Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1185 results about "Information Harvesting" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Information Harvesting (IH) was an early data mining product from the 1990s. It was invented by Ralphe Wiggins and produced by the Ryan Corp, later Information Harvesting Inc., of Cambridge, Massachusetts. IH sought to infer rules from sets of data. It did this first by classifying various input variables into one of a number of bins, thereby putting some structure on the continuous variables in the input. IH then proceeds to generate rules, trading off generalization against memorization, that will infer the value of the prediction variable, possibly creating many levels of rules in the process. It included strategies for checking if overfitting took place and, if so, correcting for it. Because of its strategies for correcting for overfitting by considering more data, and refining the rules based on that data, IH might also be considered to be a form of machine learning.
Analysis of data flows in complex enterprise it environments
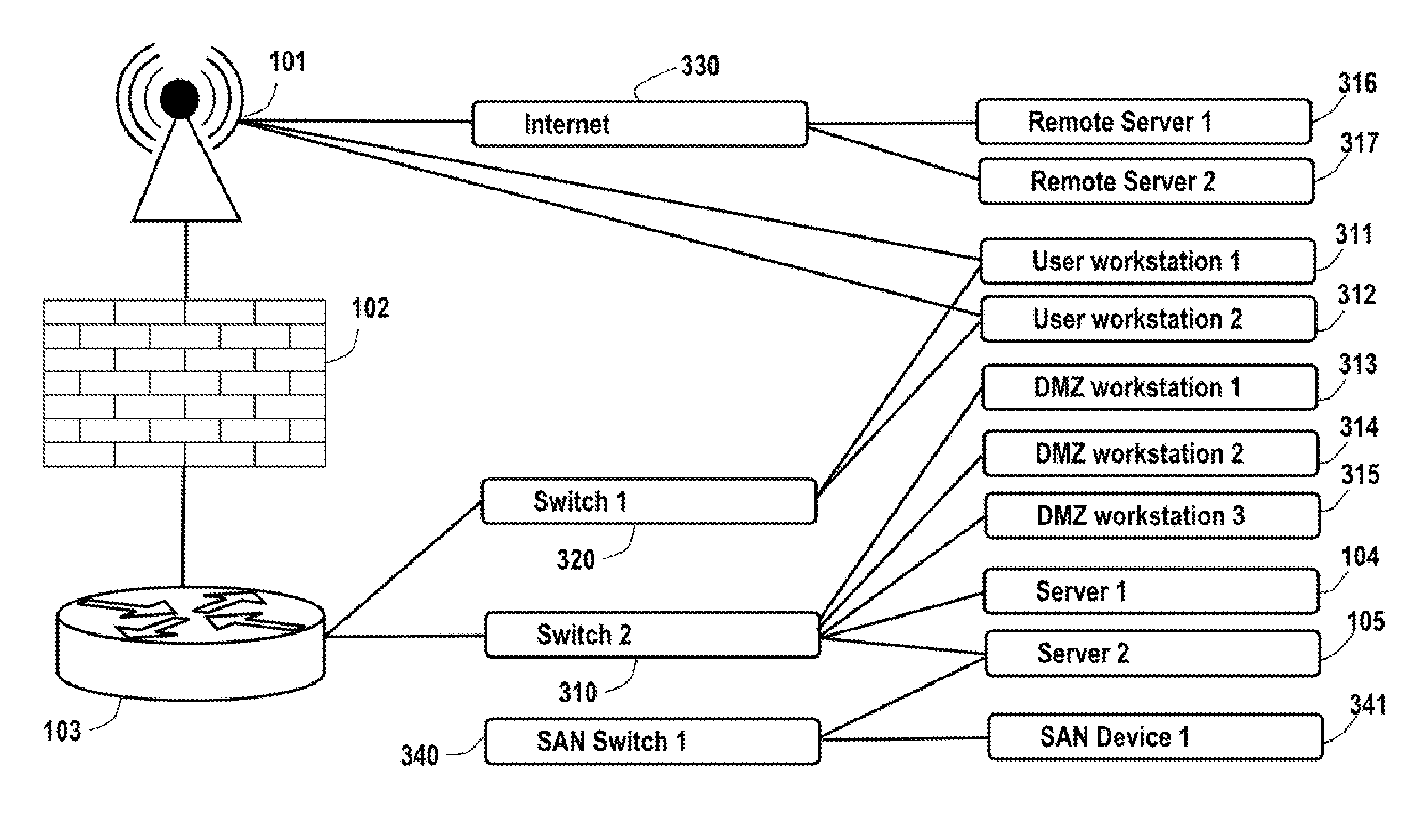
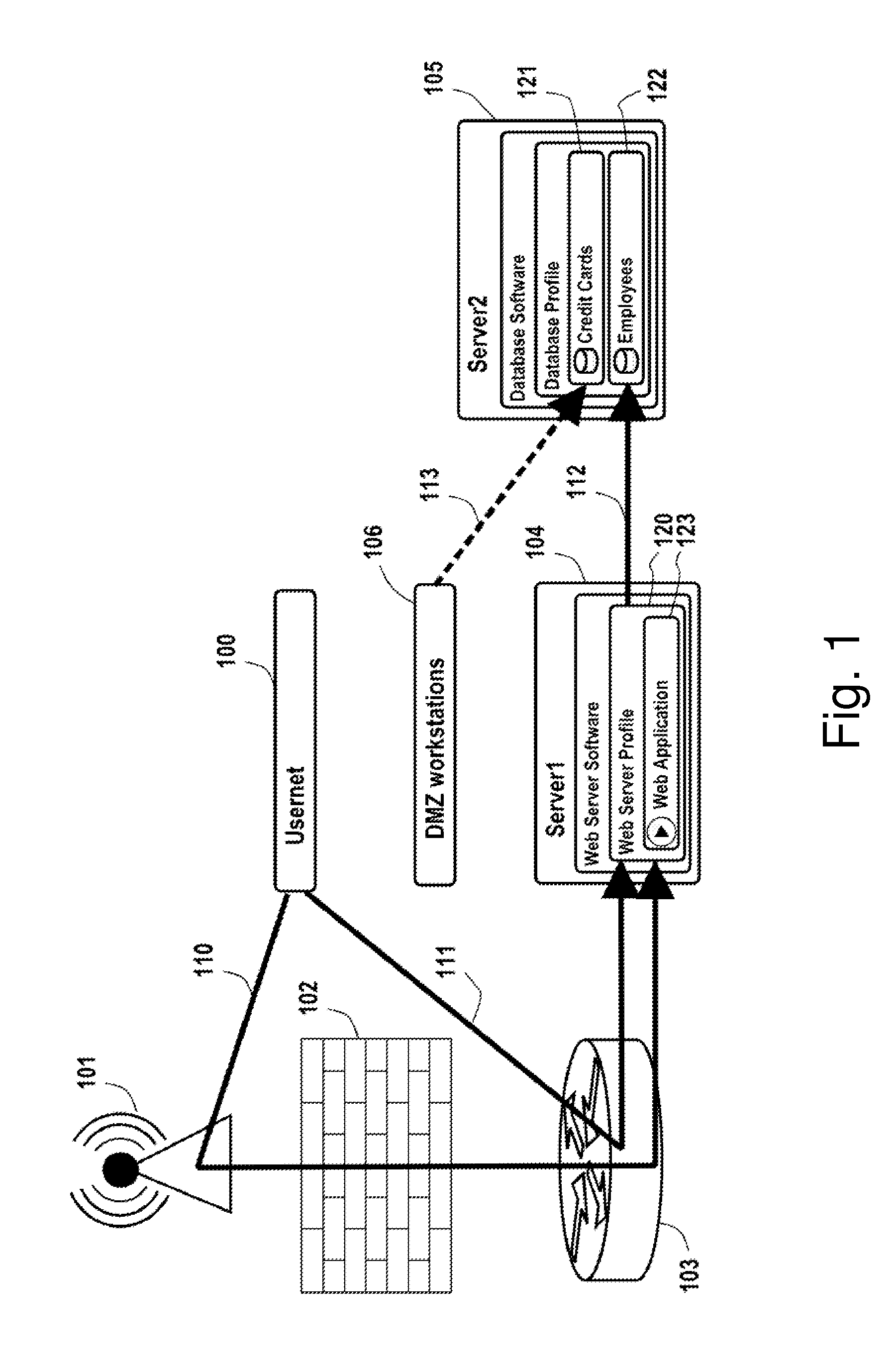
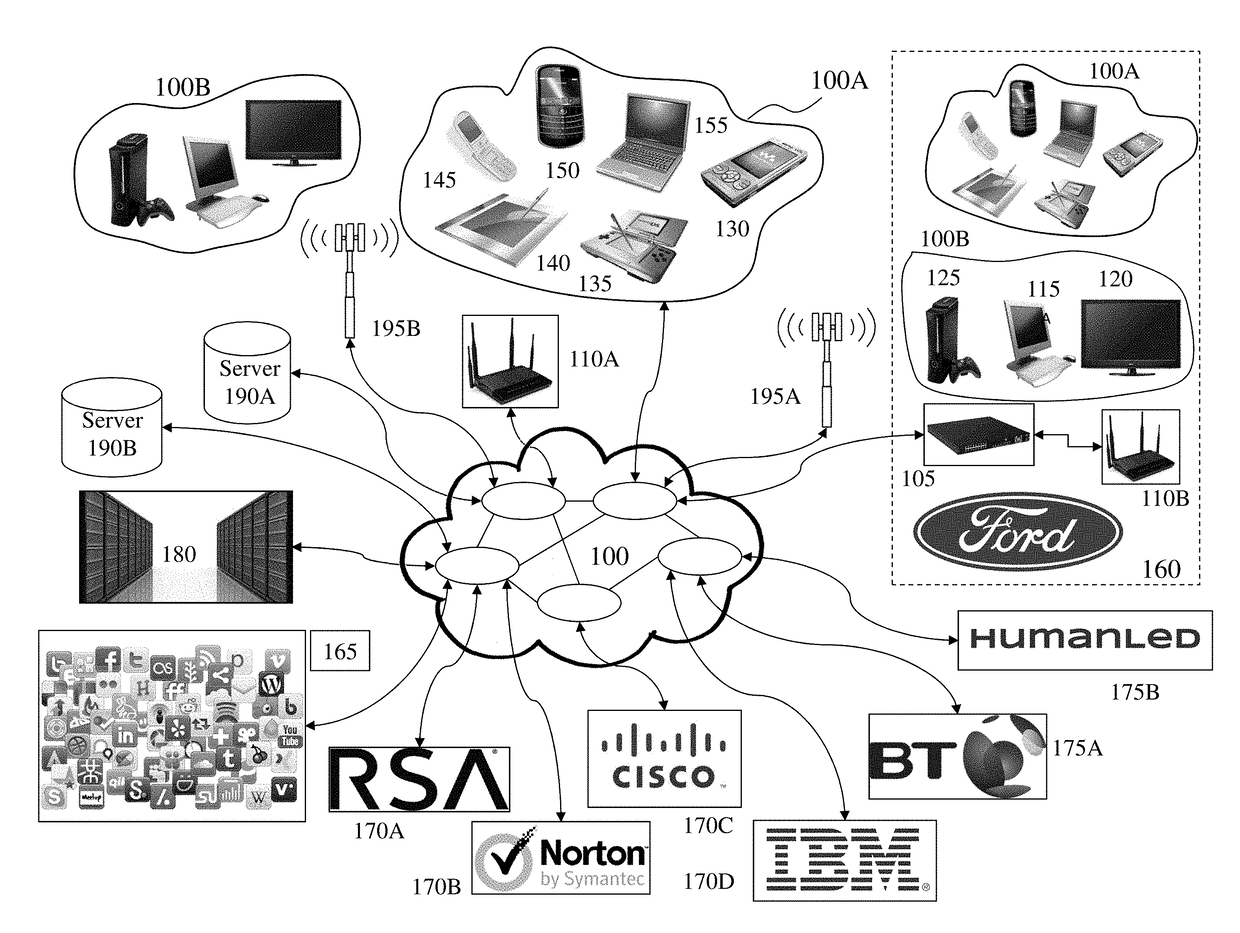
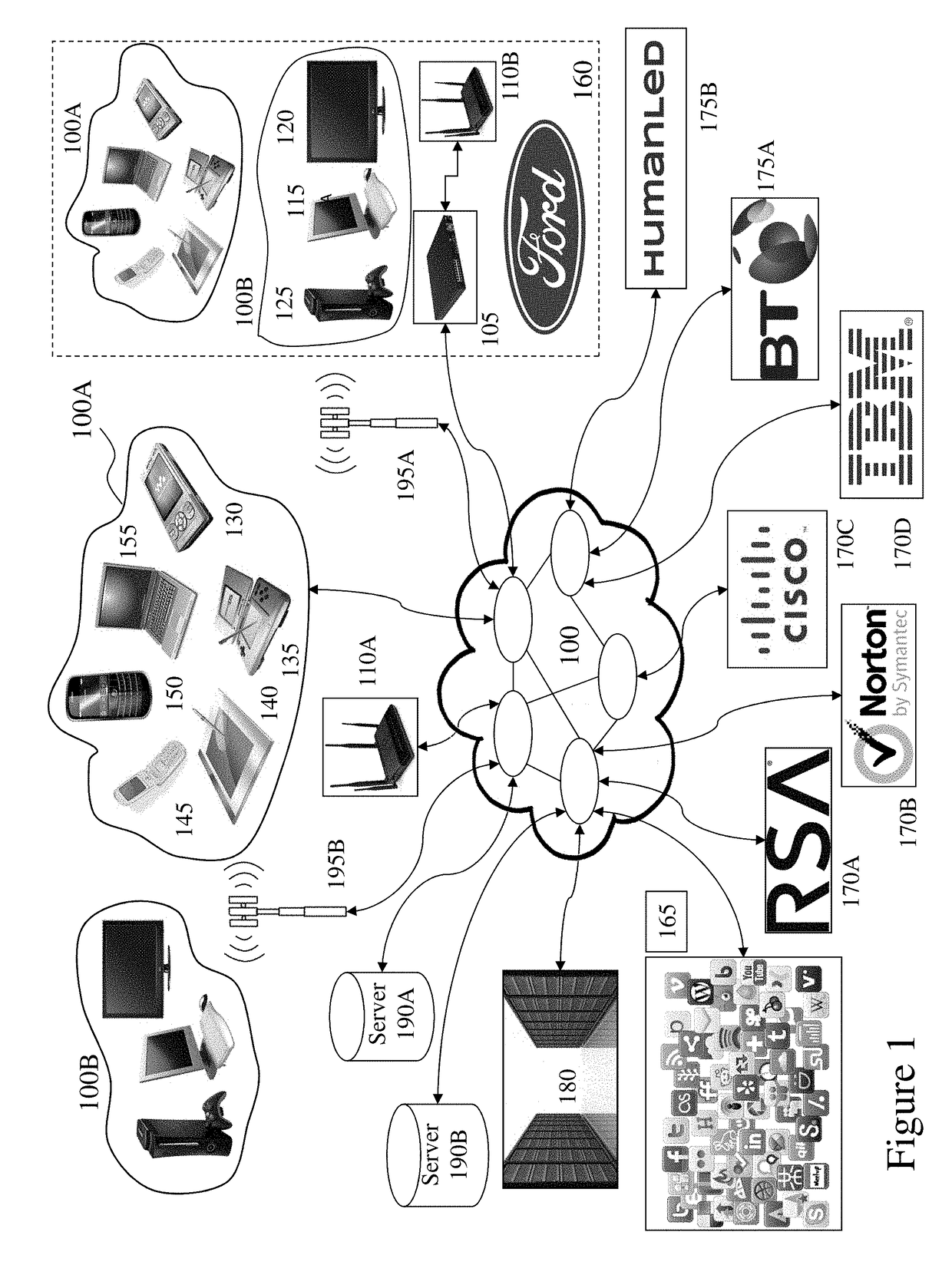
The present technology enables identification, visualization, and analysis of data flows via network components in complex enterprise IT environments including but not limited to servers, workstations, switches, routers, wireless access points, traffic shapers, firewalls, storage systems and SAN systems. The technology is based on a combination of information collection, information filtering, mapping, grouping, marking, report generation, and verification.
Owner:MODELIZEIT INC
Form-based ontology creation and information harvesting
InactiveUS8103962B2Digital data information retrievalNatural language data processingUser inputInformation Harvesting
Owner:BRIGHAM YOUNG UNIV
Optimization of microgrid energy use and distribution
ActiveUS20110035073A1Low costCostBatteries circuit arrangementsLevel controlPersonalizationMicrogrid
Owner:INTEGRAL ANALYTICS
Roadside assistance service provider assignment system
Owner:ALLSTATE INSURANCE
Dynamic information extraction with self-organizing evidence construction
InactiveUS20050154701A1Digital data processing detailsSpecial data processing applicationsPaper documentData analysis system
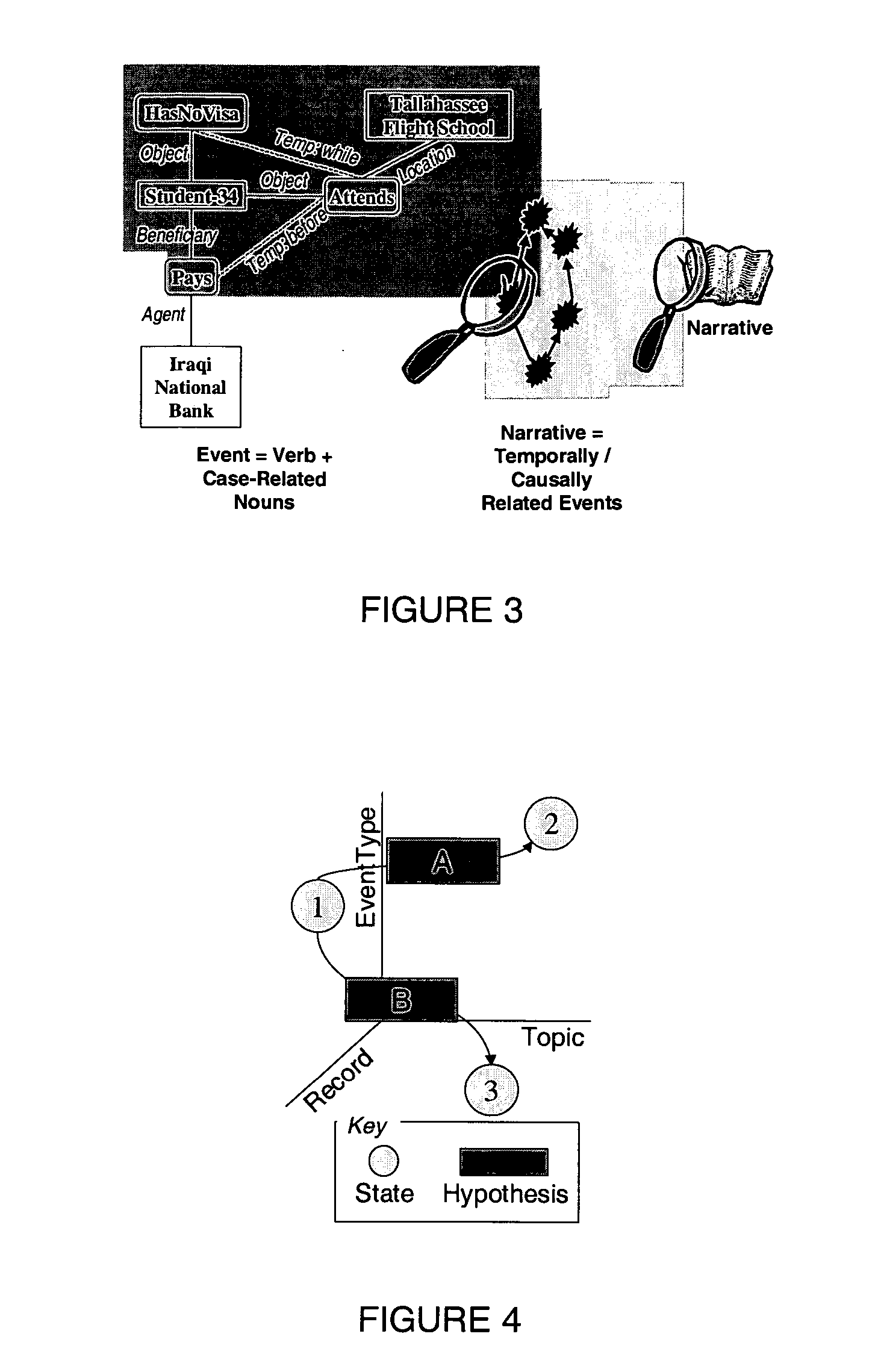
A data analysis system with dynamic information extraction and self-organizing evidence construction finds numerous applications in information gathering and analysis, including the extraction of targeted information from voluminous textual resources. One disclosed method involves matching text with a concept map to identify evidence relations, and organizing the evidence relations into one or more evidence structures that represent the ways in which the concept map is instantiated in the evidence relations. The text may be contained in one or more documents in electronic form, and the documents may be indexed on a paragraph level of granularity. The evidence relations may self-organize into the evidence structures, with feedback provided to the user to guide the identification of evidence relations and their self-organization into evidence structures. A method of extracting information from one or more documents in electronic form includes the steps of clustering the document into clustered text; identifying patterns in the clustered text; and matching the patterns with the concept map to identify evidence relations such that the evidence relations self-organize into evidence structures that represent the ways in which the concept map is instantiated in the evidence relations.
Owner:TECHTEAM GOVERNMENT SOLUTIONS
Communication statistic information collection apparatus
ActiveUS20050276230A1Solve large capacityCost of apparatus can be reducedError preventionFrequency-division multiplex detailsInformation HarvestingOperating system
Owner:ALAXALA NETWORKS
Method and system for automatic product searching, and use thereof
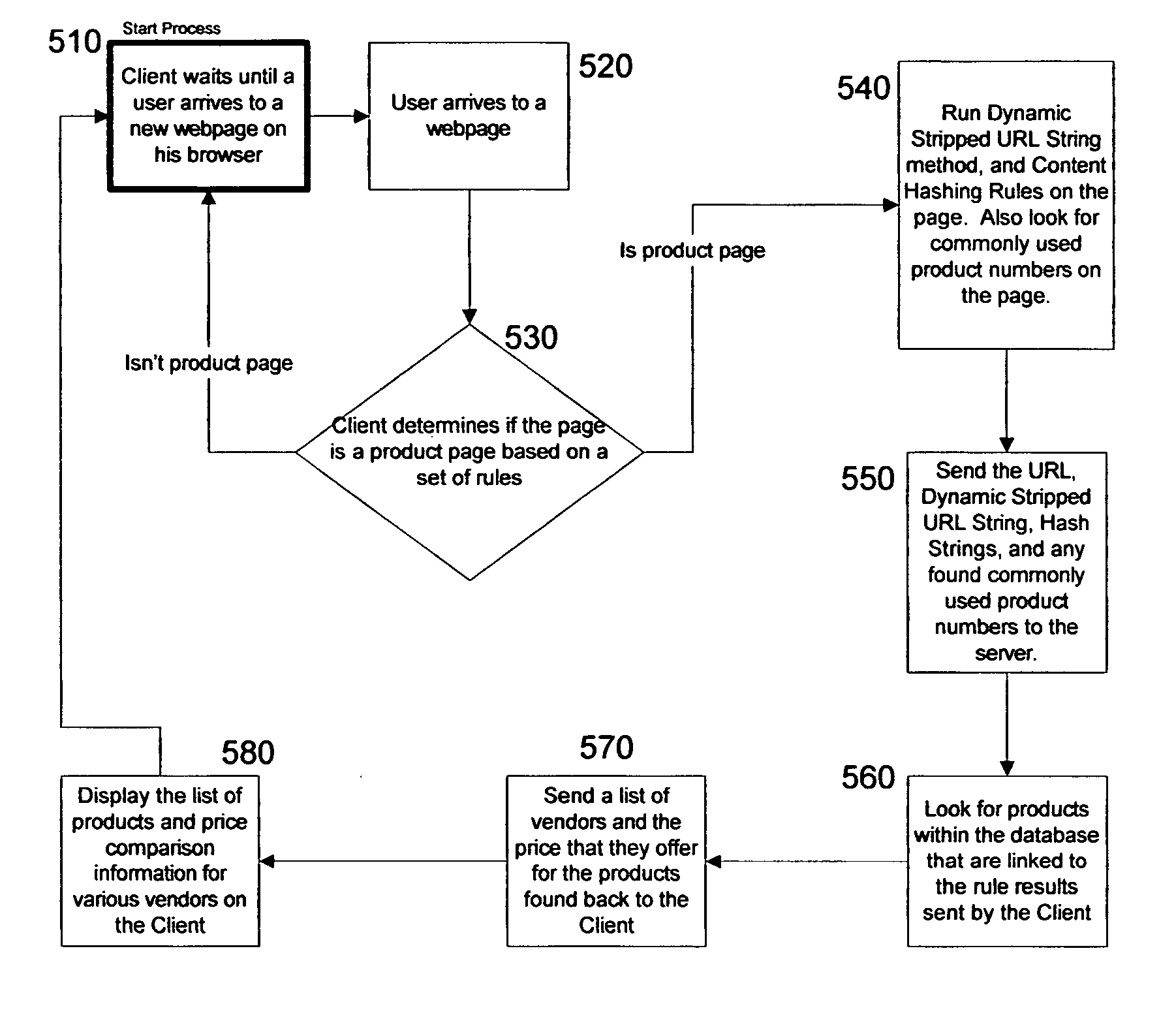
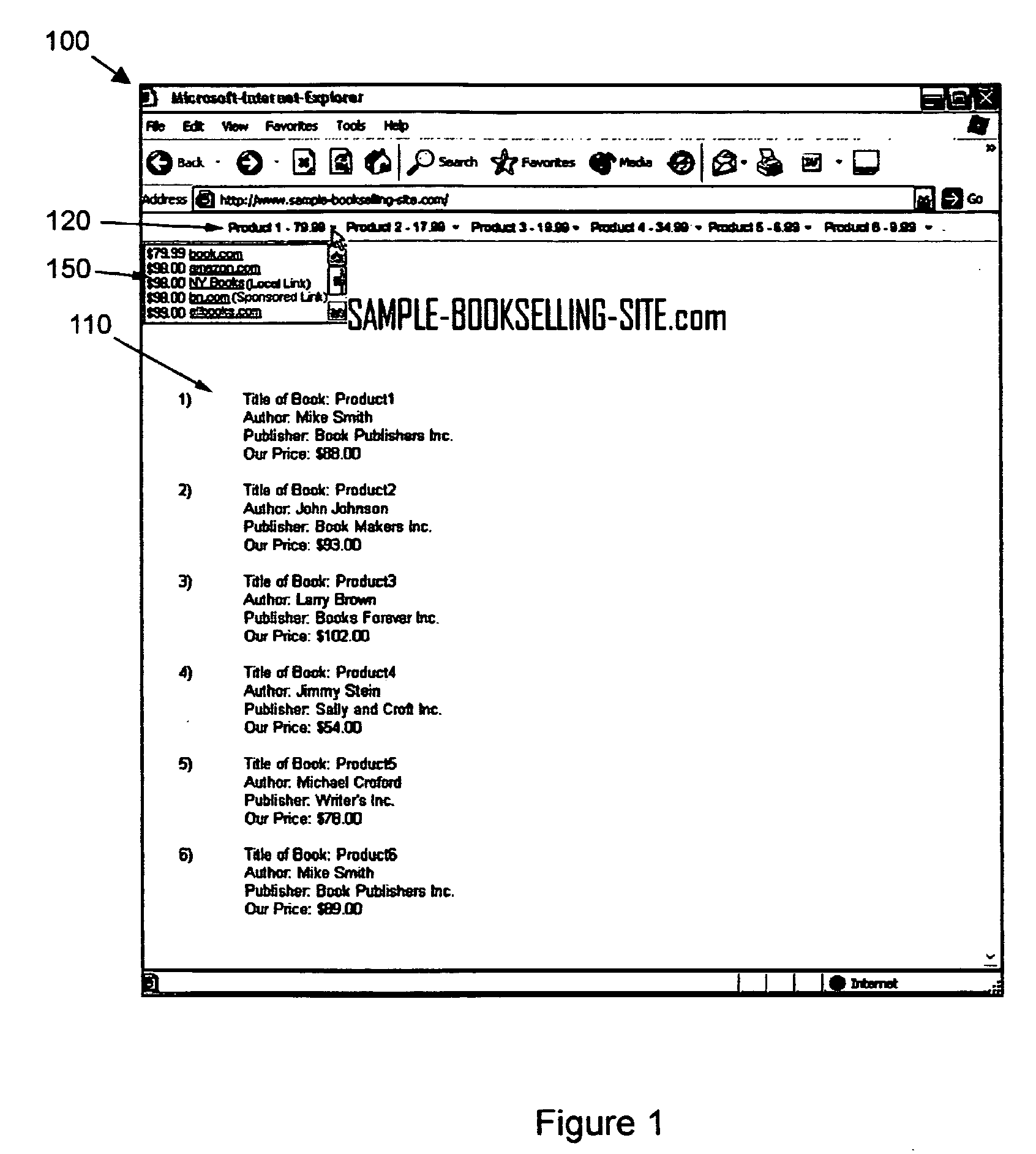
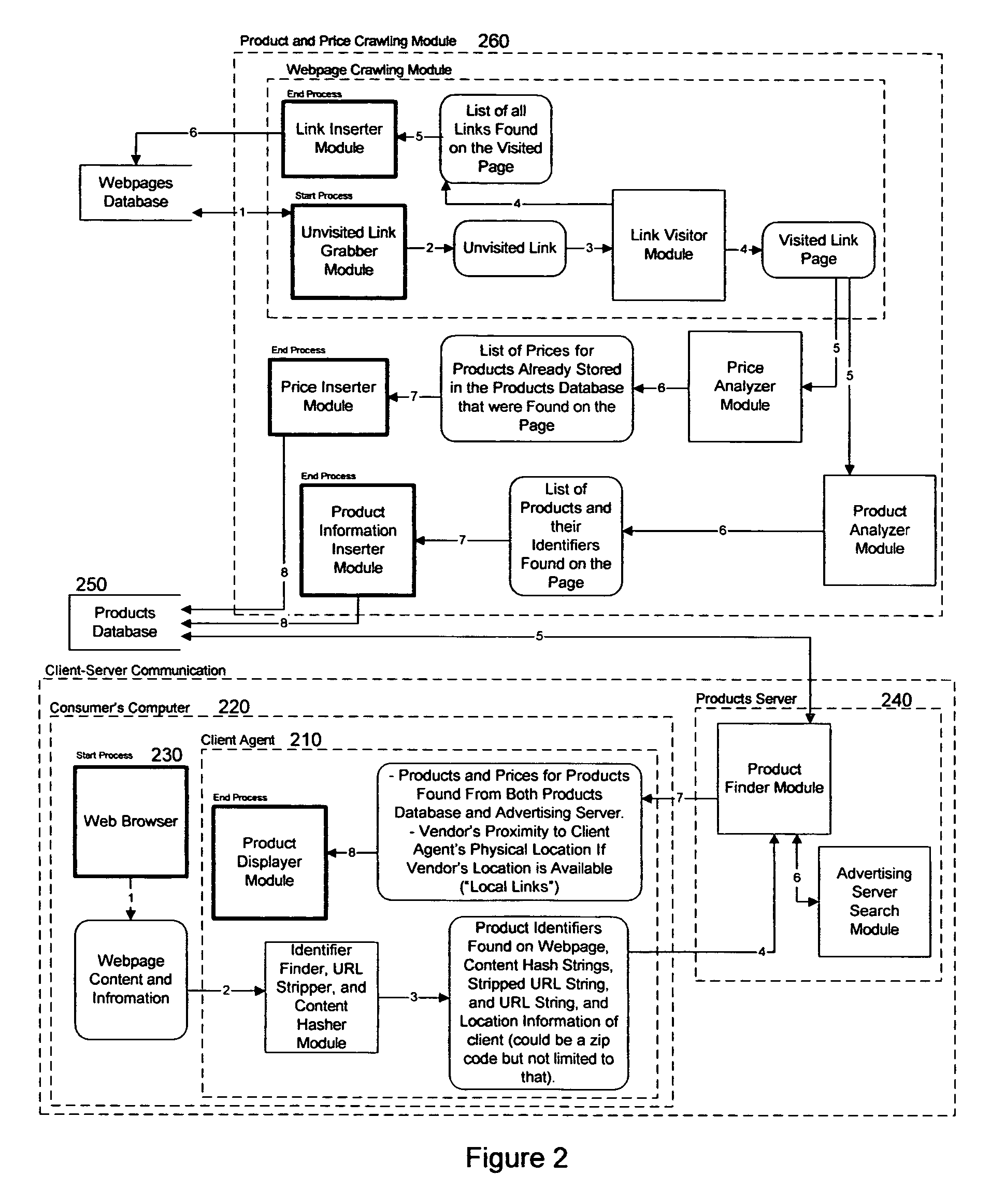
A client application monitors web pages visited by a consumer and determines if the visited web page is product oriented and, if so, then contacts a product server to automatically retrieve and display corresponding product purchasing information if available in product centric database. However, if the web page is not found in the database, it and its product information is added thereto. The database is created by a product information gathering web crawler and a second web product price crawler using the harvested product information to find prices corresponding to the product on unvisited web pages.
Owner:ZICHERMAN AMIR SHLOMO
Packet forwarding device equipped with statistics collection device and statistics collection method
InactiveUS20050013300A1Accurate statistic informationIncrease speedError preventionTransmission systemsDecision tableInformation Harvesting
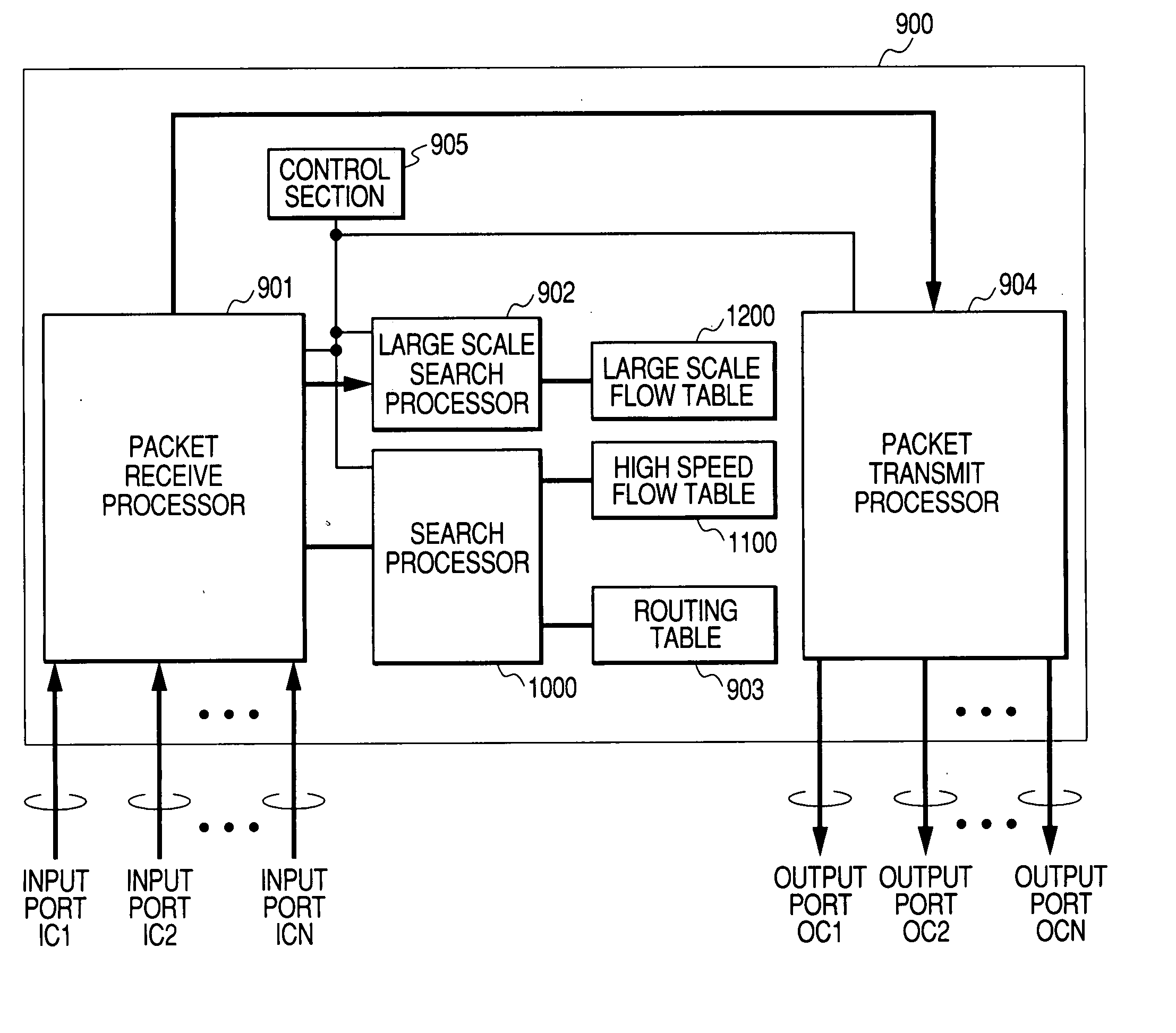
A packet forwarding device equipped with a statistics collection device and statistics collection method for high speed ports at a low cost while maintaining the required statistical accuracy for each flow. In order to collect a statistic flow with the required accurate statistic information this device contains a high speed flow table, a flow table made up of many flow entries, a search decision table to decide whether to search the high speed flow table or large volume flow table; and the table to be searched is decided when a packet is received. The accuracy of the statistic information for the flow requiring accurate statistic information is guaranteed by the high speed flow table. Further by setting the large volume flow table and sampling rate as needed, statistic information for many flow entries can be collected with a sufficient flow of sampled statistic information, without lowering packet forwarding performance.
Owner:ALAXALA NETWORKS
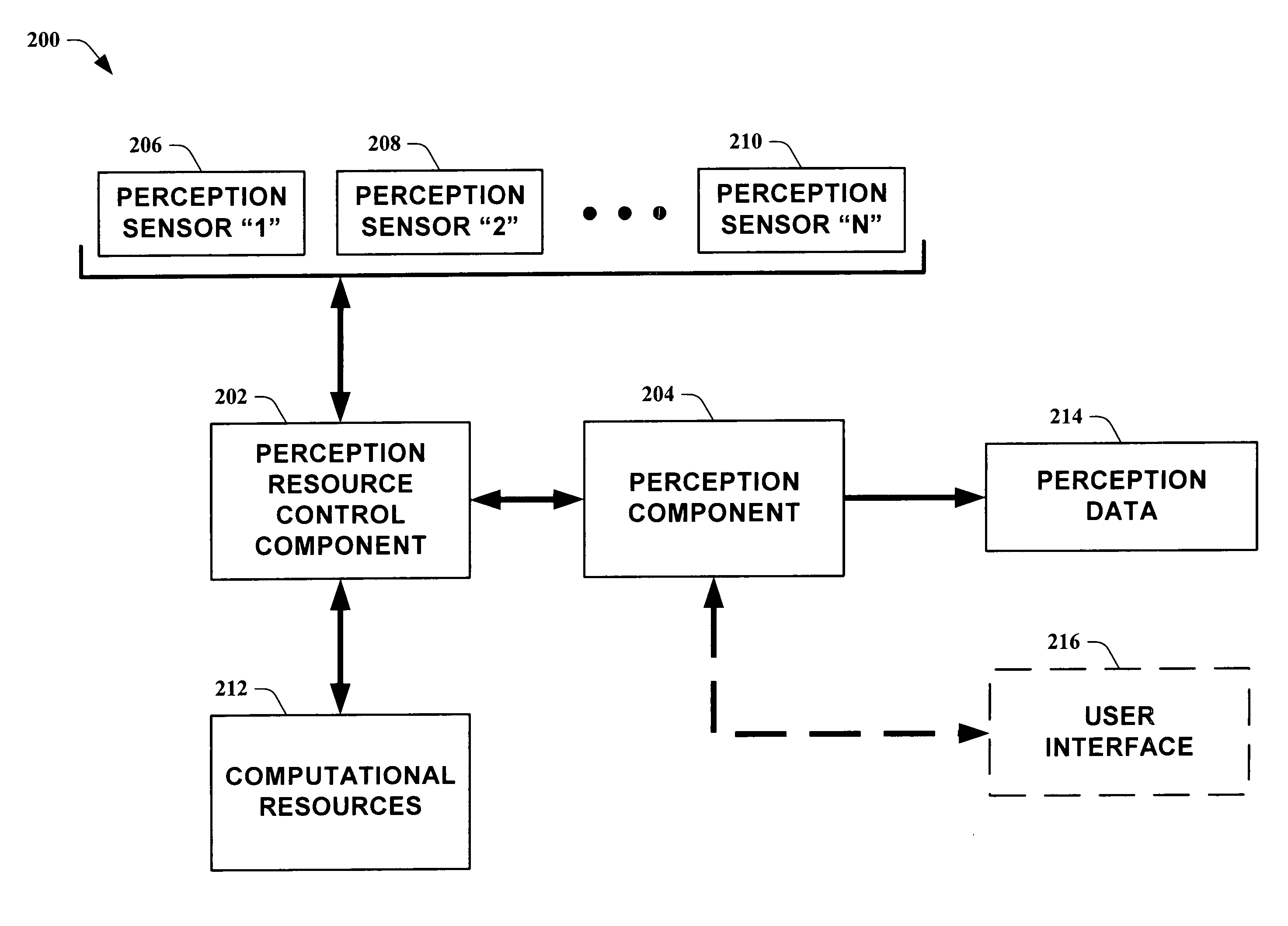
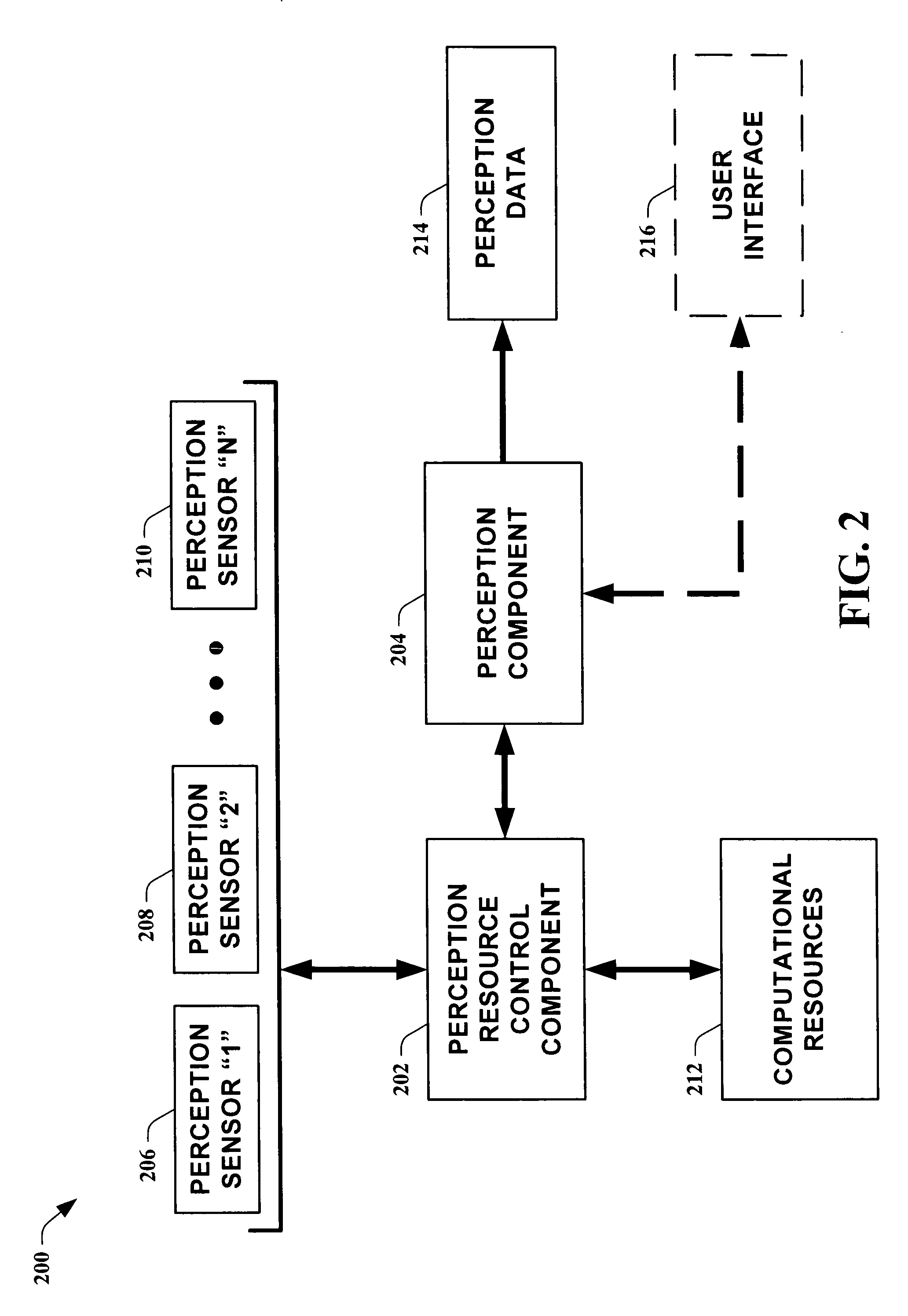
Systems and methods for guiding allocation of computational resources in automated perceptual systems
ActiveUS20050132378A1Facilitate in inferring human-centric notion of contextReducing computational resource burdenDigital computer detailsBiological neural network modelsPattern perceptionInformation Harvesting
The present invention leverages analysis methods, such as expected value of information techniques, rate-based techniques, and random selection technique, to provide a fusion of low-level streams of input data (e.g., raw data) from multiple sources to facilitate in inferring human-centric notions of context while reducing computational resource burdens. In one instance of the present invention, the method utilizes real-time computations of expected value of information in a greedy, one-step look ahead approach to compute a next best set of observations to make at each step, producing “EVI based-perception.” By utilizing dynamically determined input data, the present invention provides utility-directed information gathering to enable a significant reduction in system resources. Thus, of the possible input combinations, the EVI-based system can automatically determine which sources are required for real-time computation relating to a particular context.
Owner:MICROSOFT TECH LICENSING LLC
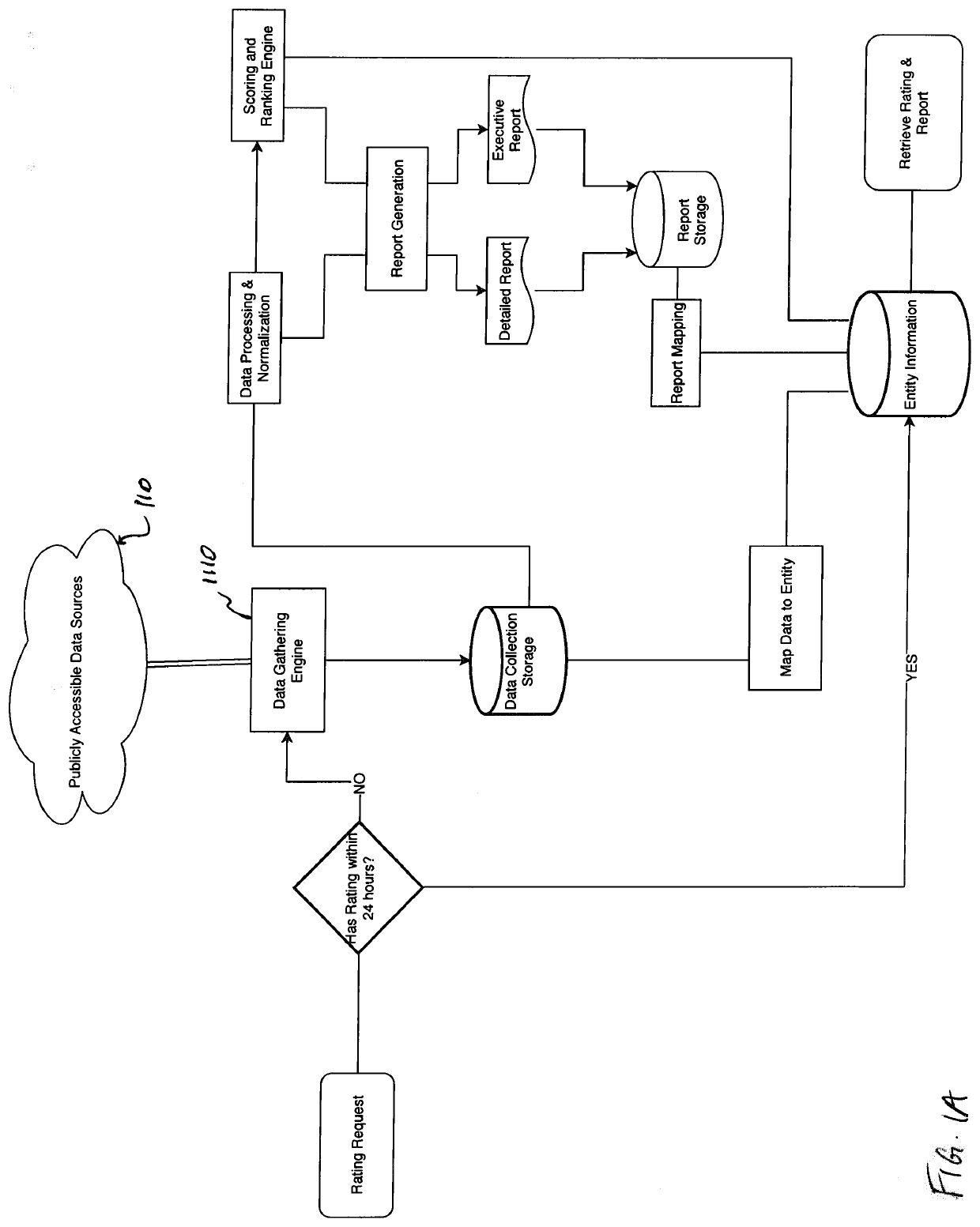
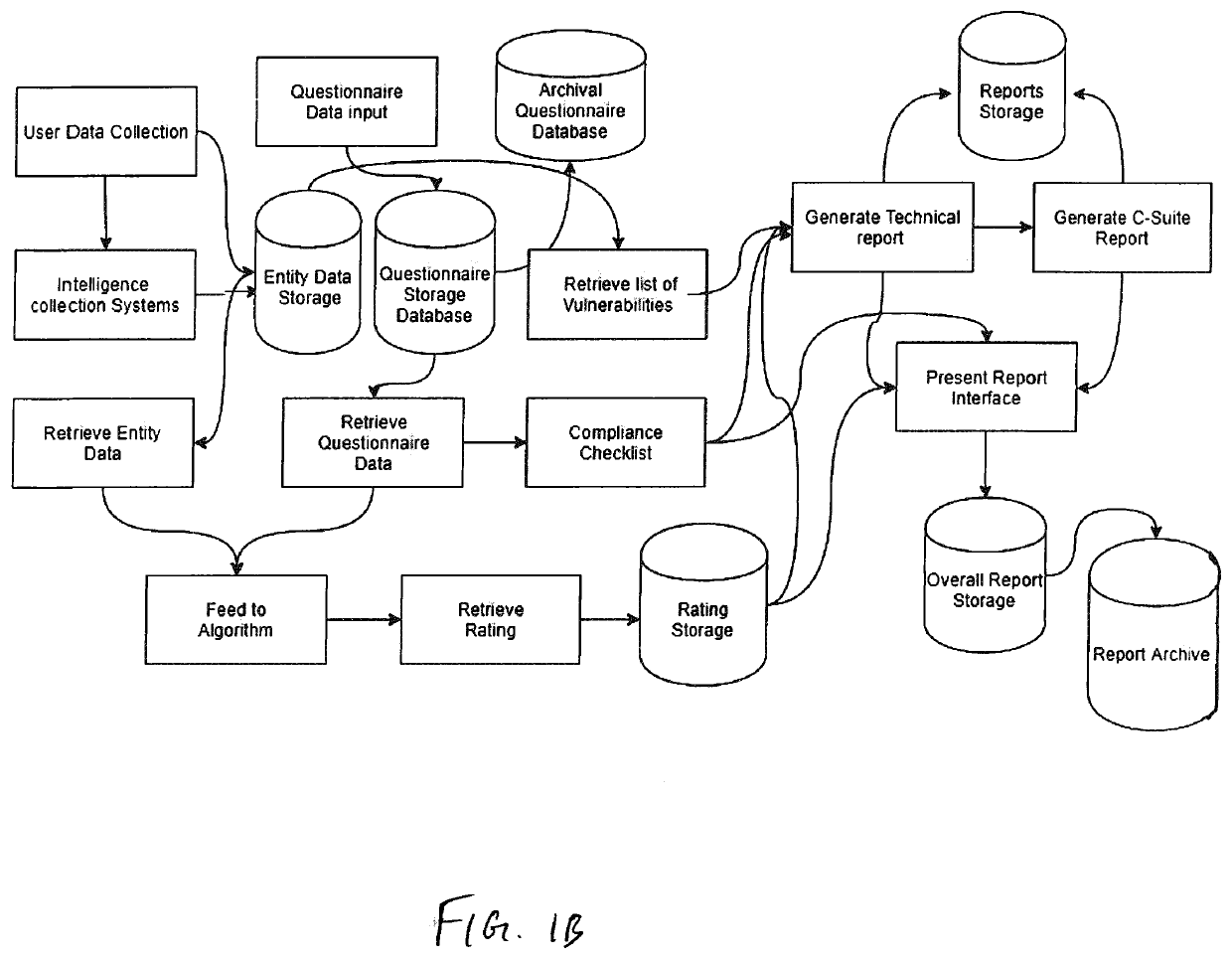
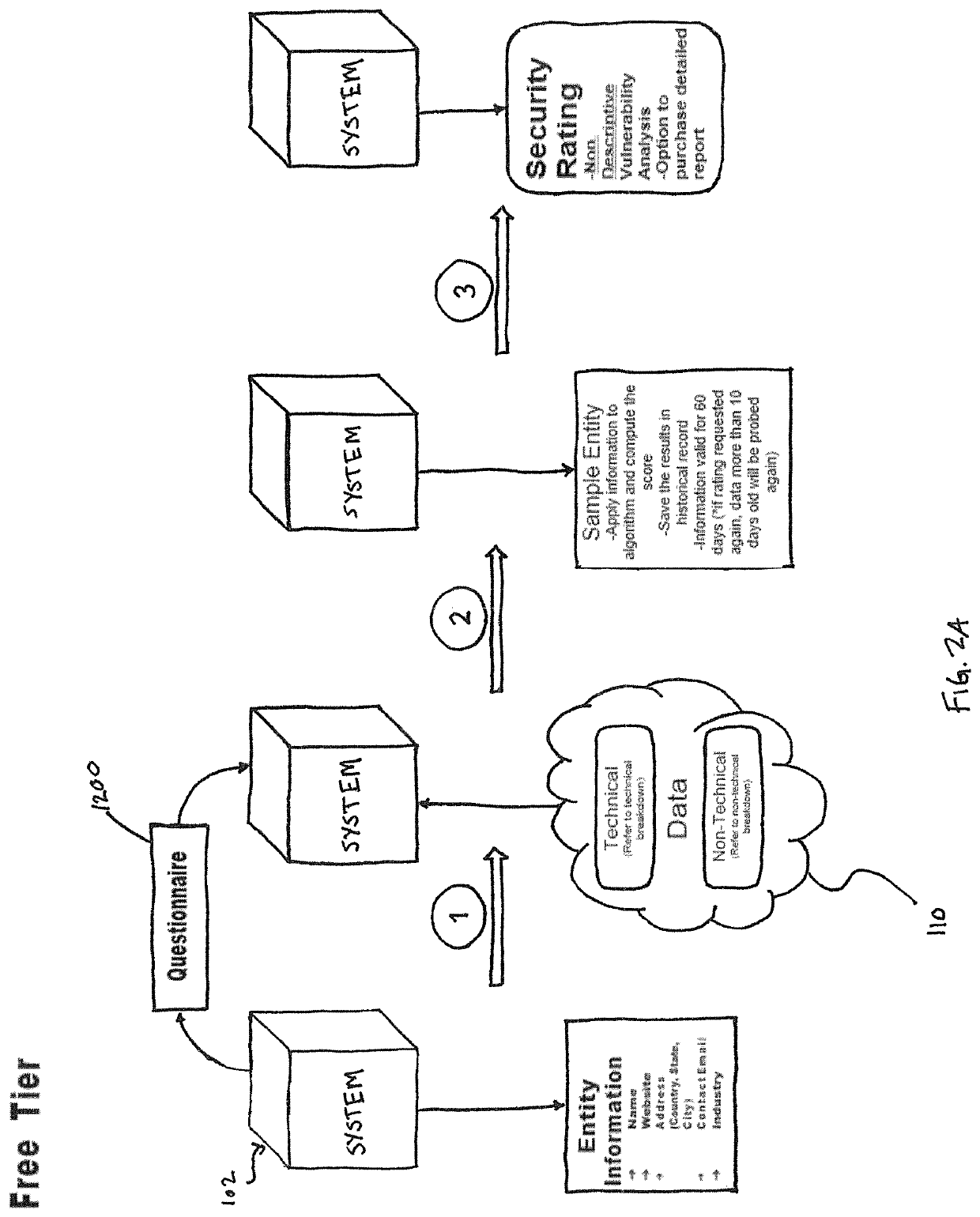
System and method for determining cybersecurity rating and risk scoring
A system for deriving a rating representative of a level of cybersecurity of a user is configured to execute steps of a method comprising (i) requesting, from the user, identifying information about the user; (ii) requesting, from the user, input in response to a set of predetermined questions provided to the user based on the identifying information about the user; (iii) collecting, based on at least the identifying information, public domain data about the user and data from the user's digital assets; and (iv) computing, based on the collected data and the input to the set of predetermined questions provided by the user, a numerical value defining the cybersecurity rating.
Owner:CYBERLAB
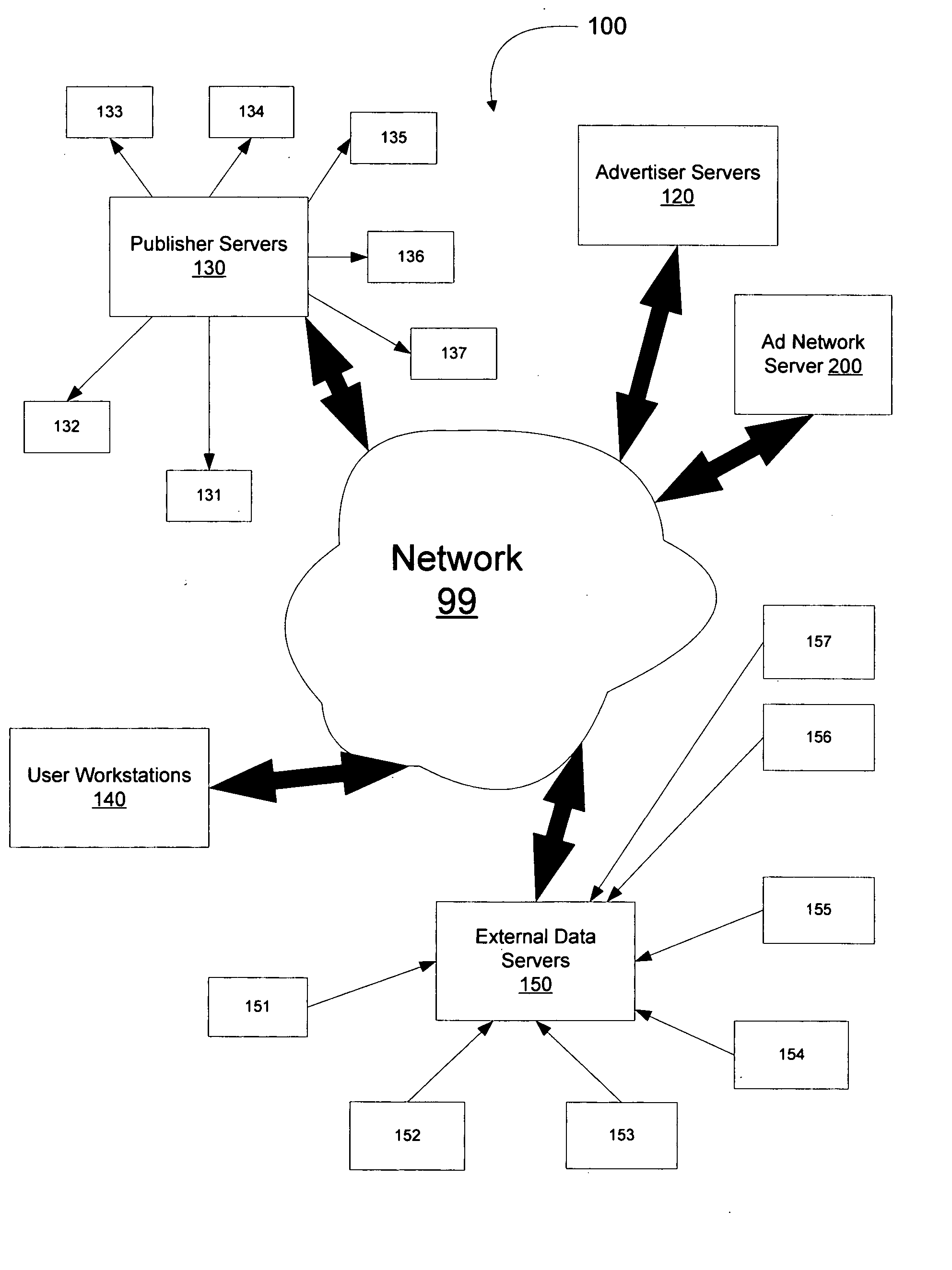
Method and system for advertisement campaign optimization
InactiveUS20050182676A1Improve efficiencyImproving flexibleMarketingSpecial data processing applicationsExternal dataNetwork service
A system and method is disclosed for optimizing advertisement campaigns in consideration data including information not relating to the advertisement campaigns according to the advertisement network server. A campaign optimization unit optimizes advertisement campaign in consideration of data retrieve from data servers including local advertisement network server and external data servers that physically located away from the advertisement network server. Information collectors are used to obtain, collect, and validate data from local ad network server, and data from various sources via network. The system will consider any authorized information in order to maximize the effectiveness of automatic campaign optimization.
Owner:CHAN BRIAN KA KUI
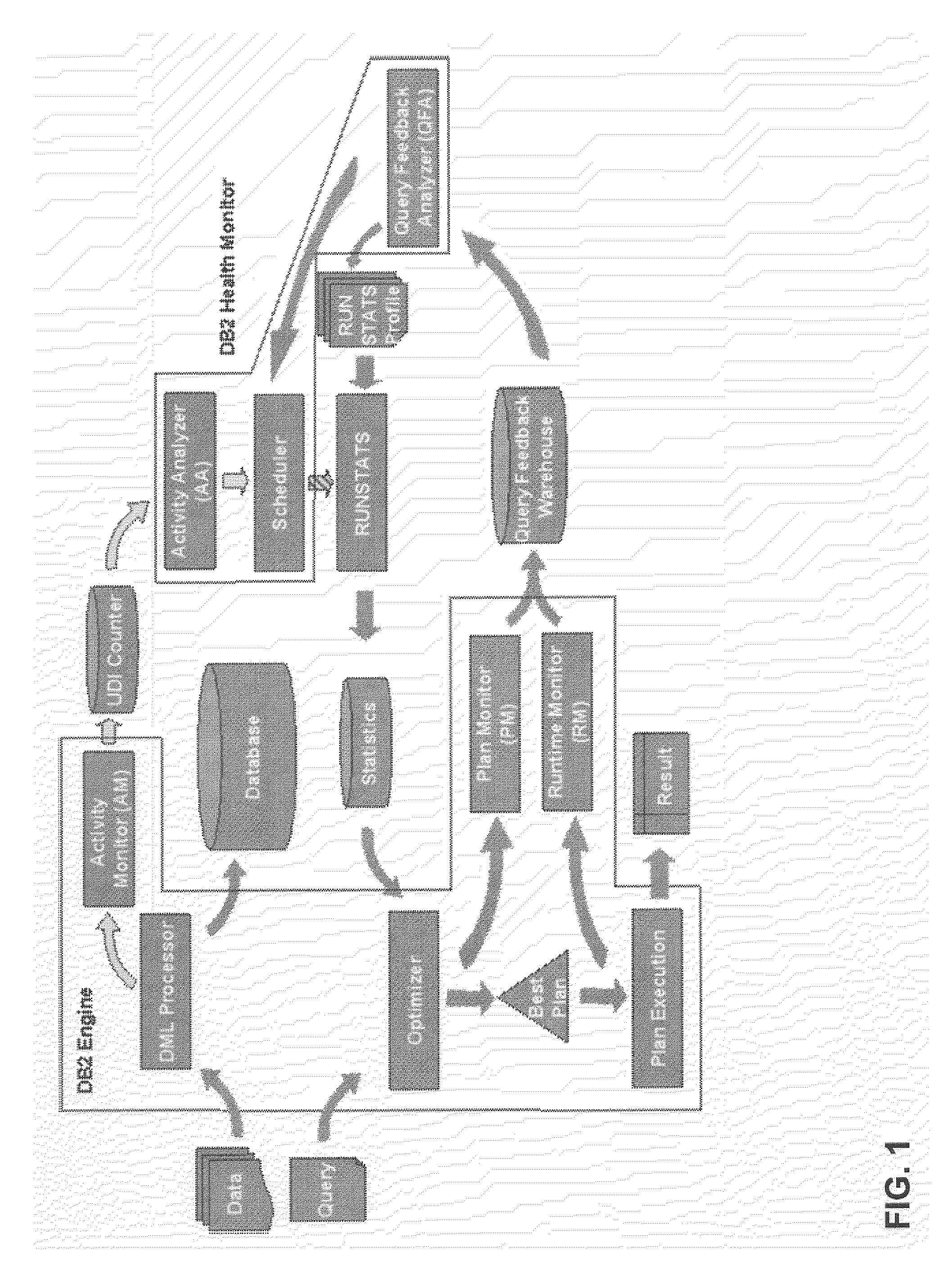
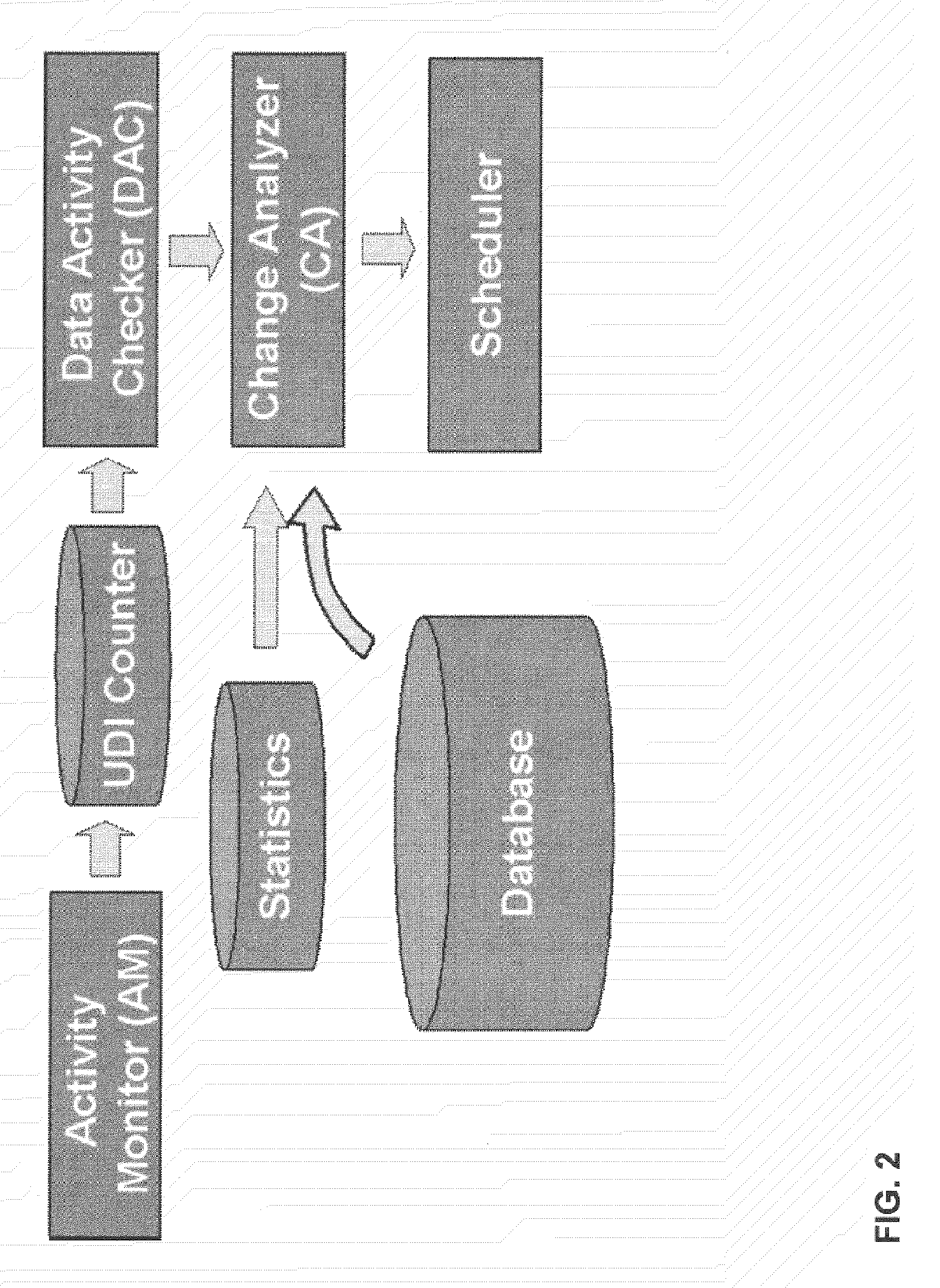
System and method for updating database statistics according to query feedback
ActiveUS20080133454A1Fast executionSmall sizeData processing applicationsDigital data information retrievalLearning basedQuery optimization
An autonomic tool that supervises the collection and maintenance of database statistics for query optimization by transparently deciding what statistics to gather, when and in what detail to gather them. Feedback from data-driven statistics collection is simultaneously combined with feedback from query-driven learning-based statistics collection, to better process both rapidly changing data and data that is queried frequently. The invention monitors table activity and decides if the data in a table has changed sufficiently to require a refresh of invalid statistics. The invention determines if the invalidity is due to correlation between purportedly independent data, outdated statistics, or statistics that have too few frequent values. Tables and column groups are ranked in order of statistical invalidity, and a limited computational budget is prioritized by ranking subsequent gathering of improved statistics. Multiple tables can have their statistics refreshed over time, and the maintenance effort is concentrated on the most important tables.
Owner:WORKDAY INC
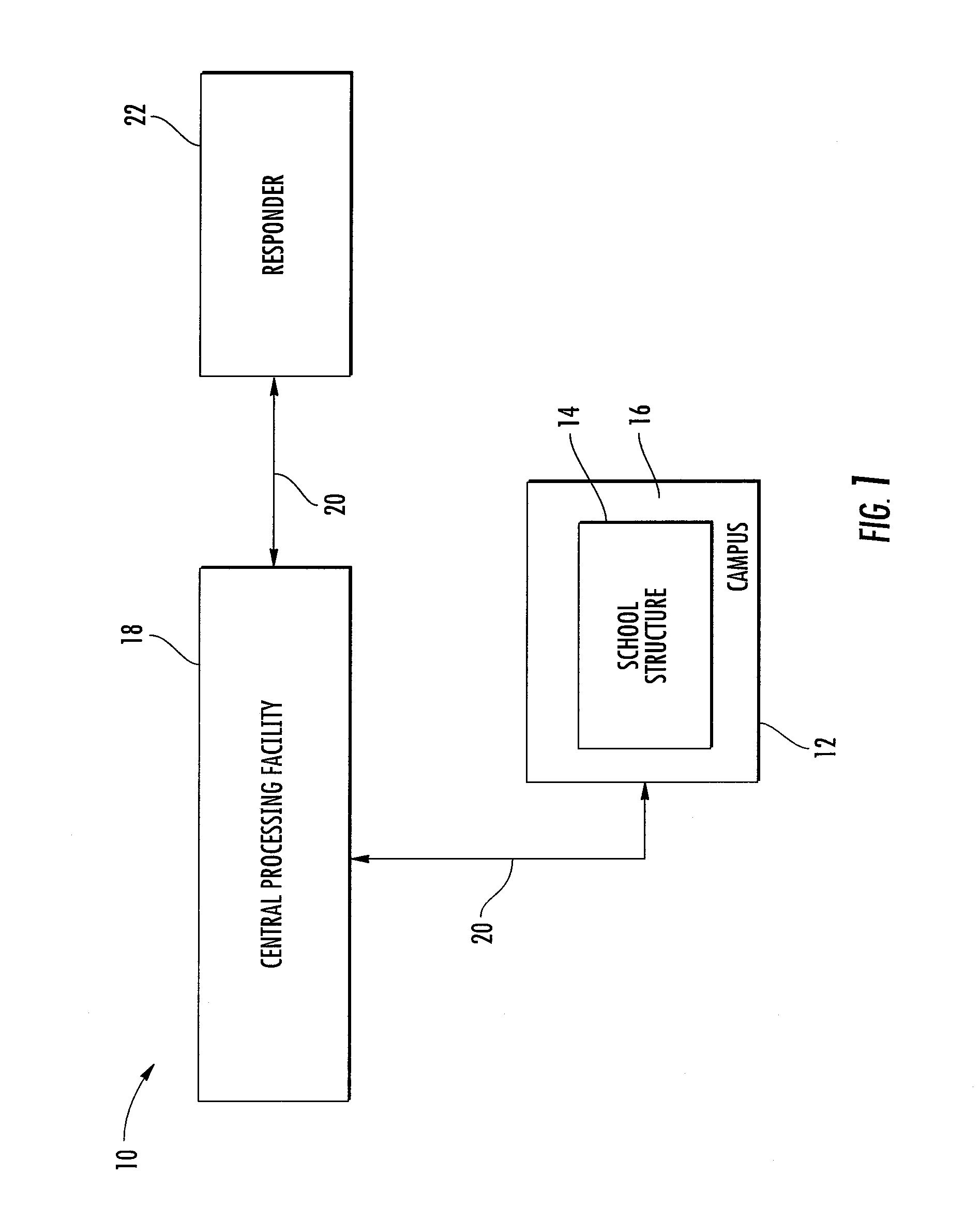
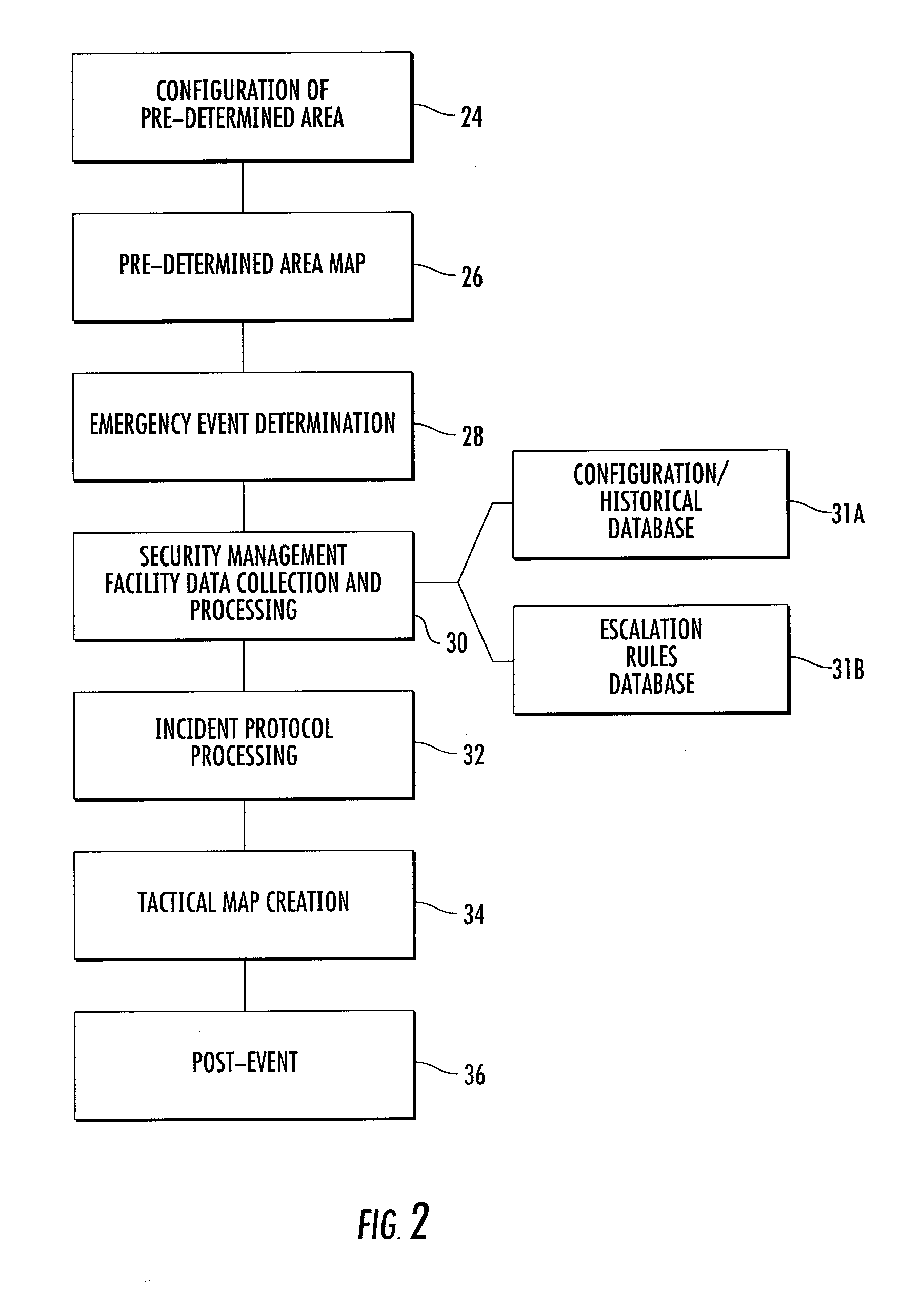
Systems and methods for monitoring and tracking emergency events within a defined area
InactiveUS20140368643A1Color television detailsClosed circuit television systemsInformation HarvestingInformation seeking
The present invention provides a system, methods, and apparatus to provide surveillance, security, alerting, and tracking functionality. The security system comprises the necessary hardware and software to provide surveillance of a pre-determined area, using a central processing facility located off site to allow for an independent monitoring, information gathering, and decision making component. Such information is collected and the data can be converted into a tactical map. The tactical map includes useful information which can be supplied to responders in an easy to view and understand format.
Owner:PREVVIO IP HLDG
Security threat information gathering and incident reporting systems and methods
ActiveUS20170346846A1Improve the level ofEnhance client communicationTransmissionEvent levelCountermeasure
A common misconception equates information with intelligence. To transform information into intelligence a number of analytical steps must occur within a framework designed to yield very specific datum associable with other raw or formulated datum, that provides an answer or solution to a sub-problem. Every organization has threats and risks including cyber threats, threats to infrastructure, etc. that can impact the organization on many levels. However, most organizations do not understand how to quantify and assess these risks / threats yet alone assess different preemptive actions for mitigating impact. It would therefore be beneficial to provide organizations with a software based system that provides threat information gathering, incident reporting, and asset identification / valuation as part of its compounded intelligence and supports predictive context specific analysis of risks and countermeasures. Further, distributed countermeasure monitoring provides incident levels of known and unknown, or yet to be categorized threats.
Owner:FINDLAY VALERIE ANN
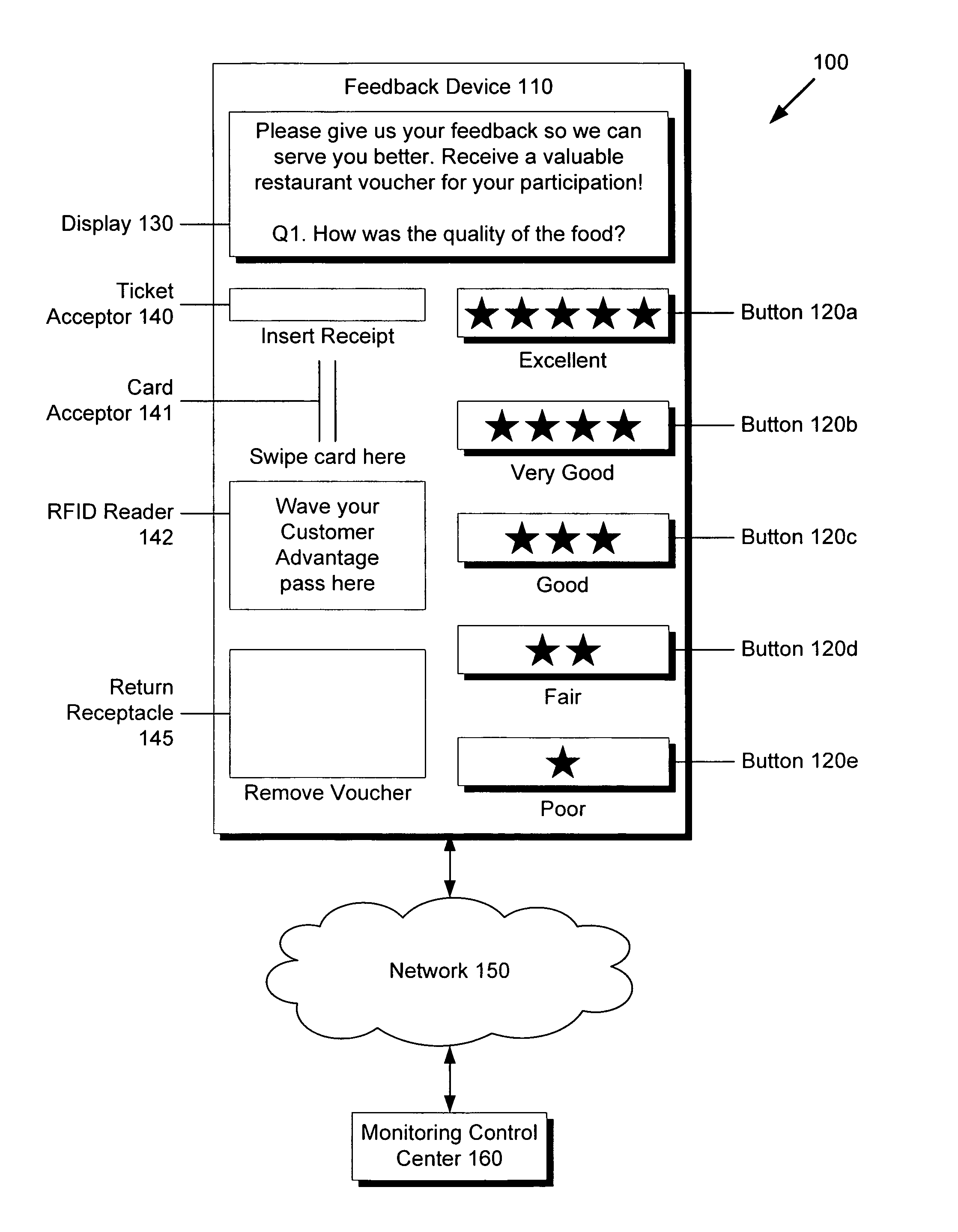
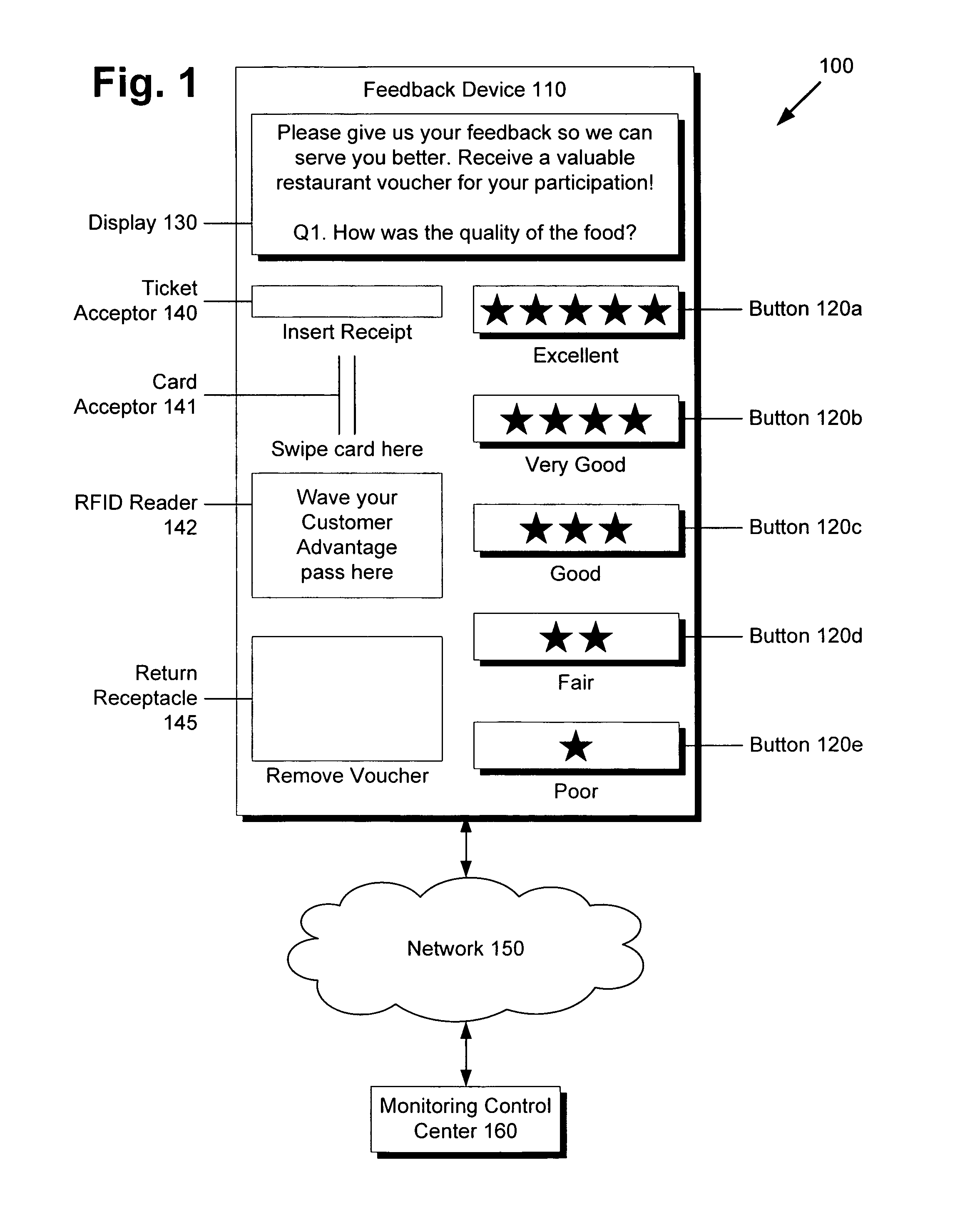
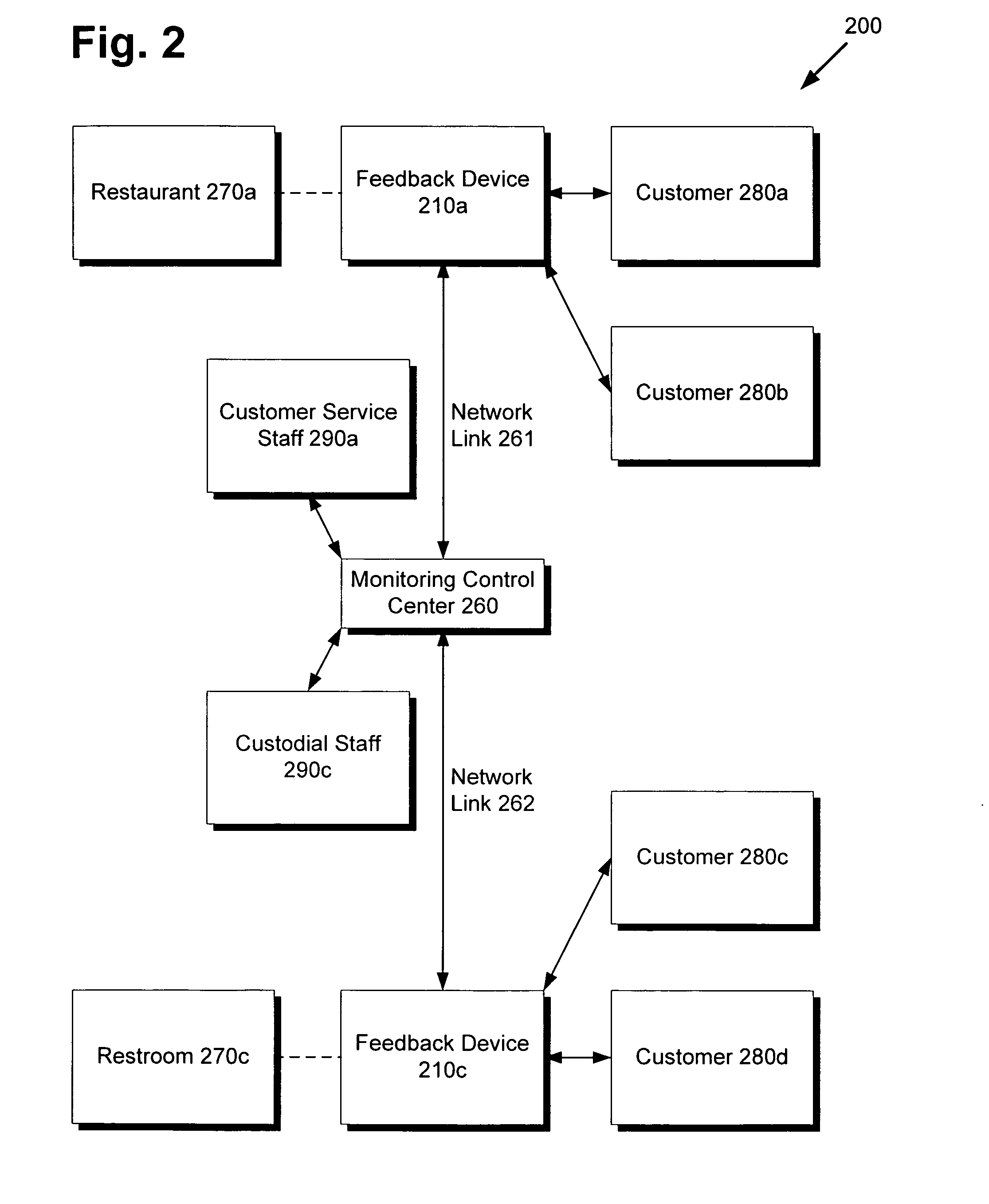
System and method for distributed and real-time collection of customer satisfaction feedback
There is provided a device and a method for collecting information from a customer concerning a point of interest. The device comprises a memory including a unique location identifier associated with a point of interest and a processor, the processor configured to store in the memory a received unique customer identifier and received information concerning the point of interest from a customer. The device can transmit this stored data to a center via a network, where the center can aggregate the data. There is also provided a system for distributed collection of information from customers concerning points of interest, utilizing a plurality of devices and a center for aggregating data. The center can apply data analysis and mining to the aggregate data, allowing rapid and real-time reaction to feedback from customers, efficient turnaround for resolving customer service issues, and enabling efficient research of customer preferences and trends.
Owner:DISNEY ENTERPRISES INC
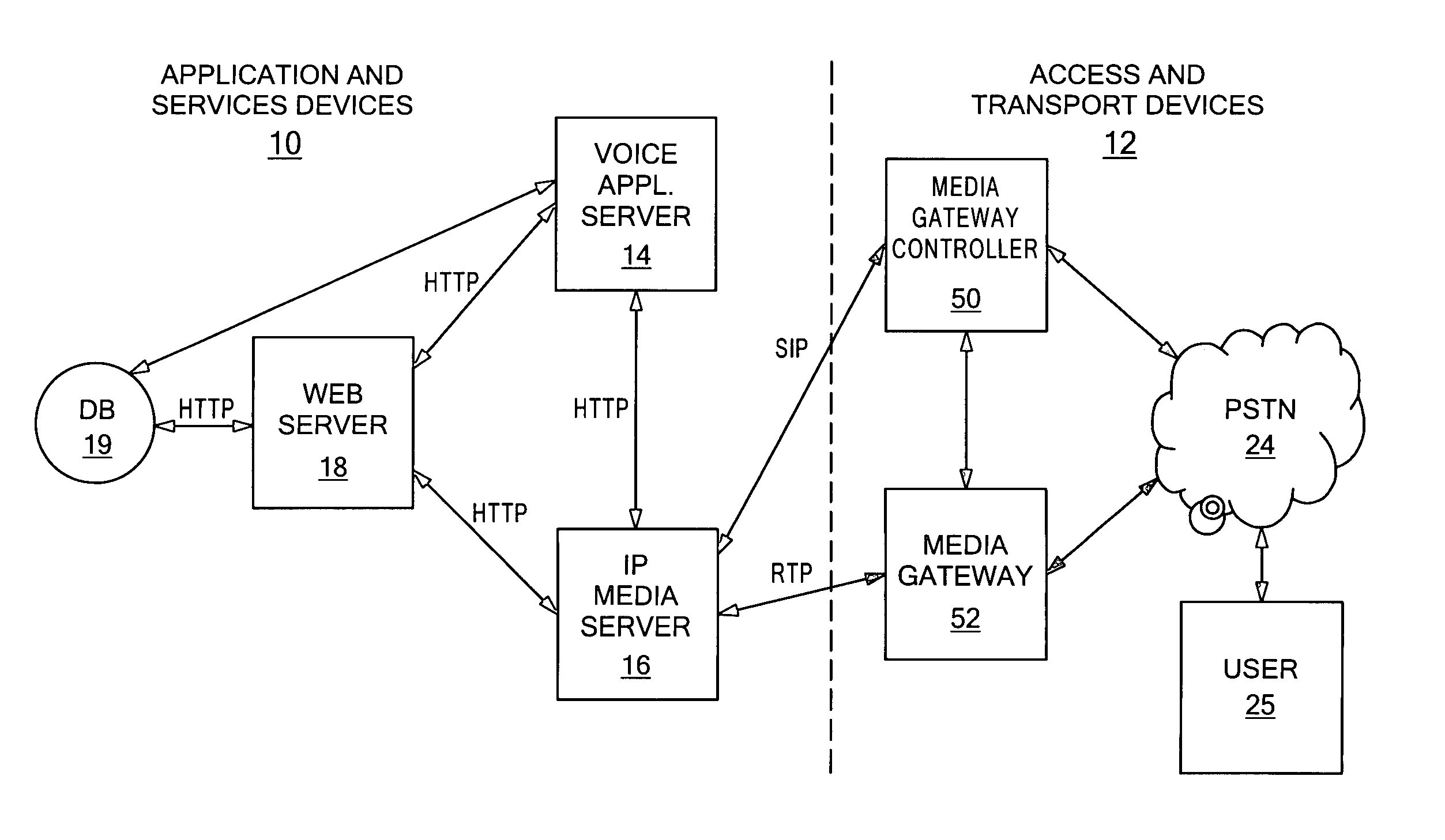
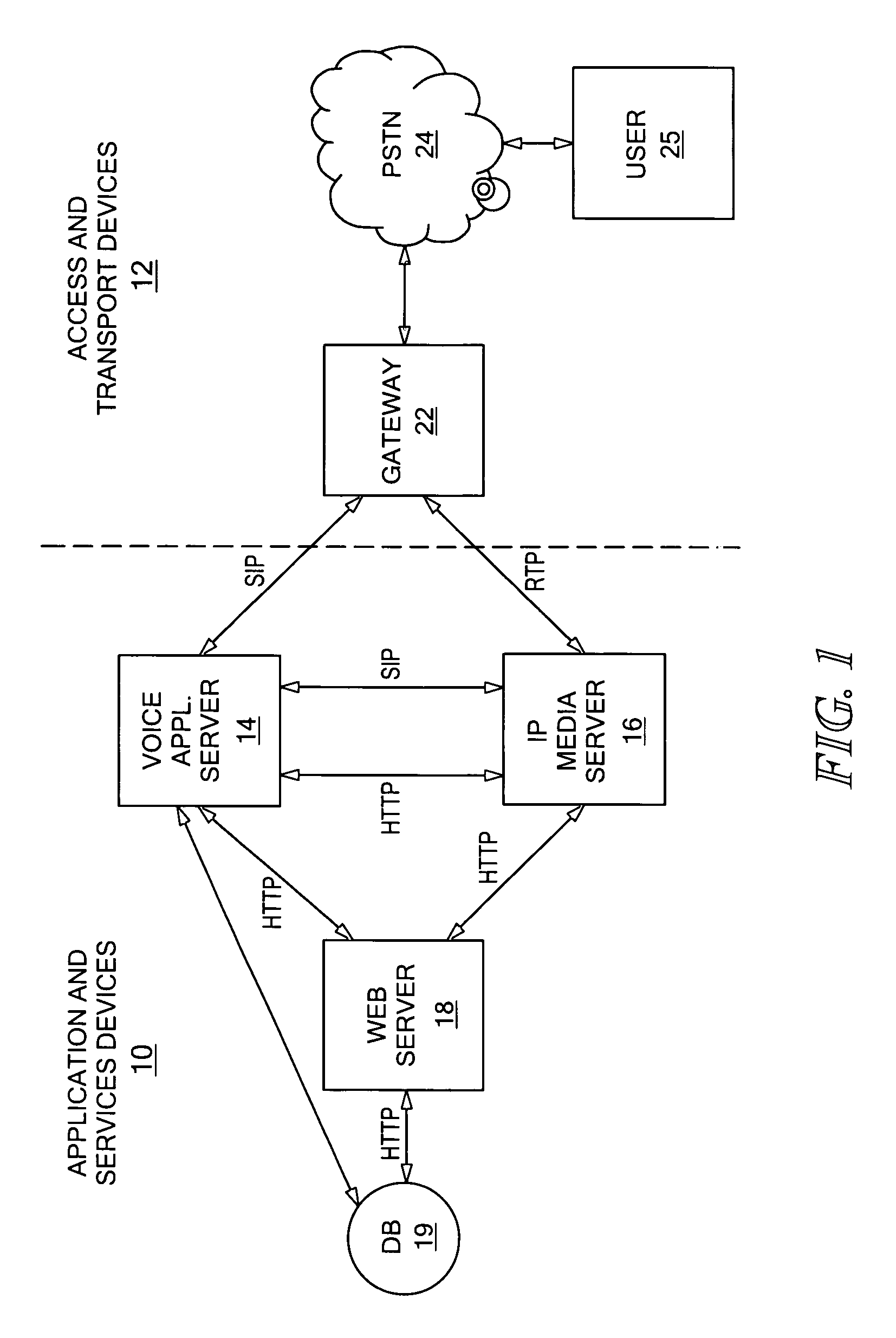
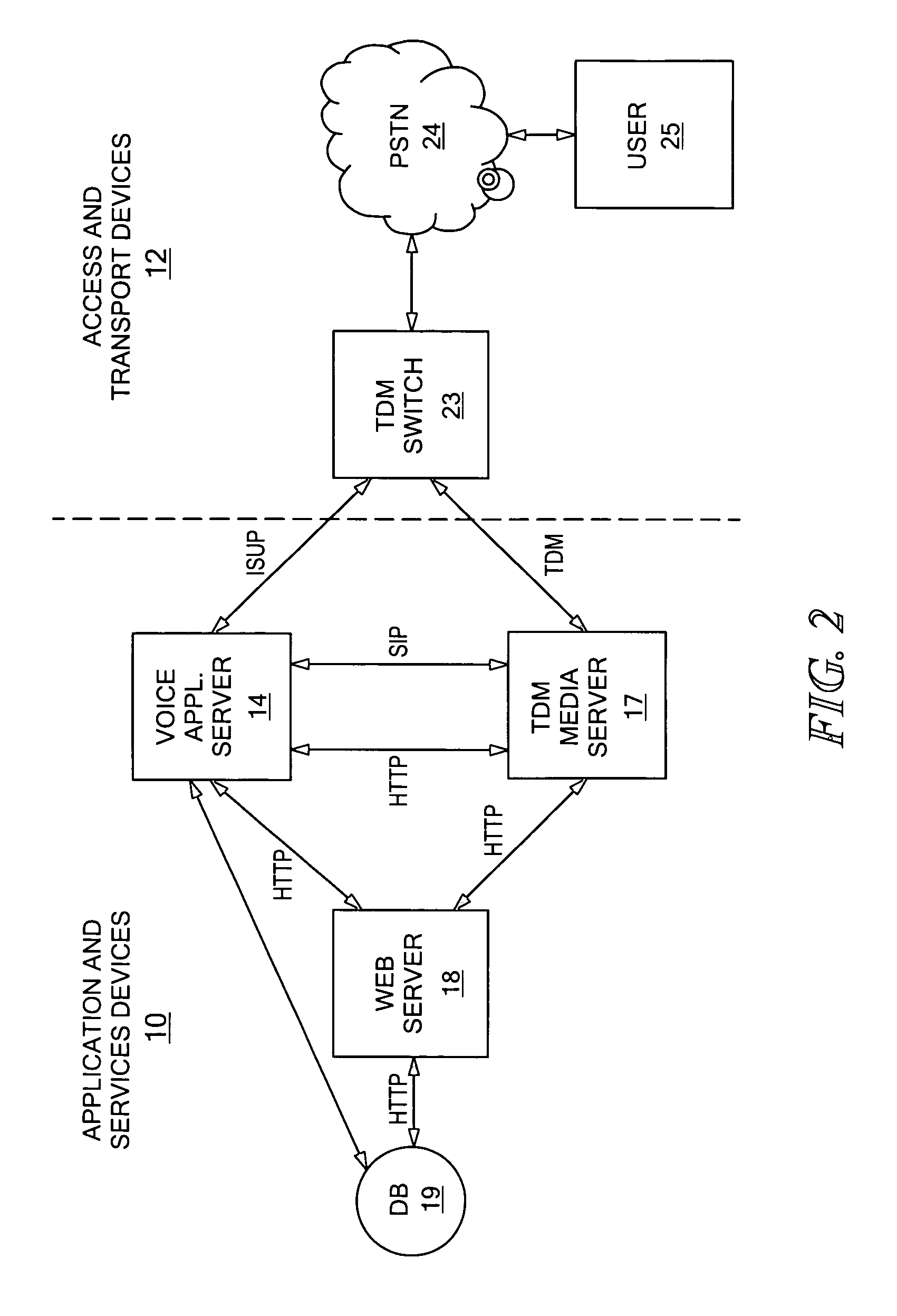
Universal voice browser framework
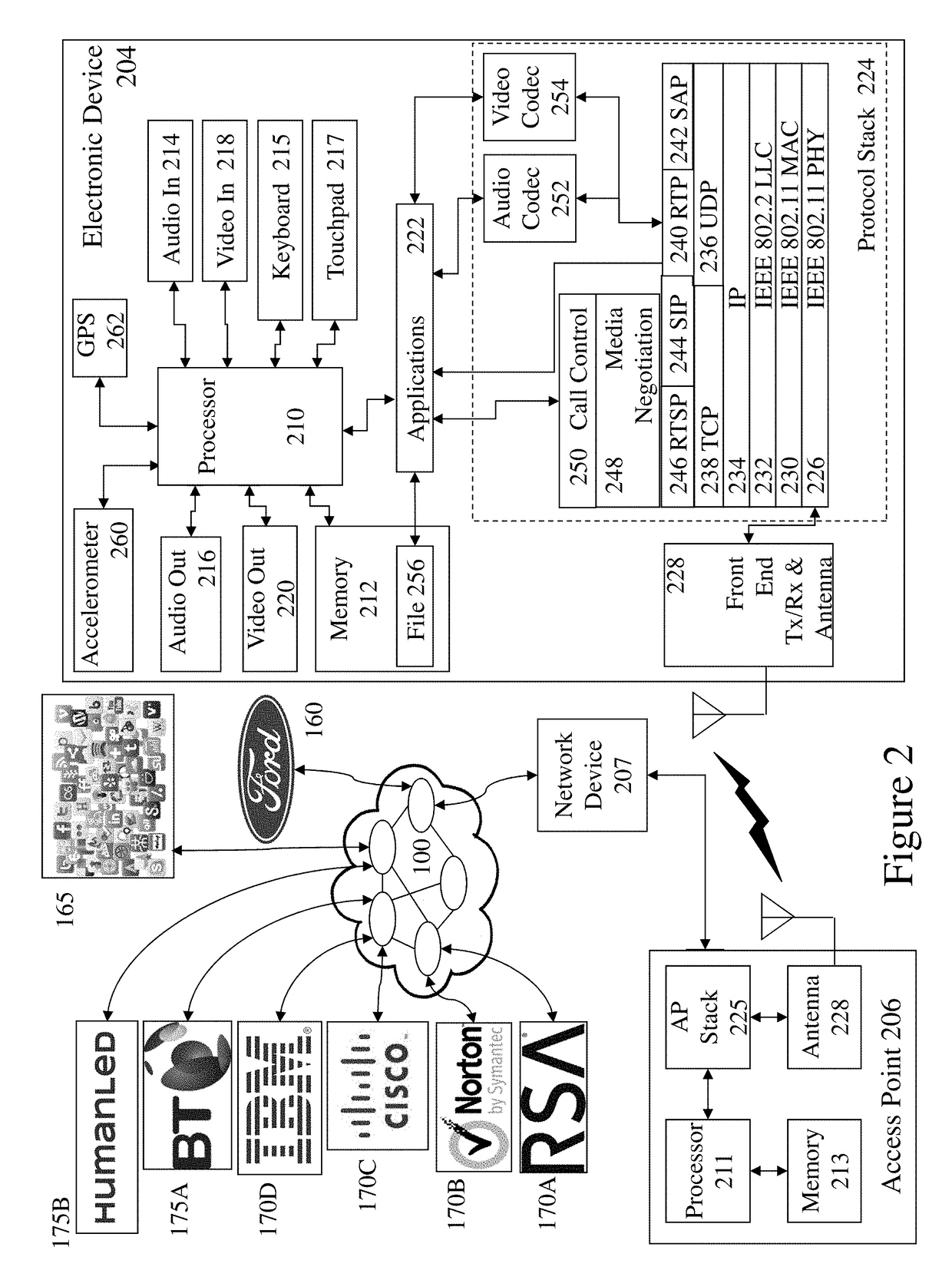
ActiveUS7149287B1Easy to useReduce performanceInterconnection arrangementsSpecial service for subscribersApplication serverProcedural programming
A system and method for providing voice communications over a network, including a media server having a voice rendering platform for supporting voice-based user interactions. The voice rendering platform provides prompting, information collection and validation, and audio recording and transcoding. A separate application server is responsible for performing call control actions. During a user dialog, control is passed to the media server for rendering and receiving data, and passed back to the application server for call control actions. The media server includes a script execution environment for rendering the voice components of the user dialogs. The application server is an execution platform for applications written in a procedural programming language. Voice communications over a network are provided without combining call control and voice rendering functionality into a single, script execution platform.
Owner:DIALOGIC INC
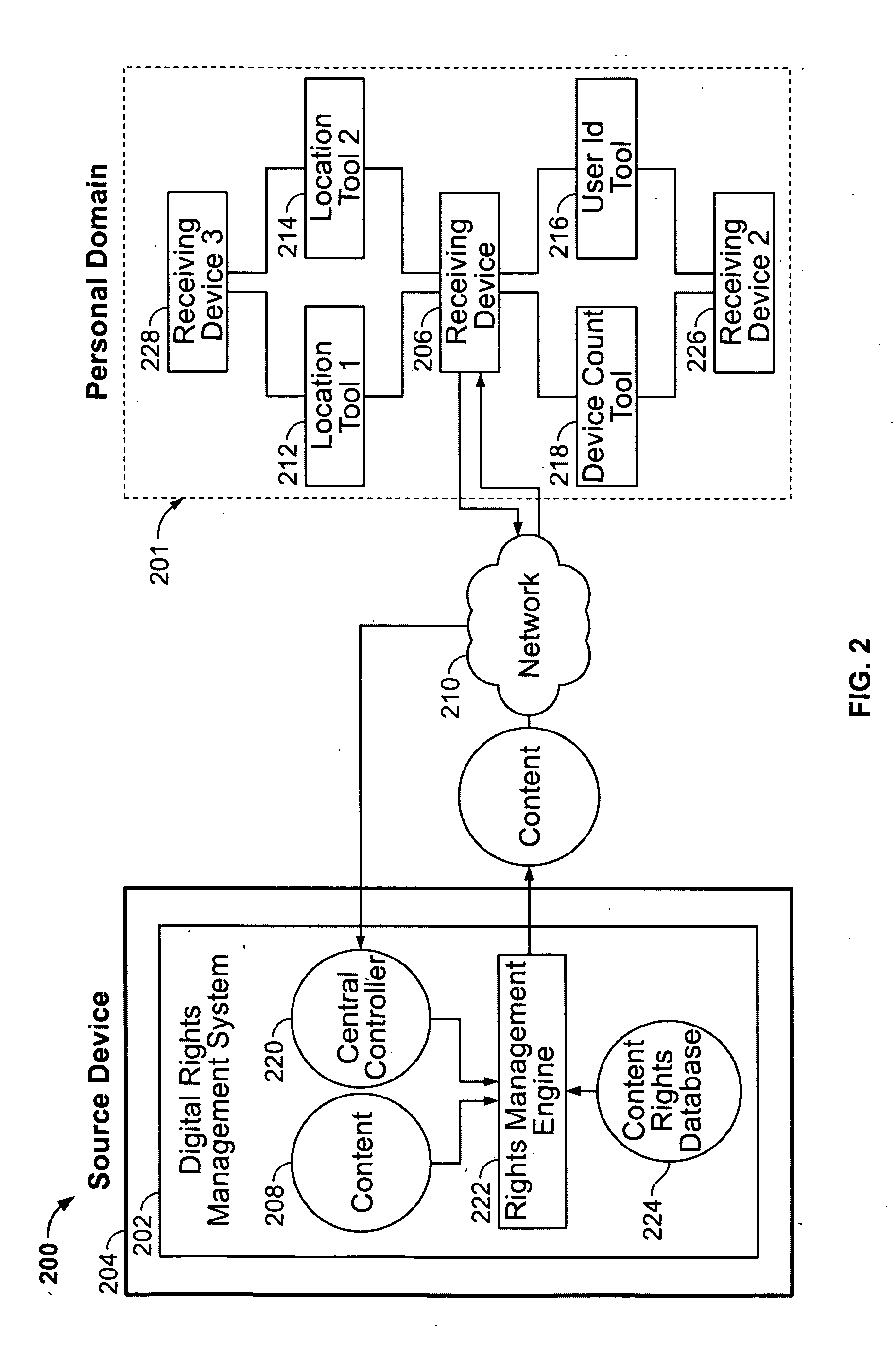
Digital rights management using multiple independent parameters
InactiveUS20050192902A1Different success rateProgram/content distribution protectionSpecial data processing applicationsInternet privacyDigital content
A method and system for controlling distribution of digital content within a personal domain or localized personal domain that includes multiple receiving devices and makes use of independent parameters (e.g., “who,”“what” and “how many”) to determine a threat index. A rights management engine develops usage rights for devices in the domain, based on the threat index and a risk tolerance threshold for the digital content. The system may include a plurality of information-gathering tools for collecting the independent parameters for a personal domain of connected receiving devices.
Owner:MOTION PICTURE ASSOC OF AMERICA
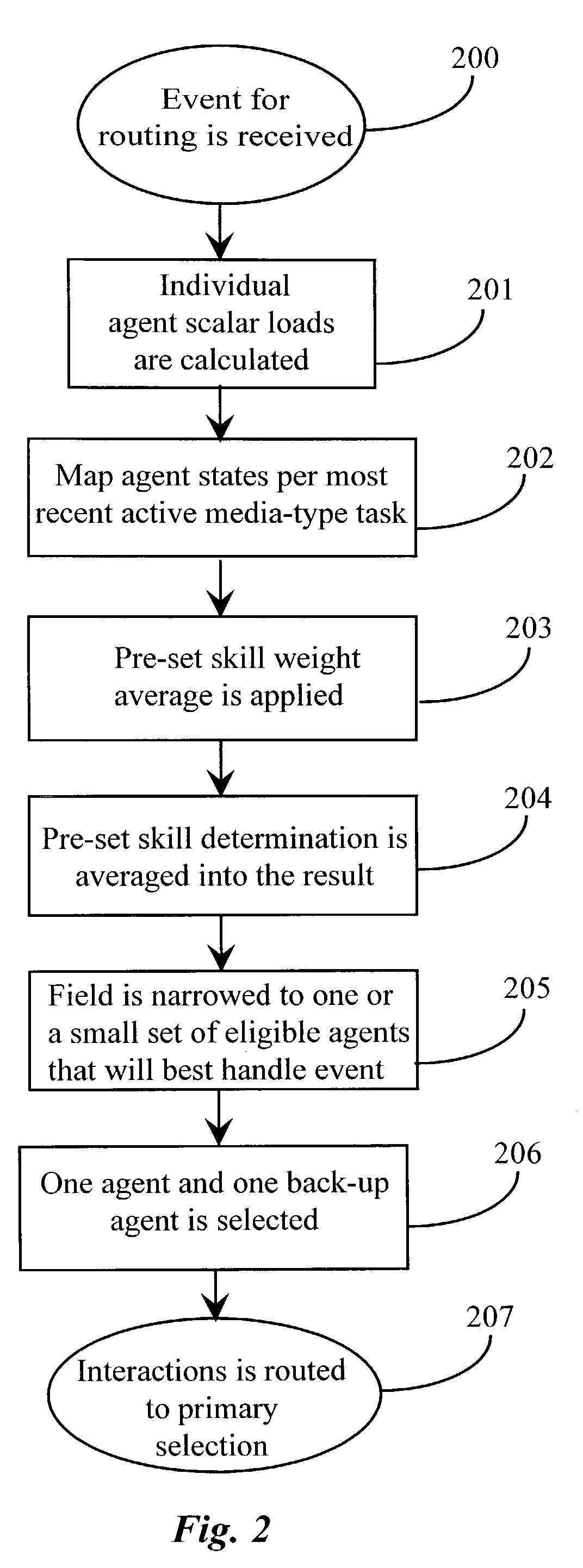
Method and apparatus for multimedia interaction routing according to agent capacity sets
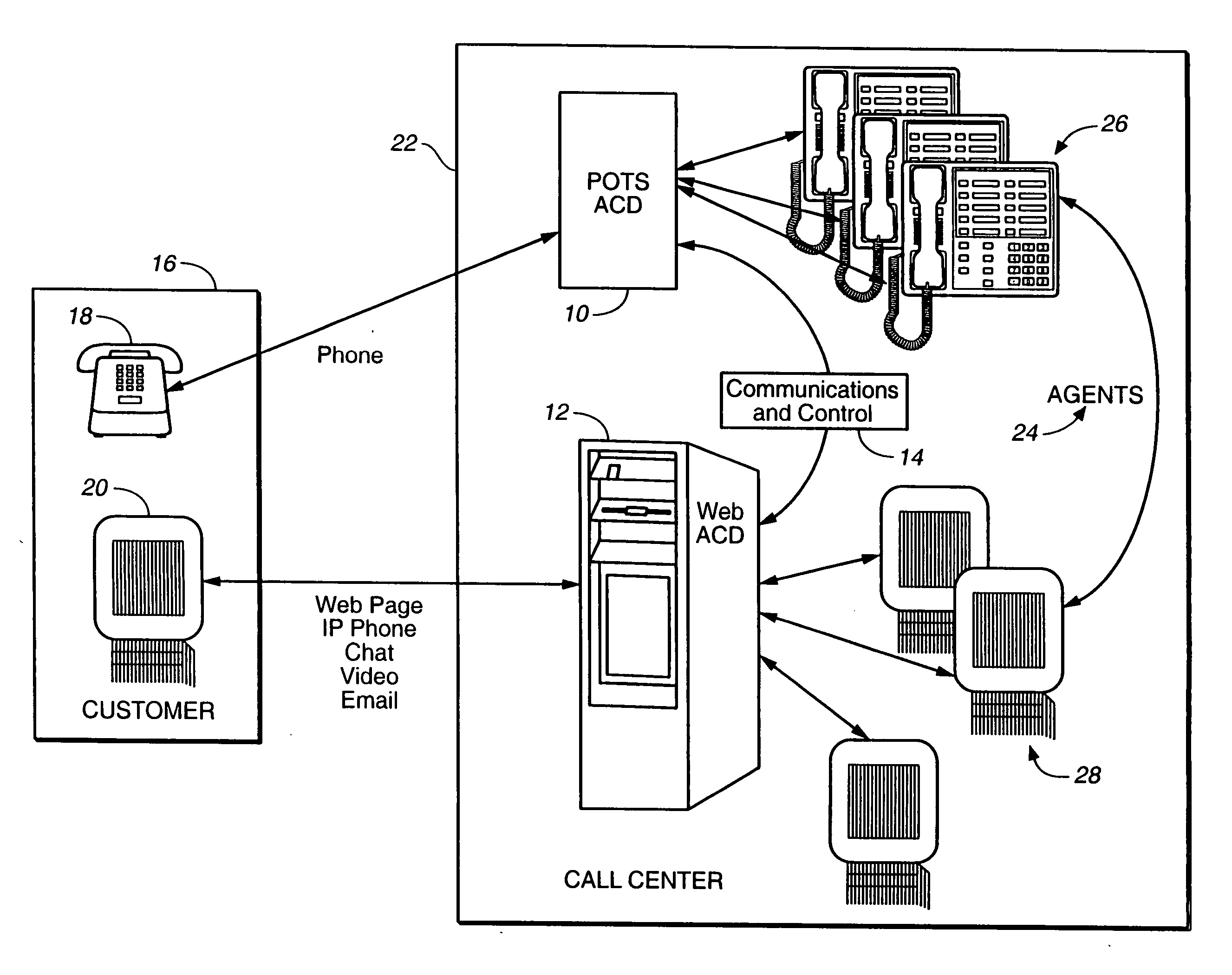
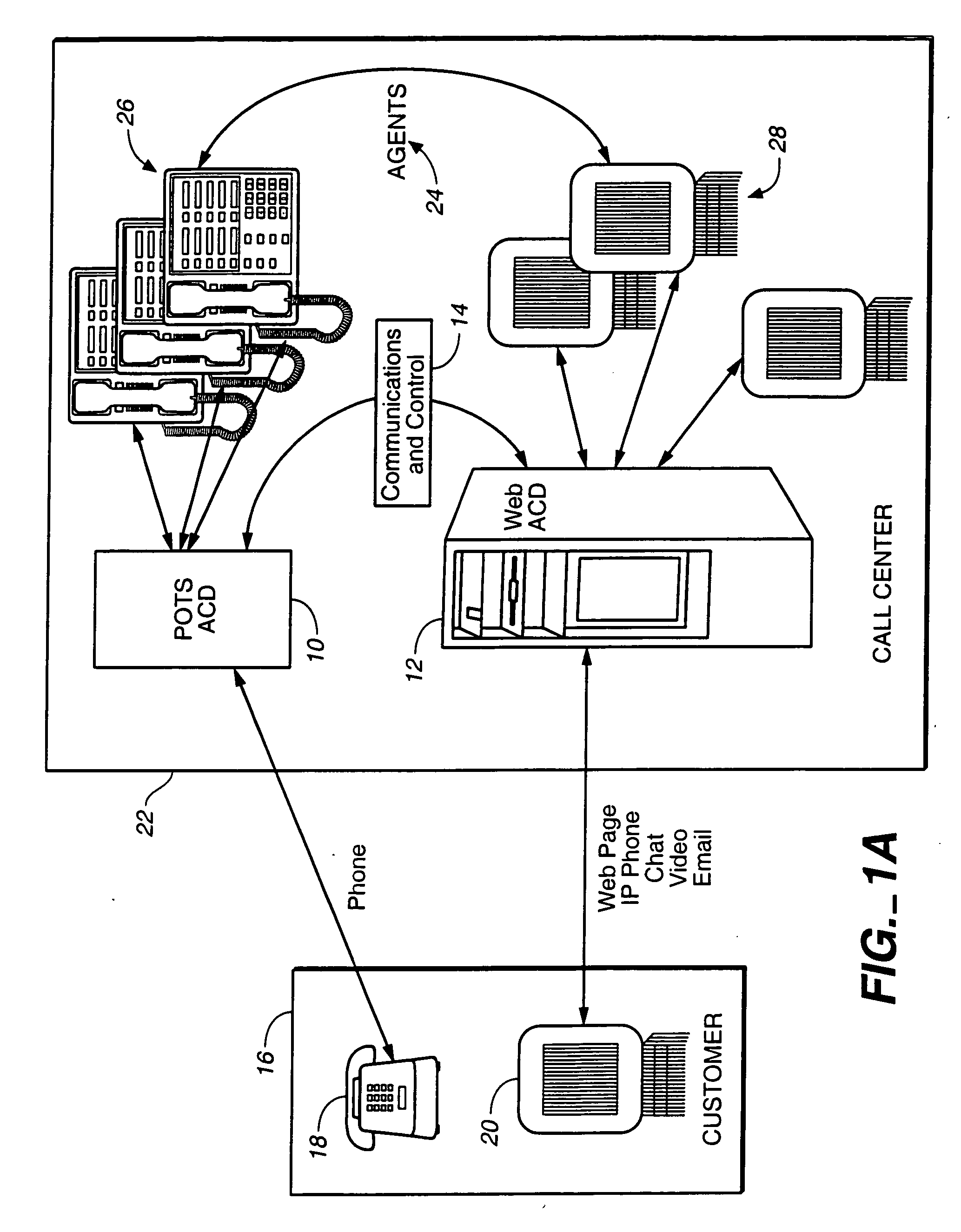
A routing software application for predicting a best routing destination from a pool of considered routing destinations for an incoming event into a communications routing system has a detection module for detecting the arrival of the event for routing; at least one instance of an information gathering routine for gathering and compiling information about the considered destinations; at least one reporting module for organizing and reporting the gathered information; and a processing module for computing values from the gathered information and selecting the best routing destination based on isolation of the best computed value. In a preferred embodiment scalar load information per media type and per destination and agent skill information related to at least media skills per type of media per destination is processed by the processing module, which isolates, identifies, and selects at least the best destination for routing.
Owner:GENESYS TELECOMMUNICATIONS LABORATORIES INC
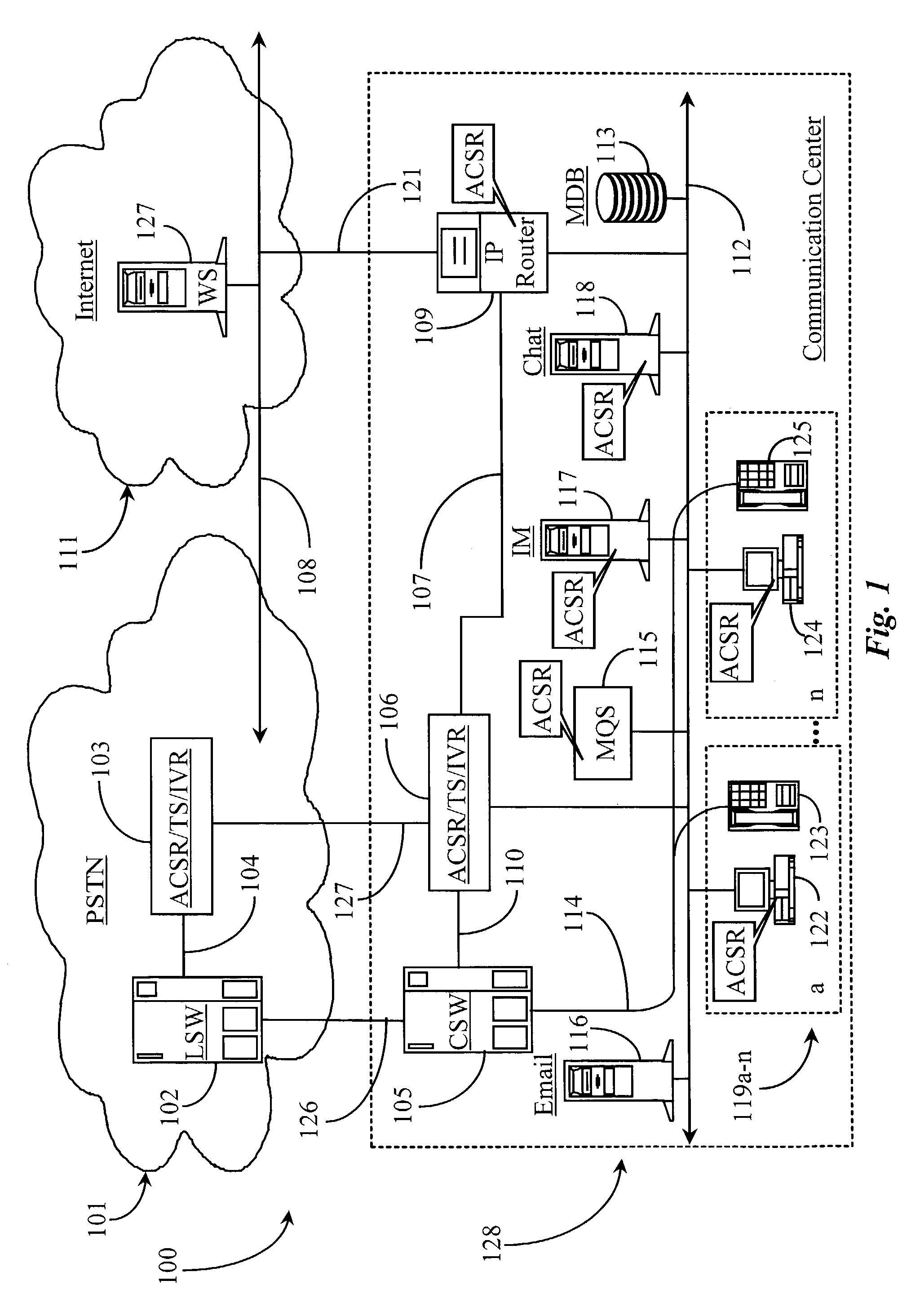
Automatic call distribution system using computer network-based communication
InactiveUS20060203993A1Significant informationSpecial service for subscribersCathode-ray tube indicatorsDigital videoDrag and drop
Multiple communication types are integrated into a call center. The communication types can be chat, email, Internet Protocol (IP) voice, traditional telephone, web page, digital image, digital video and other types. Features of the invention include allowing a single agent to handle multiple customers on multiple channels, or “endpoints.” Prioritizing and assigning calls to agents based on a specific criteria such as the number of endpoints assigned to an agent, the agents availability, the priority of a customer call, the efficiency of a given agent and the agent's efficiency at handling a particular communication type call. An agent user interface is described that allows the agent to have control over accepting multiple calls. The agent can drag and drop canned responses, images, URLs, or other information into a window for immediate display on a customer's computer. The system provides for detailed agent performance tracking. The system provides failure recovery by using a backup system. If the network server fails, then the customer is connected directly to an agent. When a failed computer comes back on line, the statistics gathered are then used to synchronize the returned computer. The system provides extensive call recording or “data wake” information gathering. The system provides flexibility in transferring large amounts of historic and current data from one agent to another, and from storage to an active agent. The system integrates human agents' knowledge with an automated knowledge base. The system provides for an agent updating, or adding, to the knowledge base in real time. The system also provides for “blending” of different communication types.
Owner:AVAYA TECH LLC
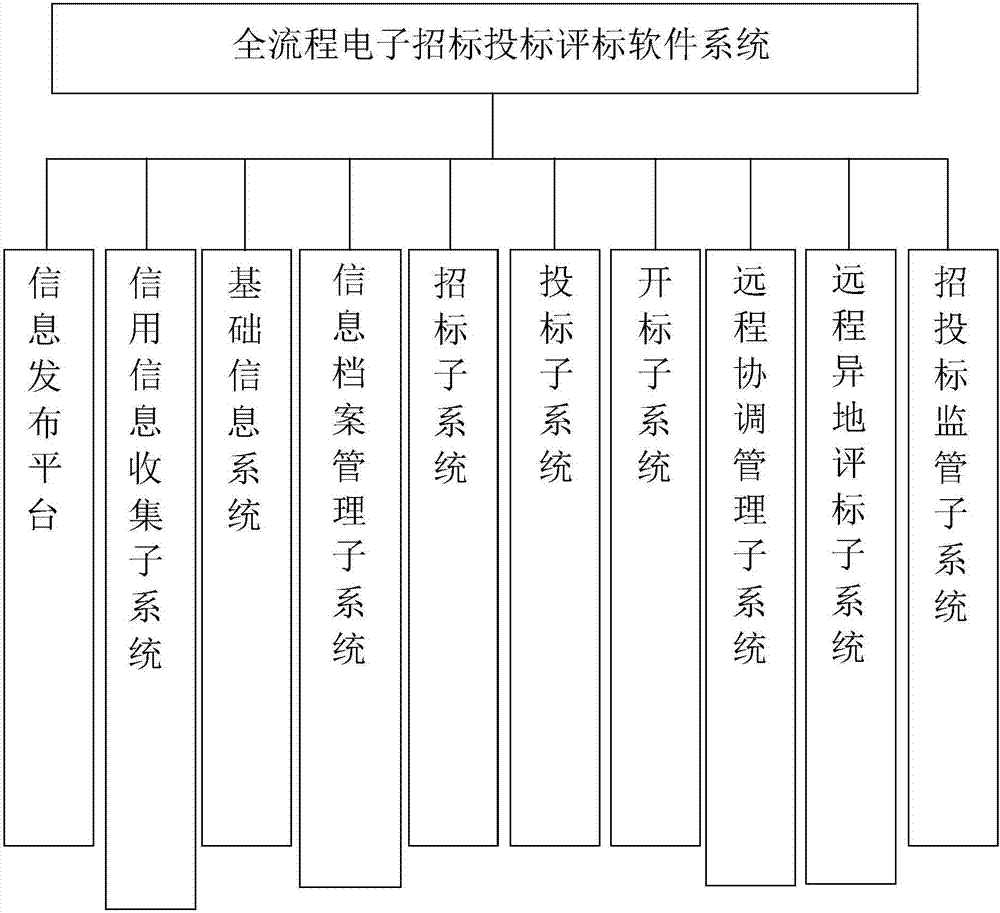
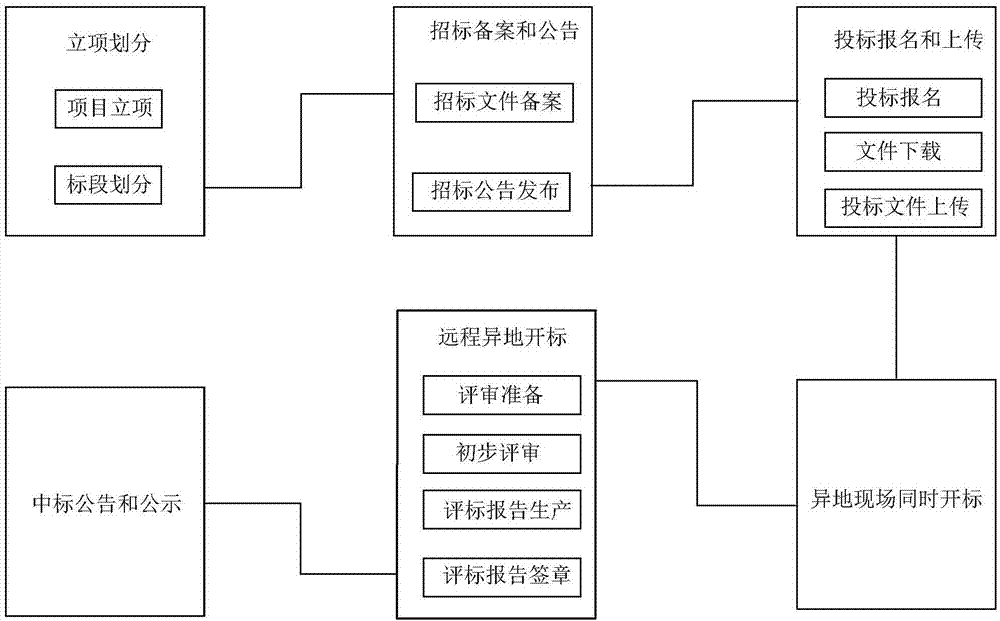
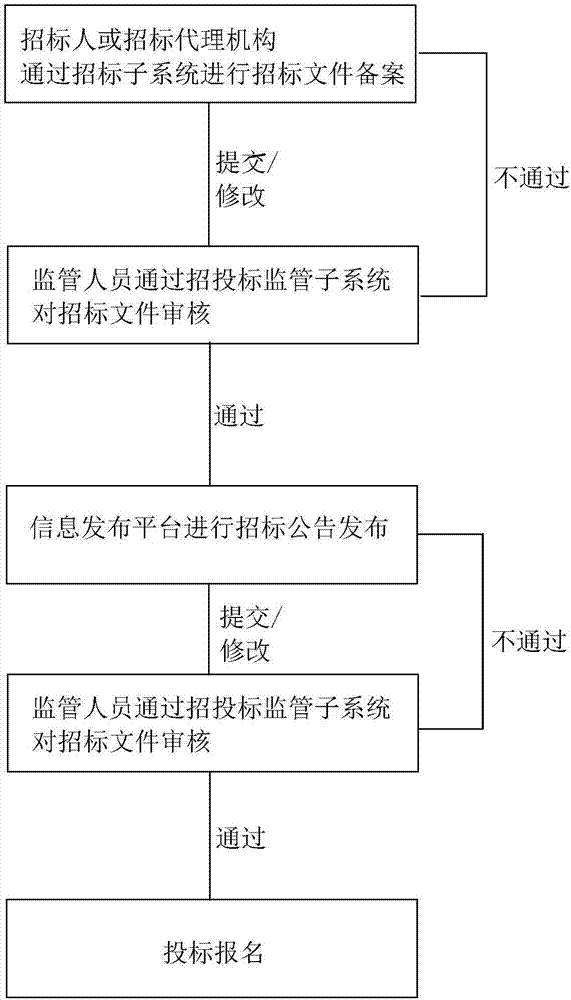
All process electronic tendering and bidding bid evaluation system and method
InactiveCN107392570AAchieve publicityAchieve justiceOffice automationCommerceMutual correlationFinancial transaction
The present invention relates to the Internet tendering and bidding field, especially to an all process electronic tendering and bidding bid evaluation system and method. The system comprises an information publishing platform, a credit information collection subsystem, a basic information system, an information archive management subsystem, a tendering subsystem, a bidding subsystem, a bid opening subsystem, a remote coordination management subsystem, a remote nonlocal bid evaluation subsystem and a tendering and bidding supervision subsystem. The all process electronic tendering and bidding bid evaluation system and method can provide a special platform aiming at different users, 10 application systems cover three platforms of tendering and bidding transaction, administrative supervision and public service, systems are mutually associated and restricted to form whole resultant force and construct the new system of tendering and bidding management.
Owner:江苏省鸿源招标代理股份有限公司
Apparatus and methods for managing malfunctions on a wireless device
ActiveUS20060211415A1Radio/inductive link selection arrangementsTransmission monitoringEvent dataInformation Harvesting
Apparatus and methods for managing predetermined malfunction events in a wireless device operating in a wireless communications network. Malfunction event data and operational data are recorded by the wireless device based on a selected malfunction event tracking configuration. Further, a recovery module associated with the wireless device operates to attempt to recover information leading up to and including the malfunction event. The collected information may be transmitted to a user manager in the form of a malfunction event log. The malfunction event log may be analyzed to characterize the malfunction, and is particularly useful for determining the sequence and identity of events leading to the malfunction, including a crash, freeze and reset.
Owner:QUALCOMM INC
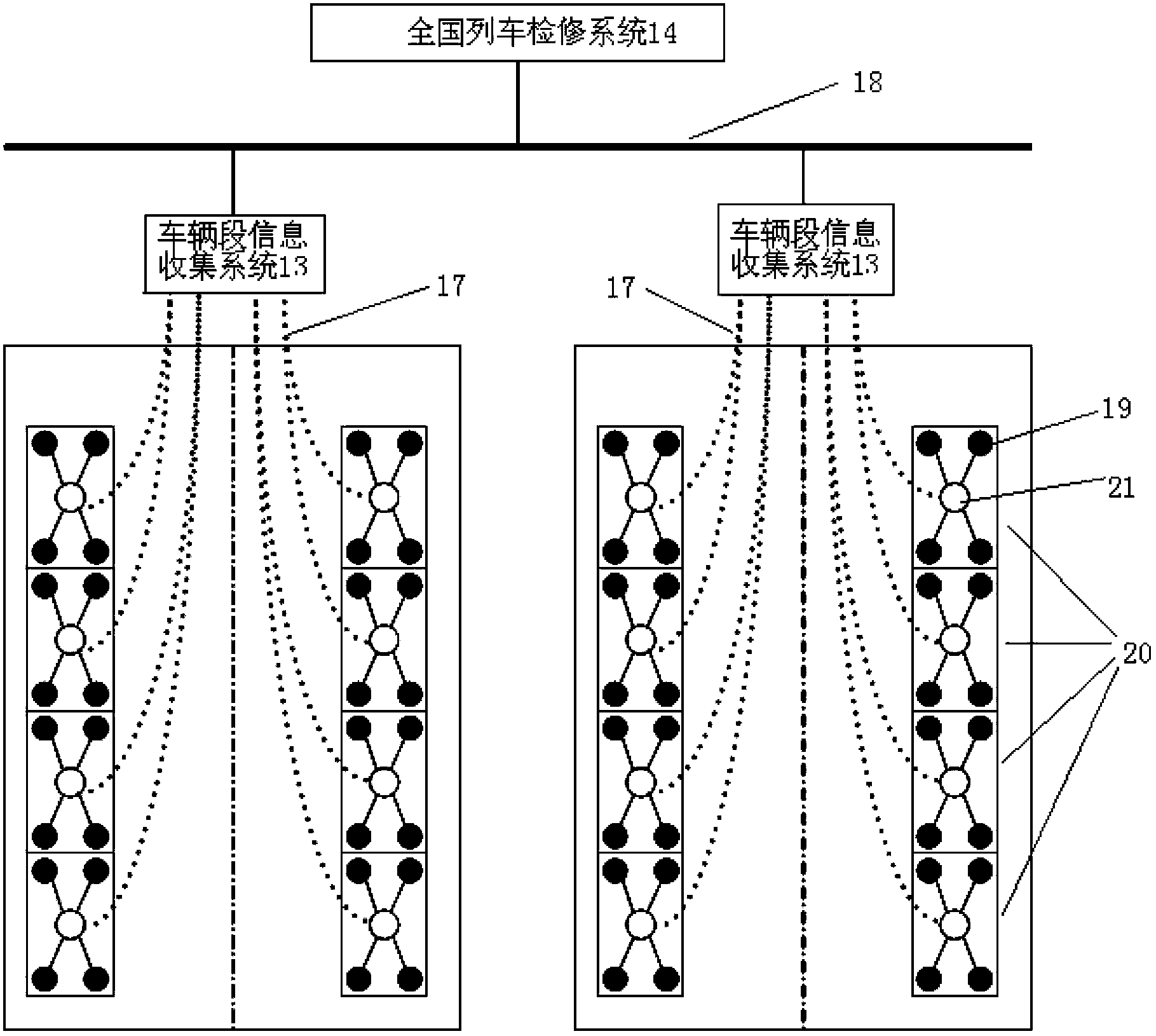
High-speed train running gear fault diagnosis and remote monitoring system based on Internet of Things
ActiveCN103852271AImprove maintenance efficiencyReduce operational riskRailway vehicle testingCollection systemEngineering
The invention relates to a high-speed train running gear fault diagnosis and remote monitoring system based on Internet of Things (IOT). The system provided by the invention comprises vehicle-mounted sensors, a signal conditioning and filtering device, a central processing system, a data input and output interface device, a vehicle depot information collection system, a nationwide train maintenance system and a man-machine interaction device. With the arrangement of a plurality of the vehicle-mounted sensors, accurate fault identification and positioning of key equipment of running gears are realized, prediction of faults is realized, train operational risks are reduced, remote diagnosis of faults is achieved, fault diagnosis cost is lowered, and fault diagnosis cycle is shortened.
Owner:CRRC QINGDAO SIFANG CO LTD
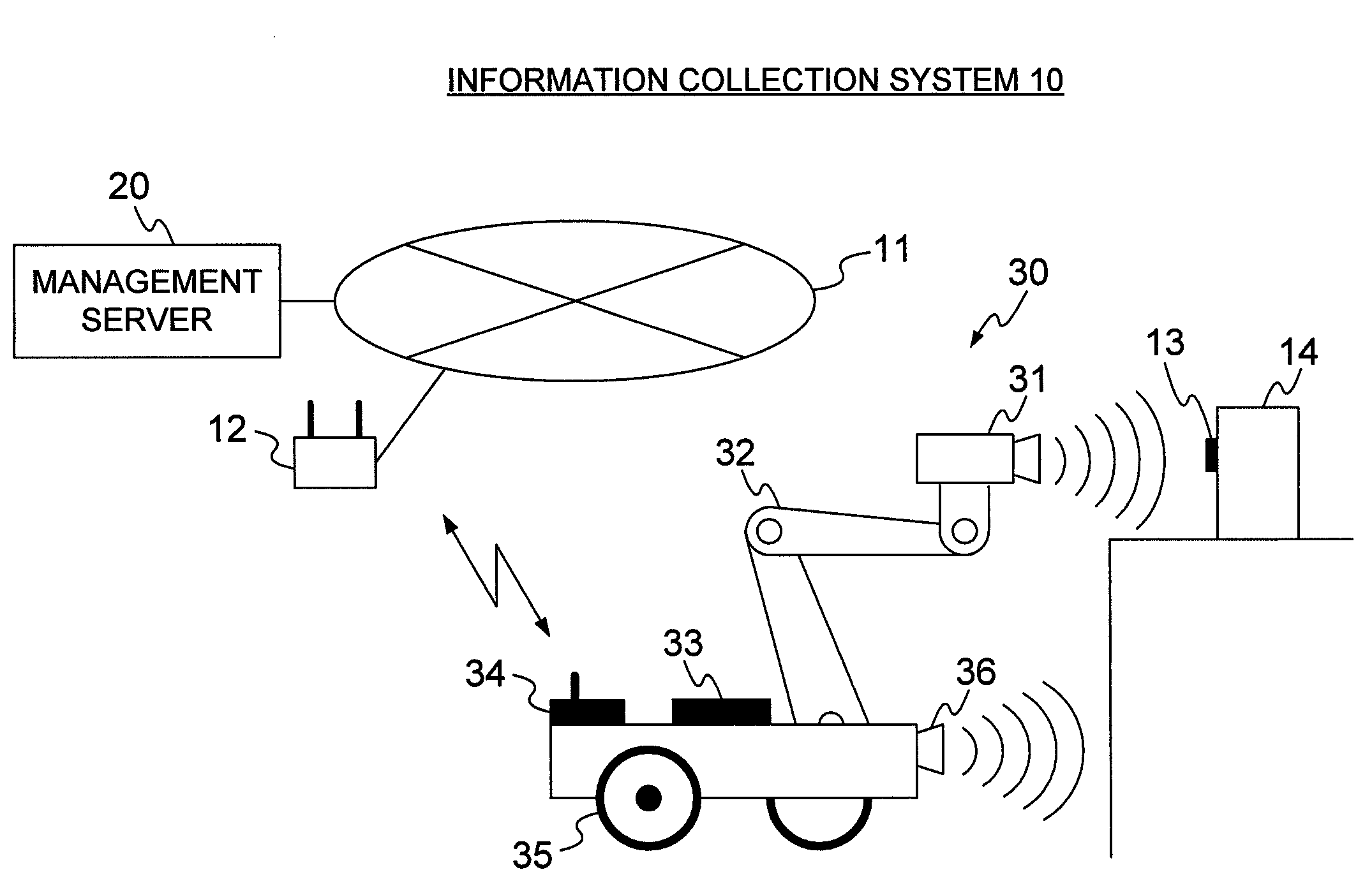
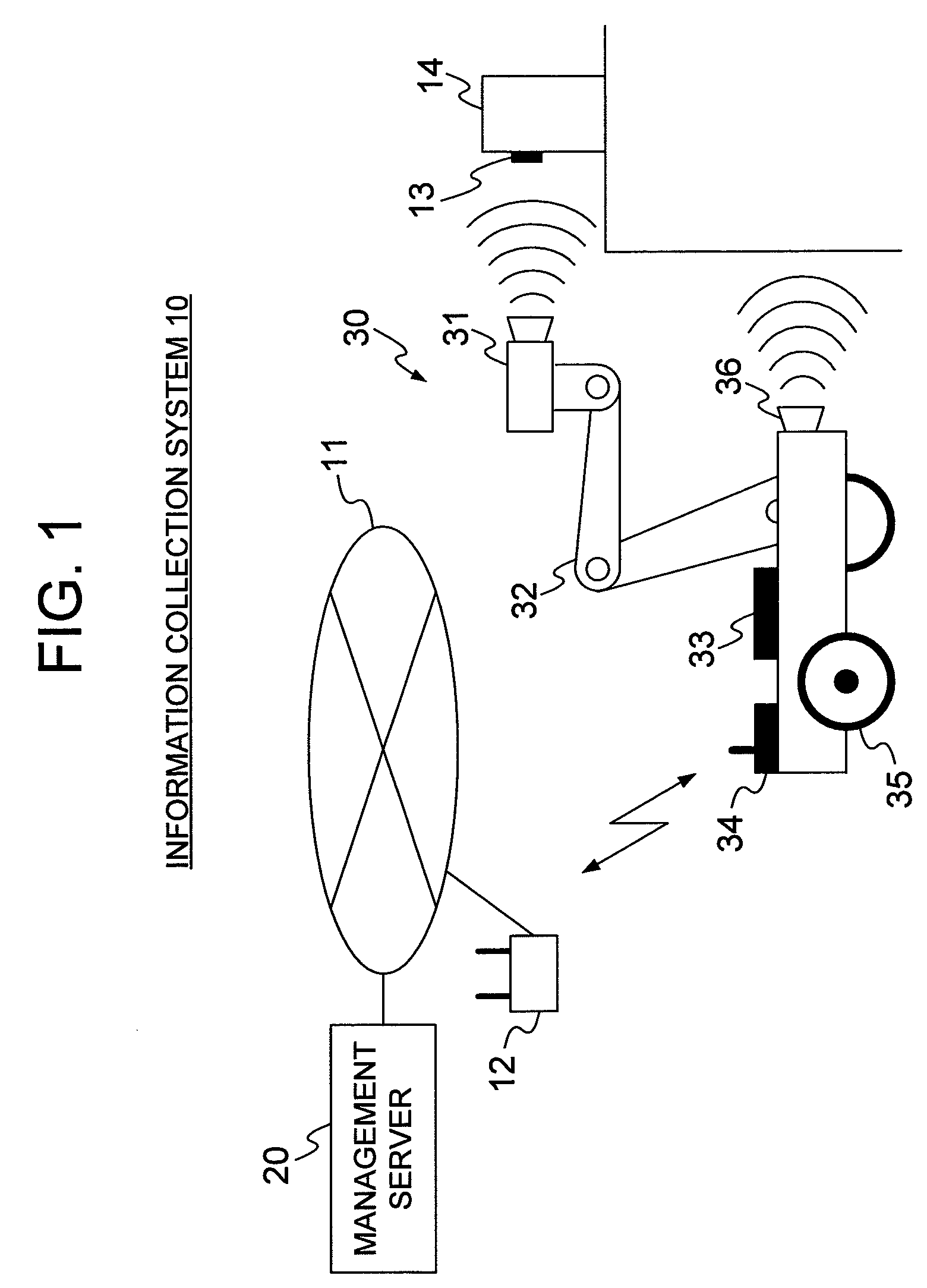
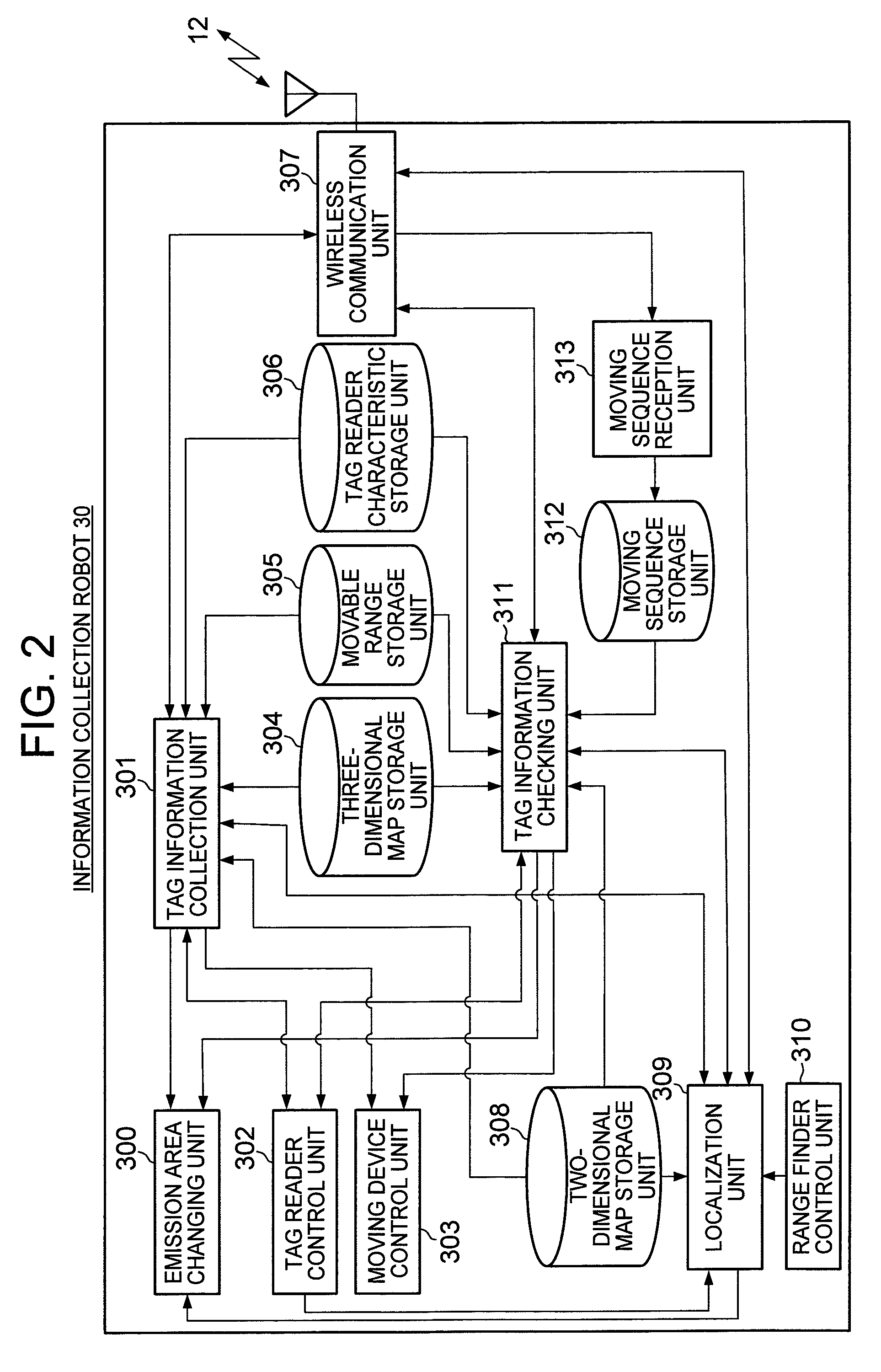
Information collection system and information collection robot
InactiveUS8022812B2Reduce failed acquisitionRoad vehicles traffic controlNavigation instrumentsCollection systemData acquisition
Owner:HITACHI LTD
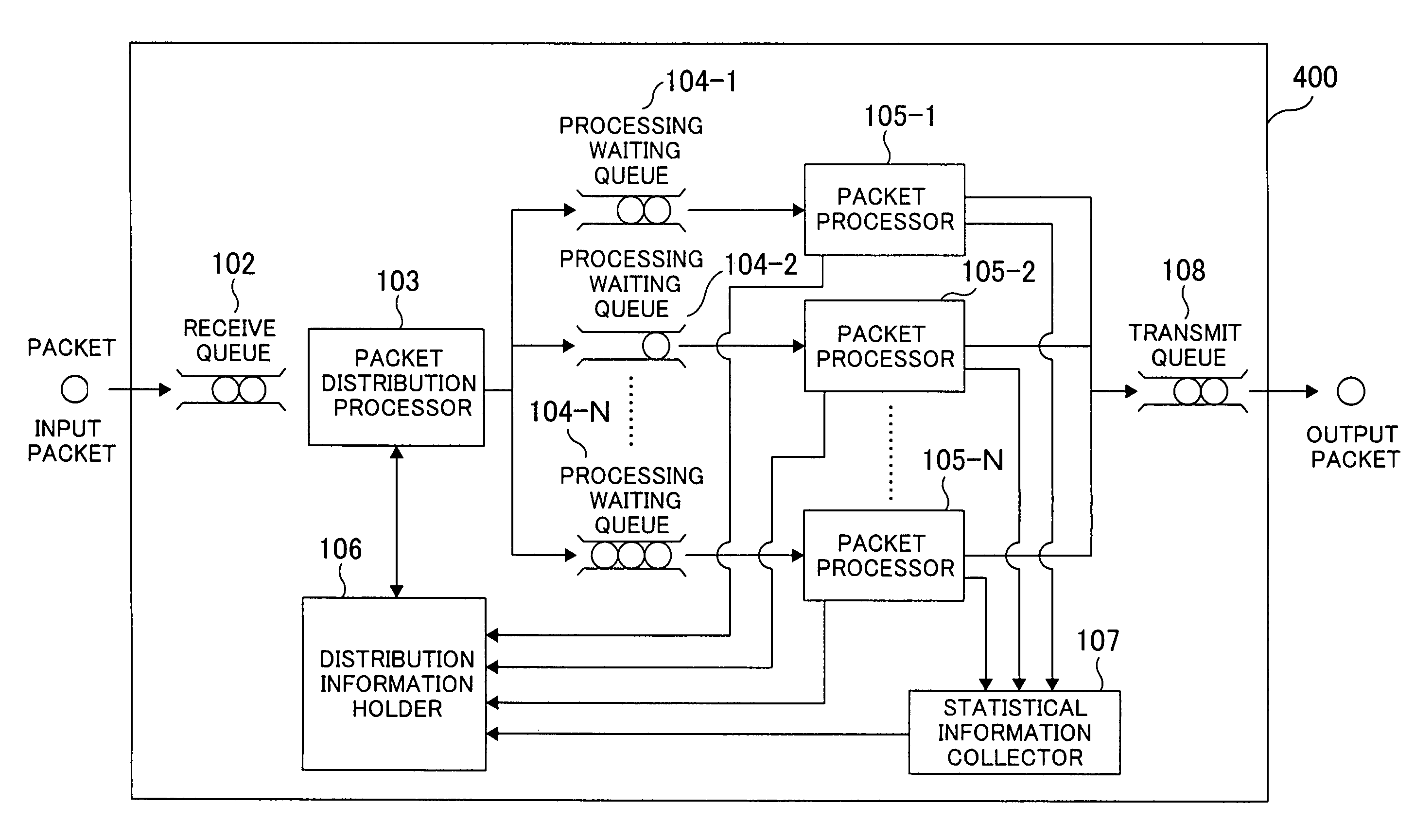
Network relay apparatus and packet distribution method
The present invention provides a network relay apparatus capable of assuring the prevention of occurrence of order reversion of packets within flows and shifting a packet distribution destination according to load information. The network relay apparatus includes: a packet distribution processor for distributing input packets to thereby achieve load dispersion of packet processing; a statistical information collector for regularly collecting load conditions of respective packet processors; and a distribution information holder for retaining information for specifying the packet distribution destinations upon distribution of the packets. Information about the load conditions of the respective packet processors are compiled and distributed to the packet processor smallest in load. Timing provided to change the packet distribution destination is assumed to be given when a processing waiting queue does not include a packet corresponding to its flow.
Owner:HITACHI LTD
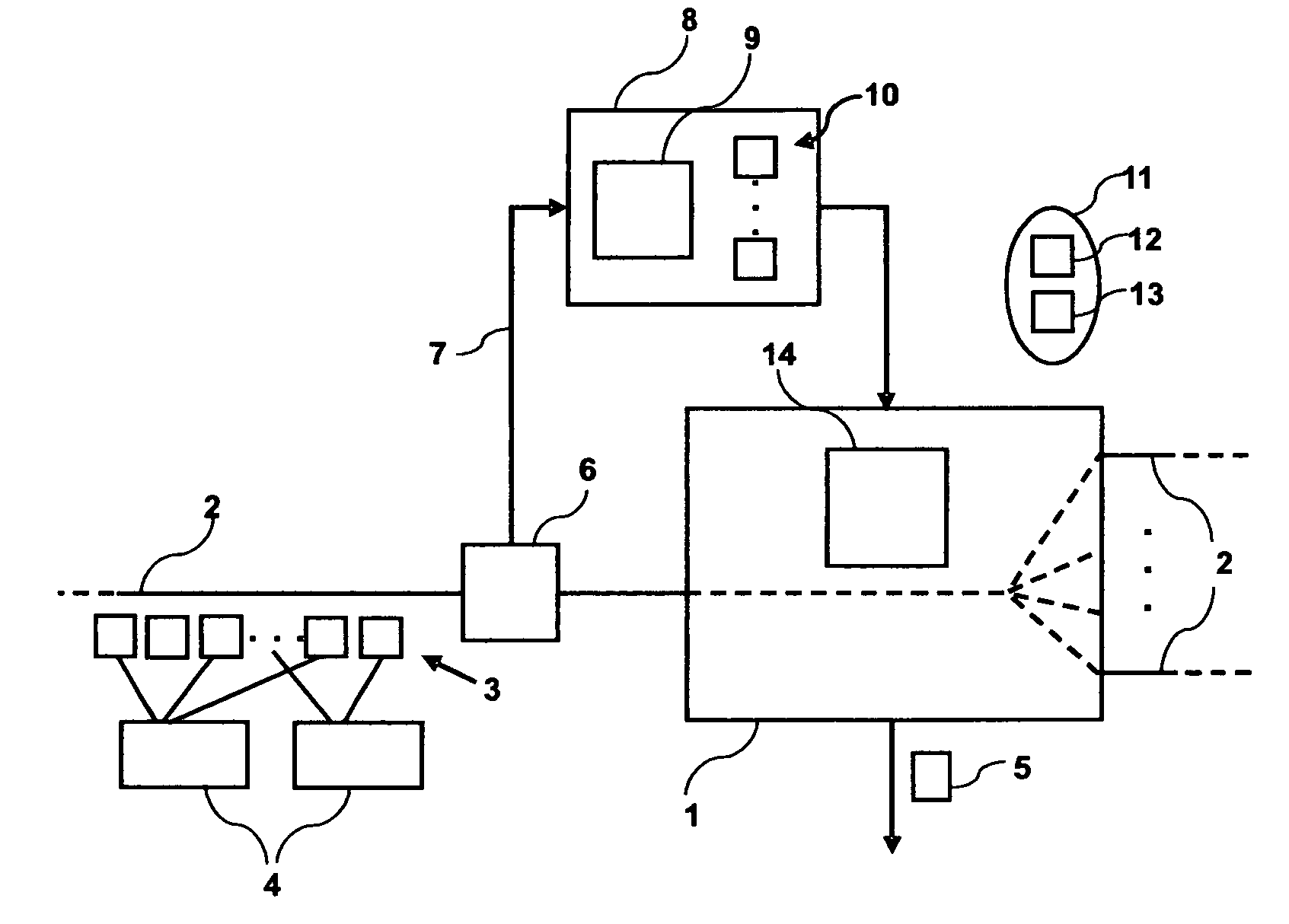
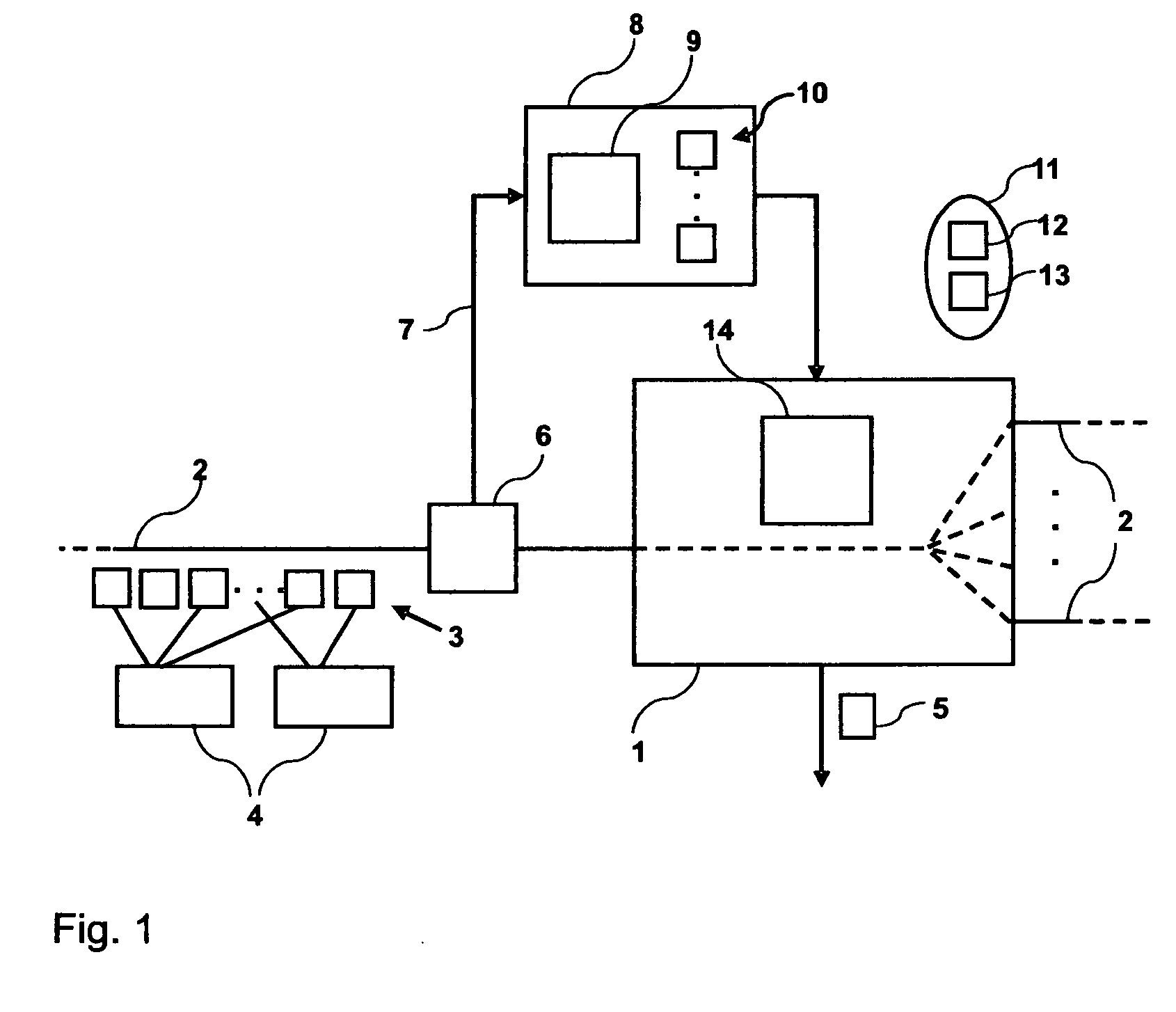
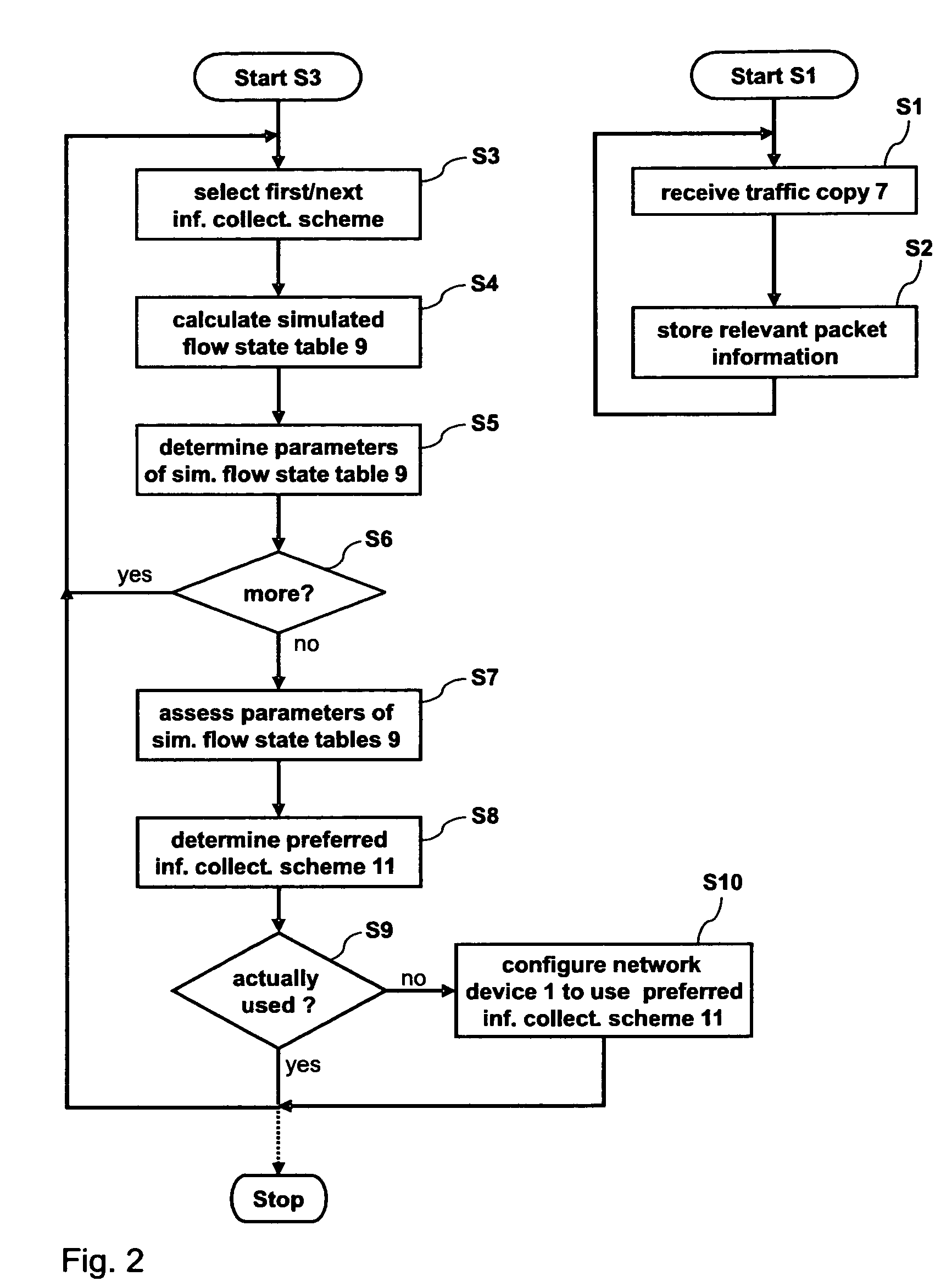
Method and device for configuring a network device
InactiveUS20070147246A1Improve fidelityLess resource-intensiveError preventionFrequency-division multiplex detailsInternet trafficInformation Harvesting
A method for configuring network device adapted to process network traffic comprising a plurality of network flows and to export network flow information. For configuring the network device, a copy of the network traffic that is processed by the network device is created. A simulation of a process of collecting the network flow information using the copy of the network traffic is performed. Based on the results of the simulation, a preferred information collection scheme is determined. The network device is then configured to collect the network flow information to be exported according to the preferred information collection scheme.
Owner:IBM CORP
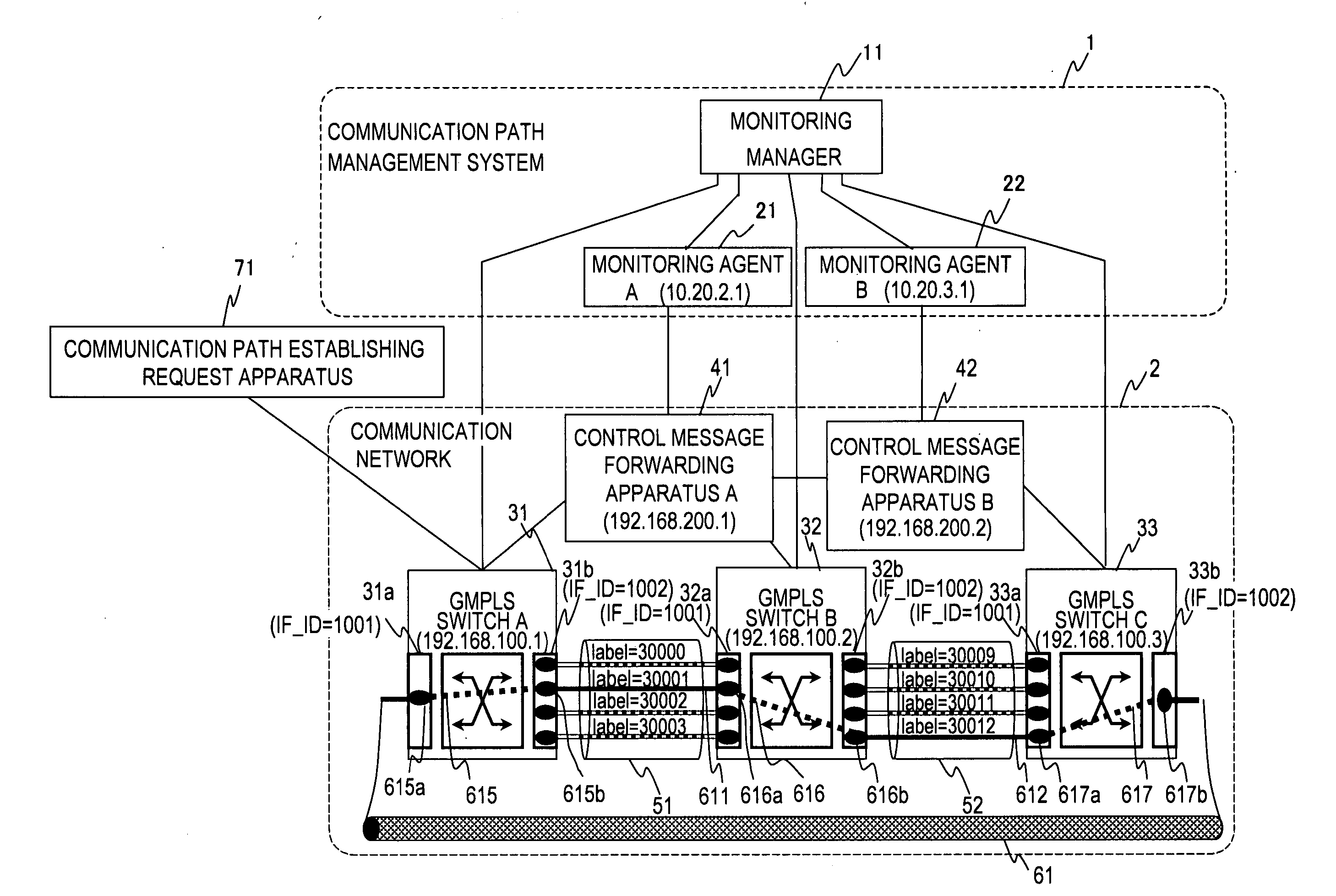
Communication path monitoring system and communication network system
InactiveUS20060256711A1Small information amountError preventionFrequency-division multiplex detailsNetworked systemMonitoring system
Information that is not dependent on how a GMPLS switch or an MPLS router is set up (information independent of the type of GMPLS switch or MPLS router) is used to obtain attribute values of communication paths and manage communication path configurations in a communication network. Provided is a communication path management system for managing a communication network system in which a communication path is established by transferring communication path establishment control information between data switching apparatuses, including: an information collecting module which collects the communication path establishment control information; an information accumulating module which accumulates the communication path establishment control information collected by the information collecting module; and an information searching module which searches the communication path establishment control information accumulated by the information accumulating module, wherein which communication path is established is derived from the communication path establishment control information searched by the information searching module.
Owner:HITACHI LTD
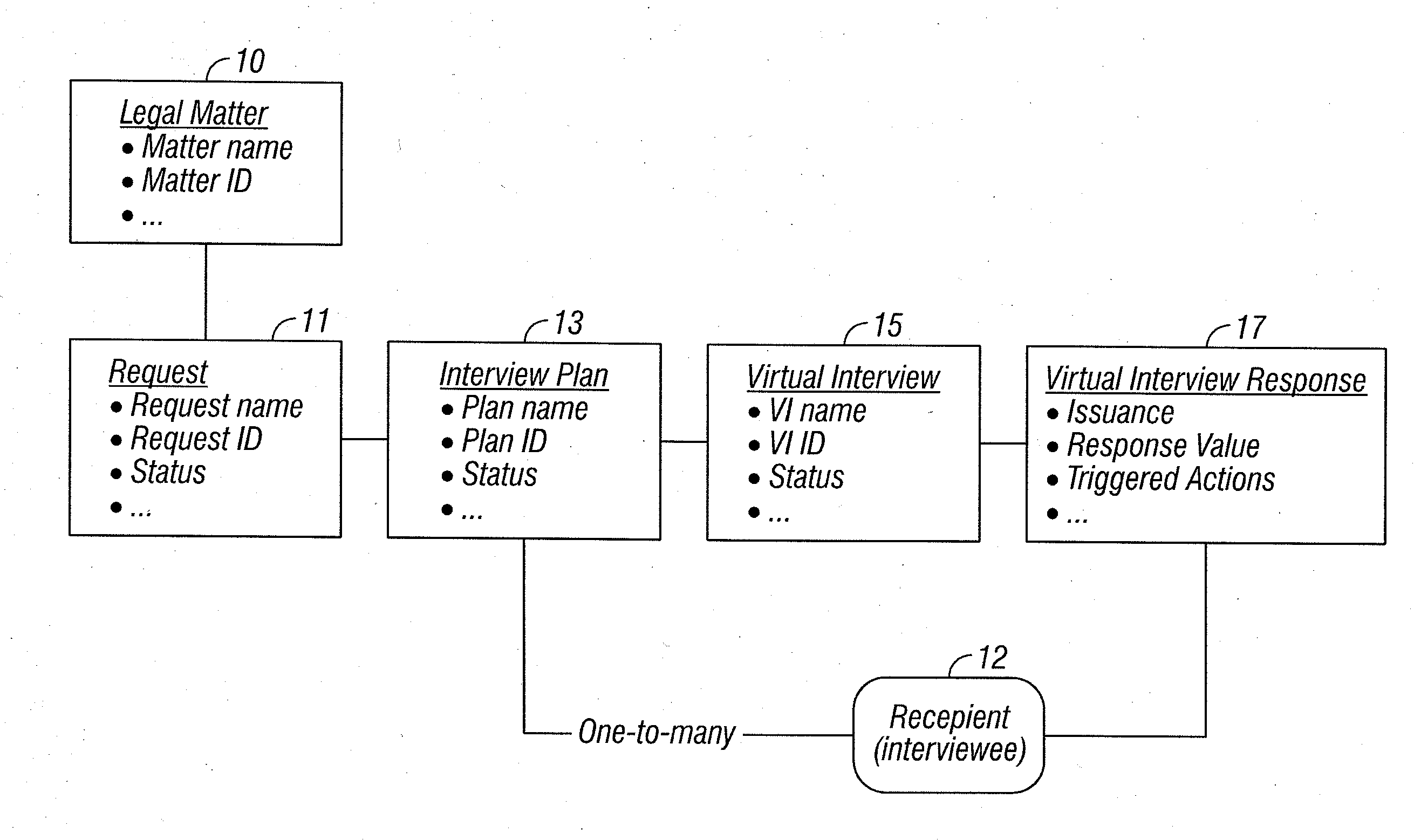
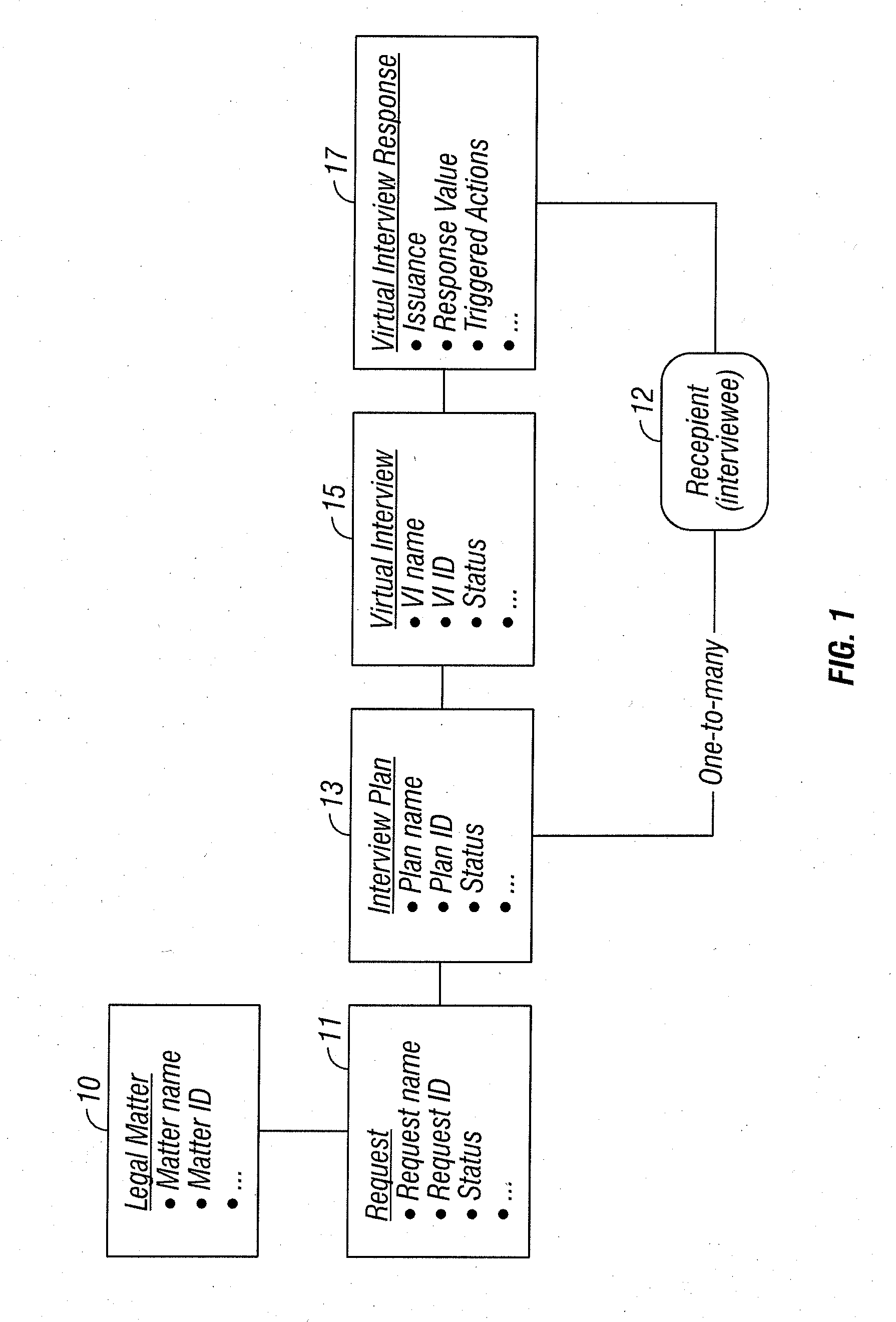
Conducting a virtual interview in the context of a legal matter
InactiveUS20090286219A1Quality improvementIncrease credibilityOffice automationResourcesFactoidInformation Harvesting
A virtual interview is conducted in the context of a legal matter, for example, using online forms, thus enabling rapid and large-scale information capture from distributed recipients. A user can define questions and virtual interviews once, and use them again and again; can define an approved set of questions to insure consistency of interview practice; and can de facto improve the consistency and credibility of information gathering in legal matters. Users can pre-establish action items that are automatically created upon receiving specific responses to virtual interviews. Interview response may be managed by exception, i.e. exception alerting, and tools are provided to view exceptional cases for follow-up action. For example, alerts can be issued on the basis of such factors as: if any one responded that they had data at home, send an alert to the attorney and an action item to do an appropriate collection; and if anyone responds that they know others in scope, initiate an action item assigned to paralegal to add identified individuals to scope. A user can conduct many interviews systematically to determine where all key facts related to the matter are located; to update information in a highly distributed way for effective legal management; and to manage responses efficiently.
Owner:IBM CORP
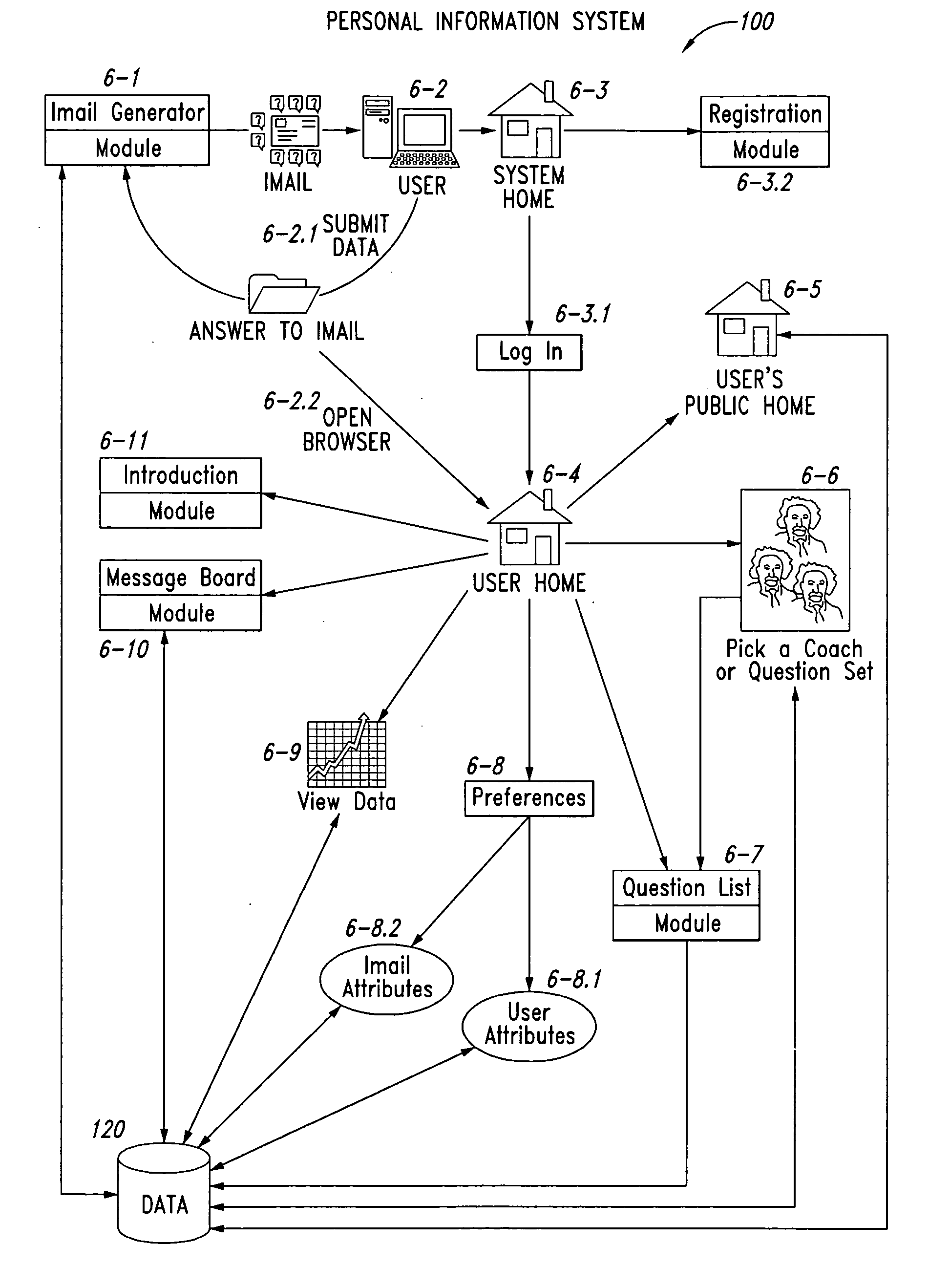
Personal information system and method
InactiveUS20050055232A1Office automationSpecial data processing applicationsInformation systemLibrary science
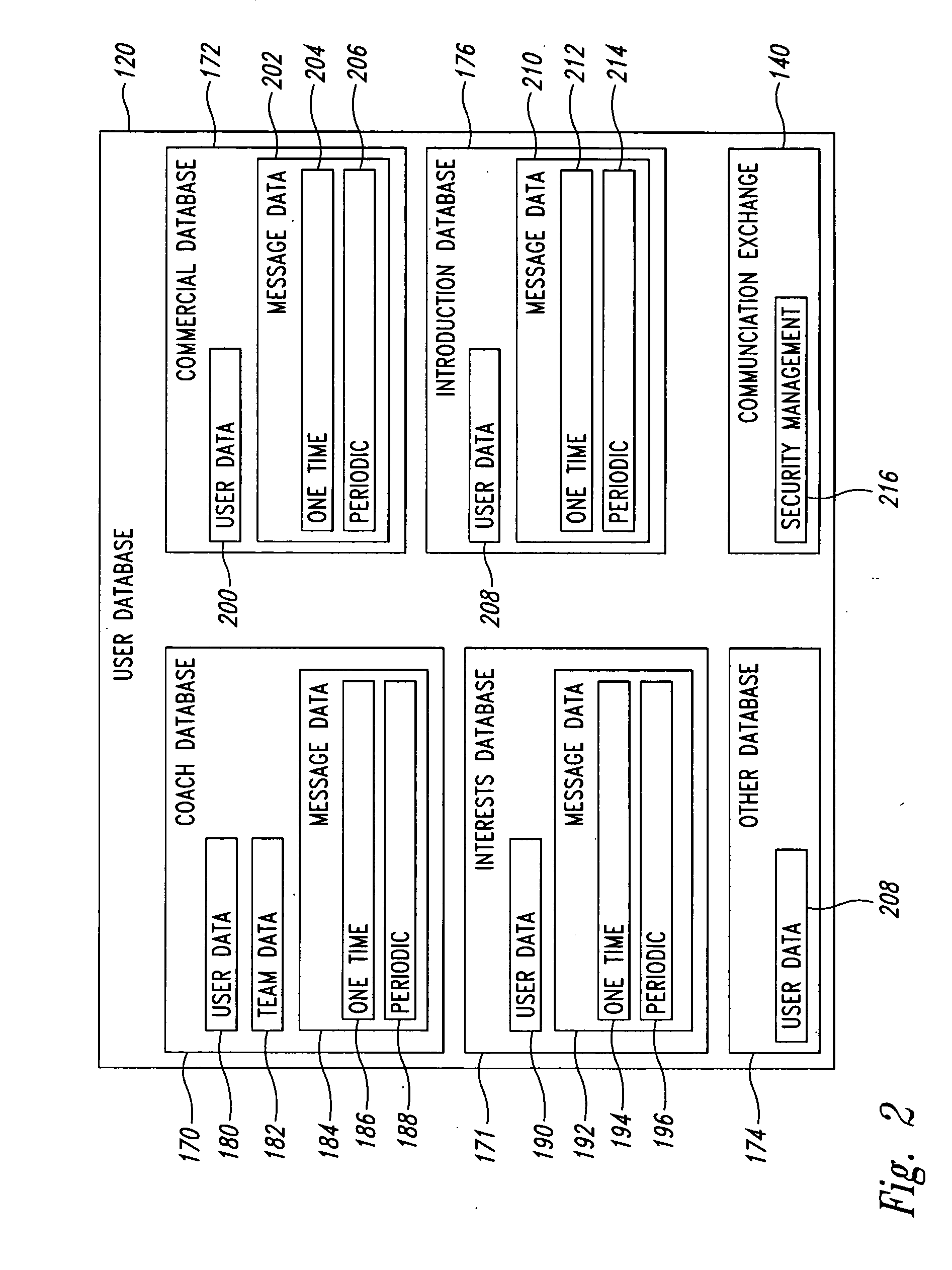
A personalized information system and method assists users in collecting information regarding goals and other interests by periodically sending related messages containing repeated questions to users. A user can select from a collection of predetermined questions, can originate questions, and can rely upon coaches or experts to develop related questions. The collected information can be reviewed by the user, a coach, or other expert to alter the questions, provide suggestions, or take other action. Information collection can be aided by allowing the user to respond to the questions directly within received e-mails without having to log onto another system. Vendors can also market goods and services to the users based on the collected information along with other financial transaction information as permitted by the users. Some implementations also provide for introductions between users based upon shared interests and other factors.
Owner:YATES PHILIP
System And Method For Stabilizing A Wireless Monitoring Network
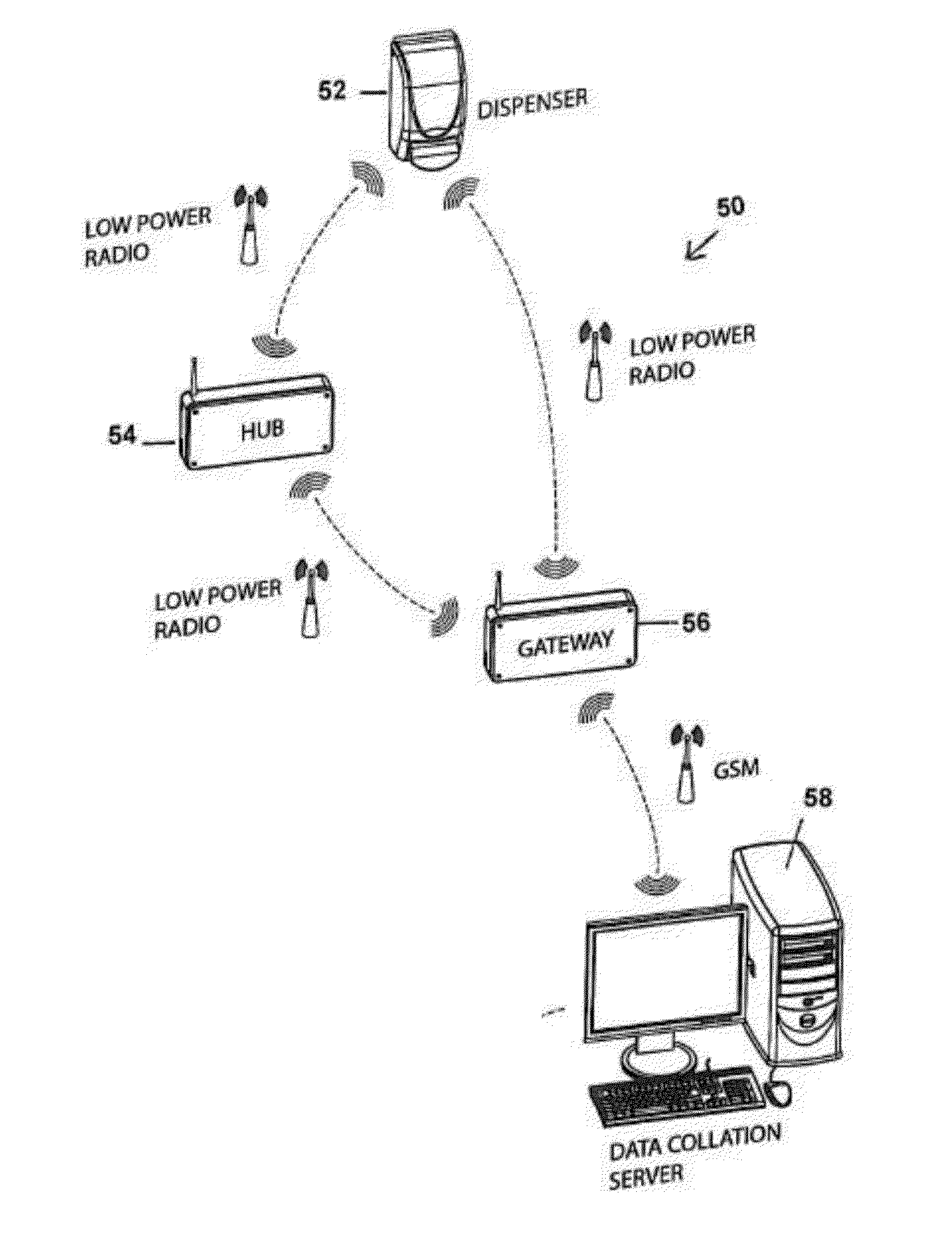
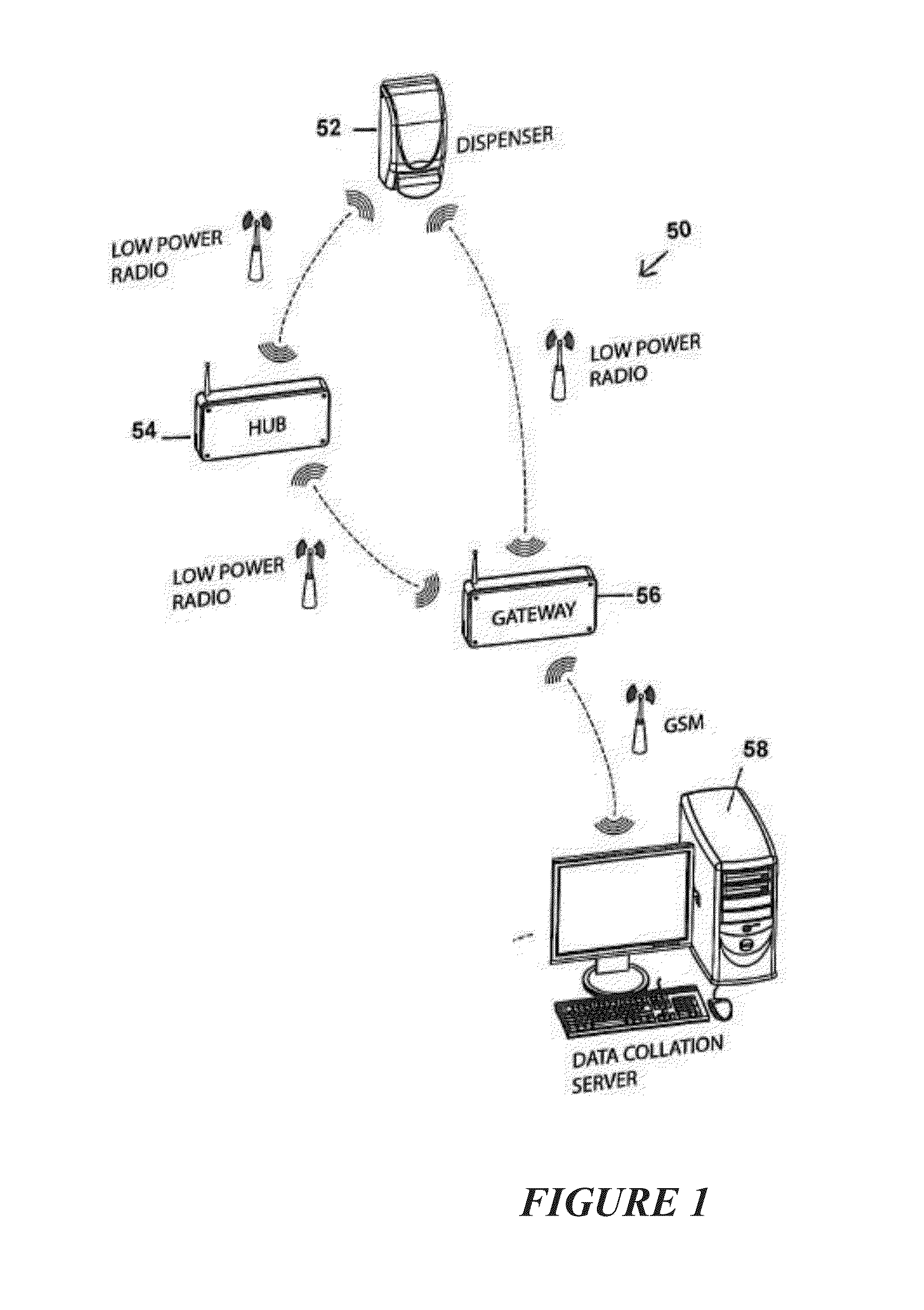
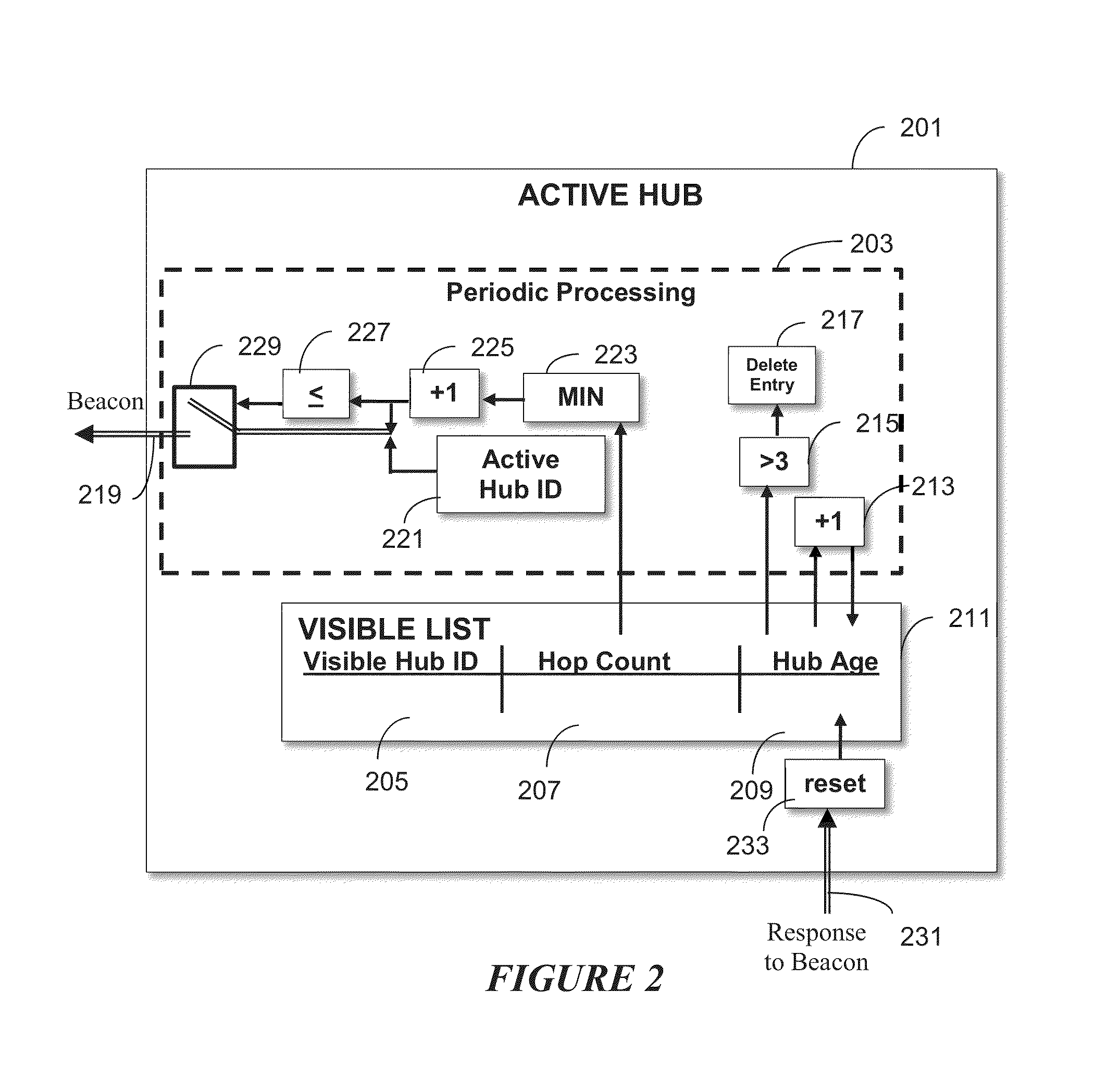
Stabilization of a wireless information collection system for dispenser usage compliance in a facility is provided. This system and method enable network stabilization by providing a network “heartbeat.” The network stabilization operates independently from information collection. Therefore, the system and method are able to improve the reliability of wireless information collection systems where the frequency of data collection is not steady.
Owner:DEB IP
Network security evaluation device based on attack graph adjacent matrix
The invention provides a network security evaluation device based on an attack graph adjacent matrix. The network security evaluation device comprises an information collection device, an atom attack graph generation device, a matrix calculation device, a network safety analyzing device and a result appearing device, wherein the information collection device is used for collecting all information in a network; the atom attack graph generation device is used for generating an initial atom attack graph between a main engine pair needed for carrying out subsequent analysis on network safety; the matrix calculation device is used for converting the generated atom attack graph into the corresponding adjacent matrix and is also used for calculating a corresponding iteration matrix of the adjacent matrix through setting iteration times; the network safety analyzing device is used for obtaining information including a key main engine, a key path and the like on the basis of the finally-generated iteration matrix; the result appearing device is used for visually appearing the found key main engine and key path and a network vulnerability index. The network security evaluation device disclosed by the invention is high in efficiency and is suitable for large-scale and high-speed networks. The network security evaluation device can improve the instantaneity of evaluating a target network. The evaluation accuracy rate is high, and the key path and the key main engine can be accurately recognized. The visualization degree is high so that the network security evaluation device is convenient for a manager to check, analyze and maintain.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com