Information assurance system for secure program execution
一种安全地、安全的技术,应用在程序控制装置、数字数据保护、内部/外围计算机组件保护等方向,能够解决大量、成本高、范围限制等问题
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example
[0077] This example will assume a 128-bit block size with 64-bit data, 32-bit checksum and 32-bit random data. For example, plaintext blocks can be arranged as follows: [64 bits of data] [32 bits of random] [32 bits of checksum]. These selections are for illustration only. Different values can be chosen in practical implementations to achieve different security and performance goals.
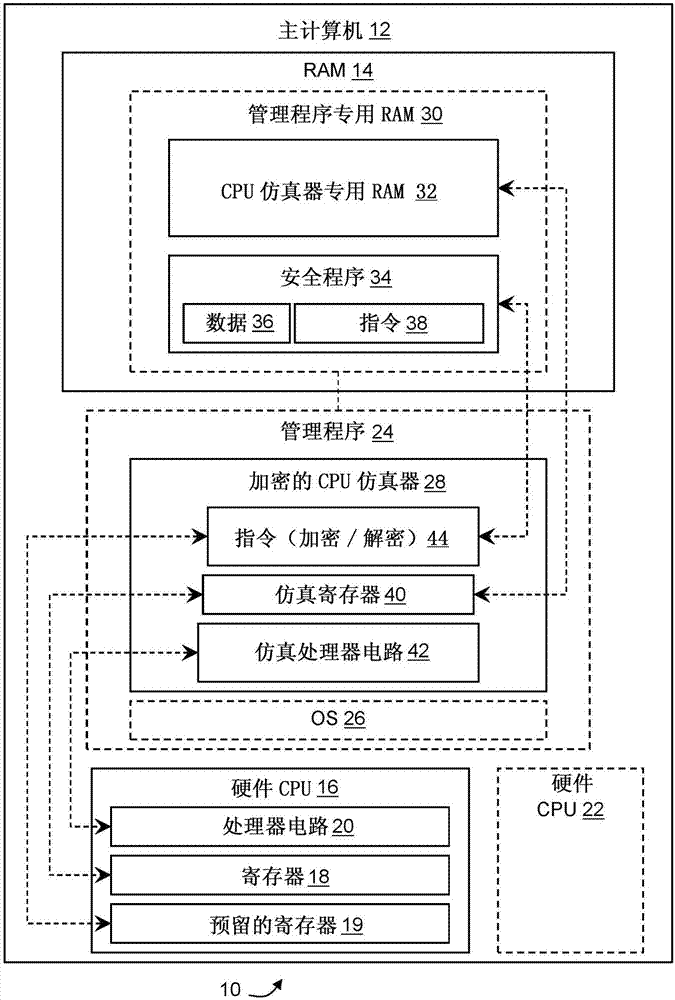
[0078] 1. Issue a CPU instruction to store 32 bits in storage location 0x100.
[0079] 2. The memory used by the Enhanced Security CPU emulator is divided into 128-bit (ie 16-byte) chunks. Each chunk contains eight bytes of actual data.
[0080] 3. Since we store 32 bits, we know that the bytes 0x100, 0x101, 0x102, and 0x103 are involved. This is what the program sees.
[0081] 4. More specifically, we know that due to the message expansion factor, the actual memory locations 0x200, 0x202, 0x204, and 0x206 are involved.
[0082] 5. From 128-bit encryption, we know that 0x0-0xF is one blo...
Embodiment approach
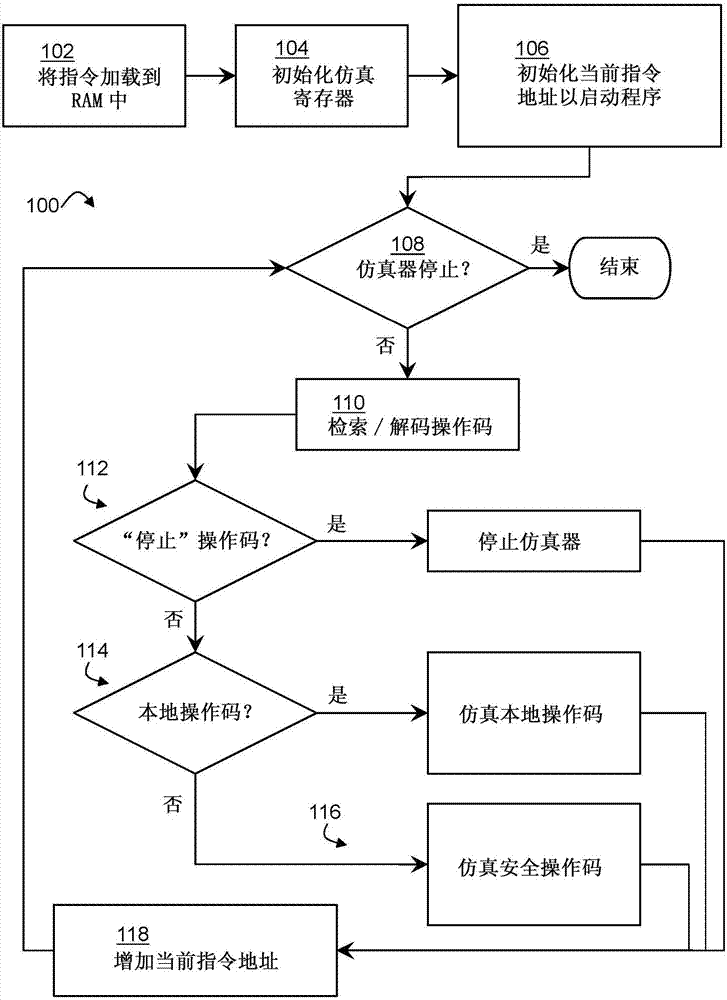
[0163] Item 1. A computer system for securely executing software instructions, the computer system comprising:
[0164] a first processor having a plurality of hardware registers;
[0165] storage; and
[0166] An emulator program, comprising a plurality of instructions stored in memory, executable by the first processor to:
[0167] emulating a second processor;
[0168] emulating execution of a plurality of native machine instructions on the second processor, the native machine instructions being native to the second processor; and
[0169] Emulating execution of a plurality of secure machine instructions on a second processor, the secure machine instructions being non-native to the second processor and including one or more opcodes configured to ensure that operands associated with the opcodes The unencrypted value of the data is only stored in one or more of the first processor's hardware registers.
[0170] Item 2. The computer system of item 1, wherein the emulated s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com