Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
38 results about "Control system security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Control system security is the prevention of (intentional or unintentional) interference with the proper operation of industrial automation and control systems. These control systems manage essential services including electricity, petroleum production, water, transportation, manufacturing, and communications. They rely on computers, networks, operating systems, applications, and programmable controllers, each of which could contain security vulnerabilities. The 2010 discovery of the Stuxnet worm demonstrated the vulnerability of these systems to cyber incidents. The United States and other governments have passed cyber-security regulations requiring enhanced protection for control systems operating critical infrastructure.
Robot control system
ActiveCN106426184ACost-effectiveHigh speed data exchangeProgramme-controlled manipulatorDual coreMotion planning
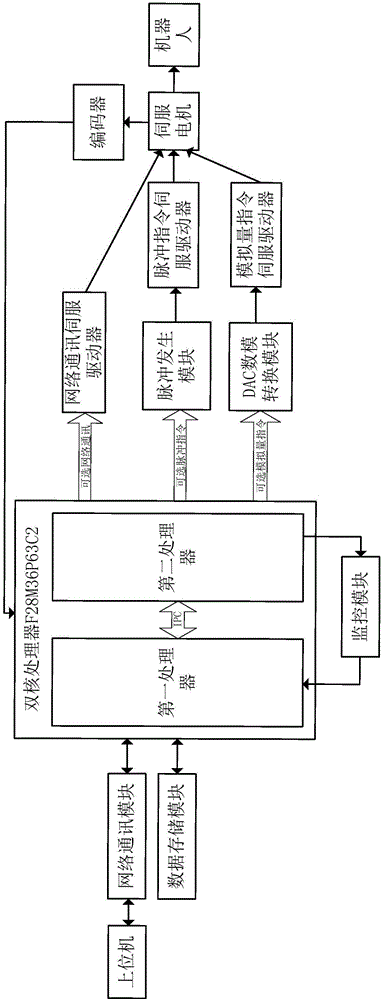
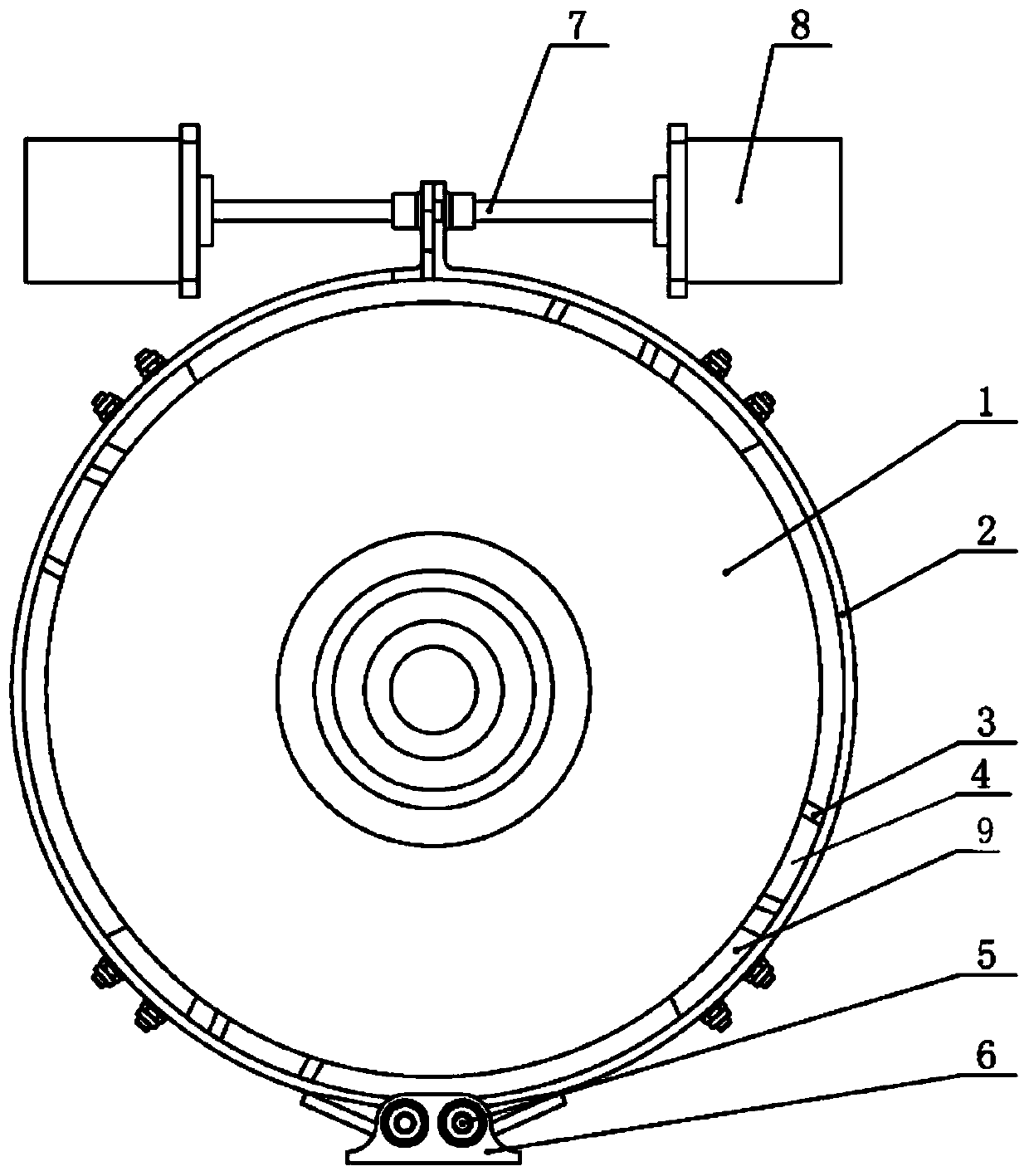
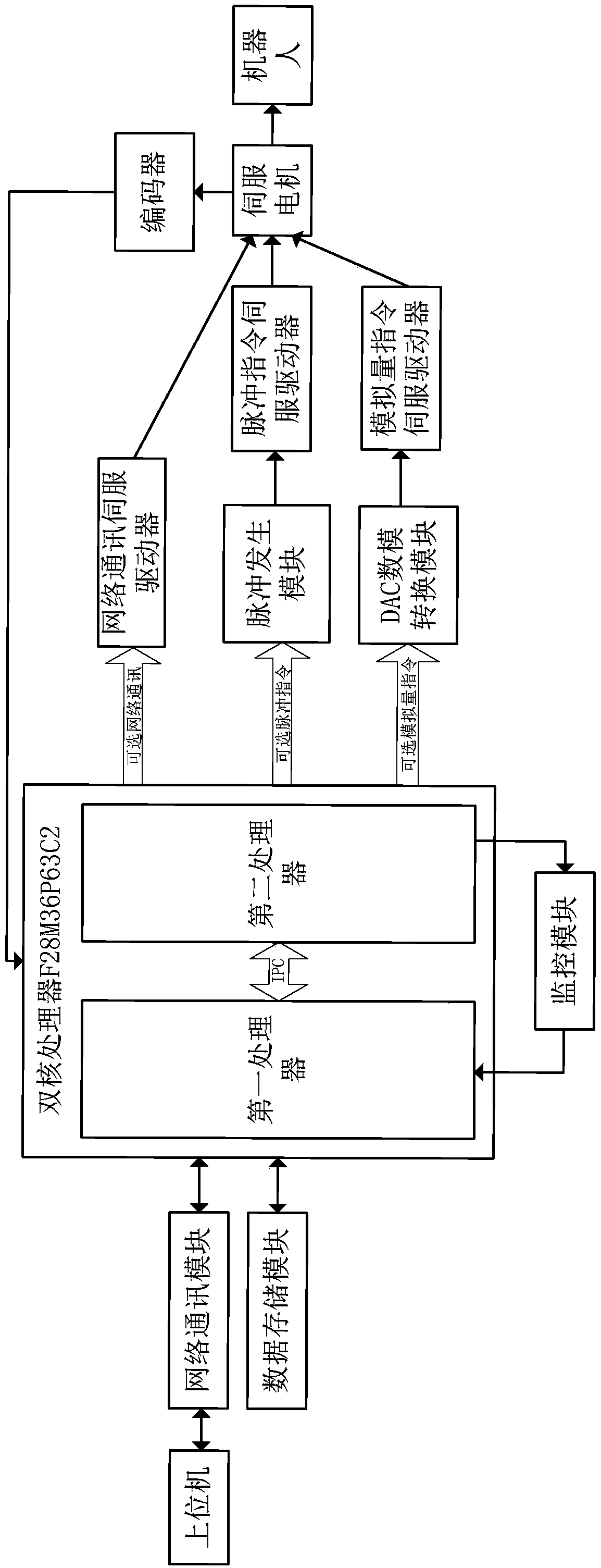
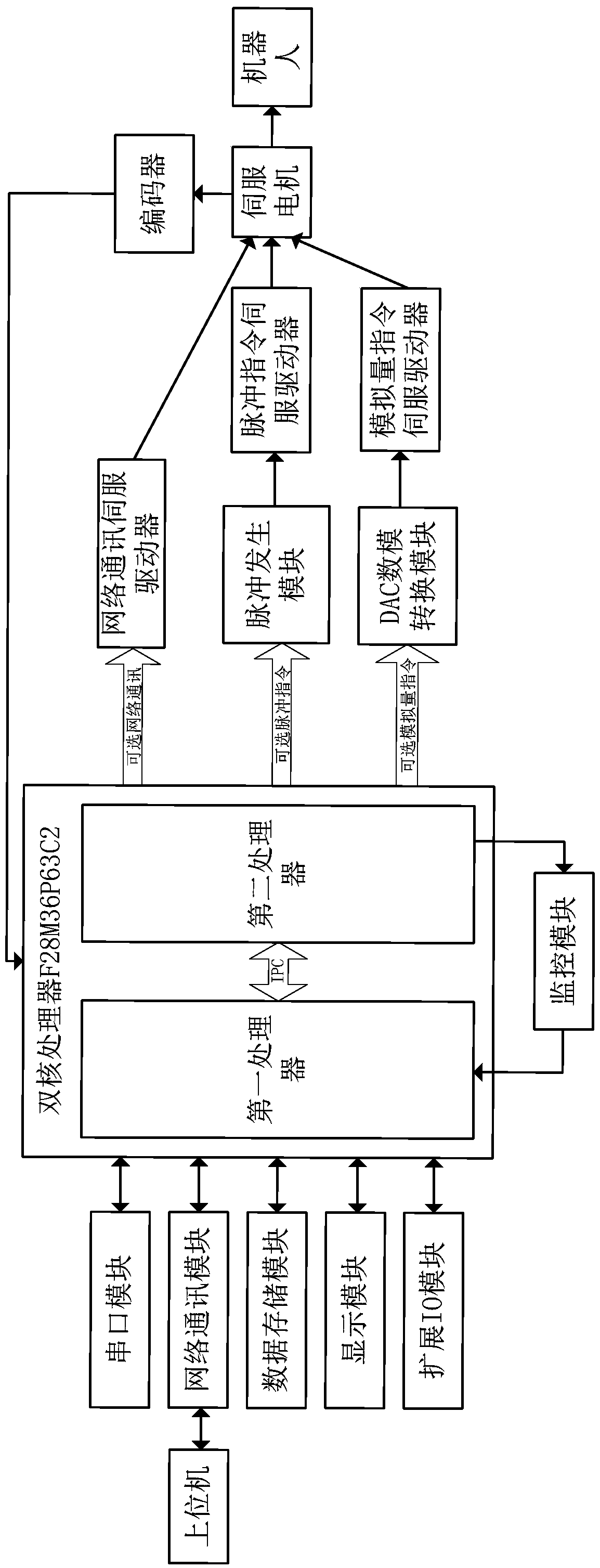
The invention discloses a robot control system which comprises a dual-core processor, wherein the dual-core processor comprises an advanced reduced instruction set computer machine (ARM) processor and a digital signal processor (DSP). According to the robot control system, an ARM+DSP control strategy is adopted; a conventional control mode of industrial computer PC+movement control card+servo drive+servo motor is replaced; an ARM is responsible for movement planning and track planning of a robot; the DSP is responsible for dynamic and kinematic calculation of the robot, the strong calculation performance of the DSP and the peripheral control property of the ARM are sufficiently utilized, and due to the function distribution, the expense of a main control chip can be effectively reduced, a relatively great amount of resources can be used for controlling the security and the precision of the control system, and the cost performance can be greatly improved; the robot control system has EtherNet and pulse analog quantity control modes which can be selected by users, and a servo drive and a servo motor applicable to multiple control modes are provided, so that control methods can be conveniently switched by the users, and relatively good universality can be achieved.
Owner:GUANGZHOU INST OF ADVANCED TECH CHINESE ACAD OF SCI +1
Method and apparatus for combining encryption and steganography in a file control system
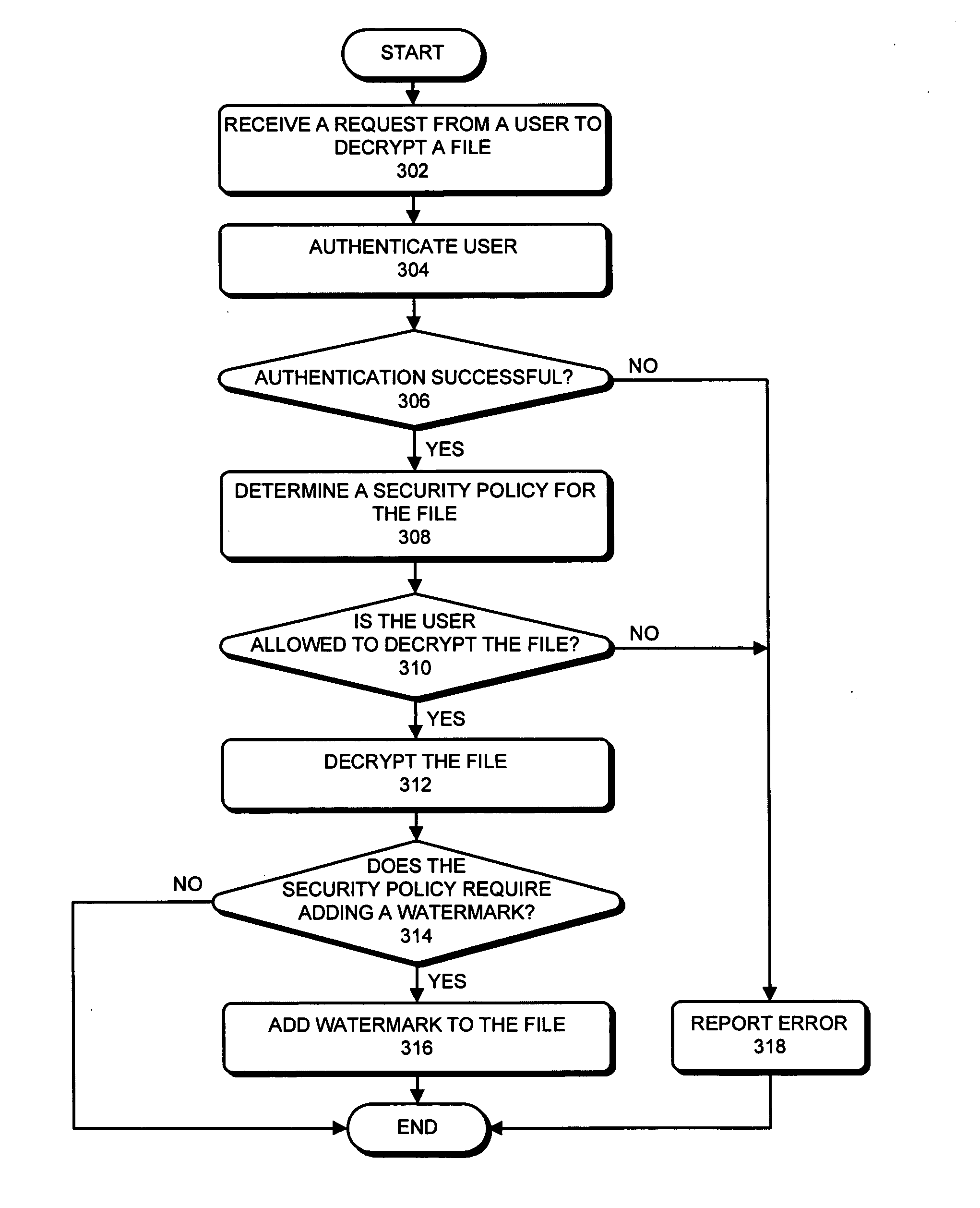
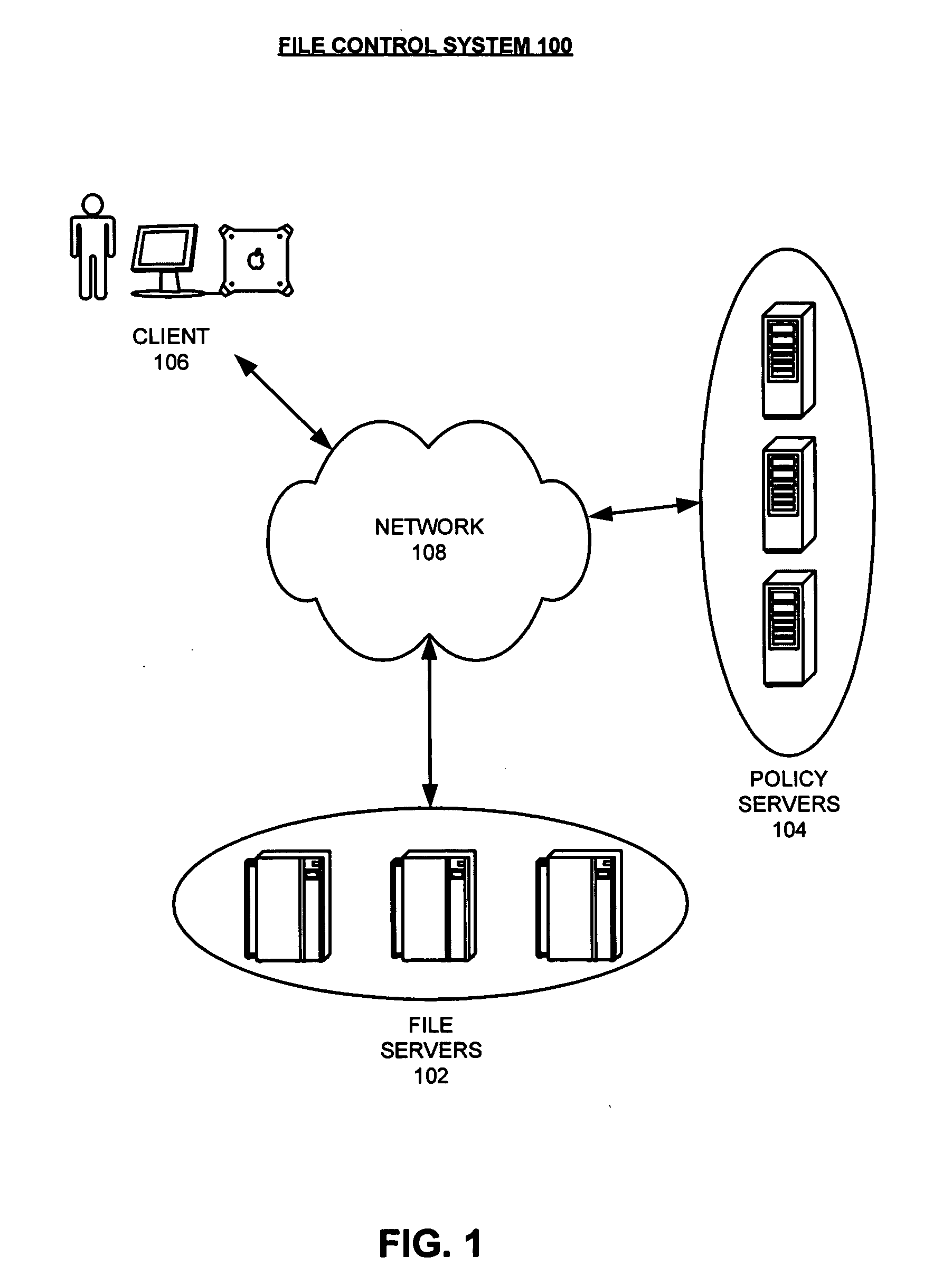
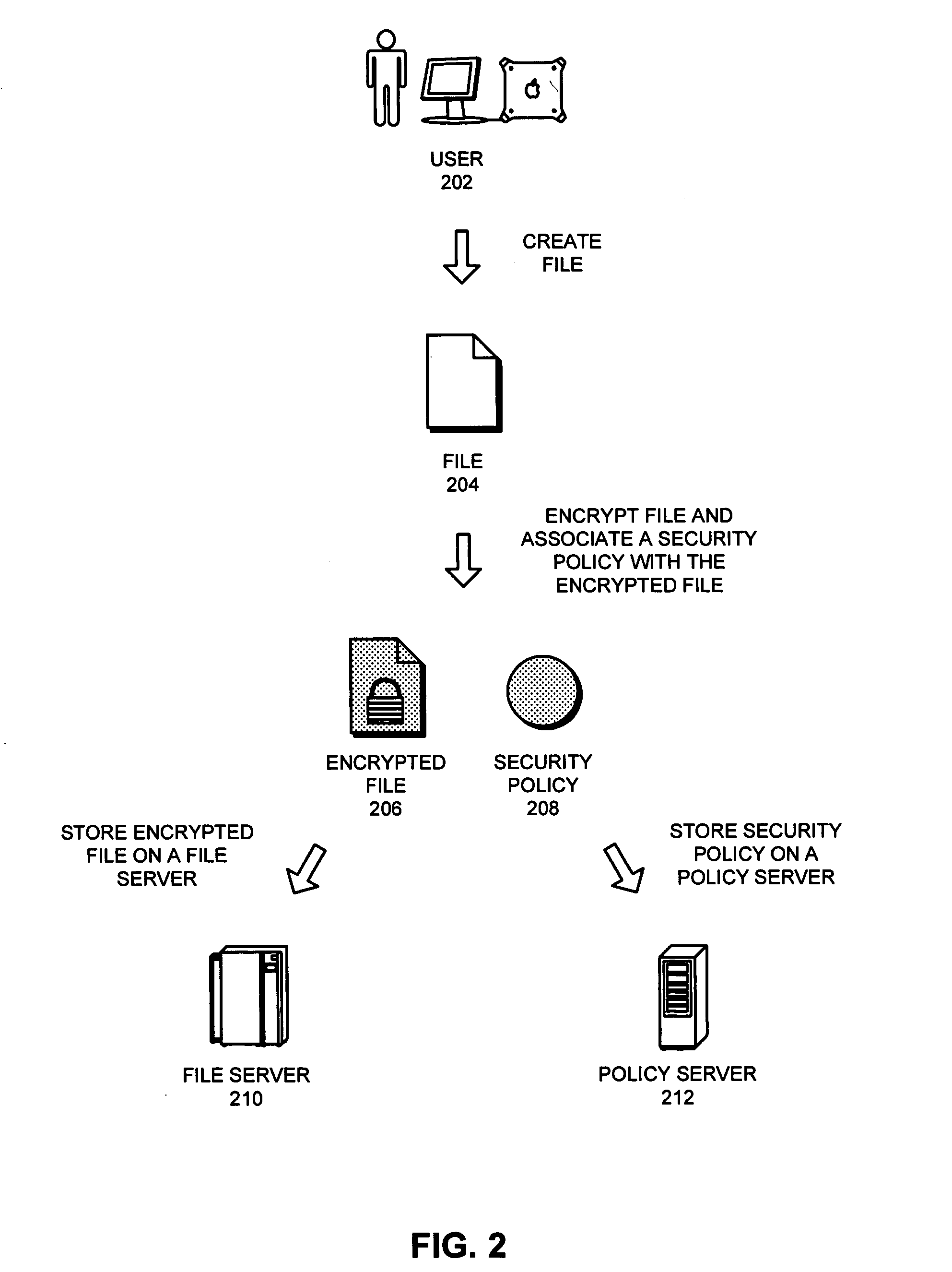
One embodiment of the present invention provides a system that improves security of a file control system. During operation the system receives a request from a user to decrypt a file. The system then decrypts the file. Next, the system adds a watermark to the decrypted file which allows the decrypted file to be subsequently traced back to the origin of the decrypted file, thereby improving security of the file control system. Note that the watermark can include a user identifier, an Internet Protocol (IP) address associated with the user, a hardware address or identifier associated with the user, a timestamp, or any other information that can be used to identify the origin of the decrypted file.
Owner:ADOBE INC
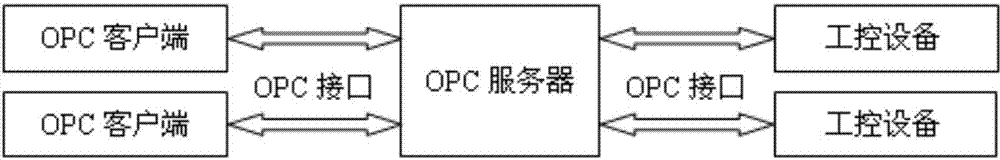
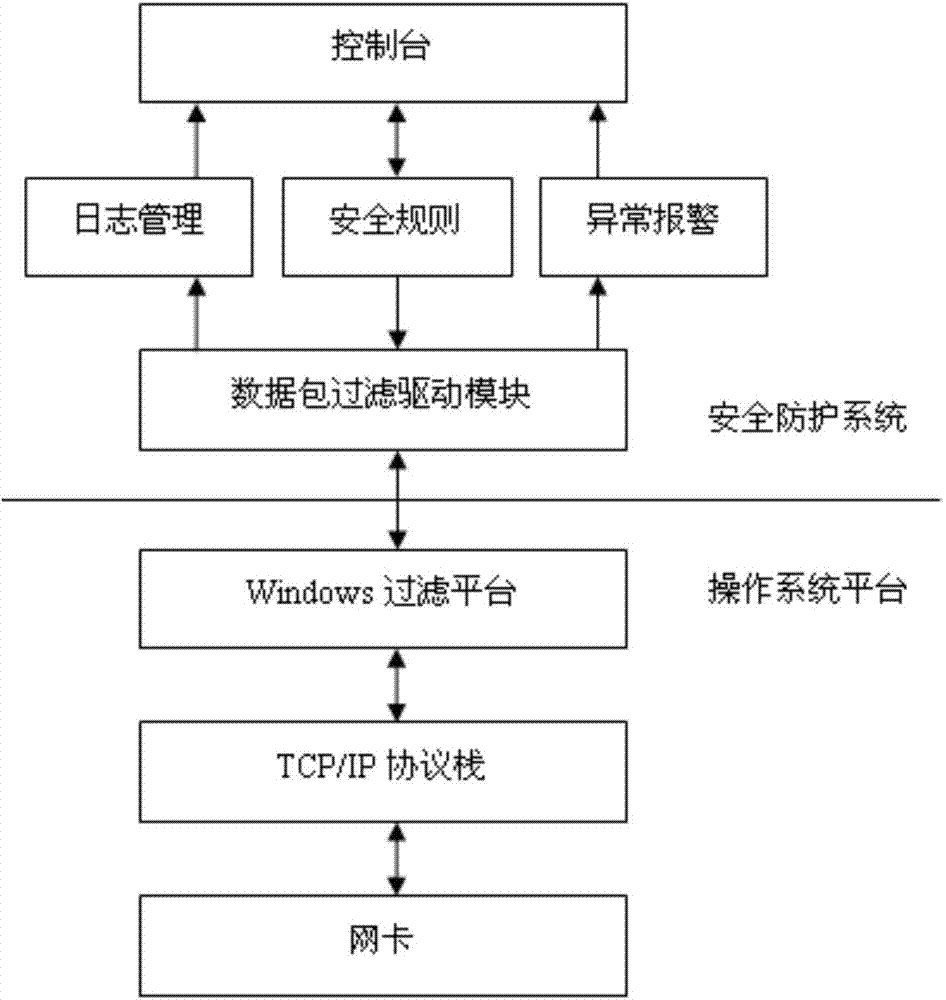
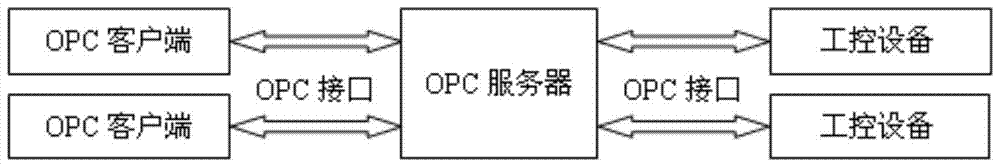
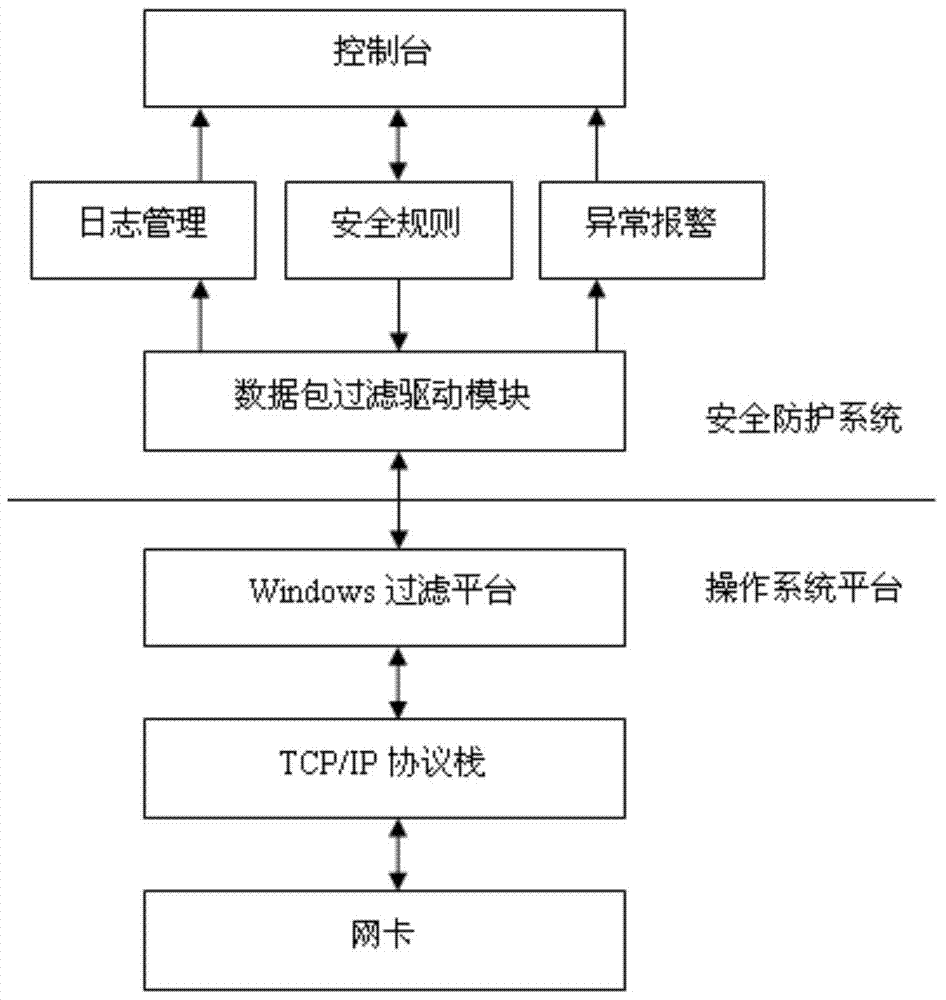
OPC server safety defending system
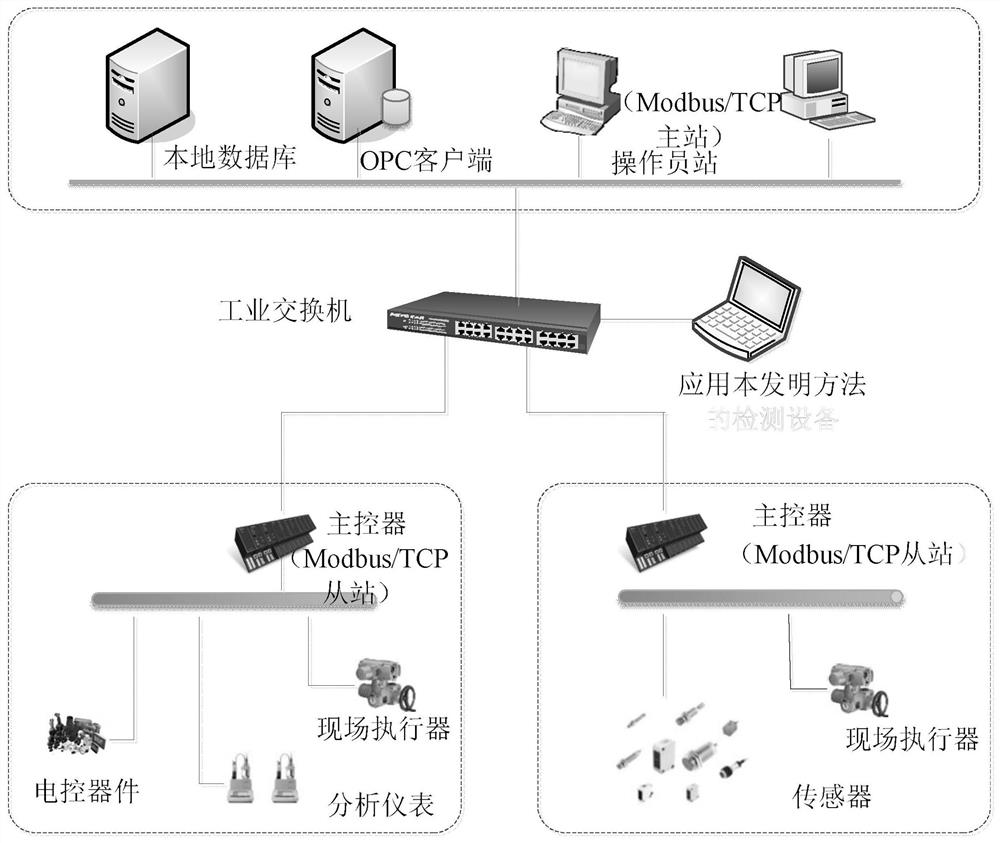
The invention discloses an OPC server safety defending system and aims at solving the technical problem that existing servers and industrial control systems are poor in safety. According to the technical scheme, the system comprises a safety defending system body and an operating system platform, and the safety defending system is composed of a control console and a data package filtration driving module. The operating system platform is composed of a Windows filtration platform and a network card. According to an OPC server network communication system structure, safety rules are set on a network layer, a transmission layer and an application layer of an OPC server, deep safety check and audit are conducted on data packages entering and exiting from the OPC server, vicious access behaviors and data packages are identified, filtered and removed, and the safety defending capability of the OPC server and the industrial control system is improved.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
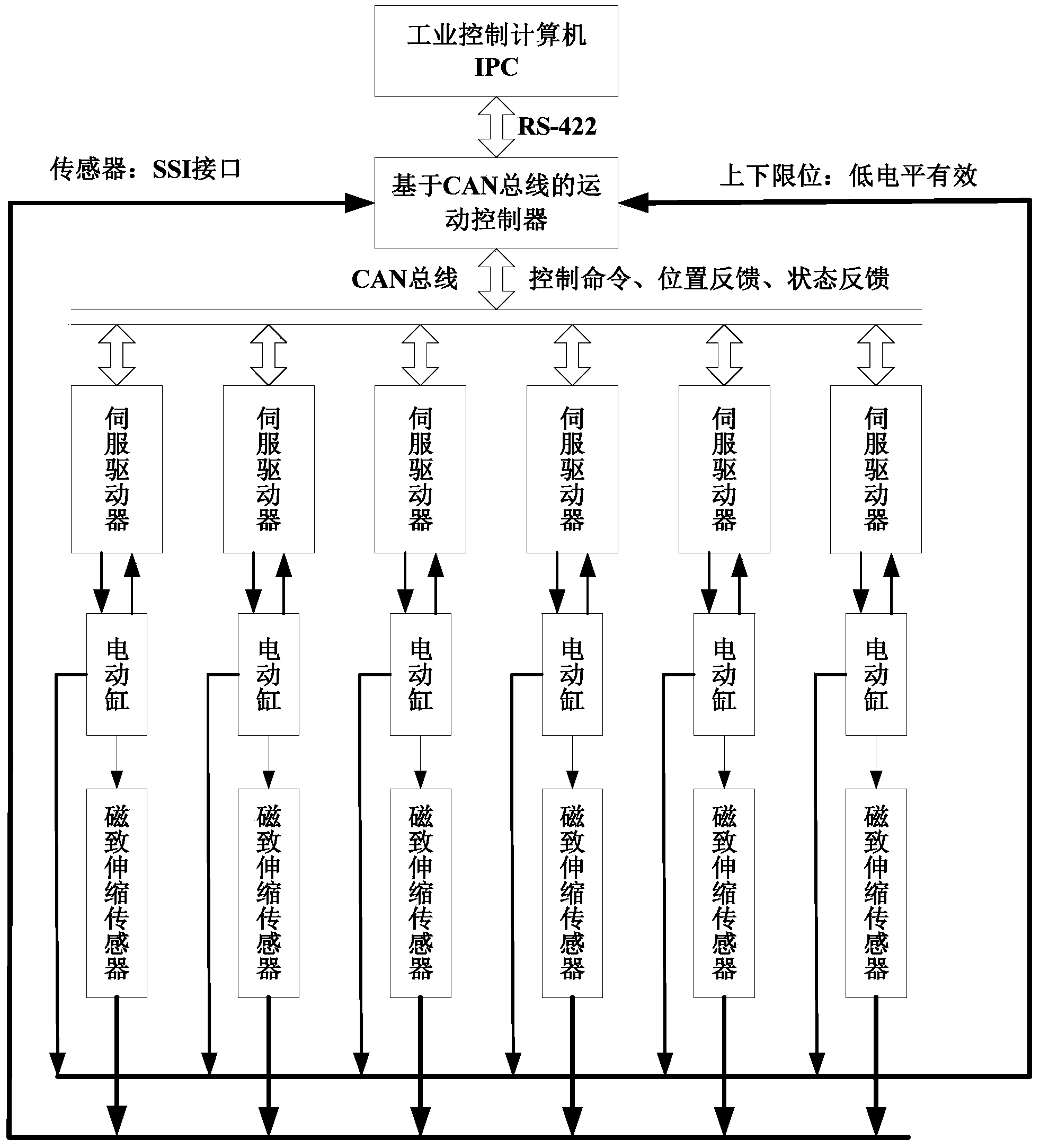
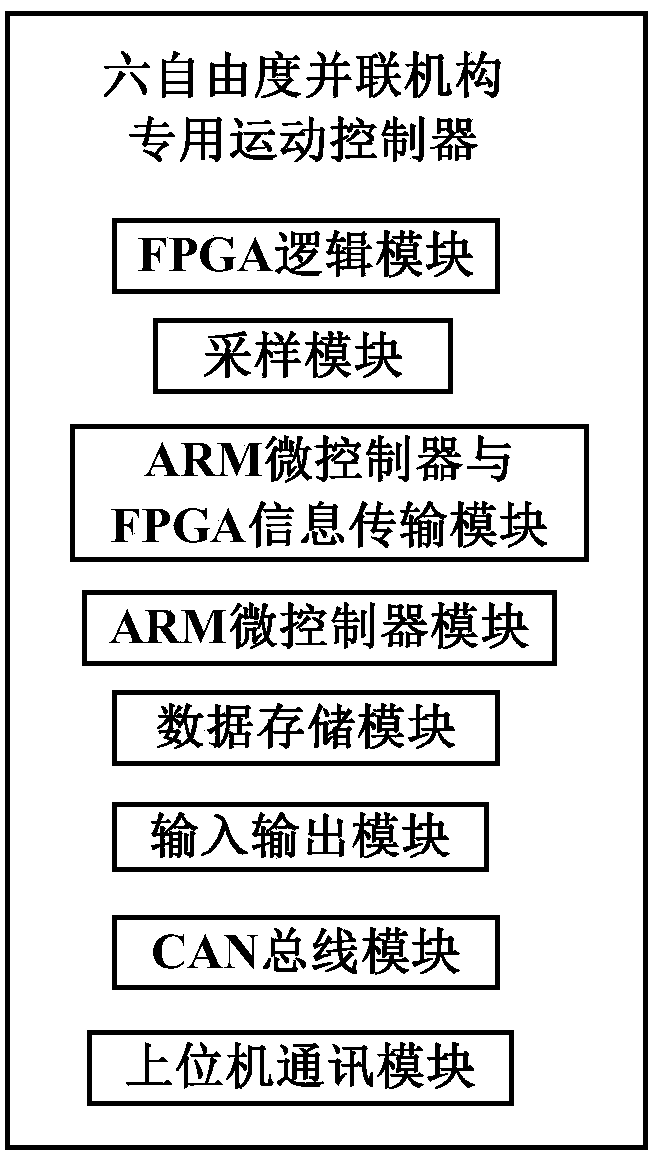
Specialized sport controller hardware platform used for 6-degree-of-freedom parallel robot
InactiveCN104339354AEasy to controlDifferent control implementations for controllersProgramme-controlled manipulatorTransmissionKinematicsControl system
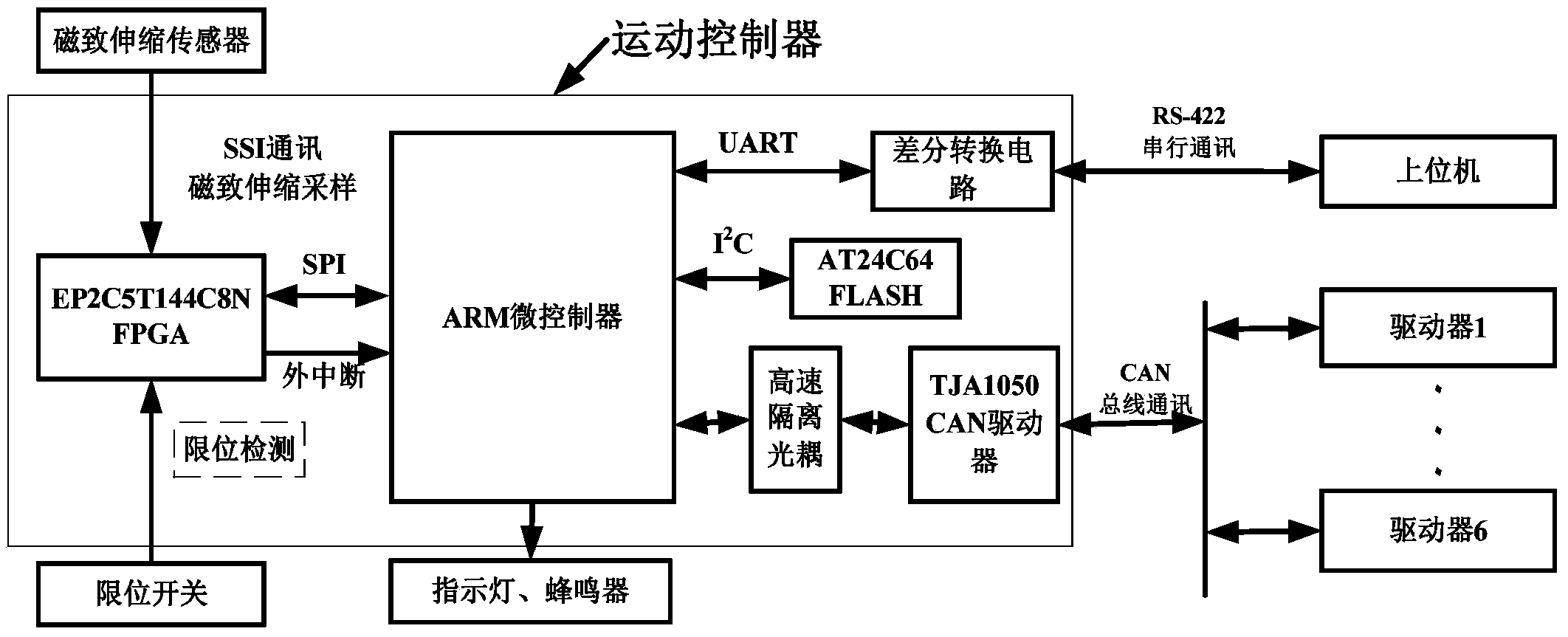
The invention discloses a specialized motion controller hardware platform used for a 6-degree-of-freedom (dof) parallel robot. On one hand, the control on a plurality of motors is realized through a bus way, the concrete bottom layer driving is completed by intelligent equipment, the control precision is effectively guaranteed, the real-time monitoring to the equipment state and faults can be conducted, and the specialized sport controller hardware platform has good consistency and expandability; on the other hand, the sampling function of an external sensor is finished by an auxiliary function chip FPGA, an ARM micro-controller as a main control chip obtains needed data through an external port as needed, the function distribution can effectively reduce the expense of the main control chip, and more resources can be used for the control system security and the accurate control; in addition, the kinematic algorithm of the 6-dof parallel robot is integrated in a motion controller, and the specialized motion controller can realize the control on a mechanism through a simple order in all occasions and obtain necessary data.
Owner:XIDIAN UNIV
Control System Security Appliance
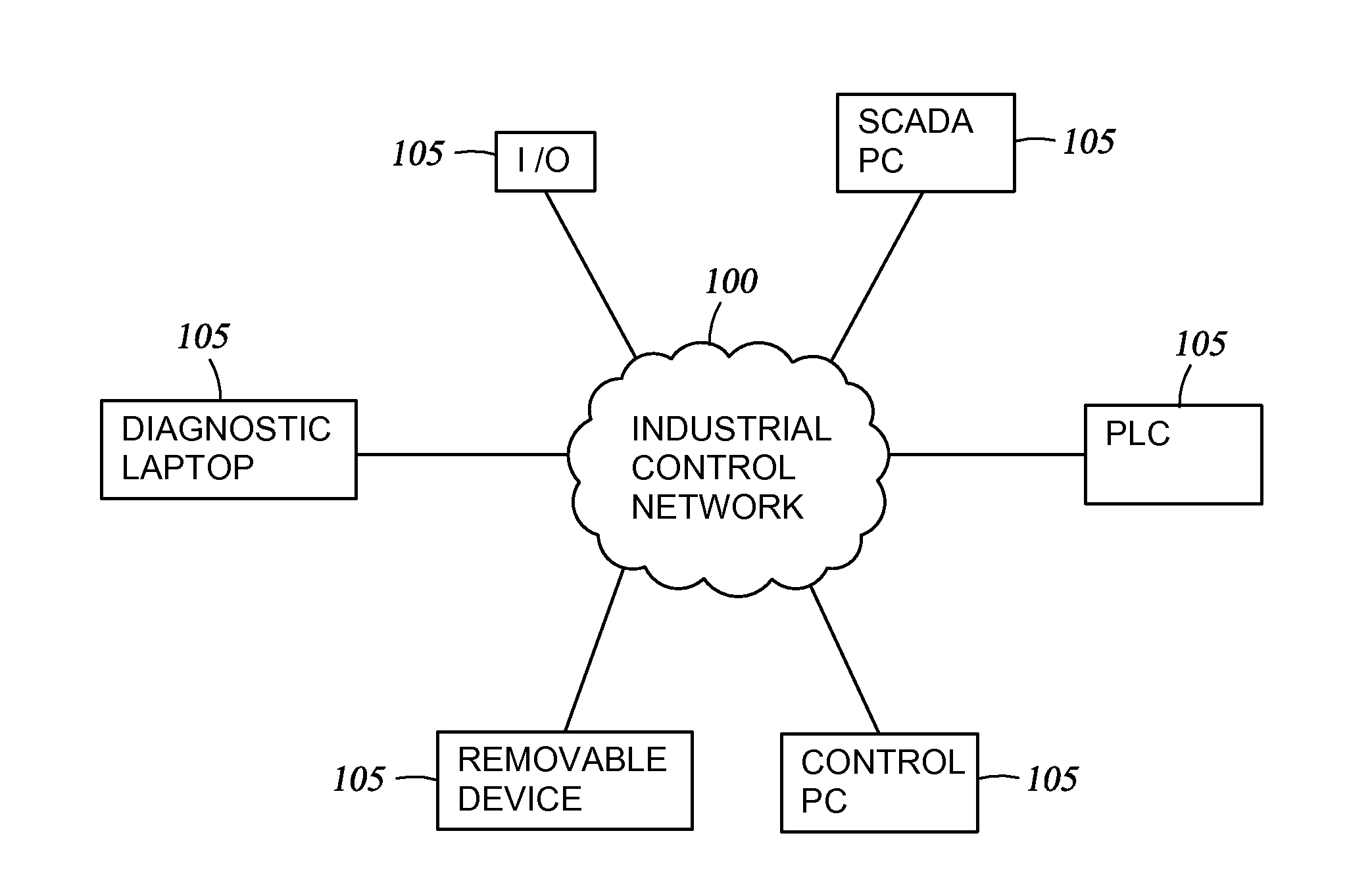
A widespread security strategy for industrial control networks is physical isolation of the network, also known as an “air gap.” But the network might still be infected with unauthorized software if, say, an infected USB drive were to be plugged into one of the network's computers. The invention relates to a security module placed between the network and a device in the network. Each security module in the network mimics the Internet protocol (IP) configuration of its protected device. Each security module includes a private encryption key and a signed public key that it automatically shares with other security modules discovered on the network. These keys permit the security module to perform asymmetric point-to-point encryption of traffic from the protected device to the corresponding security module for a target device node and to detect (and thus block) unauthorized devices.
Owner:NAT OILWELL VARCO LP
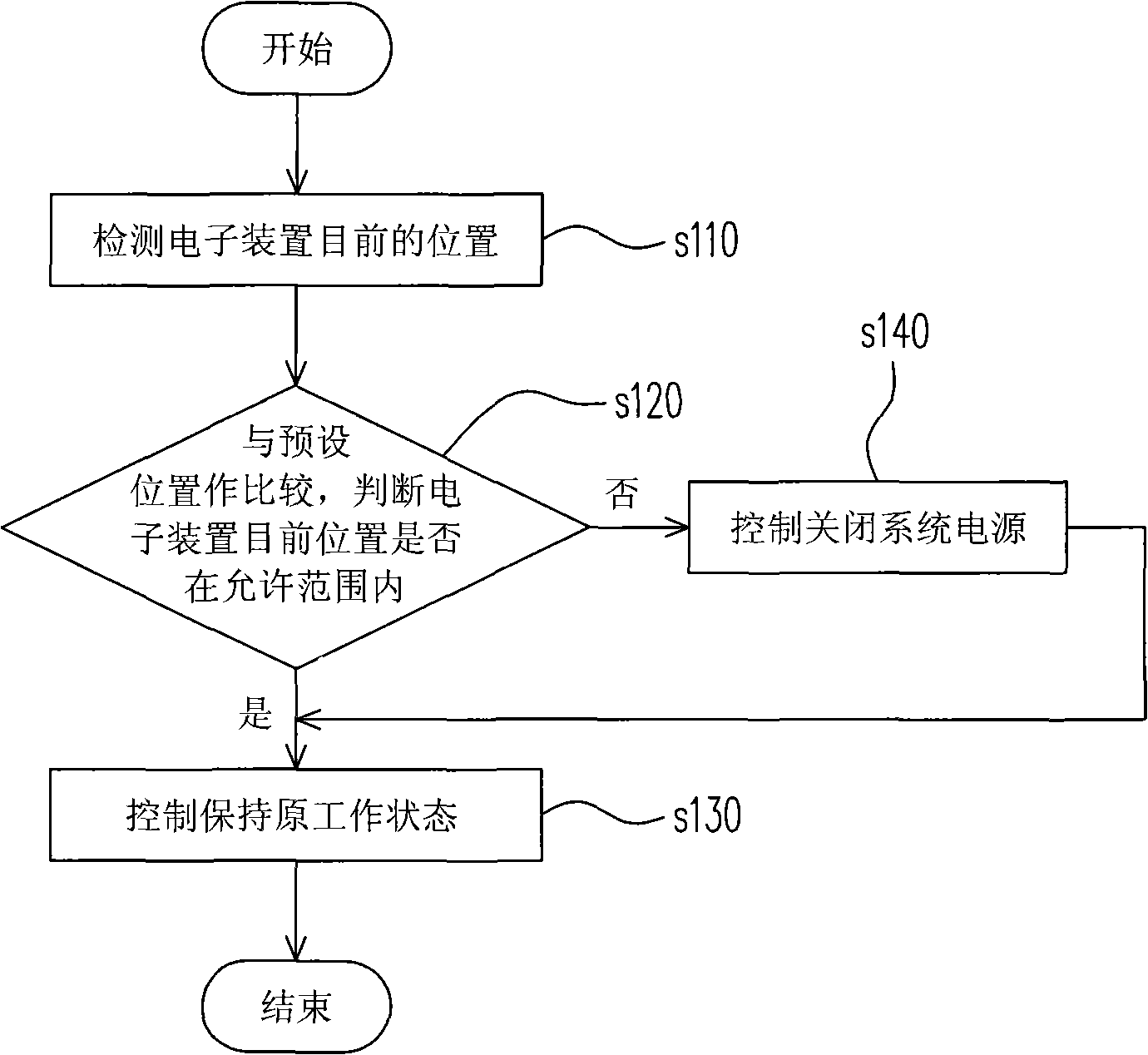
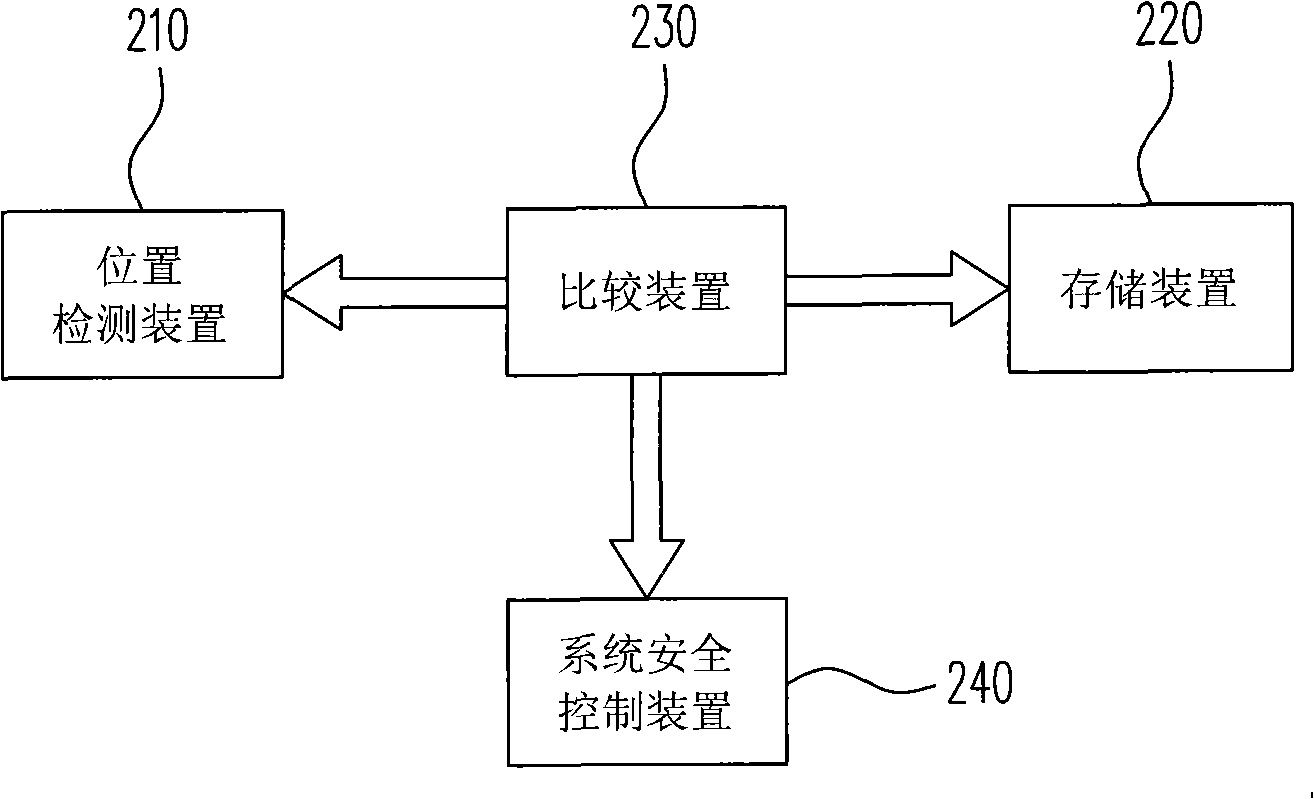
Method and system for controlling system security based on position information
InactiveCN101295334AProtection securityAvoid gettingPlatform integrity maintainanceLocation detectionControl system
The invention discloses a method and a system for controlling safety of a system based on position information, the method comprises the following steps: the current position information of an electronic device is detected; the comparison with the preset position information is carried out, whether the current position of the electronic device is in the allowable range or not is judged, and if not, a power supply of the system is controlled to be closed. The system comprises a position detection device for detecting the current position information of the electronic device; a comparison device, which is connected with the position detection device and used for comparing the current position information of the electronic device with the preset position information and judging whether the current position of the electronic device is in the allowable range or not; a system safety control device, which is connected with the comparison device; when the current position of the electronic device exceeds the allowable range, the power supply of the system of the electronic device is controlled to be closed. The system has the advantages that the system can limit the range of the workplace of the electronic device, thus protecting the information safety of the system and being applicable to the machines used in certain specific places.
Owner:MITAC COMP (SHUN DE) LTD +1
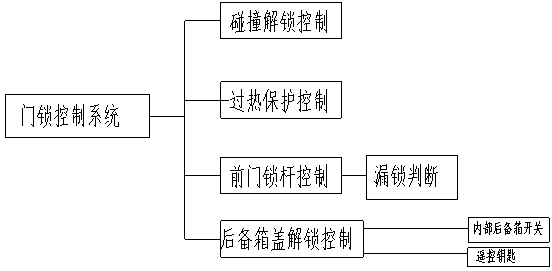
Door lock control system of intelligent automobile body controller
InactiveCN103266817AAvoid damageImprove securityPedestrian/occupant safety arrangementNon-mechanical controlsRemote controlControl system
The invention discloses a door lock control system of an intelligent automobile body controller. The door lock control system drives a door lock motor via a relay, controls the door lock motor to rotate in different directions, and can enable a door lock to be unlocked and locked. The door lock control system further has the functions of collision unlocking control and overheat protect control, in case of collision, locking operation via remote control or a front-row lock rod is shielded and can only be performed after one ignition cycle, and when door lock operation is in an overheat protect state, door lock operation is determined according to the fact whether the door lock operation is triggered by a user or triggered automatically. The door lock control system of the intelligent automobile body controller is high in safety performance, the service life of a door lock mechanism is prolonged, and safety of persons in an automobile and safety of the automobile are guaranteed.
Owner:NINGBO XINGFENG MACHINERY
Intelligent light control system
InactiveCN105188202AImprove securityAvoid wastingElectric light circuit arrangementEnergy saving control techniquesWireless controlEmbedded system
The invention provides an intelligent light control system, which comprises a main controller used for generating a wireless control signal upon receiving a triggering instruction sent by a user; and a wireless controller used for controlling the on / off state of a light fixture according to the wireless control signal, detecting the current signal of the light fixture in real time, and then feeding the state information corresponding to the current signal back to the main controller. The main controller receives and displays the received state information to a user, so that the user can check the state information in real time. According to the technical scheme of the invention, by means of the main controller, the wireless controller and the light fixture, the visualization and the intellectualization of the entire intelligent light control system are realized, while the wiring operation is not required during the entire control process. Therefore, the waste of cables due to the traditional wiring mode can be avoided. The investment cost of the traditional wiring operation is effectively reduced. Meanwhile, the current signal of the light fixture is detected in real time by the wireless controller, and then the corresponding state information of the light fixture is fed back to the main controller. In this way, the complex process of the manual signal detection operation is avoided. The above system is time-saving and labor-saving in operation. The security of the whole control system is better and the later maintenance efficiency of the system is higher.
Owner:汤毅
Improved train control system security data interaction method
ActiveCN110267266AIncrease the lengthMake up for loopholesNetwork traffic/resource managementEncryption apparatus with shift registers/memoriesOccupancy rateTransceiver
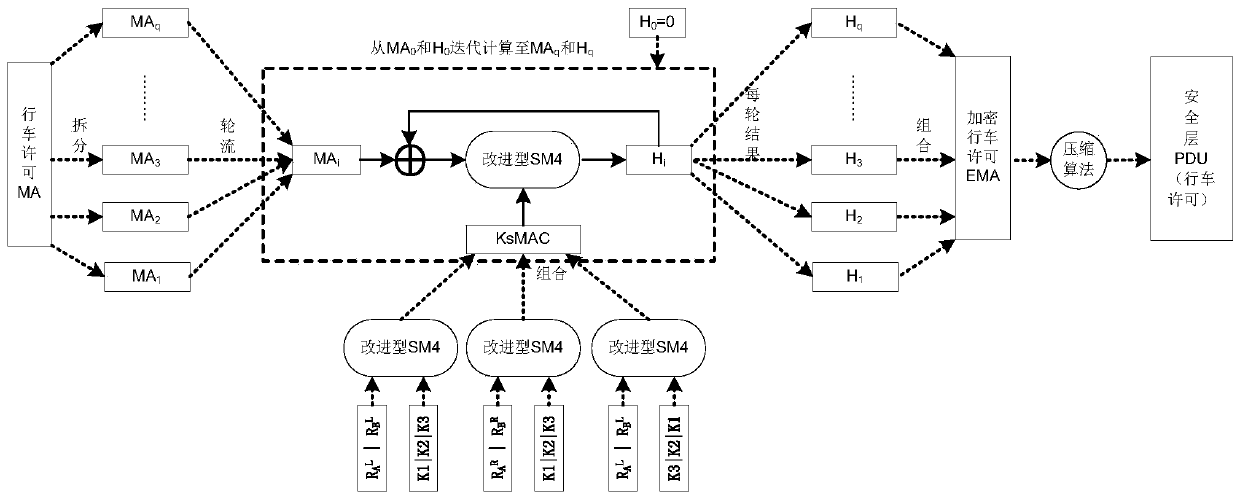
The invention discloses an improved train control system secure data interaction method, which comprises the following steps of: expanding the shared key of a data transceiver and the length of a random number generated and shared by the transceiver, and calculating a session key with an increased key length by matching with a corresponding SM4 algorithm; dividing the security data X of the train control system into blocks according to N bits, using a data block and a full text of a session key as input in each round, performing iterative computation by using a corresponding SM4 algorithm, and generating an N-bit operation result Hi corresponding to the corresponding data block; regarding the operation result Hi as encrypted data of the corresponding data block, and covering the corresponding data block, so that the security encryption of the security data X of the train control system is realized; and selecting a corresponding lossless compression algorithm according to the type of the train control system security data, performing data lossless compression on the full-text encrypted train control system security data X, and sending the compressed data X to a receiver. According to the method, the data security is greatly improved, and meanwhile, the occupancy rate of wireless resources is reduced.
Owner:CHINA RAILWAYS CORPORATION +2
Network control system security control method based on hybrid triggering under multi-network attacks
ActiveCN111679572AReduce loadImprove data transfer efficiencyInformation technology support systemAdaptive controlLyapunov stabilityMix network
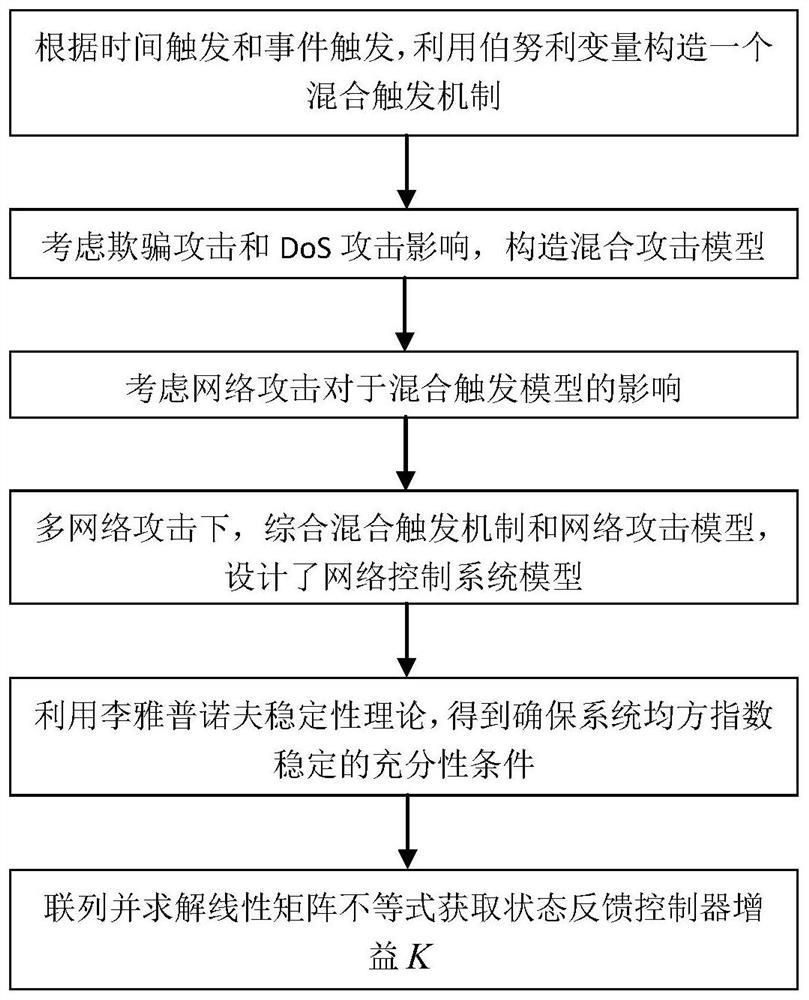
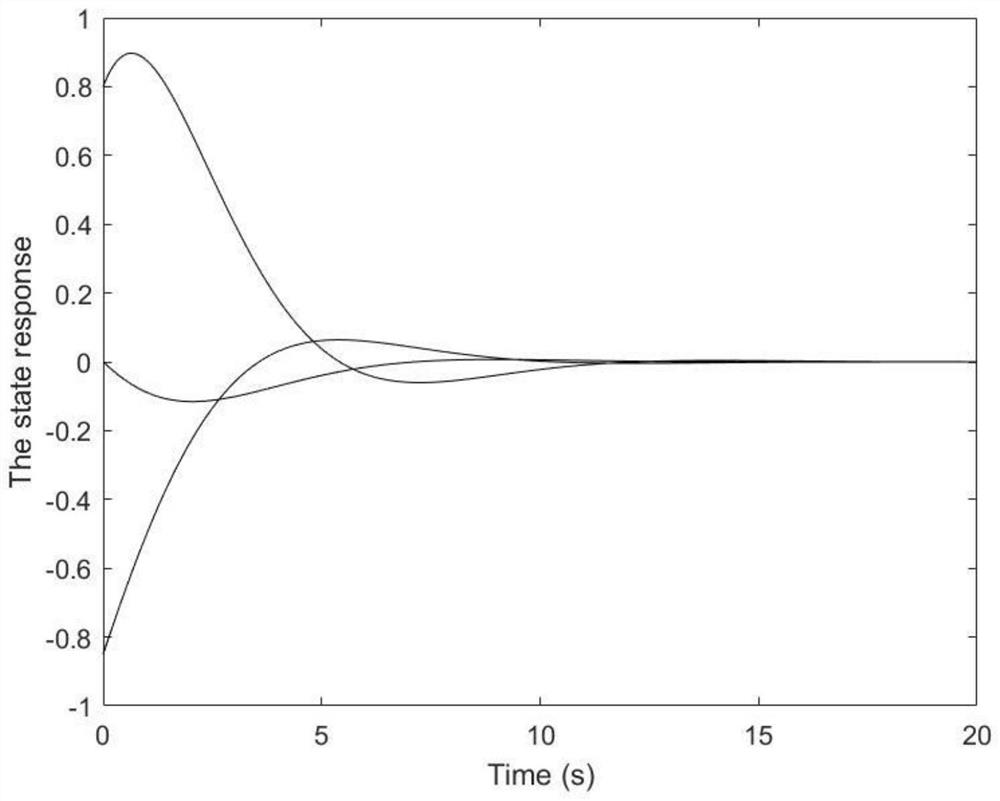
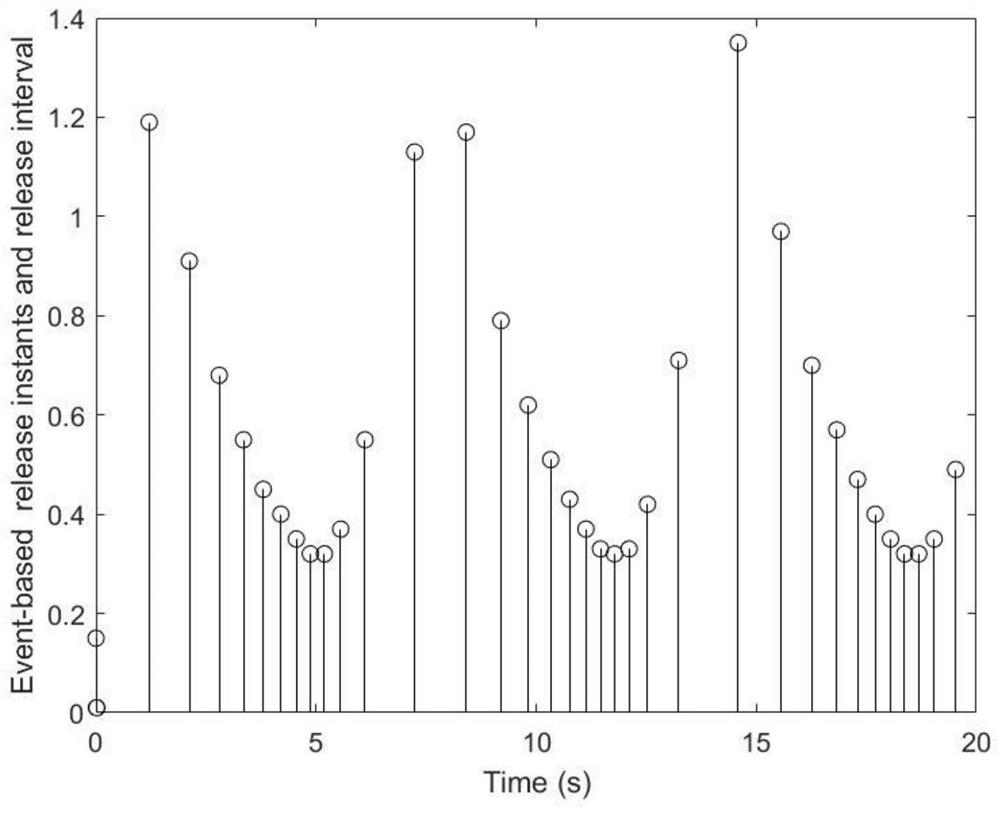
The invention discloses a network control system security control method based on hybrid triggering under multi-network attacks. On the basis of the prior art, the invention provides a network controlsystem security controller design method based on a hybrid triggering mechanism under a hybrid network attack background. A time triggering mechanism and an event triggering mechanism are introducedto reduce the network load while the influence of DoS attacks and spoofing attacks on the network security is considered, so that the security and stability of the control system are ensured, the occupation of network bandwidth by transmission data is reduced, and the data transmission efficiency of the system is improved. Based on the newly established system model, the gain of the controller isobtained by utilizing a linear matrix inequality and a Lyapunov stability theory, so that the requirement on network bandwidth is reduced while the stability of the system is ensured.
Owner:NANJING UNIV OF FINANCE & ECONOMICS +1
Tramcar intersection safety zone control device based on fixing equipment
PendingCN107839718ARealize safety judgmentReduce in quantityRoad traffic warning meansControl systemSafety zone
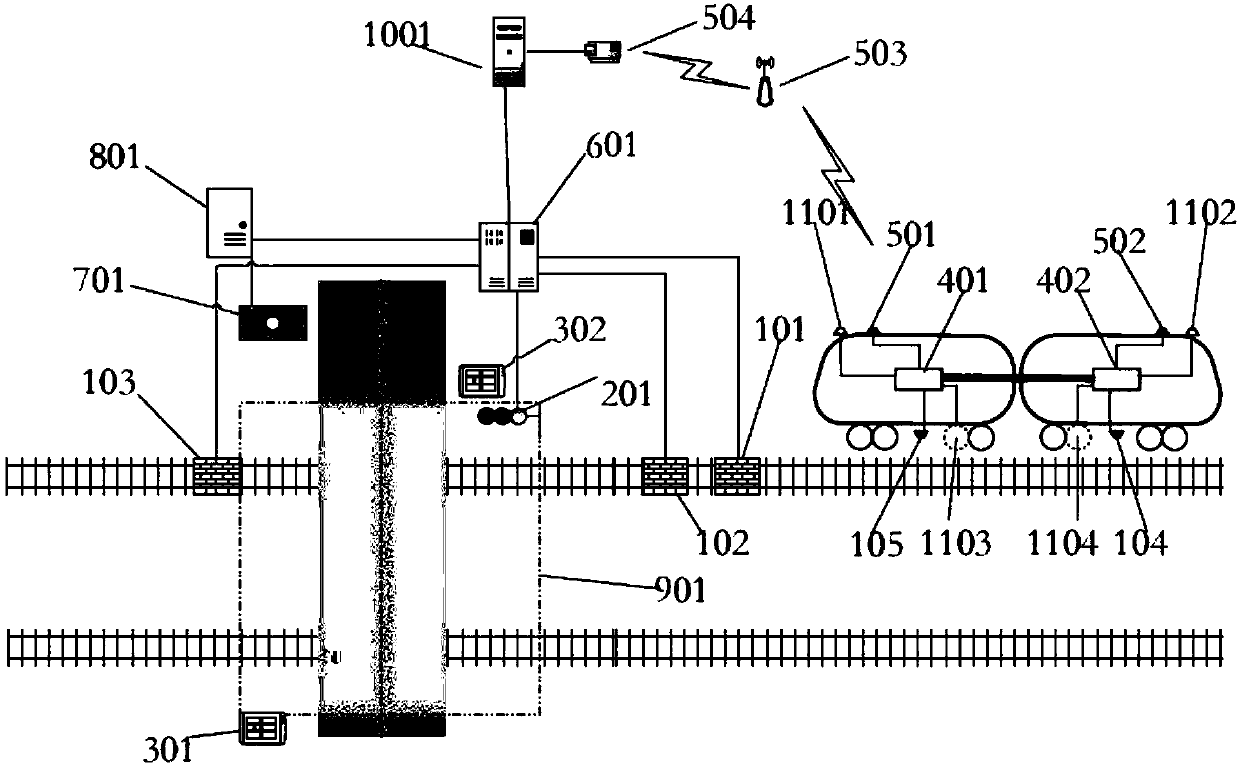
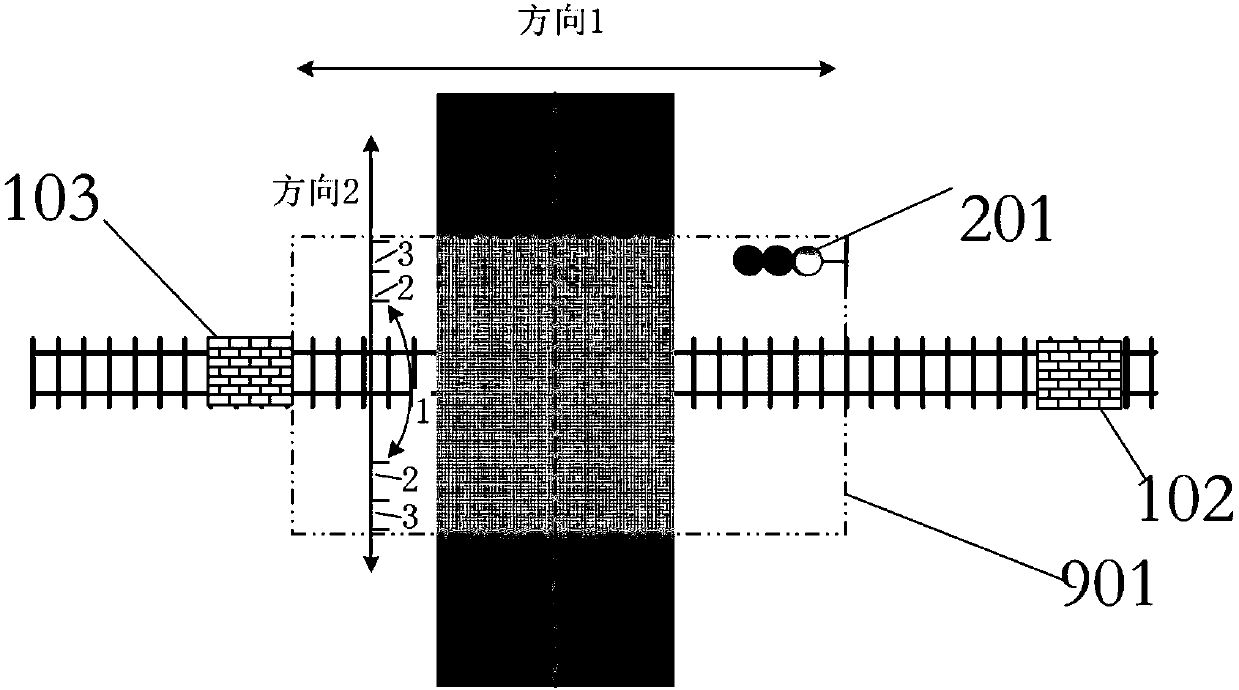
The invention provides a tramcar intersection safety zone control device based on fixing equipment. The tramcar intersection safety zone control device comprises a train position detecting system, anintersection safety zone control system and an intersection environment sensing system and is characterized in that the intersection environment sensing system collects the environment state information of an intersection in real time and transmits the environment state information to the intersection safety zone control system; the train position detecting system comprises a train position grounddetecting device; the first ground detecting device and the second ground detecting device of the train position ground detecting device are sequentially mounted in the train entering direction of aplanar intersection, the first ground detecting device is used for receiving train feature information and priority pass request information and transmitting the information to the intersection safetyzone control system, and the second ground detecting device is used for receiving train feature information and the state information of a train approaching the intersection and transmitting the information to the intersection safety zone control system.
Owner:CHINA ACADEMY OF RAILWAY SCI CORP LTD +3
Externally holding belt type tooth form brake
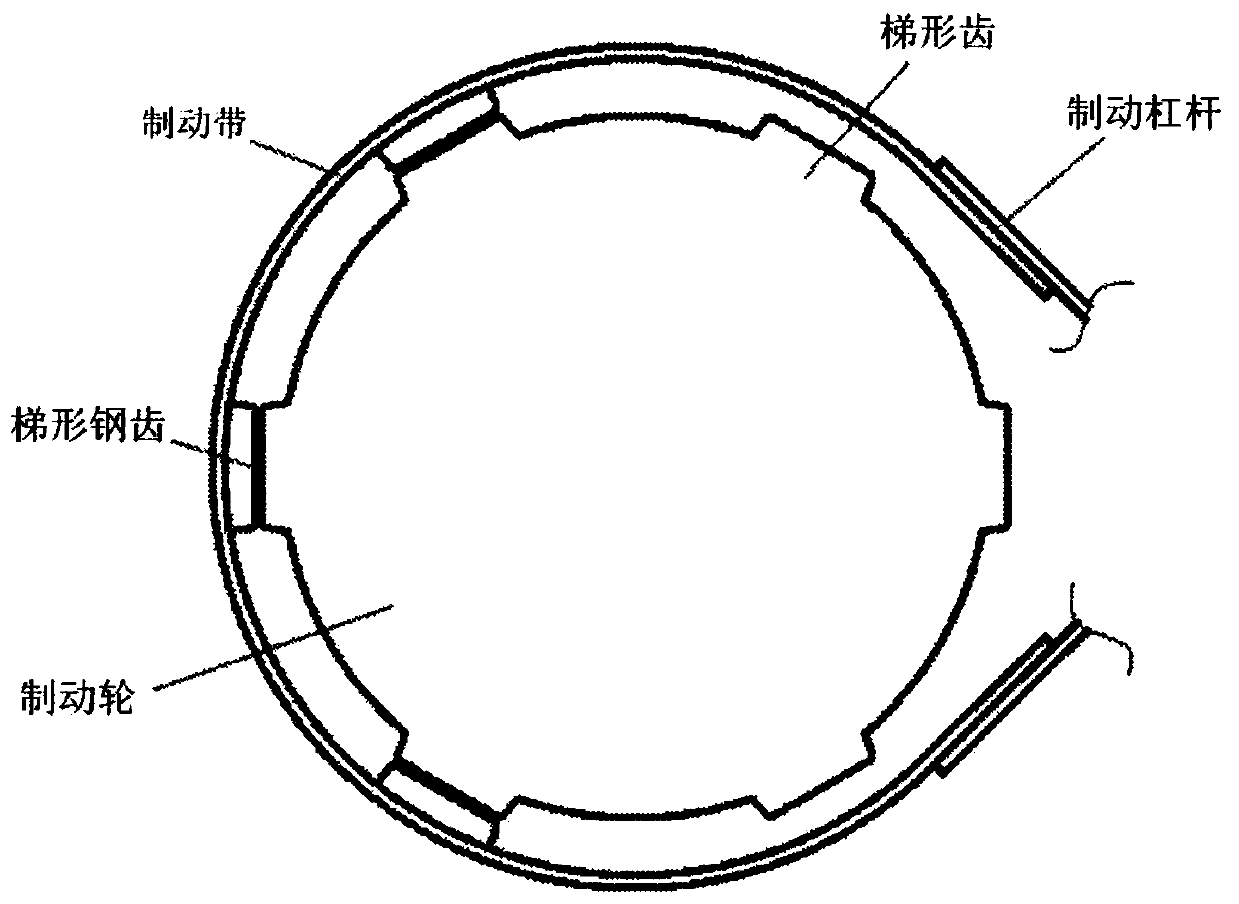
ActiveCN110439940AReduce energy consumptionLow costMechanically actuated drum brakesSpeed control systemControl system
The invention provides an externally holding belt type tooth form brake and belongs to the technical field of vehicle speed control systems. The externally holding belt type tooth form brake comprisesa braking hub, a braking belt and a driving mechanism; the braking belt adopts a segmentation symmetric type structure, concentric and uniform contraction is realized in the braking contraction process, gaps of all meshing tooth pairs in the circumferential direction are synchronously reduced, multi-teeth meshing is facilitated, and the stress is shared; and the driving mechanism adopts a lead screw nut driven by a motor, a braking state of the braking belt can be self-maintained by the application of the mechanical self-locking property of the driving mechanism and does not need to be maintained by continuous work output of an operation mechanism, the energy consumption of a control system is greatly reduced, and meanwhile the safety and the braking reliability of the control system areimproved. Meanwhile, elastic toothed sleeves are arranged on trapezoidal teeth on the braking hub, and the effects of relieving impact and uniformly stressing each tooth are achieved.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Smart home control system
ActiveCN108427303AImprove securityAdd funComputer controlTotal factory controlRemote controlControl system
The invention provides a smart home control system. The control system comprises a control device, an auxiliary device and a plurality of household devices connected with the control device; the auxiliary device is used for collecting identity information and action information, and the control device judges whether to make an operation permission for operating the household devices available according to the identity information and determines an operation instruction for the household devices according to the action information when the operation permission is available. According to the smart home control system, before an operator operates the household devices, the smart home control system judges the identity information of the operator and makes the operation permission available tothe operator with the correct identity information, and the operator can operate the household devices in the smart home control system through the action information; the safety of the smart home control system is improved, and meanwhile the operator can control the household devices at his / her will through action instead of using a remote control to operate the household devices.
Owner:GREE ELECTRIC APPLIANCES INC
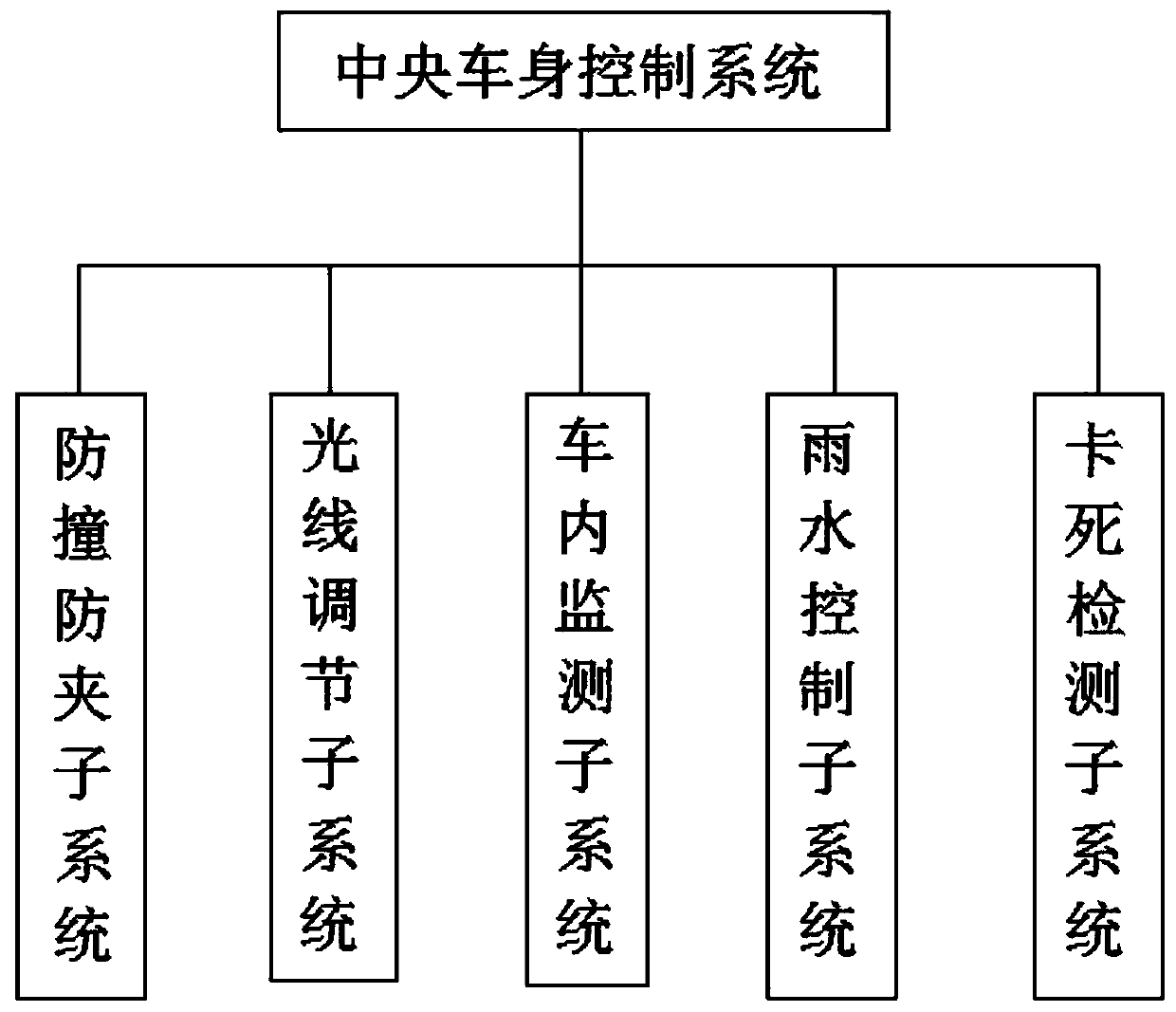
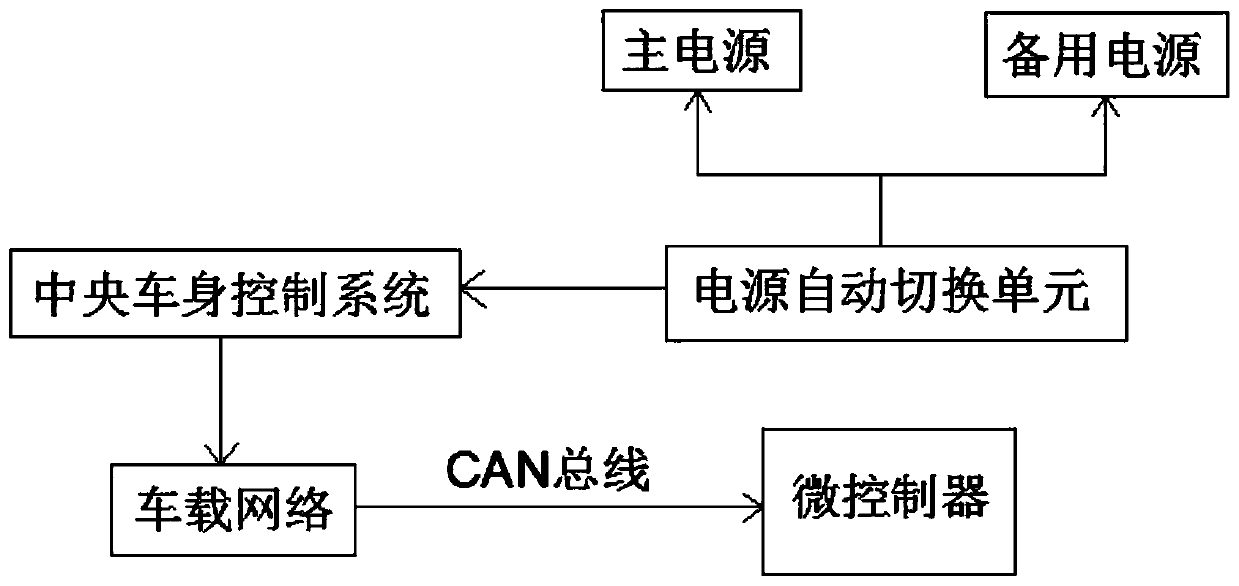
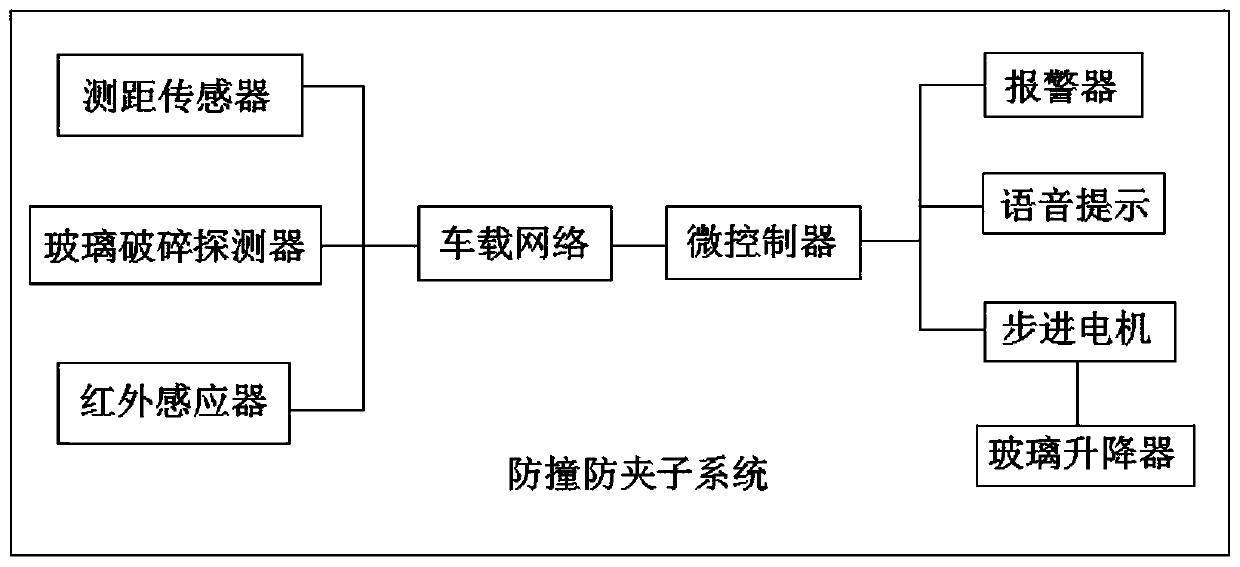
Intelligent vehicle window control system and control method thereof
InactiveCN109854119AMonitoring and management intelligent liftingImprove securityPower-operated mechanismSignalling/lighting devicesMicrocontrollerControl system
The invention relates to the technical field of an intelligent vehicle window, and specifically relates to an intelligent vehicle window control system and a control method thereof. The system includes a central vehicle body control system; an anti-collision clamp proof subsystem, a light adjustment subsystem, an in-vehicle monitoring subsystem, a rainwater control subsystem and a dead locking detection subsystem are separately disposed in the central vehicle body control system; an input end of the central vehicle body control system is electrically connected with a power supply automatic switching unit, and an input end of the power supply automatic switching unit is separately electrically connected with a main power source and a backup power source; and an output end of the central vehicle body control system is electrically connected with a vehicle-mounted network, and the vehicle-mounted network is connected with a microcontroller via a CAN bus. The intelligent vehicle window control system and the control method thereof can effectively overcome the defect of lack of security of a traditional intelligent vehicle window control system existing in the prior art.
Owner:范建明
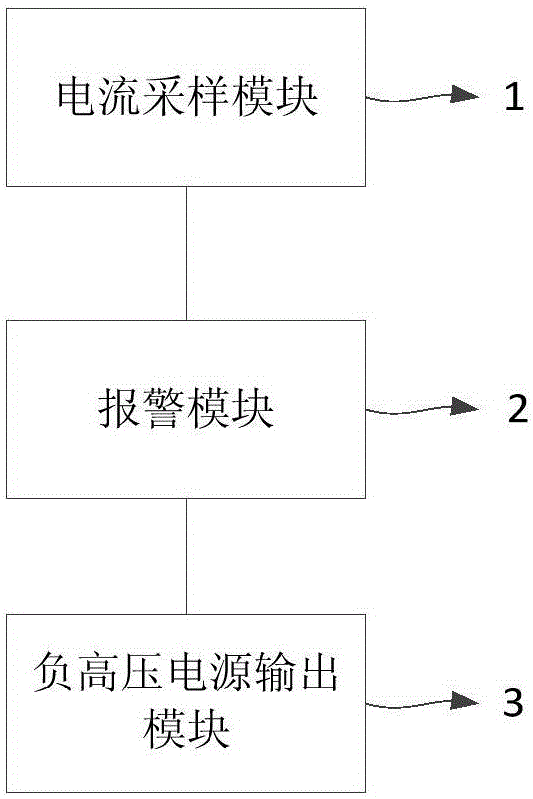
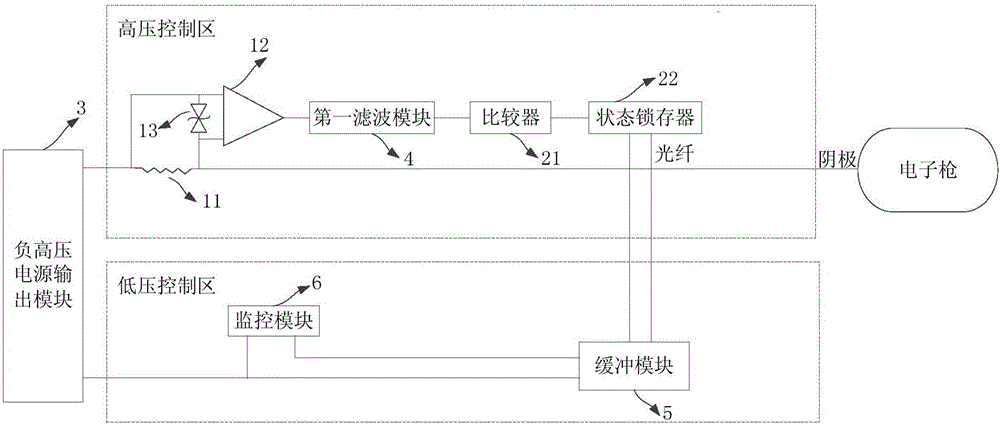
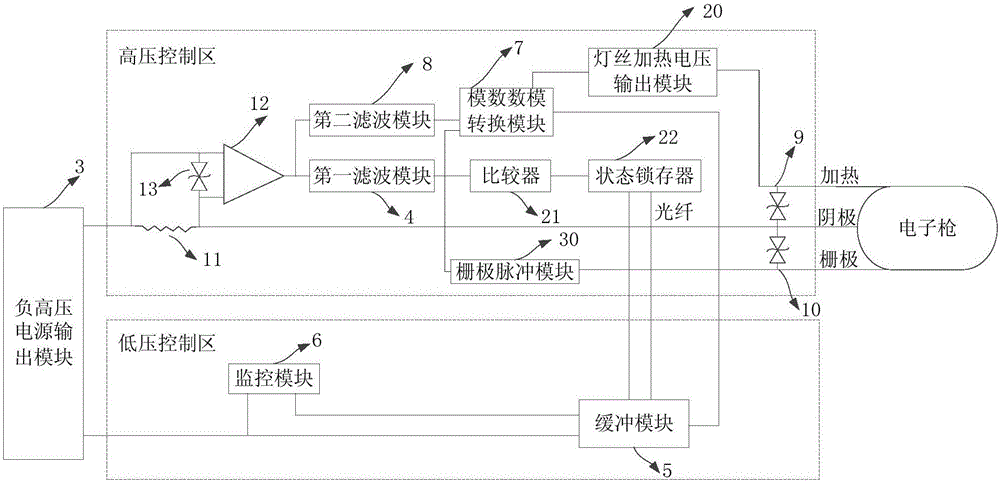
Protective device and method of electronic gun beam flow controlling system
ActiveCN106848997AImprove securityArrangements responsive to excess currentControl systemComputer module
The embodiment of the invention discloses a protective device and method of an electronic gun beam flow controlling system. The device comprises a current collecting module, a warning module and a negative high voltage power output module, wherein the current collecting module is separately connected with a cathode of an electron gun and the negative high voltage power output module and used for sampling the current of the cathode of the electron gun so as to obtain a sampled current; the warning module is connected with the current collecting module and used for judging whether arcing of a current circuit occurs or not according to the sampled current and outputting a warning signal when the arcing occurs; the negative high voltage power output module is connected with the warning module and used for cutting off high-voltage output when receiving the warning signal. By means of the device and method, arcing protection can be conducted on the electronic gun beam flow controlling system, and the safety of the control system is improved.
Owner:SHANGHAI UNITED IMAGING HEALTHCARE
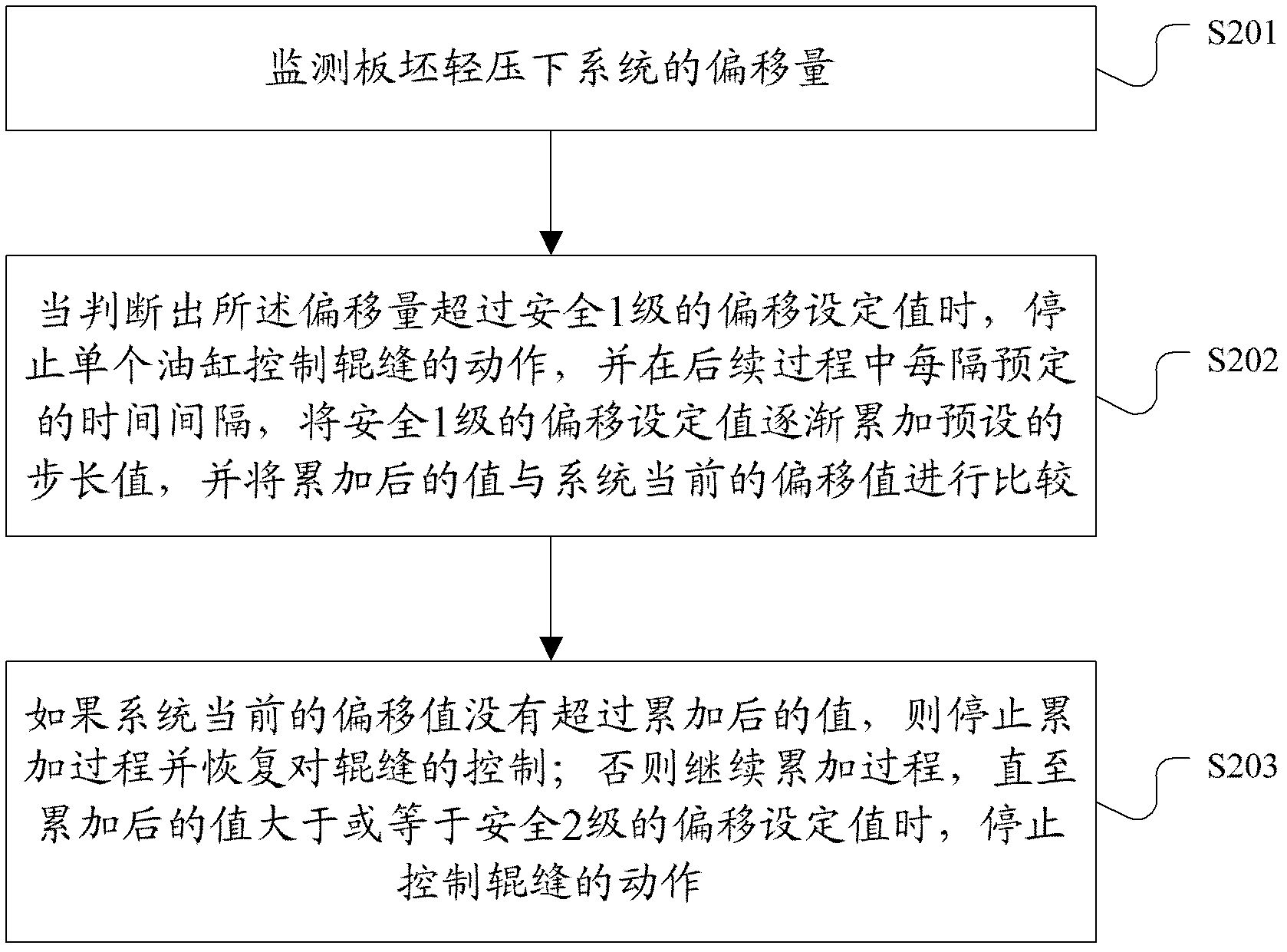
Method and device for controlling system security under light press of slab
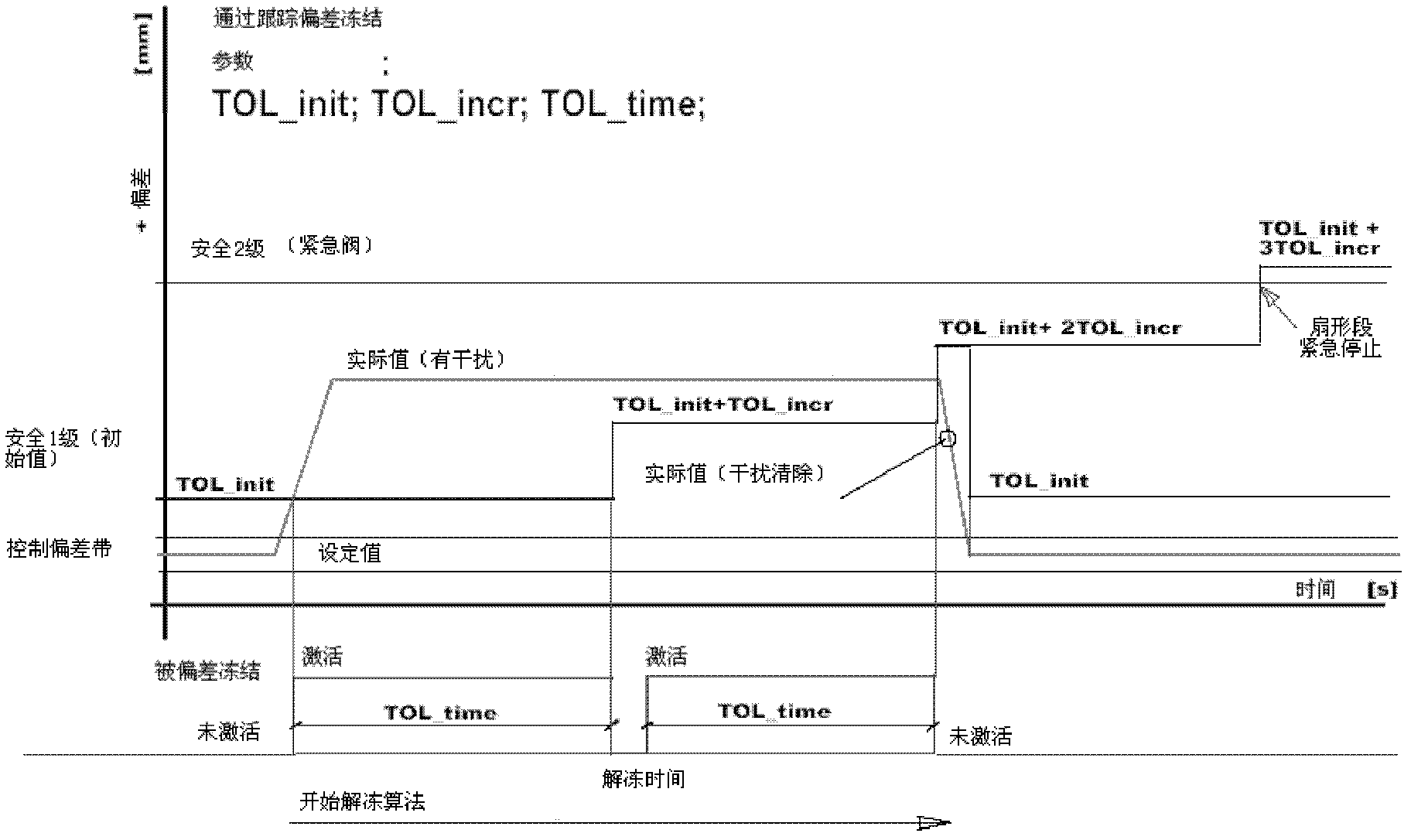
ActiveCN102554169AImplement automatic recoveryDoes not affect productionControl system securitySystem safety
The embodiment of the invention provides a method and a device for controlling the system security under the light press of a slab. The method comprises the following steps: monitoring an offset value of the system under the light press of the slab, wherein the offset value is equal to an absolute value of a difference value between an actual value and a set value of a roll gap; when the offset value is judged to exceed the offset set value with first-level security, stopping the action that single oil cylinder controls the roll gap, gradually accumulating the offset value with first-level security to a preset step value at a scheduled time interval in the follow-up process, and comparing the accumulated value with the current offset value of the system; if the current offset value of the system does not exceed the accumulated value, stopping the accumulation process and restoring the control on the roll gap, or continuously carrying out the accumulation and comparison process until the accumulated value is greater than or equal to an offset set value with second-level security, and stopping the action of controlling the roll gap.
Owner:CONTINUOUS CASTING TECH ENG OF CHINA
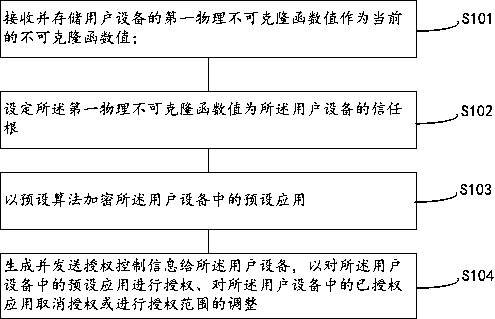
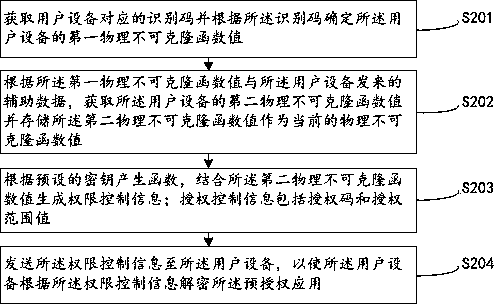
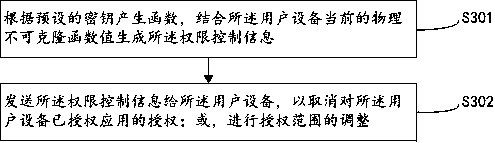
Authority control method, authority control equipment, user equipment and system
ActiveCN109902479AImprove securityIncrease flexibilityDigital data authenticationControl systemPhysical unclonable function
The embodiment of the invention relates to an authority control method, authority control equipment, user equipment and a system. The method comprises the following steps: extracting a physical unclonable function value of user equipment; Setting a physical unclonable function value of the user equipment as a trust root; Encrypting a preset application in the user equipment; And generating and sending authority control information to the user equipment so as to authorize a preset application in the user equipment, cancel authorization for an authorized application in the user equipment or adjust an authorization range. According to the embodiment of the invention, the remote authority control system is established by taking the physical unclonable function value of the user equipment as the trust root, the security is high, and the flexibility is high.
Owner:OPEN SECURITY RES INC
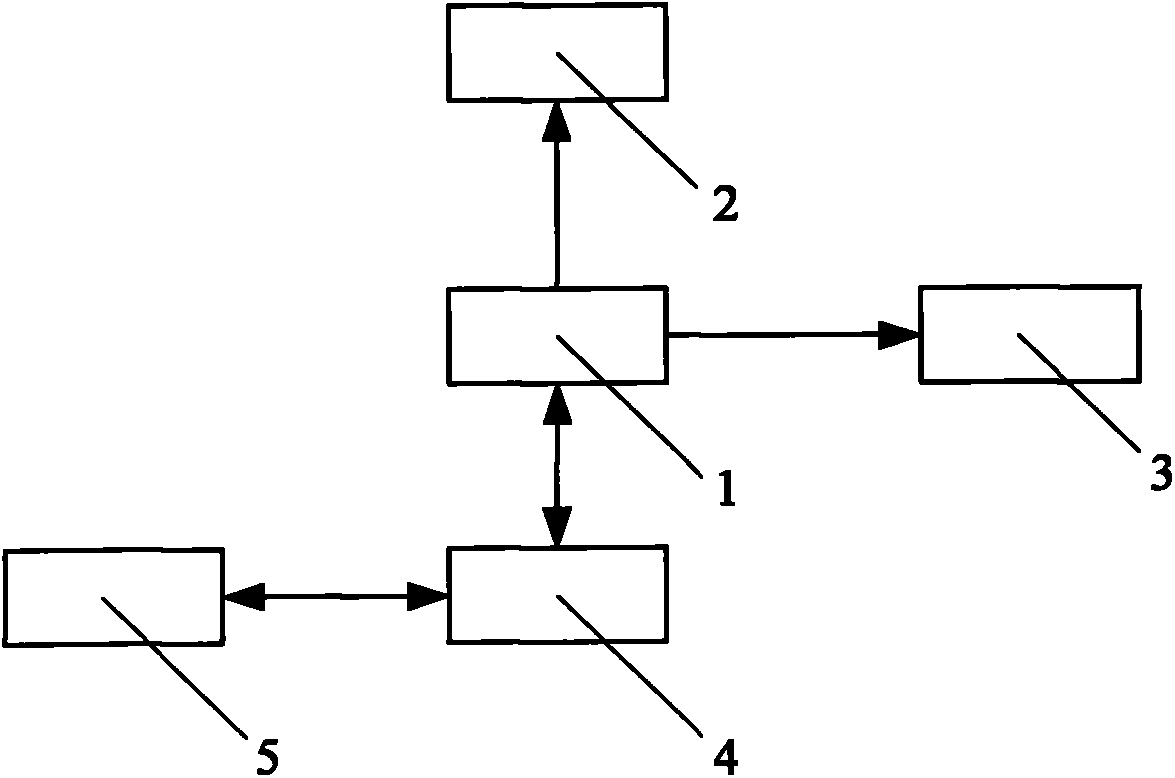
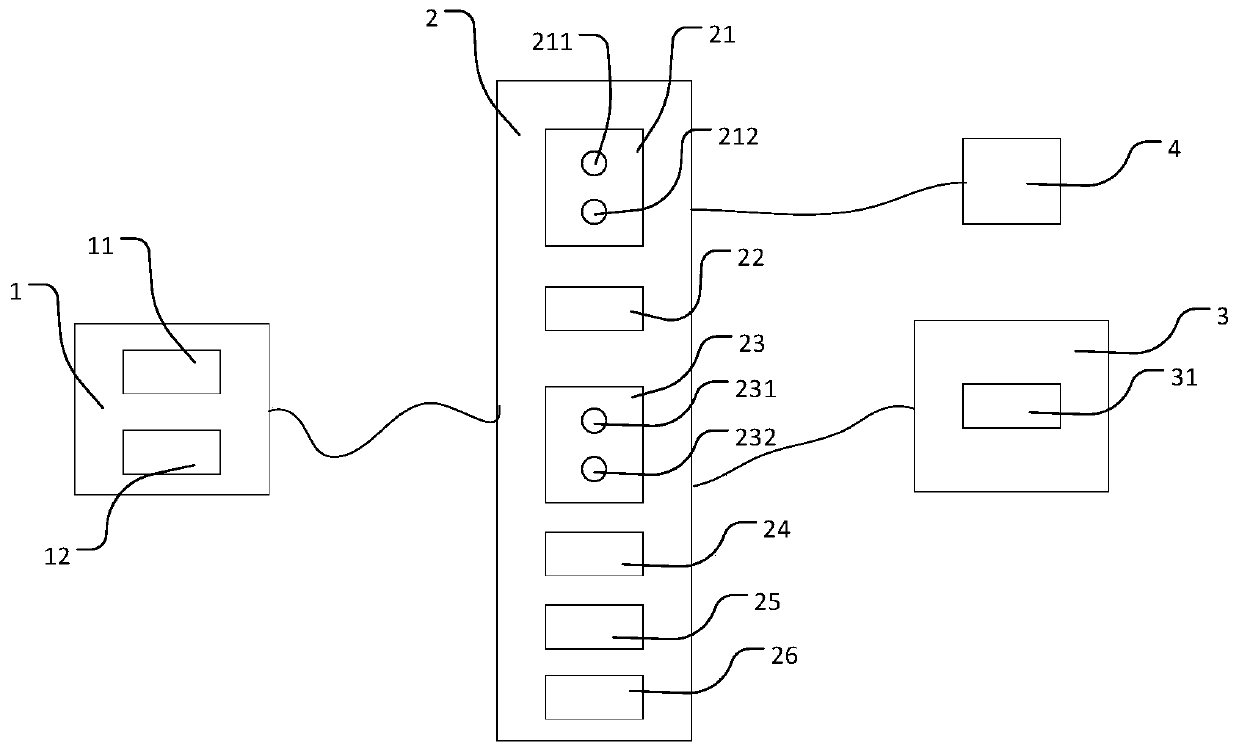
Control system of 57 mm digitalized figure anti-aircraft gun
InactiveCN103105097AImprove work efficiencySimple control methodWeapon componentsAutomatic controlControl system
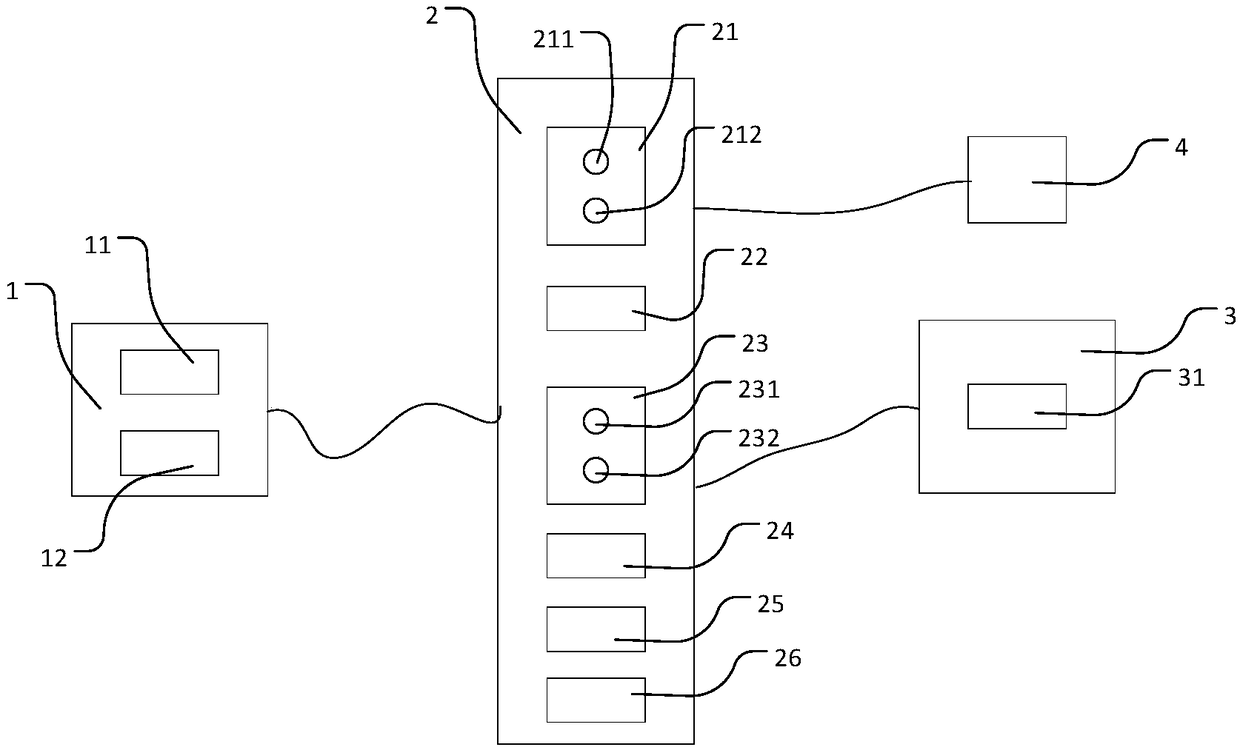
The invention discloses a control system of a 57 mm digitalized figure anti-aircraft gun and relates to the field of automatic control. A gun controller (1) is connected with a percussion device (2) and a firing angle displayer (3), the gun controller (1) is further connected with an operation control terminal (4), and the operation control terminal (4) is connected with a remote command center (5). The method is high in safety and operation efficiency, and capable of remote controlling in non-local places. The remote command center (5) conducts remote communication with the operation control terminal (4) and sends command information, after the operation control terminal (4) receives the command information, and the gun controller (1) sends a signal to control the percussion device (2) and the firing angle displayer (3) according to the control command sent by the operation control terminal (4). The gun controller (1) is arranged in the digitalized figure anti-aircraft gun. The control system is high in safety, low in accident occurrence frequency, simple in control method, high in operating efficiency, capable of using a plurality of control modes for controlling figure operation, and wide in application range.
Owner:COMP APPL TECH INST OF CHINA NORTH IND GRP
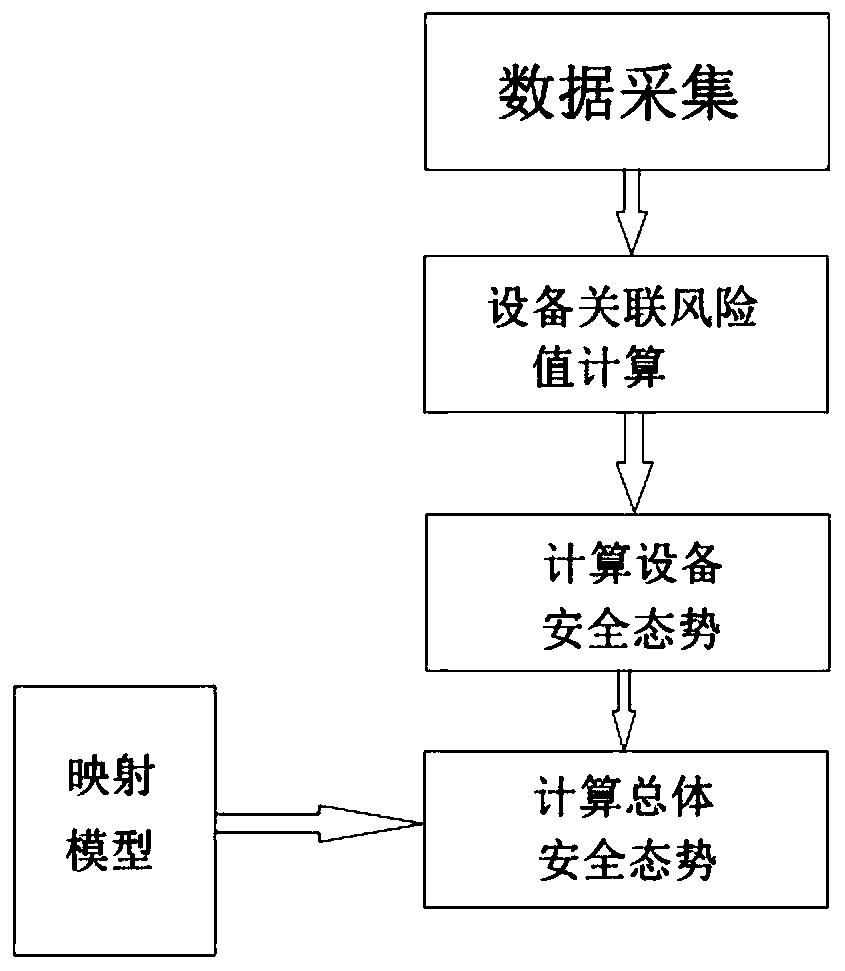
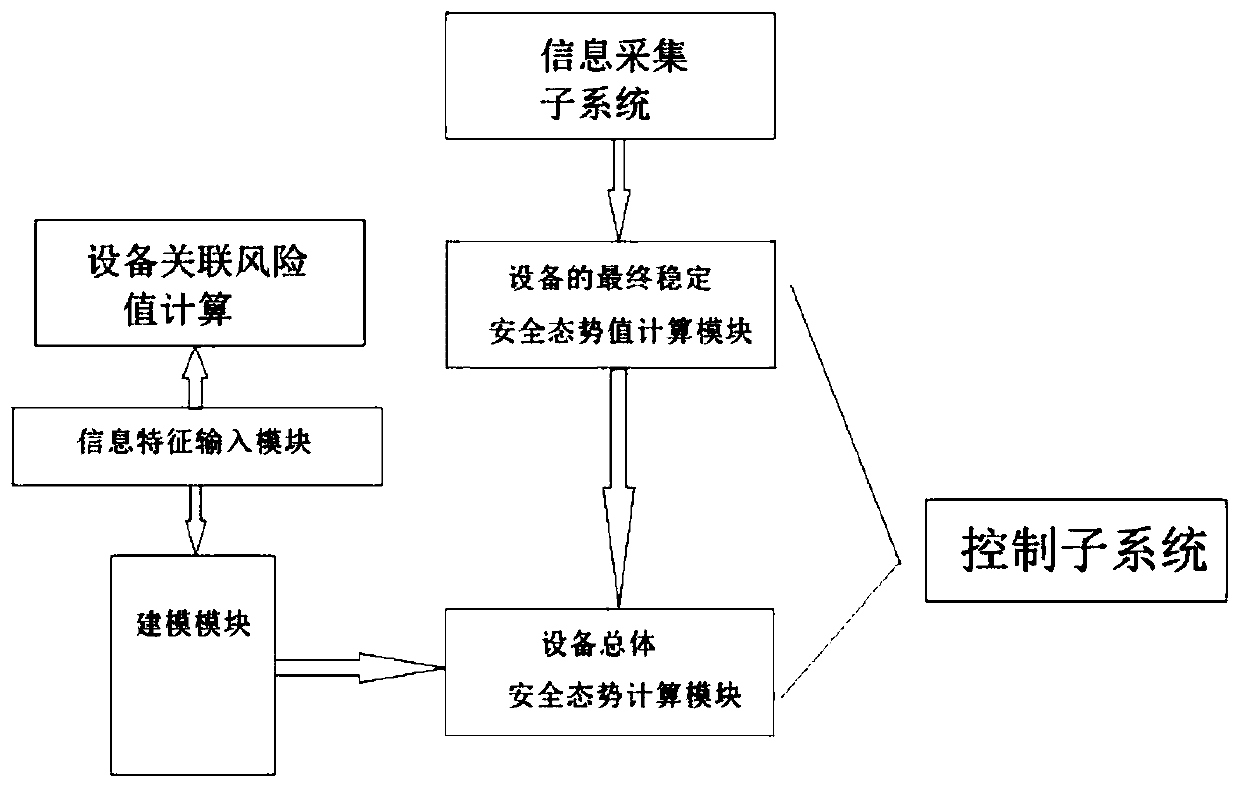
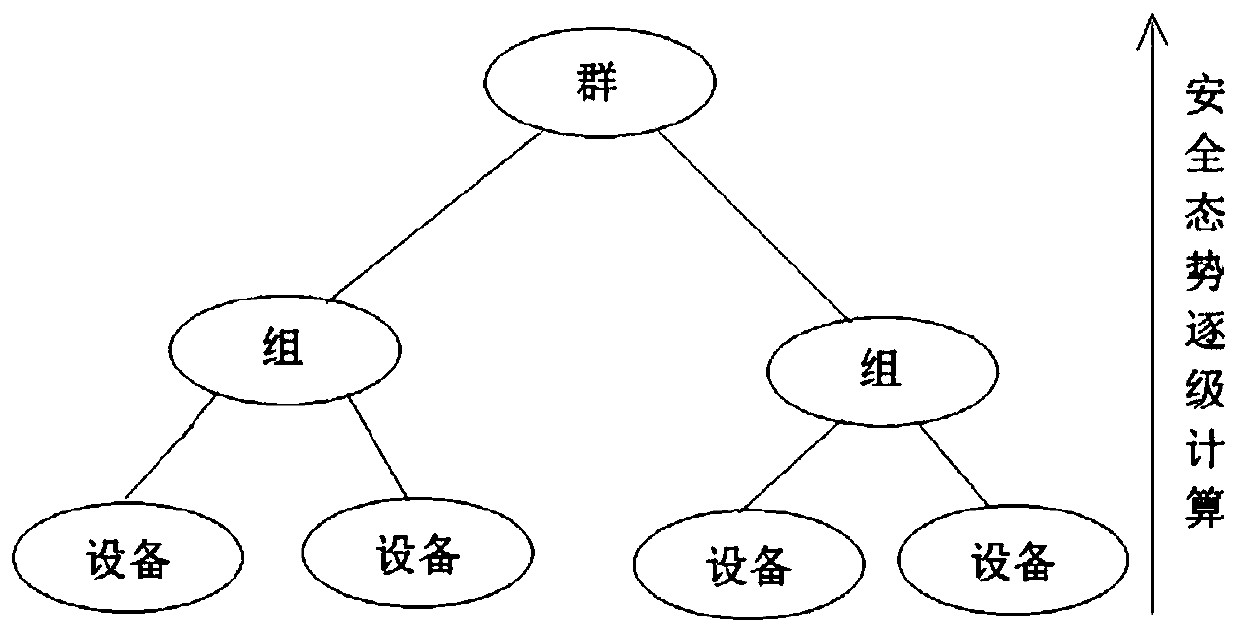
Industrial control system safety prediction method and system
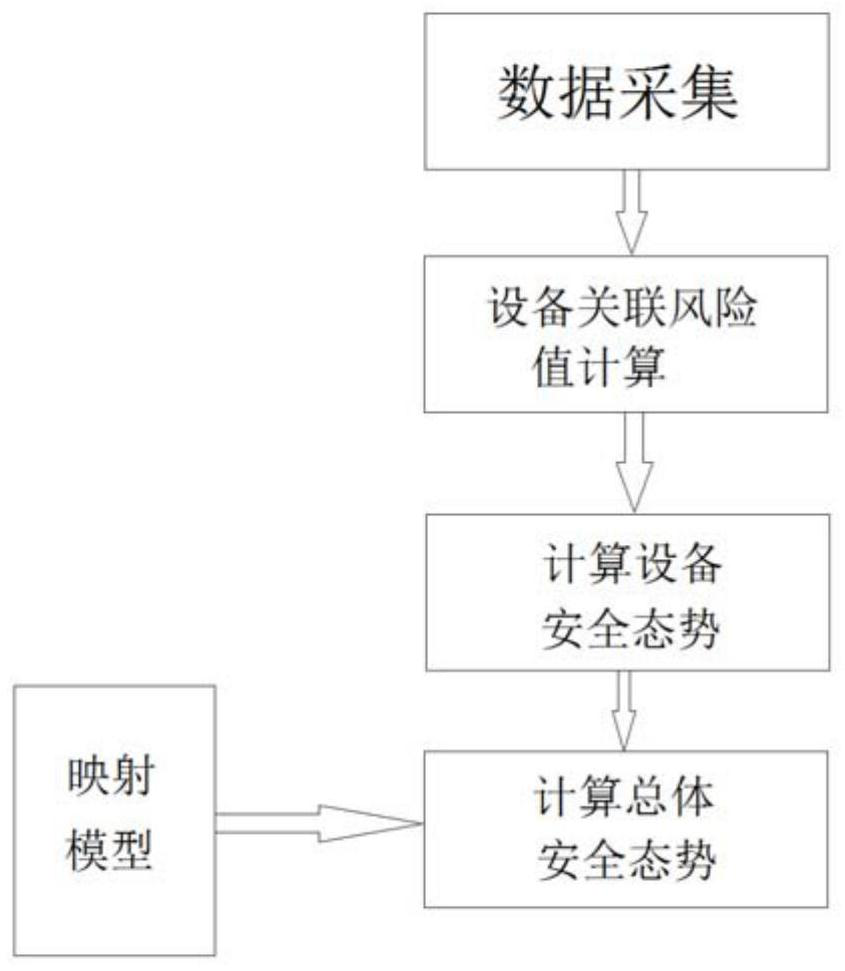
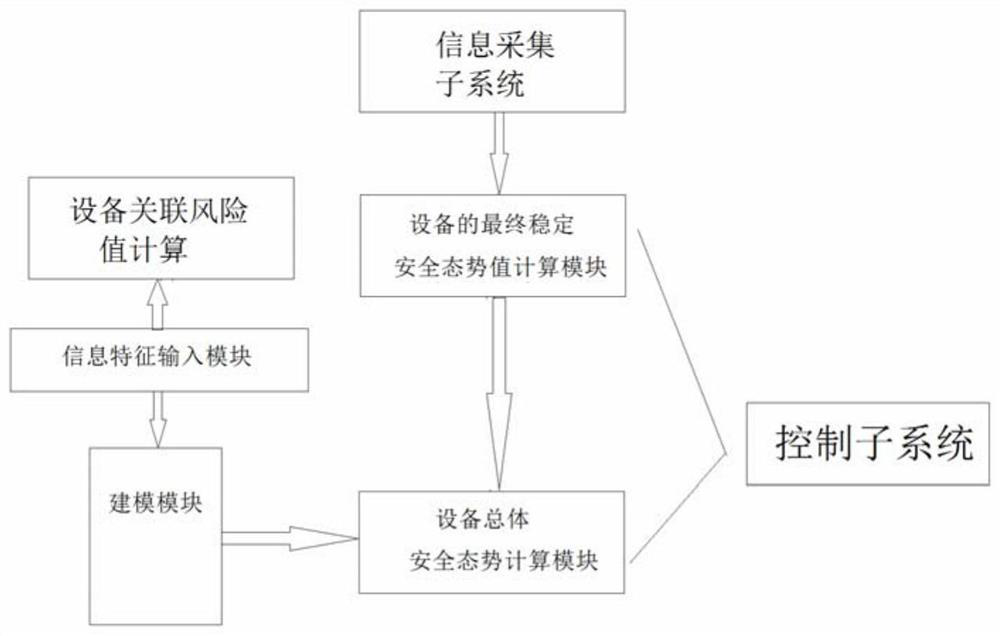
ActiveCN111381573ARealize early warning of faultsRealize early warningElectric testing/monitoringAcquisition apparatusData modeling
The invention provides an industrial control system safety prediction method and system; an industrial control system comprises equipment and a data acquisition device connected to the equipment, andthe method comprises the following steps: step 1, receiving historical data of each piece of equipment input by a user; 2, collecting equipment information, calculating an association risk value between two pieces of equipment, and storing the association risk value as an equipment association risk value table; 3, calculating a security situation value of each piece of equipment; and 4, obtainingthe overall security situation of each device, and judging whether to give an alarm or not. According to the invention, historical data is used for modeling to form a cascade system, the overall safety of the industrial control system can be predicted, and early discovery and early maintenance can be realized.
Owner:四川安控科技股份有限公司
Intelligent access control system
InactiveCN111063086AImprove securityEasy to operateIndividual entry/exit registersComputer hardwareInformation control
The embodiment of the invention provides an intelligent access control system. In the practical application, information of a user is acquired by an information acquisition device to obtain target information, a control device receives the target information and sends the target information to a background server, the background server judges the target information, if storage information matchedwith the target information is stored in the background server, that is, the user corresponding to the target information conforms to the door opening standard, the background server sends a door opening instruction to the control device when the user conforms to the door opening standard, the control device receives the door opening instruction and then controls a relay to be switched on, an electromagnetic lock is controlled to be opened after the relay is controlled to be switched on, the control device controls a motor to rotate at the moment, the motor drives a door body to rotate along the axis of the door body in the rotating process, the door body is opened at the moment, and automatic access control opening is achieved. Compared with the prior art, the intelligent access control system is high in safety and easy to operate.
Owner:西安帝凡合赢科技发展有限公司
Mine downhole power transformation chamber and construction method
InactiveCN107701209AMeet the installation and working environment requirementsGuaranteed uptimeUnderground chambersTunnel/mines ventillationAutomatic controlControl system
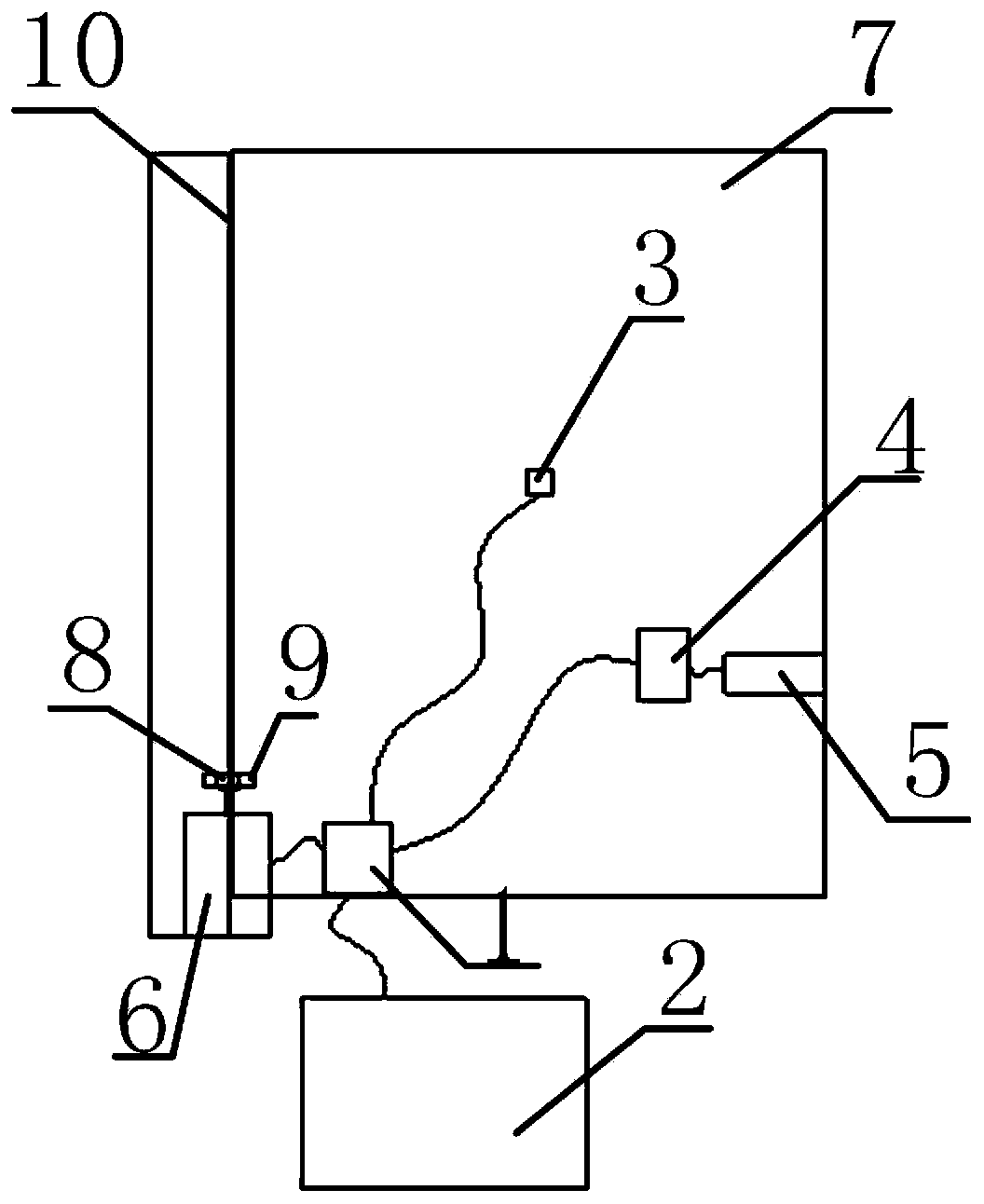
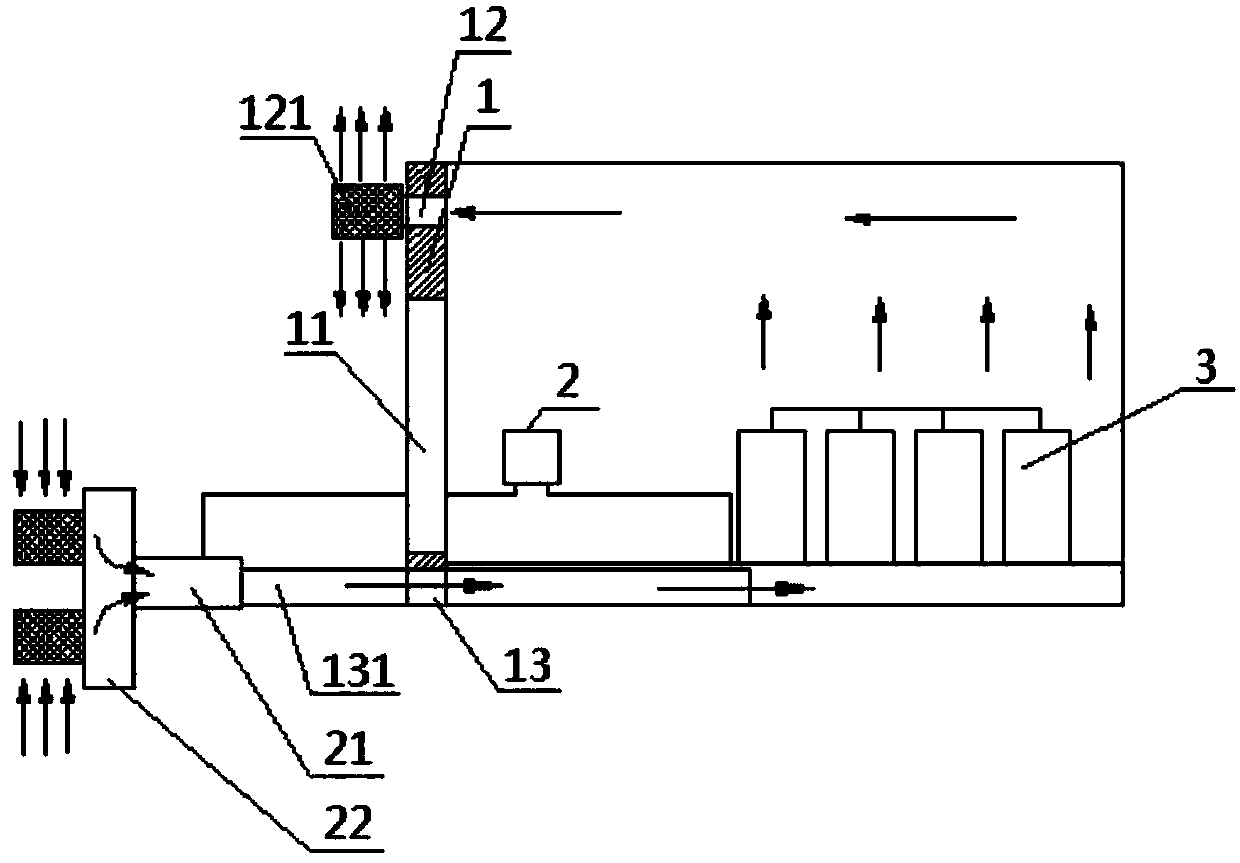
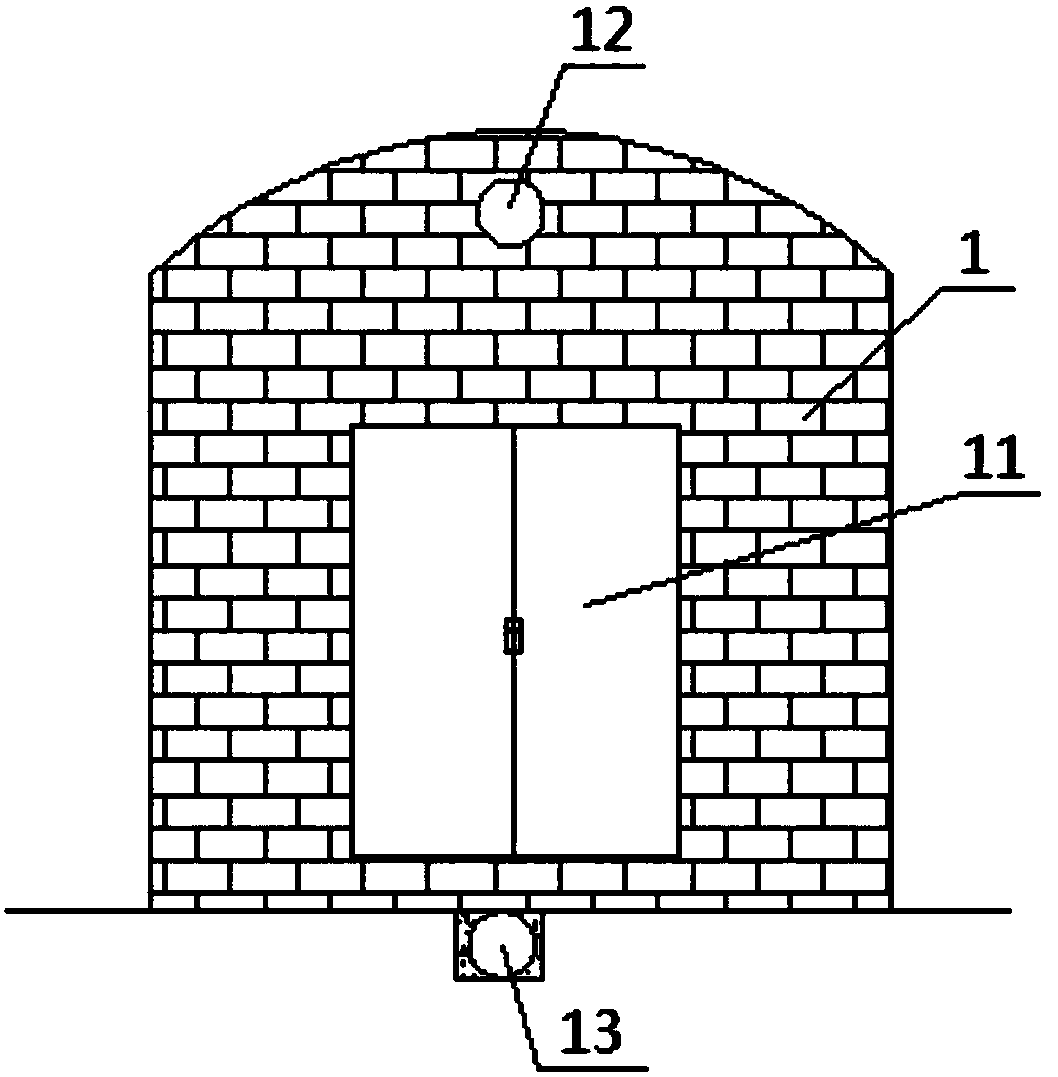
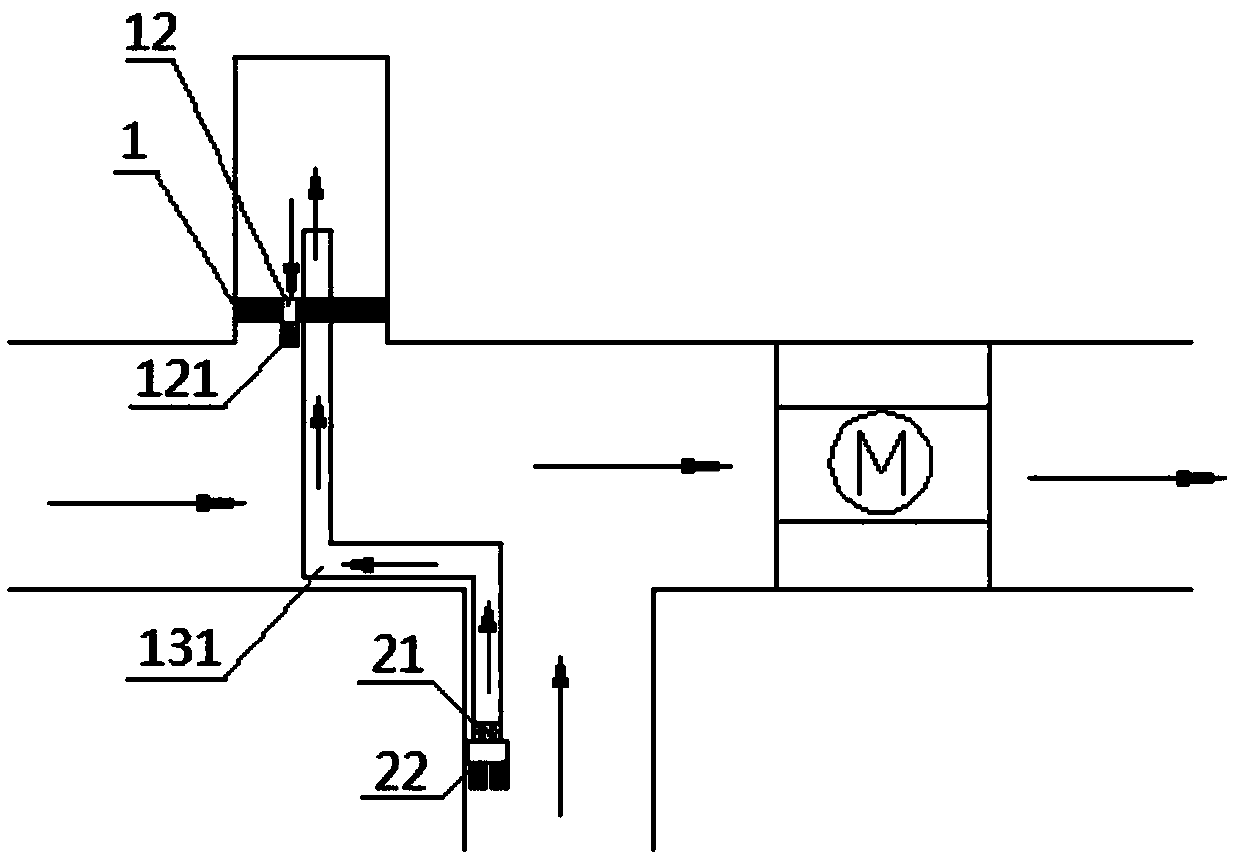
The invention provides a mine downhole power transformation chamber and a construction method. The mine downhole power transformation chamber comprises a chamber sealing retaining wall, an automatic control unit, an axial flow fan and an air purifying device. The power transformation chamber is a fully-sealed space, the chamber sealing retaining wall is arranged at the position where the chamber is connected with a mine tunnel, a chamber sealing door is arranged on the middle-lower portion of the chamber sealing retaining wall, an air outlet is formed in the upper portion of the chamber sealing retaining wall, and an air inlet is formed in the bottom of the chamber sealing retaining wall. The air purifying device is arranged at an inlet of the axial flow fan, and an outlet of the axial flow fan is connected to the air inlet. The automatic control unit is connected with the air purifying device. By implementing the mine downhole power transformation chamber and the construction method,the indoor environment of the power transformation chamber can meet the requirements of the mounting and working environment for mine downhole precision electrical appliance equipment, unattended operation and automatic control can be achieved, and a control system involved in the mine downhole power transformation chamber is high in safety, low in operation cost and capable of being reasonably applied and implemented in various complex mine downhole exploiting environments; and good popularization prospects are achieved.
Owner:GUIZHOU KAILIN GRP CO LTD
opc server security protection system
Owner:NORTHWESTERN POLYTECHNICAL UNIV
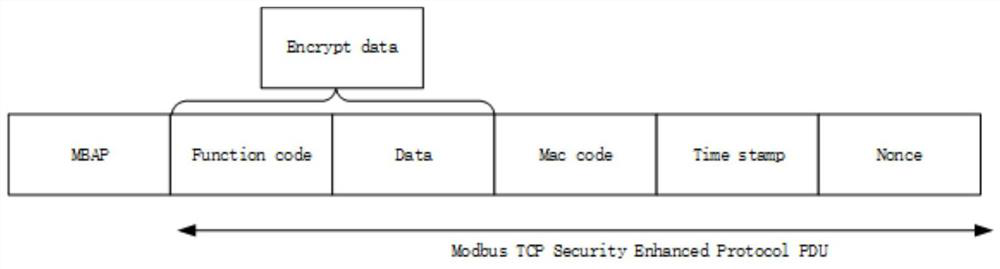
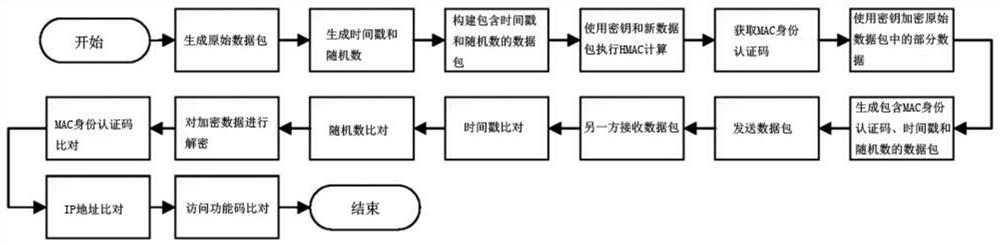
A modbustcp protocol security enhancement method and system
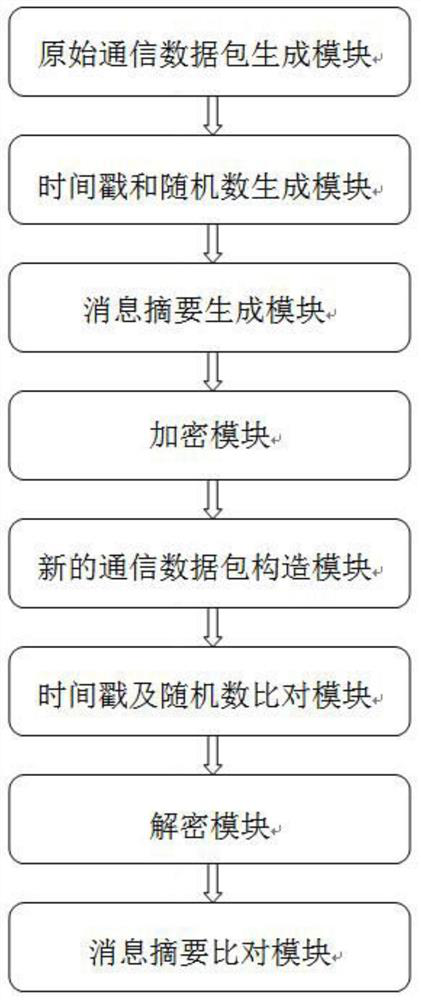
ActiveCN113472520BComprehensive and in-depth protectionLittle impact on transmission efficiencyEncryption apparatus with shift registers/memoriesUser identity/authority verificationConfidentialityTimestamping
The present invention relates to a ModbusTCP protocol security enhancement method and system. The present invention uses the HMAC algorithm in the ModbusTCP protocol to provide identity authentication and integrity protection for the communication data of the industrial control system at the same time, and adopts the SM4 packet whose encryption and decryption speed is faster than the asymmetric encryption algorithm. The cryptographic algorithm provides confidentiality for the communication data of the industrial control system, and uses time stamps plus random numbers combined with random number set tables to prevent replay attacks at a finer granularity; on the premise of ensuring usability, the present invention comprehensively improves the industrial use of the ModbusTCP protocol. Control system security.
Owner:SHANDONG COMP SCI CENTNAT SUPERCOMP CENT IN JINAN
A robot control system
ActiveCN106426184BCost-effectiveHigh speed switchingProgramme-controlled manipulatorControl mannerDual core
The invention discloses a robot control system which comprises a dual-core processor, wherein the dual-core processor comprises an advanced reduced instruction set computer machine (ARM) processor and a digital signal processor (DSP). According to the robot control system, an ARM+DSP control strategy is adopted; a conventional control mode of industrial computer PC+movement control card+servo drive+servo motor is replaced; an ARM is responsible for movement planning and track planning of a robot; the DSP is responsible for dynamic and kinematic calculation of the robot, the strong calculation performance of the DSP and the peripheral control property of the ARM are sufficiently utilized, and due to the function distribution, the expense of a main control chip can be effectively reduced, a relatively great amount of resources can be used for controlling the security and the precision of the control system, and the cost performance can be greatly improved; the robot control system has EtherNet and pulse analog quantity control modes which can be selected by users, and a servo drive and a servo motor applicable to multiple control modes are provided, so that control methods can be conveniently switched by the users, and relatively good universality can be achieved.
Owner:GUANGZHOU INST OF ADVANCED TECH CHINESE ACAD OF SCI +1
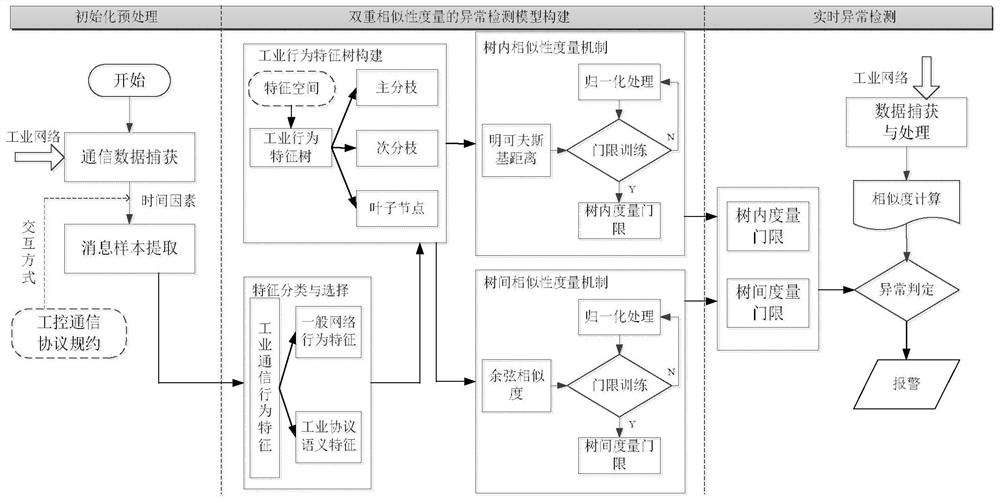
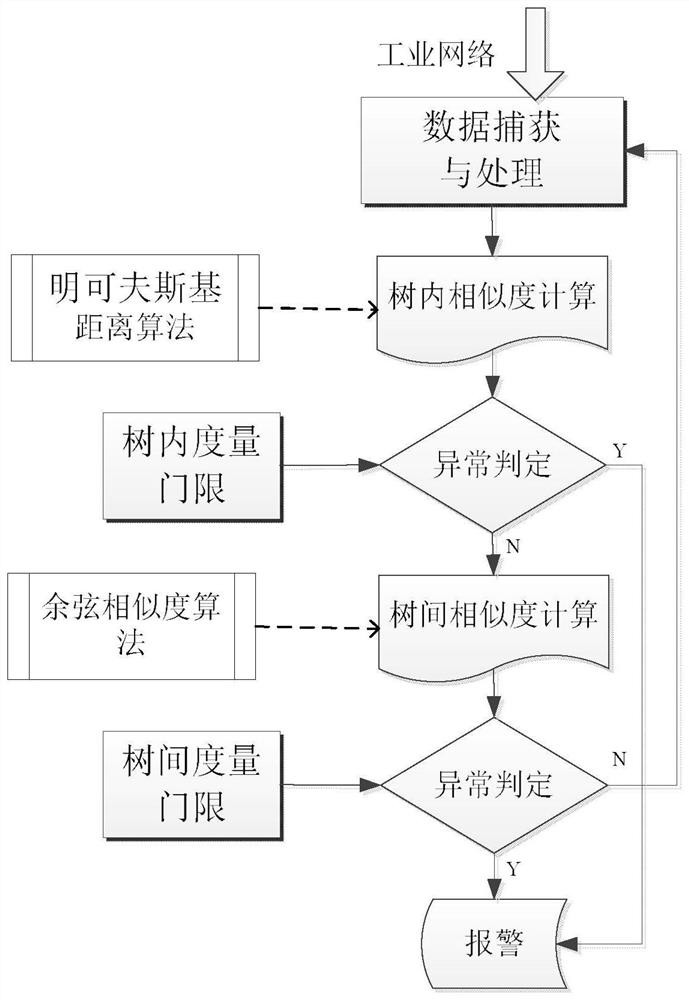
A Method of Industrial Communication Anomaly Detection Based on Dual Similarity Measures
ActiveCN110266680BComprehensive anomaly detectionImprove anomaly detection performanceTransmissionReal time analysisNetwork behavior
An industrial communication anomaly detection method based on dual similarity measures. This method analyzes the communication data in the industrial control network and extracts the industrial communication behavior characteristics according to the industrial communication interaction mode and the industrial protocol specification. Based on these characteristics, the behavior characteristic tree is constructed, respectively. Intra-tree similarity measurement and inter-tree similarity measurement, so as to discover abnormal communication conditions in industrial control networks. Through the above method, the present invention can comprehensively consider general network behavior characteristics and industrial protocol semantic characteristics, and detect industrial communication abnormalities caused by malicious attacks or misoperations and generate alarms through real-time analysis and abnormal judgment of industrial communication data to ensure Industrial control system security.
Owner:沈阳邦粹科技有限公司
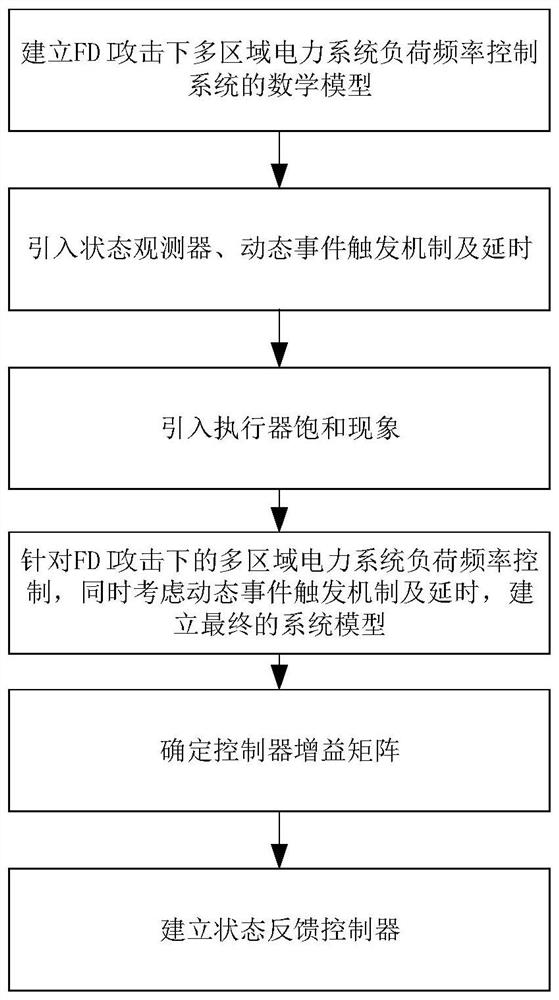
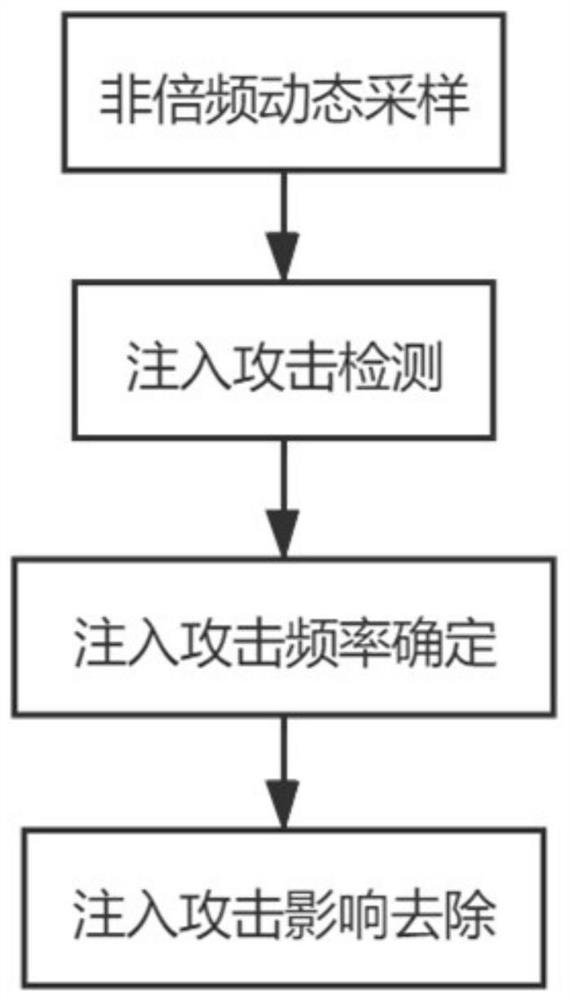
Control system security dynamic event trigger control method under false data attack
PendingCN114709841AAvoid transmissionRelieve pressureContigency dealing ac circuit arrangementsPower oscillations reduction/preventionAttackActuator saturation
A control system security dynamic event trigger control method under false data attack designs a false data injection attack model with an observer module, a sensor module, a controller module and an actuator saturation module, and introduces a dynamic event trigger mechanism in consideration of limited communication network bandwidth resources. An improved event triggering scheme is presented. The main idea of the event triggering mechanism is to detect whether a current sampling signal satisfies a preset triggering algorithm, if so, the sampled signal is transmitted to the controller, otherwise, the sampled signal is abandoned. The method has the advantages that the improved event triggering scheme ensures that the system can operate safely and stably on the premise of global stability, meanwhile, transmission of redundant signals is reduced, the pressure of network transmission is relieved, and bandwidth resources are saved. In addition, the introduced observer module and actuator saturation module are closer to the operating environment and requirements of the power grid, the network control performance is ensured, and the expected control effect is achieved.
Owner:YINGKOU ELECTRIC POWER SUPPLY COMPANY OF STATE GRID LIAONING ELECTRIC POWER SUPPLY +1
A remote wireless control system of a cutting and separating device and its application method
The invention discloses a remote wireless control system of a cutting and separating device and a method for using the same. The invention relates to the technical field of remote wireless control of a wireless cutting and separating device. The remote wireless control system of a cutting and separating device includes a signal receiver and a signal transmitter. The input terminal of the signal receiver is connected to the output terminal of the signal transmitter; the signal transmitter is composed of a power switch 1, a control panel 1, an antenna 1, an enabling switch 1 and a battery compartment 1; the control panel 1 includes communication detection, charging, detonation, Check mark, power 0~A and channel function; the signal receiver is composed of power switch 2, control panel 2, antenna 2, enabling switch 2, battery compartment 2 and wiring terminals; control panel 2 includes check mark, power 0~A And the channel function; the beneficial effect of the present invention is: by adding double switches for protection, the safety performance of the remote wireless control system is improved, and loopholes are avoided.
Owner:苏州信卓胜电子科技有限公司
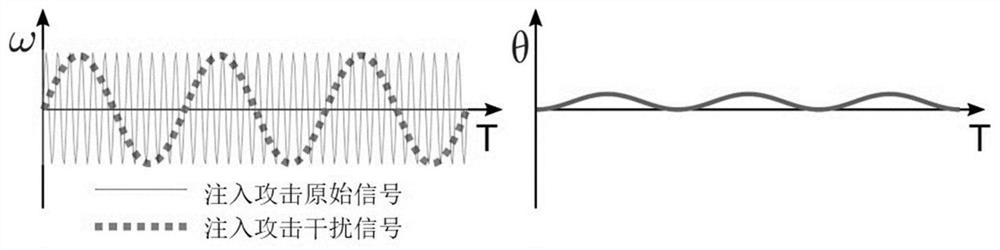
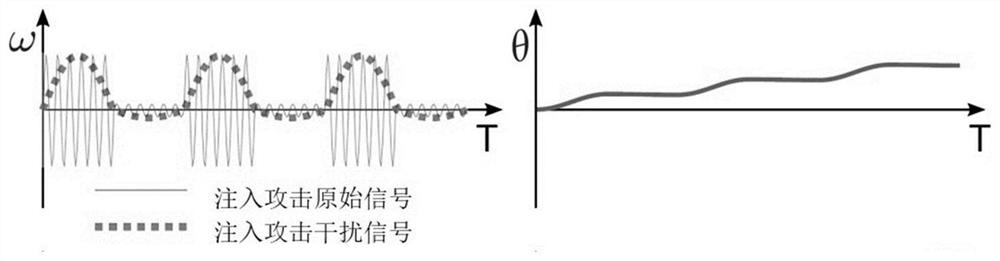
Method and system for detecting and defending resonance hidden injection attack of inertial sensor
ActiveCN112964254AImprove integrityProtection securityNavigation by speed/acceleration measurementsHigh level techniquesFrequency spectrumAccelerometer
The invention discloses a method and system for detecting and defending a resonance hidden injection attack of an inertial sensor, and belongs to the field of mobile sensing and control system security. According to the method, on the basis of the characteristic that spectrum aliasing exists in injection attacks, motion is sampled at multiple sampling rates, and whether an attack exists or not is judged; and if the attack exists, with the overlapping of the resonance frequency of the inertial sensor and the Nyquist region under different sampling rates comprehensively considered, an attack frequency is calculated, and the separation of the motion information and attack signals is realized. According to the method, extra hardware does not need to be added, the method is suitable for outbound packaged gyroscopes and accelerometers, the injection attack of the inertial sensor using sound wave resonance is conveniently, practically and efficiently detected, the influence of the attack is eliminated on the premise of ensuring the integrity of motion data, and the safety and reliability of a motion measurement and driving system can be improved.
Owner:XI AN JIAOTONG UNIV
A smart home control system
ActiveCN108427303BImprove securityAdd funComputer controlTotal factory controlHome useInformation control
The invention provides a smart home control system. The control system comprises a control device, an auxiliary device and a plurality of household devices connected with the control device; the auxiliary device is used for collecting identity information and action information, and the control device judges whether to make an operation permission for operating the household devices available according to the identity information and determines an operation instruction for the household devices according to the action information when the operation permission is available. According to the smart home control system, before an operator operates the household devices, the smart home control system judges the identity information of the operator and makes the operation permission available tothe operator with the correct identity information, and the operator can operate the household devices in the smart home control system through the action information; the safety of the smart home control system is improved, and meanwhile the operator can control the household devices at his / her will through action instead of using a remote control to operate the household devices.
Owner:GREE ELECTRIC APPLIANCES INC
A method and system for predicting the security of an industrial control system
ActiveCN111381573BRealize early warning of faultsRealize early warningElectric testing/monitoringAcquisition apparatusData modeling
The present application provides a method and system for predicting the safety of an industrial control system. The industrial control system includes equipment and a data acquisition device connected to the equipment. The method includes the following steps: Step 1: Receive the information of each equipment input by the user Historical data; Step 2: Collect device information, calculate the associated risk value between two devices, and save it as a device associated risk value table; Step 3: Calculate the security situation value of each device; Step 4: Obtain the overall security of each device situation, and judge whether to call the police. Through the present invention, the cascade system is formed by using historical data modeling, and the overall safety of the industrial control system can be predicted, so as to achieve early detection and early maintenance.
Owner:四川安控科技股份有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com