perform an invoked SIP procedure in response to the SIP request. The SIP request may include any standardized SIP request including an SIP INVITE request or an SIP REGISTER request.
Owner:NOKIA TECHNOLOGLES OY
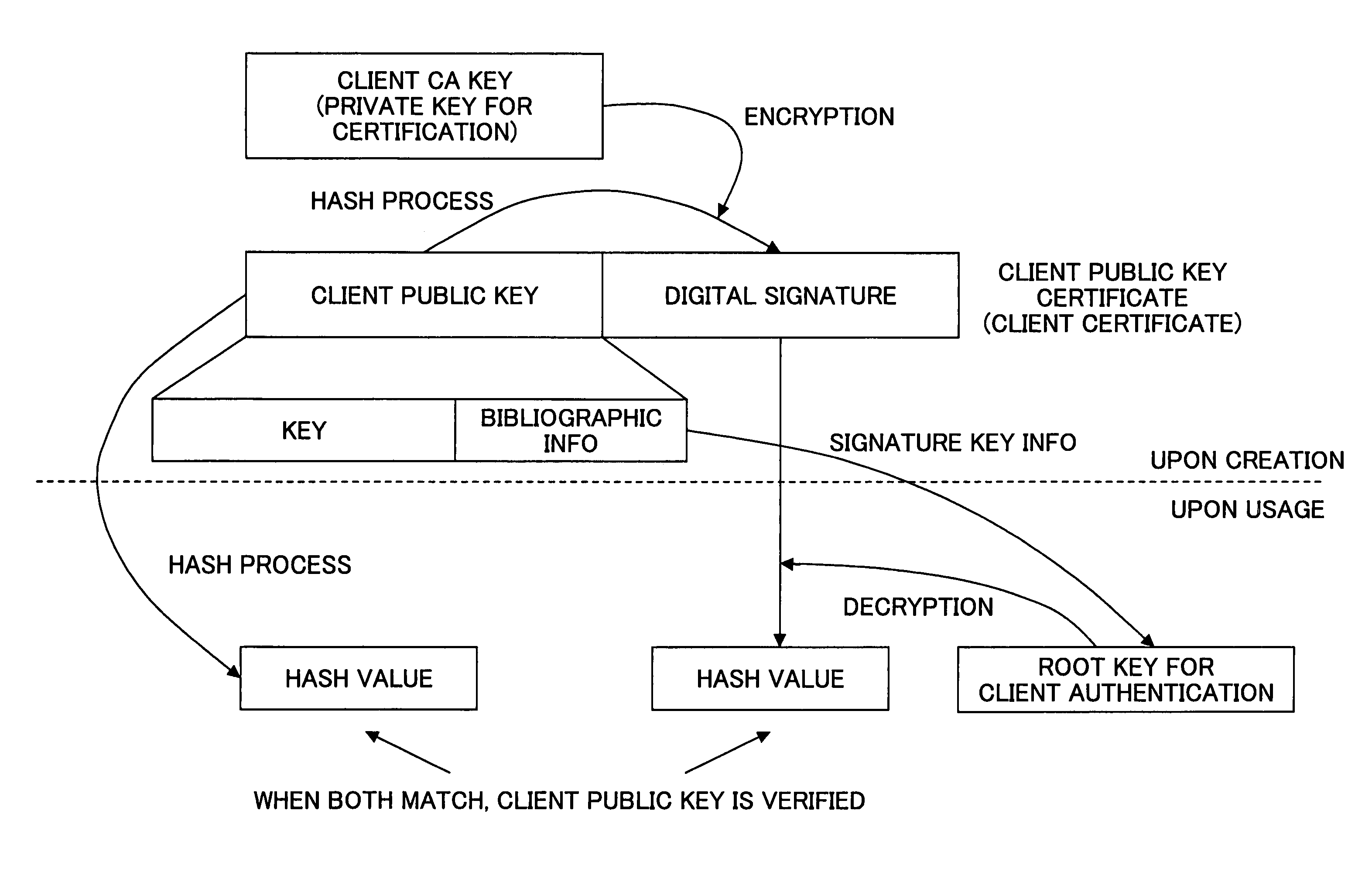
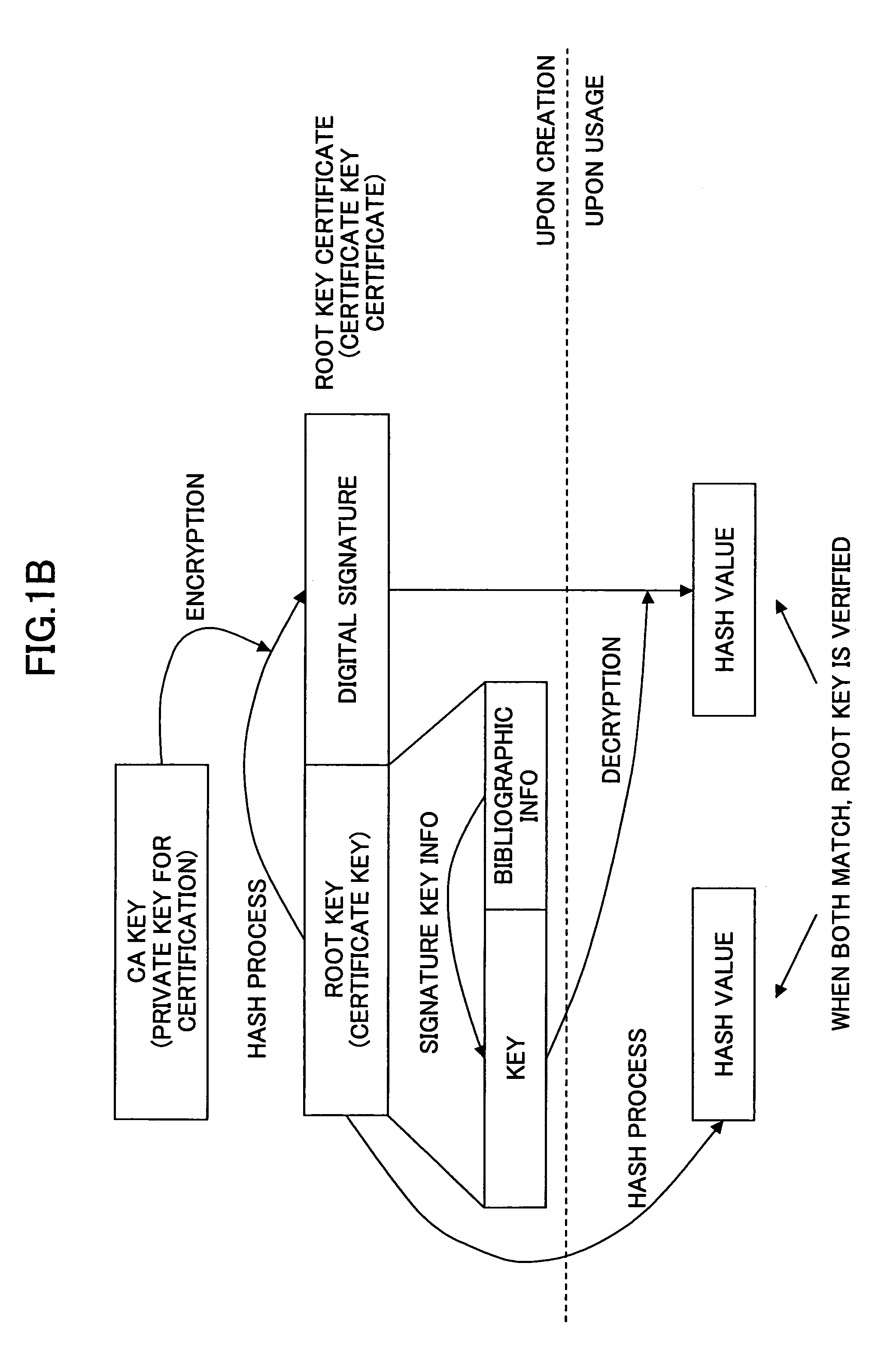
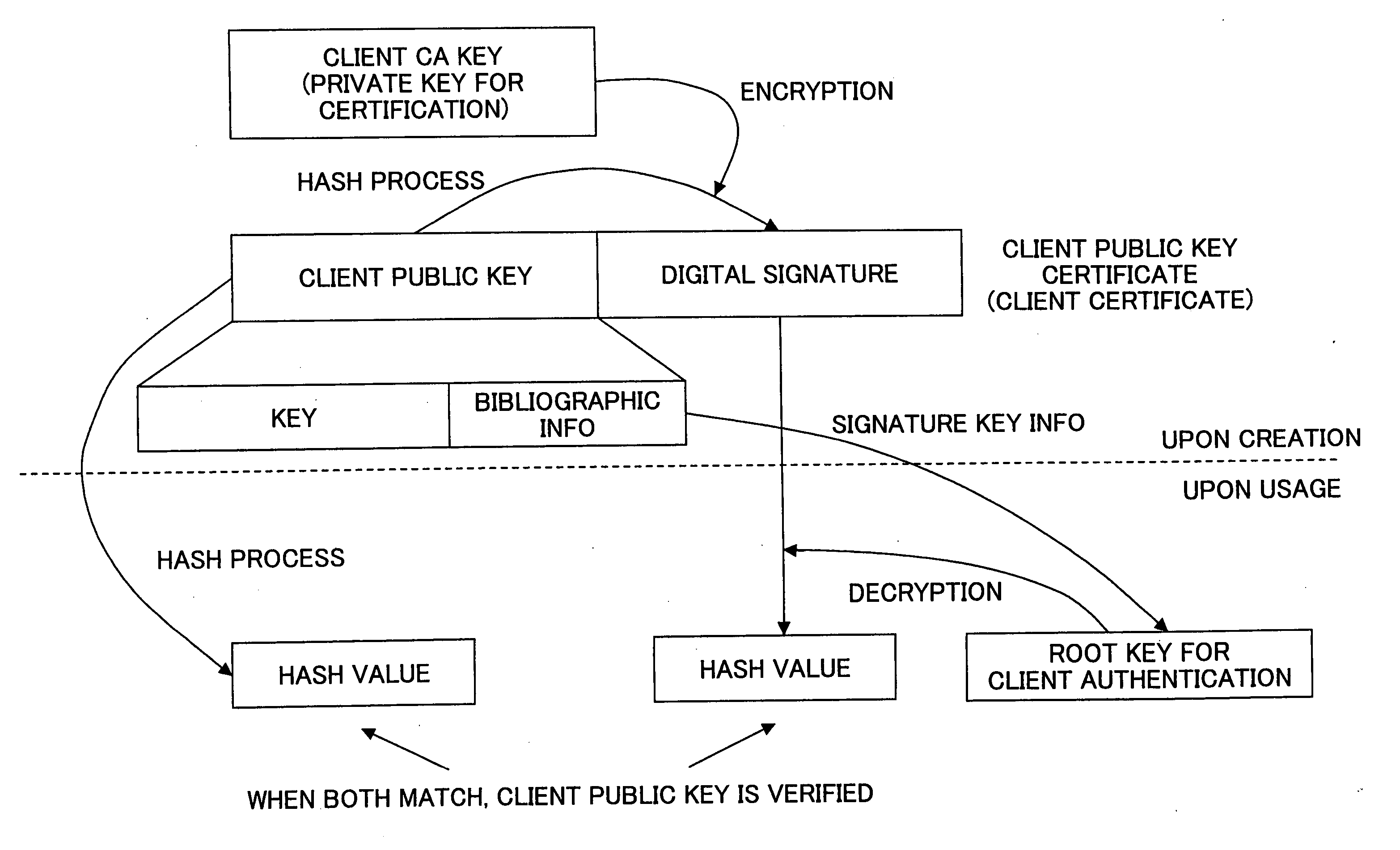
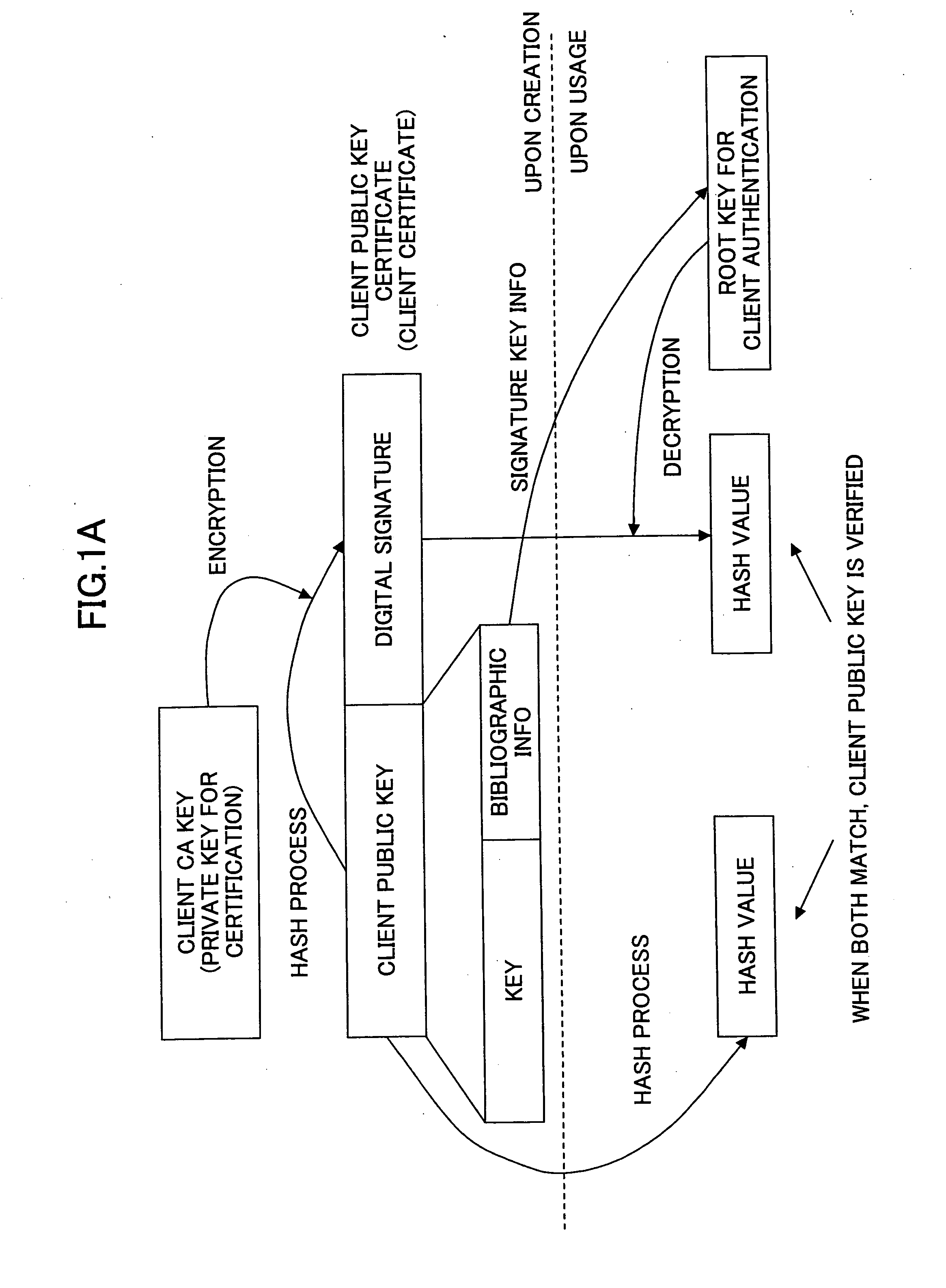
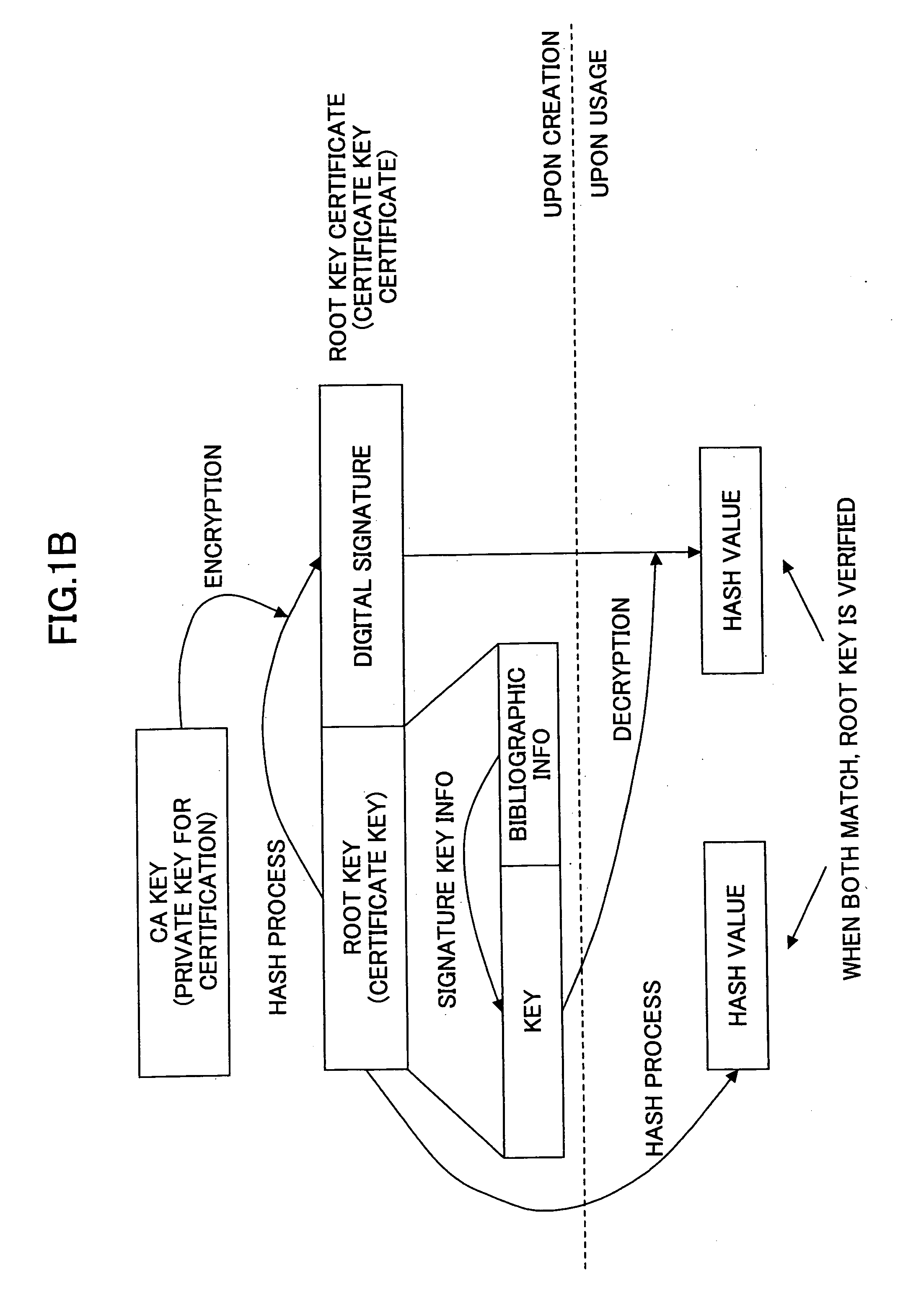
Digital certificate management system, digital certificate management apparatus, digital certificate management method, update procedure determination method and program
ActiveUS6981139B2Security updateSafely update a public keyKey distribution for secure communicationMultiple keys/algorithms usageClient-sideServer authentication
In a digital certificate management system, a client / server system is connected to a digital certificate management apparatus capable of communicating with clients and servers. Mutual authentication is performed between the clients and the servers by using digital certificates and communications are performed over a communication channel established based on mutual authentication. The digital certificate management apparatus includes a certification key update part updating a server certification key used for mutual authentication and stored in each of the clients that become communication parties of one of the servers. The certification key updating part includes a key obtaining part, a certificate obtaining part, and first and second transmission parts. The second transmission part performs an operation of transmitting the new server certificate to each of the servers after there are responses, indicating that the new server certification key is received, from all of the clients that become communication parties of the server.
Owner:RICOH KK
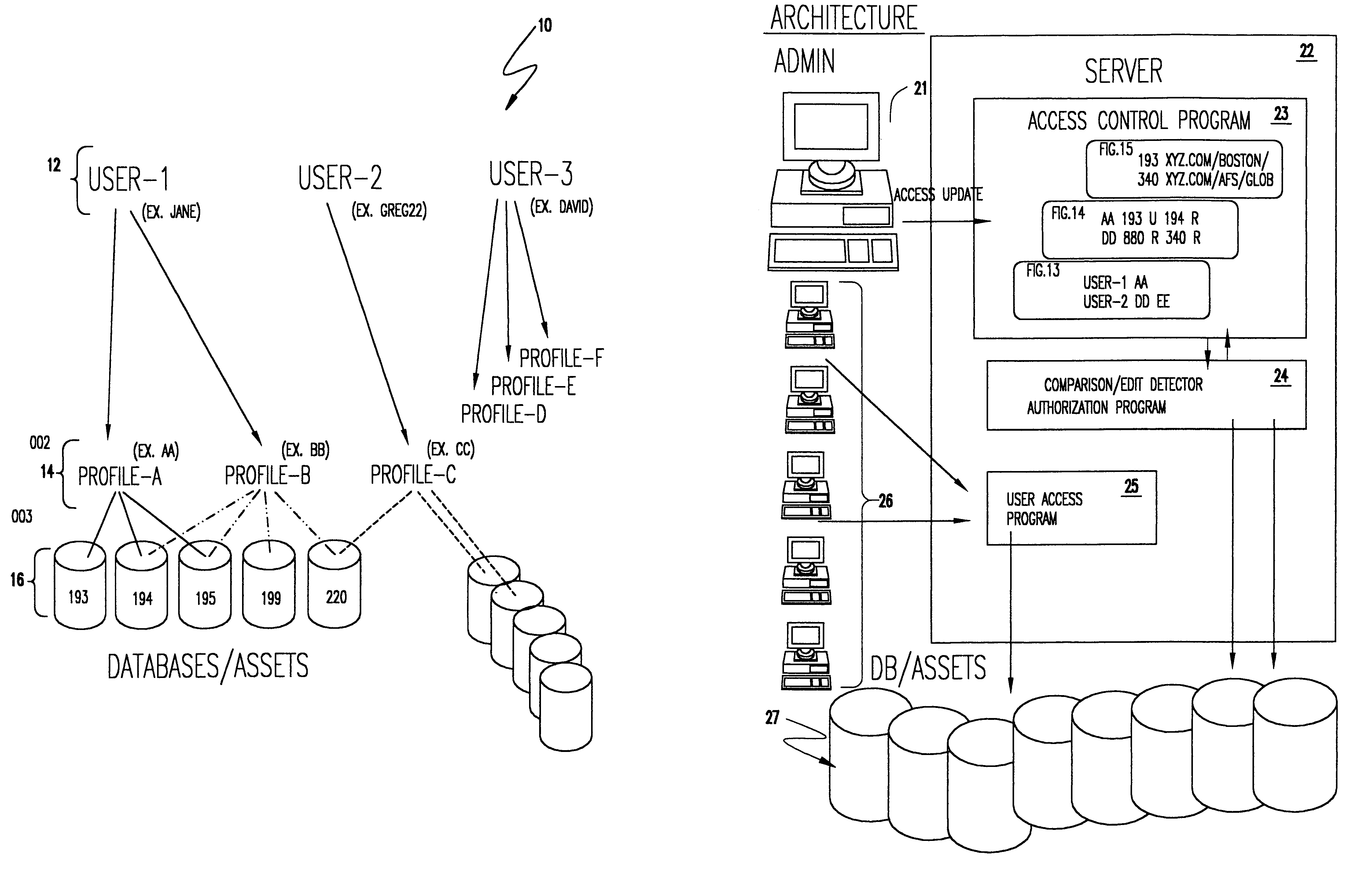
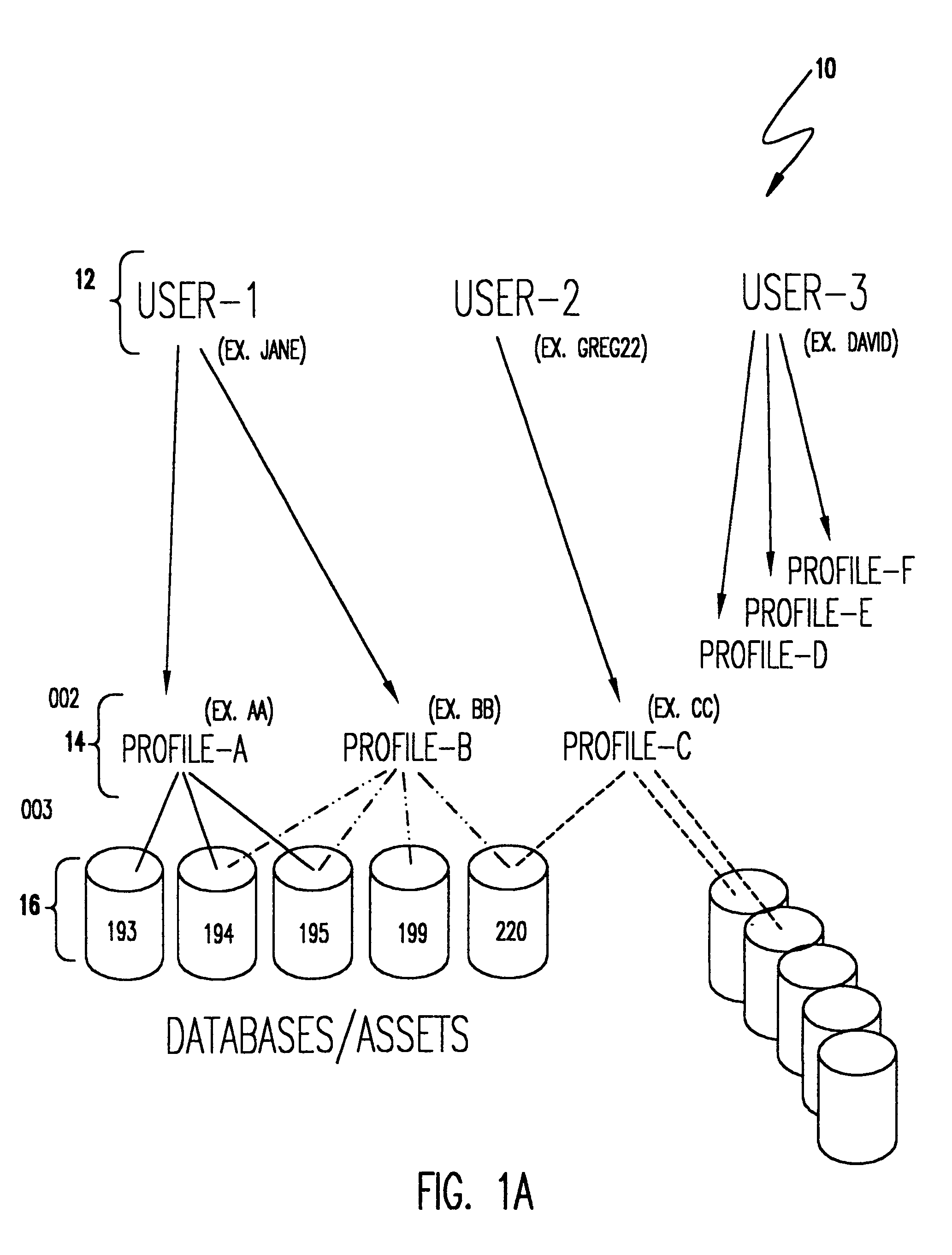
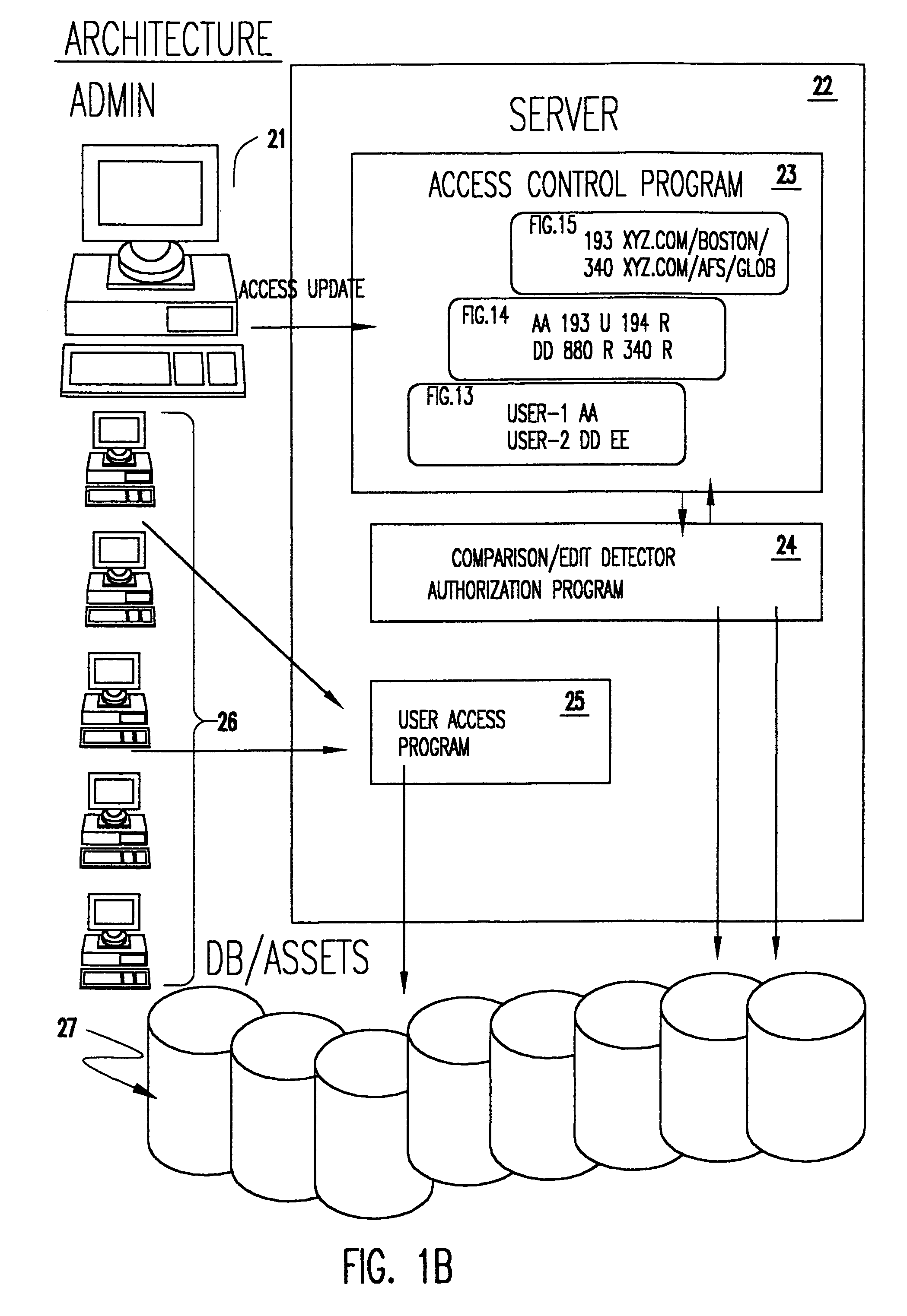
Enhancement to a system for automated generation of file access control system commands
InactiveUS6978381B1Minimize complexityMinimize the numberDigital data processing detailsUnauthorized memory use protectionData processing systemControl system
A secure data processing system having a plurality of resources accessible over a network arrangement such as the Internet and including a server, maintains lists of three categories of access authorization information. A resource list contains path or location information such as a universal resource locator (URL). A profile list maintains a plurality of profile data specifying individual resources or combinations of resources. A user list contains a userID or other data by which a user may be authenticated to the server and one or more profiles freely assignable to respective users. An access control program allows administrator supervision of editing of the lists of user access authorization information. An authorization program performs authorizations to resources for all users based on the profile information of respective users upon completion of editing. A user is authenticated by the server upon communication by the user to the server and user requests of authenticated users to resources for which authorization has already been performed in accordance with the path or location information in the resource list.
Owner:IBM CORP
Personal device, terminal, server and methods for establishing a trustworthy connection between a user and a terminal
InactiveUS7149895B1Complete banking machinesDigital data processing detailsComputer terminalServer authentication
The invention is related to a system which allows a user to authenticate unknown terminals. The invention uses a first authentication step wherein the terminal authenticates itself to a server. Depending on whether the personal device has its own output means, such as a loudspeaker or a screen, the final message, whether the terminal can be trusted or not, can be output on the personal device or on the terminal itself. In the case where the device has no output means of its own, this message can originate in the device and be transmitted from there to the terminal. The user can input authentication information into his personal device, which can then be fully or partially transmitted to the terminal. In the end, the terminal may use the transmitted information to give out the authenticity output message. After the first authentication step follows a second authentication step, wherein the server authenticates itself to the personal device, if there is one. Upon success of both authentication steps, the authenticity output message can be given to the user.
Owner:PAYPAL INC
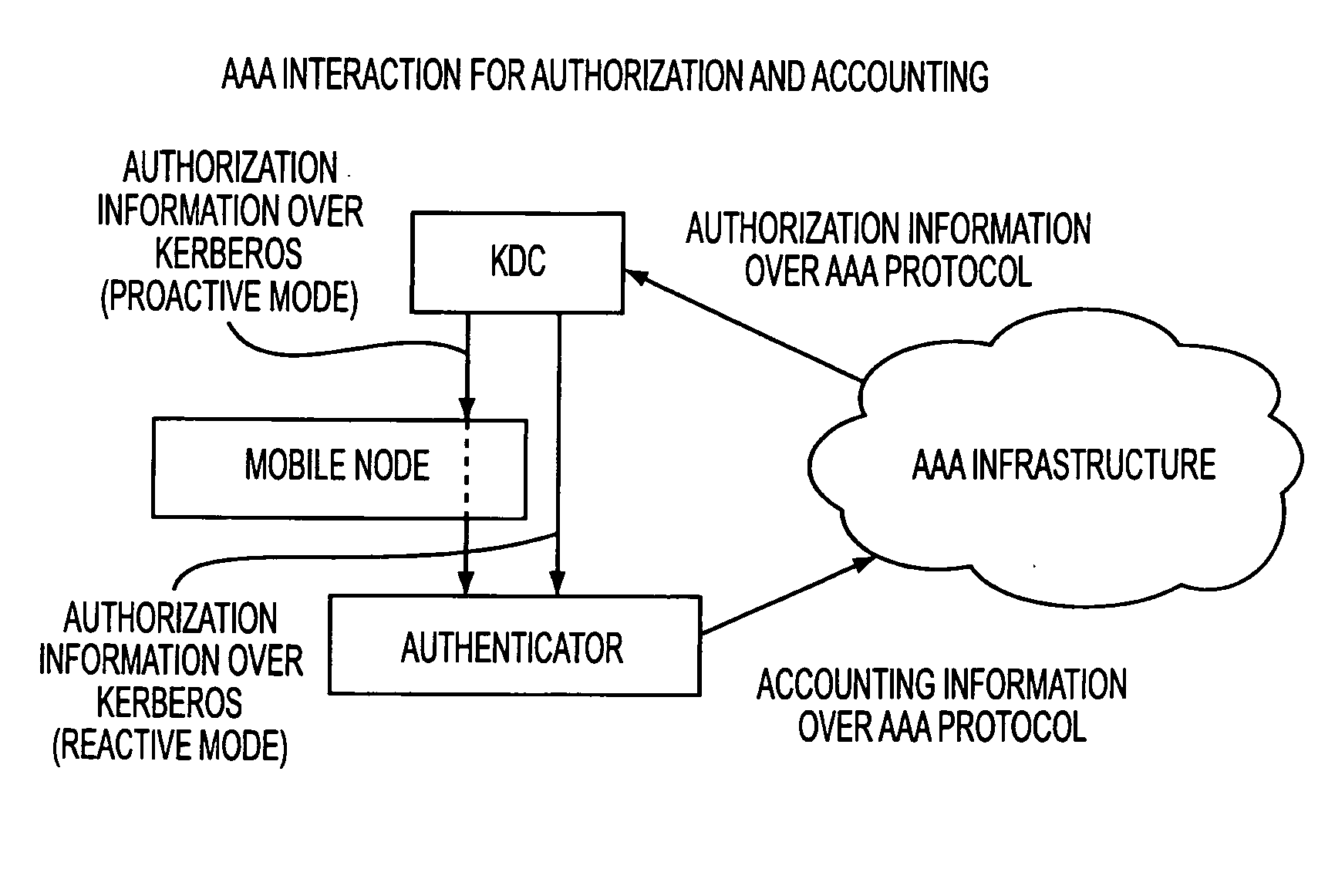
Kerberized handover keying
ActiveUS20080175393A1Key distribution for secure communicationDigital data processing detailsRe keyingProtocol for Carrying Authentication for Network Access
A media-independent handover key management architecture is disclosed that uses Kerberos for secure key distribution among a server, an authenticator, and a mobile node. In the preferred embodiments, signaling for key distribution is based on re-keying and is decoupled from re-authentication that requires EAP (Extensible Authentication Protocol) and AAA (Authentication, Authorization and Accounting) signaling similar to initial network access authentication. In this framework, the mobile node is able to obtain master session keys required for dynamically establishing the security associations with a set of authenticators without communicating with them before handover. By separating re-key operation from re-authentication, the proposed architecture is more optimized for a proactive mode of operation. It can also be optimized for reactive mode of operation by reversing the key distribution roles between the mobile node and the target access node.
Owner:TELCORDIA TECHNOLOGIES INC +1
Method for protecting safety of account number cipher
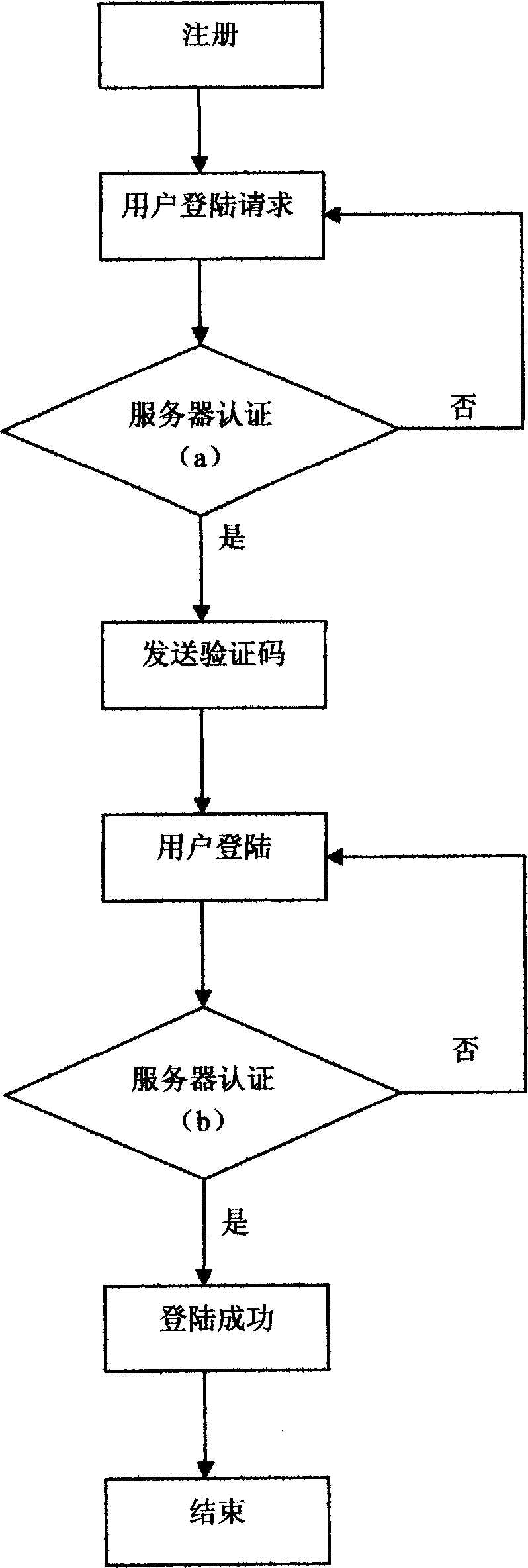
InactiveCN1832401AImprove authentication strengthResistance to attacksMultiple keys/algorithms usageUser identity/authority verificationMobile Telephone NumberAuthentication server
This invention relates to a method for protecting safety of codes of account numbers including the following steps: a user should submit the account number name and its cell phone number to a registration certification server system, which binds the name and the number, logs on the request, then the server certifies and sends it the verification code, the user logs on then the server certifies it.
Owner:陈珂
Unified identity verification
Apparatus, systems, and methods are disclosed that operate to register one time, at a server associated with an authenticating entity, information comprising an identity uniquely associated with an individual account owner and an account held by the authenticating entity. Further activity includes receiving an authentication request at the server from a requesting party to authenticate an unauthenticated individual purporting to be the individual account owner, and authenticating, by the server, the unauthenticated individual as the individual account owner by matching a token presented by the unauthenticated individual, to the identity. Responsive solely to the authenticating, only a selected portion of the information previously authorized by the individual account owner is provided for sharing with the plurality of selected requesting parties. Additional apparatus, systems, and methods are disclosed.
Owner:PAYPAL INC
Method for communicating between a server and a client and corresponding client, server and system
ActiveUS20140040991A1Convenient for userDigital data processing detailsMultiple digital computer combinationsExpiration TimeTime segment
The invention relates to a method for communicating between a server and a client. The server and the client access at least one session extension key and / or a key associated with the session extension key, as an associated key. The server authorizes to extend an open communication session with the client until an expiration time only if the client sends to the server authentication data allowing the server to authenticate at least the client on a basis of the session extension key. The expiration time is a time at which the communication session is open completed by a predetermined extension time period. The invention also relates to corresponding client, server and system.
Owner:THALES DIS FRANCE SA
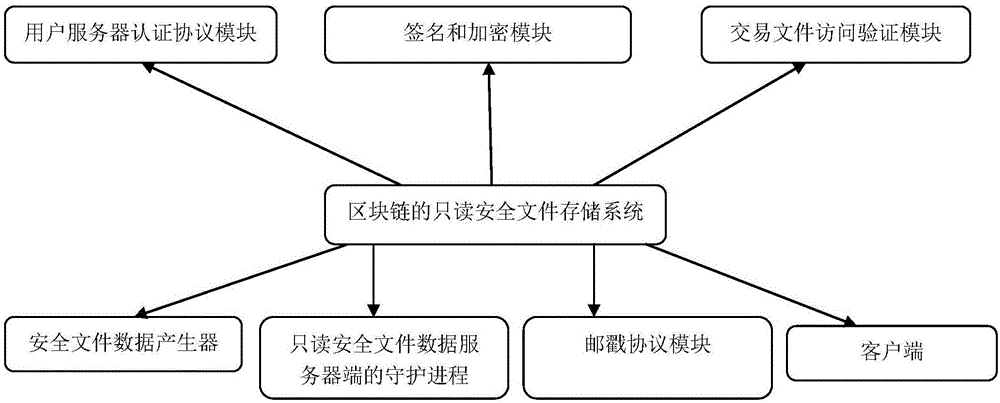
Read-only security file storage system for block chain and method thereof
InactiveCN106295401AFaster and more complete recoveryExtended storage timeInput/output to record carriersDigital data protectionData integrityCiphertext
The invention provides a read-only security file storage system for a block chain. The system comprises: (1) a user server authentication protocol module used for executing a mutual authentication protocol between a user and a server via a self-certified path name; (2) a signature and encryption module used for correctly encrypting a transaction file; (3) a transaction file access verification module used for verifying the trustworthiness of the user; (4) a security file data generator; (5) a daemon of a read-only security file data server; and (6) a client, wherein a traditional path is converted into data and digital signature is carried out in a client environment, then the data is distributed to an arbitrary number of running servers, and the daemon receives the request of the client and returns the data; and (7) a postmark protocol module used for detecting the integrity of transaction data. By adoption of the storage system and the method provided by the invention, the storage time of a large file system is shortened, and a creator can complete cryptographic operation, data creation and decryption according to ciphertext in an environment without a network.
Owner:SHENZHEN FANXI ELECTRONICS CO LTD
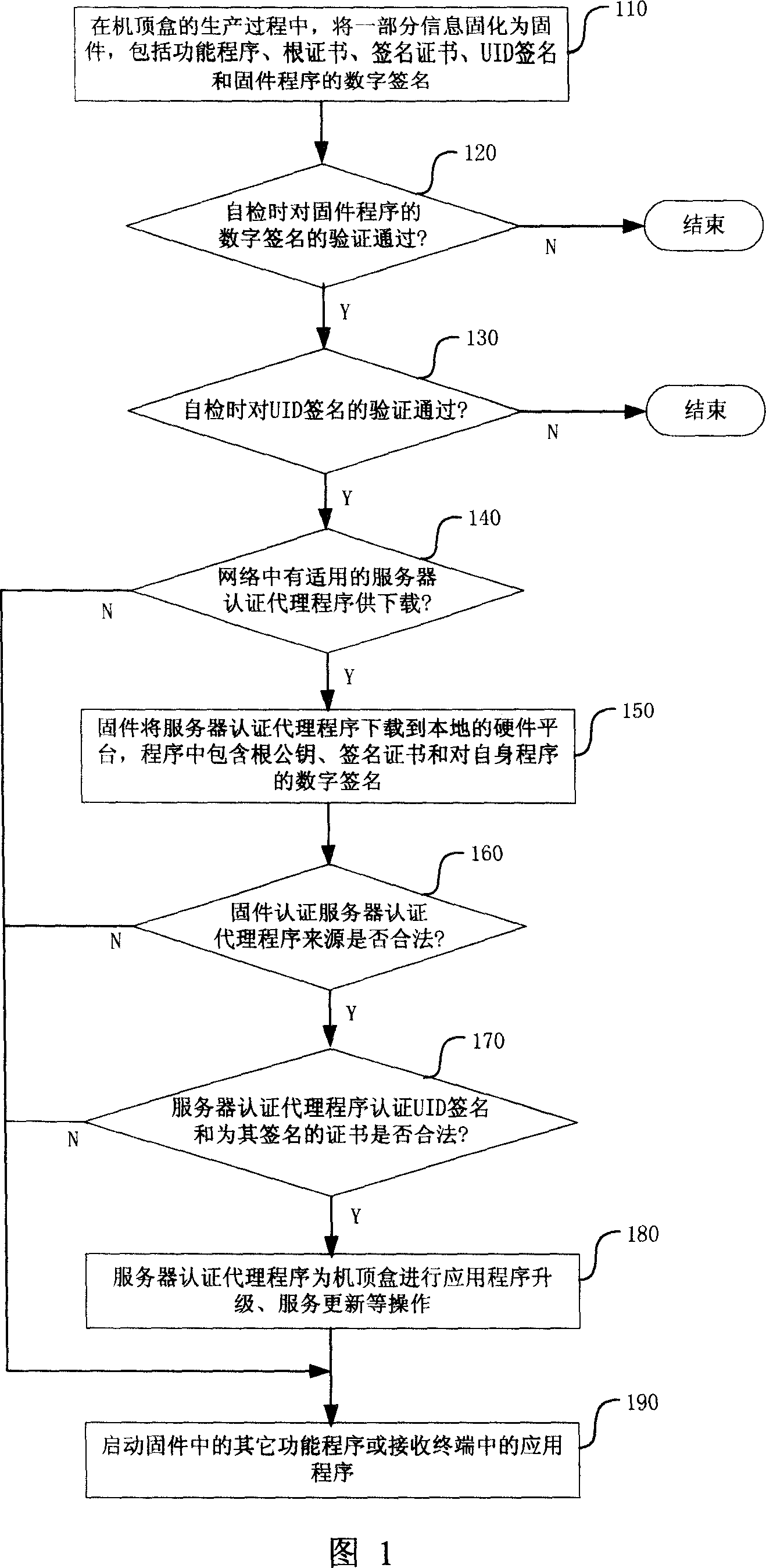
Method and system for authenticating legality of receiving terminal in unidirectional network
ActiveCN101145906ARealize the identification of legitimacyPrevent imitationUser identity/authority verificationDigital signatureTerminal equipment
The invention relates to a method and system for legality authentication of receiving terminals in a unidirectional network. The digital signature of UID of chips is written in terminal equipment, terminal firmware downloads a server authentication agent program from the network, the program runs on the hardware platform of the terminal, and UID signature is decrypted by using a built-in public key or the public key of the signature certificate acquired from the network; if the decrypted value and the abstract value of UID read out from the chips are determined to be identical and the signature certificate is in a trust chain established by the rood certificate, the terminal is legal, or the terminal is illegal. Also, in the process of self-test of the firmware, the decrypted value can be obtained by using the public key in the signature certificate to decrypt UID signature, then UID of the chips is read out and the abstract value thereof is calculated, and if the two values are identical, the self-test passes, or the work state ends. By using the self-test of the terminal firmware or the mutual authentication between the server authentication agent program and the firmware, the invention makes clone and copied set-top boxs not work normally in the network.
Owner:北京邦天信息技术有限公司
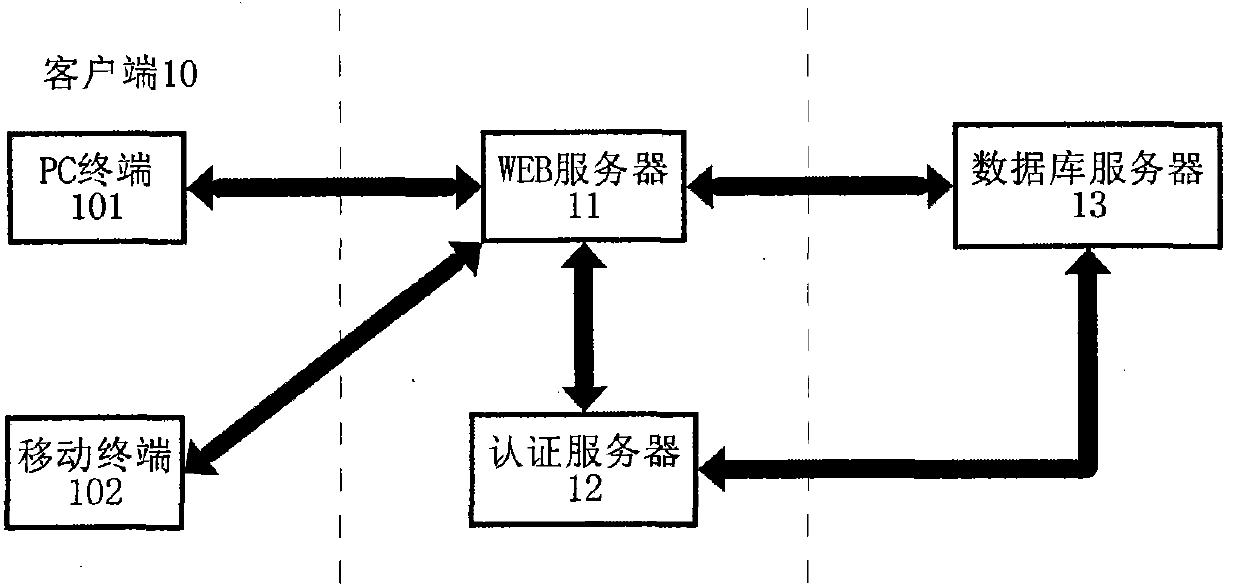
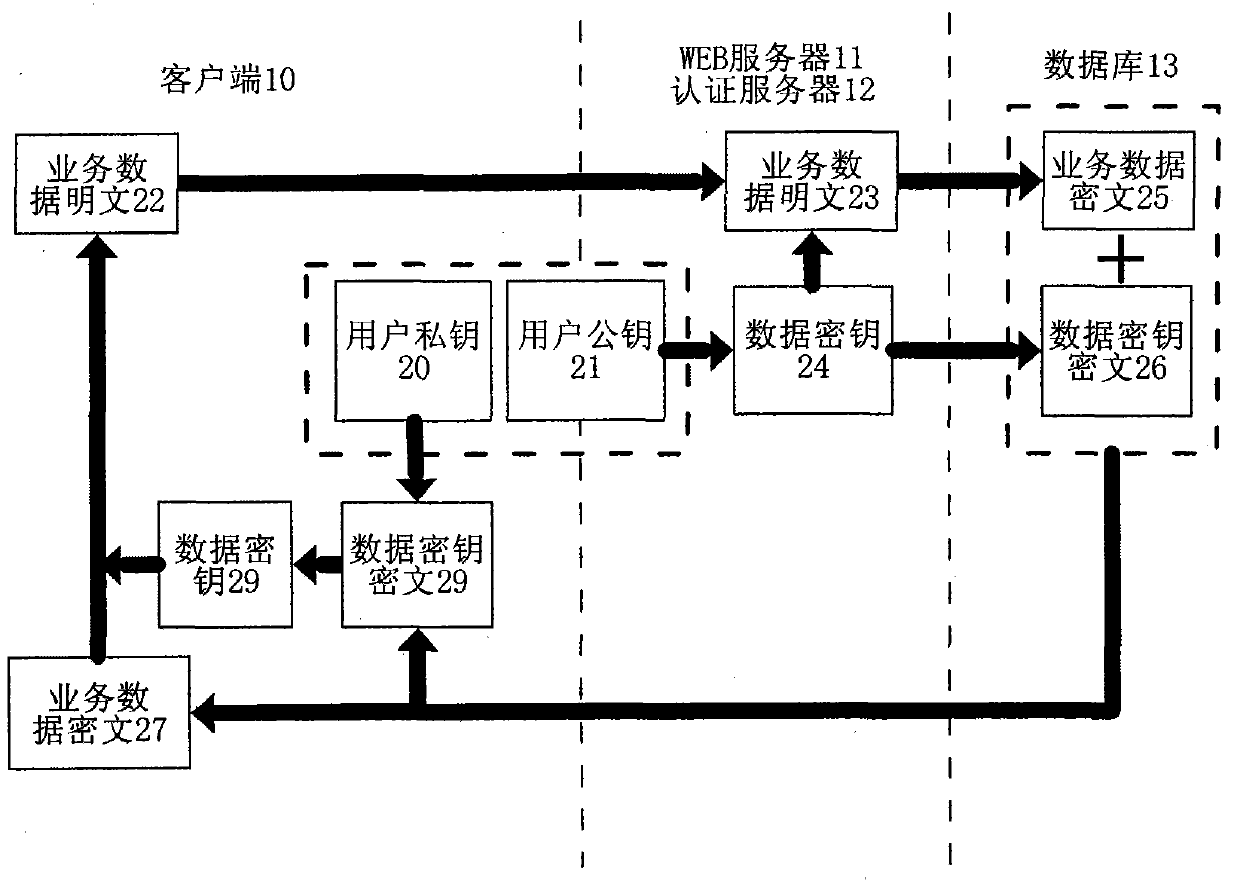
Method and system for improving SaaS application security
InactiveCN101771699AImprove securityPrevent leakageEncryption apparatus with shift registers/memoriesPublic key for secure communicationWeb serviceCiphertext
The invention provides a method and a system for improving SaaS application security. The encryption method includes that a public password belonging to the client is set up; a data password used for encrypting business data for the client is randomly generated when the business data of the client is saved; the data password is used as the password to encrypt the business data according to a symmetrical cryptographic algorithm; the business data are encrypted through the public password and according to an unsymmetrical cryptographic algorithm; the business data cryptograph and the data password cryptograph are saved in a server; the client gets the cryptograph saved in the server after successfully decrypting the challenge message of the server with the private password; the client decrypts the data password cryptograph with the private password and further decrypts the business data according to the symmetrical cryptographic algorithm. The system includes a WEB server, an authentication server and a database server which can transmit data each other. The invention effectively prevents the administrator from reveal and malicious use of the data password.
Owner:SOUTH CHINA UNIV OF TECH +1
User Authentication and Authorisation in a Communications System
ActiveUS20090013381A1Efficient combinationEncryption apparatus with shift registers/memoriesUser identity/authority verificationCommunications systemUser authentication
Owner:TELEFON AB LM ERICSSON (PUBL)
Digital certificate management system, digital certificate management apparatus, digital certificate management method, update procedure determination method and program
InactiveUS20060036850A1Security updateSafely update a public keyKey distribution for secure communicationMultiple keys/algorithms usageClient server systemsServer authentication
In a digital certificate management system, a client / server system is connected to a digital certificate management apparatus capable of communicating with clients and servers. Mutual authentication is performed between the clients and the servers by using digital certificates and communications are performed over a communication channel established based on mutual authentication. The digital certificate management apparatus includes a certification key update part updating a server certification key used for mutual authentication and stored in each of the clients that become communication parties of one of the servers. The certification key updating part includes a key obtaining part, a certificate obtaining part, and first and second transmission parts. The second transmission part performs an operation of transmitting the new server certificate to each of the servers after there are responses, indicating that the new server certification key is received, from all of the clients that become communication parties of the server.
Owner:RICOH KK
Barcode authentication for resource requests
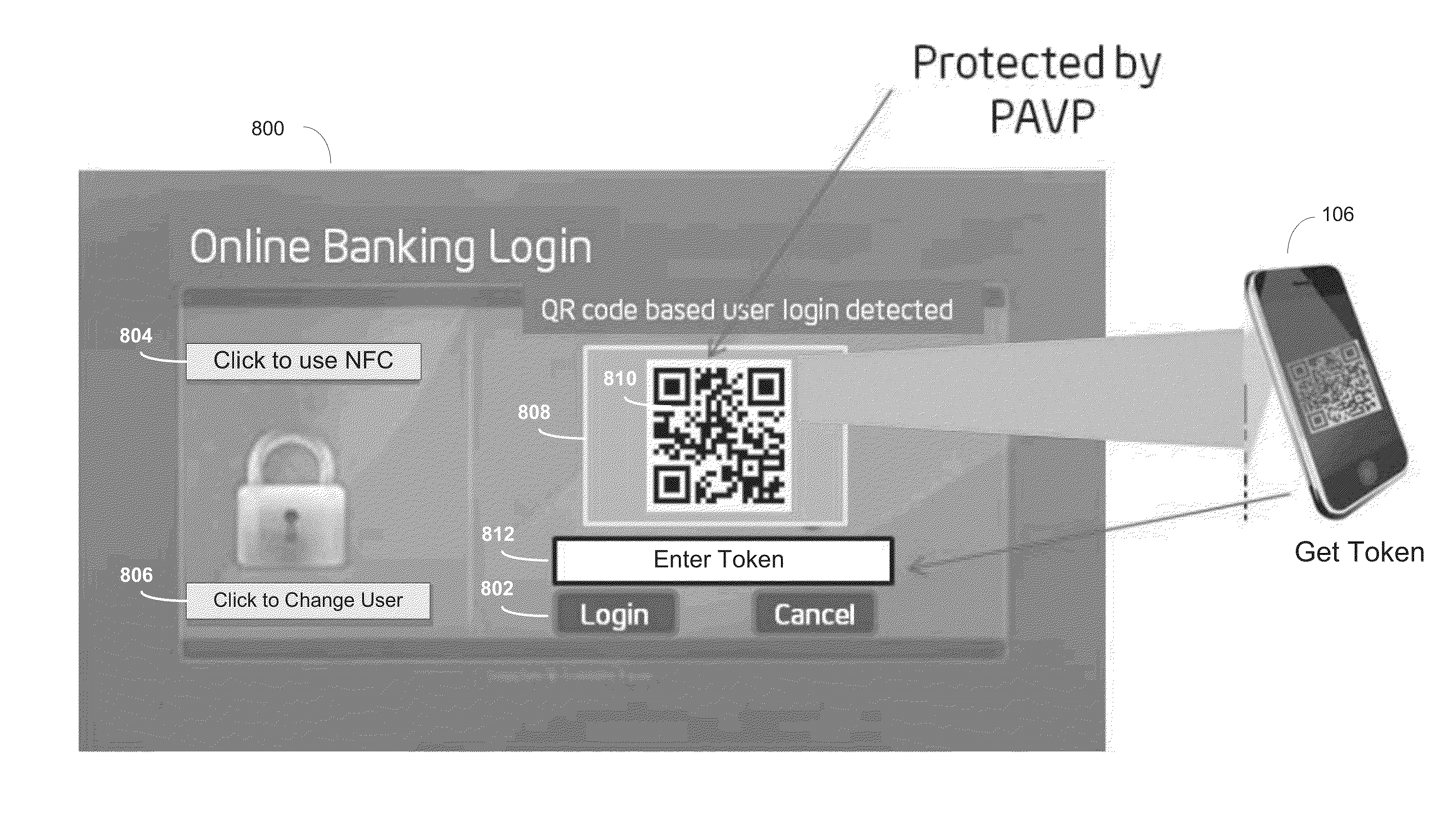
InactiveUS20140230039A1Digital data processing detailsMultiple digital computer combinationsBarcodeClient-side
Mobile device, client device and server associated with client-server authentication are described. In embodiments, the mobile device may comprise a camera and a token extractor. The token extractor may be coupled to the camera and configured to analyze an image, captured by the camera. The captured image may contain a barcode and may be displayed on a client device in response to a request of a server for access to a resource. The barcode may contain a token, which may be extracted by the token extractor to be used to gain access to a resource requested from a server. Other embodiments may be described and / or claimed.
Owner:INTEL CORP
Systems and methods for performing single sign-on by an intermediary device for a remote desktop session of a client
ActiveUS20160094539A1Digital data processing detailsMultiple digital computer combinationsRemote desktopClient-side
The present disclosure is directed to systems and methods for performing single sign on by an intermediary device for a remote desktop session of a client. A first device intermediary to a plurality of clients and a plurality of servers authenticates a user and establishes a connection to the user's client device. The device provides a homepage including links to one or more remote desktop hosts associated with the user. The device receives a request to launch an RDP session with a remote desktop host via the homepage and generates RDP content, including a security token, for the user. The device receives a second request that includes the security token to launch the RDP session. The device validates the user using the security token and establishes a connection to the remote desktop host. The device signs into the desktop host using session credentials.
Owner:CITRIX SYST INC
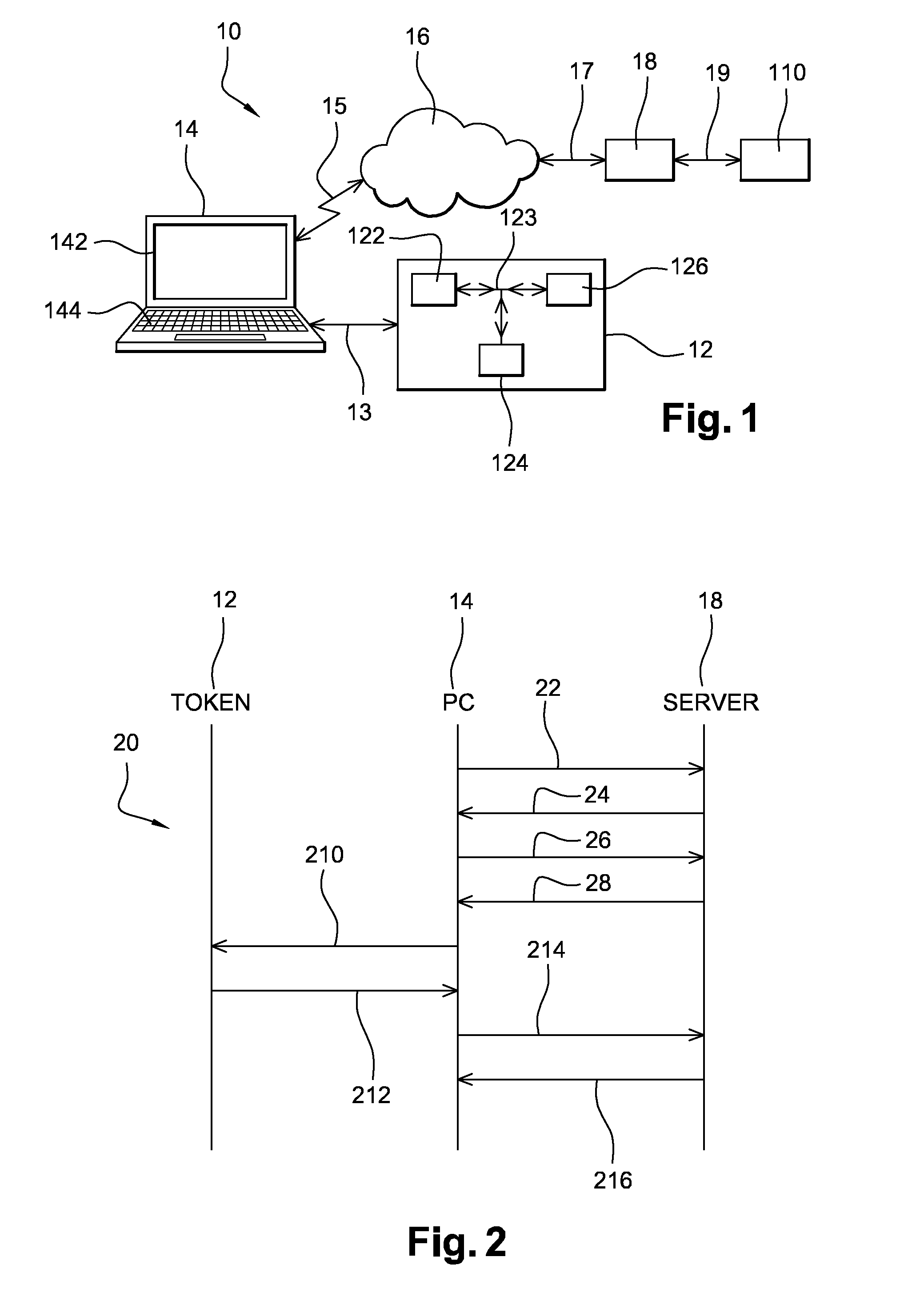
System for enforcing security policies on mobile communications devices
A system for enforcing security policies on mobile communications devices is adapted to be used in a mobile communications network in operative association with a subscriber identity module. The system having a client-server architecture includes a server operated by a mobile communications network operator and a client resident on a mobile communications device on which security policies are to be enforced. The server is adapted to determine security policies to be applied on said mobile communications device, and to send thereto a security policy to be applied. The client is adapted to receive the security policy to be applied from the server, and to apply the received security policy. The server includes a server authentication function adapted to authenticate the security policy to be sent to the mobile communications device; the client is further adapted to assess authenticity of the security policy received from the server by exploiting a client authentication function resident on the subscriber identity module.
Owner:TELECOM ITALIA SPA
Secret user session managing method and system under web environment, recording medium recorded program executing it
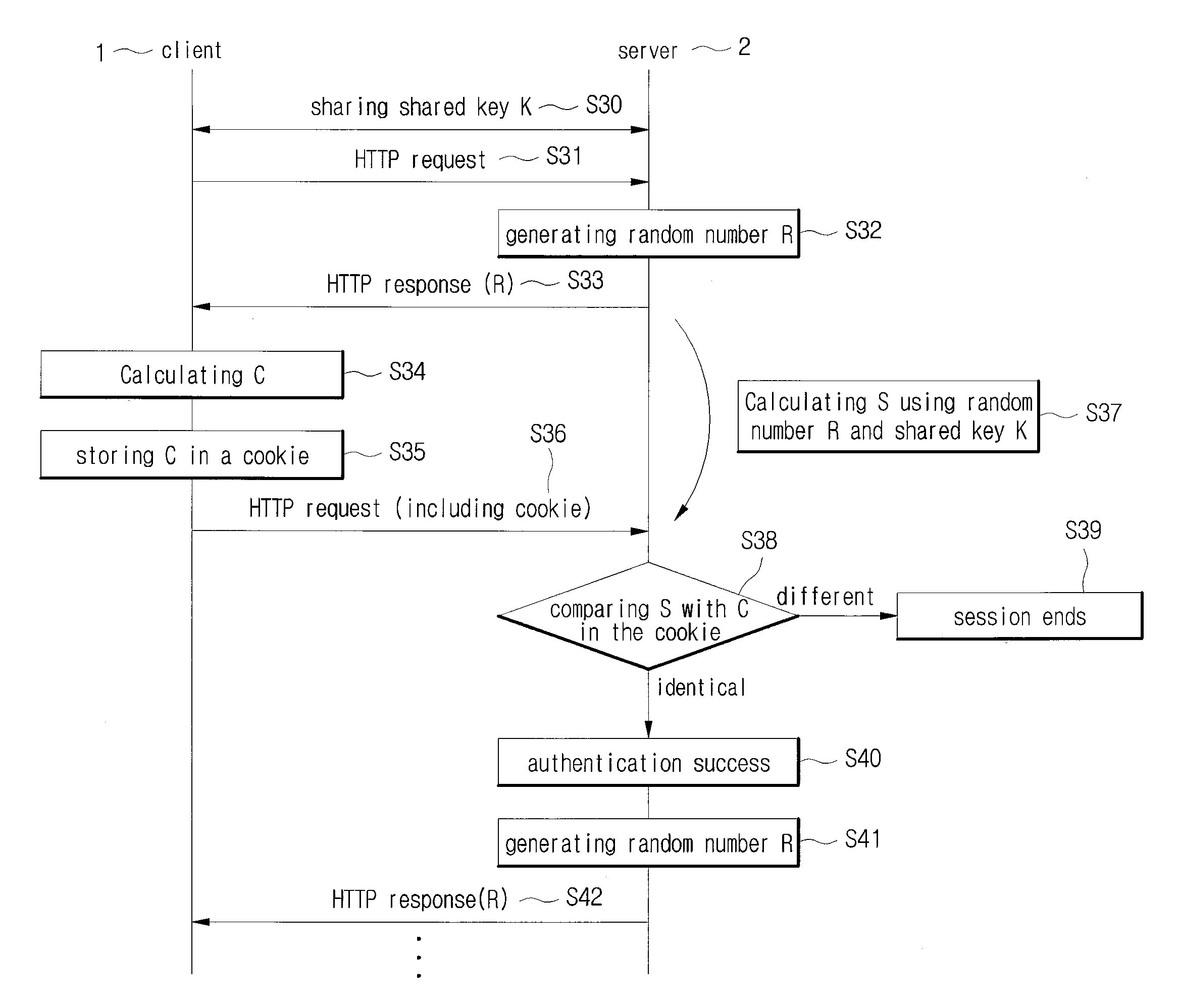
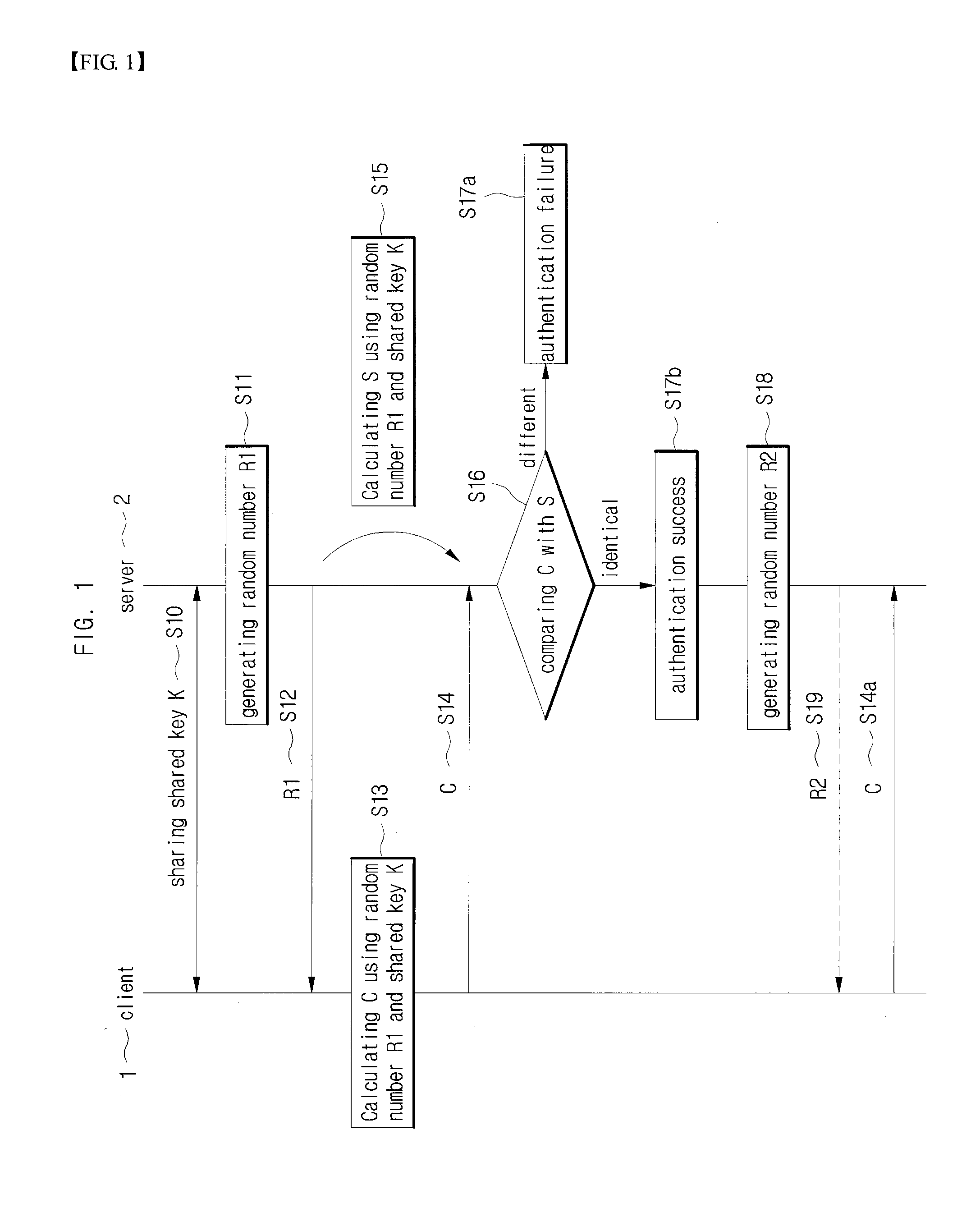
InactiveUS20090094372A1Avoid spreadingReduce errorsMultiple digital computer combinationsTransmissionSession managementNetwork connection
The present invention provides a secure user session managing method and system between a client and a server connected through network in web environment. The user session managing method includes: allowing the server to receive a first HTTP request including a cookie from the client, wherein the cookie includes a client authentication value and the client authentication value is calculated by using a shared key stored in the client and session information included in a HTTP response transmitted right before to the client; comparing a server authentication value with the client authentication value included in the cookie, wherein the server authentication value is calculated by employing the session information and the shared key stored in the server; and determining a transmitter's authentication failure or success of the client according to the result of the comparison. User session can be secured by applying the challenge-response authentication algorithm to the HTTP protocol.
Owner:INHA UNIV RES & BUSINESS FOUNDATION
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com