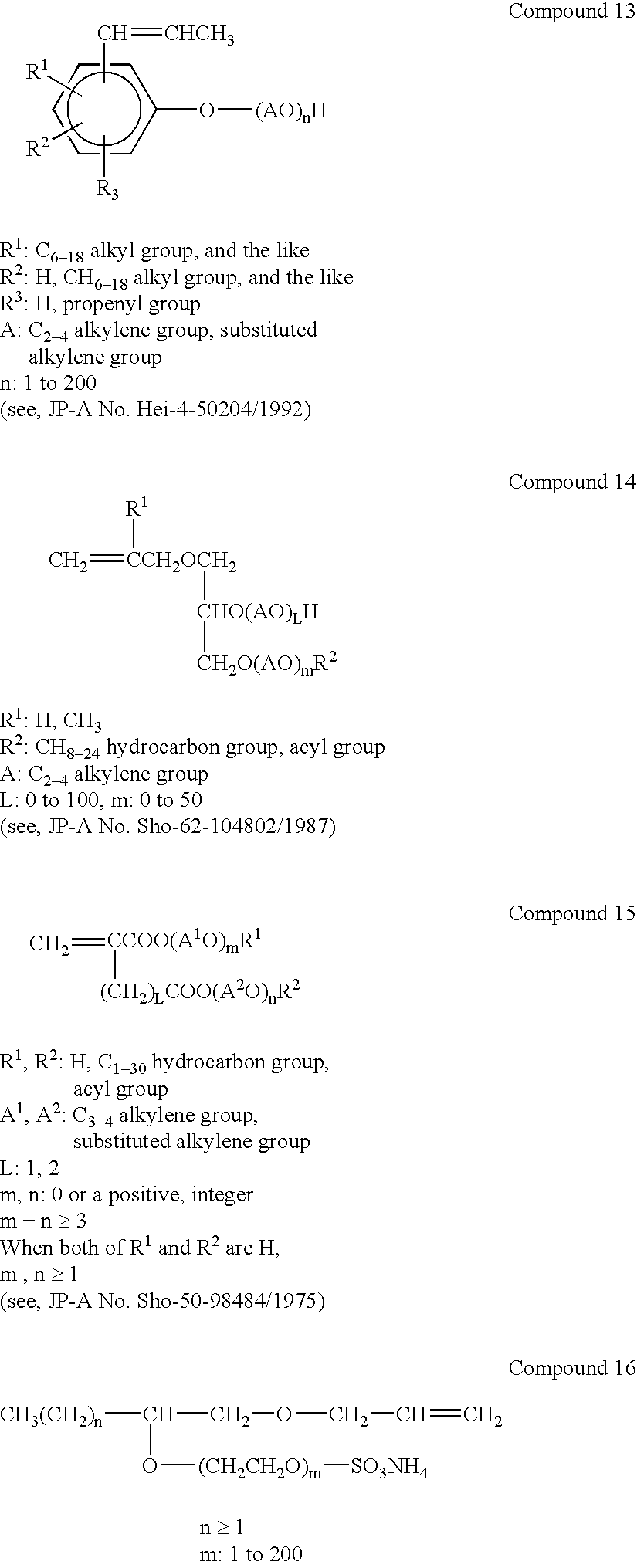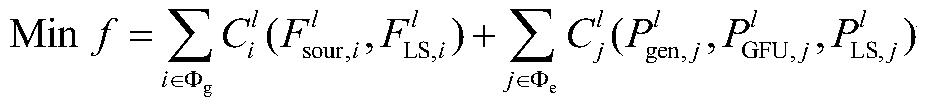Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
93results about How to "Improve vulnerability" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
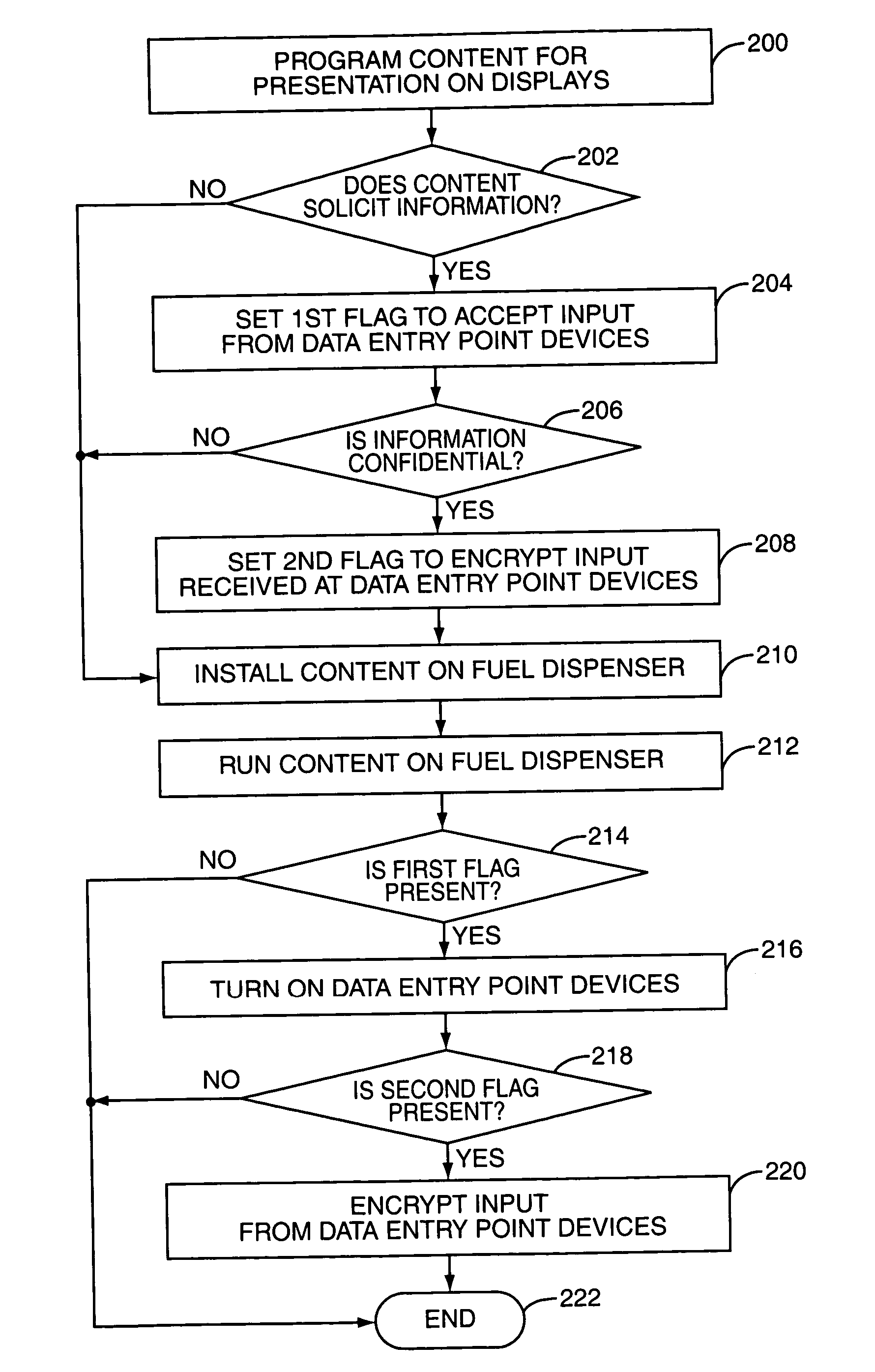
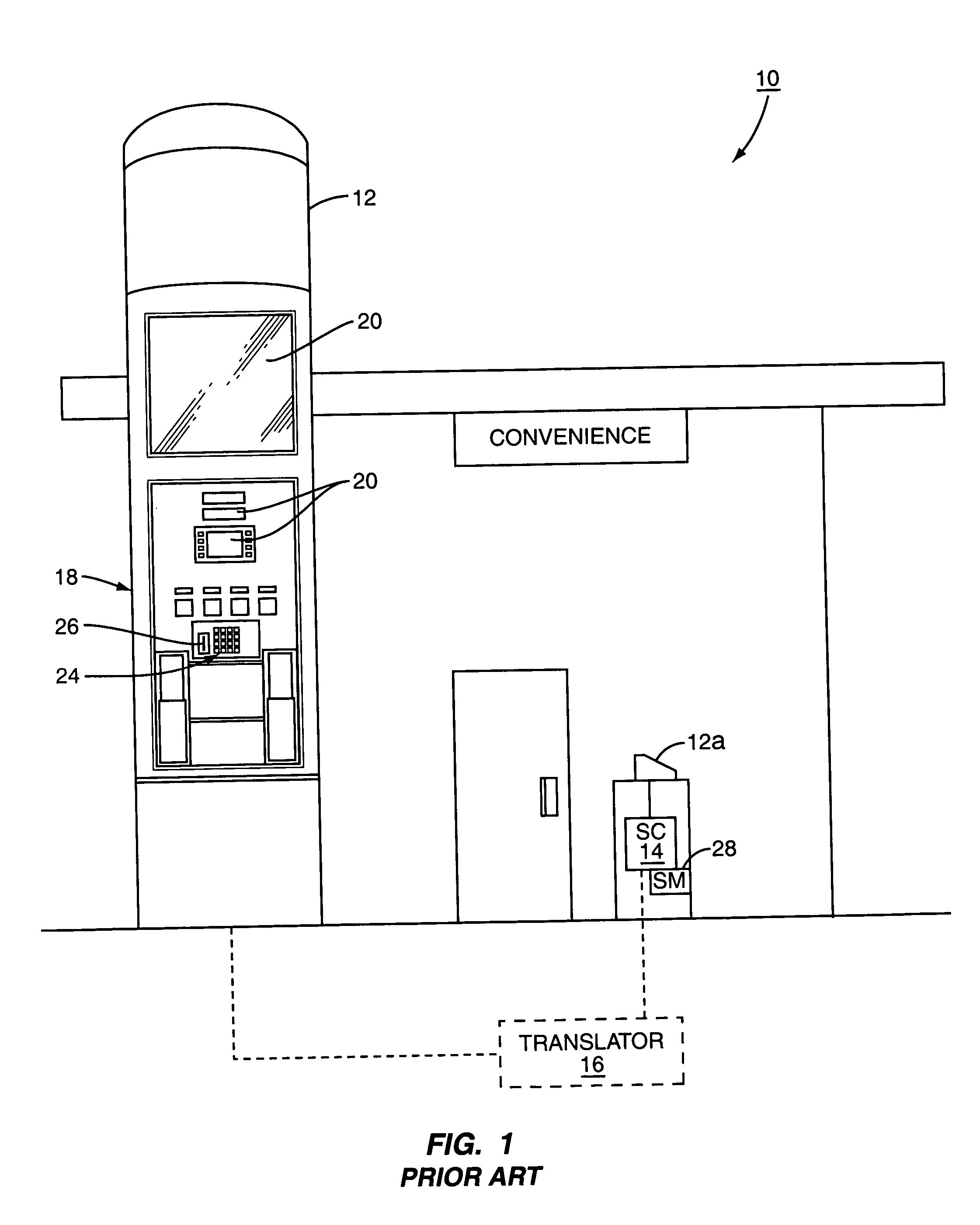
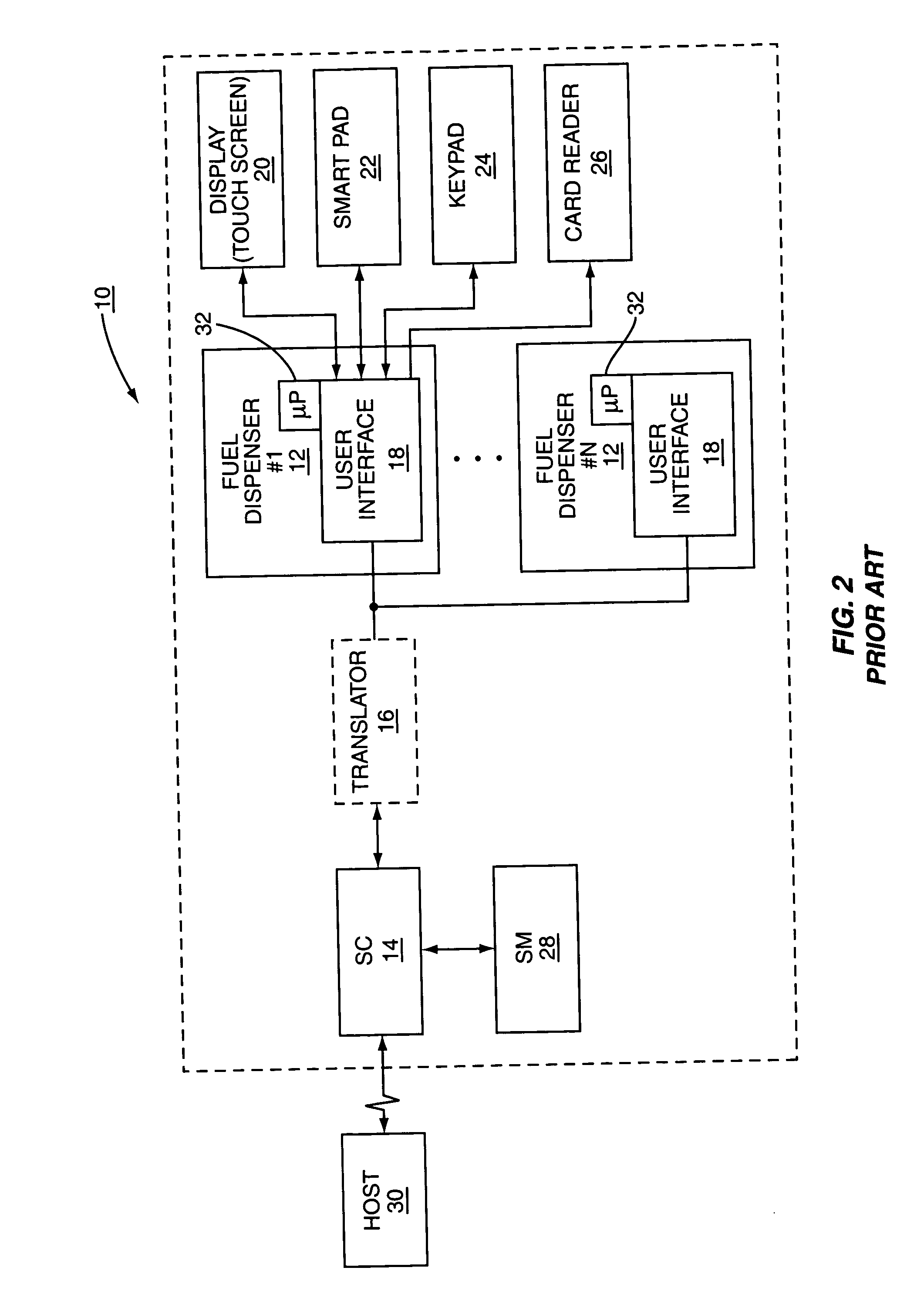
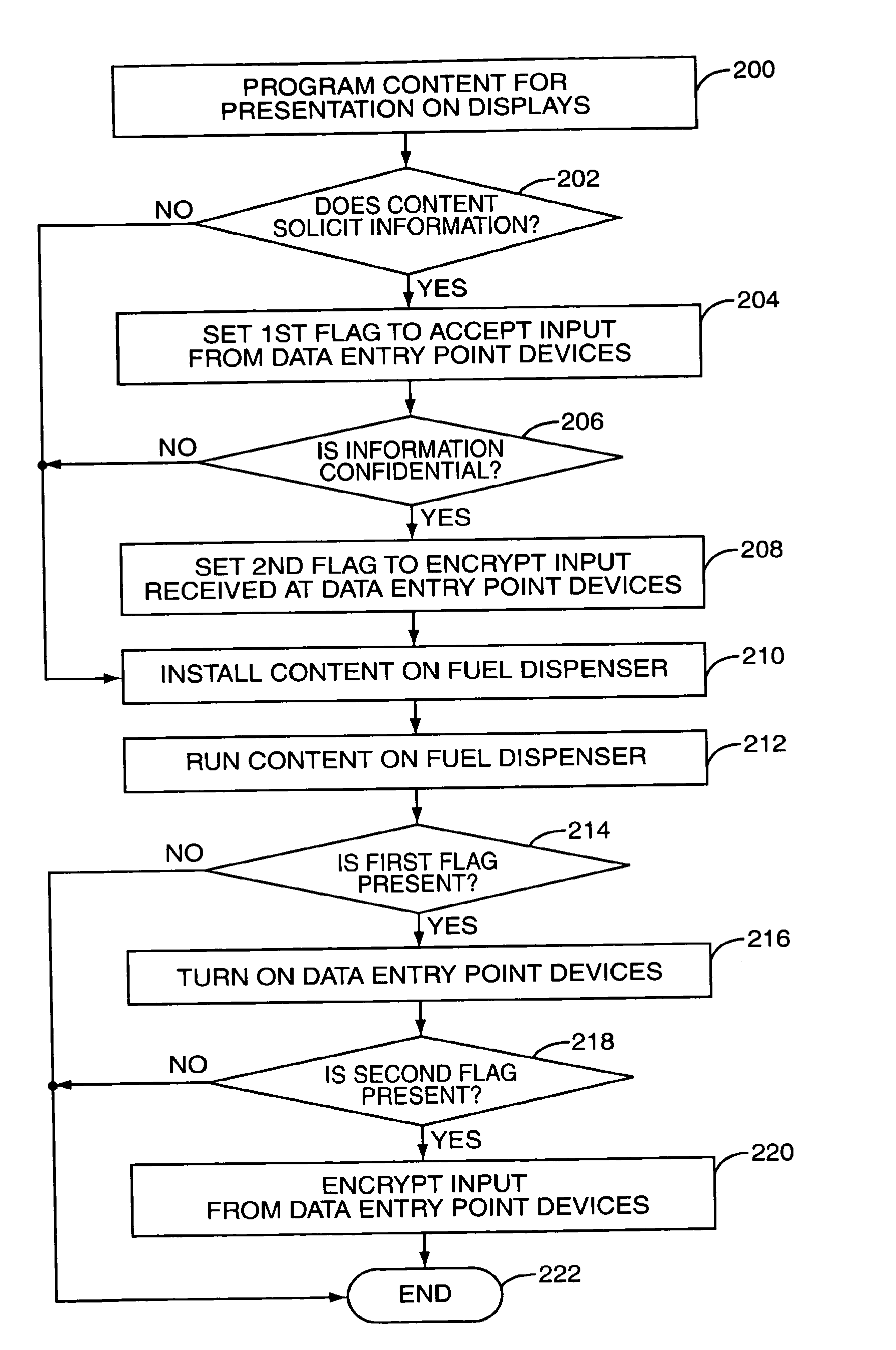
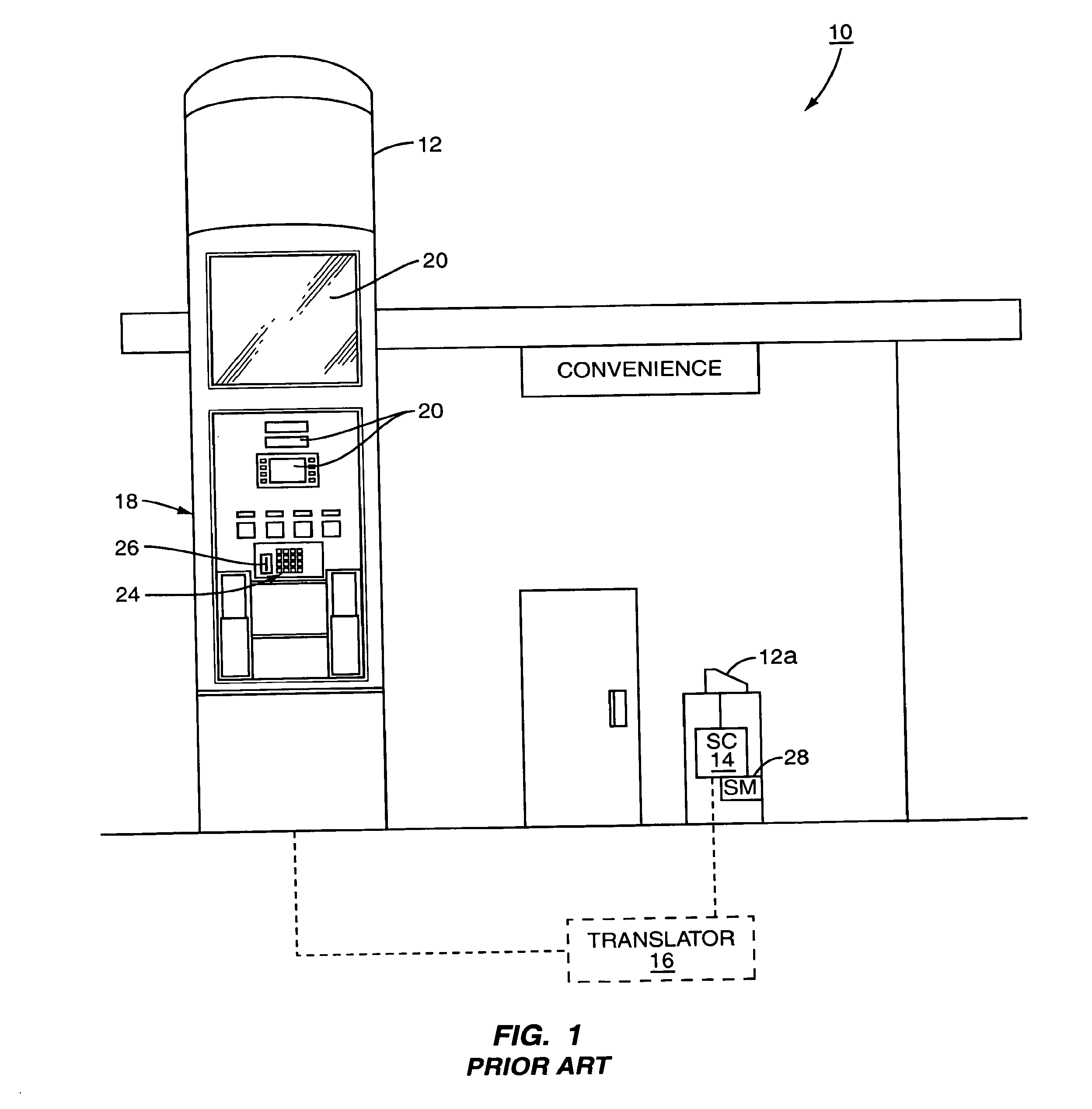
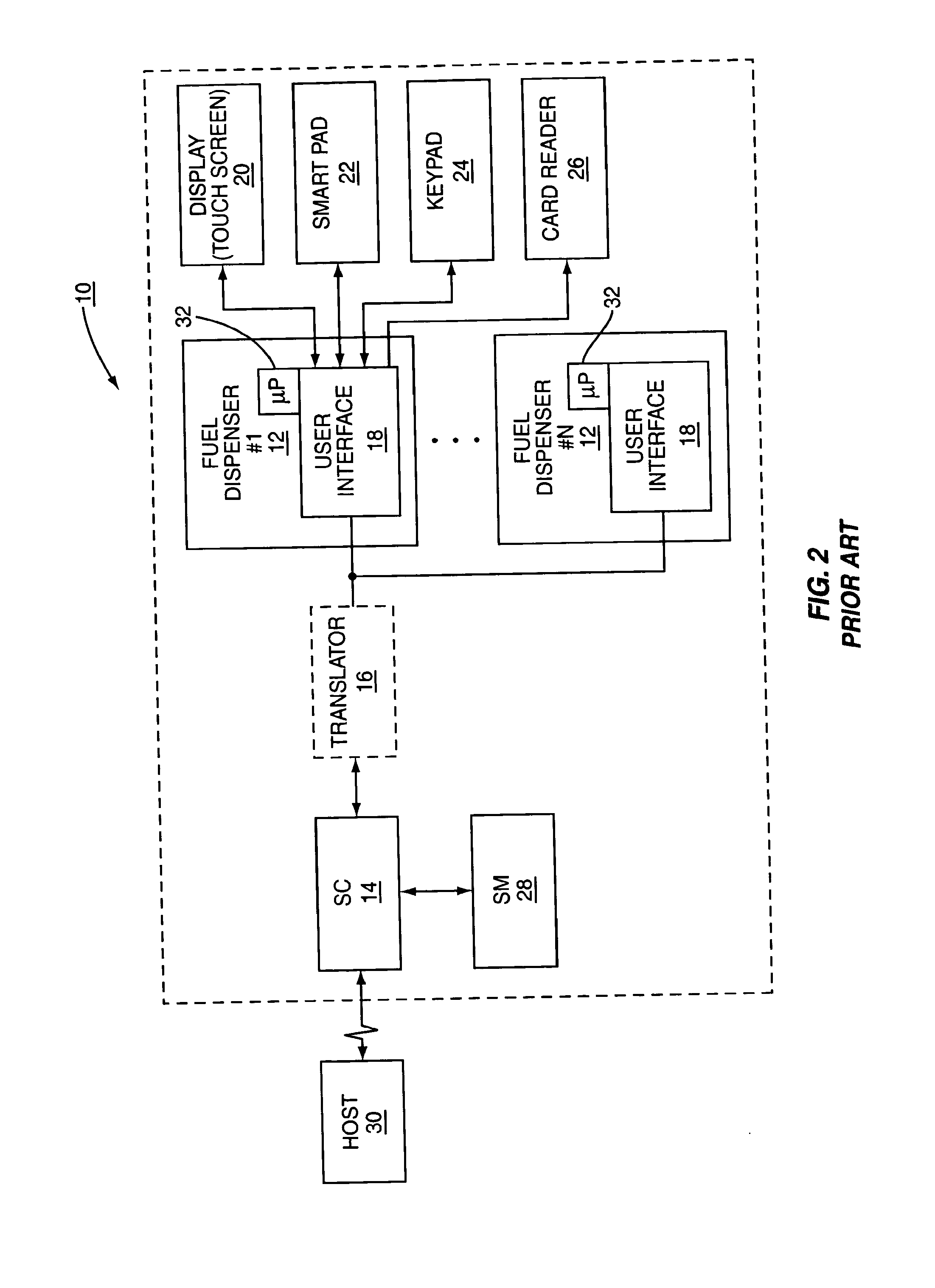
System and method for selective encryption of input data during a retail transaction
ActiveUS20070033398A1Enhance security vulnerabilityImprove vulnerabilityAcutation objectsUser identity/authority verificationPersonal identification numberPointing device
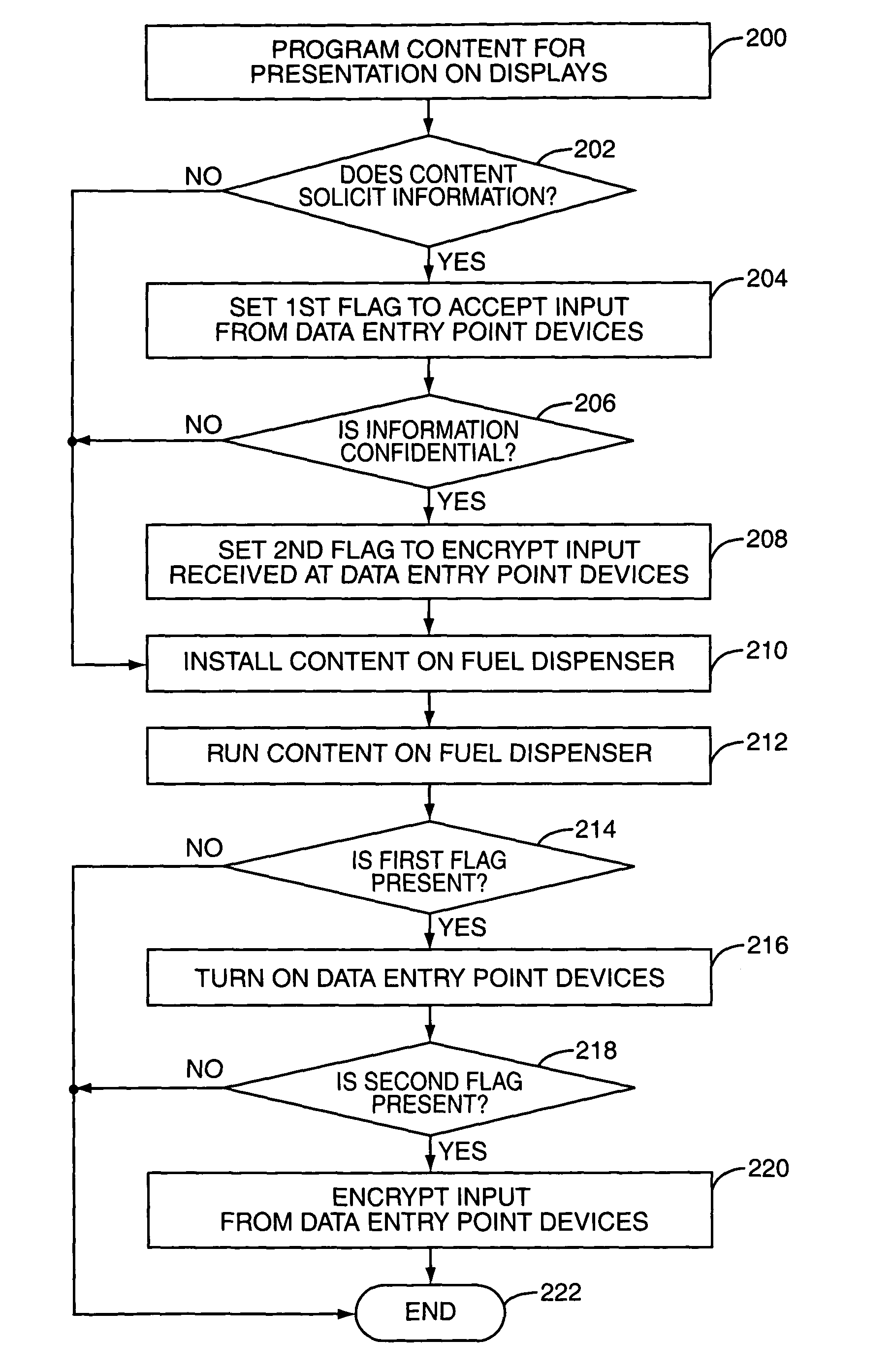
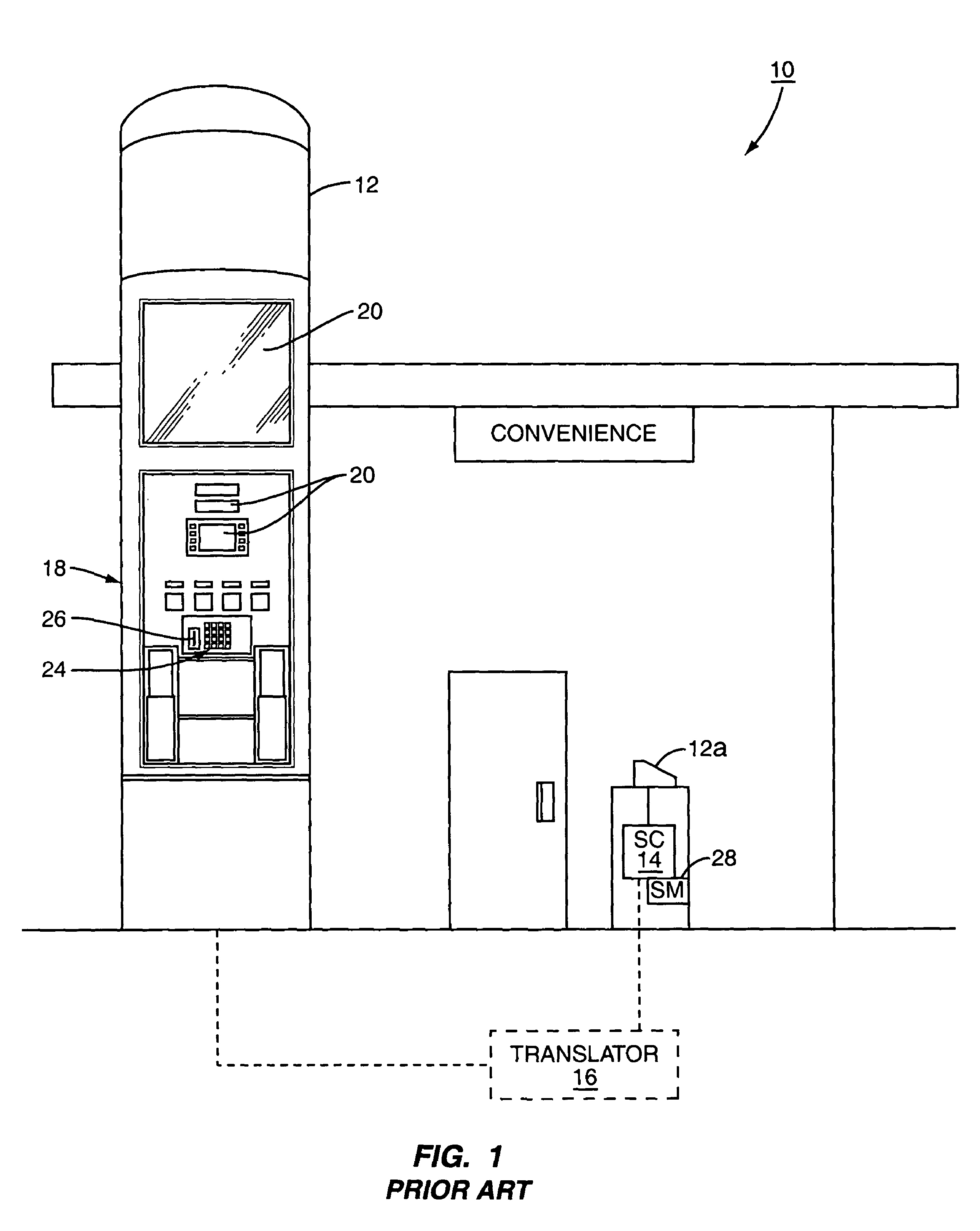
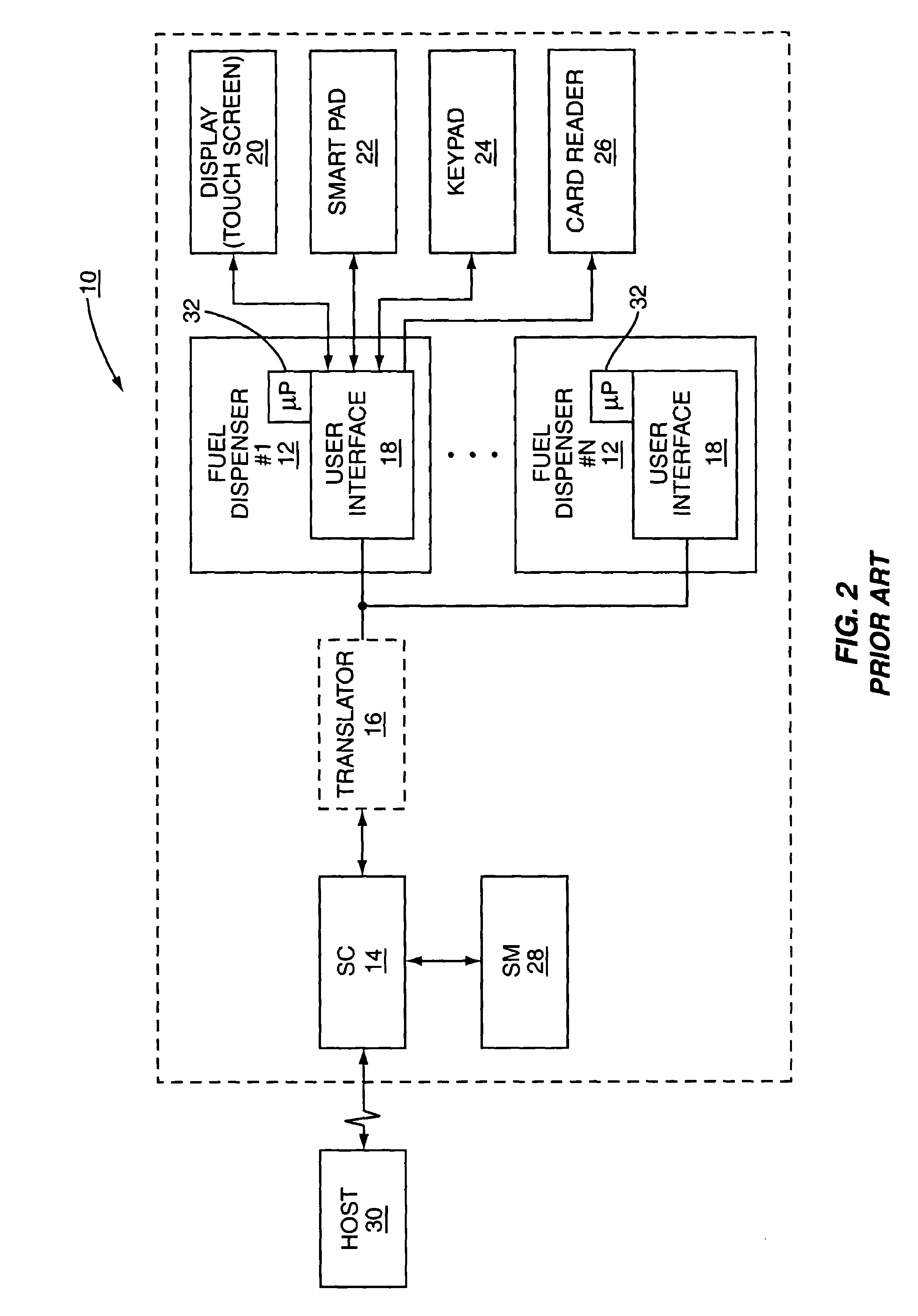
A retail environment having retail terminals with data entry point devices selectively encrypts input received by the data entry point devices and passes the encrypted data to a security module. The selective encryption is based on whether or not sensitive or confidential information, such as a personal identification number (PIN) associated with a debit card, is being input. To prevent hacking of the software of the retail terminal, content destined for display on the retail terminal is authenticated prior to display. In this manner, the retail terminal may be assured that confidential information is input only when desired, and thus may be encrypted only as needed.
Owner:GILBARCO
Thermosetting Resin Composition and Application Thereof
InactiveUS20100240811A1Excellent dielectric propertiesIncrease thermal resistanceBiocideOrganic chemistryTetrabromobisphenol ASolvent
The present invention discloses a thermosetting resin composition including: a bi-functional or multi-functional epoxy resin, a SMA uses as a curing agent, an allyl phenol such as diallyl bisphenol A used as a co-curing agent and a toughening agent a low-bromine or high-bromine BPA epoxy resin or tetrabromobispheno A (TBBPA or TBBA) uses as a flame retardant agent, and an appropriate solvent. After the resin composition of the invention is cured, the resin composition has lower dielectric property and better thermal reliability and tenacity. A copper clad laminate made of an enhanced material such as glass fiber has lower dielectric constant (Dk) and loss tangent (Df), high Tg, high thermal decomposition temperature (Td), better tenacity and PCB manufacturability, and thus very suitable to be used as a copper clad laminate and a prepreg for manufacturing PCBs or applied as a molding resin material for contraction, automobile and air navigation.
Owner:ITEQ DONGGUAN +1
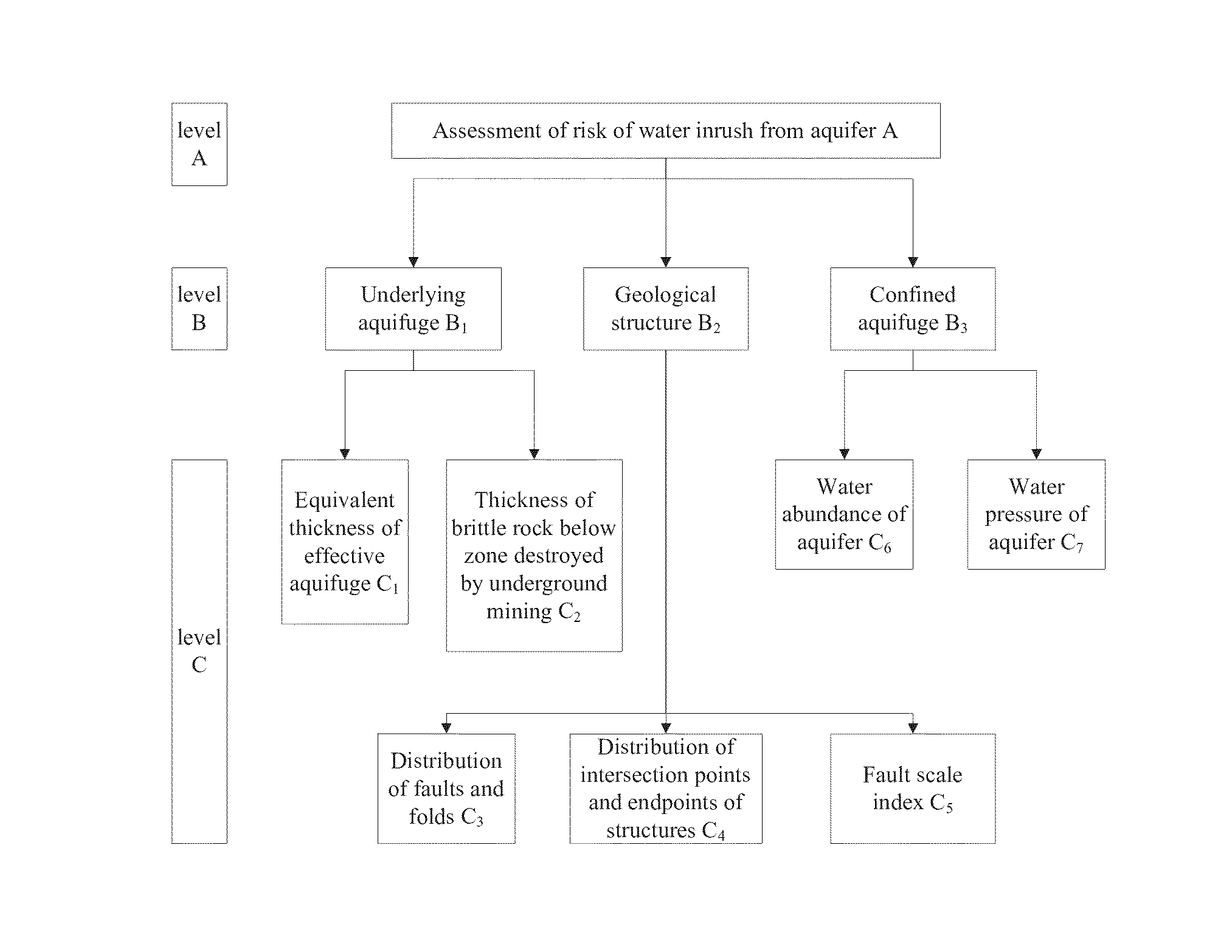
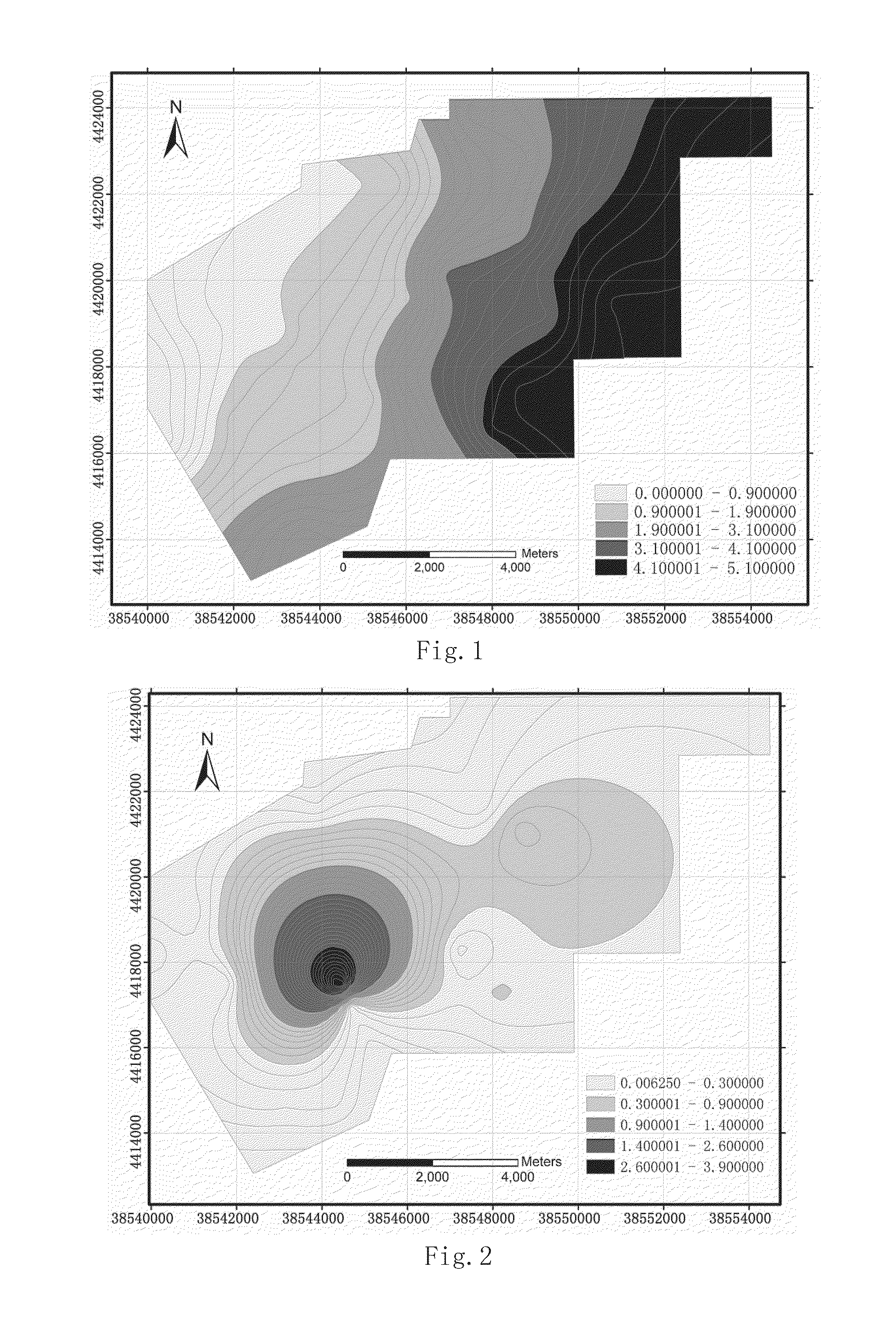
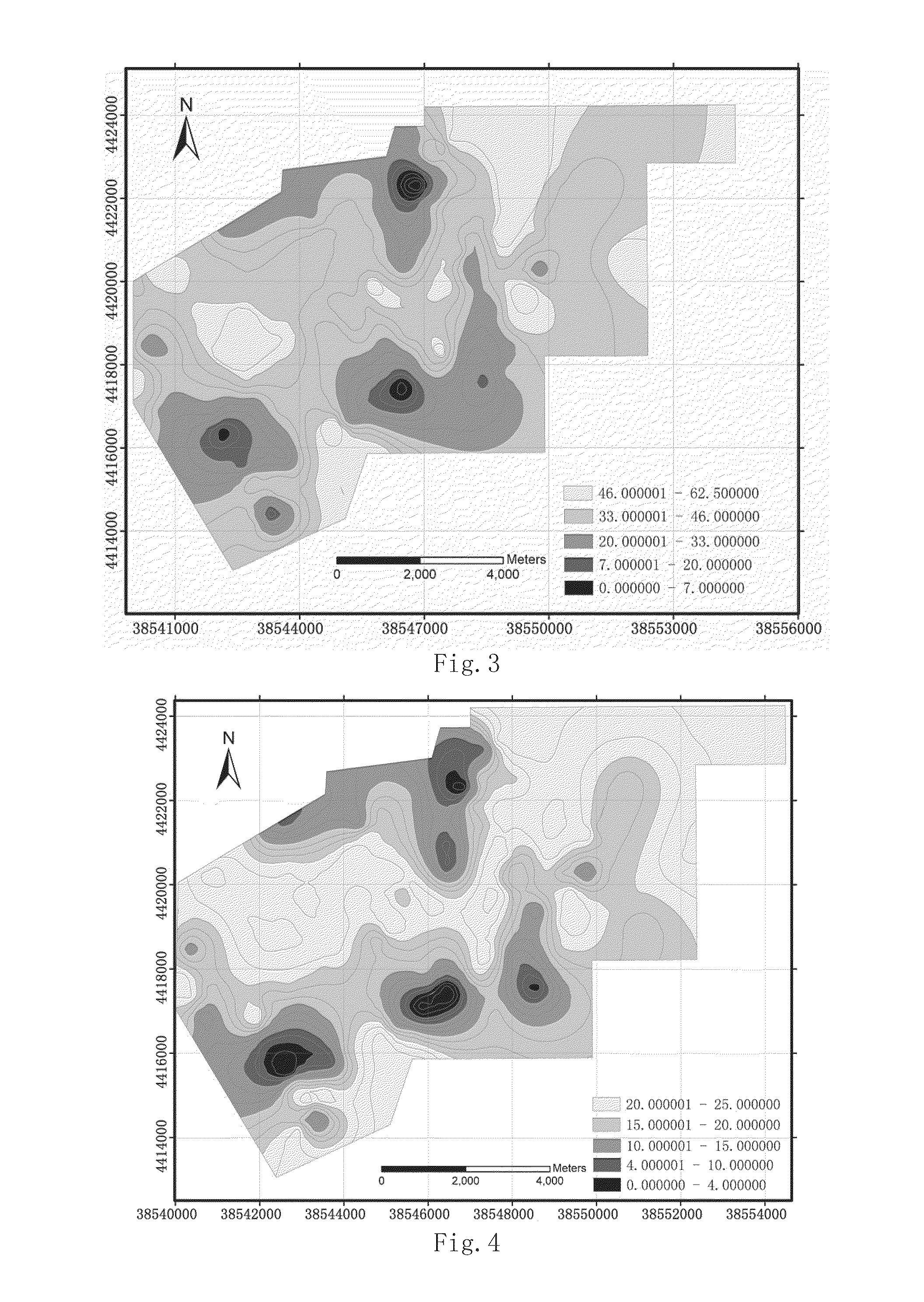
Vulnerability Assessment Method of Water Inrush from Aquifer Underlying Coal Seam
InactiveUS20160070828A1Improve vulnerabilitySolve the real problemMining devicesSeismologySuperimpositionThematic map
A vulnerability assessment method of water inrush from an aquifer underlying coal seam includes steps of: collecting main control factors determined by geological data of a target area to be assessed; quantifying relevant data against the main control factors to form thematic maps; performing normalization processing against attribute data corresponding to the respective thematic maps; establishing databases of normalized attribute data corresponding to the normalized thematic maps by utilizing GIS; determining a weight of each main control factor based on a constant weight model; determining a variable weight of each main control factor based on a zonation variable weight model; performing composite superimposition on the normalized thematic maps of the respective single main control factors, and newly building a topological relation of the relevant data among the attribute databases for performing multi-factor fitting analysis; and establishing a vulnerability assessment model based on the zonation variable weight model.
Owner:CHINA UNIV OF MINING & TECH BEIJNG
Transfer-molded power device and method for manufacturing transfer-molded power device
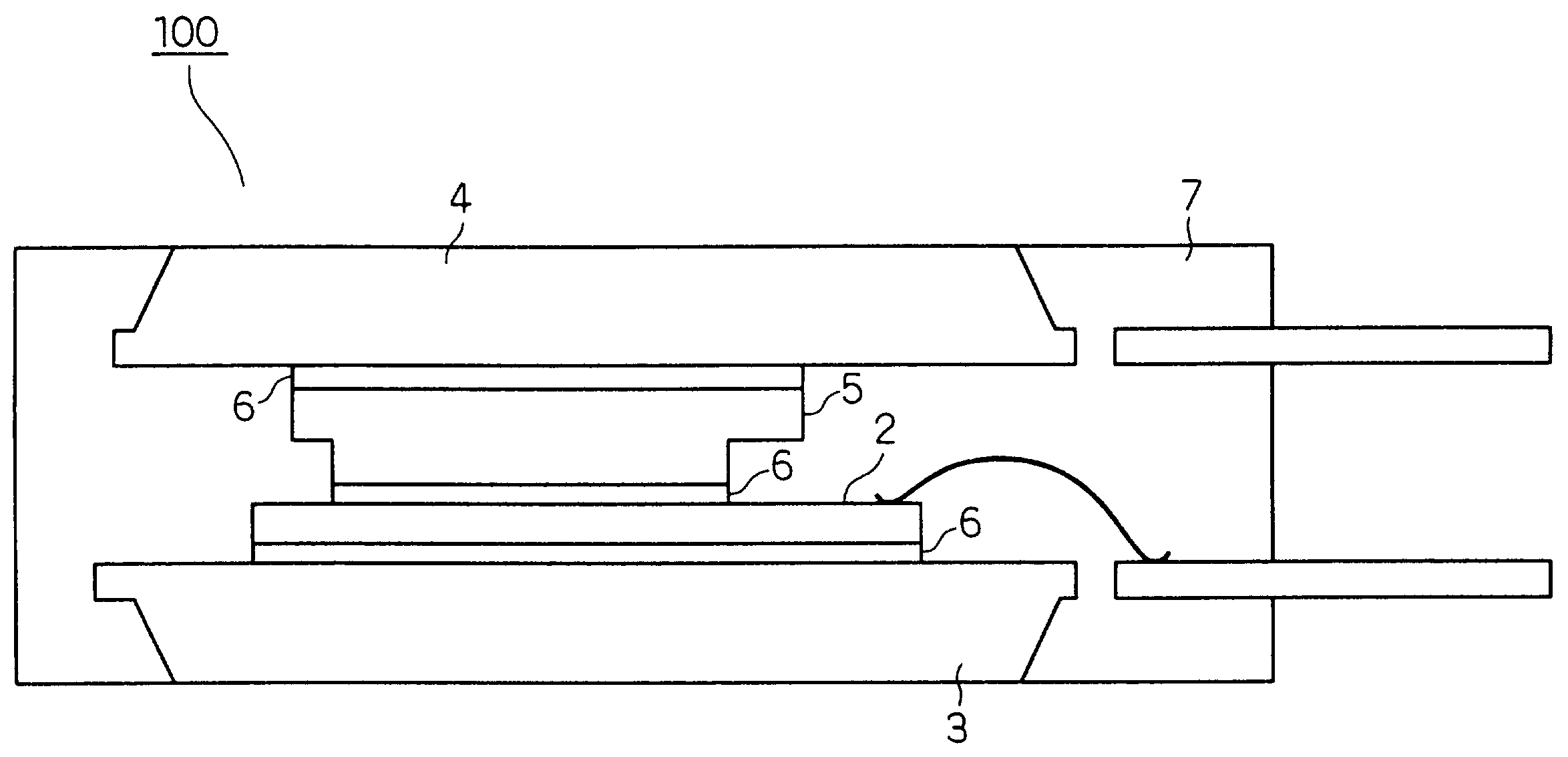
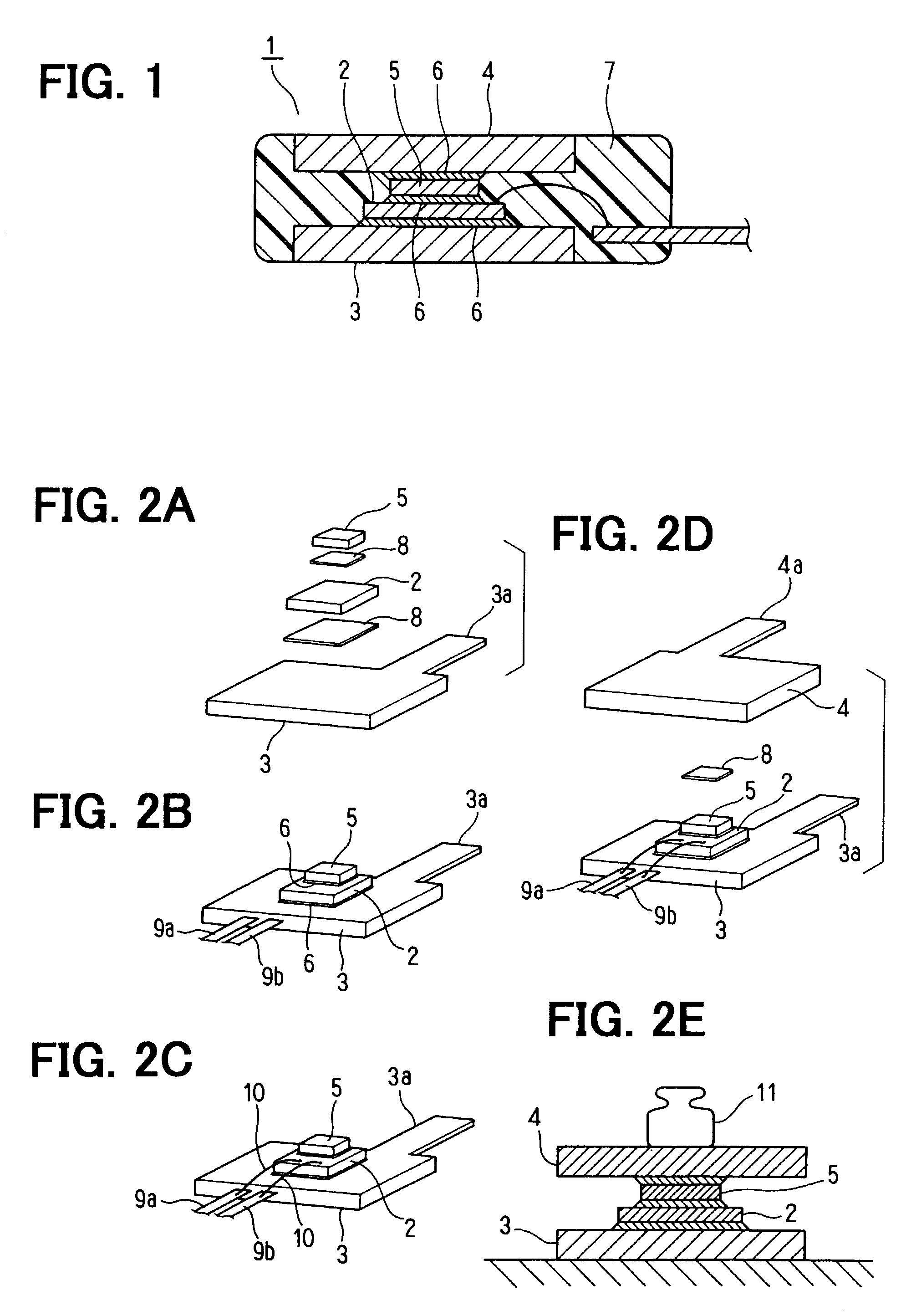
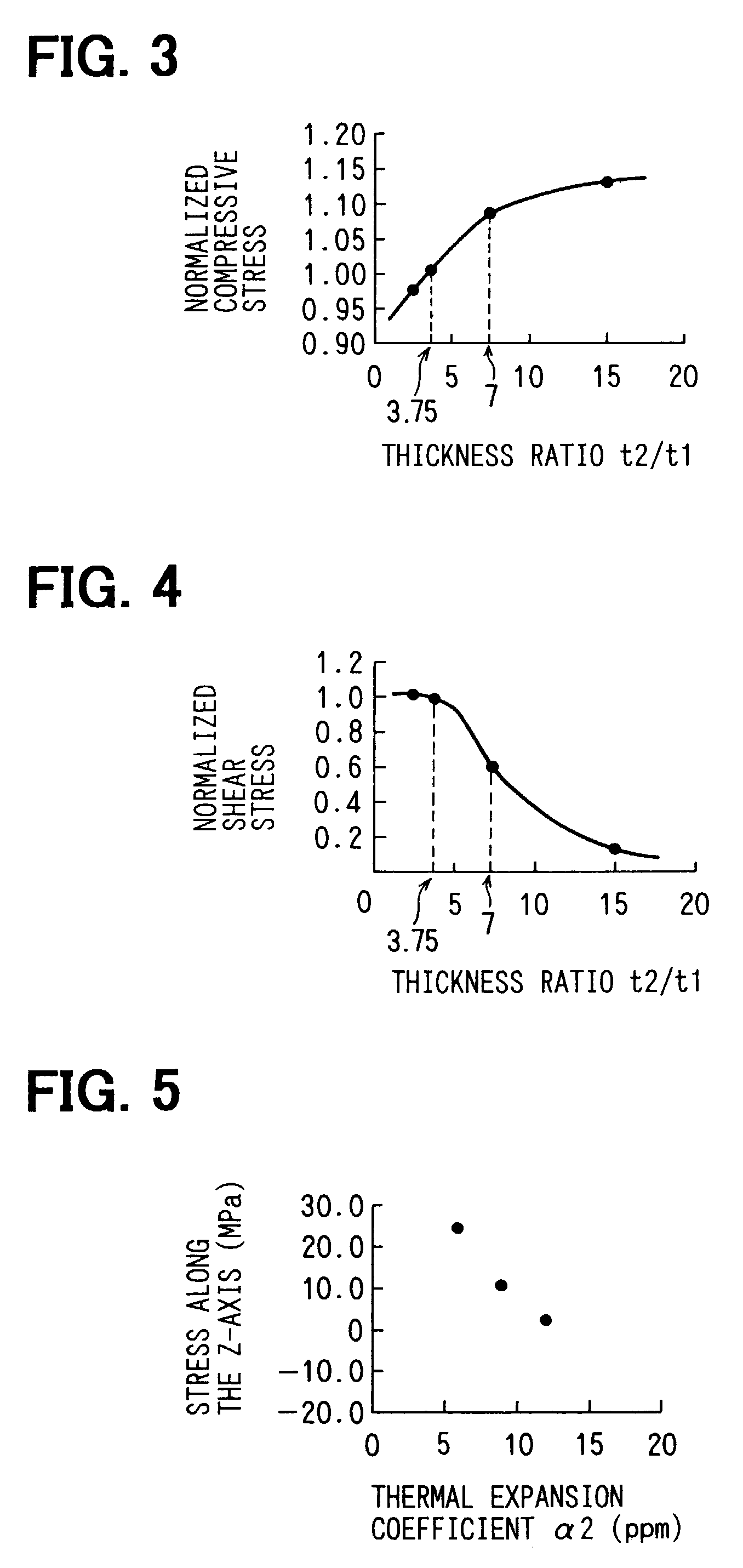
InactiveUS7145254B2Improve vulnerabilityPreventing a solder from breakingSemiconductor/solid-state device detailsSolid-state devicesSemiconductor chipTransfer molding
A semiconductor device includes a semiconductor chip that generates heat in operation, a pair of heat sinks for cooling the chip, and a mold resin, in which the chip and the heat sinks are embedded. The thickness t1 of the chip and the thickness t2 of one of heat sinks that is joined to the chip using a solder satisfy the equation of t2 / t1≧5. Furthermore, the thermal expansion coefficient α1 of the heat sinks and the thermal expansion coefficient α2 of the mold resin satisfy the equation of 0.5≦α2 / α1≦1.5. In addition, the surface of the chip that faces the solder has a roughness Ra that satisfies the equation of Ra≦500 nm. Moreover, the solder is a Sn-based solder to suppress relaxation of a compressive stress in the chip, which is caused by the creeping of the solder.
Owner:DENSO CORP
Dosage forms useful for modifying conditions and functions associated with hearing loss and/or tinnitus
InactiveUS6524619B2Increased vulnerabilityImproves NO-dependent vasodilatationSalicyclic acid active ingredientsBiocideWhole bodyActive agent
The invention defines interdependent biofactors and biomolecules, and clinically useful formulations that are comprised of them. The active agents are demonstrated to be complementary in their physiologic functions especially as these relate to the quenching of free radicals and to the support of endothelial physiology, the reduction of hyperinsulinemia and improvements in vascular health. The active components of the invention are selected for inclusion in precise combinations specifically because they improve these various conditions and physiological functions, and by so doing reduce a variety of risks associated with hearing loss and tinnitus. The resulting enhancement of general systemic vascular health, improvement in local VIIIth nerve vascular health, modulation of conditions surrounding blood fluid dynamics, the consequences of hyperinsulinemia, and improvements in free radical defenses, all reduce the potential for cochlear hair cell death and VIIIth nerve atrophy, and the hearing loss and possible deafness that accompany them.
Owner:CHRONORX
Systems and methods for determining optimal remediation recommendations in penetration testing
ActiveUS10382473B1High vulnerabilityHigh degreeComputer security arrangementsTransmissionNetworked systemCost effectiveness
Methods and systems for providing a recommendation for improving the security of a networked system against attackers. The recommendation may include a recommendation of a single attacker step to be blocked to achieve optimal improvement in security, or of multiple such attacker steps. If the recommendation includes multiple attacker steps, the steps may be ordered such that the first attacker step is more important to block, provides a greater benefit by blocking, or is more cost effective to block than subsequent attacker steps in the ordered list of attacker steps.
Owner:XM CYBER LTD
Program Vulnerability Identification
ActiveUS20160300065A1Easy to identifyFacilitates remediationPlatform integrity maintainanceApplication softwareSource code
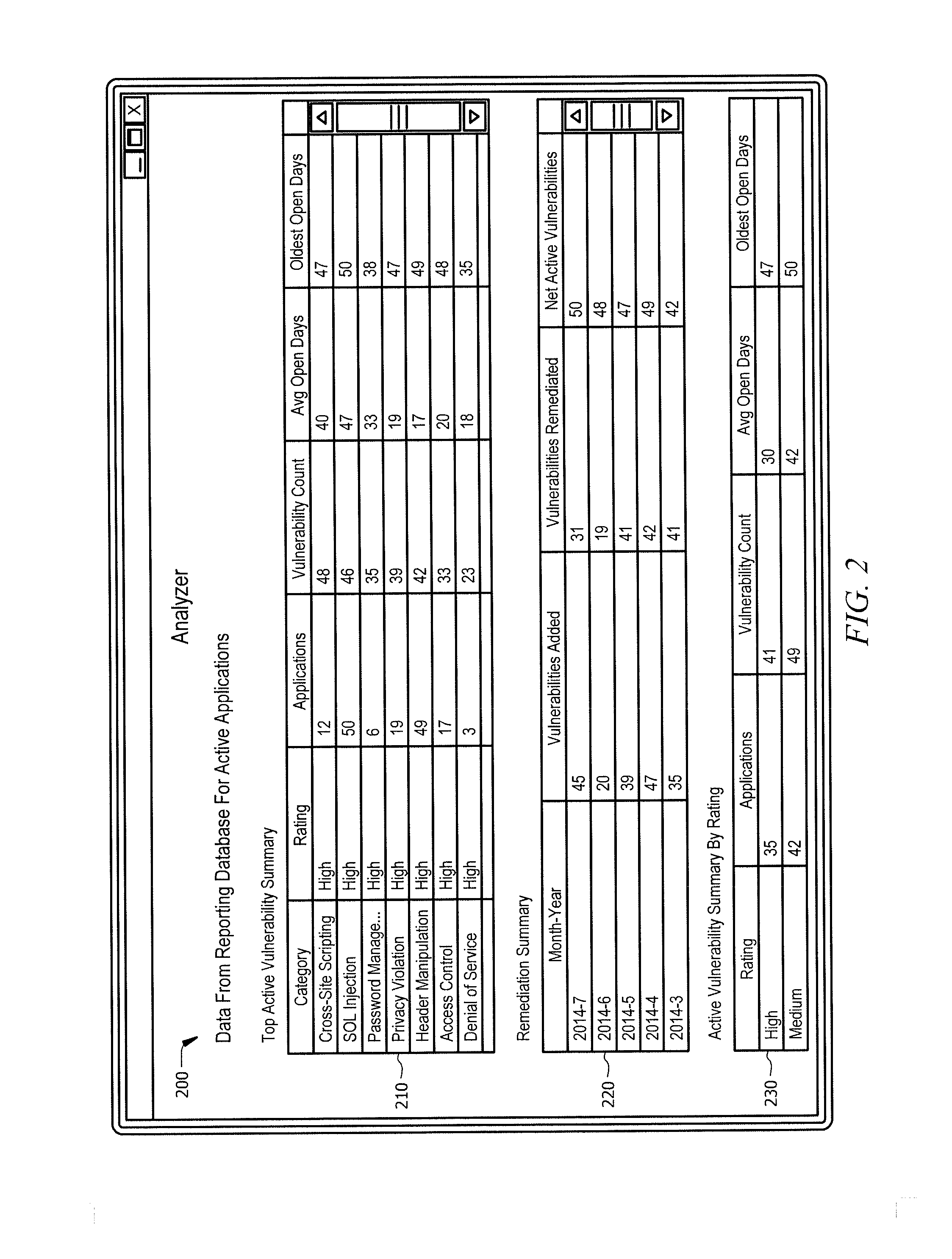
In one embodiment, a system for identifying and tracking application vulnerabilities includes an interface, a processor, and a memory. The interface is operable to receive a plurality of applications from one or more business units, each of the plurality of applications including source code. A process is communicatively coupled to the interface and is operable to identify a vulnerability associated with the source code of each of the plurality of applications. A memory is communicatively coupled to the interface and the processor and operable to store the vulnerability and the source code associated with the vulnerability in a vulnerability database. The processor is further operable to create a vulnerability tag for the vulnerability stored in the vulnerability database. The memory may also store the vulnerability tag for the vulnerability in a reporting database.
Owner:BANK OF AMERICA CORP
System and method for selective encryption of input data during a retail transaction
ActiveUS7953968B2Improve vulnerabilityAcutation objectsUser identity/authority verificationPersonal identification numberPointing device
Owner:GILBARCO
On-board water treatment and management process and apparatus
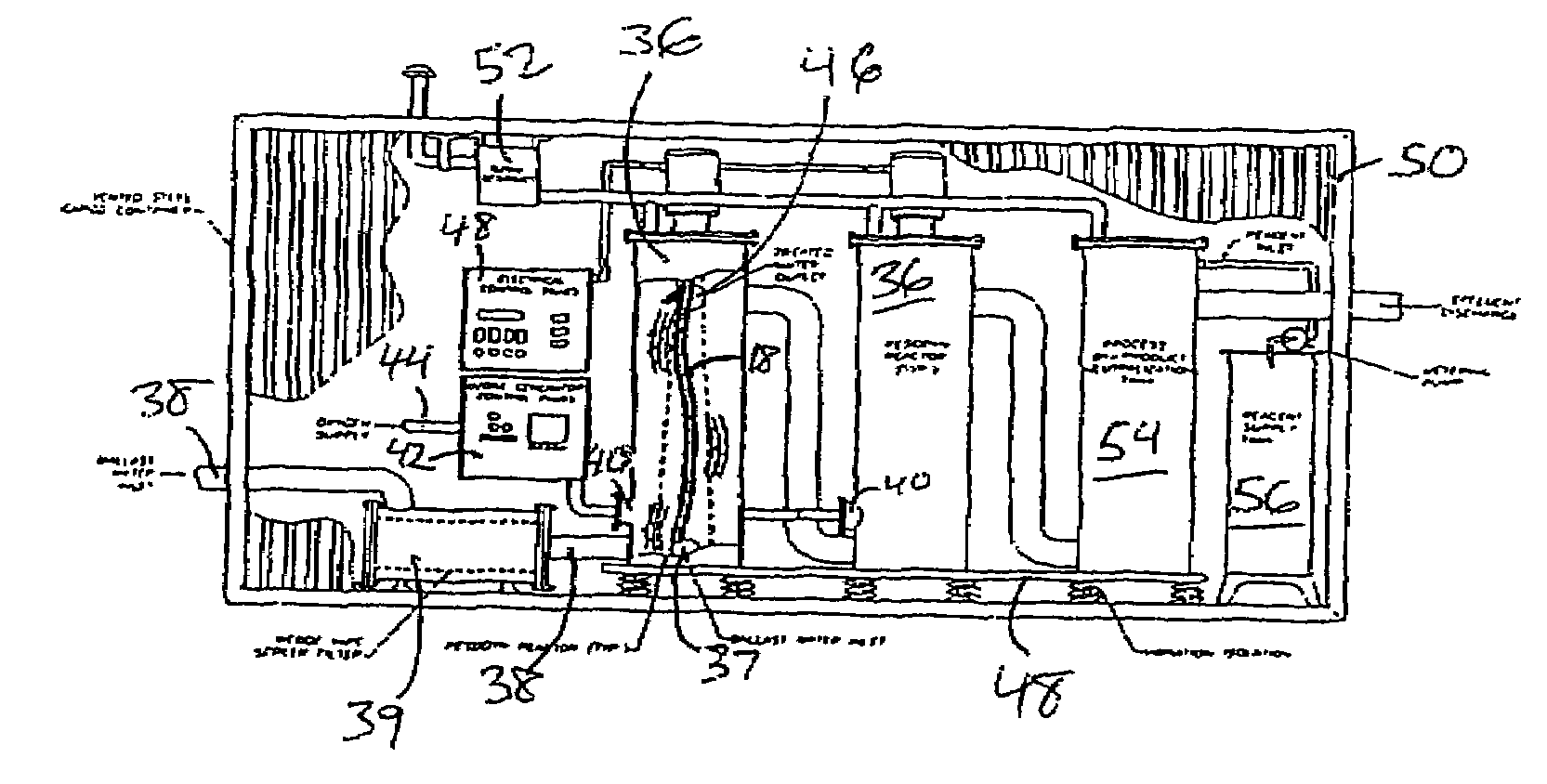
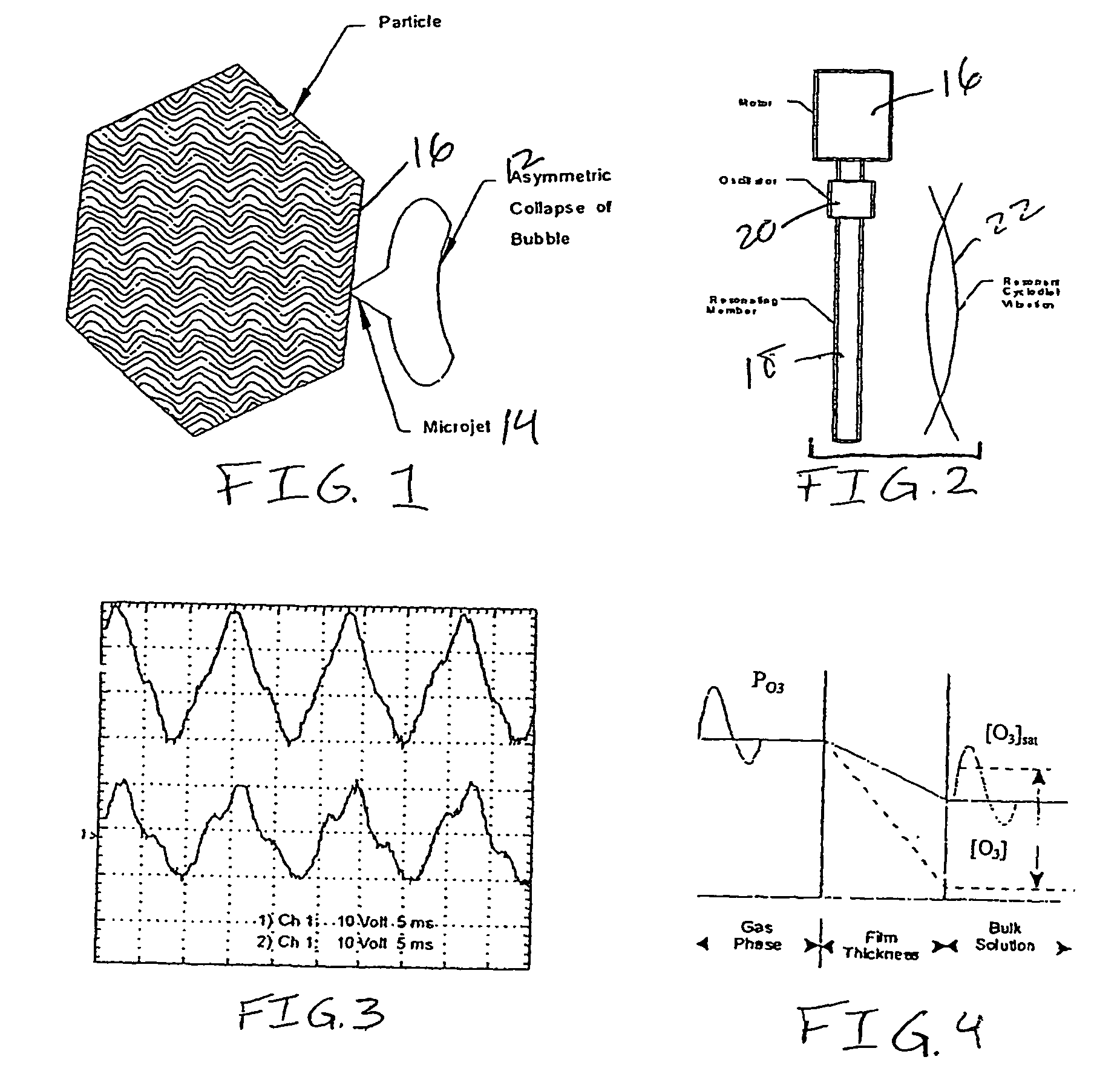
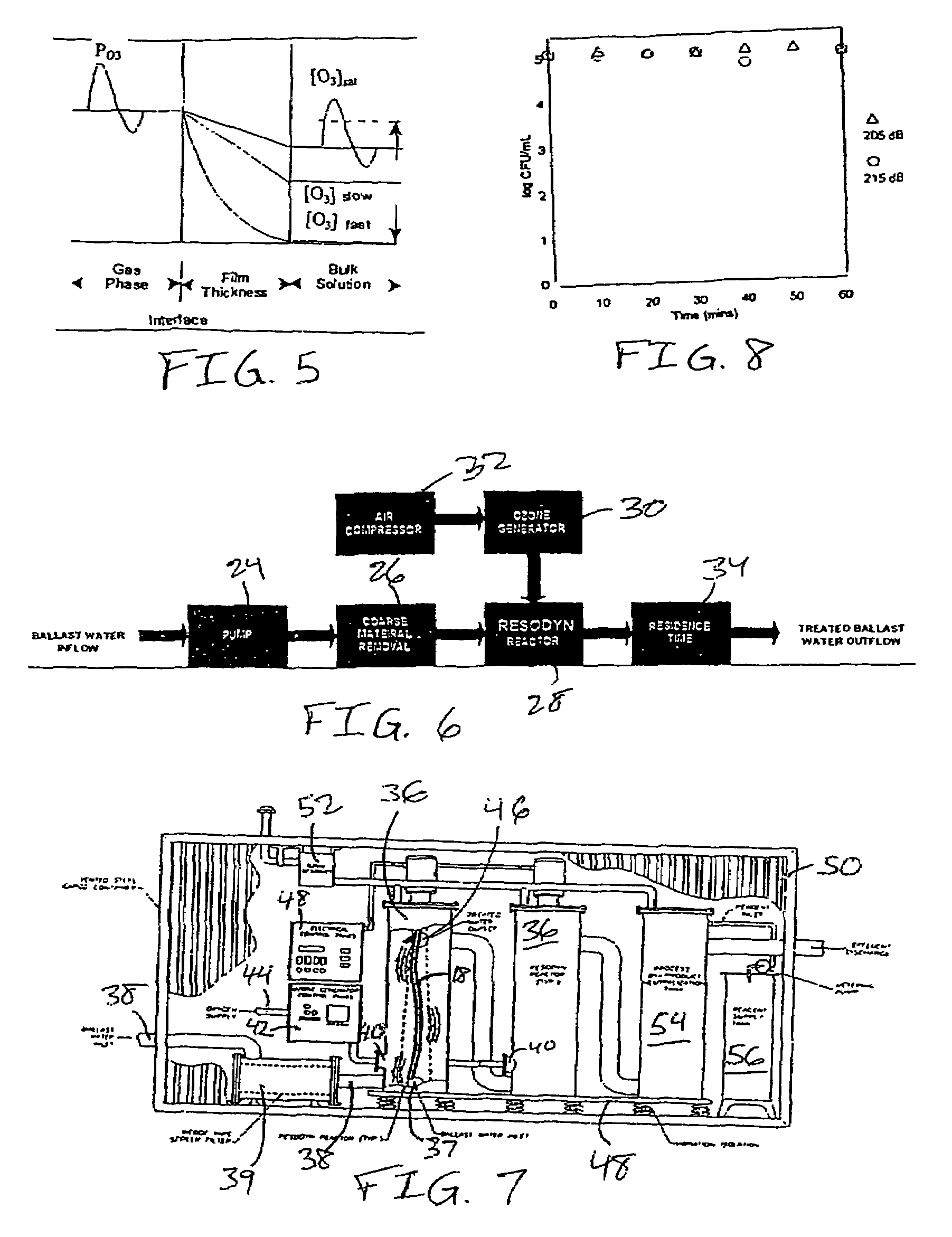
InactiveUS7595003B2Inhibit side effectsImprove efficiencyShaking/oscillating/vibrating mixersTreatment involving filtrationAcoustic energyOn board
A contactor apparatus is provided to treat ballast water that has exited a ballast tank before being expelled from a water-borne ship. Within the contactor apparatus, means are provided for supplying a combination of acoustic energy and dissolved ozone. The acoustic energy can be provided at two or more frequencies (e.g., at 16 and 20 kHz). The acoustic energy and dissolved ozone, together, offer a more-effective and more-efficient mode of disinfecting the ballast water before release.
Owner:ENVIRONMENTAL TECH
System and method for selective encryption of input data during a retail transaction
ActiveUS20110231648A1Improve vulnerabilityAcutation objectsTransmissionPersonal identification numberComputer module
A retail environment having retail terminals with data entry point devices selectively encrypts input received by the data entry point devices and passes the encrypted data to a security module. The selective encryption is based on whether or not sensitive or confidential information, such as a personal identification number (PIN) associated with a debit card, is being input. To prevent hacking of the software of the retail terminal, content destined for display on the retail terminal is authenticated prior to display. In this manner, the retail terminal may be assured that confidential information is input only when desired, and thus may be encrypted only as needed.
Owner:GILBARCO
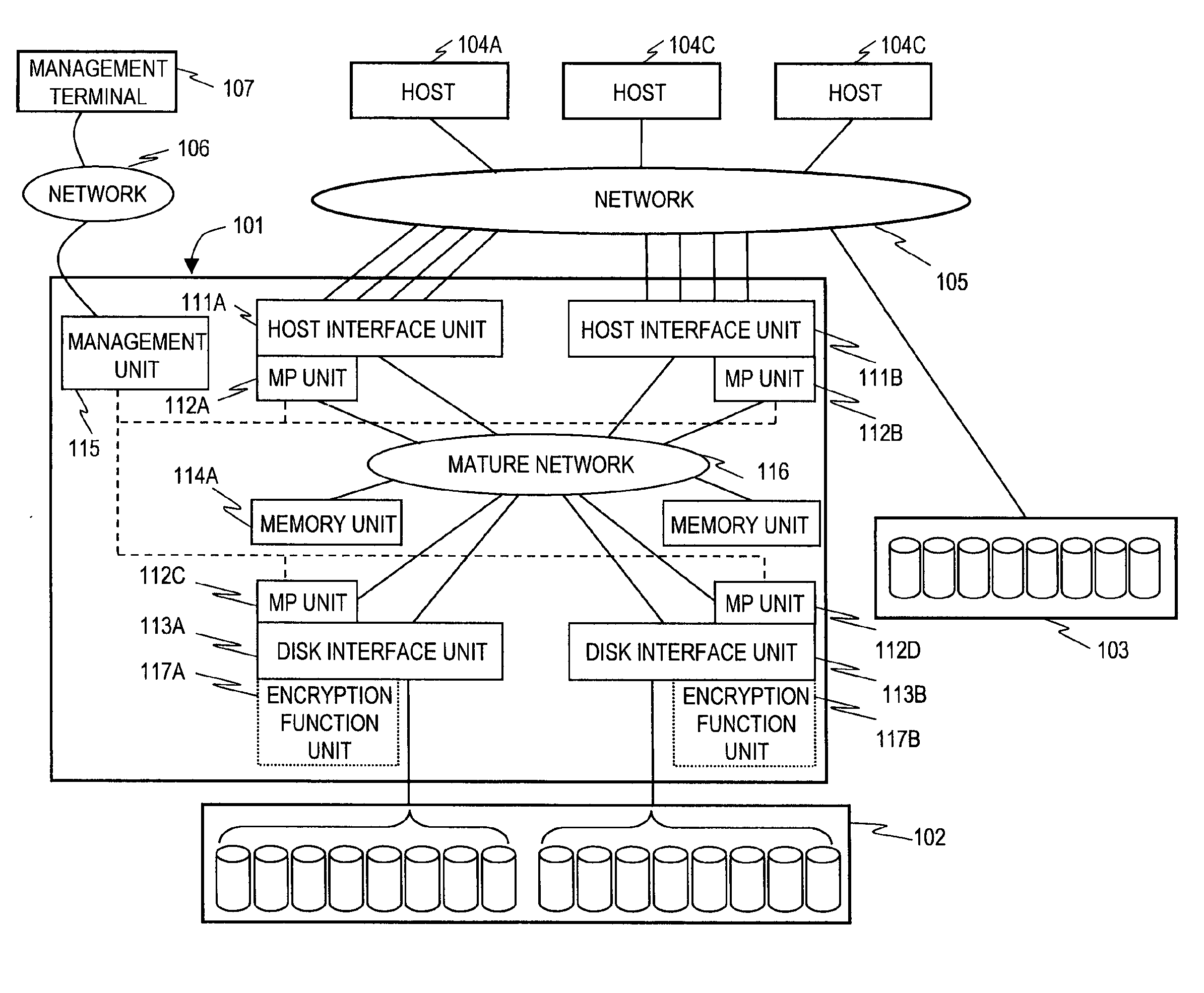
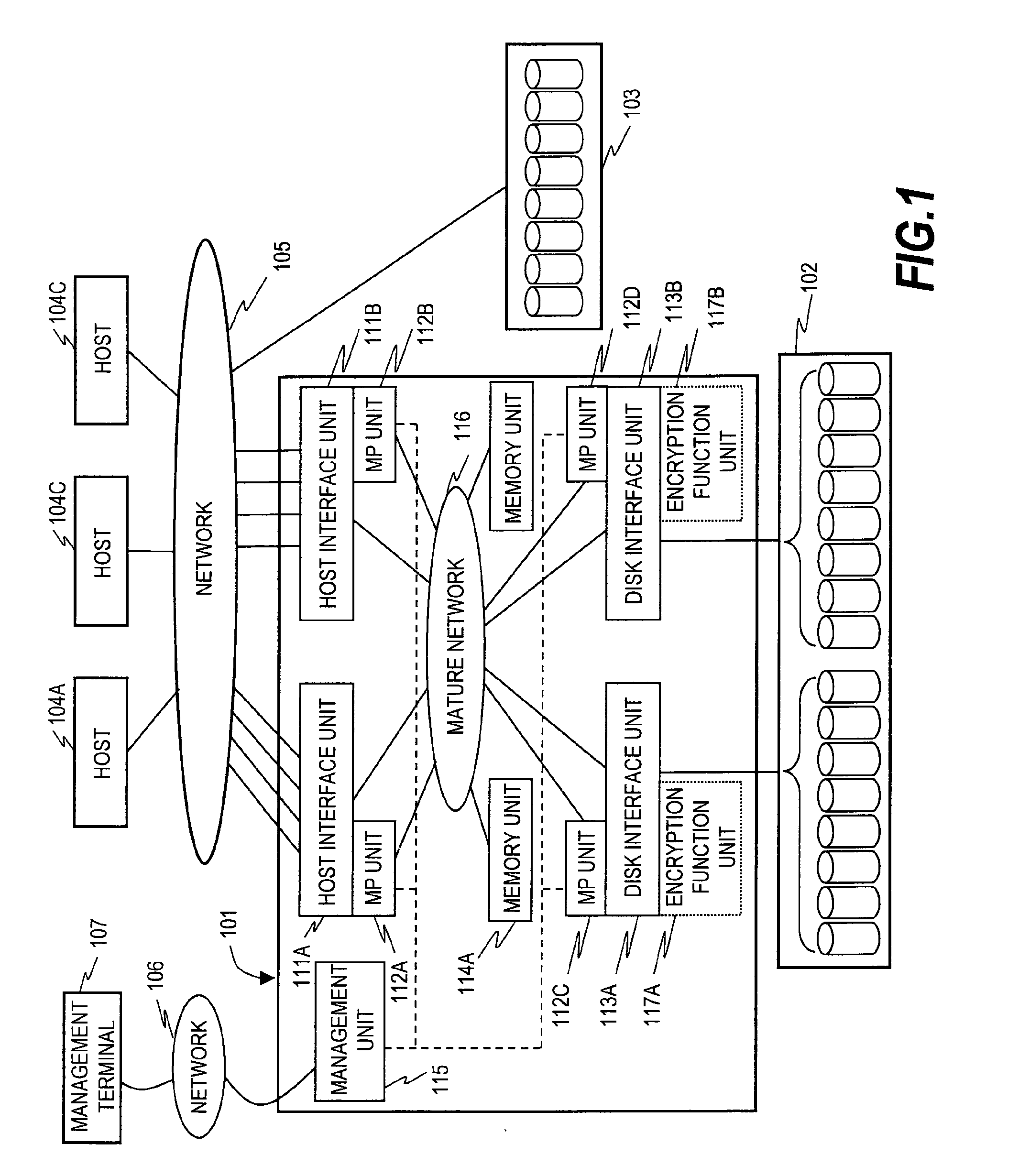
Storage system for data encryption
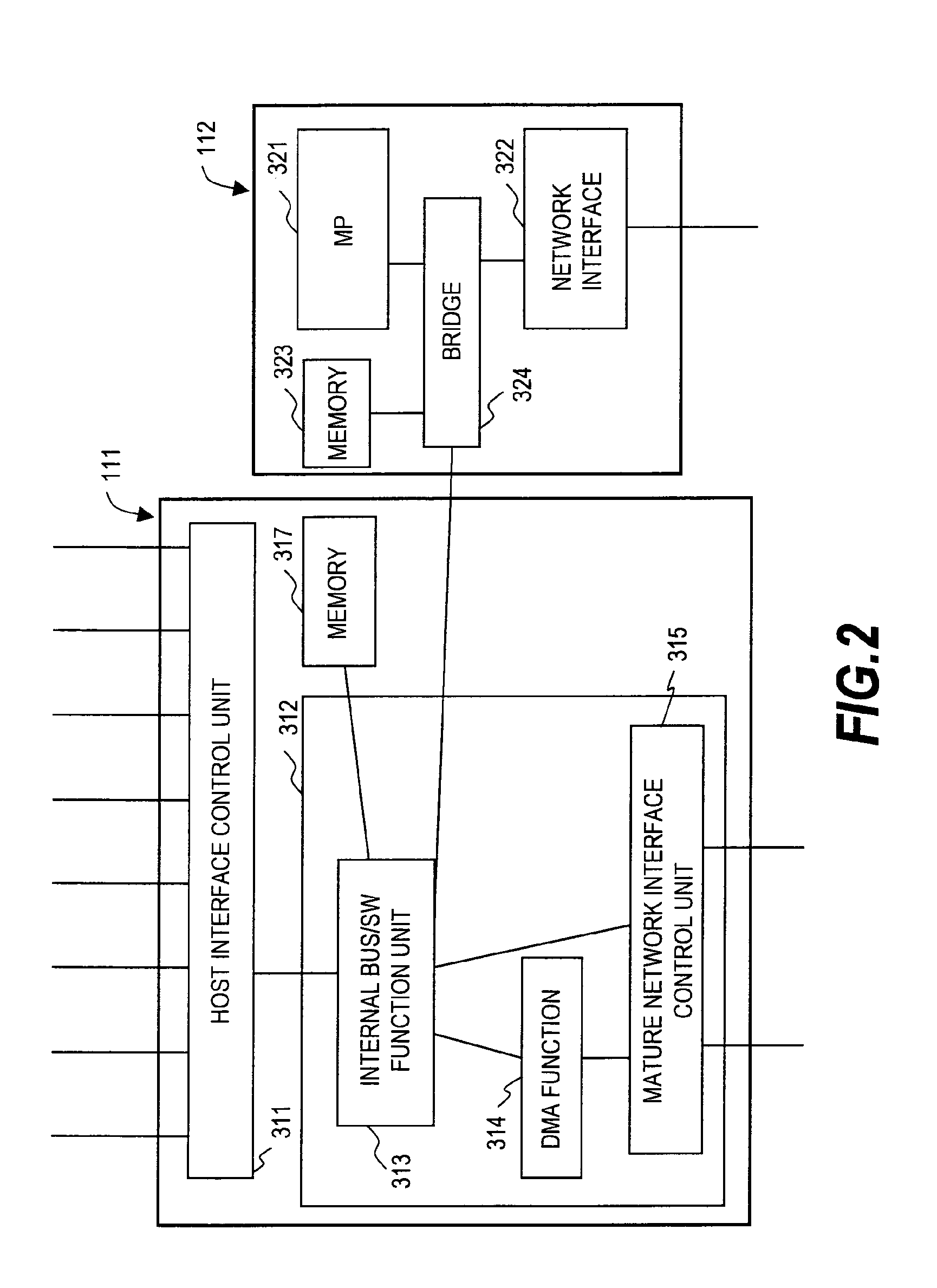
InactiveUS20100042832A1Cooperate effectivelyImprove vulnerabilityError detection/correctionComputer security arrangementsNetwork connectionEncryption decryption
A storage system including a host interface connected via a network to a host computer; a disk interface connected to a disk drive; a memory module that stores control information of a cache memory for an access to the disk drive and the storage system; a processor that controls the storage system; a network that interconnects the host interface, the disk interface, the memory module, and the processor; and an encryption module that encrypts data read / written by the host computer, in which the processor reads data from an area of the disk drive from the memory module, decrypts the read data with a corresponding encryption key, encrypts the decrypted data with a different encryption key, and writes the encrypted data in a different area.
Owner:HITACHI LTD
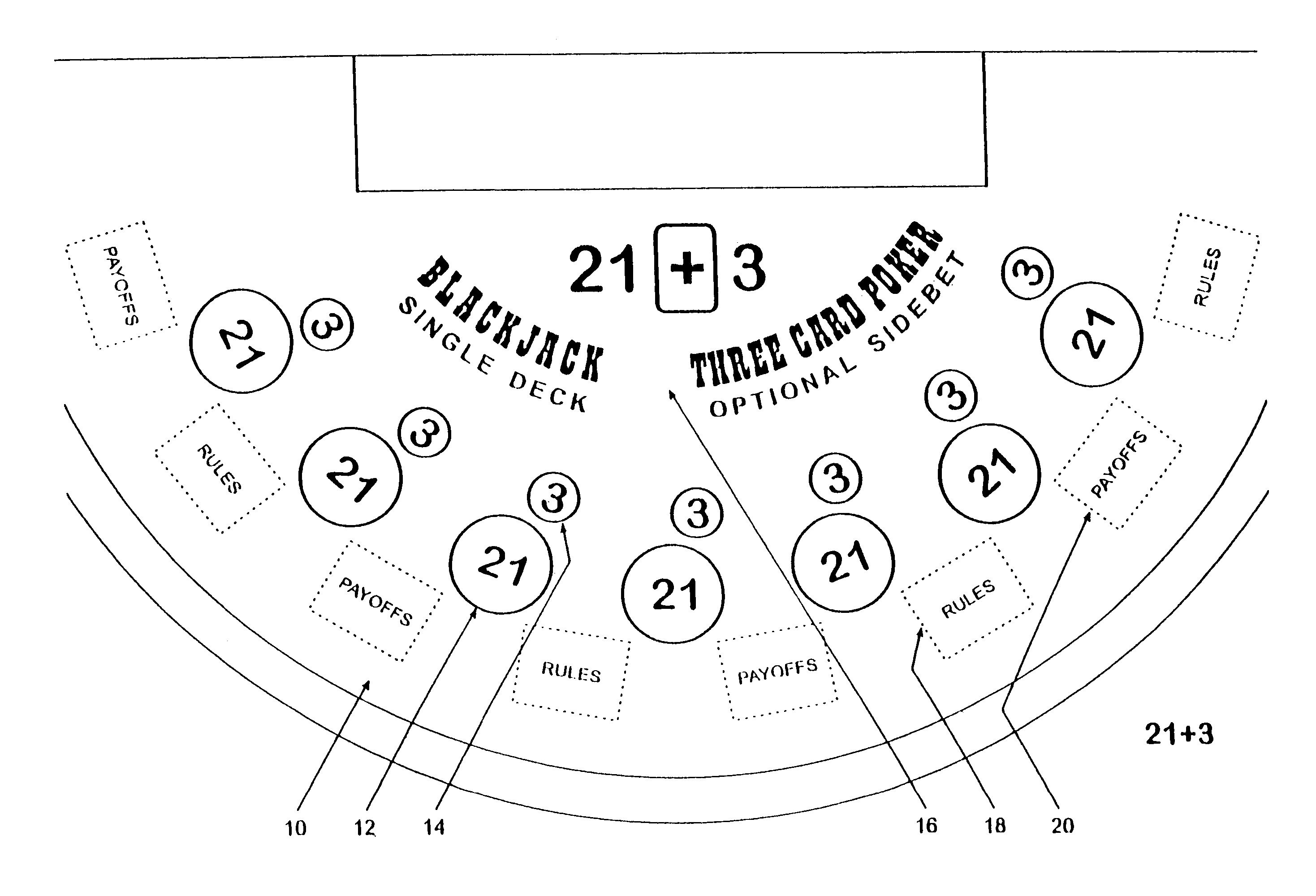
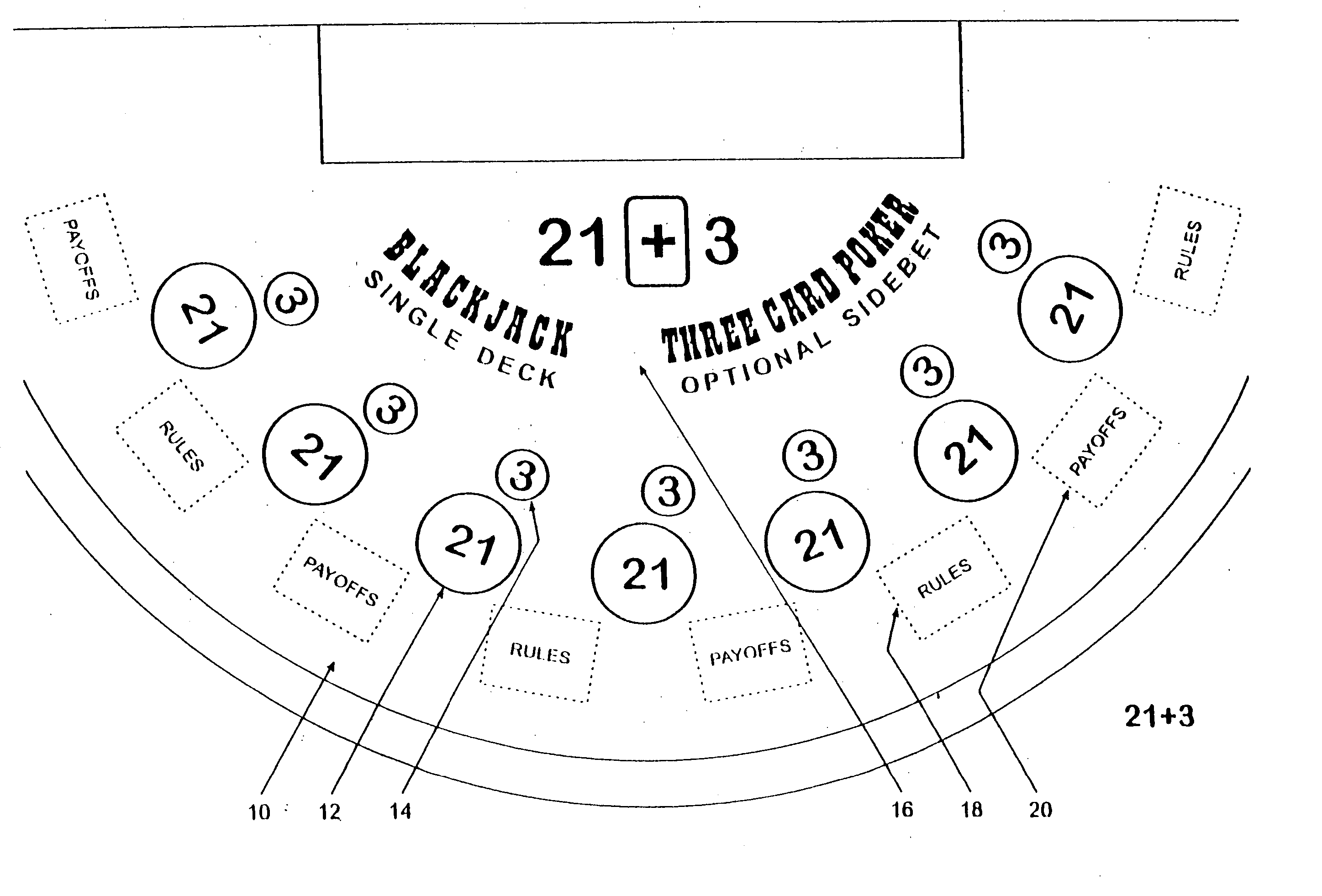
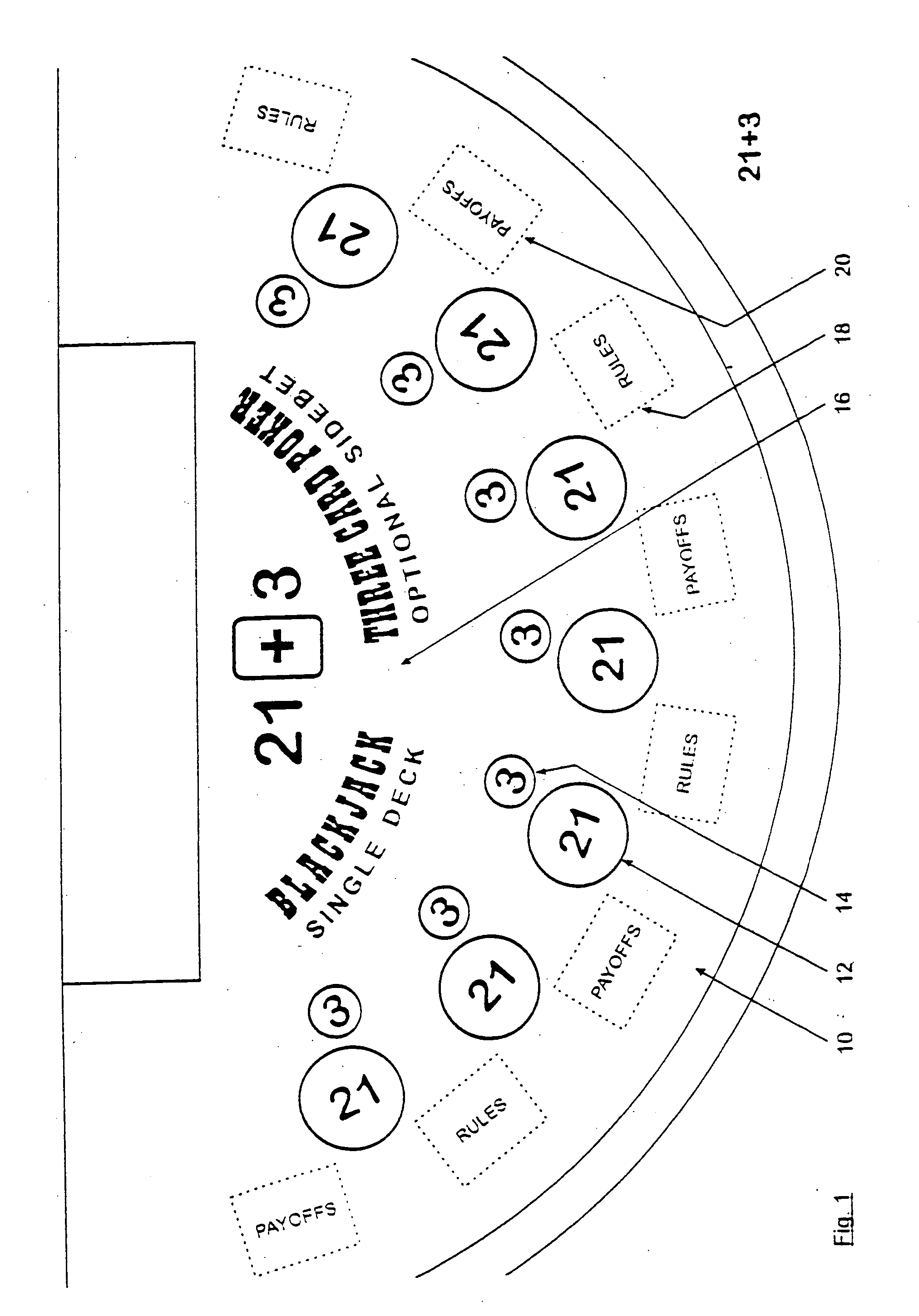
Method for playing Blackjack with a three card poker wager ("21+3")
Card games that combine the play of Blackjack (“21”) with a 3-card Poker wager or side bet (“21+3”). Each player places a basic Blackjack wager and an optional 3-card Poker wager before the cards are dealt. Each player is then dealt a card with the dealer receiving a face-up card. Each player is dealt a second card. At this point, the outcome of each 3-card Poker hand is determined, where a 3-card Poker hand consists of the 2-card hand dealt to that player and the dealer's face-up card. After settling the Poker wagers, the game of Blackjack continues in a typical fashion. The invention advantageously retains all the features and advantages of Blackjack as well as provides the dynamics of 3-card Poker, without interfering with the card sequence, for enhanced player anticipation and enjoyment.
Owner:GALAXY GAMING
Method and system for authenticating image contents
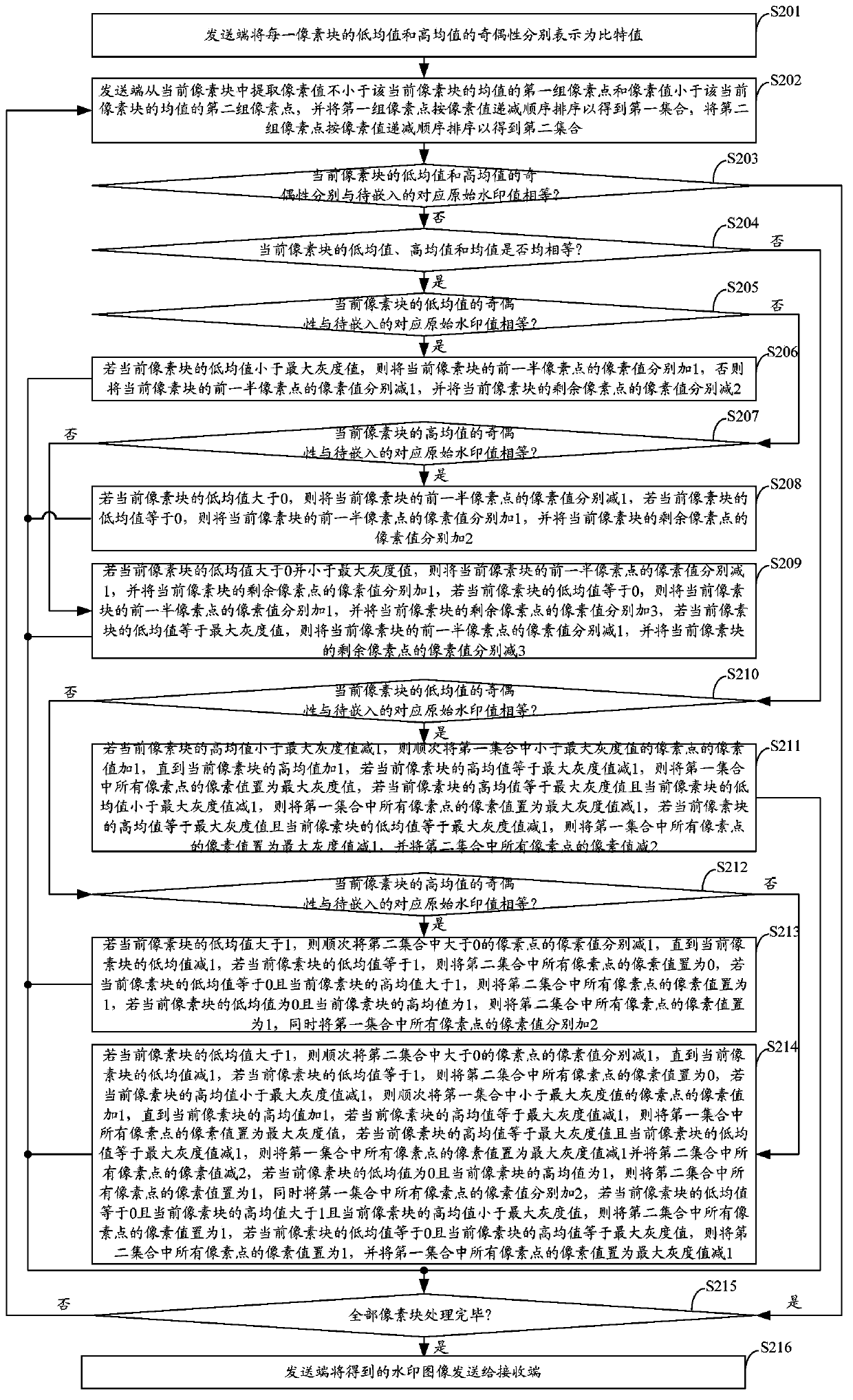
InactiveCN103426141AQuality assuranceAchieve authenticationImage data processing detailsPattern recognitionPixel based
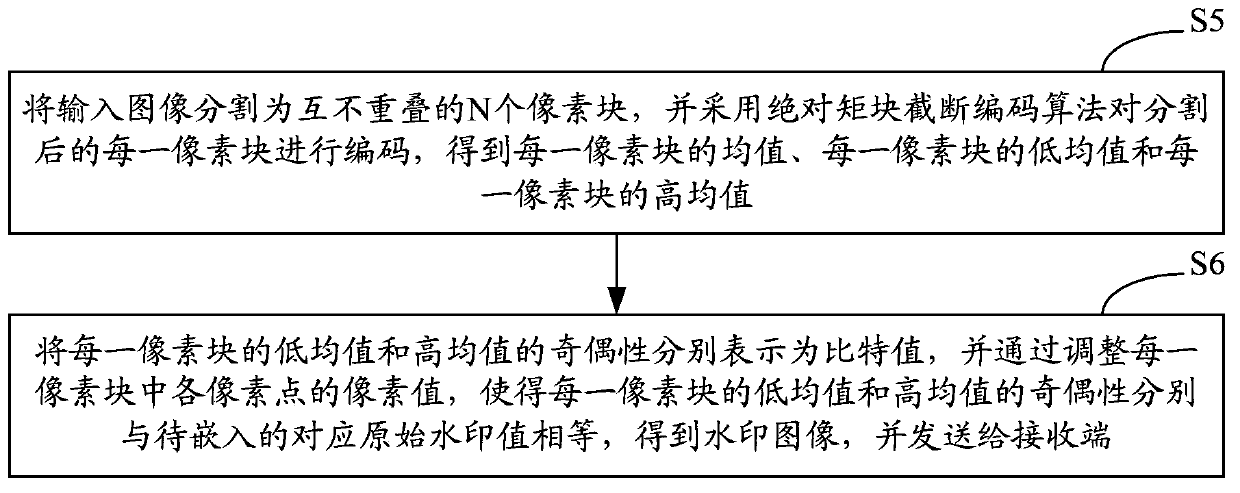
The invention belongs to the technical field of digital watermark technologies, and provides a method and a system for authenticating image contents. According to the method and system, an AMBTC (Absolute Moment Block Truncation Coding) algorithm is utilized for guiding the embedding and extraction of a digital watermark, and the parity of a low mean value and a high mean value of each pixel block is correspondingly equal to a to-be-embedded 2-byte watermark by adjusting the pixel value of each pixel in each pixel block of the input image. The image is not really subjected to BTC (Block Truncation Coding) compression, but the AMBTC quantized data are utilized for guiding the watermark embedding and extraction process, so that image authentication of a semi-fragile watermark is realized while the quality of the image is guaranteed. In addition, as an embedding mechanism based on a pixel domain and an extraction mechanism based on a compression domain are used, the method and system for authenticating the image contents can suppress brightness and contrast change operations efficiently, and have good fragility for the other operations.
Owner:华盾技术(深圳)有限责任公司
Active power distribution network energy storage planning method based on fragility theory
InactiveCN106130007AImprove business performanceReduce economic costsAc network circuit arrangementsPower gridFragility
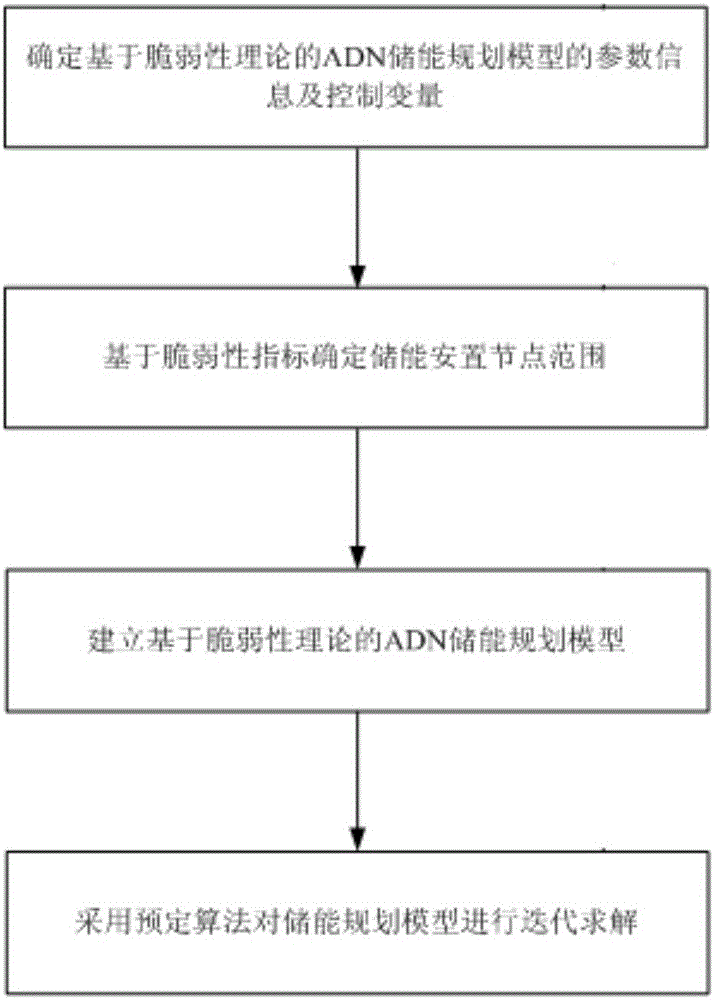
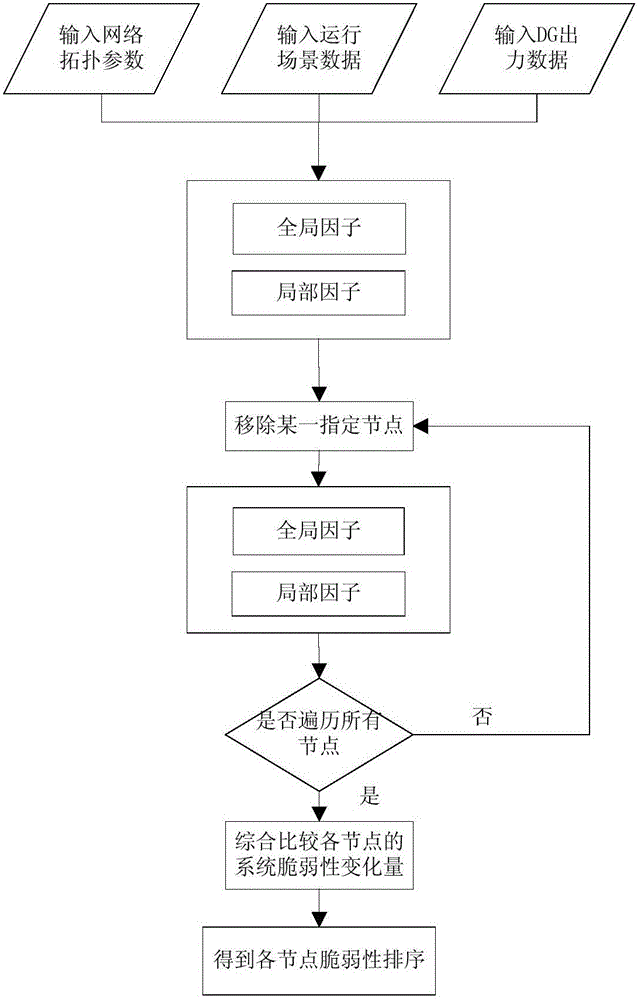
The invention belongs to a power grid energy storage planning field, and particularly relates to an active power distribution network energy storage planning method based on a fragility theory. The active power distribution network energy storage planning method is characterized by comprising the following steps: firstly determining the parameter information and control variable of an AND energy storage planning model based on the fragility theory; then taking the initial set Omega g composed of all energy storage installation nodes to be selected in a determined representation system as the control variable of an energy storage configuration node range model, using comprehensive fragility variable delta R before and after system placement energy storage as an evaluation index, researching the fragility degree of each node in an active power distribution network, and determining the range of the energy storage installation nodes to be selected in the system; establishing the AND energy storage planning model based on the fragility theory; and finally carrying out iterative solving on the energy storage planning model by using a pre-defined algorithm. According to an energy storage location planning model based on the fragility theory provided by the invention, the two aspects of economical efficiency and improvement on system fragility can be taken into account comprehensively, and the obtained planning scheme has relatively high application value.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
Stretch blow receptacle and molding method of the same
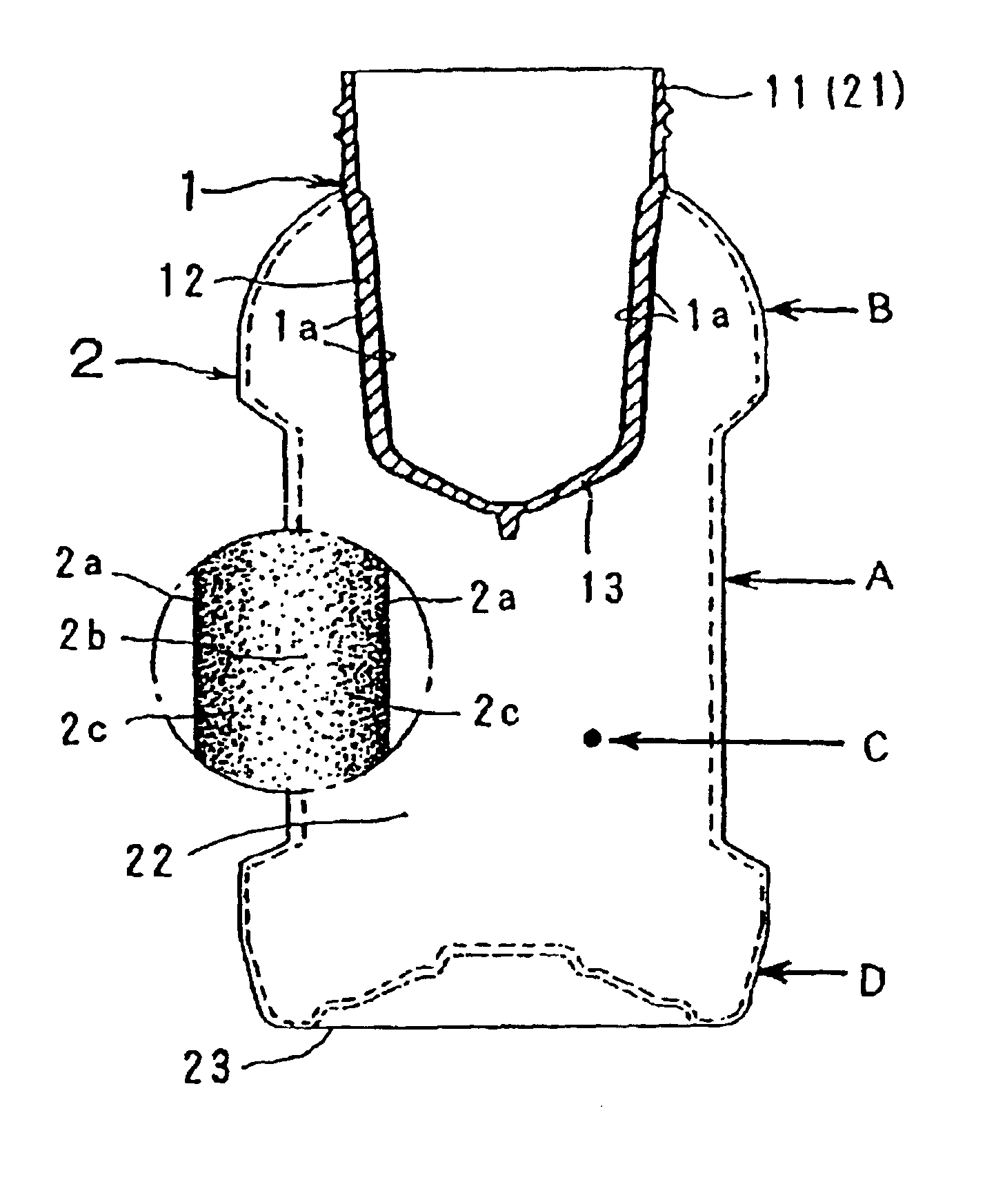
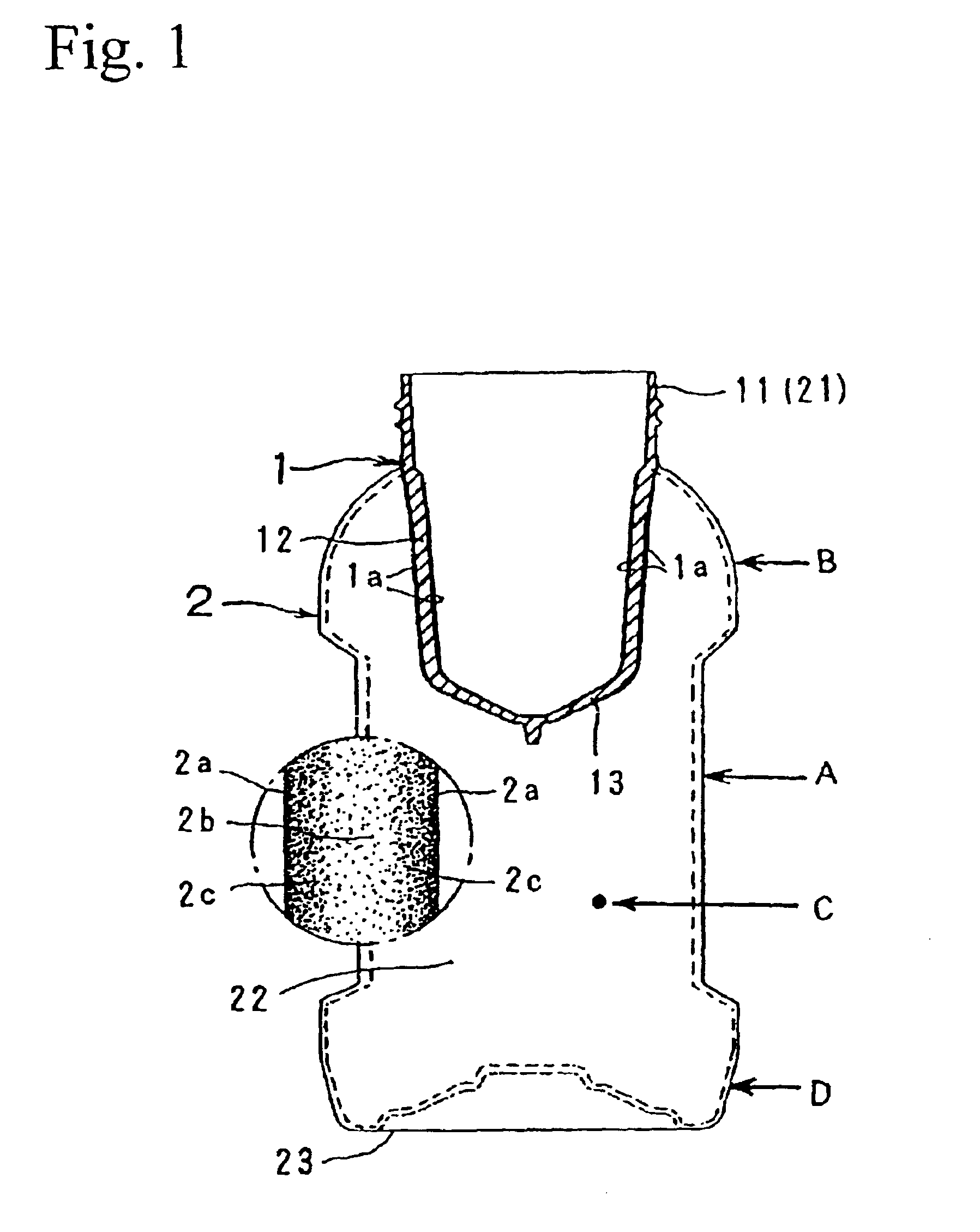
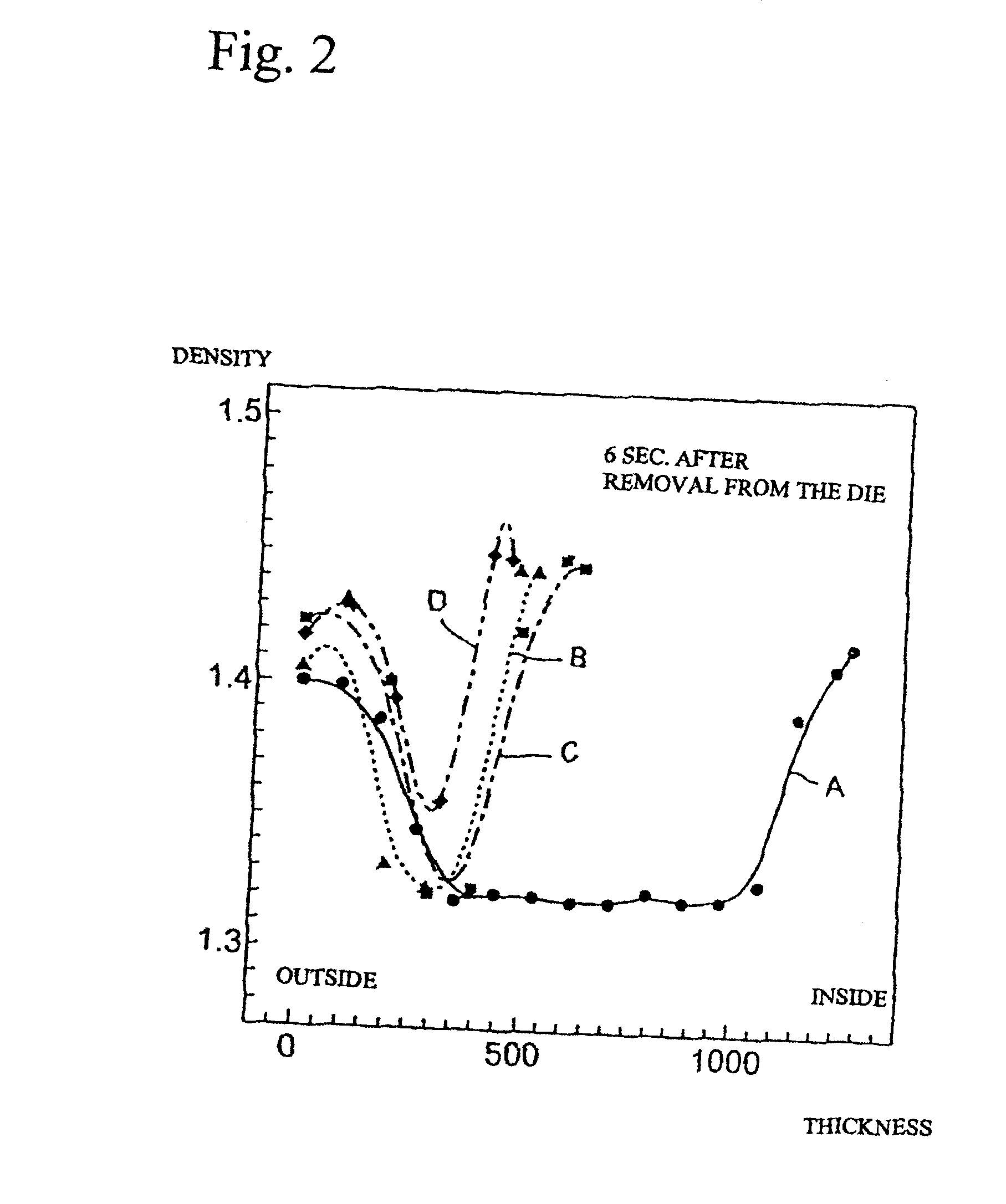
InactiveUS6890621B2FragilityImprove drop strengthBottlesSynthetic resin layered productsHigh densitySurface layer
Improve the strength of the stretch blow receptacle and make the heat resistant treatment easier, by making the receptacle wall cross-section multi-layered in view of crystalline density, and the crystalline density of the surface layer high density. The inventions concerns a thin plastic receptacle 2 molded by stretch blowing of a bottomed preform 1 in the longitudinal and transversal directions. The wall cross-section is composed of inside and outside surface layers 2a whose crystalline density is high by stretching, a core layer 2b presenting a lower density than the surface layers 2a, and an intermediate layer 2c presenting a graduated density between both layers 2a, 2b.
Owner:A K TECH LAB INC
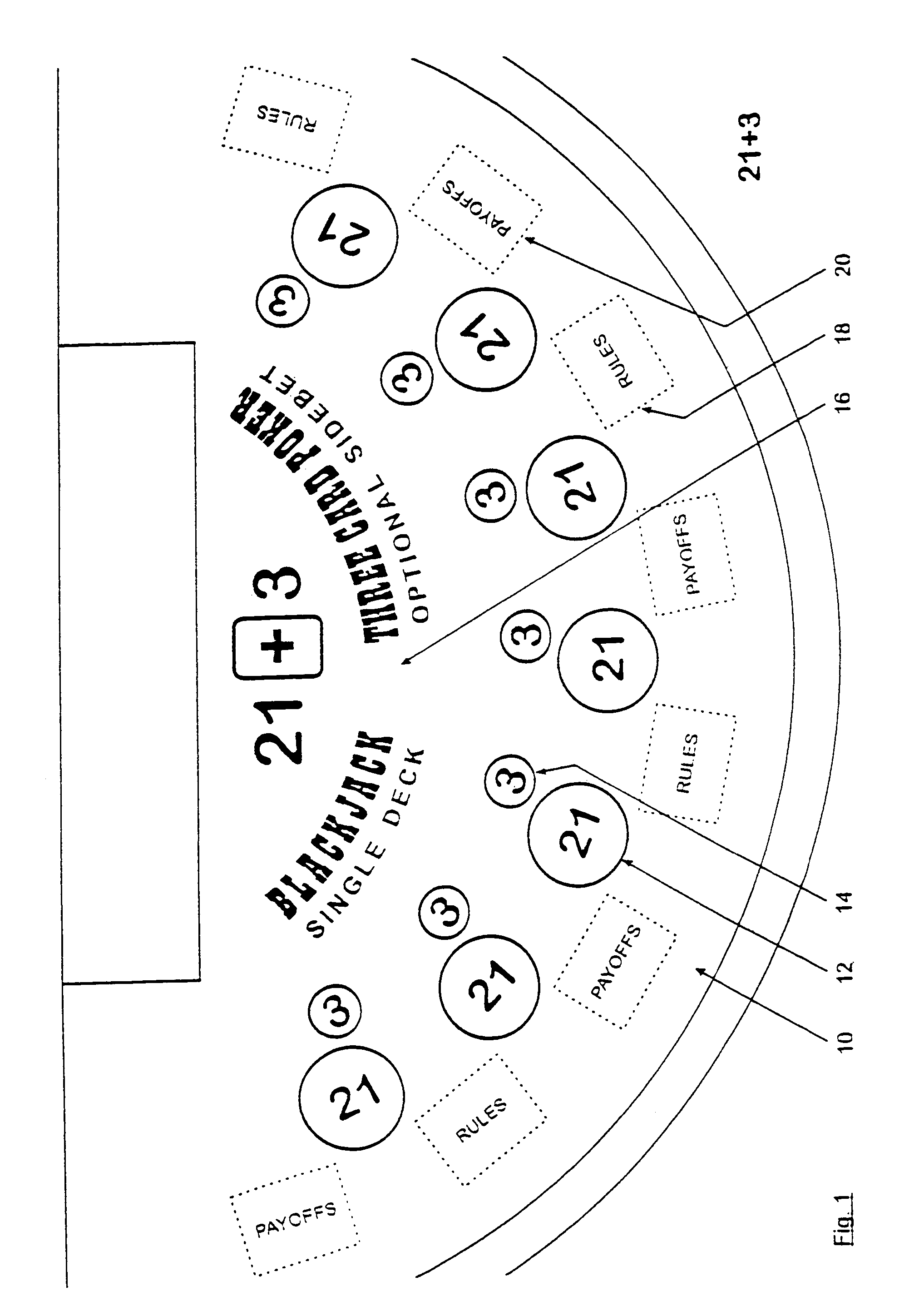
Method for playing Blackjack with a three card poker wager ("21+3")
InactiveUS20050121854A1Improve expectationsIncrease revenue generationBoard gamesCard gamesMultimedia
Owner:GALAXY GAMING
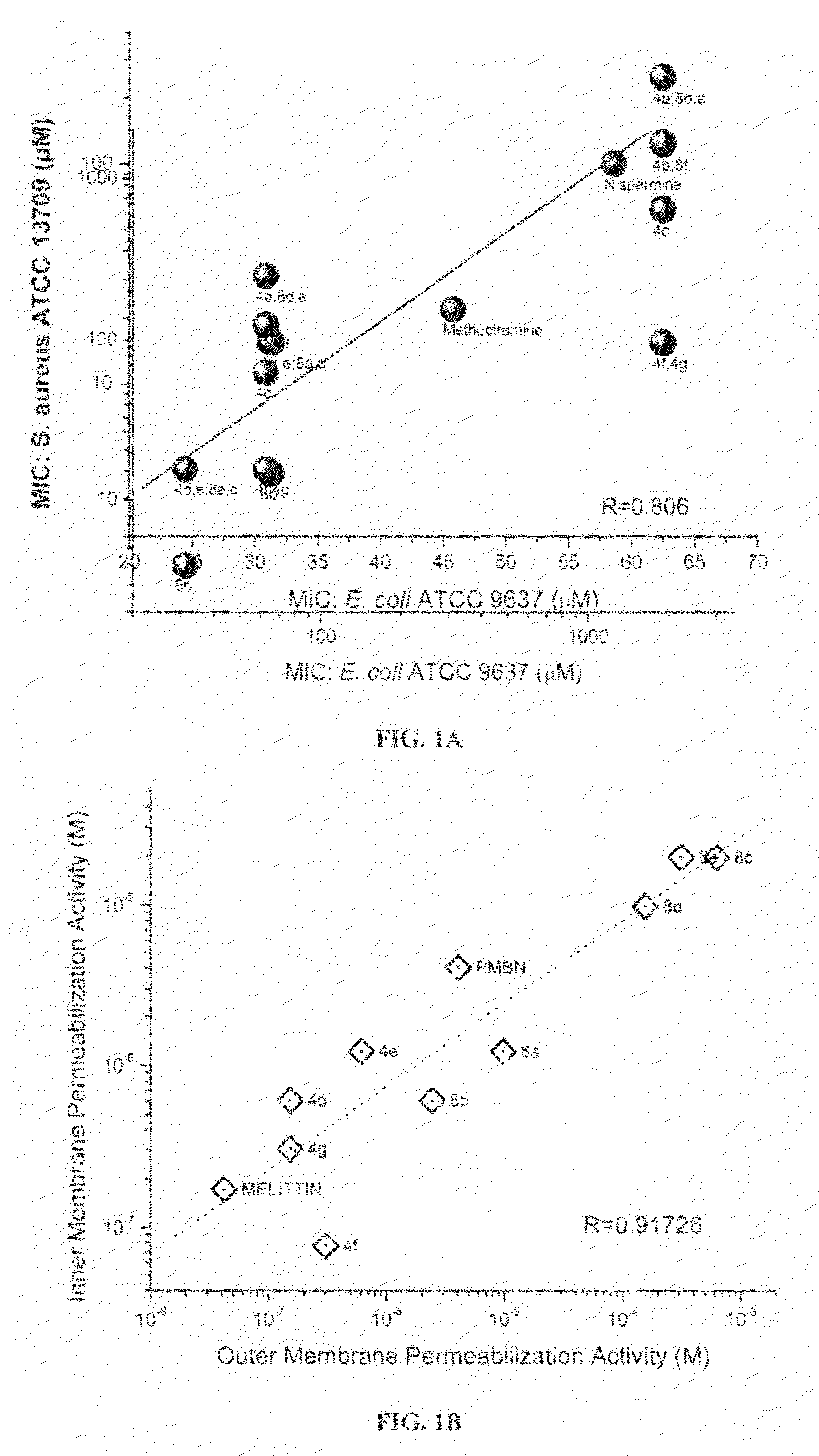
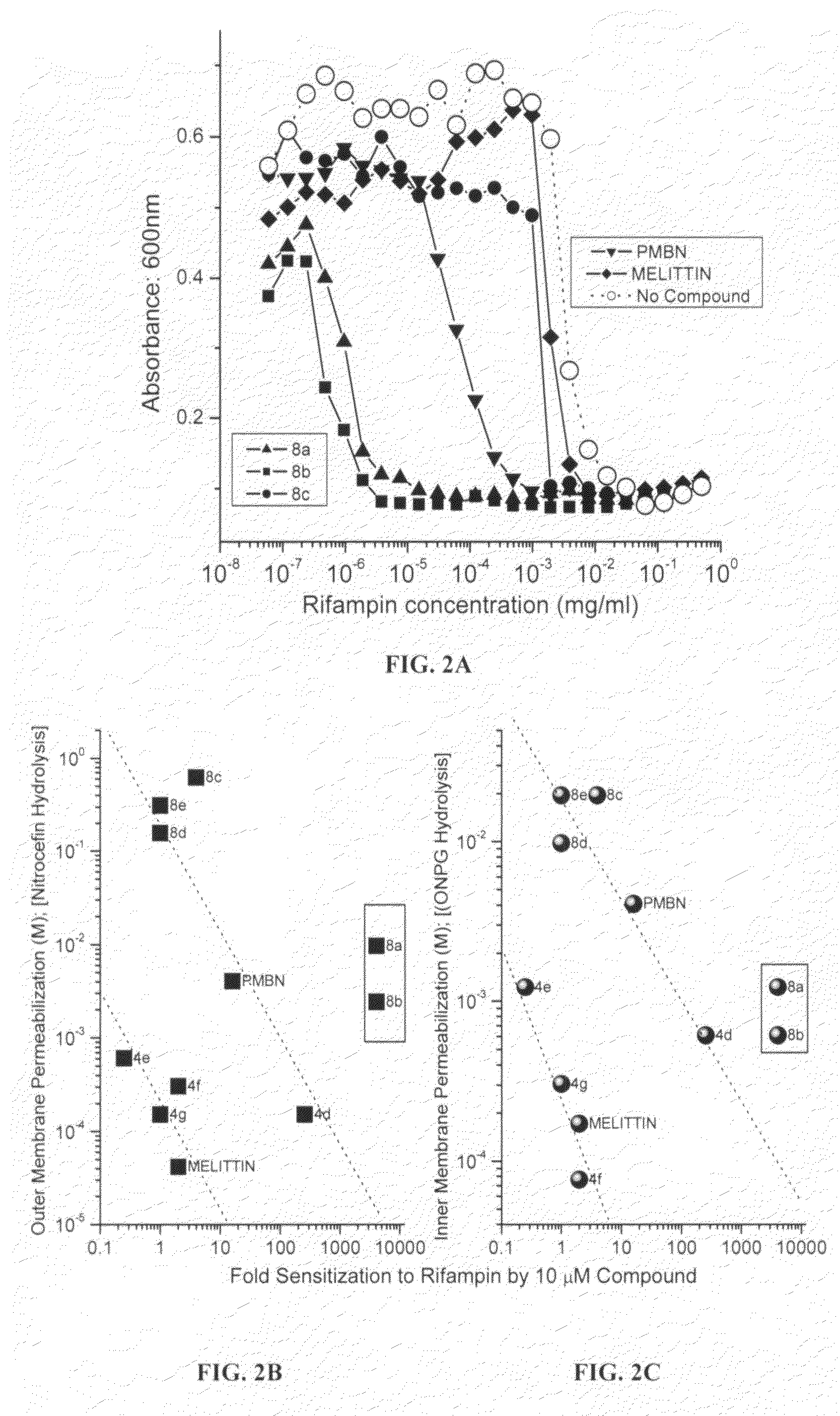
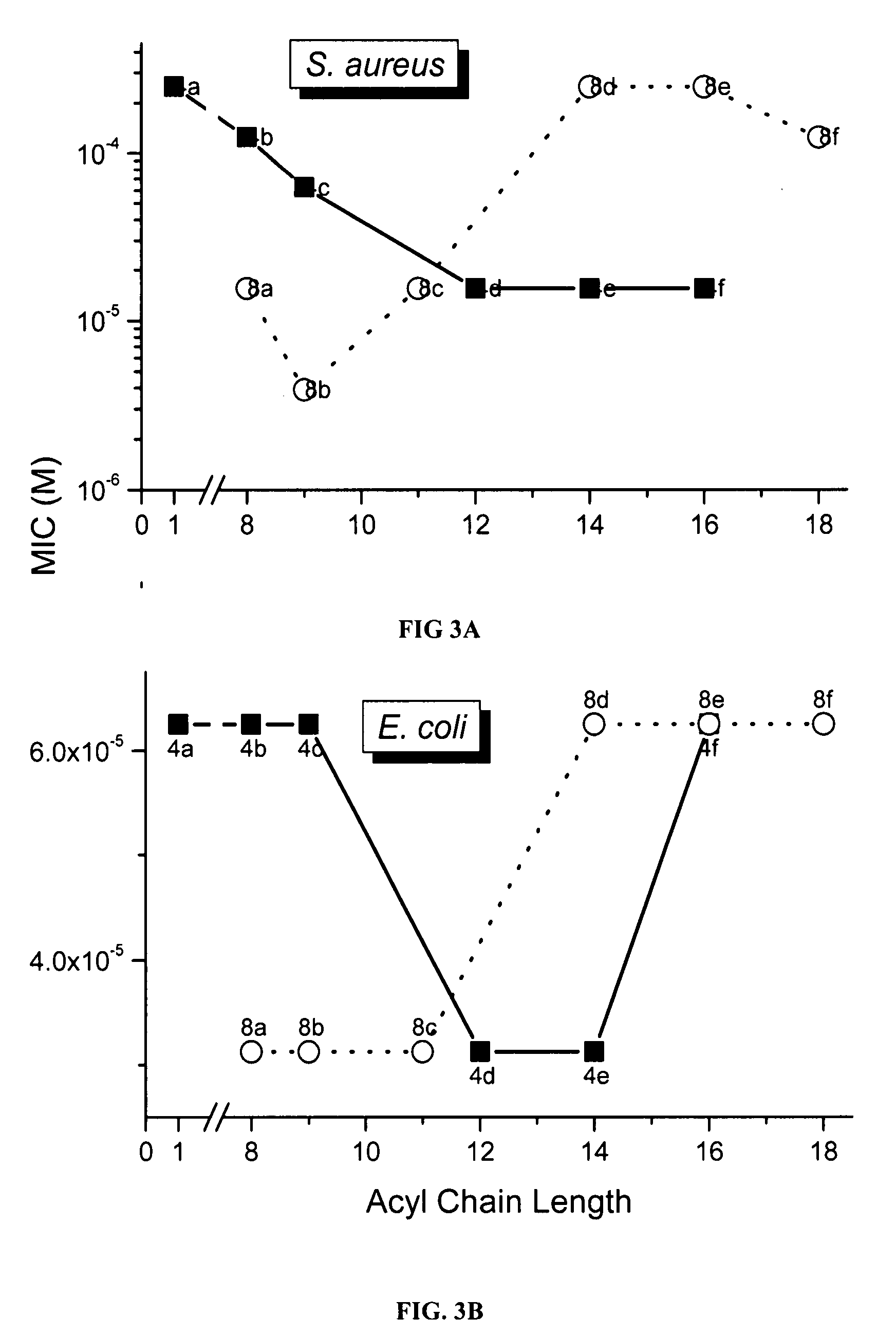
Polyamines and their use as antibacterial and sensitizing agents
InactiveUS20070197658A1High activityHigh propensityBiocideOrganic chemistryEscherichia coliChain length
Polyamines with varying chain-lengths were evaluated for antimicrobial activity in order to test the hypothesis that these bis-cationic amphipathic compounds may also bind to and permeabilize intact Gram negative bacterial membranes. The compounds were found to possess significant antimicrobial activity and mediated via permeabilization of bacterial membranes. Homologated spermine, bis-acylated with C8 or C9 chains was found to profoundly sensitize E. coli to hydrophobic antibiotics such as rifampicin.
Owner:KANSAS UNIV OF
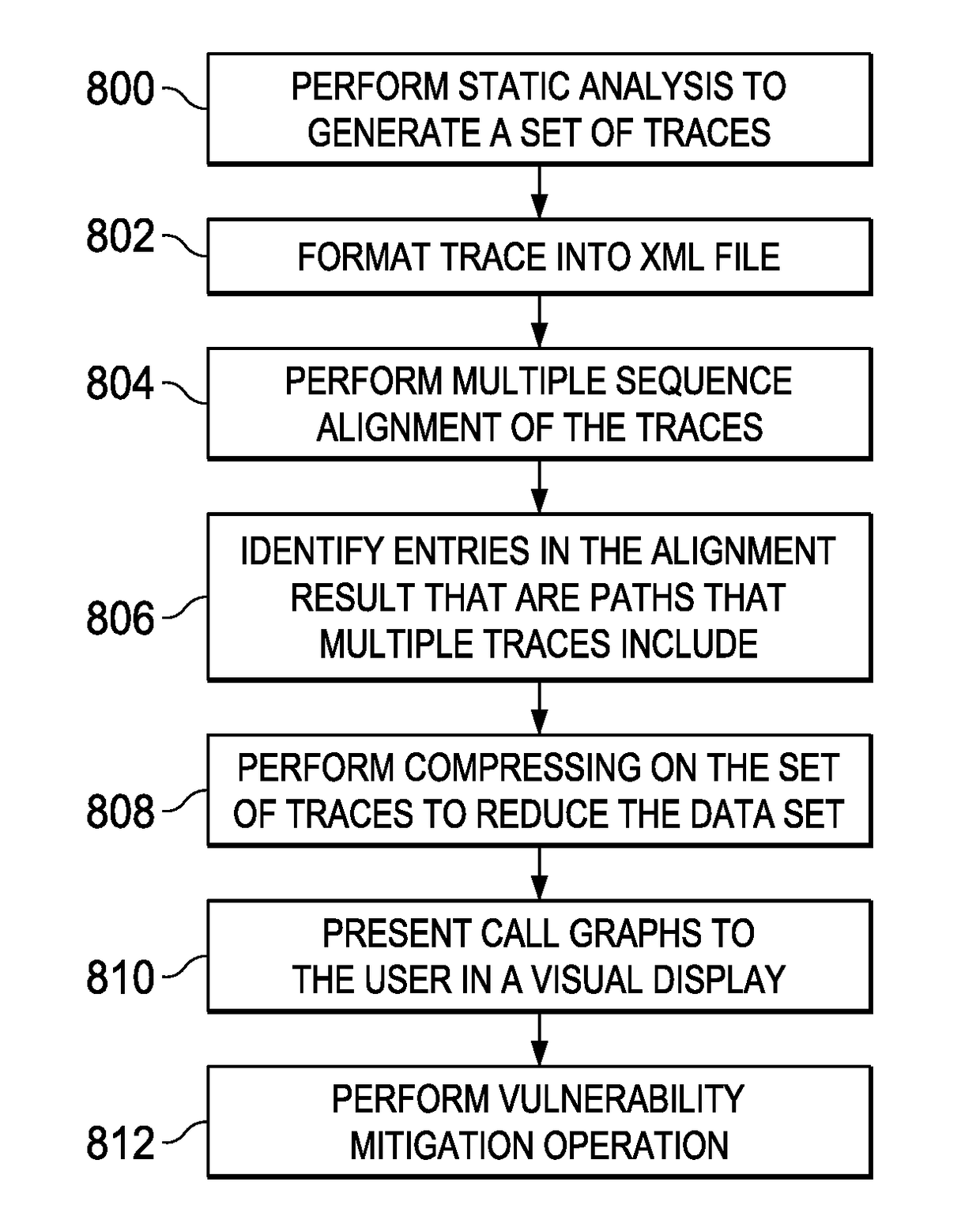
Using multiple sequence alignment to identify security vulnerability code paths
ActiveUS20170337123A1Enhanced security vulnerability determinationSimple processReverse engineeringSoftware testing/debuggingCode trackingMultiple sequence alignment
A static analysis tool is augmented to provide for enhanced security vulnerability determination from generated code traces. According to this disclosure, a multiple sequence alignment is applied to a set of traces generated by static analysis of application source code. The output of this operation is an alignment result that simplifies the traces, e.g., by representing many common nodes as a single node. In particular, the sequence alignment identifies entries in the alignment result that represent at least one code execution path that multiple traces in the set of traces include. A call graph can then be output that includes the at least one code execution path identified, and that call graph can also be simplified by applying a compression portions of the traces that are used to generate it. Using multiple sequence alignment and simplified call graphs enable a user to identify security vulnerabilities more efficiently.
Owner:IBM CORP
Coating composition for ink-jet recording medium and ink-jet recording medium
InactiveUS20040077781A1Adversely affecting ink permeabilityMaintain transparencyDuplicating/marking methodsSpecial tyresColloidal silicaSilylene
The present invention relates to a coating composition for a recording medium useful in ink jet printing of photographic images to provide a high gloss finish. The coating composition for an ink jet recording medium comprises colloidal silica and a synthetic resin emulsion having two or more glass transition points. The synthetic resin emulsion is obtained by emulsion-polymerizing, simultaneously or separately, (A) a radical-polymerizable unsaturated monomer having a silyl group and (B) another radical-polymerizable unsaturated monomer which is copolymerizable unsaturated monomer which is copolymerizable with (A), in the presence of a radical polymerizable surfactant.
Owner:CELANESE INT CORP
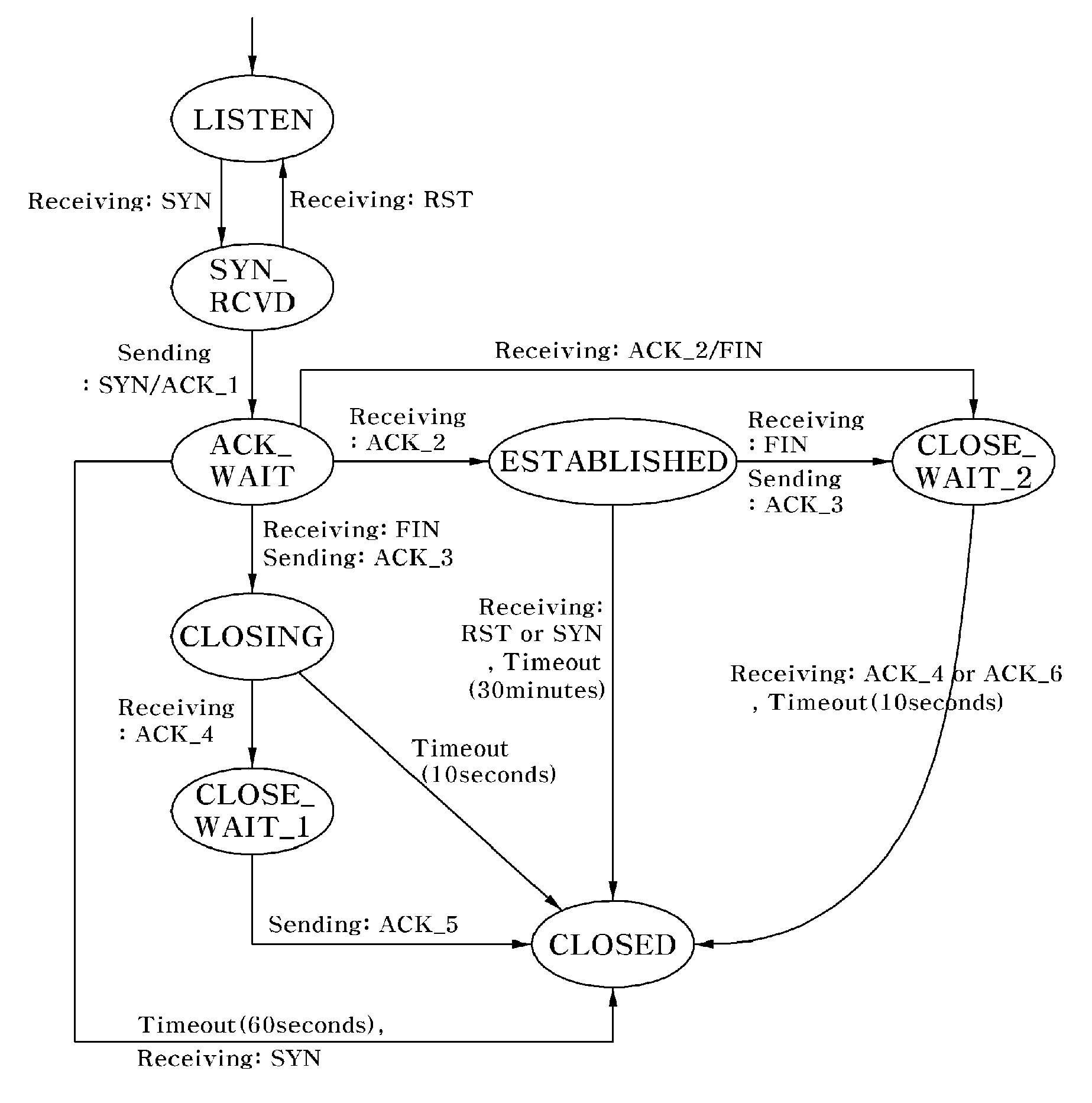
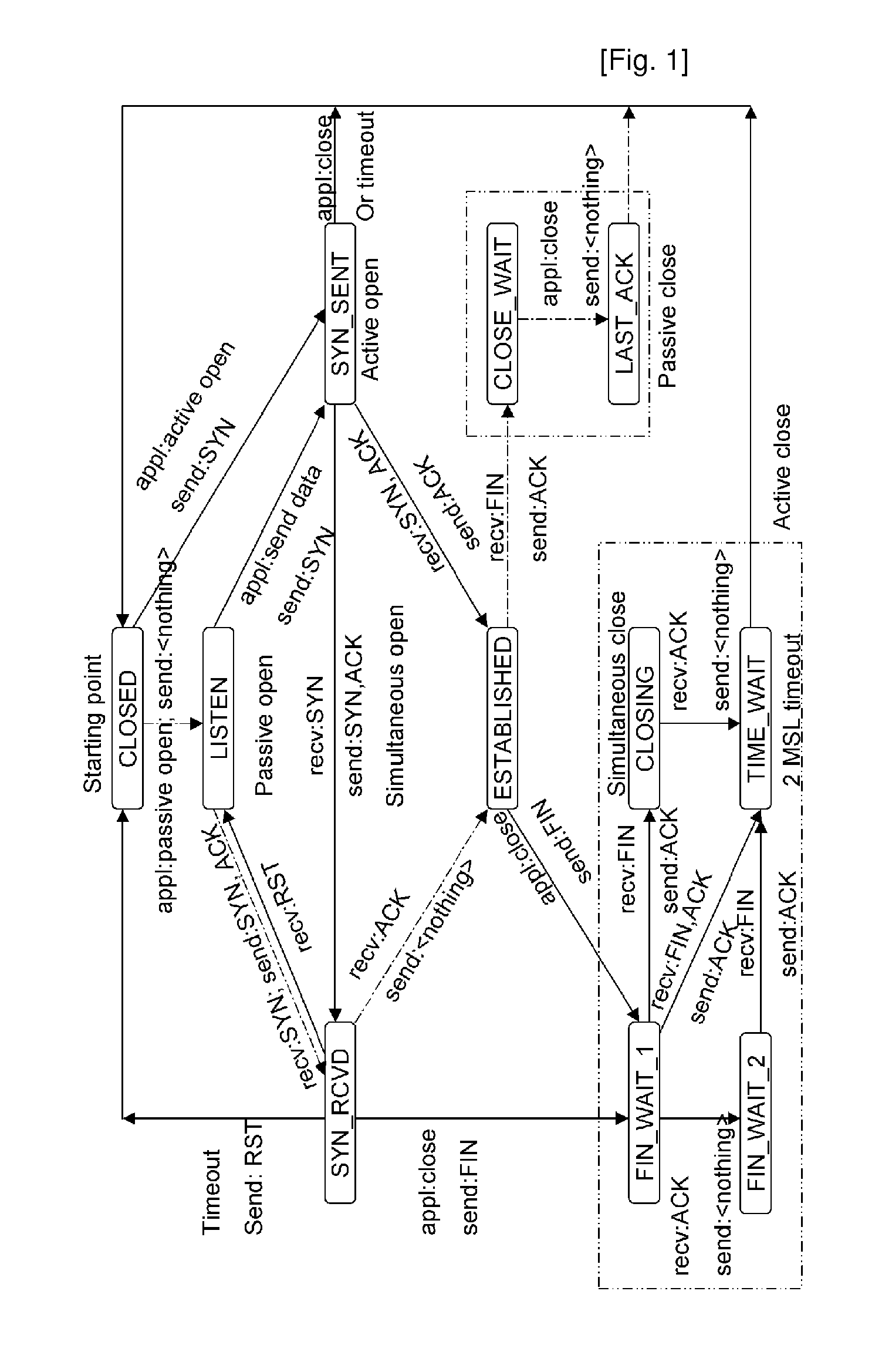
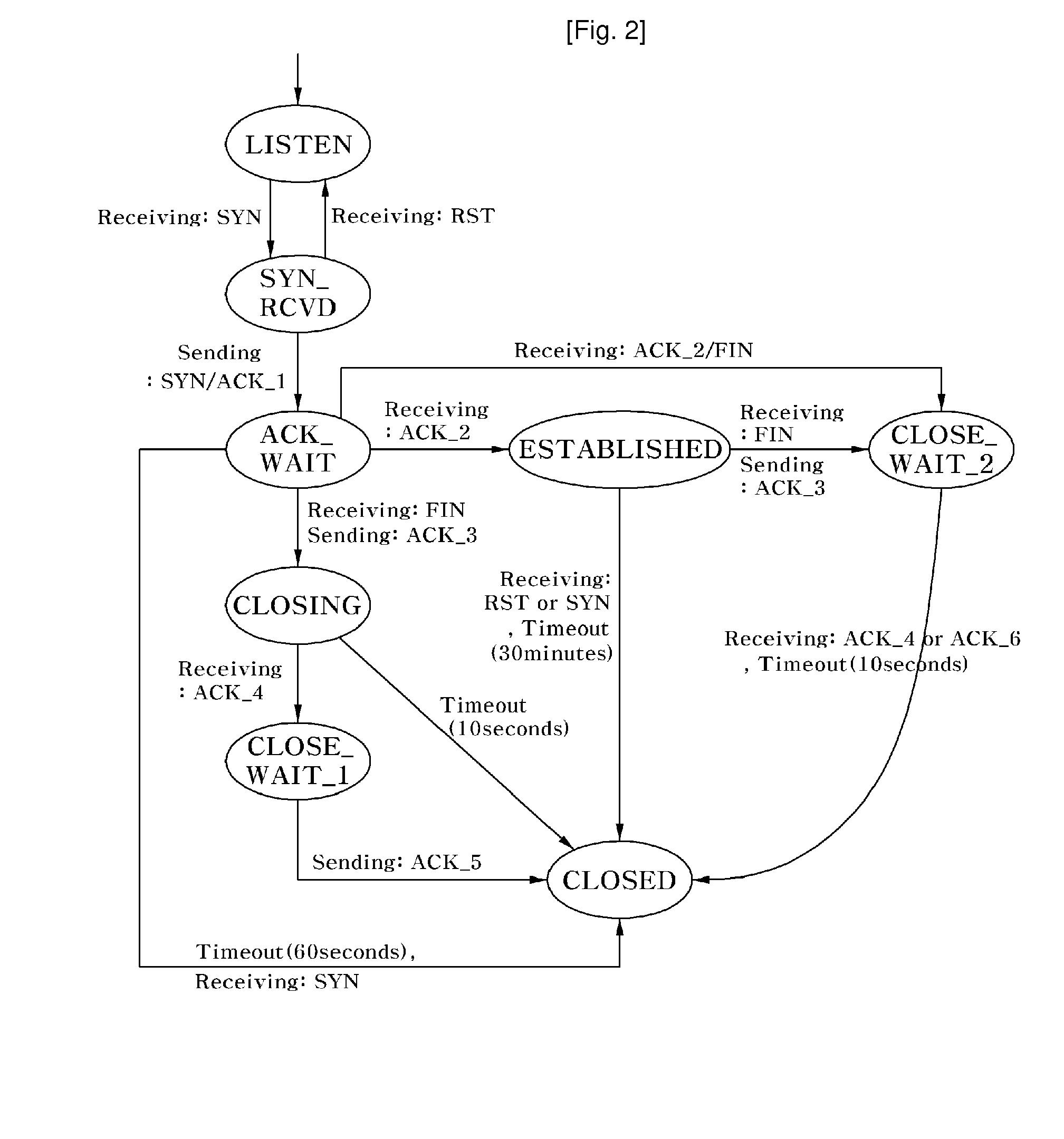
Method for Preventing Denial of Service Attacks Using Transmission Control Protocol State Transition
InactiveUS20100088763A1Reduce loadSecurity serviceMemory loss protectionData taking preventionState switchingClient-side
Disclosed is a method of preventing a denial of service (DoS) attack using transmission control protocol (TCP) state transition. Flow of packets transmitted between a client and a server using TCP is monitored to prevent the DoS attack, e.g., SYN flooding, and to efficiently reduce the load on the server and provide mor secure service. By applying the method to a firewall, a proxy server, an intrusion detection system, etc., of a server, it is possible to make up for vulnerabilities regarding a DoS attack without disturbing a conventional TCP state transition operation and detect, verify and block DoS attacks abusing the vulnerabilities, thereby providing more secure service.
Owner:SAMSUNG SDS CO LTD
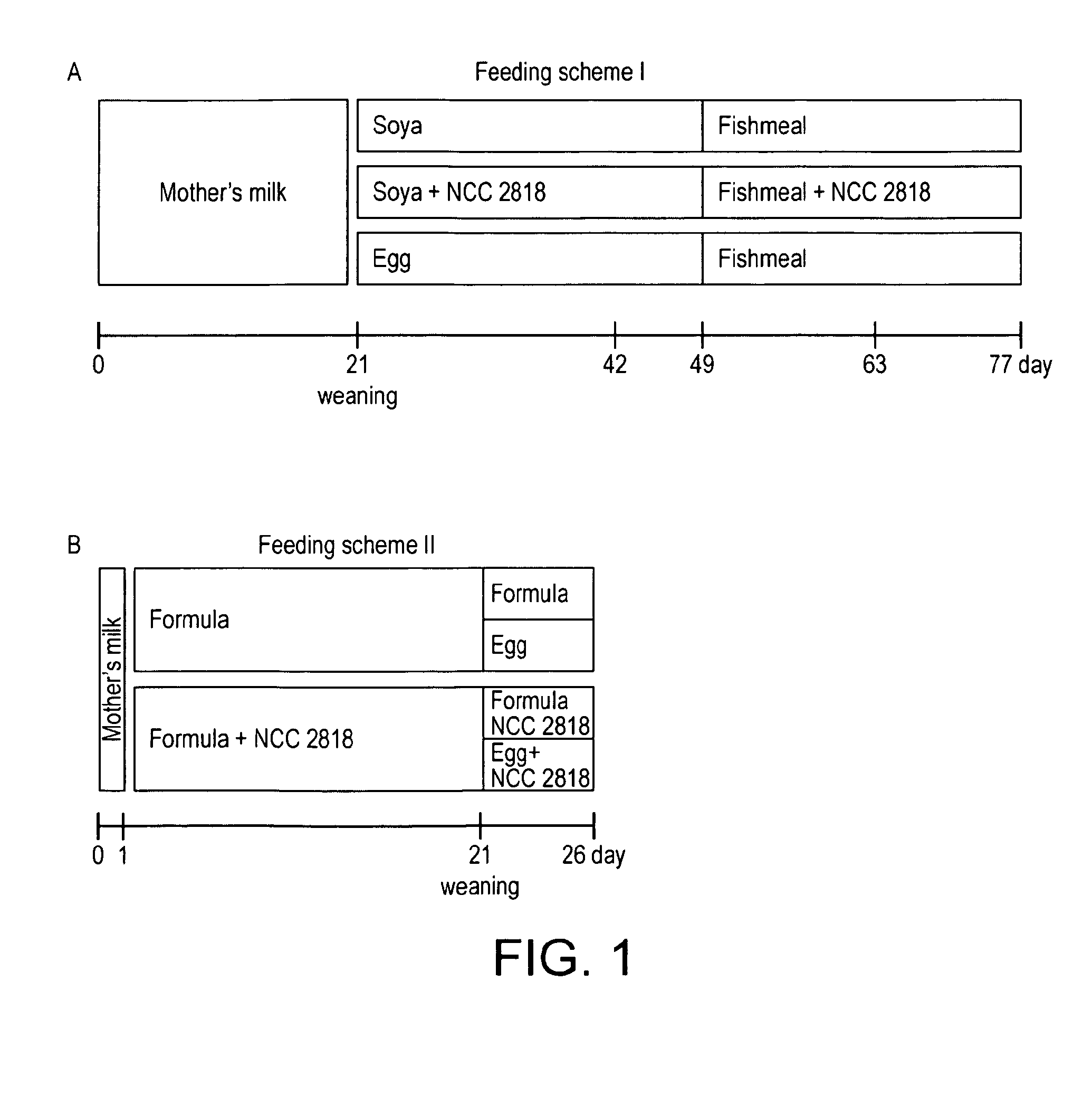
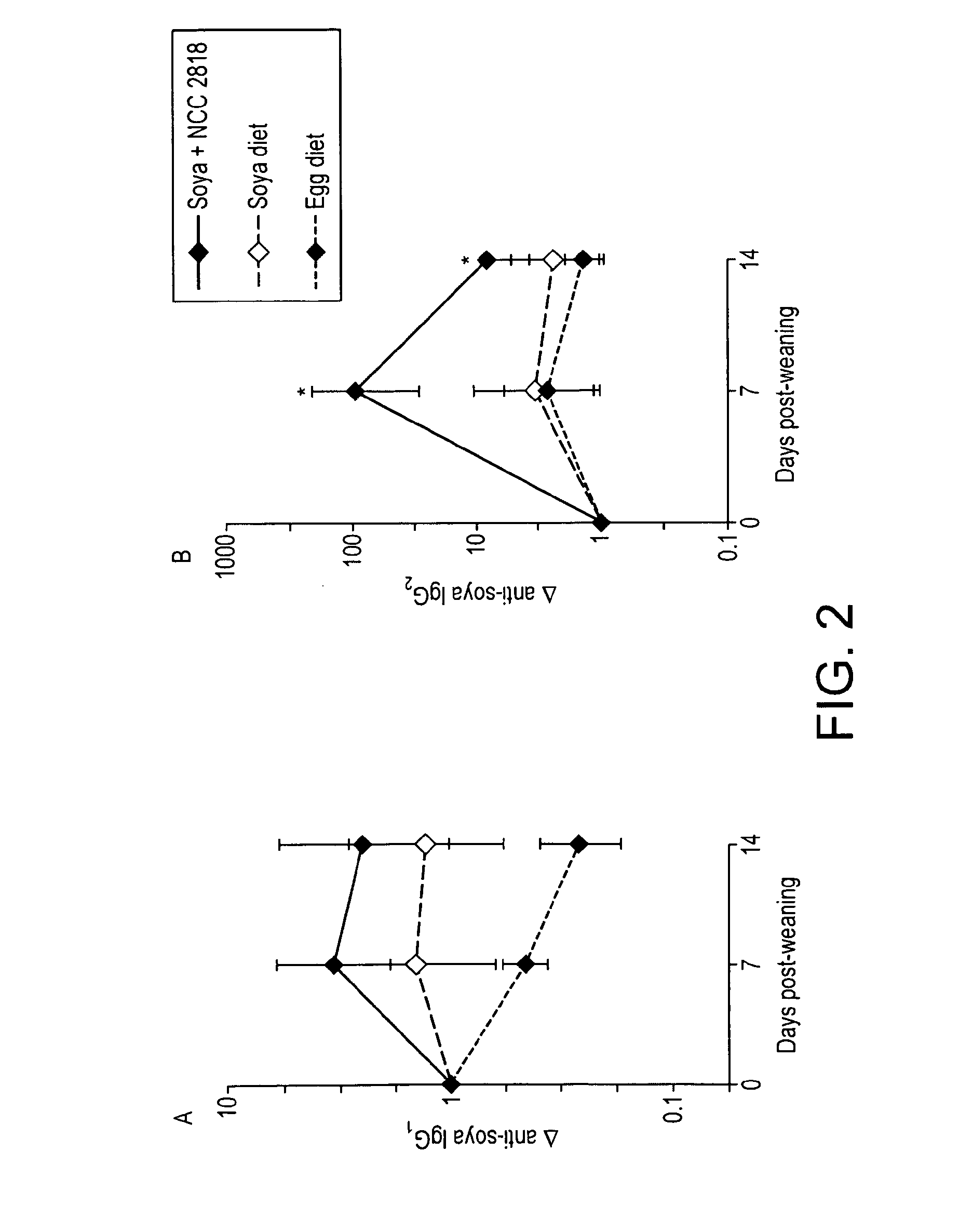
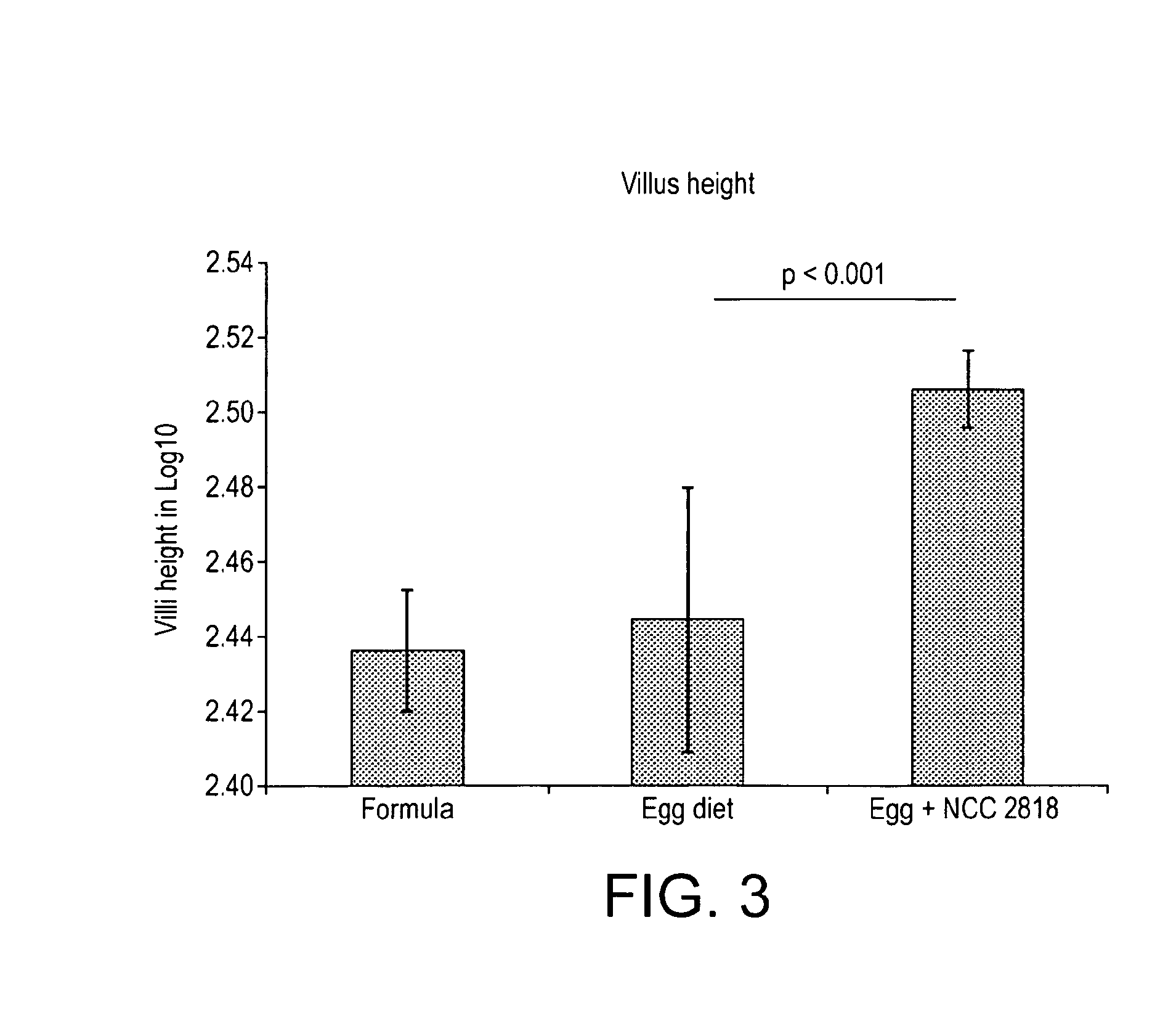
Probiotic for administration to healthy young mammals during the weaning period for improving tolerance to newly introduced food stuffs
InactiveUS20140170126A1Enhancement of transient increase in humoral immune responsePrevent stateBiocideOrganic active ingredientsWeaningTolerability
The current invention is based upon administration of a probiotic, B. Lactis NCC2818 to healthy young mammals during the critical weaning period (in infants this period is usually from about 3 months to about 12, 18 or 24 months old), so as to accelerate the young mammal's adaptation to new food. The effectiveness of the invention is evidenced herein by morphological and immunological changes observed in a piglet animal model of weaning. Thus, administration of the probiotic according to the invention had a prophylactic effect, preventing the severe discomfort and pathological states associated with the introduction to novel foods during the weaning period.
Owner:NESTEC SA
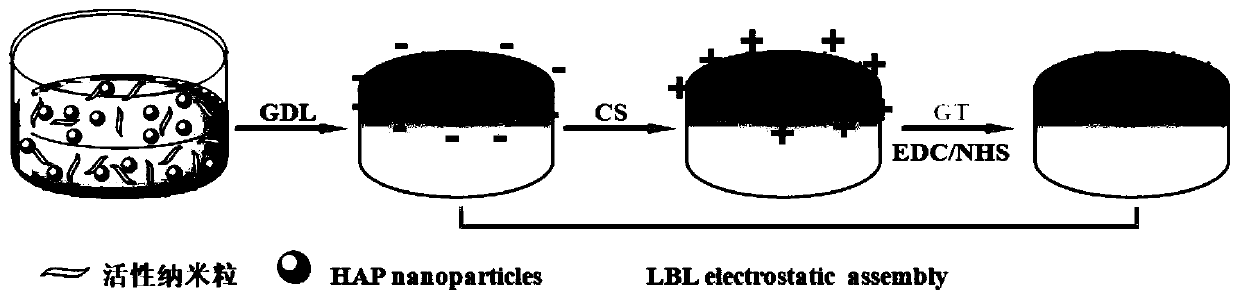
Alginate complex gel stent material constructed based on homogeneous phase crosslinking and layer-by-layer self-assembly technology and preparation method thereof
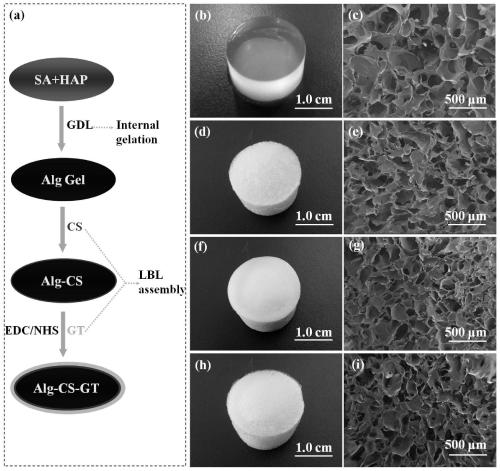
InactiveCN110302427AGood 3D shapeUniform pore structurePharmaceutical delivery mechanismProsthesisPolymer scienceSILK SERICIN
The invention relates to a gel material, in particular to an alginate complex gel stent material constructed based on homogeneous phase crosslinking and layer-by-layer self-assembly technology and a preparation method thereof, and belongs to the technical field of tissue engineering. Alginate gel is prepared with an HAP / GDL compound as an endogenous crosslinking agent, wherein the mole ratio of HAP to GDL is 1:10, and meanwhile, it is determined that the mole ratio of the Ca element in the HAP to -COOH in sodium alginate (SA) is 0.18-0.36; afterwards, chitosan (CS) with positive electricity and B-type gelatin (GT) (collagen or sericin) with negative electricity are alternately deposited on the surface of the alginate gel through the electrostatic effect; and finally, the GT (collagen or sericin) on the outermost layer is subjected to covalent crosslinking through an EDC / NHS mixture, and therefore an alginate complex gel stent with homogeneous phase crosslinking is prepared.
Owner:HAINAN NORMAL UNIV
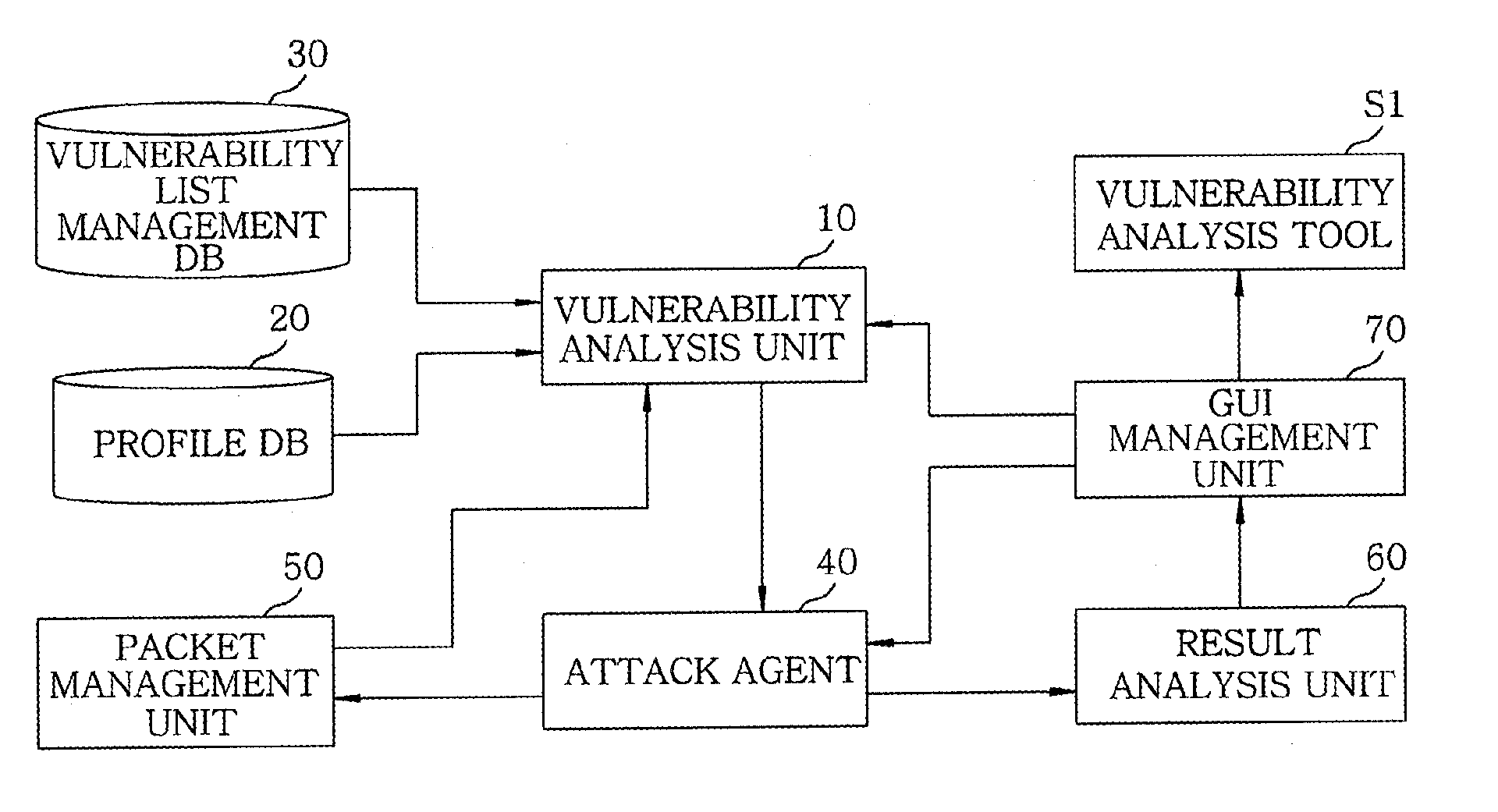
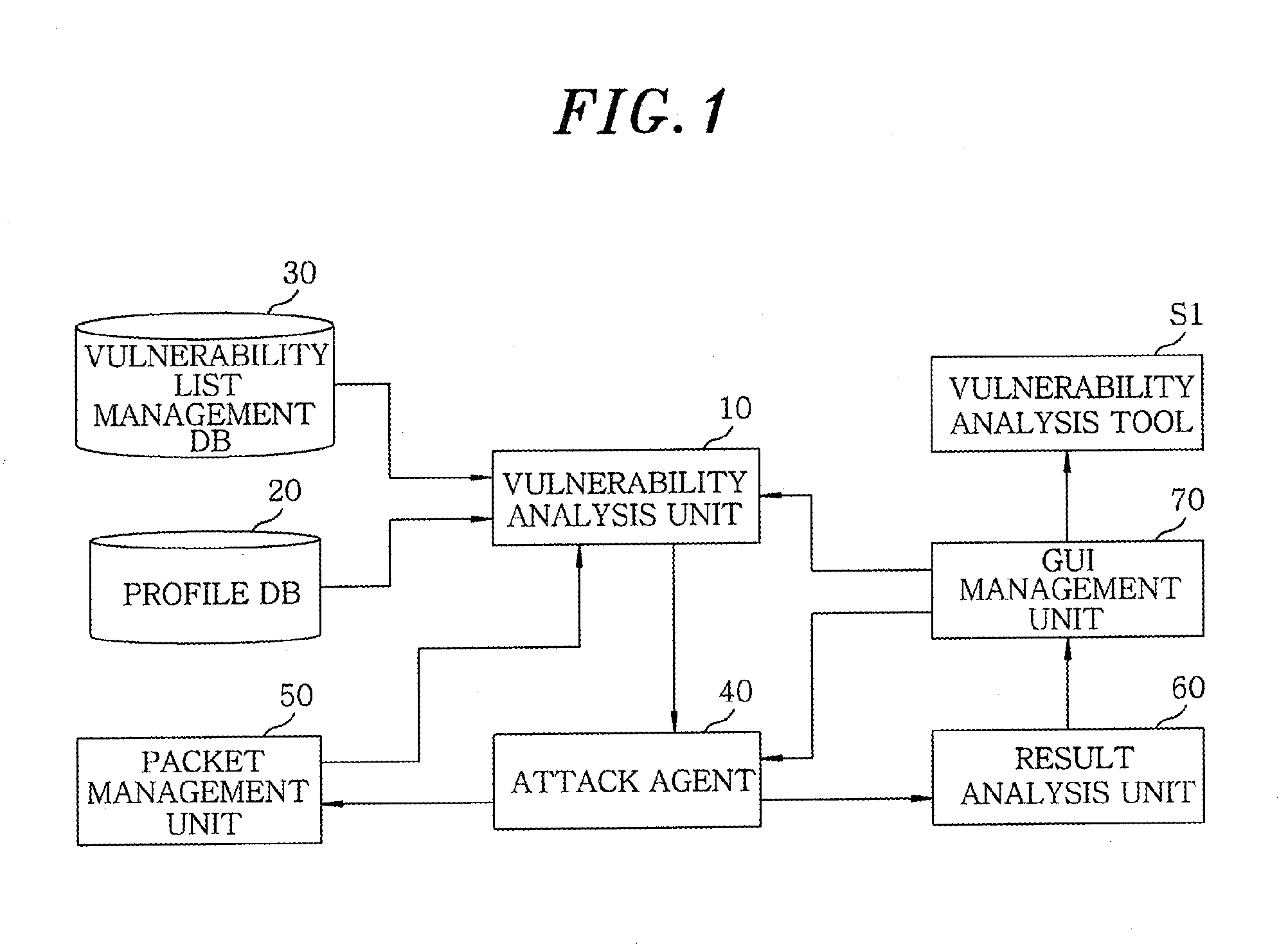
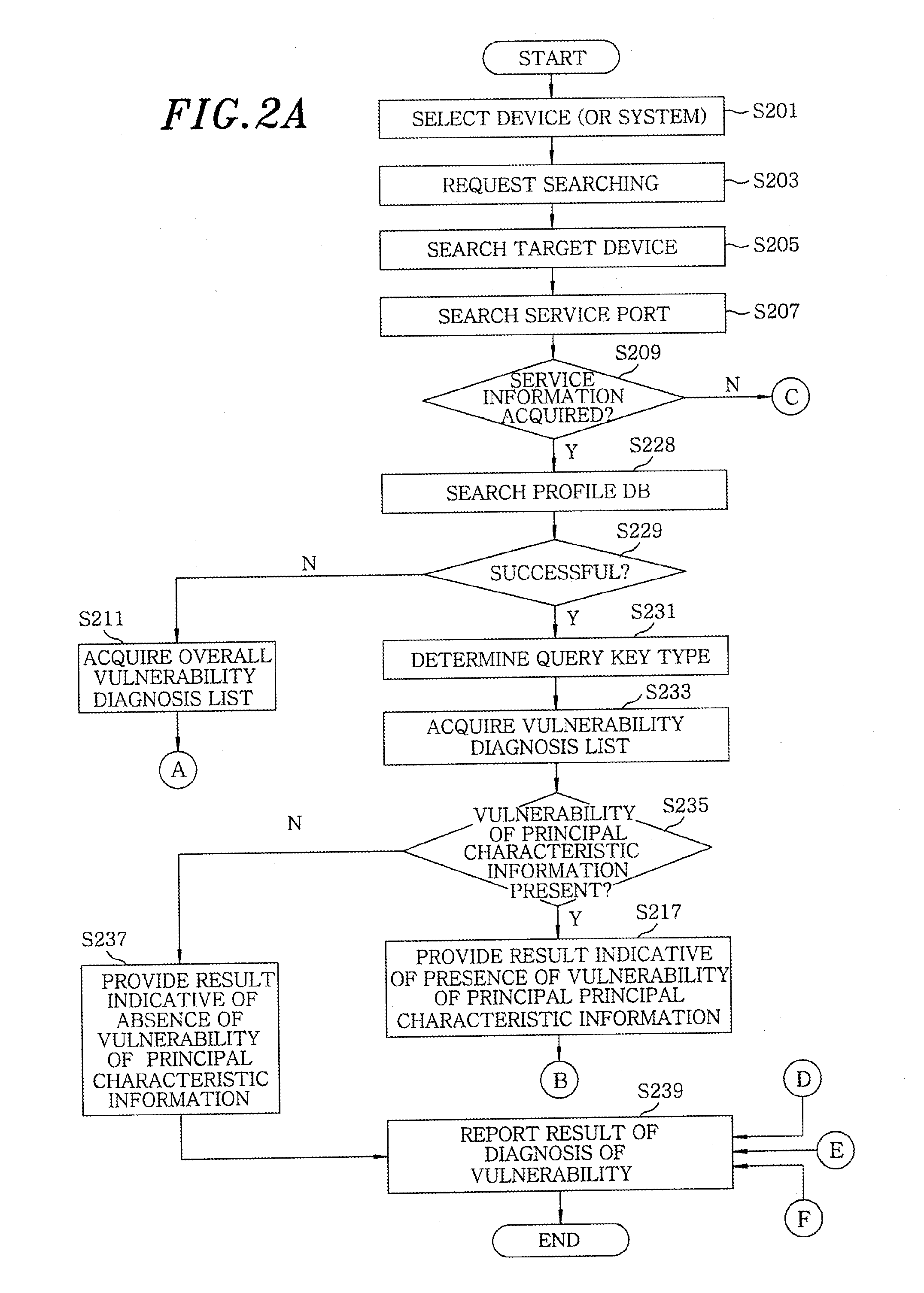
Apparatus and method for remotely diagnosing security vulnerabilities
InactiveUS20110093954A1Reliably analyze vulnerabilityAccuracyMemory loss protectionData taking preventionManagement unitService information
An apparatus for remotely diagnosing security vulnerabilities, includes a vulnerability analysis unit for obtaining service information by searching a target device of a specific network and a port of the target device, searching a profile DB for principal characteristic information of the acquired service information, determining a query key type based on the retrieved principal characteristic information to acquire a vulnerability diagnosis list present in the principal characteristic information from a vulnerability list management DB; and an attack agent for diagnosing a vulnerability of the principal characteristic information on the vulnerability diagnosis list based on preset characteristic information. Further, the apparatus includes a result analysis unit for reporting a result of the diagnosis of the vulnerability of the principal characteristic information; and a GUI management unit for performing interfacing of the result of the diagnosis of the vulnerability of the principal characteristic information to a vulnerability diagnosis tool.
Owner:ELECTRONICS & TELECOMM RES INST
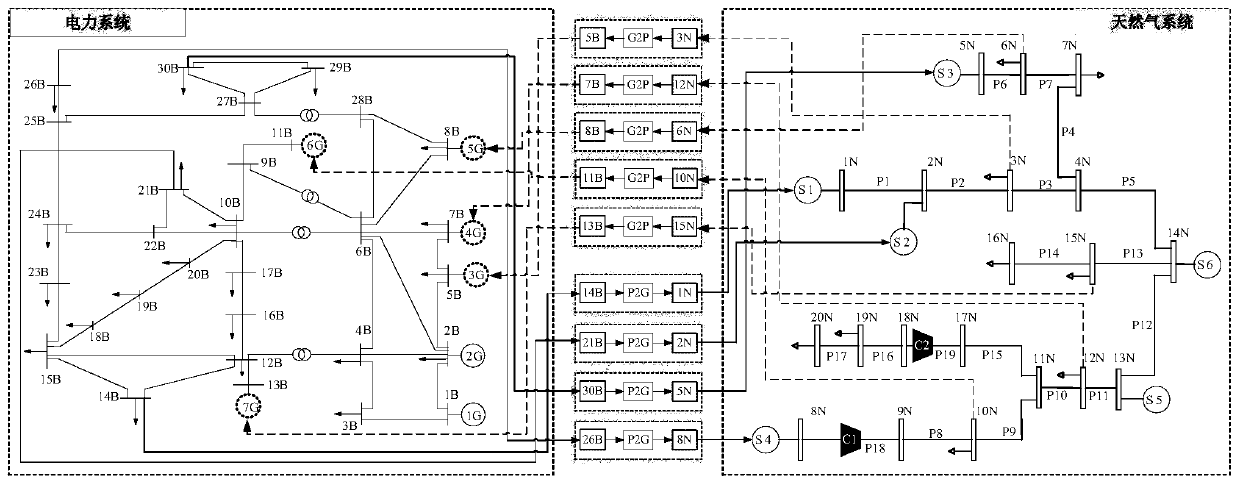
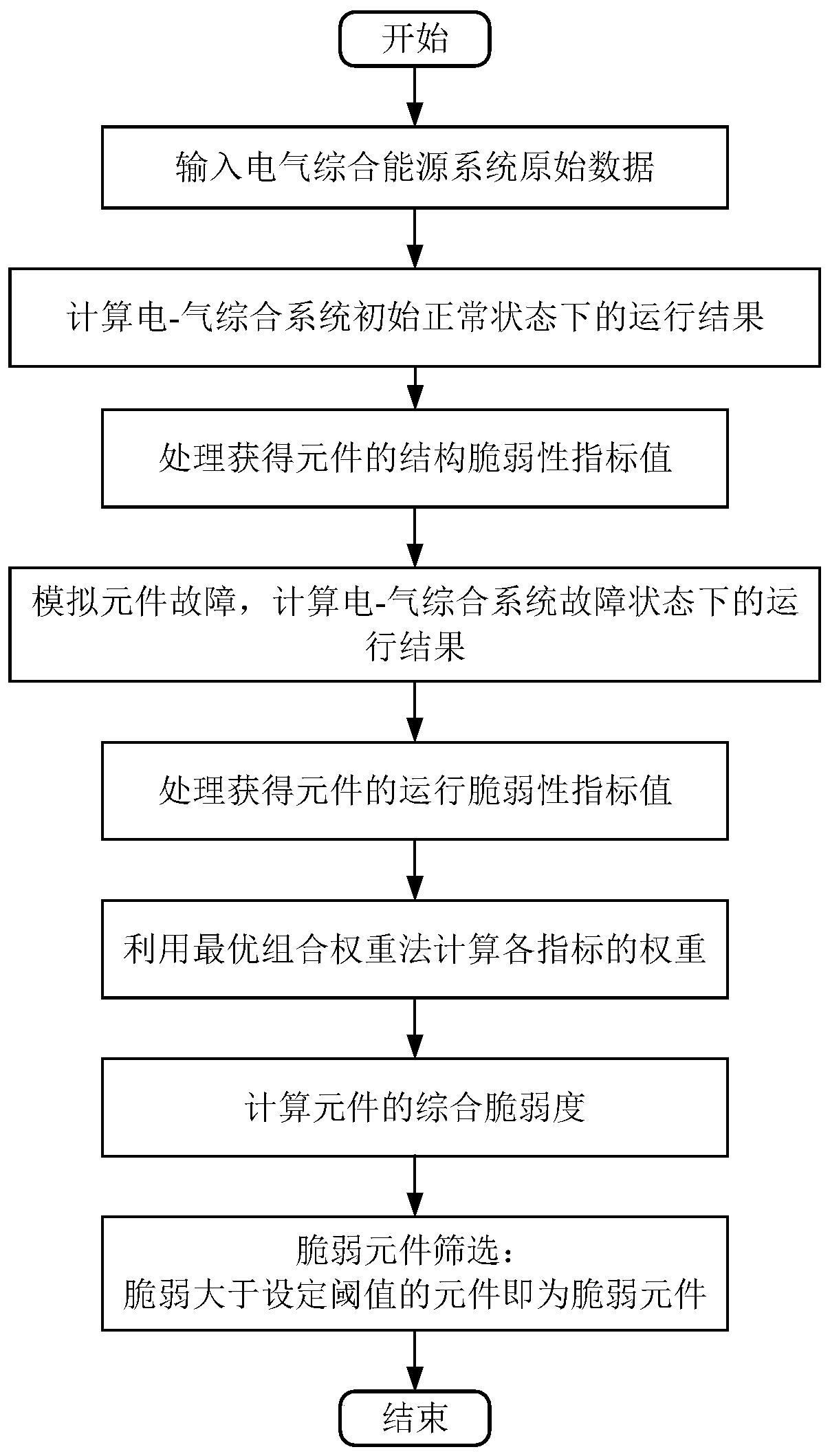
Method for improving element vulnerability of electricity-gas comprehensive energy system
ActiveCN111444593AImprove vulnerabilityImprove operational reliabilityDesign optimisation/simulationAc networks with different sources same frequencyElectricity systemPower flow
The invention discloses a method for improving the element vulnerability of an electricity-gas comprehensive energy system. The method includes: inputting original data, and establishing an electricity-gas comprehensive energy system operation state model to obtain an operation result in an initial normal state; extracting a network topology structure of the comprehensive energy system, and performing processing to obtain structural vulnerability parameters of the elements; simulating an element fault to obtain an operation result of the system in a fault state; obtaining the gas flow distribution entropy of the natural gas system and the power flow distribution entropy of the power system, and obtaining the operation vulnerability parameter of the element; and calculating the weight of each parameter by using an optimal combination weight method to obtain the comprehensive vulnerability of the element. According to the method, key protection can be rapidly carried out on the element with high vulnerability, the reliability of the element is improved by thickening the power line and reinforcing the natural gas pipeline, the overall operation reliability and robustness of the systemare effectively improved, and the probability of large-area faults of the system is reduced.
Owner:ZHEJIANG UNIV
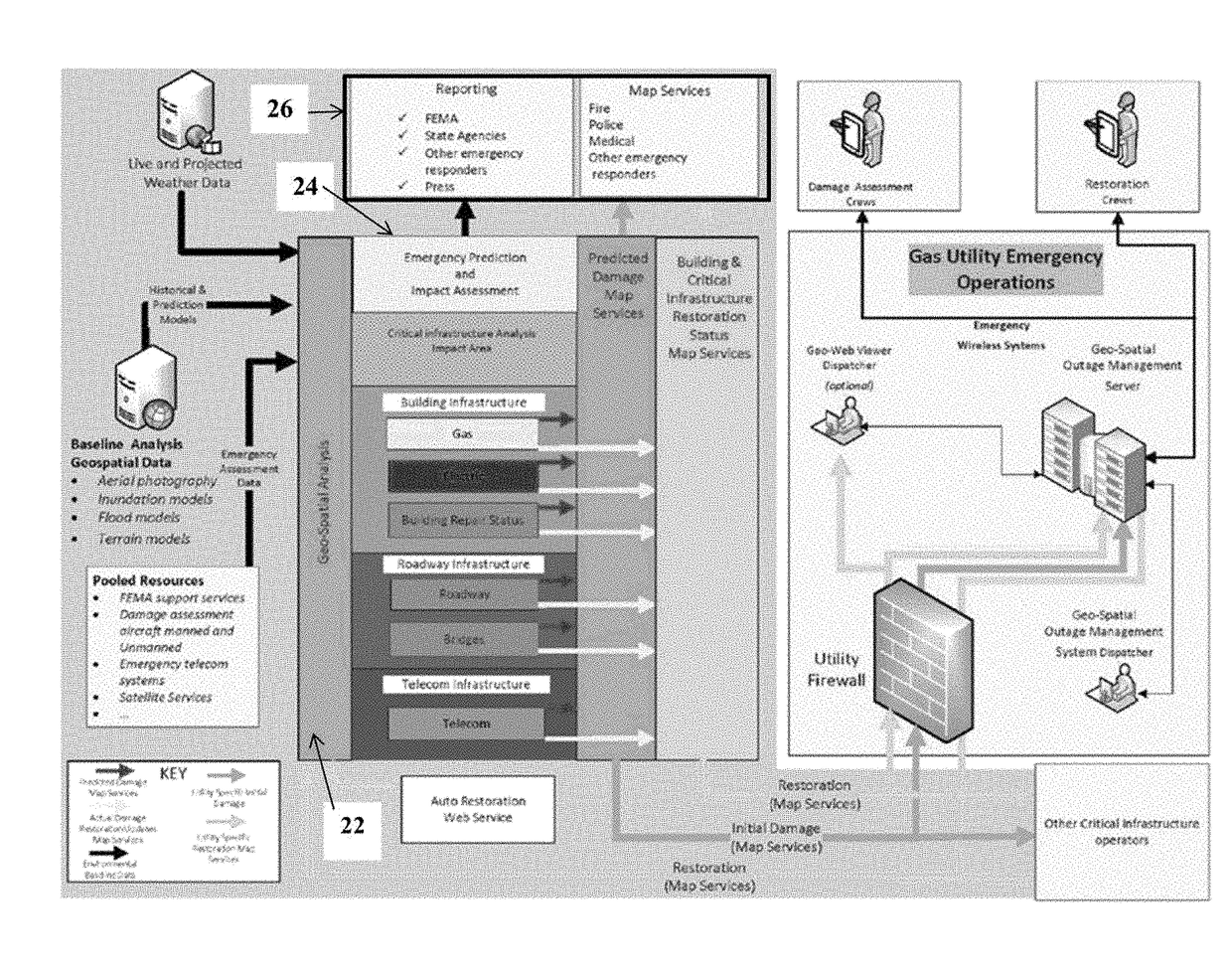
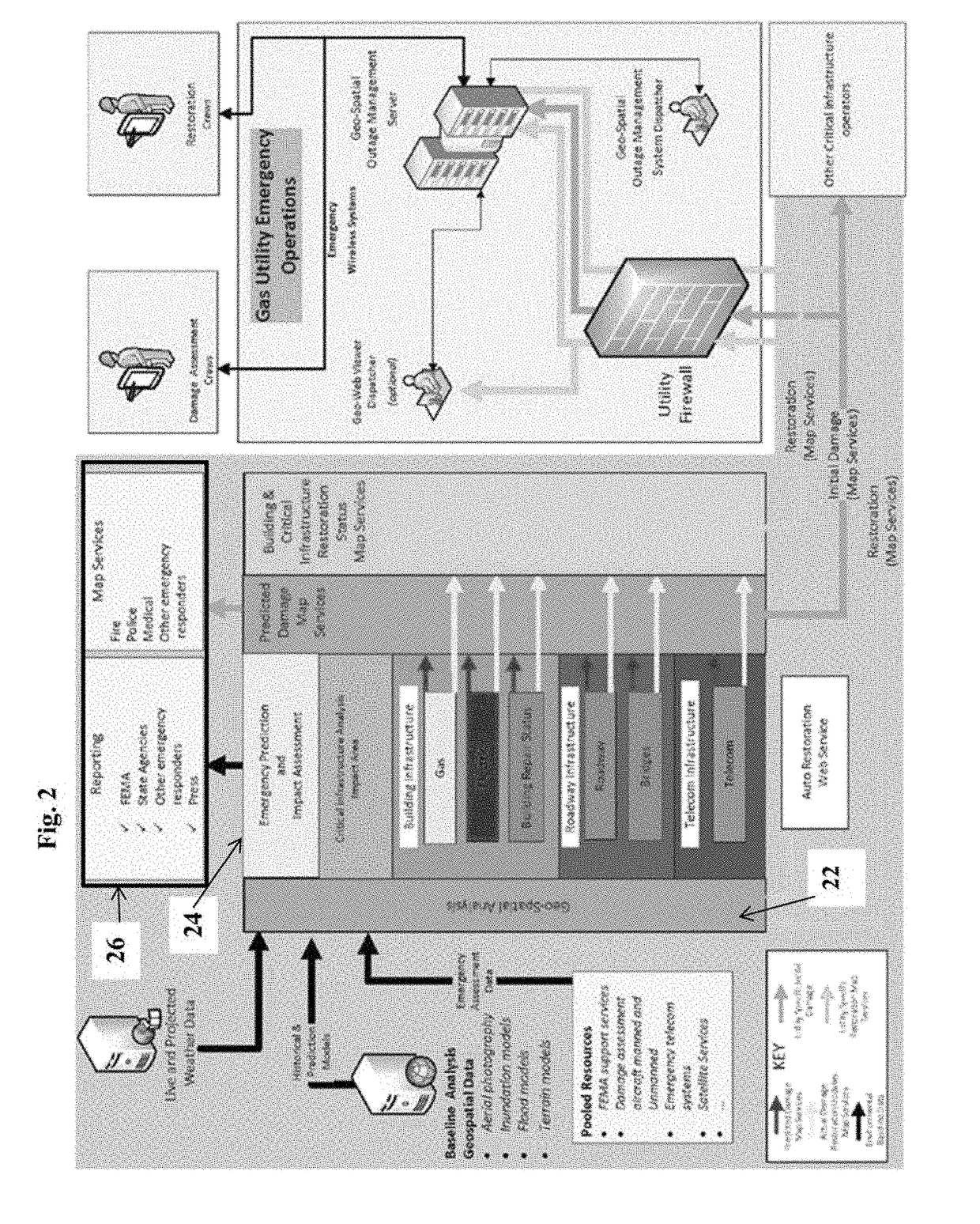
Utility situational awareness system
ActiveUS20170185698A1Improve vulnerabilityReduce riskGeometric CADData processing applicationsService locationGeographic information system
A method and software-implemented system that provides a situational awareness tool for infrastructure operators and government agencies to assess vulnerabilities, and optimize the deployment of prevention and mitigation technologies. The invention automatically obtains current supply information from each of more than one participating utility provider. The supply information from the different sources is standardized and combined with geographic information to provide a building level map of utility service and outages. The service locations, e.g., residential and commercial buildings, are represented as building polygons corresponding to building footprint, and can be color-coded to indicate service status.
Owner:GAS TECH INST
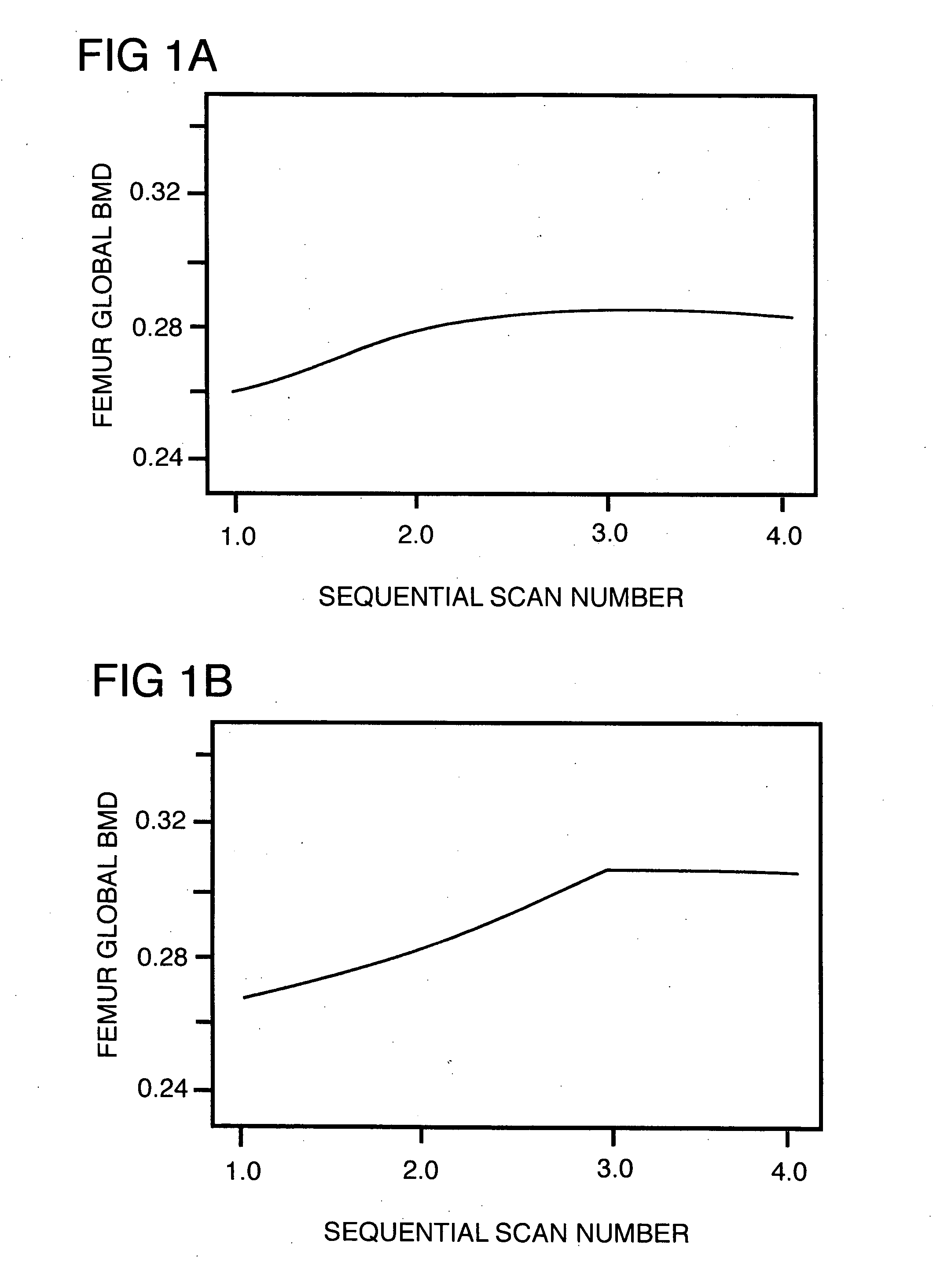
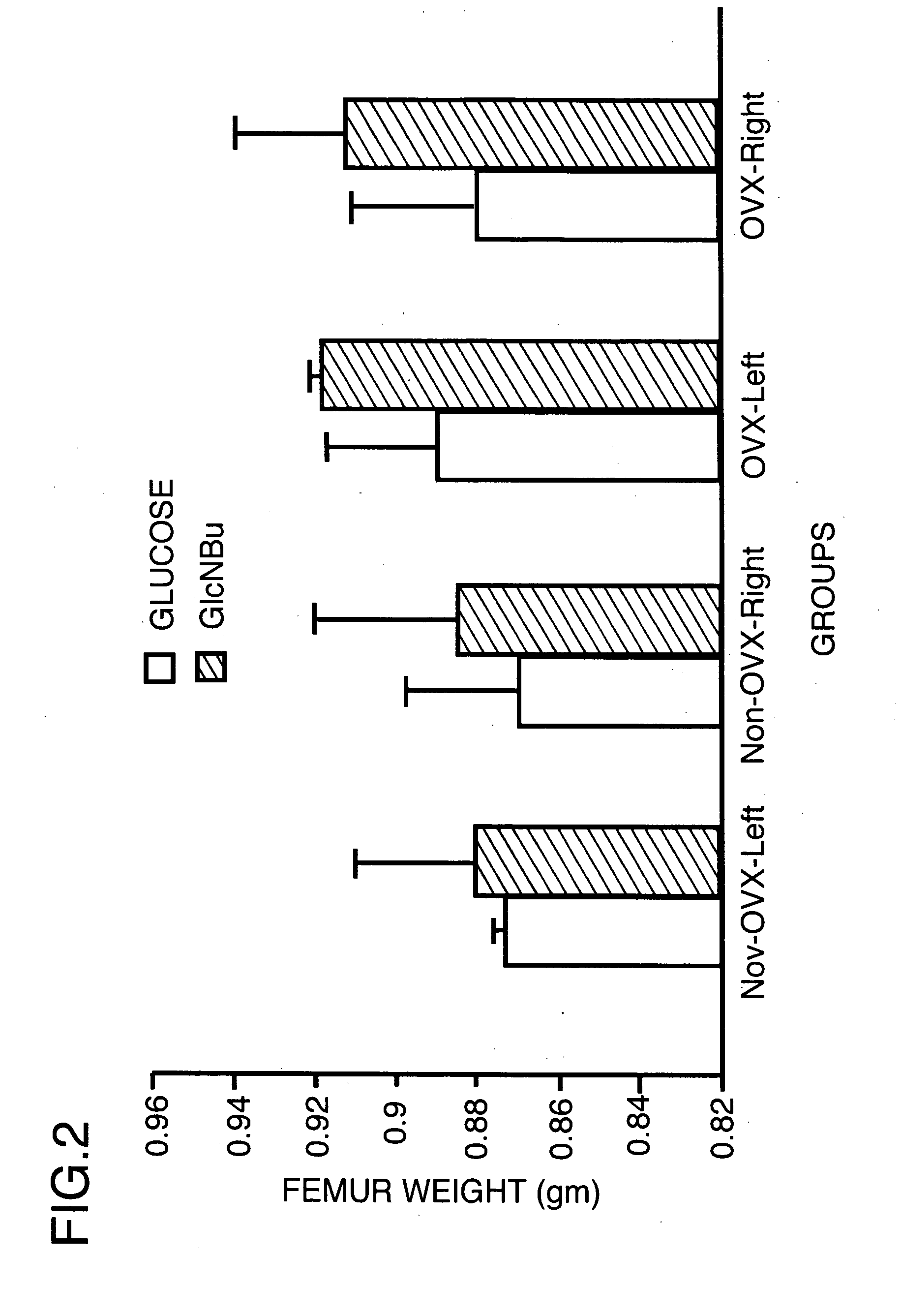
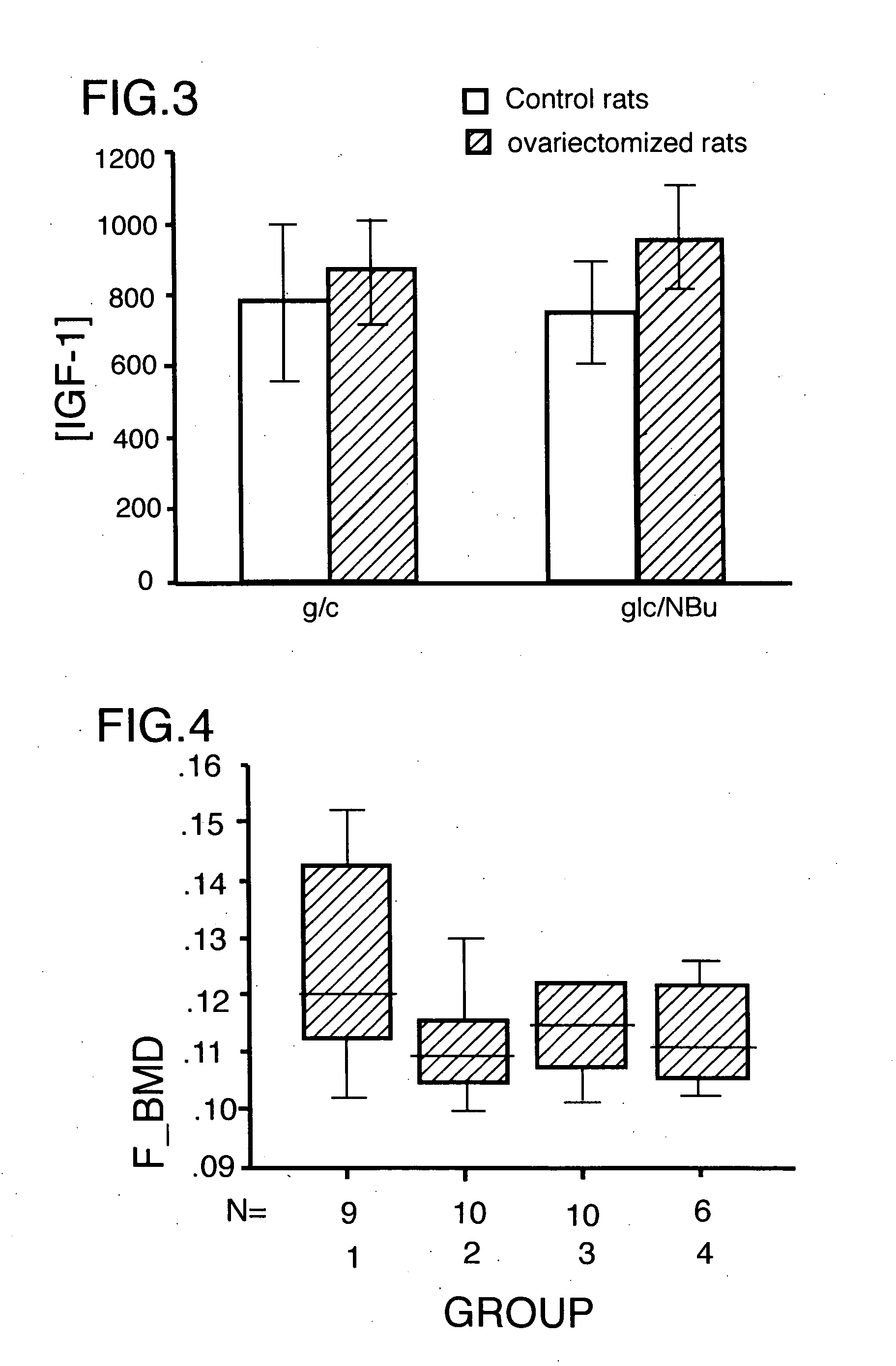
Method for increasing the bone mineral density and bone micro-architecture or connectivity of a mammal using N-acylated glucosamines
ActiveUS20060046976A1Prevent and diminish risk of fracturePromote healingBiocideSugar derivativesMammalVolumetric Mass Density
A method of treating a mammal for a purpose selected from the group consisting of (a) increasing bone mineral density (BMD), (b) treating low BMD, (c) preventing and treatment of low impact fractures, (d)treatment of high impact fractures; (e) treating osteoporosis; (f) modulating a growth factor that influences bone metabolism; and (g) improving bone micro-architecture or connectivity of bone; the method comprising administering to the mammal an effective amount of a N-acylated-2-glucosamine derivative of the general formula (I):- wherein R is an alkyl radical of the general formula CnH2n+1 and n is selected from 2-12; or pharmaceutically-acceptable salts, esters and glucosides thereof; or pharmaceutically-acceptable compositions thereof.
Owner:ANACOTI
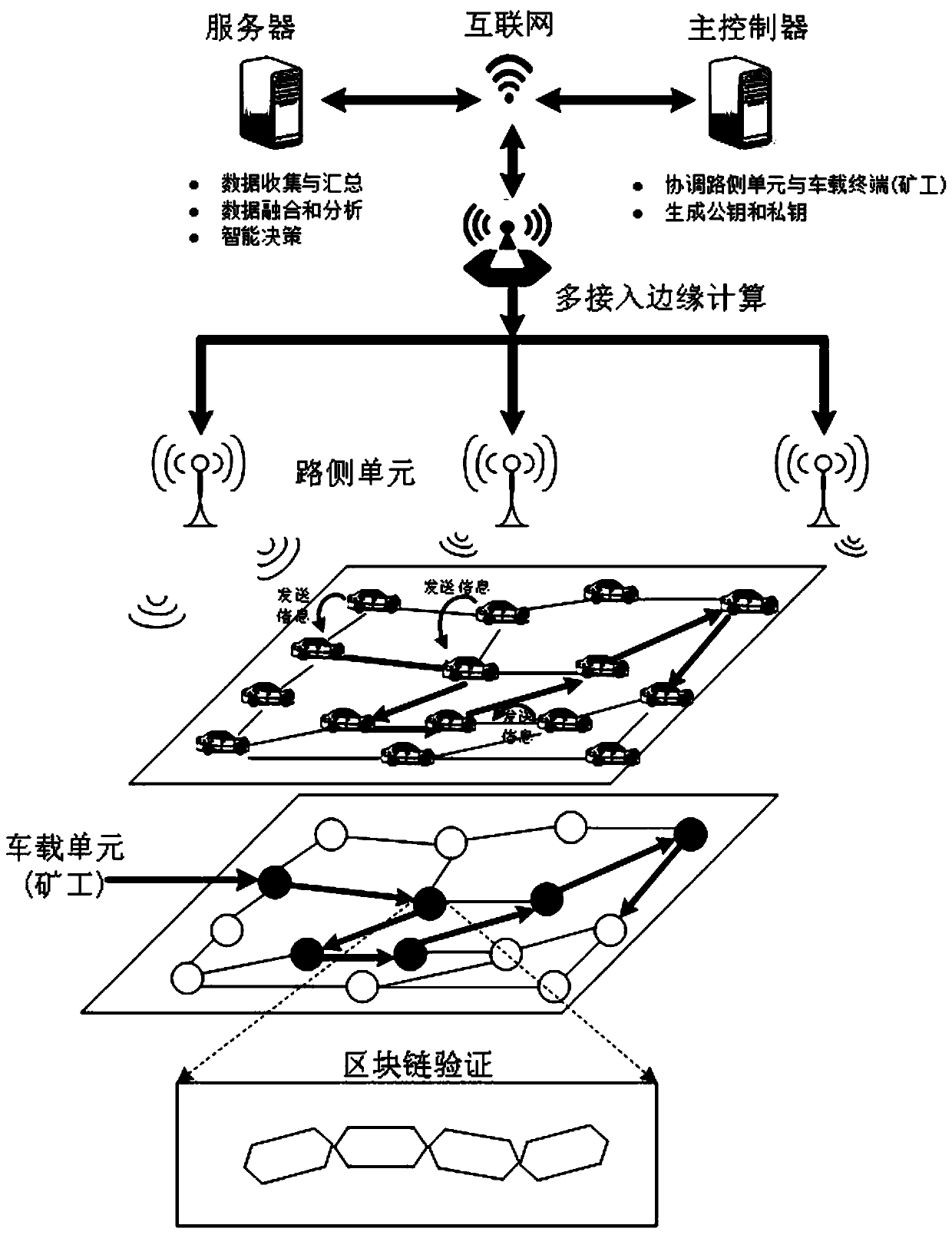
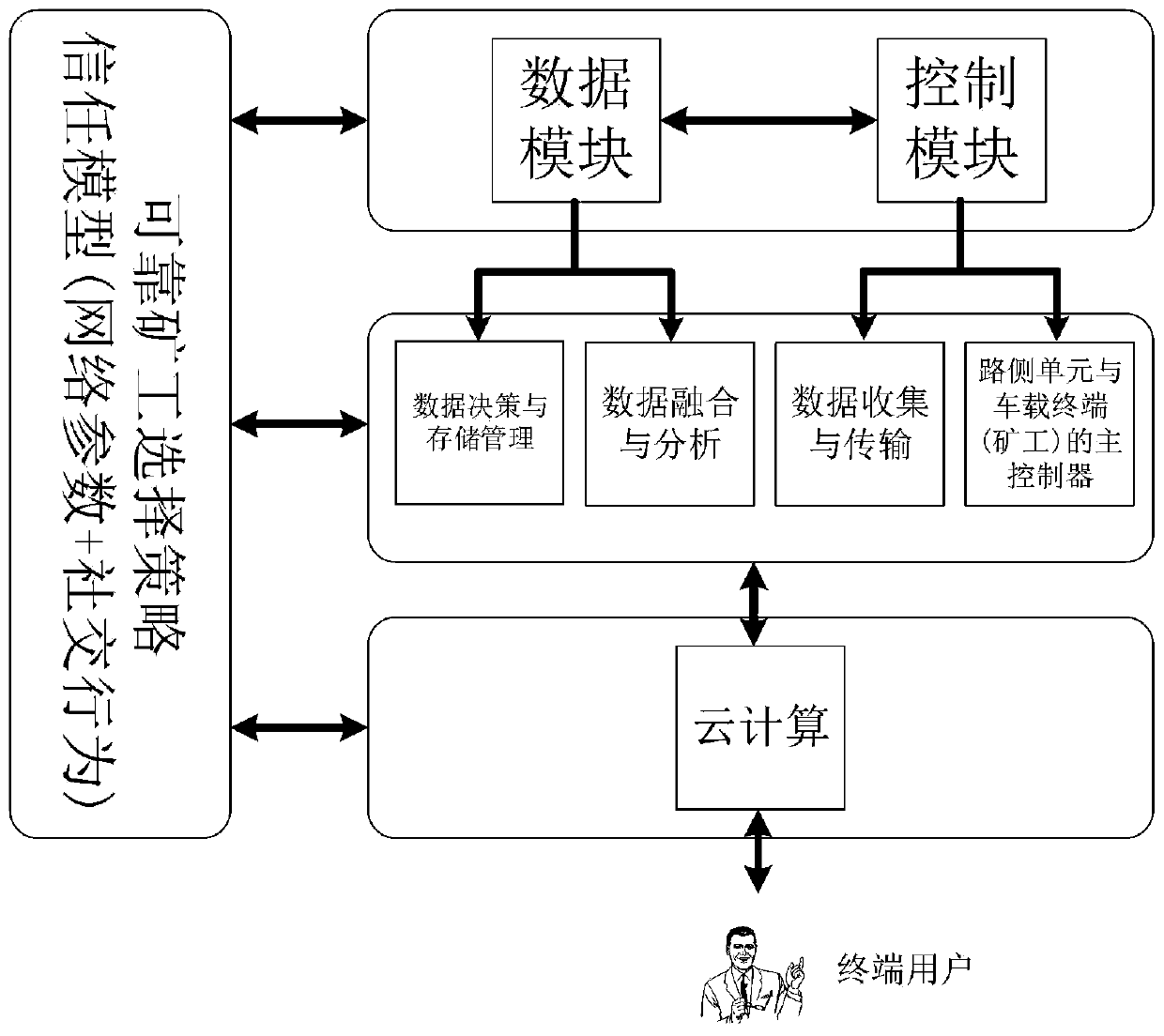
Block chain technology-based secure Internet of Vehicles social network construction method
ActiveCN111064800AImprove vulnerabilityImprove securityData switching networksVirtualizationIn vehicle
The invention discloses a block chain technology-based secure Internet of Vehicles social network construction method. The whole network comprises a main controller, a road side unit and a local controller (vehicle-mounted miner) three-level architecture, the characteristics of programmability, virtualization and zoning of the network are enhanced by using a software definition means, but the vulnerability of a network single-point fault can be caused. According to the invention, with the assistance of the blockchain technology, transaction authentication is realized and data anonymity is realized in a completely distributed manner by a trust degree algorithm-based system consensus mechanism design and a reliable miner selection method, so that the security of the system is ensured.
Owner:HANGZHOU YUNXIANG NETWORK TECH
Liquid crystal display panel and liquid crystal display device
InactiveCN106773357AControl deformationUniform thicknessNon-linear opticsLiquid-crystal displayEngineering
The invention provides a liquid crystal display panel and a liquid crystal display device. The liquid crystal display panel includes a color filter (1), a thin film transistor array substrate (2) facing the color filter (1), a liquid crystal arranged between the color filter (1) and the thin film transistor array substrate (2), and a plurality of light resistance spacing columns (4) which are supported between the color filter (1) and the thin film transistor array substrate (2) in a zone between the color filter (1) and the thin film transistor array substrate (2); and the light resistance spacing columns (4) are made of a glue material, one ends of the light resistance spacing columns (4) are fixedly attached on the color filter (1), and the other ends of the light resistance spacing columns (4) are fixedly attached on the thin film transistor array substrate (2). The liquid crystal display panel has high mechanical strength, can lower fracture risk, can allow even thickness of the liquid crystal, and can improve the product yield.
Owner:WUHAN CHINA STAR OPTOELECTRONICS TECH CO LTD
Pressure sensor
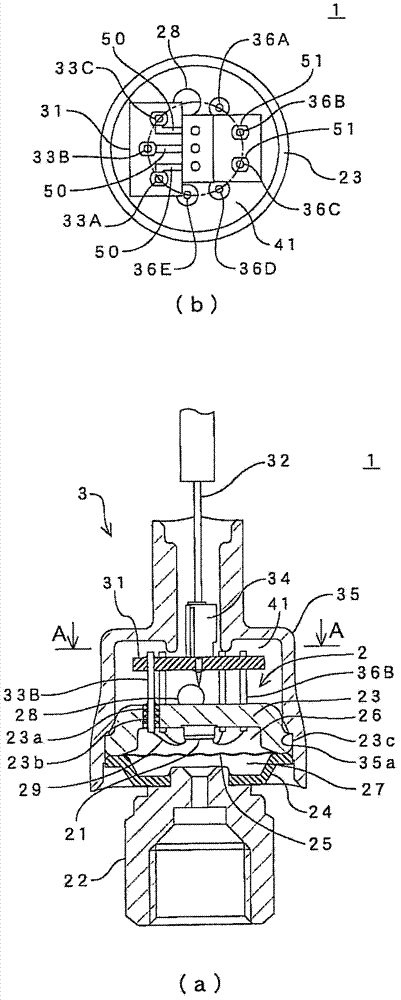
ActiveCN102778323AGuaranteed air tightnessImprove vulnerabilityFluid pressure measurement using piezo-electric devicesEngineeringElectrical bonding
A pressure sensor (1) comprises a pressure detecting part (2) which possesses a pressure detecting element (21); an output guide pin (33) connected with the pressure detecting element and protruded to the exterior of the pressure detecting part; and a wiring substrate fixed with the output guide pin capable of being electrically connected with an external output conducting wire (32), and on which adjusting guide pins (36B,36C) connected with the pressure detecting element and protruded to the exterior of the pressure detecting part are fixed. Because not only the output guide pin, but also the adjusting guide pins used for correcting voltage, etc., are fixed on the wiring substrate together, the overall structure strengths of the output guide pin, the wiring substrate and the adjusting guide pin can be improved, and the vulnerability of the surrounding structure of the output guide pin can be improved. According to the invention, the tightness of the pressure detecting part can be kept, and the vulnerability of the surrounding structure of the output guide pin can be improved.
Owner:FUJIKOKI MFG CO LTD
Image watermark embedding and extracting method combining ridgelet transformation and DCT (Discrete Cosine Transform)
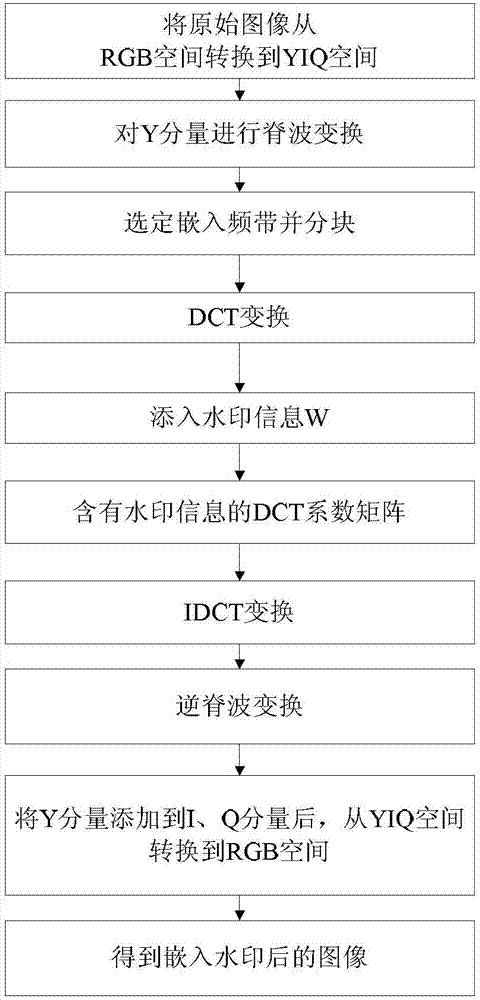
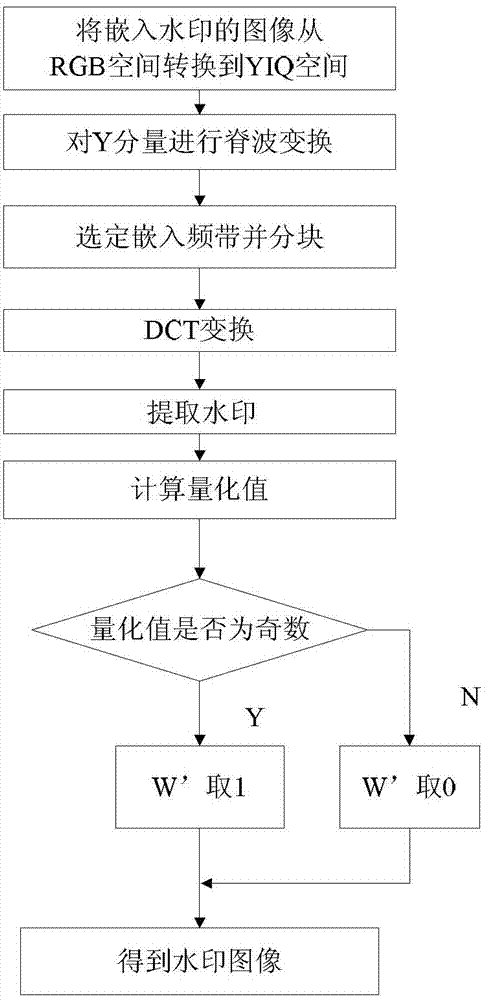
ActiveCN103079066AImprove robustnessPrevent tamperingTelevision systemsDigital video signal modificationPattern recognitionWatermark method
The invention discloses an image watermark embedding and extracting method combining ridgelet transformation and DCT (Discrete Cosine Transform). The watermark embedding method comprises the following steps of transforming an image from an RGB (red, green and blue) space to a YIQ (Luminance and Chrominance) space; performing ridgelet transformation on the Y component; selecting an embedding frequency band and dividing into blocks; performing DCT, and adding watermark information to obtain a DCT factor matrix which contains the watermark information; performing IDCT (Inverse Discrete Cosine Transform) and inverse ridgelet transformation; and transforming the image from the YIQ space to the RGB space to obtain the image into which a watermark is embedded. The watermark method comprises the following steps of transforming the image from the RGB space to the YIQ space; performing ridgelet transformation on the Y component; selecting the embedding frequency band and dividing into blocks; performing DCT; extracting the watermark; and calculating a quantized value to obtain the watermark image. The robustness of the watermarking algorithm is enhanced, and the method has higher robustness and invisibility.
Owner:NORTH CHINA UNIVERSITY OF TECHNOLOGY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com