Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
77 results about "Computer system design" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
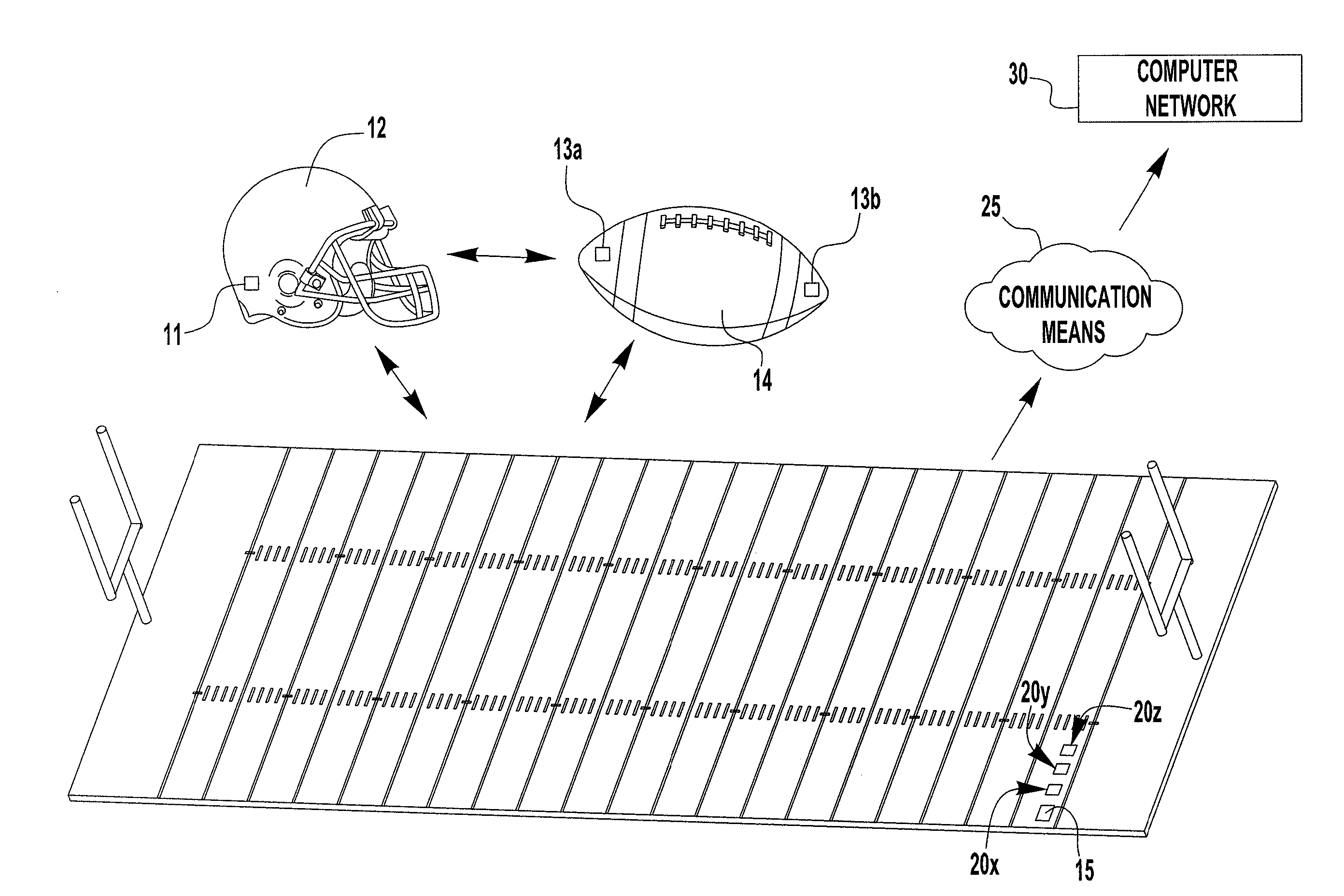
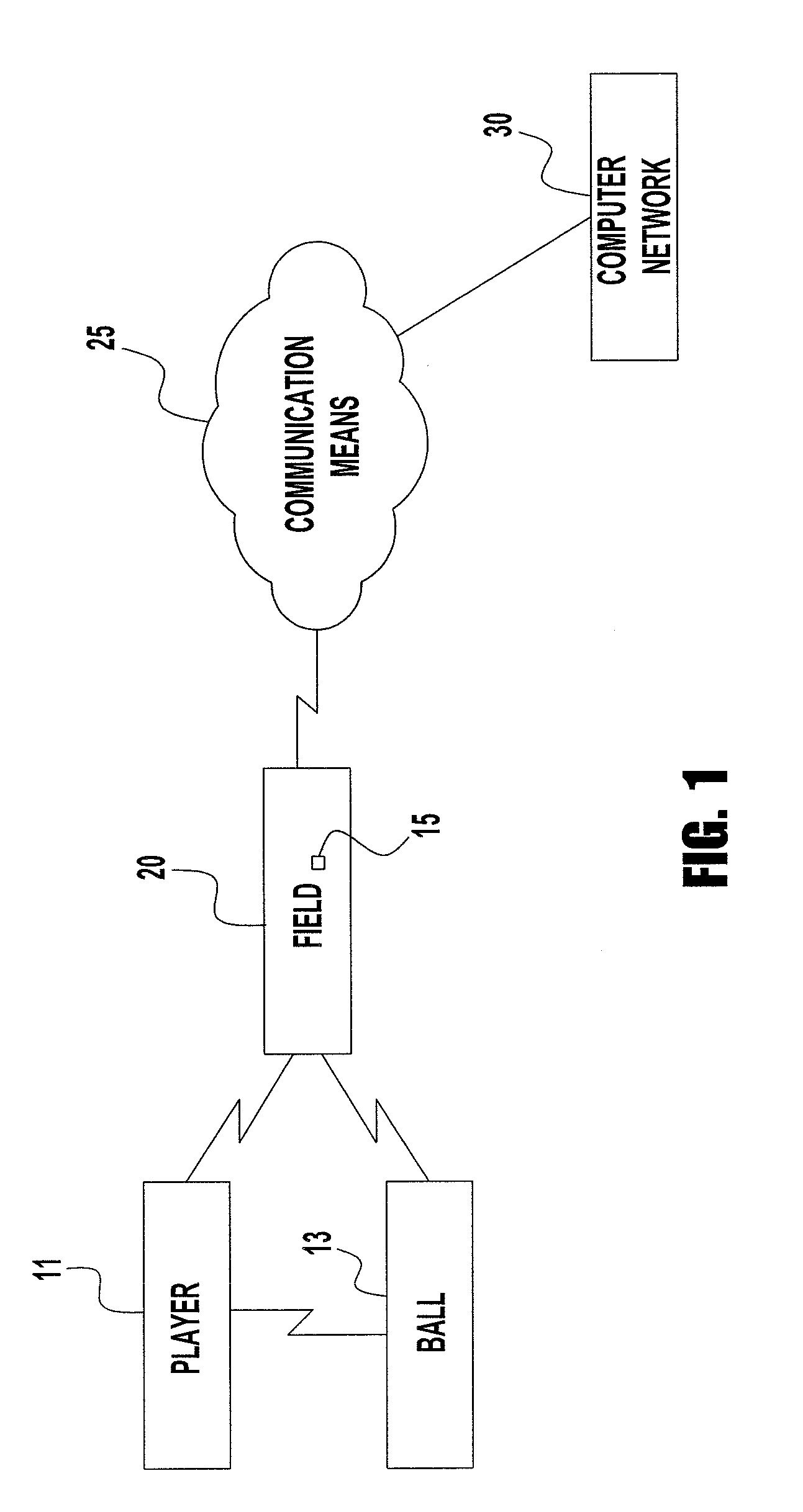
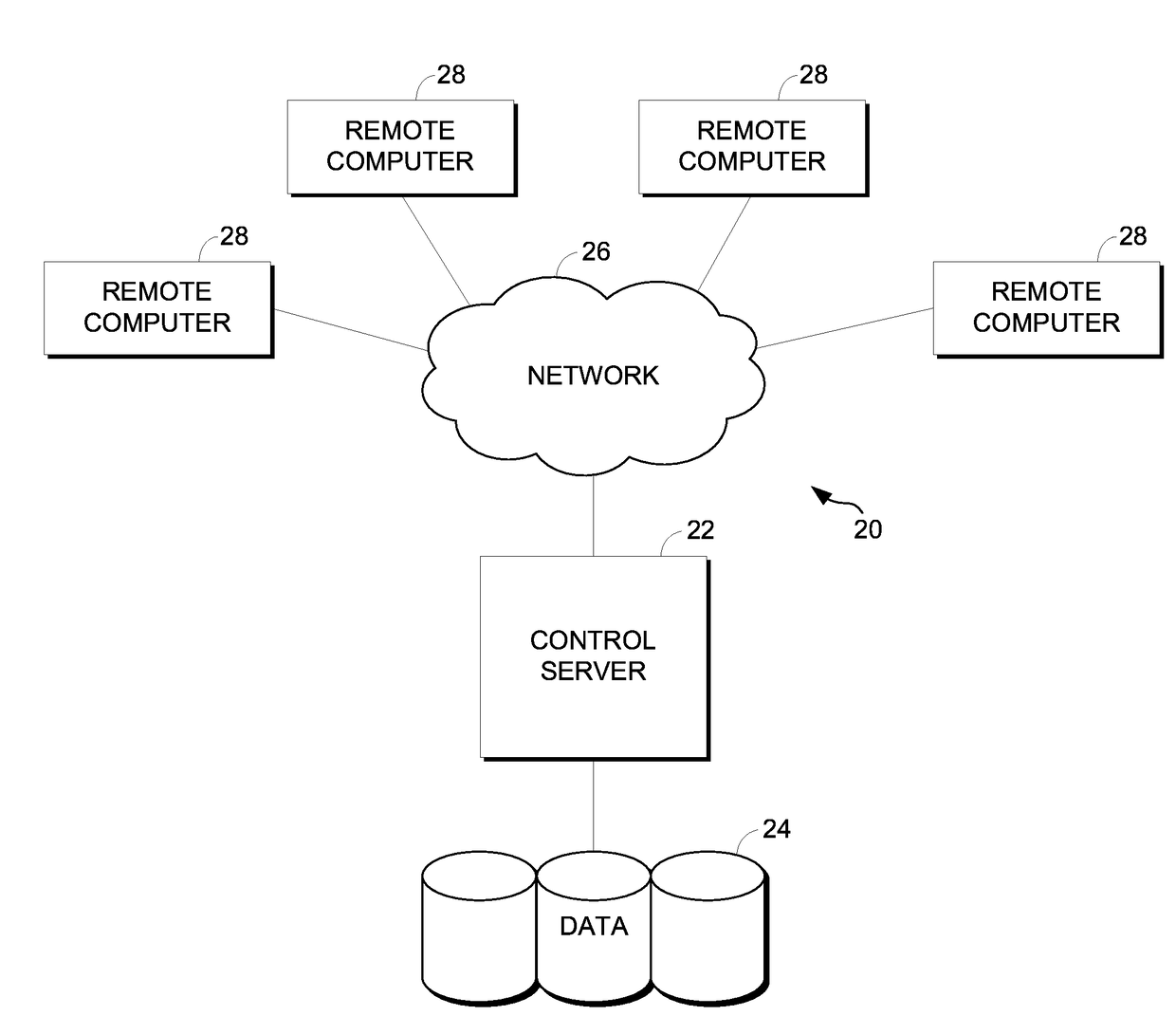
Active sports tracker and method
InactiveUS20070135243A1Easy to analyzeImprove abilitiesSki bindingsGymnastic exercisingComputer system designSimulation
A sports tracking and analysis system includes a RFID tag implanted onto an item associated with a player and at least one RFID tag implanted on a game ball. The tags and reader are arranged to transfer data such as the time and location of player and ball to each other for readers positioned throughout the field. The readers communicate the data to a computer system designed to process the data and generate player performance statistics including real-time measurements of many characteristics and, over time or based on input data, historical performance statistics. A method of tracking and analyzing the performance of a sports game is also included.
Owner:RUEISTIC TECH
System and Method for Forensic Identification of Elements Within a Computer System
ActiveUS20100030996A1Memory adressing/allocation/relocationComputer security arrangementsMemory forensicsComputer system design
A system and method for employing memory forensic techniques to determine operating system type, memory management configuration, and virtual machine status on a running computer system. The techniques apply advanced techniques in a fashion to make them usable and accessible by Information Technology professionals that may not necessarily be versed in the specifics of memory forensic methodologies and theory.
Owner:FIREEYE SECURITY HLDG US LLC
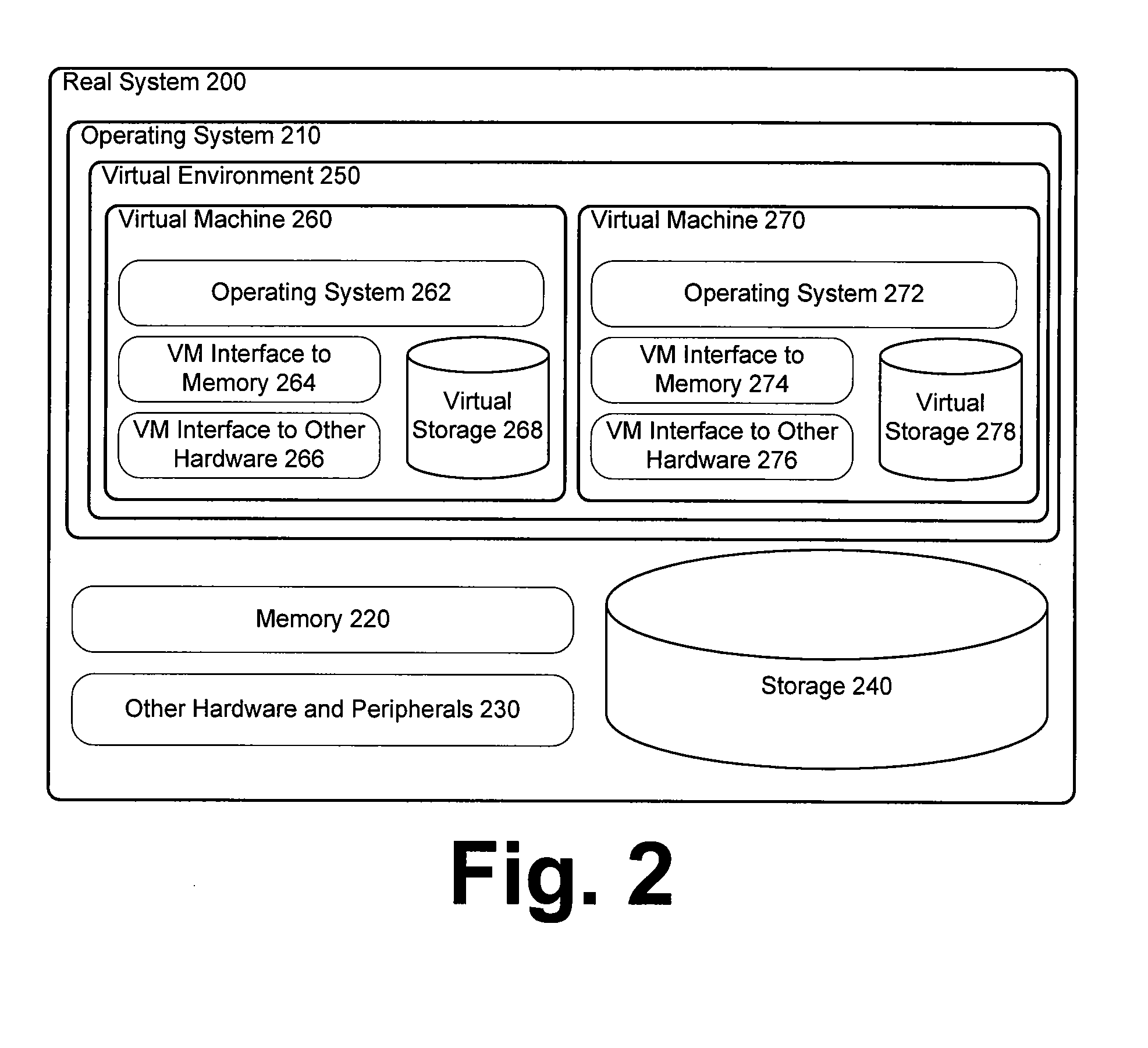
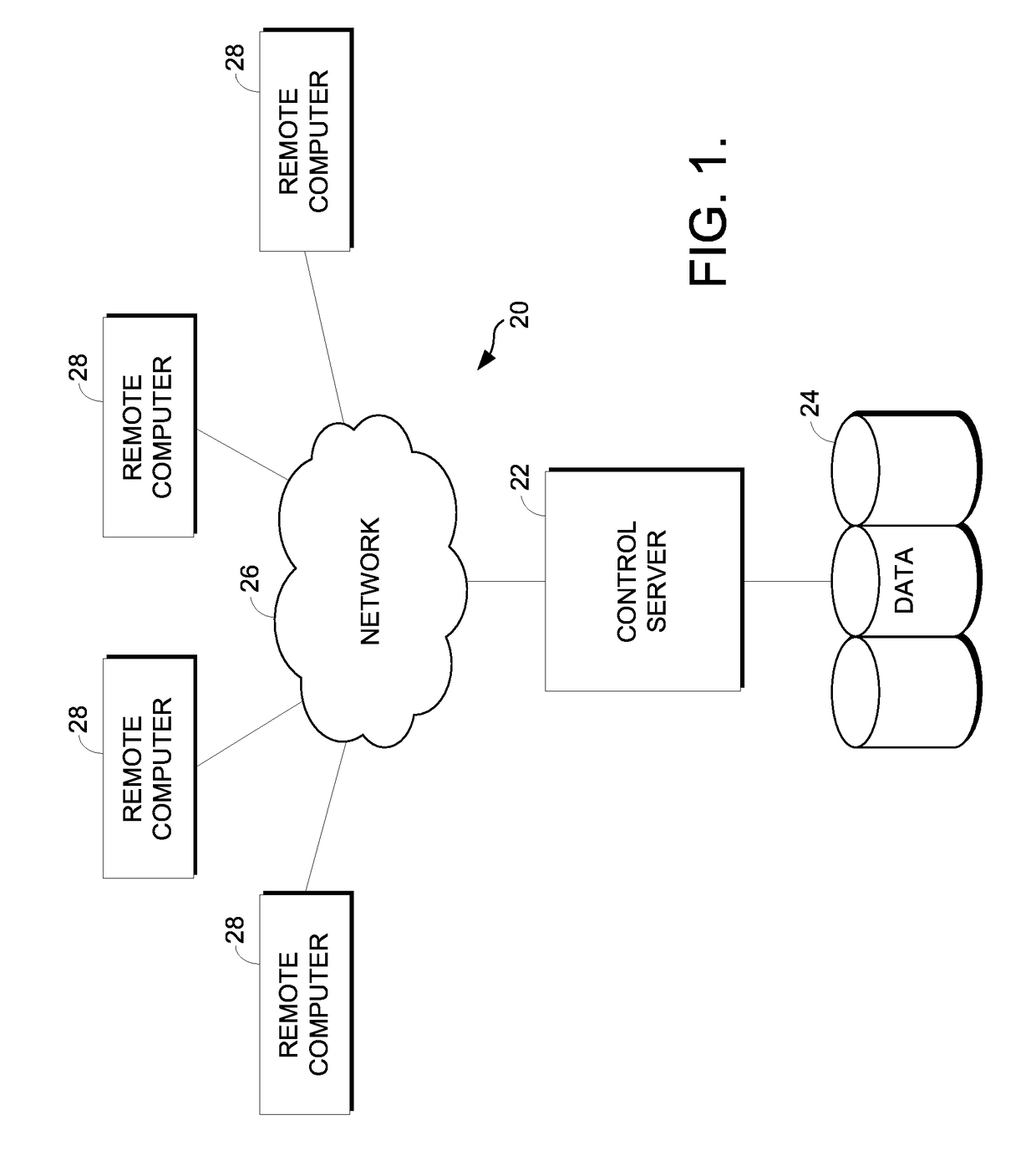
Computer systems and methods for platform independent presentation design
InactiveUS7236982B2Eliminate dependenciesDigital data information retrievalDigital data processing detailsComputer system designAlgorithm
Methods, computer systems and computer program products for constructing a presentation in a platform independent manner. A layout is defined that includes a top split. The top split includes a first orientation parameter specifying an orientation for any daughter split created within the top split. A request is received to create a daughter split within the top split. In response, the daughter split is constructed within the top split in accordance with the first orientation parameter. The daughter split includes a second orientation parameter specifying an orientation for any child split created within the daughter split. The layout is converted into the presentation. A database for storing the layout. The database including a layout table having a row for storing an identity of the layout and an identity of the top split in a hierarchy of splits within the layout. The database also including a layoutdata table that has a row for each split in the hierarchy of splits within the layout.
Owner:PIC WEB SERVICES
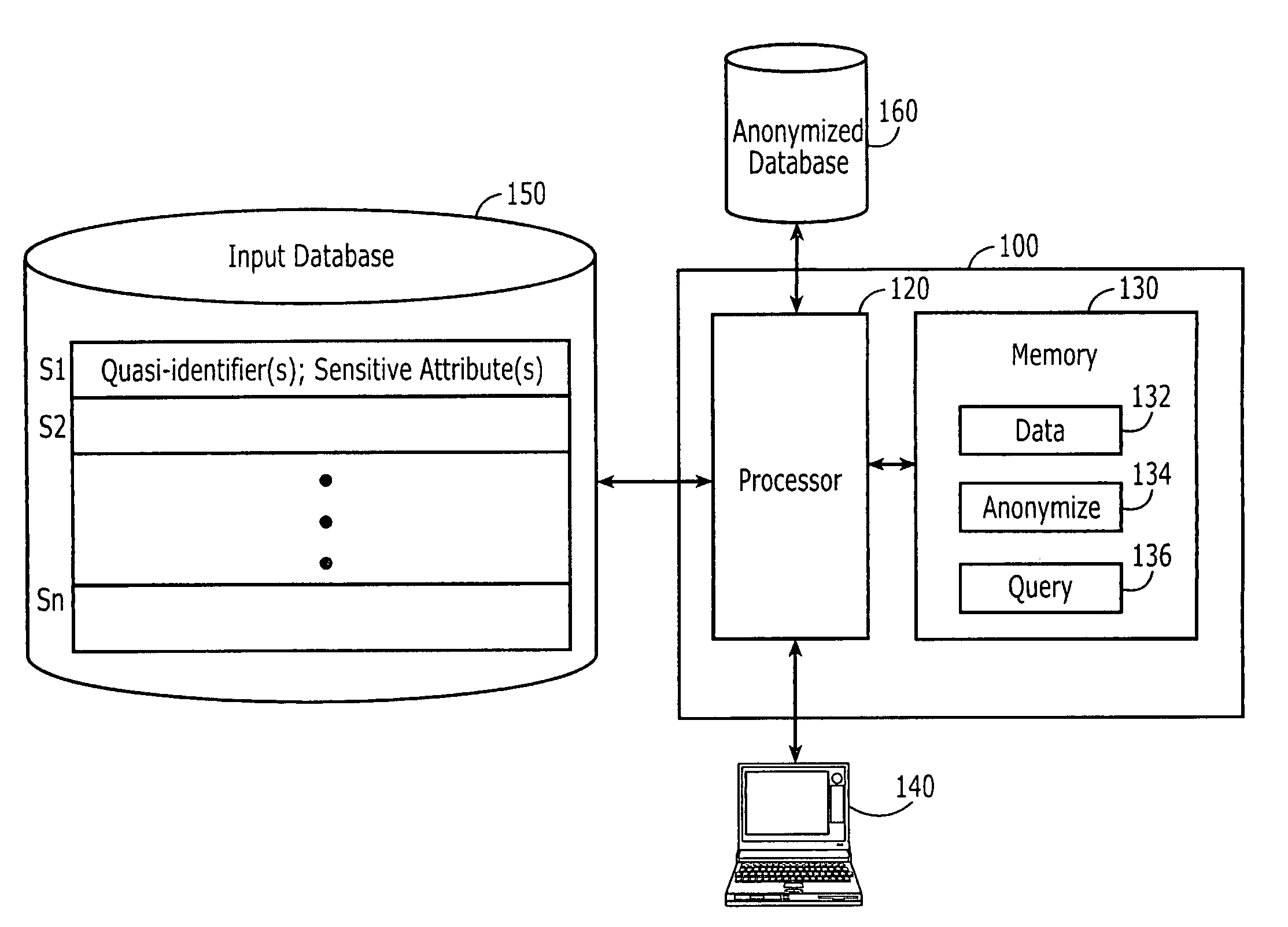
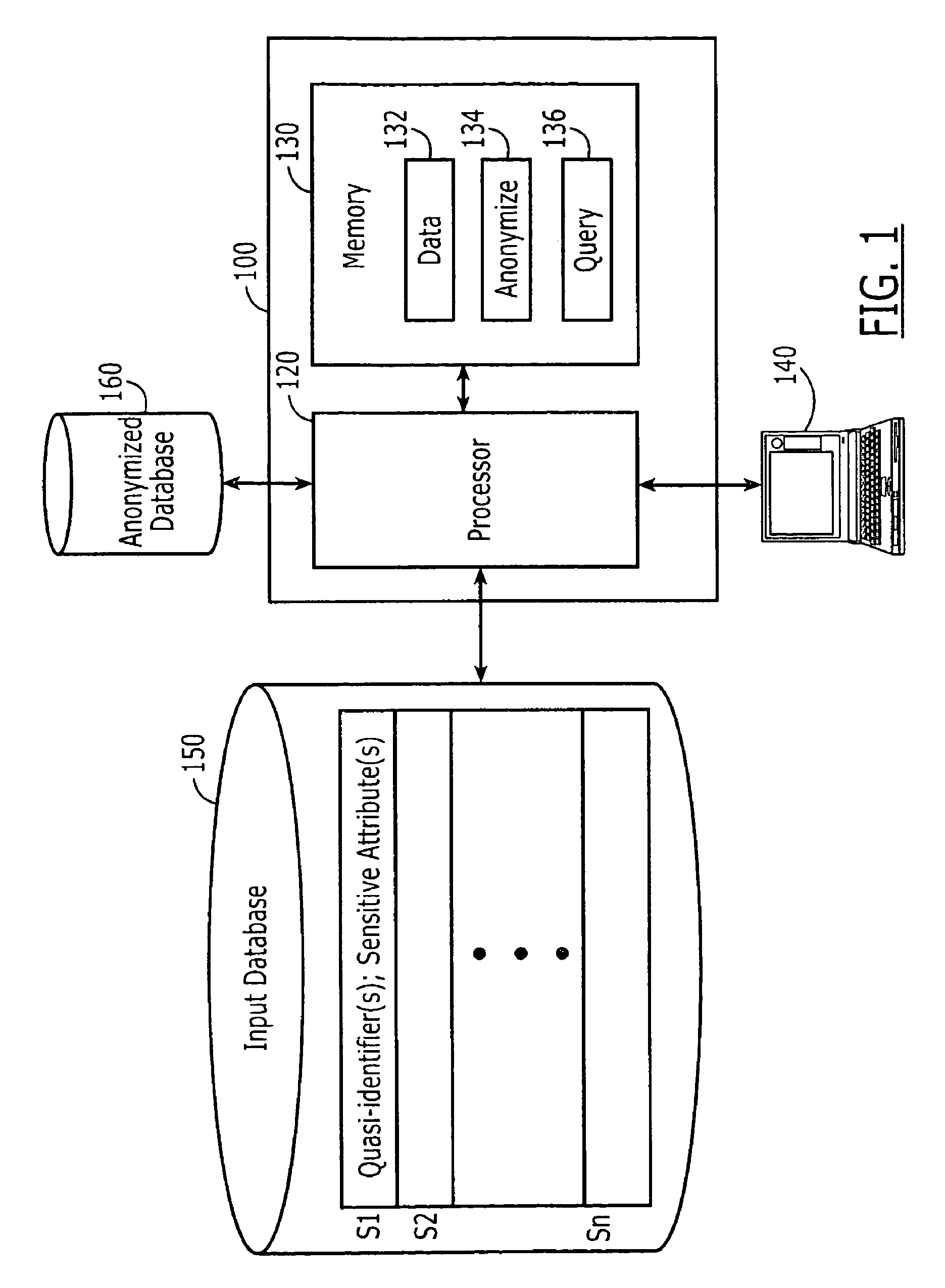
Computer systems, methods and computer program products for data anonymization for aggregate query answering
ActiveUS20100114920A1Small cost increaseLow costDigital data processing detailsComputer security arrangementsComputer system designComputerized system
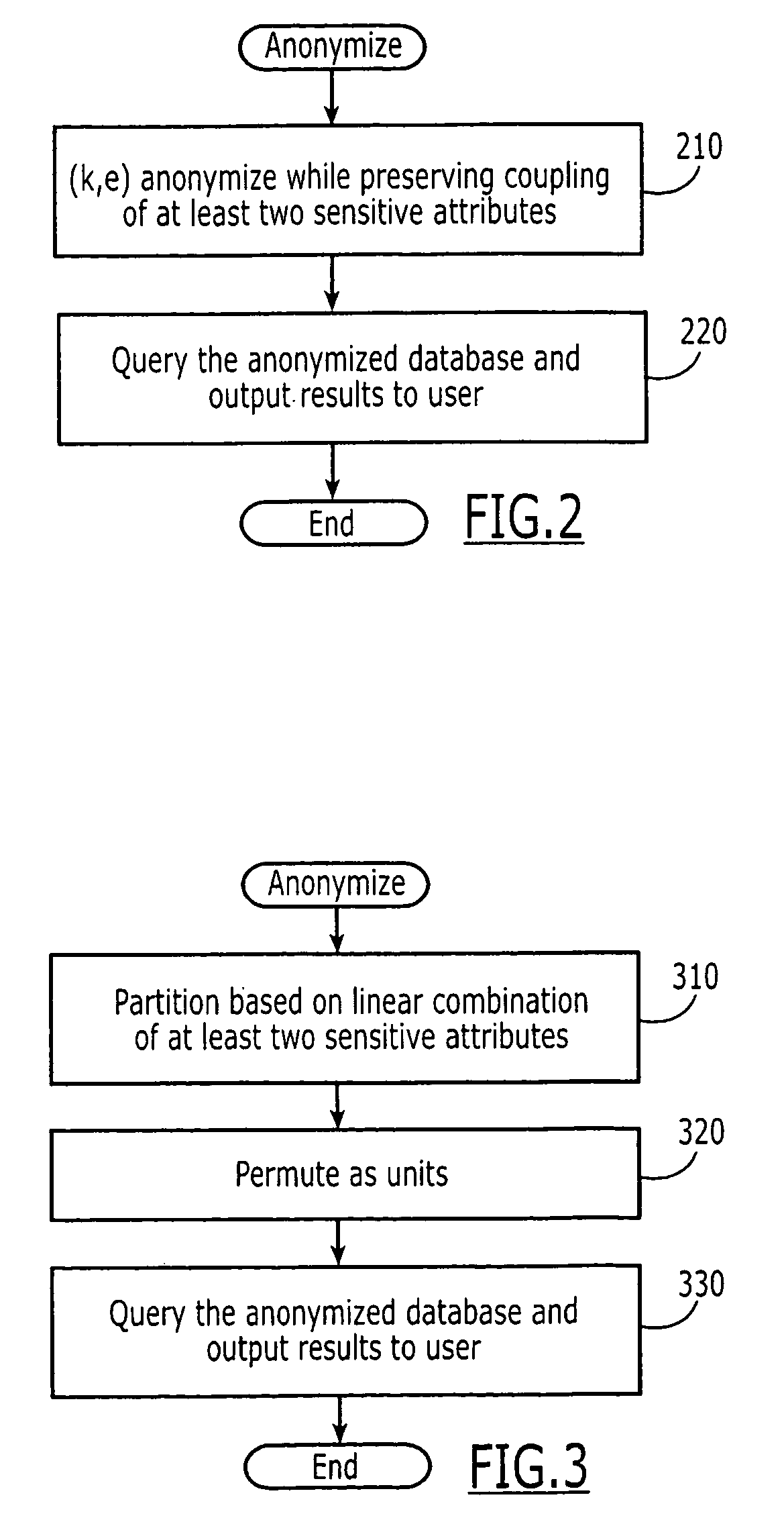
Computer program products are provided for anonymizing a database that includes tuples. A respective tuple includes at least one quasi-identifier and sensitive attributes associated with the quasi-identifier. These computer program products include computer readable program code that is configured to (k,e)-anonymize the tuples over a number k of different values in a range e of values, while preserving coupling at least two of the sensitive attributes to one another in the sets of attributes that are anonymized to provide a (k,e)-anonymized database. Related computer systems and methods are also provided.
Owner:AT&T INTPROP I L P
Partial Timing Modeling for Gate Level Simulation
ActiveUS20100031209A1Computer aided designSoftware simulation/interpretation/emulationComputer architectureComputerized system
Various apparatuses, methods and systems for creating an integrated circuit and performing a gate level simulation of a circuit are disclosed herein. For example, some embodiments of the present invention provide a system for performing a gate level simulation of a circuit including a computer system, a design verification tool and an output device. The design verification tool, executable on the computer system, includes a simulator and a partial timing model generator. The partial timing model generator is operable to generate a representation of the circuit for simulation by cutting a first portion of a circuit out of a full gate level netlist for the circuit and leaving a second portion of the circuit represented by the full gate level netlist, and to overlay a simplified representation of the first portion of the circuit over the representation of the circuit. The first portion of the circuit is cut out at timing paths. The simulator is operable to perform a gate level simulation of the circuit based on the representation of the circuit. The output device is connected to the computer system and is operable to provide an indication of a result of the gate level simulation of the circuit.
Owner:TEXAS INSTR INC
Computer systems and methods for automatically viewing multidimensional databases
Owner:TABLEAU SOFTWARE INC
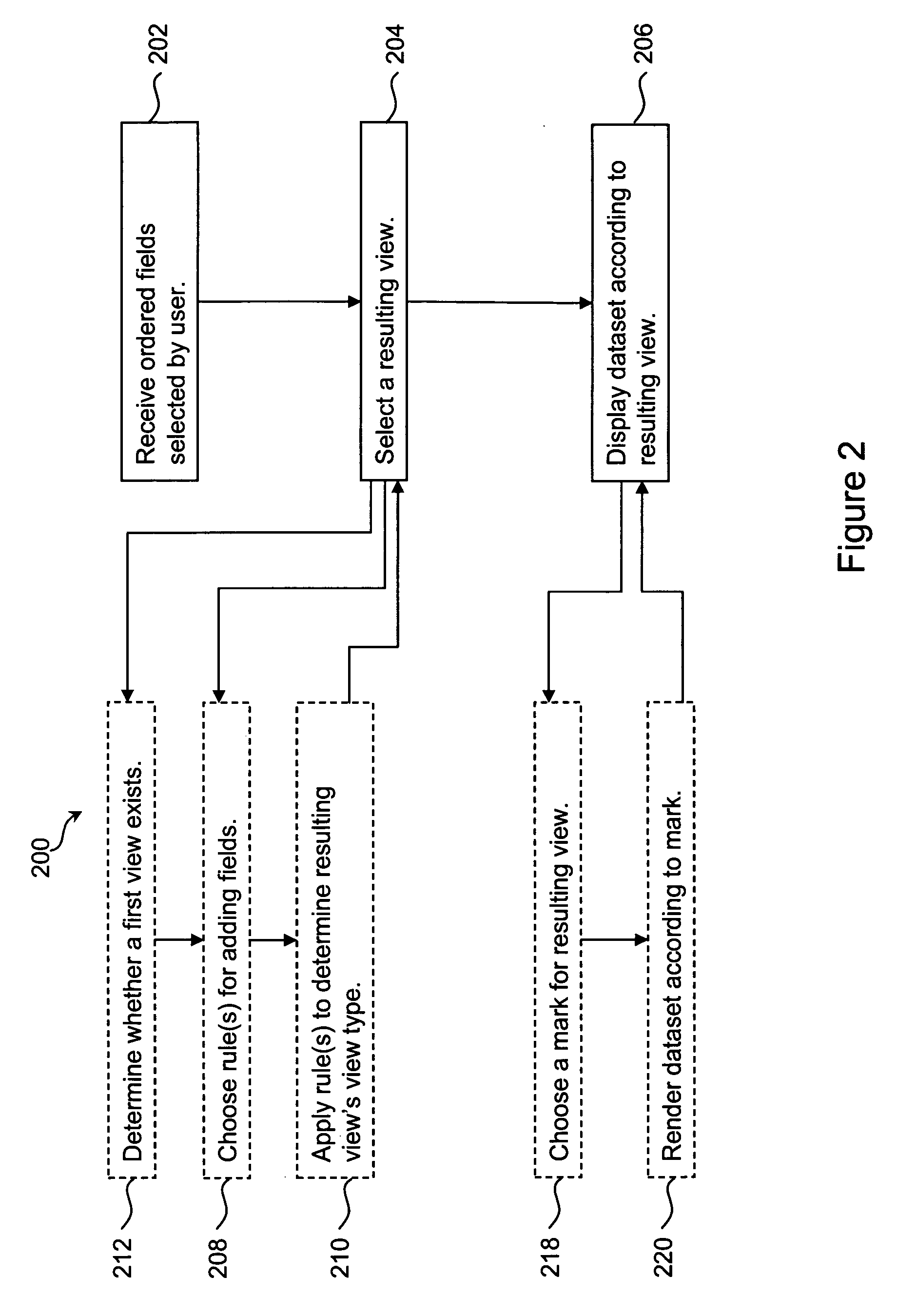
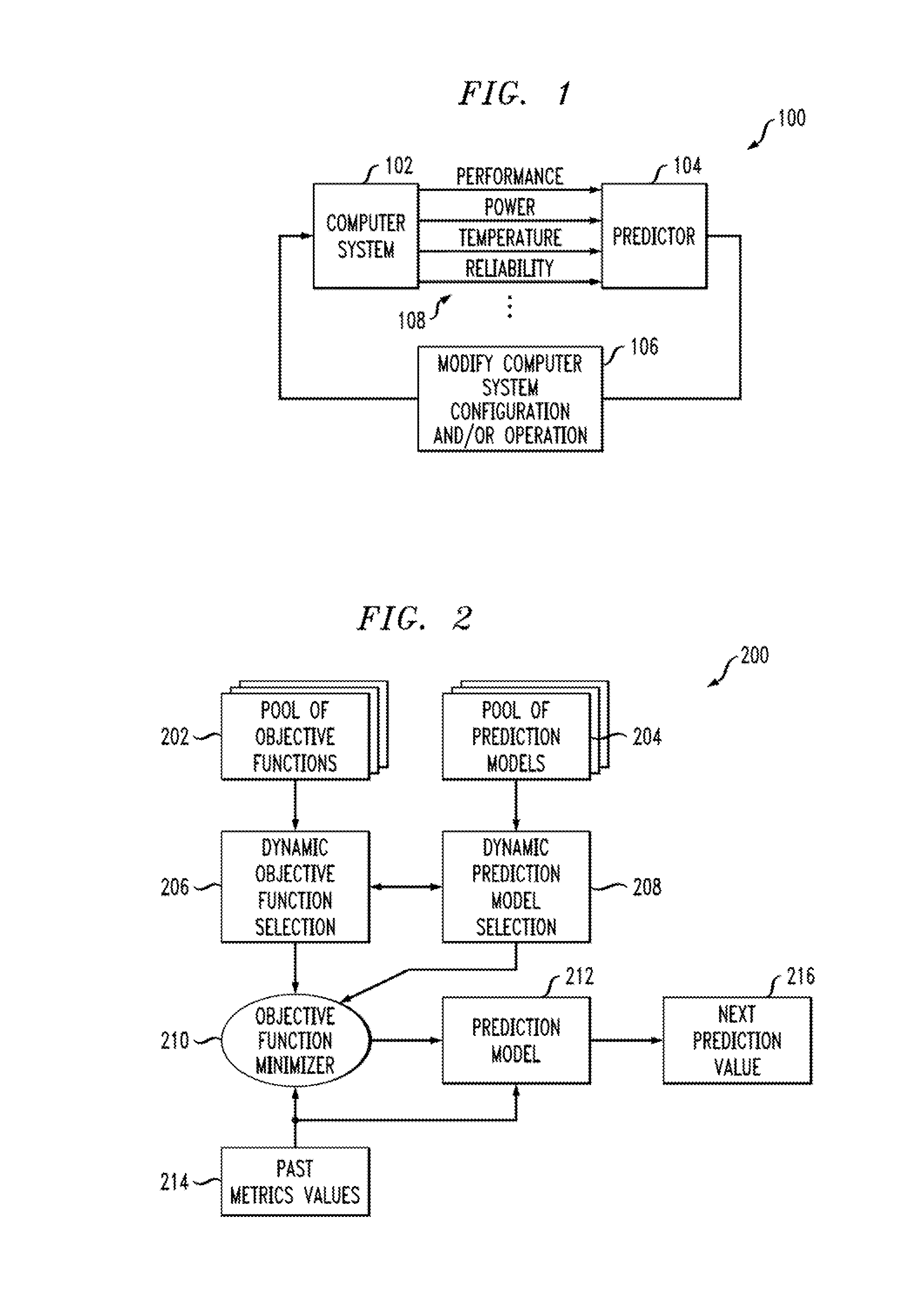
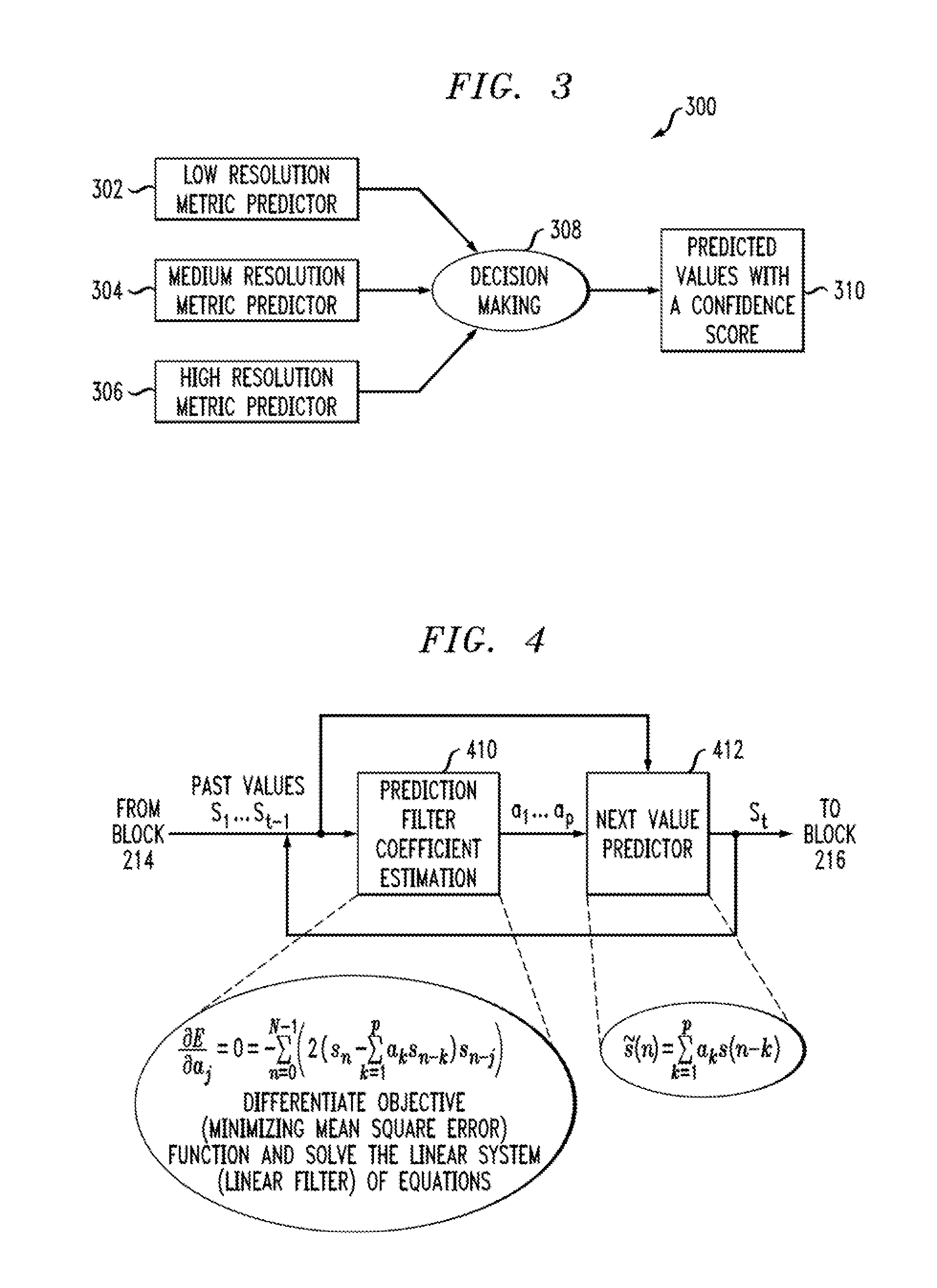
Apparatus And Method For Predicting A Metric Associated With A Computer System
ActiveUS20080177686A1Easy to useAccurate modelingDigital computer detailsChaos modelsComputer system designAlgorithm
An objective function is dynamically chosen from a pool of available objective functions, and a prediction model is dynamically chosen from a pool of available prediction models. Points of inflection are determined for the chosen objective function, based on past values of a metric, to obtain a set of equations that can be solved to obtain model parameters associated with the chosen prediction model. The equations arc solved to obtain the model parameters, and a future value of the metric is predicted based on (i) at least some of the past values of the metric and (ii) the chosen prediction model, with the obtained associated model parameters.
Owner:TWITTER INC
Quality metrics for automatic evaluation of dual ish images
ActiveUS20170323431A1Improve discriminationIncrease the number ofImage enhancementImage analysisComputer system designComputerized system
The present disclosure is directed to a computer system designed to (i) receive a series of images as input; (ii) compute a number of metrics derived from focus features and color separation features within the images; and (iii) evaluate the metrics to return (a) an identification of the most suitable z-layer in a z-stack, given a series of z-layer images in a z-stack; and / or (b) an identification of those image tiles that are more suitable for cellular based scoring by a medical professional, given a series of image tiles from an area of interest of a whole slide scan.
Owner:VENTANA MEDICAL SYST INC
Computer System and Method for Resolving Dependencies in a Computer System
ActiveUS20100138818A1Multiprogramming arrangementsProgram loading/initiatingComputer system designComputerized system
A computer system and a method are disclosed for use in automatically deploying an application program to execute with one or more library resources. The computer system includes a deployment unit which deploys the application program into a runtime execution environment. When a predetermined trigger condition is detected, the deployment unit clones a first library resource to create a clone, transforms the application to depend upon the clone and resolves the dependencies of the application using the clone. In one embodiment, the trigger condition relates to a pinning situation, whereby a library upon which the application program depends cannot be wired to the application program to resolve the dependency. Here, the clone now satisfies that dependency. In another embodiment, the trigger condition is a mandatory cloning property that requires the library to be cloned. The mandatory cloning property may also be user-specified through a user interface.
Owner:GOPIVOTAL
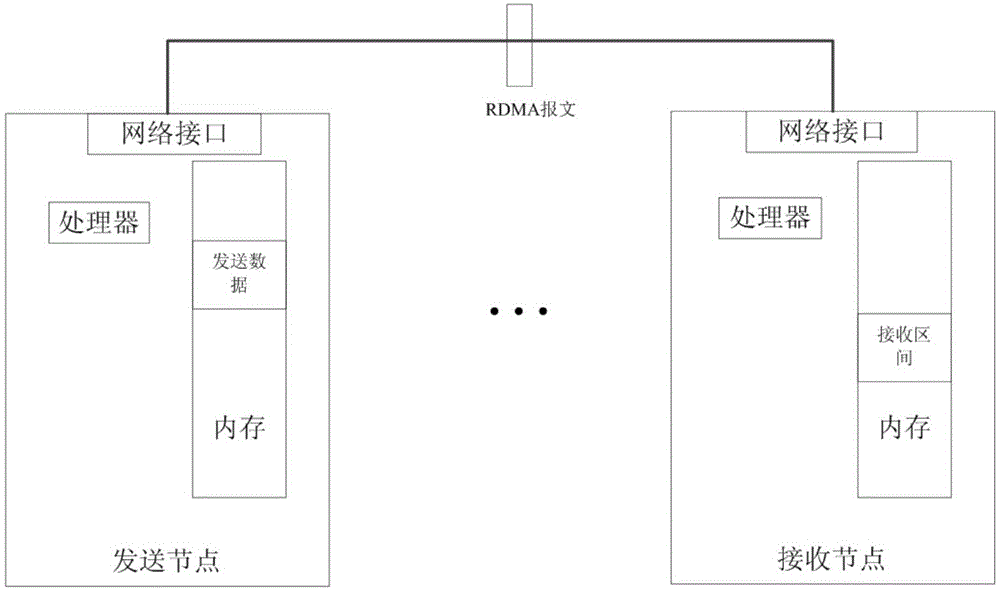
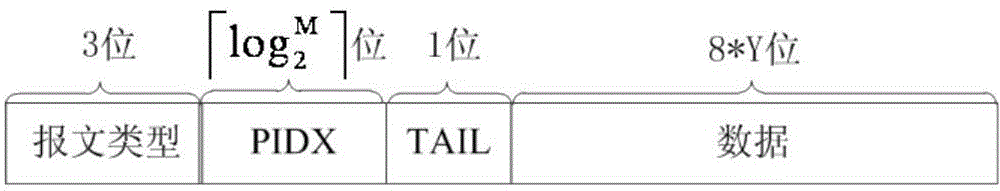
Receiver sliding window-based data transmission method in parallel computer system
ActiveCN104484295ASave resourcesReduce overheadDigital computer detailsElectric digital data processingComputer system designSlide window
The invention discloses a receiver sliding window-based data transmission method in a parallel computer system, and aims at guaranteeing the integrity and the correctness of out-of-order and unreliable network-based RDMA (remote direct memory access) transmission data in the design of the existing parallel computer system. The technical scheme is that the data transmission method comprises the following steps of: firstly, establishing connection between a sending node and a receiving node; setting up a receiving window at the receiving window, wherein the receiving window is only used for recording and receiving the numbers of RDMA messages nor performing caching on RDMA messages entering the receiving window; sending the RDMA messages to the receiving node by the sending node and responding retransmission request messages sent back by the receiving node; meanwhile, receiving the RDMA messages, of which the message numbers are located in the receiving window, by the receiving node, and writing data in the RDMA messages in internal storage of the receiving node; receiving the RDMA messages, sent by the receiving node, by the sending node to finish message response, and ending the RDMA transmission by the sending node. Compared with the existing method, the receiver sliding window-based data transmission method disclosed by the invention has the advantages that the hardware resource cost can be reduced, the retransmission cost is reduced, and the transmission efficiency is improved.
Owner:NAT UNIV OF DEFENSE TECH
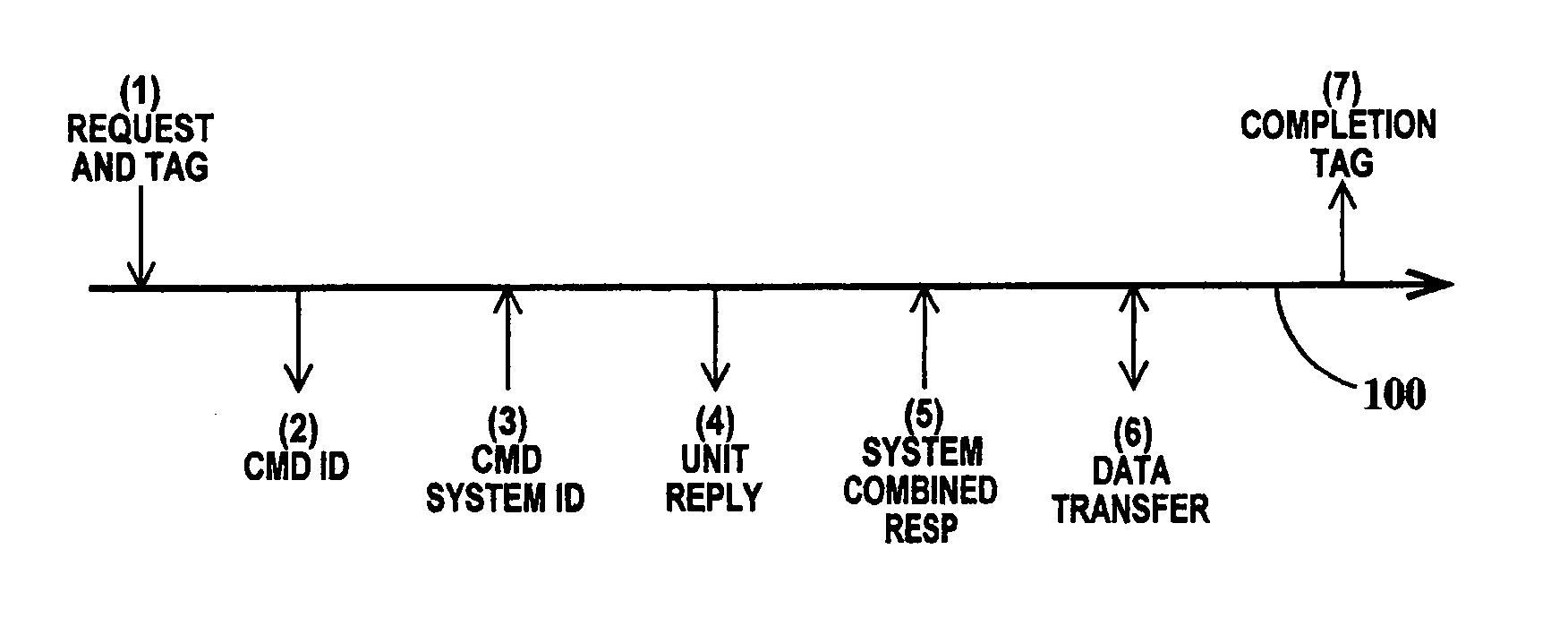
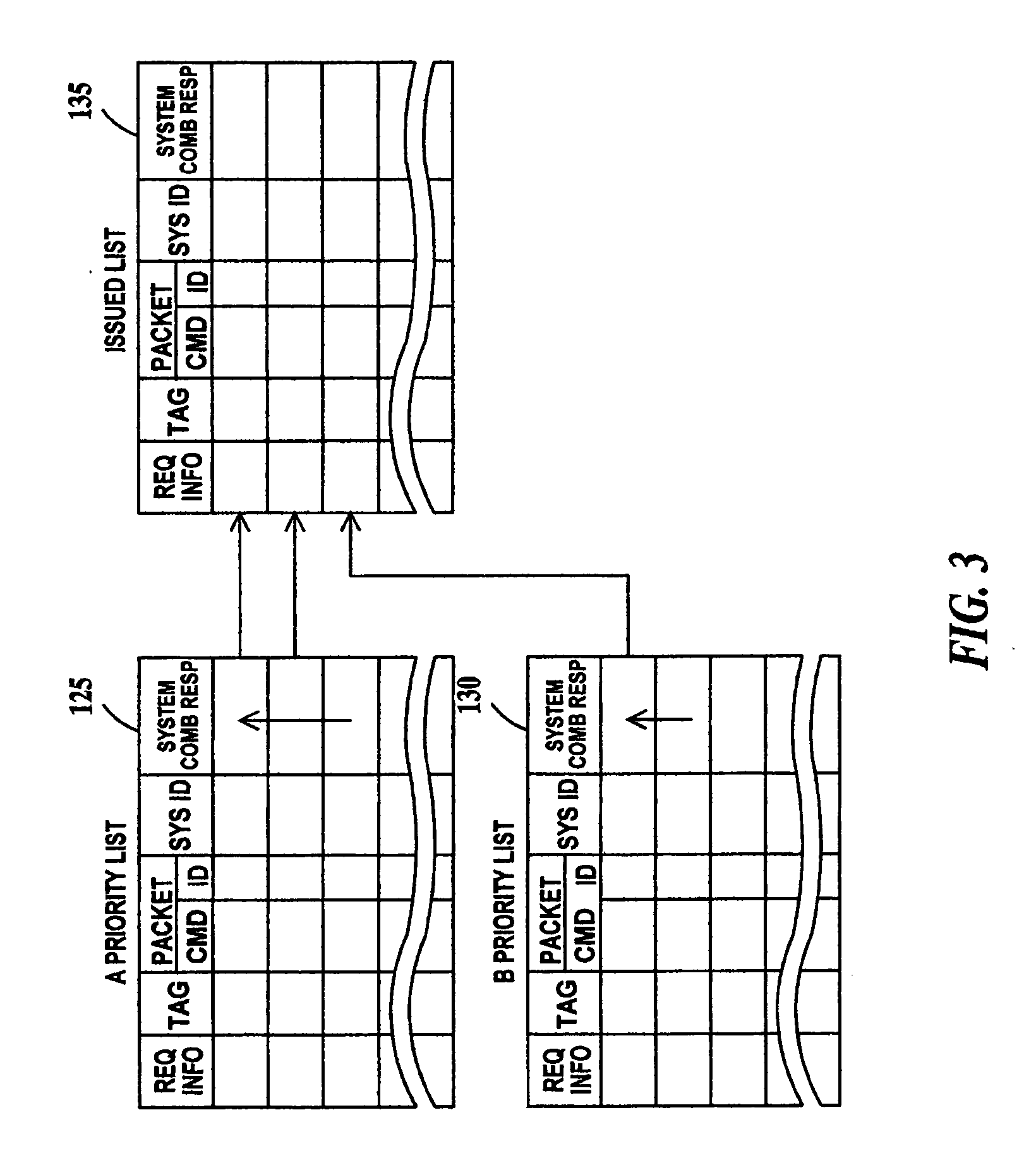
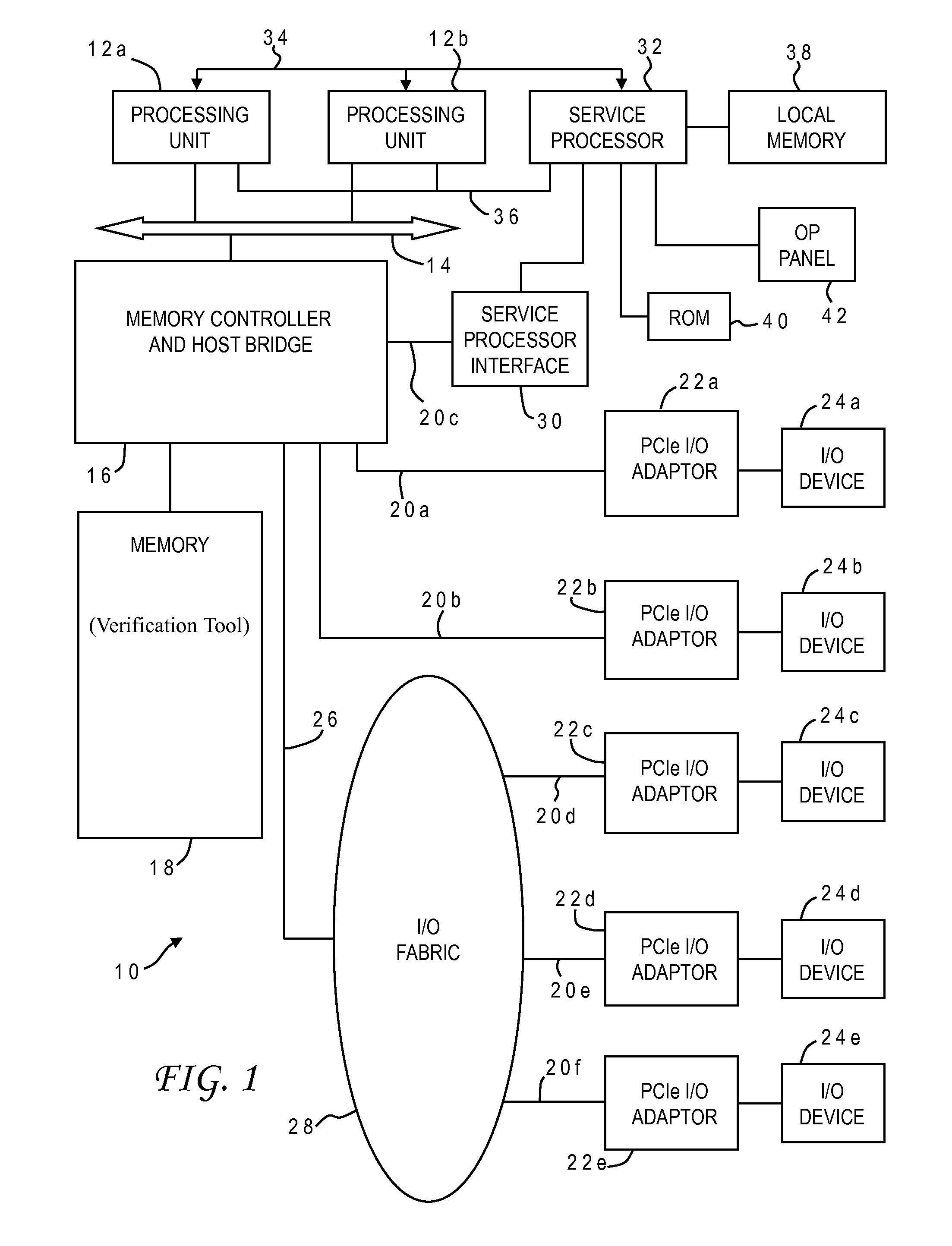
Method for verification of command processing in a computer system design having a multiple priority command queue
InactiveUS20050160320A1Error detection/correctionSpecific program execution arrangementsComputer system designValidation methods
A method for verification of multiple priority command processing, including: inputting over time, multiple simulated requests into a simulation model of the computer system, each request having a priority and each request comprising a request and tag transaction, a command ID transaction, command system ID transaction, a system combined response transaction and a completion tag transaction; sorting the priority of each request based; issuing an error if any particular command ID transaction is not a transaction of a request previously sorted; issuing an error if any particular command system ID transaction is not a transaction of a request having a previously issued command ID transaction, if any particular system combined response transaction is not a transaction of a request having a previously issued command system ID transaction and if any particular completion tag transaction is not a transaction of a request having a previously issued system combined response transaction.
Owner:IBM CORP
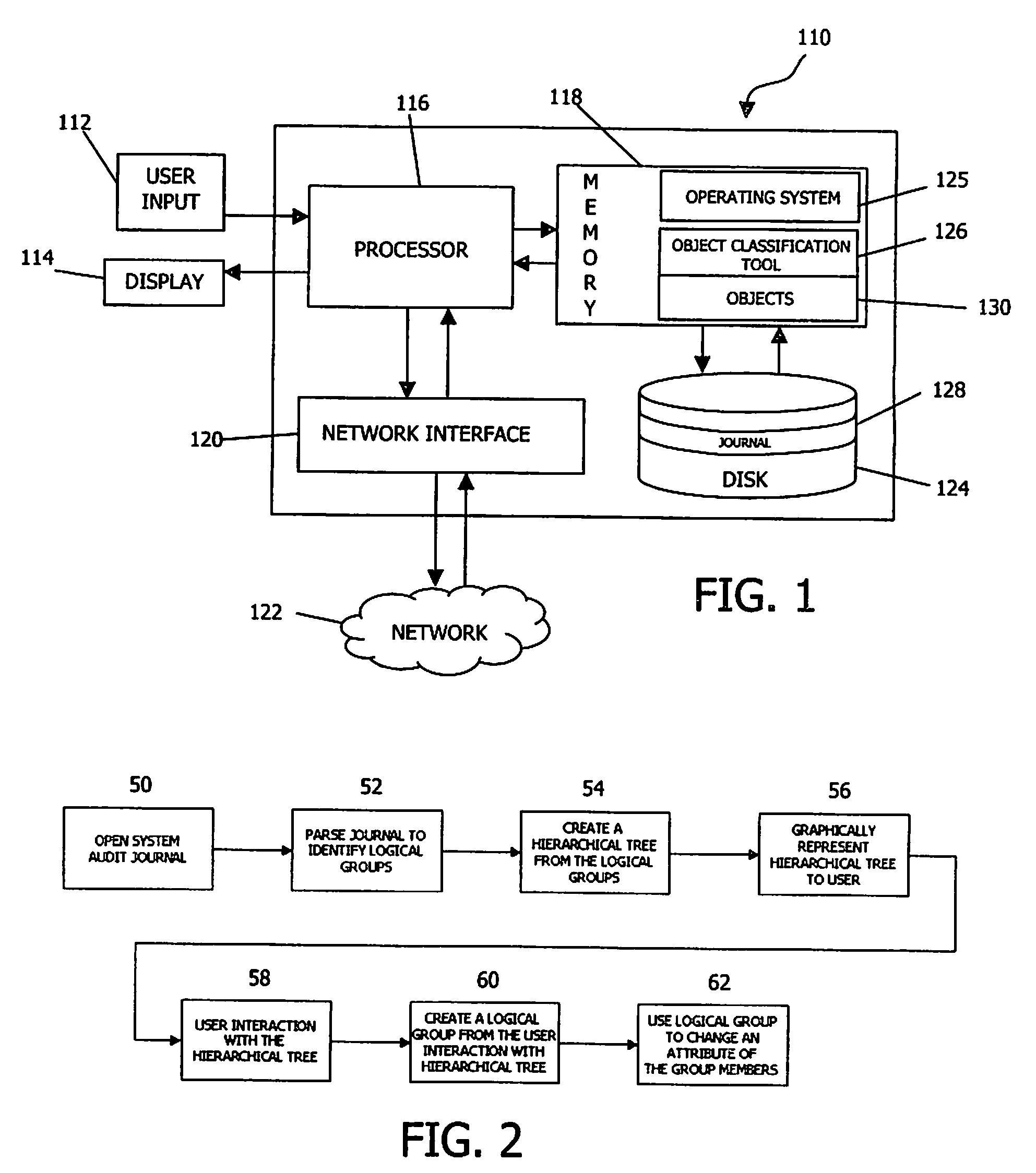
Logical Classification of Objects on a Computer System
ActiveUS20080154919A1Digital data processing detailsComputer security arrangementsGraphicsComputer system design
A method, apparatus and program product for classifying objects on a computer system. An audit journal of interactions with objects is evaluated to identify a plurality of logical groups of objects. A graphical construct, such as a hierarchical tree, is created from the plurality of logical groups. And, in response to user input directed to the graphical construct, at least one object is classified based upon a logical group within which the object is arranged.
Owner:DAEDALUS BLUE LLC
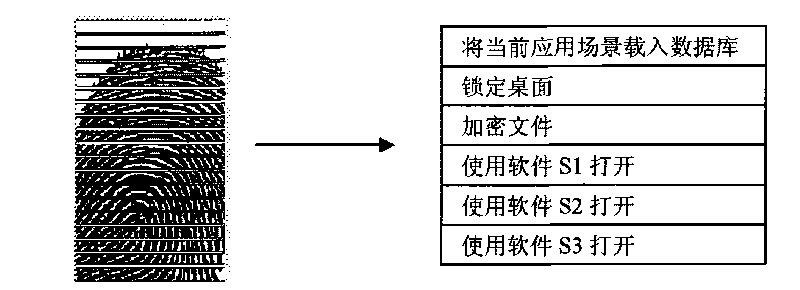
Computer system for fingerprint identification and fingerprint identification method thereof
The invention relates to a computer system for fingerprint identification and a fingerprint identification method thereof, belonging to the technical field of a computer. The computer system designed by the invention comprises a computer mainframe, an input and an output devices, a graphical operating system and application program, and is structurally characterized by further comprising a fingerprint input device, fingerprint service program and a fingerprint data base, wherein the fingerprint input device is used for collecting user fingerprint characteristics and transmitting the information into the fingerprint service program; the fingerprint service program is used for reading, writing or updating the fingerprint data base according to the information, and transferring the application program; the graphical operating system is used for outputting the information into the output device to be displayed; and the fingerprint data base is used for recording the corresponding relationship among the user, the fingerprint, the context, the operation and the operation weighting coefficient. The invention can be used for managing various application scenes in a centralized way by establishing the unified fingerprint data base, provides unified fingerprint identification service and has the characteristics of convenient and rapid use.
Owner:TSINGHUA TONGFANG CO LTD
Determining maliciousness in computer networks
A computer implemented method provides a technical solution to the technical problem of detecting and preventing malicious activity in a computer network, the technical solution involving calculating, based on hypergraph data, a maliciousness value indicating a likelihood of association of one or more nodes of the hypergraph with a known malicious actor, and programmatically performing, based on the calculated maliciousness value, one or more actions by a computer system designed to ensure security of the computer system.
Owner:KUDU DYNAMICS LLC
Computer systems, methods and computer program products for data anonymization for aggregate query answering
ActiveUS8112422B2Low costDigital data information retrievalDigital data processing detailsComputer system designComputerized system
Computer program products are provided for anonymizing a database that includes tuples. A respective tuple includes at least one quasi-identifier and sensitive attributes associated with the quasi-identifier. These computer program products include computer readable program code that is configured to (k,e)-anonymize the tuples over a number k of different values in a range e of values, while preserving coupling at least two of the sensitive attributes to one another in the sets of attributes that are anonymized to provide a (k,e)-anonymized database. Related computer systems and methods are also provided.
Owner:AT&T INTPROP I LP
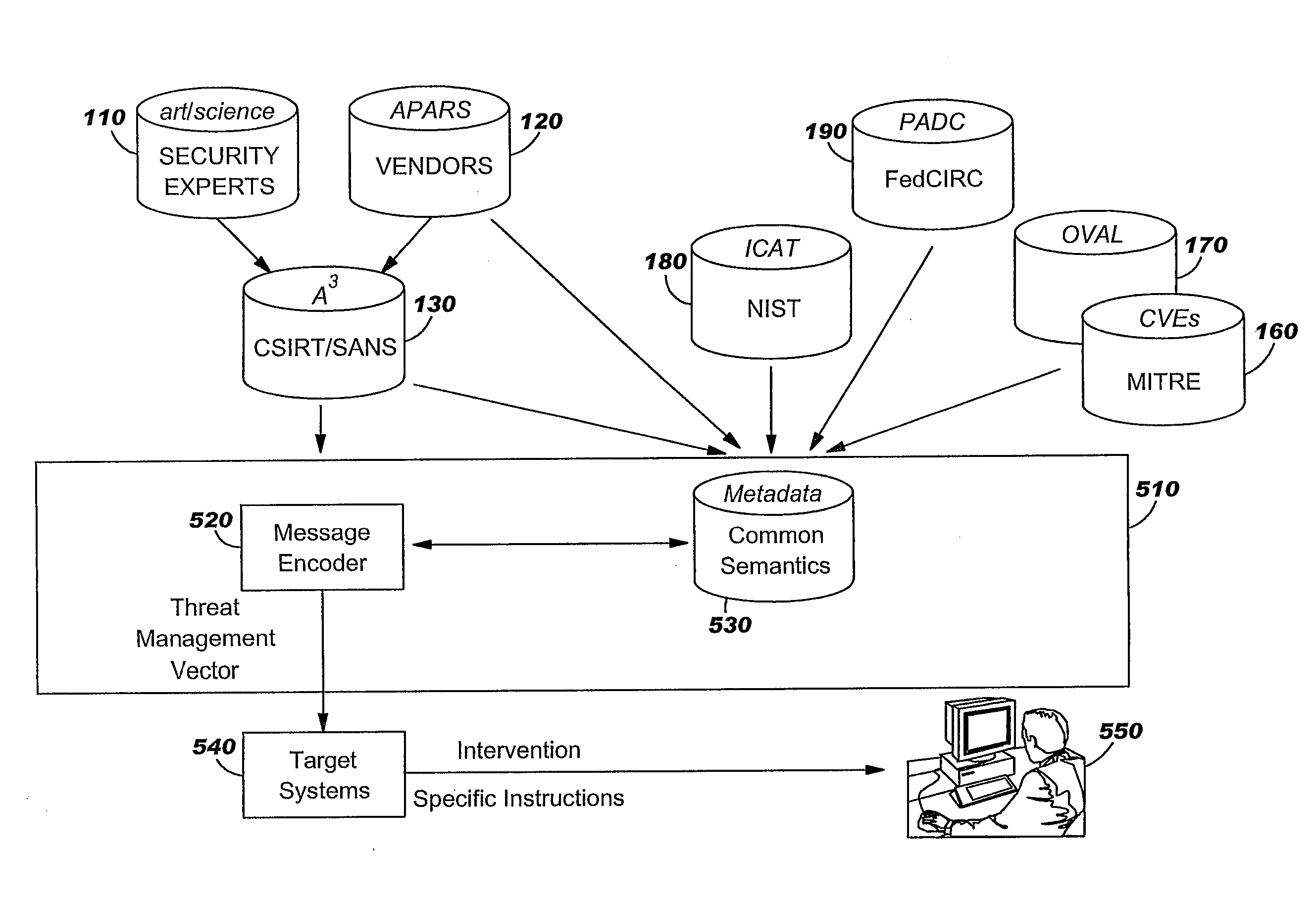
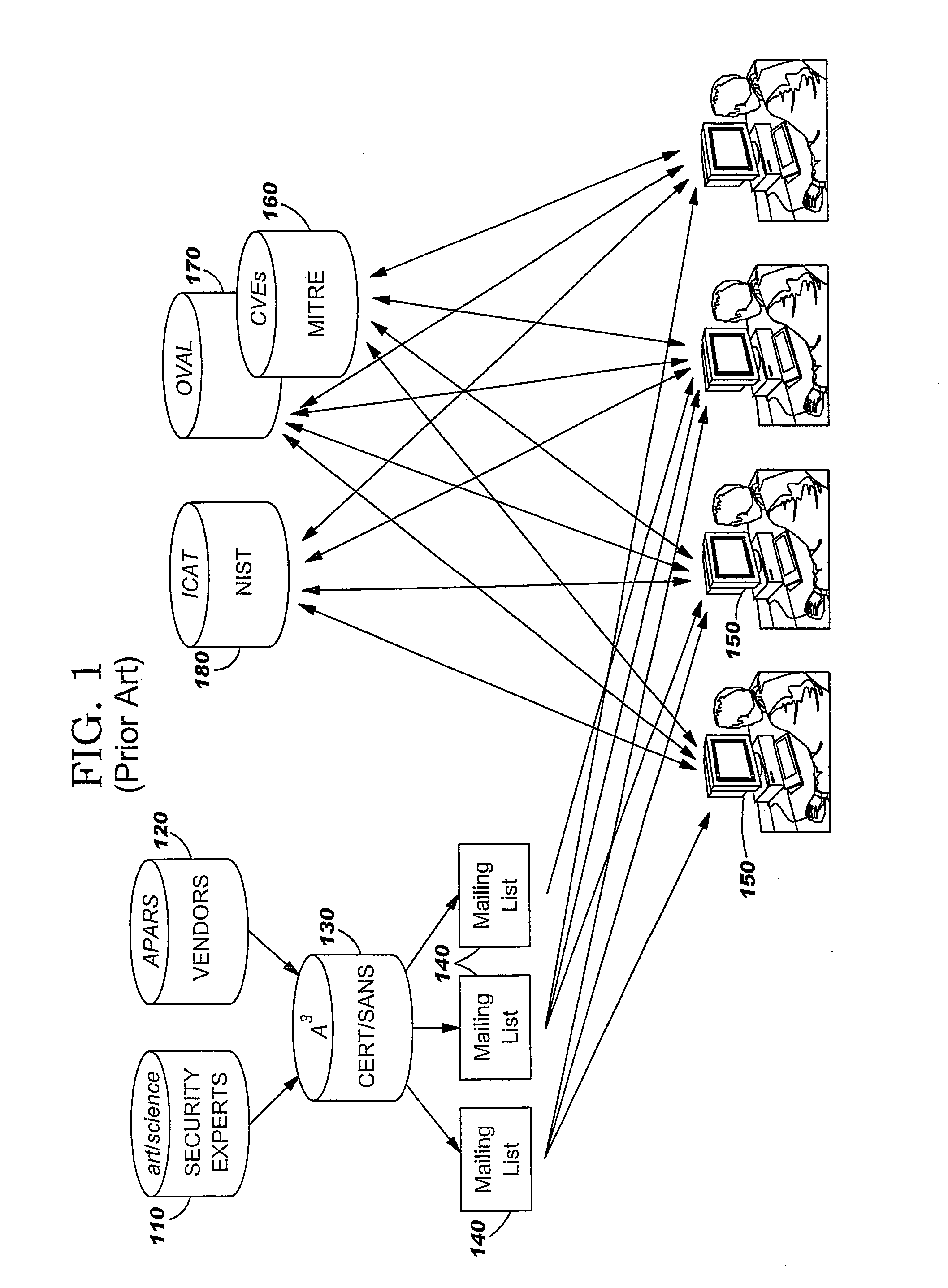
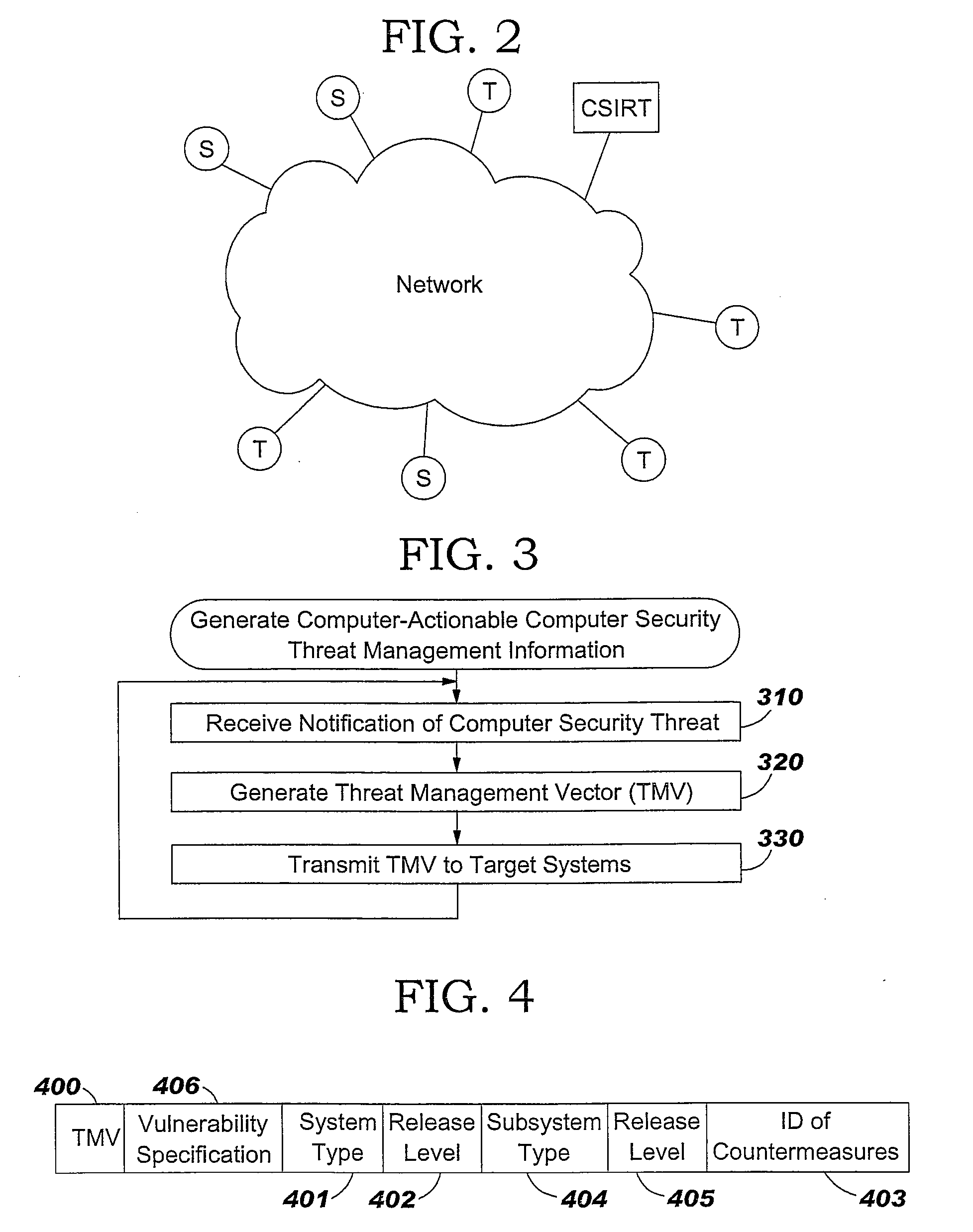
Method for Adminstration of Computer Security Threat Countermeasures to a Computer System
ActiveUS20090328206A1Memory loss protectionError detection/correctionComputer system designCountermeasure
A countermeasure for a computer security threat to a computer system is administered by establishing a baseline identification of an operating or application system type and an operating or application system release level for the computer system that is compatible with a Threat Management Vector (TMV). A TMV is then received, including therein a first field that provides identification of at least one operating system type that is affected by a computer security threat, a second field that provides identification of an operating system release level for the operating system type, and a third field that provides identification of a set of possible countermeasures for an operating system type and an operating system release level. Countermeasures that are identified in the TMV are processed if the TMV identifies the operating system type and operating system release level for the computer system as being affected by the computer security threat. The received TMV may be mutated to a format for processing of the countermeasure.
Owner:TREND MICRO INC
Positioning printing system for report
ActiveCN102722899AImprove accuracyImprove design efficiencySpecial data processing applicationsEditing/combining figures or textComputer system designSystems design
The invention provides a positioning printing system for a report. The system comprises a computer system and a printer connected with the computer system. The computer system is provided with a form positioning printing system design module, a positioning printing content input and storage module, a positioning printing content previewing and printing function module and a positioning printing page setting module, wherein the form positioning printing system design module is used for interface design and program design; the positioning printing content input and storage module is used for providing an input interface for positioning printing contents; the positioning printing content previewing and printing function module realizes a report positioning printing function after the system runs; and the positioning printing page setting module is used for regulating left and right margins or top and bottom margins of a positioning printing page to meet the requirements of different printers. Positioning printing accuracy and the positioning-printed report design efficiency are improved; when a part of contents of the report are moved outside a screen, or the report is over-sized, and a part of contents exceed the screen, the contents exceeding the screen can be effectively printed, so that an overall report positioning printing effect is ensured; and moreover, the contents which can be seen can be displayed on a display screen of a computer, so that the operation of a user is facilitated.
Owner:CHONGQING UNIV
Determining and Downloading Portions of a Software Application in a Computer System
ActiveUS20100257520A1Multiple digital computer combinationsSpecific program execution arrangementsComputer system designComputerized system
Determining and downloading portions of a software application in a computer system. The software application may include a plurality of portions. Which of those plurality of portions are currently present on the computer system and which of those plurality of portions are not currently present on the computer system may be determined. The portions of the software application which are not currently present on the computer system may be downloaded to the computer system. The portions of the software application which are currently present on the computer system may not be downloaded to the computer system.
Owner:NATIONAL INSTRUMENTS
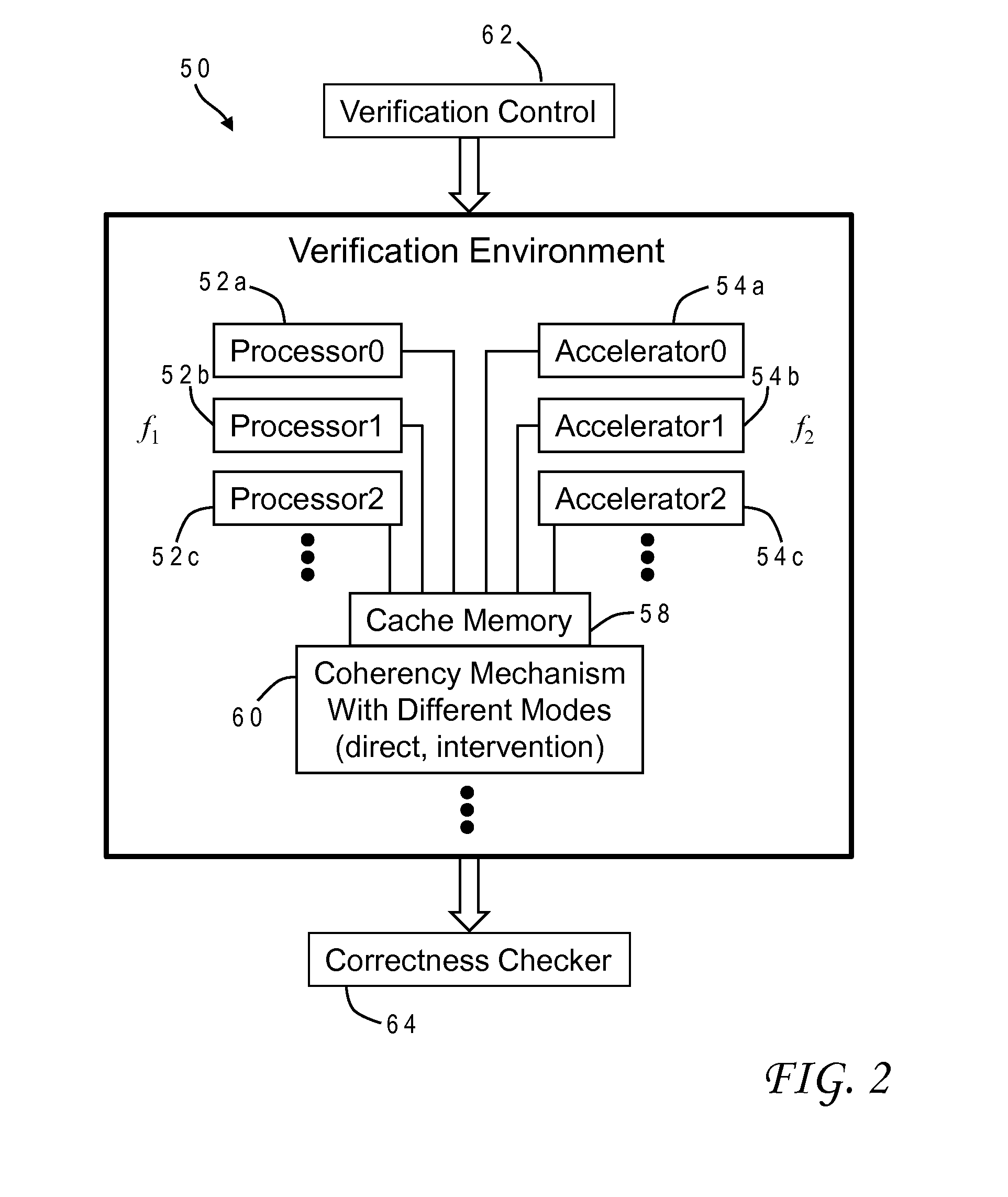
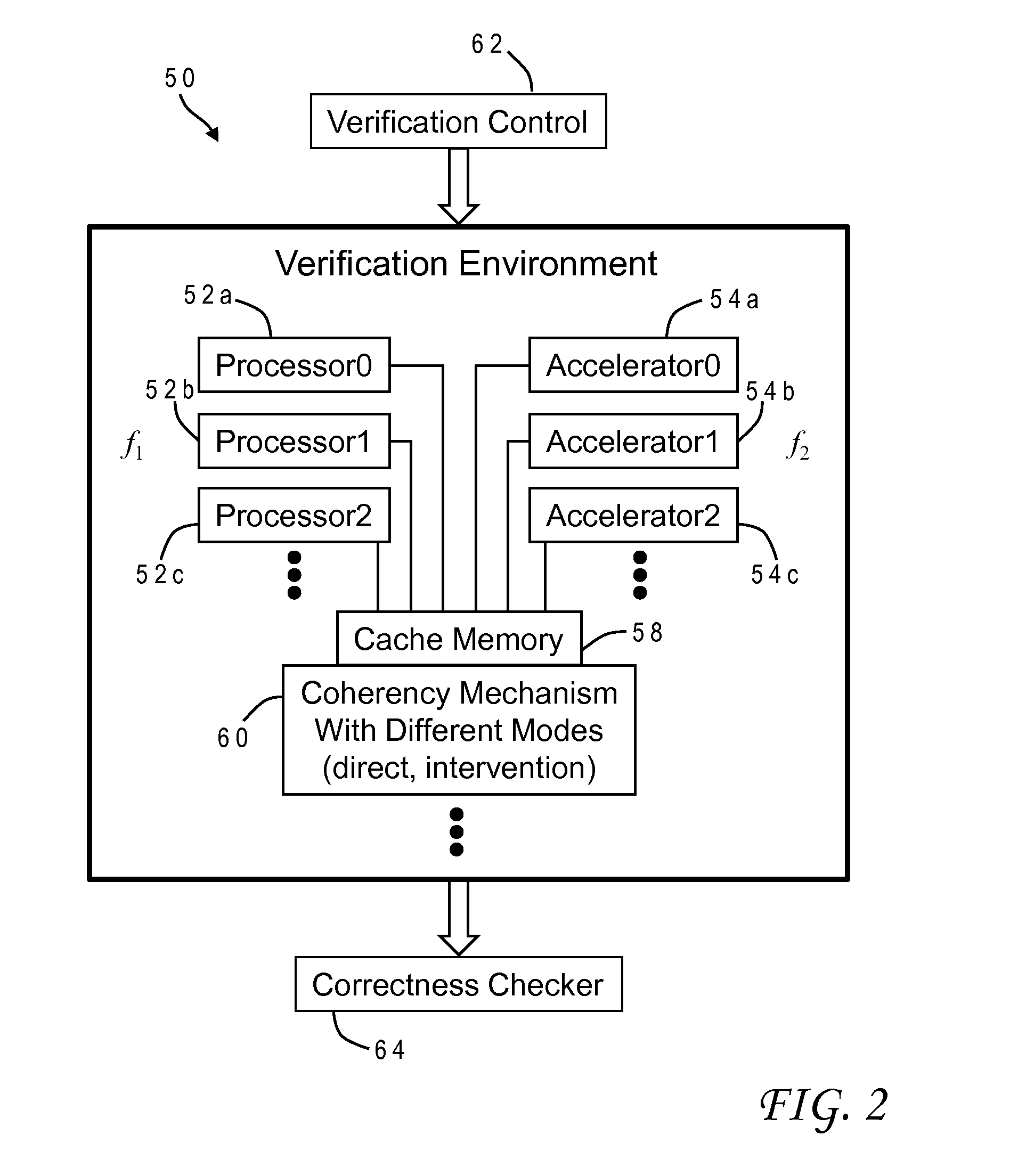
Efficient validation of coherency between processor cores and accelerators in computer systems
ActiveUS20140237194A1Maintain data consistencyVerify correctnessMemory adressing/allocation/relocationComputer system designAs Directed
A method of testing cache coherency in a computer system design allocates different portions of a single cache line for use by accelerators and processors. The different portions of the cache line can have different sizes, and the processors and accelerators can operate in the simulation at different frequencies. The verification system can control execution of the instructions to invoke different modes of the coherency mechanism such as direct memory access or cache intervention. The invention provides a further opportunity to test any accelerator having an original function and an inverse function by allocating cache lines to generate an original function output, allocating cache lines to generate an inverse function output based on the original function output, and verifying correctness of the original and inverse functions by comparing the inverse function output to the original function input.
Owner:GLOBALFOUNDRIES US INC
Method and System for Autonomic Verification of HDL Models Using Real-Time Statistical Analysis and Layered Feedback Stages
InactiveUS20090249123A1High bandwidthOvercomes shortcomingElectronic circuit testingFault responseSelf-healingComputer system design
Real-time statistical analysis is used to perform autonomic self-healing within the context of a 3-tier regression system for analysis of a computer system design component. Throughout the system, there are mechanisms for implementing self-healing if breakage is detected. The regression layer with the highest throughput is maintained in a much cleaner state than otherwise, thereby creating a more efficient environment for identifying and removing defects in the design.
Owner:GLOBALFOUNDRIES INC
Efficient validation of coherency between processor cores and accelerators in computer systems
InactiveUS20140236561A1Maintain data consistencyVerify correctnessMemory adressing/allocation/relocationDesign optimisation/simulationComputer system designAs Directed
A method of testing cache coherency in a computer system design allocates different portions of a single cache line for use by accelerators and processors. The different portions of the cache line can have different sizes, and the processors and accelerators can operate in the simulation at different frequencies. The verification system can control execution of the instructions to invoke different modes of the coherency mechanism such as direct memory access or cache intervention. The invention provides a further opportunity to test any accelerator having an original function and an inverse function by allocating cache lines to generate an original function output, allocating cache lines to generate an inverse function output based on the original function output, and verifying correctness of the original and inverse functions by comparing the inverse function output to the original function input.
Owner:GLOBALFOUNDRIES INC
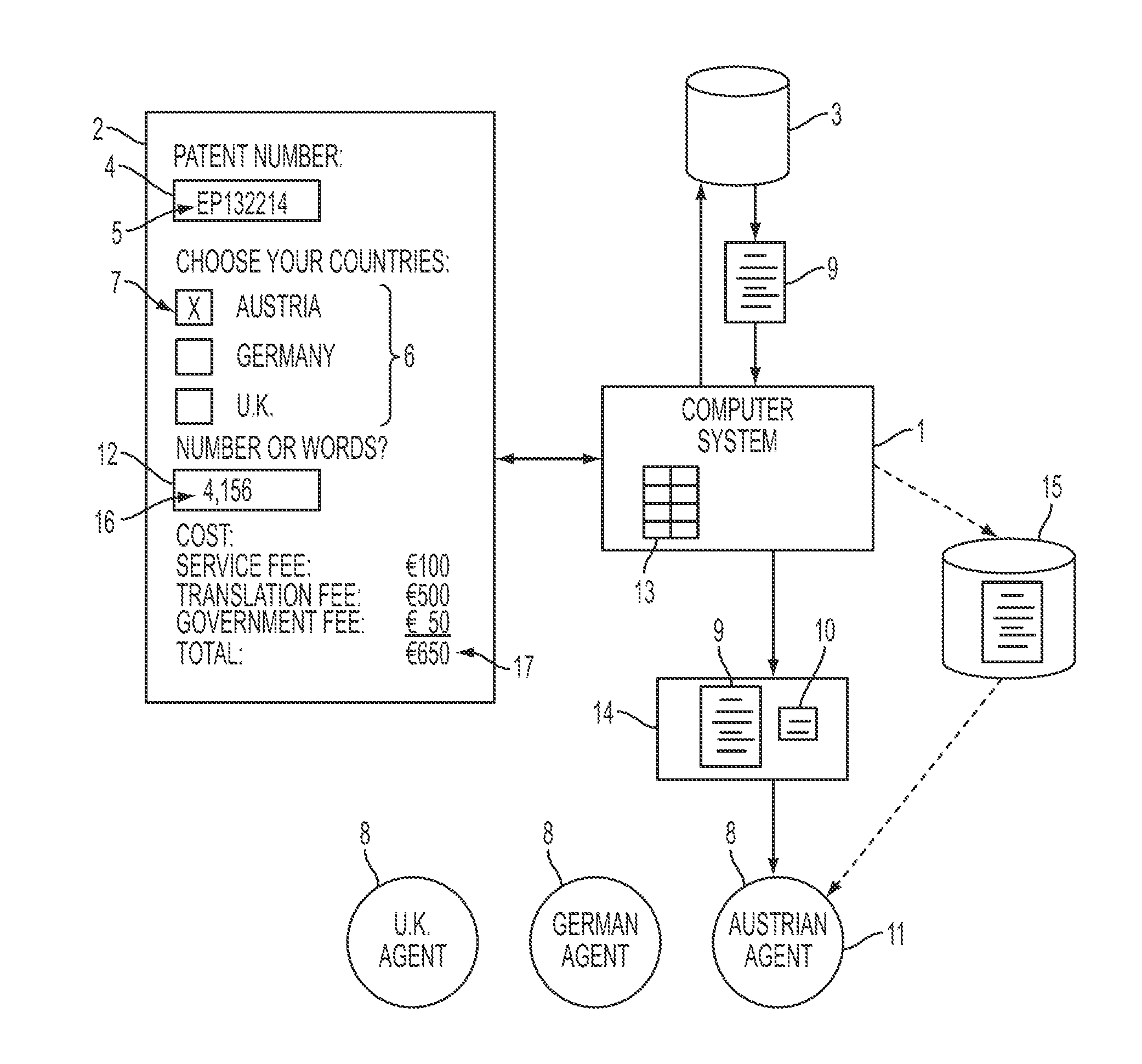
Computer system for distributing a validation instruction message
InactiveUS20130144810A1Office automationElectric/magnetic computingComputer system designComputerized system
A computer-implemented system for providing validation instructions to European attorneys. The computer system is designed to send a validation instruction message to a number of European attorneys, asking them to validate a granted European patent. The computer system is designed to communicate with an interface, a specification database and a number of European agents. The system is set up so that when the computer system receives a European patent identifier and a country selection via the interface, the computer system: (a) obtains, from the specification database, a European patent specification corresponding to the European patent identifier; and (b) provides the European patent specification and a validation instruction message to a particular European agent corresponding to the country selection. The system is further adapted to calculate and bill the total validation cost up-front.
Owner:INOVIA HOLDINGS PTY LTD
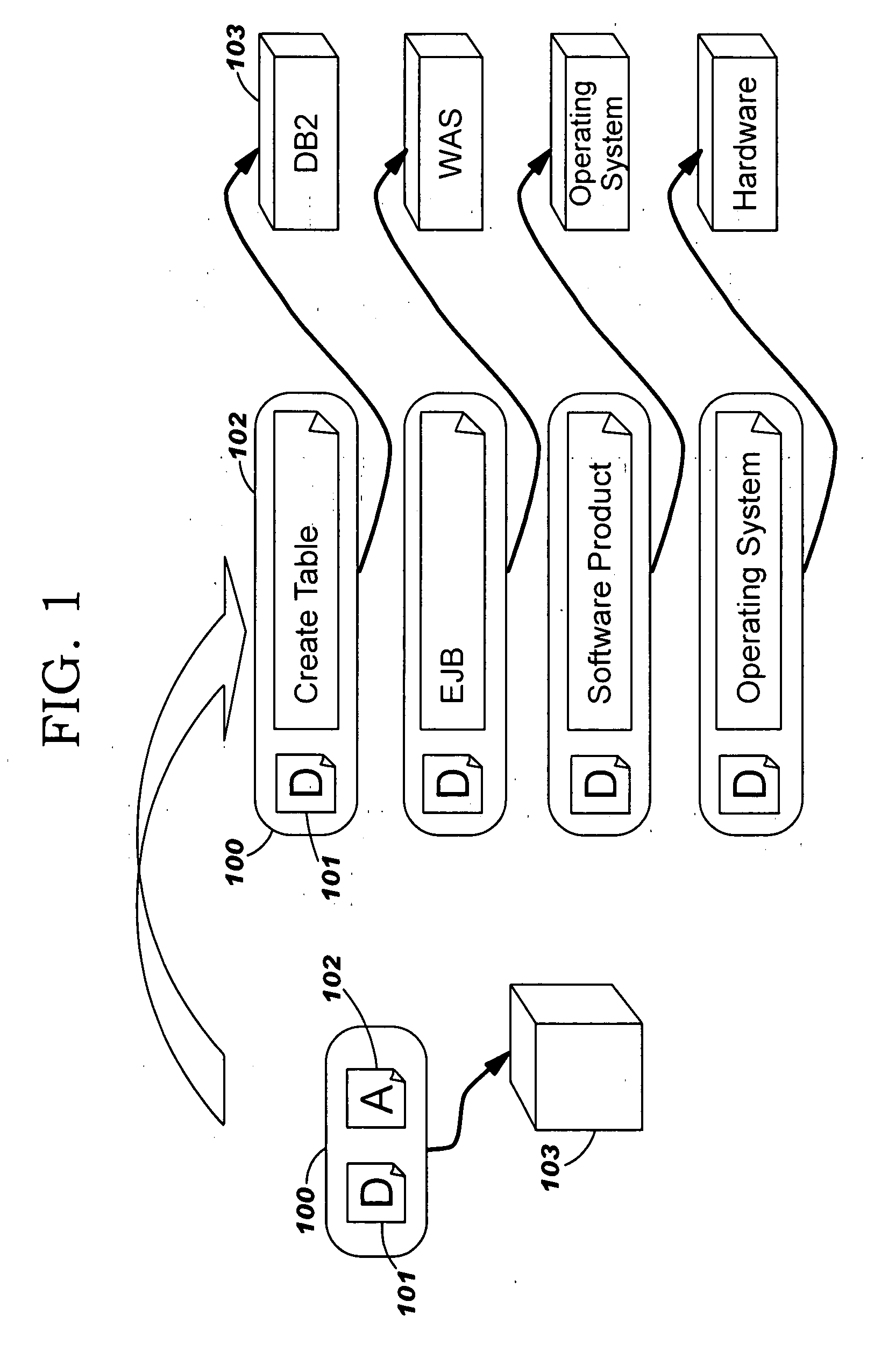
Describing Runtime Components of a Solution for a Computer System
InactiveUS20050278694A1Specific program execution arrangementsMemory systemsComputer system designSoftware engineering
An apparatus for describing runtime components of a solution on a computer system comprises a description of the software components of a solution instance comprising relationships between the software components. The description may be a logical description independent of a particular physical instantiation of the solution instance.
Owner:IBM CORP
Computer systems, methods and programs for providing uniform access to configurable objects derived from disparate sources
ActiveUS7353237B2Avoid wastingEasy to adjustData processing applicationsSpecific program execution arrangementsUniform memory accessProgramming language
Owner:SAP AG
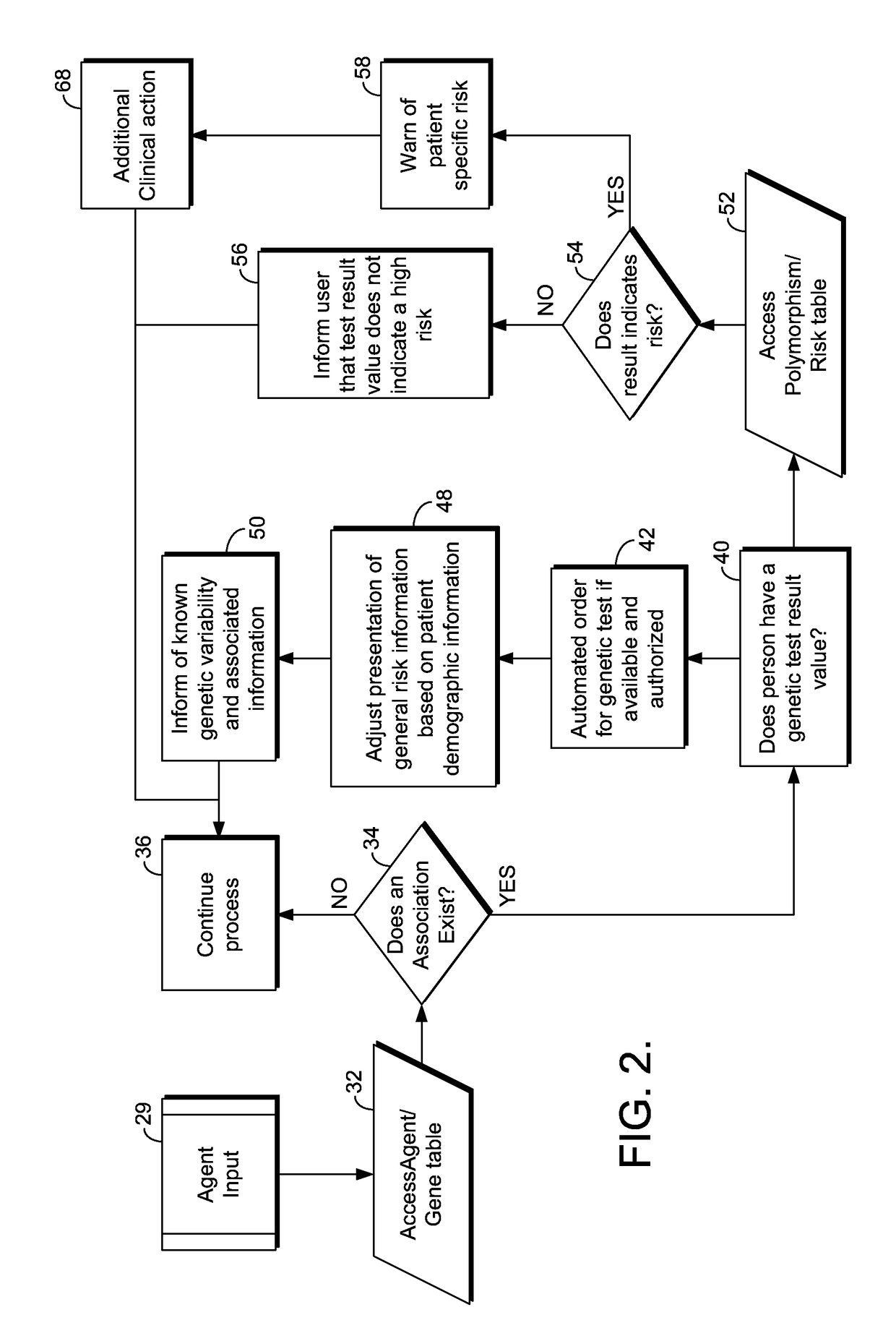
Computer System for Providing Information about the Risk of an Atypical Clinical Event Based Upon Genetic Information
InactiveUS20170213011A1Medical communicationHealth-index calculationMedical recordComputer system design
Processes implemented within a computer system for preventing atypical clinical events resulting from administering unsuitable clinical agent(s) are provided. Initially, the processes involve receiving a list of possible clinical agent(s) that may be administered to a patient during a medical procedure. The processes further involve acquiring heredity data associated with the clinical agent(s) by comparing the clinical agent(s) against a data set or the patient's medical records. If the heredity data indicates that the patient scheduled to receive the clinical agent(s) would experience atypical clinical events as a potential outcome, a warning that the clinical agent(s) should not be administered by a clinician is presented or reference information about the atypical clinical event is output. Accordingly, a preemptive determination of the atypical clinical events potentially occurring upon administering the clinical agent(s) to the patient is made.
Owner:CERNER INNOVATION
System and method for enhancing elevator positioning
PendingUS20190062105A1Enhancing elevator positioningPrecise positioningImage enhancementImage analysisComputer system designSystems design
A method and a system for enhancing elevator positioning includes a camera system designed to record pictures and a computer system designed to determine an absolute distance or a distance between two elements of the recorded pictures. The device is designed to determine the relative distance between the floor of an elevator car and the floor of a landing.
Owner:KONE CORP
Methods and apparatus for constructing switch arrays for routing of optical signals so as to minimize power dissipation
InactiveUS20050084264A1Multiplex system selection arrangementsOptical multiplexSystems designComputer system design
Techniques and systems for design of optical switch arrays so as to minimize power requirements are described. A design system includes a computer system hosting a design program. The design program receives parameters for the switch array, including a number N of outputs required, and either a maximum number L of stages allowed or maximum and average power requirements allowed. If power requirements are used as parameters, the design program uses N and the power requirements to compute the value of L. The design program then constructs a minimum power sequence of L switches or N switches, whichever is less. If N is less than L+1, N outputs are present and the array is complete. If N is greater than L+1, the design program then adds switches one at a time to the minimum power switch path of the array, until the array provides N outputs.
Owner:LUCENT TECH INC
Method for monitoring SQL statement performance
InactiveCN103793526AAvoid full table scanEasy to customizeError detection/correctionSpecial data processing applicationsComputer system designOperational system
The invention provides a method for monitoring SQL statement performance, and belongs to the field of computer system design and the field of databases. The performance of related SQL statements is monitored by reading a data dictionary of oracle and performance data of the operating system-level, and the dependence on a graphic interface tool is reduced. The method solves the problems that a traditional imaging management tool is high in cost and hard to manage, and the processing time of database maintenance workers is shortened.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Method for replacing storage based on Oracle ASM
InactiveCN104573052AAvoid human errorGuaranteed stabilityInput/output to record carriersSpecial data processing applicationsSystems designComputer system design
The invention discloses a method for replacing the storage based on Oracle ASM and relates to the field of computer system design and databases. The method includes utilizing the Rebalance characteristic of the data file storage mode ASM of the Oracle database to add a newly stored disk into an ASM disk group where a database document of the database system is stored, and then deleting the stored disk to be replaced from the ASM disks, wherein ASM automatically distributes deleted disk data in the ASM disk group on the surplus disks of the ASM disk group in balance to achieve storage replacement. The method is achieved through the Oracle ASM automatically, manual error operation is avoided as much as possible, meanwhile non-breaking storage replacement in business production system is achieved, system working stability is ensured, and the system storage and replacement efficiency is improved.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
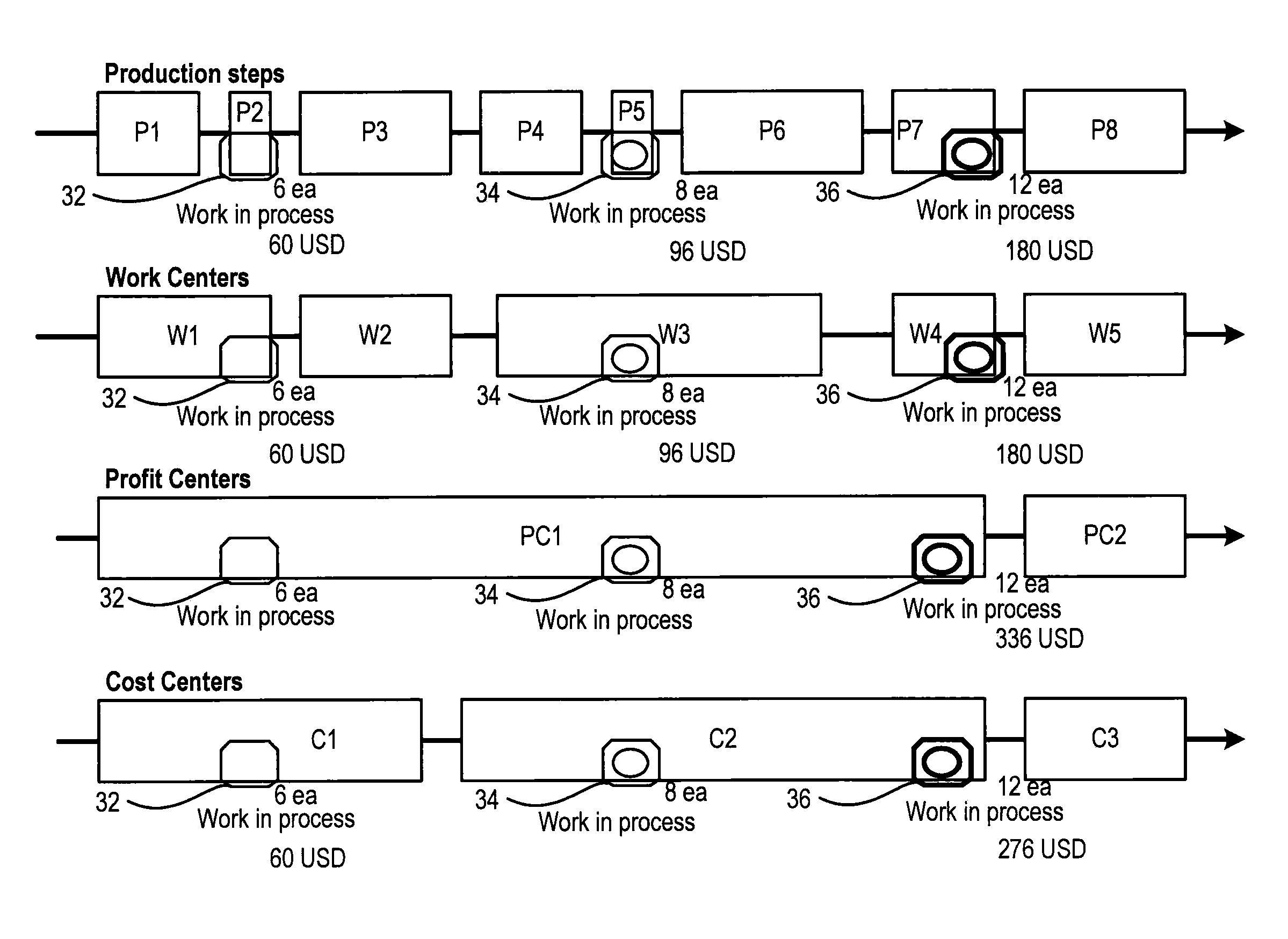
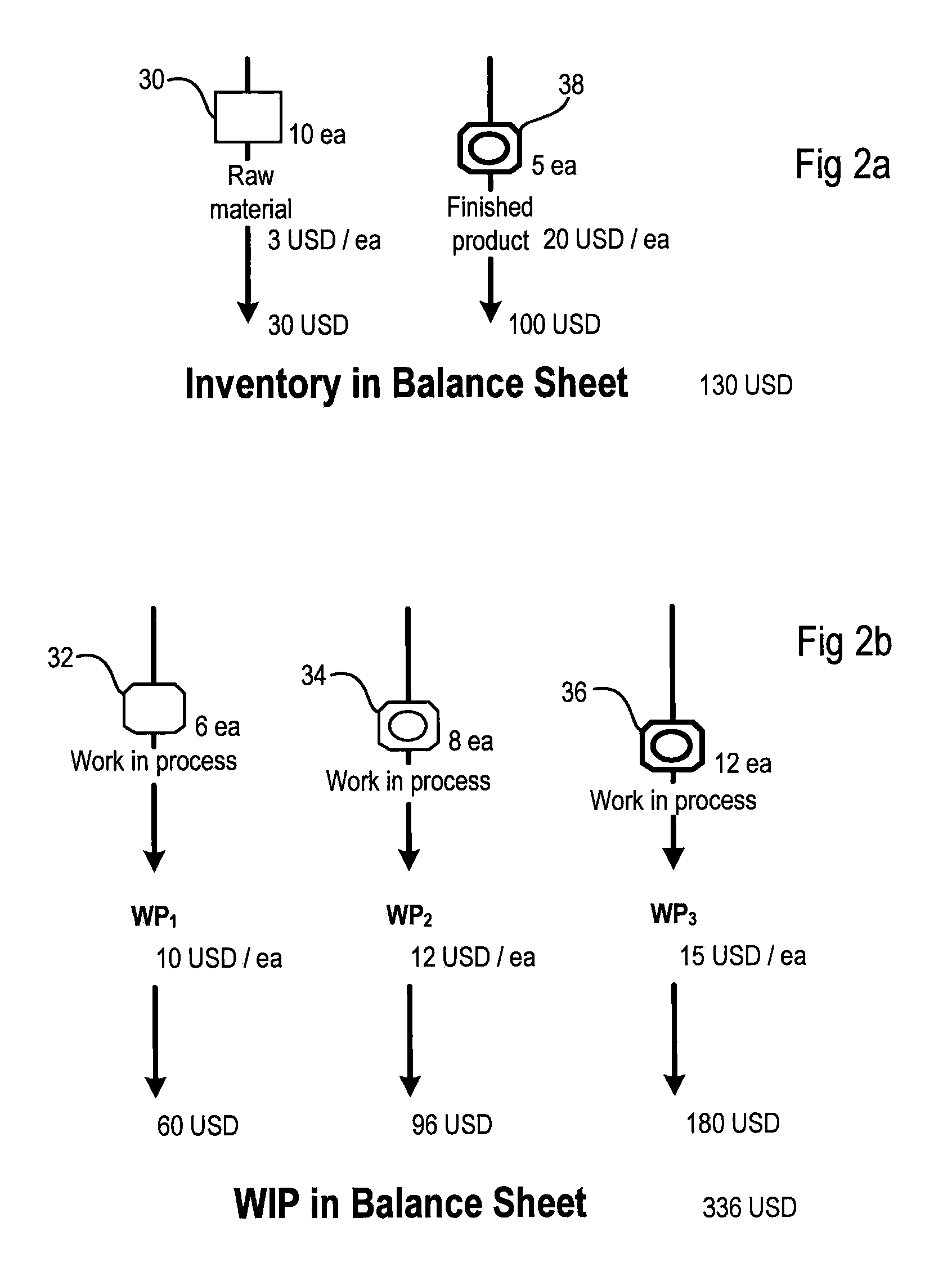
Computer-implemented methods and computer systems for managing and valuating inventory
ActiveUS8843403B2LogisticsSpecial data processing applicationsComputer system designComputer science
Methods and computer systems are provided managing and valuating inventory. In one embodiment, a computer system may assign every item of goods which is entering a working process to an identifier. The computer system may then track the goods in the working process. Further, the computer system may update a given identifier when the goods assigned to this identifier enter another stage in the working process, assign at least one price to each stage in the working process, determine the content of one or more identifiers, and calculate a price for goods in the working process.
Owner:SAP AG
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com