Security measurement method of industrial control system based on attack graph
An industrial control system and security measurement technology, applied in the field of network security, can solve the problems of lack of system-wide security measurement scheme, failure to consider the vulnerability relationship of system equipment, and few security measurement methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
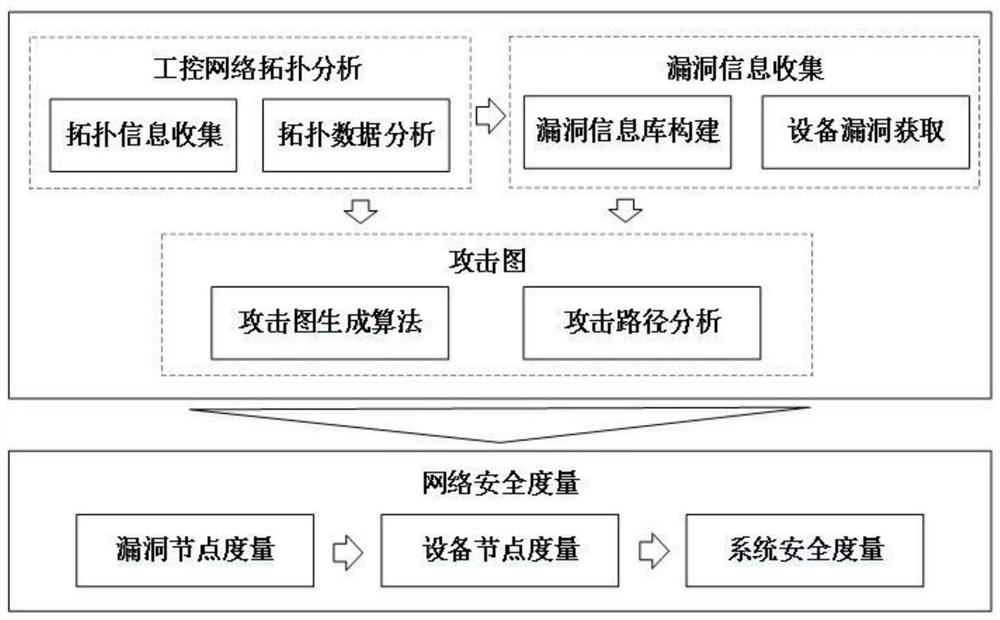
[0084] This embodiment provides an attack graph-based industrial control system security measurement method, which includes the following four steps. The overall architecture of this method is shown as follows figure 1 Shown:
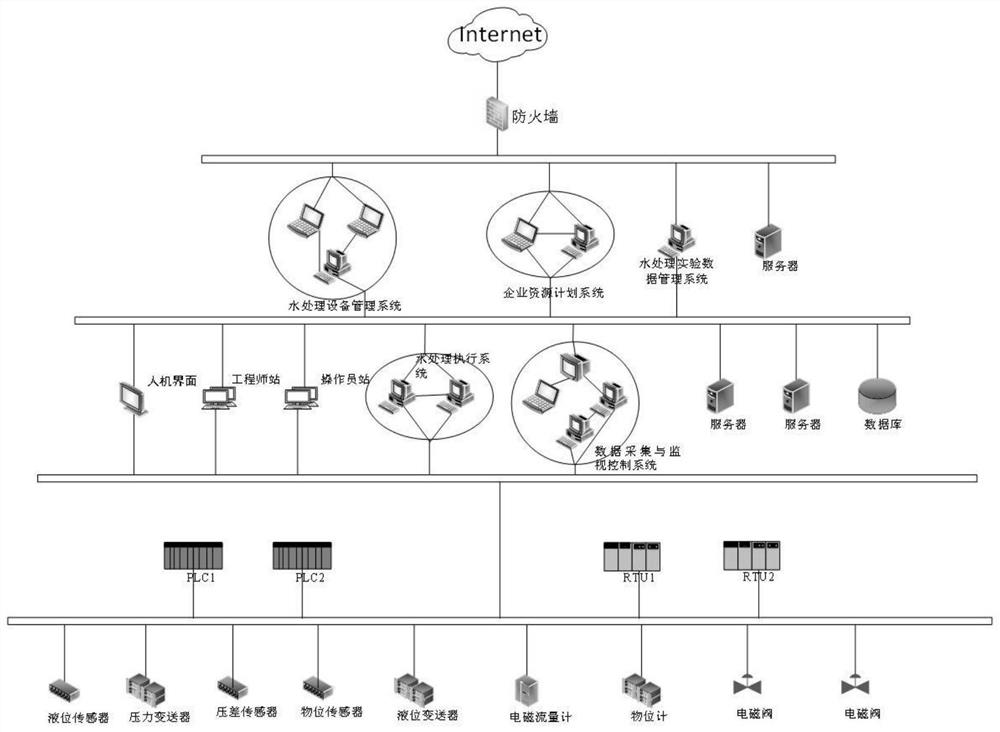
[0085] Step 1: Obtain the topology information of the industrial control network, detect the equipment of a specific industrial control system (that is, the target industrial control system for security measurement), grasp the equipment information in the industrial control network, and analyze the association of the equipment;
[0086] The first step is the foundation, which mainly obtains the self-information and related information of the equipment of the target industrial control system in the entire industrial control network;
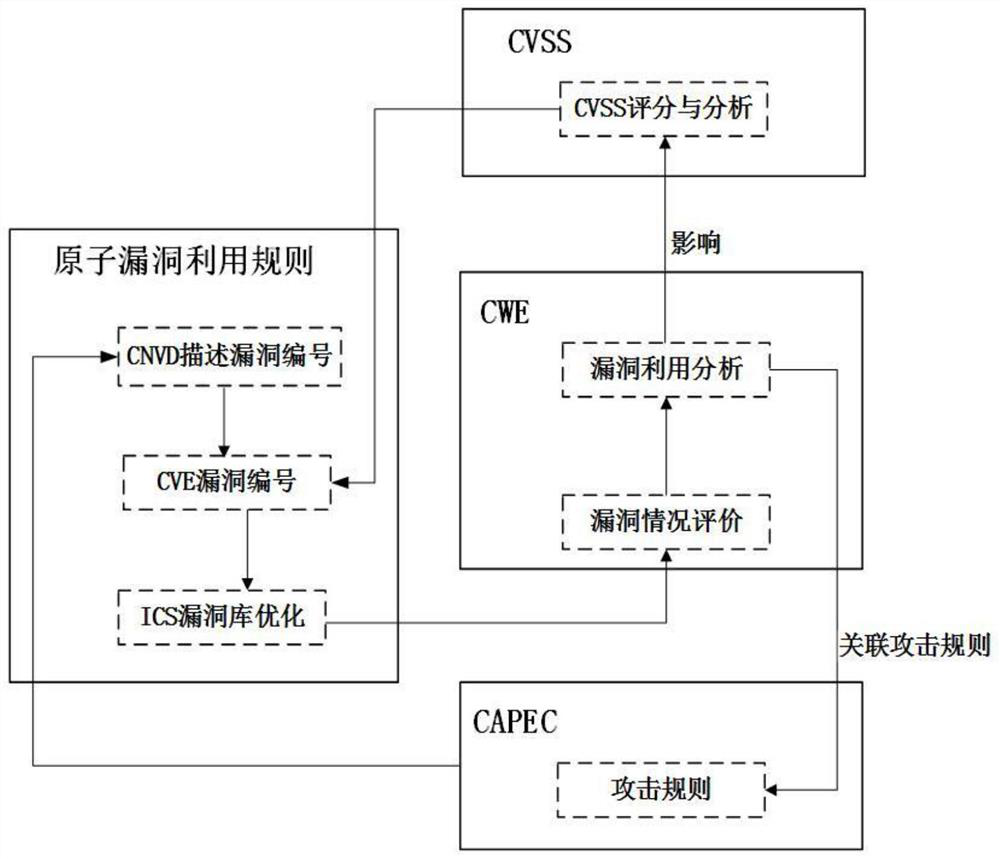
[0087] Step 2. Based on the detection results of the devices in the industrial control network, that is, the device information and association of the specific industrial control system in step 1, collect device vulnerabili...
Embodiment 2
[0153] A server comprising:
[0154] one or more processors;
[0155] a storage device on which one or more programs are stored,
[0156] When the one or more programs are executed by the one or more processors, the one or more processors are made to implement the method for measuring security of an industrial control system based on an attack graph described in Embodiment 1.
Embodiment 3
[0158] A computer-readable medium, on which a computer program is stored, wherein, when the computer program is executed by a processor, the attack graph-based industrial control system security measurement method described in Embodiment 1 is implemented.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com