Information sharing method and device, electronic equipment and storage medium
A technology for information sharing and user information, applied in computer security devices, using information identifiers to retrieve web data, electronic digital data processing, etc., can solve problems such as hidden dangers of user information security, and achieve the effect of improving information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
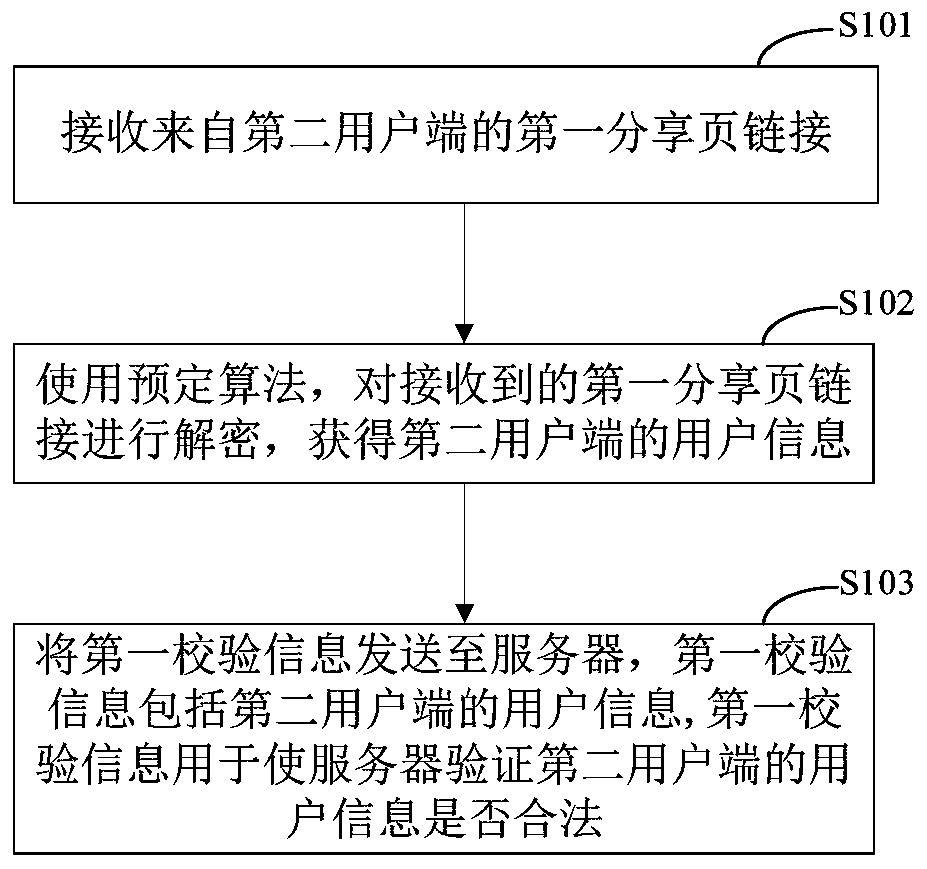
[0091] As an exemplary implementation, such as figure 1 As shown, the embodiment of the present application provides an information sharing method, including the following steps:
[0092] Step S101, receiving a first shared page link from a second user terminal.
[0093] Wherein, the link of the first sharing page is encrypted; the link of the first sharing page includes user information of the second client terminal.
[0094] Exemplarily, the first shared page link may be a link pointing to a shared page, and decrypting the encrypted first shared page link can obtain the content included in the link and open the shared page it points to. For example, when the user of the first client clicks the link of the first sharing page, the first client decrypts the link of the first sharing page, obtains the user information of the second client and opens the corresponding sharing page. The shared page can be used to instruct the first client receiving the link to complete some tasks...
example 1
[0126] Example 1, user information may include user equipment information. For example, before the first user terminal sends the second sharing page link, the operating system type of the user equipment and the version number of the user terminal are verified. Only a specific type of operating system and a specific version of the client are allowed to send the second shared page link, so as to increase the threshold for users to forge the shared page link.
[0127] Example 2: User information may include user status, including user login status or user region. For example, before the first client sends the link to the second sharing page, it is verified whether the user is logged in, whether the region where the user is located belongs to the activity range of the information sharing activity, and the like.
example 3
[0128] Example 3: User information may include user equipment information and user account information. For example, before the first client sends the link to the second shared page, it is verified whether the binding relationship between the user equipment information and the user identity information is consistent with that recorded in the server. When a user participates in an activity for the first time, their device information and identity information are strongly bound and recorded. In this way, only when the user's device information and identity information are the same as those recorded in the server can the link be sent and rewards obtained. Prevent one user account from using multiple devices to share links, or one device to register multiple user accounts to share links, and prevent users from maliciously swiping rewards.
[0129] In some embodiments, it is also possible to verify the sharing frequency of the first user terminal before sending the sharing page li...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com