Method and system of preventing files from being damaged by malicious operation behaviors
A malicious operation and file technology, applied in the field of information security, can solve the problems of affecting file operation, unable to control illegal operation of illegal programs, unable to guarantee the normal operation behavior of whitelisted programs, etc., to achieve the effect of reducing the frequency of risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] The present invention will be further described in detail below in conjunction with examples, but the embodiments of the present invention are not limited thereto.
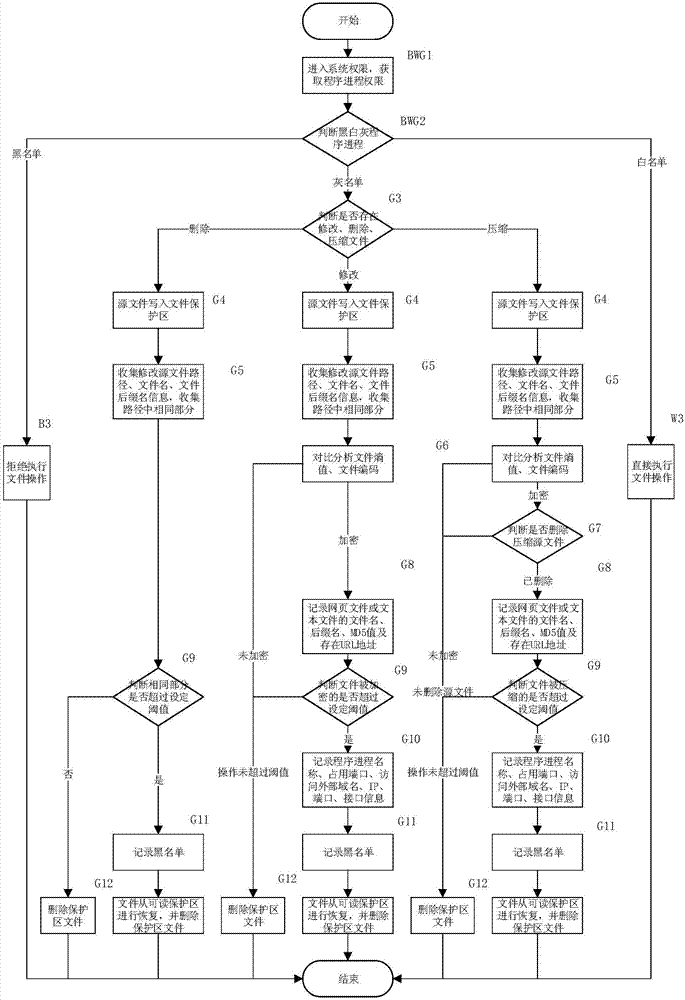
[0044] A method of protecting files from corruption by malicious manipulation, comprising:
[0045] If there is a process of deleting files, the whitelist program can directly delete the file, the blacklist program directly prevents file deletion, and the gray list program suspends the process and backs up the file to the readable protection area, and releases the process after the backup is completed.
[0046] If there is a process of modifying the file, the whitelist program will allow it, and the blacklist program will directly prevent the file from being modified. The gray list will suspend the process and back up the file to the readable protection area. After the backup is completed, the process will be released. Value comparison results to determine whether the current process has performed an encryp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com