Control system security dynamic event trigger control method under false data attack
A false data attack and event-triggered technology, applied in the field of power systems, can solve problems such as excessive data consumption, excessive consumption of network resources, and less consideration of actuator execution capabilities, so as to save network communication resources, reduce pressure, and avoid transmission.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0083] This example is implemented under the great premise of the technical solution of the present invention, and provides a detailed implementation scheme and a specific operation process, but the protection scope of the present invention is not limited to the following examples.
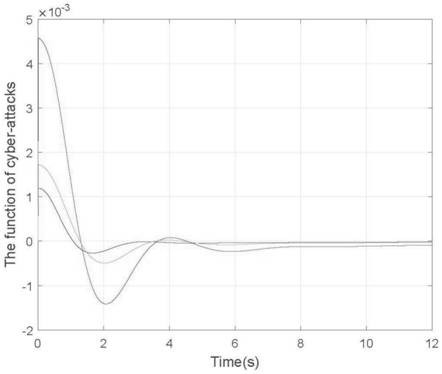
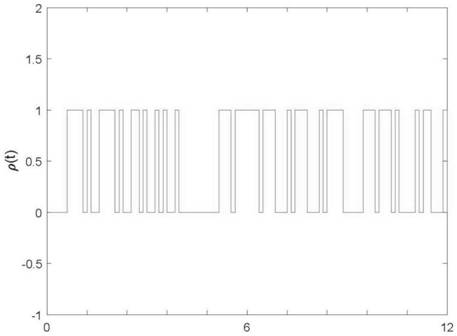
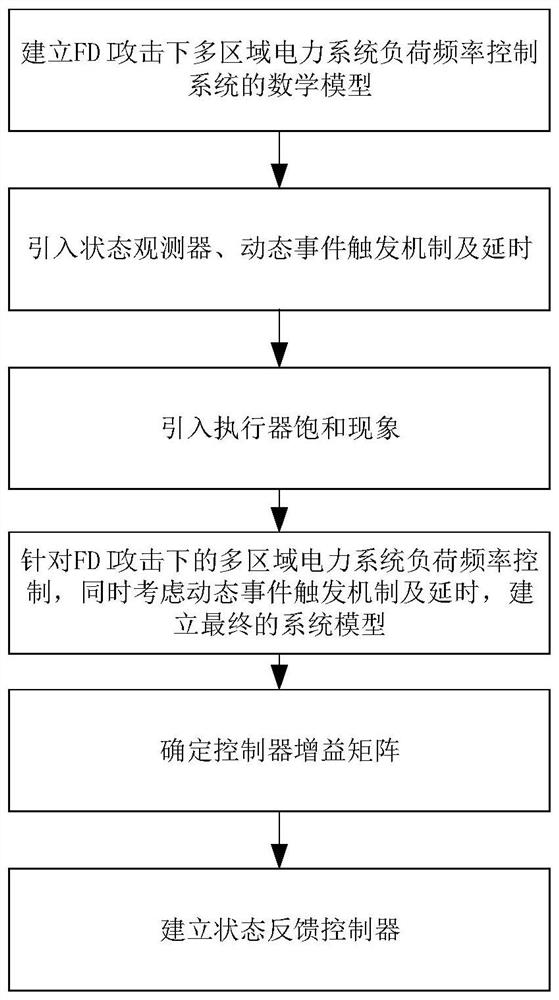
[0084] like figure 2 The present invention considers the linear control model of the three-region interconnected power system. The structure of the power system mainly includes a turbine, a governor, a generator, a power system synchronous vector measurement unit (PMU), a sensor, an event generator, a holder, and a controller. It is composed of actuators, and the PMU is used for dynamic monitoring on the back street of the generator; a dynamic event trigger controller is introduced behind the sensor, and the control process is operated by the event generator; if the dynamic trigger strategy is satisfied, the event generator will execute the trigger. That is, non-uniform sampling is performed, and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com