Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
258 results about "Computer communication networks" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
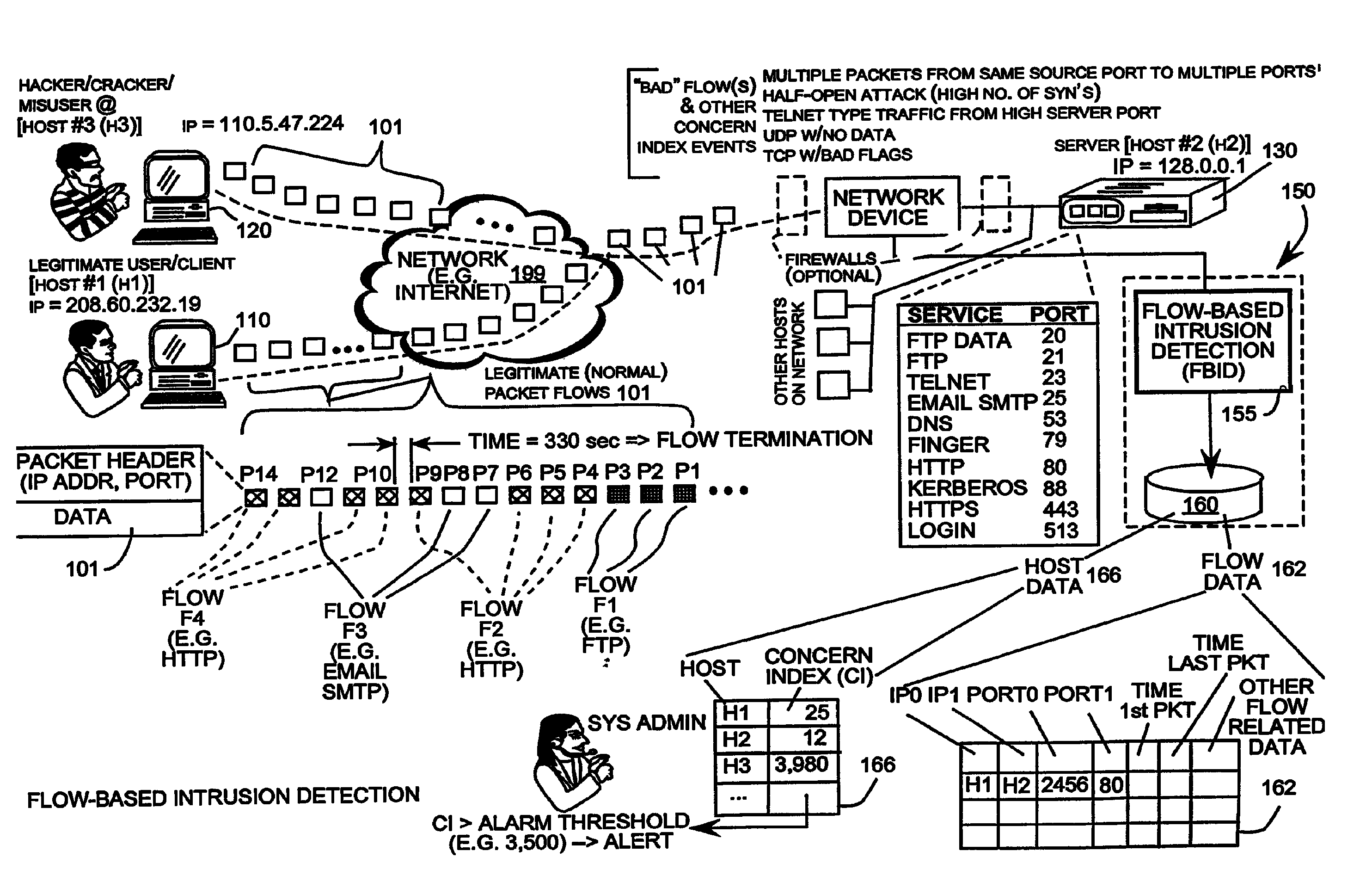
Packet sampling flow-based detection of network intrusions
InactiveUS7512980B2The method is accurate and reliableEasy to solveMemory loss protectionDigital data processing detailsComputer communication networksDistributed computing
A flow-based intrusion detection system for detecting intrusions in computer communication networks. Data packets representing communications between hosts in a computer-to-computer communication network are processed and assigned to various client / server flows. Statistics are collected for each flow. Then, the flow statistics are analyzed to determine if the flow appears to be legitimate traffic or possible suspicious activity. A concern index value is assigned to each flow that appears suspicious. By assigning a value to each flow that appears suspicious and adding that value to the total concern index of the responsible host, it is possible to identify hosts that are engaged in intrusion activity. When the concern index value of a host exceeds a preset alarm value, an alert is issued and appropriate action can be taken.
Owner:CISCO TECH INC
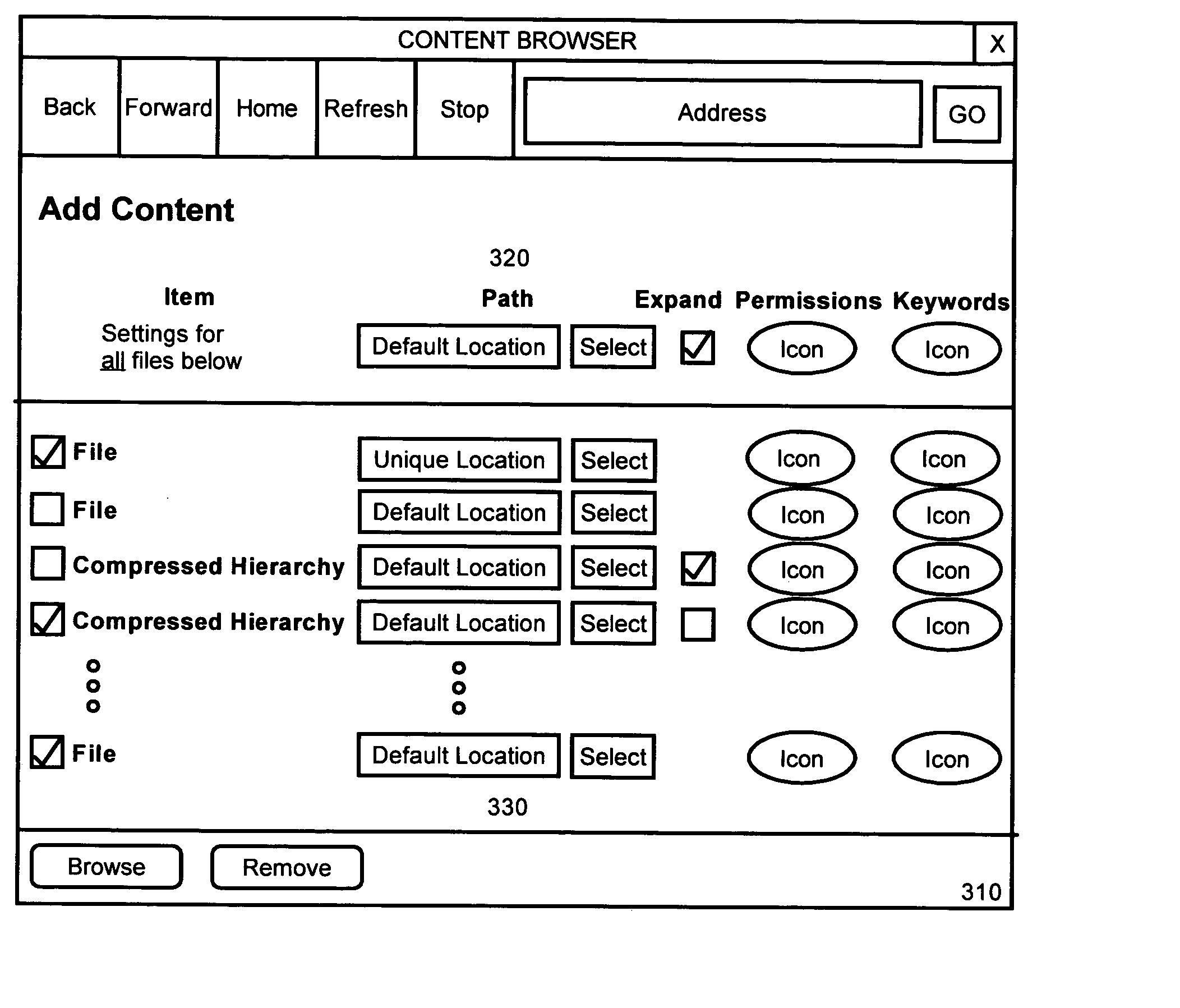
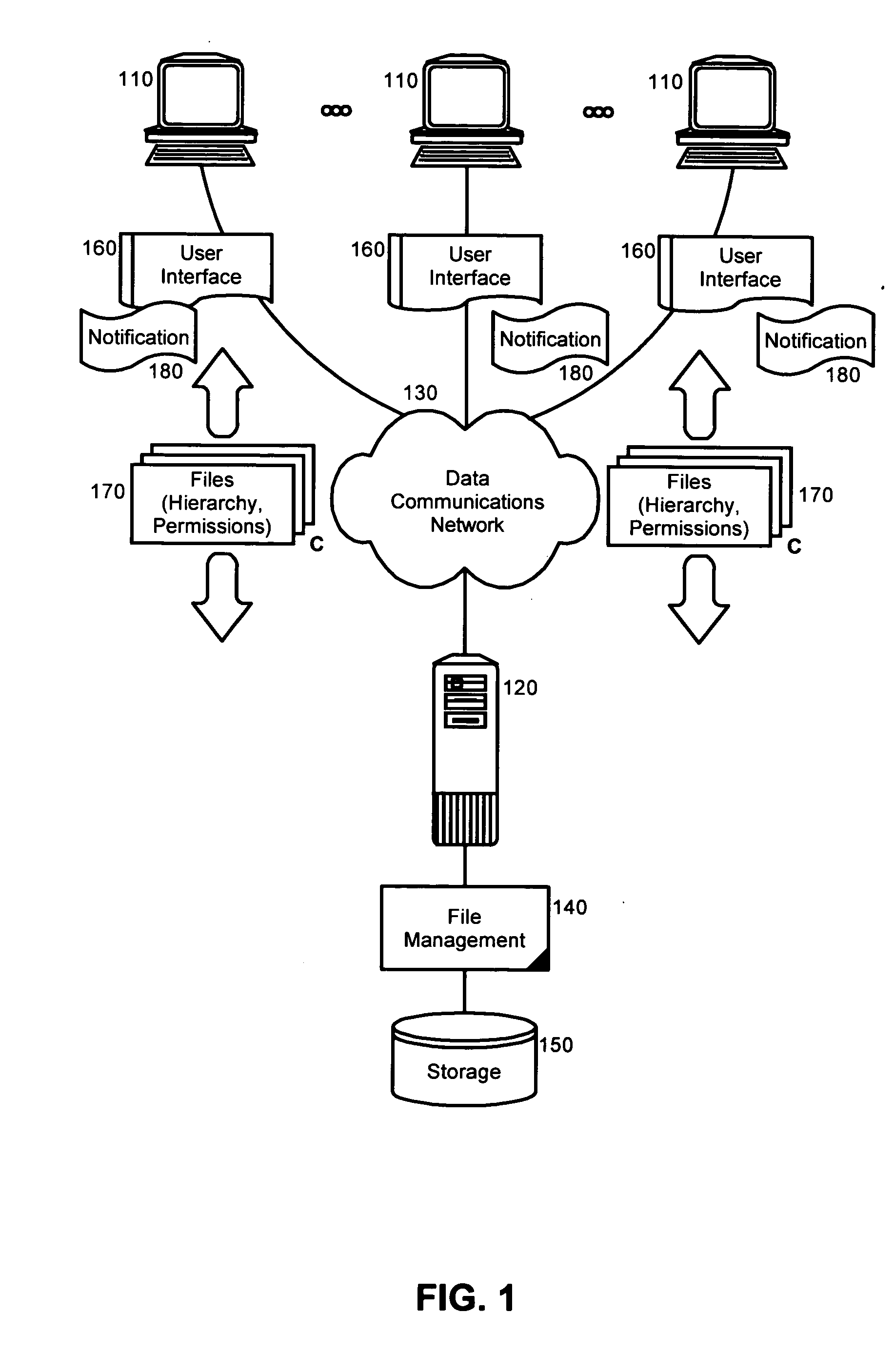
Centralized management of digital files in a permissions based environment
InactiveUS20060075071A1Multiple digital computer combinationsTransmissionCentralized managementBiological activation
A centralized file management method, apparatus and article of manufacture for use in a permissions based environment. A network file transfer method can include the steps of, responsive to the activation of a browse control in a file transfer user interface, displaying a file hierarchy for locally accessible files. At least one file can be selected from the hierarchy and the displaying and selecting steps can be repeated for additional activations of the browse control. Finally, subsequent to the repeating step, each of the selected files can be uploaded to a centralized data store over a computer communications network. In a preferred aspect of the invention, the method can include compressing at least two of the selected files into a compressed file, recording a file hierarchy for the at least two selected files, aggregating the file hierarchy and the compressed file, and, uploading the aggregation to the centralized data store along with the selected files.
Owner:GILLETTE JOSEPH G
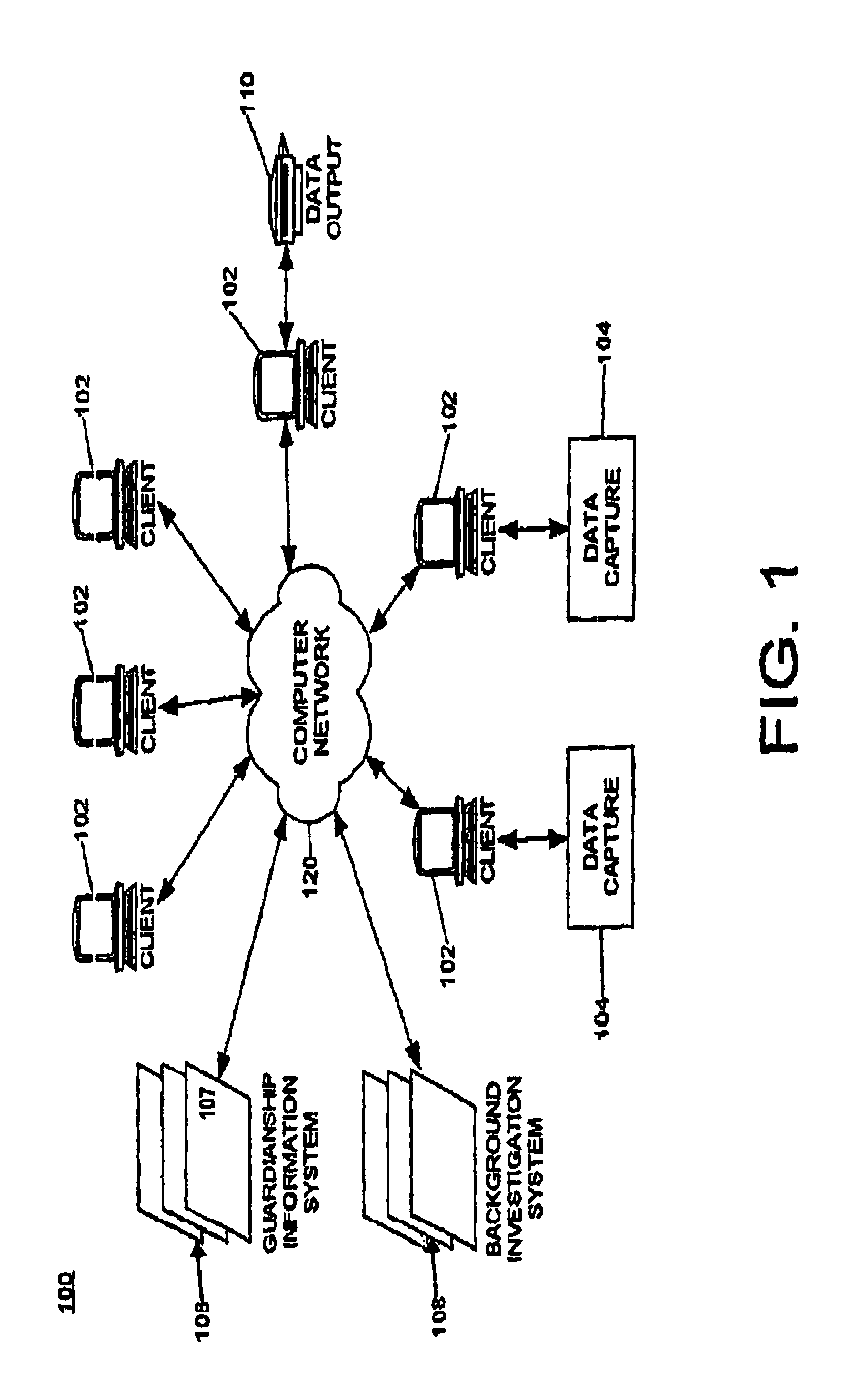
Integrated guardianship information system
InactiveUS6973462B2Digital data processing detailsMultiple digital computer combinationsComputer communication networksWorld Wide Web
An integrated guardianship system. The system can include a Clerk of the Court system for processing ward data and guardianship data; a guardian background investigation system communicatively linked to the Clerk of the Court system over a computer communications network; and, at least one database for storing ward, guardianship and background data, wherein the ward, guardianship and background data can be accessed by an authorized system communicatively linked to the computer communications network. Notably, the guardian background investigation system can conduct background investigations of guardians based on guardian data electronically provided by the Clerk of the Court system over the computer communications network. The background investigations, in turn, can produce guardian background data. Finally, the guardian background investigation system can electronically provide the guardian background data to the Clerk of the Court system over the computer communications network.
Owner:FLORIDA ATLANTIC UNIVERSITY
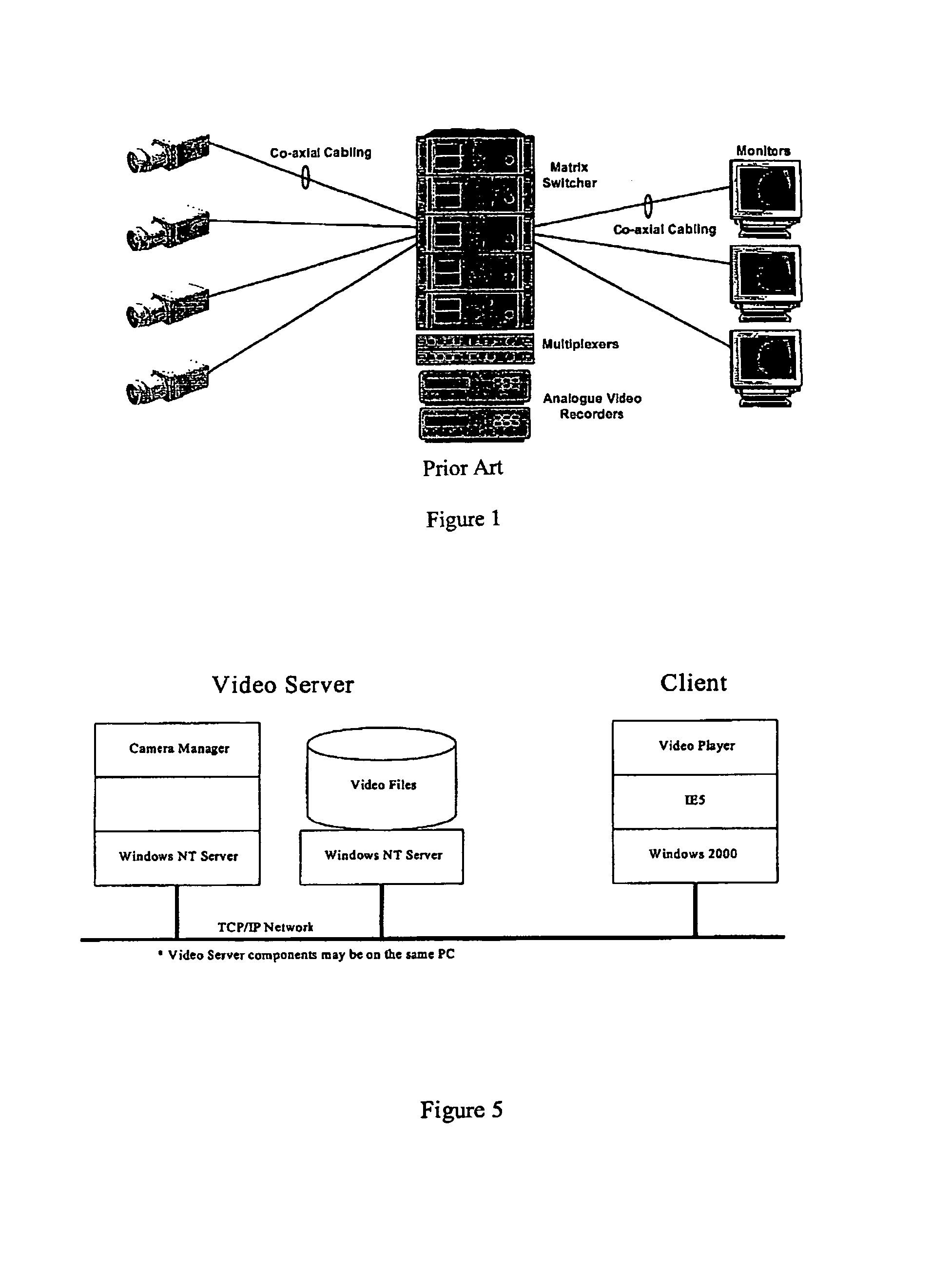
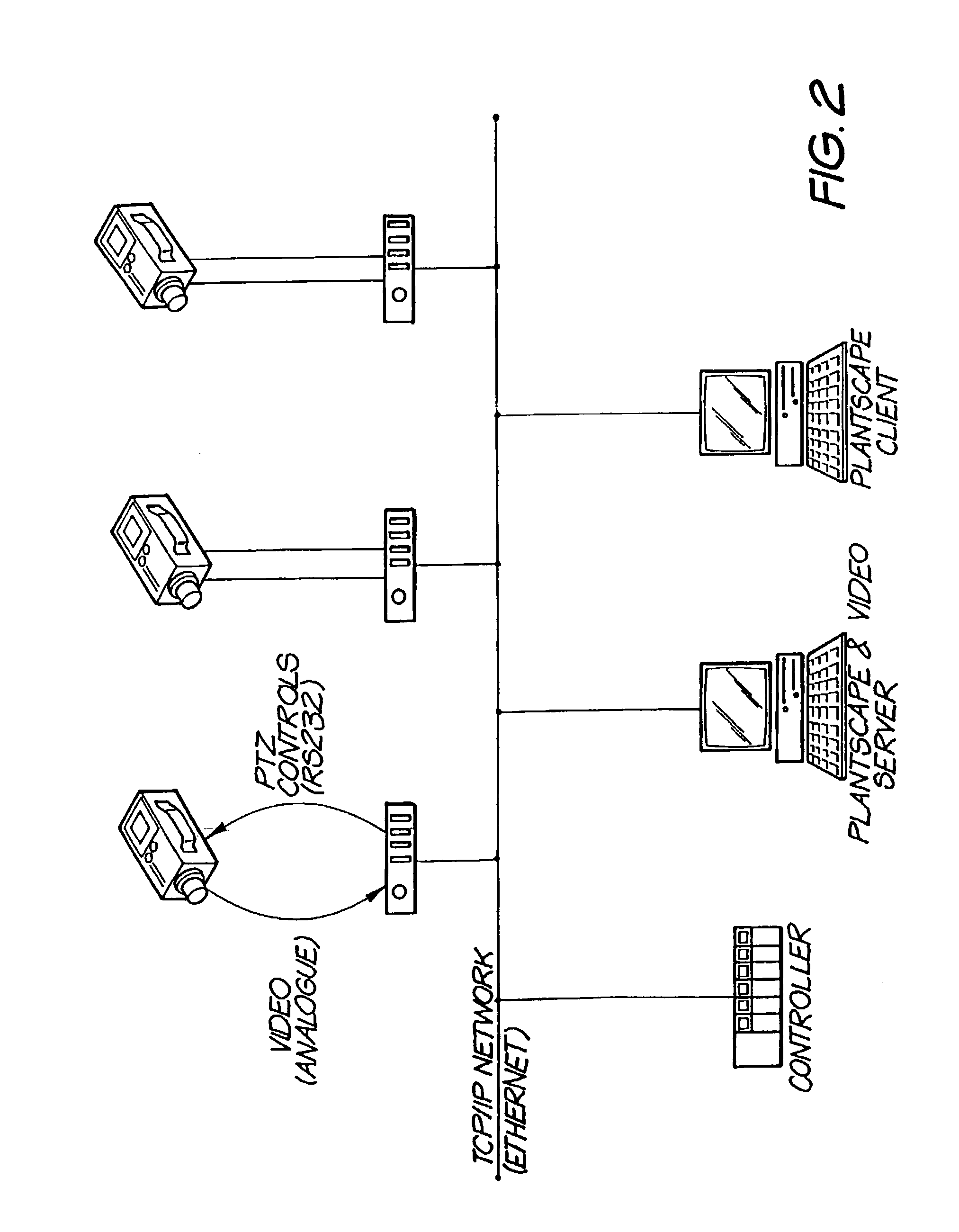
System and method for digital video management
InactiveUS7859571B1Smooth playbackTelevision system detailsColor television detailsTime scheduleDigital video
A digital video management system which provides live digital video signals from a number of cameras to a number of client terminals, via a computer communications network, in real time. The system stores live video signals in response to a video recording trigger which may be either a schedule, an event, or an operator action. The invention is particularly suitable for use in integrated security and process control environments.
Owner:HONEYWELL INC
Second Screen Dilemma Function
InactiveUS20150086174A1Display delayTelevision system detailsPulse modulation television signal transmissionVideo tapeComputer communication networks
Systems for, and methods of, displaying video information comprising: a second screen device obtaining current play position data of a video being played on a primary screen device (e.g., obtaining from the primary screen device an identification of a current play position of the video, or obtaining information to generate an acoustic fingerprint of the video); determining a current play position of the video playing on the primary screen device based upon the current play position data (e.g., identification of the current play position or the acoustic fingerprint); downloading information (e.g., video map, subtitles, moral principles, objectionable content, memorable content, performers, geographical maps, shopping, plot point, item, ratings, and trivia information) over a computer communications network into the memory of the second screen device; and displaying information on the second screen device synchronized with the contemporaneously played video on the primary screen device.
Owner:CUSTOMPLAY
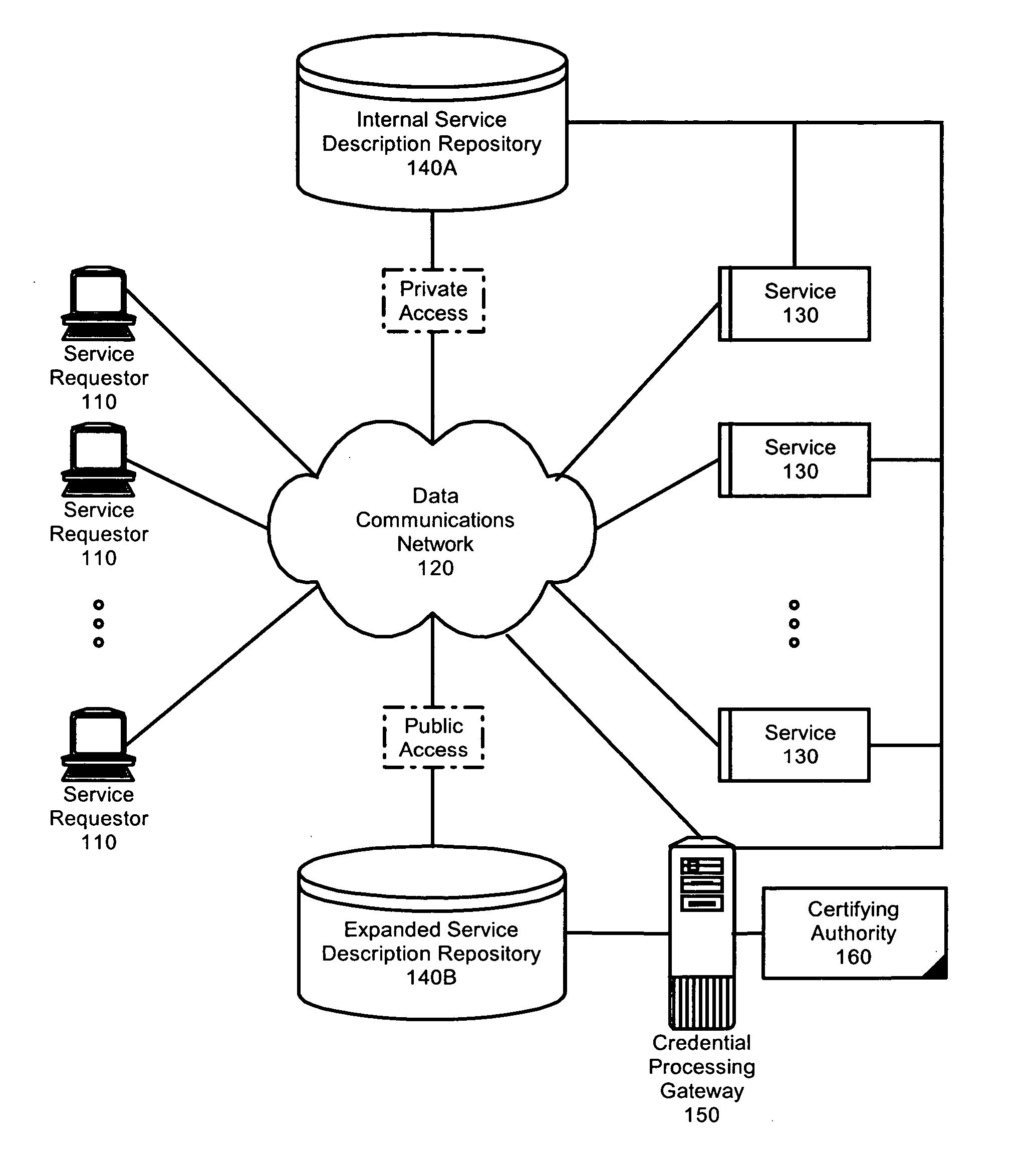
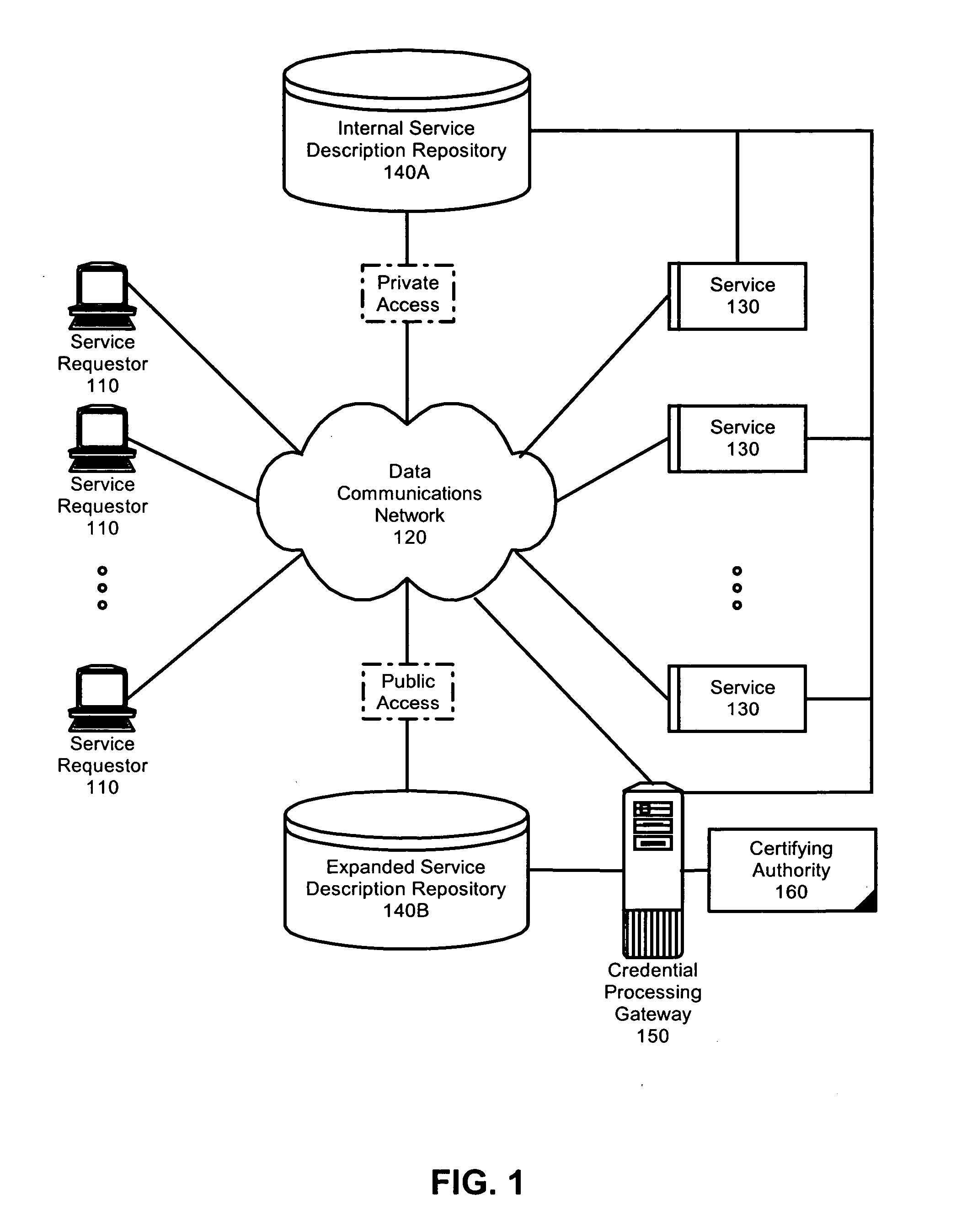
Federated identity brokering
InactiveUS20060021010A1Make up for deficienciesDigital data processing detailsUser identity/authority verificationTrusted authorityFederated identity
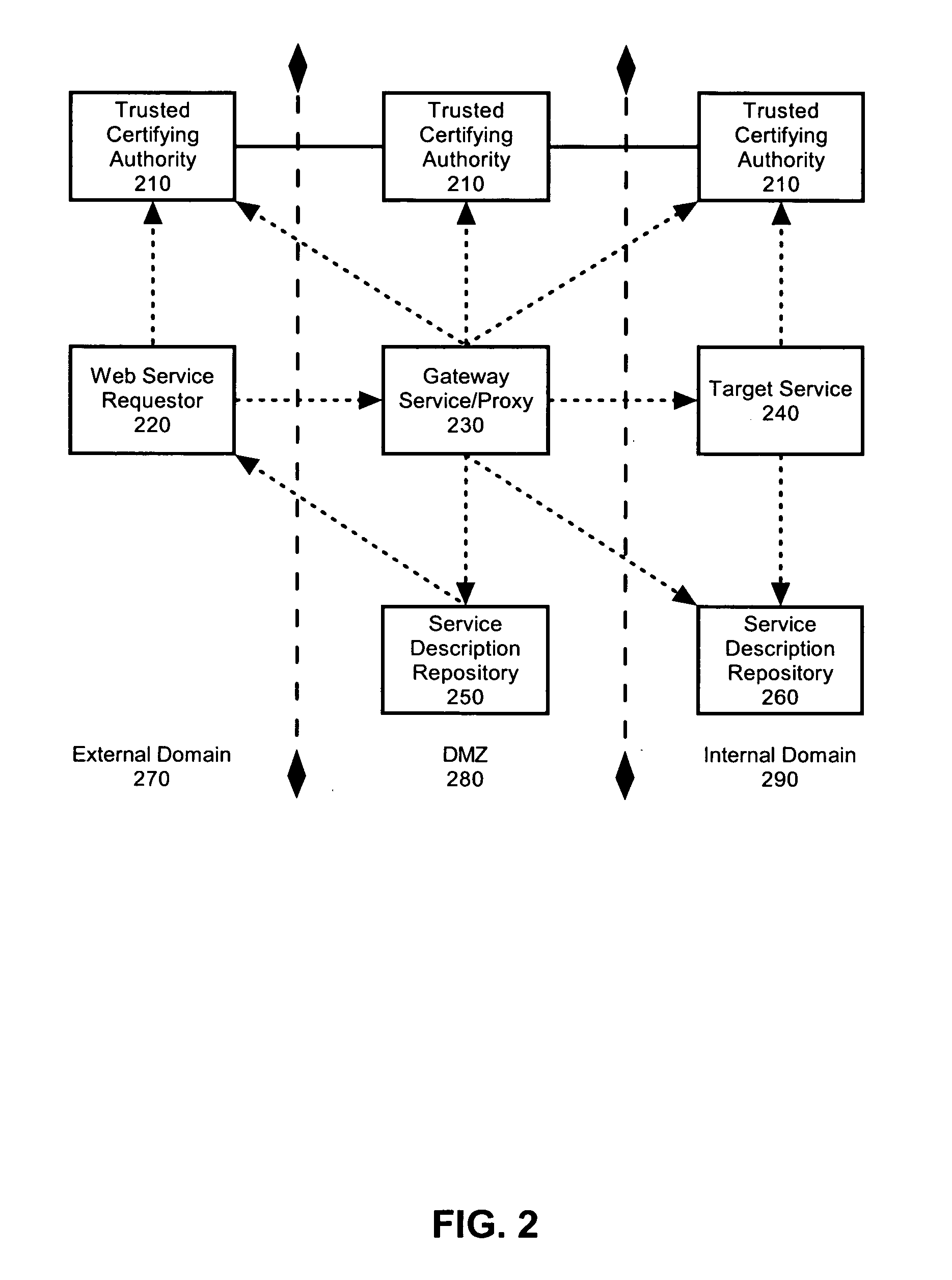
A method, system and apparatus for federated identity brokering. In accordance with the present invention, a credential processing gateway can be disposed between one or more logical services and one or more service requesting clients in a computer communications network. Acting as a proxy and a trusted authority to the logical services, the credential processing gateway can map the credentials of the service requesting clients to the certification requirements of the logical services. In this way, the credential processing gateway can act as a federated identity broker in providing identity certification services for a multitude of different service requesting clients without requiring the logical services to include a pre-configuration for specifically processing the credentials of particular service requesting clients.
Owner:IBM CORP
Sequence number based TCP session proxy
InactiveUS20070283429A1High speed communicationReduces commitmentMultiple digital computer combinationsProgram controlNetwork packetByte
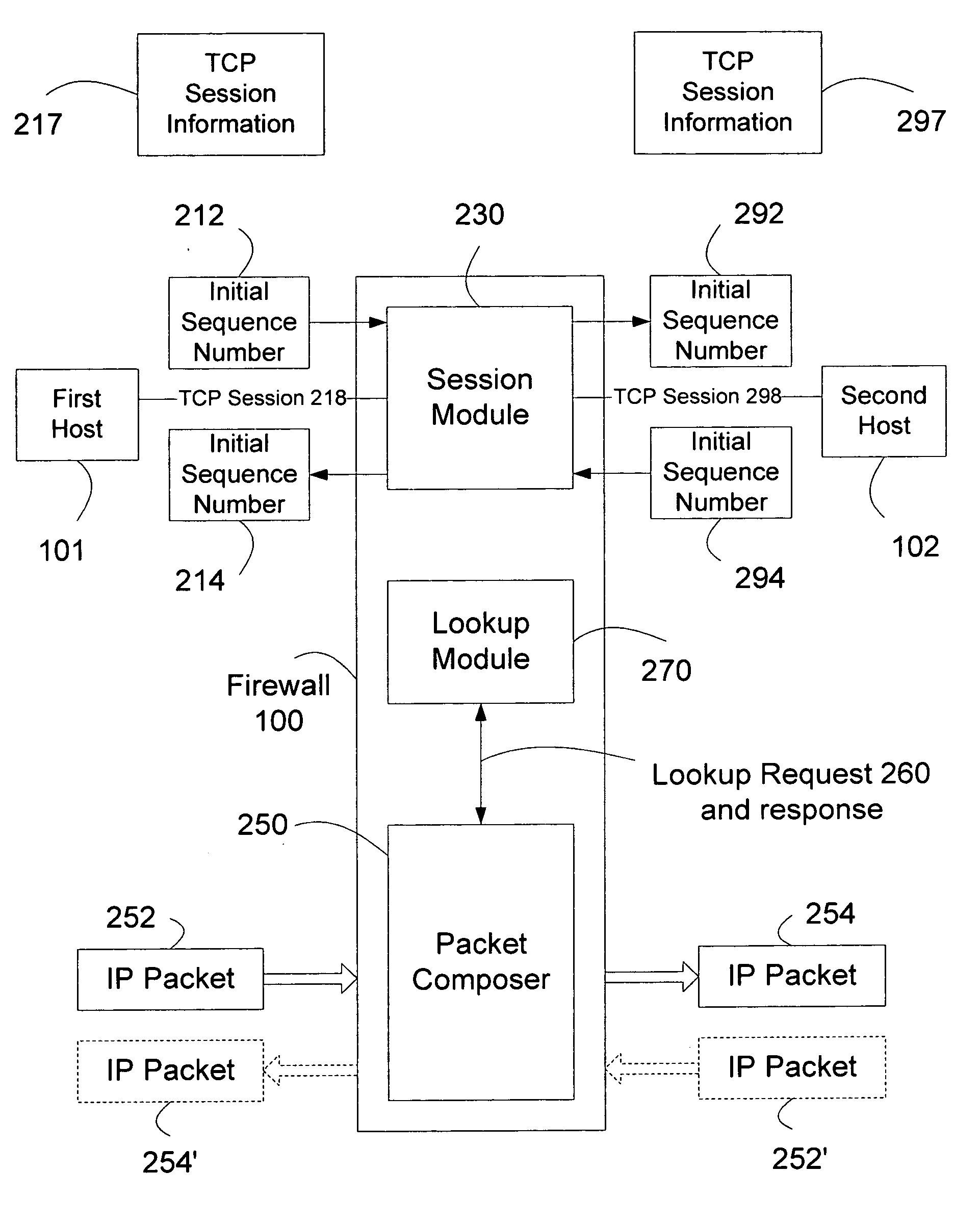
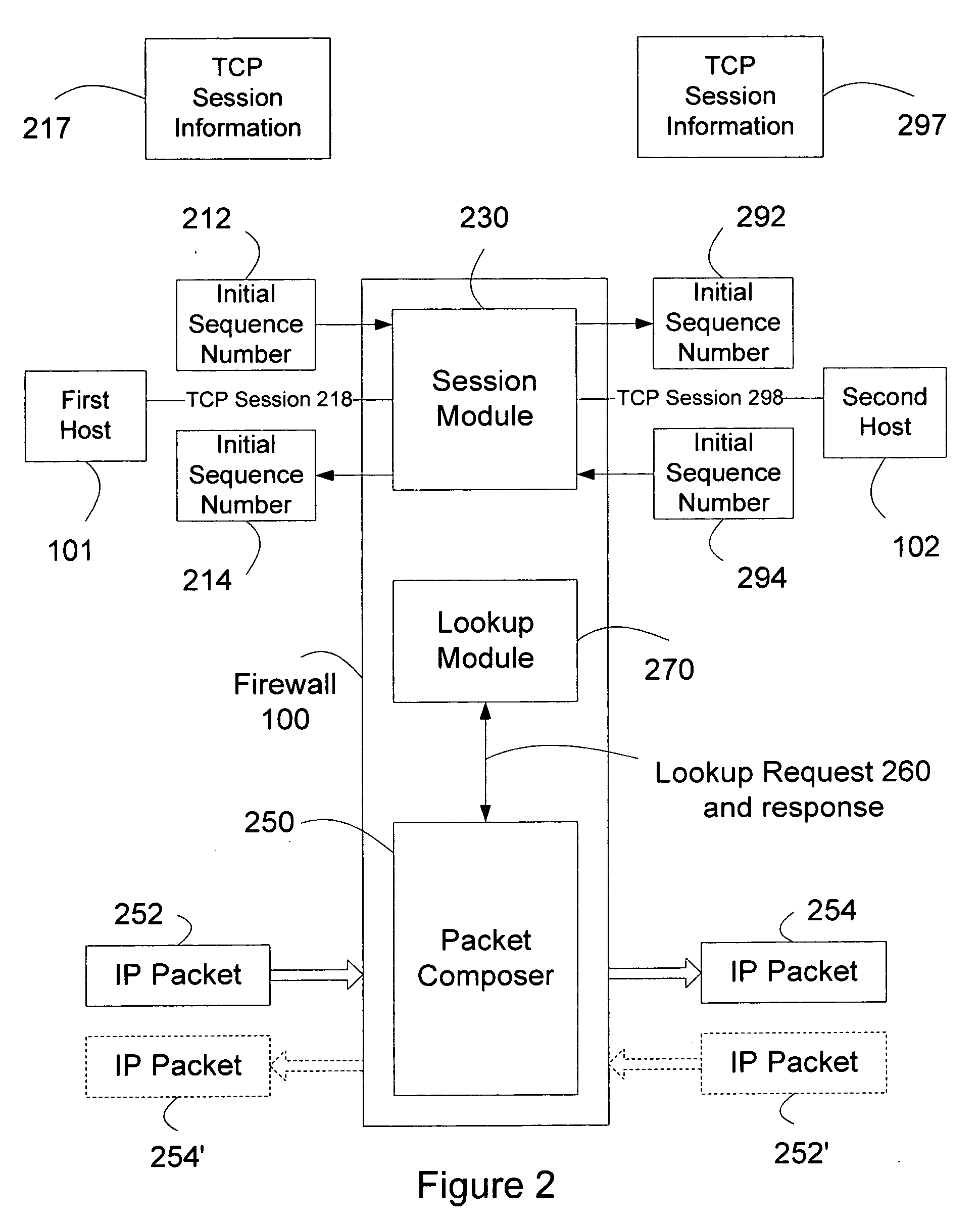
In a computer communication network including a firewall which protects a secured host against attack from outside computers, the host communicating with an outside computer, through the firewall, via data packets which include byte sequence numbers. In a communication between the host and computer in which one of them acts as a source and the other as a destination for the communication, a sequence number offset is derived by the firewall which characterizes the byte sequence number received from the source and the byte sequence number the firewall will provide to the destination for that communication. In a communication received from the source, the firewall adds the offset to byte sequence numbers in a packet passing between the source and destination, in order to determine the byte sequence numbers it will provide to the destination. Thus, proper sequence numbers can be provided to both locations, without the firewall having to restructure packets. This speeds communication between the source and destination and substantially reduces the commitment of processing and storage resources.
Owner:A10 NETWORKS
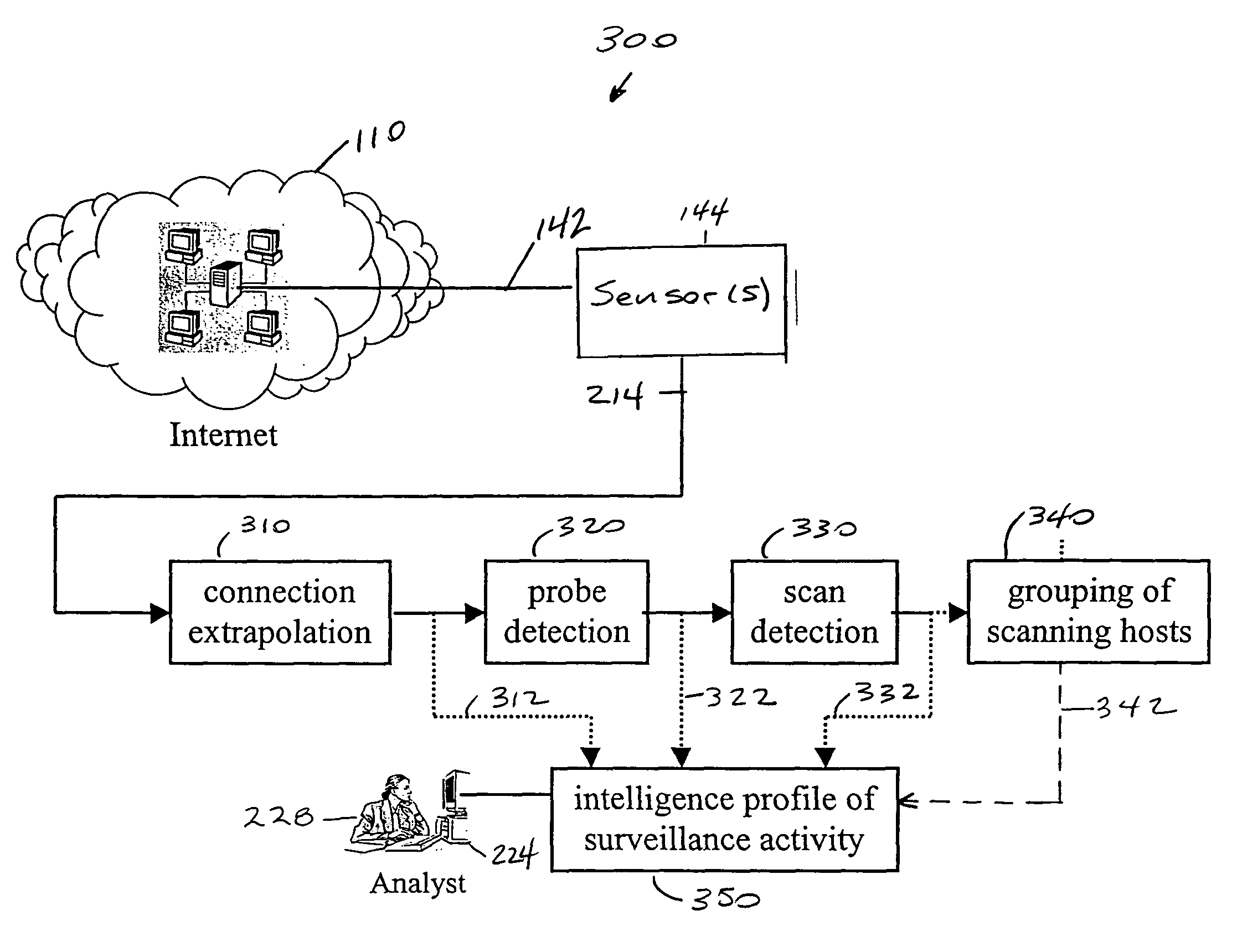
Detecting probes and scans over high-bandwidth, long-term, incomplete network traffic information using limited memory
ActiveUS7752665B1Robust against stealthy attackImprove productivityMemory loss protectionUnauthorized memory use protectionAdaptive learningNetwork connection
A method for detecting surveillance activity in a computer communication network comprising automatic detection of malicious probes and scans and adaptive learning. Automatic scan / probe detection in turn comprises modeling network connections, detecting connections that are likely probes originating from malicious sources, and detecting scanning activity by grouping source addresses that are logically close to one another and by recognizing certain combinations of probes. The method is implemented in a scan / probe detector, preferably in combination with a commercial or open-source intrusion detection system and an anomaly detector. Once generated, the model monitors online activity to detect malicious behavior without any requirement for a priori knowledge of system behavior. This is referred to as “behavior-based” or “mining-based detection.” The three main components may be used separately or in combination with each other. The alerts produced by each may be presented to an analyst, used for generating reports (such as trend analysis), or correlated with alerts from other detectors. Through correlation, the invention prioritizes alerts, reduces the number of alerts presented to an analyst, and determines the most important alerts.
Owner:FORCEPOINT FEDERAL
Integrated information communication system
InactiveUS6618366B1Metering/charging/biilling arrangementsInterconnection arrangementsCommunications systemCommunication quality
To provide an integrated information communication system without using dedicated lines or the Internet, ensuring communication speed, communication quality, communication trouble countermeasures in a unified manner, wherein security and reliability in communication is ensured. The system is comprised of an access control apparatus for connecting a plurality of computer communication networks or information communication equipment to each, and a relay device for networking the aforementioned access control apparatus, the system having functions for performing routing by transferring information by a unified address system, and is configured such that the aforementioned plurality of computer communication networks or information communication equipment can perform communications in an interactive manner.
Owner:THE DISTRIBUTION SYST RES INST
System and Method For Providing A Personalized Shopping Experience and Personalized Pricing of Products and Services With A Portable Computing Device
ActiveUS20130181045A1Customer relationshipDiscounts/incentivesPersonalizationComputer communication networks
A system and method for providing a personalized shopping experience with a portable computing device (“PCD”) are described. The system and method may include checking-in PCD consumers upon entering an establishment of a merchant. The checking-in of the PCD consumer may include verifying credentials for gaining access to a central mobile payment controller and receiving a merchant identifier corresponding to a merchant from a computer communications network. Next, a scan of a machine-readable code associated with at least one of a good and a service may be received. Information associated with the machine-readable code may be retrieved from a database. Subsequently, a personalized price for the at least one good or service may be determined by applying one or more rules. The personalized price may be transmitted over a computer communications network to the portable computing device for display to the PCD consumer.
Owner:QUALCOMM INC
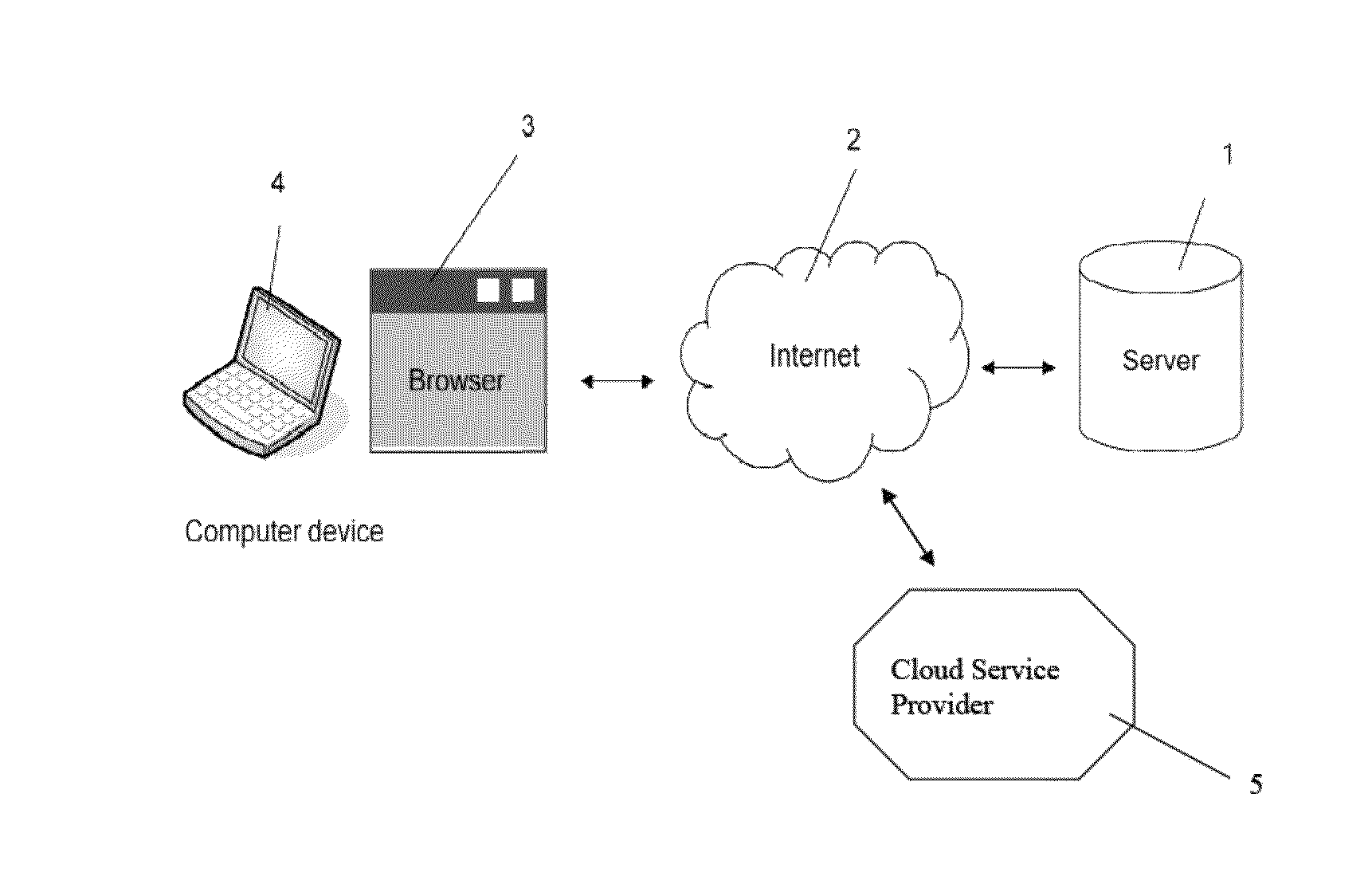
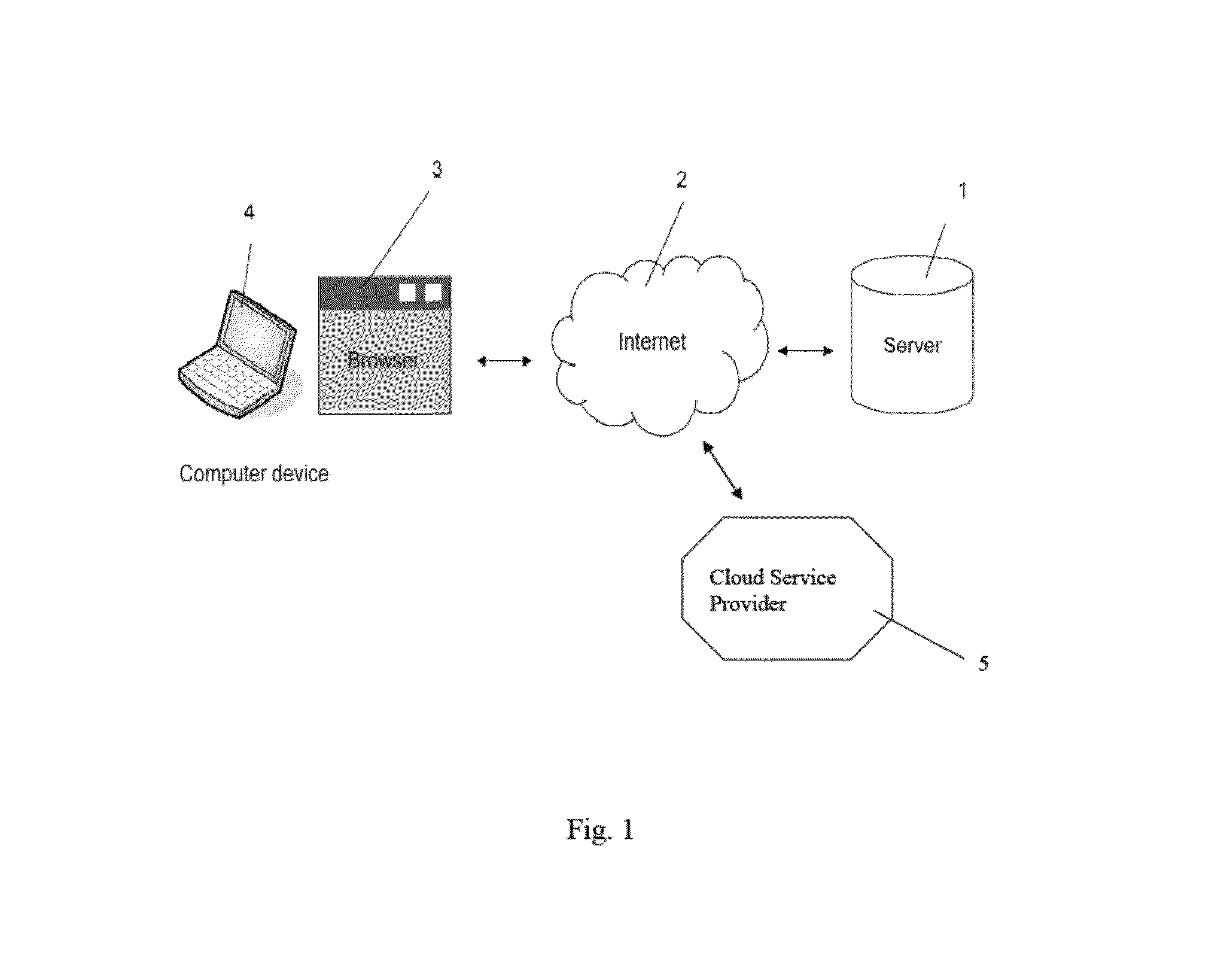
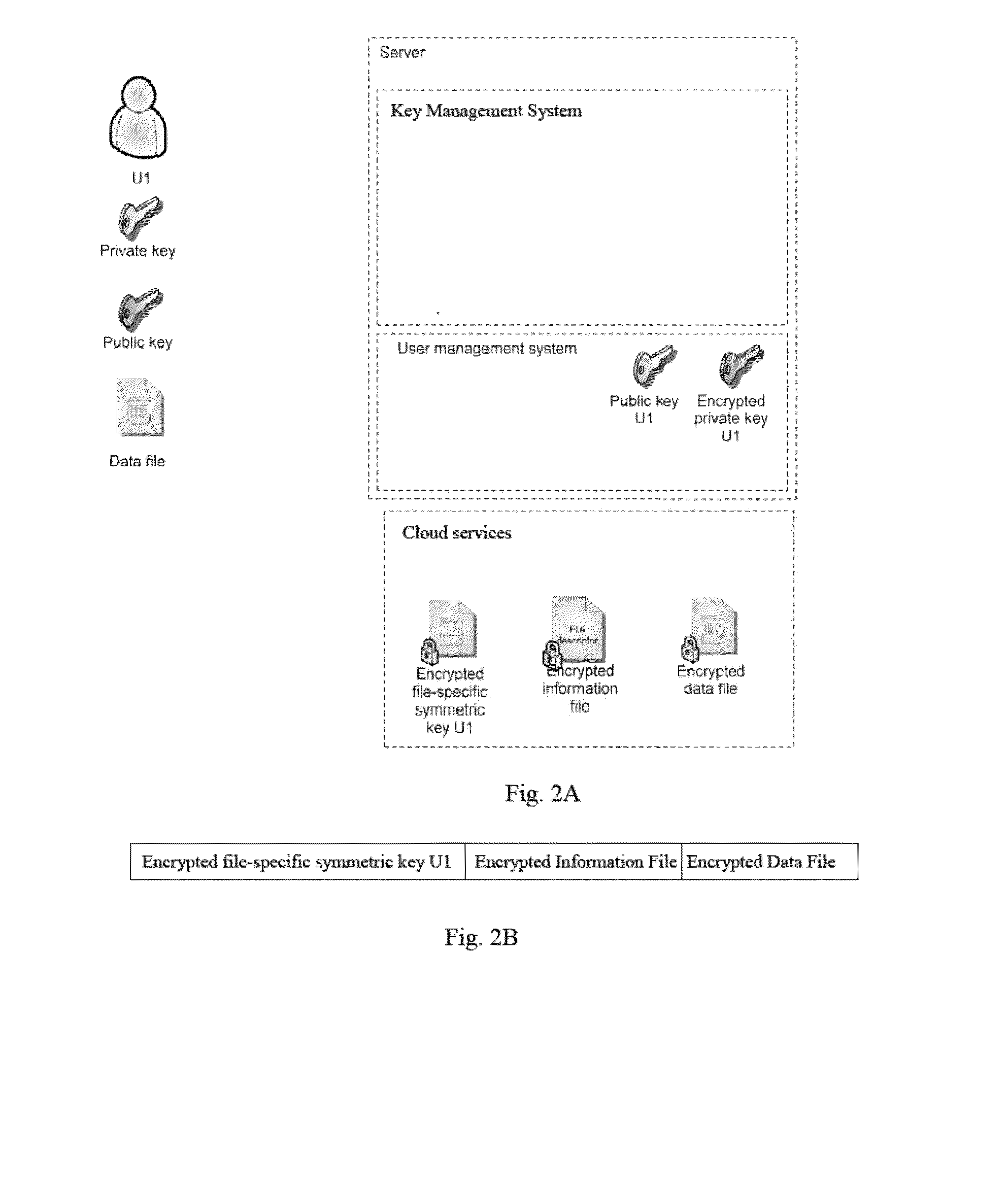
Method for secure storing and sharing of a data file via a computer communication network and open cloud services
ActiveUS20150113279A1User identity/authority verificationComputer security arrangementsWeb browserPassword
A computer implemented method, server computer and computer program for securely storing a data file via a computer communication network and open cloud services. The method includes: providing a user's computer with code for providing a unique user name; asking the user for a password; generating an asymmetric key pair having one public key and one private key; encrypting the private key via a hash of the password; generating a file-specific symmetric key specific for the data file; encrypting the data file via the file-specific symmetric key; encrypting the file-specific symmetric key via the public key; where the code is executed by a web browser on the computer; storing the encrypted file-specific symmetric key as a header part of the encrypted data file, and interacting with the file exchange interface of a cloud service which receives the encrypted data file, and storing the encrypted data file and header part.
Owner:INVENIA
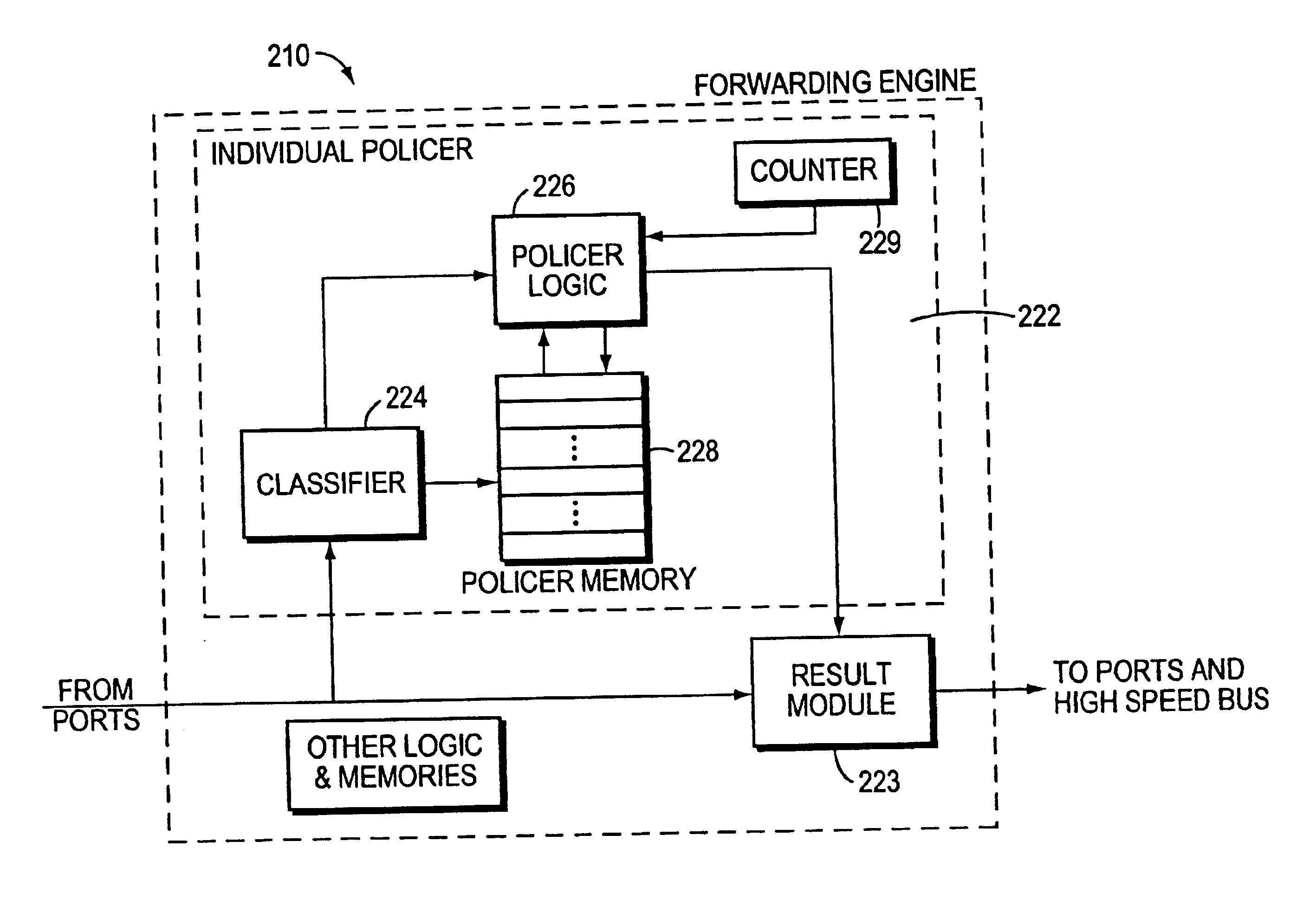
Distriburted QoS policing system and method
InactiveUS6826150B1Optimizing cost-accuracy tradeoffReduce information exchangeError preventionTransmission systemsTraffic capacityTraffic congestion
A method for policing traffic on a computer communications network having a multitude of nodes interconnected by various communications media. An individual policer is established at each node for monitoring and / or policing the traffic incoming to that node. Traffic policy parameters are established for traffic-classes and the policy is implemented at each individual policer. Thresholds may be established and when the thresholds are met or exceeded the individual policer will export the traffic conditions at the respective node. The other individual policers or a master policer will receive the exported information. -The individual policers police the traffic incoming to its associated node depending on the traffic condition information received from all the nodes. Several classes may be handled by each individual policer. Leaky bucket algorithms may be used in some instances.
Owner:CISCO TECH INC
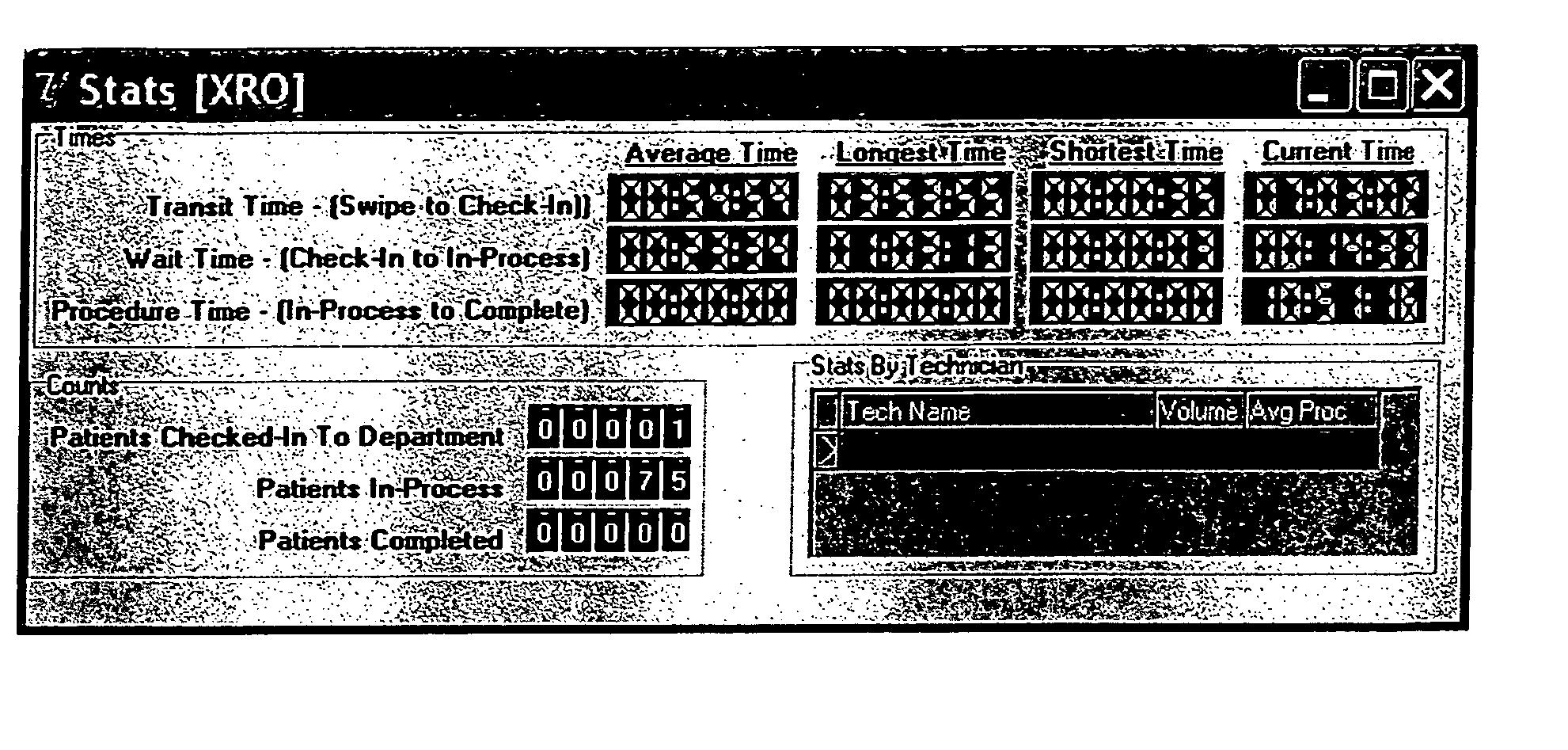
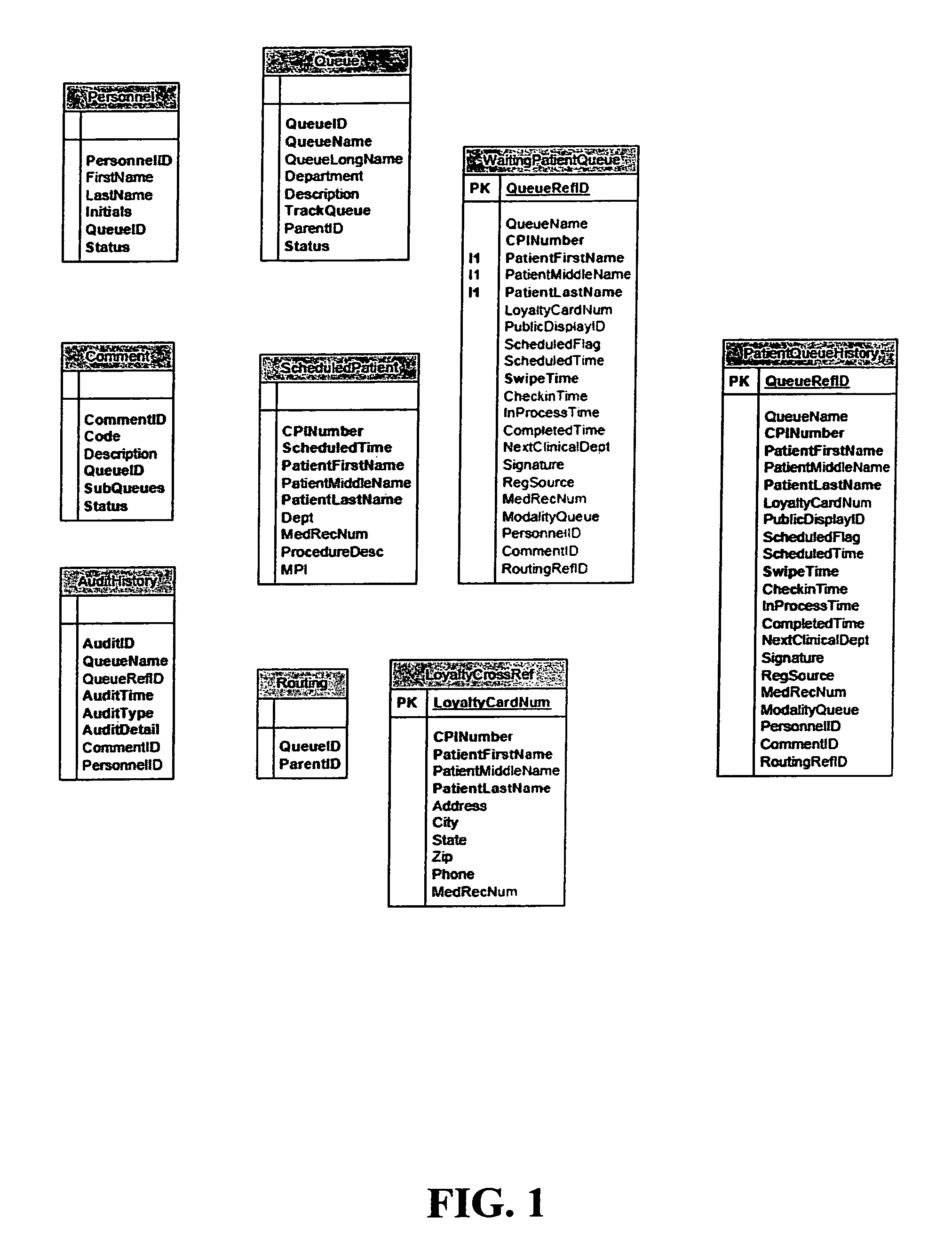
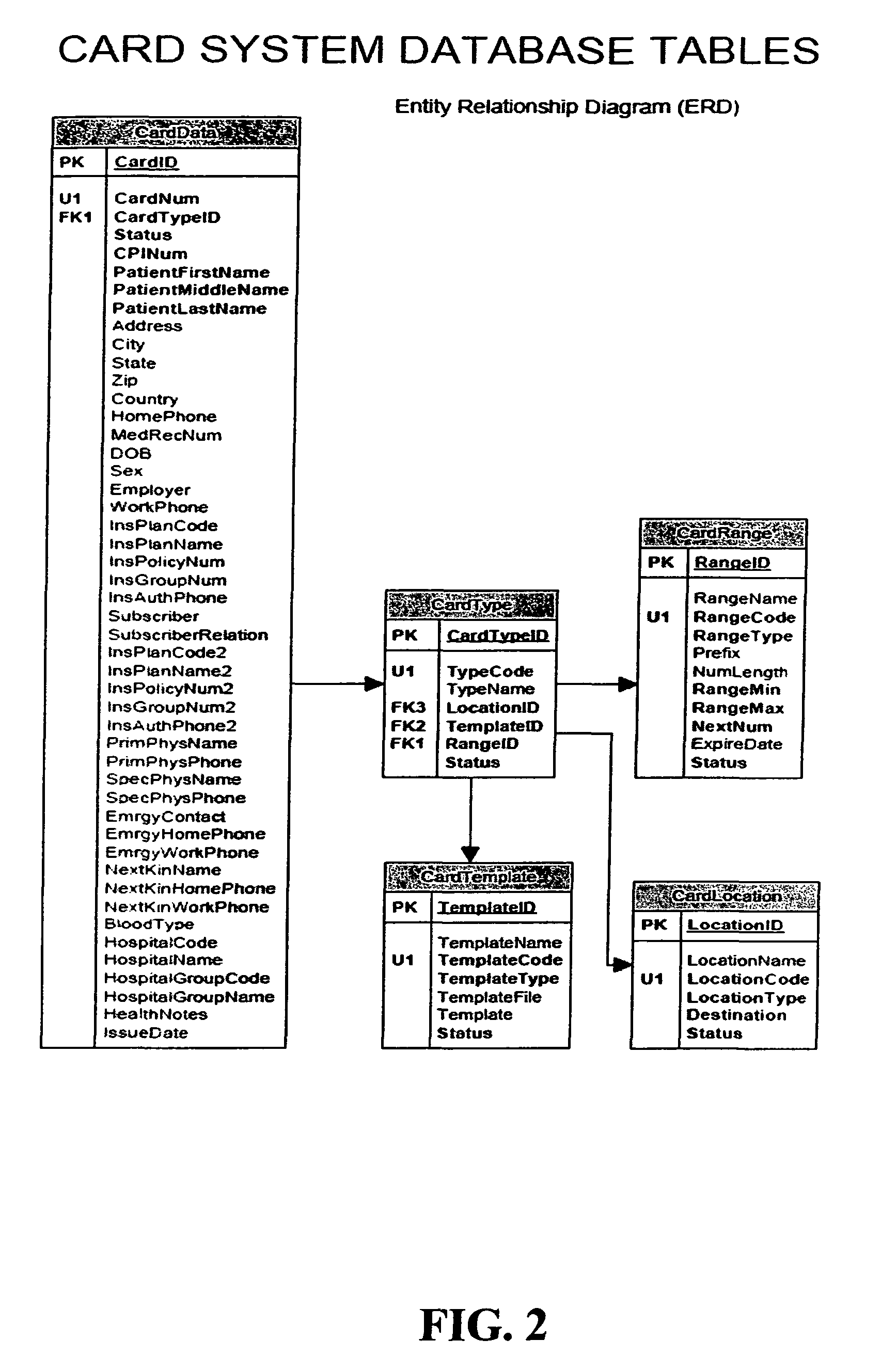
Automated patient management system
ActiveUS8000979B2Improve satisfactionImprove processing efficiencyHealthcare resources and facilitiesResourcesPatient managementComputer communication networks
A system for making the process of registering at and receiving treatment in a healthcare facility more efficient and safe has been developed. The system utilizes computer communications network-based systems, software, various input and output stations, and a patient identification card (e.g., Loyalty Card) that work together to allow (a) providers to direct, track, and optimize the efficiency of patient activity and (b) patients to have ready access to their status and, in some cases, control of the healthcare process.
Owner:JELLYFISH HEALTH
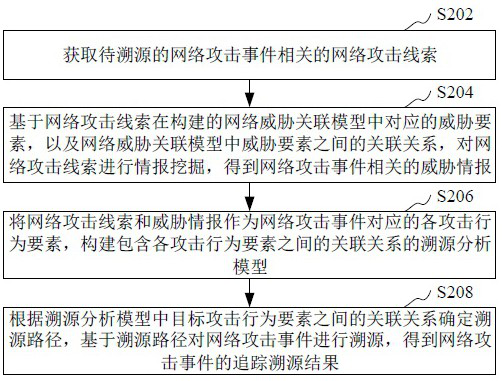
Network attack event traceability processing method and device, equipment and storage medium
The invention relates to the technical field of network security, in particular to a network attack event traceability processing method and device, equipment and a storage medium. The method comprises the steps of obtaining a network attack clue related to a to-be-traced network attack event; performing intelligence mining on the network attack clue based on the constructed network threat association model to obtain threat intelligence related to the network attack event; taking the network attack clue and the threat intelligence as attack behavior elements corresponding to the network attackevent, and constructing a traceability analysis model containing an association relationship between the attack behavior elements; and determining a traceability path according to the association relationship between the target attack behavior elements in the traceability analysis model, and performing traceability on the network attack event based on the traceability path to obtain a traceability result of the network attack event. By adopting the method, accurate tracking and tracing of the network attack event can be realized, so that the security of a computer communication network is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Optimizing package delivery using social networks
In an embodiment of the invention, a method for optimizing package delivery using social networks is provided. The method includes receiving an order to purchase a product by a purchaser in an e-commerce computing application executing in memory of a host server from over a computer communications network, retrieving a list of social networking contacts for the purchaser, determining whether or not a contact amongst the social networking contacts has ordered a product from the e-commerce computing application, and rendering a prompt in the e-commerce computing application to the purchaser to consolidate shipment of the product ordered by the purchaser with a product ordered by the contact in response to determining that the contact has also ordered a product from the e-commerce computing application not yet shipped to the contact.
Owner:IBM CORP
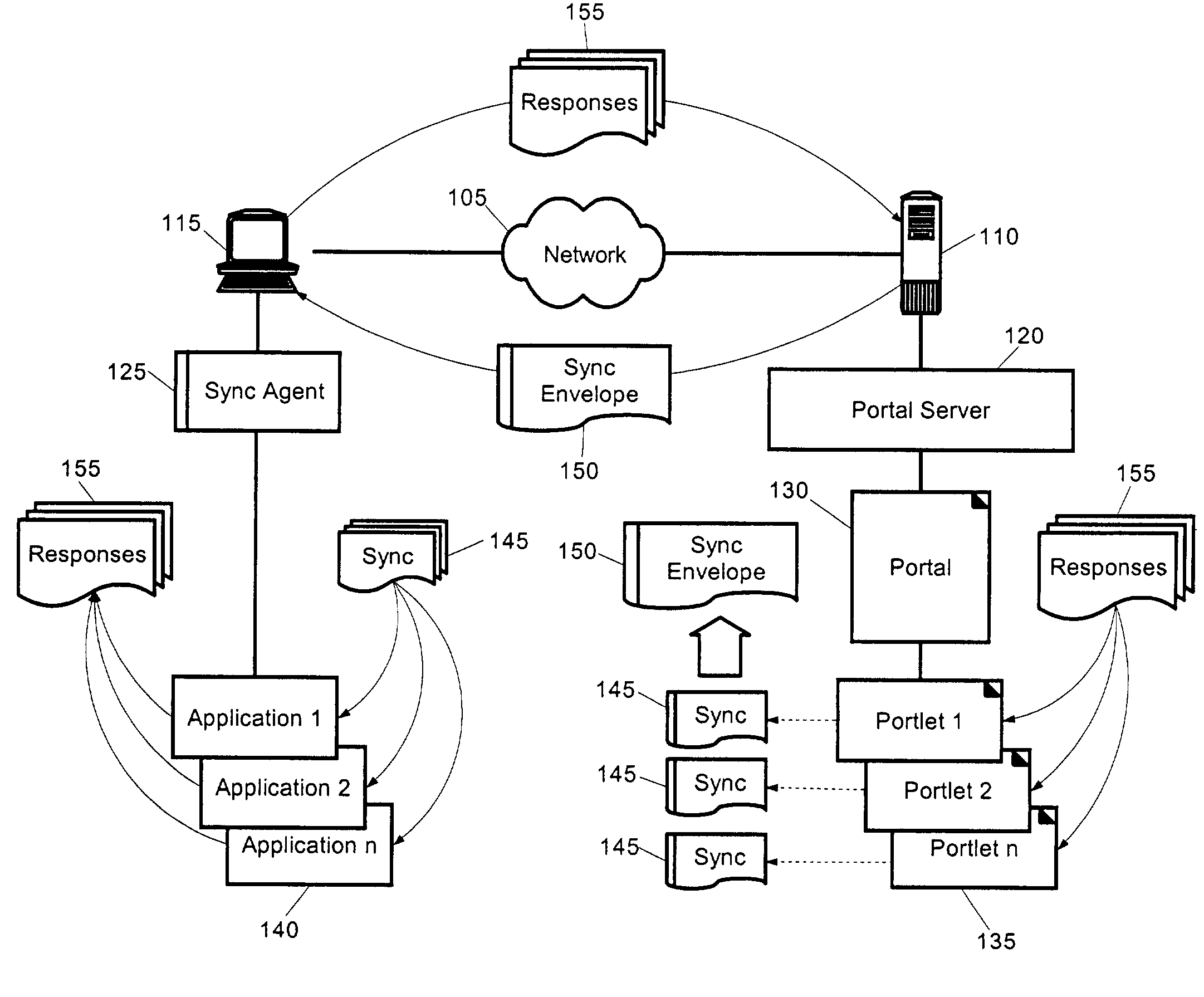
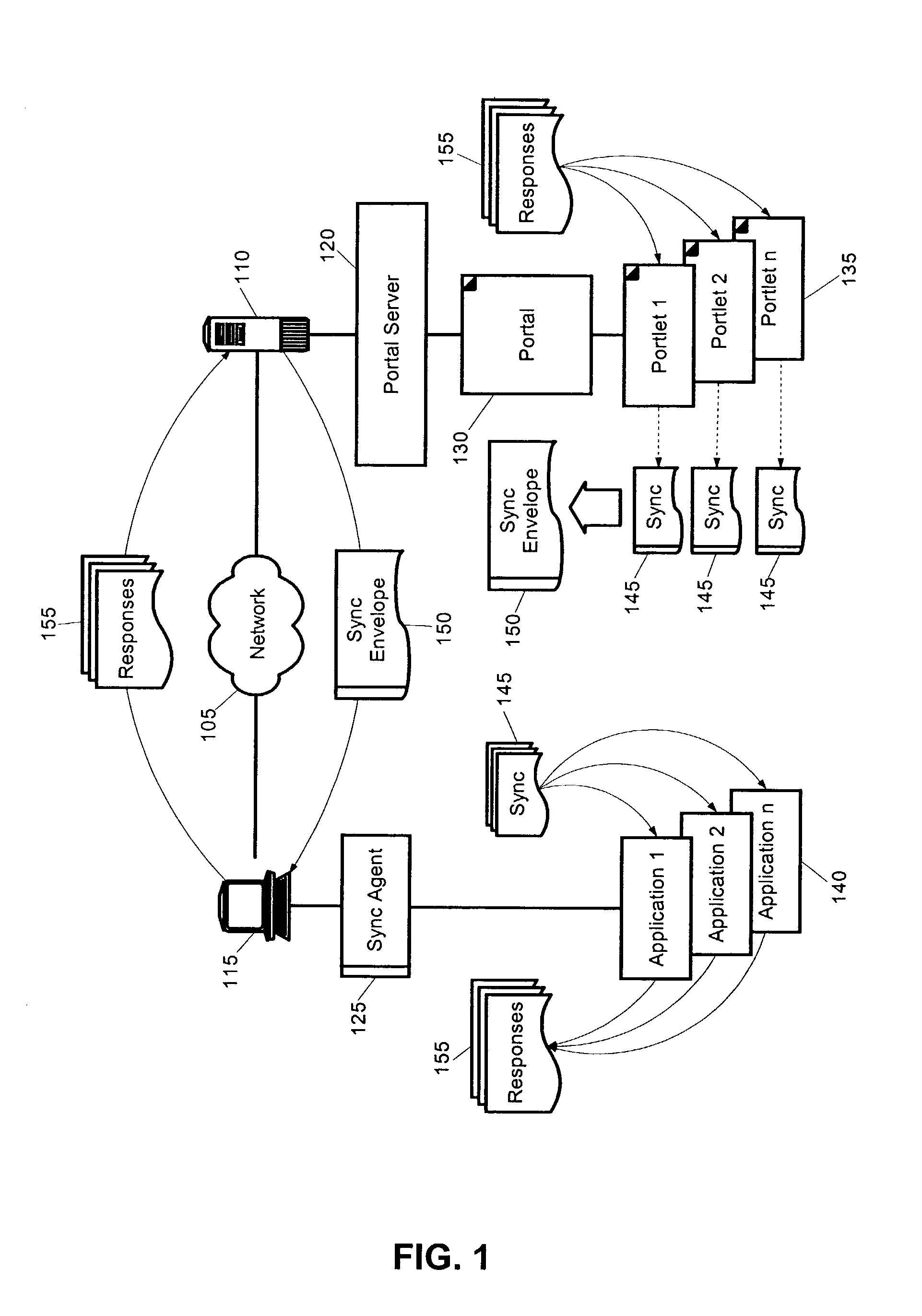
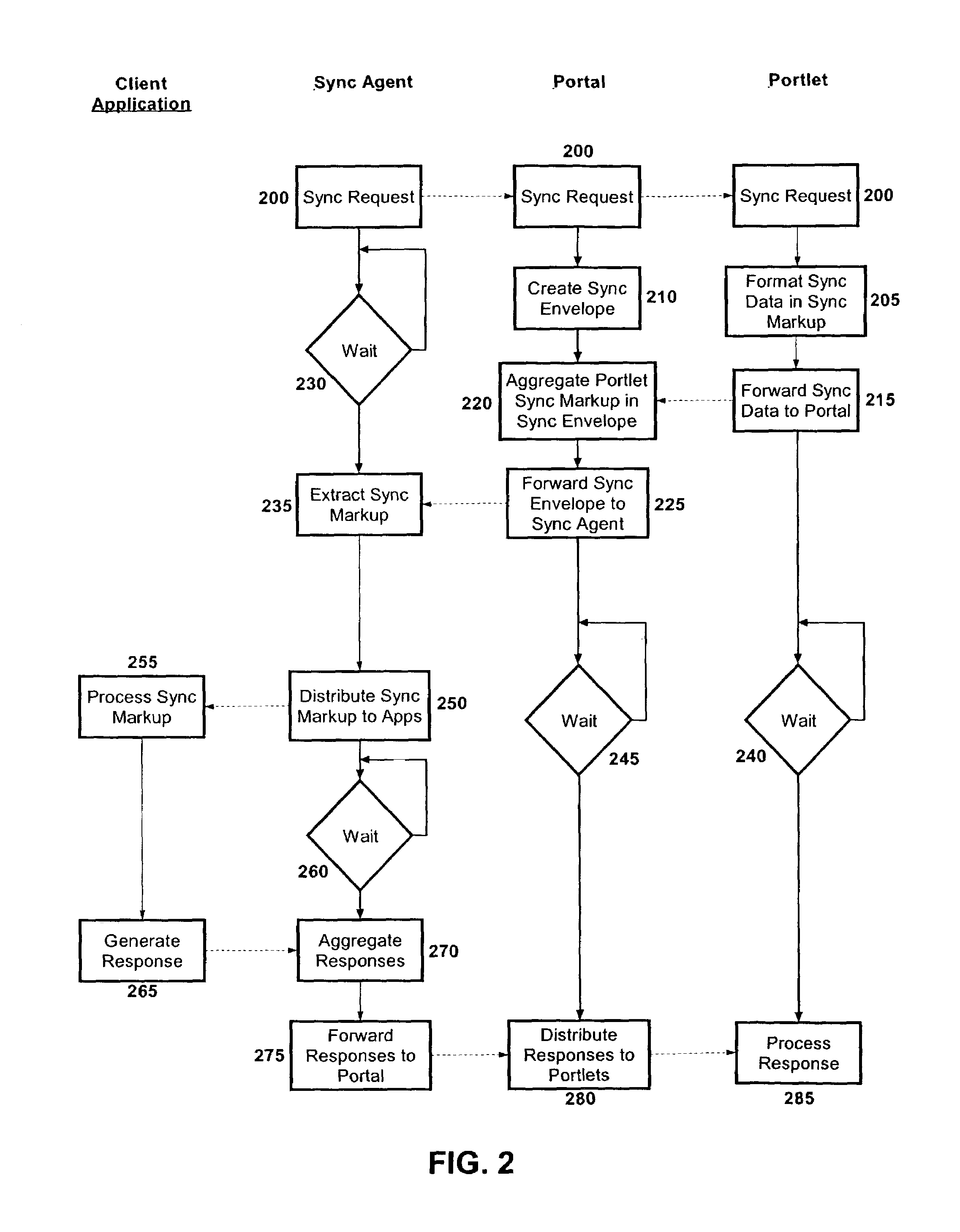
Portal/portlet application data synchronization
InactiveUS7103844B2Data processing applicationsMultiple digital computer combinationsData synchronizationContent distribution
A portlet data synchronization system, method and apparatus. The system can include a portal server configured to distribute portal content to requesting clients over a computer communications network. The system further can include one or more portlets hosted within the portal content through the portal server. Finally, the system can include a synchronization aggregator configured to aggregate synchronization markup for individual ones of the portlets in a single synchronization envelope. The synchronization aggregator further can be have a configuration for distributing responses to the synchronization markup to respective ones of the portlets.
Owner:IBM CORP
Multi-parameter monitoring and health management system based on smart watch
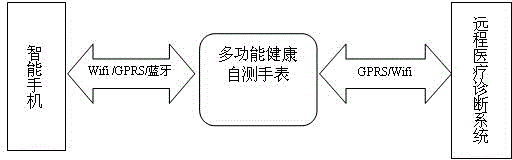
ActiveCN104305972ARealize acquisitionIn line with daily habitsTransmission systemsTime-pieces with integrated devicesNetwork terminationNetwork communication
The invention relates to a multi-parameter monitoring and health management system based on a smart watch. The multi-parameter monitoring and health management system comprises a remote medical system, a smart mobile phone and the multifunctional health self-testing watch; the remote medical system is connected into a computer communication network; the computer communication network is provided with a user network terminal; the multifunctional health self-testing watch is provided with a health information sensor used for collecting needed health information and provided with a network communication circuit capable of being in communication with the user network terminal and a mobile communication circuit capable of being in communication with the smart mobile phone; when the multi-parameter monitoring and health management system is used, a user can wear the multifunctional health self-testing watch like a common watch, and then health information collection can be achieved; the collected health information is sent to the remote medical system and the smart mobile phone. The multi-parameter monitoring and health management system is convenient to carry; various sensors can be arranged according to needs; the needs for monitoring various health and disease conditions are met.
Owner:BEIJING HUIREN KANGNING TECH DEV
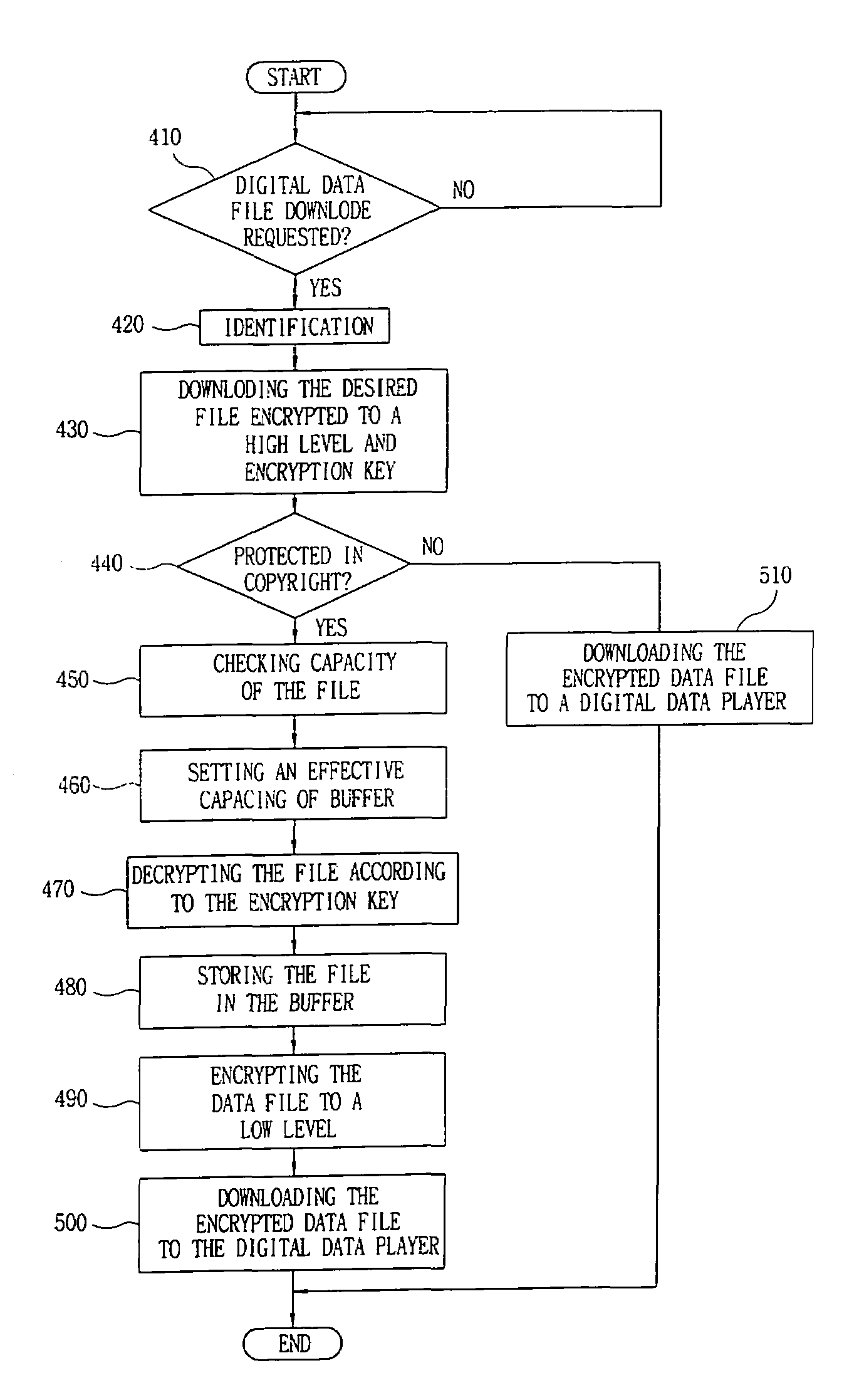
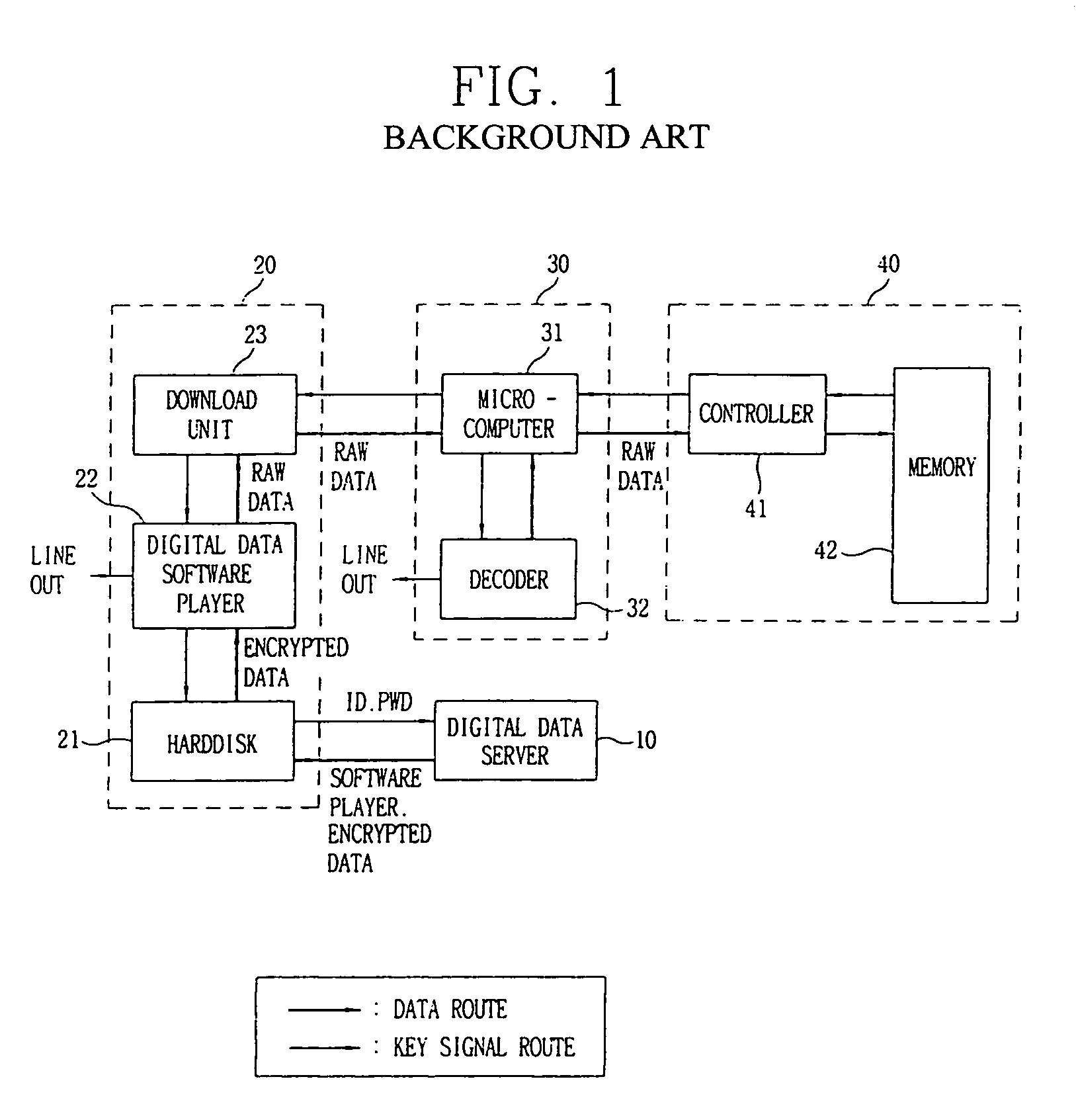
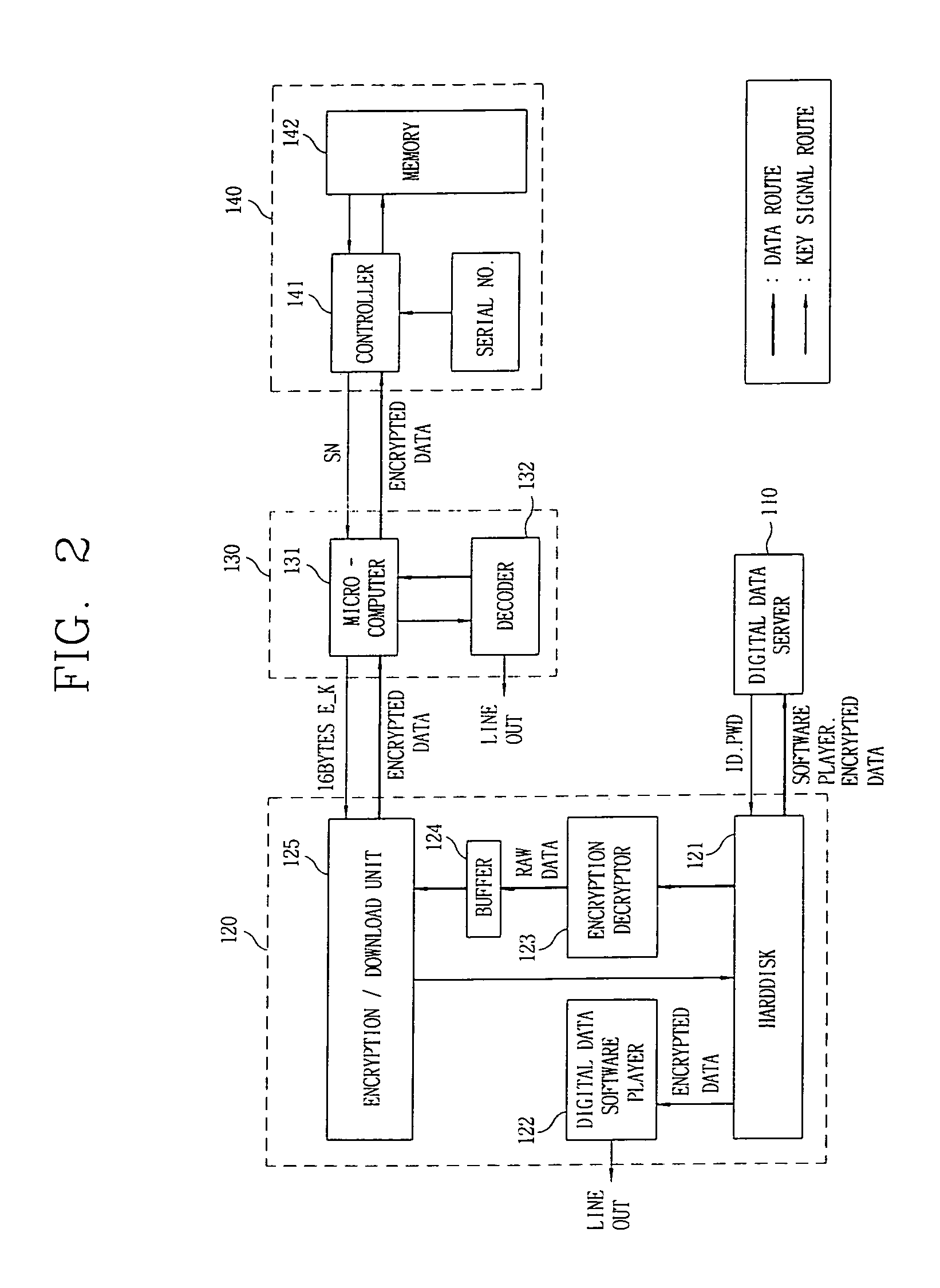
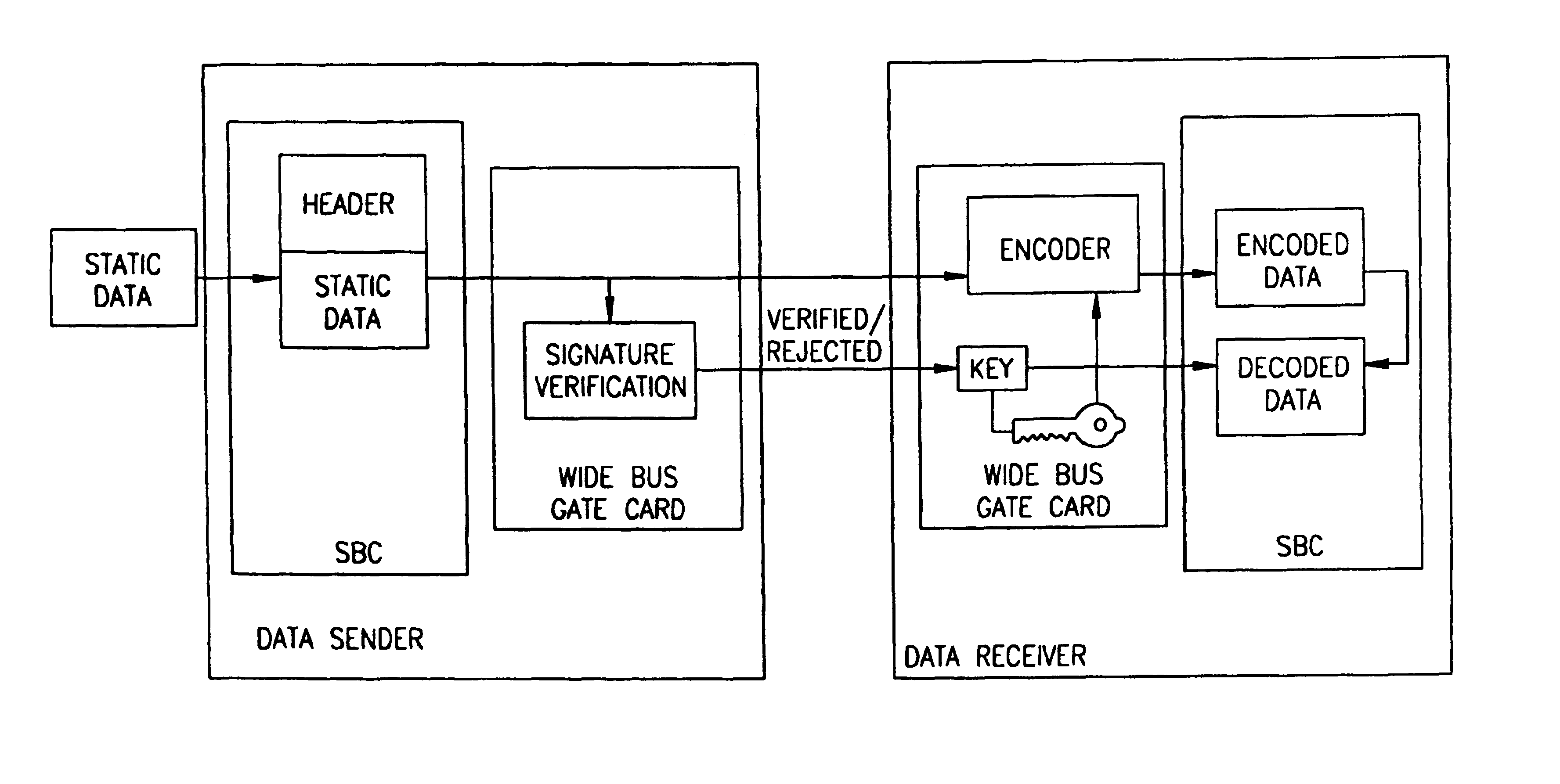
Digital data file encryption apparatus and method and recording medium for recording digital data file encryption program thereon
InactiveUS7130426B1Program control using stored programsMultiple keys/algorithms usageDigital dataData file
A digital data file encryption system and method where digital data encrypted to a high level and an encryption key are received and stored in a computer. The stored, encrypted digital data is decrypted on the basis of the encryption key and stored in a buffer of a predetermined size. Output digital data from the buffer is reencrypted to a low level of encryption and downloaded to a digital data playing device or a data storage medium. Therefore, a digital audio or video data file is prevented from being diverted in unencrypted form from a computer communication network when it is transmitted to a personal computer through the computer communication network and, in turn, downloaded to the digital data playing device. Further, the digital data playing device is prevented from rising in cost due to the use of simple encryption for data downloaded to the playing device.
Owner:LG ELECTRONICS INC
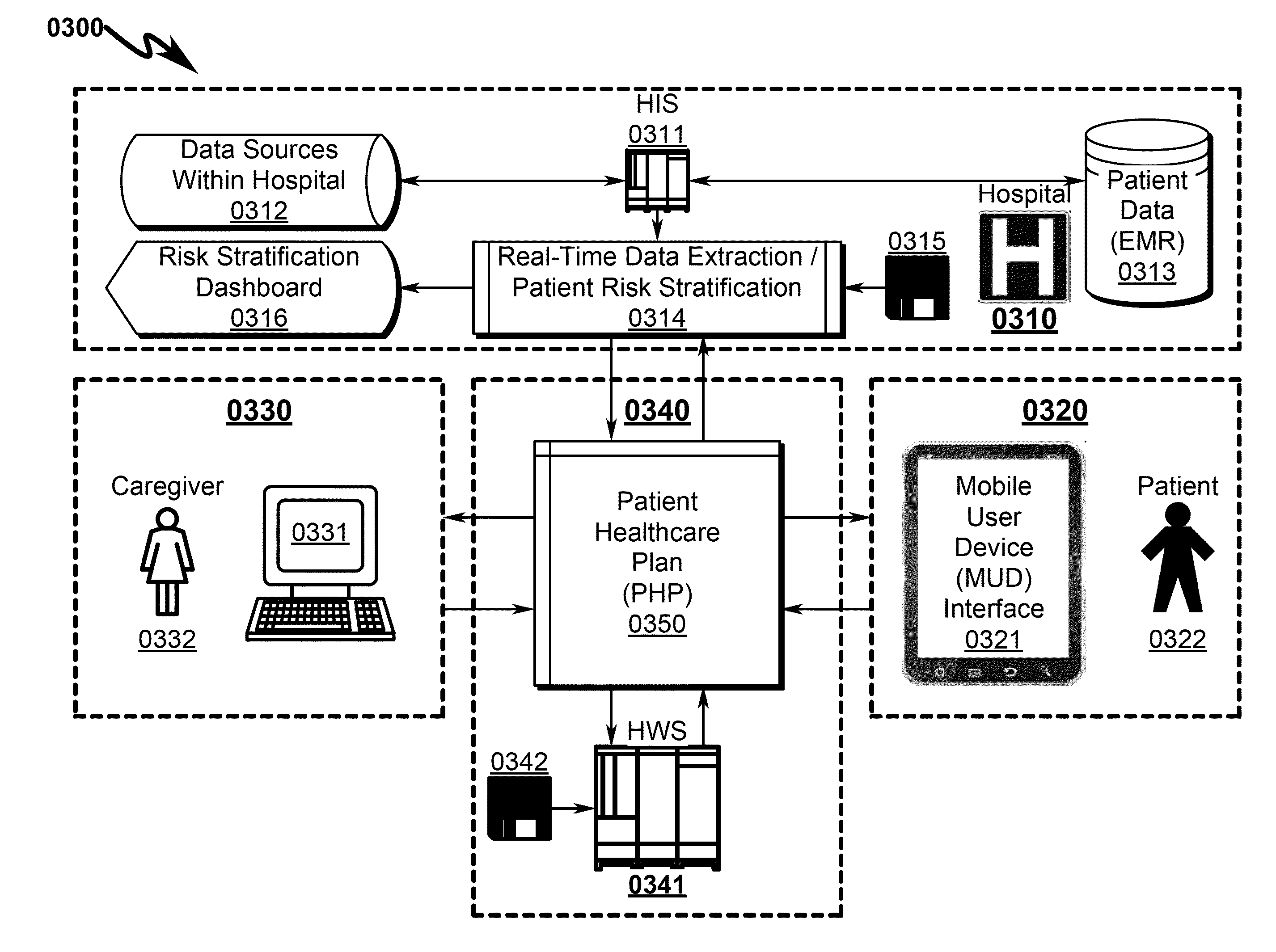
Healthcare delivery system and method
ActiveUS20140297301A1Risk minimizationTherapiesOffice automationMedical recordComputer communication networks
A system and method integrating healthcare delivery to patients using data bridges that connect healthcare providers, patients, patient medical education, and patient monitoring devices is disclosed. The system incorporates a mobile user interface device (MUD) allowing user inputs or detected events from a variety of medical instrumentation devices (MID) to be controlled by a healthcare web server computer (HWS) over a computer communication network (CCN). Information retrieved from the MID and transmitted by the MUD to the HWS is then used by a patient healthcare monitor (PHM) process to populate a medical records database (MRD). MRD contents are then matched to patient healthcare plan (PHP) event / time triggers (ETT) that drive information from a provider content database (PCD) to the MUD through the HWS over the CCN. Healthcare provider update / control of the PHP / ETT / PCD allow integration of patient educational materials with patient health status monitoring.
Owner:VIVIFY HEALTH INC
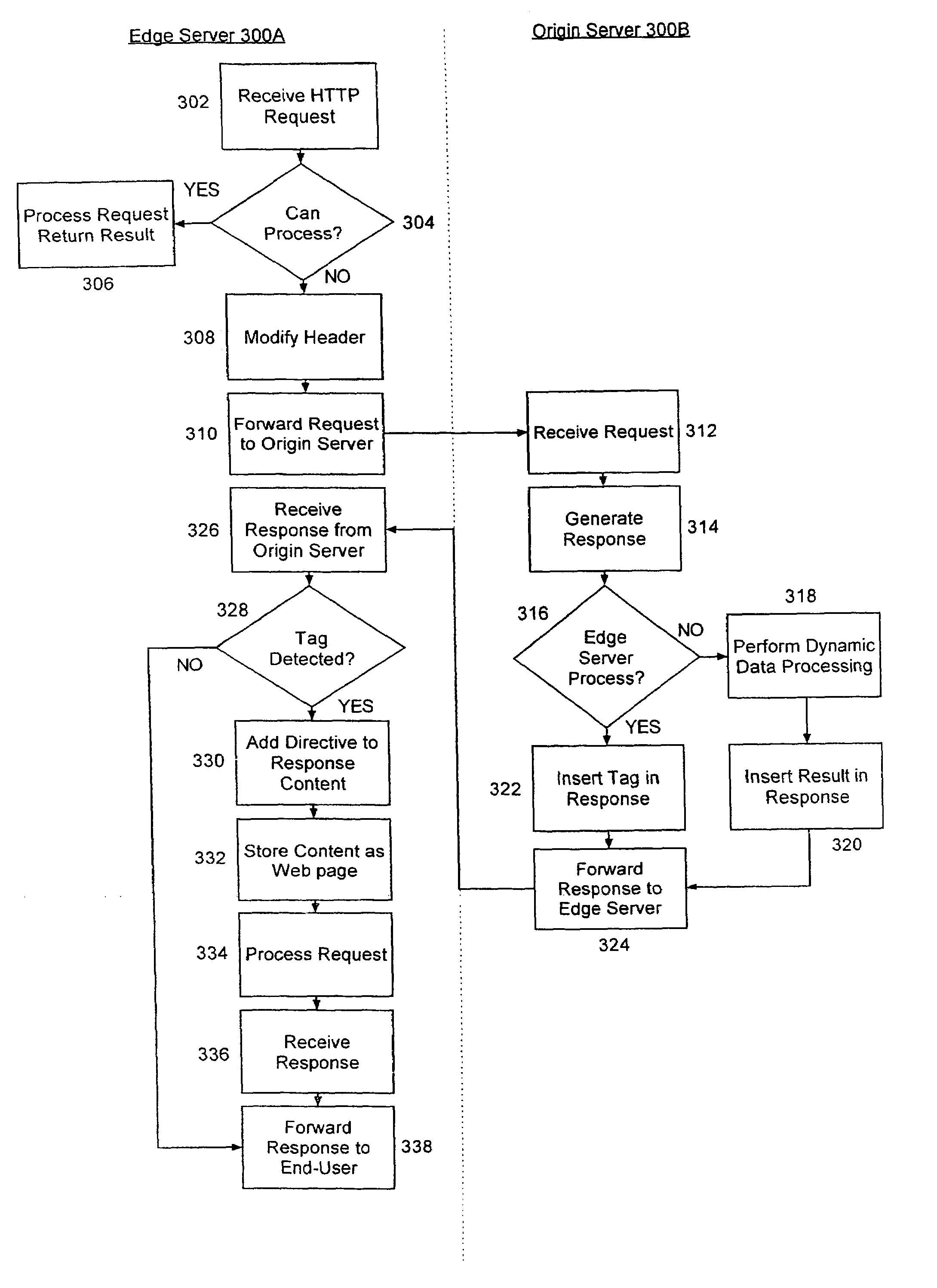
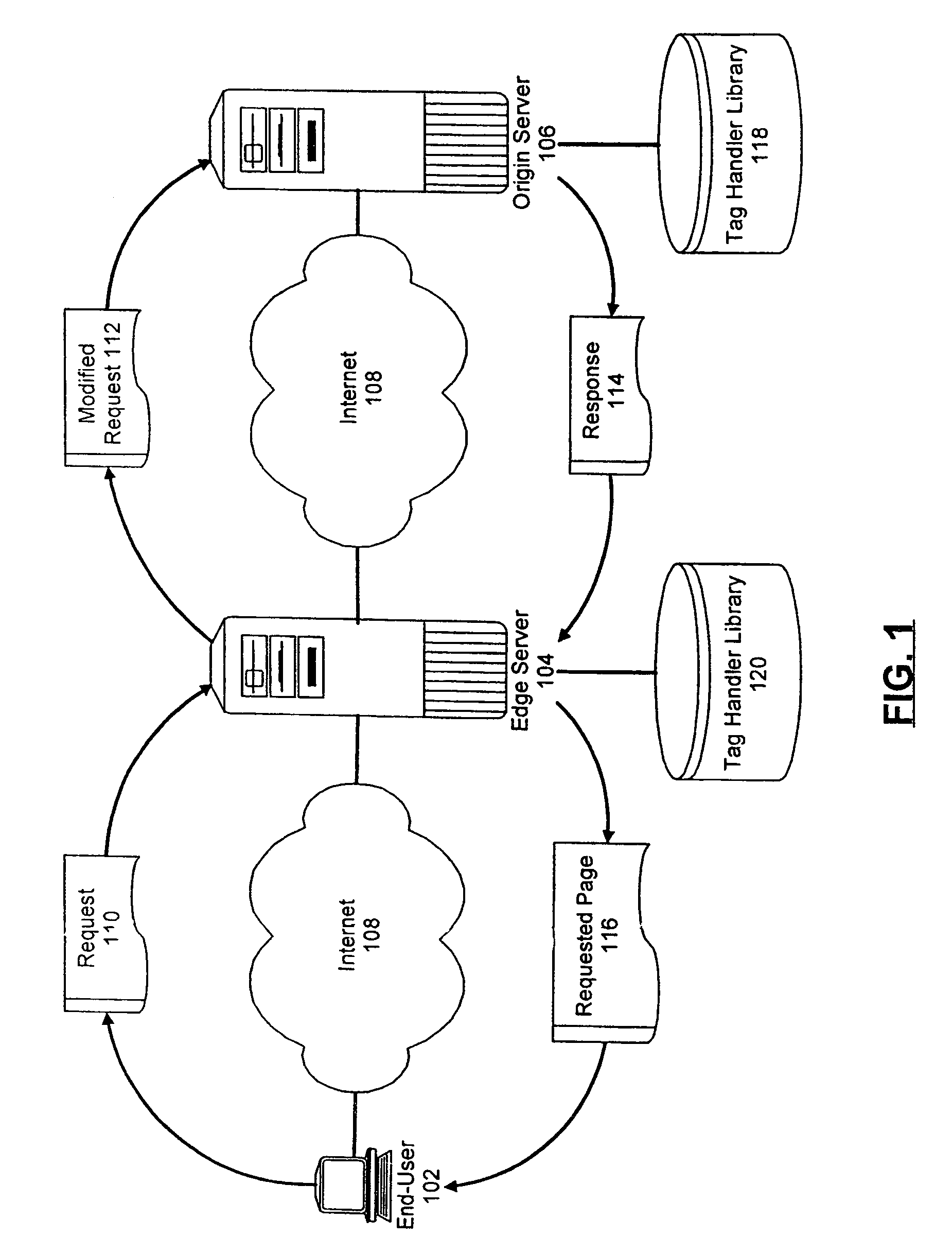
Selectively handling data processing requests in a computer communications network
InactiveUS7155478B2Blocking in networkNetwork latencyMultiple digital computer combinationsTransmissionComputer networkEdge server
A system and method for selectively handling requests for dynamic data processing. In the system and method, requests for dynamic data processing can be received in an origin server, but the dynamic data processing can be deferred to an edge server in those circumstances where it is dynamically determined that the edge server is capable of performing such dynamic data processing. In this way, network transmission latencies can be avoided by performing dynamic data processing in those edge servers closest to the requesting user.
Owner:LINKEDIN
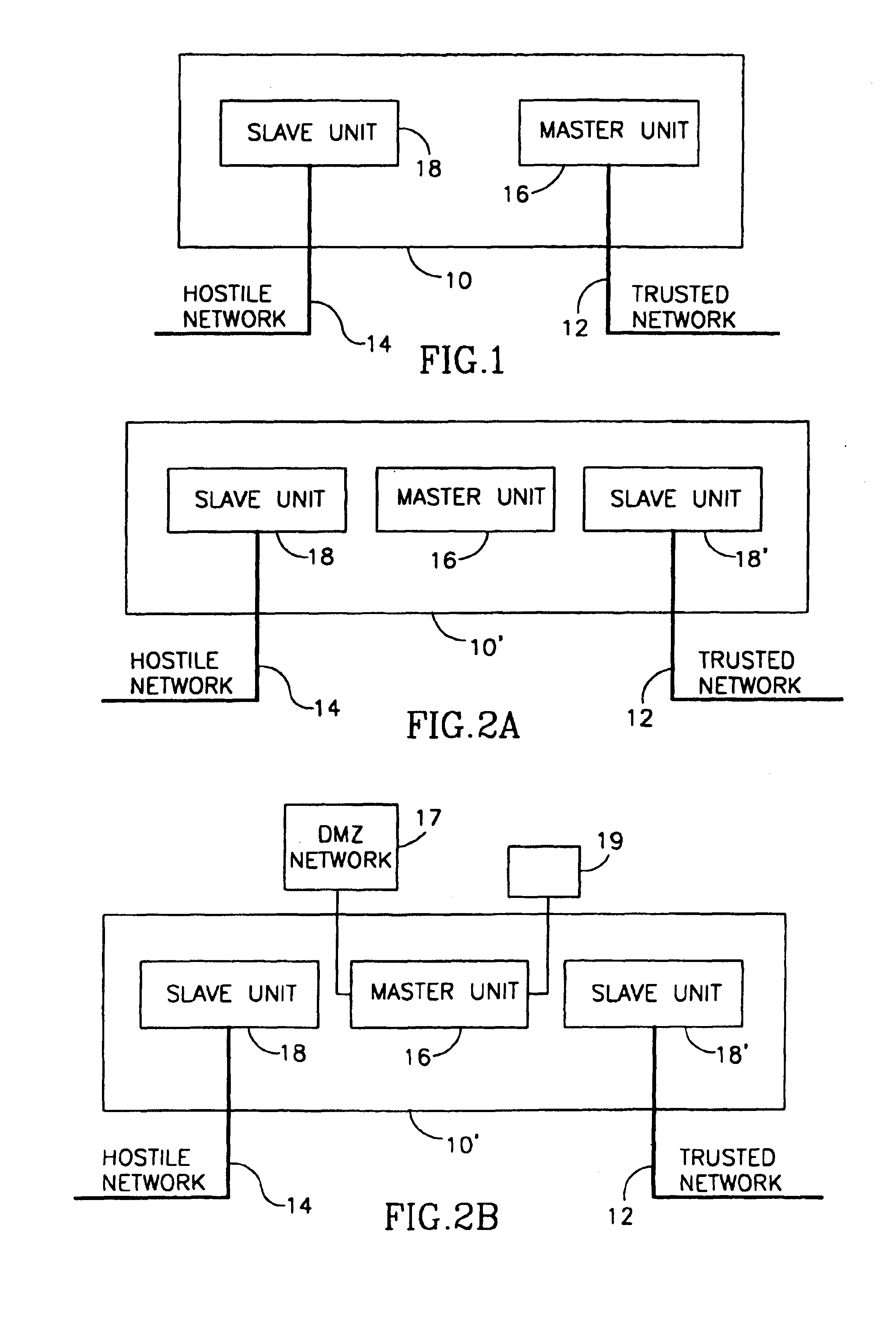
System and method for securing a computer communication network
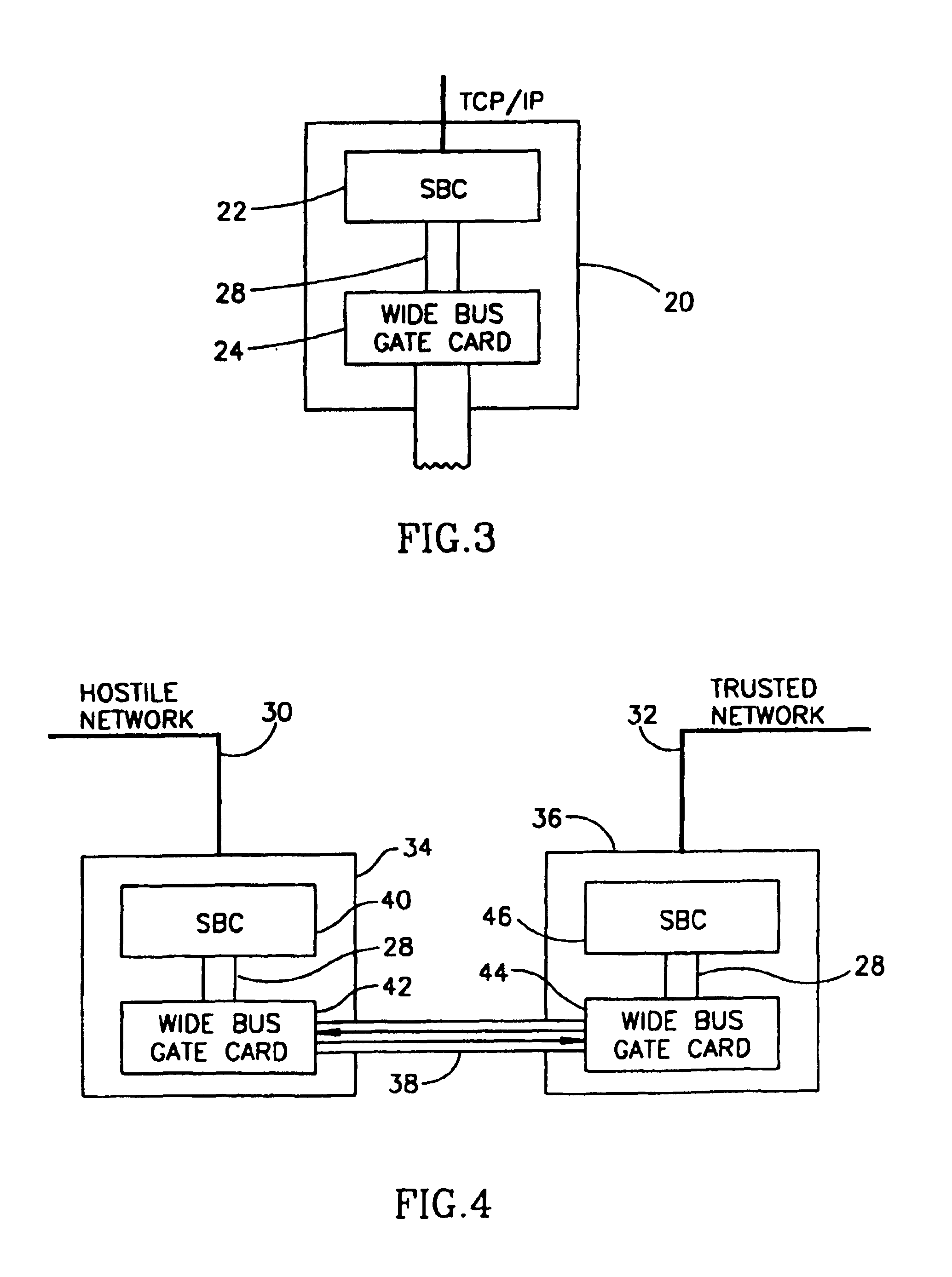
InactiveUS6865672B1Different solutionDigital data processing detailsUnauthorized memory use protectionCommunication unitComputer network
A system for providing a trusted computer communication network including a master decision maker unit coupled to the trusted network; and at least one slave communication unit coupled to the master unit by a wide bus connection that has multiple unidirectional communication channels, and connected to a non-trusted network; wherein the trusted network is physically isolated at all times from the non-trusted network, and all data transported between the trusted network and the non-trusted network is transported between the master unit and the slave unit.
Owner:SPEARHEAD TECH
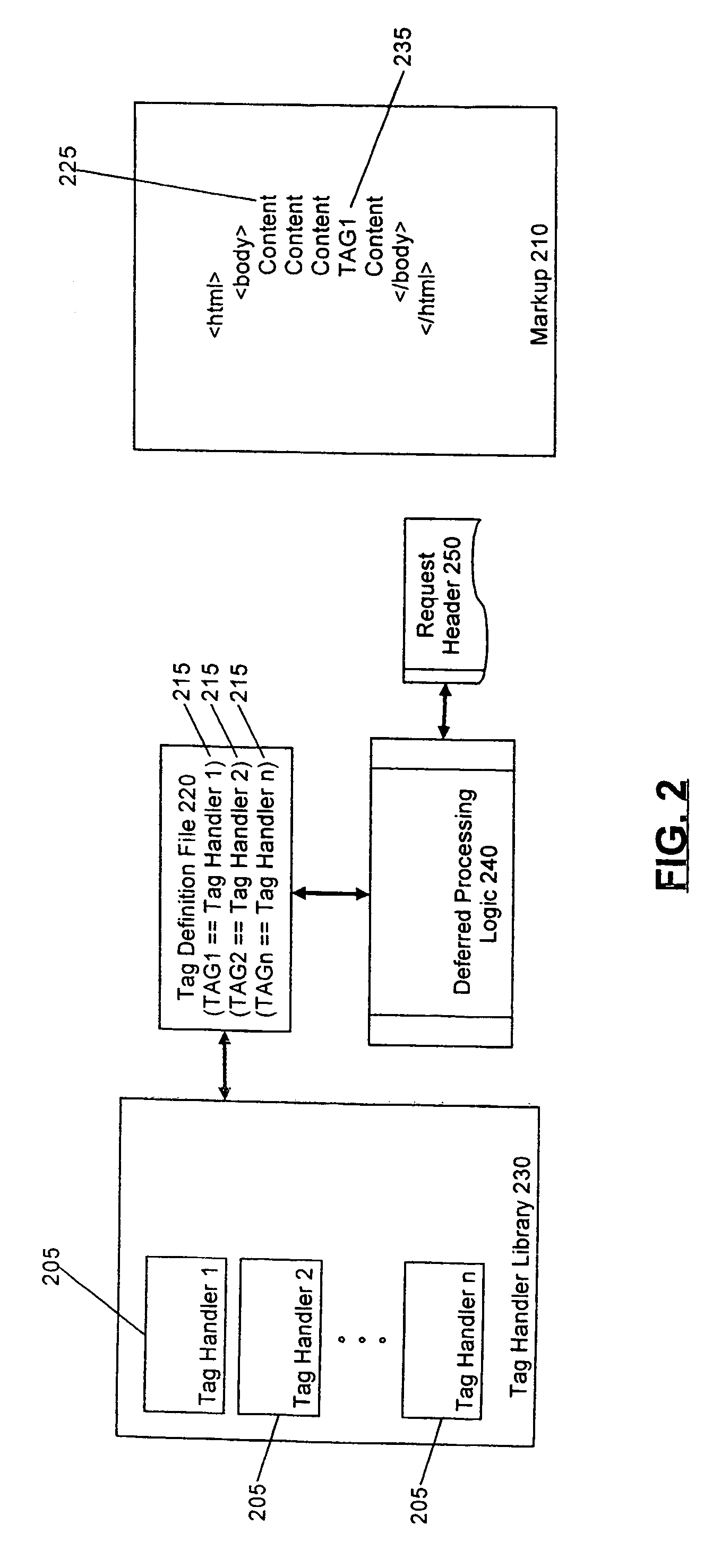
Dispatching request fragments from a response aggregating surrogate
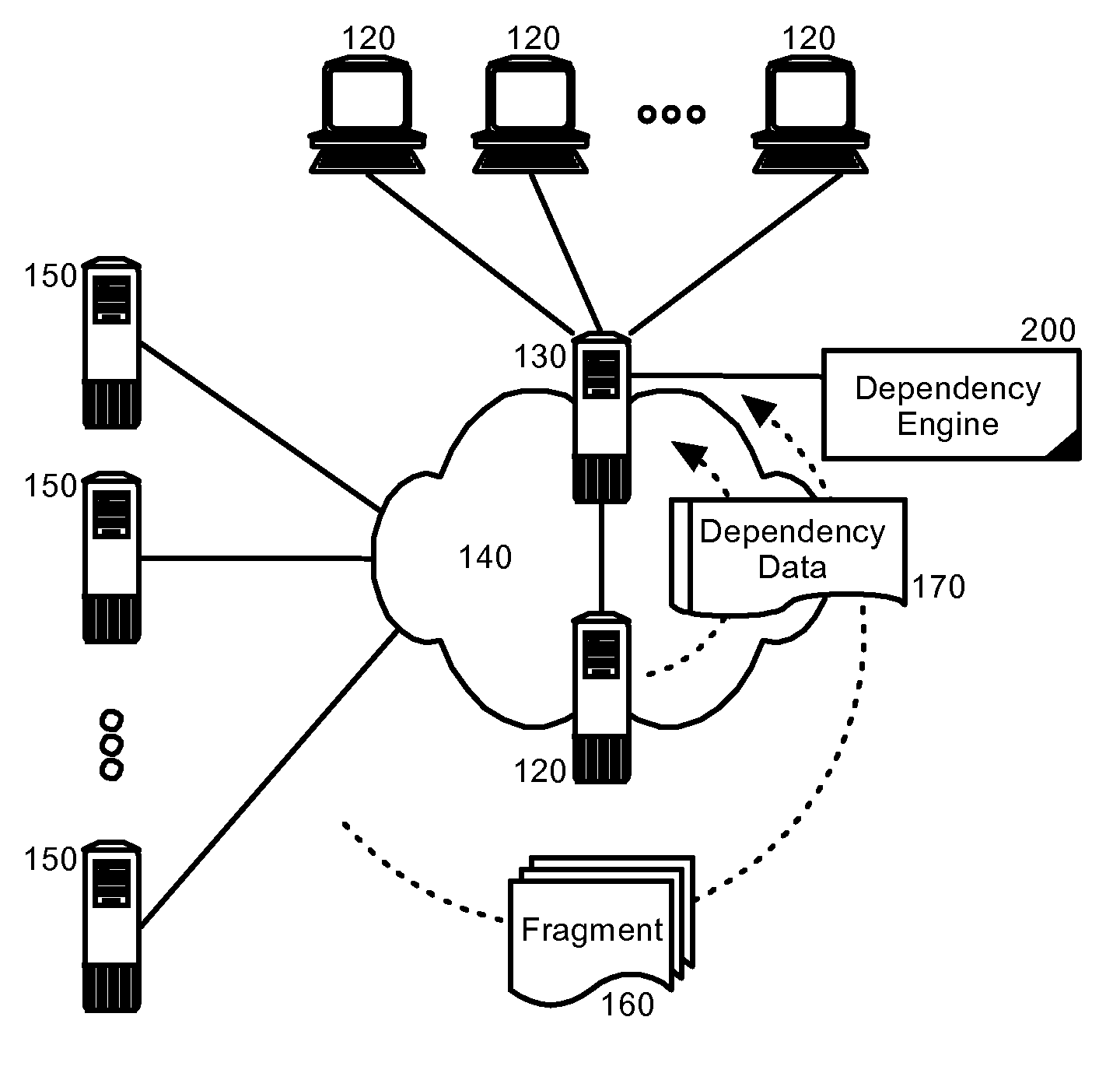
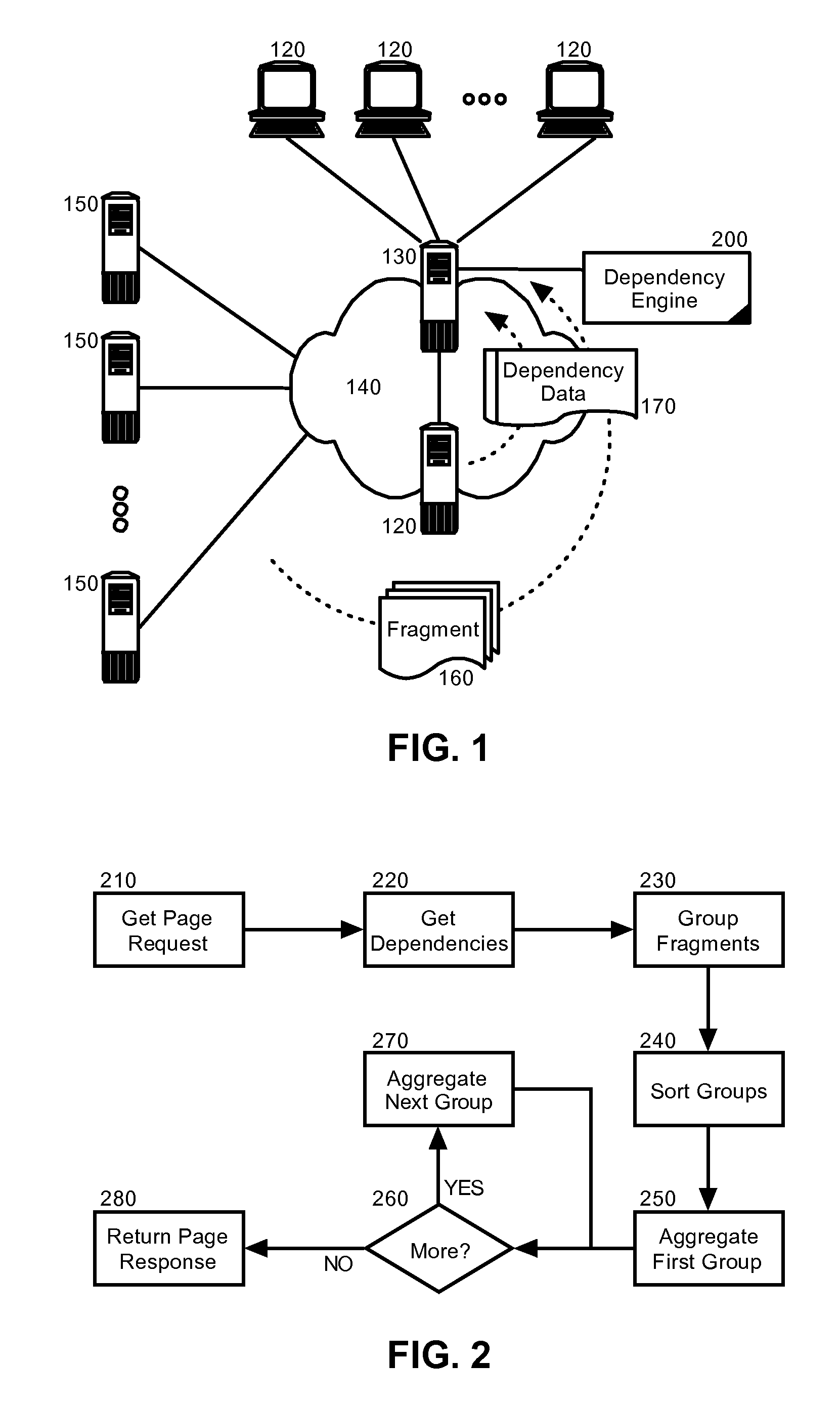
InactiveUS20080016194A1Digital computer detailsWebsite content managementData processing systemContent distribution
Embodiments of the present invention address deficiencies of the art in respect to edgified content delivery and provide a method, system and computer program product for dispatching of request fragments from a response aggregating surrogate. In one embodiment, an edgified content distribution data processing system can include an origin server configured to server markup specified pages formed from dynamically arranged fragments and a surrogate server communicatively linked to the origin server over a computer communications network and acting as a surrogate at an edge of the network on behalf of the origin server. A dependency engine can be coupled to the surrogate server and can include program code enabled to group the fragments according to interdependencies among the fragments and to load fragment groups in sequence to satisfy the interdependencies.
Owner:IBM CORP
Method and Apparatus for Heuristic/Deterministic Finite Automata
InactiveUS20070271613A1Overcome disadvantagesMore scalableMemory loss protectionError detection/correctionAnti virusExtensibility
One embodiment of the present invention is a method for processing data in a computer or computer communications network that includes the steps of analyzing data using at least a first Heuristic / Deterministic Finite Automata (H / DFA), to classify data based upon pre-programmed programmed classification values assigned to different possible input data and / or pre-trained or dynamically updated heuristic engine output, and to select data for further processing based upon the resultant classification values that the logically interconnected look-up tables and / or heuristic components output given the input data. This exemplary embodiment overcomes disadvantages of previous methods for providing access control list, firewall, intrusion detection, intrusion prevention, spam filtration, anti-spyware, anti-phishing, anti-virus, anti-trojan, anti-worm, other computer security, routing, and / or switching related functionality. Heuristic algorithms, or a combination of logically interconnected look-up tables and heuristic techniques can also implement the H / DFA functionality. There are significant advantages in speed and scalability.
Owner:TECHGUARD SECURITY L L C
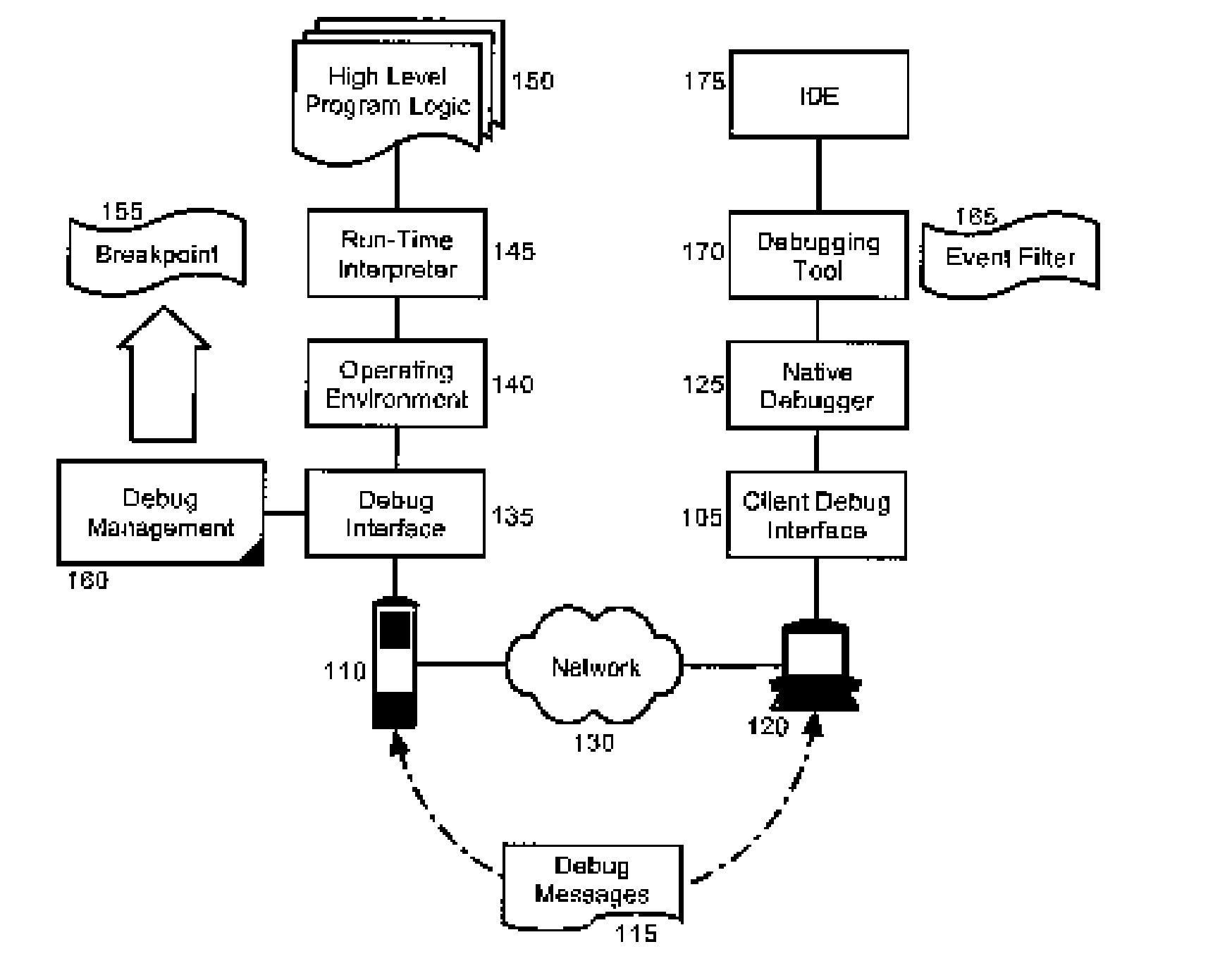
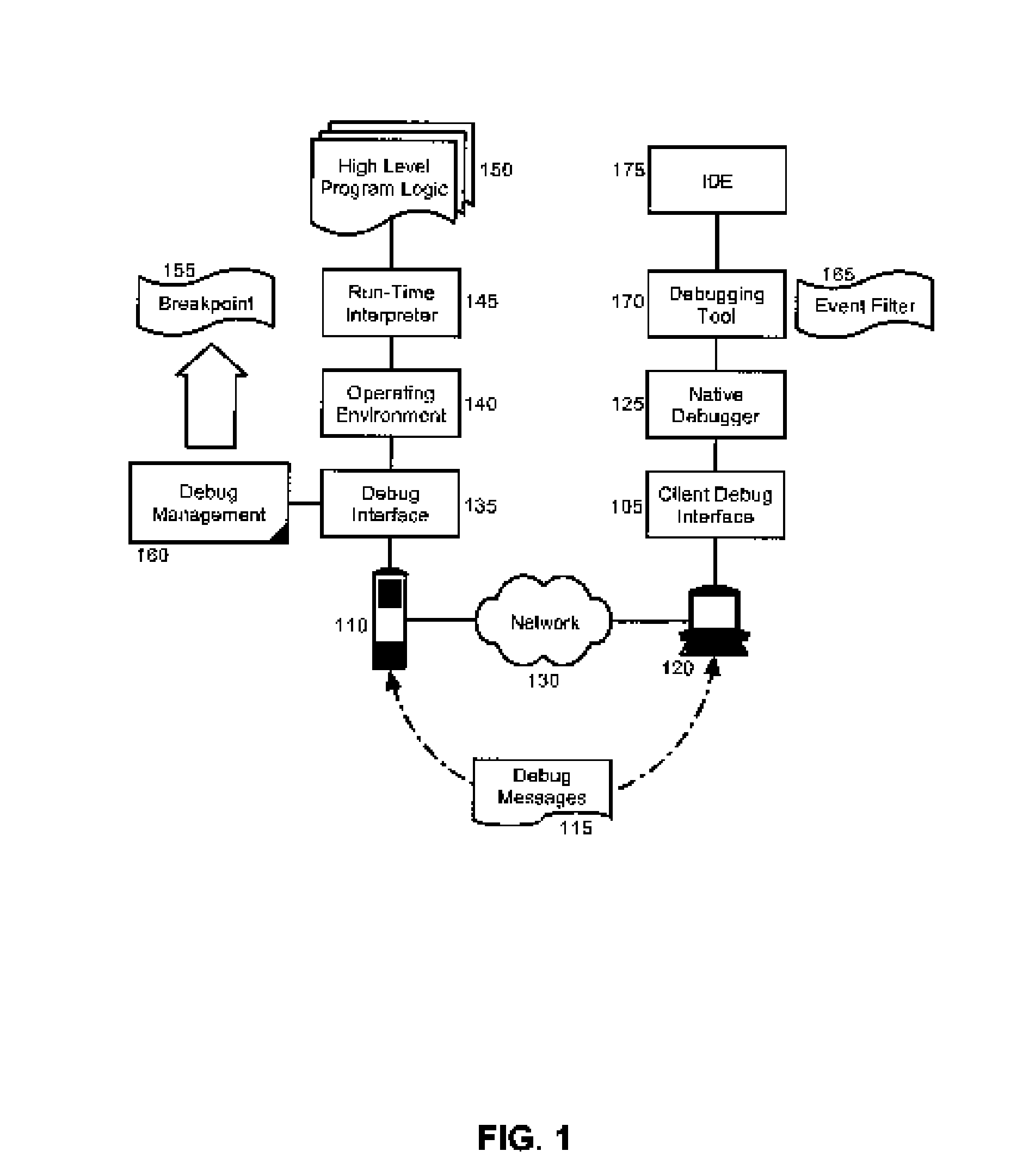
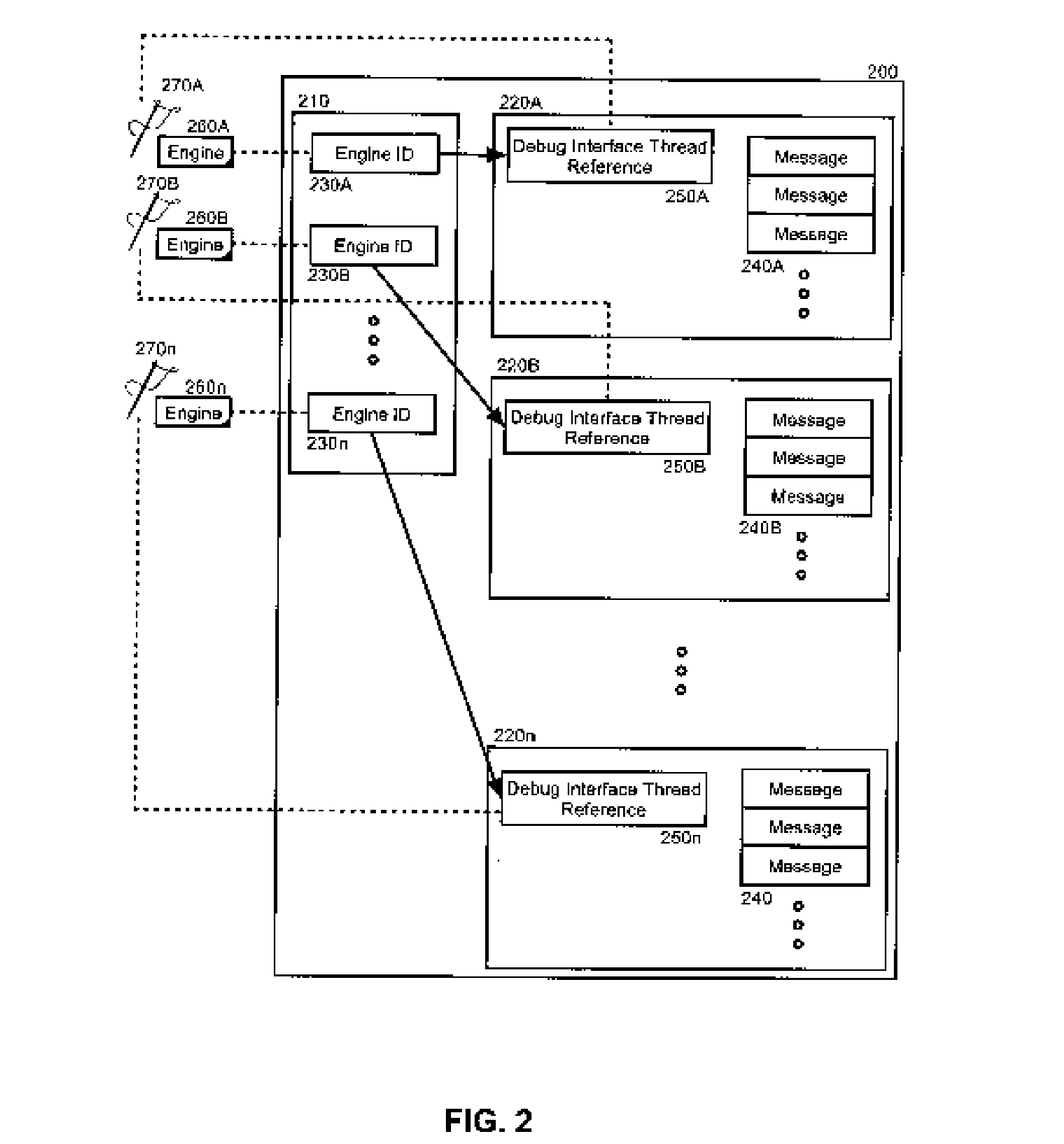
Debugging a High Level Language Program Operating Through a Runtime Engine
InactiveUS20060174225A1Error detection/correctionSpecific program execution arrangementsMessage queueComputer communication networks
In a remote runtime engine, a method for debugging a remotely executing high level language specified computer program can include the steps of interpreting a high level language specified computer program and receiving debug messages from a debug tool over a computer communications network. Consequently, the received debug messages can be applied to the high level language specified computer program. Additionally, debug messages can be sent to the debug tool over the network. In a particular aspect of the invention, the method can include setting a breakpoint in the runtime engine on a method specifying logic for receiving the debug messages. Responsive to reaching of the breakpoint, the receiving and applying steps can be performed for a debug message in a message queue in the debug tool. Similarly, a breakpoint can be set in the remote runtime engine, and responsive to reaching the breakpoint, the sending step can be performed.
Owner:IBM CORP
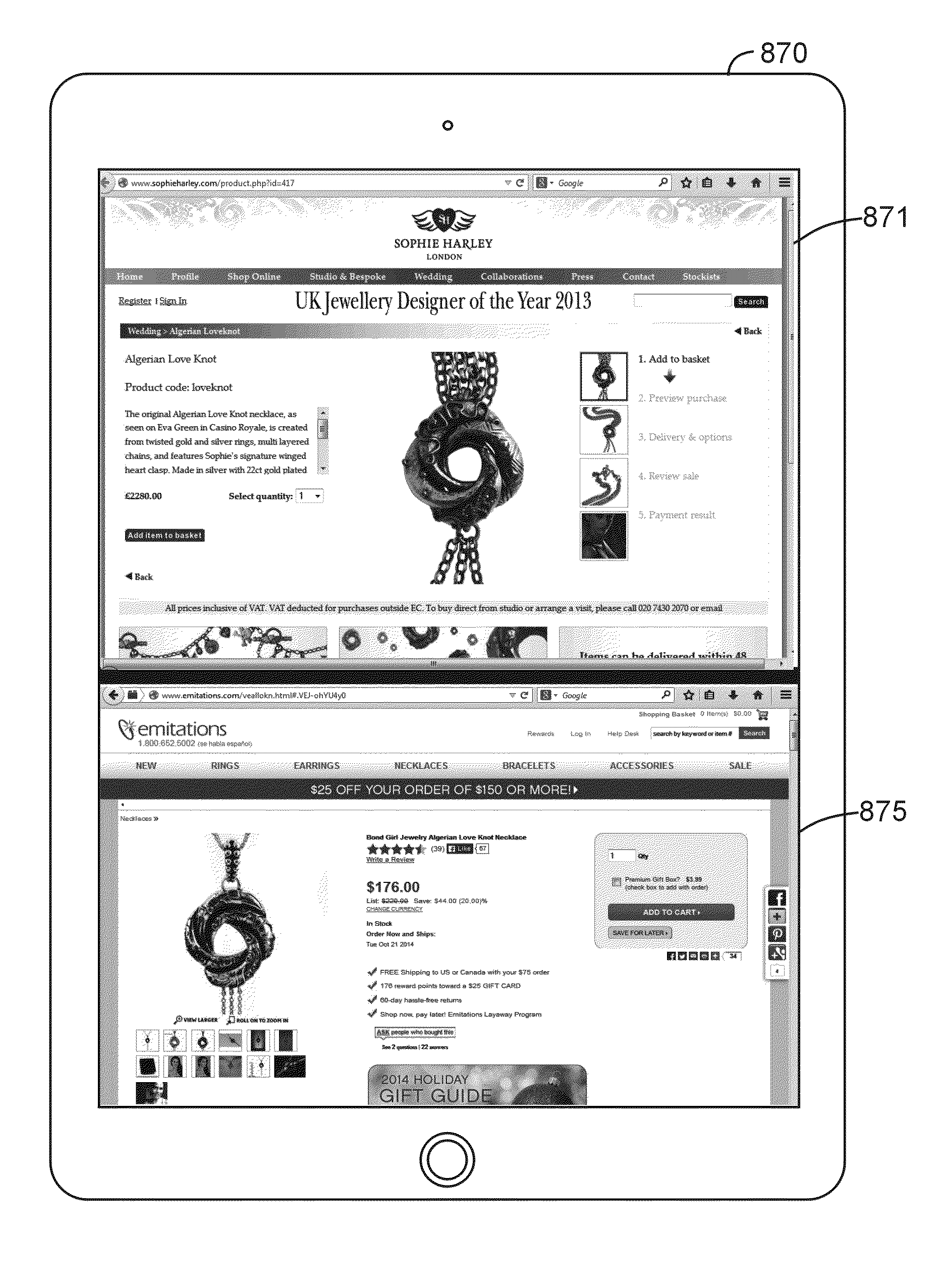
Second Screen Shopping Function
InactiveUS20150110457A1Display delayTelevision system detailsUsing non-detectable carrier informationVideo tapeComputer communication networks
Systems for, and methods of, displaying video information comprising: a second screen device obtaining current play position data of a video being played on a primary screen device (e.g., obtaining from the primary screen device an identification of a current play position of the video, or obtaining information to generate an acoustic fingerprint of the video); determining a current play position of the video playing on the primary screen device based upon the current play position data (e.g., identification of the current play position or the acoustic fingerprint); downloading information (e.g., video map, subtitles, moral principles, objectionable content, memorable content, performers, geographical maps, shopping, plot point, item, ratings, and trivia information) over a computer communications network into the memory of the second screen device; and displaying information on the second screen device synchronized with the contemporaneously played video on the primary screen device.
Owner:CUSTOMPLAY
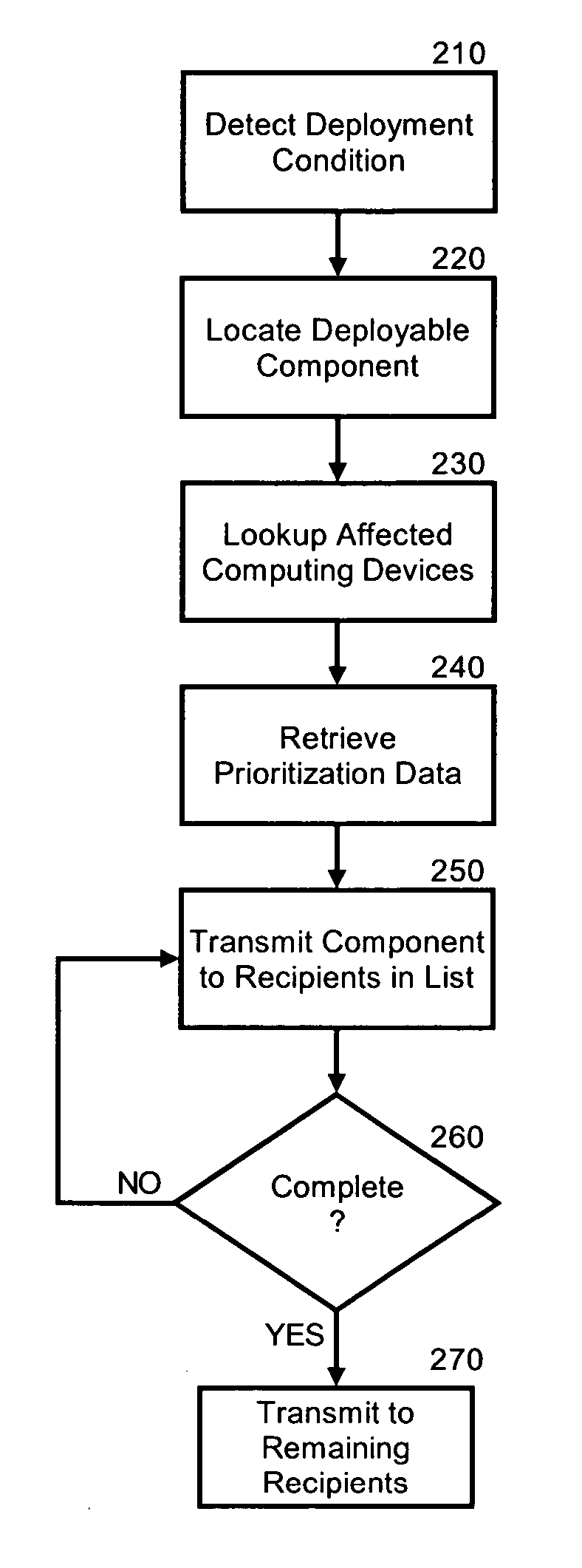
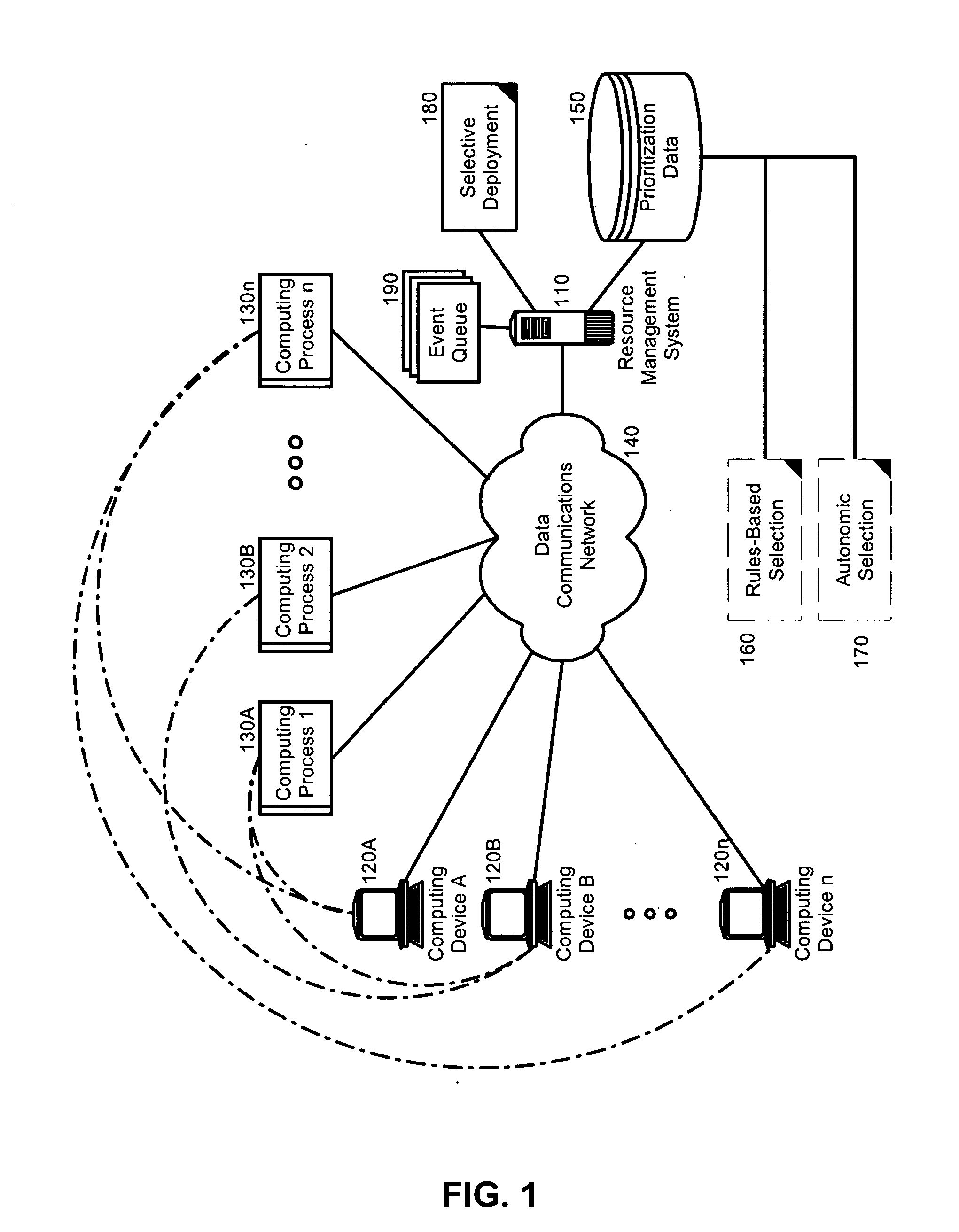
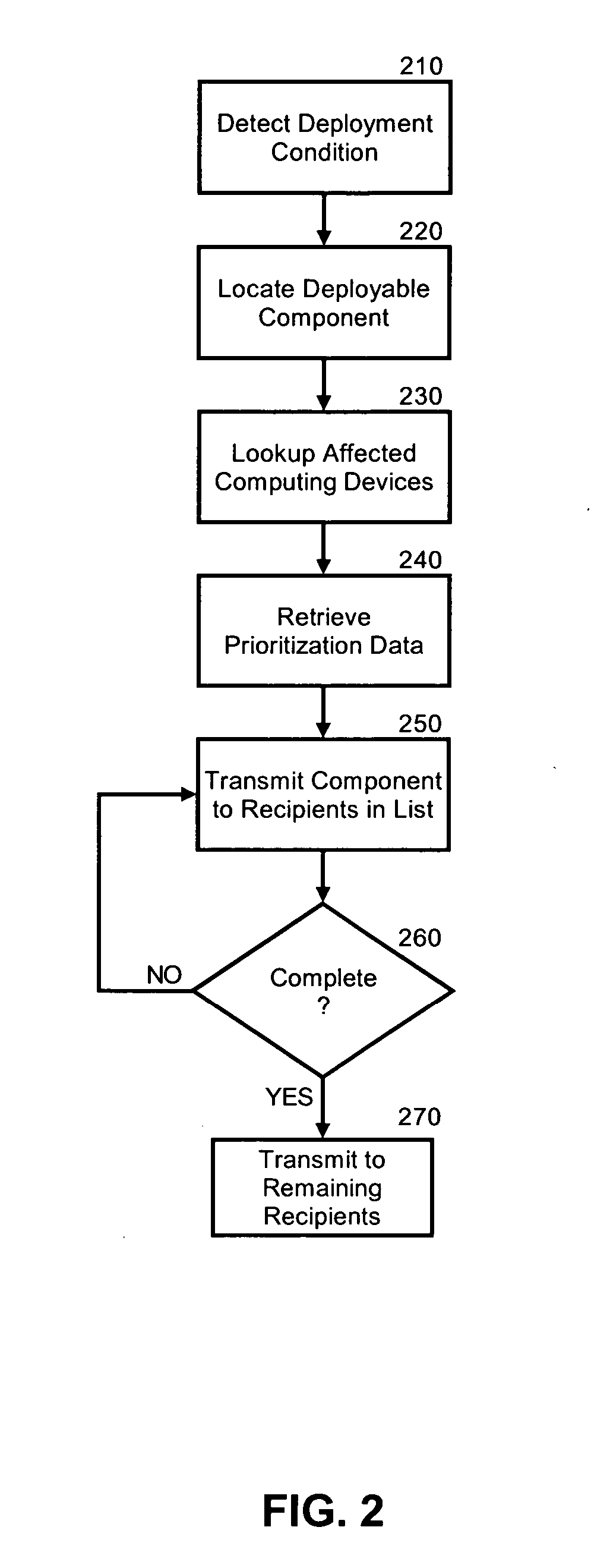
Prioritization of application component distribution
InactiveUS20060031371A1Make up for deficienciesCriteria allocationMultiple digital computer combinationsResource Management SystemData selection
A method, system and apparatus for the prioritized distribution of application components based upon computing process impact. An application component distribution system which has been configured in accordance with the present invention can include a resource management system configured to manage communicatively coupled client computing devices over a computer communications network. A data store can be arranged to store prioritization data specifying which of the client computing devices are to first receive distributions of specified application components. Finally, a selective deployment processor can be programmed to selectively deploy application components to the client computing devices based upon the prioritization data.
Owner:IBM CORP
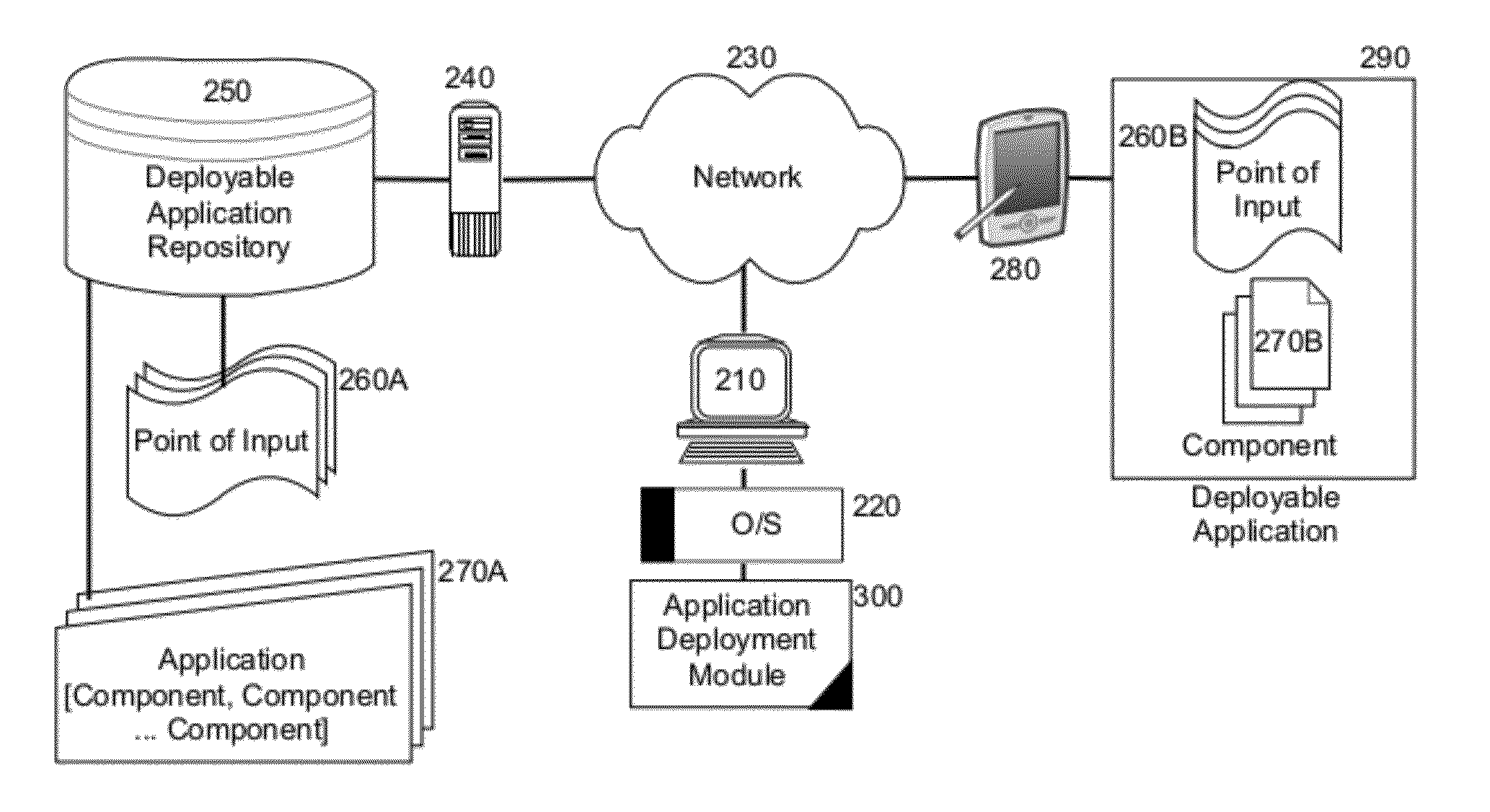
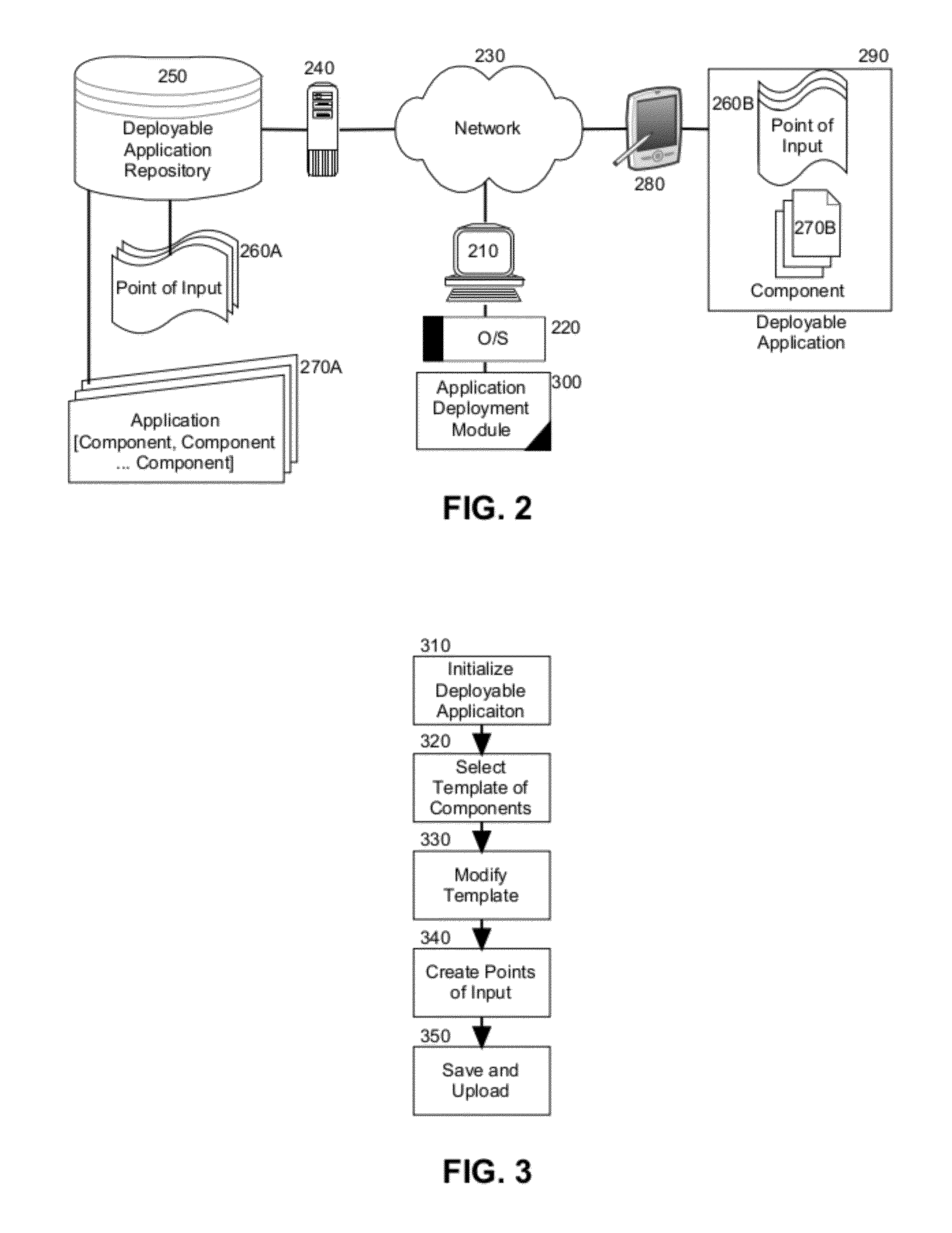
Crowdsourcing location based applications and structured data for location based applications
Embodiments of the present invention provide a method, system and computer program product for deploying a location based applications providing crowdsourced structured points of input for data entry. In an embodiment of the invention, a method for deploying a location based application providing crowdsourced structured points of input for data entry includes the selection of a location based application component, such as a map, for inclusion in a deployable application and the definition of a point of input for the location based application component. In this regard, the point of input can include at least one user interface control accepting data input of structured data. Finally the deployable application can be uploaded to a deployable application repository over a computer communications network for deployment to requesting mobile devices over the computer communications network.
Owner:IBM CORP
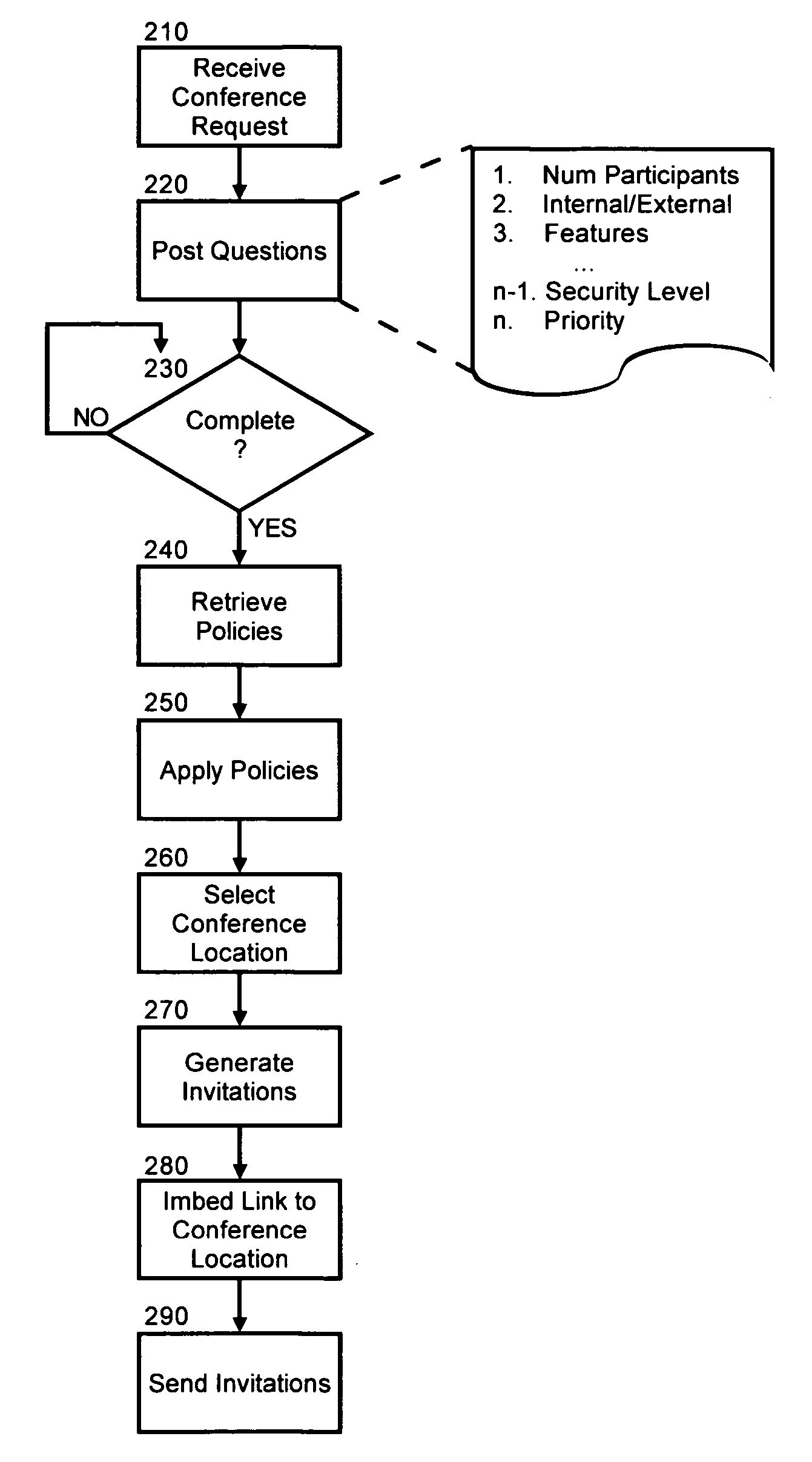
Policy based provisioning of web conferences
InactiveUS20050193129A1Special service provision for substationMultiple digital computer combinationsComputer communication networksEnd user
A method, system and apparatus for the policy driven provisioning of a Web conference. A Web conference provisioning system can include a policy manager coupled to at least two different Web conferencing platforms over a computer communications network. The policy manager can have a configuration for processing a request for a Web conferencing from a communicatively linked end user to select one of the Web conferencing platforms to host the Web conference. Preferably, two of the different Web conferencing platforms can include a CPE based platform and a hosted platform.
Owner:IBM CORP
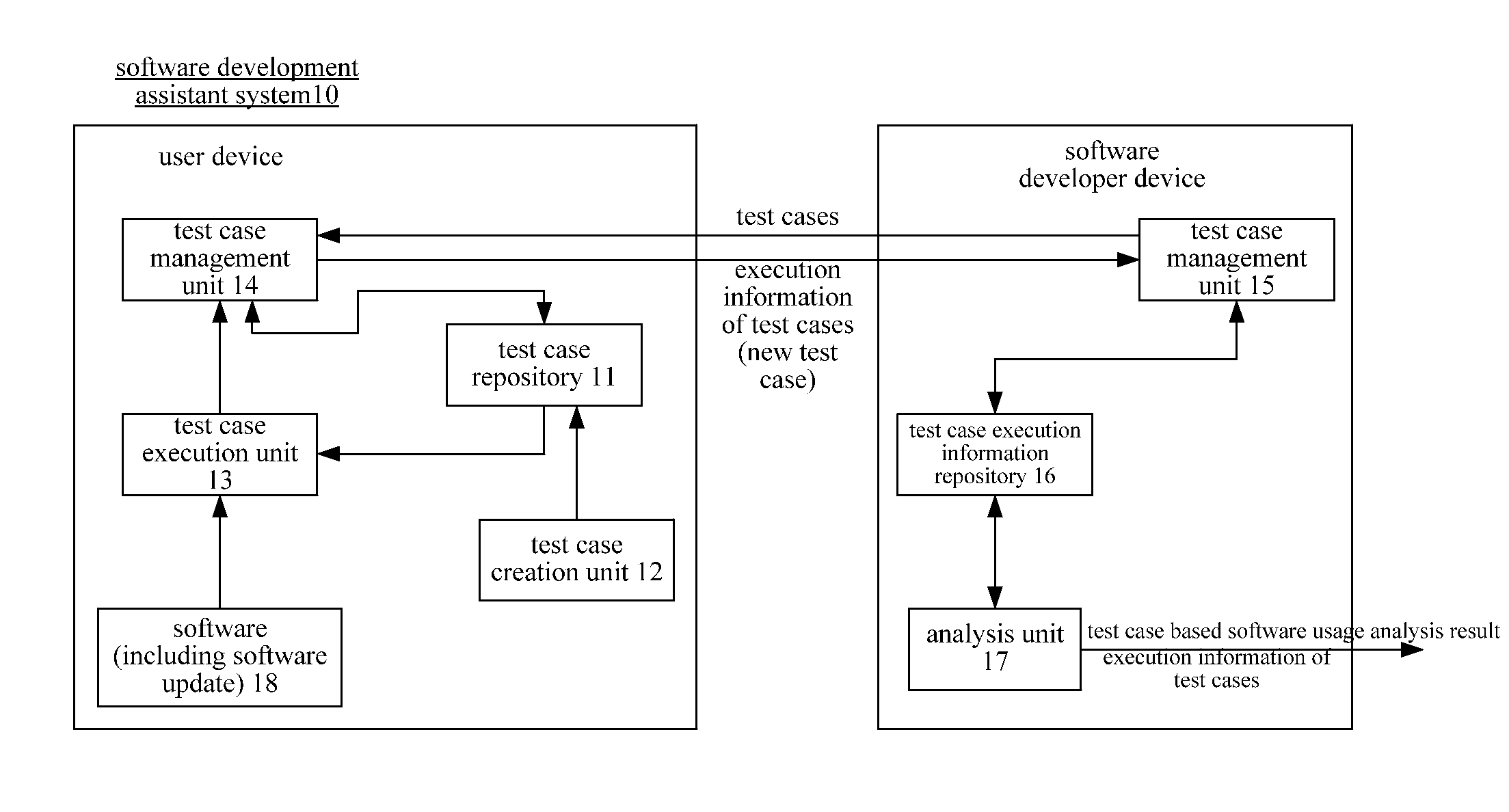
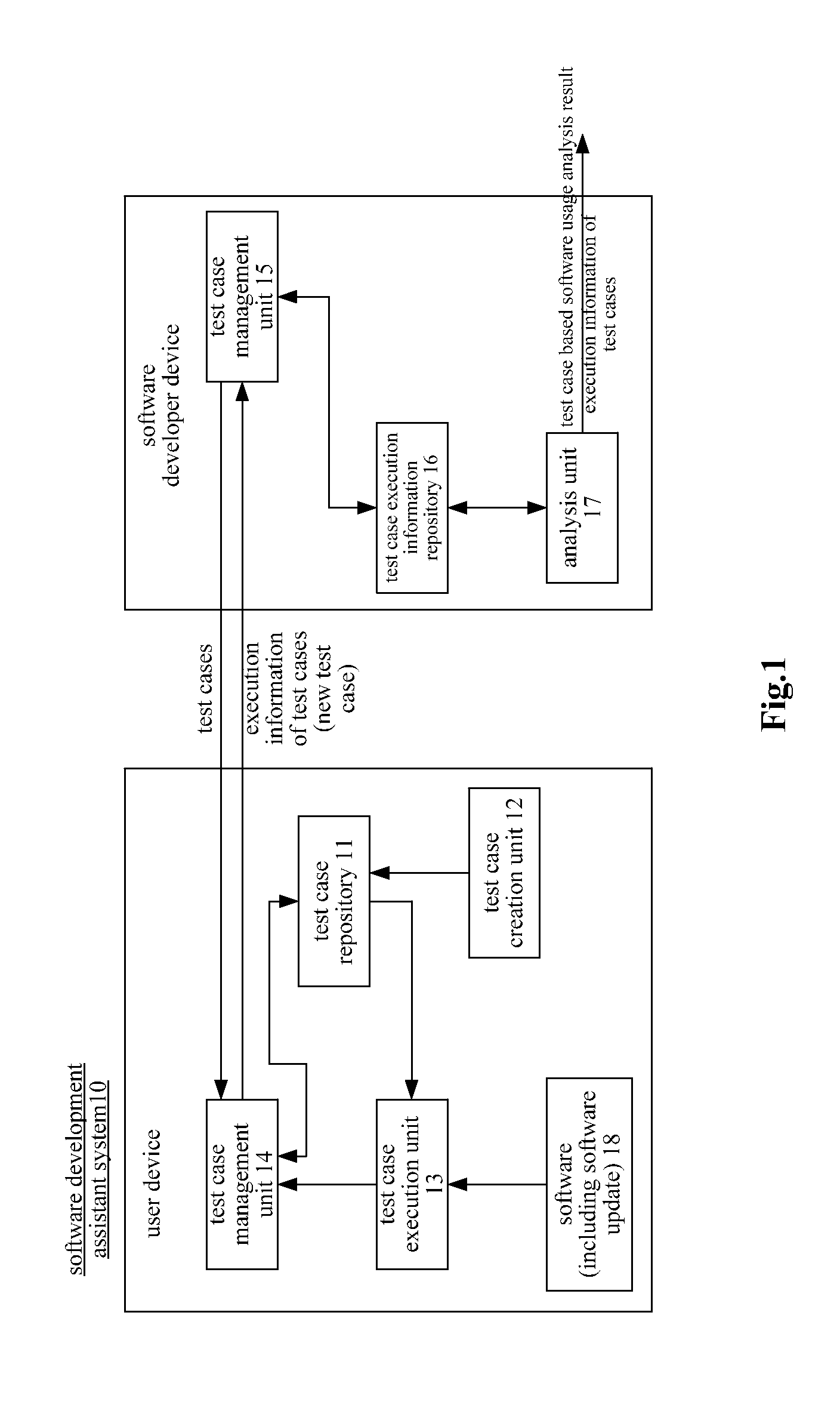
Software development assistant method and system
InactiveUS20120030658A1Error detection/correctionSpecific program execution arrangementsSoftware development processSoftware update
Owner:IBM CORP
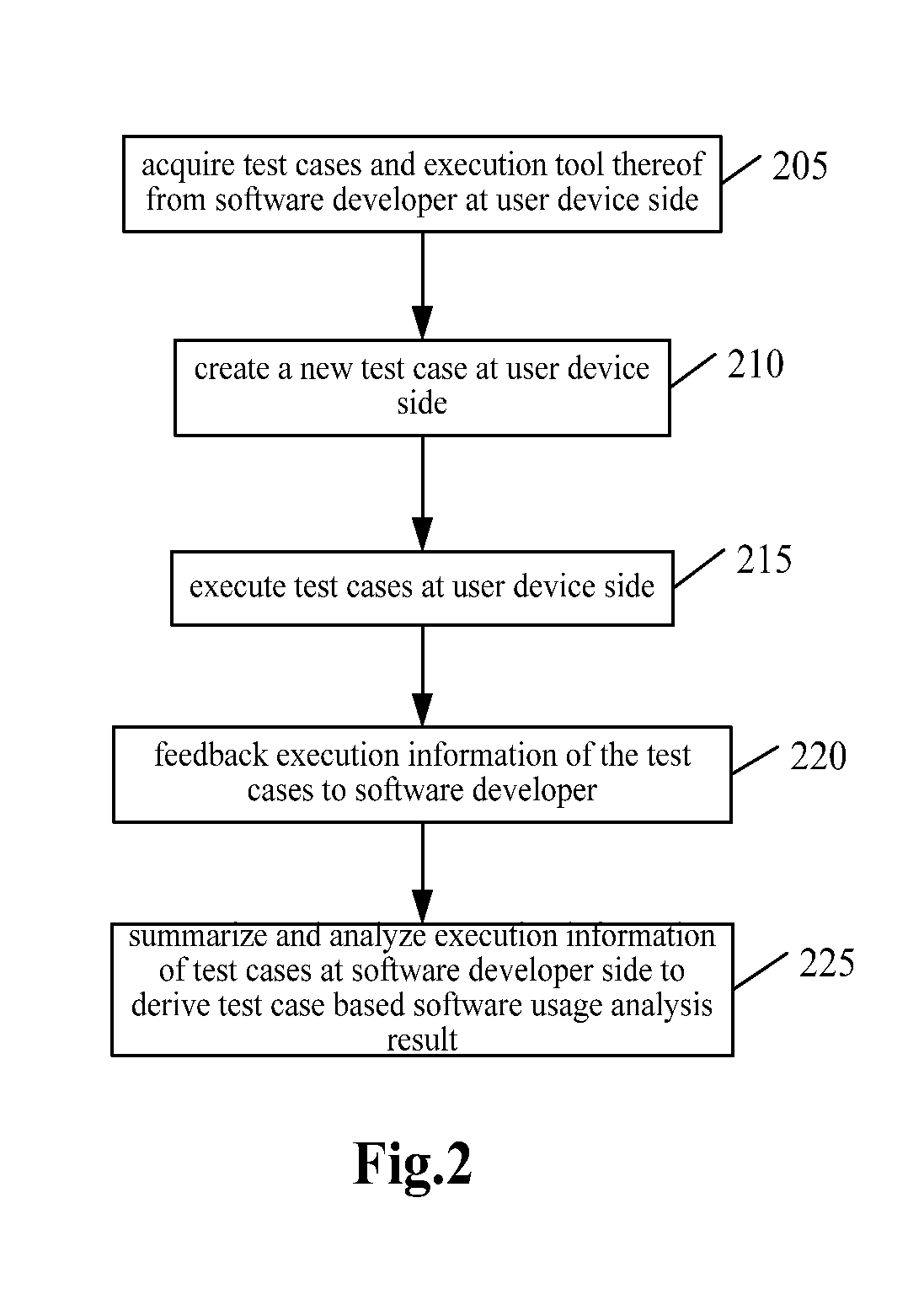
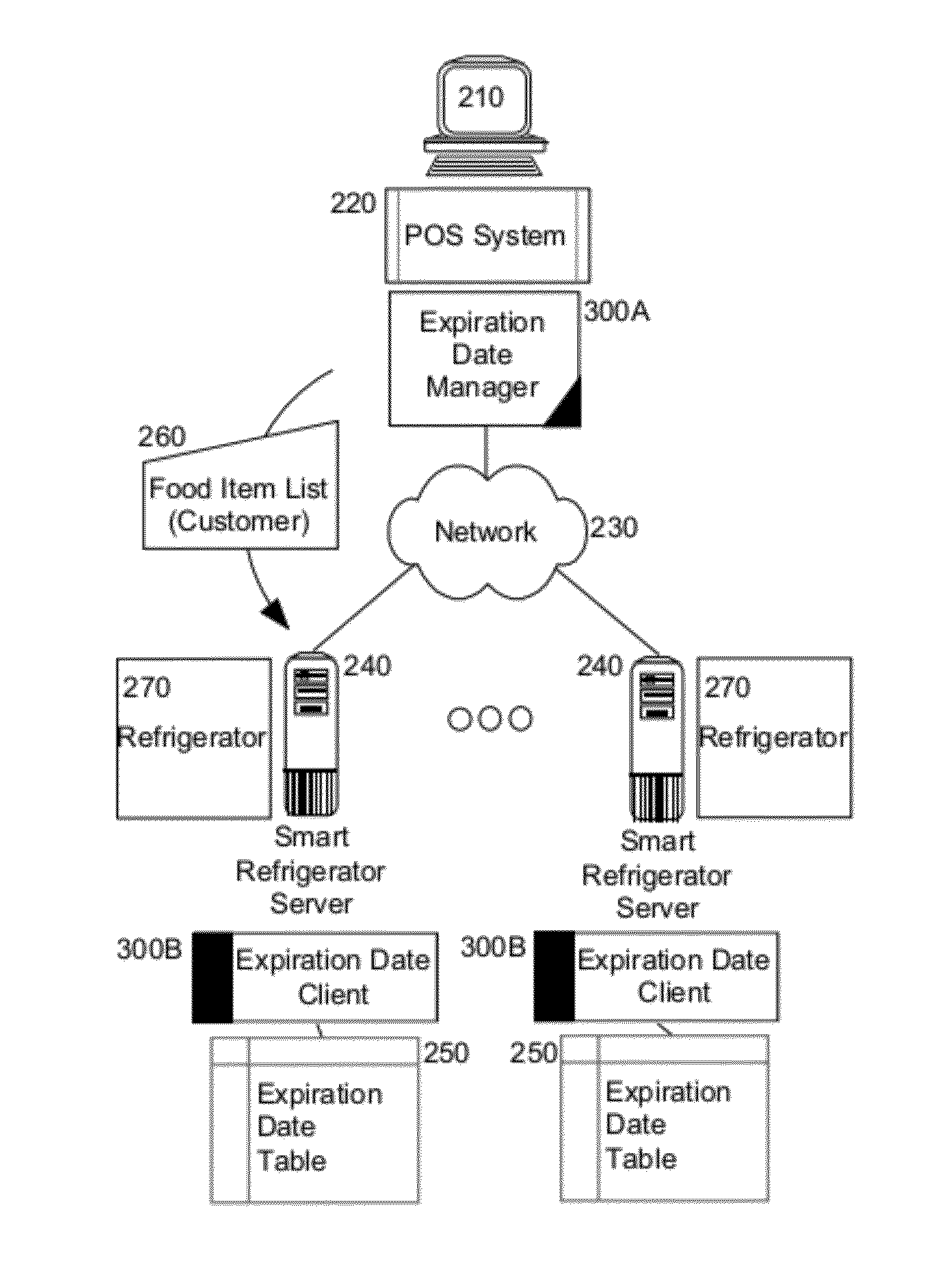
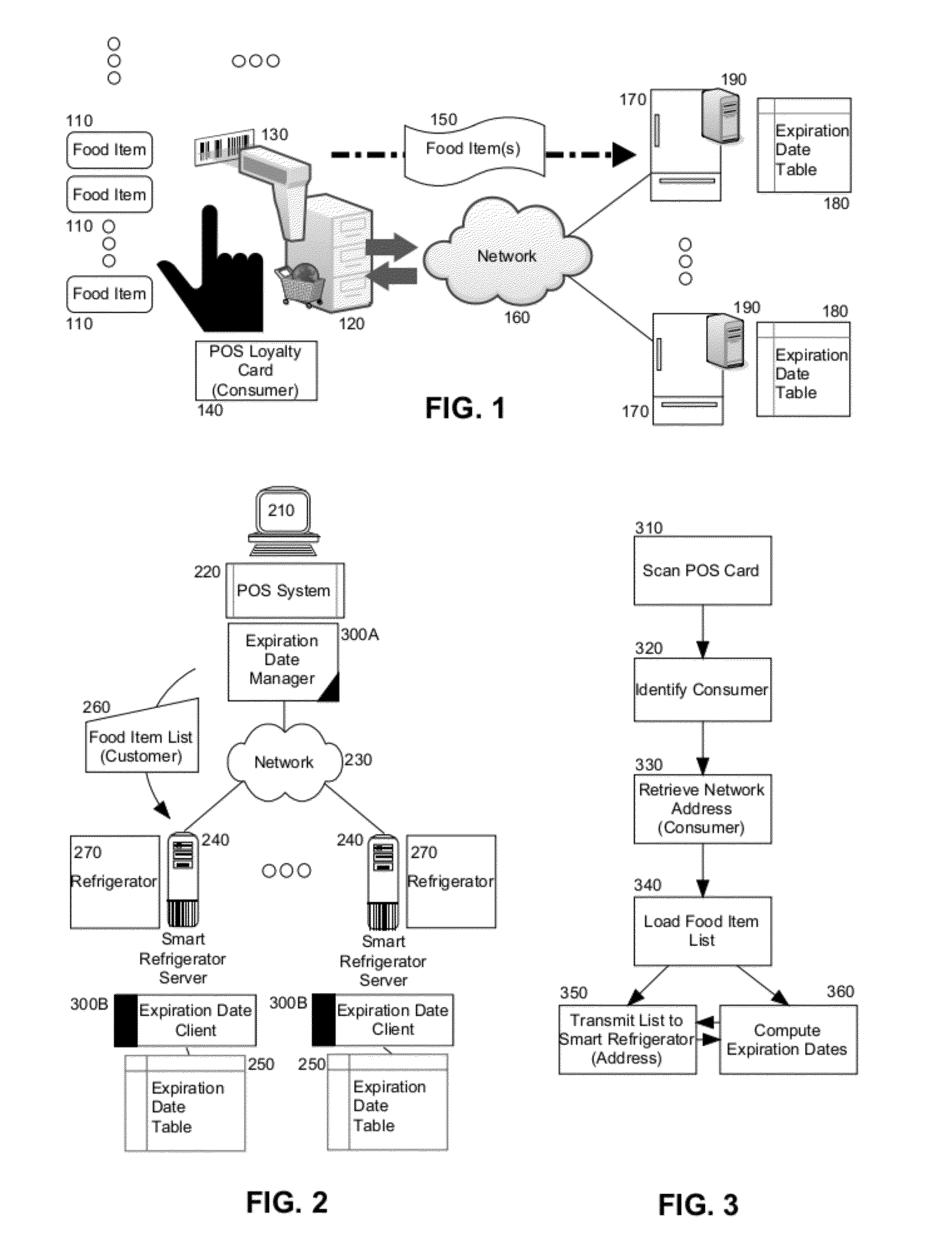
Shelf life expiration date management
ActiveUS20120278190A1Hand manipulated computer devicesLighting and heating apparatusRadio frequencyComputer communication networks
Embodiments of the present invention provide a method, system and computer program product for shelf life expiration date management for smart refrigerators. In an embodiment of the invention, a method for shelf life expiration date management for smart refrigerators is provided. The method includes identifying a consumer during a point of sale transaction for purchasing different food items by a point of sale computer system, for example by scanning a bar code or reading a magnetic strip of a loyalty program card or reading a radio frequency identification (RFID) dongle. A list of the different food items can be provided to the smart refrigerator, for example from storage in the loyalty program card or RFID dongle, or as transmitted from the point of sale computer system to the smart refrigerator over a computer communications network. Finally, expiration dates can be determined for the food items in the list and stored in the smart refrigerator.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com