A method for defending against denial of service attacks based on cloud computing platform
A denial of service attack and cloud computing platform technology, applied in the field of information security, can solve the problems of high harm, low attack rate, and few attack launching nodes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
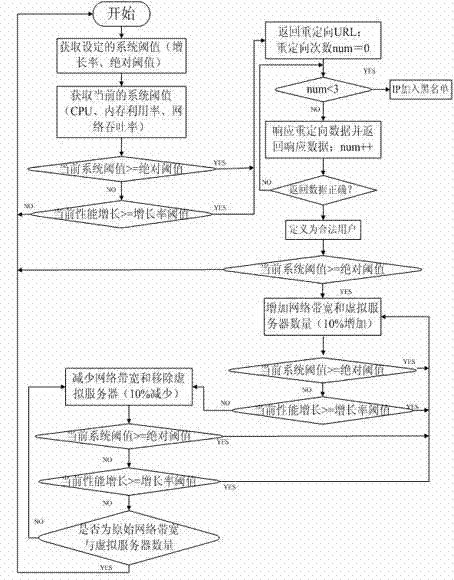
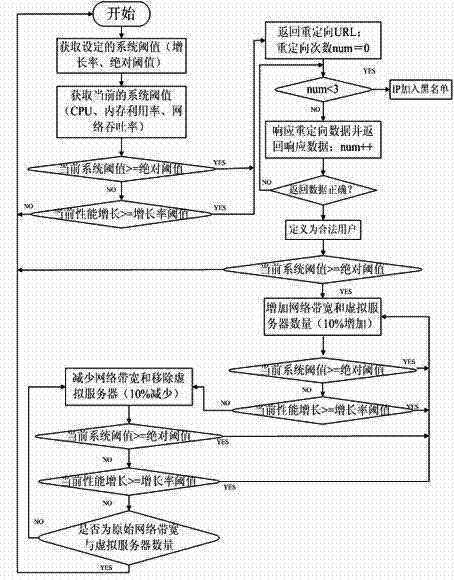
[0032] Method of the present invention is:
[0033] Step 1. Monitor the server to obtain the current system performance (CPU, memory utilization, network throughput) information and performance growth rate;
[0034] Step 2. Start the defense system when the system performance threshold or growth threshold is higher than the highest threshold;
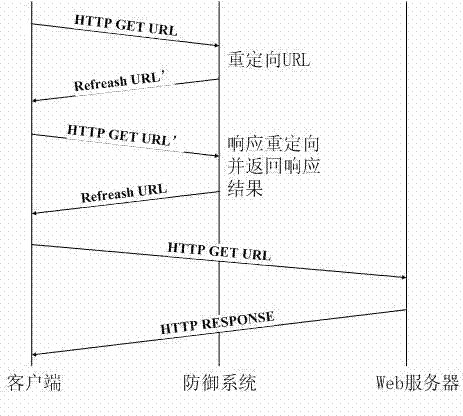
[0035] Step 3. After the client establishes a TCP connection with the server, the defense system intercepts its GET request to the URL sent by the server;
[0036] Step 4. The defense system returns to the client a packet containing a cookie redirected to the URL. And define the redirection times num=0;
[0037] Step 5. In the case of the number of redirections num<3, if the client is a legal host, it will respond to the redirection data packet according to the rules of the HTTP protocol; if the client is a zombie host, it cannot respond to this Redirect data packets to respond or respond to errors; redirection times num++;
[0038]...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com