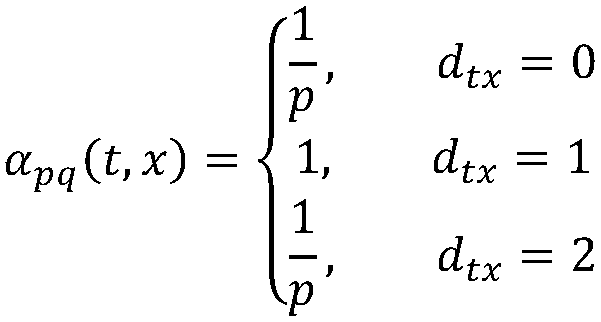Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
38 results about "Data anonymity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
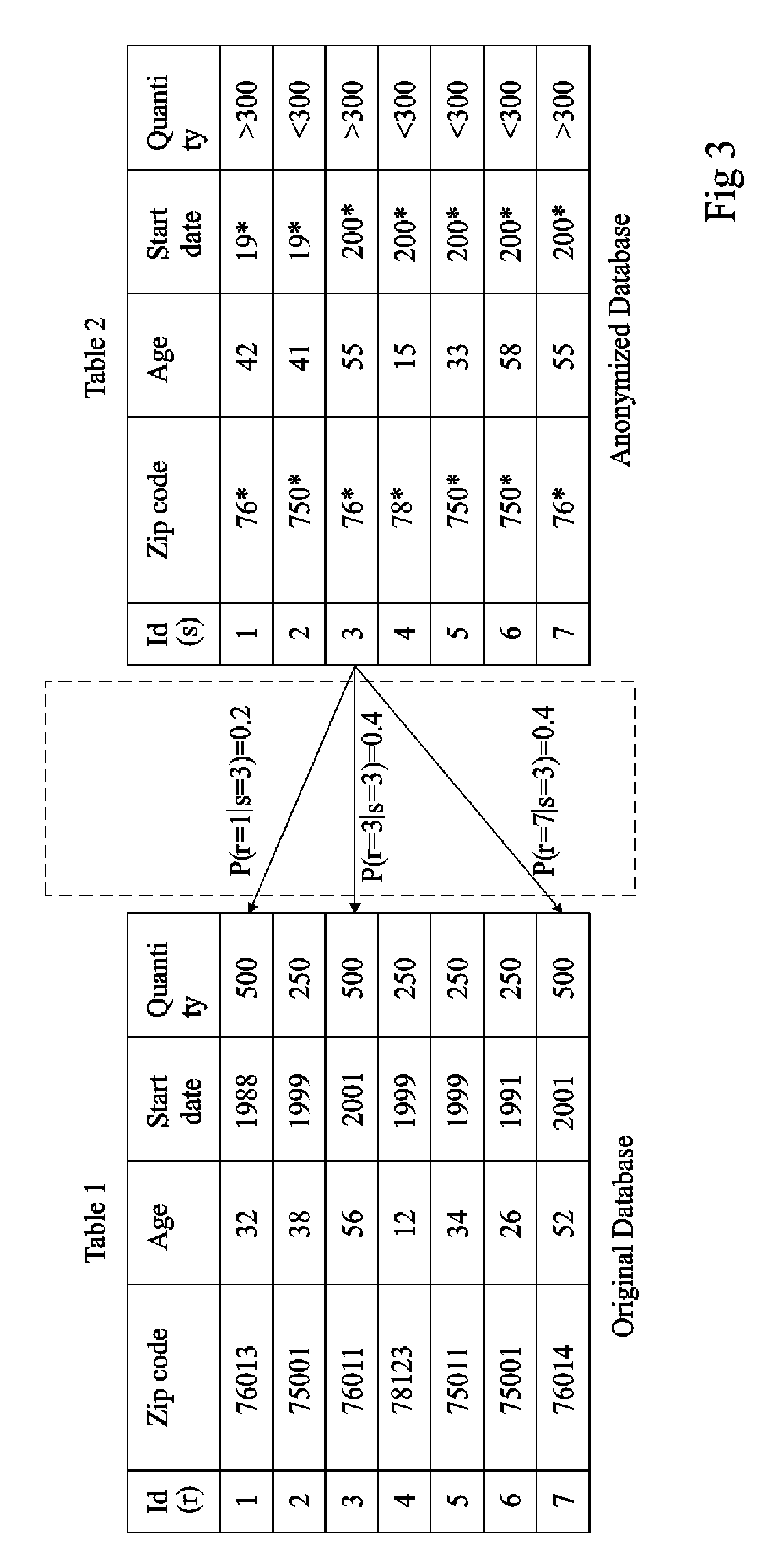
Anonymity. Anonymity in psychological research means that the data collected from participants is confidential and cannot be traced to any particular individual. This is typically done by assigning numbers to research participants and not asking for specific identifying information like name or address.
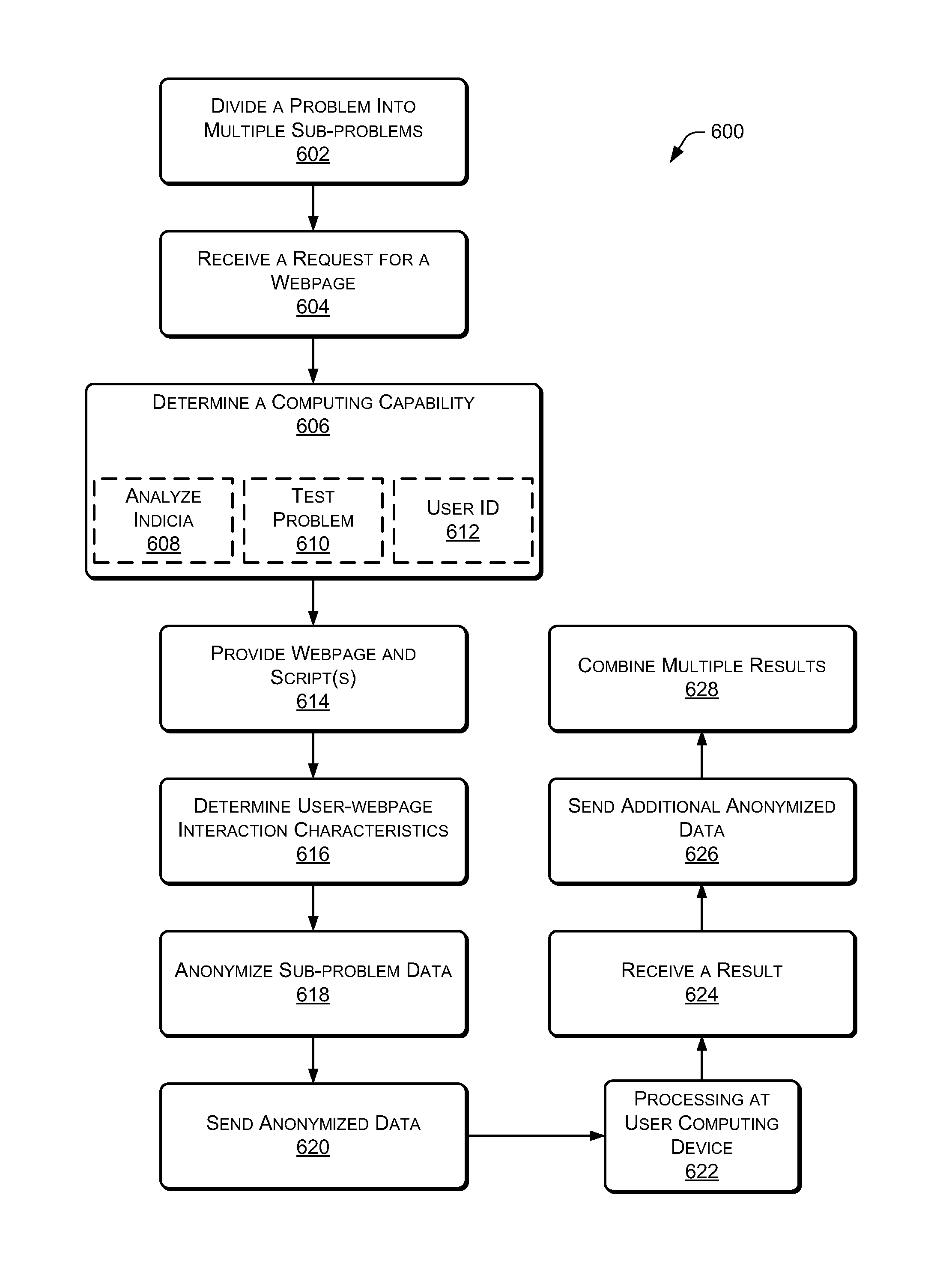
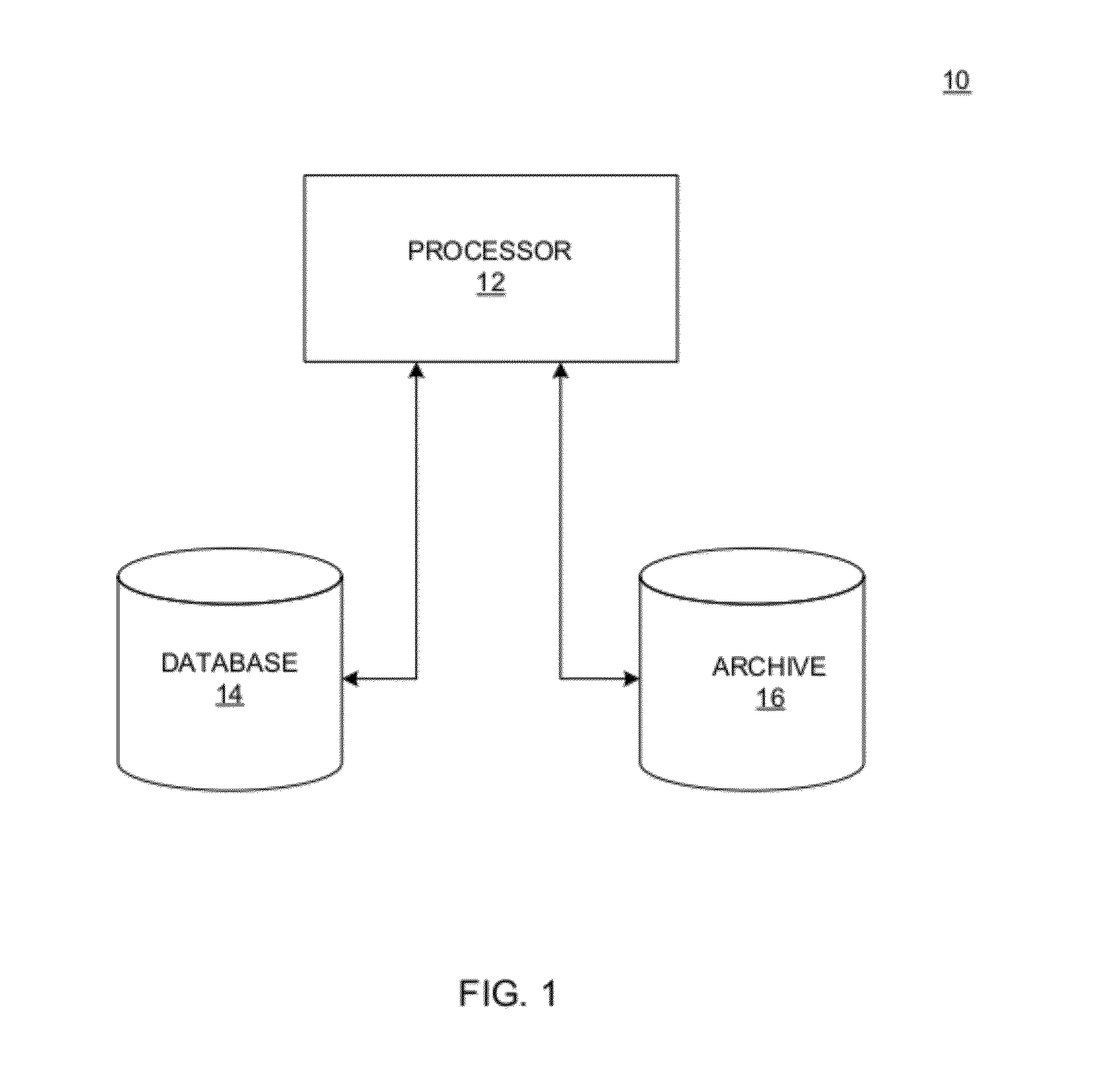
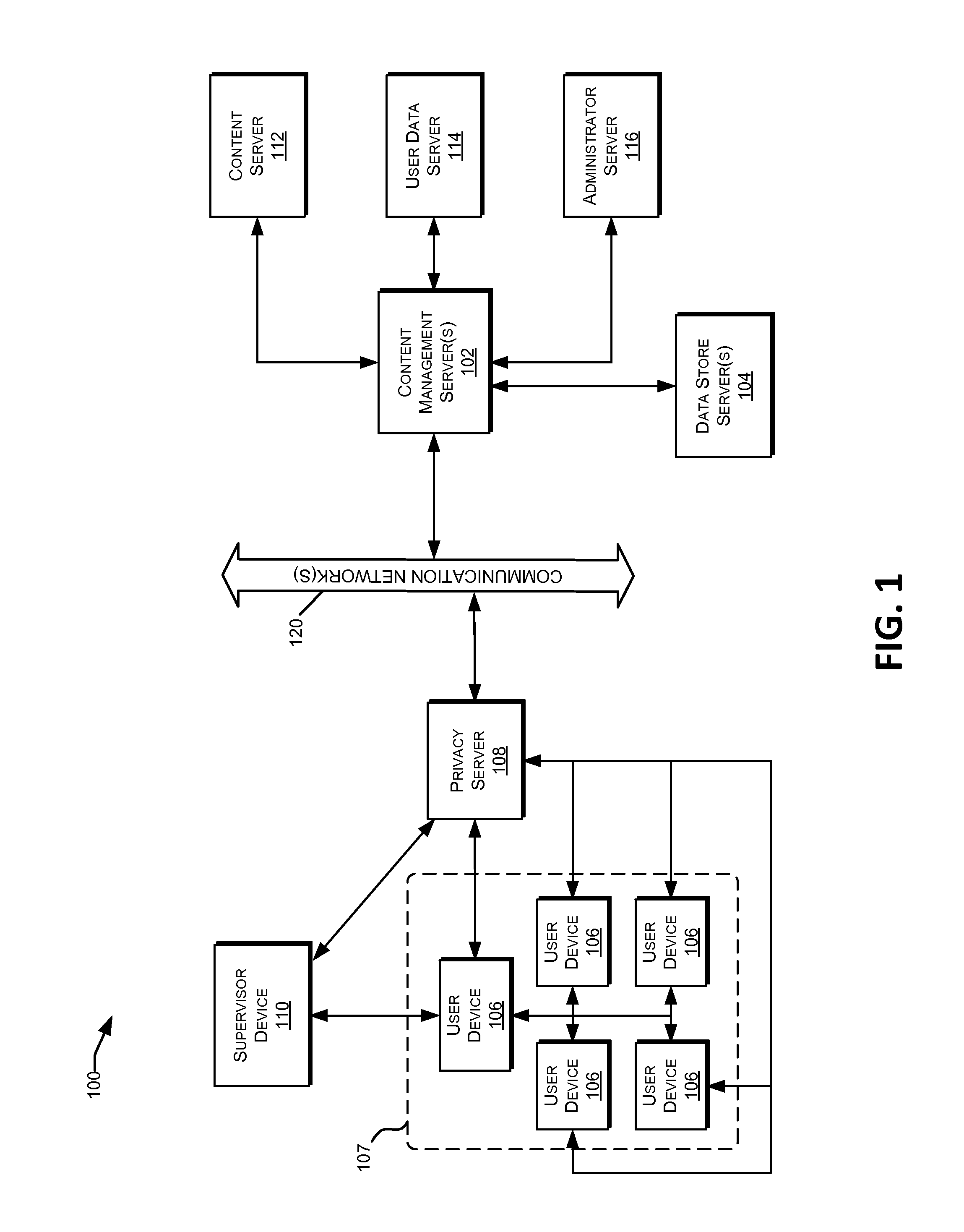
Data anonymity and separation for user computation
InactiveUS8930896B1Computer security arrangementsTransmissionScripting languageComputational problem
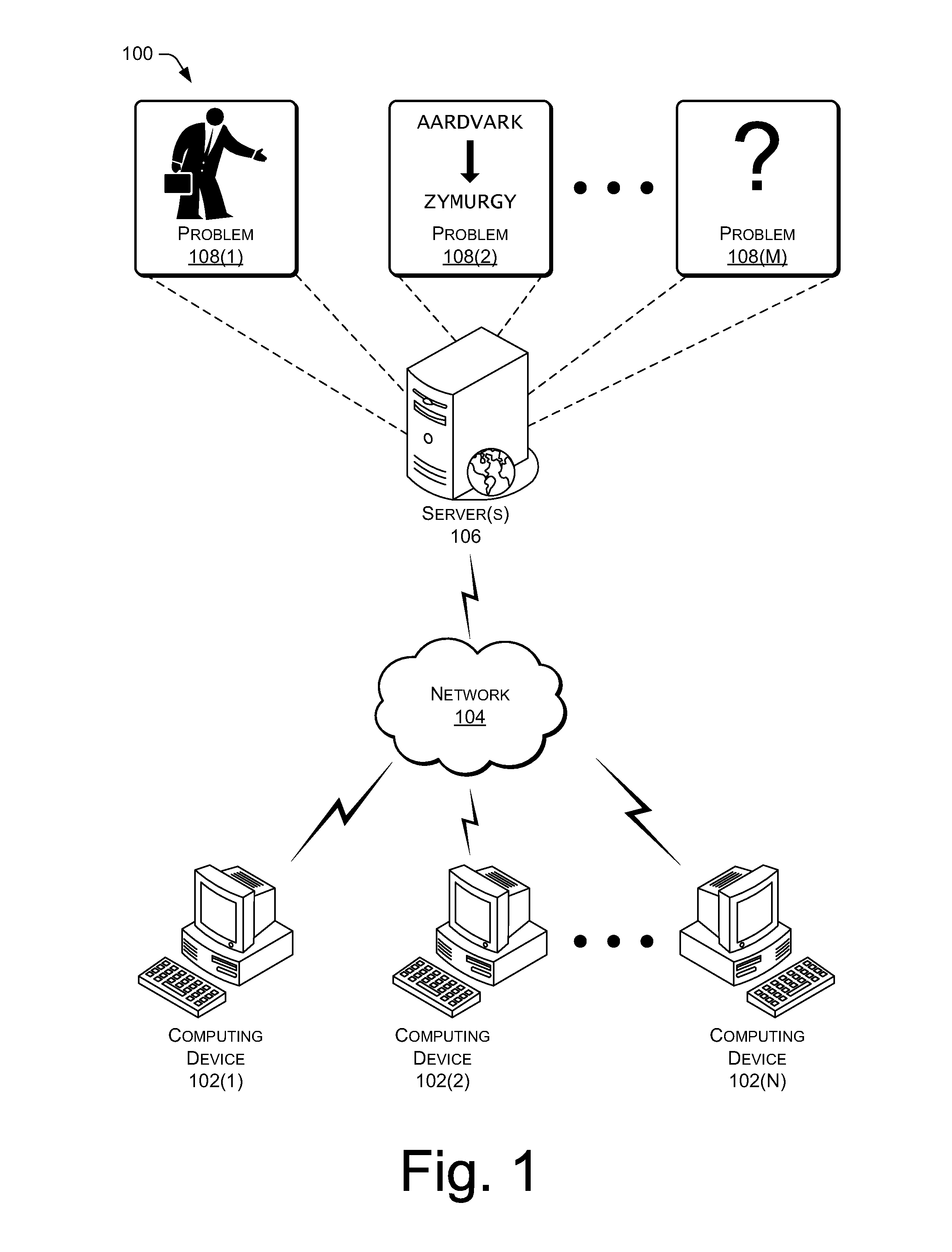
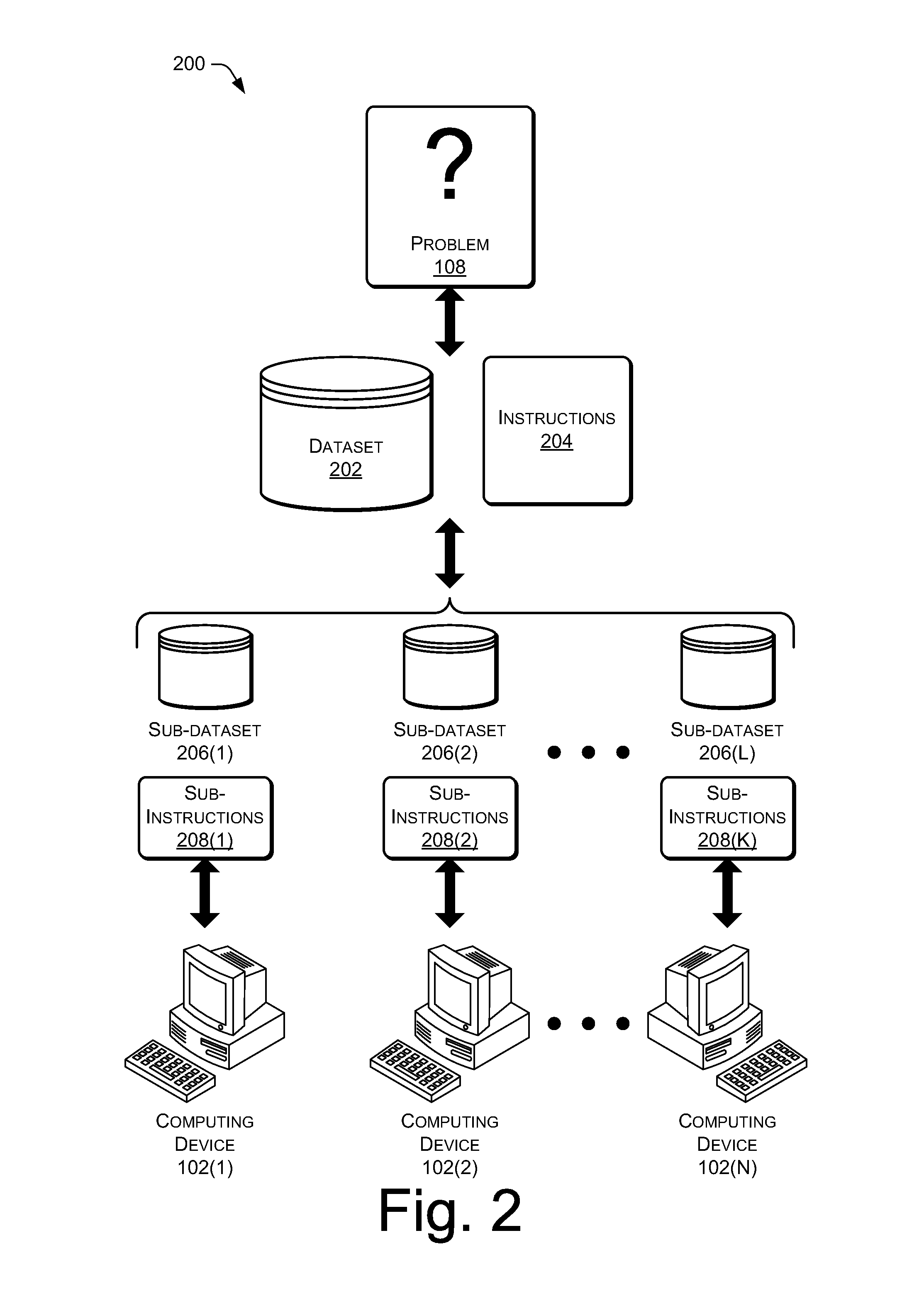
This disclosure includes techniques for using distributed computing over a network to resolve difficult computational problems. Anonymization of the data allows computing devices in the distributed computing system to solve the computational problem without exposing private aspects of the data. Individual computing devices receive instructions and data that correspond to a piece of a larger computational problem. In one implementation, a user may request a webpage from a web server and receive the webpage along with commands in a scripting language that instructs the user's computer to process a piece of the larger computational problem. The web server may assign the piece of the problem to the user's computer based on processing capabilities of the user's computer. Combining solutions received from multiple distributed computing devices and reversing the anonymization process yields a solution to the computational problem.
Owner:AMAZON TECH INC
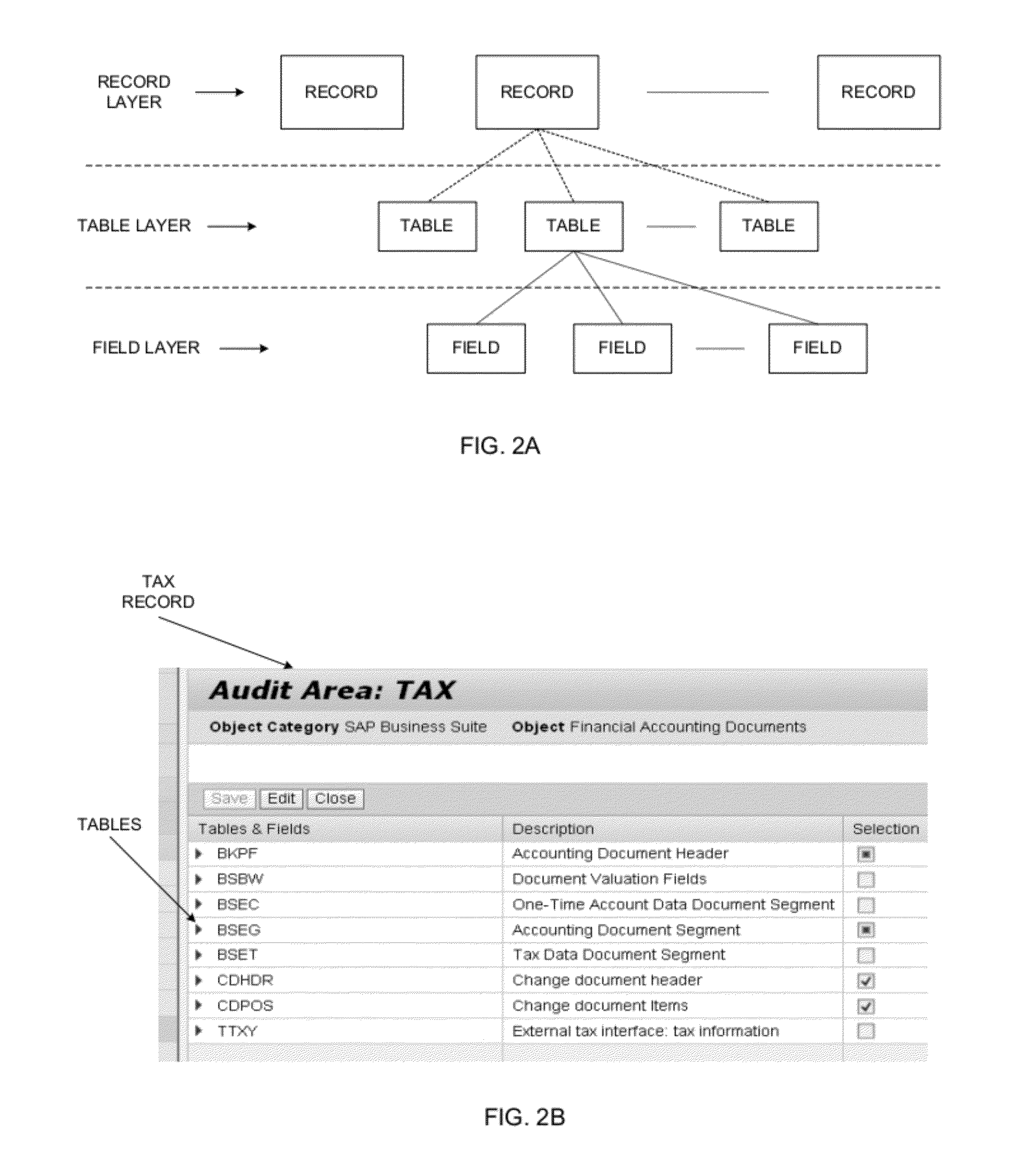
Rule-based anonymizer for business data
ActiveUS20120233129A1Digital data processing detailsComputer security arrangementsObject storeBusiness data
A method of anonymize business data. The method includes responsive to a request from an application for data objects stored in a database system, retrieving the data objects from a non-transitory storage of the database system, prior to transmitting the data object to the application, retrieving pre-determined rules from a rule engine, wherein the rules include conditions for retaining data, comparing the request against the rules to determine portions of the data objects that are to be anonymized, anonymizing the portions of the data objects, and transmitting the data object to the application.
Owner:SAP AG
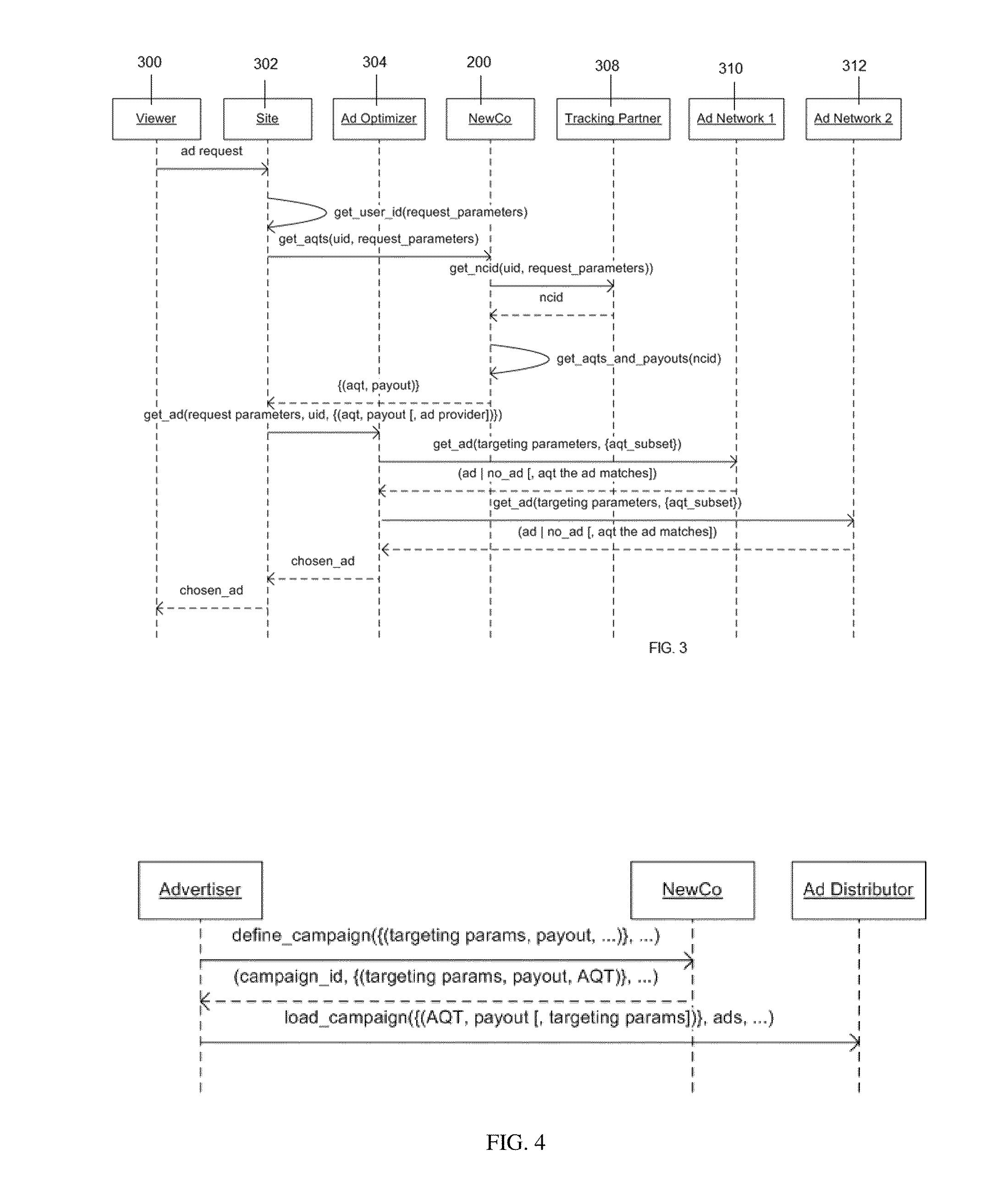
Privacy-safe targeted advertising method and system
A method and system for sophisticated consumer deep profile building provided as a service in a certifiably clean, i.e., privacy-safe, manner to advertisers, ad networks, publishers, aggregators and service providers. In an embodiment, an entity provides a tracking and targeting service that acts as a container for sensitive consumer information. The entity preferably implements a stringent policy of transparency and disclosure, deploys sophisticated security and data anonymization technologies, and it offers a simple, centralized consumer service for privacy disclosure, review and deletion of collected profile information, opt-in, opt-out, and the like. In exchange, advertisers, ad networks, publishers, aggregators and service providers (including, without limitation, mobile operators, multiple service providers (MSPs), Internet service providers (ISPs), and the like), receive privacy-safe targeting services without ever having to touch sensitive information.
Owner:SIMEONOV SIMEON S
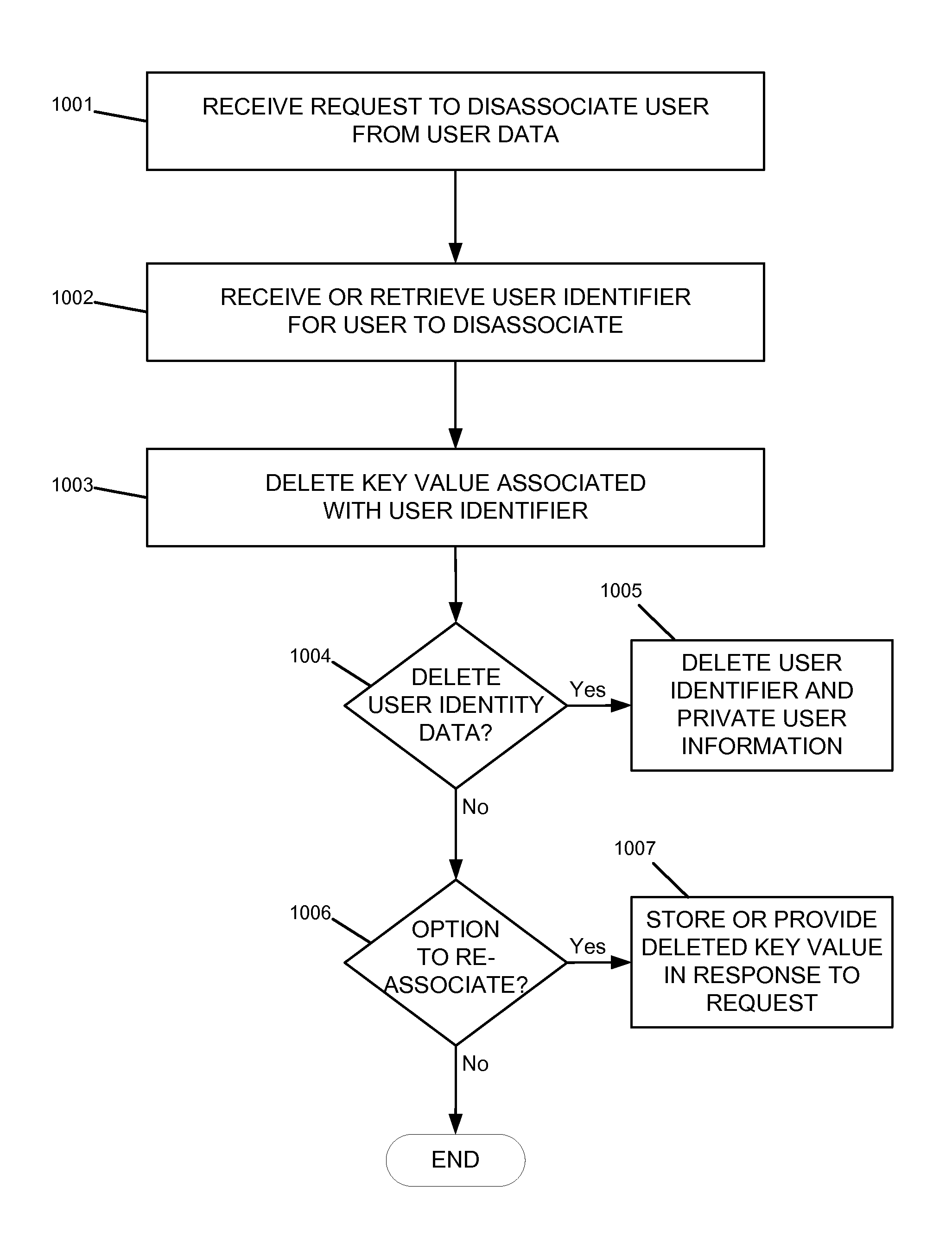
Data access and anonymity management
Techniques described herein provide data access and data anonymity management within various implementations of content distribution networks. In some embodiments, a data anonymity management system may include multiple different data stores configured to store identity data, user data, and / or linking data, as well as a data anonymity server configured to support data anonymity features such as active user data anonymity, one-way linking and permanently breakable links between user identity data and associated user data. In some embodiments, storage systems and techniques may be used for storing identity data, user data, and link data in multiple different data stores, with different data storage requirements and different processes and policies for data availability, data backup, online disaster recovery, offline storage archiving, and the like. Additionally, cryptographic hash functions may be used to implement one-way encryption between identity data and user data.
Owner:PEARSON EDUCATION
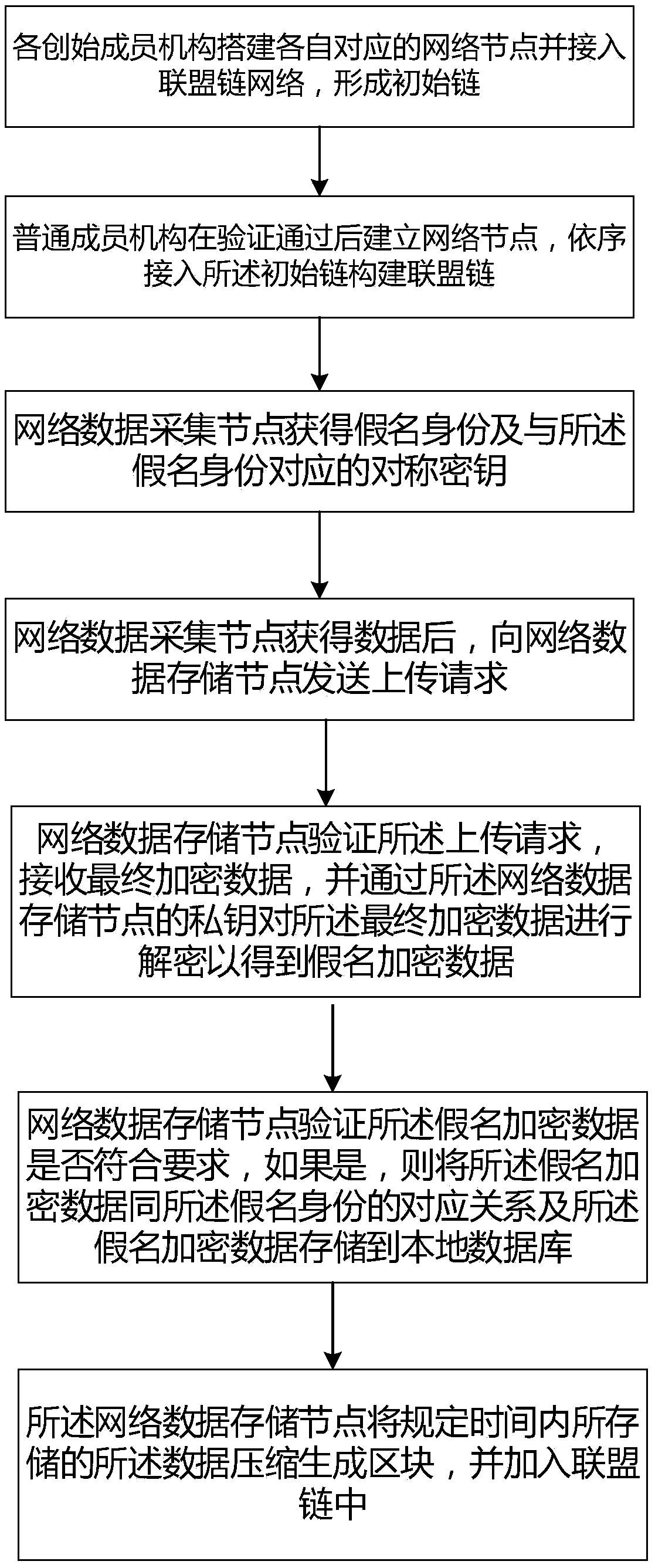
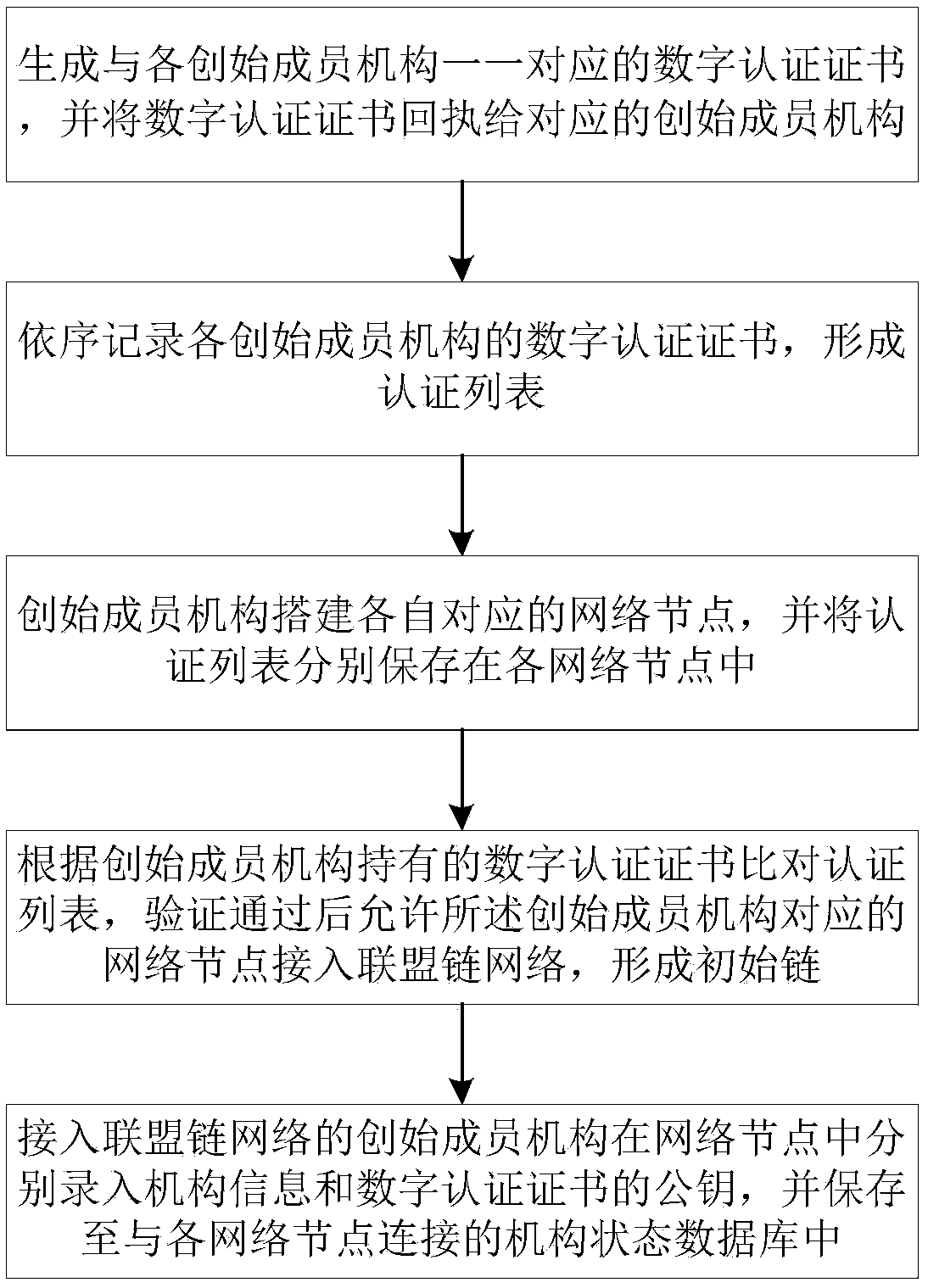
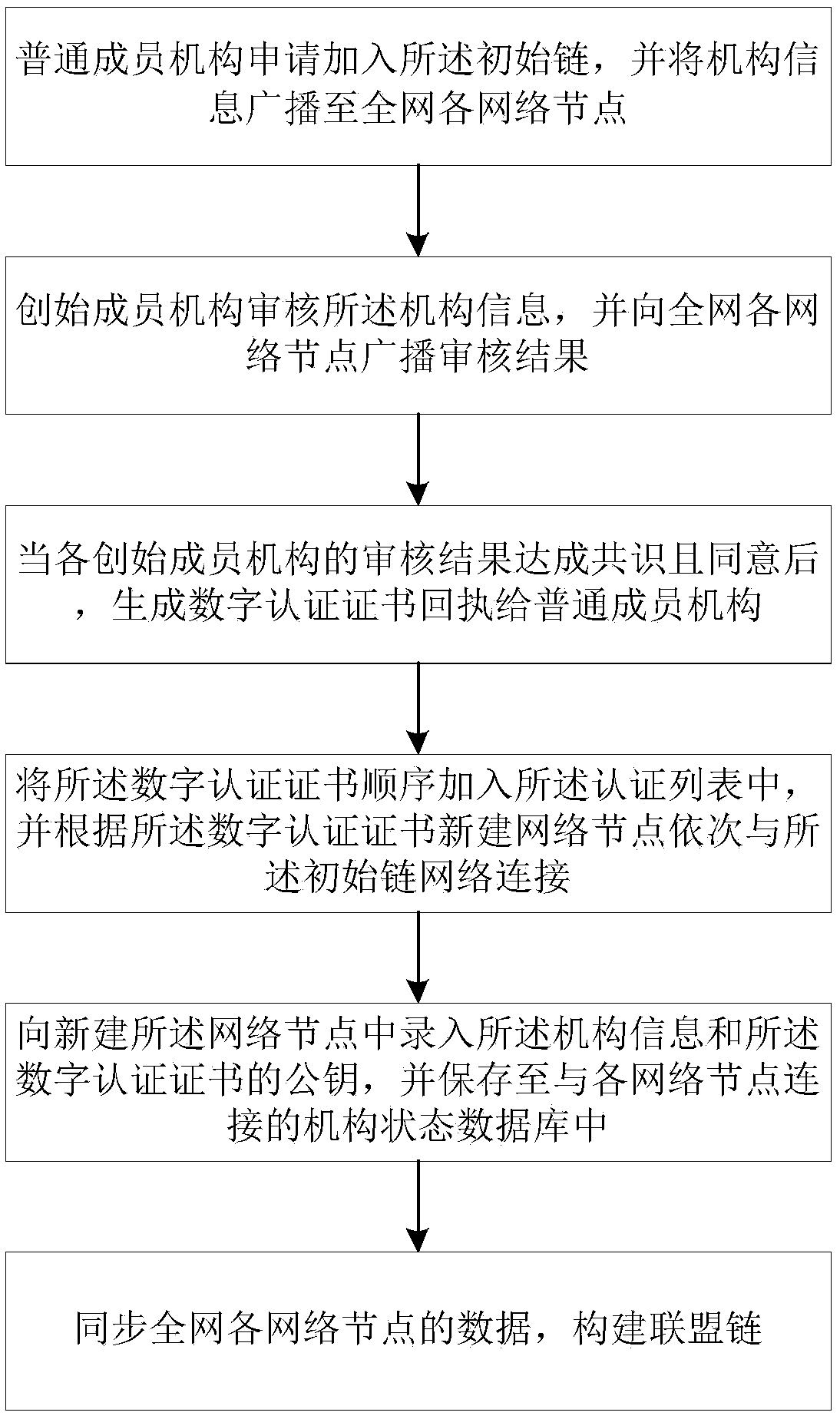
User data anonymous sharing method based on league chain encryption
InactiveCN108833385ARealize privacy protectionLimit Access ThresholdTransmissionData compressionChain network
The invention discloses a user data anonymous sharing method based on league chain encryption. The method comprises the steps as follows: each founding member mechanism builds a respectively corresponding network data collection node and accesses a league chain network, to form an initial chain; a common member mechanism builds the network data collection node after passing through verification, and sequentially accesses the initial chain to build a league chain; the network data collection node acquires a pseudonym identity and symmetric keys corresponding to the pseudonym identity; after acquiring data, the network data collection node sends an uploading request to a network data storage node; the final encrypted data is decrypted via the private key pair of the network data storage nodeto acquire pseudonym encryption data; the network data storage node stores a corresponding relationship between the pseudonym encryption data and the pseudonym identity into a local database; and thenetwork data storage node compresses the data stored within set time into a block, and adds the block into the league chain. Through building the league chain, the permissions of the common member mechanisms are effectively controlled, and the privacy of each member mechanism is ensured.
Owner:深圳崀途科技有限公司
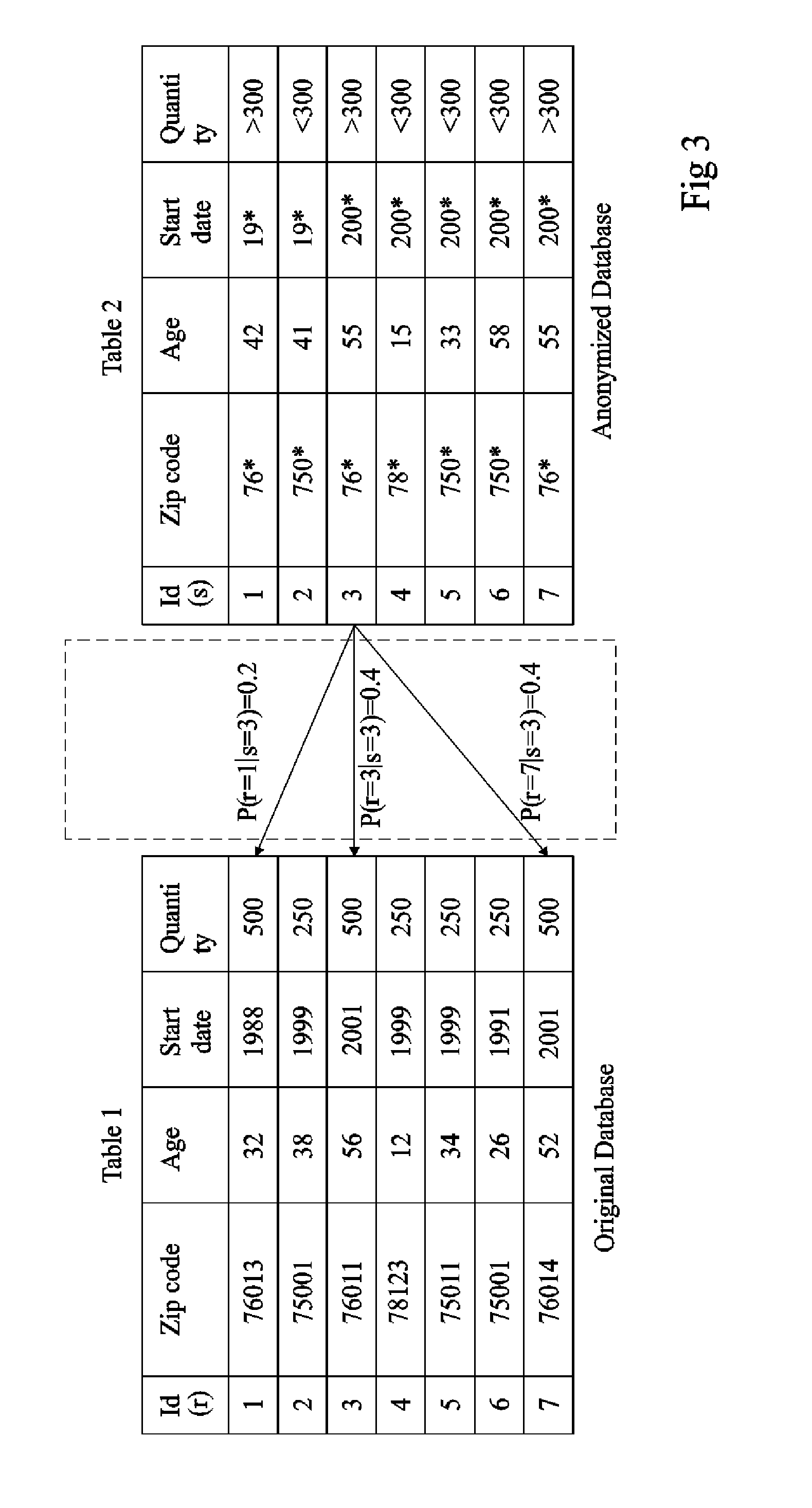
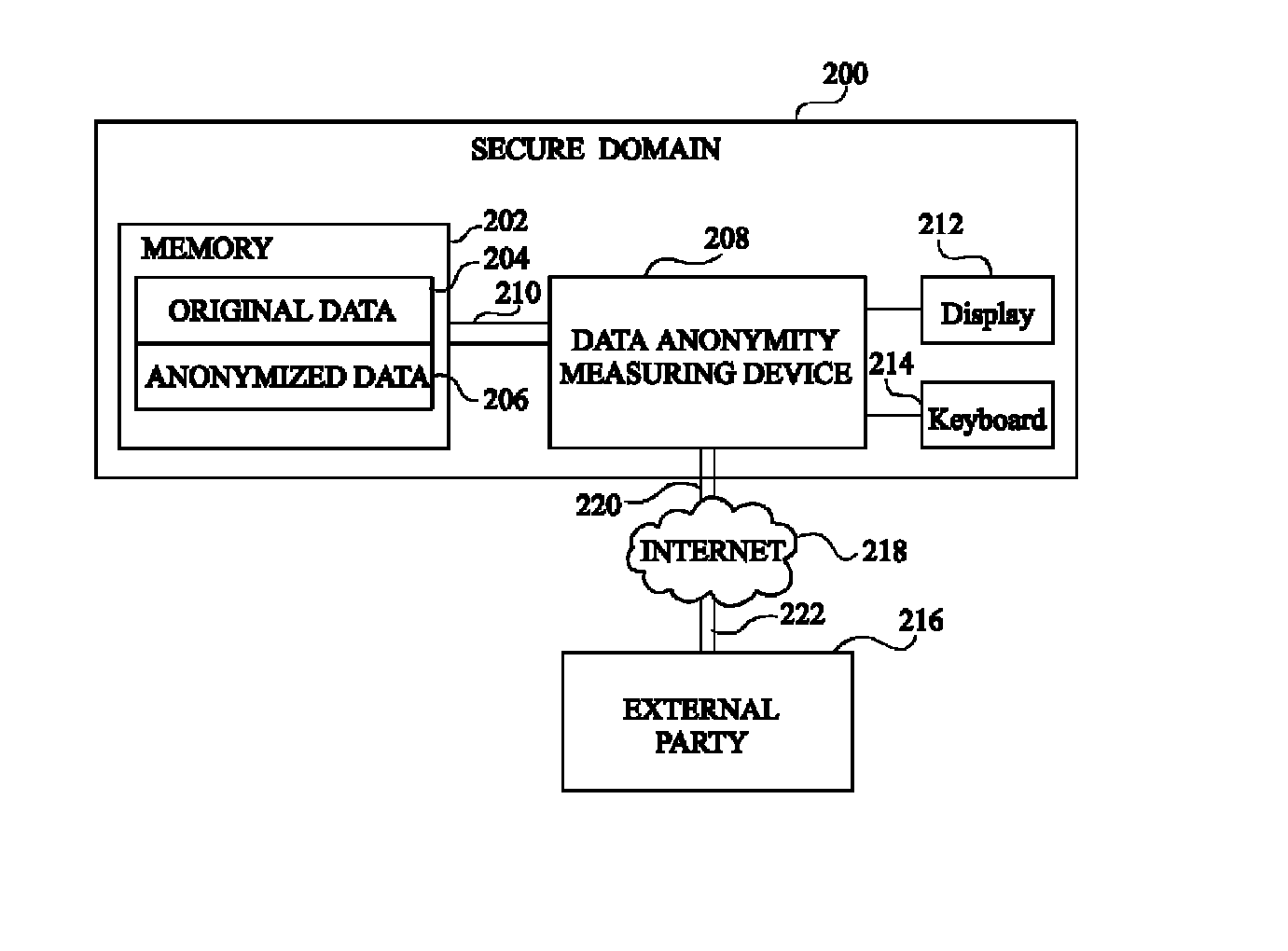
Anonymity measuring device
The invention concerns a data anonymity measuring device for selectively transmitting an anonymised database to a third party comprising: calculation means (402) coupled to at least one memory, the memory storing an original database (204) and said anonymized database (206), said calculation means arranged to calculate the conditional entropy for each entry in said anonymized database based on entries in said original database; comparing means (406) arranged to compare at least one of said conditional entropies with a threshold value; and output means (410) arranged to transmit said anonymized database based on the result of said comparison.
Owner:ACCENTURE GLOBAL SERVICES LTD
Data access and anonymity management
Techniques described herein provide data access and data anonymity management within various implementations of content distribution networks. In some embodiments, a data anonymity management system may include multiple different data stores configured to store identity data, user data, and / or linking data, as well as a data anonymity server configured to support data anonymity features such as active user data anonymity, one-way linking and permanently breakable links between user identity data and associated user data. In some embodiments, storage systems and techniques may be used for storing identity data, user data, and link data in multiple different data stores, with different data storage requirements and different processes and policies for data availability, data backup, online disaster recovery, offline storage archiving, and the like. Additionally, cryptographic hash functions may be used to implement one-way encryption between identity data and user data.
Owner:PEARSON EDUCATION
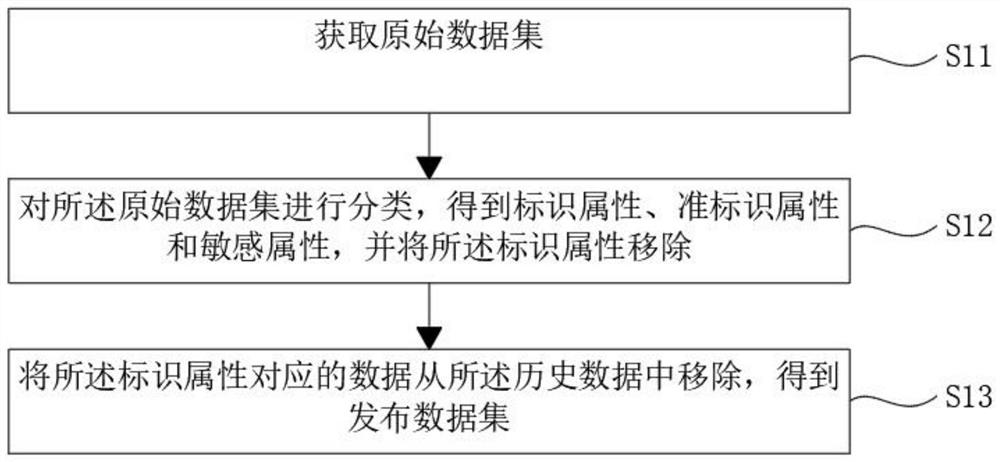
Minimum information loss control method in business data anonymity release
The invention discloses a minimum information loss control method in business data anonymity release. The method comprises the steps that firstly, nonsensitive items in a dataset are generalized to the highest level knot; secondly, privacy checking is performed on the generalized dataset, if the confidence coefficient is larger than a privacy constraint condition p, the current dataset is partially deleted and processed, when the current dataset is partially deleted and processed, privacy checking is constantly called and stopped until the current dataset is in accordance with a data privacy protection anonymity condition, the current dataset which is in accordance with the privacy protection anonymity requirements is transferred to a minimum information control mechanism, and whether grouping and refining continue to be performed or not is determined through the front and back information loss comparison. If the information loss after grouping and refining processing is small, grouping and refining processing continues to be performed, and meanwhile the above process is performed on multiple sub-branch groups formed by one group. If the information loss increases on the contrary after grouping and refining, then the current branch group is directly released.
Owner:北京睿航至臻科技有限公司
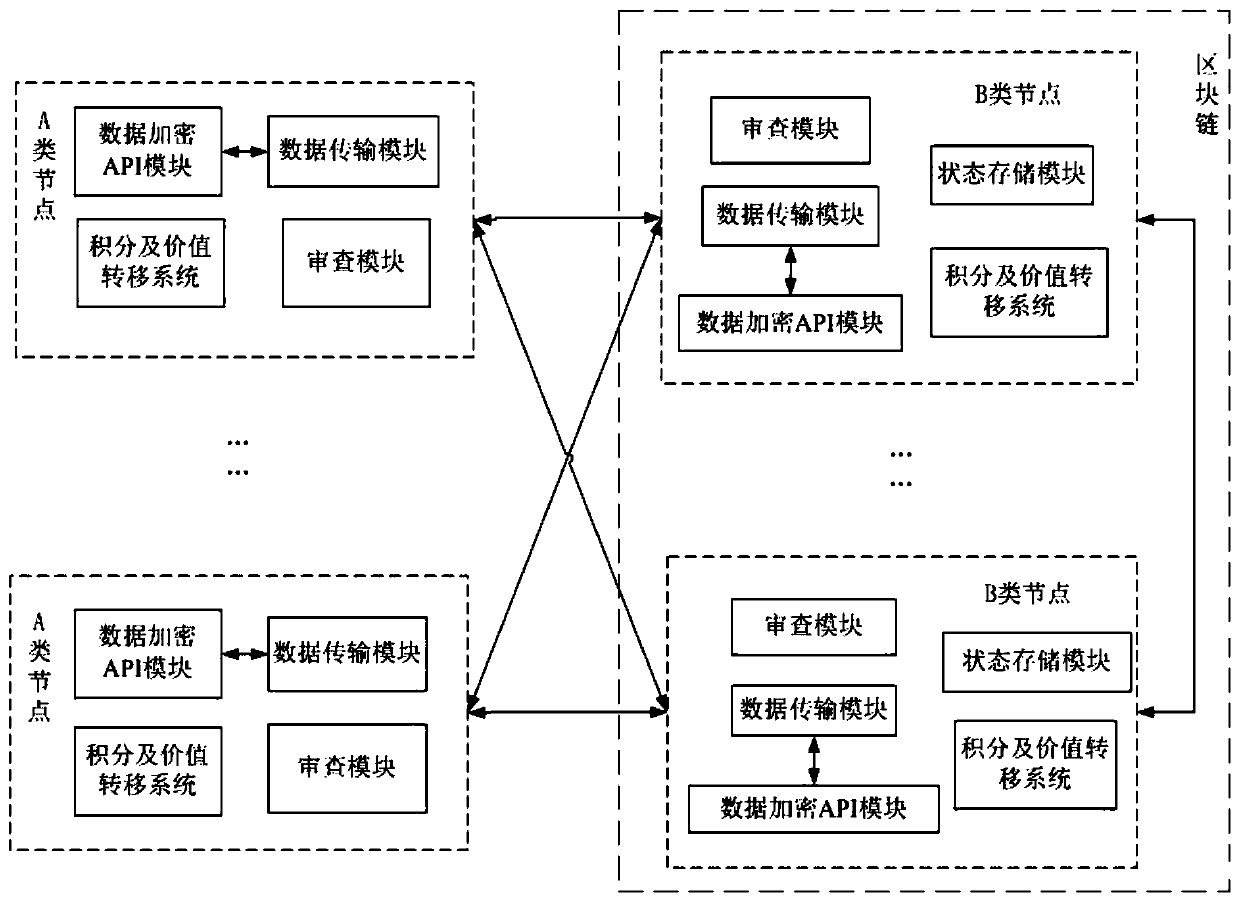
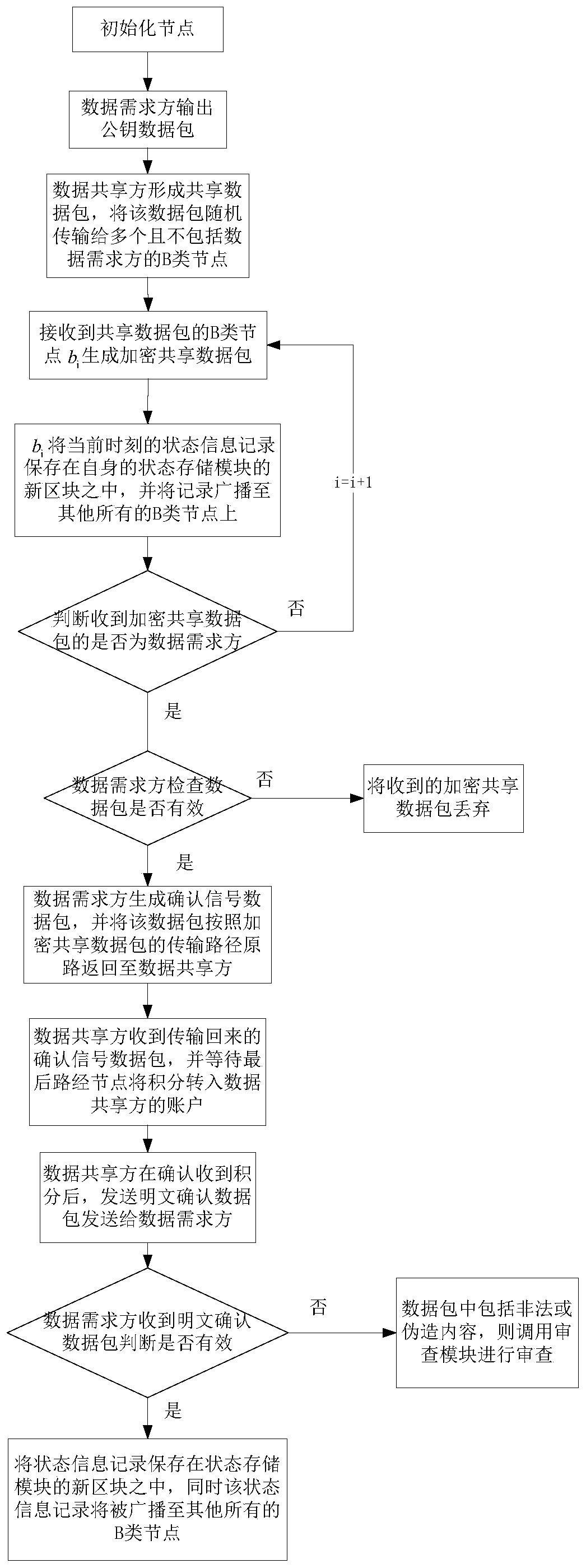
Data anonymity sharing system and method based on block chain
ActiveCN110096894AViolation of authenticityGuarantee authenticityDigital data protectionTransmissionTransfer systemData transport
The invention provides a data anonymity sharing system and method based on a block chain, and relates to the technical field of computers. The system comprises a data demander and a data sharing party, wherein the data demander comprises a plurality of B-class nodes, and the data sharing party comprises a plurality of A-class nodes; the nodes are mutually connected, and a block chain is established between the B-class nodes; a program running on each node comprises a data transmission module, an integral and value transfer system, an examination module and a data encryption API module; and theB-class node also comprises a state storage module. According to the method, the privacy of a user and the reliability of data can be guaranteed to the maximum extent, the user can obtain a certificate, and information leakage is avoided.
Owner:NORTHEASTERN UNIV LIAONING
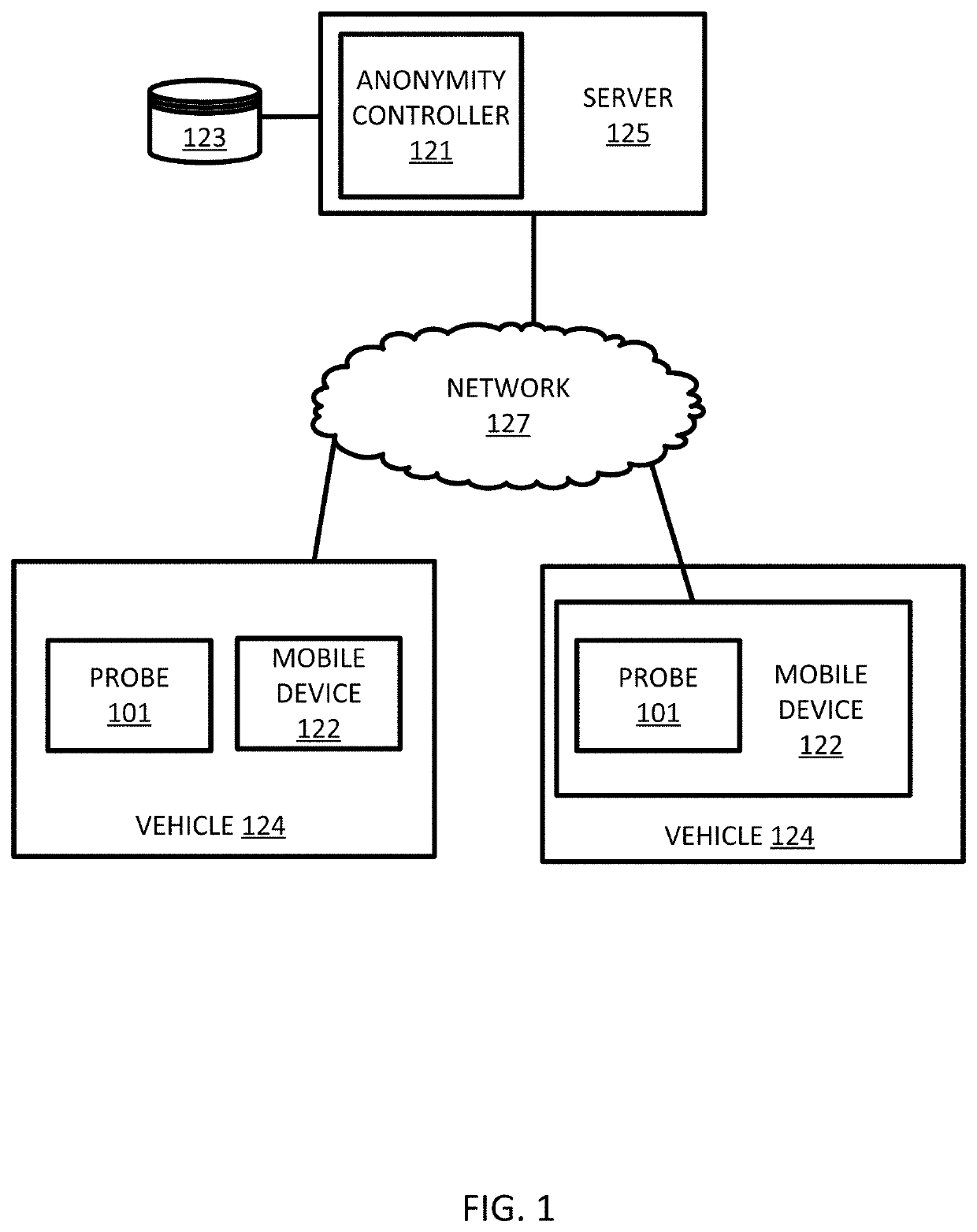
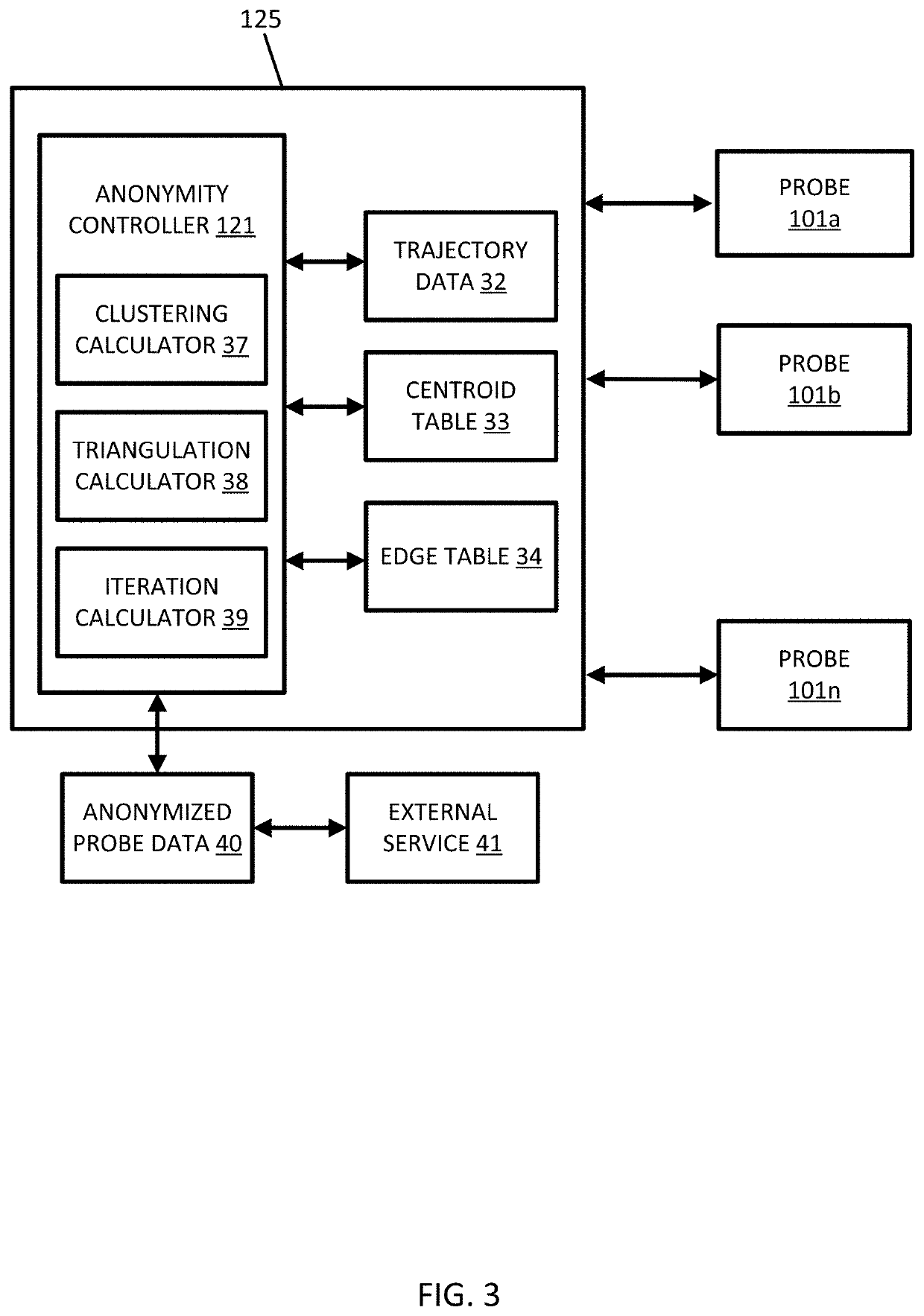
Triangulation for k-anonymity in location trajectory data
ActiveUS20200019585A1Particular environment based servicesRelational databasesGeographic regionsAlgorithm
An apparatus for providing anonymity in geographic data for probe devices in a geographic region for a location-based service includes at least a database and a triangulation calculator. The database is configured to store trajectory data based on sequences of sensor measurements of the probe devices. The triangulation calculator is configured to calculate triangles from the trajectory data. Each of the triangles is defined by vertices. The triangulation calculator is configured to calculate a similarity score for the vertices based on trajectory data associated with adjacent vertices. At least one vertex is modified in response to the similarity score.
Owner:HERE GLOBAL BV
Anonymity measuring device
The invention concerns a data anonymity measuring device for selectively transmitting an anonymised database to a third party comprising: calculation means (402) coupled to at least one memory, the memory storing an original database (204) and said anonymized database (206), said calculation means arranged to calculate the conditional entropy for each entry in said anonymized database based on entries in said original database; comparing means (406) arranged to compare at least one of said conditional entropies with a threshold value; and output means (410) arranged to transmit said anonymized database based on the result of said comparison.
Owner:ACCENTURE GLOBAL SERVICES LTD
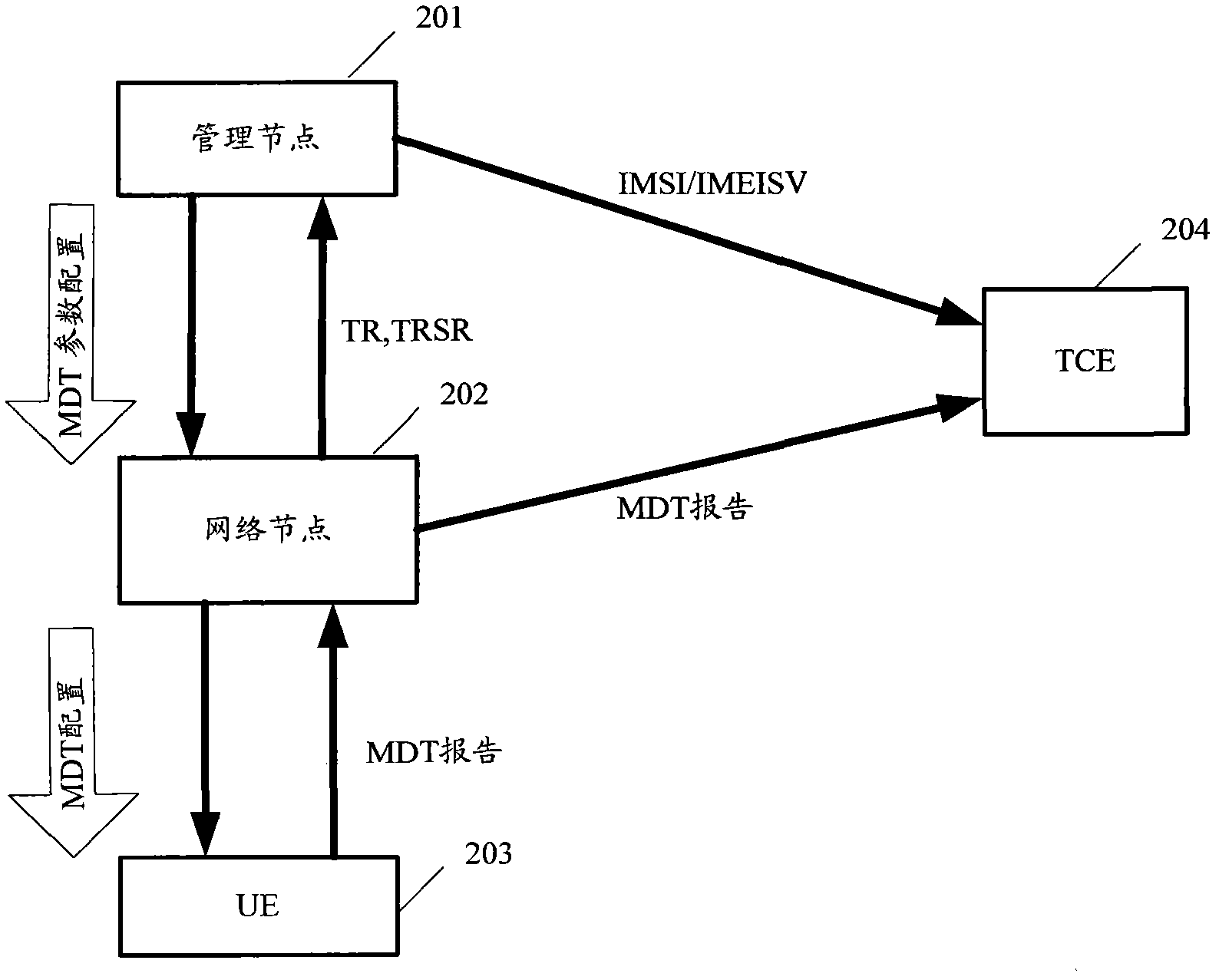
Method of achieving Mobile Data Terminal (MDT) measurement anonymity report
ActiveCN103037428ARealize anonymous reporting of measurementsSecurity arrangementMobile data terminalType Allocation Code
The invention provides a method of achieving a Mobile Data Terminal (MDT) measurement anonymity report. The method of achieving the MDT measurement anonymity report includes that MDT data anonymity configuration information is obtained through a mobile management entity (MME). The MDT data anonymity configuration information is used for indicating whether a type allocation code (TAC) degree is adopted to conduct the MDT measurement anonymity report. When the MDT data anonymity configuration information indicates that the TAC degree is adopted to conduct the MDT measurement anonymity report, then the MME send the TAC of a Users Experience (UE) to the TCE. Under other conditions such as Trace, the MME sends the International Movable Subscriber Identity (IMSI) or International Movable Equipment Identity Software Version (IMEISV) of the Internet Explorer (LE) to the TCE. The method of achieving the MDT measurement anonymity report is capable of sending various UE marks to the TCE according to various anonymity requirements and therefore achieves the MDT measurement anonymity report.
Owner:BEIJING SAMSUNG TELECOM R&D CENT +1
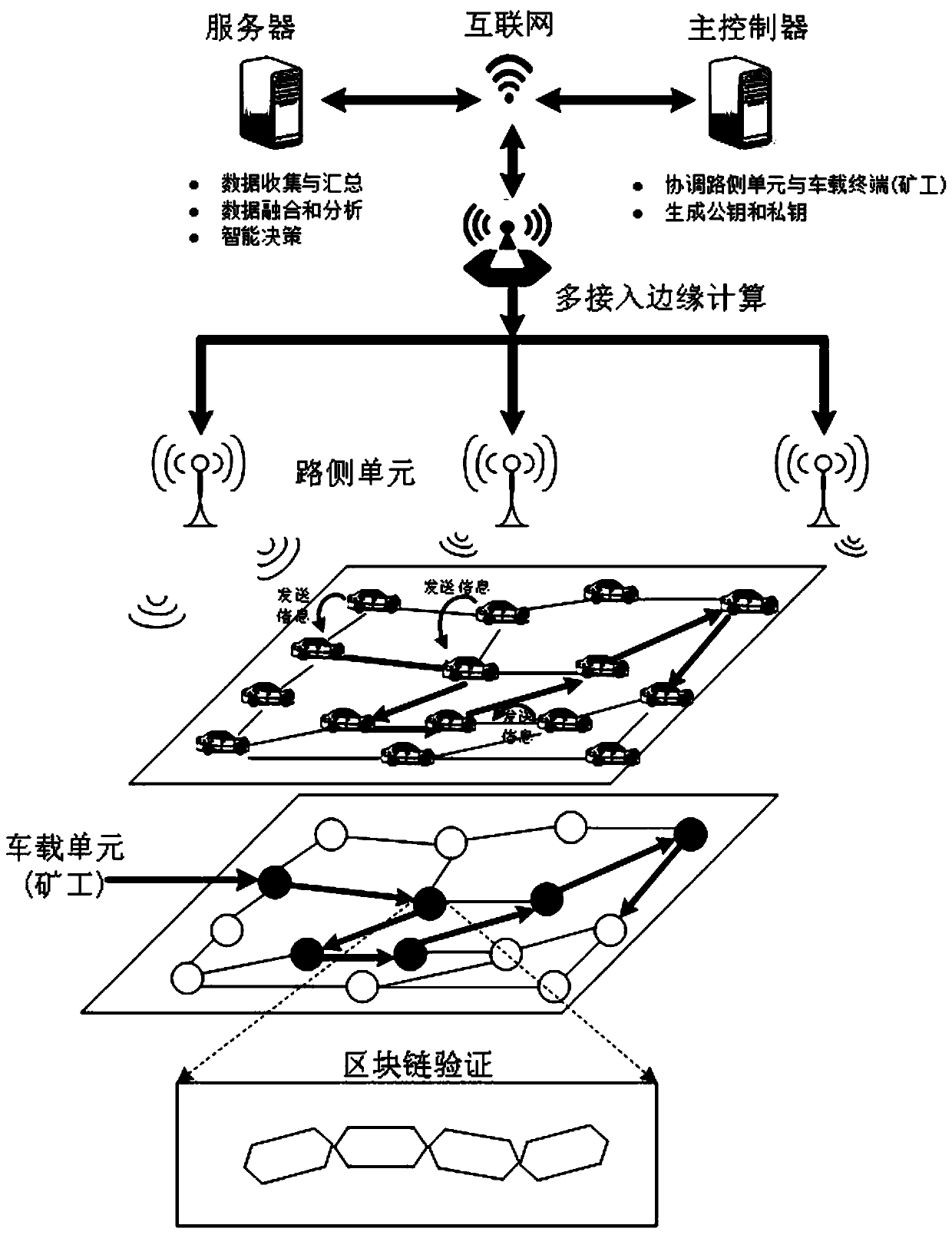
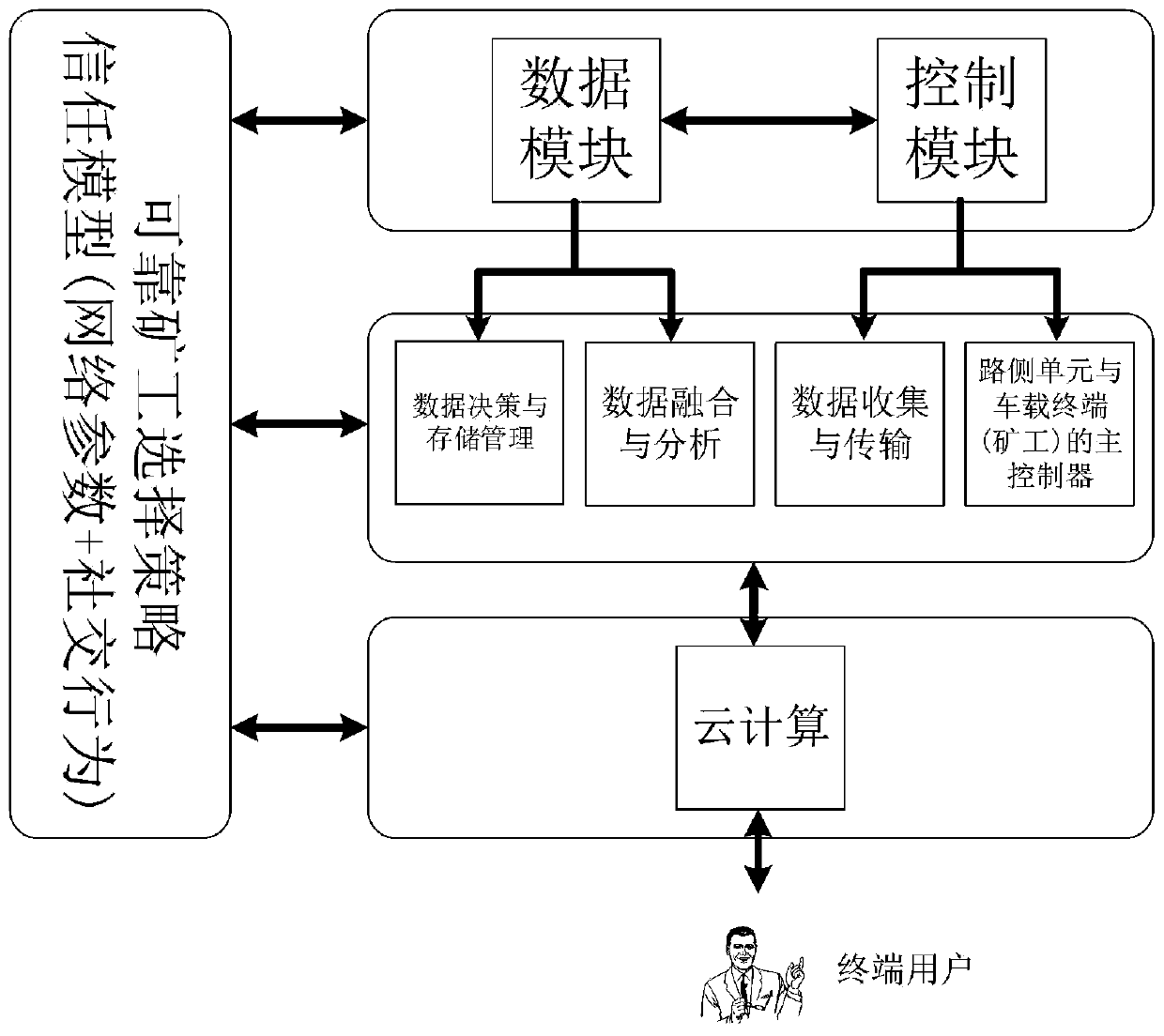
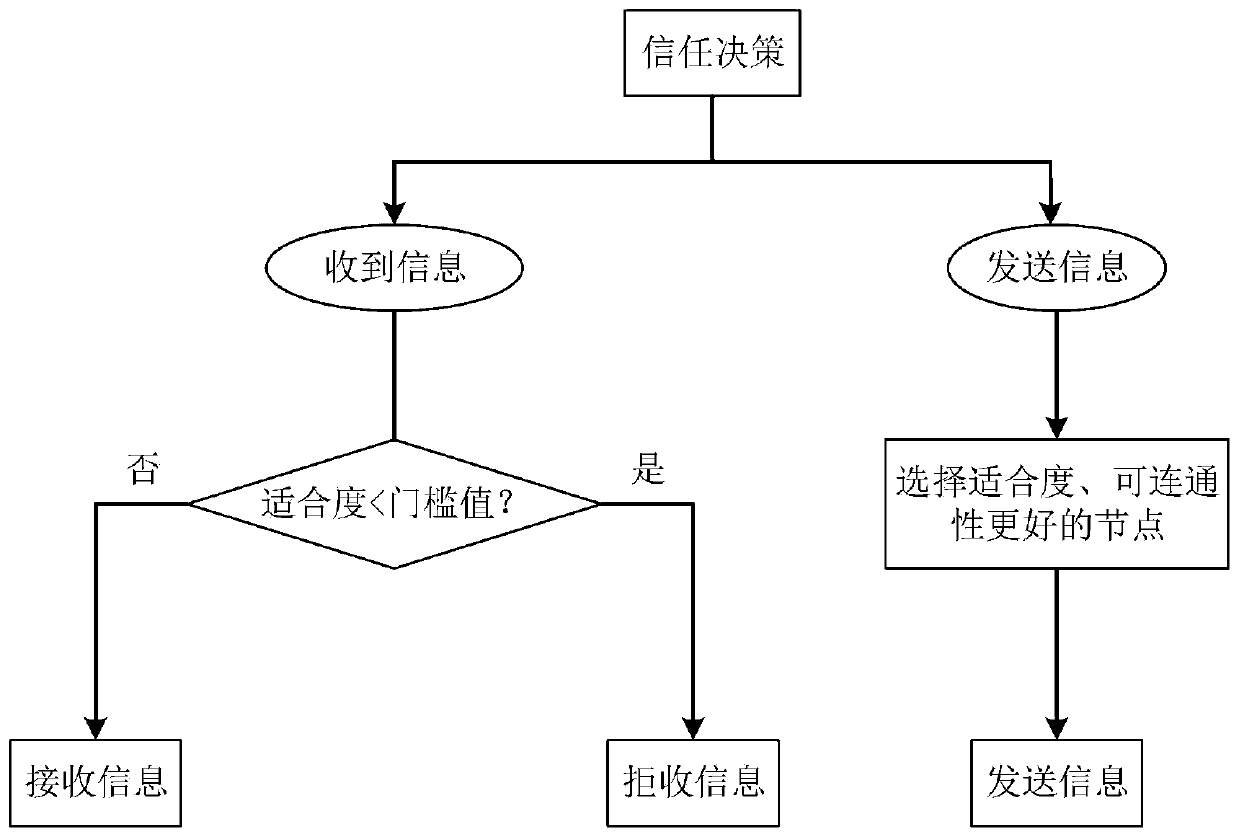
Block chain technology-based secure Internet of Vehicles social network construction method
ActiveCN111064800AImprove vulnerabilityImprove securityData switching networksVirtualizationIn vehicle
The invention discloses a block chain technology-based secure Internet of Vehicles social network construction method. The whole network comprises a main controller, a road side unit and a local controller (vehicle-mounted miner) three-level architecture, the characteristics of programmability, virtualization and zoning of the network are enhanced by using a software definition means, but the vulnerability of a network single-point fault can be caused. According to the invention, with the assistance of the blockchain technology, transaction authentication is realized and data anonymity is realized in a completely distributed manner by a trust degree algorithm-based system consensus mechanism design and a reliable miner selection method, so that the security of the system is ensured.
Owner:HANGZHOU YUNXIANG NETWORK TECH
Methods and apparatus for anonymising user data by aggregation
In a method of anonymising user data by aggregation, at least one server-side device (1) receives an anonymous aggregation command from a user client device (2). The anonymous aggregation command includes a specification of a set of users and an action to be taken. A list of users who meet the specification in the anonymous aggregation command is generated. The list of users who meet the specification is validated as meeting at least one criterion for anonymous aggregation. The action in the anonymous aggregation command is triggered to be taken in respect of the validated list of users who meet the specification.
Owner:BLACKBERRY LTD
Multi-domain data privacy protection method for cloud platform
ActiveCN110378148AMeet needsReduce the risk of privacy breachesDigital data protectionData privacy protectionOriginal data
The invention discloses a multi-domain data privacy protection method for a cloud platform, and relates to the technical field of multi-domain data privacy protection. The method aims to solve the problems that an existing multi-domain data privacy protection method generally adopts static anonymity to publish data, is not flexible enough, cannot limit the data range obtained by data analysts andcannot meet the requirement for using original data. The method comprises the steps of data anonymization treatment and original data recovery treatment. The invention aims at specific requirements indata analysis and transaction processing scenes. Corresponding privacy protection strategies are adopted. For structured data tables in different fields, the effect of reducing the cloud data privacyleakage risk is achieved through a privacy protection technology taking data anonymity as a main body. Meanwhile, certain transaction processing requirements are met. The anonymized data is stored and used for data analysis, so that the risk of privacy information leakage is reduced. The data is dynamically anonymized. The data range which can be obtained by data analysts is limited. Meanwhile, the data privacy is better protected.
Owner:HARBIN INST OF TECH
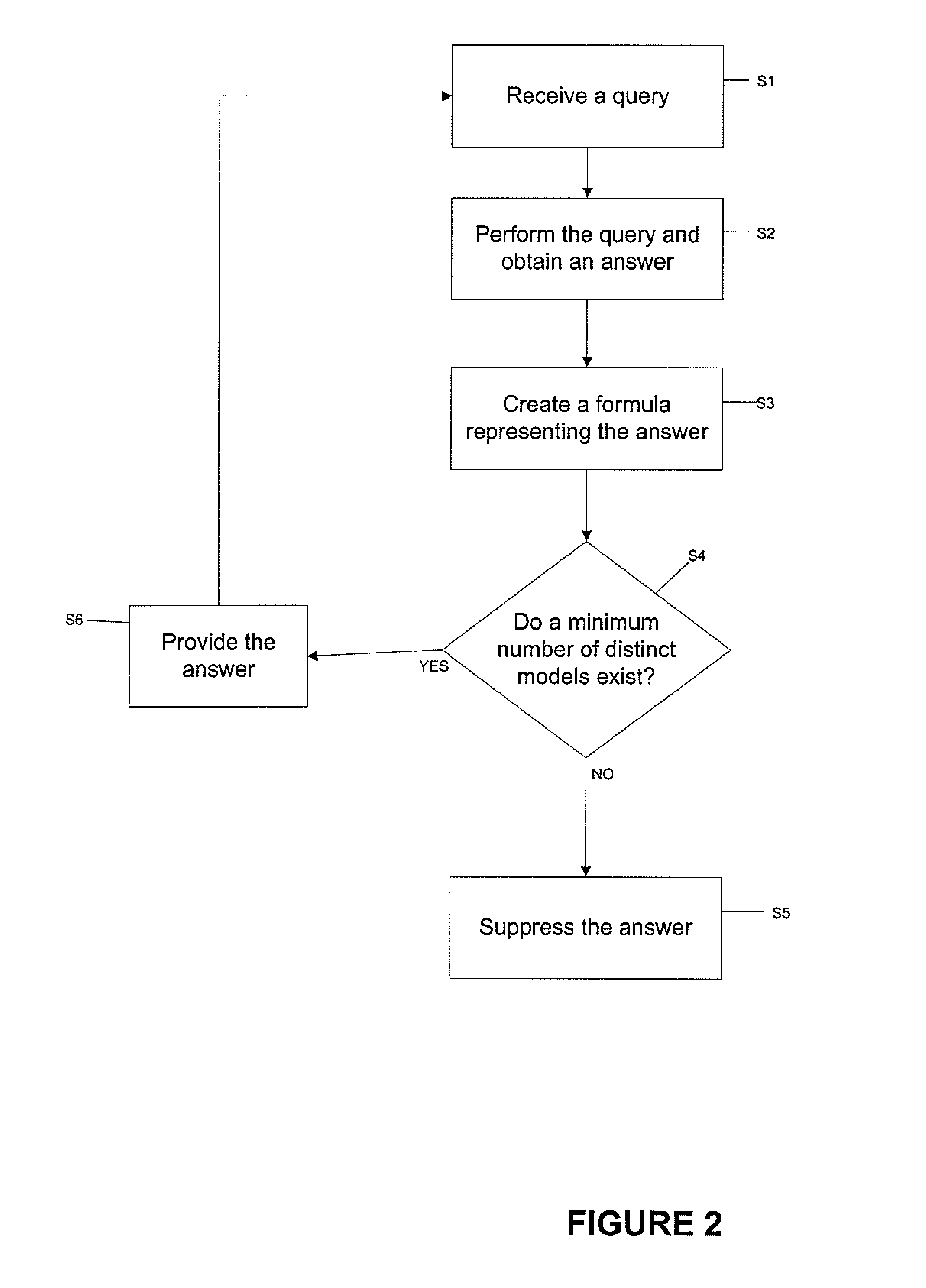
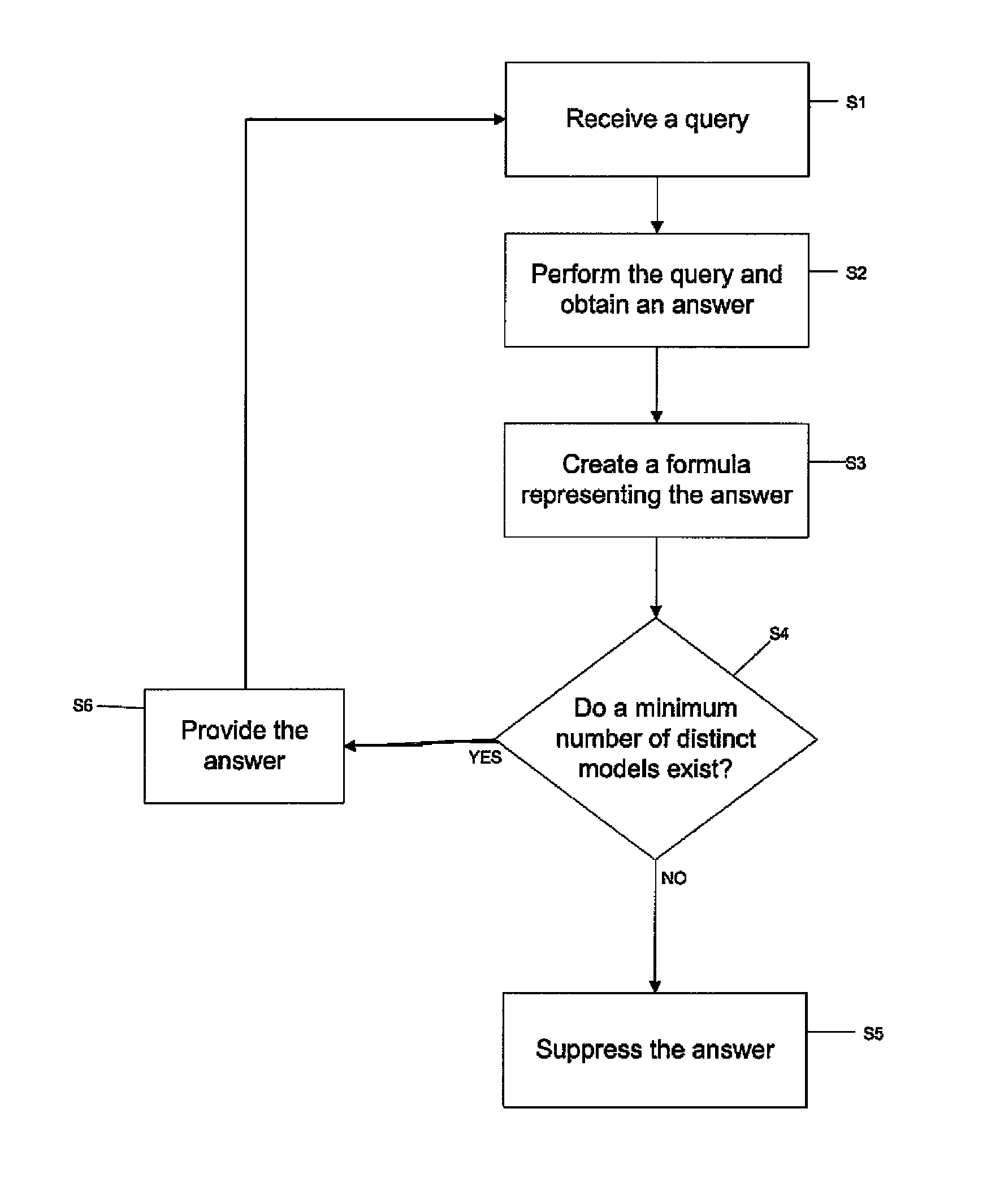
Model-theoretic approach to data anonymity and inference control
ActiveUS20130124452A1Accurate specificationsDigital data information retrievalSoftware engineeringPrior informationData management
A system and method for secure data management is presented. The method comprises receiving a query, performing the query and obtaining answers to it, creating certain formulas representing the answers; and determining whether there is a minimum number of distinct models of these formulas conjoined with the relevant anonymity predicates along with previous answers and general background knowledge, and when that number of models does not exist, suppressing the answers. In one aspect, the method further comprises creating formulas encoding the information conveyed by the answer; and combining the formulas encoding the information with prior information.
Owner:TELCORDIA TECHNOLOGIES INC
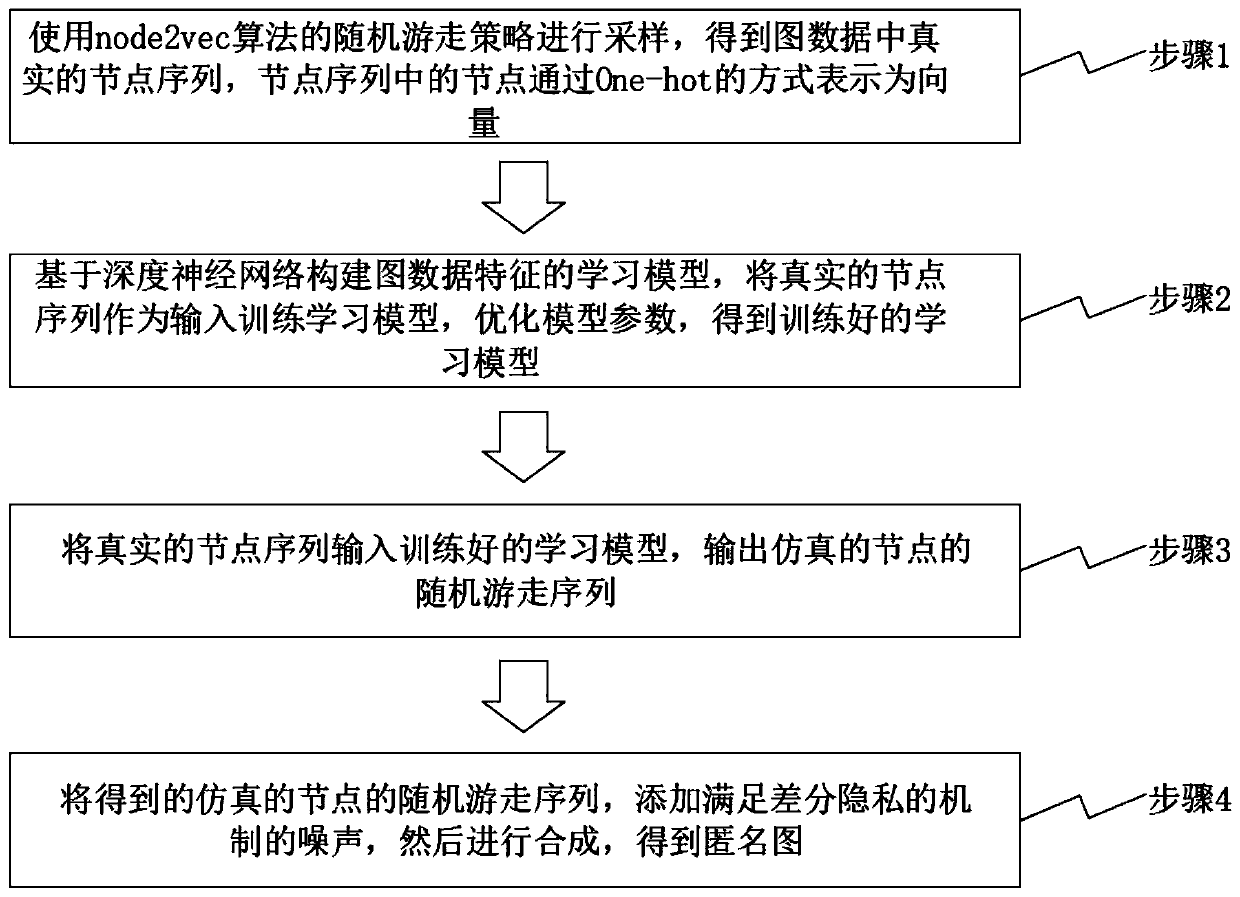
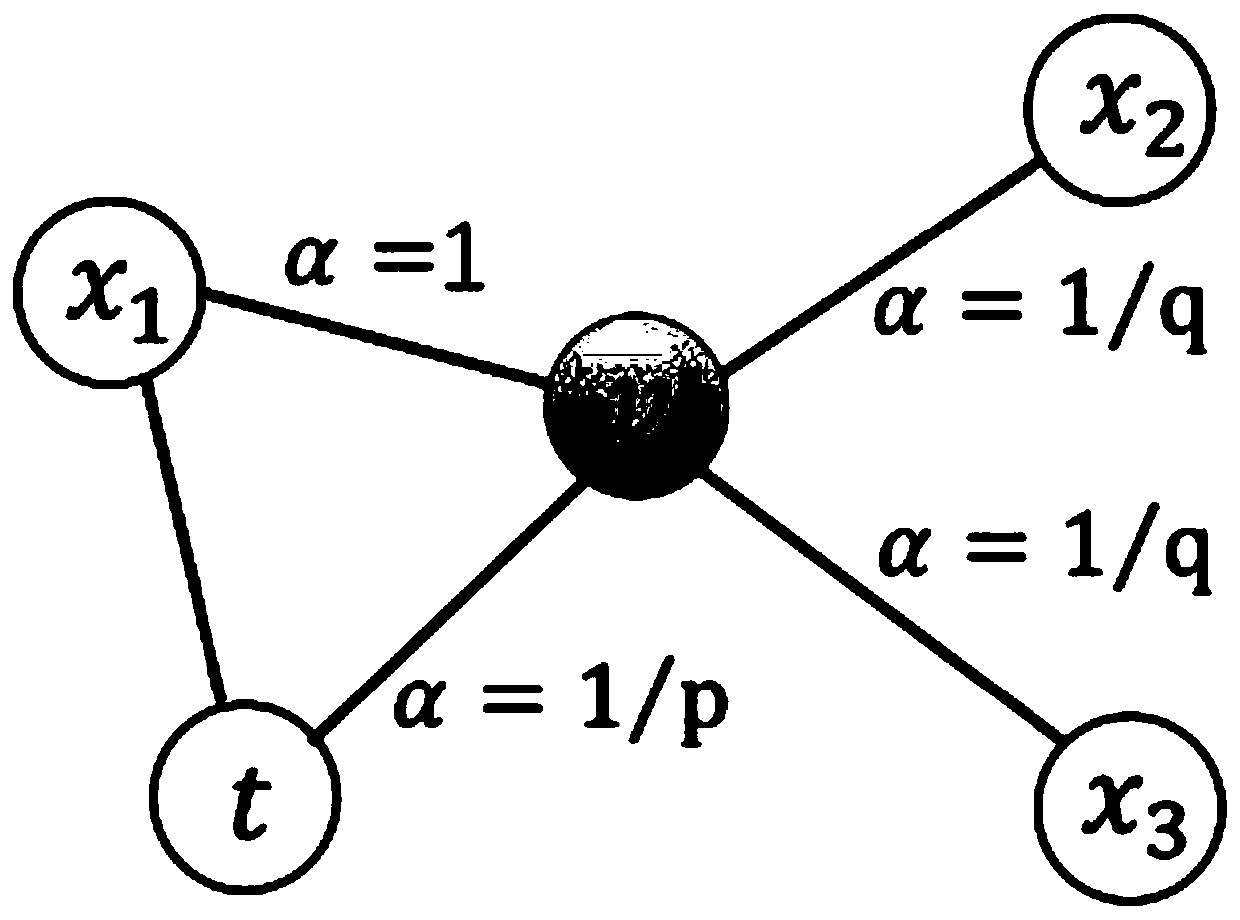
Graph data anonymization method and device based on deep neural network, and storage medium
PendingCN111475838AImprove data availabilityGuaranteed anonymityDigital data protectionNeural architecturesDifferential privacyEngineering
The invention provides a graph data anonymization method and device based on a deep neural network and a storage medium. According to the method, an anonymous graph with high anonymity and high data availability can be generated for data release, and the method comprises the following steps: 1, sampling by using a random walk strategy of a node2vec algorithm to obtain a real node sequence in graphdata, and representing nodes in the node sequence as vectors in an One-hot manner; 2, constructing a learning model of graph data features based on a deep neural network, training the learning modelby taking a real node sequence as input, and optimizing model parameters to obtain a trained learning model; 3, inputting a real node sequence into the trained learning model, and outputting a randomwalk sequence of the simulated nodes; 4, adding noise meeting a differential privacy mechanism to the obtained random walk sequence of the simulated node, and then performing synthesis to obtain an anonymous graph.
Owner:NAT UNIV OF DEFENSE TECH
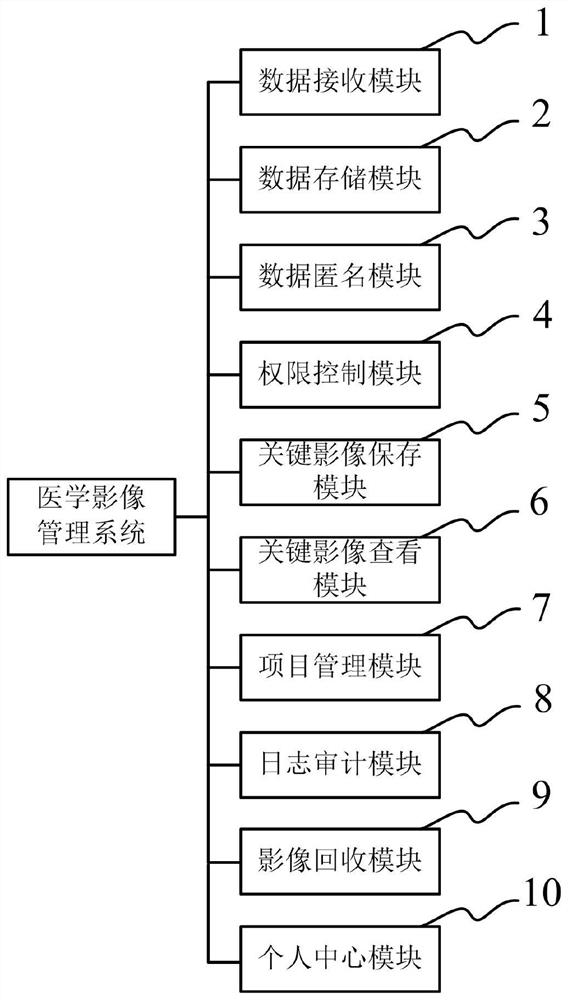
Personalized medical image management system
The invention discloses a personalized medical image management system. The system comprises a data receiving module, a data storage module, a data anonymity module, an authority control module, a keyimage storage module, and a key image viewing module; the data receiving module is used for receiving a DICOM image file corresponding to primary image examination and associating the DICOM image file with an item to which the DICOM image file belongs; the data storage module is used for importing and storing the DICOM image file; the data anonymity module is used for anonymously processing the patient name, the patient number, the gender, the birth date and the hospital name in the DICOM image file; the authority control module is used for an administrator to set a specific film reader of the item, specific authority of each film reader, a specific quality inspector and specific authority of the specific quality inspector; the key image storage module is used for storing key image information formed after the DICOM format image is marked, measured and processed by the film reader, and the key image information comprises a key image, marking time and a marker; and the key image viewing module is used for viewing the stored key image information by the film reader and the quality inspector according to the corresponding authority.
Owner:杭州英放生物科技有限公司
Data processing method and device for realizing privacy protection
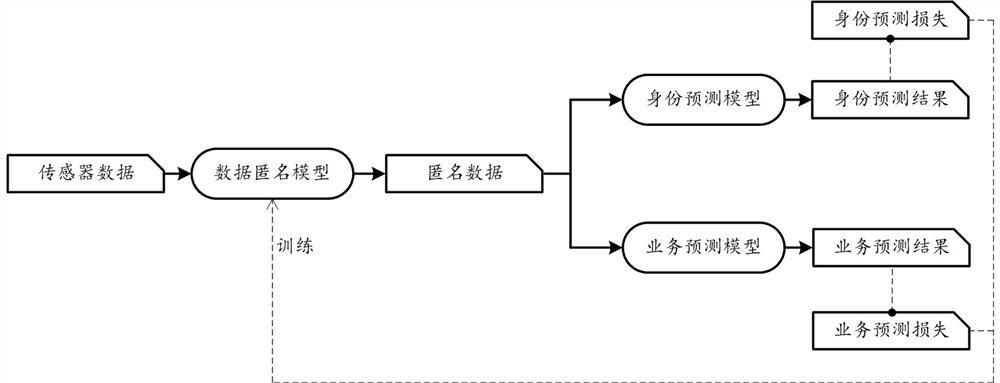
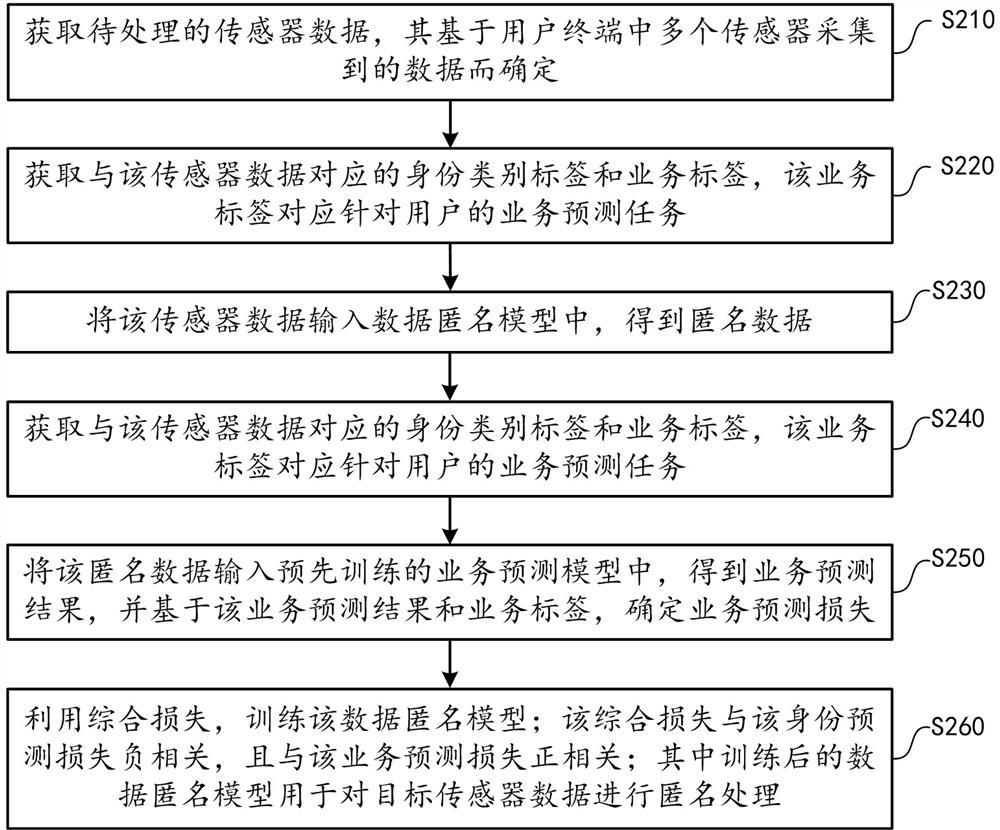
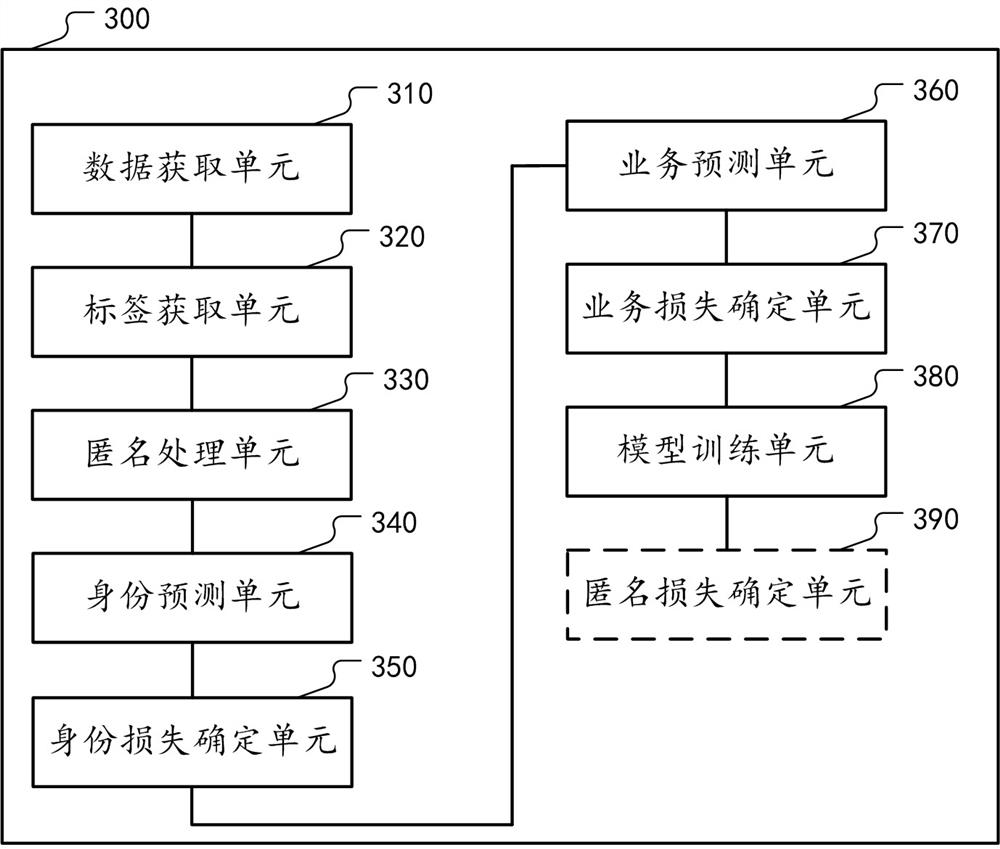
ActiveCN111523146ARealize anonymizationPrevent leakageDigital data protectionMachine learningIdentity recognitionPrivacy protection
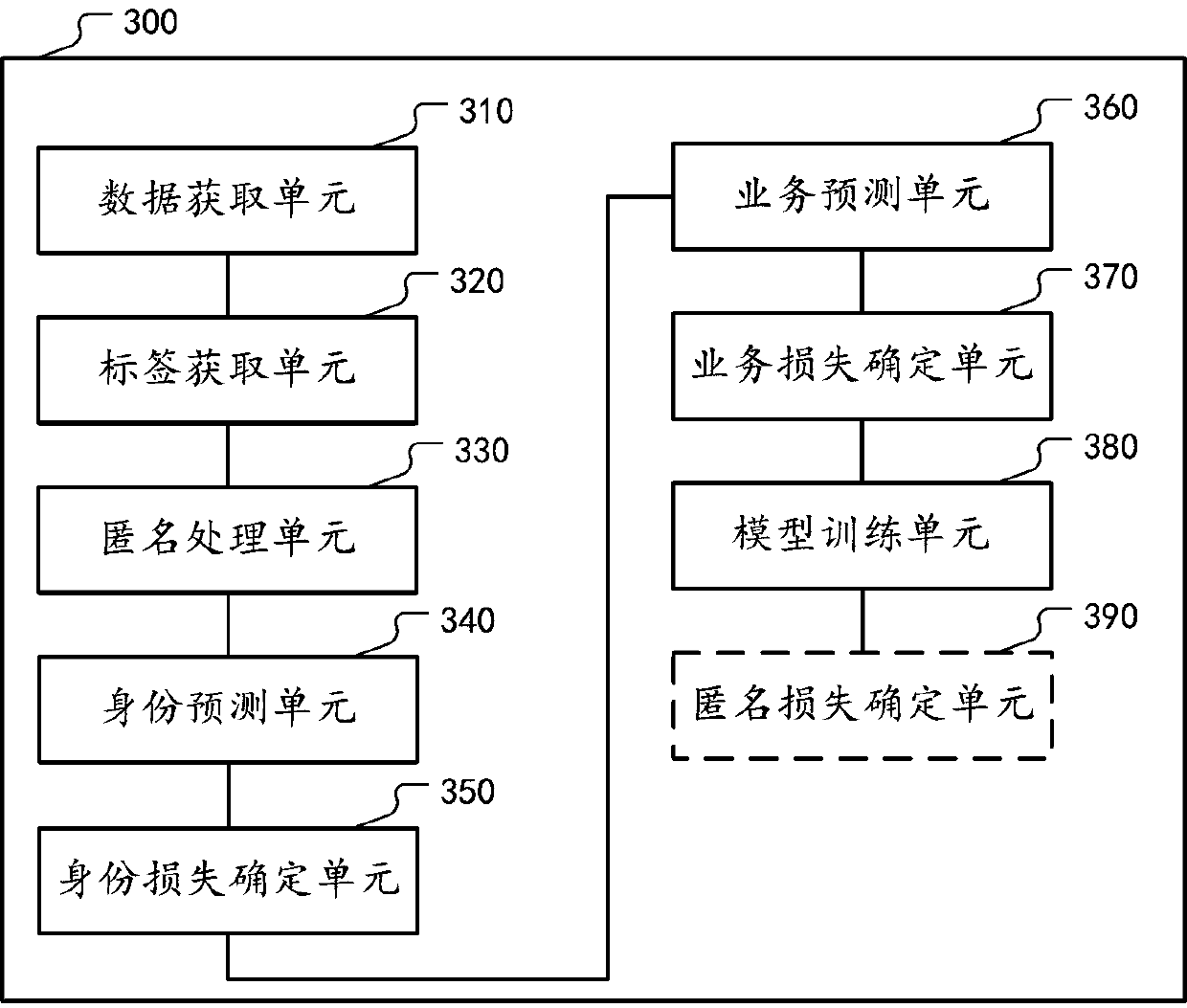
The embodiment of the invention provides a data processing method for realizing privacy protection, and the method comprises the steps: obtaining to-be-processed sensor data, a corresponding identitytype label and a service label, wherein the service label corresponds to a service prediction task for a user; then, inputting the sensor data into a data anonymity model to obtain anonymity data; furthermore, on one hand, inputting the anonymous data into a pre-trained user identity recognition model to obtain an identity prediction result, wherein the identity prediction result is used for determining identity prediction loss in combination with an identity category label; on the other hand, inputting the anonymous data into a pre-trained service prediction model to obtain a service prediction result, wherein the service prediction result is used for determining service prediction loss in combination with the service label; then, training the data anonymity model by utilizing the comprehensive loss; wherein the comprehensive loss is negatively correlated with the identity prediction loss and positively correlated with the service prediction loss; wherein the trained data anonymity model is used for carrying out anonymity processing on the target sensor data.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
Track data anonymity removing method based on deep learning
ActiveCN110502919AImprove performanceCharacter and pattern recognitionDigital data protectionData setDe-anonymization
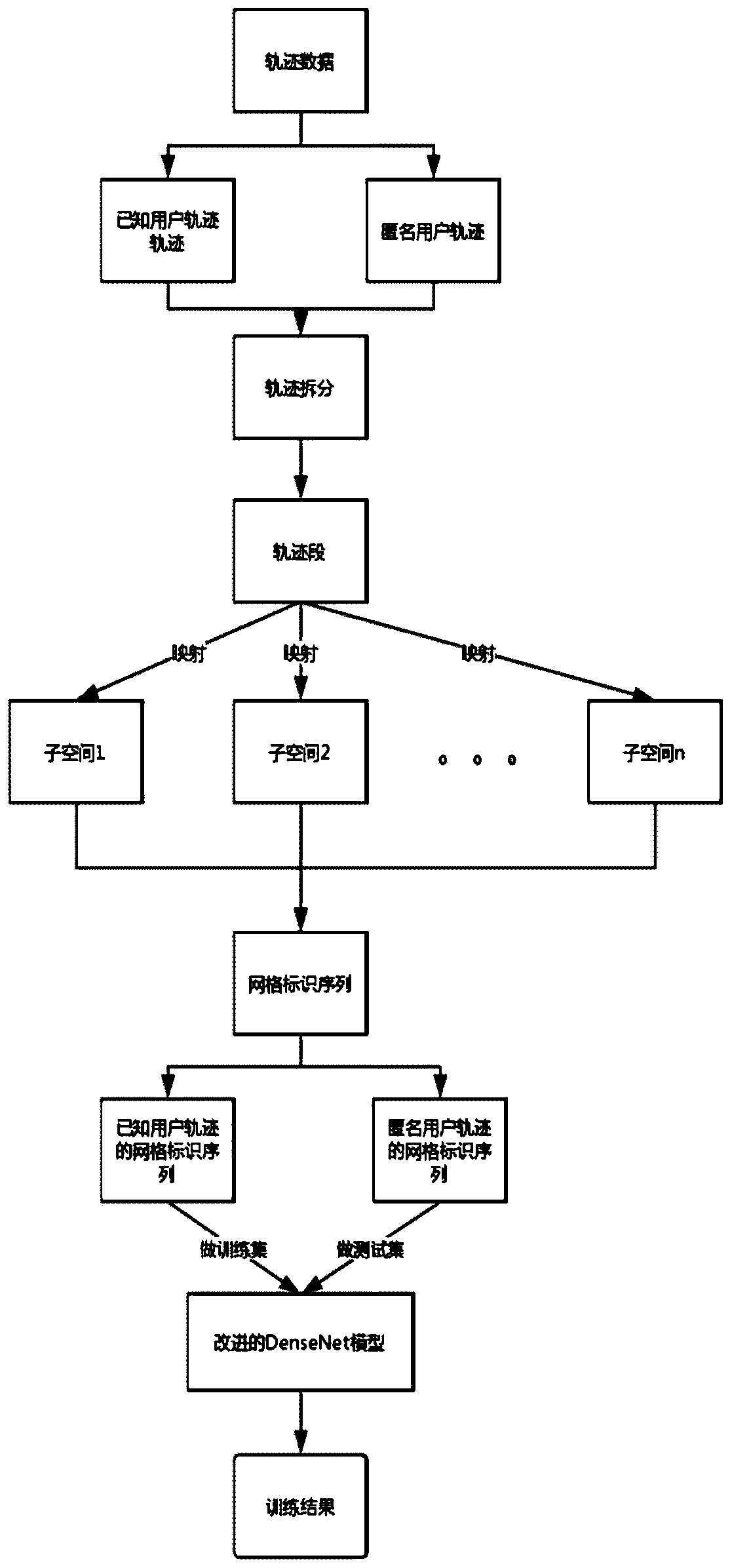
The invention discloses a track data anonymity removing method based on deep learning, which comprises the following steps: firstly, under preset division precision, dividing a space into a pluralityof subspaces similar to a grid shape; dividing the trajectory data into two groups, one group being a known user trajectory and the other group being an anonymous user trajectory; splitting the two groups of trajectories into trajectory segments, and mapping the trajectory segments into grid data to obtain a group of grid identification sequences corresponding to the trajectories; secondly, inputting the set of grid identification sequences in the previous step into an improved DenseNet model, taking a known user track as a training set, and taking an anonymous user track as a test set; finally, classifying the tracks through a model, enabling the anonymous data to correspond to data in a known user data set, and finding out real user information corresponding to the anonymous user track data. According to the invention, the de-anonymization of the private trajectory data is realized to verify the effectiveness of the attack, so that the privacy risk of the anonymous trajectory data isrevealed.
Owner:WUHAN UNIV OF TECH
Differential privacy protection method and system for track time mode
ActiveCN111950028APrivacy protectionAccurate timeCharacter and pattern recognitionDigital data protectionTime segmentDifferential privacy
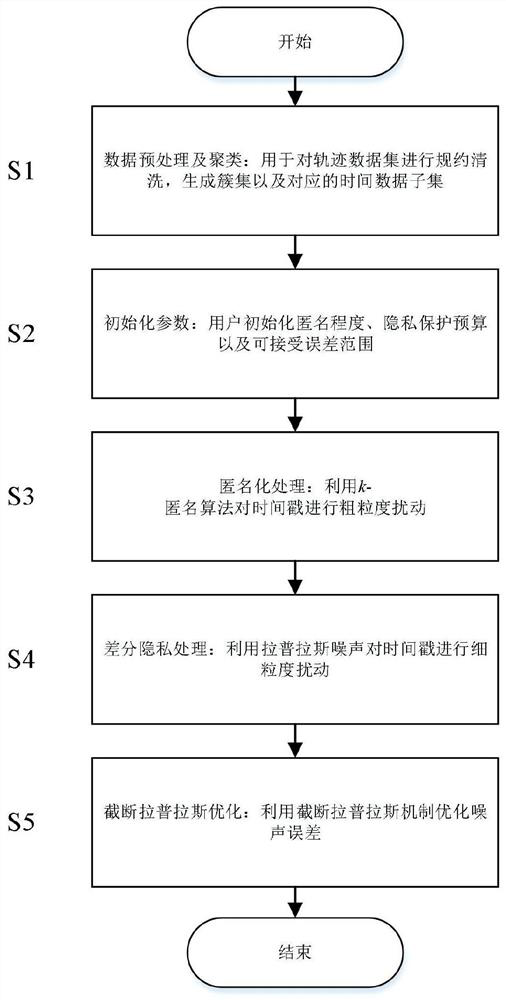
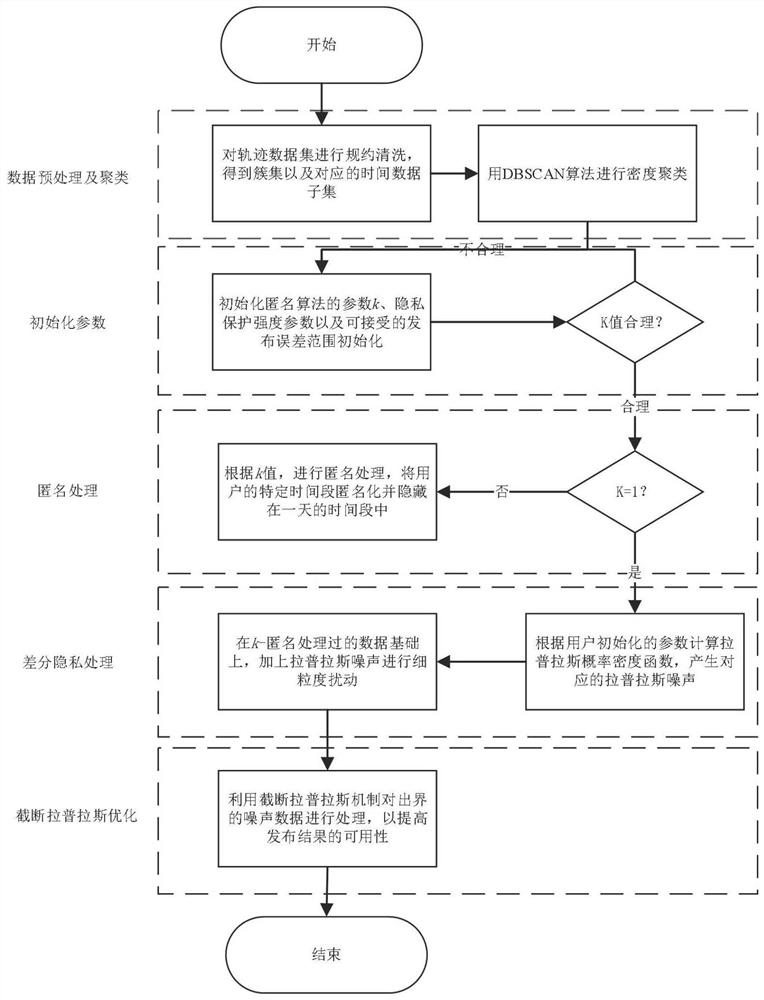
The invention relates to a differential privacy protection method and system for a track time mode, and belongs to the field of data mining. The method comprises the following steps: firstly, based onan anonymization thought, carrying out coarse-grained disturbance on track time data by using kanonymity, and anonymously hiding data in an original single time period into a whole day; then, using aLaplace mechanism for carrying out fine-grained disturbance on a timestamp of a track; and finally, limiting the noise disturbance error within a fixed range based on a truncation Laplace mechanism,thereby improving the precision of the published data. The problem of individual privacy leakage caused by periodicity of the track time mode is solved.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Privacy protection method for data integration of DaaS application
PendingCN110866277APrevent leakageBalanced Value Domain Balanced DistributionDigital data protectionData setPrivacy protection
The invention discloses a privacy protection method for data integration of a DaaS application, and the method comprises the following steps: 1, carrying out the multi-round cooperation among tenantsunder the condition that the anonymity of data is met, and each round employing an attribute plus a fine data set with the maximum information gain; 2, setting reputation levels of the cloud service providers, and dividing the cloud service providers according to the reputation levels; 3, for the cloud service providers with the reputation levels lower than the preset reputation level, using a privacy protection mechanism based on segmentation, hiding the incidence relation between data, ensuring value domain equilibrium distribution of attributes in a grouping equalization mode, and preventing the cloud service providers from leaking data privacy of tenants; and for the cloud service providers higher than the preset reputation level, verifying correctness and integrity of data returned bythe cloud service providers by adopting a classification index tree data structure. According to the method, through a classification index tree data structure, the cloud tenants have the capabilityof verifying the correctness and integrity of a result set returned by the cloud service provider.
Owner:INST OF ELECTRONICS & INFORMATION ENG OF UESTC IN GUANGDONG +1
Model-theoretic approach to data anonymity and inference control
ActiveUS8775364B2Accurate specificationsDigital data information retrievalSoftware engineeringPrior informationTheoretical methods
A system and method for secure data management is presented. The method comprises receiving a query, performing the query and obtaining answers to it, creating certain formulas representing the answers; and determining whether there is a minimum number of distinct models of these formulas conjoined with the relevant anonymity predicates along with previous answers and general background knowledge, and when that number of models does not exist, suppressing the answers. In one aspect, the method further comprises creating formulas encoding the information conveyed by the answer; and combining the formulas encoding the information with prior information.
Owner:TELCORDIA TECHNOLOGIES INC
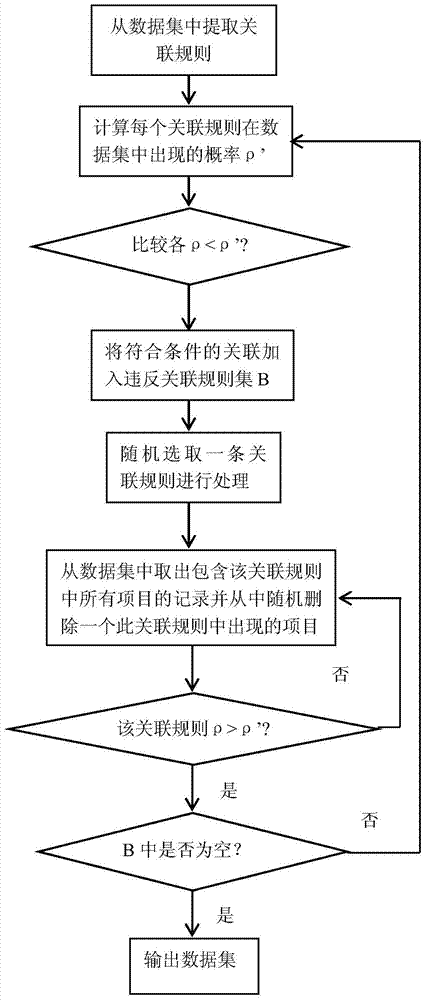
MapReduce-based distributed data anonymity processing method
ActiveCN106599726AEasy to handleImprove efficiencyDigital data protectionPlatform integrity maintainanceData explosionOriginal data
The invention discloses a MapReduce-based distributed data anonymity processing method, which comprises a server side and computer terminals, wherein an original data table is stored in the server side to carry out global generalization on data and give a generalized lattice which is likely to meet k- anonymity; the server side utilizes a method of bisection to allocate a computational node to each computer terminal; each computer terminal carries out computation in parallel and returns a value to the server side according to a computation condition; if the return value does not meet k- anonymity, the server side sends a descendant node determined by the method of bisection to each computer node, otherwise the server side sends an ancestor node determined by the method of bisection to a computer; and each computer terminal recalculates according to a new node given by the server side until all nodes which meet k- anonymity are found. The method solves the trouble between explosive data growth and existing server storage and computational capabilities, and the efficiency of massive data processing is improved.
Owner:徐工汉云技术股份有限公司
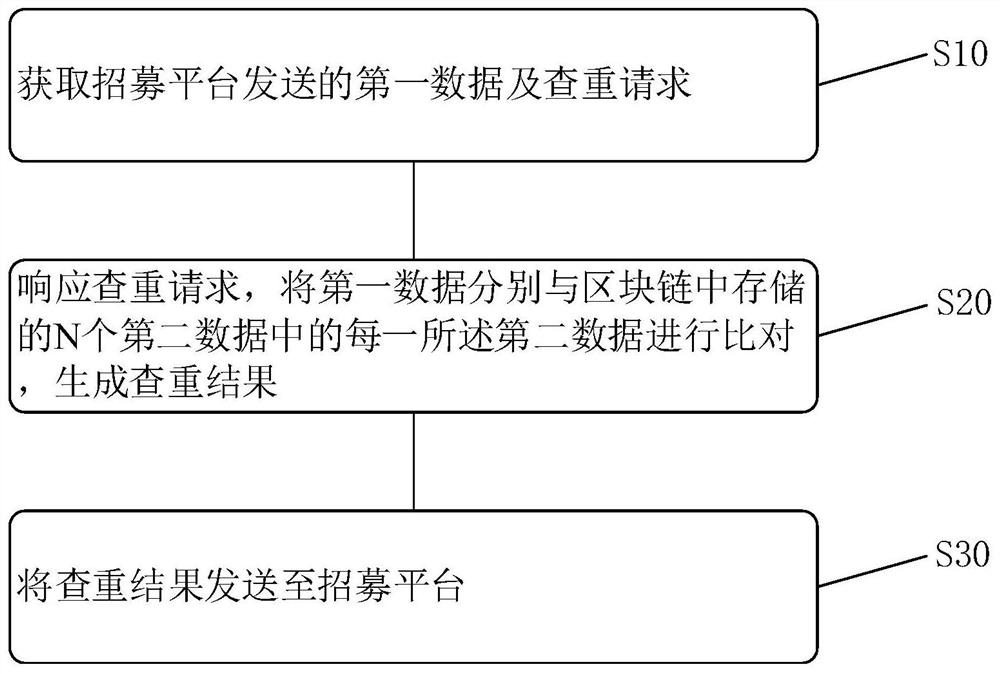
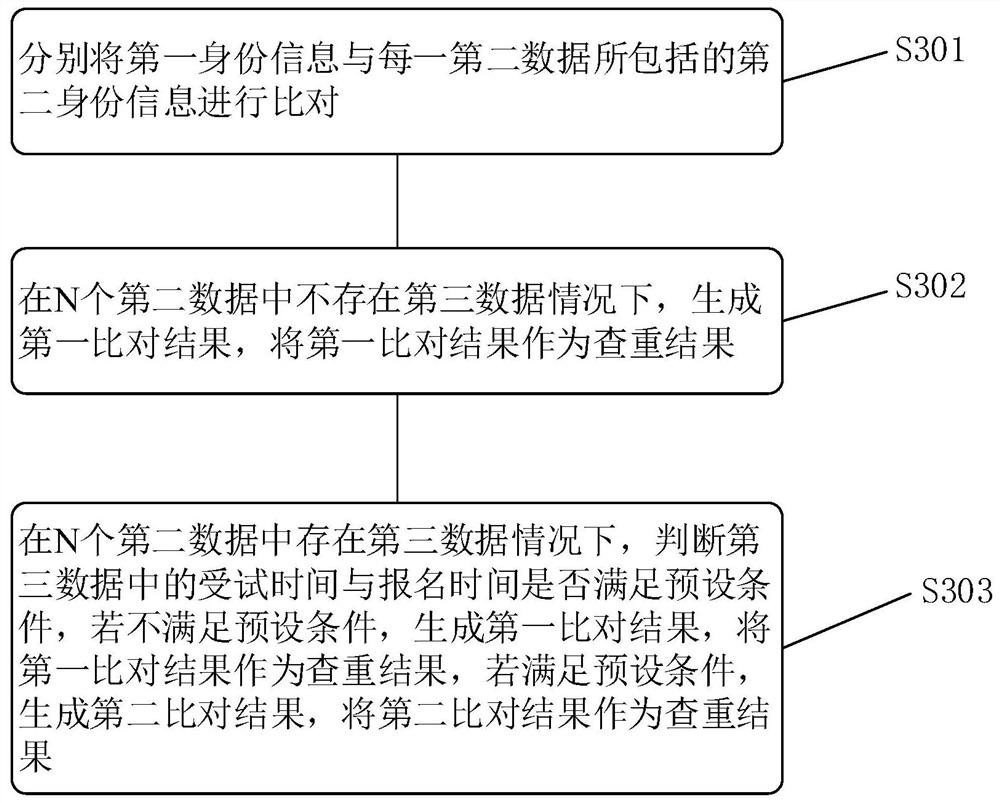
Subject recruitment method and device, terminal equipment, storage medium
ActiveCN111984727BGuaranteed to be true and effectivePrevent leakageDatabase distribution/replicationDigital data protectionMedicineTerminal equipment
This application is applicable to the field of blockchain technology, and provides methods and devices for recruiting subjects, terminal equipment, and storage media. The method for recruiting subjects includes: acquiring first data sent by a recruiting platform, and comparing the first data with each of the second data in N pieces of second data stored in the blockchain to generate a duplicate check As a result, the duplicate check result is sent to the recruitment platform, and the recruitment platform determines whether the applicant meets the recruitment conditions according to the duplicate check result. Based on the decentralization of blockchain and the immutability of data, data can be shared among multiple recruitment platforms through blockchain to determine whether applicants meet the recruitment conditions, and to ensure that the data is authentic and valid. It effectively excludes professional subjects, and based on the data anonymity of the blockchain, multiple recruitment platforms cannot access each other's data, which can prevent information leakage and protect personnel privacy.
Owner:CHANGSHA DUXACT BIOTECH CO LTD +1
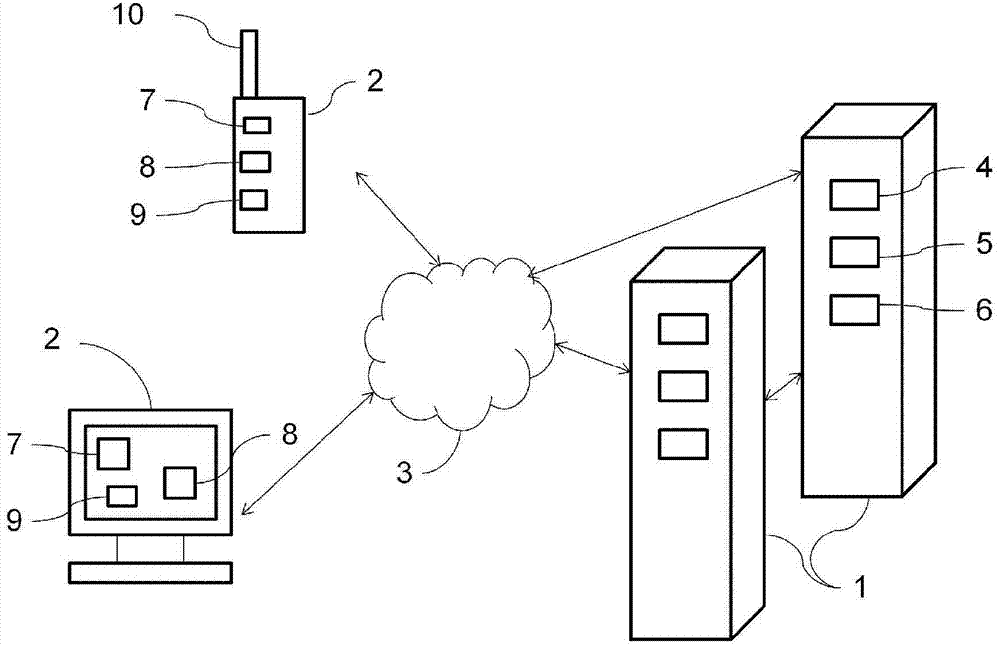
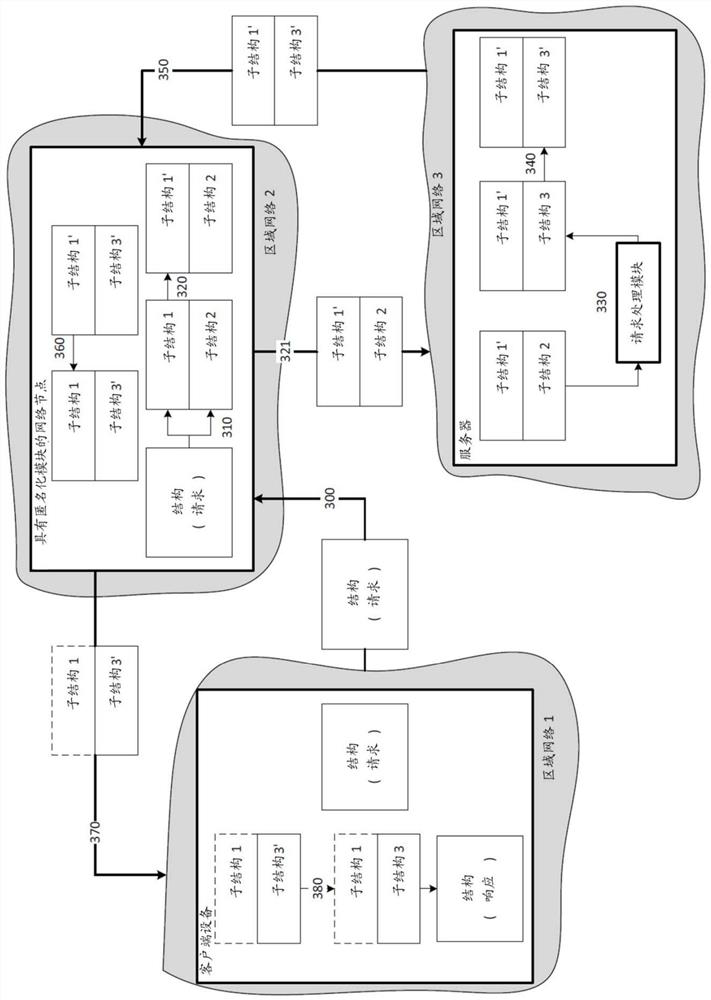
System and method for anonymous and consistent data routing in a client-server architecture
The present invention relates to systems and methods for anonymous and consistent data routing in a client-server architecture. Disclosed herein are systems and methods for sending user data in a client-server architecture with data anonymity and consistency. In an exemplary aspect, a client device may identify a structure to send to a server, where the structure includes user data. The client device may divide the structure into two or more substructures, and for each corresponding substructure in the two or more substructures, the client device may: (1) assign confidentiality to a corresponding a substructure; and (2) sending the corresponding substructure to the corresponding node based on the assigned confidentiality and the security degree of the corresponding node among the plurality of nodes. The respective nodes may be configured to apply the respective transformations to the respective substructures and to transmit the transformed respective substructures to the server. The server is configured to combine the received plurality of transformed substructures into a transformed structure.
Owner:AO KASPERSKY LAB
Anonymous method based on sensitive hierarchical information entropy
PendingCN114580010ASolve the problem of low data availabilityIncrease information entropyDigital data protectionData setData availability
The invention relates to the technical field of data anonymity, in particular to an anonymity method based on sensitive hierarchical information entropy, which comprises the following steps: acquiring a published data set; establishing an anonymous model based on the published data set; establishing an information loss measurement standard model based on the information entropy of the published data set; traversing the published data set based on the information loss measurement standard model to obtain a maximum tuple with the maximum privacy security index, and adding the maximum tuple into a corresponding equivalent group in the anonymous model; and replacing the value of the maximum tuple with the quasi-identification attribute center of the equivalent group to obtain an anonymous data set, and processing the published data set by introducing an information loss measurement standard model established by the information entropy and an anonymous model to obtain the anonymous data with the highest information entropy, namely the highest data availability. The problem that an existing anonymous method is low in data availability after data anonymization is solved.
Owner:GUILIN UNIVERSITY OF TECHNOLOGY
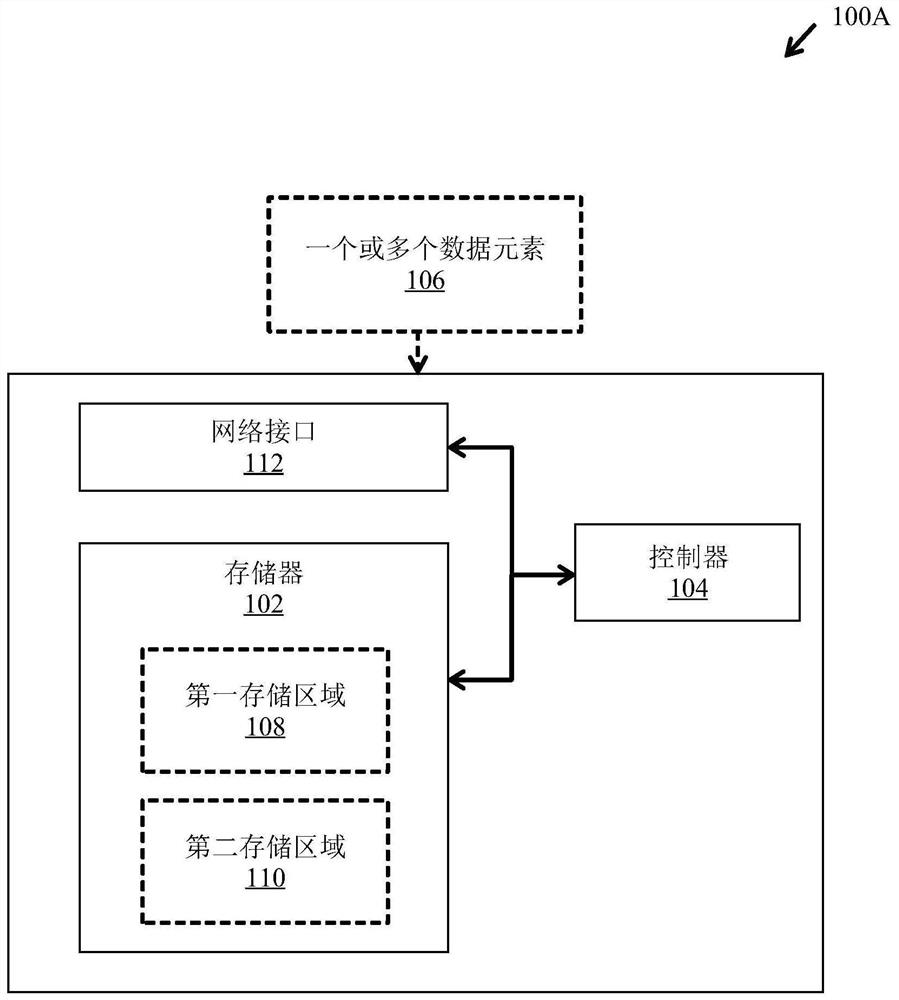
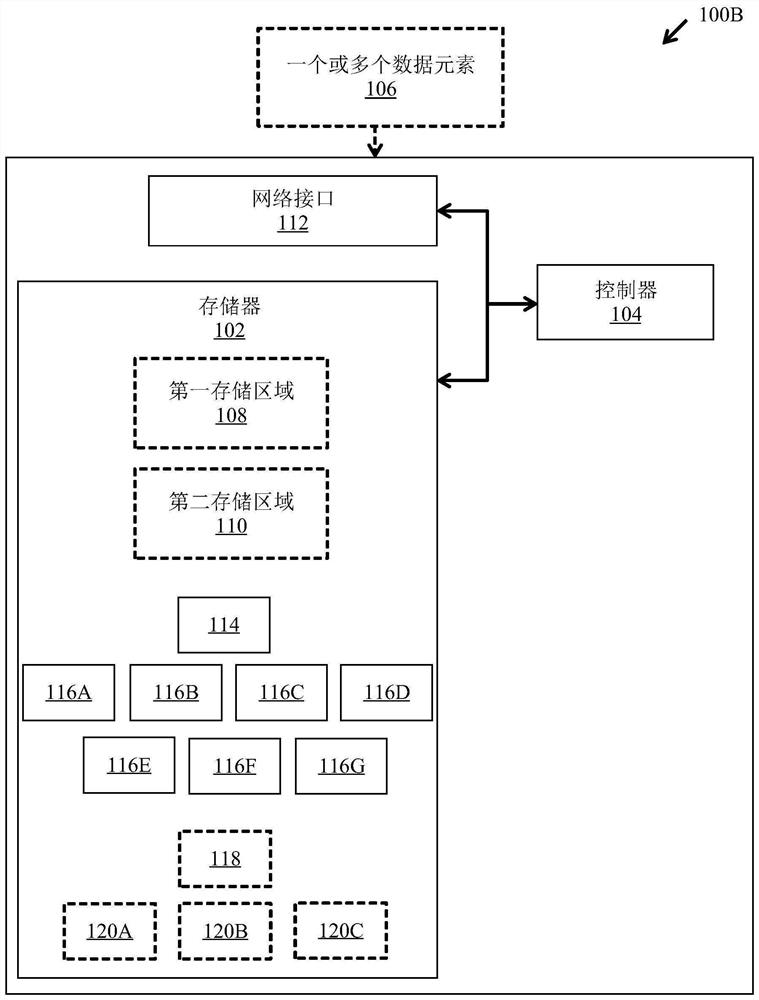
Data storage apparatus and method for anonymously perceiving deduplication
A data storage device includes a memory and a controller, where the controller receives an indication of data to be anonymized. The controller also parses a data element to be stored and generates a copy of one or more data portions to be anonymized. The controller also deletes one or more data portions to be anonymized to generate modified data elements to be stored. The controller also generates a copy of the modified data element to be stored with deduplication. Accordingly, the data storage device takes into account data anonymity (i.e., anonymity-aware deduplication) during deduplication, thereby enabling efficient deduplication even in the presence of anonymous data.
Owner:HUAWEI TECH CO LTD
Data processing method and device for realizing privacy protection
ActiveCN111523146BRealize anonymizationPrevent leakageDigital data protectionMachine learningIdentity recognitionPrivacy protection
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
A distributed data anonymous processing method based on mapreduce
ActiveCN106599726BEasy to handleImprove efficiencyDigital data protectionPlatform integrity maintainanceOriginal dataData explosion
The invention discloses a MapReduce-based distributed data anonymity processing method, which comprises a server side and computer terminals, wherein an original data table is stored in the server side to carry out global generalization on data and give a generalized lattice which is likely to meet k- anonymity; the server side utilizes a method of bisection to allocate a computational node to each computer terminal; each computer terminal carries out computation in parallel and returns a value to the server side according to a computation condition; if the return value does not meet k- anonymity, the server side sends a descendant node determined by the method of bisection to each computer node, otherwise the server side sends an ancestor node determined by the method of bisection to a computer; and each computer terminal recalculates according to a new node given by the server side until all nodes which meet k- anonymity are found. The method solves the trouble between explosive data growth and existing server storage and computational capabilities, and the efficiency of massive data processing is improved.
Owner:徐工汉云技术股份有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com