Building method of combined attack correlation and attack scene modelling on the basis of attack mode
A technology of attack scenarios and construction methods, which is applied in the field of intrusion alarm event correlation, can solve problems such as unsatisfactory effects and incompleteness, and achieve the effects of improving correlation analysis and prediction performance, improving accuracy, and simplifying calculations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049] The present invention will be described in detail below in conjunction with the drawings.
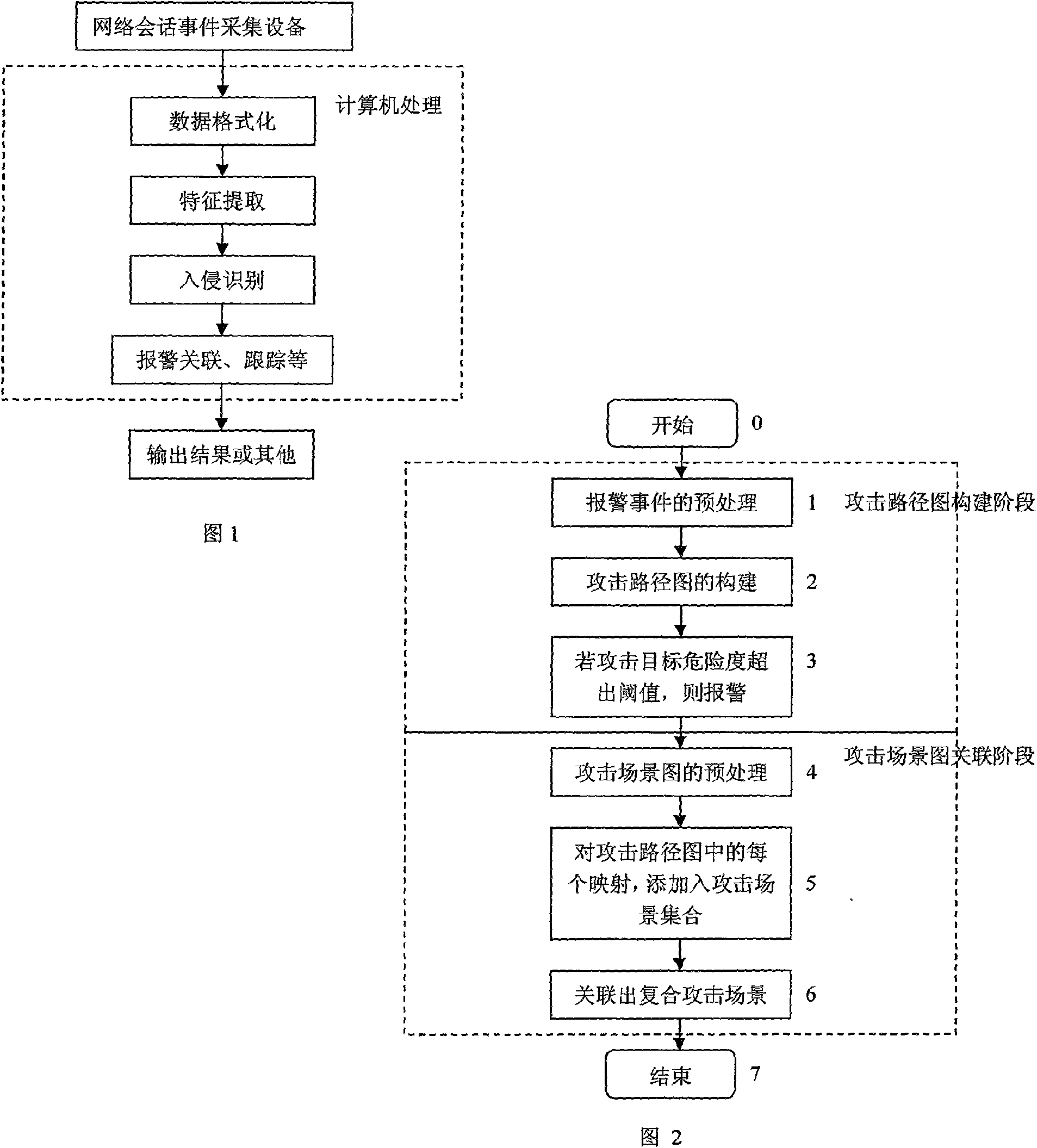
[0050] Such as figure 1 As shown, the intrusion detection system obtains network message data through the network session event collection device, and undergoes preprocessing such as message data formatting and feature extraction, and then intrusion identification, and subsequent processing such as alarm correlation and intrusion tracking.
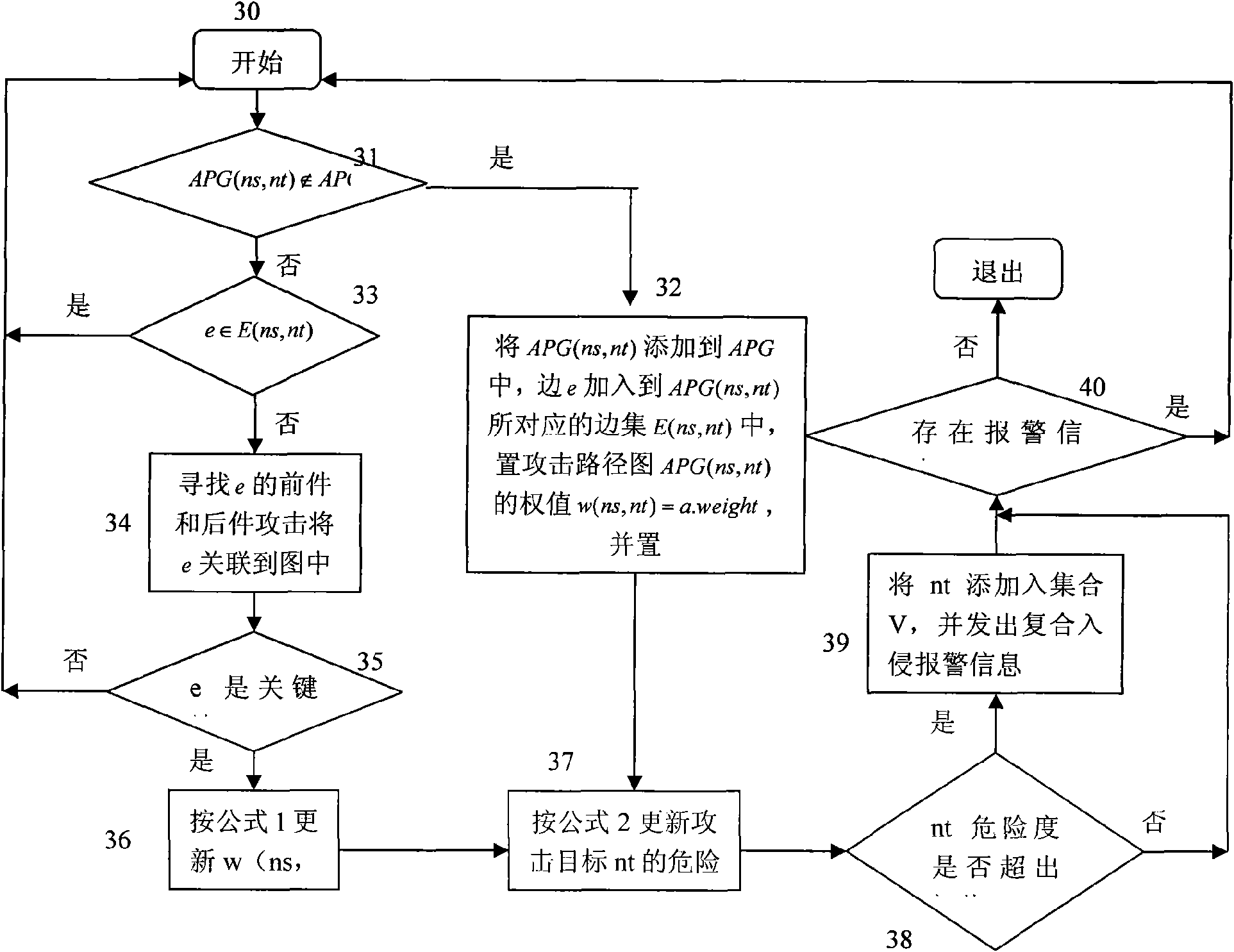
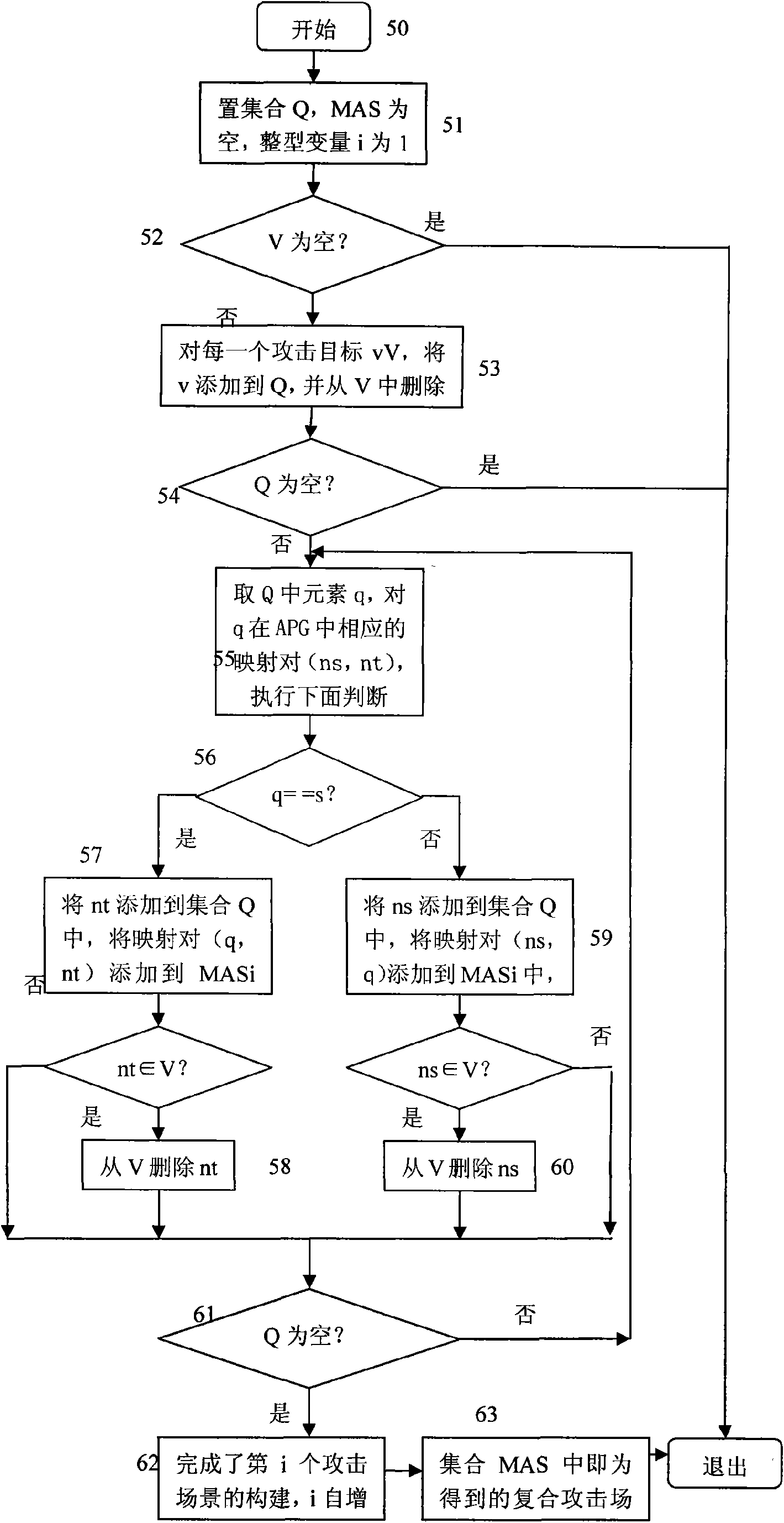
[0051] Alarm correlation is the main method to improve the prediction accuracy of the network intrusion detection system. The idea of the present invention is to improve the performance of the entire network intrusion detection system by improving the correlation accuracy of the alarm information. The alarm correlation process is the flow chart of the compound attack correlation and attack scenario construction method based on attack mode modeling of the present invention. figure 2 Shown.
[0052] Step 0 is the initial state of the network in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com