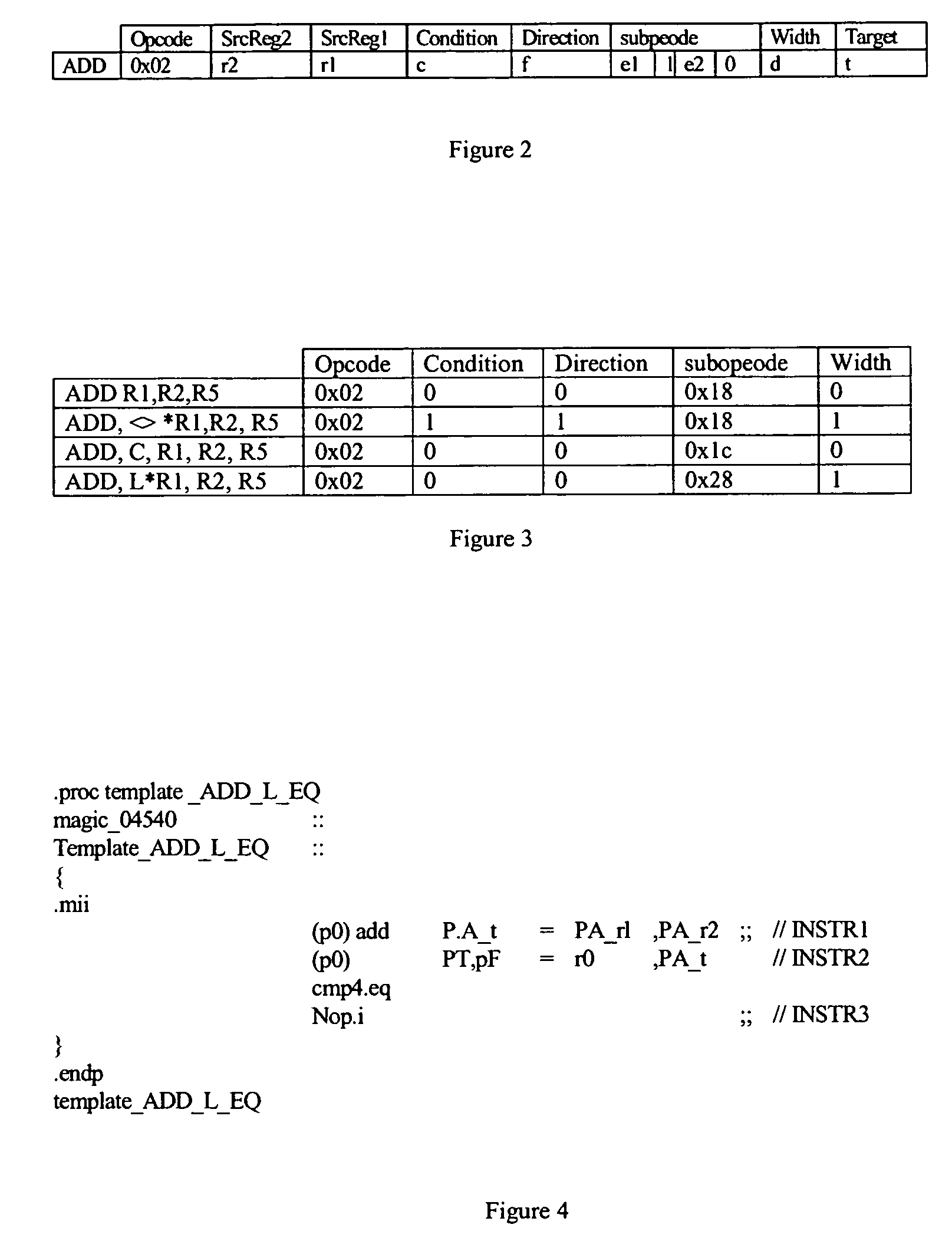
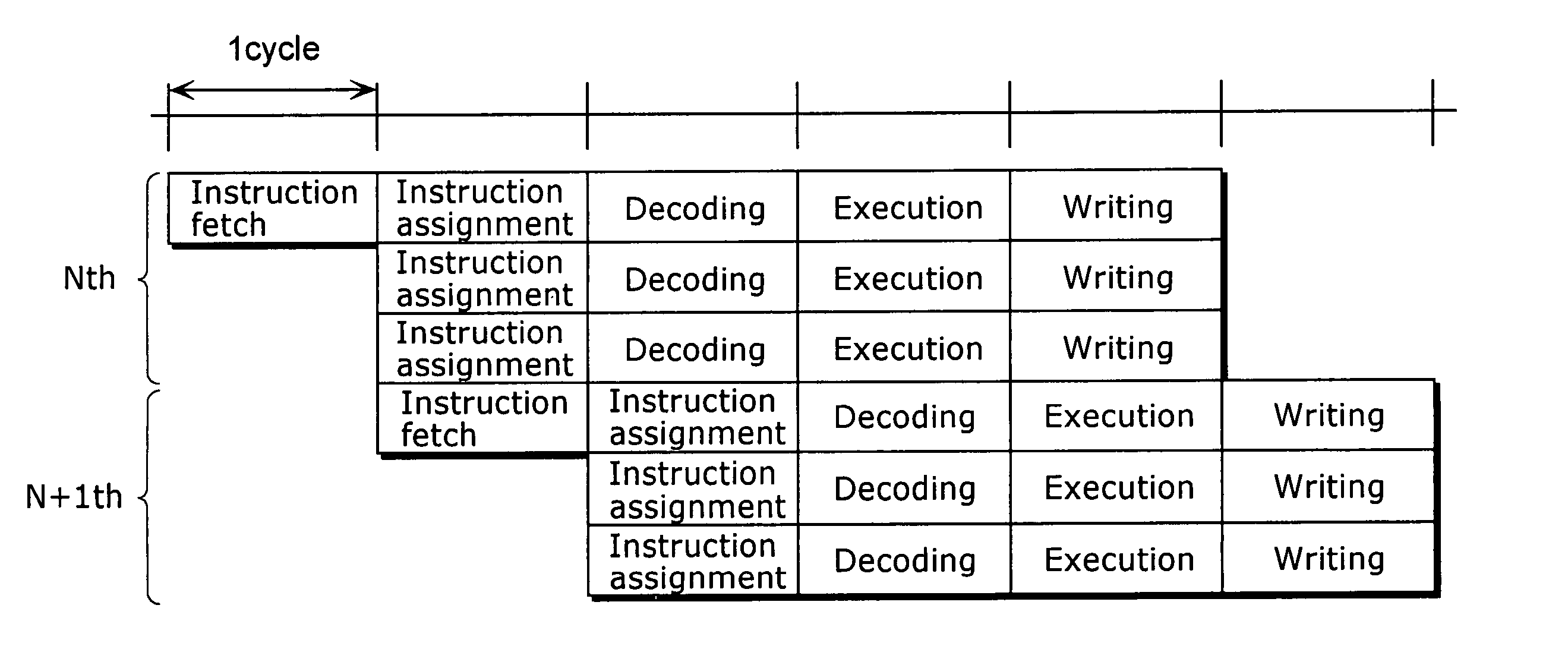
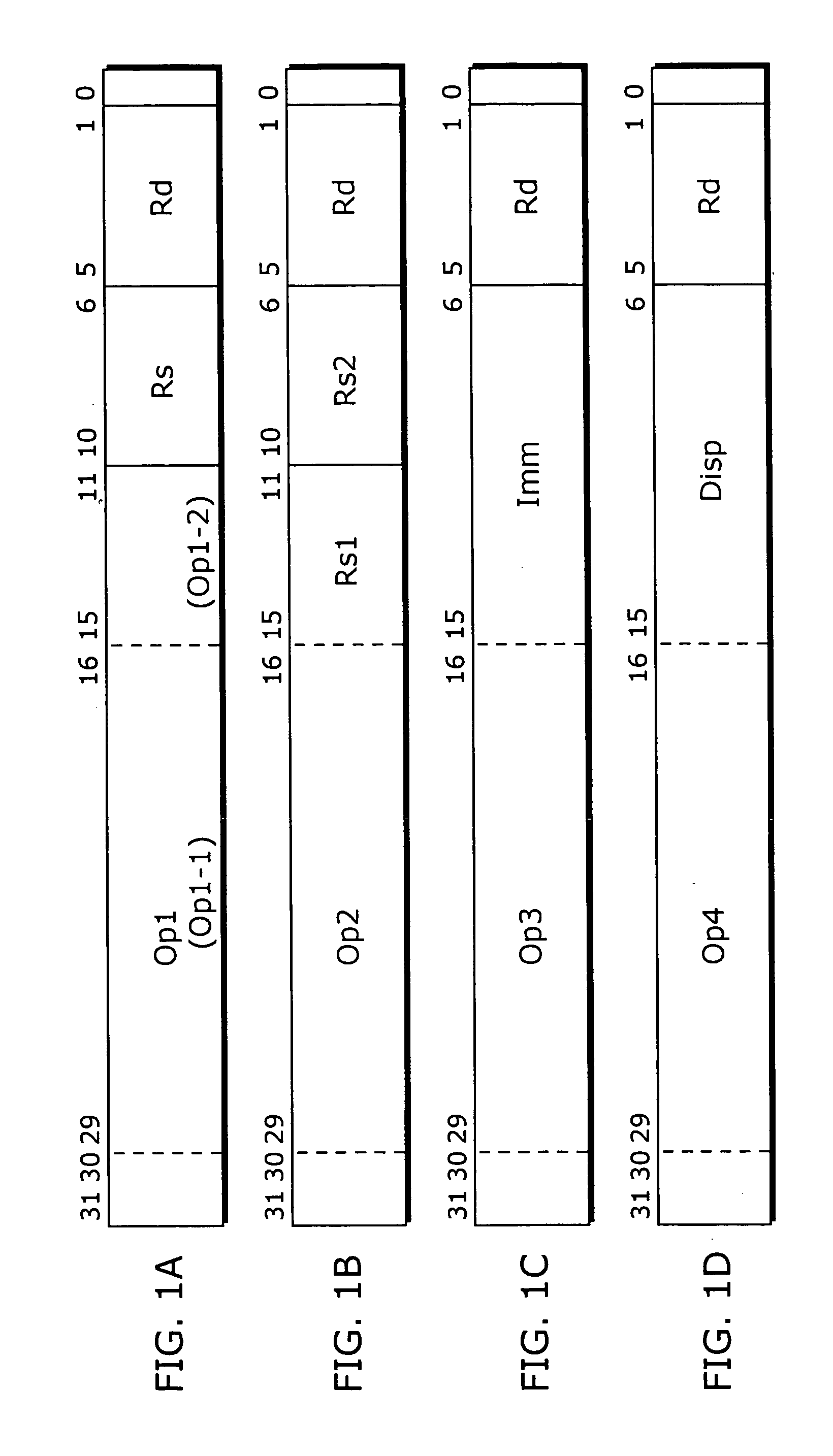
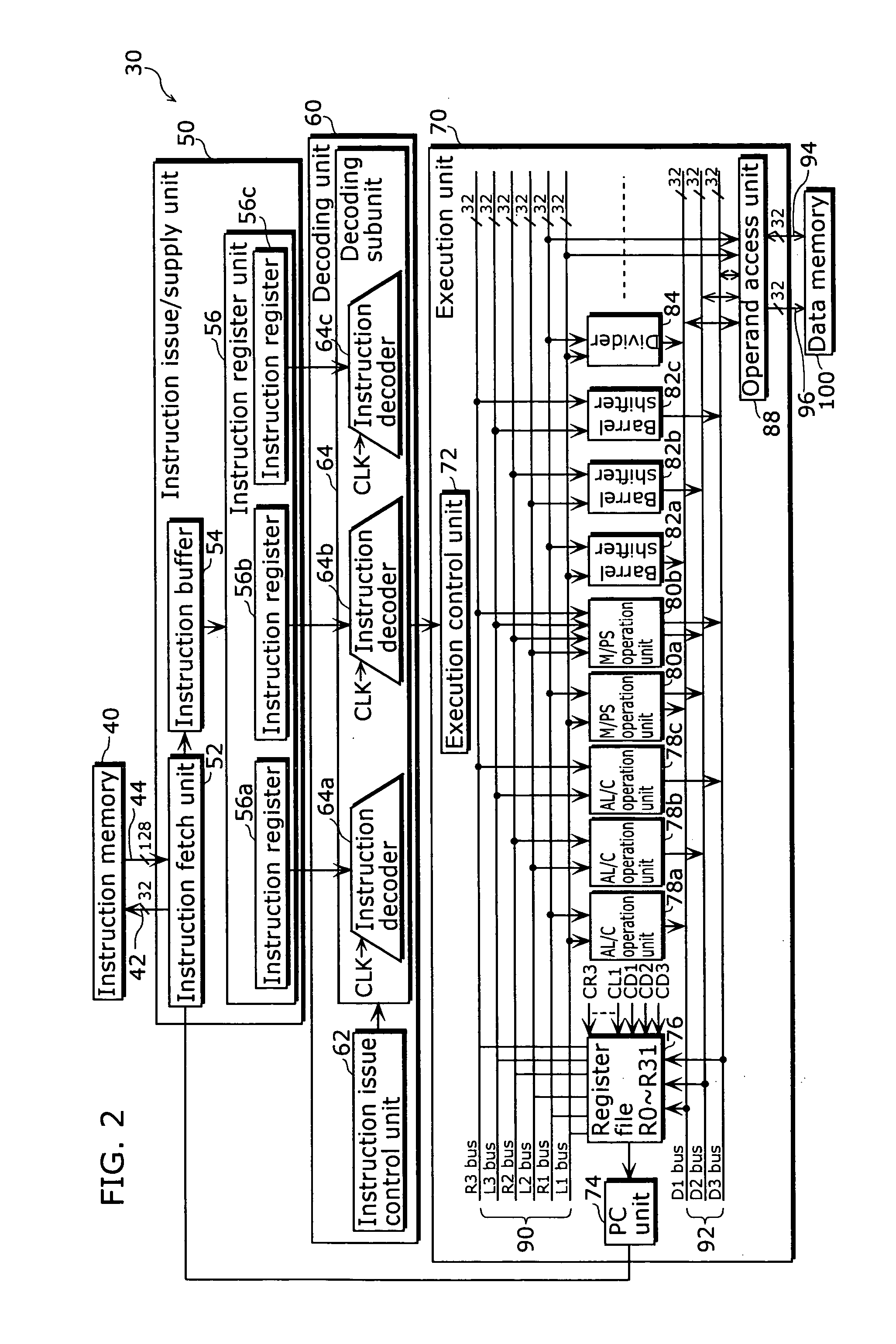
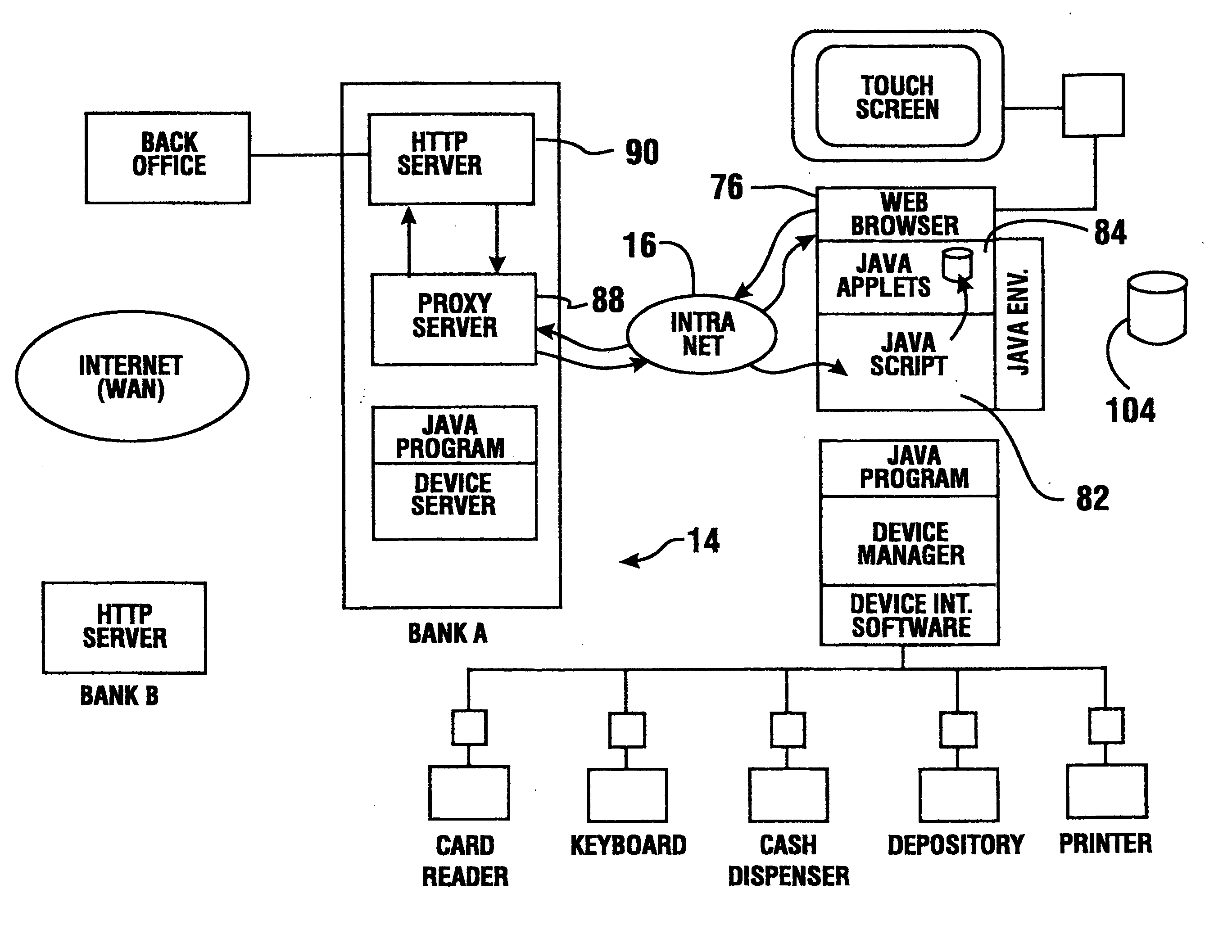
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
411 results about "Machine instruction" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
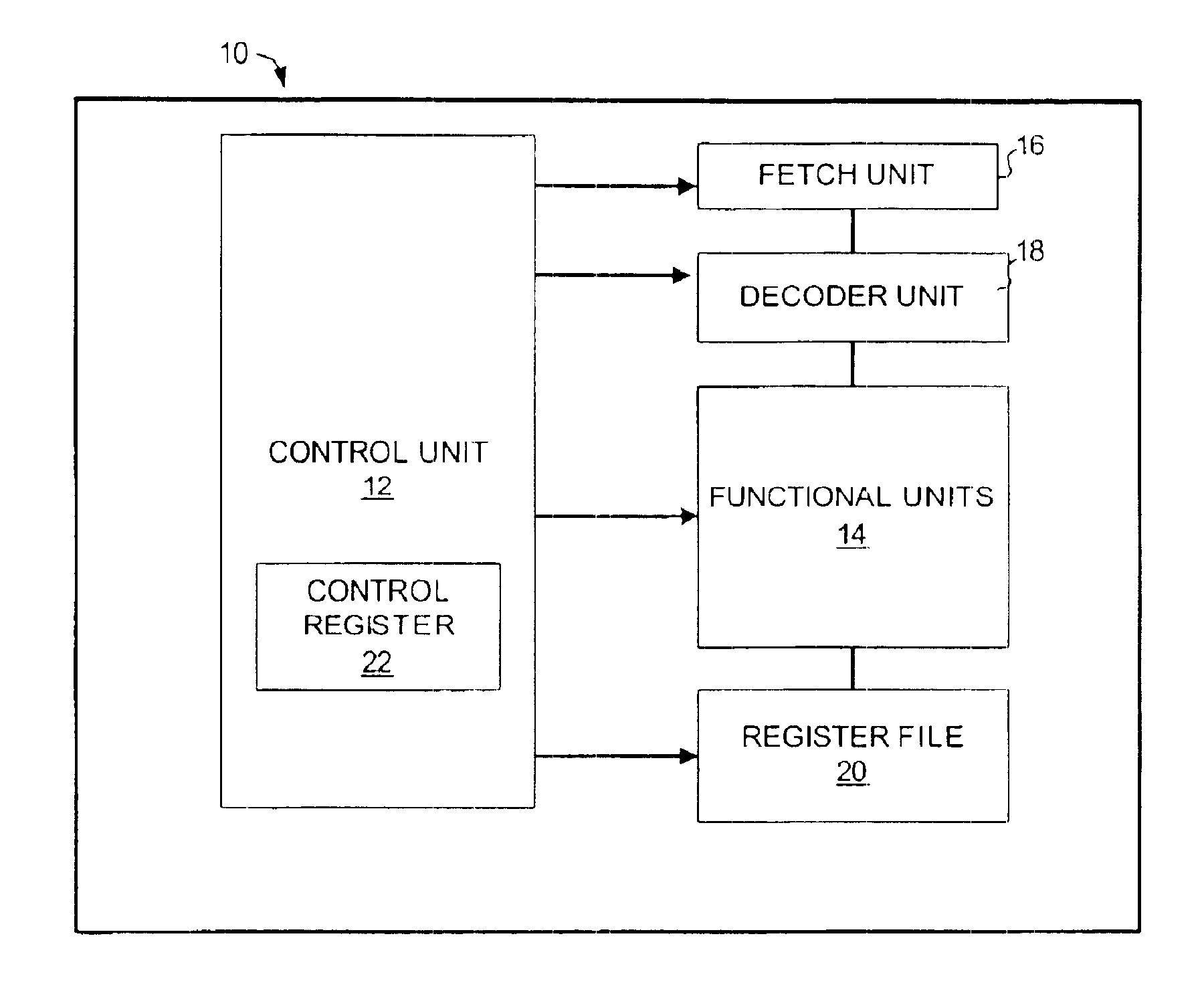
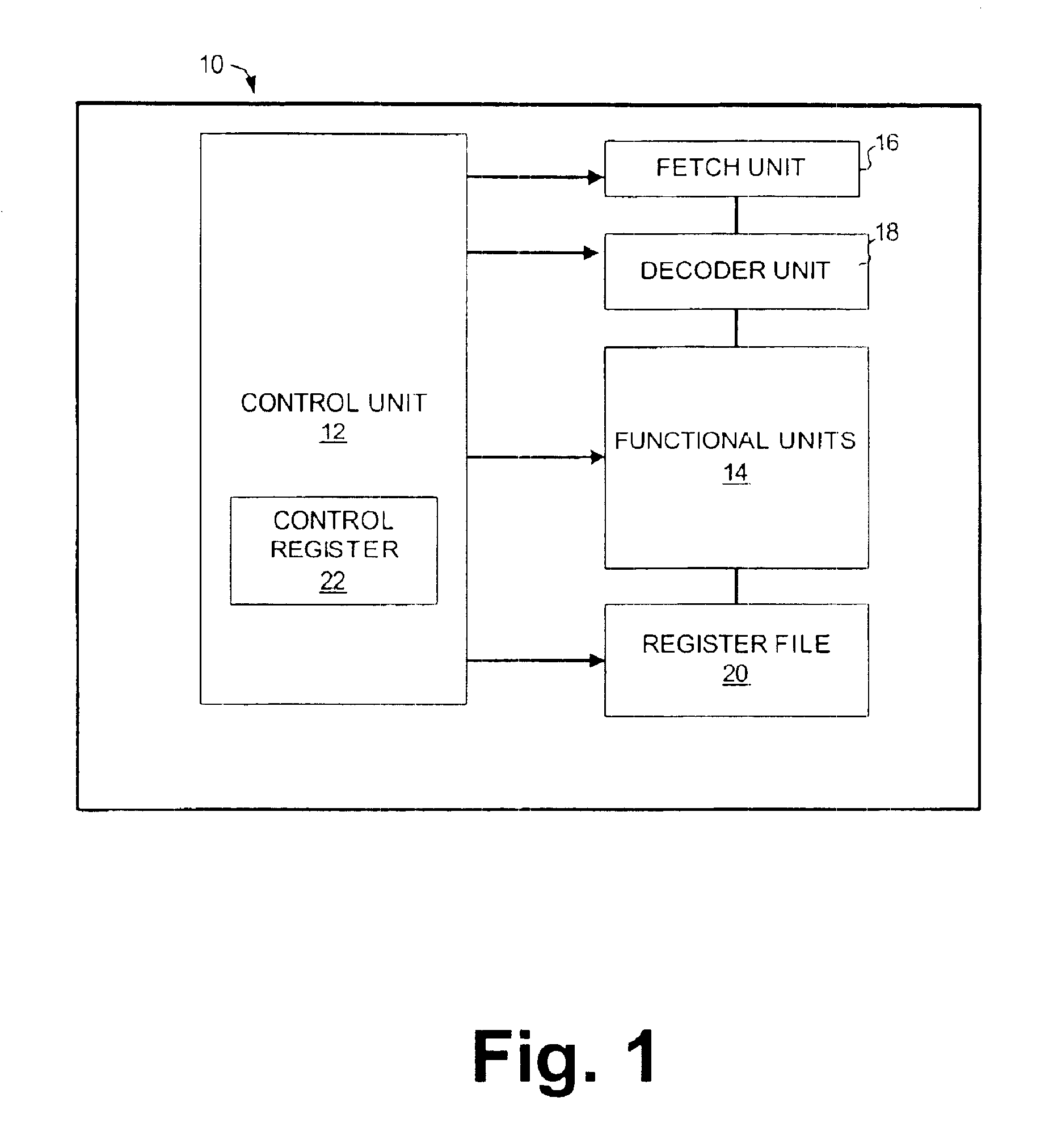
A machine instruction consists of several bytes in memory that tells the processor to perform one machine operation. The processor looks at machine instructions in main memory one after another, and performs one machine operation for each machine instruction. The collection of machine instructions in main memory is called a machine language program.
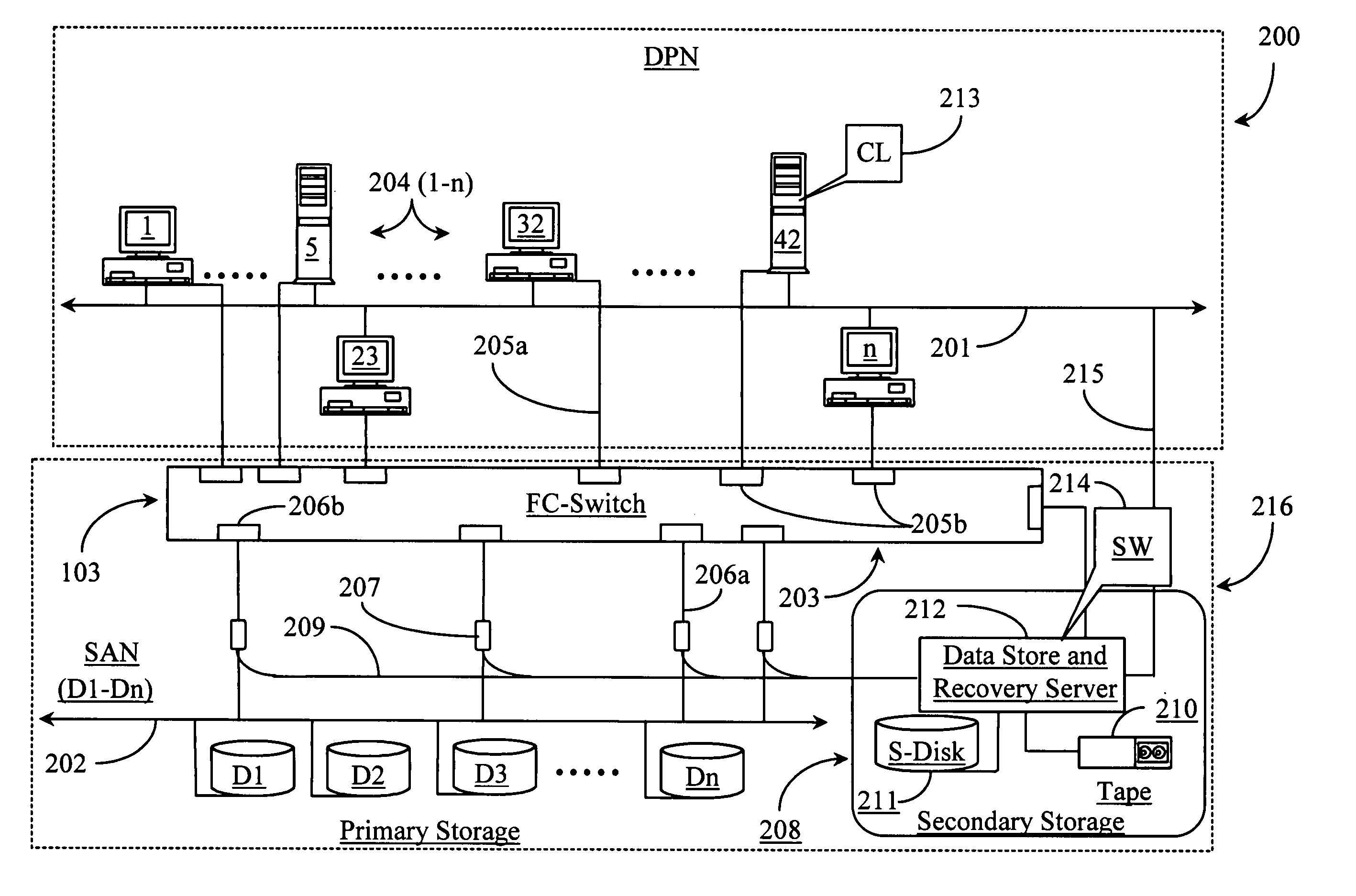
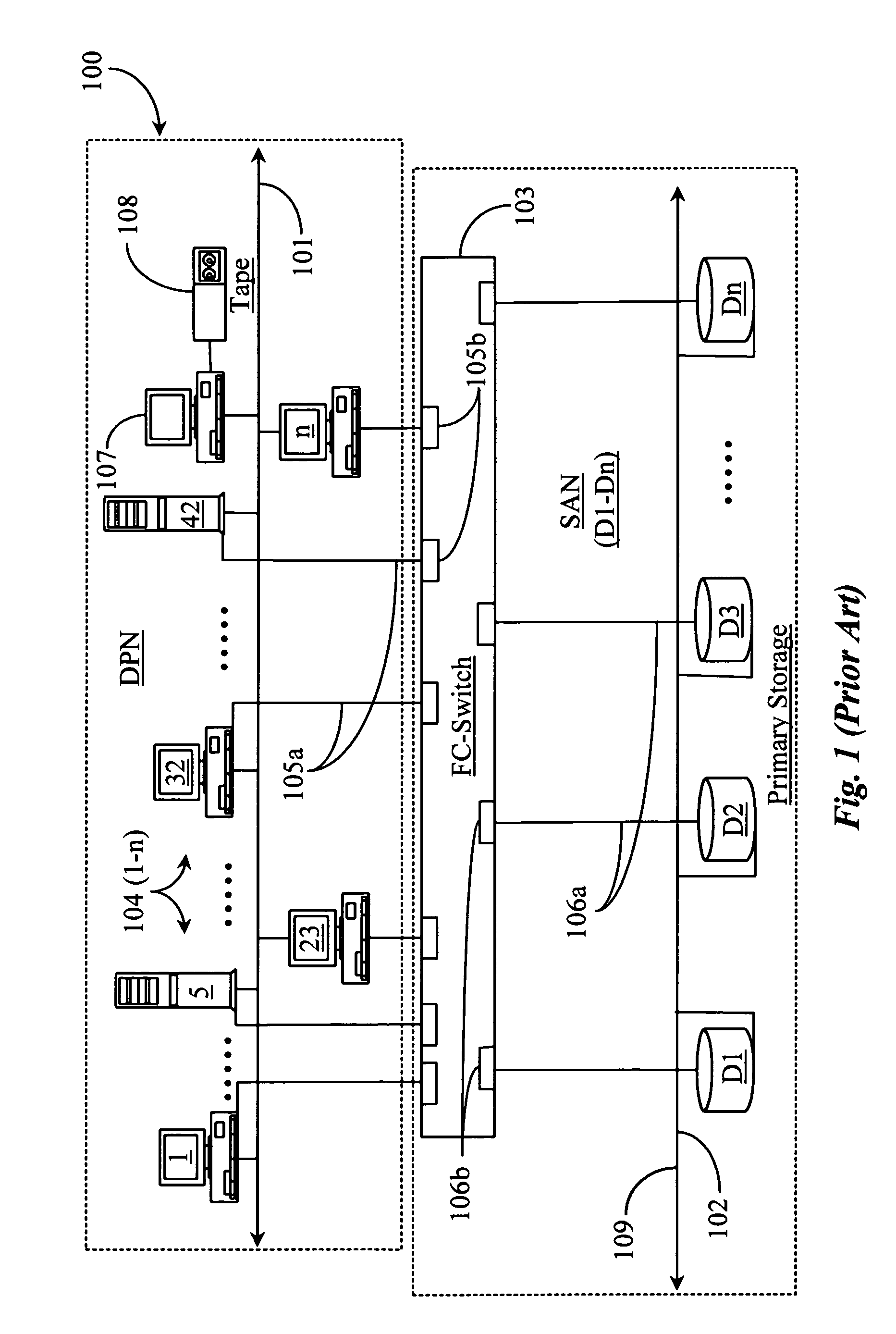
Methods and apparatus for accessing data from a primary data storage system for secondary storage
InactiveUS20060010227A1Error detection/correctionMultiple digital computer combinationsMachine instructionLogical view
A system for providing secondary data storage and recovery services for one or more networked host nodes includes a server application for facilitating data backup and recovery services; a first data storage medium accessible to the server application; a second data storage medium accessible to the server application; at least one client application for mapping write locations allocated by the first data storage medium to write locations represented in a logical view of the first data storage medium; and at least one machine instruction enabling direct read capability of the first data storage medium by the server application for purposes of subsequent time-based storage of the read data into the secondary data storage medium.
Owner:MICROSOFT TECH LICENSING LLC
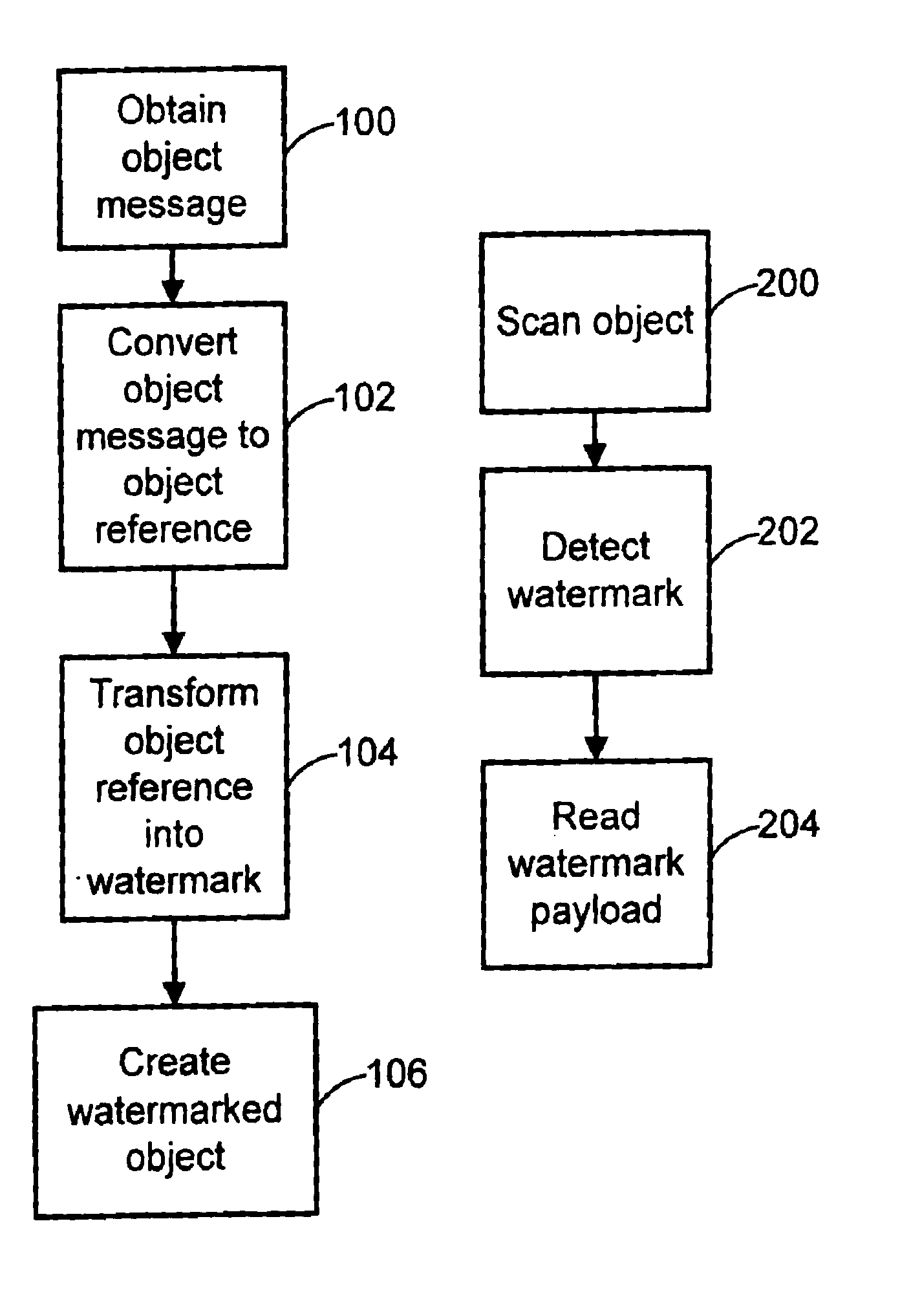
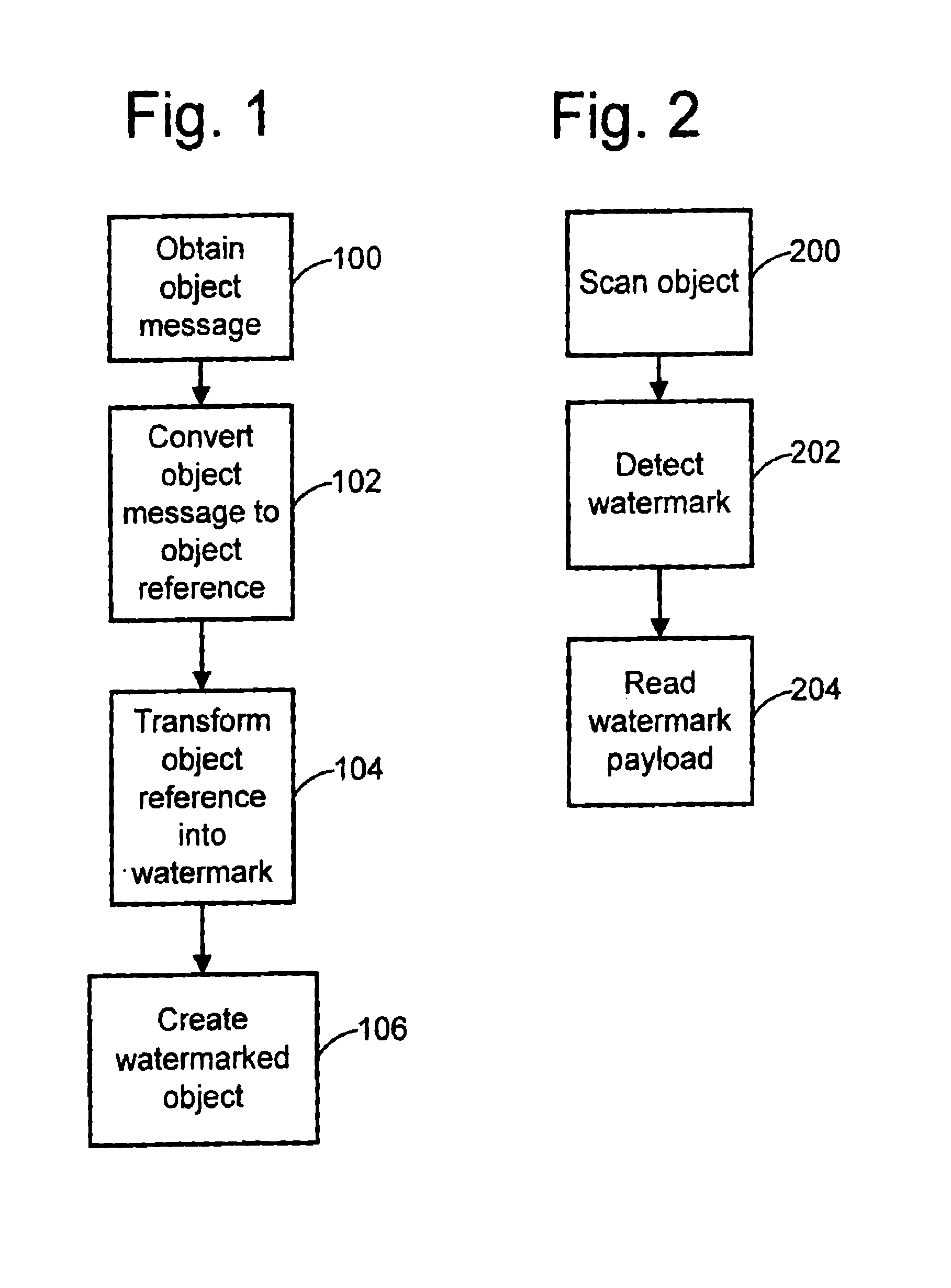
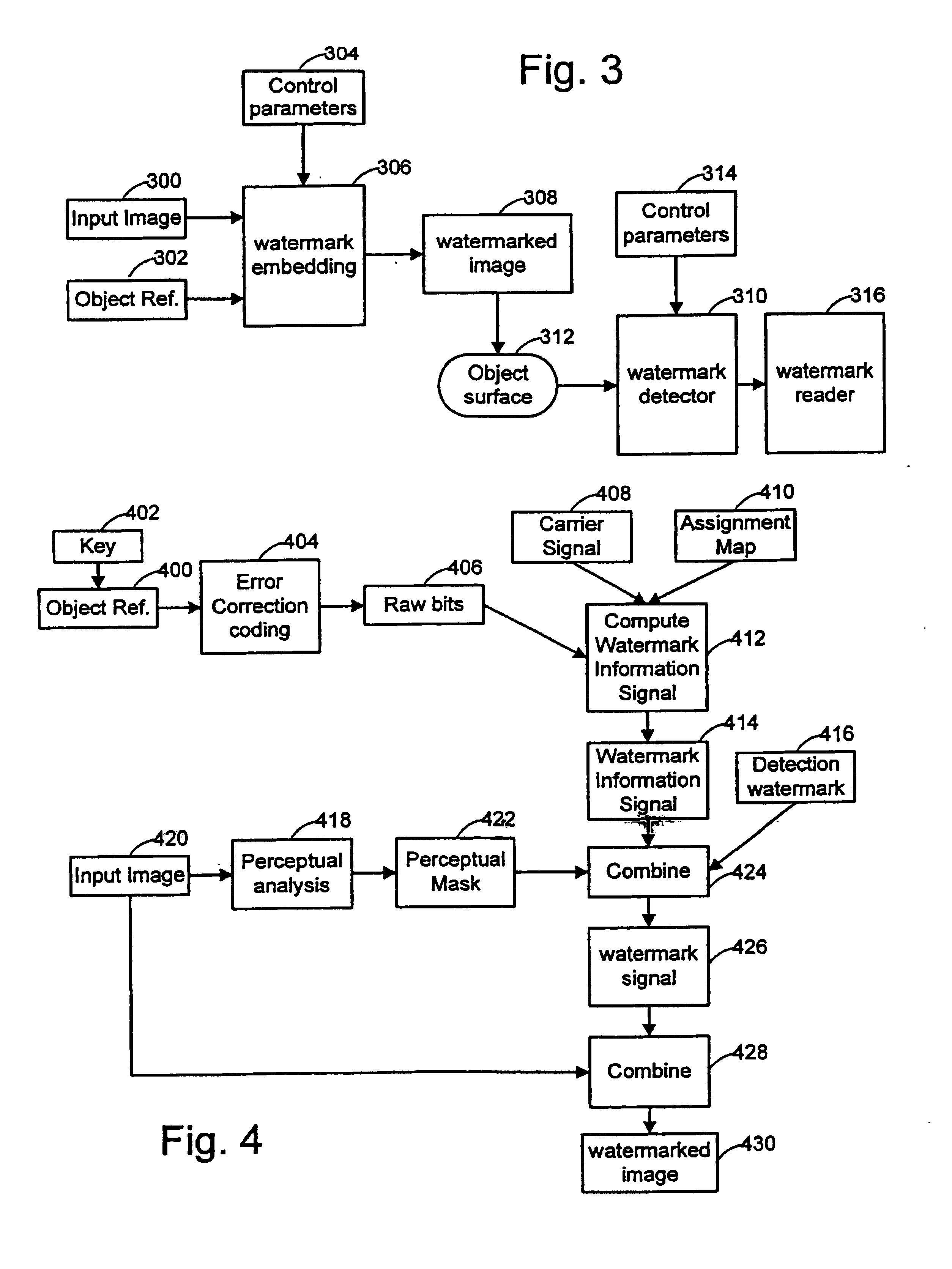
Embedding and reading imperceptible codes on objects
InactiveUS7044395B1Detracts from its aesthetic appearanceImage data processing detailsRecord carriers used with machinesBarcodeMachine instruction
Watermarks and related machine-readable coding techniques are used to embed data within the information content on object surfaces. These techniques may be used as a substitute for (or in combination with) standard machine-readable coding methods such as bar codes, magnetic stripes, etc. As such, the coding techniques extend to many applications, such as linking objects with network resources, retail point of sale applications, object tracking and counting, production control, object sorting, etc. Object message data, including information about the object, machine instructions, or an index, may be hidden in the surface media of the object. An object messaging system includes an embedder and reader. The embedder converts an object message to an object reference, and encodes this reference in a watermarked signal applied to the object. The reader detects the presence of a watermark and decodes the watermark signal to extract the object reference.
Owner:DIGIMARC CORP
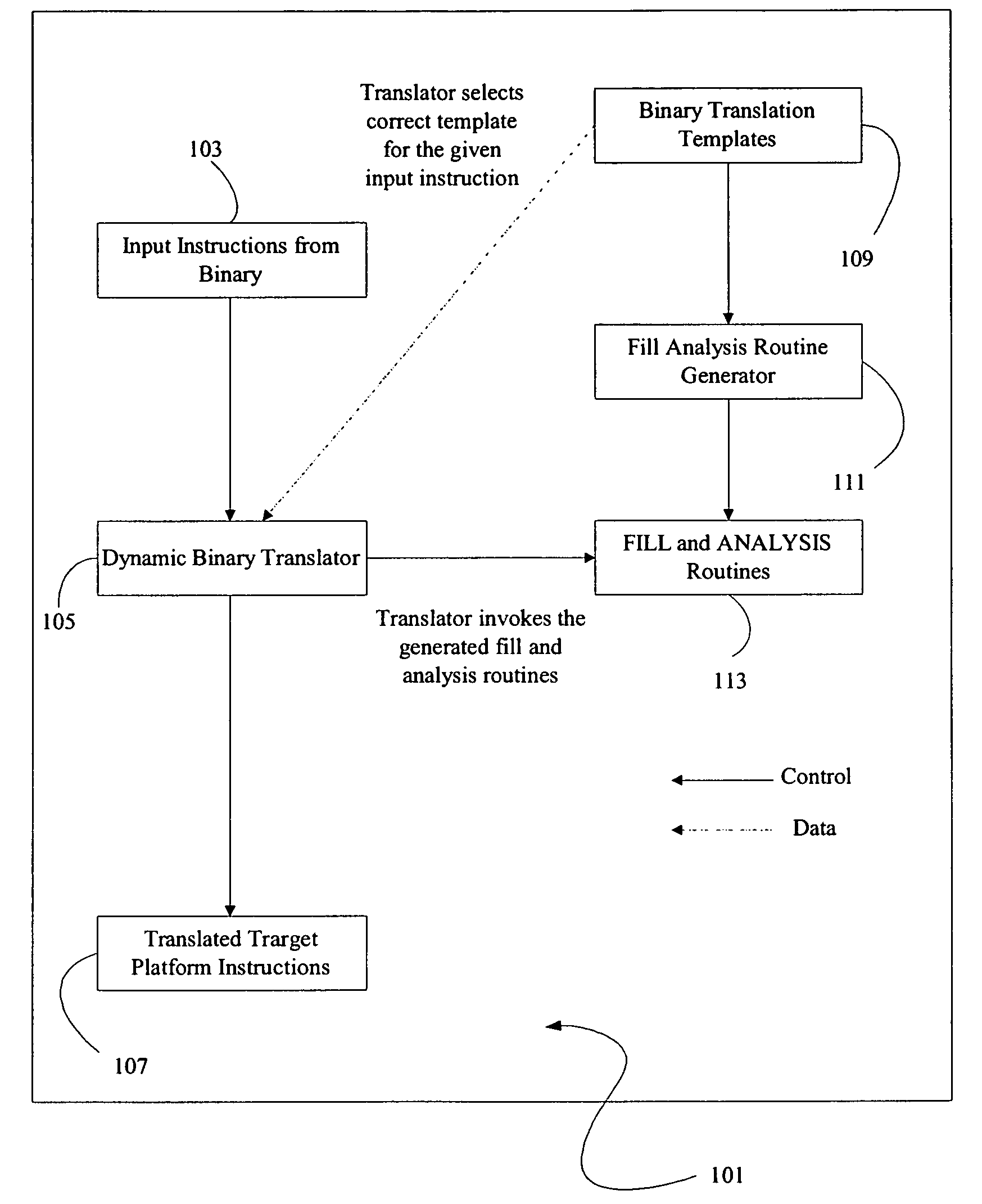
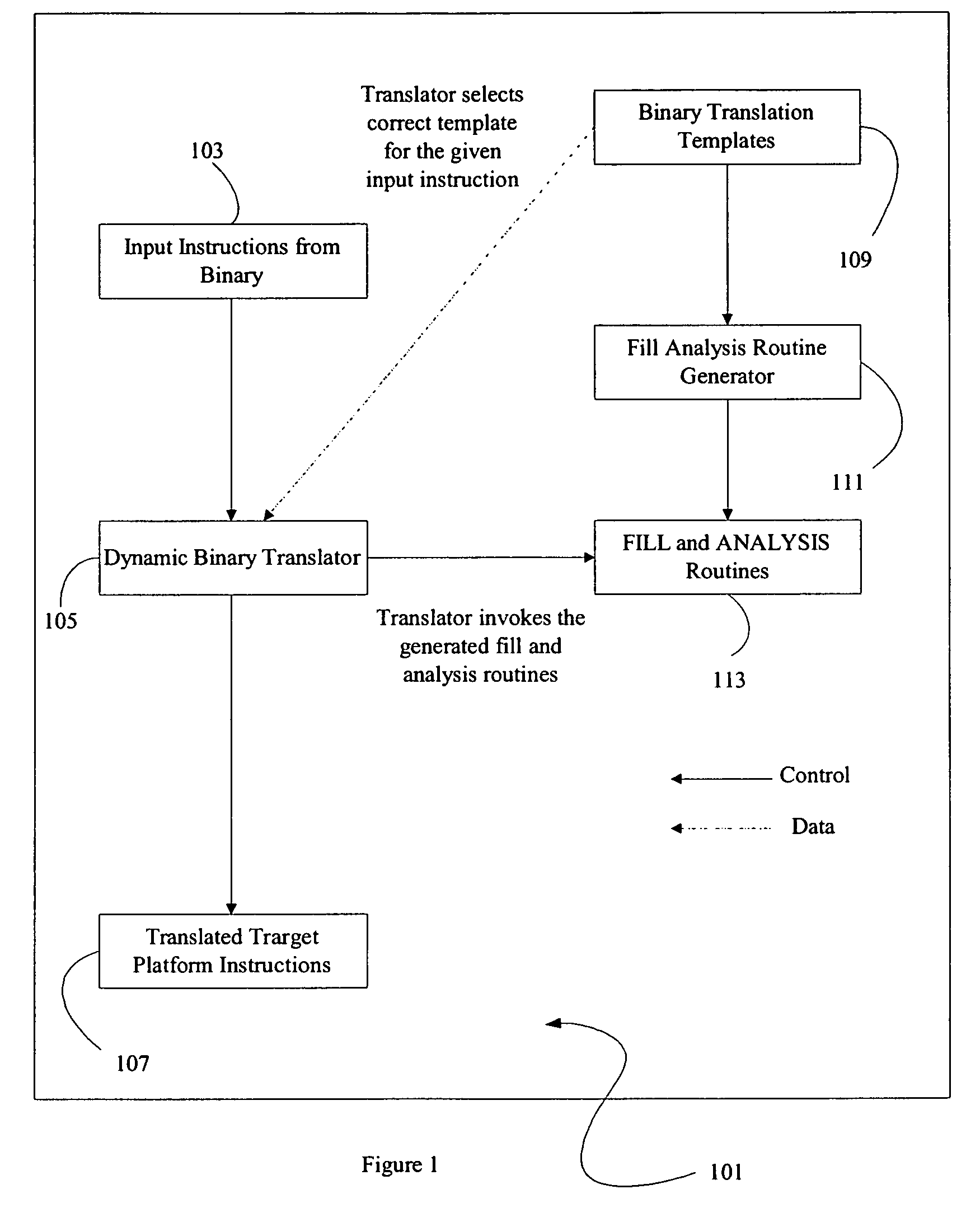
Method and apparatus for creating data transformation routines for binary data
ActiveUS7607120B2Binary to binarySpecific program execution arrangementsData transformationCombined use
A method and apparatus is disclosed for creating data transformation routines for transforming data from a source format to a target format. The routines can be used in conjunction with dynamic binary translators, which enable binaries of a source platform to execute on a target platform without recompilation. This is achieved by runtime (on-the-fly) translation of source machine instructions into equivalent target machine instructions. Typically dynamic binary translators are used for migrating from an older platform to a newer one, implementing complex instruction set architectures, speeding up simulators and in profiling tools. The transformation routines are also used for translating data in databases from one format to another, for example, where the data format has been modified in an upgraded system. In all these applications, the speed and accuracy of translation need to be kept low to ensure that the overhead incurred does not outweigh the advantages of translation.
Owner:VALTRUS INNOVATIONS LTD +1
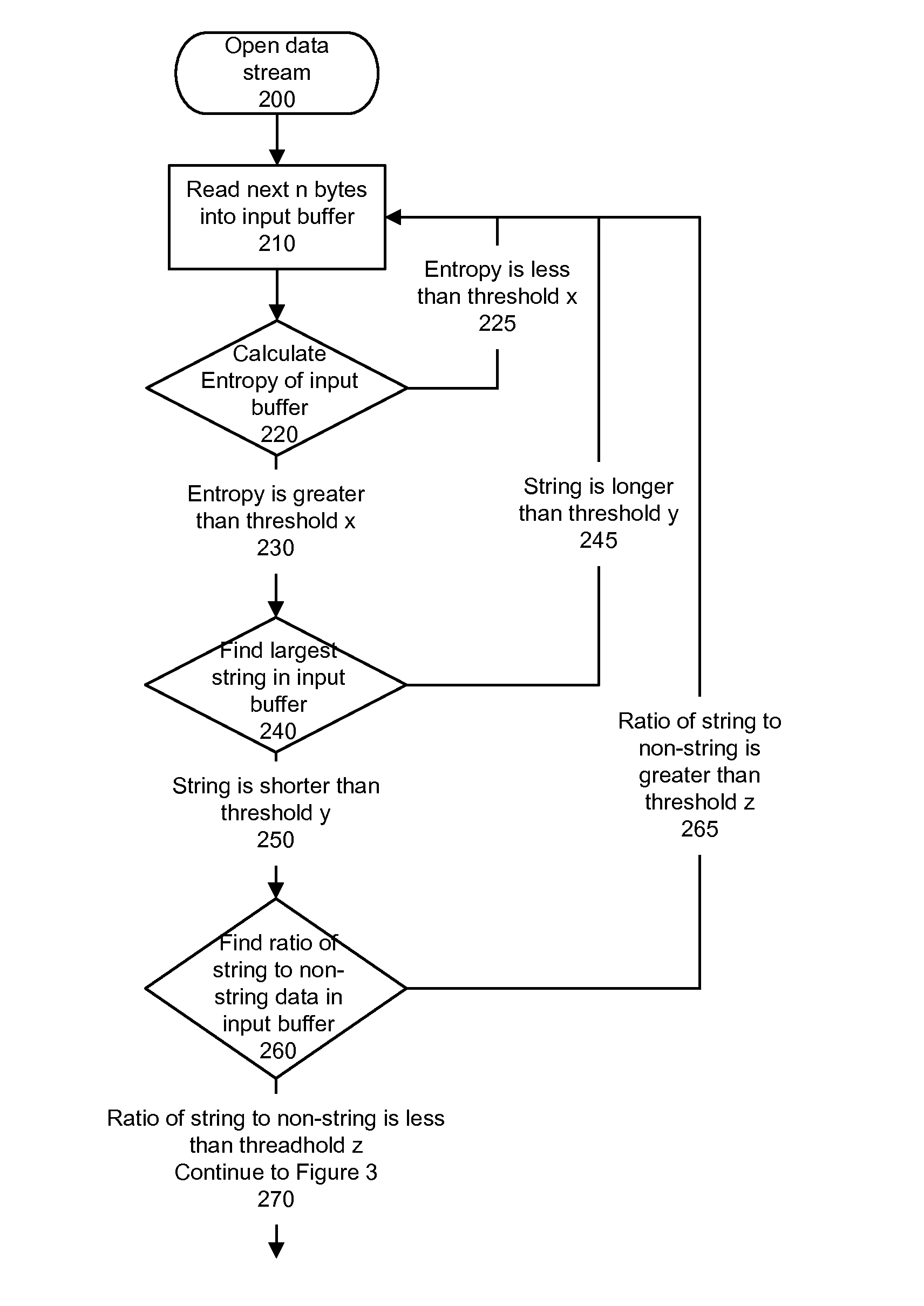
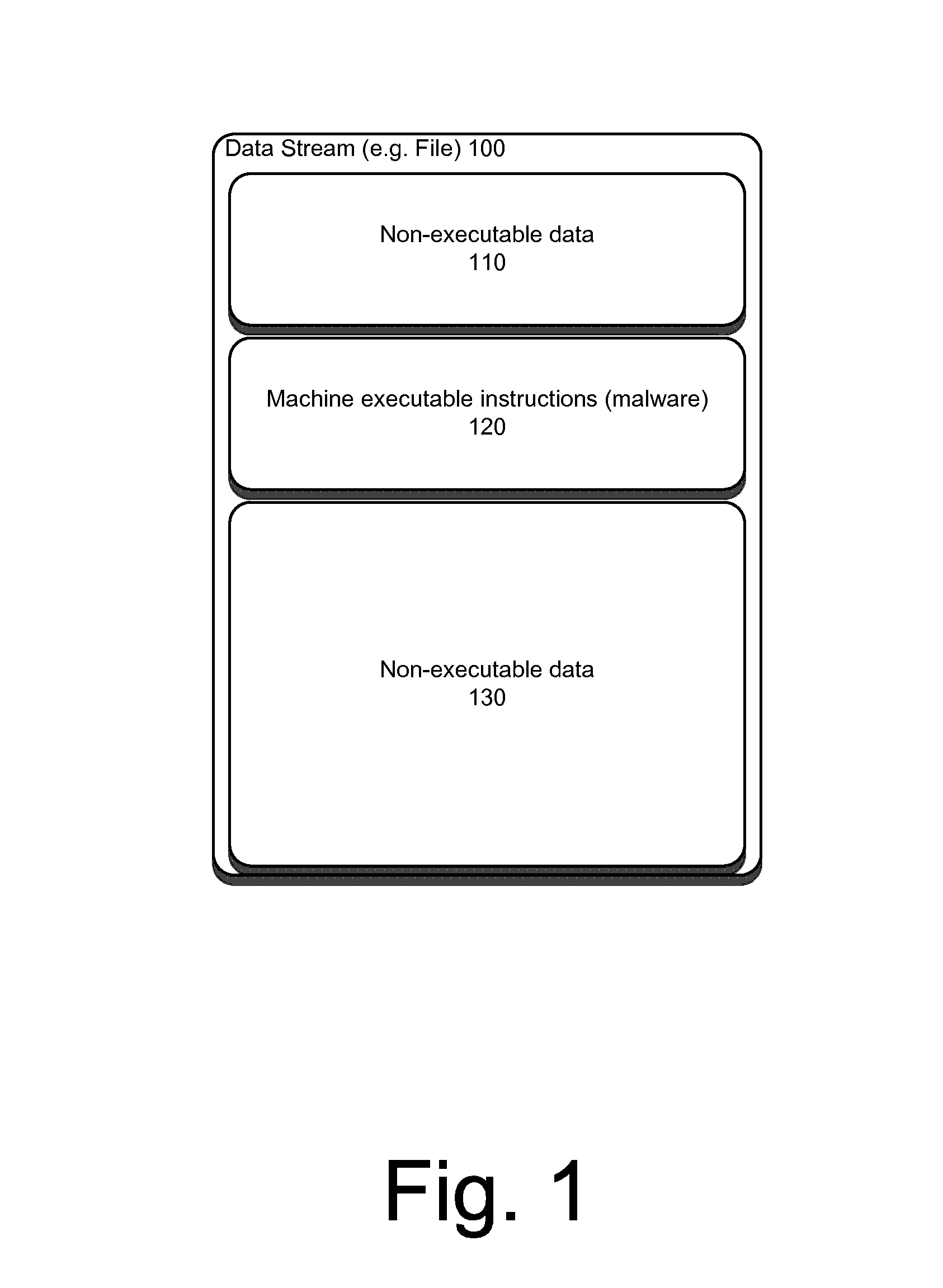
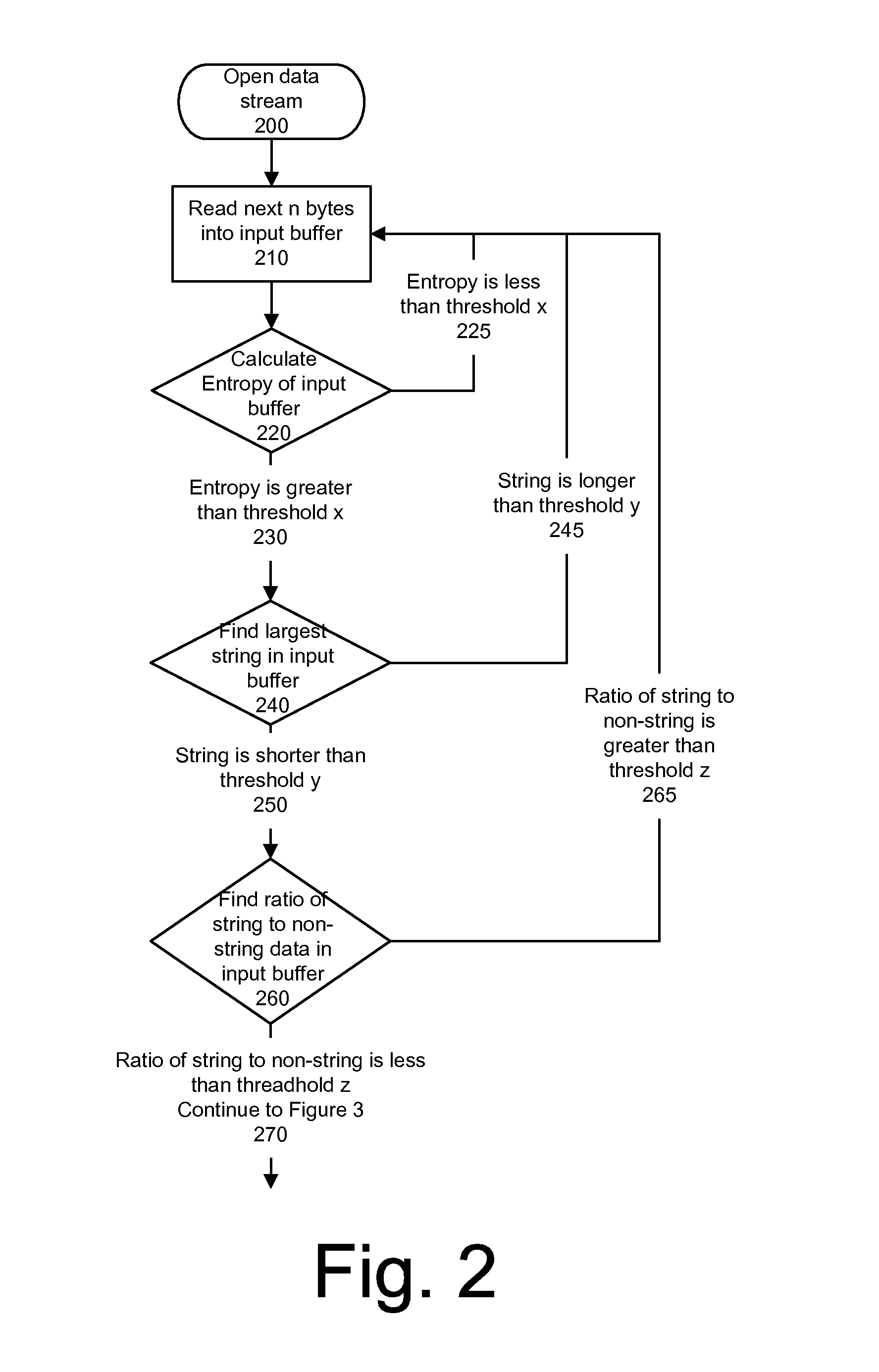
System and method for detecting executable machine instructions in a data stream
ActiveUS20140237600A1Effective presenceReliable identificationMemory loss protectionError detection/correctionData streamAlgorithm
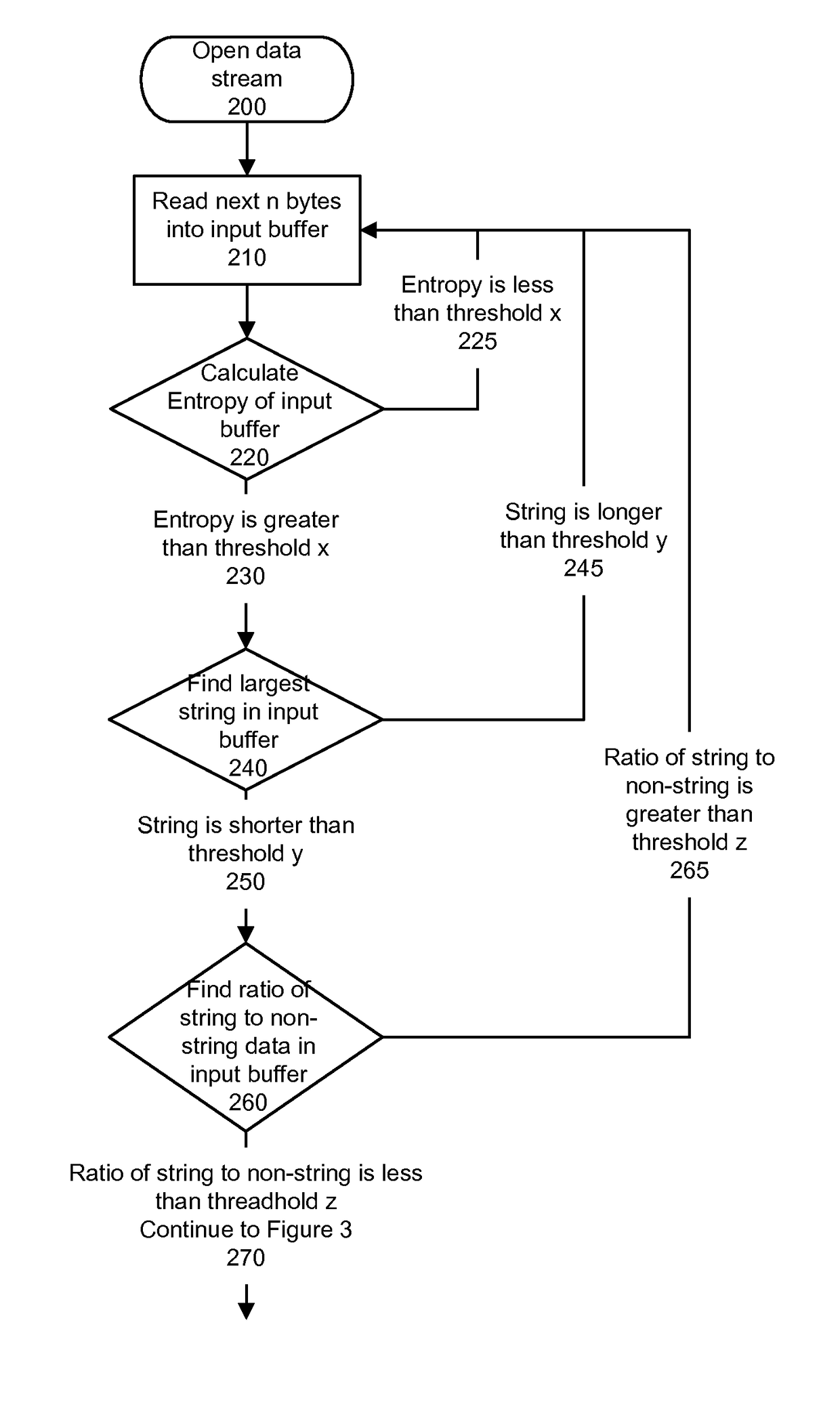
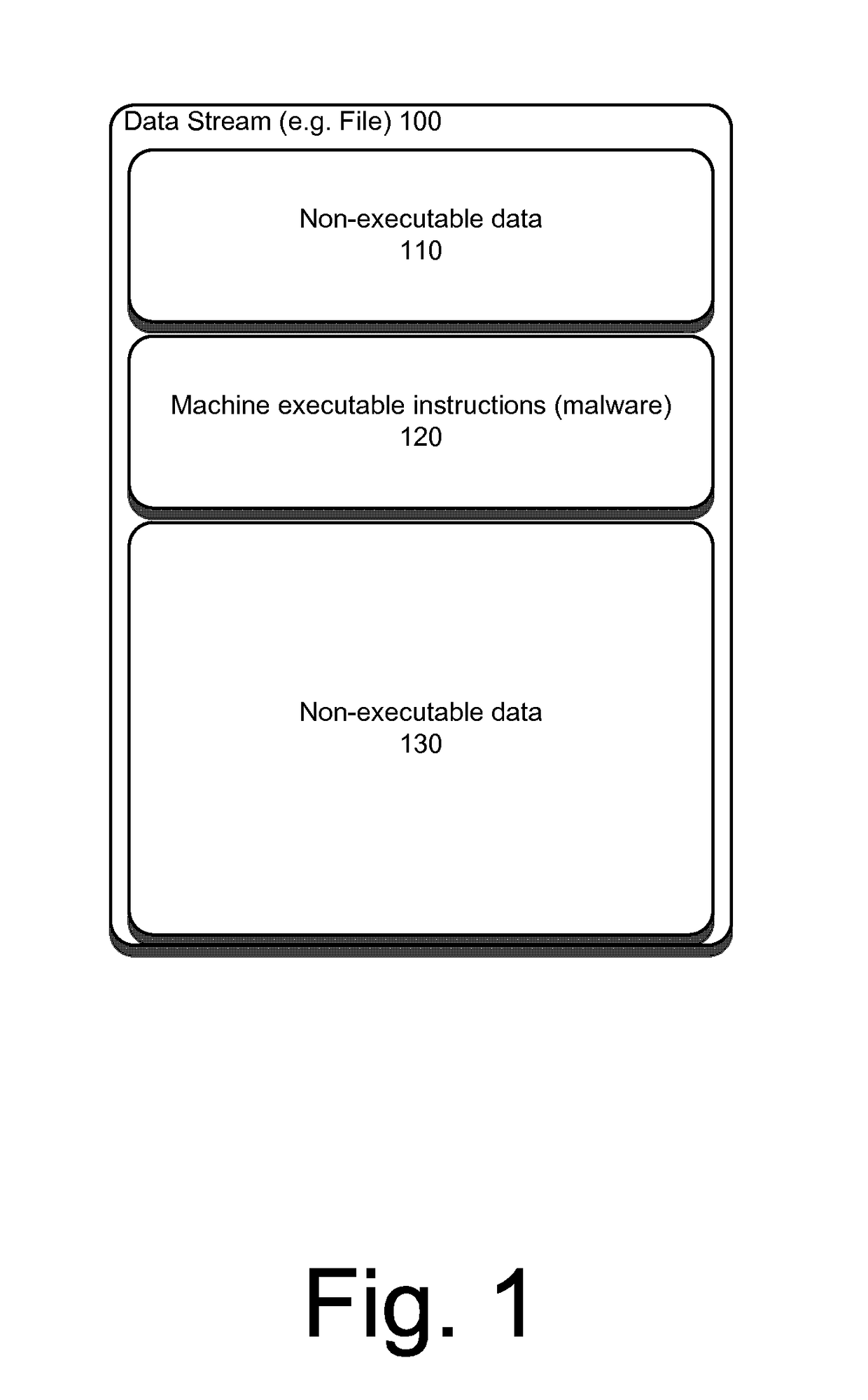
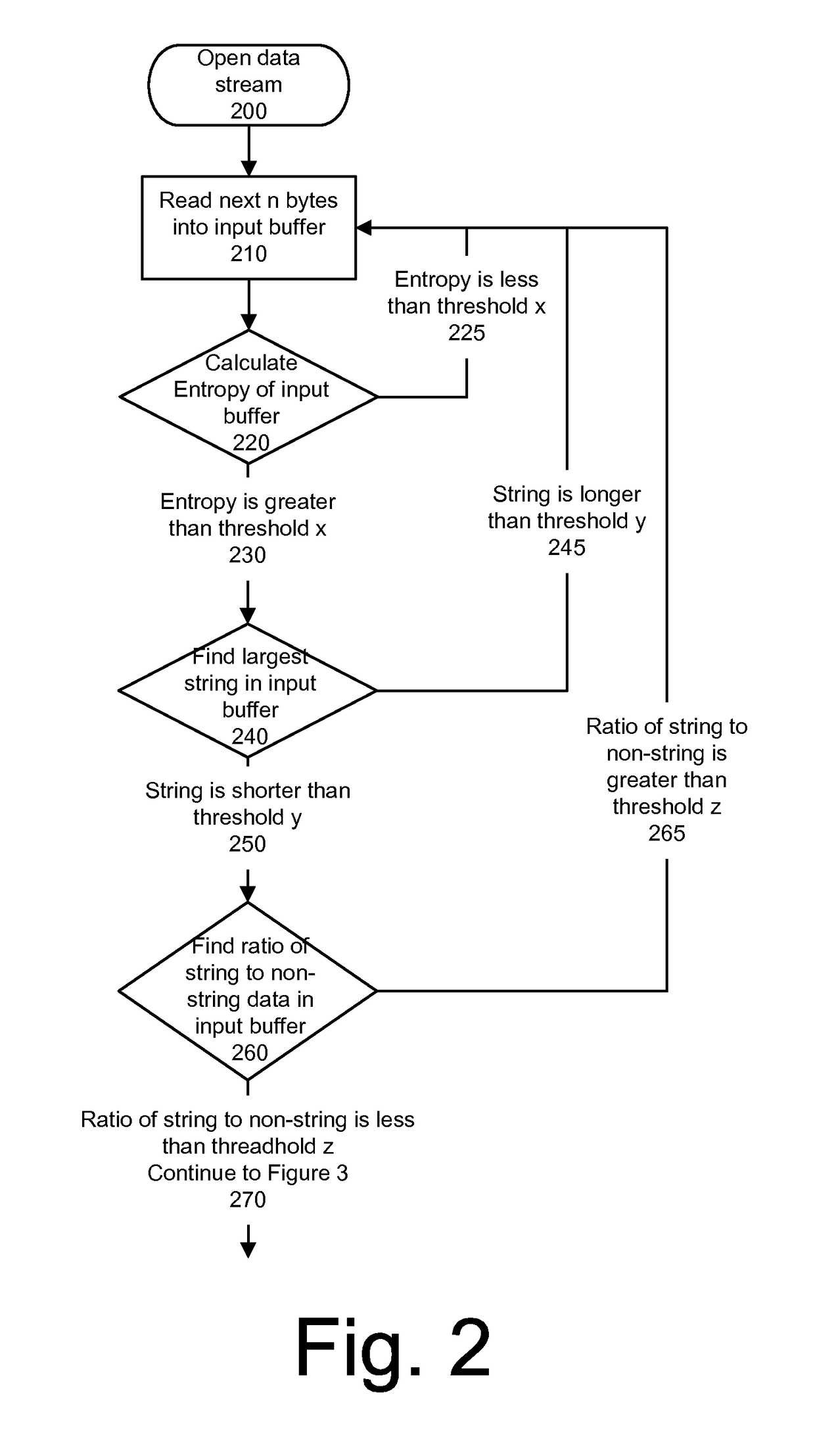
Detecting executable machine instructions in a data is accomplished by accessing a plurality of values representing data contained within a memory of a computer system and performing pre-processing on the plurality of values to produce a candidate data subset. The pre-processing may include determining whether the plurality of values meets (a) a randomness condition, (b) a length condition, and / or (c) a string ratio condition. The candidate data subset is inspected for computer instructions, characteristics of the computer instructions are determined, and a predetermined action taken based on the characteristics of the computer instructions.
Owner:GOOGLE LLC
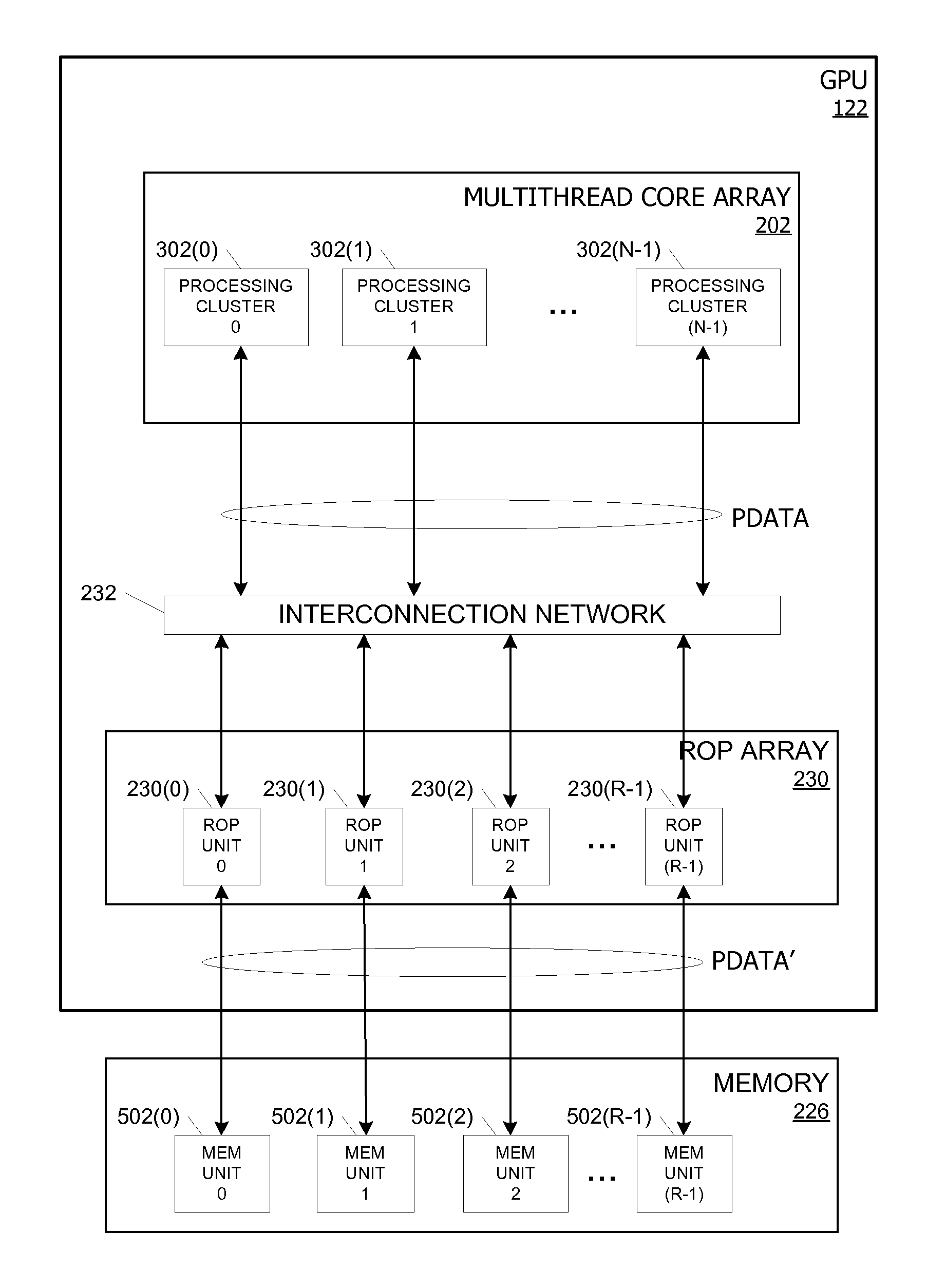
Atomic memory operators in a parallel processor
ActiveUS7627723B1Direct performanceLower performance requirementsCathode-ray tube indicatorsProcessor architectures/configurationMachine instructionParallel processing
Owner:NVIDIA CORP
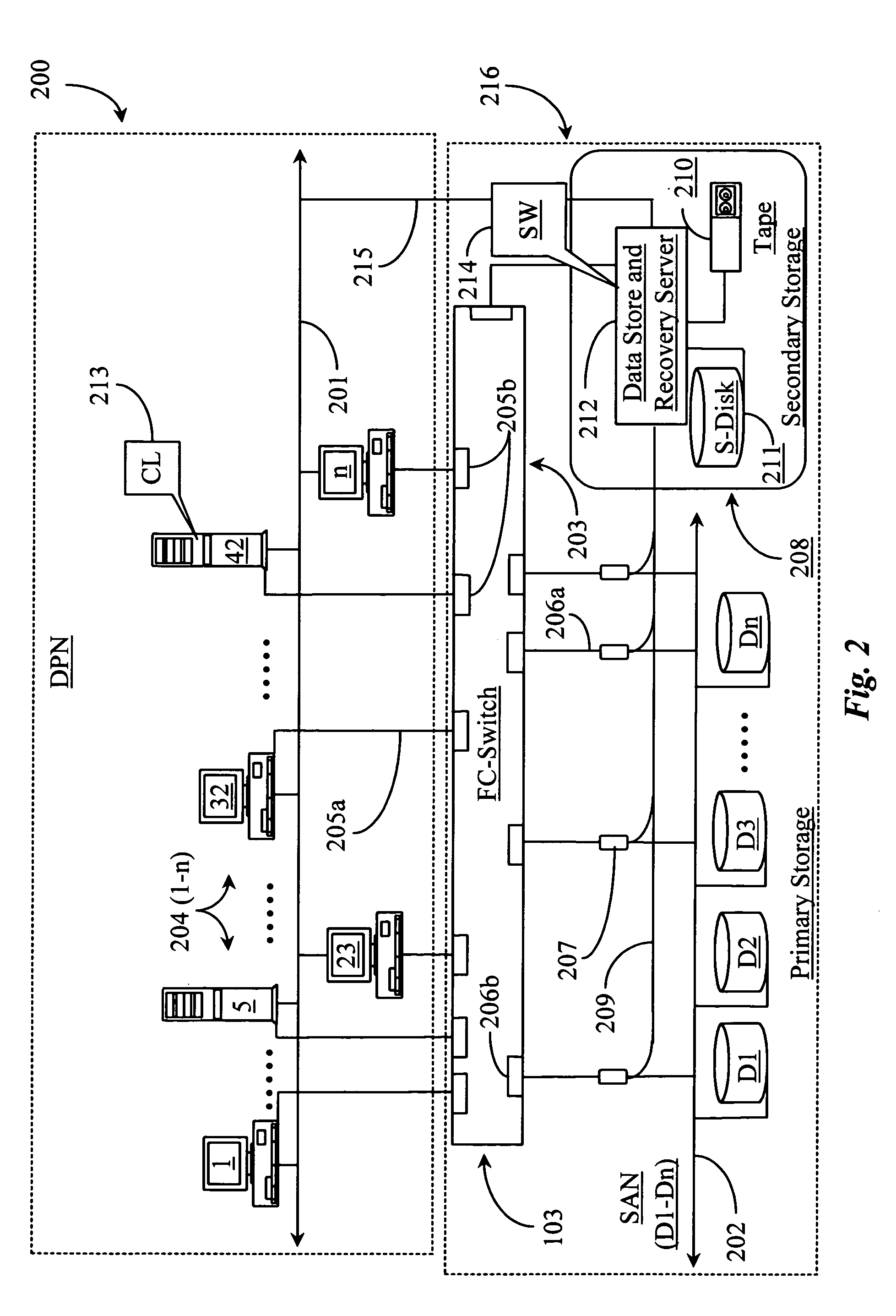
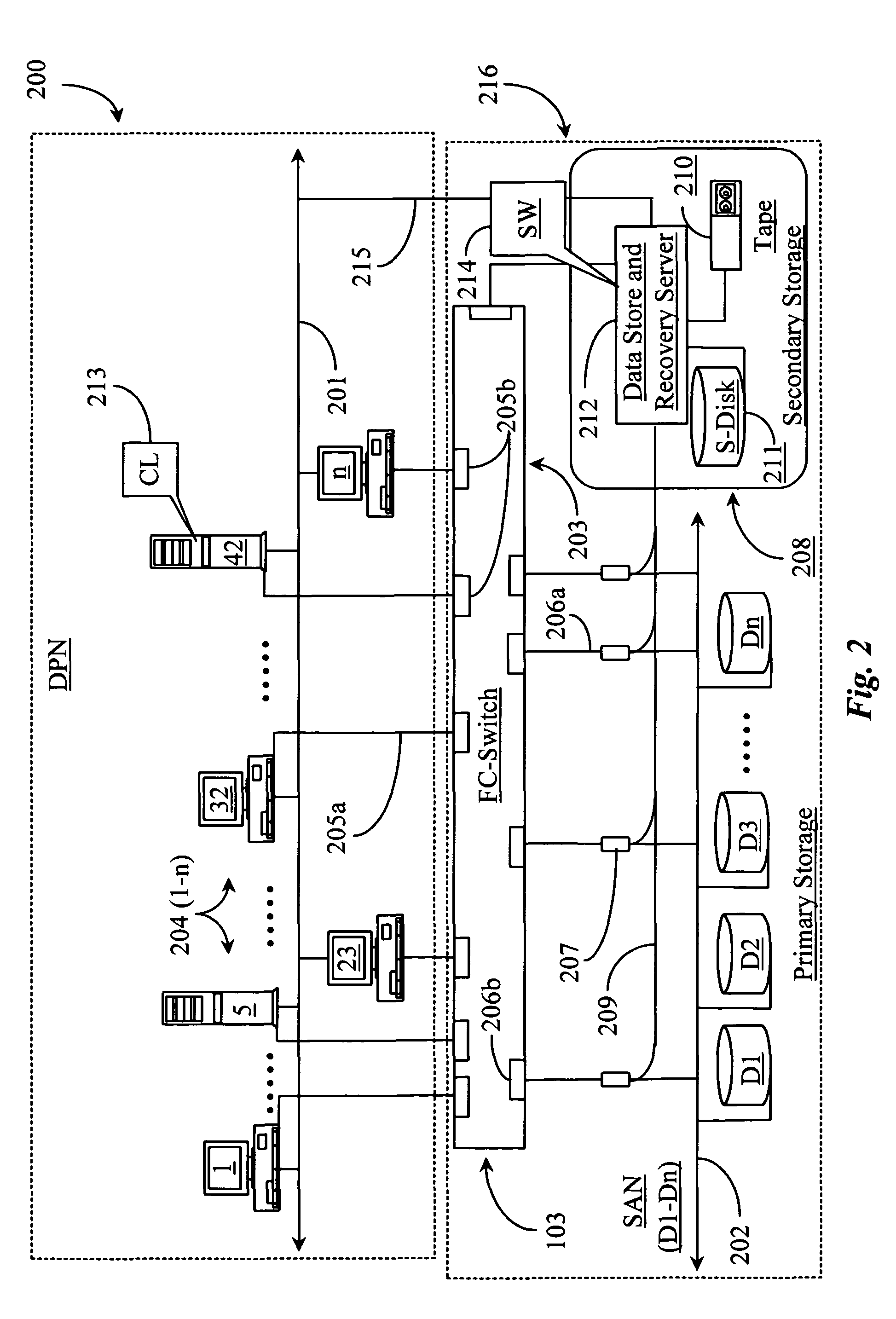
Methods and apparatus for accessing data from a primary data storage system for secondary storage
InactiveUS8055745B2Error detection/correctionMultiple digital computer combinationsMachine instructionClient-side
A system for providing secondary data storage and recovery services for one or more networked host nodes includes a server application for facilitating data backup and recovery services; a first data storage medium accessible to the server application; a second data storage medium accessible to the server application; at least one client application for mapping write locations allocated by the first data storage medium to write locations represented in a logical view of the first data storage medium; and at least one machine instruction enabling direct read capability of the first data storage medium by the server application for purposes of subsequent time-based storage of the read data into the secondary data storage medium.
Owner:MICROSOFT TECH LICENSING LLC
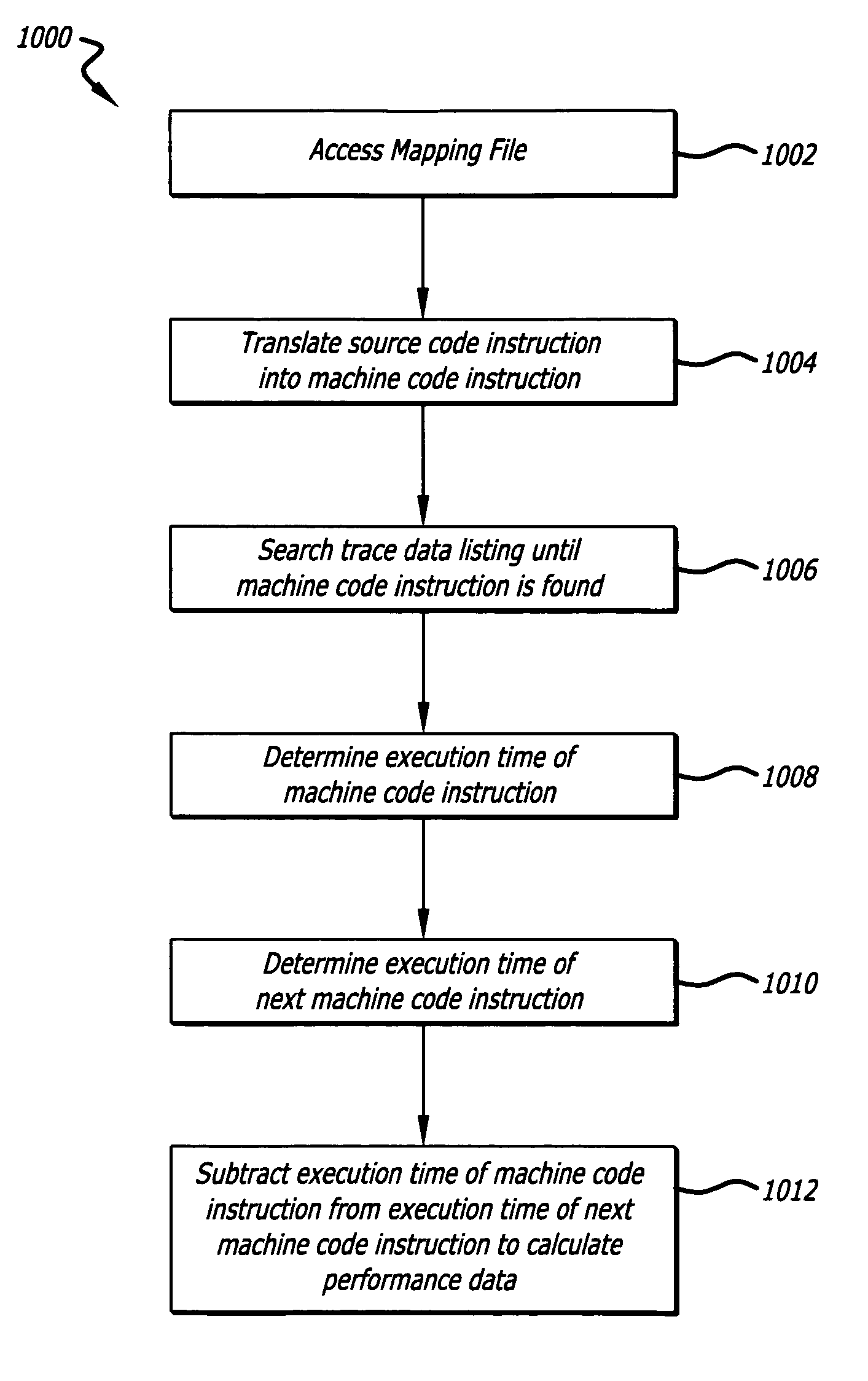
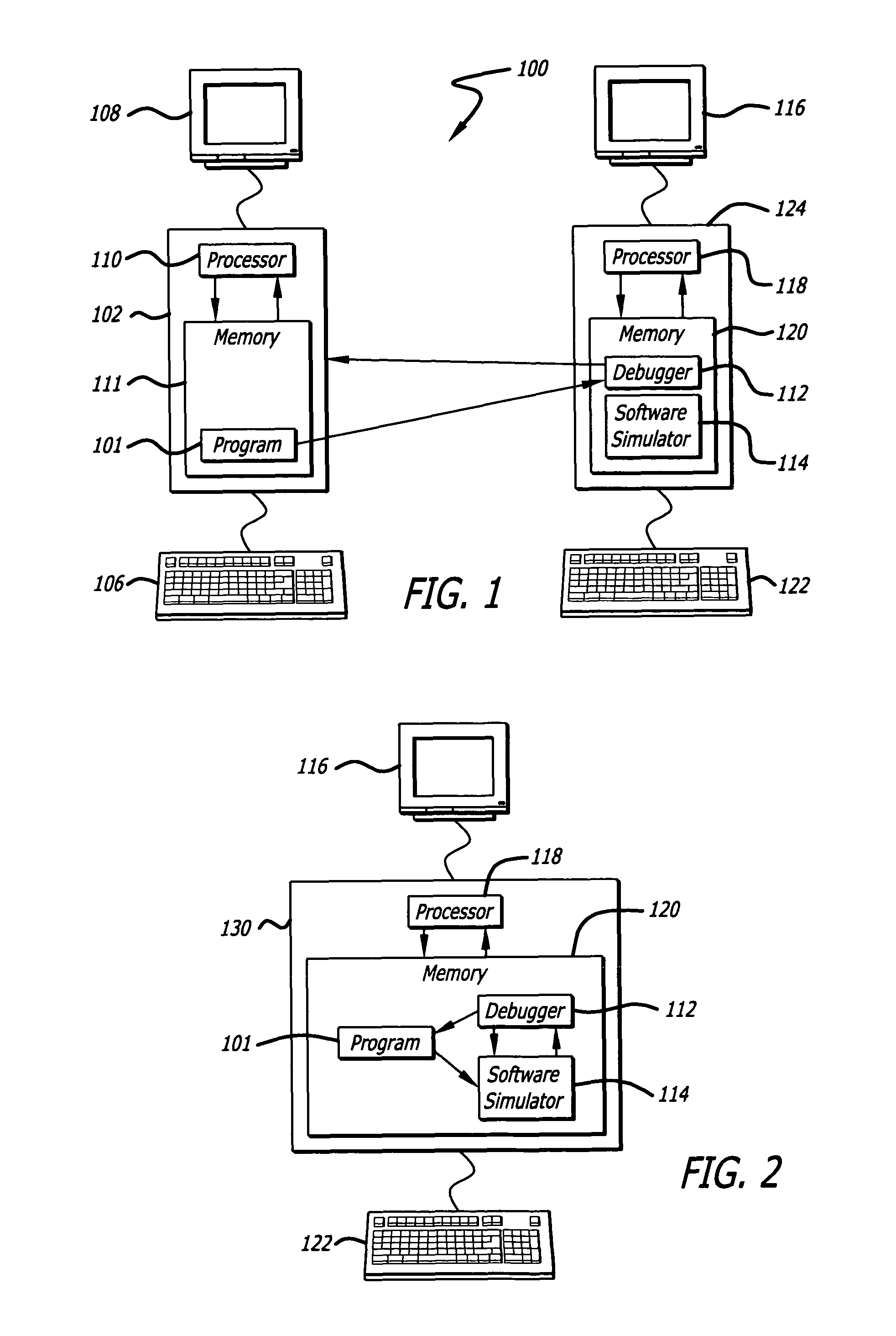
Post-execution software debugger with performance display
ActiveUS7653899B1Error detection/correctionSpecific program execution arrangementsParallel computingMachine instruction
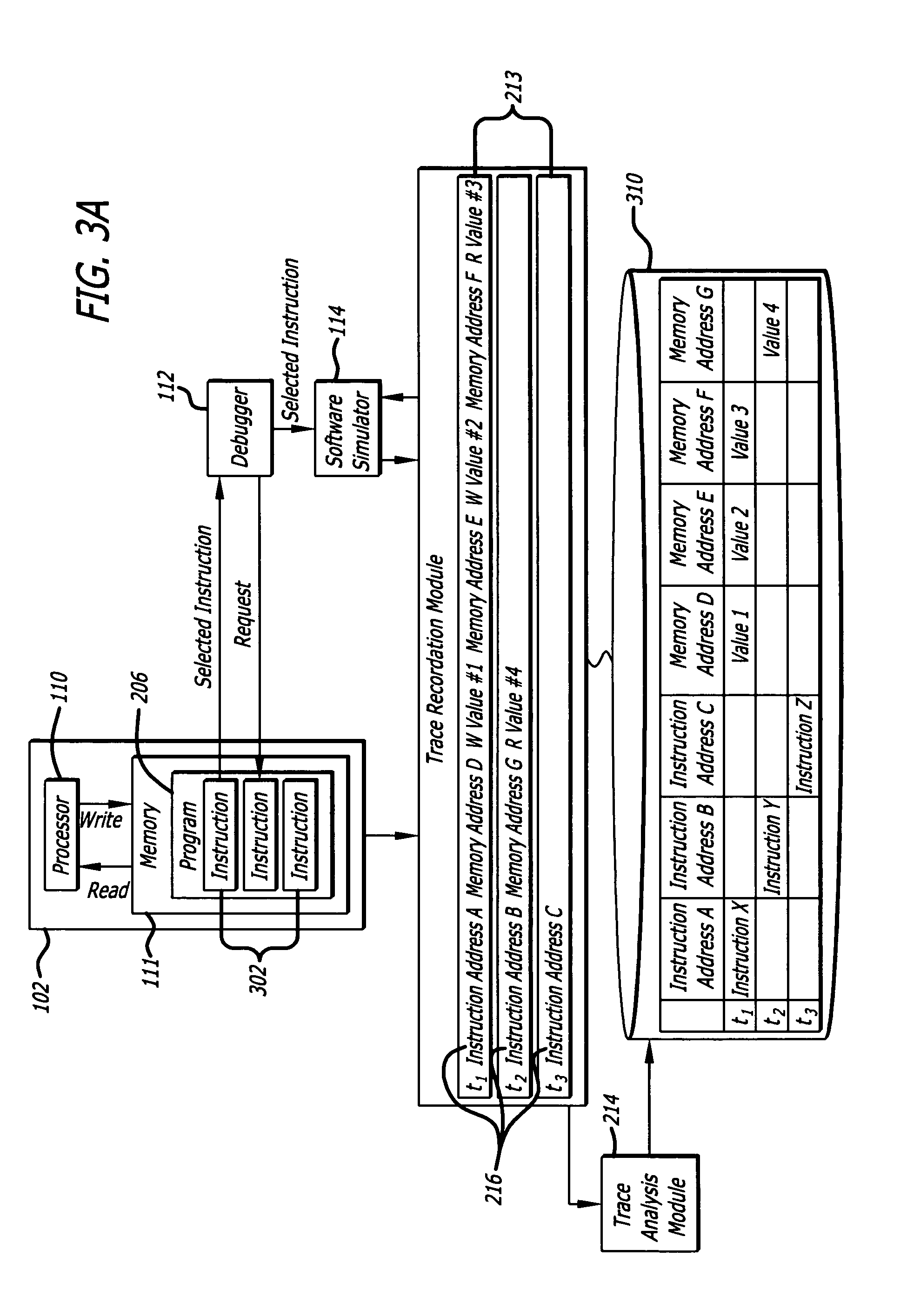
A method for finding an error in a computer program is disclosed. A sequence of machine instructions performed by a processor is recorded as trace data. A mapping file is accessed. A source code instruction is translated into a machine code instruction according to a mapping found in the mapping file. Further, at least a portion of the trace data is searched through until the machine code instruction is found. In addition, a first execution time of the machine code instruction is determined by reviewing the trace data in a first vicinity that an address of the machine code instruction is located. Further, a second execution time of the next machine code instruction is determined by reviewing the trace data in a second vicinity that an address of the next machine code instruction is located. Accordingly, performance data is calculated by subtracting the first execution time from the second execution time. The performance data is displayed.
Owner:GREEN HILLS SOFTWARE
System and method for detecting executable machine instructions in a data stream
ActiveUS10019573B2Effective presenceReliable identificationPlatform integrity maintainanceData streamAlgorithm
Detecting executable machine instructions in a data stream is accomplished by accessing a plurality of values representing data contained within a memory of a computer system and performing pre-processing on the plurality of values to produce a candidate data subset. The pre-processing may include determining whether the plurality of values meets (a) a randomness condition, (b) a length condition, and / or (c) a string ratio condition. The candidate data subset is inspected for computer instructions, characteristics of the computer instructions are determined, and a predetermined action is taken based on the characteristics of the computer instructions.
Owner:GOOGLE LLC
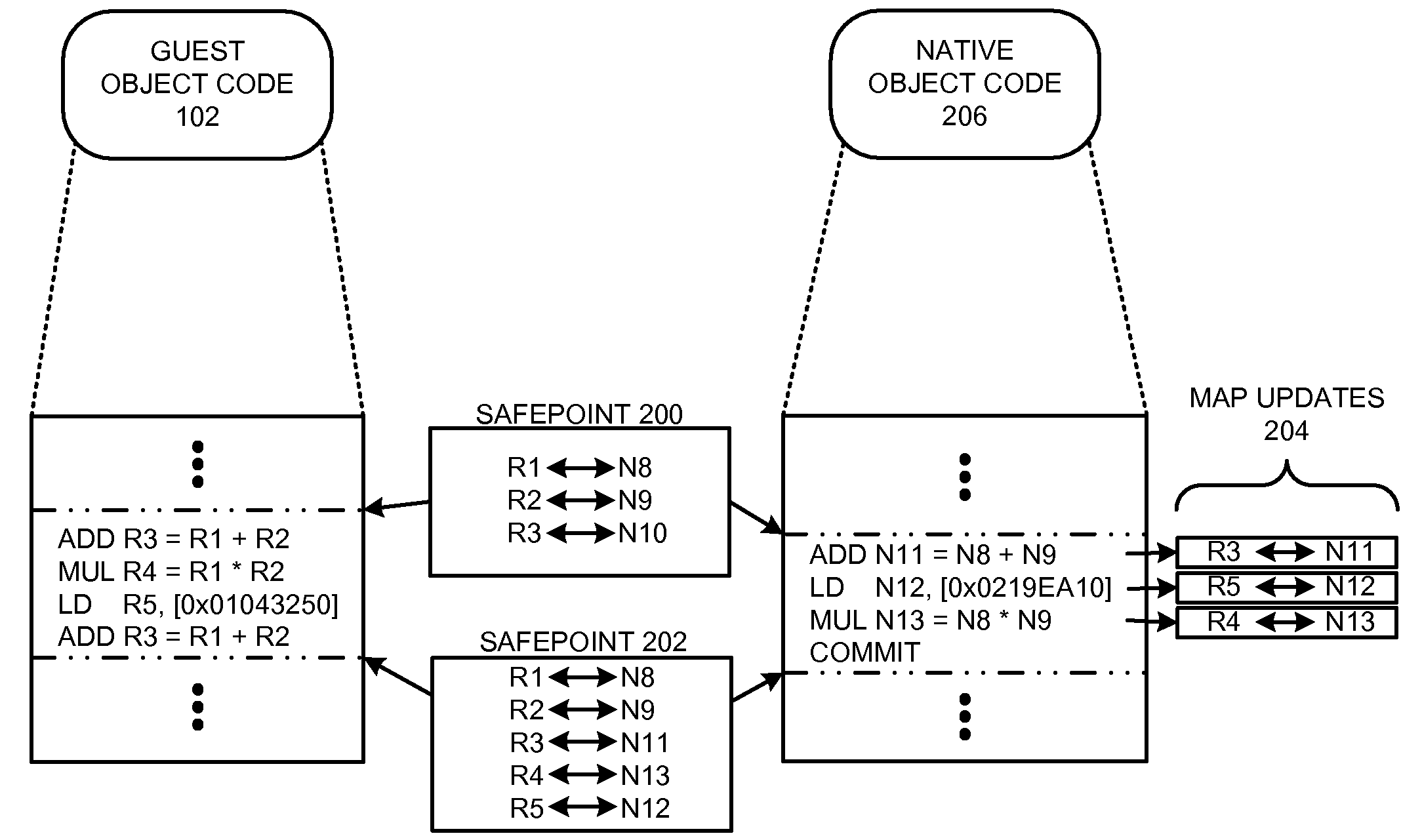
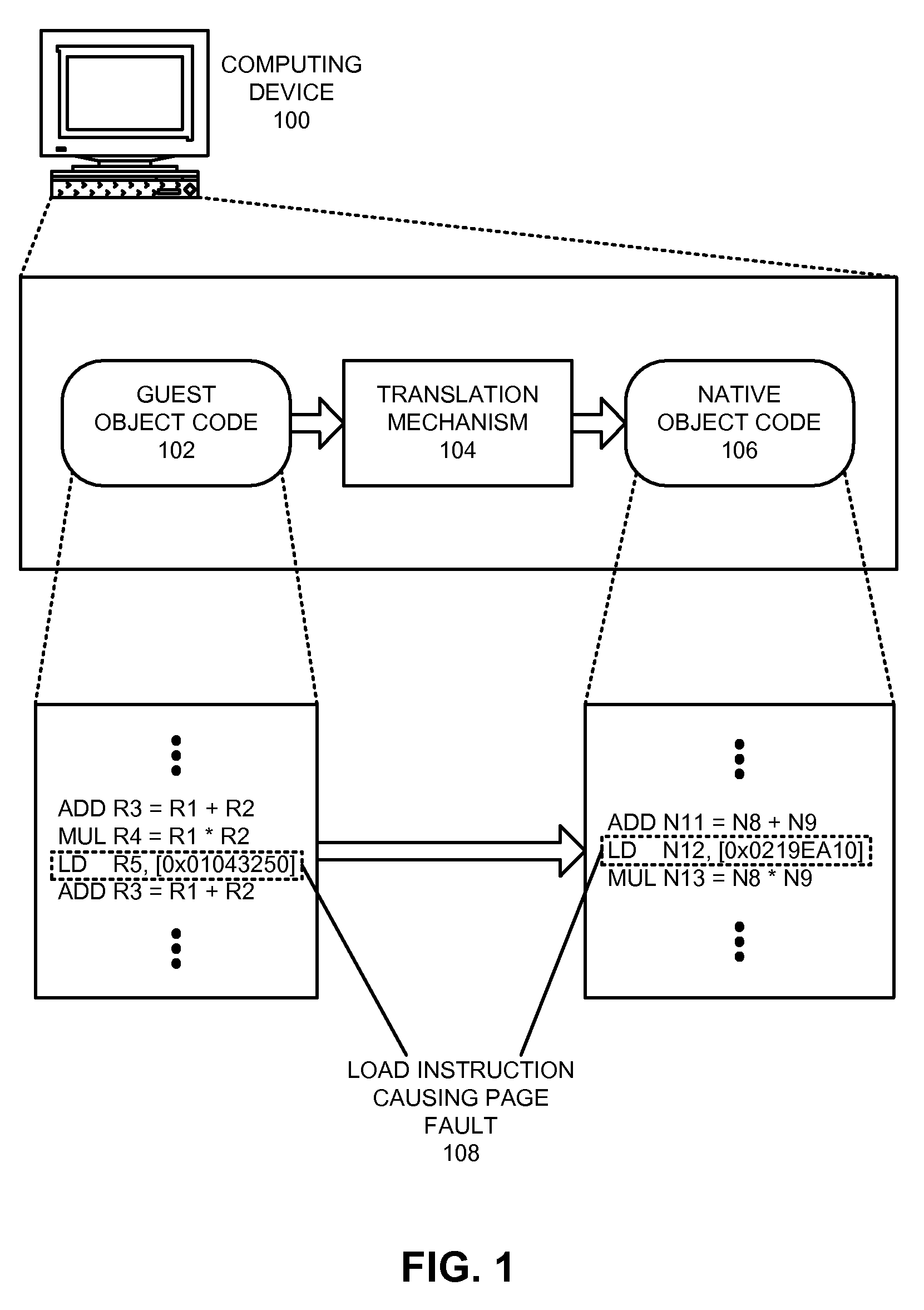
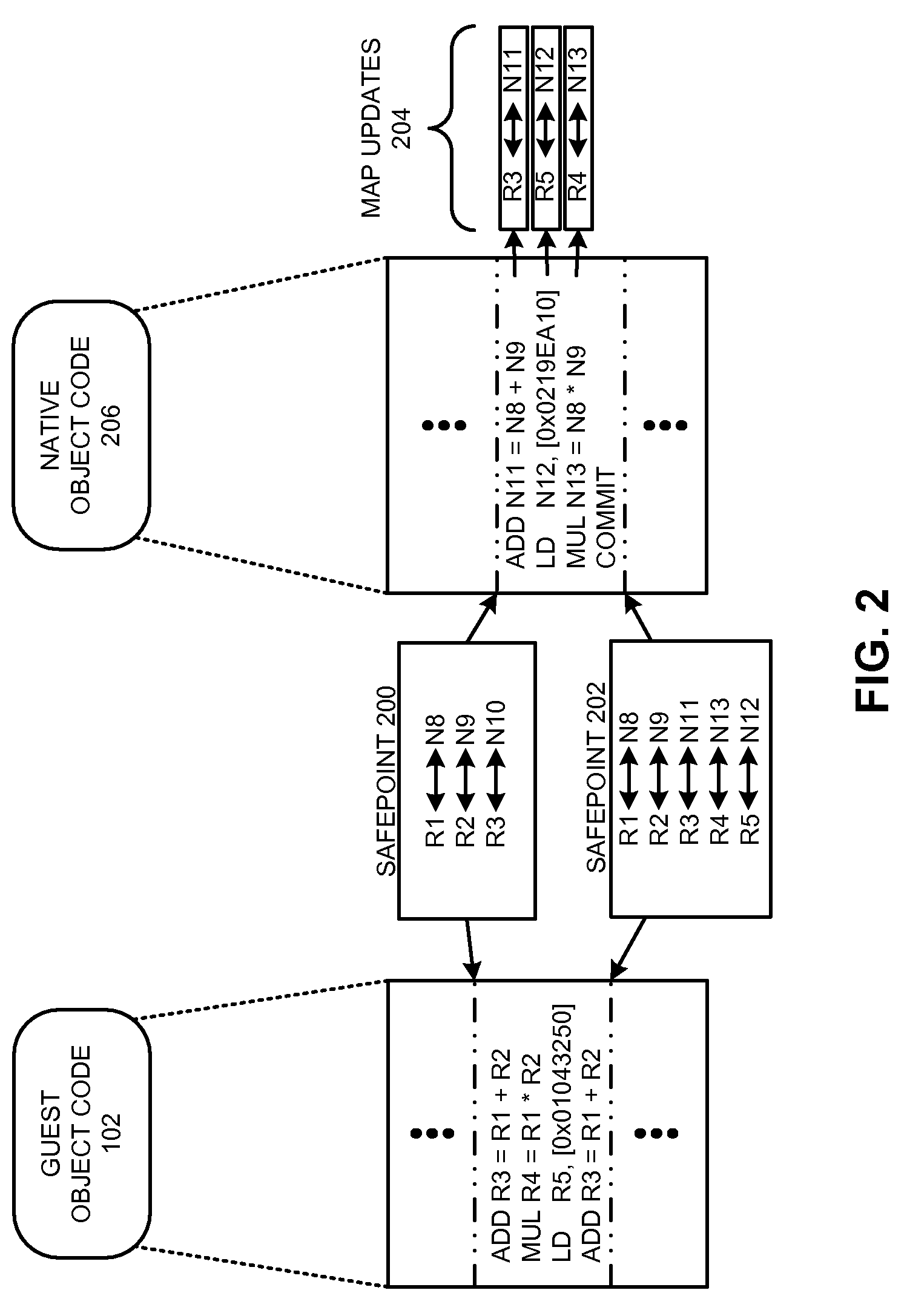
Using safepoints to provide precise exception semantics for a virtual machine
InactiveUS20100153776A1Facilitates precise exception semantics for a virtual machineEasy to implementFault responseSoftware simulation/interpretation/emulationSemanticsMachine instruction
One embodiment of the present invention provides a system that provides precise exception semantics for a virtual machine. During operation, the system receives a program comprised of instructions that are specified in a machine instruction set architecture of the virtual machine, and translates these instructions into native instructions for the processor that the virtual machine is executing upon. While performing this translation, the system inserts one or more safepoints into the translated native instructions. The system then executes these native instructions on the processor. During execution, if the system detects that an exception was signaled by a native instruction, the system reverts the virtual machine to a previous safepoint to ensure that the virtual machine will precisely emulate the exception behavior of the virtual machine's instruction set architecture. The system uses a gated store buffer to ensure that any stores that occurred after the previous safepoint are discarded when reverting the virtual machine to the previous safepoint.
Owner:SUN MICROSYSTEMS INC
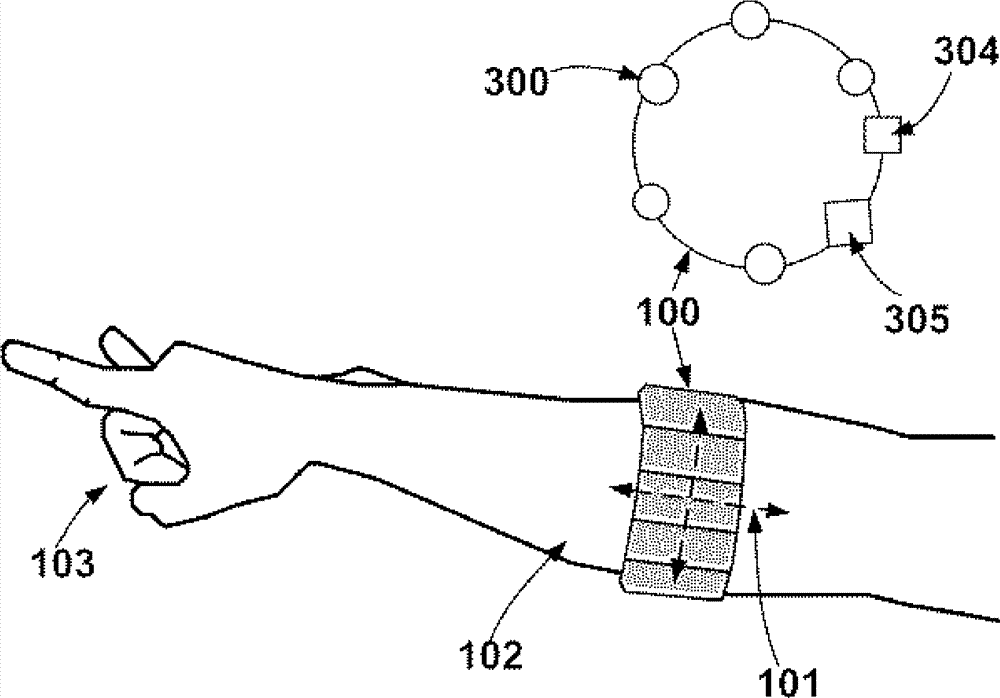
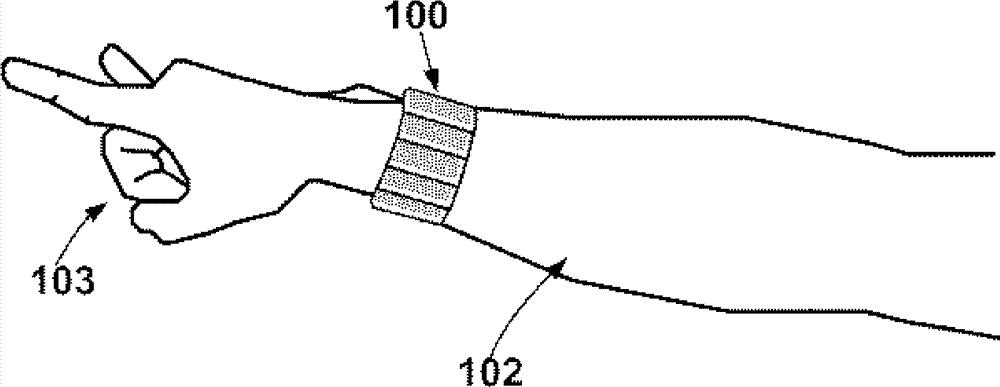
Gesture recognition device based on arm muscle current detection and motion sensor
InactiveCN103777752AInput/output for user-computer interactionGraph readingCurrent sensorMachine instruction
The invention discloses a gesture recognition device based on arm muscle current signal detection and a motion sensor, and the gesture recognition device serving as a machine instruction input device can be used for any electronic system needing man-machine interaction. The device comprises a hand ring or an arm ring, wherein according to the shape, the hand ring or the arm ring can be worn on the wrist or the front arm, biological currents generated in the motion process of the arm muscles are extracted through one or more muscle skin current sensors tightly attached to the skin, the currents pass through an amplifier circuit, a filter circuit and an analog-digital conversion circuit, and characteristic parameters of gestures are extracted through real-time digital signal algorithm processing, and therefore the gestures are recognized. The recognized gestures are mapped to be all kinds of control instructions allowed to be configured, and the instructions are transmitted to a controlled mainframe in a wireless or wired mode through Bluetooth or others. The gestures are judged through the arm muscle currents and the motion sensor, and a bran-new man-machine interaction instruction input mode is achieved.
Owner:上海威璞电子科技有限公司
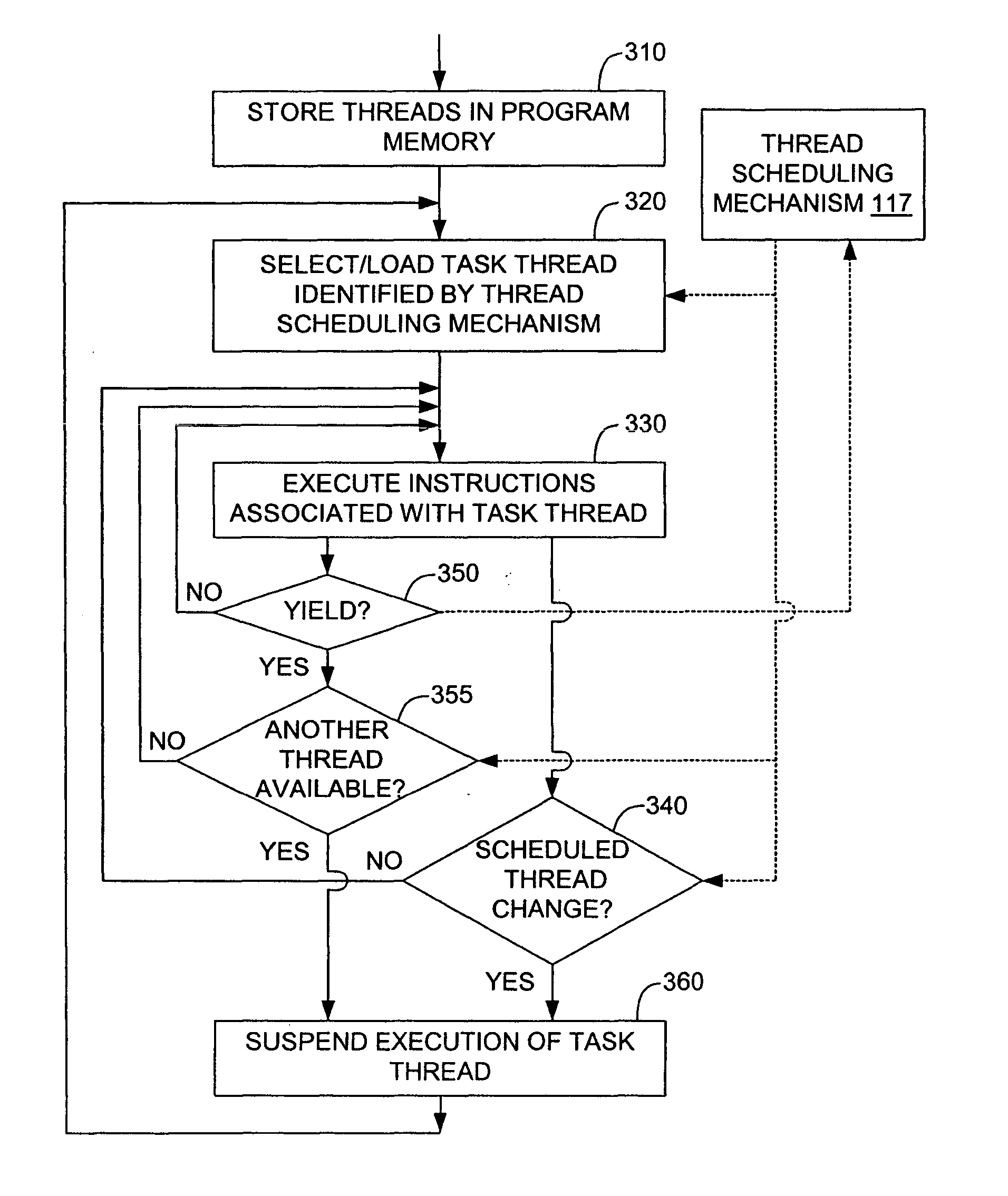
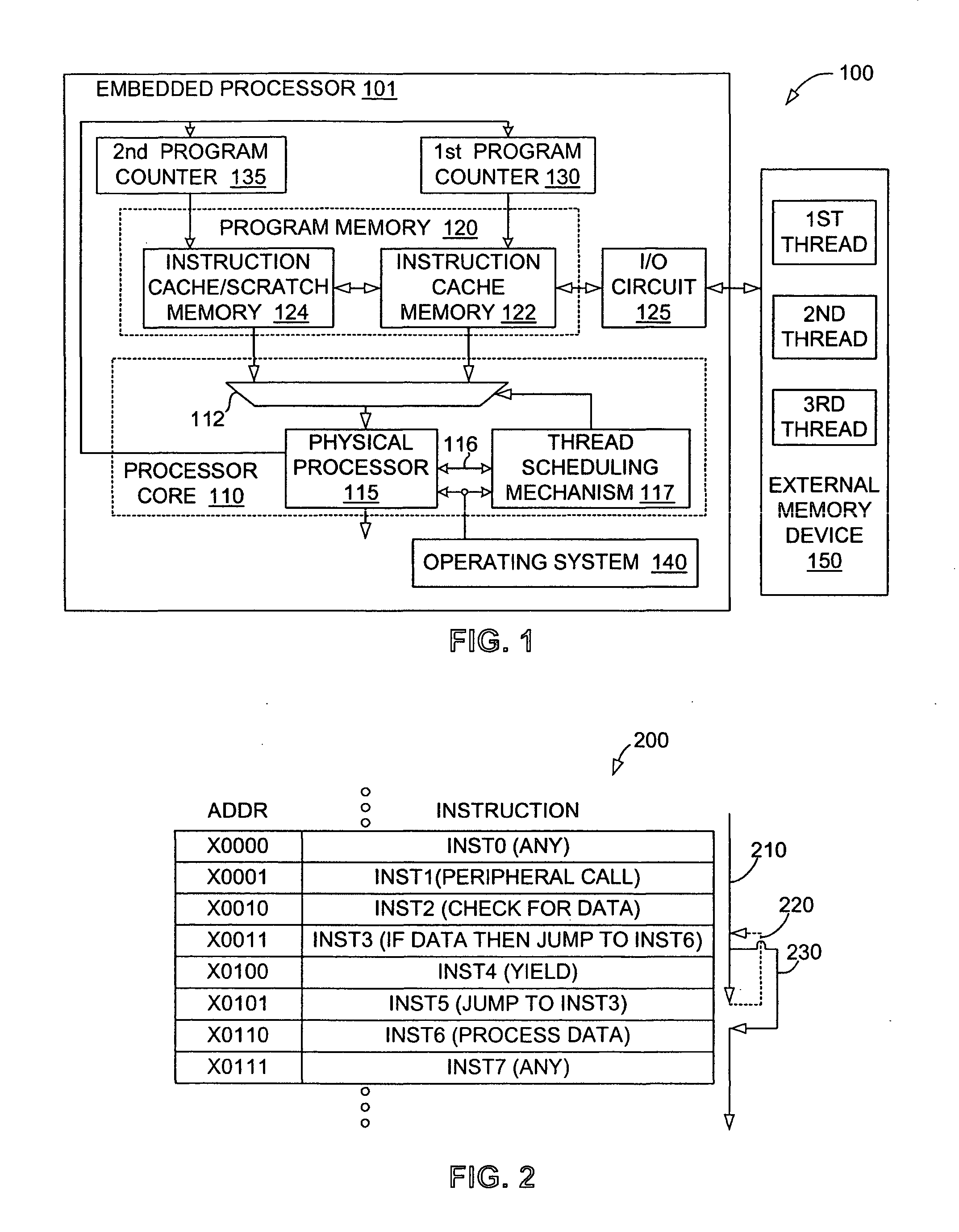
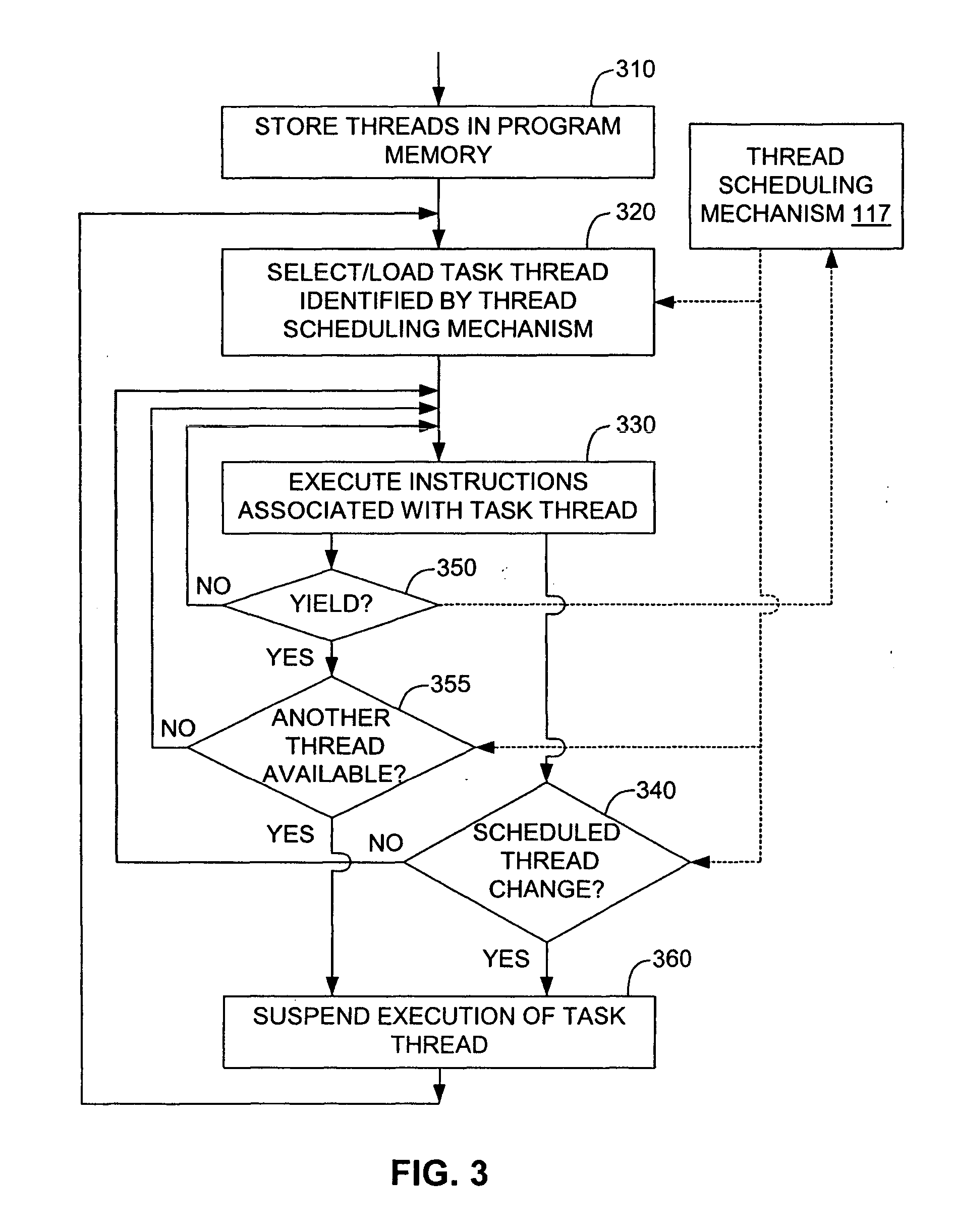
Machine instruction for enhanced control of multiple virtual processor systems
InactiveUS20050108711A1Facilitates increased processor efficiencyEasy to cleanMultiprogramming arrangementsConcurrent instruction executionControl systemThread scheduling
Owner:INFINEON TECH AG
Compiler apparatus and compilation method
InactiveUS20040154006A1Avoid changeReduce power consumptionEnergy efficient ICTSoftware engineeringMachine instructionInstruction cycle
A compiler apparatus that is capable of generating instruction sequences for causing a processor with parallel processing capability to operate with lower power consumption is a compiler apparatus that translates a source program into a machine language program for the processor including a plurality of execution units which can execute instructions in parallel and a plurality of instruction issue units which issue the instructions executed respectively by the plurality of execution units, and includes: a parser unit operable to parse the source program; an intermediate code conversion unit operable to convert the parsed source program into intermediate codes; an optimization unit operable to optimize the intermediate codes so as to reduce a hamming distance between instructions placed in positions corresponding to the same instruction issue unit in consecutive instruction cycles, without changing dependency between the instructions corresponding to the intermediate codes; and a code generation unit operable to convert the optimized intermediate codes into machine language instructions.
Owner:SOCIONEXT INC
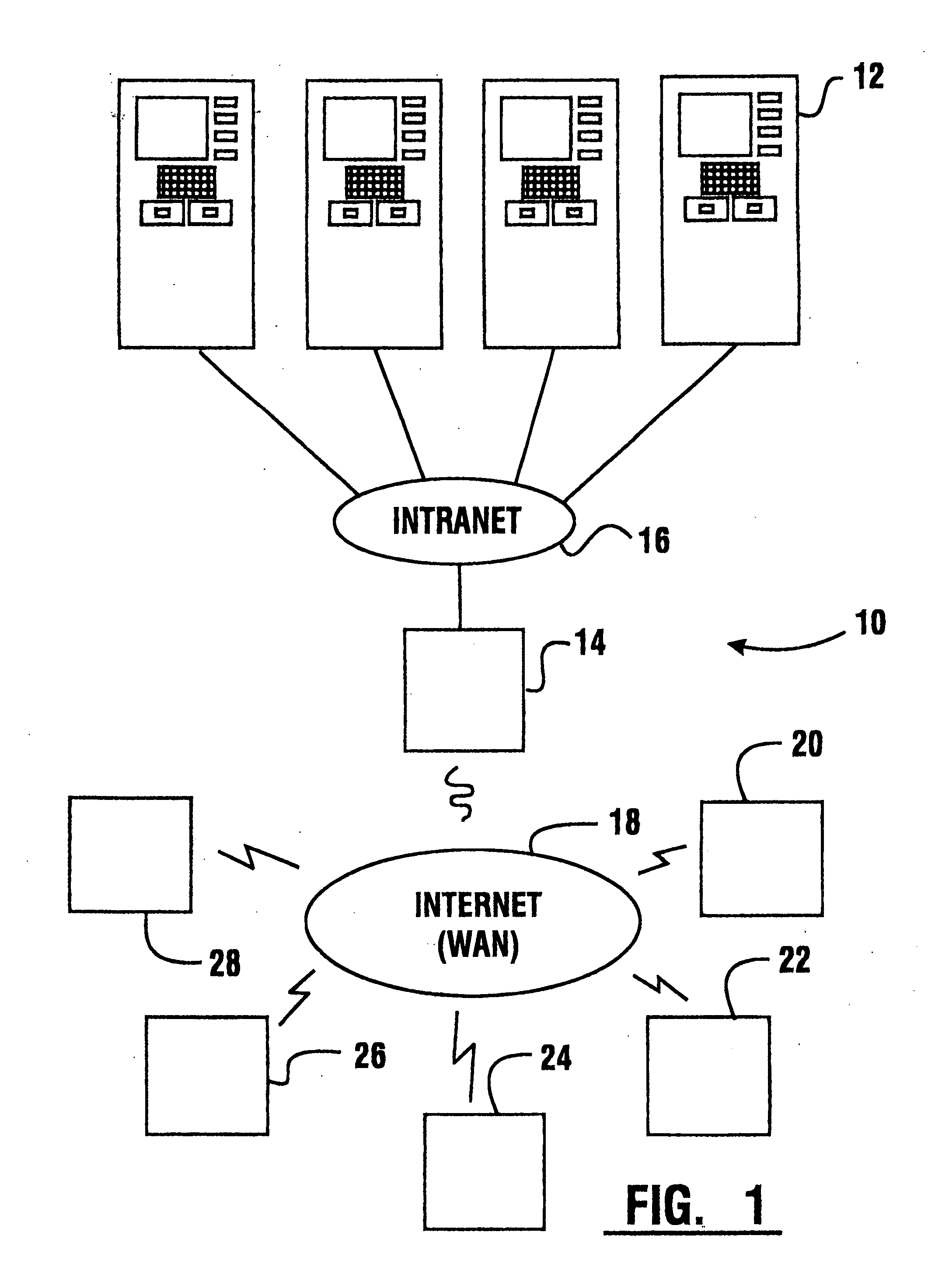
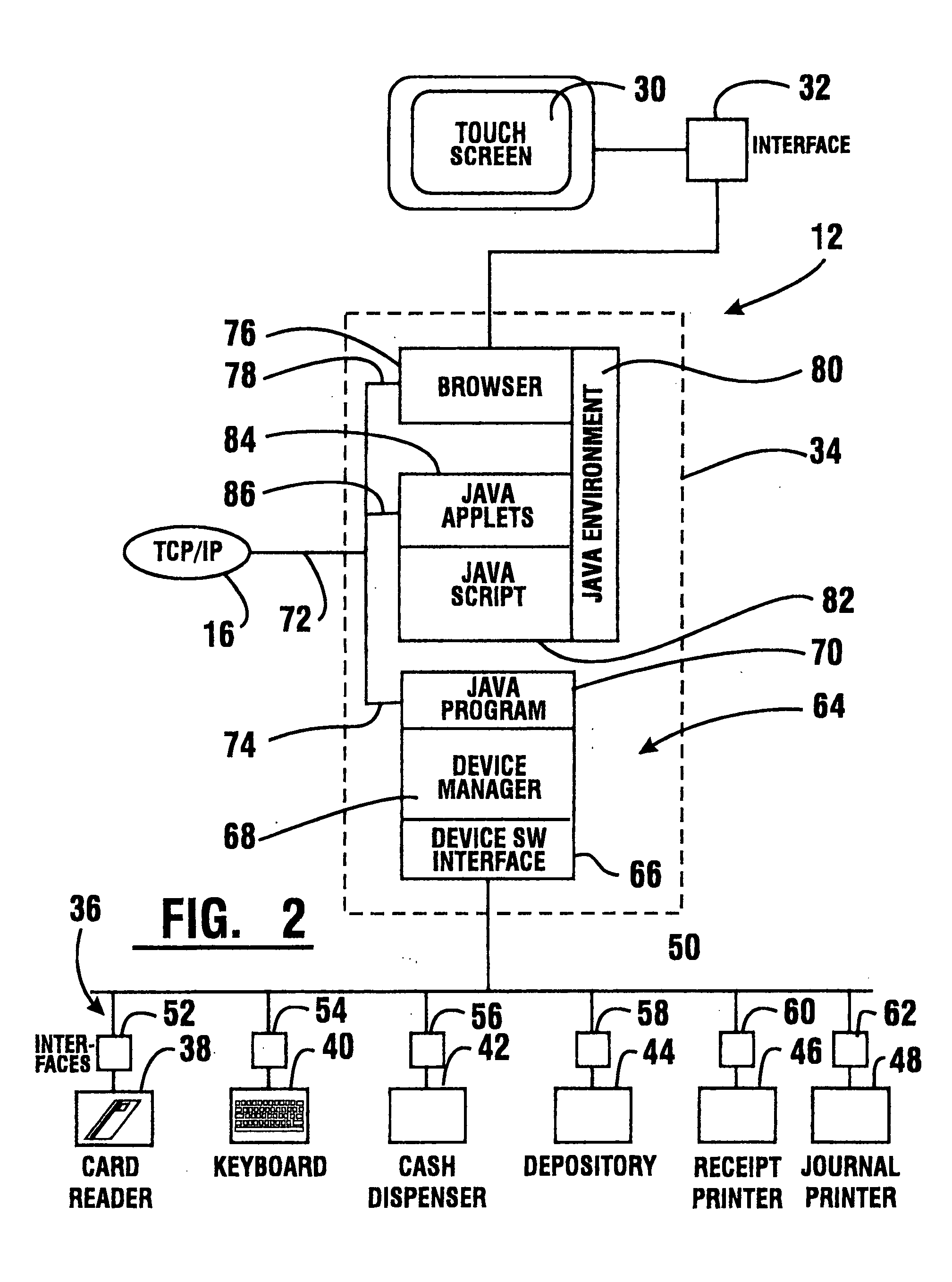
Method of developing automated banking machine instructions
InactiveUS20050216888A1Easy to operateMaintain securityPayment architectureATM softwaresComputer printingTransaction data
A method for visual programming an automated transaction machine (12). The method includes the creation of terminal directors (225) that generally correspond to transactions performed by the automated transaction machine. The terminal directors are programmed by visually creating associations (238) between a plurality of ATM objects (230, 232) in a work space (224). Exemplary ATM objects include an authorization object (260), a back stage control object (262), a card reader object (264), a customer profile object (266), a depositor object (268), a dispenser object (270), keypad object (272), a logic object (274), a OCS object (276), a presenter object (278), a PIN entry object (280), a printer object (282), a sync object (284), and a transaction data object (286). A portion of the exemplary ATM objects are operative to interface with a device interface layer (728) for communicating with physical hardware devices (724, 726).
Owner:DIEBOLD NIXDORF
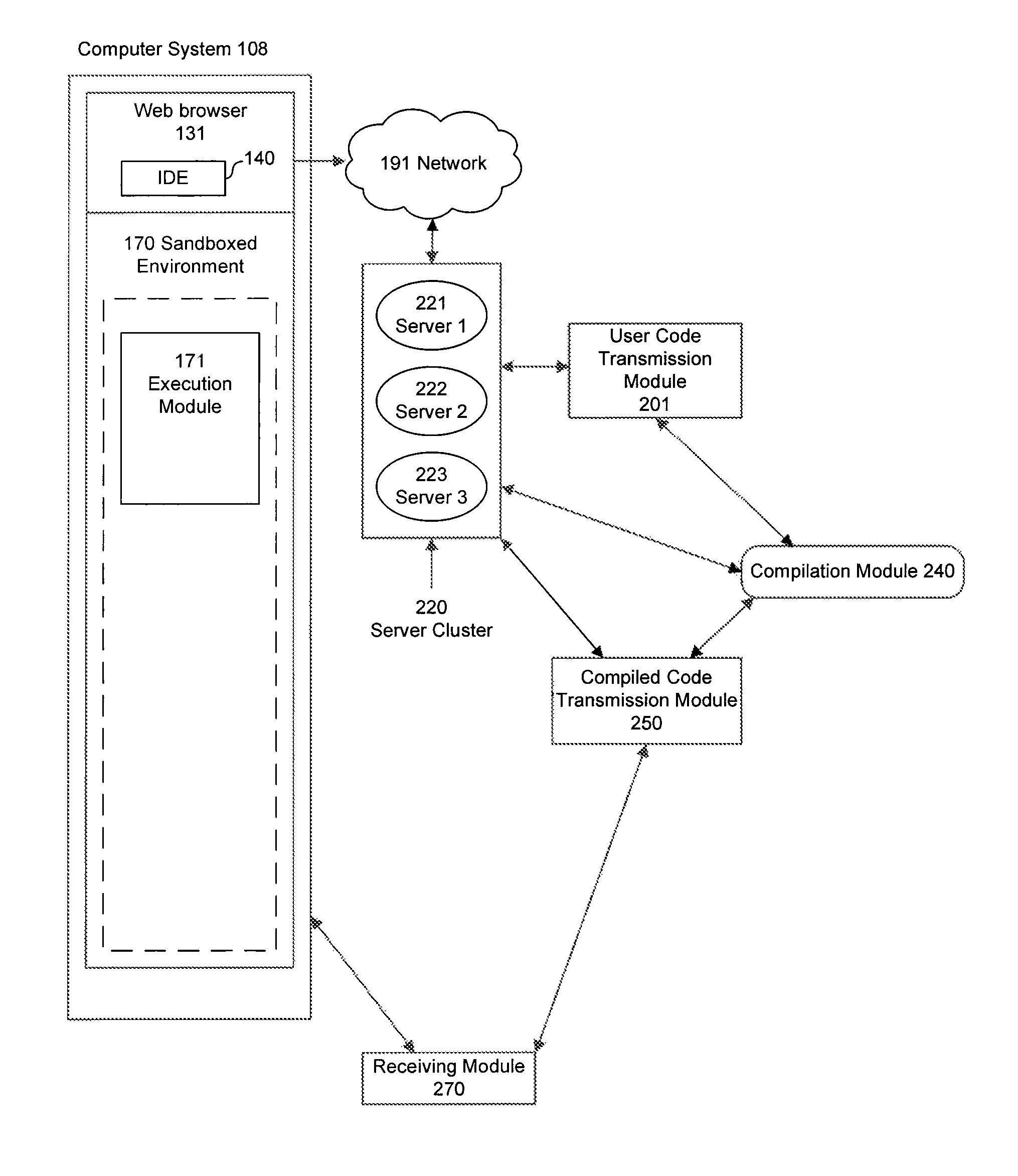
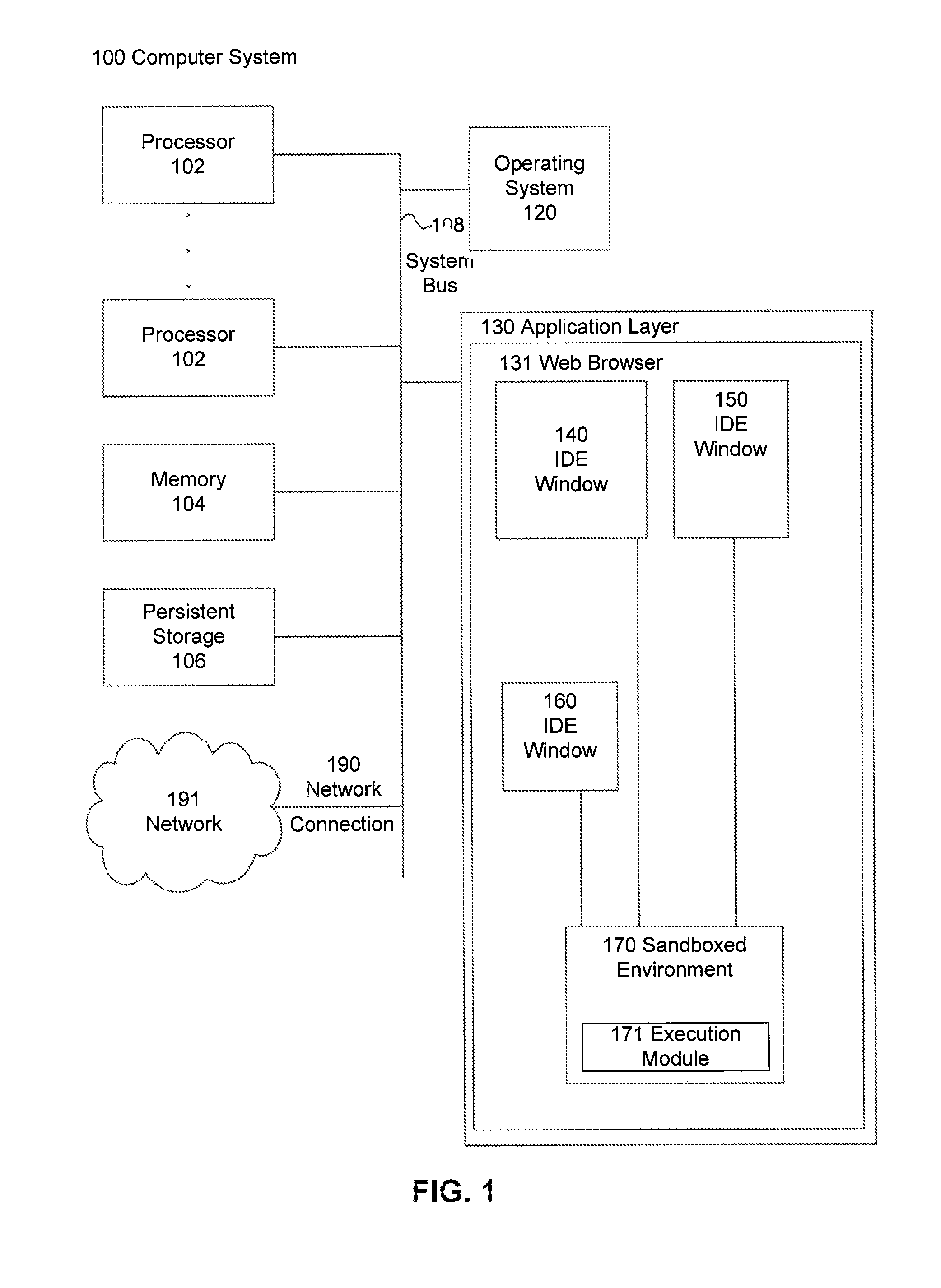
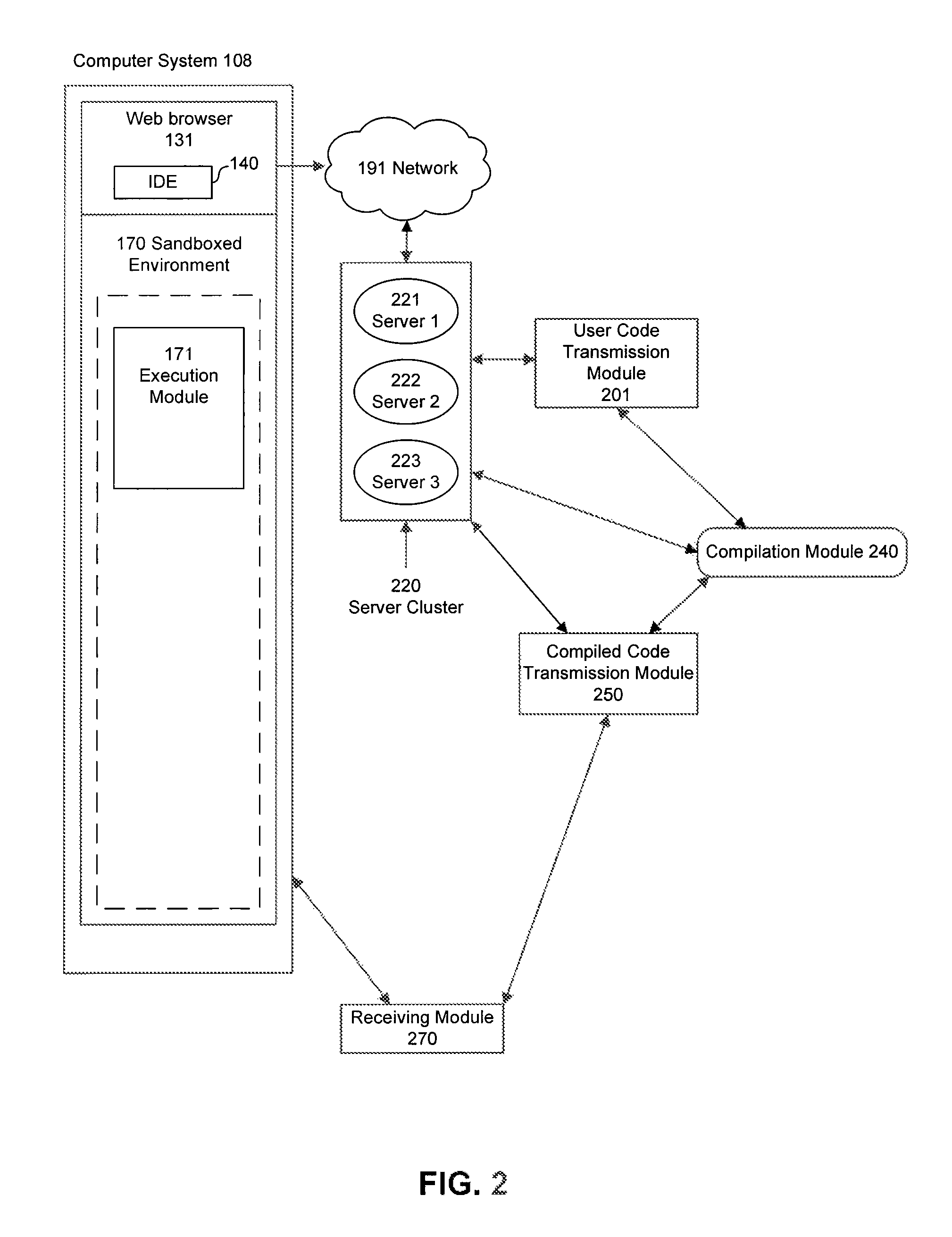
Integrated development environment with network-based compilation and sandboxed native machine-language capabilities
InactiveUS8281288B1Improve performanceEasy to compileMultiple digital computer combinationsSoftware designWeb browserNetwork connection
An IDE is provided by a web browser on a client machine, the IDE having a document editor that allows a user to generate source code. The source code is transmitted from the client machine to one or more servers via a network connection to be compiled into compiled native machine instructions. The compiled native machine instructions are received from the one or more servers by the client machine. The compiled native machine instructions are executed in a sandboxed environment on the client machine, such that system calls originating from the compiled native machine instructions that present a security risk are blocked using the sandboxed environment and system calls originating from the compiled native machine instructions that do not present a security risk are allowed in the sandboxed environment.
Owner:GOOGLE LLC
Secure communications in gaming system
ActiveUS20080171598A1Apparatus for meter-controlled dispensingVideo gamesSecure communicationMachine instruction
Secure communications are provided in a gaming system environment using a hash manager to hash information, store the hashed information to a database, and to retrieve and unhash the information when needed. Information may include a user identifier, pass phrase and / or package of executable gaming machine instructions. This approach may provide security without requiring a user to reenter log in information (e.g., user identifier and / or pass phrase) during a login or security session.
Owner:LNW GAMING INC
Software analyzer
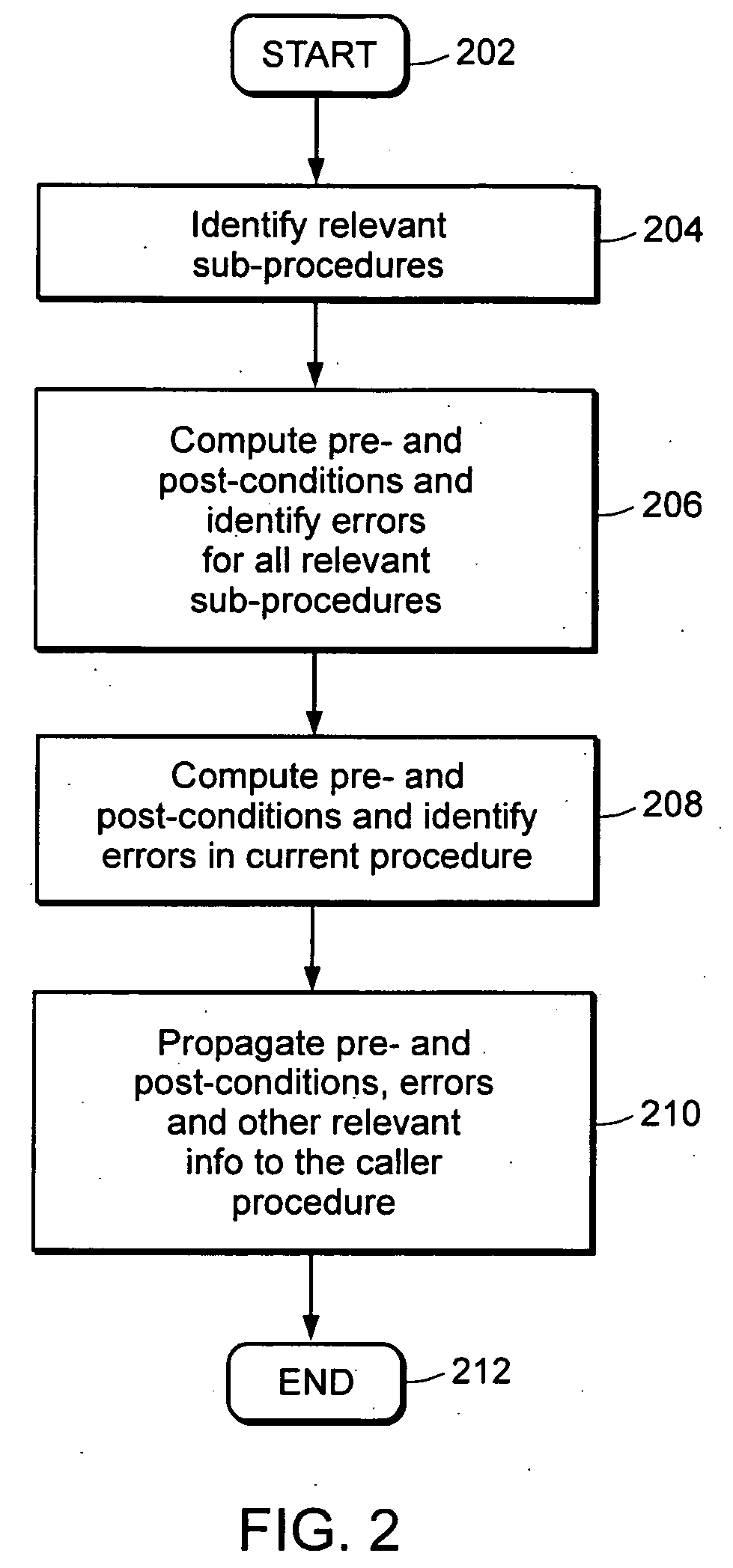
InactiveUS20060150160A1Minimizing chanceHigh precisionError detection/correctionSpecific program execution arrangementsValue setMachine instruction
It is possible to identify pre- and post-conditions on a set of machine instructions by determining and analyzing possible value sets for variables and expressions. Stepping forward and backward through the set of instructions and tracking value sets at all points of reference allows for the value sets to be maximally restricted, which, in turn, gives an indication of allowed domains for different variables. These domains can be used to derive pre- and post-conditions for the set of instructions.
Owner:SOFCHECK
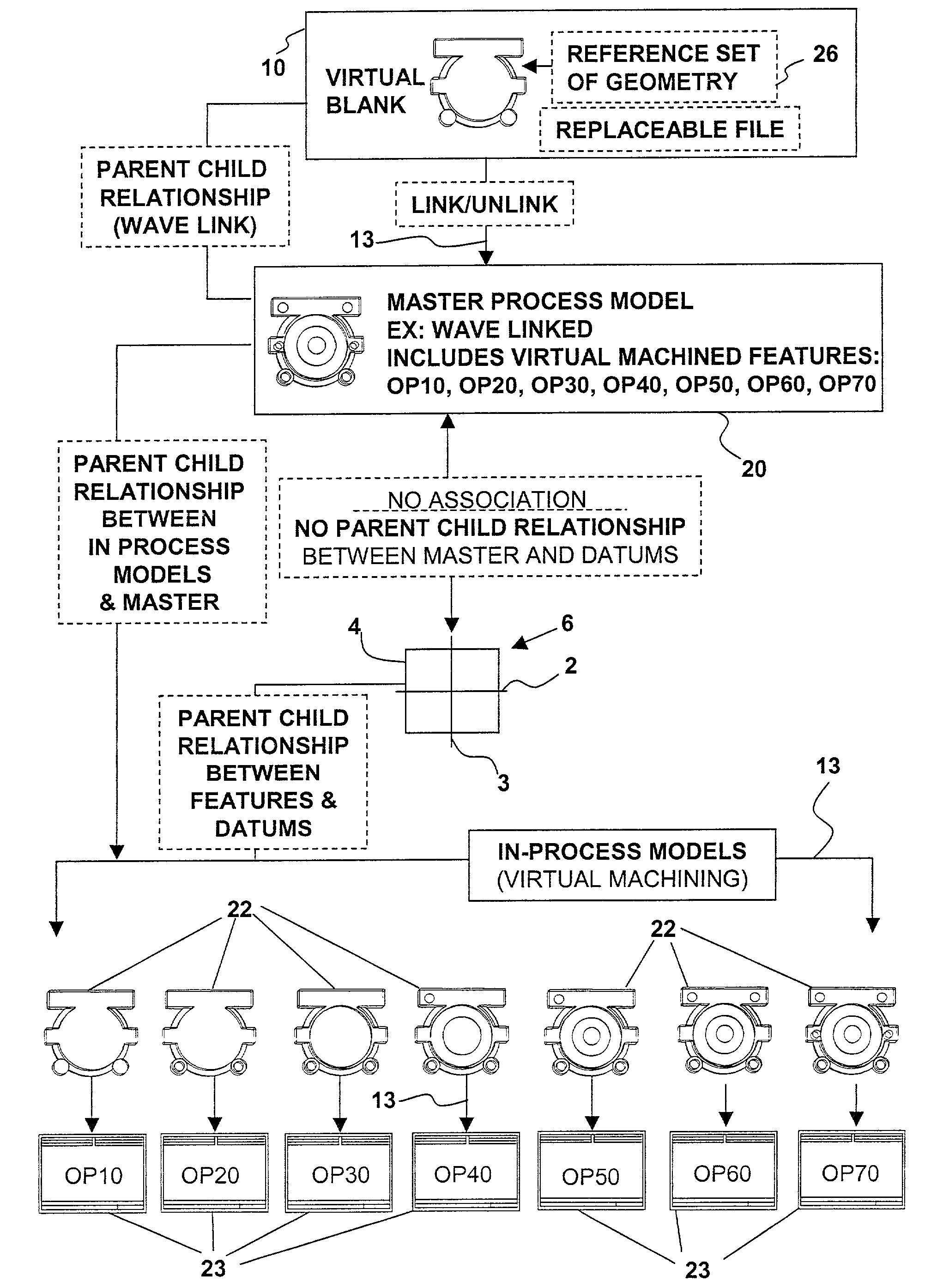
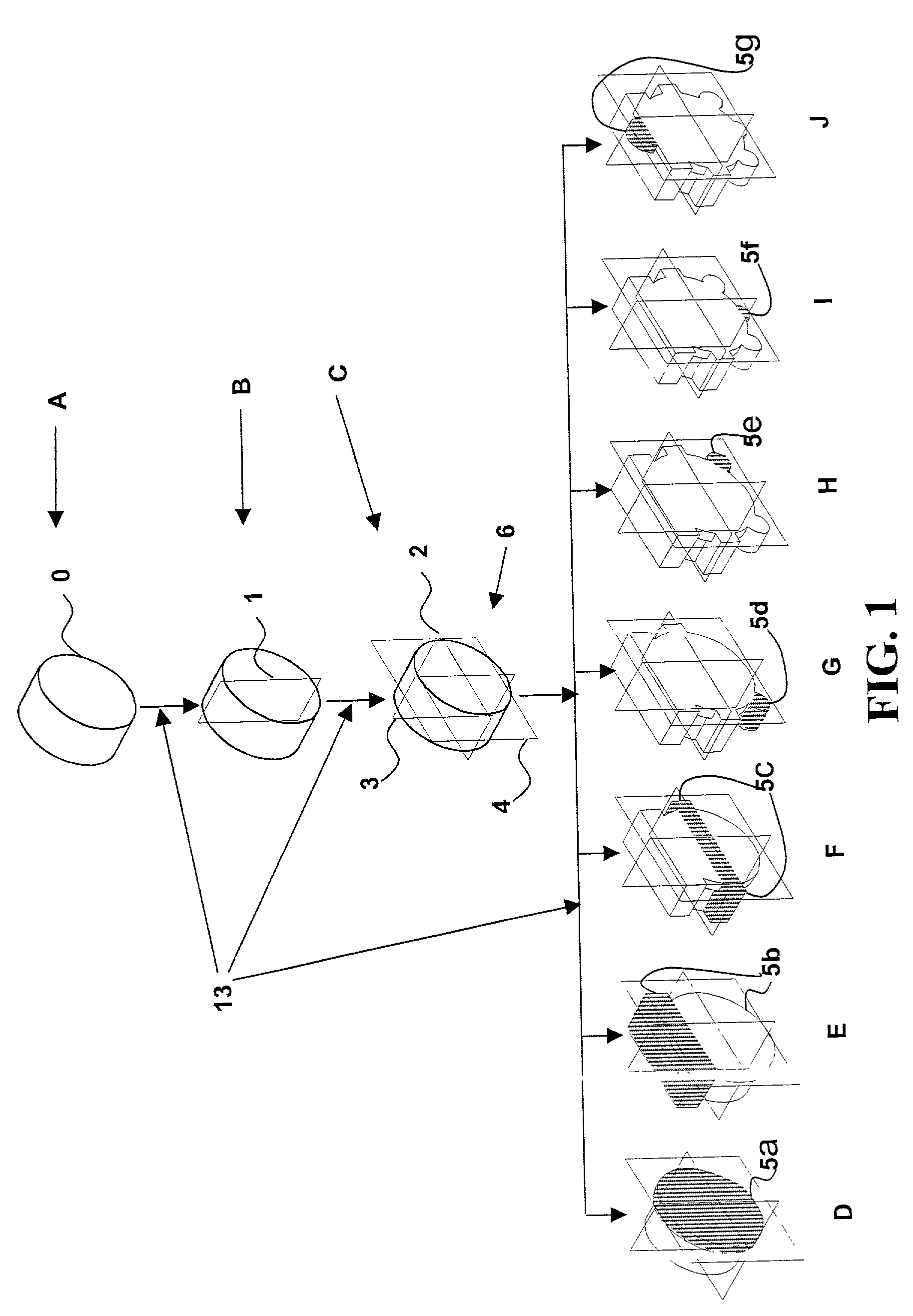
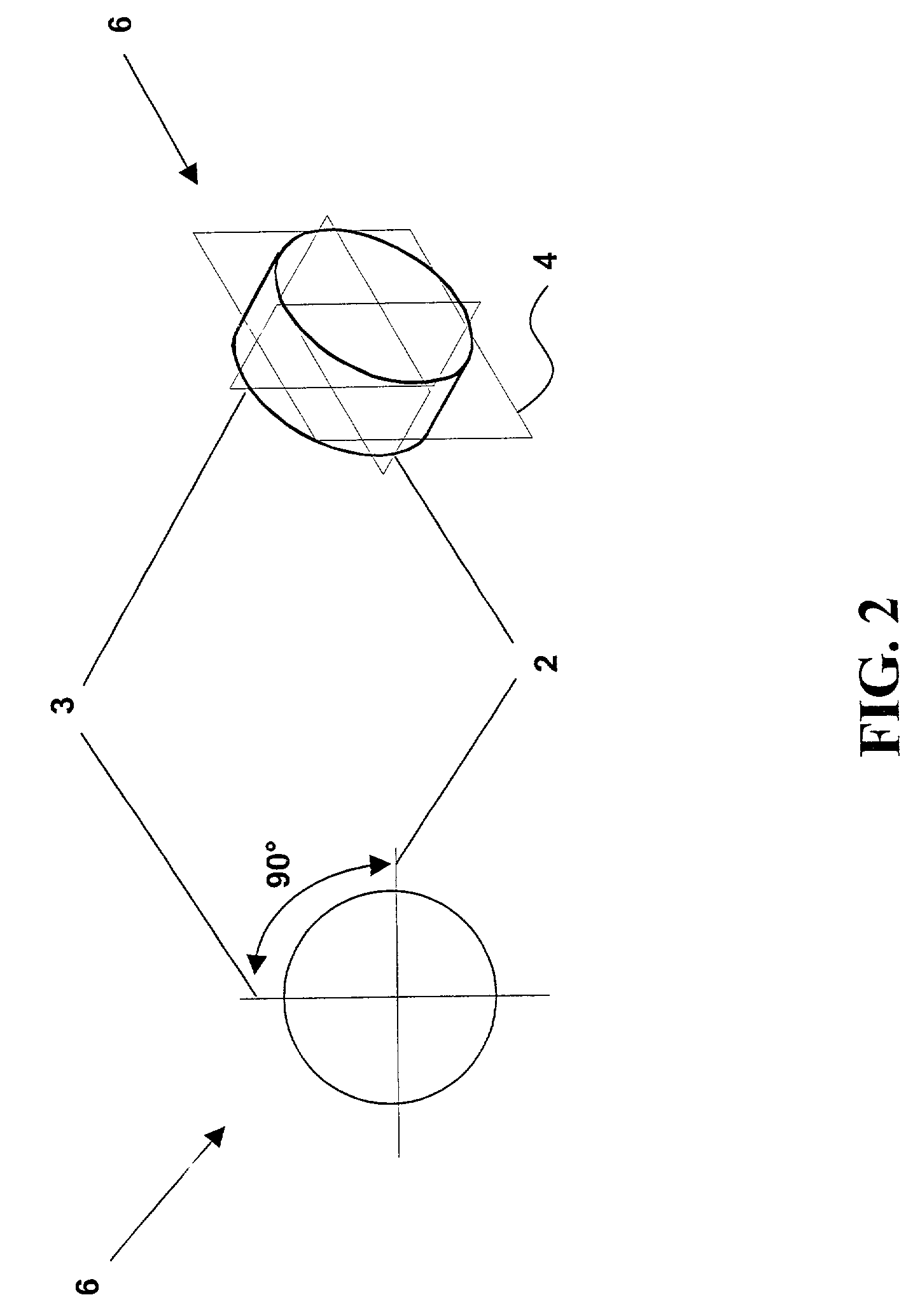
Horizontally-structured CAD/CAM modeling for virtual concurrent product and process design
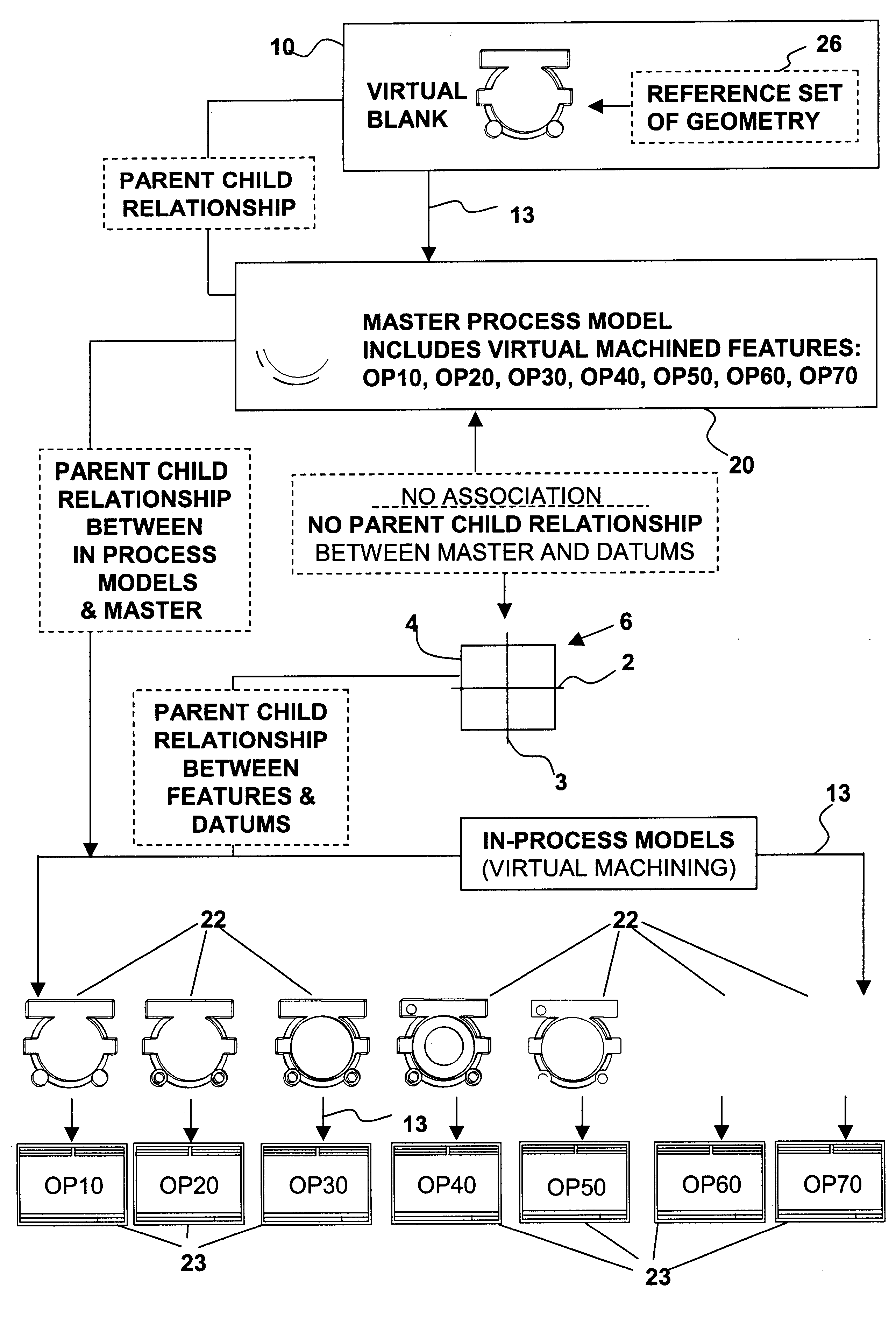
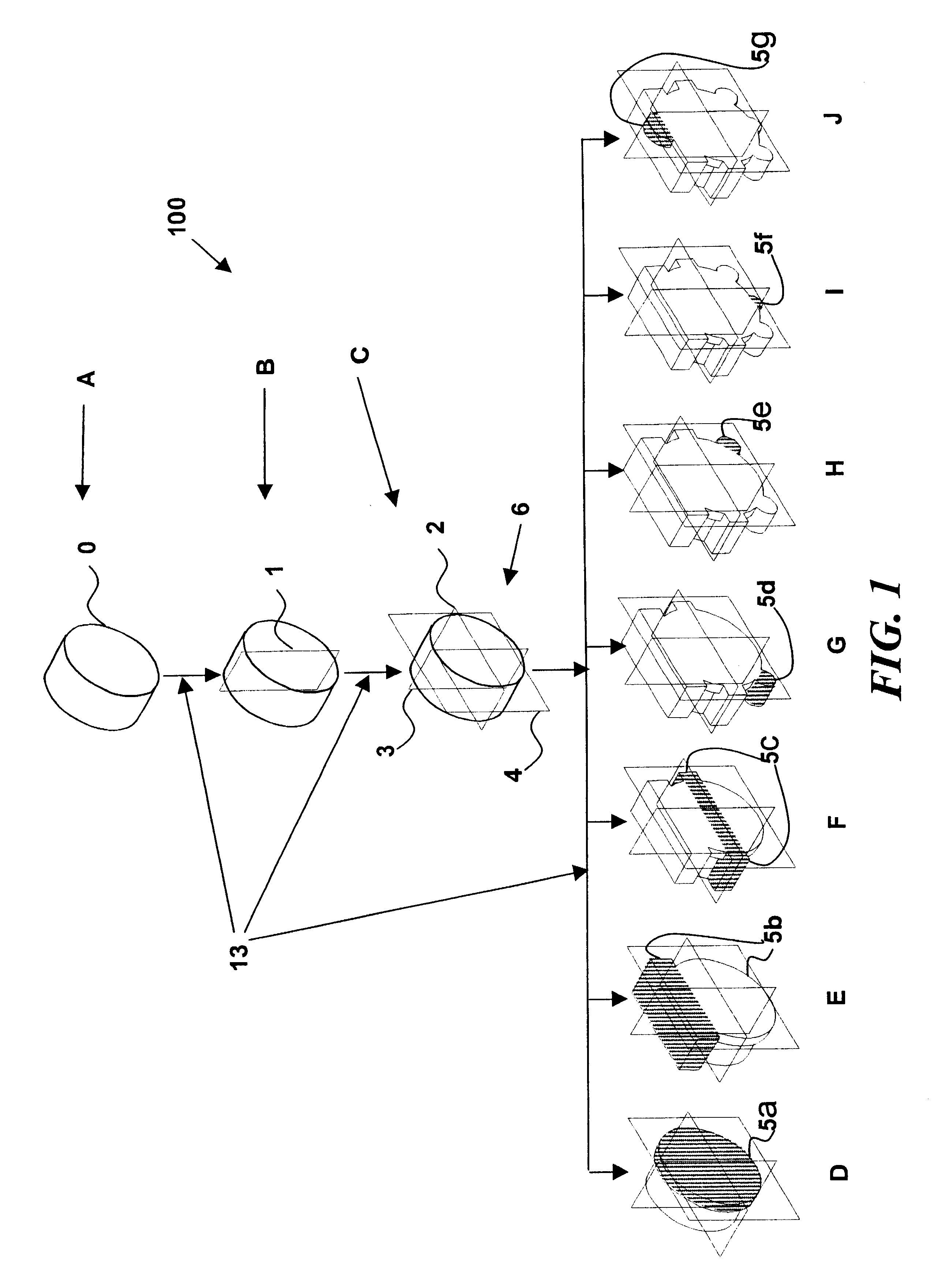
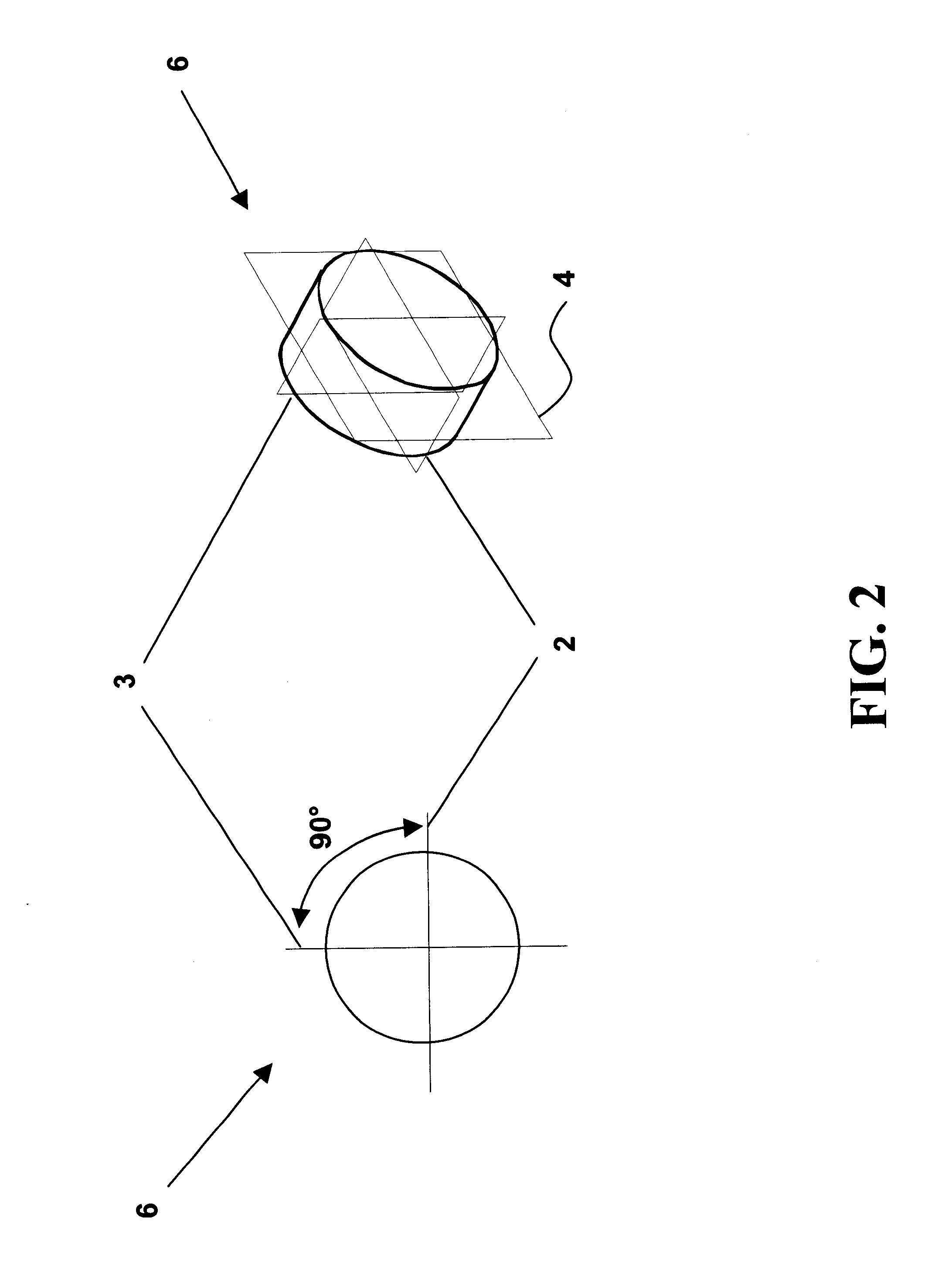
Disclosed herein is a method of horizontally structured CAD / CAM modeling and manufacturing for concurrent product and process design, comprising: selecting a blank for machining into an actual part establishing a coordinate system; and creating a master product and process concurrent model comprising: a virtual blank corresponding to the blank; a manufacturing feature; virtual machining of the manufacturing feature into the virtual blank; where the manufacturing feature exhibits an associative relationship with the coordinate system. The method also includes generating a product drawing of the actual part; and generating machining instructions to create the actual part by machining the manufacturing feature into the blank. Also disclosed herein is a horizontally structured CAD / CAM model for concurrent product and manufacturing processes comprising: a blank for machining into an actual part; a coordinate system; and a master product and process concurrent model comprising: a virtual blank corresponding to the blank; a manufacturing feature; the manufacturing feature virtual machined into the virtual blank; and the manufacturing feature exhibiting an associative relationship with the coordinate system. Further disclosed is a storage medium encoded with a machine-readable computer program code for horizontally structured CAD / CAM modeling. The storage medium including instructions for causing a computer to implement the method of horizontally structured CAD / CAM modeling and manufacturing for concurrent product and process design. Additionally disclosed is a computer data signal for horizontally structured CAD / CAM modeling. The computer data signal comprising code configured to cause a processor to implement a method of horizontally structured CAD / CAM modeling and manufacturing for concurrent product and process design.
Owner:STEERING SOLUTIONS IP HLDG +1
High speed virtual machine and compiler
InactiveUS20030191792A1Multiprogramming arrangementsConcurrent instruction executionData setProcessor register
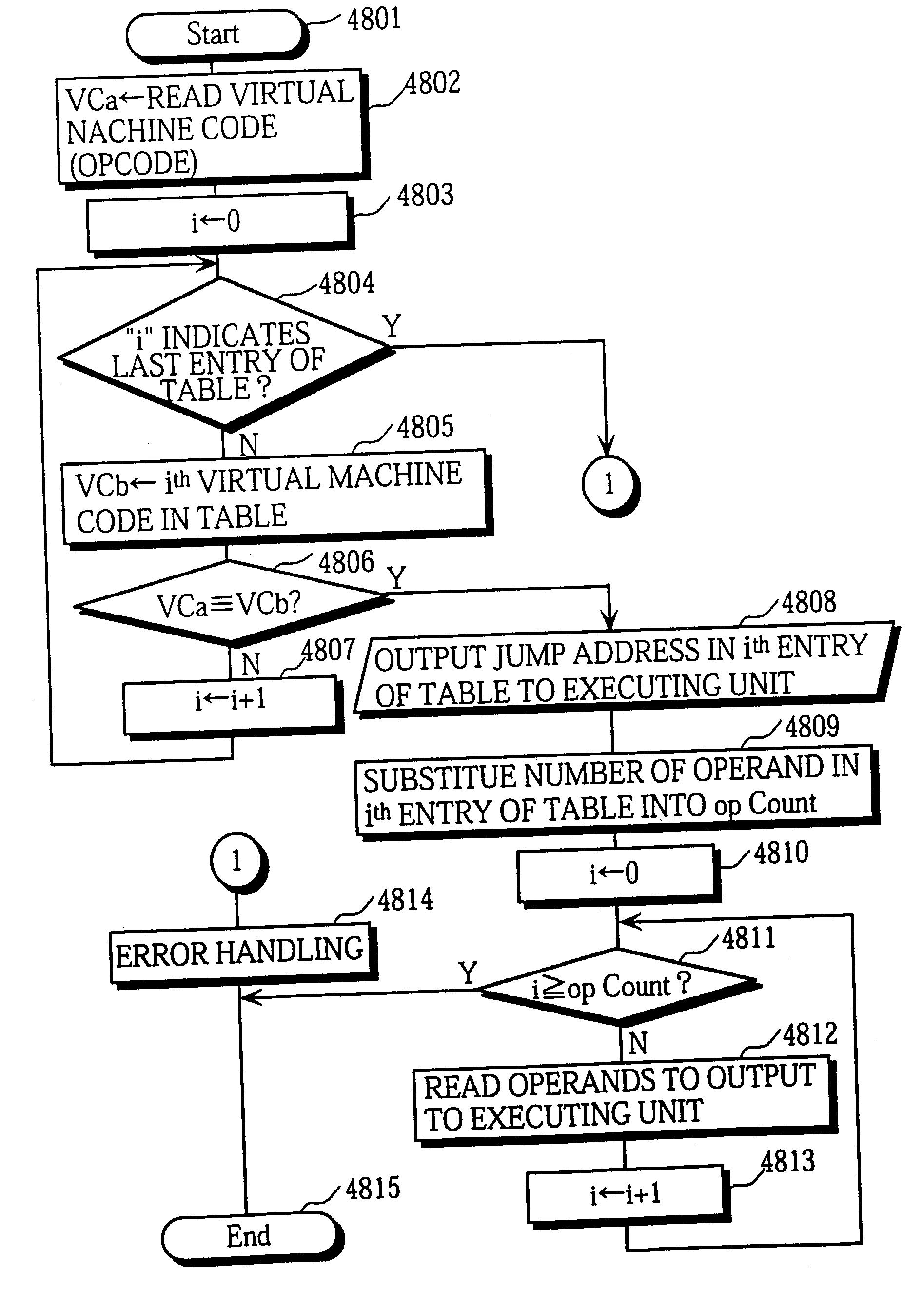
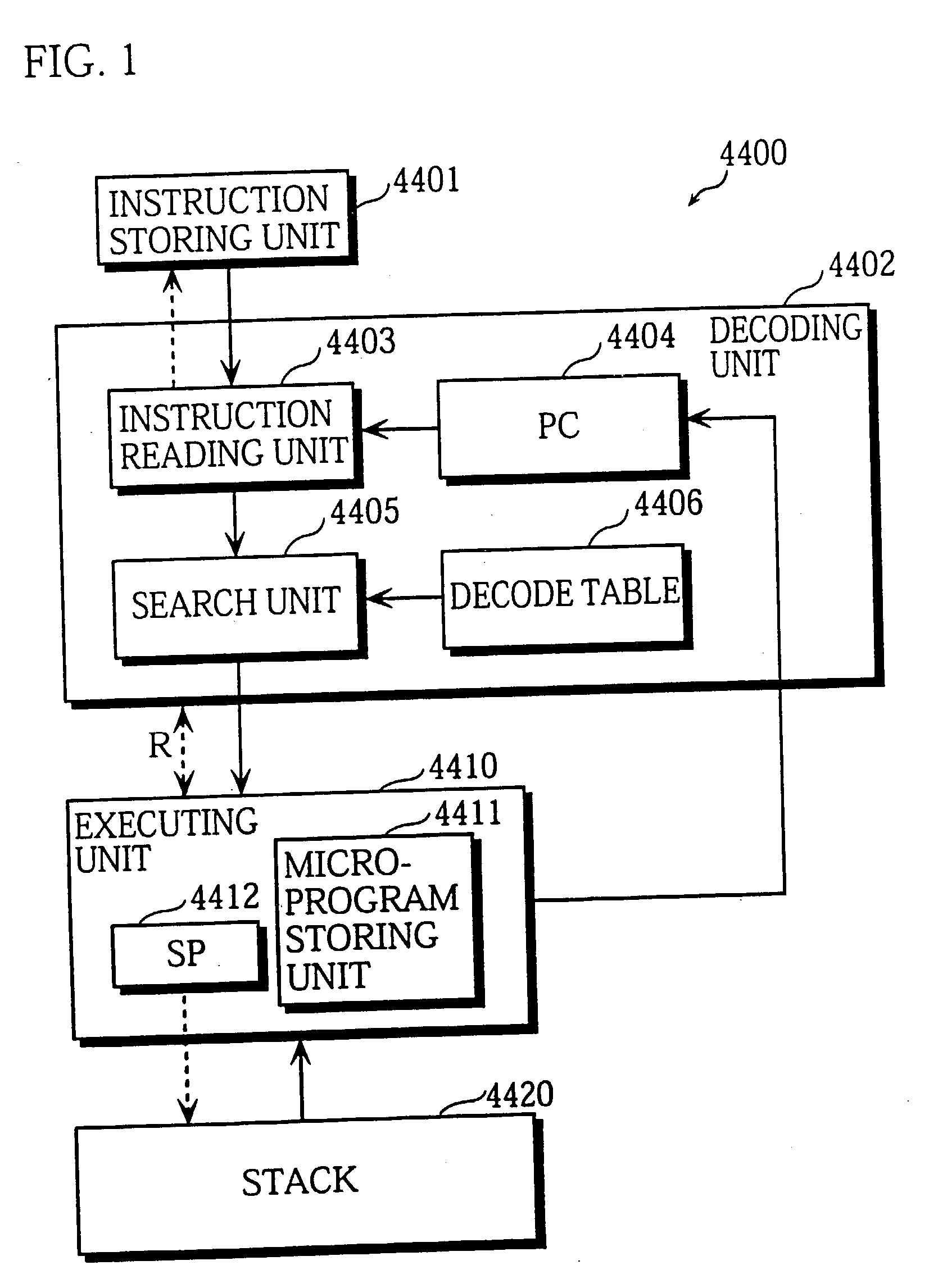
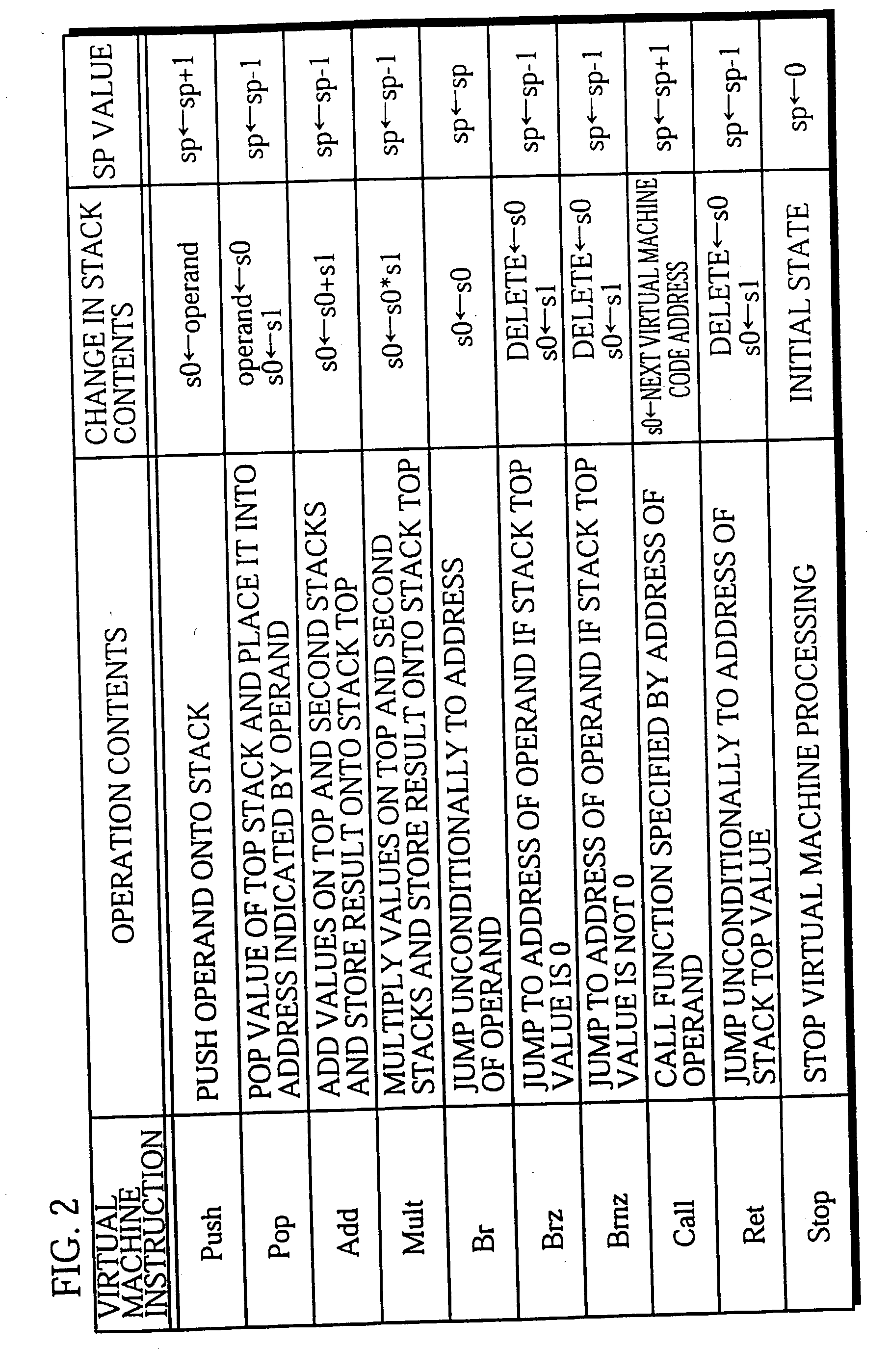
A virtual machine with a stack architecture includes: a stack 120 whose top level (TOS) and the second level from the top (SOS) are mapped to registers of a real machine 201; an instruction storing unit 102 for storing a virtual machine instruction sequence to be executed; next instruction information storing unit 101 for storing a plurality of sets of next instruction information that are each associated with a different virtual machine instruction in the virtual machine instruction sequence, the set of next instruction information for a given virtual machine instruction indicating a change in a number of sets of data stored in the stack 120 due to execution of a virtual machine instruction executed after the given virtual machine instruction; a decoding unit 103 for decoding a virtual machine instruction and an associated set of next instruction information after reading them from the instruction storing unit 102 and the next instruction information storing unit 101; and an executing unit 110 for executing the decoded virtual machine instruction and performing a stack handling in. the stack 120 in advance for a virtual machine instruction that is to be executed next based on the set of next instruction information.
Owner:PANASONIC CORP
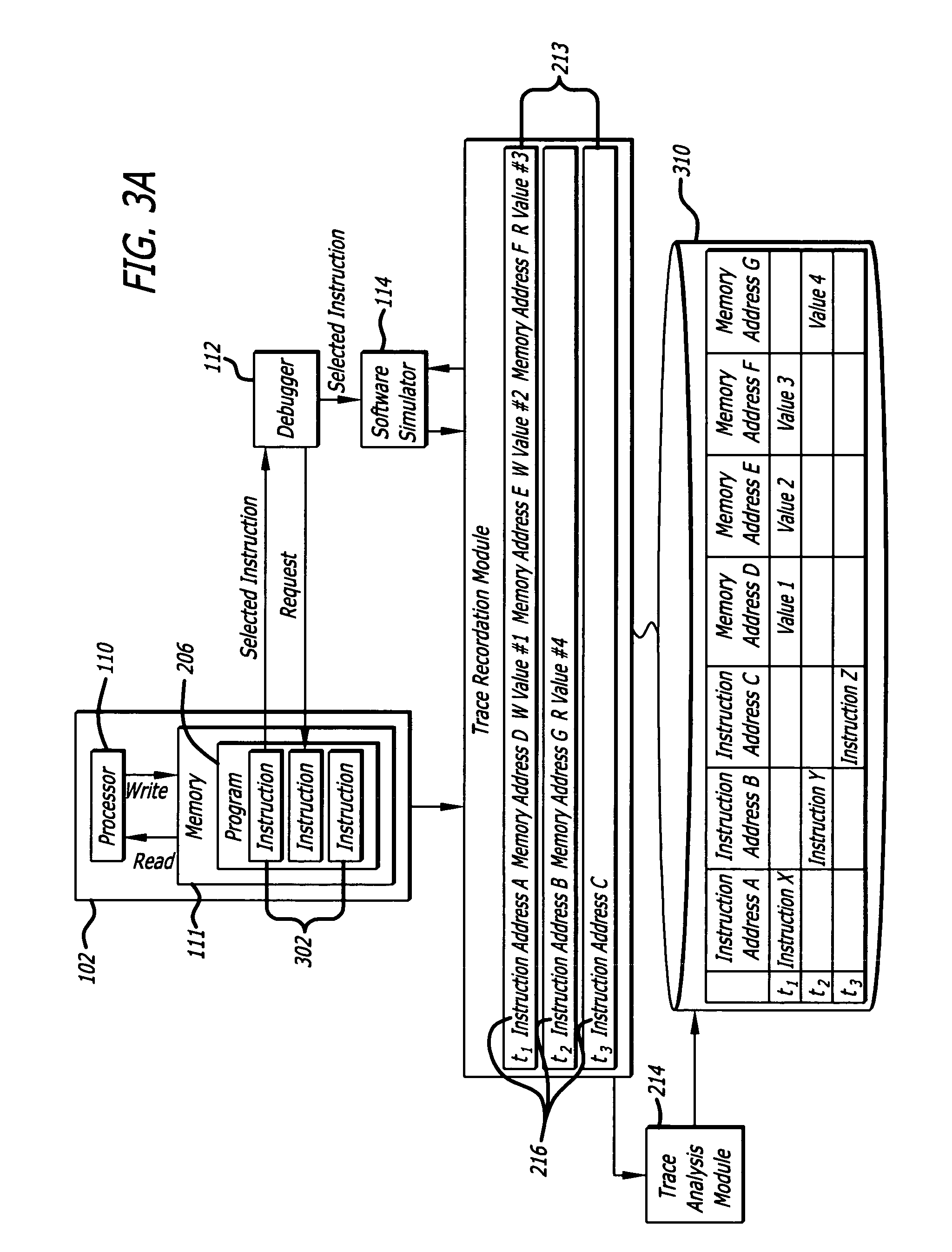
Backward post-execution software debugger
A method finds an error in a computer program. A plurality of execution breakpoints are set in the computer program. A portion of the execution of the computer program is simulated as recorded in the trace data in the reverse order until one a plurality of conditions is met, wherein one of the plurality of conditions is an attempt to execute a machine instruction associated with one of the plurality of execution breakpoints.
Owner:GREEN HILLS SOFTWARE
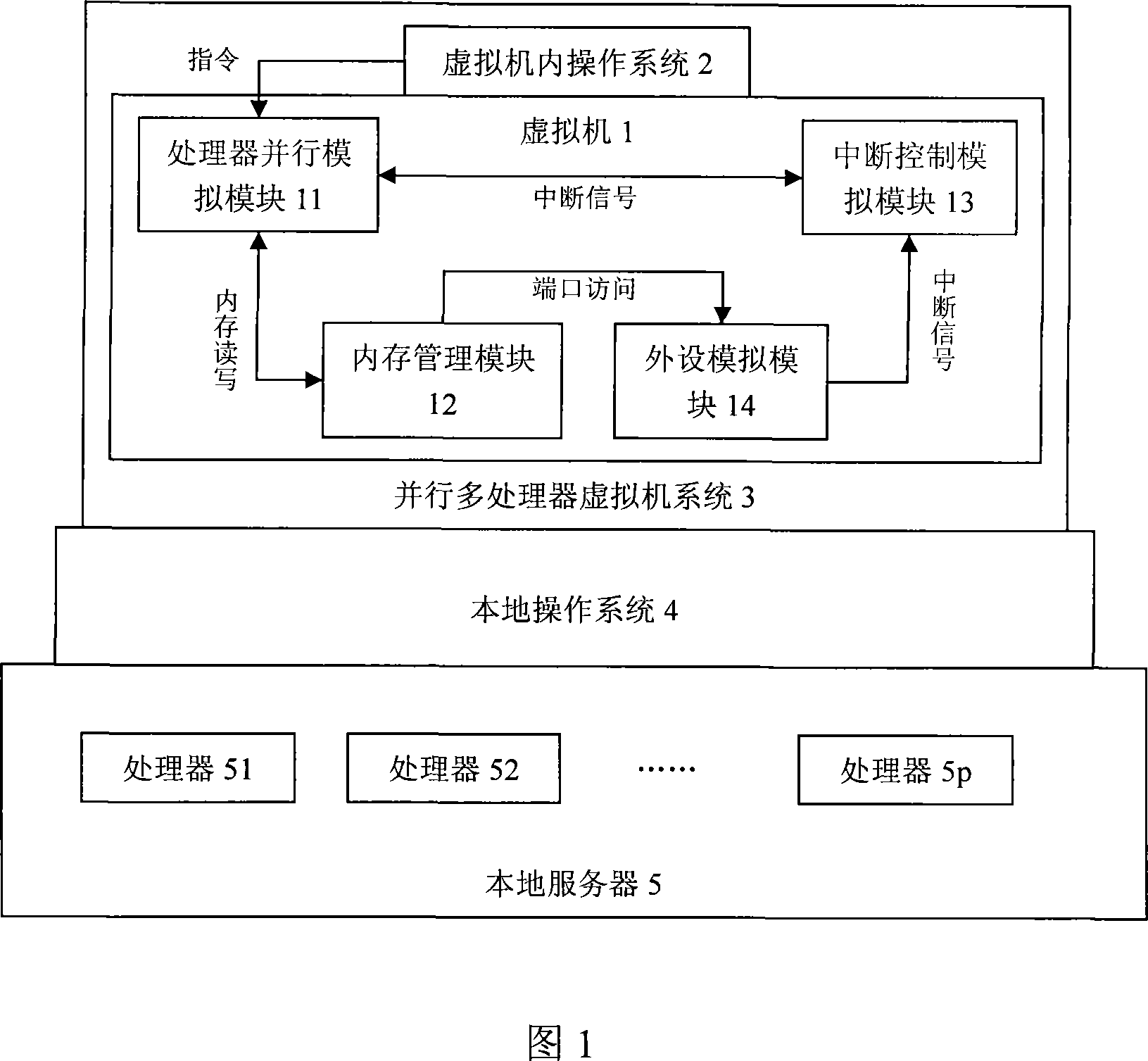
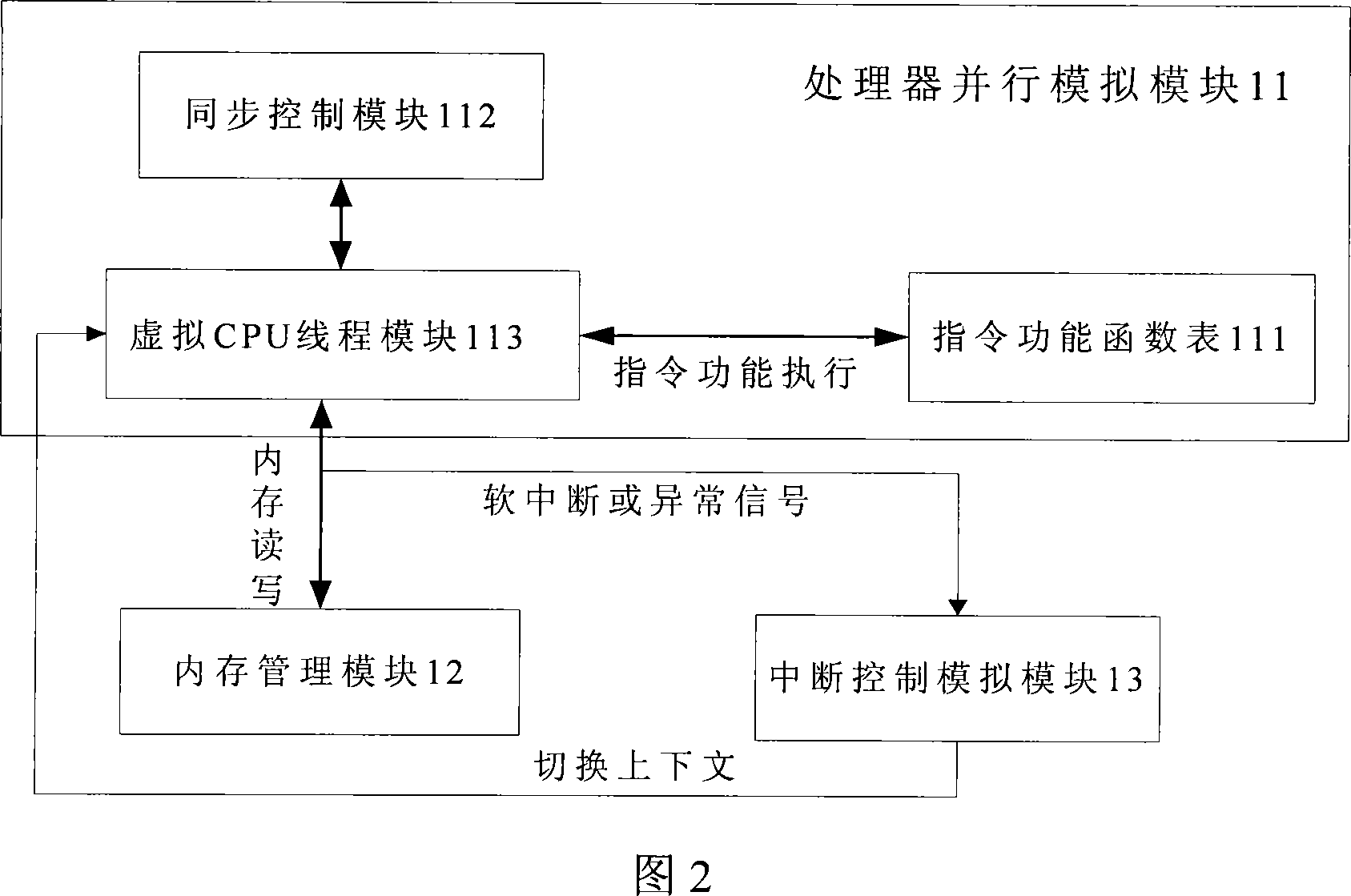
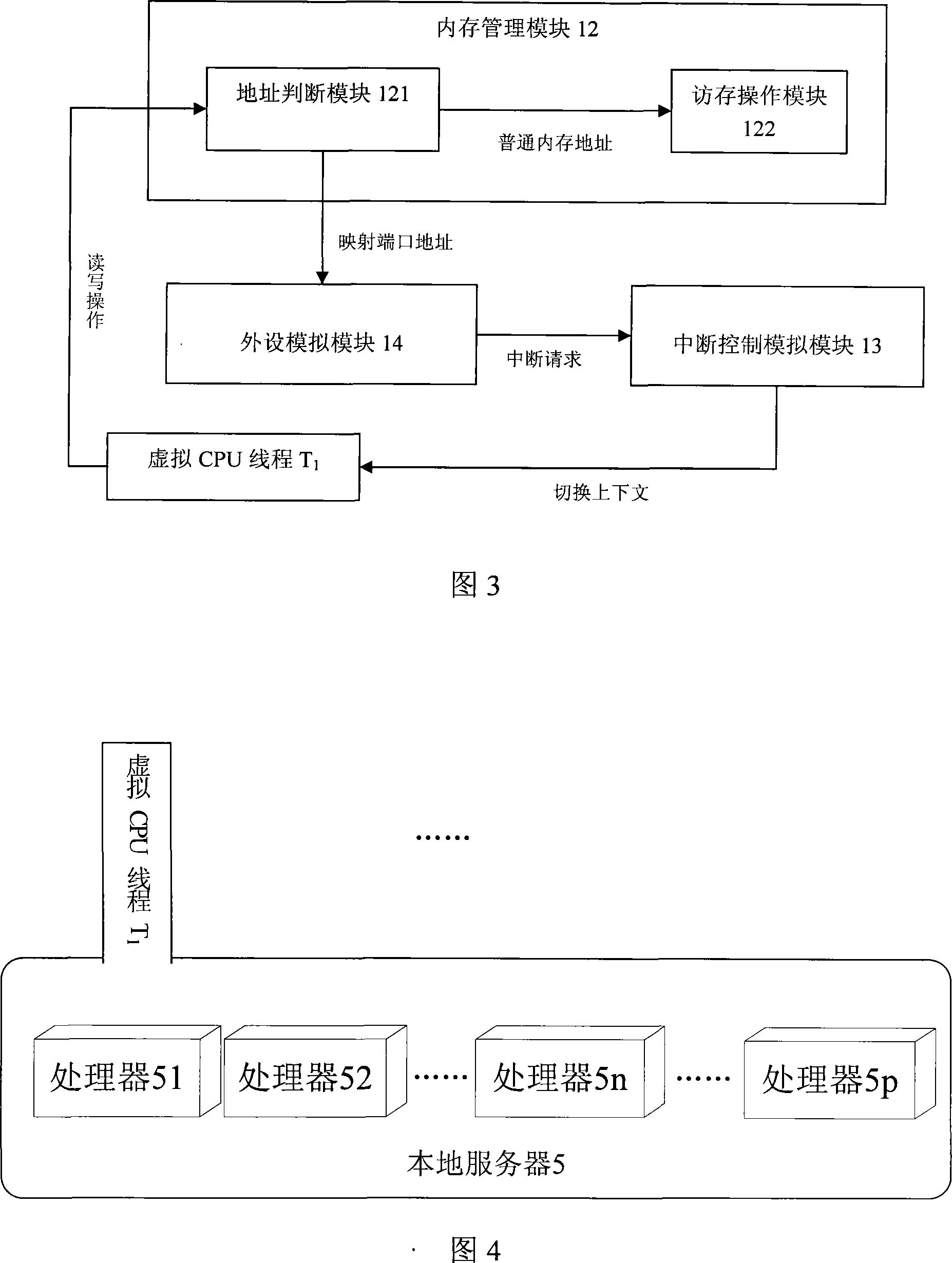
Paralleling multi-processor virtual machine system
InactiveCN101183315AMake the most of processing resourcesIncrease workloadMultiprogramming arrangementsSoftware simulation/interpretation/emulationOperational systemMulti processor
The invention discloses a concurrent multiprocessor virtual machine system supporting CPU simultaneous execution, which comprises a virtual machine and an operating system running on the virtual machine. The virtual machine system can simulate not less than one virtual processor, which comprises a processor concurrent simulation module, a memory management module, an interrupt controlling simulation module and a peripheral simulation module; the machine instruction of the operating system is transferred to the processor simulation module through the memory management module of the virtual machine; the processor simulation module can simulate multiple virtual processors used for executing the operating system instruction translated by an instruction translation module and make the processors concurrently execute; the invention also provides a synchronous and access control algorithm in the concurrent execution process; and the peripheral simulation module and the processor simulation module are coordinated by the interrupt controlling simulation module. The invention has the advantages of suitability for simulating a concurrent execution environment of complete simulating hardware on an SMP server or a multi-core server.
Owner:HUAZHONG UNIV OF SCI & TECH
Automated engraving of a customized jewelry item
ActiveUS7069108B2Reduce the amount requiredCost effectiveSpecial data processing applicationsEngravingIcon designPersonalization
A method for manufacturing a ring (i.e. class, championship, or affiliation) begins by receiving order data specifying a series of personalization elements, such as the addition of text and icon designs. A geometric model for each personalization item is constructed. To assemble text panels, the operating system provides font geometry for a desired TrueType font. Then a set of splines are created from the font geometry and are then tessellated to generate polyline sets of data, which are then spaced and mapped between two boundary curves. The personalization elements are then projected onto one of the model's 3D surfaces. A set of machining instructions for a milling machine is generated by obtaining a set of machining pattern strategies, generating a set of curves, projecting the toolpath onto the surface of the ring to calculate the 3D toolpath, and rotating it to a desired angle.
Owner:JOSTENS INC
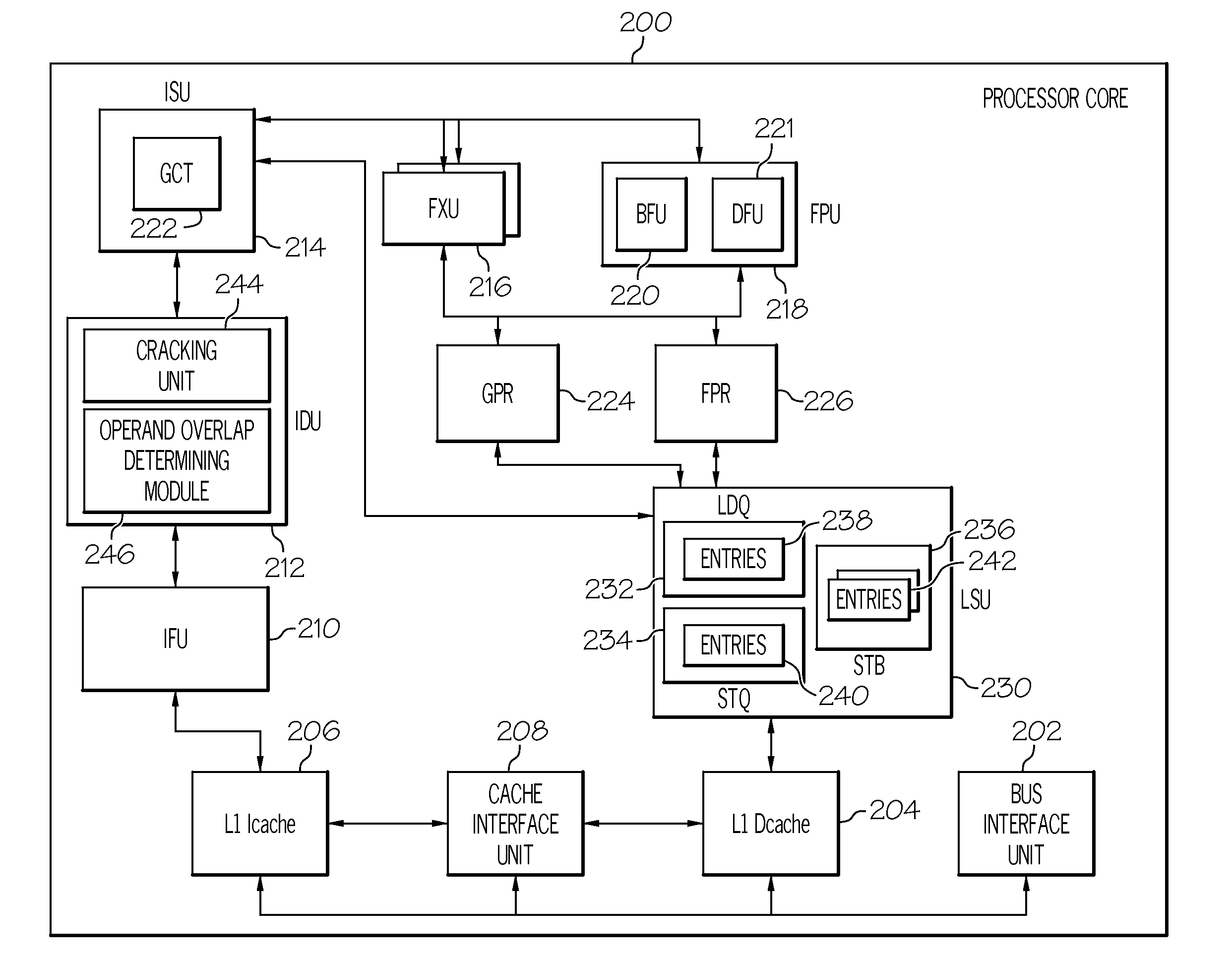
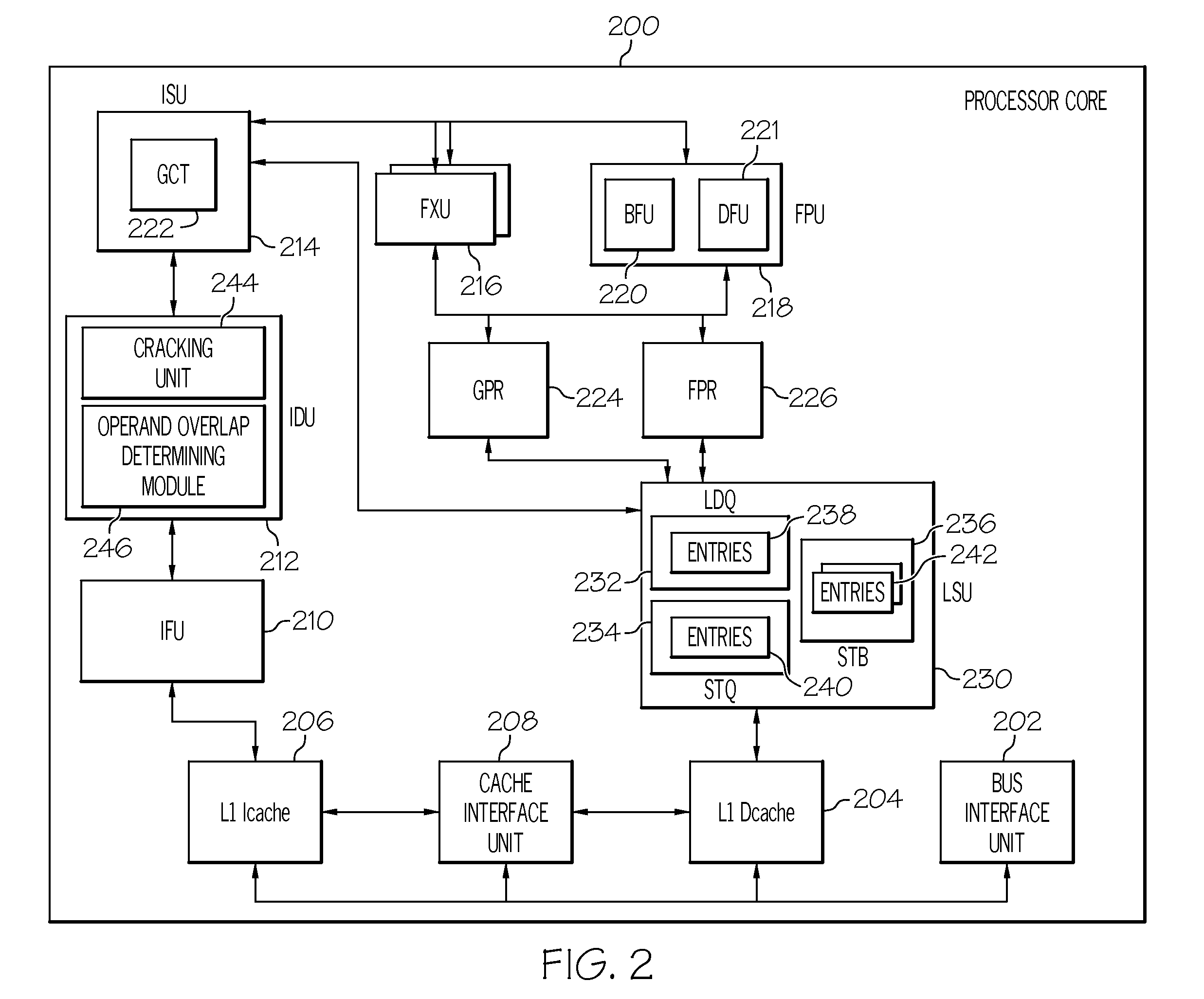
Cracking destructively overlapping operands in variable length instructions
ActiveUS20110276764A1Instruction analysisMemory adressing/allocation/relocationInformation processingMachine instruction
A method, information processing system, and computer program product manage computer executable instructions. At least one machine instruction for execution is received. The at least one machine instruction is analyzed. The machine instruction is identified as a predefined instruction for storing a variable length first operand in a memory location. Responsive to this identification and based on fields of the machine instruction, a relative location of a variable length second operand of the instruction with location of the first operand is determined. Responsive to the relative location having the predefined relationship, a first cracking operation is performed. The first cracking operation cracks the instruction into a first set of micro-ops (Uops) to be executed in parallel. The second set of Uops is for storing a first plurality of first blocks in the first operand. Each of said first block to be stored are identical. The first set Uops are executed.
Owner:IBM CORP
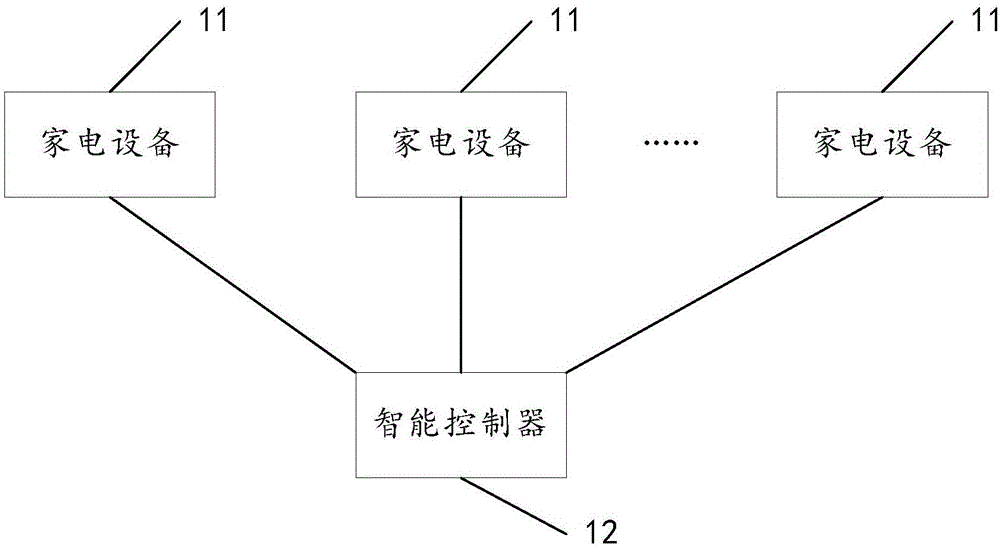
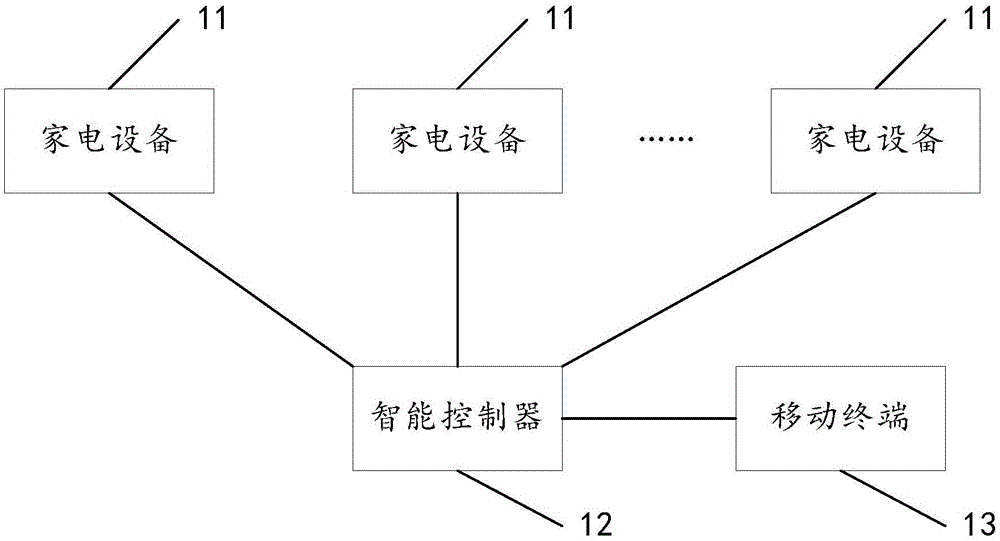
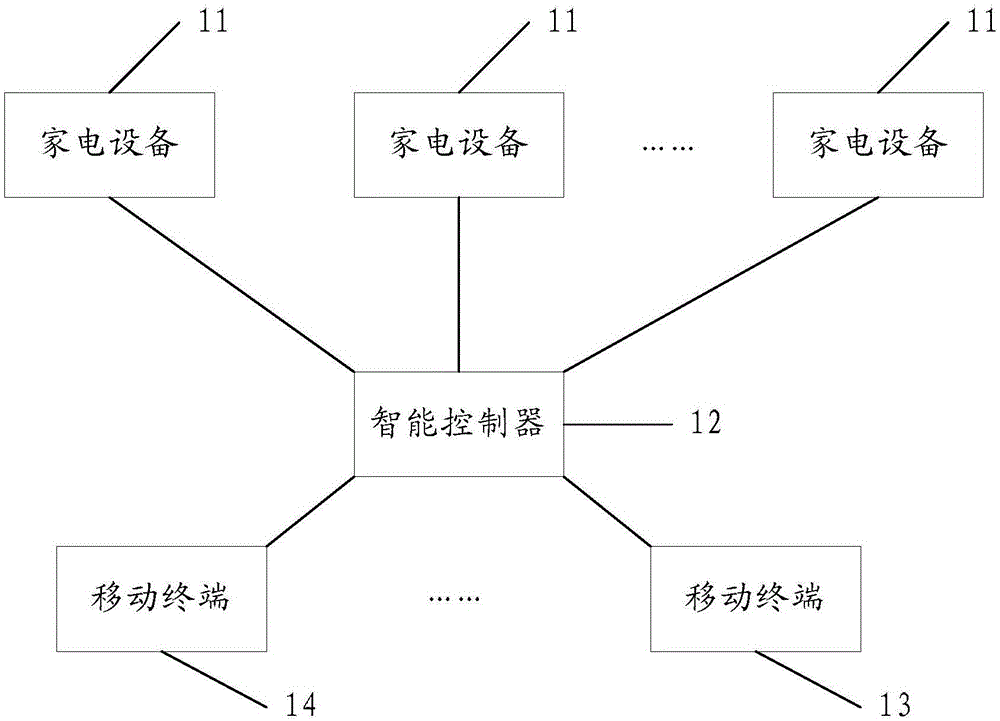
Smart home control system and control method
ActiveCN105159122AUnified control methodUnified operationComputer controlProgramme total factory controlControl systemShortest distance
An embodiment of the invention discloses a smart home control system and a control method, relates to the field of internet of things, and is to solve the problems that a user cannot control a plurality of different types of household appliances through a unified manner, and the operation process is complex. The concrete scheme is that the smart home control system comprises at least one household appliance and an intelligent controller connected with the household appliance through a short-distance communication module. The intelligent controller is used for obtaining control information comprising identification of the household appliance and a first control instruction, if capacity information indicates that the household appliance can execute a first working mode, and a first working parameter is within the range of working parameters corresponding to the first working mode and indicated by the capacity information, determining a first machine instruction corresponding to the first control instruction according to mapping relation, and sending the first machine instruction to the household appliance according to the identification of the household appliance; and the household appliance is used for receiving the first machine instruction sent by the intelligent controller, and executing the first machine instruction.
Owner:HISENSE
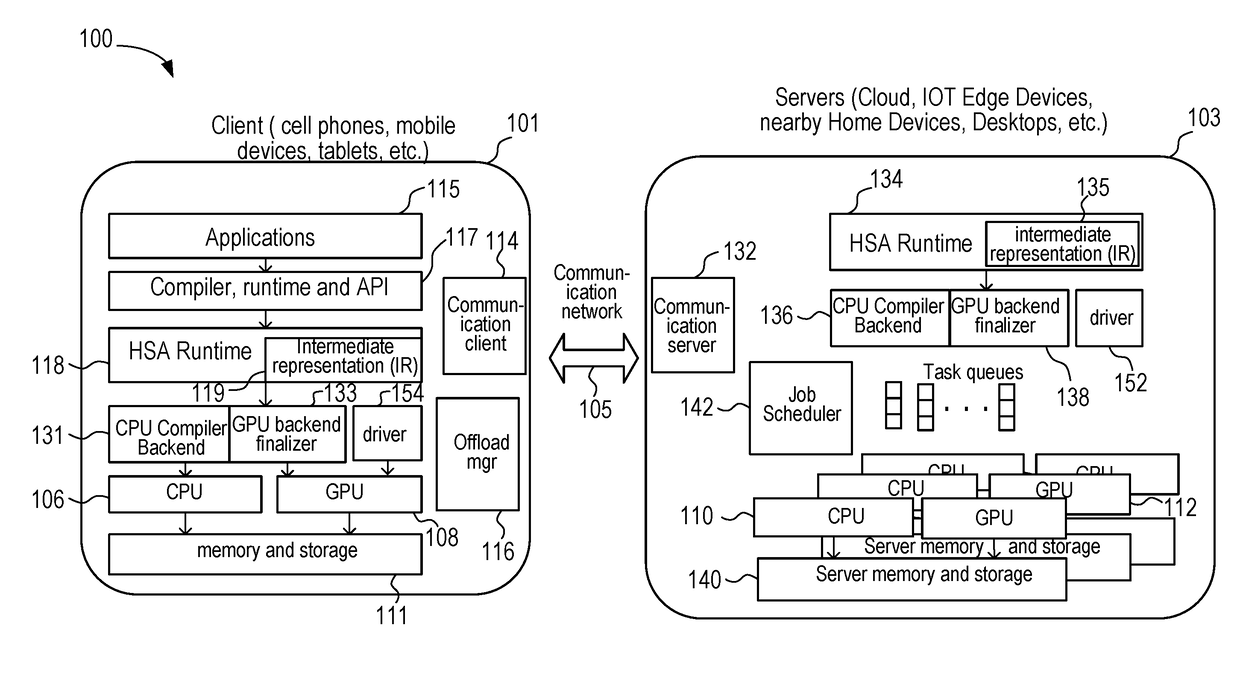
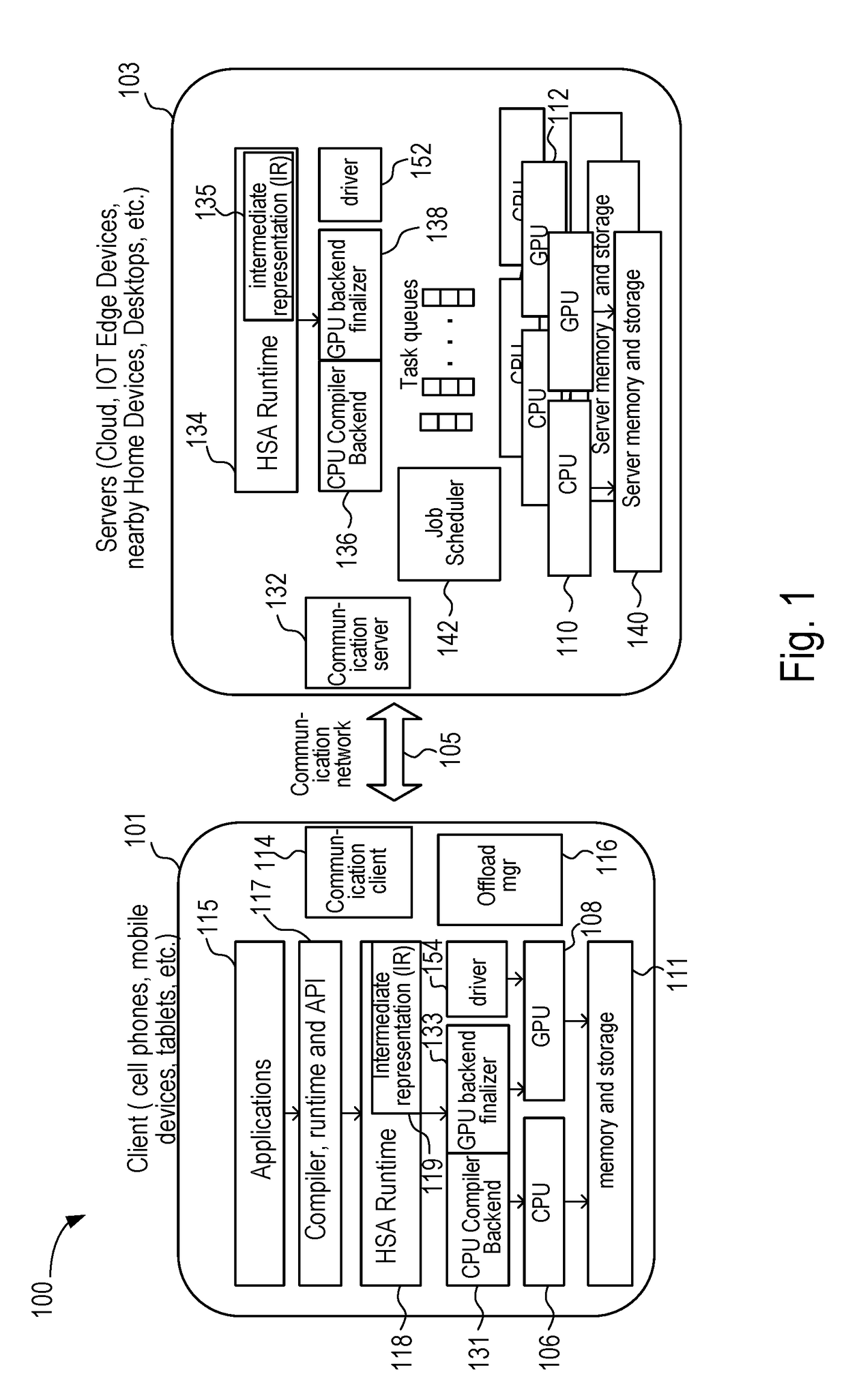
Offloading Execution of an Application by a Network Connected Device
A client device detects one or more servers to which an application can be offloaded. The client device receives information from the servers regarding their graphics processing unit (GPU) compute resources. The client device selects one of the servers to offload the application based on such factors as the GPU compute resources, other performance metrics, power, and bandwidth / latency / quality of the communication channel between the server and the client device. The client device sends host code and a GPU computation kernel in intermediate language format to the server. The server compiles the host code and GPU kernel code into suitable machine instruction set architecture code for execution on CPU(s) and GPU(s) of the server. Once the application execution is complete, the server returns the results of the execution to the client device.
Owner:ADVANCED MICRO DEVICES INC
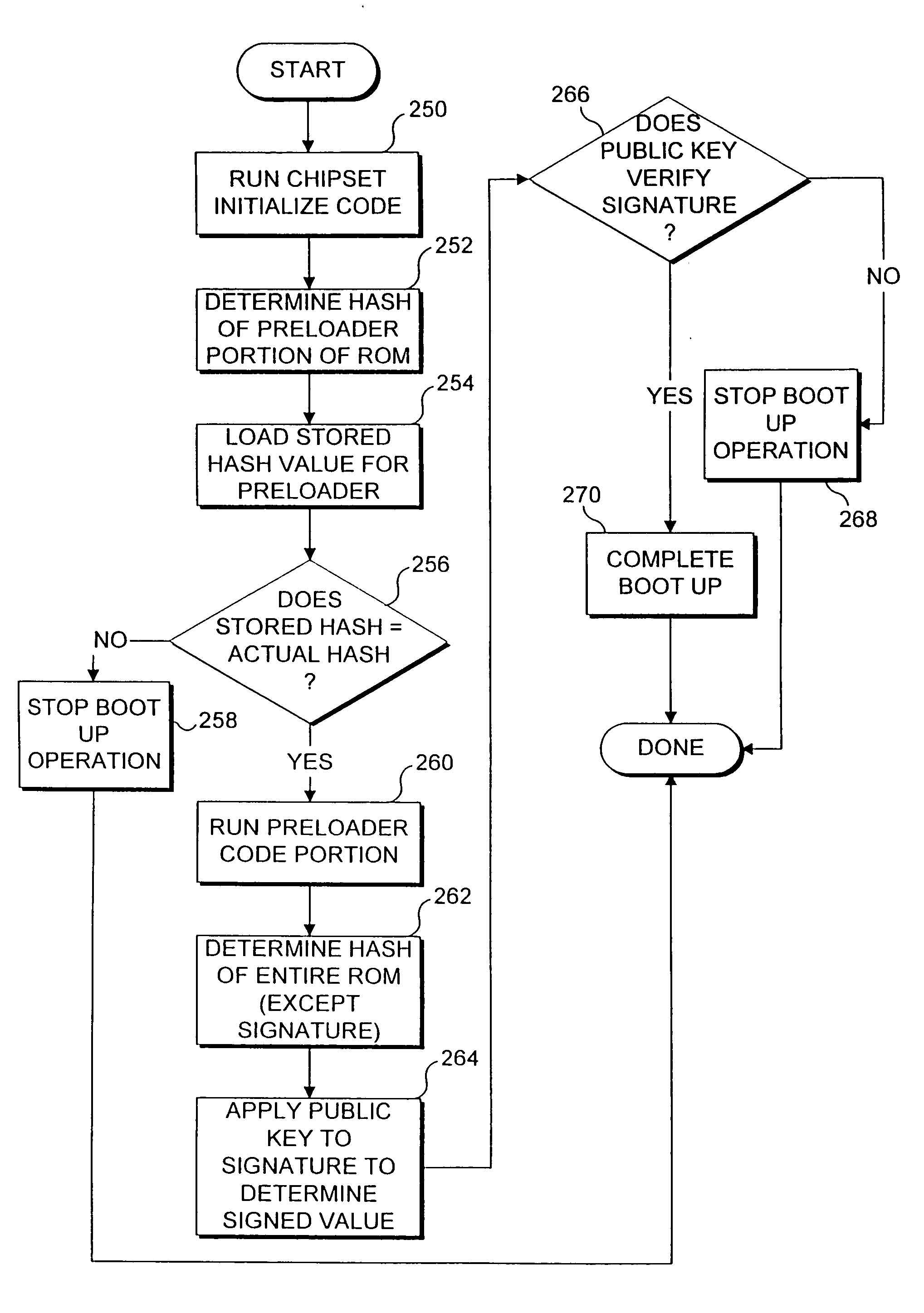
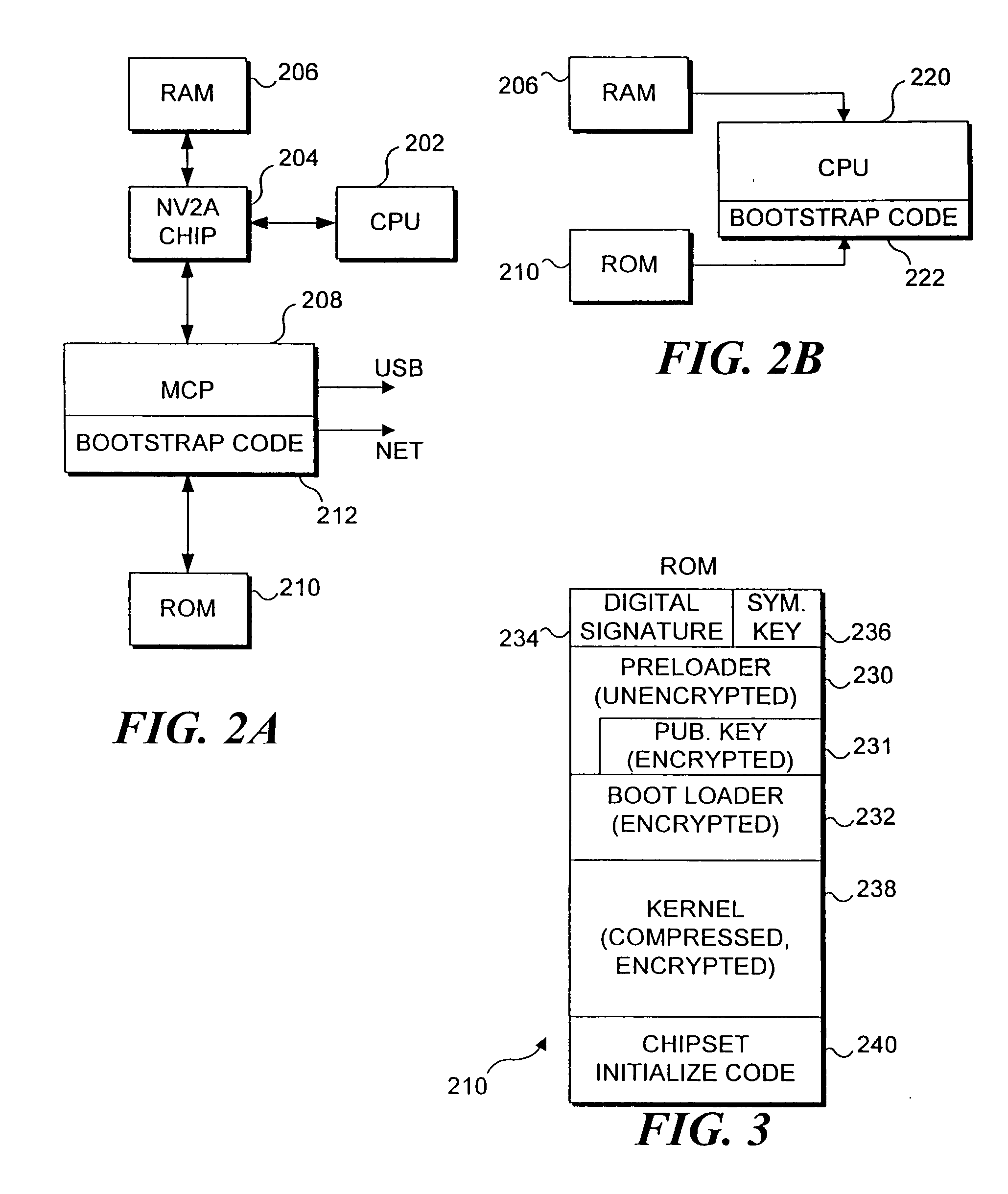
Use of hashing in a secure boot loader
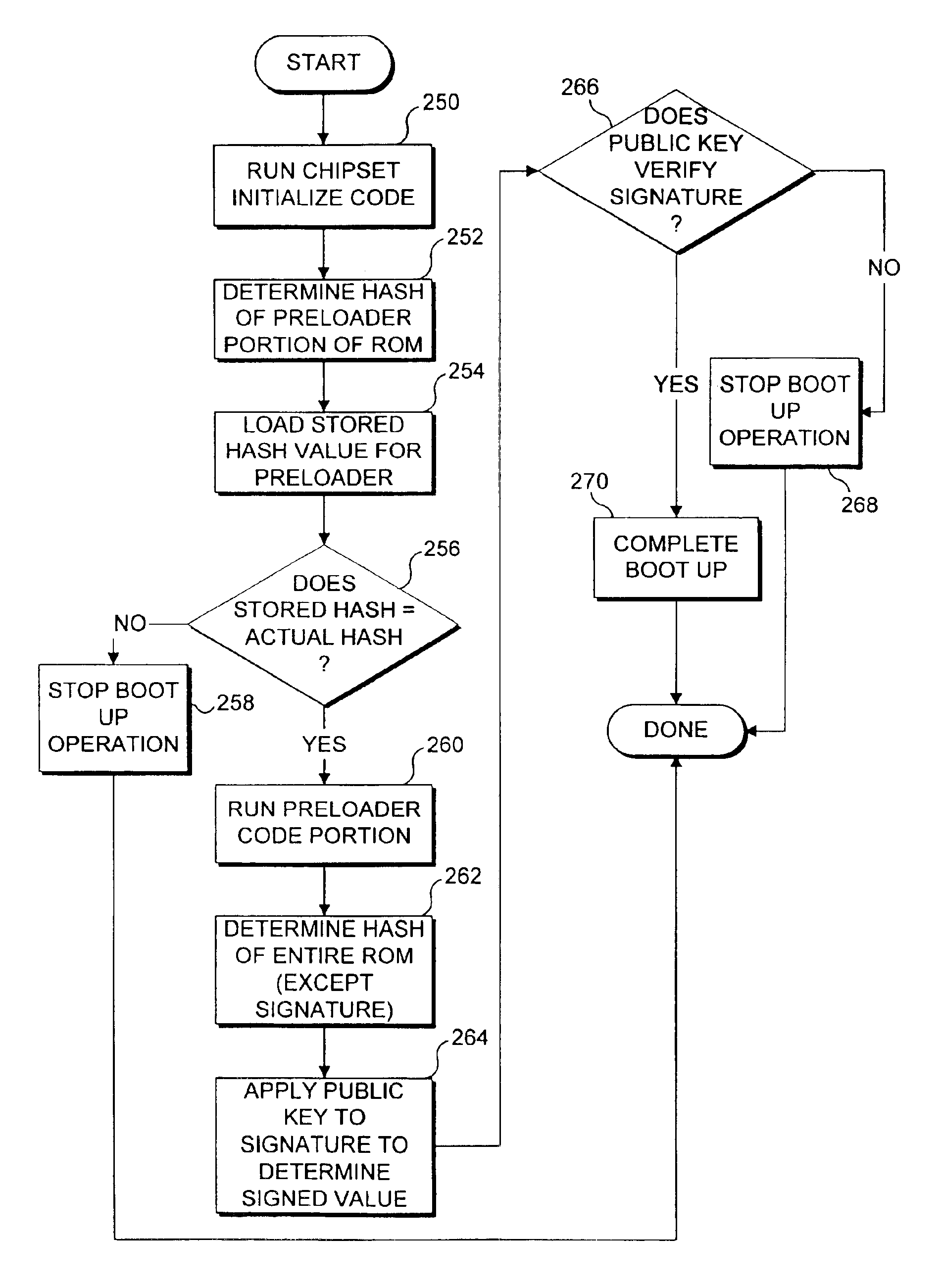
InactiveUS6907522B2Digital data processing detailsUser identity/authority verificationDigital signatureMachine instruction
Machine instructions comprising a bootstrap code are buried within a critical component of an electronic game console where they cannot readily be accessed or modified. A preloader portion in a read only memory (ROM) is hashed by the bootstrap code and the result is compared to an expected hash value maintained in the bootstrap code. Further verification of the boot-up process is carried out by the preloader, which hashes the code in ROM to obtain a hash value for the code. The result is verified against a digital signature value that defines an expected value for this hash. Failure to obtain any expected result terminates the boot-up process. Since the bootstrap code confirms the preloader, and the preloader confirms the remainder of the code in ROM, this technique is useful for ensuring that the code used for booting up the device has not been modified or replaced.
Owner:MICROSOFT TECH LICENSING LLC
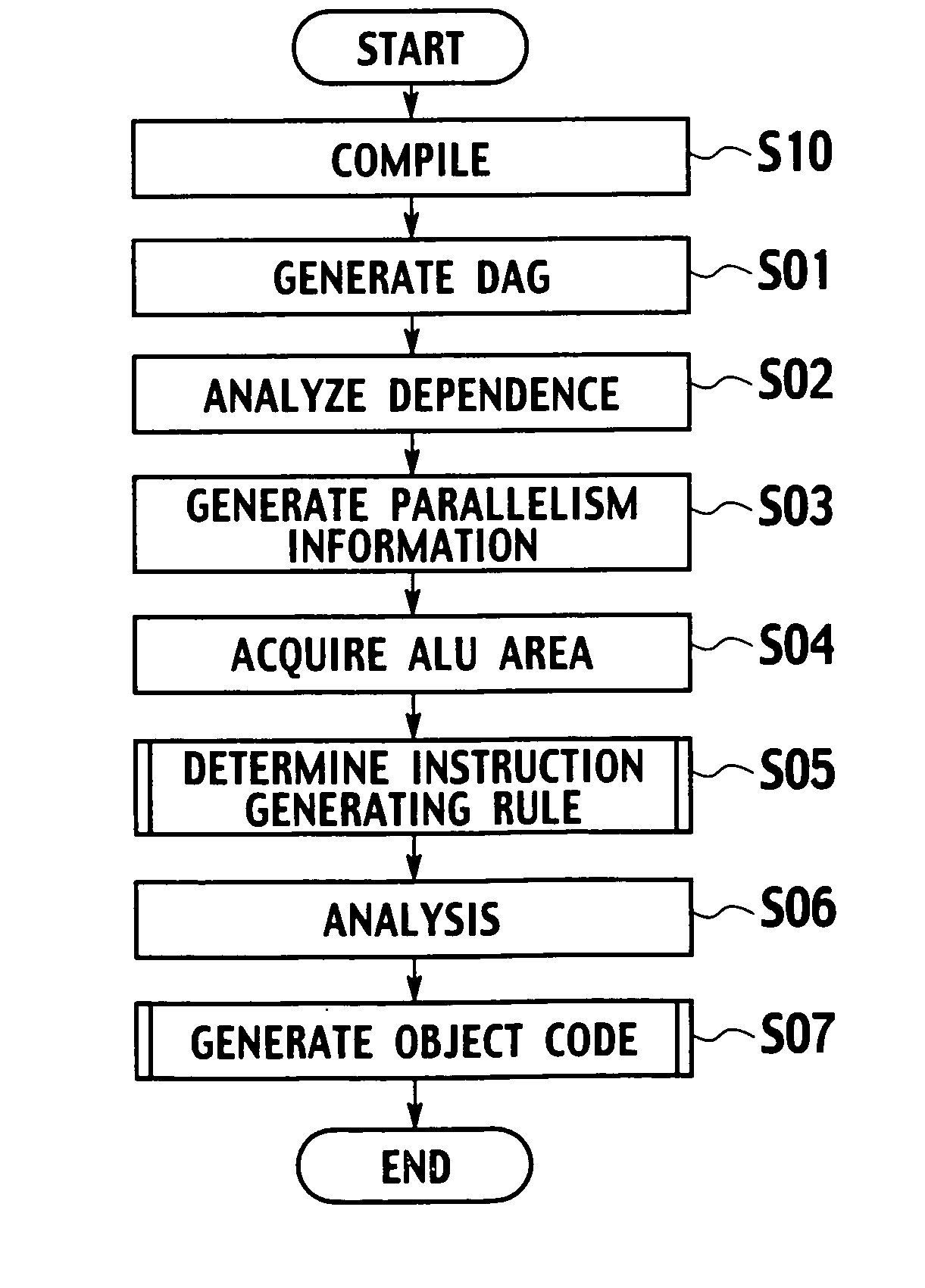
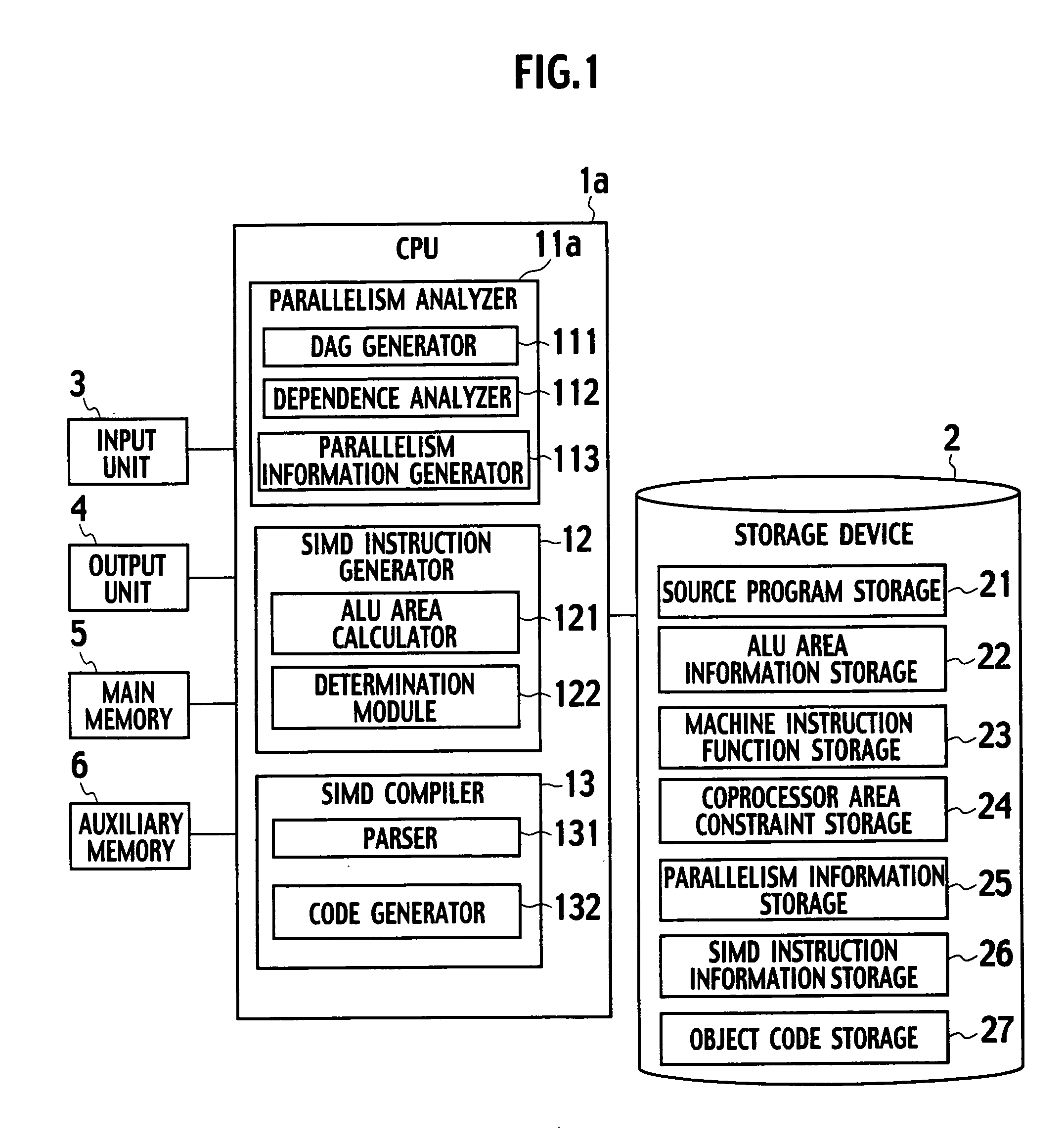
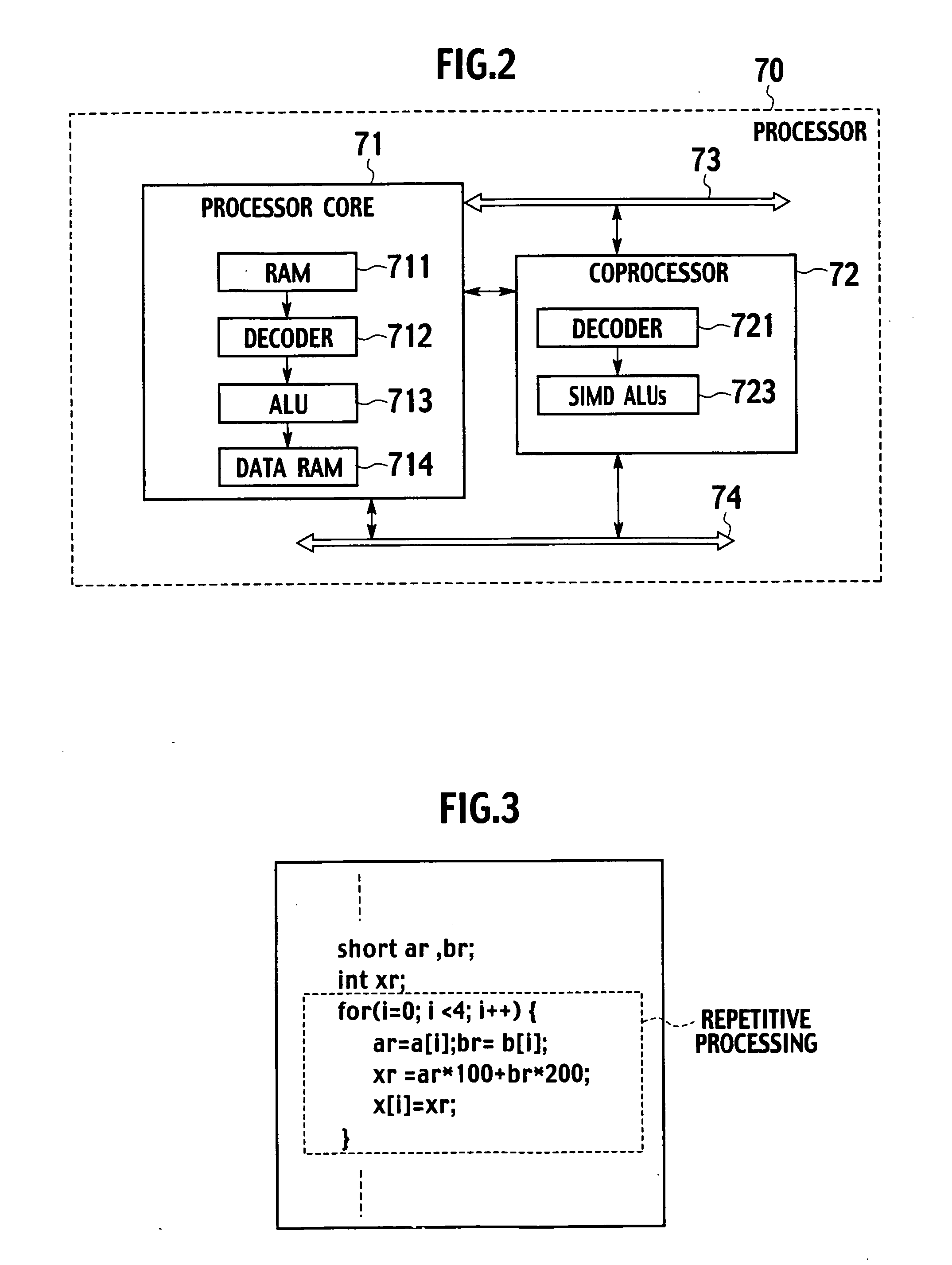
Instruction generator, method for generating instructions and computer program product that executes an application for an instruction generator
An instruction generator comprising a storage device configured to store a machine instruction function incorporating both an operation definition defining a program description in a source program targeted for substitution to a SIMD instruction, and the SIMD instruction. A parallelism analyzer is configured to analyze the source program so as to detect operators applicable to parallel execution, and to generate parallelism information indicating the set of operators applicable to parallel execution. A SIMD instruction generator is configured to perform a matching determination between an instruction generating rule for the SIMD instruction and the parallelism information, and to read the machine instruction function out of the storage device in accordance with a result of the matching determination.
Owner:KK TOSHIBA
Use of hashing in a secure boot loader
InactiveUS20050138270A1Computer security arrangementsProgram loading/initiatingDigital signatureMachine instruction
Owner:MICROSOFT TECH LICENSING LLC
Rounding operations in computer processor
InactiveUS6889242B1Improve execution speedImprove simplicityComputation using denominational number representationRight shiftMachine instruction
Various methods for performing rounding operations in a computer processor are described. A machine instruction sets the rounding mode, which is automatically applied to subsequent machine instructions. Using machine instructions to round results according to the selected rounding mode has several advantages over software-implemented rounding techniques, such as faster execution and concise code. A variety of rounding modes can be specified. Depending in part on the specified rounding mode and on the sign of the value to be rounded, a rounding term is added to the value to be rounded. Adding this rounding term ensures that the desired result is obtained. The value thus obtained is then right-shifted.
Owner:III HLDG 12 LLC
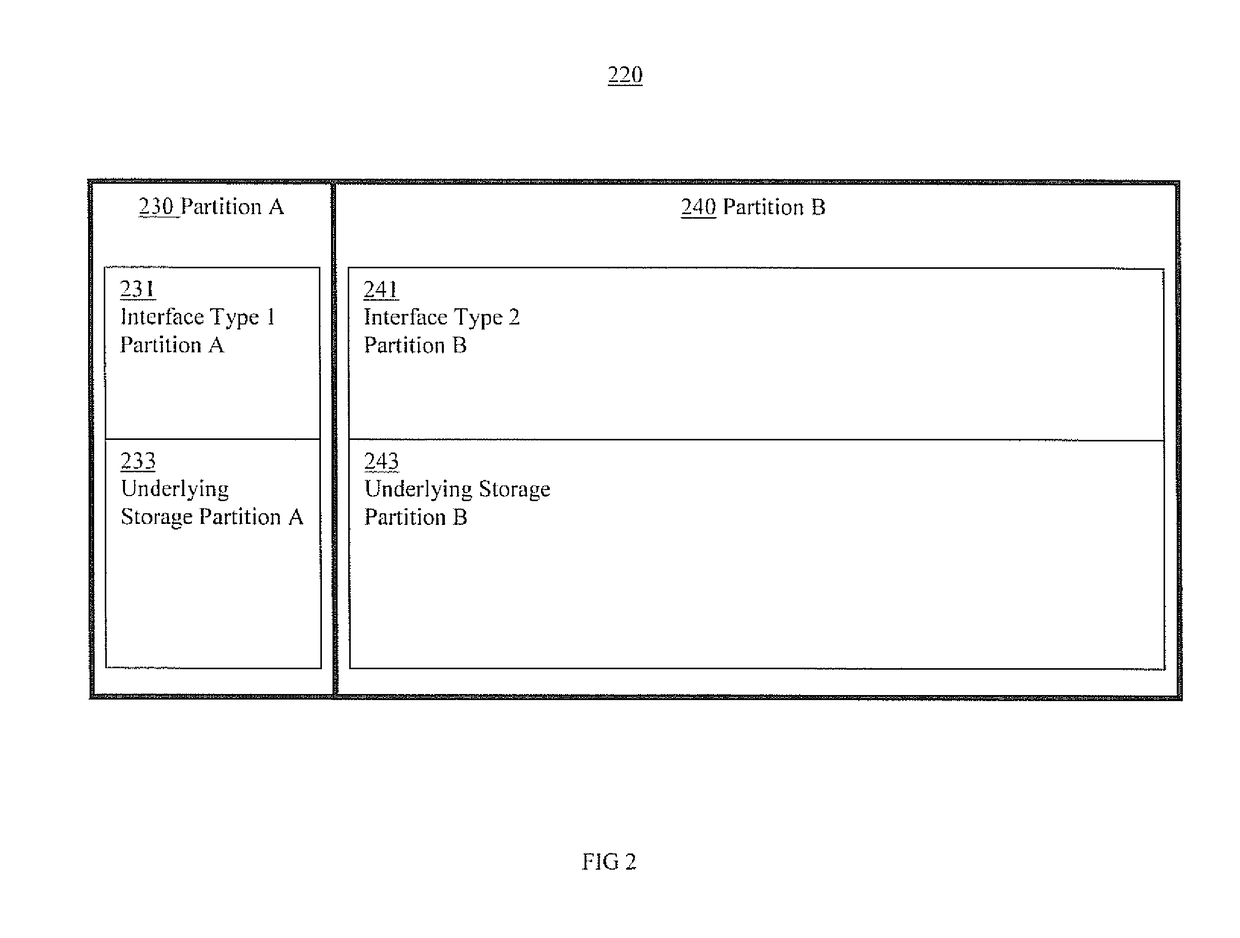
Selective underlying exposure storage mapping
ActiveUS20170139838A1Memory architecture accessing/allocationInput/output to record carriersMachine instructionJoint management
An apparatus for mapping user data into a selective underlying exposure address (SUE) space includes a memory that stores machine instructions and a processor that executes the instructions to combine first user data from a plurality of logically-addressed blocks to create a SUE page. The SUE page corresponds to a respective physical page of a respective physical block on each of a plurality of dies for which corresponding physical blocks of memory cells are jointly managed as a unit in a storage device. The processor further executes the instructions to store mapping information associating the first user data with the SUE page in a logical address space in the storage device.
Owner:SAMSUNG ELECTRONICS CO LTD
Horizontally-structured CAD/CAM modeling for virtual fixture and tooling processes
Disclosed herein is a method of horizontally structured CAD / CAM modeling and manufacturing process for fixtures and tooling comprising: selecting a contact area geometry; generating a tooling model corresponding to the contact area geometry; virtual machining the tooling model to generate the fixtures and tooling; and generating machining instructions to create the fixtures and tooling; where the tooling model exhibits an associative relationship with the contact area geometry. Also disclosed herein is a horizontally structured CAD / CAM model for fixtures and tooling, comprising: a selected contact area geometry; a tooling model that corresponds to the contact area geometry, generated from the selected contact area geometry; where the tooling model includes virtual machining operations to generate the fixtures and tooling; and the tooling model exhibits an associative relationship with the contact area geometry. Further disclosed is a storage medium encoded with a machine-readable computer program code for horizontally structured CAD / CAM modeling. The storage medium including instructions for causing a computer to implement the method of horizontally structured CAD / CAM modeling and manufacturing for fixtures and tooling. Additionally disclosed is a computer data signal for horizontally structured CAD / CAM modeling. The computer data signal comprising code configured to cause a processor to implement a method of horizontally structured CAD / CAM modeling and manufacturing for fixtures and tooling.
Owner:STEERING SOLUTIONS IP HLDG +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com