System and method for creating a secure trusted social network
a social network and social network technology, applied in the field of system and method for creating a secure trusted social network, can solve the problems of not offering the same performance under heavy loads, server and bandwidth required to service the number of requests must also be able to scale, and the lack of security, control and authenticity of the requested files
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
example 1f
Sharing Bookmarks and World Wide Web Links on a Trusted Network
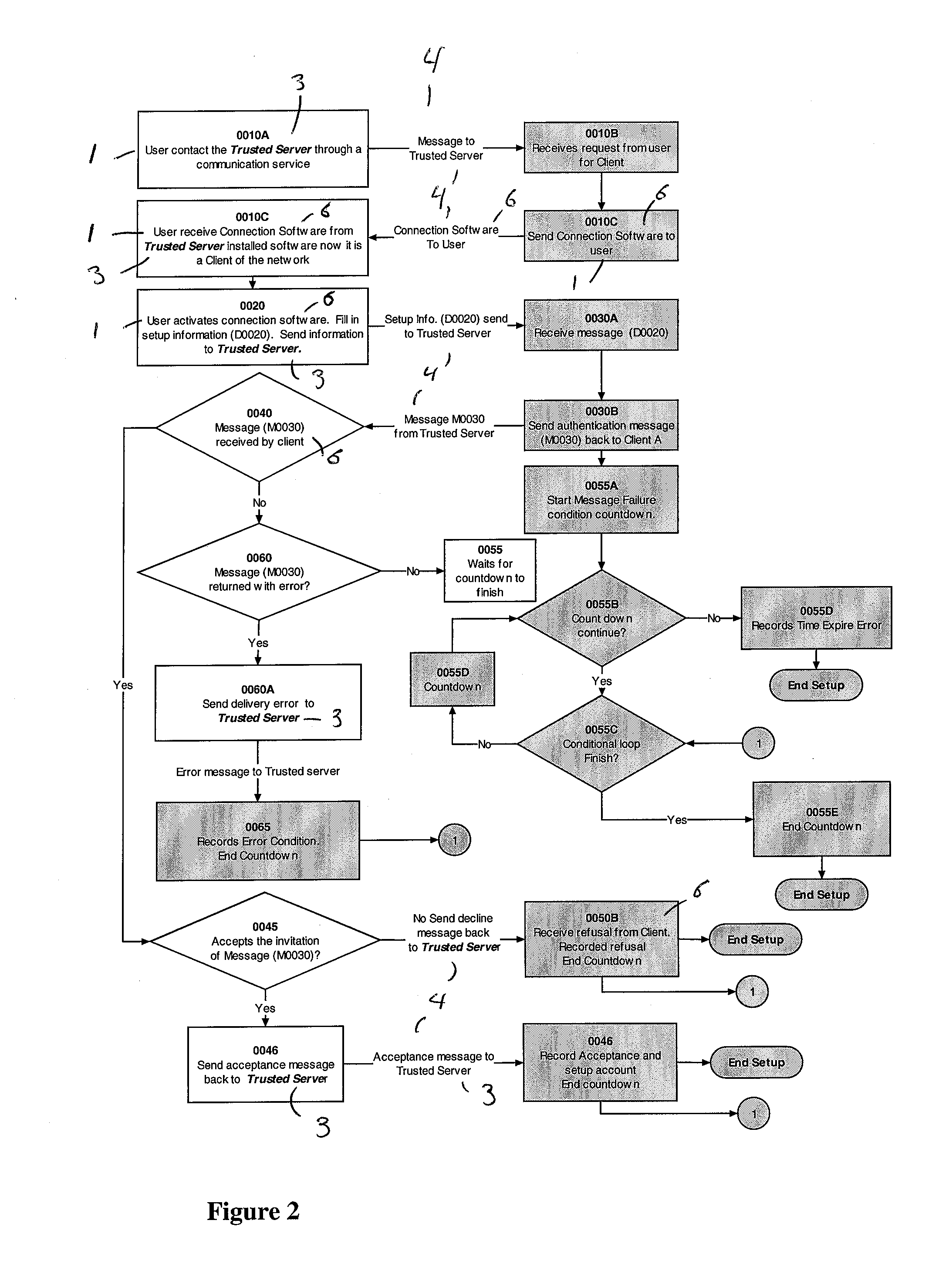
[0243] In a more specific example of collaboration, User A uses a trusted Peer-to-Peer network to create and share a series of bookmarks and World Wide Web (WWW) links. User A first defines a collection of bookmarks or WWW links that they want to share with their trusted peers. User A then marks the collection of bookmarks with the appropriate access permissions, in this case N=0. User A further decides that other users can add to the bookmark collection but may not delete from the collection, nor delete the collection entirely. Access permissions for the collection are relayed to the editing server. The editing server sends a message to User A's contact list that there is a collaboration collection of bookmarks available. Trusted peers of User A within the degree of separation of N=0 can obtain the bookmarks from User A through the trusted network. Authorized persons can add to this collection as follows: A user access...
example 1h
Synchronization as Broadcasting
[0247] In this example, the initiator of the synchronization object retains the rights to modify the object while all other trusted individuals can duplicate the object but cannot modify it. In this example, the synchronization feature functions in a fashion that is analogous to broadcasting. In this example, User A has the following groups of trusted peers that have various degree of separation from the A (expressed as a value of “n”).
n = 0n = 1CommentBB1, B2, B3Trusted peers of BCC1, C2, C3Trusted peers of CDD1, D2, D3Trusted peers of DEE1, E2, E3Trusted peers of E
[0248] User A creates a synchronization object using the client software. User A also enters a description of the object, the degree of separation required to access the object (in this case, n=1) and defines this object as the “Master synchronization object”. The client software sends a message to the synchronization server including this information. All of the trusted peers of User A ...
example 2b
Market Based on Transfer of Digital Rights
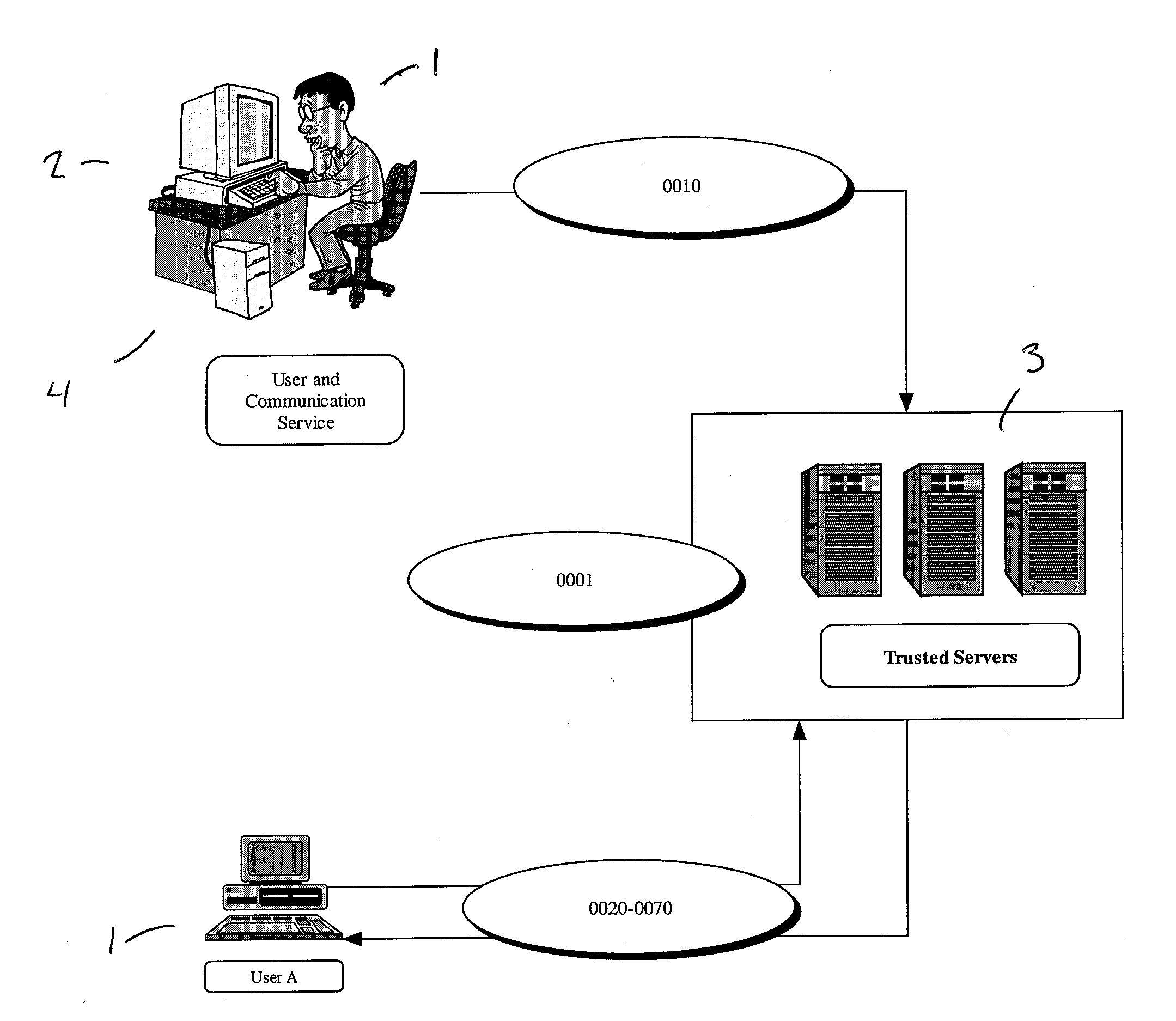
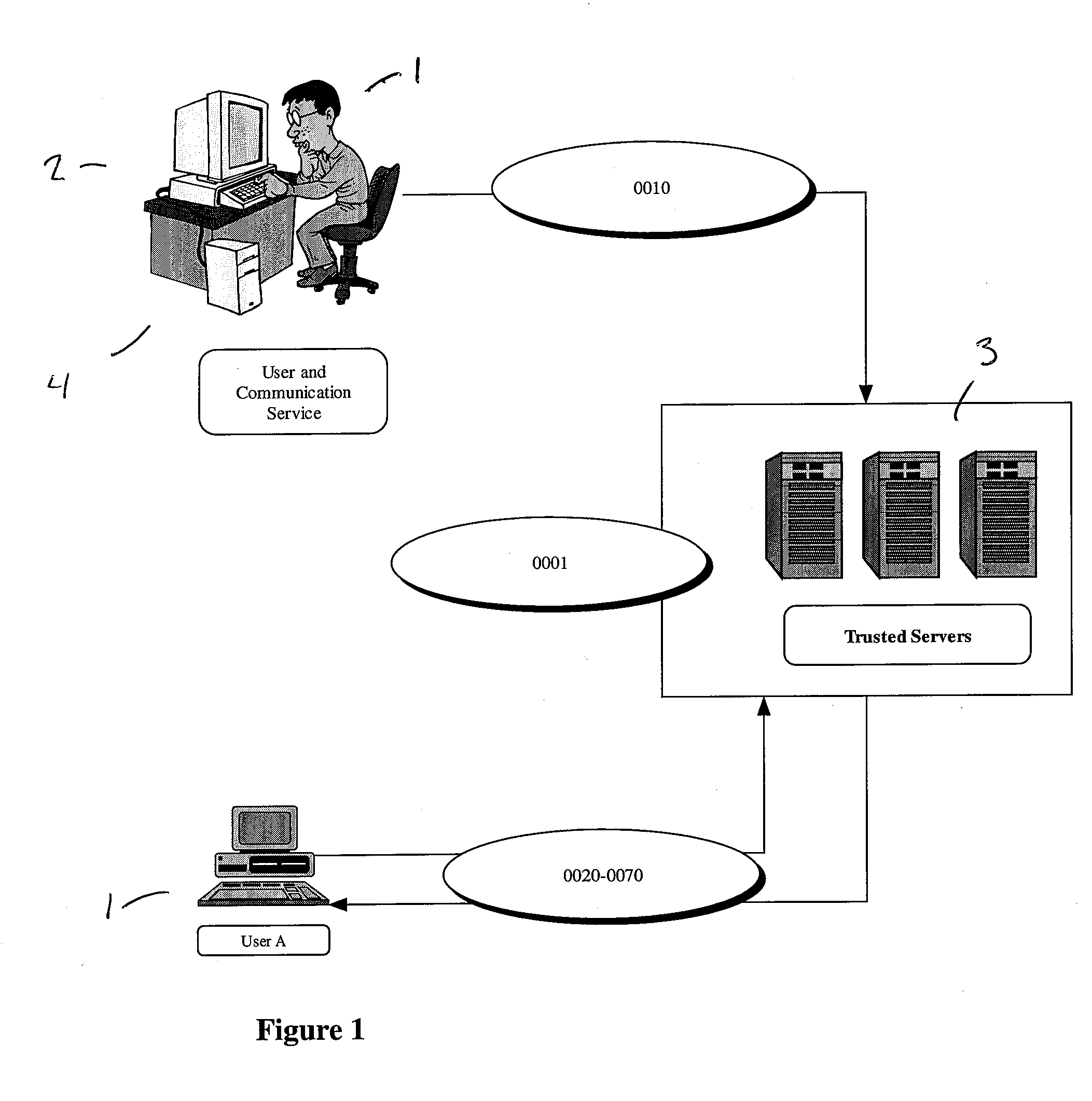
[0260]FIG. 34 illustrates an electronic market built on a trusted social network based on the transfer of digital rights. In this case, the system requires the addition of a DRM (Digital Rights Management) server, to manage the rules and regulations governing the ownership of the object, for example copyrights, licenses and the like. The main components of this system are: [0261] 1. Authentication and Authorization User A 1 is the digital rights holder of an item (such as a digital music file protected by copyright) 120 on a shared folder. User A 1 must first be identified and receive authorization from the trusted servers 3 to access the network.
[0262] 2. Initial DRM information User A 1, sends the Digital Rights Management (DRM) 165 information to the DRM server 160.
[0263] 3. Trusted peer of User A can request and obtain item. A trusted peer of User A 1, defined as User B 9, who is already authorized to be on the system can now obtain t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com