Network N-1 security-region-boundary calculation and security evaluation method
A security evaluation and network security technology, which is applied in the field of N-1 security domain boundary calculation and security evaluation of the network, can solve the problems of large amount of calculation, inconvenient security control, and does not meet real-time online requirements, so as to improve system efficiency. , control and plan intuitive effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] In order to make the object, technical solution and advantages of the present invention clearer, the implementation manner of the present invention will be further described in detail below in conjunction with the accompanying drawings.
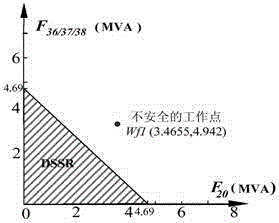
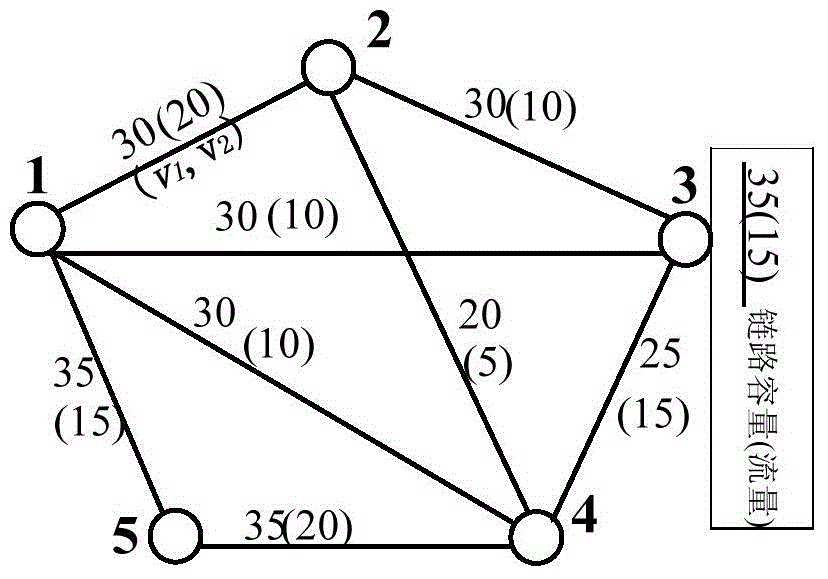
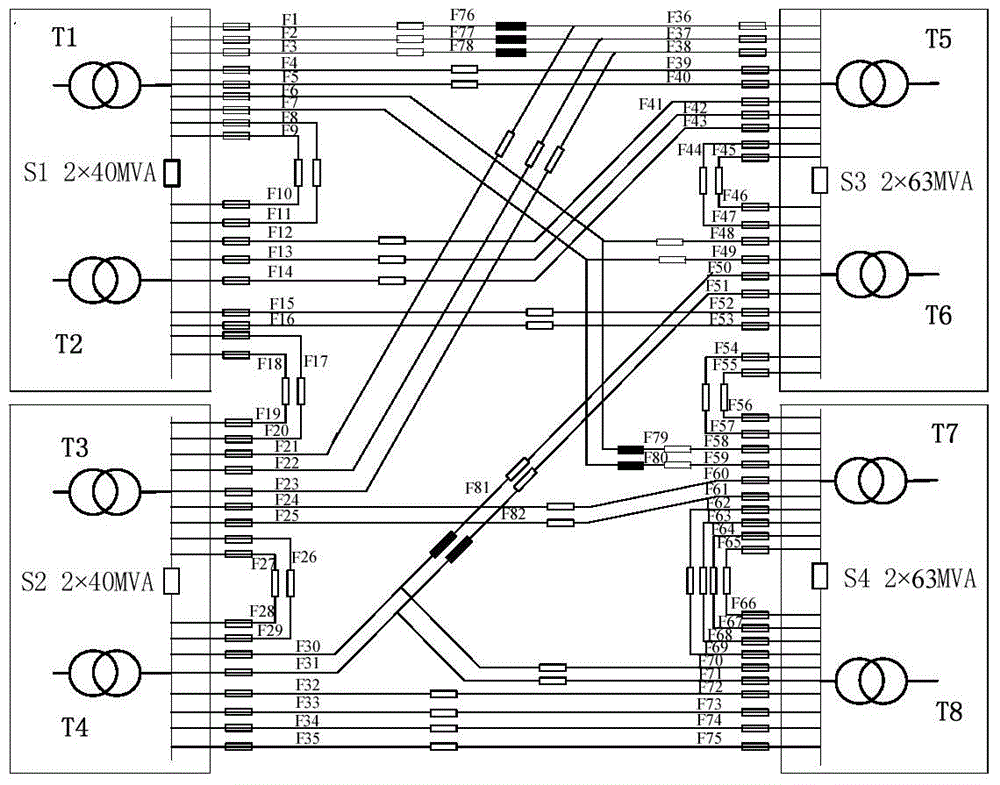
[0043] The present invention proposes a general network-oriented security domain method, whose starting point is different from invulnerability: the method can pre-calculate the security boundary after the network topology structure is given to describe the area where the system as a whole can operate safely [2] . Using the safety domain method, for any given work point, it is possible to quickly judge whether it is safe by calculating the distance from the work point to the safety boundary, that is, the position of the work point in the safety domain, and allow the operator to obtain the overall safety measure of the system, so as to Deciding whether to implement preventive controls and the direction and intensity of controls [2] . ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com